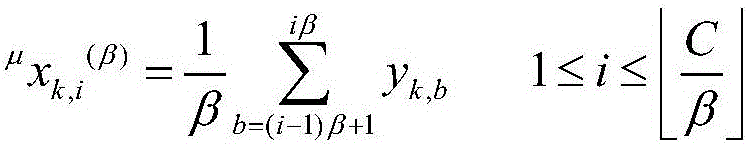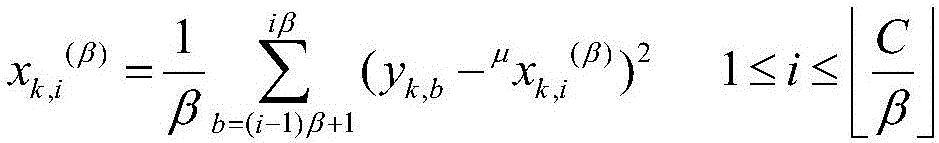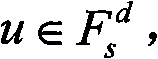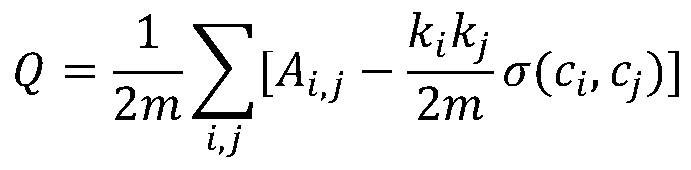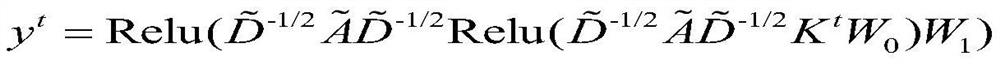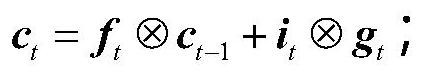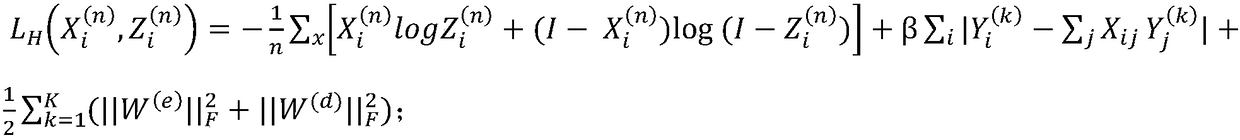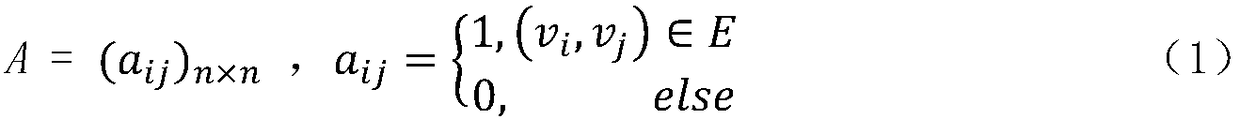Patents
Literature
1393 results about "Adjacency matrix" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In graph theory and computer science, an adjacency matrix is a square matrix used to represent a finite graph. The elements of the matrix indicate whether pairs of vertices are adjacent or not in the graph.
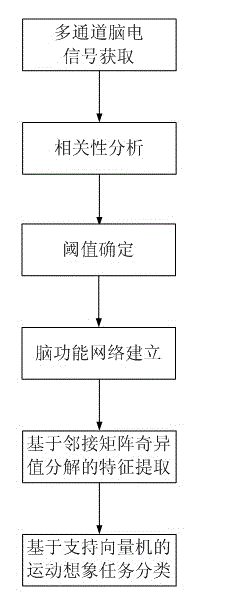
Electroencephalogram feature extracting method based on brain function network adjacent matrix decomposition
InactiveCN102722727AIgnore the relationshipIgnore coordinationCharacter and pattern recognitionMatrix decompositionSingular value decomposition
The invention relates to an electroencephalogram feature extracting method based on brain function network adjacent matrix decomposition. The current motion image electroencephalogram signal feature extraction algorithm mostly focuses on partially activating the qualitative and quantitative analysis of brain areas, and ignores the interrelation of the bran areas and the overall coordination. In light of a brain function network, and on the basis of complex brain network theory based on atlas analysis, the method comprises the steps of: firstly, establishing the brain function network through a multi-channel motion image electroencephalogram signal, secondly, carrying out singular value decomposition on the network adjacent matrix, thirdly, identifying a group of feature parameters based on the singular value obtained by the decomposition for showing the feature vector of the electroencephalogram signal, and fourthly, inputting the feature vector into a classifier of a supporting vector machine to complete the classification and identification of various motion image tasks. The method has a wide application prospect in the identification of a motion image task in the field of brain-machine interfaces.
Owner:启东晟涵医疗科技有限公司
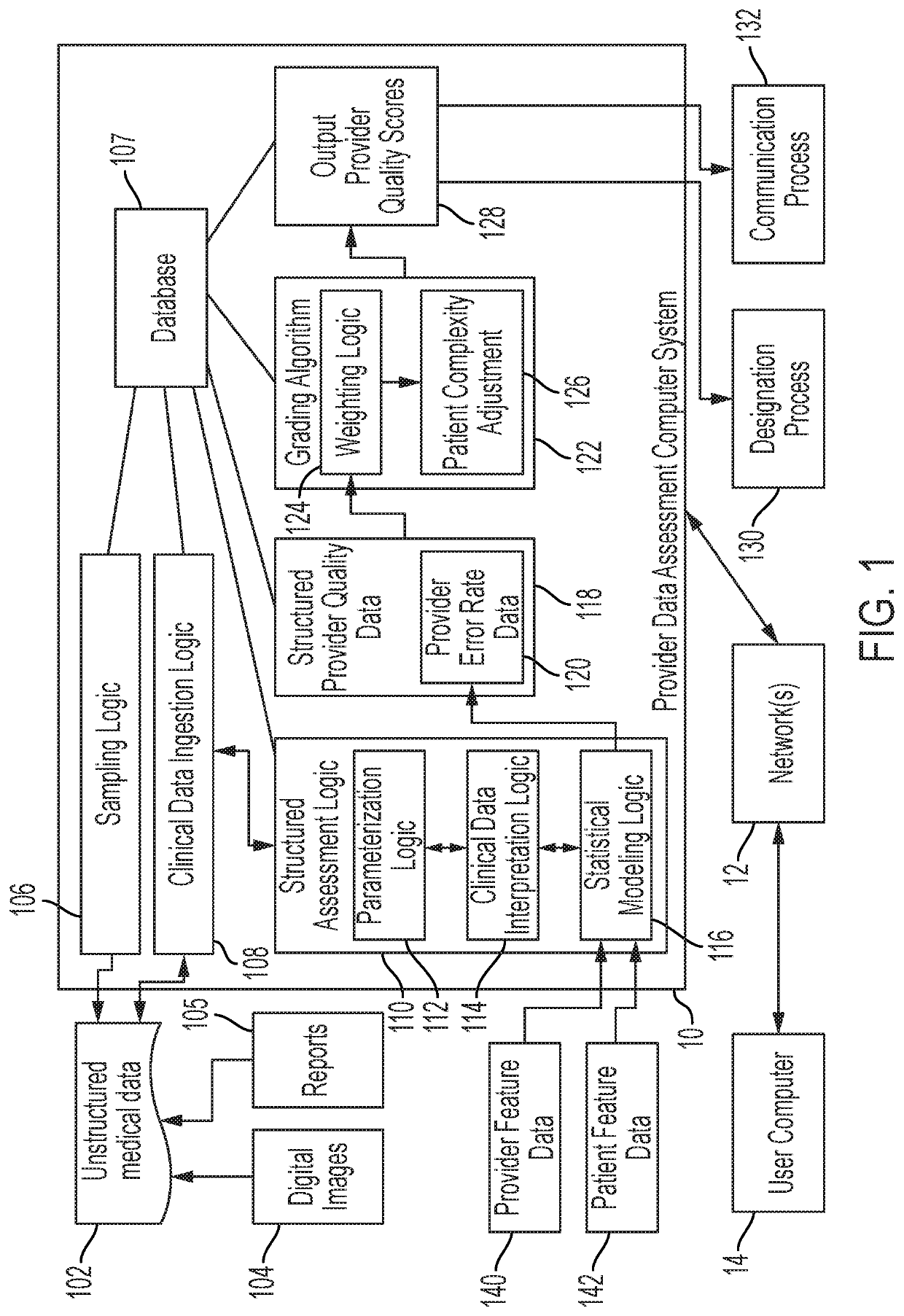
Computer-implemented natural language understanding of medical reports
ActiveUS20200334416A1High feature weightLow frequency of occurrenceMathematical modelsMedical data miningLanguage understandingNatural language understanding
A natural language understanding method begins with a radiological report text containing clinical findings. Errors in the text are corrected by analyzing character-level optical transformation costs weighted by a frequency analysis over a corpus corresponding to the report text. For each word within the report text, a word embedding is obtained, character-level embeddings are determined, and the word and character-level embeddings are concatenated to a neural network which generates a plurality of NER tagged spans for the report text. A set of linked relationships are calculated for the NER tagged spans by generating masked text sequences based on the report text and determined pairs of potentially linked NER spans. A dense adjacency matrix is calculated based on attention weights obtained from providing the one or more masked text sequences to a Transformer deep learning network, and graph convolutions are then performed over the calculated dense adjacency matrix.
Owner:COVERA HEALTH
Financial network unusual transaction community finding method based on information entropy
InactiveCN104199832AEfficient deploymentCloselyFinanceSpecial data processing applicationsModularityCommunity evaluation
The invention discloses a financial network unusual transaction community finding method based on information entropy. The method includes the specific steps of firstly, analyzing the process and the mode of an unusual transaction, and extracting features of block transactions and suspicious transactions; secondly, storing transaction amounts and traction frequency information of accounts through an adjacent matrix so as to quantize the features; thirdly, defining the information entropy of nodes; fourthly, conducting community division and finding on the financial network nodes according to the financial network unusual transaction community finding method based on the information entropy; fifthly, evaluating the community finding result. Firstly, accuracy of unusual transaction account identification and unusual transaction communication division which are achieved according to the method is calculated, and then the structure of the unusual transaction community is evaluated through the community evaluation index modularity Q. The community finding method based on the information entropy is applied to the anti-money laundering field for the first time, the money laundering accounts can be identified and tracked by finding the unusual transaction community, and unusual transactions can be prevented by analyzing the relations and the transaction laws between money laundering accounts.
