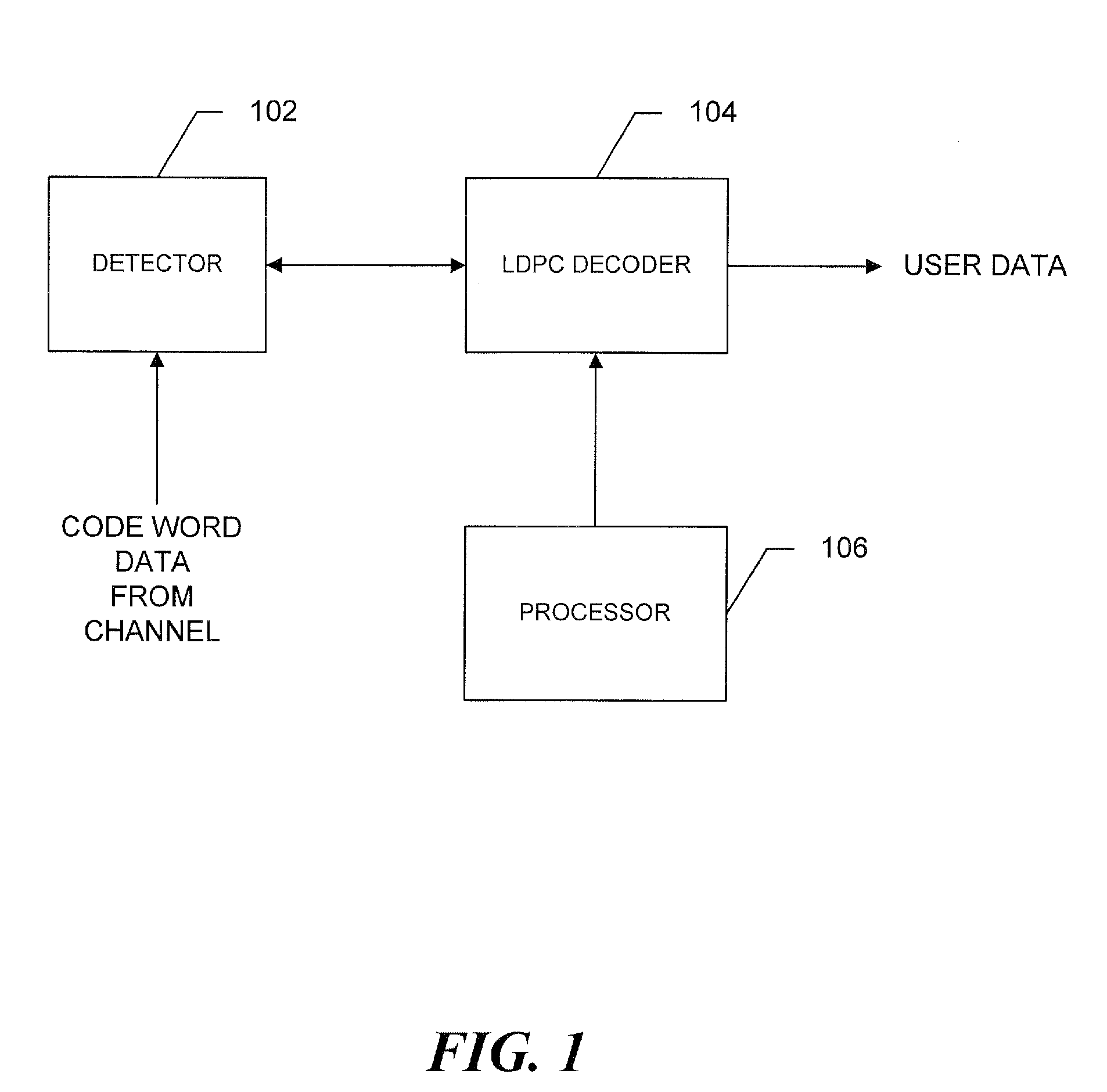
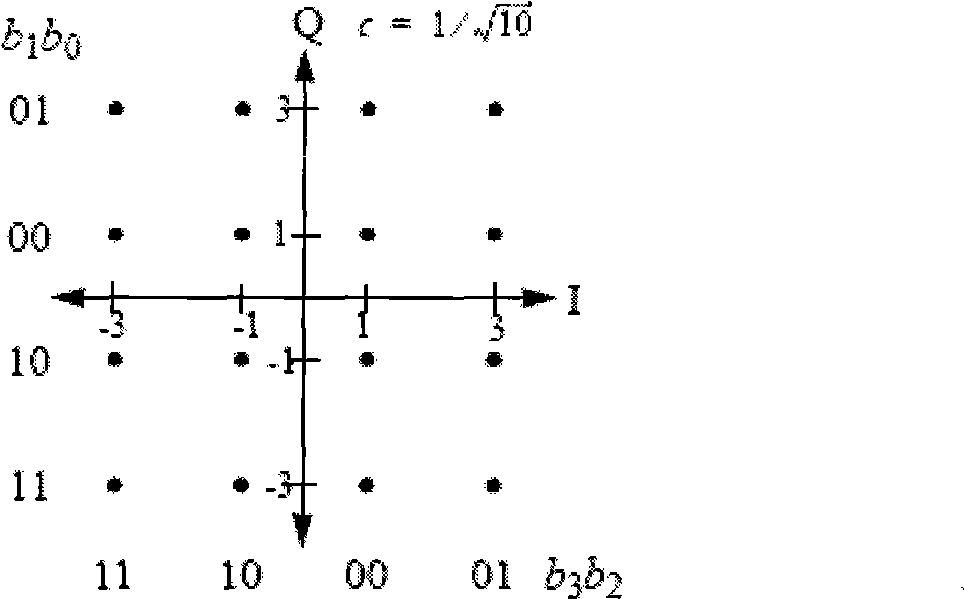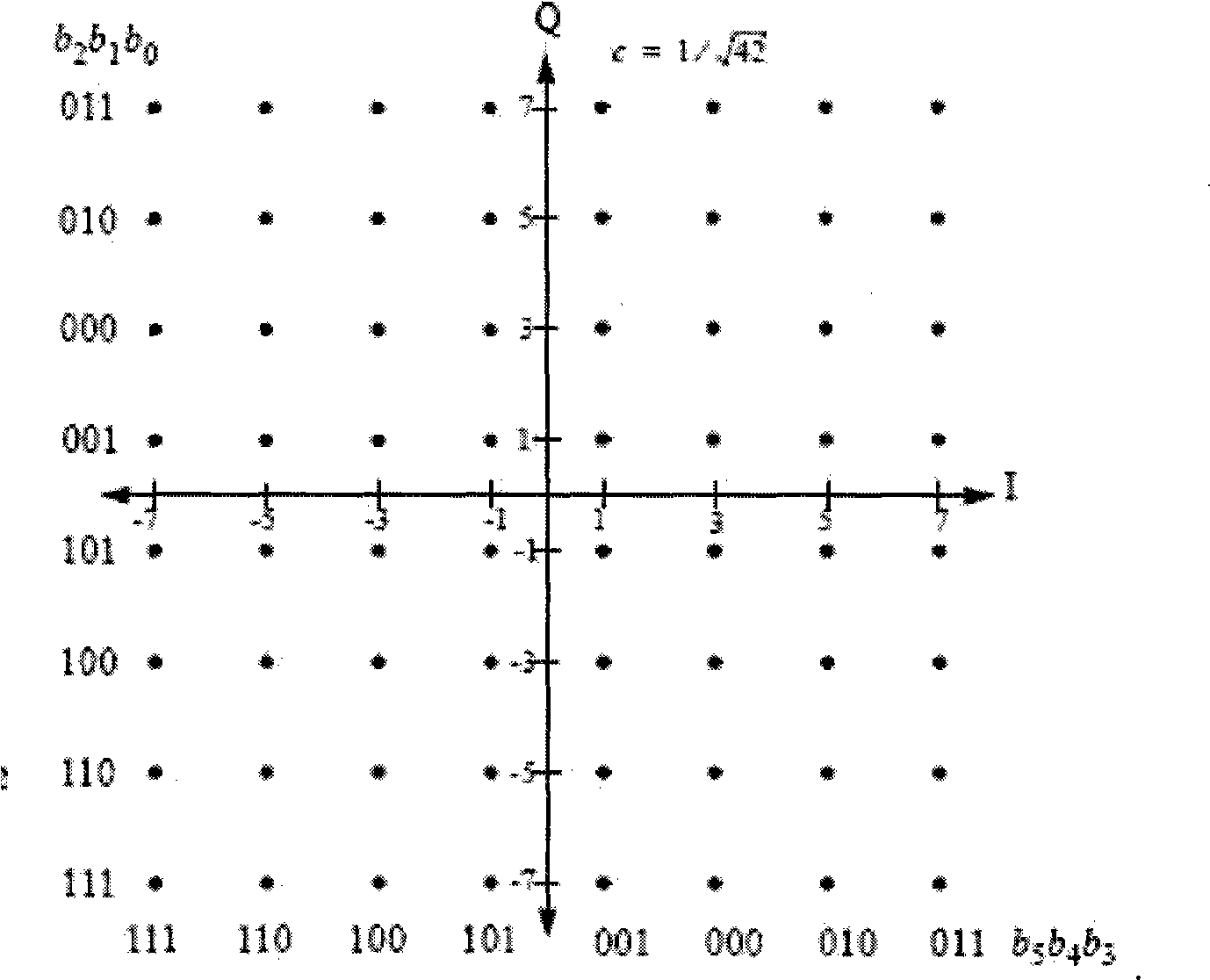Patents
Literature
367 results about "Degree distribution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
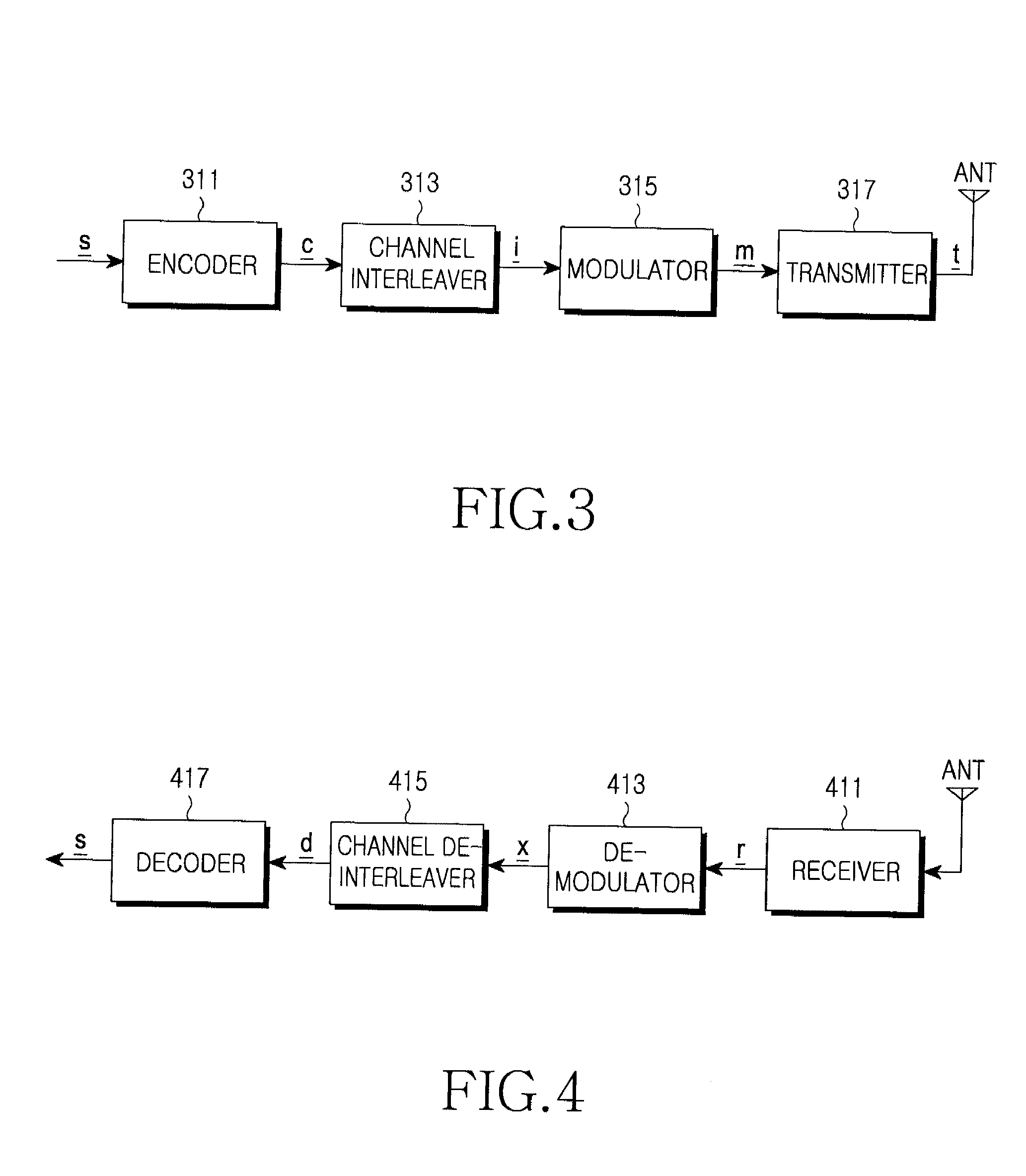
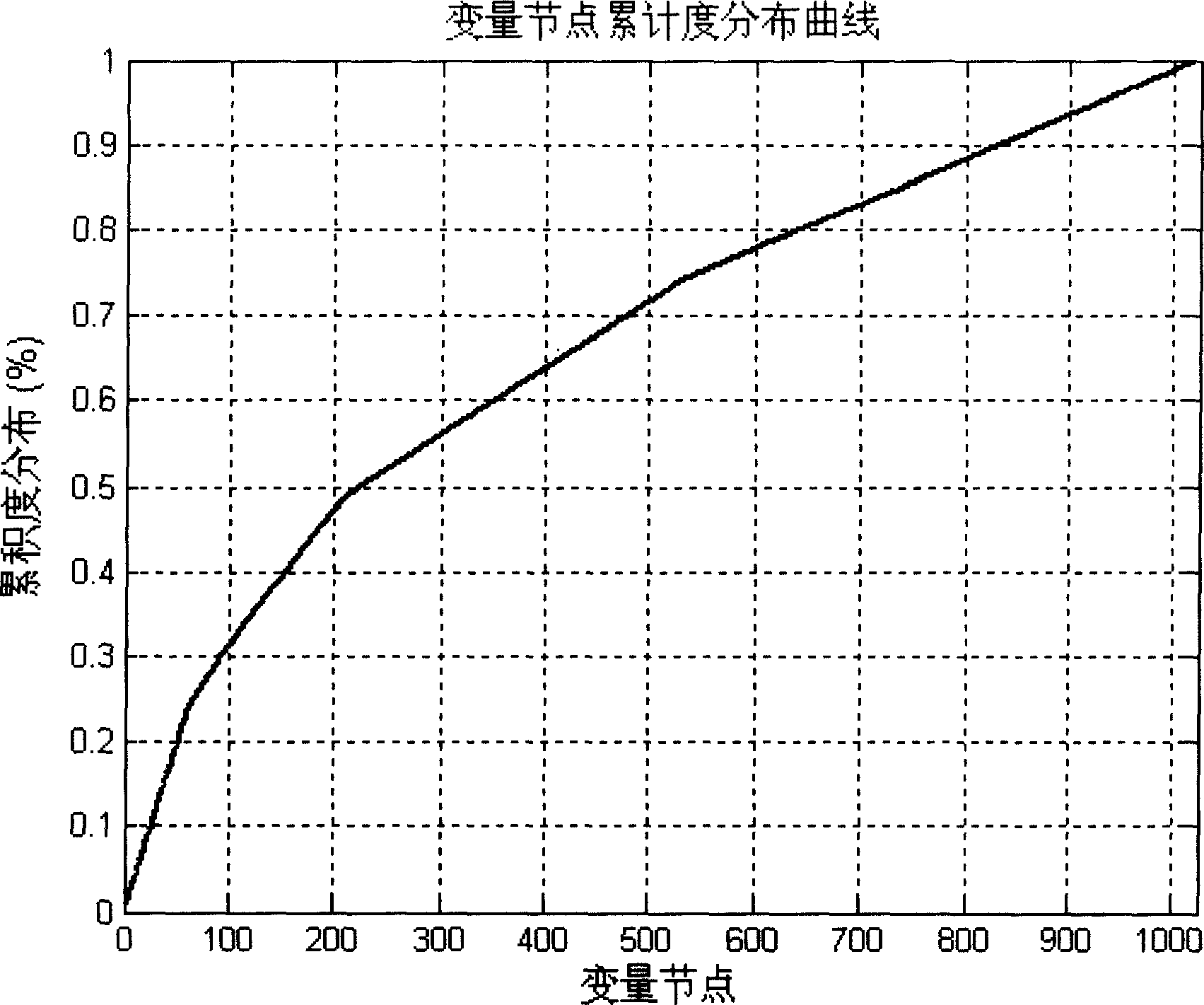
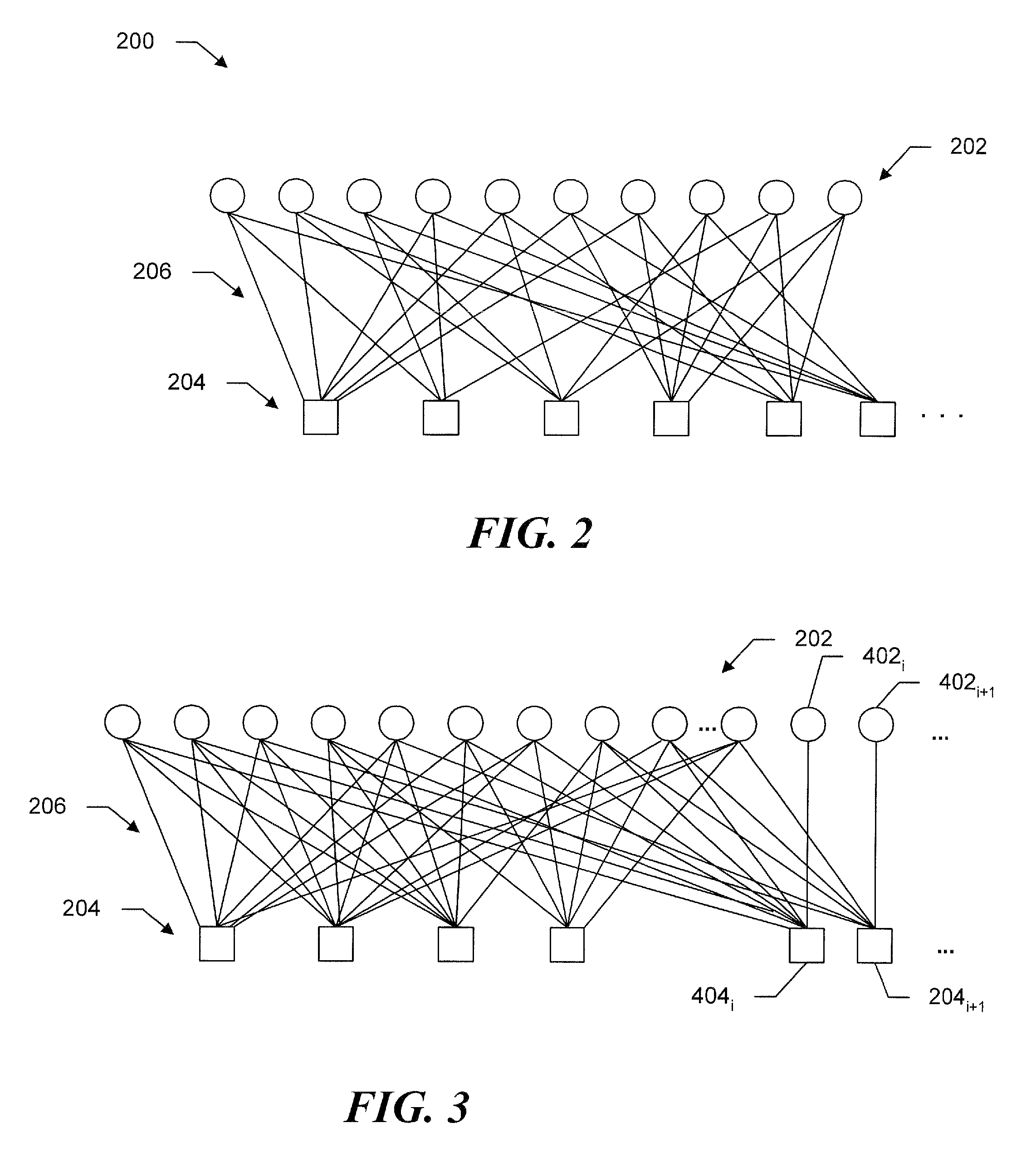
In the study of graphs and networks, the degree of a node in a network is the number of connections it has to other nodes and the degree distribution is the probability distribution of these degrees over the whole network.