Owner:XIAN UNIV OF TECH
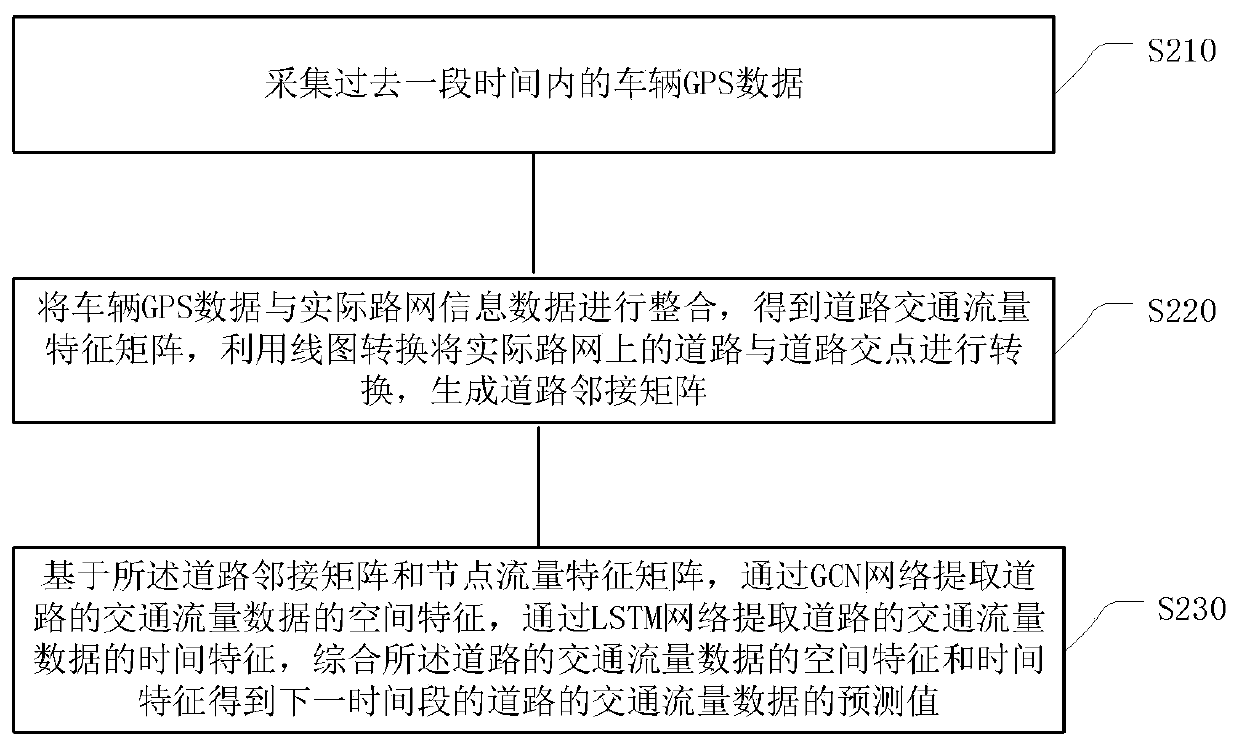
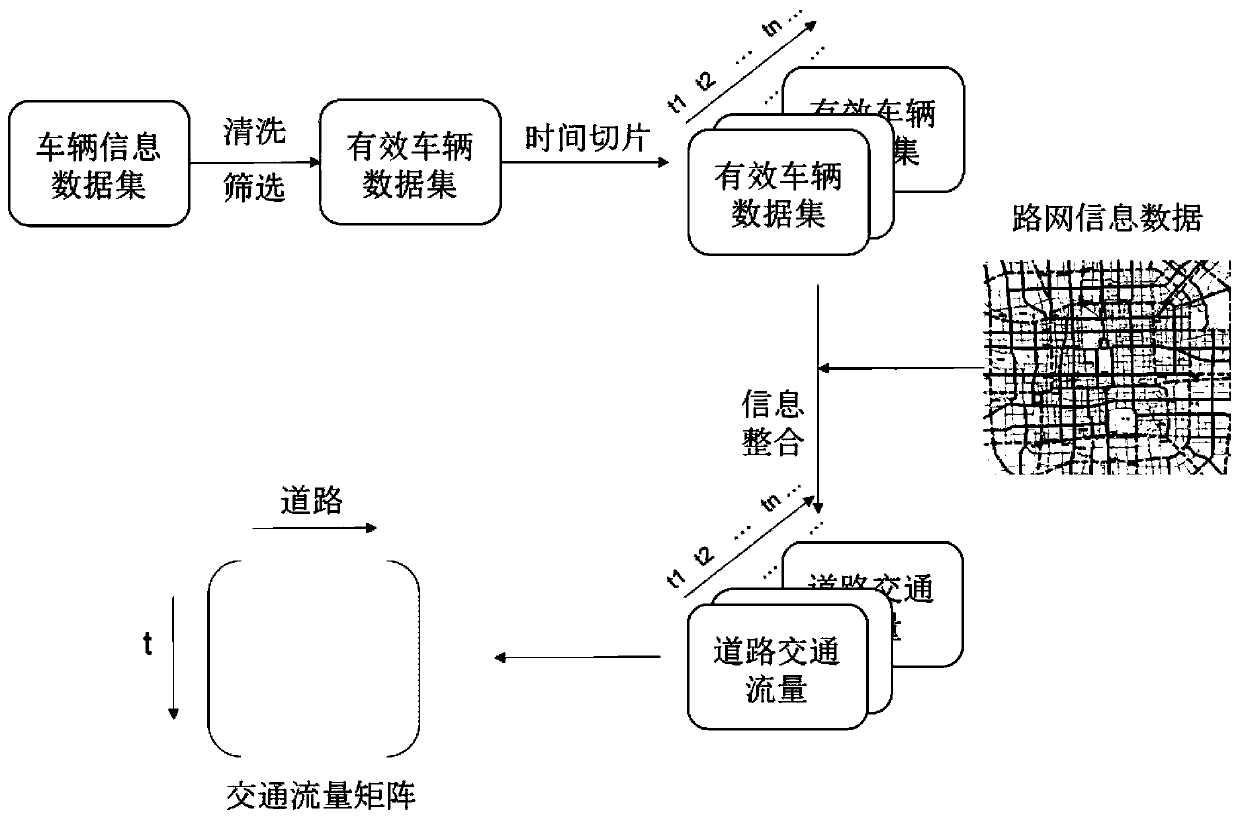
Prediction method of road traffic flow based on graph convolution network
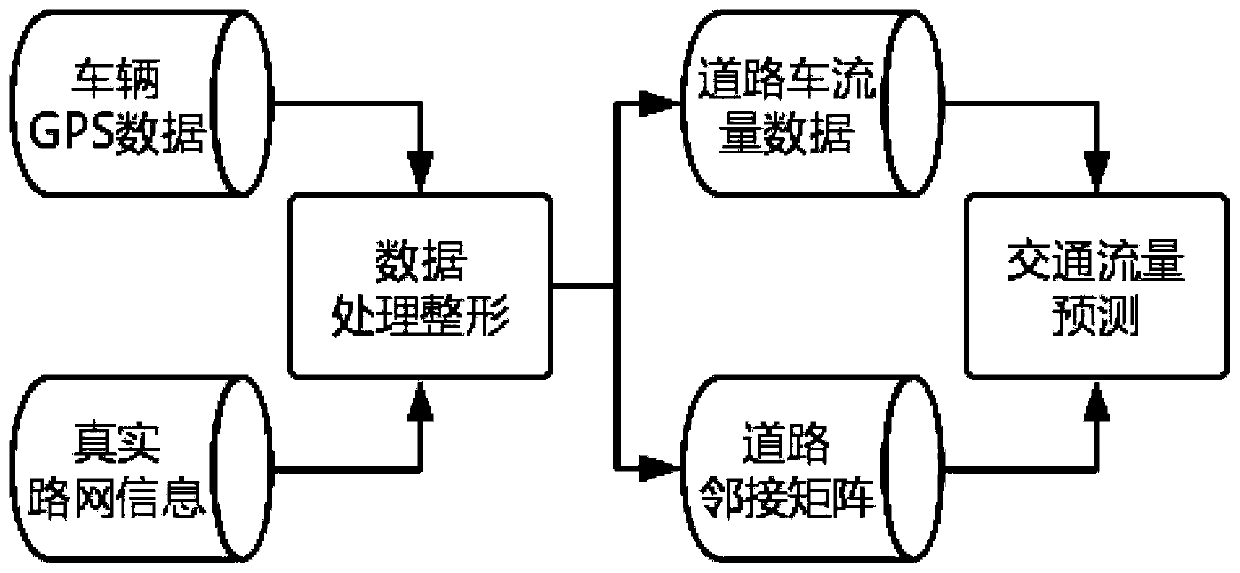
ActiveCN110264709AAchieve forecastHelp mismatchDetection of traffic movementData switching networksTraffic capacityRoad networks
The invention provides a prediction method of a road traffic flow based on a graph convolution network. The method comprises the following steps of collecting vehicle GPS data in the past period of time; integrating the vehicle GPS data with actual road network information data to obtain a road traffic flow characteristic matrix, and converting a road and a road intersection point in the actual road network through line graph conversion to generate a road adjacency matrix; and based on the road adjacency matrix and the road traffic flow characteristic matrix, acquiring a predicted value of traffic flow data of the road in the next time period by using a spatial characteristic and a time characteristic of traffic flow data of the integrated road of a GCN network and an LSTM network. Through integrally using the spatial characteristic of the road traffic flow data extracted by GCN and the time characteristic of the road traffic flow data extracted by LSTM, and combining a time period characteristic and a weather characteristic, the road traffic flow data is predicted, and a prediction effect is better than the prediction effect acquired through using only time characteristic or the spatial characteristic.