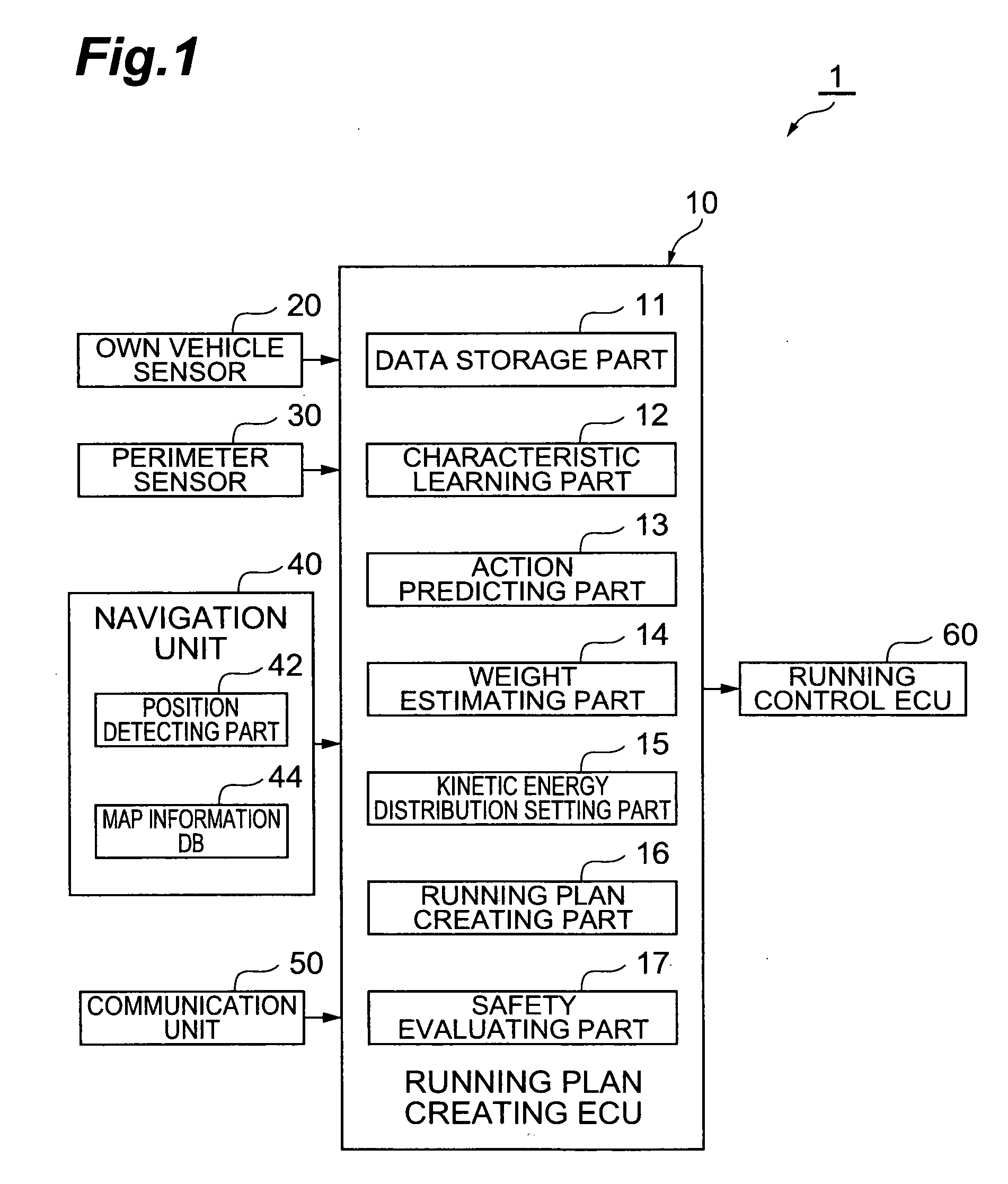
Running plan creating apparatus
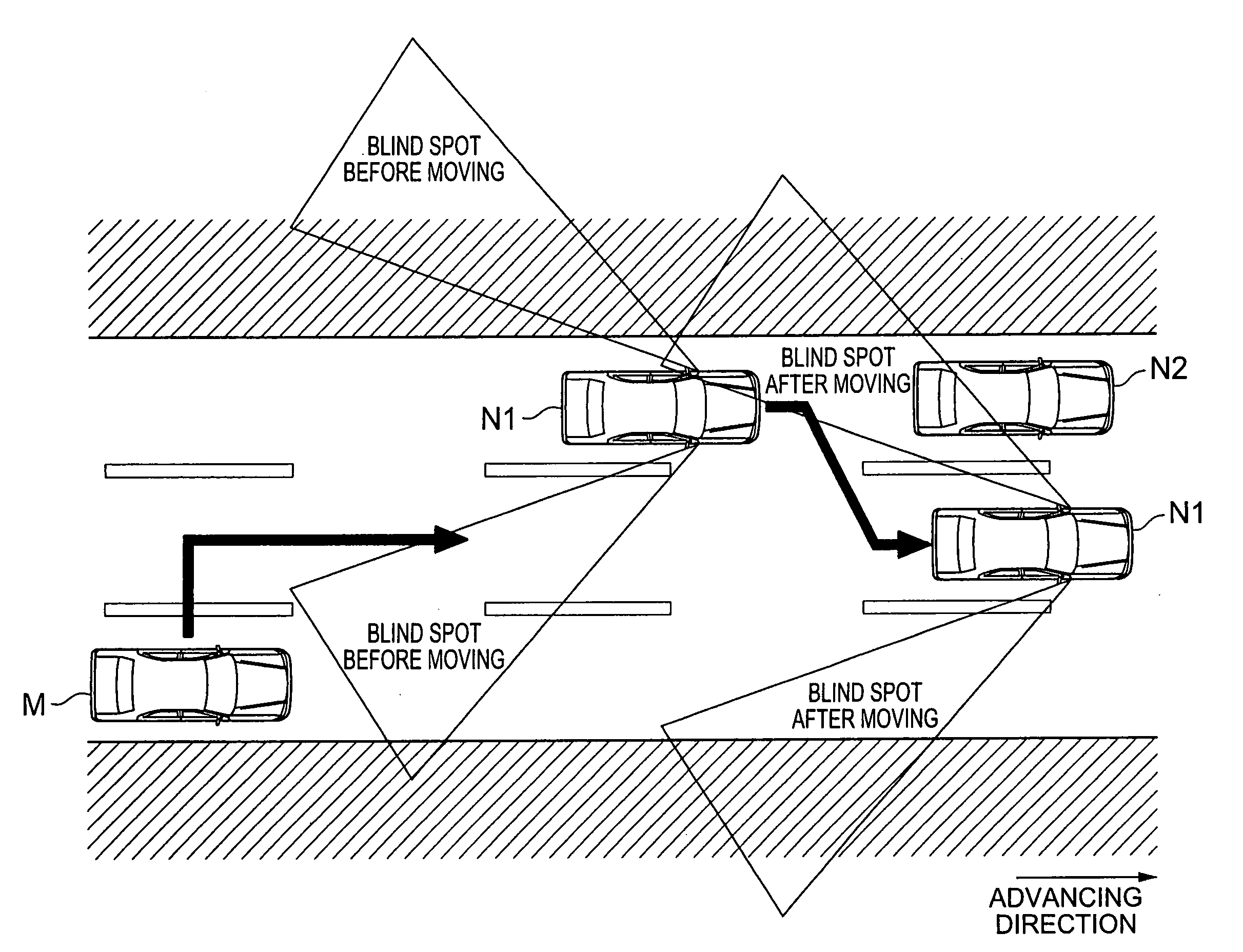
InactiveUS20090037088A1Degree of riskPotential riskAnalogue computers for vehiclesAnalogue computers for trafficEngineeringDegree distribution
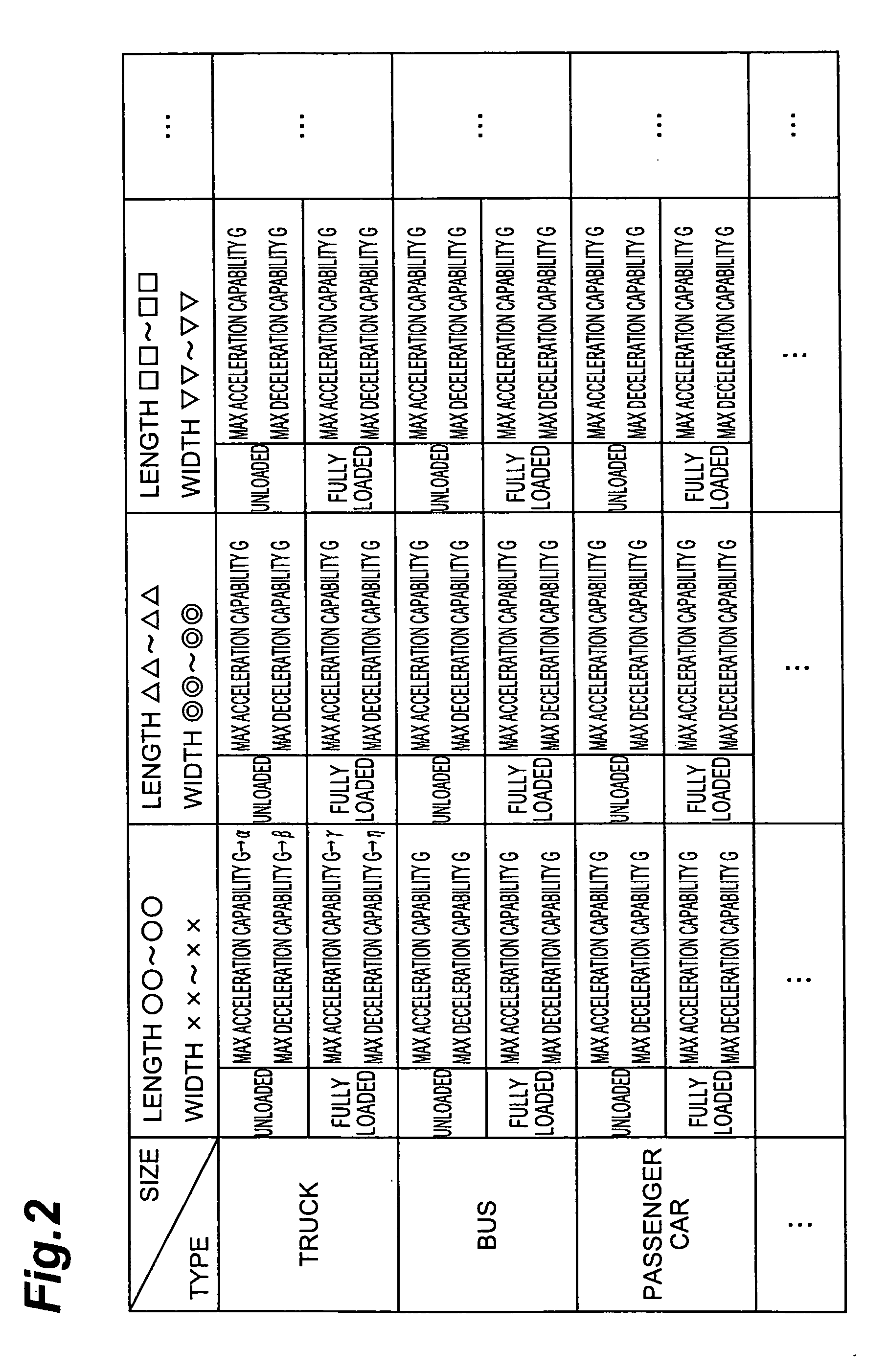
A running plan creating apparatus for creating a running plan including position information of a vehicle at each time comprises road information acquiring means for acquiring road information concerning a running path for the vehicle to run, action predicting means for predicting positions and speeds of other vehicles running about the vehicle at each time by utilizing the road information, characteristic information acquiring means for acquiring characteristic information in each of the other vehicles, risk degree estimating means for estimating respective degrees of risk of the other vehicles by utilizing the characteristic information, risk degree distribution setting means for setting a risk degree distribution at each time on the running path by utilizing the road information and the positions and degrees of risk of the other vehicles, and running plan creating means for creating the running plan of the vehicle by utilizing the risk degree distribution.
Owner:TOYOTA JIDOSHA KK
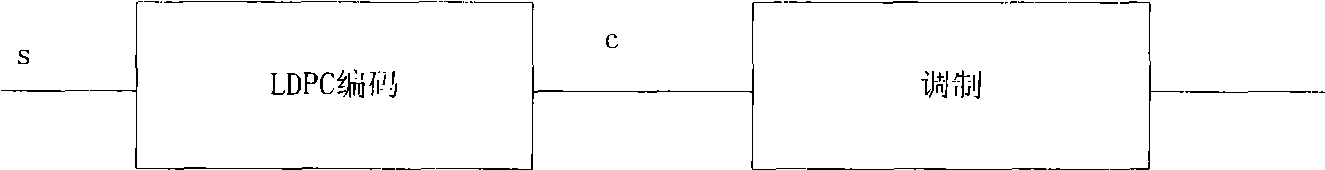
LDPC code encoding modulation method and apparatus
ActiveCN101488819APremium Coded Modulation GainError preventionError correction/detection using multiple parity bitsLow-density parity-check codeTheoretical computer science
The invention embodiment provides a coded modulation method for low density parity check code, a low density parity check code coded processing can be performed for an information sequence to obtain a code word, and the interweave processing can be performed for the code word, then the modulated processing can be performed for the code word by interweave processing; meanwhile, the invention embodiment also provides a coded modulation apparatus for the low density parity check code. The technical scheme disclosed by the invention embodiment is based on the importance of low density parity check code degree distribution, and the different bits on a star map in high order modulation have different reliabilities, and the excellent coded modulation gain can be obtained.
Owner:XFUSION DIGITAL TECH CO LTD
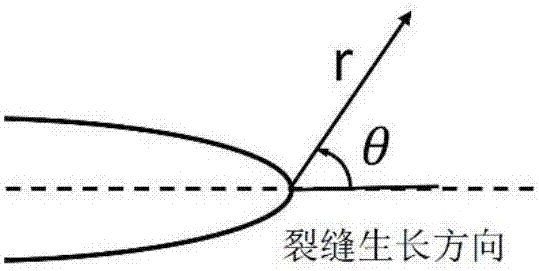
Simulating method of forming process of unconventional oil and gas reservoir hydraulic fracturing complex fracture net
ActiveCN107545113AAccurate guidanceThe process is convenient and fastFluid removalSpecial data processing applicationsHydraulic fracturingUnconventional oil
The invention discloses a simulating method of the forming process of an unconventional oil and gas reservoir hydraulic fracturing complex fracture net. The method includes the steps of a, reestablishing natural fracture distribution, estimating the properties of natural fractures, obtaining rock mechanical information and stratum stress information of a stratum from log data or a geological model, and obtaining a data file related to the well factory construction process; b, inputting the obtained parameters in an established natural fractured reservoir fracturing model coupling a well cylinder, fractures and the stratum; c, conducting numerical value solving on the model to obtain after-fracturing information such as fracture forms, opening degree distribution and pressure intensity distribution; d, analyzing the fracturing effect through a model calculating result, and making a preparation for numerical value simulation of the later-period production process. The fractured reservoirfracturing numerical value simulating method coupling the well cylinder flowing, the fracture deformation expanding, the multi-state natural fractures and the flowing of fluid in the fractures can quantitatively analyze the form of the unconventional reservoir segmented volume fracture net and is an effectively means for evaluating and optimizing the fracturing scheme.