Owner:BEIJING JIAOTONG UNIV
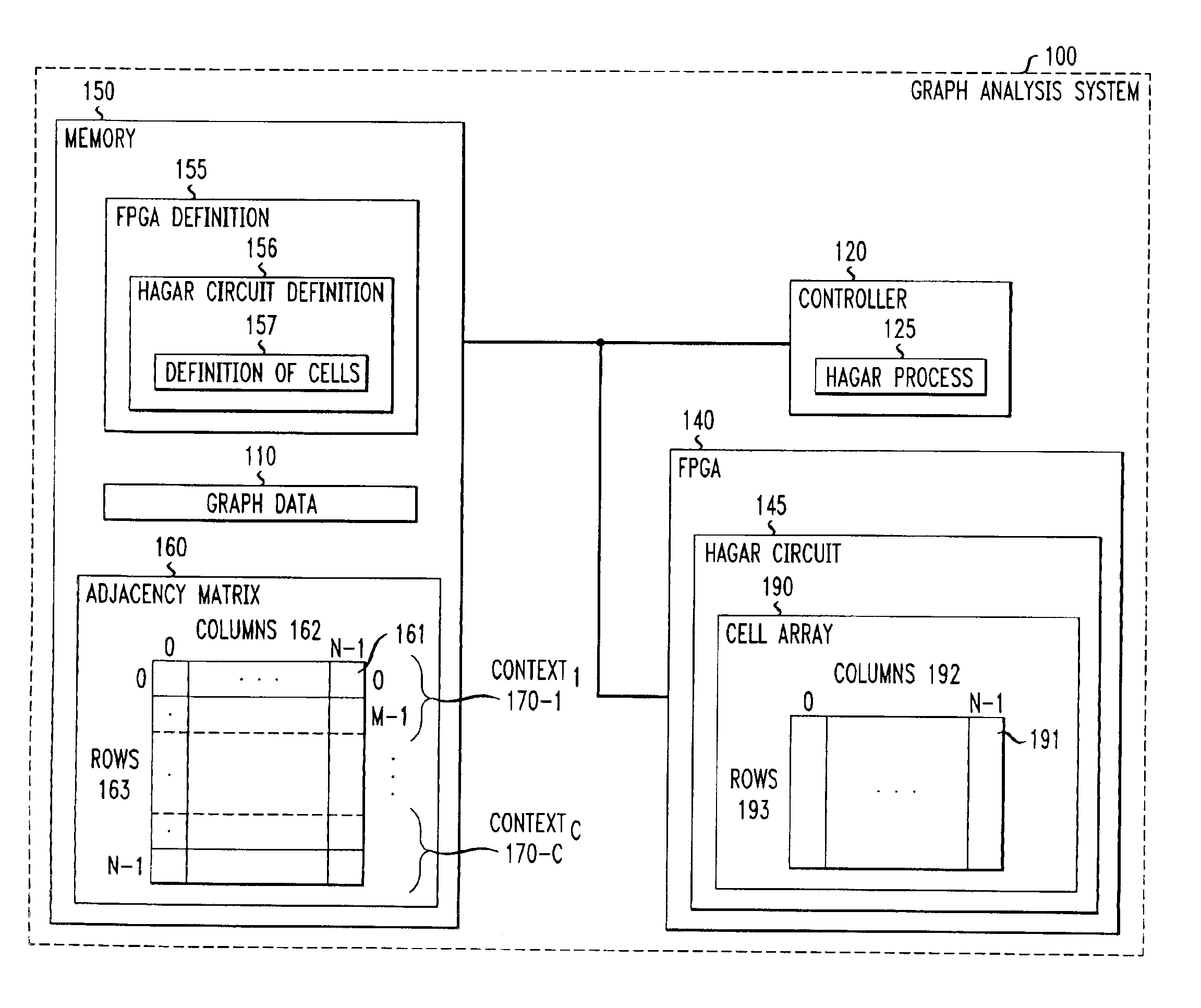
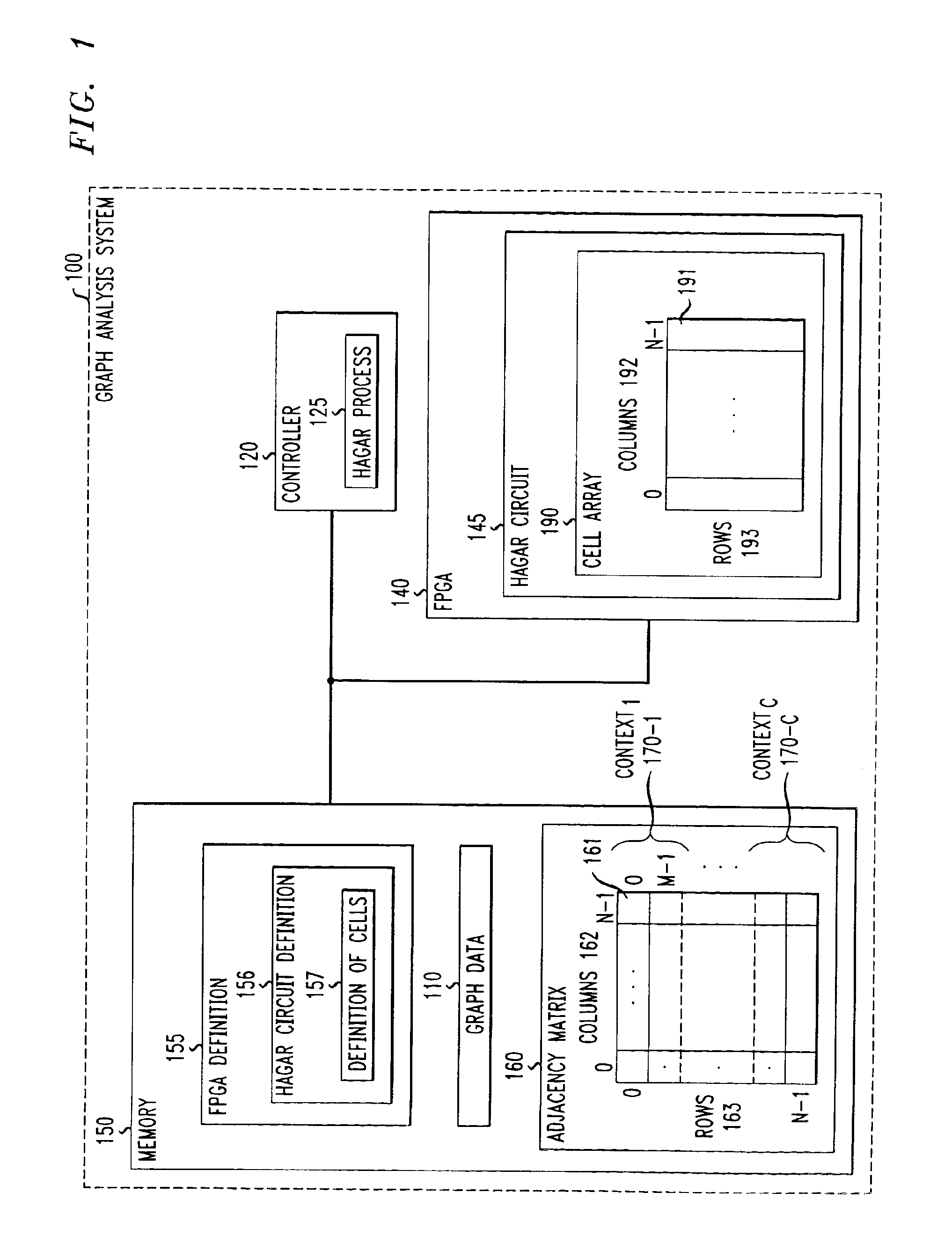
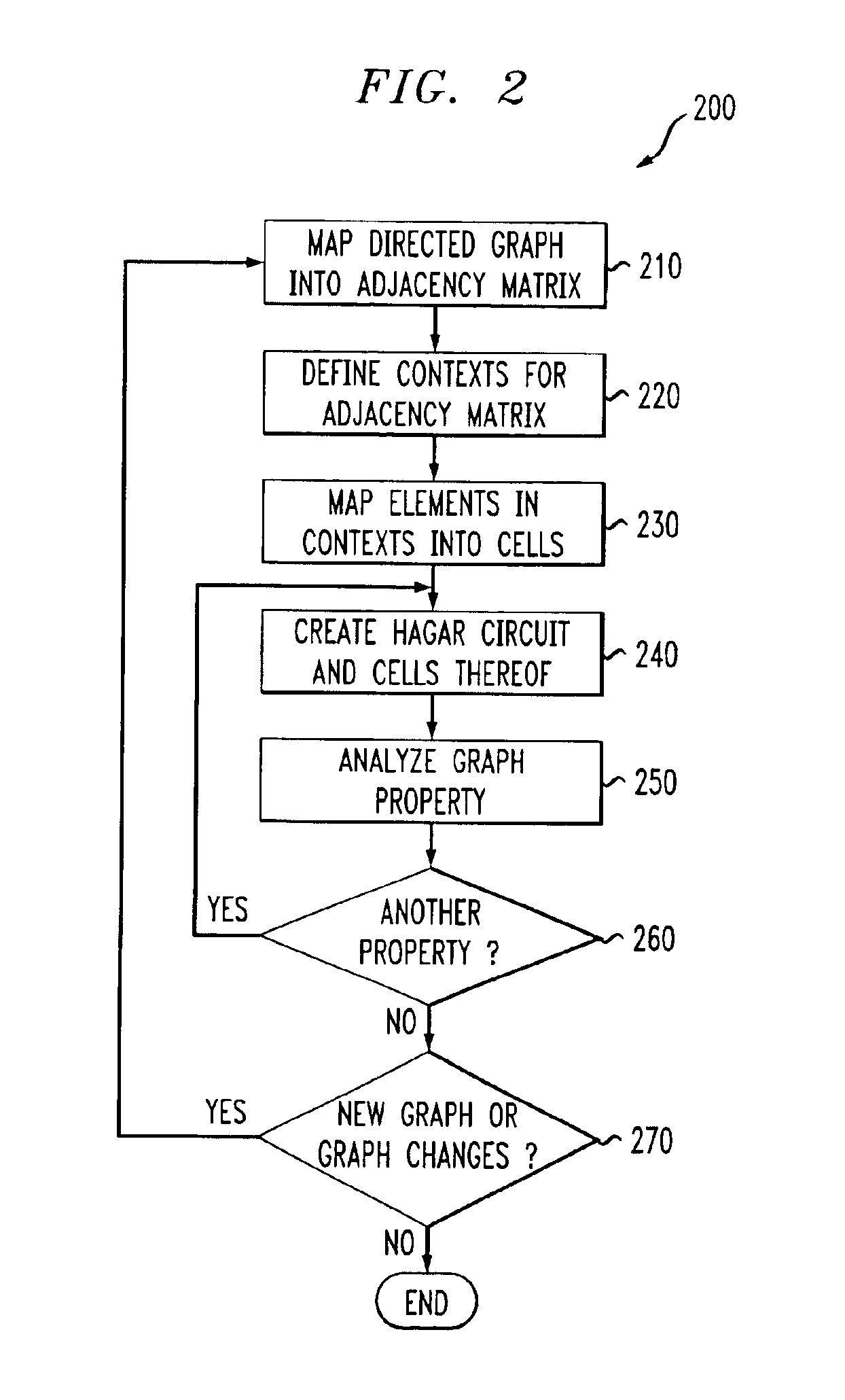
Apparatus and methods for analyzing graphs
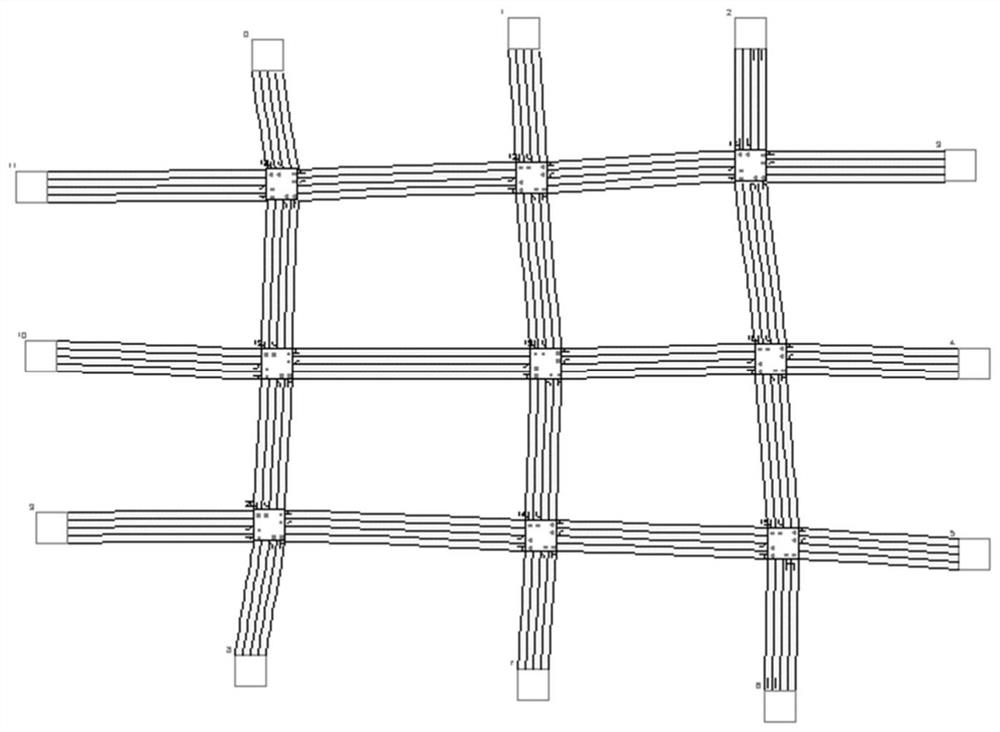
A plurality of hardware cells are defined, wherein at least a given one of the hardware cells corresponds to sets of vertices from a graph having vertices and edges interconnecting the vertices, and each of the sets are from a corresponding one of a number of portions of the graph. The given hardware cell is adapted to select one of the sets of vertices and to define for the selected set of vertices whether an edge exists in the graph between the vertices in the selected set. The hardware cells are used to analyze one or more properties of the graph, such as reachability or shortest path. The graph is mapped into an adjacency matrix, which contains a number of contexts, each context having a number of elements, and where the given hardware cell corresponds to multiple contexts of the adjacency matrix.
Owner:LUCENT TECH INC
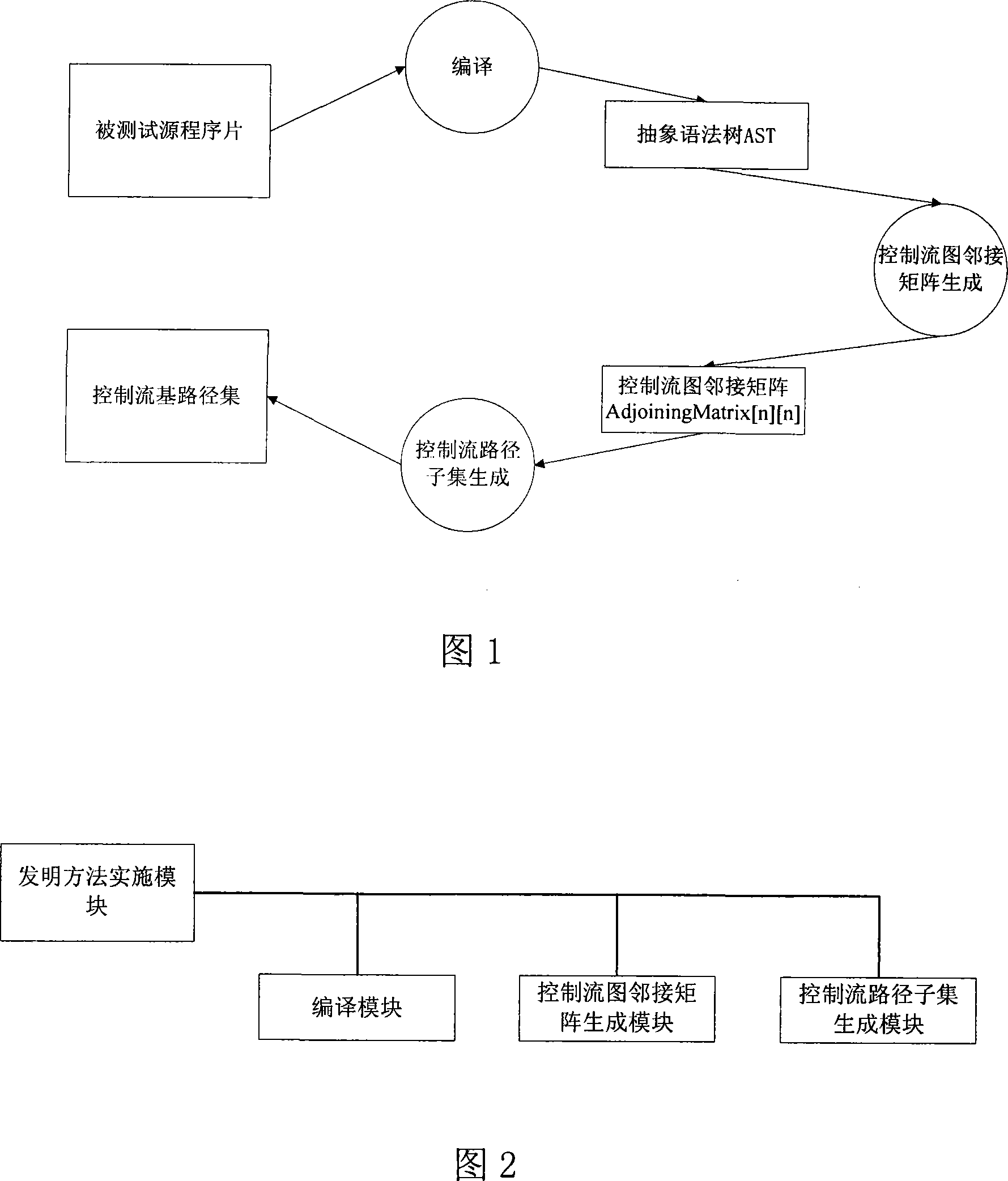
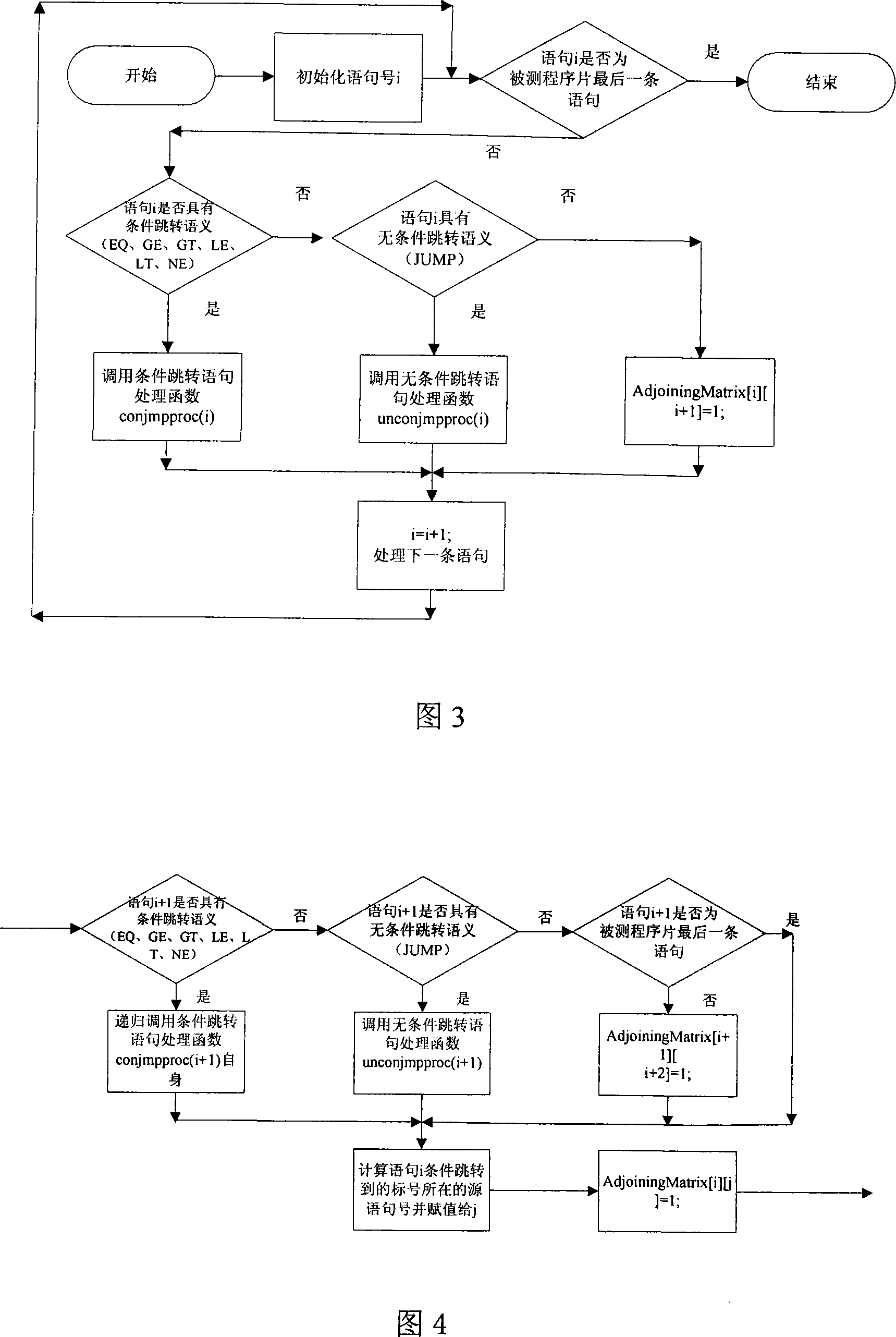
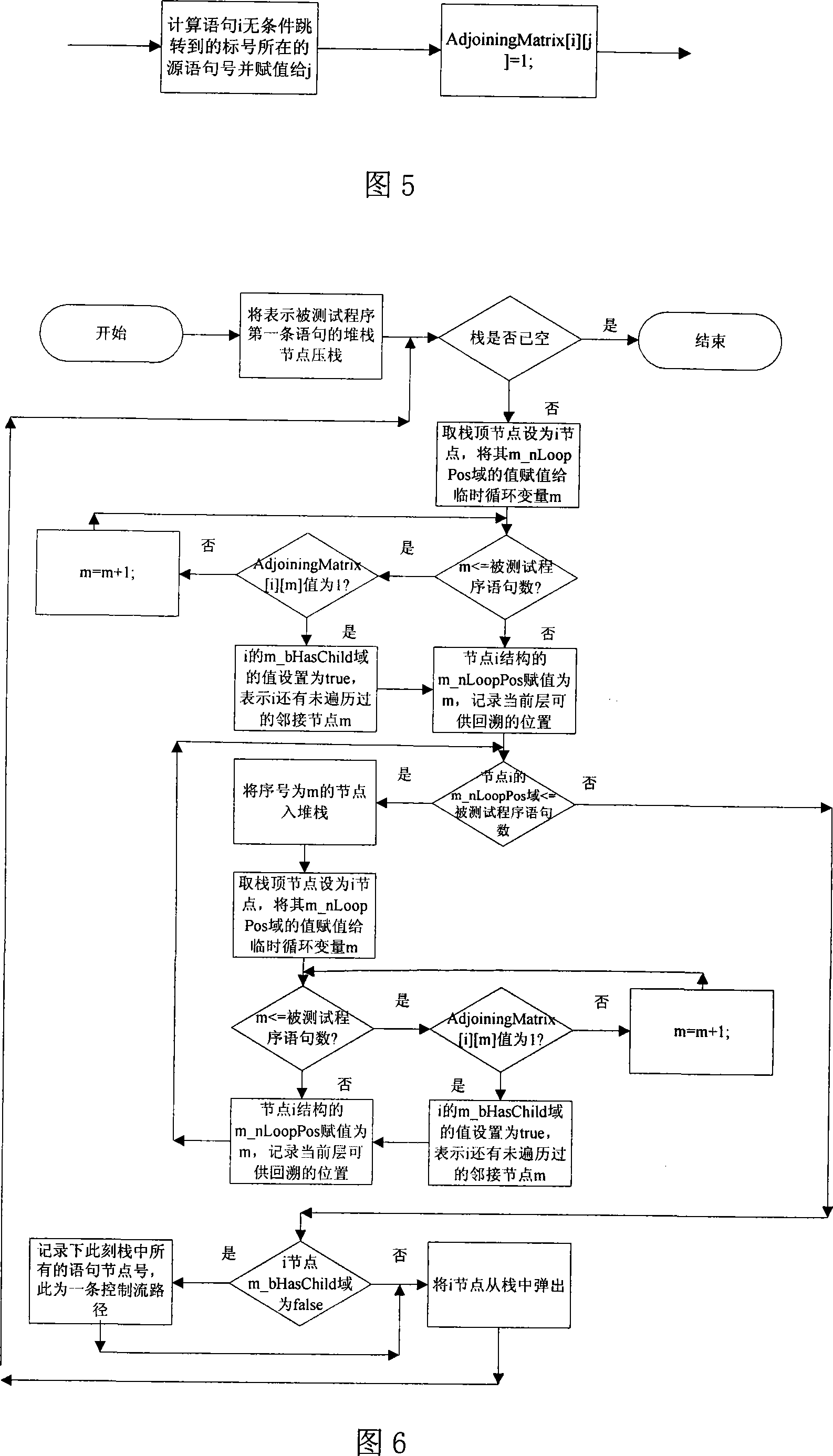
Test program control stream path set creation method based on base path
InactiveCN101216803ASolve the completeness problemSolving automation problemsSoftware testing/debuggingPath generationProgram testing
The invention pertains to a path testing in a program testing. The concept of a program control flow base path is defined through bringing in the concept of base in mathematics, a data structure showing a program structure of a source program slice is obtained by using a compiler module first; then through traversing the data structure, a control flow path generating algorithm is utilized to generate a subset compiler module of a program control flow path which is based on a base path to interpret the semanteme on a tested source program, an abstract syntax tree structure showing the structural information of the tested program control flow is output. An adjacency matrix of a control flow graph generates a module ergodicity abstract syntax tree structure, and generates the adjacency matrix representation of a program flow chart. A control flow path subset generating module acquires the control flow information of the tested program through traversing the adjacency matrix, traverses the adjacency matrix by adopting a depth-first multiple backtracking method, and processes sentence nodes, thus a program control flow path subset based on the base path is generated. The method has the outstanding advantages in generating results and flows, and can be widely used in the engineering practice of a path cover testing in a software structure testing.