Owner:SOUTHWEST PETROLEUM UNIV
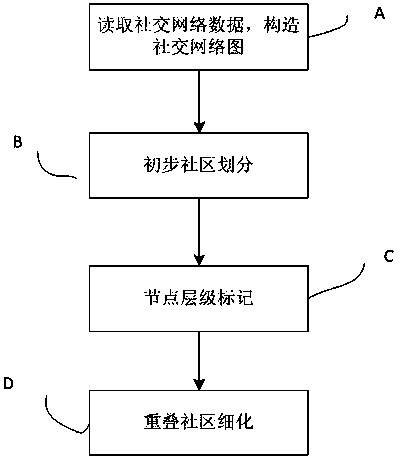
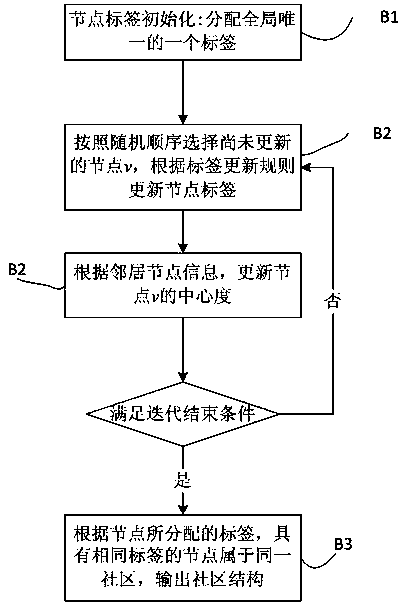
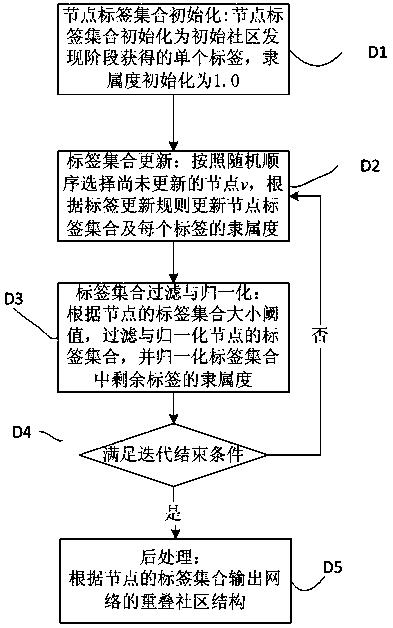
Multi-label propagation discovery method of overlapping communities in social network
InactiveCN103729475ARealize high-precision excavationImprove stabilityData processing applicationsWebsite content managementNODALSocial graph
The invention relates to the technical field of a social network and particularly relates to a multi-label propagation discovery method of overlapping communities in the social network. The multi-label propagation discovery method comprises the following steps: reading data of the social network, constructing a social network diagram which adopts social network users as nodes and user relationship as edges; according to the social network diagram, carrying out preliminary community division of the social network, and carry outing community discovery by adopting a label propagation method of comprehensively considering the node centrality and label-degree distribution constraint to obtain a non-overlapping community structure; marking the levels of the nodes according to the obtained non-overlapping community structure and the centrality value of the nodes in the communities; and according to the levels of the nodes, calculating label propagation gain among the nodes with different levels, and carrying out overlapping node mining by utilizing the multi-label propagation to obtain the overlapping community structure of the social network. The multi-label propagation discovery method has the advantages that the overlapping community structure in the social network can be effectively mined, the accuracy and the efficiency of community detection are favorably improved, and the method can be applicable to the fields of target group mining, precision marketing and the like.
Owner:FUZHOU UNIV
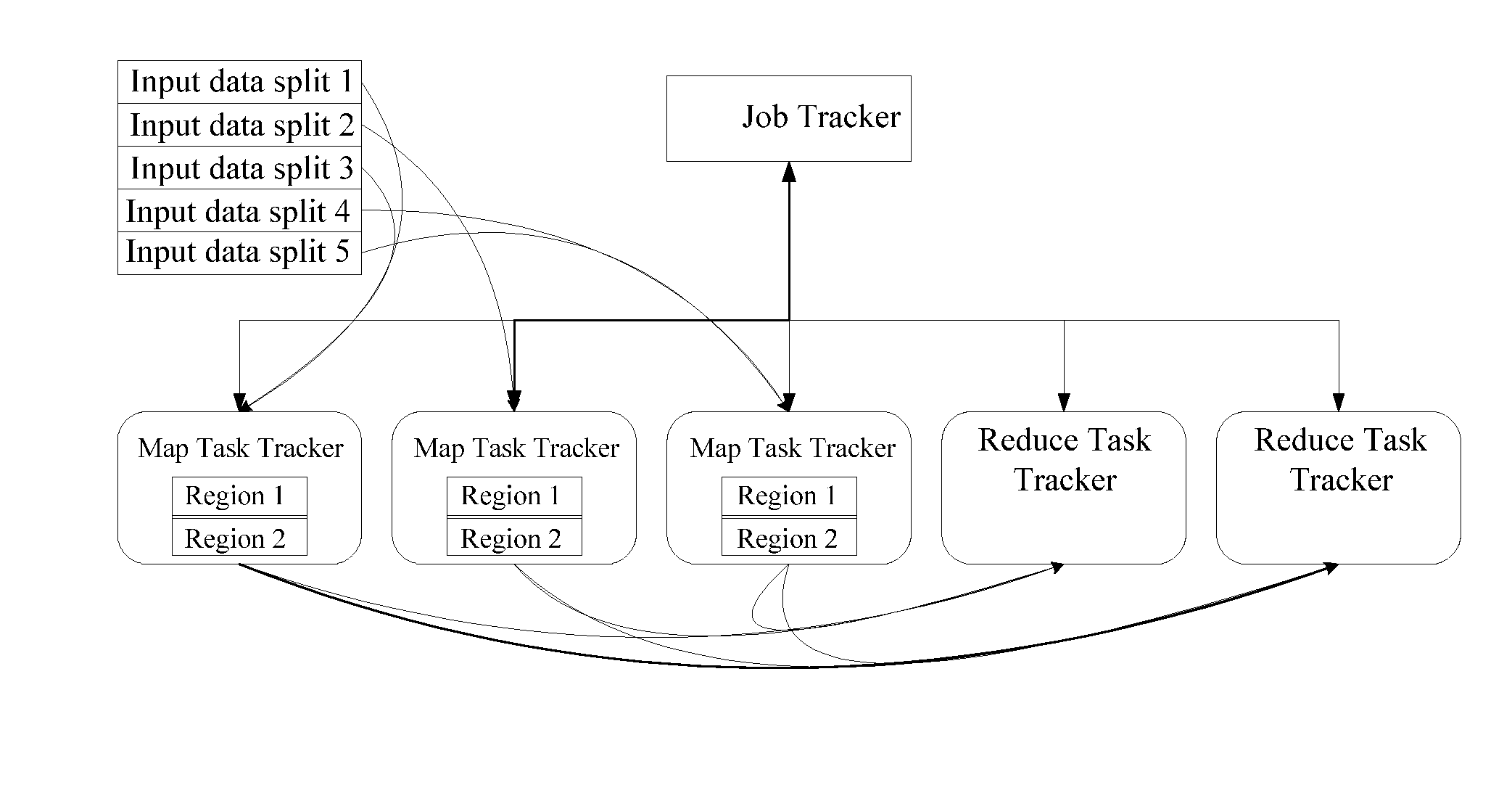
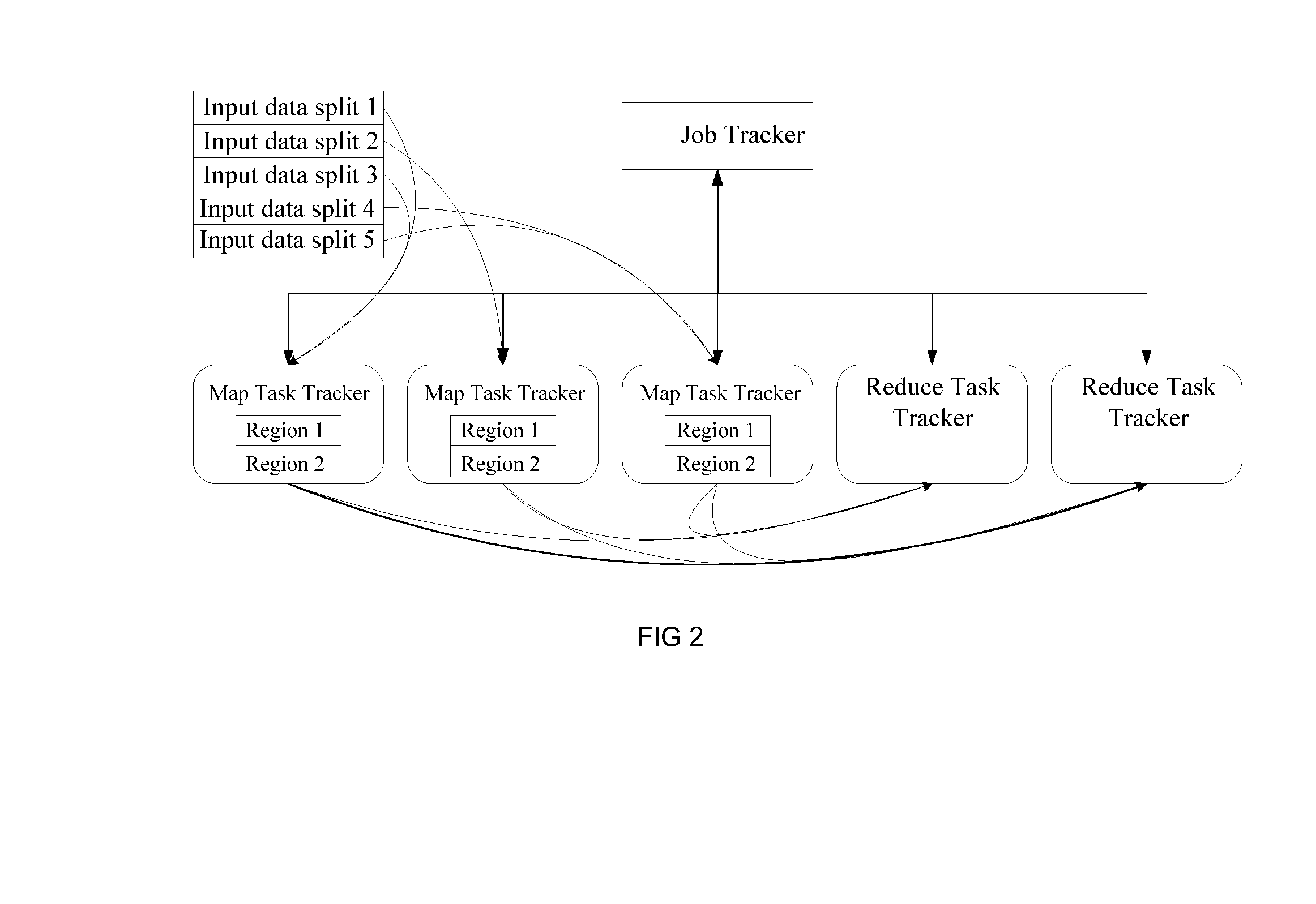
Realizing graph processing based on the mapreduce architecture
InactiveUS20140215477A1Computation loadReduce the balanceMultiprogramming arrangementsMemory systemsGraphicsAlgorithm
A method and device for realizing graph processing based on the MapReduce architecture is disclosed in the invention. The method includes the steps of: receiving an input file of a graph processing job; predicating a MapReduce task execution time distribution of the graph processing job using an obtained MapReduce task degree-execution time relationship distribution and a degree distribution of the graph processing job; and dividing the input file of the graph processing job into input data splits of MapReduce tasks according to the predicted MapReduce task execution time distribution of the graph processing job.
Owner:IBM CORP
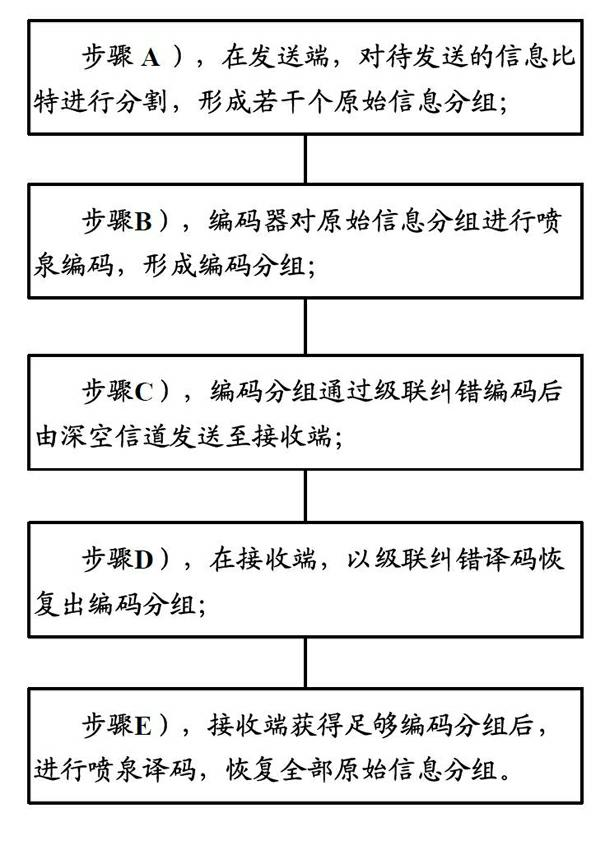
Fountain code compiling method based on deep space communication environment
ActiveCN102164026ASolve the transmission powerSolve space problemsError preventionComputer hardwareFountain code
The invention provides a fountain code compiling method based on deep space communication environment. The method comprises the following steps of: A) dividing information bits to be transmitted to form a plurality of original information groups; B) performing fountain coding on the original information groups to form code groups; C, performing concatenated error correction coding on the code groups, and transmitting the code groups to a receiver by using a deep space channel; D, performing concatenated error correction decoding to recover the code groups; and E, after enough code groups are obtained, performing fountain decoding to recover all the original information groups. In the method, partial randomness in a conventional fountain coding process is limited for the characteristics of the deep space channel so as to effectively reduce coding redundancy overhead and directively solve the problems of limitations to the transmission power and memory space of fountain codes in a deep space environment on the premise of not changing original degree distribution.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
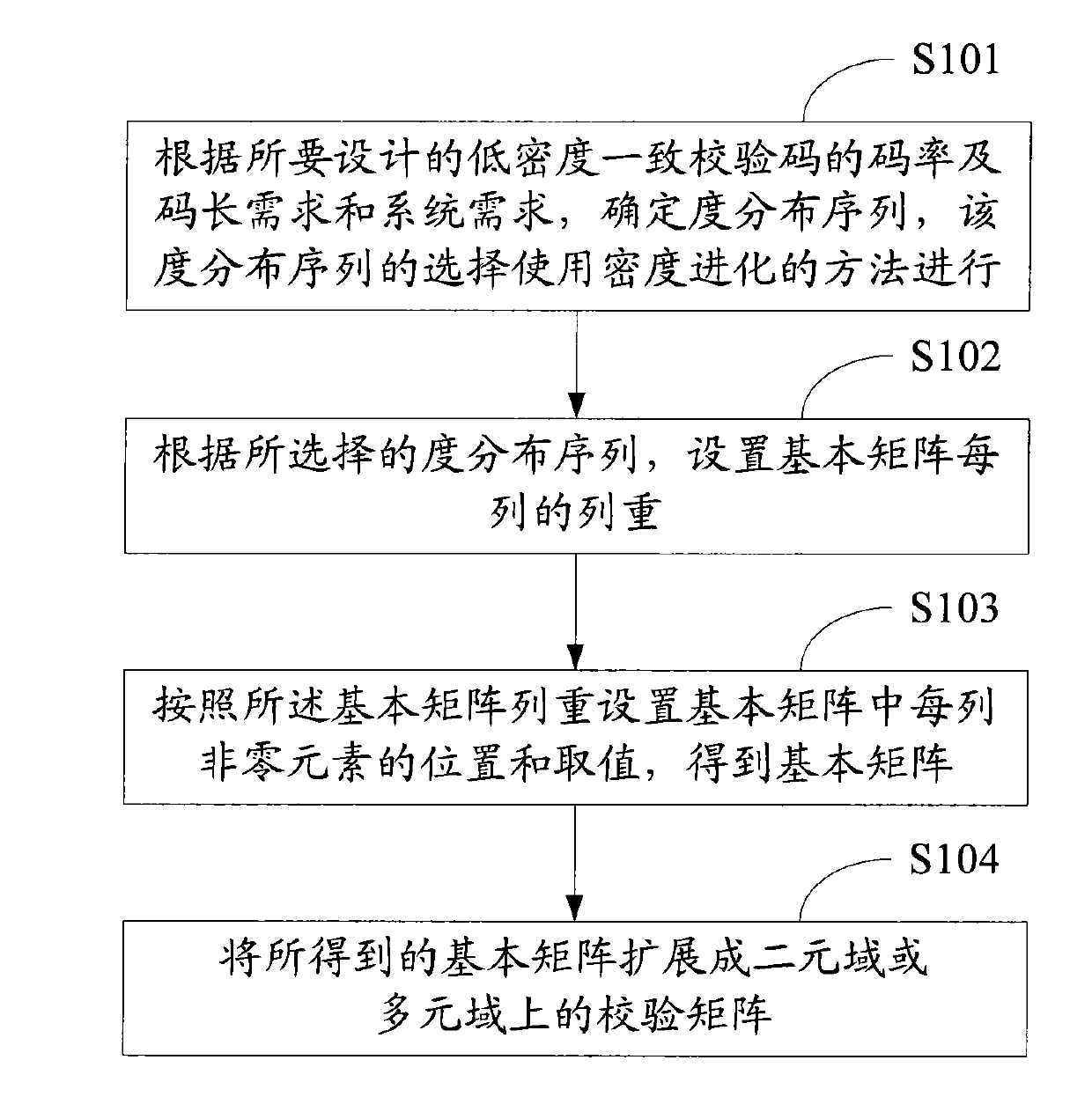
Method and device for generating and coding quasi-cyclic LDPC code
ActiveCN101662290AError correction/detection using multiple parity bitsCode conversionAlgorithmSystem requirements
The invention relates to the technical filed of the error correction and coding of communication and information systems and discloses a method for generating a quasi-cyclic low density parity check code. The method comprises the following steps: according to the requirements on code rate and code length of the low density parity check code to be designed and system requirements, determining a degree distribution sequence which is selected by adopting a density evolution method; setting the column weight of each column of a basic matrix according to the selected degree distribution sequence; setting the positions and values of non-zero elements in each column in the basic matrix according to the column weights of the basic matrix to obtain the basic matrix; and expanding the obtained basic matrix into a check matrix. At the same time, the invention also discloses a method for coding the quasi-cyclic low density parity check code and provides corresponding devices. The methods and the devices provided by the embodiment of the invention enable finally obtained code words to effectively reduce influences of cycle overlapping.
Owner:HONOR DEVICE CO LTD
Image processing based X ray welding line zone extracting method
ActiveCN105160641ASuppress interferenceImprove accuracyImage enhancementImage analysisImaging processingX-ray
The invention discloses an image processing based X ray welding line zone extracting method and relates to the field of industrial automatic detection. The method includes a step A of image pretreatment; a step B of edge detection based on least squares line fitting; a step C of scale product calculation. The invention has beneficial effects that noise interference can be suppressed prominently and edge detection accuracy can be improved. Therefore, good accuracy and robustness can be achieved in application in X ray images with a large amount of noises, low comparison degree, blur welding line zone edges and high grey degree distribution overlapping of the welding line zone and the background.
Owner:四川无为有科技有限公司
Forming method of annular magnetic body orientating along the direction of radius or diameter radiation
The invention discloses a method for forming a circular ring-shaped magnet of which the radiation orientation is along the radius direction or the diameter direction; the key points of the invention are that the oriented magnetic field is changed from the 360-degree distribution(or approximately 360-degree distribution) which is generally adopted at present to a very small part of 360 degrees of the radiation ring; the relative state between the magnetic powders in the forming process and the oriented magnetic field is changed from the relative rest(or approximately relative rest) which is generally adopted at present to the relative motion. The former mainly aims at getting larger oriented magnetic field and the latter aims at magnetizing and orienting the magnetic powders in a molding cavity at the 360-degree direction. The forming method of the invention can preferably resolve the technical problems generally existing in the making of the present radiation ring that the magnetic powders are not completely oriented due to the relatively low oriented magnetic field and the consistency of the magnetic performance of the radiation ring is not good due to the uneven distribution of the oriented magnetic field.
Owner:SHENZHEN RADIMAG TECH CO LTD
Authentication server, method and system for bidirectional authentication in mesh network
InactiveCN101222331ADecreased trustReduce the risk of attackUser identity/authority verificationData switching by path configurationAuthentication serverSecurity level
The invention relates to a bi-directional certification method for a certification server and a mesh network and a system thereof, belonging to the communication technical field; the certification server comprises a trust degree distribution module, a node state detecting module, a trust degree lowering / deprivation module and a trust degree management module, wherein the trust degree distributionmodule is used to determinate the security level of the node according to the received information of the node which requires to be certificated, and generates the trust degree time stamp after successful certification, and time stamp is sent to the node which requires to be certificated together with the signature algorithm mark after the signature; the node state detecting module is used to detect if nodes are attacked; the trust degree lowering / deprivation module is used to receive the break information or lower / deprive the trust degree of the node which is attacked; the rust degree management module is sued to store the user identity information of nodes in the Mesh network, which is successfully certificated, and the trust degree, the signatures and time stamps which are approved by the AS. The invention realizes that all nodes in the mesh network can choose correlation nodes based on the trust degree; moreover, the invention also realizes the bi-directional certification by verifying the trust degree signatures fed back from the correlation nodes at one time.
Owner:HUAWEI TECH CO LTD
High-strength steel sheet, and process for production thereof
ActiveCN102471849AEasy to processFurnace typesHeat treatment furnacesUltimate tensile strengthImpurity
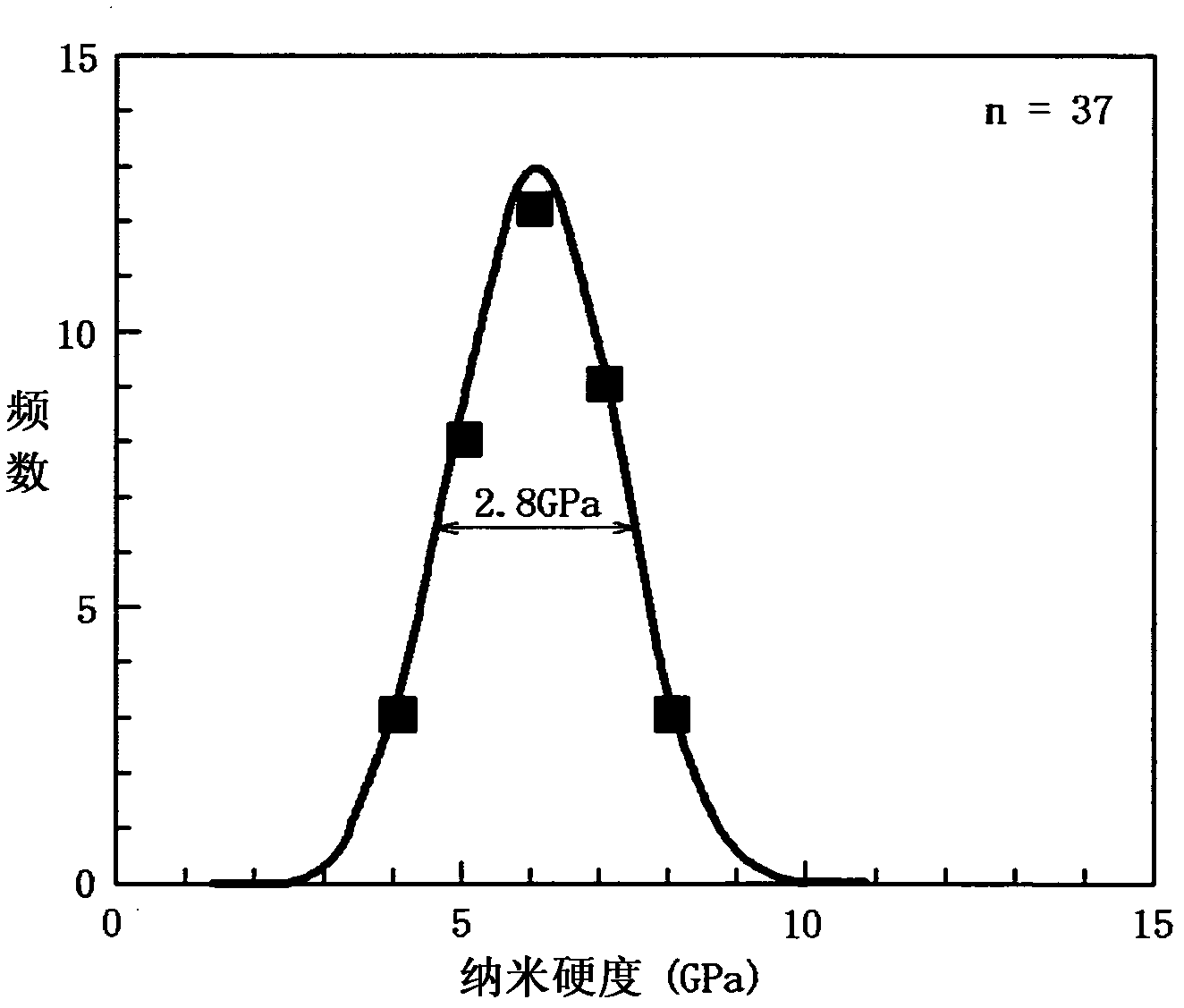
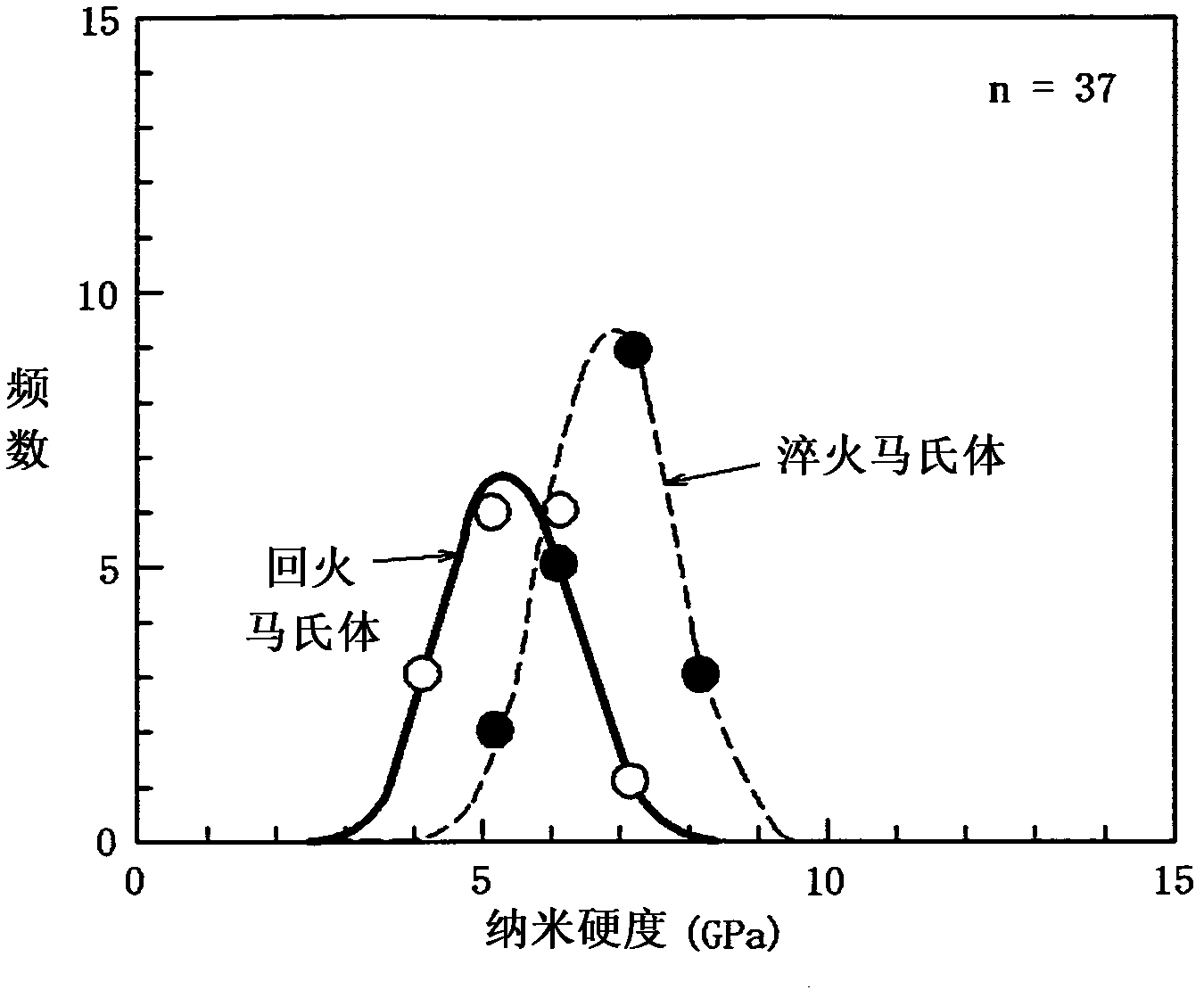
Disclosed is a high-strength steel sheet having excellent processability and a tensile strength of 980 MPa or more. The high-strength steel sheet has the following composition (in mass%): C: 0.1 to 0.3% inclusive, Si: 2.0% or less, Mn: 0.5 to 3.0% inclusive, P: 0.1% or less, S: 0.07% or less, Al: 1.0% or less, and N: 0.008% or less, with the remainder being Fe and unavoidable impurities. The steel structure of the high-strength steel sheet comprises 50% or more of martensite, 50% or less (including 0%) of ferrite, 10% or less (including 0%) of bainite, and 10% or less (including 0%) of residual austenite. In the high-strength steel sheet, the half width in the degree distribution of the nano-hardness obtained by the measurement of the hardness distribution of the martensite is 2.0 GPa or more, and the steel sheet has a tensile strength of 980 MPa or more.
Owner:JFE STEEL CORP
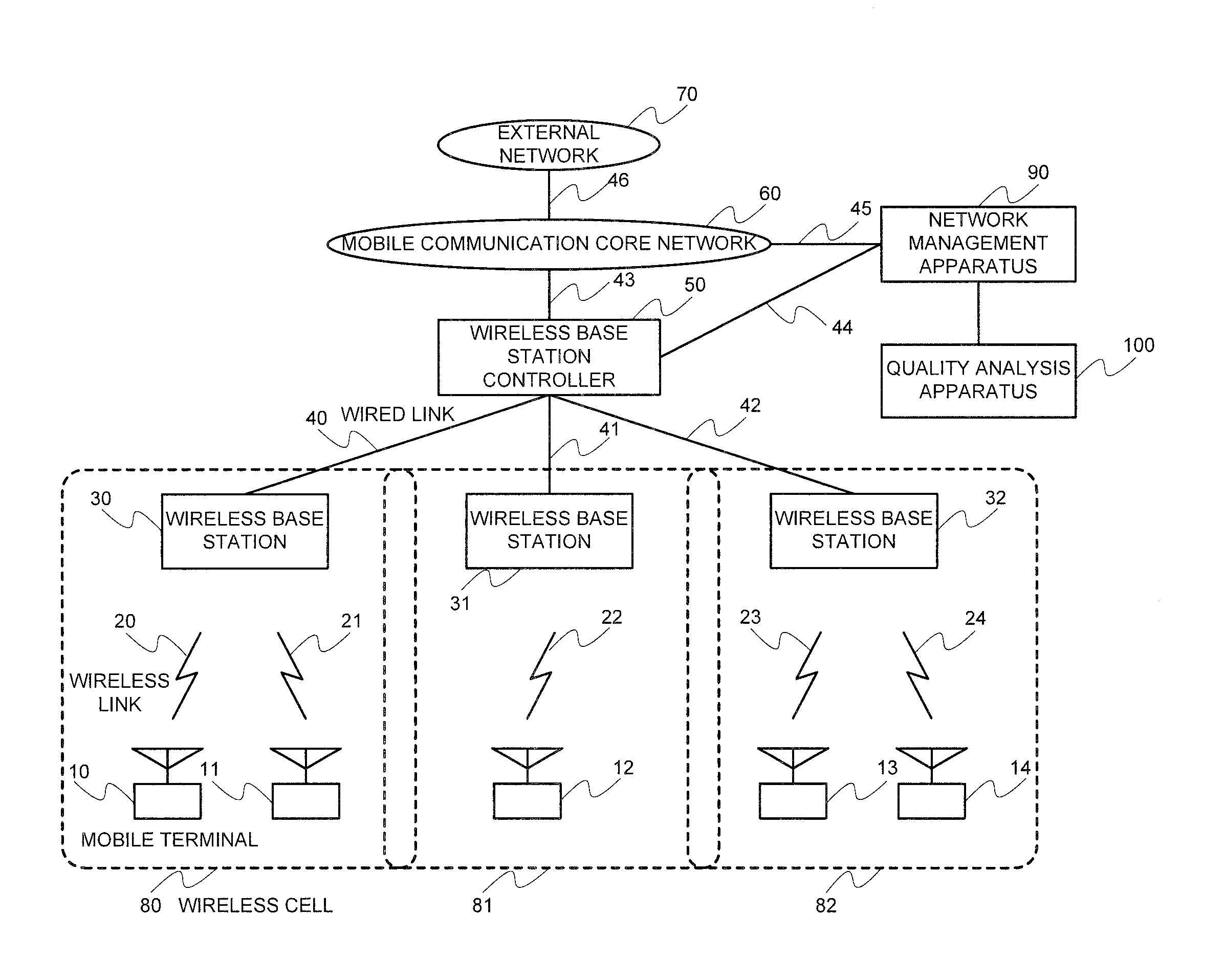
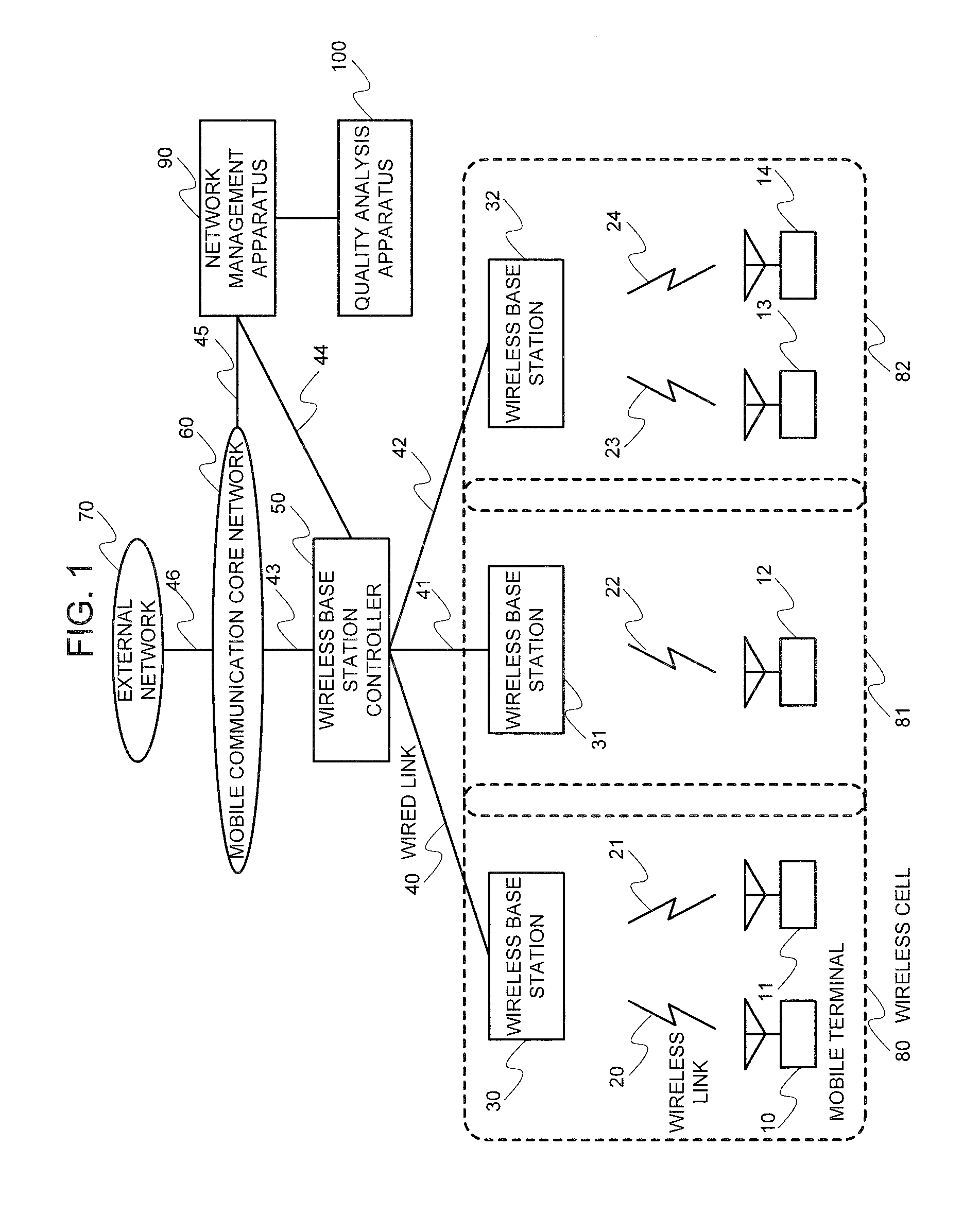
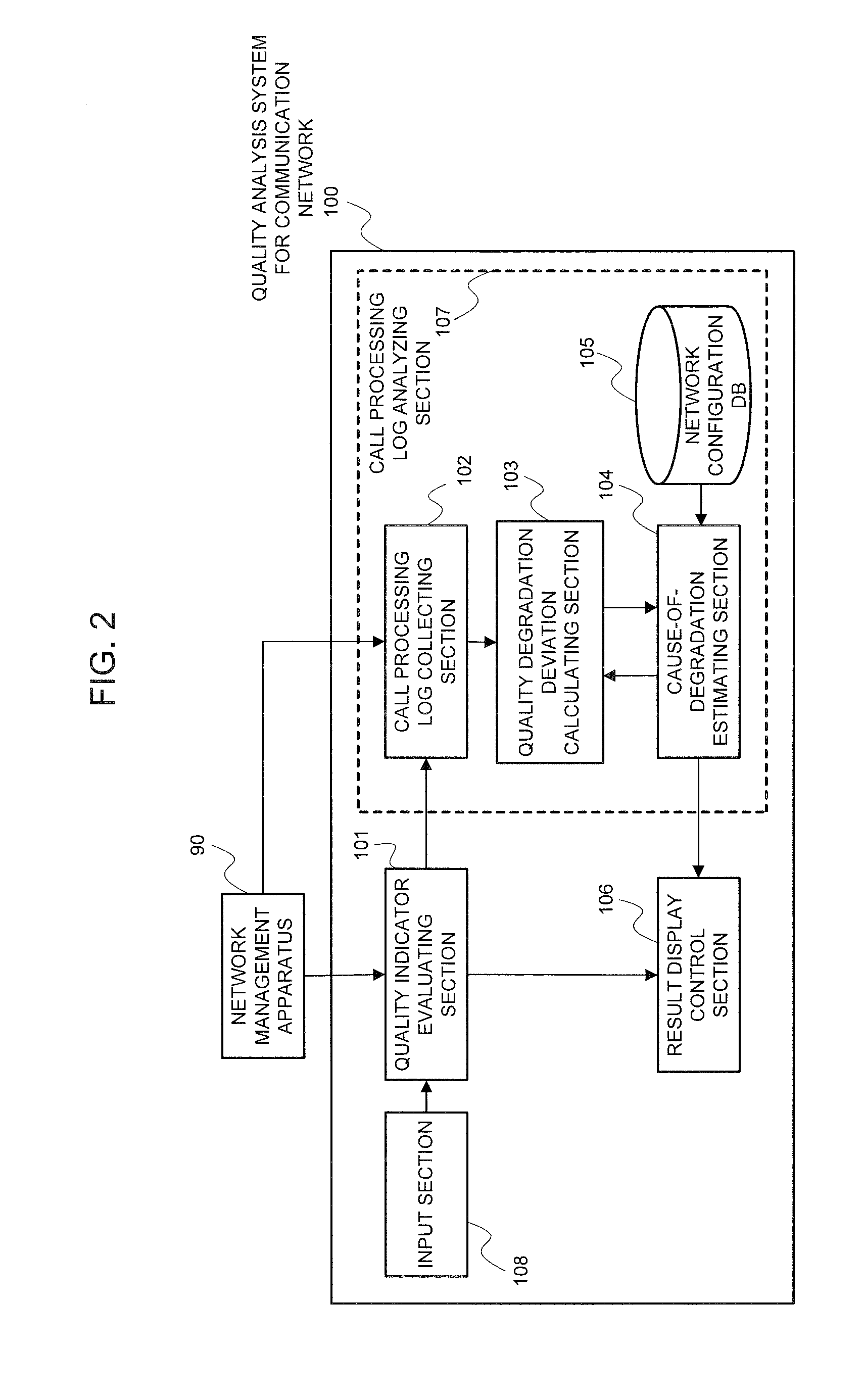
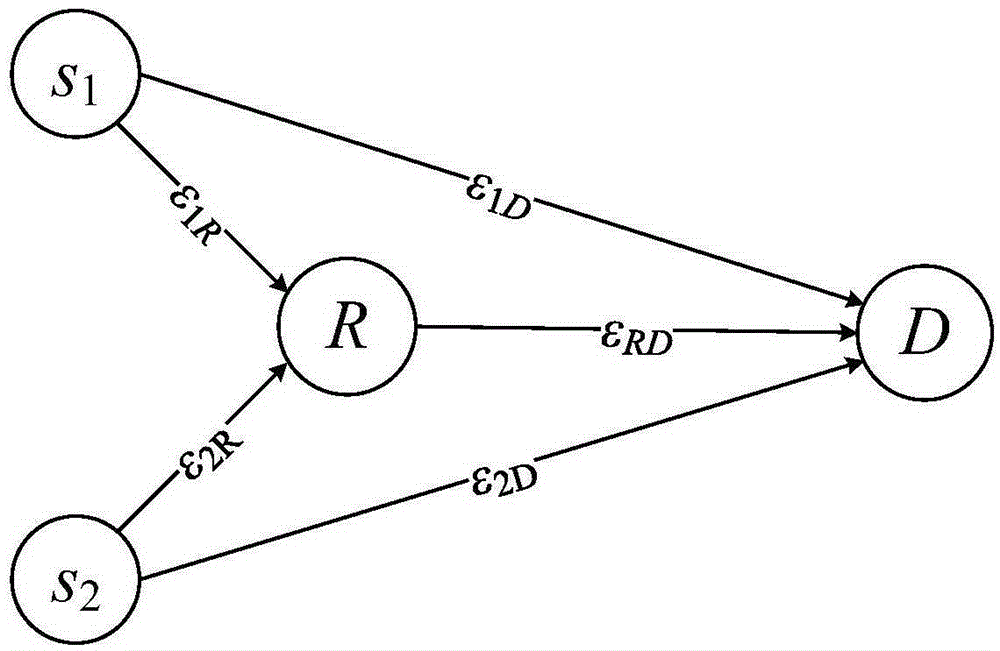
Communication network quality analysis system, quality analysis device, quality analysis method, and program
InactiveUS20100284293A1Error preventionTransmission systemsCommunication qualityNetwork communication
Provided is a communication network quality analysis technique which can identify a network side communication device, a communication area, or a terminal which causes degradation of quality of the communication network detected by an abnormal communication quality index. The technique analyzes a recording content of a call process performed by the network side communication device and acquires a distribution of quality degradation amounts in respective hierarchies such as a terminal, a network communication device, or a communication area. Thus, the technique estimates a terminal, a network side communication device, or a communication area causing degradation of the communication quality according to a degree of quality degradation degree distribution bias considering the belonging relationship of the terminal, the network side communication device, and the communication area.