Owner:SICHUAN UNIV
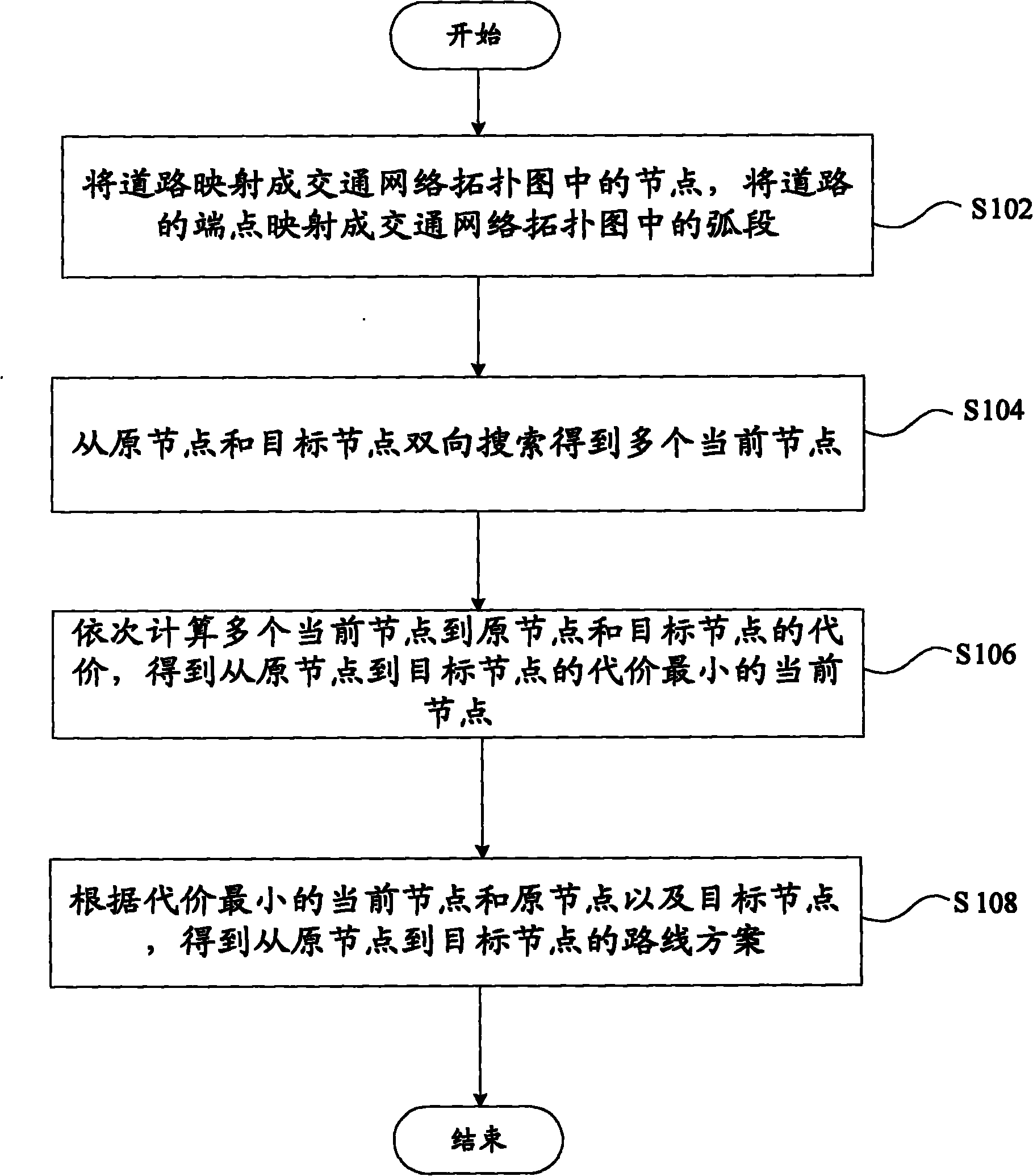
Path planning method and system
InactiveCN101944095AImprove search efficiencyReduce complexityInstruments for road network navigationSpecial data processing applicationsShortest path planningTraffic network
The invention provides a path planning method and system, wherein the method comprises the following steps: mapping roads into nodes in a traffic network topological graph and mapping endpoints of the roads into arc sections in the traffic network topological graph; searching bi-directionally from an original node and a destination node, thus obtaining a plurality of current nodes; calculating the cost from a plurality of current nodes to the original node and the destination node sequentially and obtaining a current node of the minimum cost from the original node to the destination node; and according to the current node of the minimum cost, the original node and the destination node, obtaining a path plan from the original node to the destination node. The method and the system overcome the defect in the prior art that a Dijkstra method of adjacent matrices is adopted to store traffic network topological data, although whether (i; j) is a network edge can be queried within the time O (1), the complexities for querying relevant nodes which are the most significant for the shortest path plan are all O (n), which causes higher query complexity.