Owner:NEC CORP
Method for realizing rapid modulation degree profilometry by use of two orthogonal sinusoidal gratings
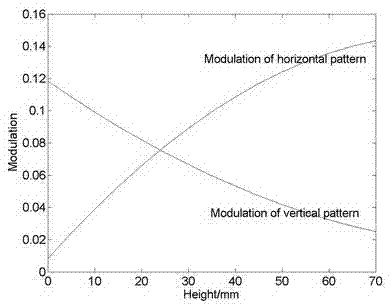
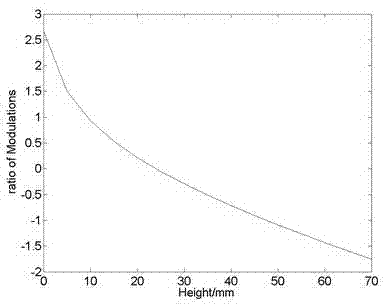
The invention discloses a method for realizing rapid modulation degree profilometry by use of two orthogonal sinusoidal gratings at a certain interval in the optical three-dimensional sensing technology. In the method, two orthogonal sinusoidal gratings at a certain interval are imaged on a measured object at the same time, and the measured object is located between the imaging surfaces of the two gratings; and a CCD (charge coupled device) camera obtains the object surface image modulated by the orthogonal gratings through a semi-transparent semi-reflecting mirror from the same direction. The images of the orthogonal gratings are separated by Fourier transform, spatial frequency-domain filtration and inverse Fourier transform so as to obtain the modulation degree distribution of the images of the two gratings on the object surface; and the object height is recovered according to the pre-calibrated corresponding relationship between the modulation degree ratio and height. In the method, the projection direction of the gratings is coaxial with the imaging direction of the CCD camera, and the method has the characteristic of vertical measurement. The method can recover the object height by acquiring only one image, and has the characteristic of real-time acquisition of three-dimensional information.
Owner:SICHUAN UNIV
Apparatus and method for transmitting/receiving signal in a communication system
InactiveUS20070283216A1Error preventionError correction/detection using LDPC codesCommunications systemLow-density parity-check code
A signal transmission apparatus in a communication system is disclosed. A channel interleaver generates an interleaved vector by channel-interleaving a Low Density Parity Check (LDPC) codeword according to a channel interleaving rule, and a modulator generates a modulation symbol by modulating the interleaved vector according to a modulation scheme. The channel interleaving rule is one of a first channel interleaving rule and a second channel interleaving rule. The first channel interleaving rule is a rule for setting degree distribution for nodes in a factor graph of the LDPC codeword separately for individual levels supported by the modulation scheme. The second channel interleaving rule is a rule for allowing coded bits included in the LDPC codeword to be interleaved according to an unequal error characteristic of the modulation scheme.
Owner:SAMSUNG ELECTRONICS CO LTD +1
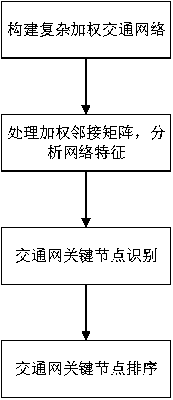
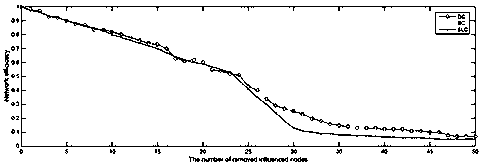
Complex weighted traffic network key node identification method based on semi-local centrality
PendingCN110135092AEfficient identificationSolve complexityGeometric CADForecastingComputation complexityRound complexity
The invention provides a complex weighted traffic network key node identification method based on semi-local centrality, comprising the following steps: S1, constructing a complex weighted traffic network: constructing a traffic network by adopting an original method, and taking road sections as nodes and road sections as edges; generating a corresponding adjacent matrix; according to the road grade, obtaining a weighted adjacency matrix through the adjacency matrix; S2, processing the weighted adjacency matrix, and analyzing network characteristics: calculating degree distribution of nodes, calculating an average clustering coefficient, and calculating an average path length; analyzing network characteristics according to the degree distribution of the nodes, the average clustering coefficient and the average path length; S3, identifying key nodes by adopting a semi-local centrality algorithm; and S4, sorting the key nodes of the traffic network: sorting the nodes in a descending order according to the importance degree to obtain the key nodes in the traffic network. The road grade is used as the weight, and the semi-local centrality algorithm is adopted, so that the problems thatthe key node identification calculation complexity of the existing traffic network is high and the traffic network characteristics are not considered are solved.
Owner:JIANGSU OPEN UNIV
Experimental method for saturated shale pore fluid separation and saturation degree calculation
ActiveCN106525688AEfficient separationGet saturation distributionWater resource assessmentAnalysis using nuclear magnetic resonanceNMR - Nuclear magnetic resonanceChemical physics
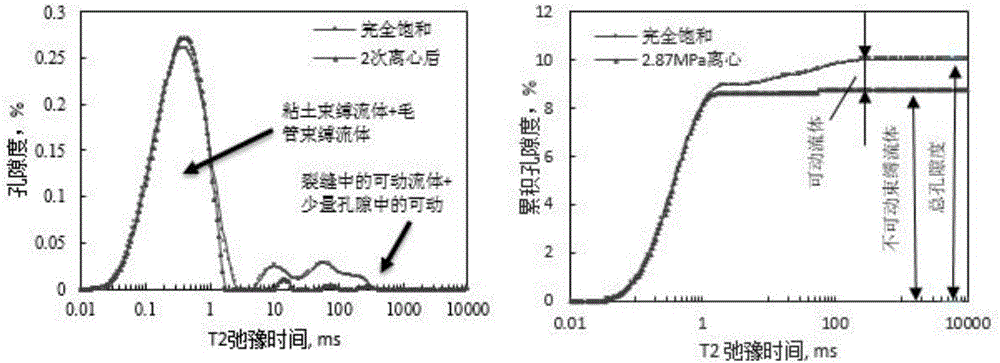
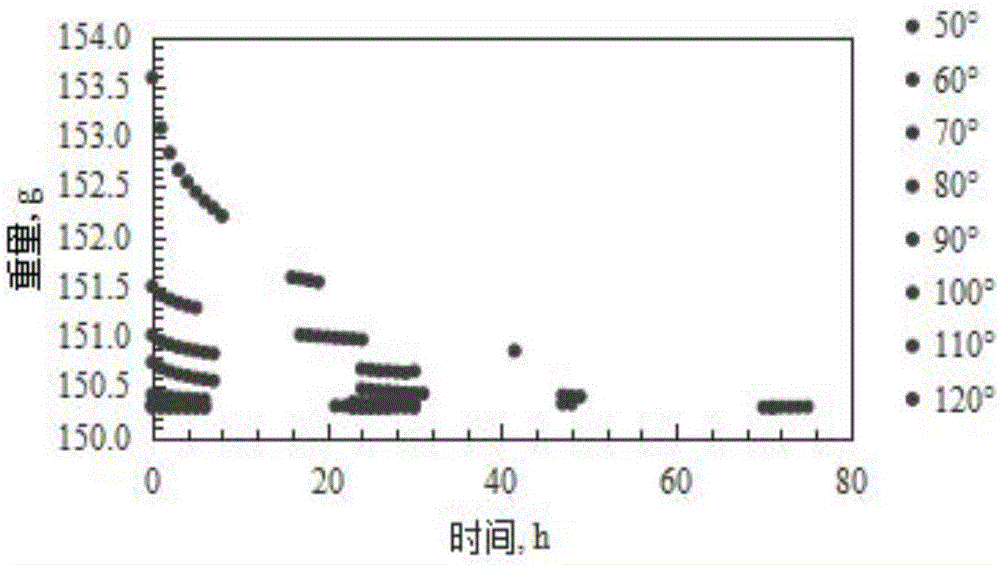
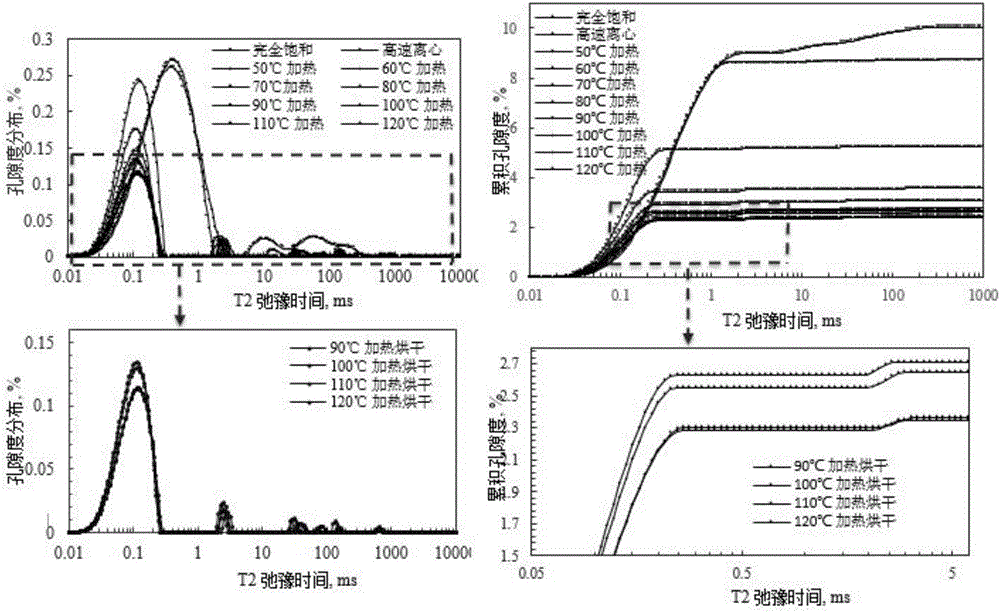
The invention discloses an experimental method for saturated shale pore fluid separation and saturation degree calculation. The method includes the steps that firstly, separation of movable water in saturated shale is carried out through two times of a high-speed centrifugation method, and then a vacuum gradient heating experiment is added to separate capillary bound water and clay bound water in pore fluid. In the whole process, by carrying out contrastive analysis on change rules of a core weight and residual fluid nuclear magnetic resonance relaxation time T2 distribution frequency spectrum obtained after each step is completed, the saturation degrees of the movable water in saturated core pores, the capillary bound water and the clay bound water are obtained, and the saturation degree distribution of the movable water in crack space and pore space is obtained. The nuclear magnetic resonance core analysis technology is further used for calculating the storage percentage of the movable water in shale cracks and large pores, and reference is provided for evaluation of seepage space of a shale reservoir.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
Dynamic social network-oriented influence maximization analysis method
PendingCN108510115ARemarkable resultsReasonable running timeForecastingResourcesNODALInfluence propagation
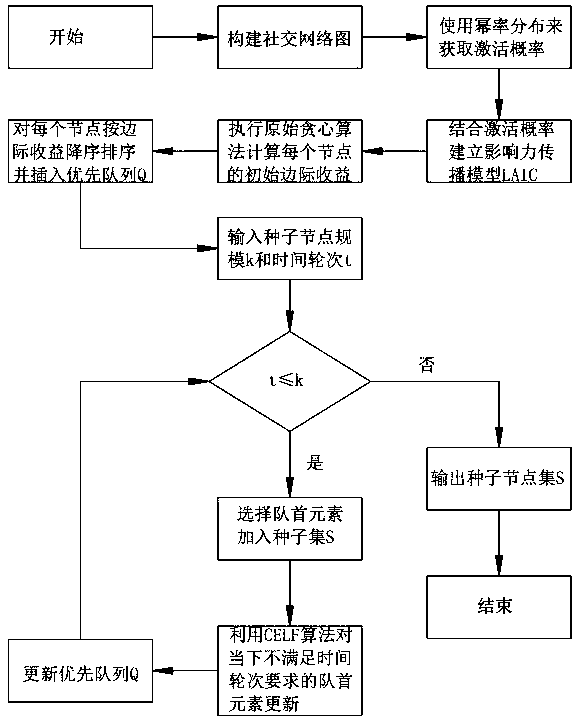
The invention discloses a dynamic social network-oriented influence maximization analysis method. The method specifically comprises the steps of (1) obtaining an activation probability, and adding a time factor into the activation probability by using power law distribution of an influence delay distribution function; (2) building an influence propagation model LAIC; (3) executing a greedy algorithm, and calculating an initial marginal income of each node by utilizing the greedy algorithm; and (4) optimizing an original greedy algorithm by using a CELF algorithm, and improving the efficiency of searching for seed nodes through sub-mode characteristics of the influence function and an influence priority queue. By analyzing the effect of the time factor in influence propagation, the power law distribution of the distribution function, consistent with real social network node degree distribution is used, and finally an excellent result and reasonable running time are achieved in selectingTOP-K nodes with highest influence, so that the problem of dynamic social network influence maximization is effectively solved.
Owner:SHANDONG UNIV OF SCI & TECH
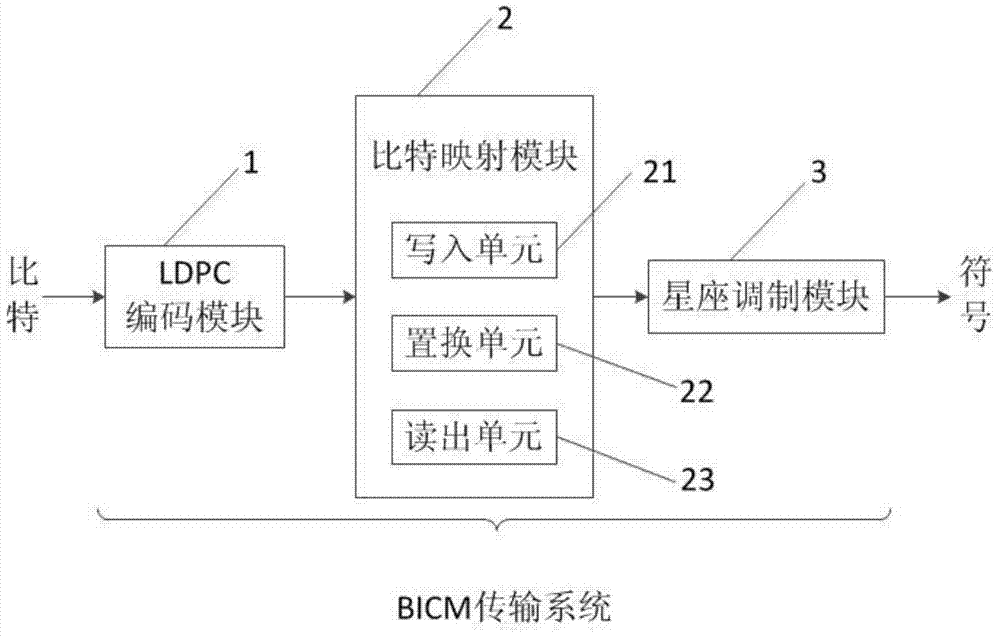
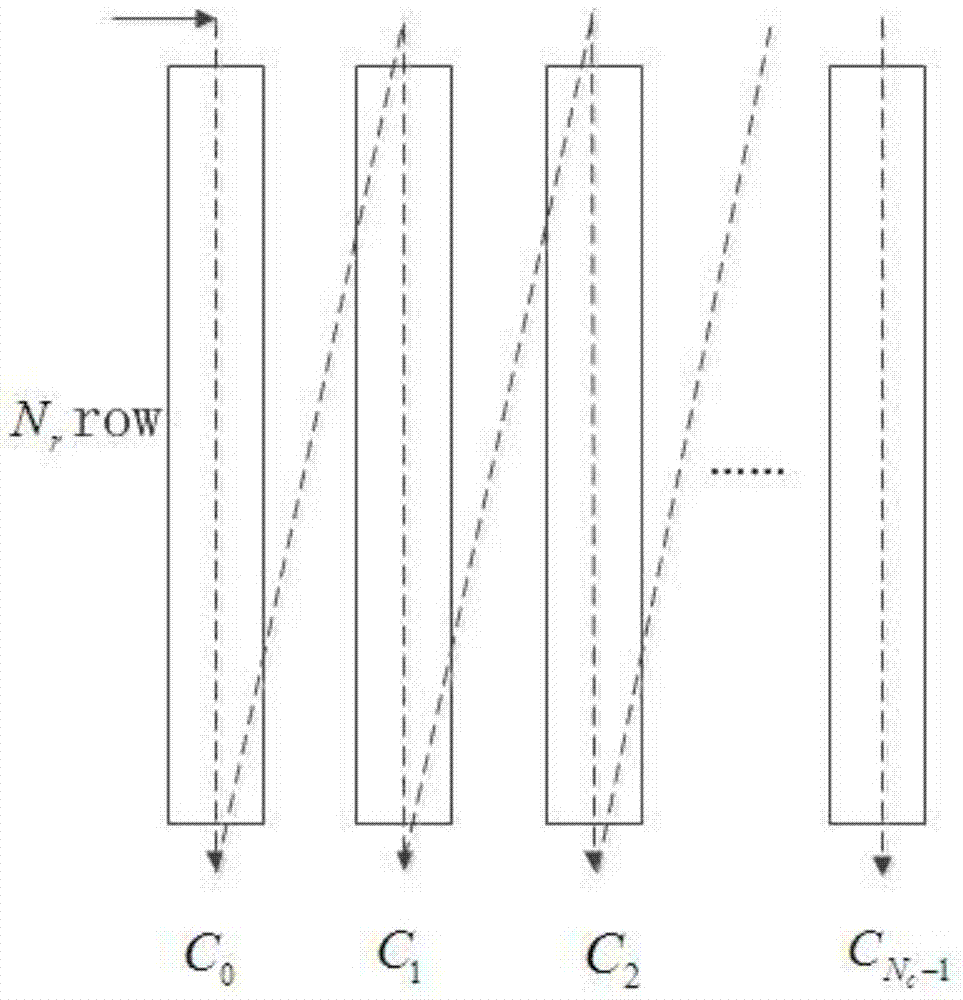
BICM transmission method and system for LDPC code words in specific degree distribution
The invention discloses a BICM transmission system for LDPC code words in specific degree distribution. The BICM transmission system comprises an LDPC coding module, a bit mapping module and a constellation modulation module. The bit mapping module comprises a writing-in unit, a replacement unit and a reading-out unit. The writing-in unit enables output bit streams of LDPC codes to be written in a storage list by columns. A bit replacement sequence is preset in the replacement unit, and bit replacement is performed on the storage list according to the bit replacement sequence. The reading-out unit is used for reading out the sequence after bit replacement. According to the technical scheme, the BICM system of the LDPC code words which conform to specific degree distribution is optimized, and therefore, compared with the LDPC code words which are not optimized, the specific LDPC code words can have better bit error rate performance in the BICM transmission system.
Owner:SHANGHAI NAT ENG RES CENT OF DIGITAL TELEVISION
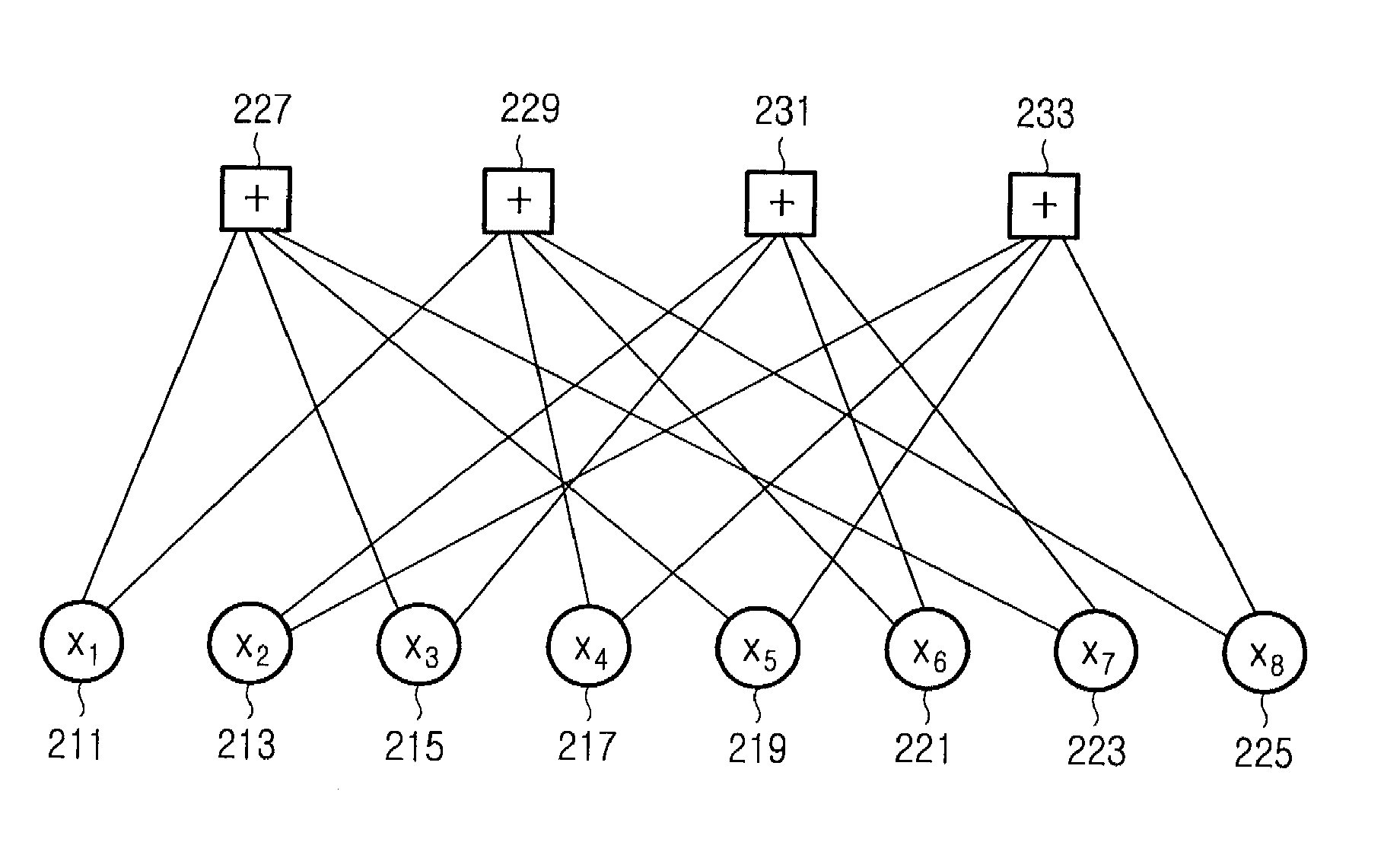
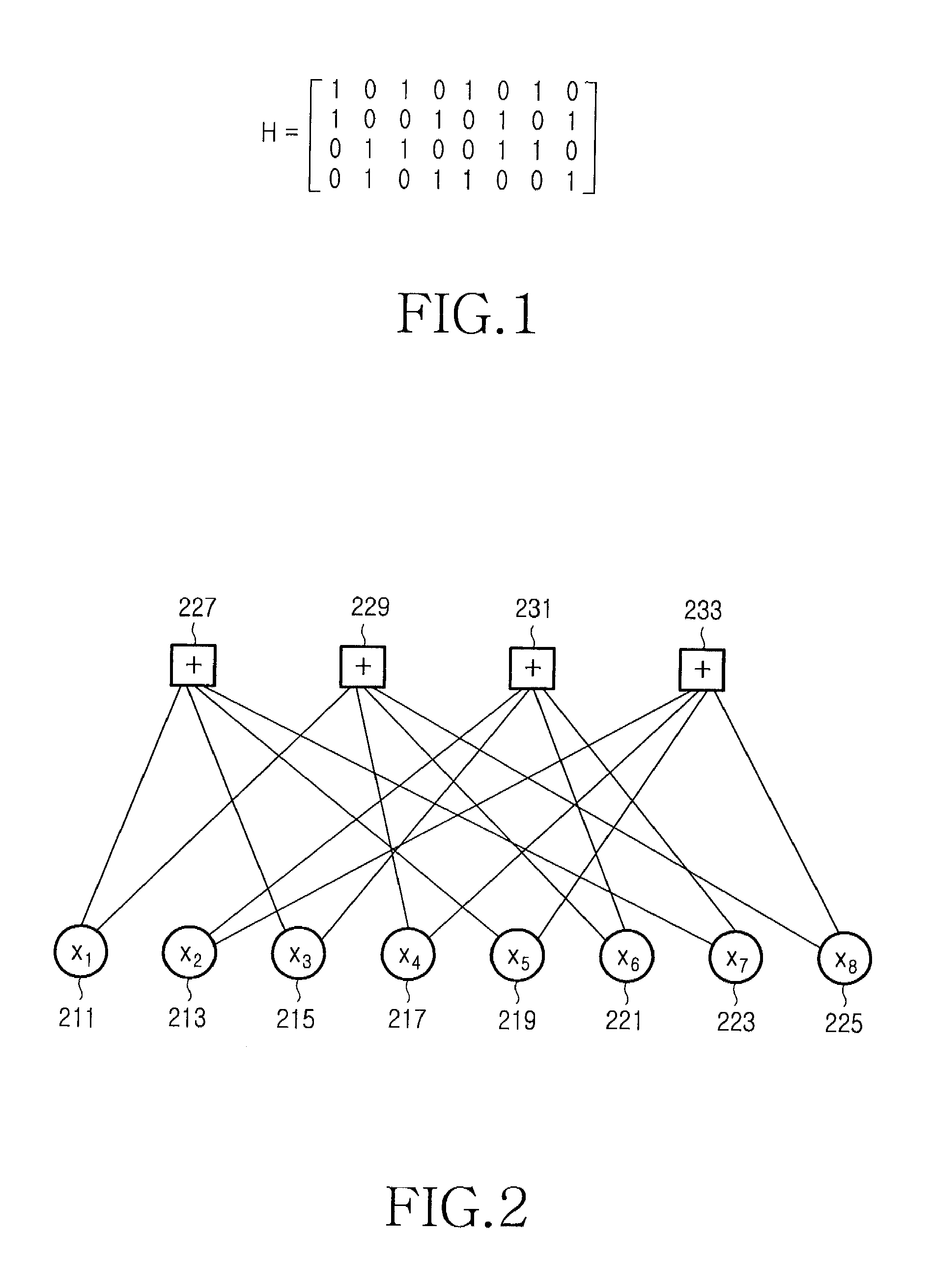
Check Matrix Generating Apparatus and Communication Apparatus
InactiveUS20080184084A1Promote generationStable characteristicsElectronic circuit testingChecking code calculationsAlgorithmLow-density parity-check code
A check matrix generating apparatus calculates a parameter for pseudo-random-number permutation matrices using a predetermined information length, a coding rate, and a maximum column degree, generates the pseudo-random-number permutation matrices from the calculated parameter for the pseudo-random-number permutation matrices by using a pseudo-random-number sequence and a Latin square matrix, determines, as a parameter, a combination of degree distributions which can be adopted for optimization of a degree distribution of generation of a check matrix which can be formed with the pseudo-random-number permutation matrices, using the predetermined information length, coding rate, and maximum column degree, optimizes the degree distribution of generation of a check matrix under a restriction condition based on the determined combination of degree distributions which can be adopted, and arranges the generated pseudo-random-number permutation matrices according to the optimized degree distribution of generation of the check matrix so as to generate the check matrix for low-density parity-check codes.
Owner:MITSUBISHI ELECTRIC CORP
Method and device of HARQ
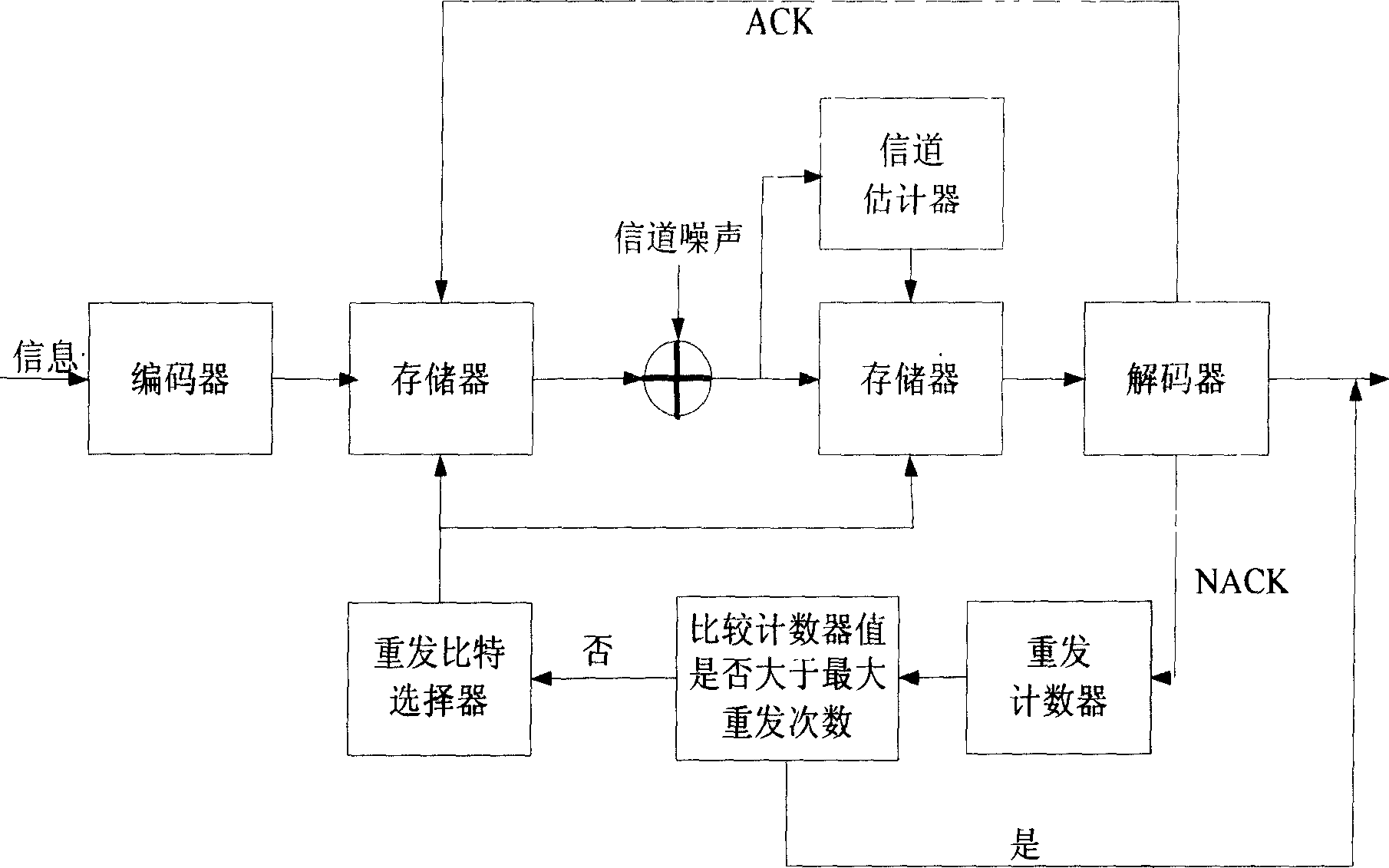
InactiveCN1758579AImprove throughputError prevention/detection by using return channelCorrect operation testingRound complexityComputer science
A method of mixed ¿C automatic request repeat used in radio communication environment is a new and practical mixed ¿C automatic request retransmission scheme which can be realized by providing different bit protective degree to different degree distribution based on difference of LDPC code nodal degree distribution. The method can use quite small bandwidth to improve system performance obviously.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Two-dimensional distribution design method for distributed fountain code
InactiveCN105262564AImprove decoding performanceImprove effectivenessError preventionComputer architectureFountain code
The invention relates to an encoding and decoding technology, and especially relates to a two-dimensional distribution design method for a distributed fountain code. The method comprises the following steps: step A, establishing a distributed network system model; step B, designing a two-dimensional distribution network coding relaying protocol, wherein the whole coding process is divided into two parts, one part is fountain coding at an information source node in the previous two stages of the conversation process, and the other part is network coding based on two-dimensional distribution in the third stage of the conversation process; step C, analyzing the decoding performance; and step D, optimizing a degree distribution function. The two-dimensional distribution design method for the distributed fountain code provided by the invention can be applicable to multi-source data download and storage in a distributed system, and can also be used as a distributed cooperative transmission scheme in cooperative communication; meanwhile, under the condition of facing to topological structures like a time varying channel, an asymmetrical network structure in a spatial information network, the distributed fountain code scheme can greatly improve the effectiveness of network system transmission and reduce the energy consumption of the system by means of network coding adaptive scheduling.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
Raptor Codes encoding/decoding method suitable for medium/short code lengths of additive white Gaussian noise channel
InactiveCN102324998AImprove effectivenessReliable deliveryError preventionError correction/detection using multiple parity bitsTanner graphReliable transmission
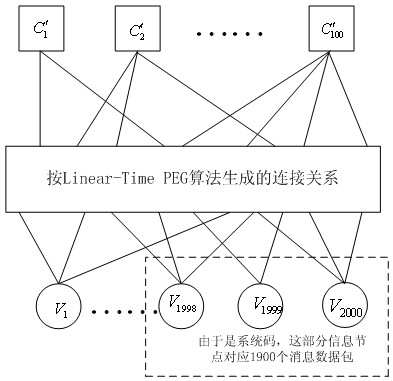
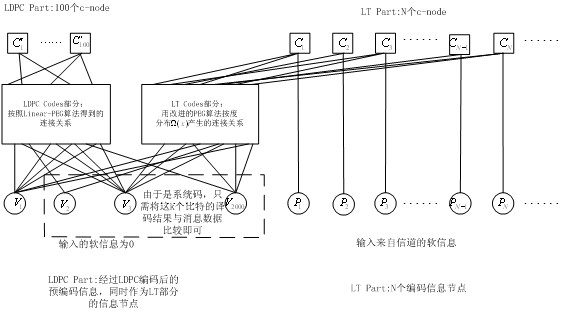
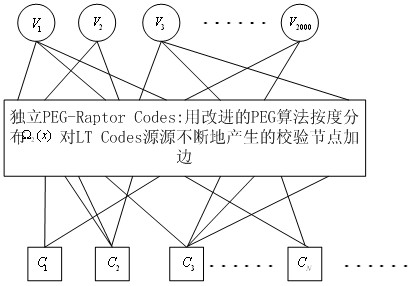
The invention discloses a Raptor Codes encoding / decoding method suitable for medium / short code lengths of an additive white Gaussian noise channel. According to the method disclosed by the invention, the degree distribution of the inner codes, i.e. LT (Linear-Time) Codes, of the Raptor Codes which are more suitable for the medium / short code lengths is proposed; and the improved PEG (Progressive Edge-Growth) algorithm is used for encoding the inner codes, i.e. the LT codes, of the Raptor Codes, wherein the encoding manner consists of two PEG encoding manners, i.e. independently carrying out PEG composition on the LT Codes and carrying out the PEG composition on the LT Codes through combining with outer codes, i.e. LDPC (Low Density Parity Check) Codes, thus the problem that excessive shortloops appear in a Tanner graph, caused by randomly selecting information packets in an LT encoding stage, is solved. With the adoption of the method disclosed by the invention, the effectiveness for the transfer of soft information when the BP (Background Processing) iterative decoding is carried out is therefore enhanced, the performance better than that of a random composition manner is obtained, and the more reliable transmission for the rateless codes with the medium / short code lengths is realized.