Owner:GUANGDONG RITU INFORMATION SYST
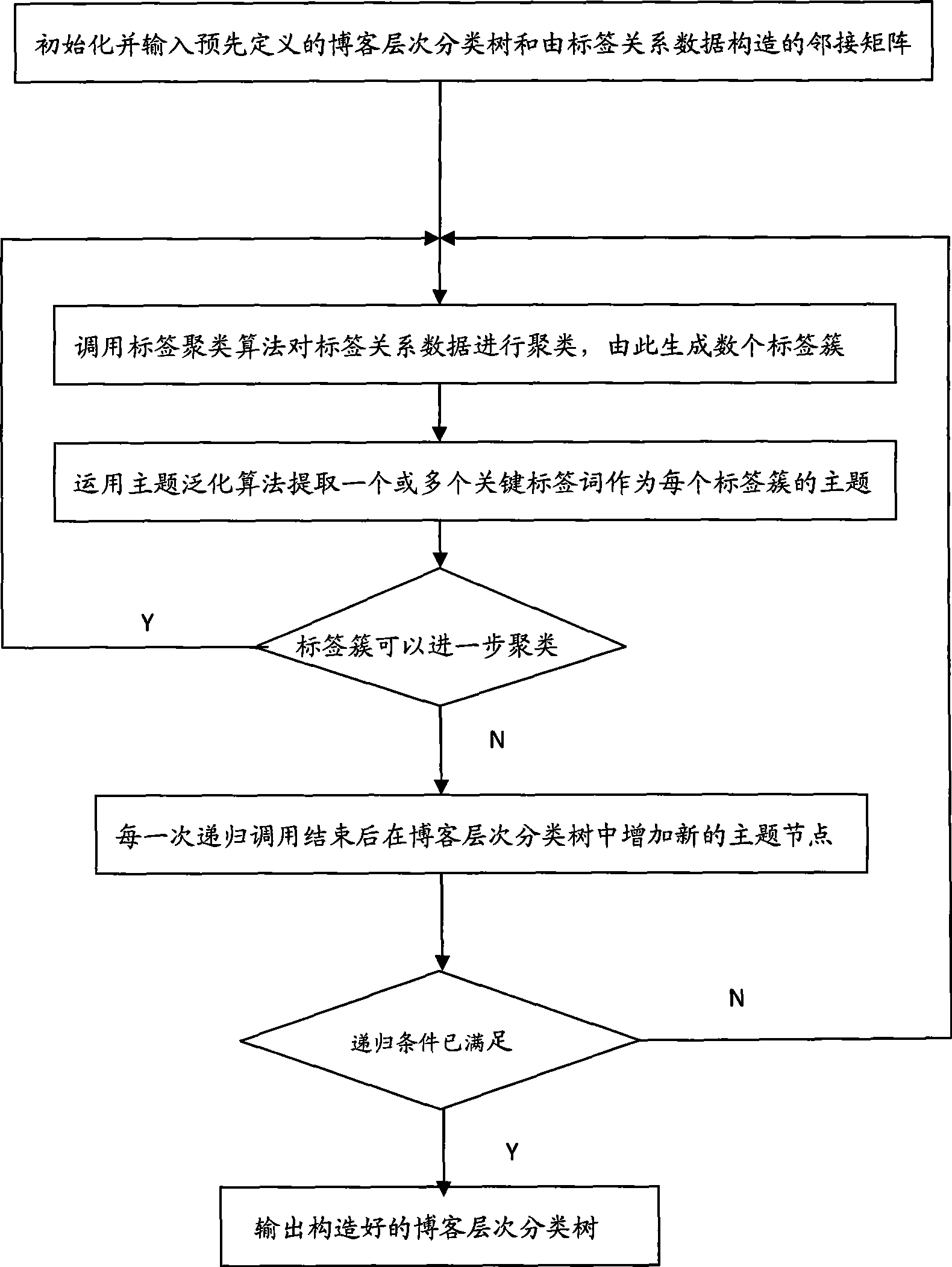
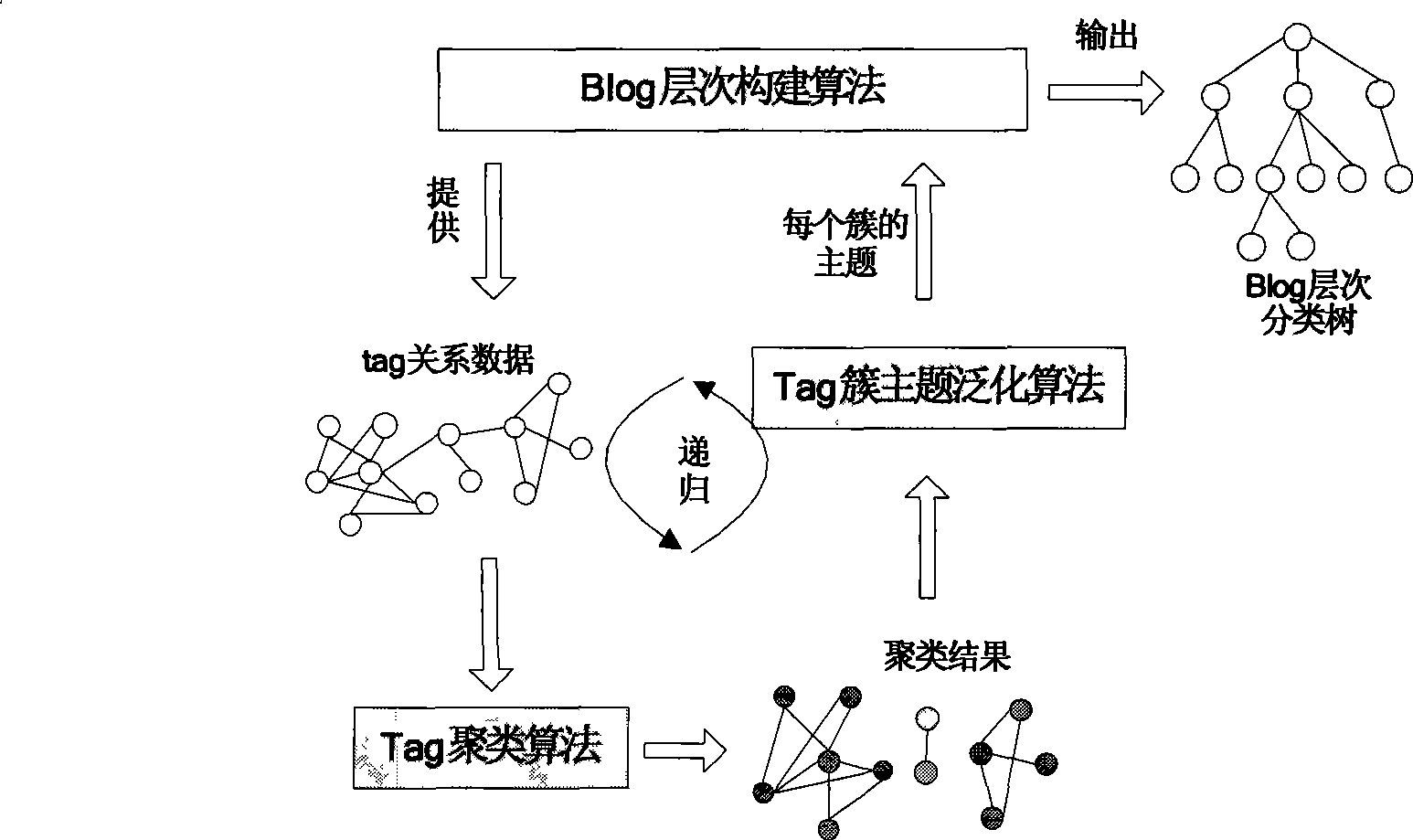
Blog hierarchy classification tree construction method based on label clustering
InactiveCN101430708ASolve searchSolve mining problemsSpecial data processing applicationsCluster algorithmData mining
The invention relates to a method for constructing a blog hierarchical classification tree based on tag clustering. The method comprises the following steps: firstly, initializing and inputting a predefined blog hierarchical classification tree and an adjacency matrix which is constructed by tag relational data; secondly, calling a tag clustering algorithm to cluster the tag relational data so as to generate a plurality of tag clusters; thirdly, applying a theme generalization algorithm to extract one or a plurality of key tag words from each tag cluster as a theme of the cluster; fourthly, recursively calling the second step and the third step when the cluster can be further clustered; fifthly, constructing a new hierarchy and increasing a new theme node in the blog hierarchical classification tree after each recursive call is completed; sixthly, outputting a constructed blog hierarchical classification tree after the recursive terminal condition is completely fulfilled. The method is provided by aiming at searching, exploiting, browsing and other problems of blog data, can quickly organize the theme hierarchical relation of mass blog data, and has higher efficiency and accuracy.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
Network security evaluation device based on attack graph adjacent matrix
The invention provides a network security evaluation device based on an attack graph adjacent matrix. The network security evaluation device comprises an information collection device, an atom attack graph generation device, a matrix calculation device, a network safety analyzing device and a result appearing device, wherein the information collection device is used for collecting all information in a network; the atom attack graph generation device is used for generating an initial atom attack graph between a main engine pair needed for carrying out subsequent analysis on network safety; the matrix calculation device is used for converting the generated atom attack graph into the corresponding adjacent matrix and is also used for calculating a corresponding iteration matrix of the adjacent matrix through setting iteration times; the network safety analyzing device is used for obtaining information including a key main engine, a key path and the like on the basis of the finally-generated iteration matrix; the result appearing device is used for visually appearing the found key main engine and key path and a network vulnerability index. The network security evaluation device disclosed by the invention is high in efficiency and is suitable for large-scale and high-speed networks. The network security evaluation device can improve the instantaneity of evaluating a target network. The evaluation accuracy rate is high, and the key path and the key main engine can be accurately recognized. The visualization degree is high so that the network security evaluation device is convenient for a manager to check, analyze and maintain.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
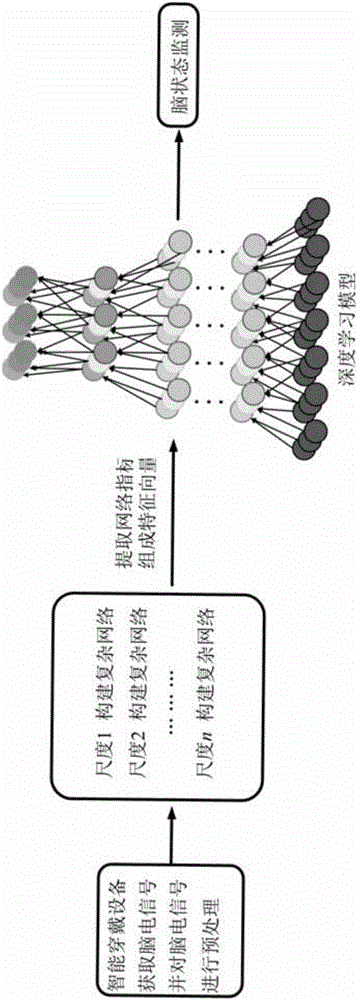
Deep learning model based on multi-scale network and application in brain state monitoring
A deep learning model based on a multi-scale network and application in brain state monitoring are provided. A model establishing method comprises steps of: preprocessing and multi-scale transforming a measured multichannel signal; obtaining a multi-scale weighted recursive network and a cross-recursive rate matrix corresponding to the multi-scale weighted recursive network of the multichannel signal in all scales; extracting the network indexes of the multi-scale weighted recursive network at different scales; at each scale, retaining relatively large elements in the cross recursive rate matrix and obtaining an unweighted adjacent matrix and a multi-scale unweighted recursive network corresponding thereto; for each value of a variable in the set range, obtaining the multi-scale unweighted recursive network and the adjacent matrix corresponding to the multi-scale unweighted recursive network, extracting the network indexes of the multi-scale unweighted recursive network at different scales, calculating the integral of the network indexes when the variable is changed in the set range, and the integral as the final network index of the multi-scale unweighted recursive network under each scale; and training the deep learning model and monitoring a brain state.
Owner:钧晟(天津)科技发展有限公司
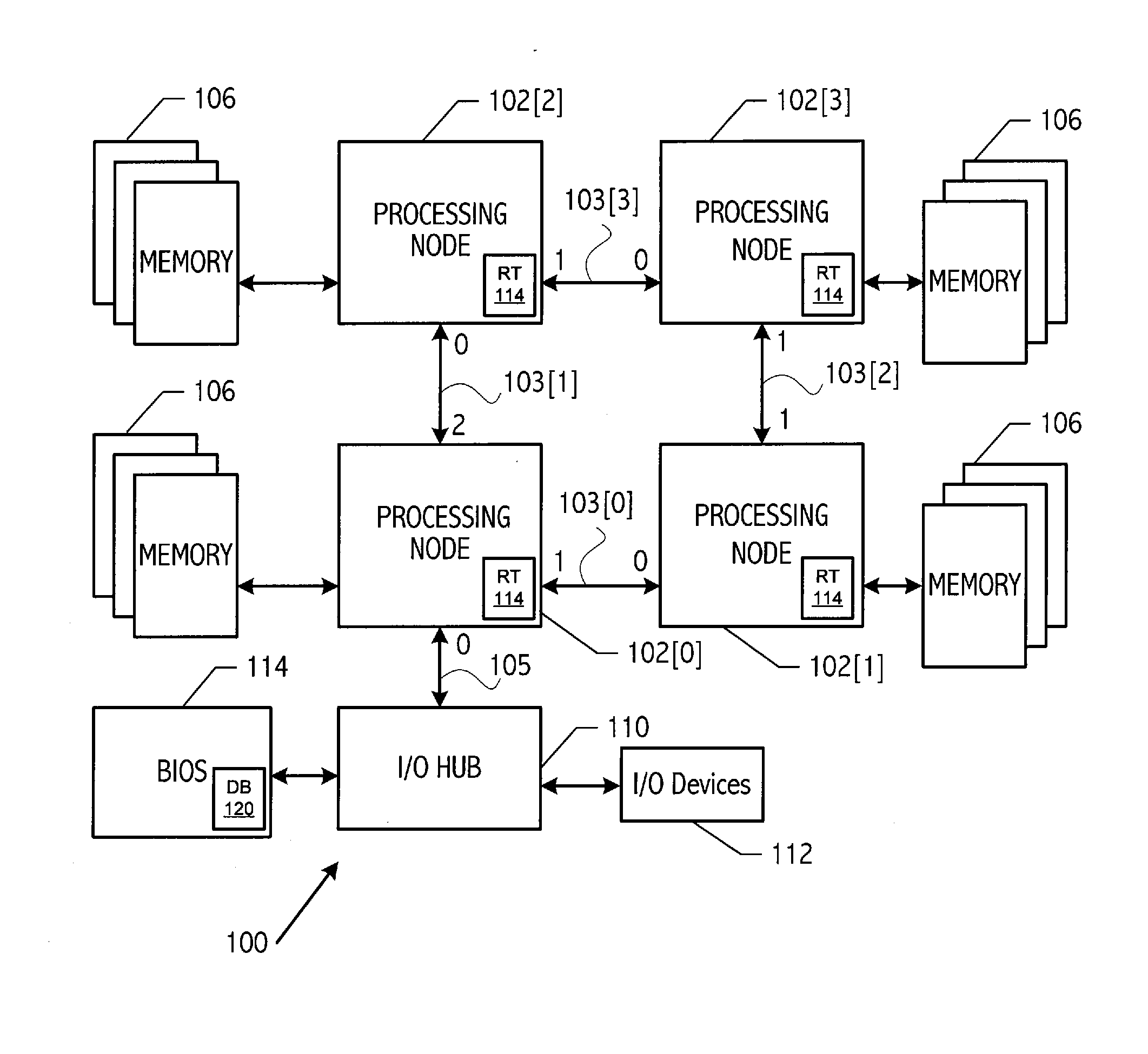
Communication network initialization using graph isomorphism
InactiveUS20090016355A1Reduce effortImprove robustnessData switching by path configurationTelecommunications linkCommunications system
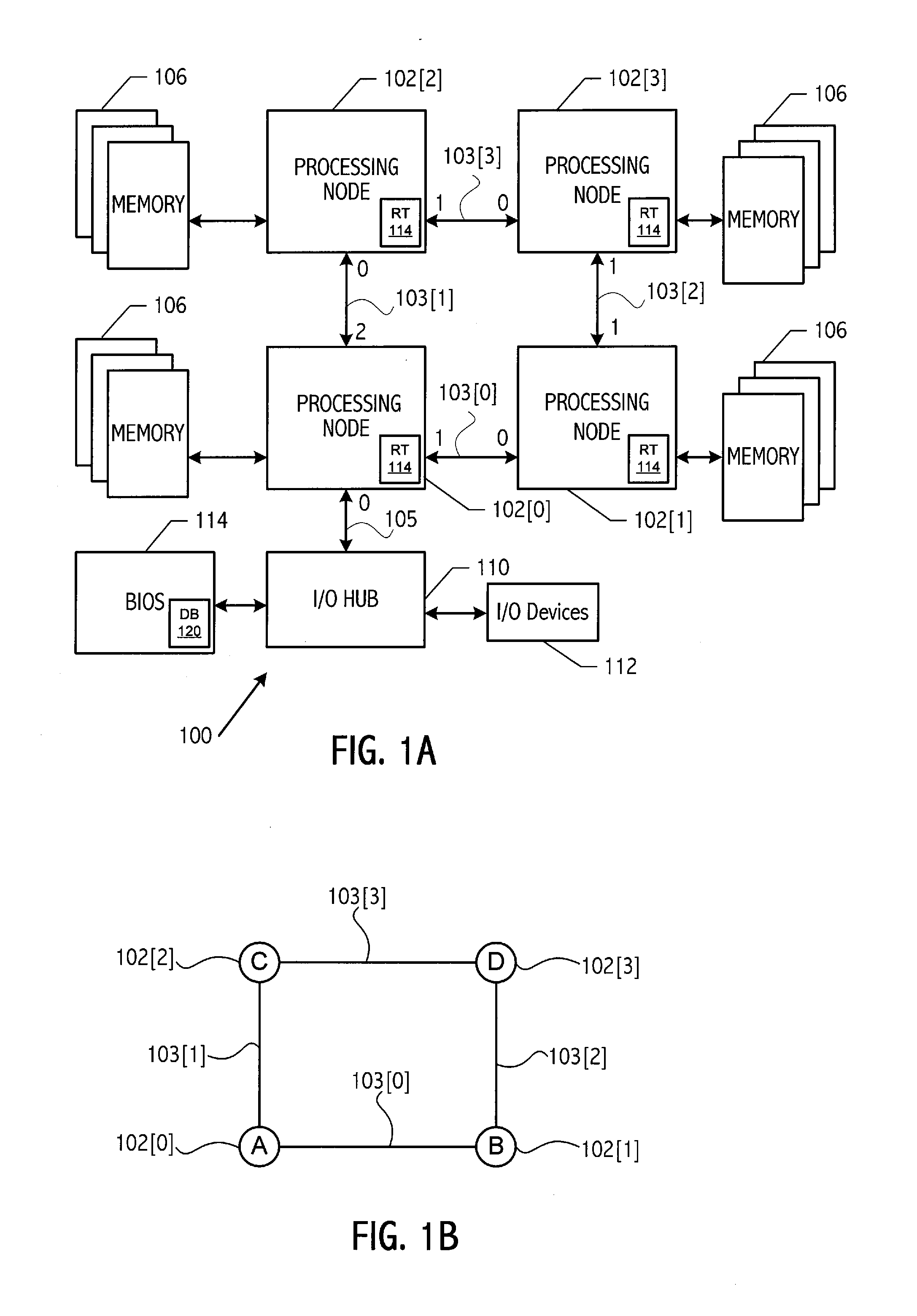
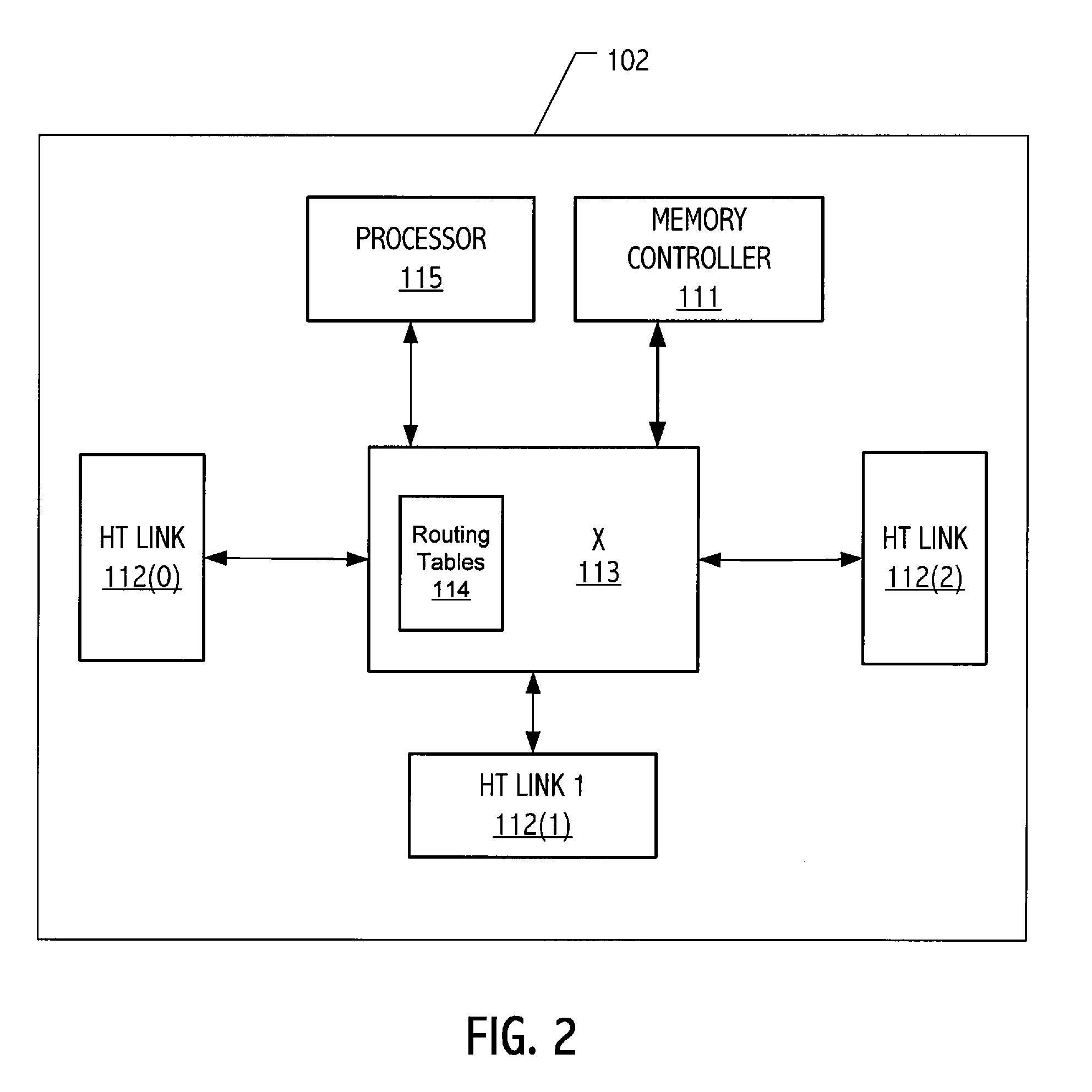
A communication system, such as a computer system, with a plurality of processing nodes coupled by communication links stores a database of abstract topologies that provides a node adjacency matrix and abstract routing between nodes. A breadth-first discovery of the actual communication fabric is performed starting from an arbitrary root node to discover the actual topography. A graph isomorphism algorithm finds a match between the discovered topology and one of the stored abstract topologies. The graph isomorphism algorithm provides a mapping between the ‘abstract’ node numbers and the discovered node numbers. That mapping may be used to rework the stored routing tables into the specific format needed. The computed routing tables are loaded into the fabric starting at the leaf nodes, working back towards the root node (i.e., start loading from the highest node number and work back to the lowest numbered node).