Owner:ZHEJIANG UNIV
Link predicting method based on local effective path degree
InactiveCN106326637AImprove forecast accuracyInformaticsSpecial data processing applicationsNODALNetwork model
The invention discloses a link predicting method based on local effective path degree. The method comprises the following steps: step one, building a network model; step two, optionally choosing two unconnected nodes in the network as seed nodes and recording local path degree of each path with the length of 2 between the two seed nodes; step three, calculating the local path degree of each path with the length of 3 between the two seed nodes; step four, calculating local effective path degree similarity indexes of the two seed nodes; step five, repeatedly performing steps 2-4 on all unconnected node pairs and calculating the corresponding local effective path degree similarity index values; and step six, ranking the similarity index values of all the unconnected nodes from high to low, determining that higher values leads to higher possibility of edge connection between corresponding node pairs and taking the node pairs corresponding to former E index values as predicted connection edges. According to the link predicting method based on local effective path degree, the influence of degree distribution and edge connection strength in local paths on the link prediction is considered; the utilization ratio of information is high; the prediction effect is excellent.
Owner:ZHEJIANG UNIV OF TECH
Wireless sensor network topology construction method
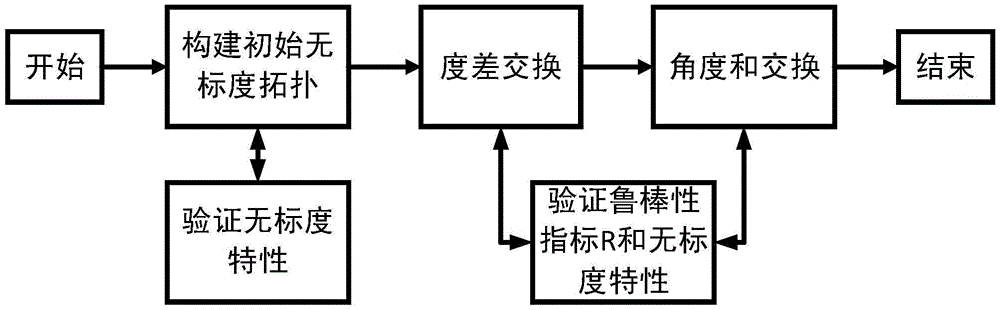
ActiveCN105554844AImprove robustnessKeep the scale-free propertyNetwork topologiesWireless sensor networkingDegree distribution
The invention relates to the network topology construction field, provides a wireless sensor network topology construction method. The wireless sensor network topology construction method comprises: step 100, constructing an initial scale-free wireless sensor network topology; step 200, optimizing the initial scale-free wireless sensor network topology according to the degree difference of every connection mode of the nodes on independent edges, thus obtaining a preliminarily optimized wireless sensor network topology; step 300, optimizing the preliminarily optimized wireless sensor network topology according to the summation of the circling angles of every connection mode of the nodes on independent edges, thus obtaining the wireless sensor network topology. According to the invention, the network topology has relatively high robustness in facing a random attack and a hostile attack without changing the node degree distribution of the nodes.
Owner:DALIAN UNIV OF TECH
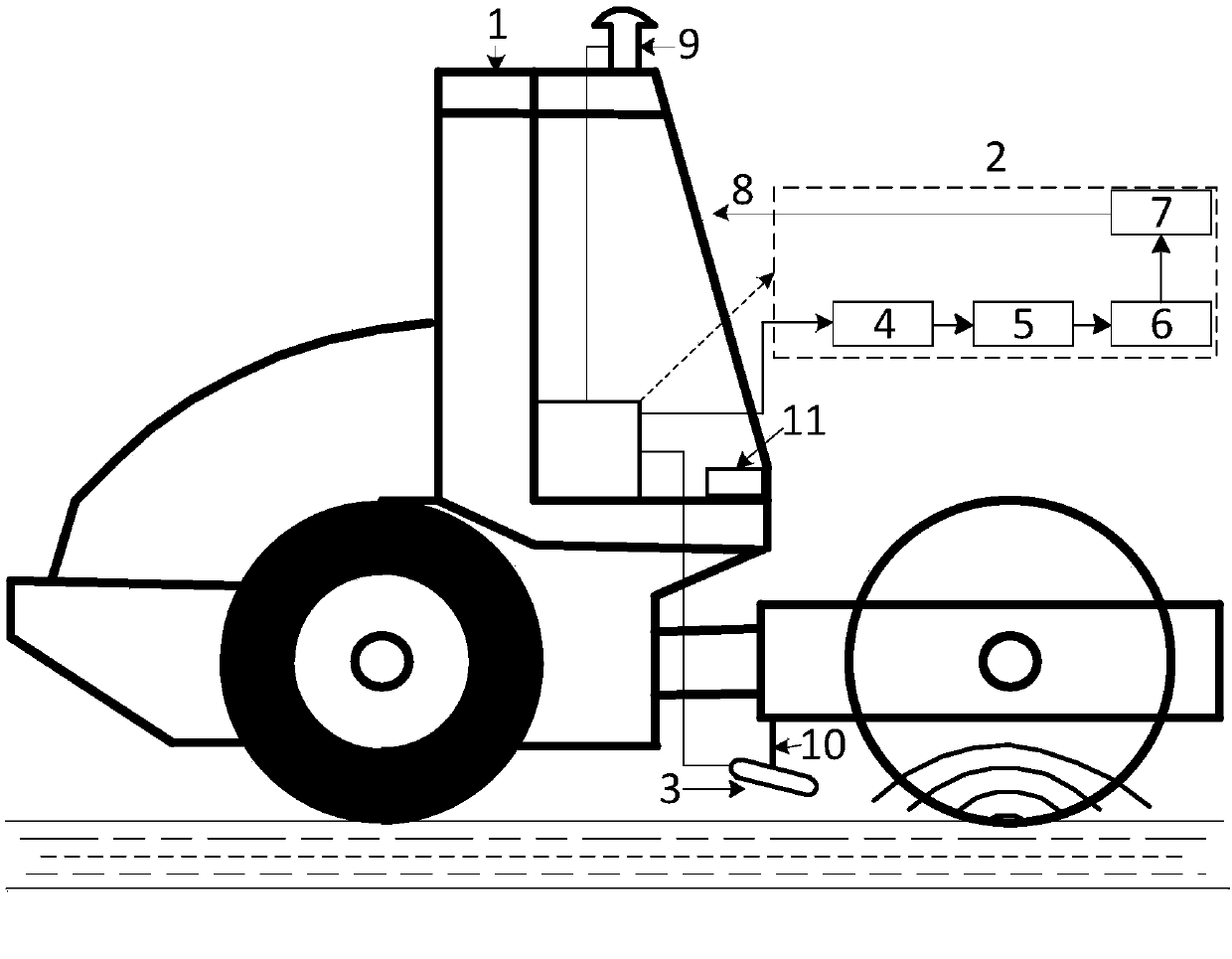
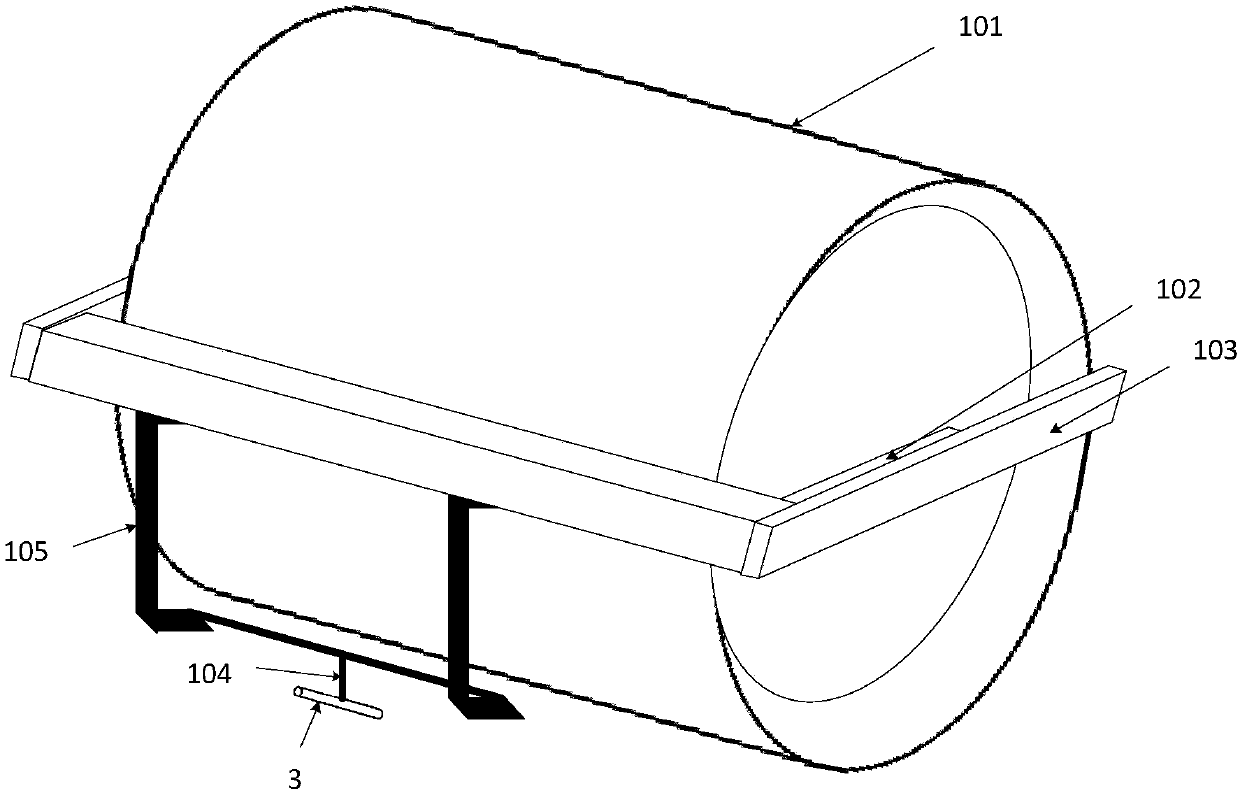
Filling continuous compaction acoustic wave detection system and method
InactiveCN107831217AAccurate and effective detectionDetection is accurate, effective, fast and non-destructiveAnalysing solids using sonic/ultrasonic/infrasonic wavesProcessing detected response signalFrequency spectrumWave field
The invention discloses a filling continuous compaction acoustic wave detection system. Based on a rolling machine, detection equipment comprises a sound field pickup, an analyzing and processing module, a displayer, a GPS receiver and the like. When a filling layer is rolled, an acoustic wave field time domain signals generated near a rolling layer are received by the sound field pickup which isarranged on an eternal machine frame of a vibrating drum of a road roller and are sampled to form acoustic wave field digital signals; meanwhile, the GPS receiver provides spatial signals related to the rolled position, the sampled acoustic wave signals are filtered and spectrally analyzed to obtain secondary harmonic amplitudes of the effective acoustic signals, a continuous compaction degree index value is established according to the relevance between the secondary harmonic amplitudes and an earth-rock material compaction degree, and combined with GPS spatial position information, a time-space compaction degree distribution diagram of a rolled area is shown on the machine-mounted displayer. The filling continuous compaction acoustic wave detection system disclosed by the invention has the characteristics of non contact, continuity, real timeliness, suitable for filling engineering continuous compaction quality control and the like. A vibrating frequency and a vibrating amplitude ofthe vibrating drum of the road roller are controlled by compaction feedback, so that an intelligent continuous compaction function can be easily achieved.
Owner:TSINGHUA UNIV +1
System LT code compiling method based on superposition degree
ActiveCN103346858AGuaranteed Partial Restoration PropertiesLow probability of decoding failureError preventionAlgorithmTheoretical computer science
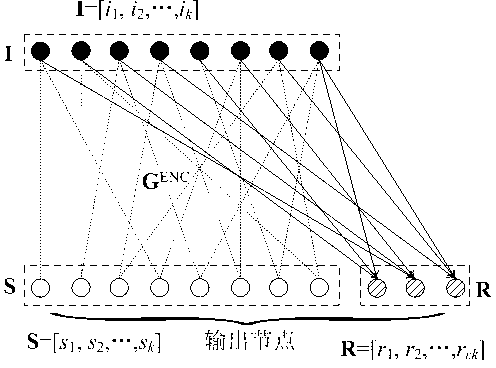
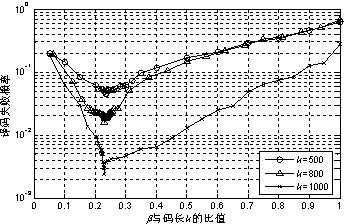
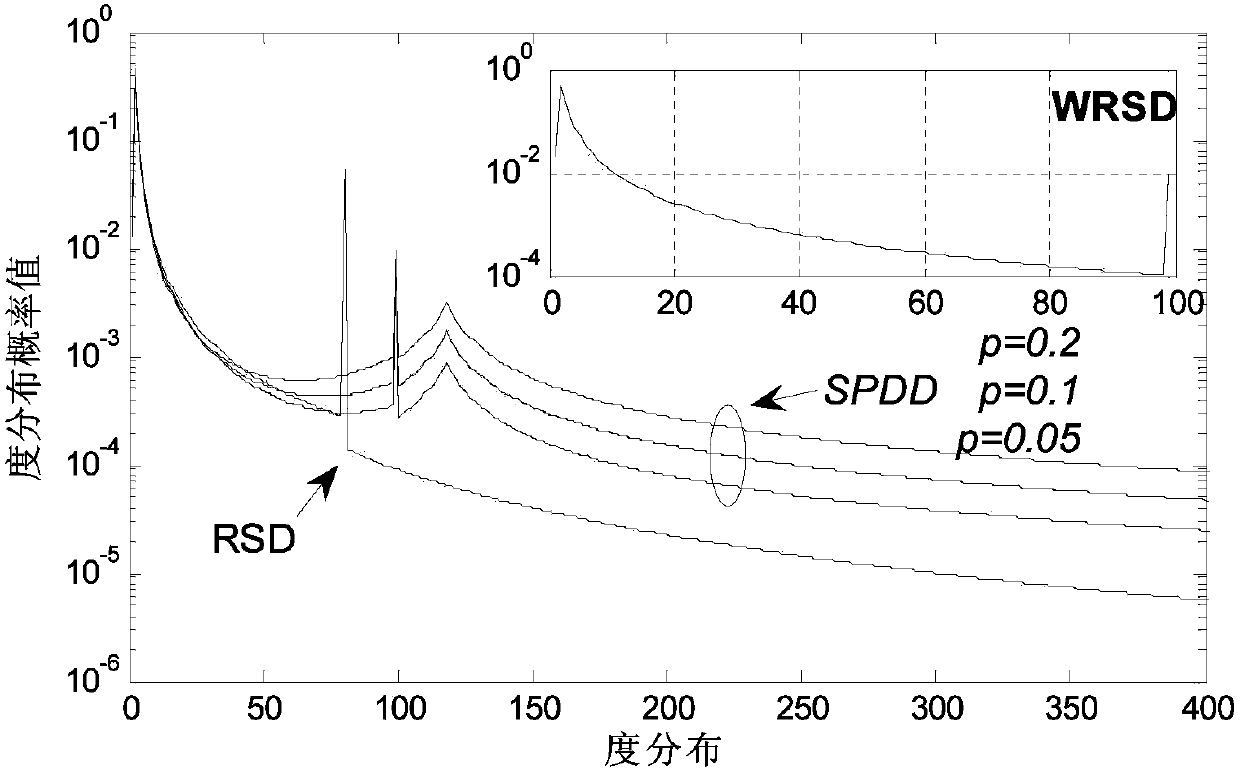
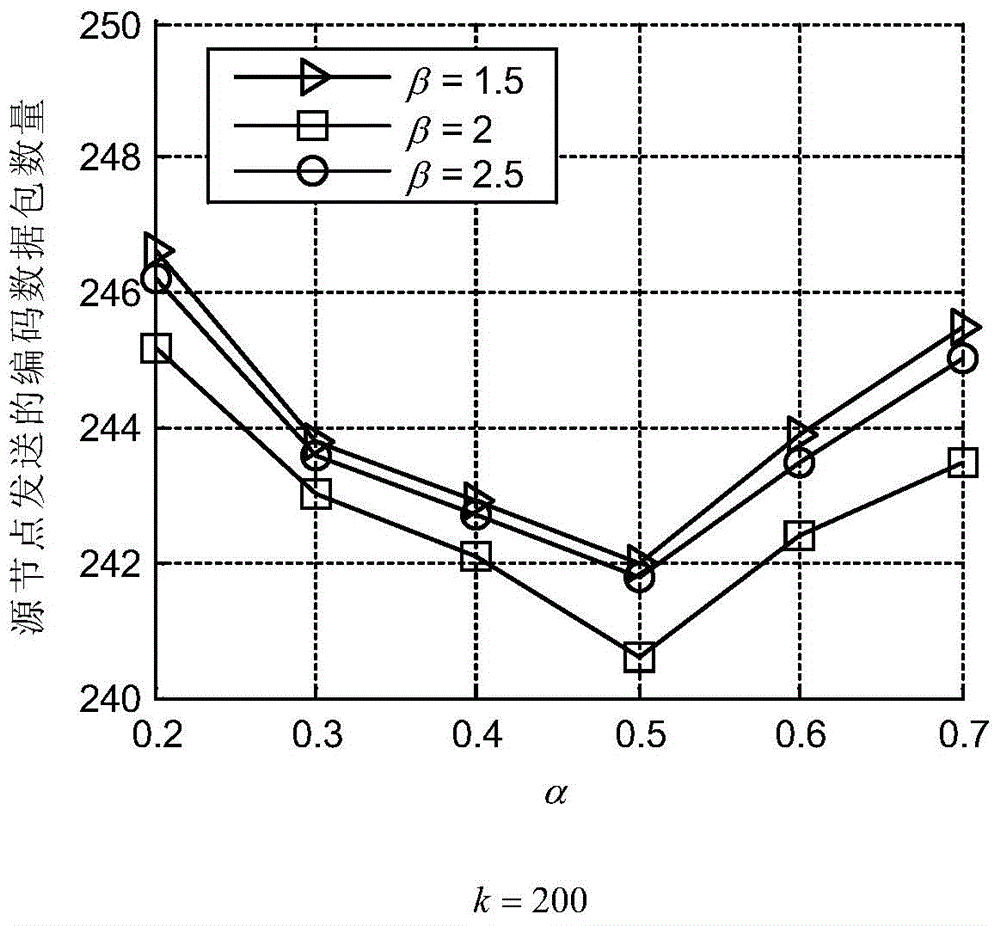
The invention provides a system LT code compiling method based on the superposition degree. The method comprises the following compiling steps: conducting initialization, defining input nodes S, middle nodes I and redundancy check nodes R, constructing a BP translatability matrix in advance, and utilizing S=I G<ENC> to generate the I; generating the R by the I in a distribution mode through the superposition degree; using the S and the R as output nodes to be sequentially sent out. SPDD degree distribution is designed and optimized for the middle nodes of system coding, a DD doping level component is arranged in a superposition mode on the basis of WRSD degree distribution, the full coverage probability on information nodes is effectively ensured, and meanwhile the method has the advantages of ensuring linear code compiling complexity and partial recovery of the middle nodes and theoretically proving the asymptotic performance of the SPDD.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
Construction method of LT fountain code codability distribution
ActiveCN105490771AReduce decoding overheadImprove performanceError preventionSoliton distributionFountain code
The invention provides a construction method of degree distribution of LT codes. The method first adjusts a binary system degree distribution, then organically combines the binary system degree distribution with robust soliton distribution, and further optimizes a degree distribution function through optimization of a translatable set value, thereby obtaining degree distribution which also has relatively good performance when code length of source data is short, i.e., binary system-robust soliton distribution is corrected. The corrected binary system-robust soliton distribution is utilizes to perform LT fountain coding on the source data, decoding spending can be reduced, decoding efficiency can be improved, and fountain codes can be well applied to the communication fields.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Method and device for generating code rate compatible with low density parity check (LDPC) codes and hybrid automatic repeat request (HARQ) schemes
InactiveCN102651652ALow degreeReduce control overheadError correction/detection using multiple parity bitsTheoretical computer scienceLow-density parity-check code
The invention relates to the technical field of mobile communication channel coding, in particular to a method and a device for generating code rate compatible with quasi-cyclic low density parity check (LDPC) codes. The method comprises the following steps that: the degree distribution of high-code-rate quasi-cyclic LDPC codes and the low-code-rate requirement of a system are obtained, and the degree distribution of low-code-rate quasi-cyclic LDPC codes is designed; variable nodes to be expanded and check nodes to be resolved in the high-code-rate quasi-cyclic LDPC codes in the low-code-rate quasi-cyclic LDPC code constructing process are determined; check matrixes of the low-code-rate quasi-cyclic LDPC codes are constructed on the basis of a constructing method and the limitation of the low-code-rate quasi-cyclic LDPC codes on the check matrix check part structure; and the check bits of the obtained quasi-cyclic LDPC codes are interwoven, and then, code rate compatible codes are obtained through residue deletion. The embodiment of the invention also provides the device for implementing the method and provides hybrid automatic repeat request (HARQ) schemes based on the code rate compatible quasi-cyclic LDPC codes.
Owner:HUAWEI TECH CO LTD
Method for automatically estimating visual significance of image and video
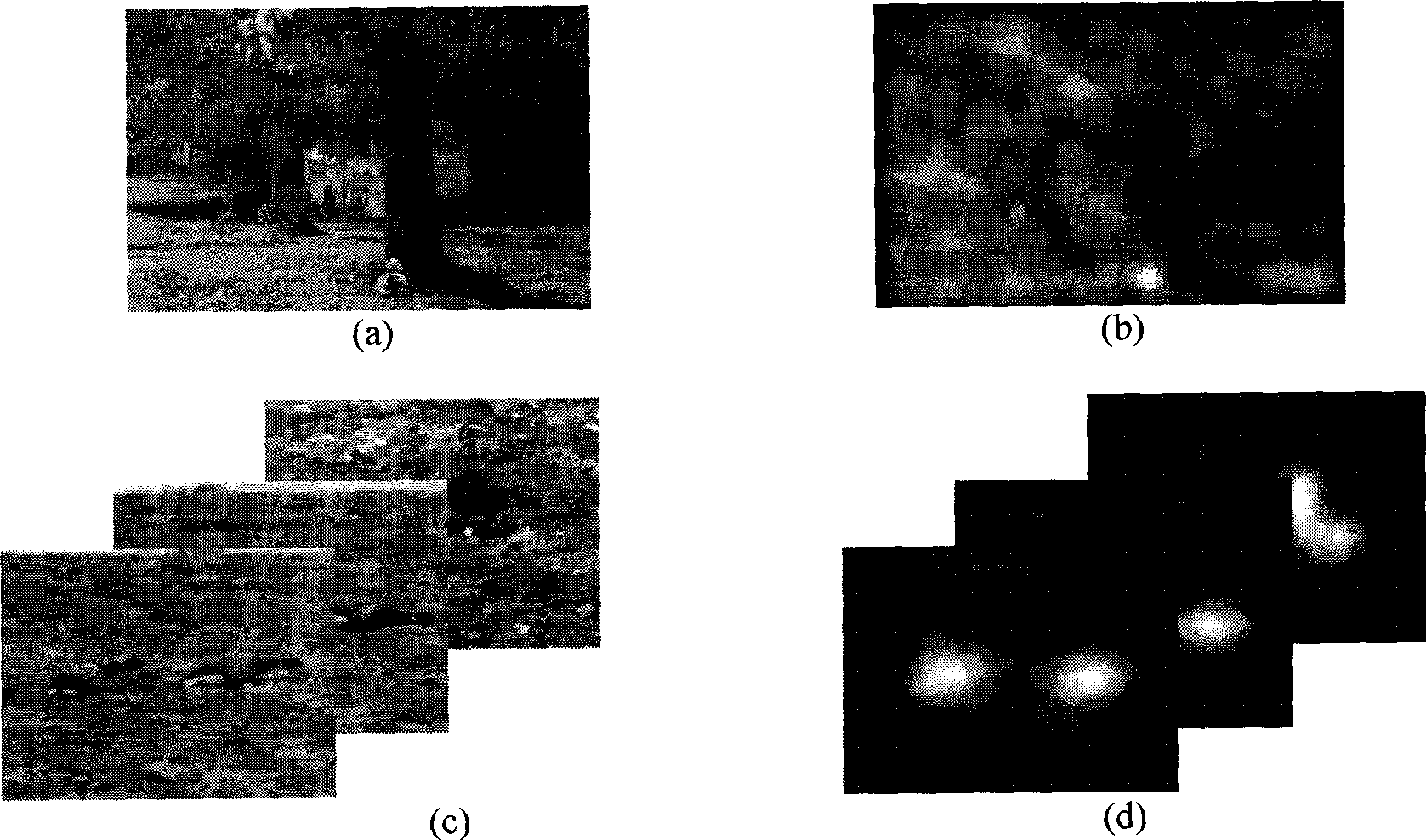
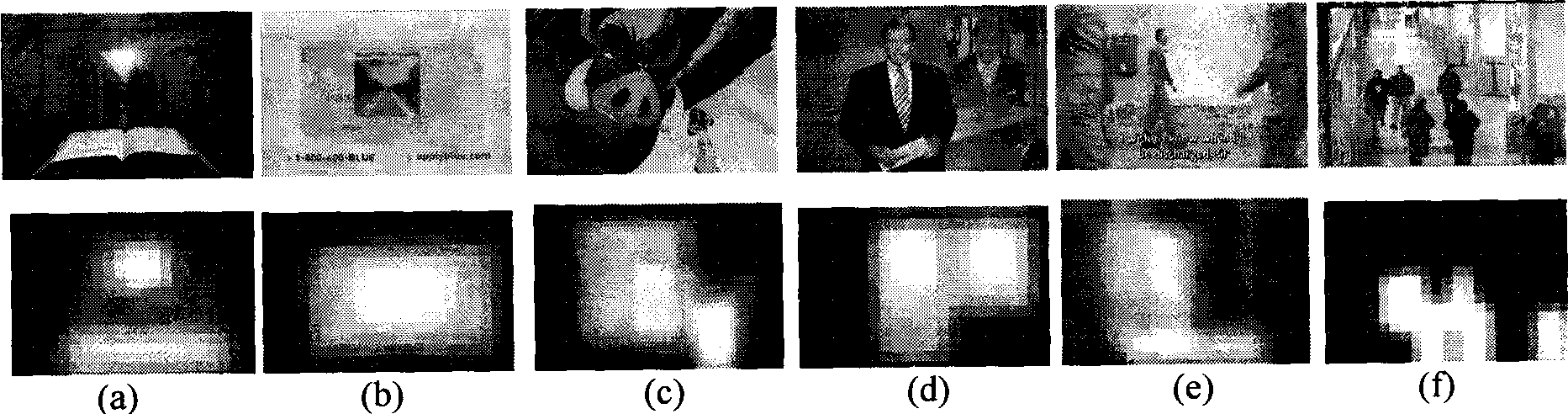
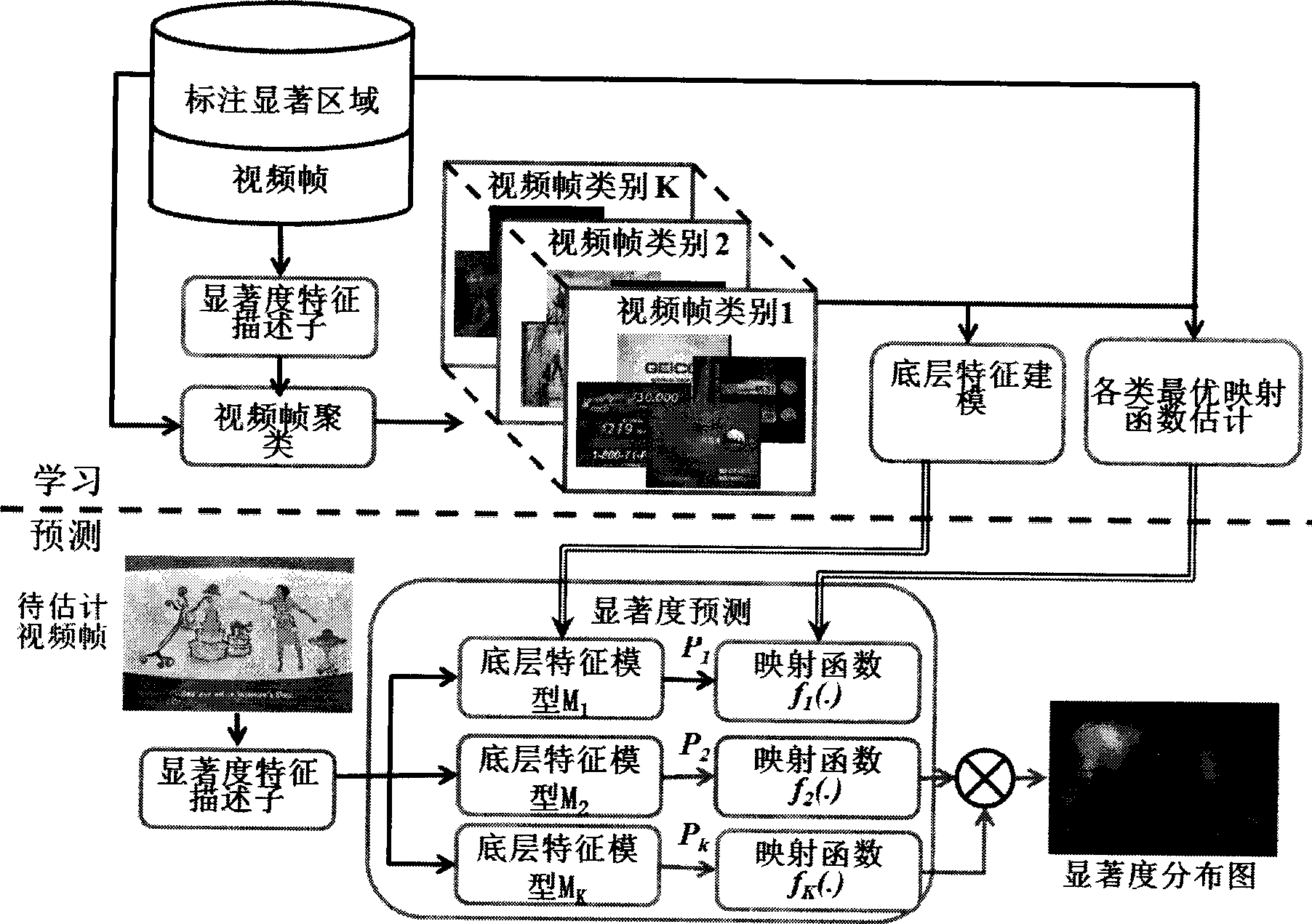
InactiveCN101477633AQuick calculationAccurate calculationCharacter and pattern recognitionSpecial data processing applicationsPattern recognitionVideo processing
The invention relates to an image and video processing method, in particular to a method for automatically estimating vision significant degree of video content by machine learning. The method comprises the following steps: automatically dividing training samples into a plurality of types; learning each type of the training samples to obtain optimal 'sample characteristics-significant degree distribution map' mapping function, and modeling bottom characteristics of each type of the training samples; and determining which type of a sample to be estimated belongs to according to the bottom characteristics, and calculating the significant degree distribution map according to the corresponding to 'sample characteristics-significant degree distribution map' mapping function. The method can rapidly and effectively estimate vision significant degree distribution map of various kinds of multimedia information such as video and images.
Owner:PEKING UNIV
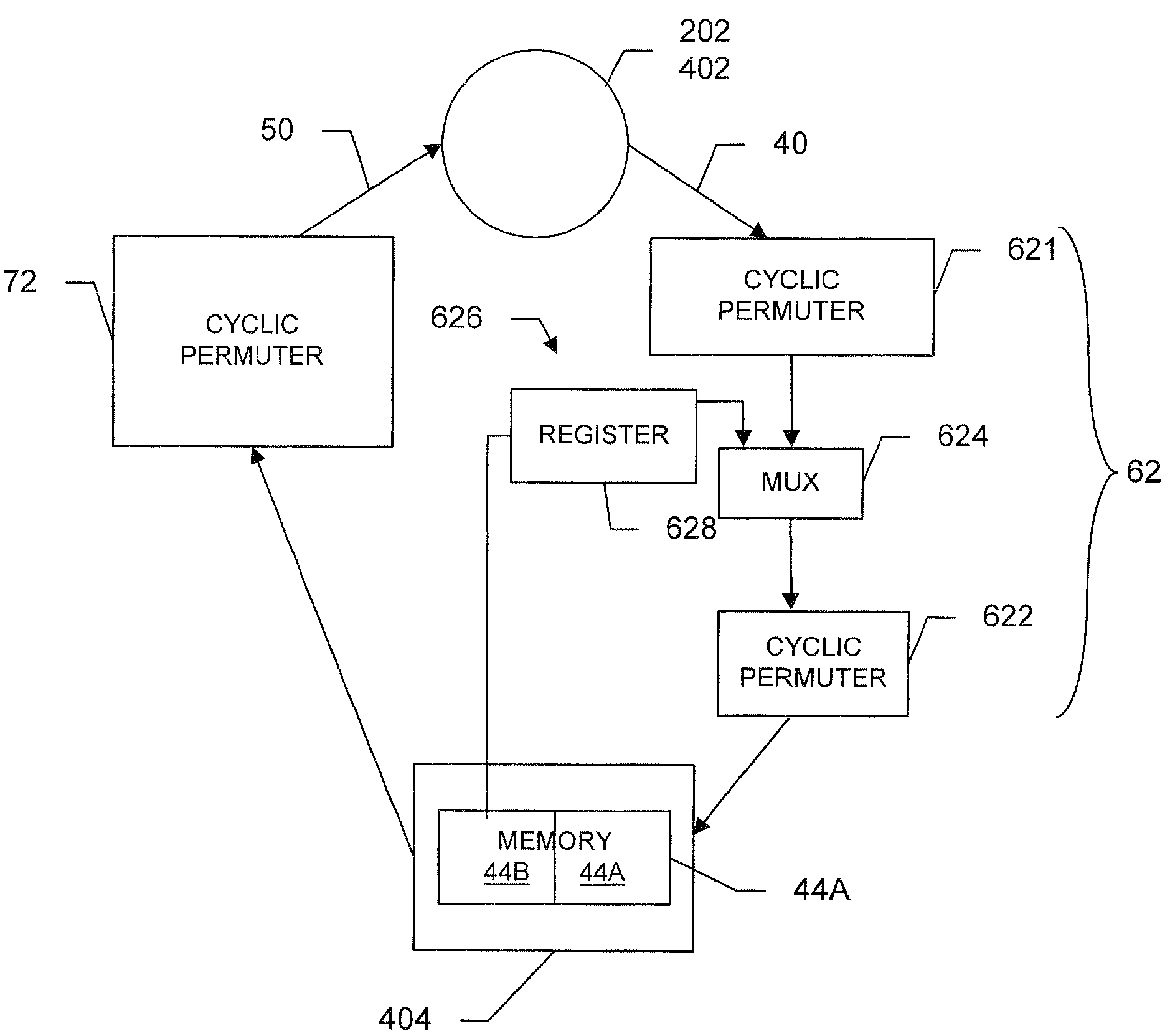
Node processor for use with low density parity check decoder using multiple variable node degree distribution codes
A decoding system for use with different degree parity constraint nodes and highly parallel processing operates by passing messages to variable nodes based on updated states of first and second check nodes, processing messages from the variable nodes and updating states of first and second check nodes in a decoder with Z processors that operate in parallel, further processing the updated state information for the second check nodes to coordinate the states of N=Z / z sets of second check nodes, where z is the number of bits associated with the second check nodes, and repeating the process utilizing the coordinated states of the second check nodes as the updated states of the second check nodes.
Owner:SEAGATE TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com