Owner:ADVANCED MICRO DEVICES INC
Multi-rate opportunistic routing method for wireless mesh network
ActiveCN101945432AImprove stabilityImprove throughputError prevention/detection by using return channelNetwork traffic/resource managementWireless mesh networkMulti rate
The invention provides a multi-rate wireless mesh network routing method for opportunistic forwarding based on characteristics of radio broadcasting, which comprises the following steps: after a node transmits data, a plurality of nodes are selected as forwarding nodes; in the early stage of network setup, the nodes acquire a direct link delivery fraction via probe packets and set up an adjacency relation; an adjacency matrix of the total network is set up by using link status packets to switch link information; a node forwarding probability analysis system model is used to deduce a measurement (integrated transmission number) applicable to the presence of arbitrary paths, and a forwarding node selection strategy and a forwarding strategy are established on the basis of the integrated transmission number; the optimal path algorithm is used to select a major path, the nodes closer to the destination node than the source node can be selected into a forwarding list, and the forwarding nodes can be confined to the vicinity of the major path according to a certain screening rule; the forwarding node closest to the destination node is set to have the highest forwarding priority, and the forwarding priority is lowered with the increase of the distance from the destination node; and the destination node transmits an end-to-end response to the source node based on a certain rule to inform the source node of the number of the received packets, and the source node performs adaptive regulation on the transmission rate according to the data.
Owner:BEIJING UNIV OF POSTS & TELECOMM
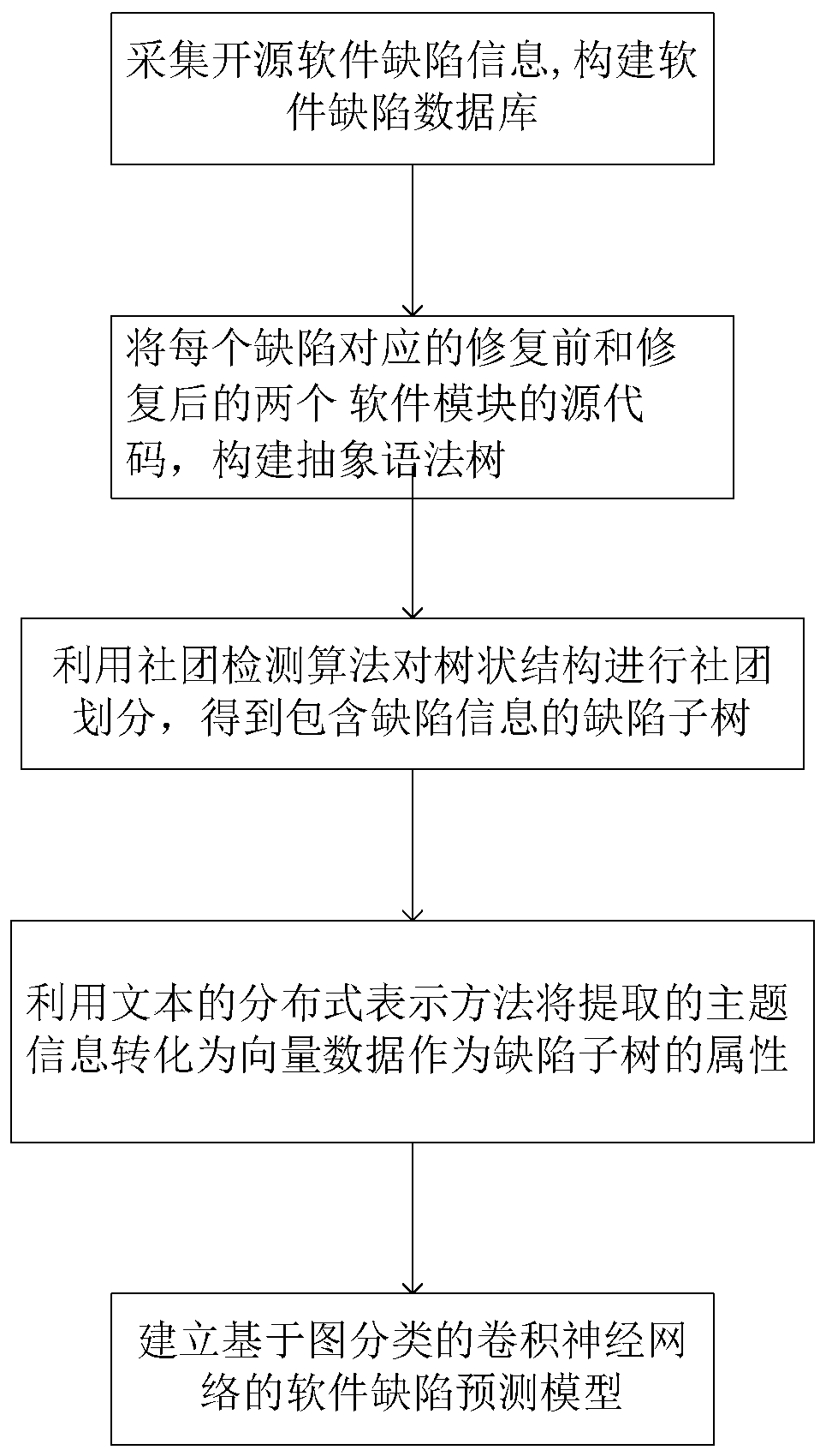
Software defect prediction method for open source software defect feature deep learning
ActiveCN110597735ASolving Design DifficultiesGood defect recognitionCharacter and pattern recognitionSoftware testing/debuggingPredictive methodsOpen source
The invention provides a software defect prediction method for open source software defect feature deep learning, and belongs to the technical field of software engineering. The method comprises the steps of collecting open source software defect information, constructing a software defect database, and generating an abstract syntax tree from source codes; pruning the abstract syntax tree by usinga community detection algorithm to obtain a defect sub-tree, establishing an information corpus of the defect sub-tree in combination with the repair description, the project basic information and the source code, extracting theme words from the information corpus, converting the theme words into vector representation, and taking the vector representation as attributes of nodes in the defect sub-tree; finally, establishing a software defect prediction model of the convolutional neural network based on graph classification, expressing the defect subtree as an adjacent matrix and an attribute matrix to serve as input of the model to train the convolutional neural network, and recognizing whether the source code of the to-be-predicted software module has defect tendency or not. According tothe method, the defect depth features are directly extracted from the structured software codes by using a deep learning method, so that a better defect recognition effect can be achieved.
Owner:BEIHANG UNIV
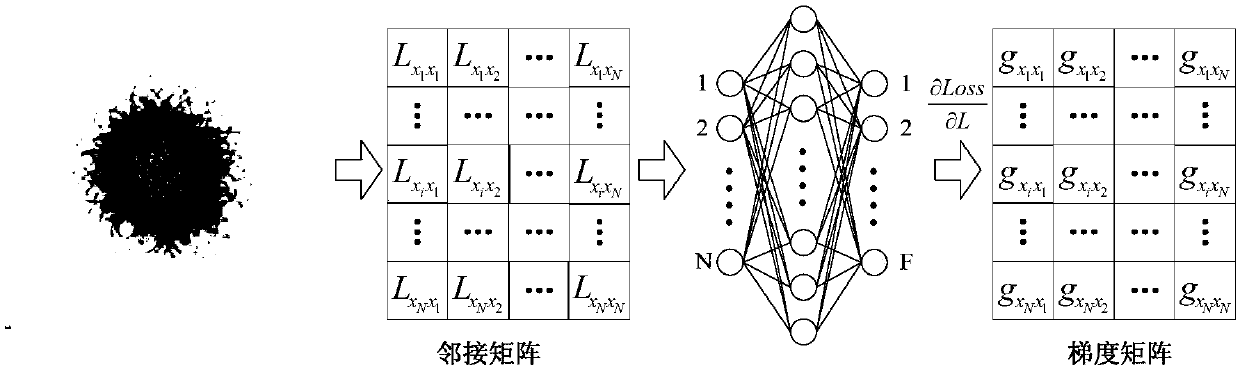
Graph convolutional network gradient-based node information hiding method
PendingCN108648095AAccurate classificationAchieve hiddenData processing applicationsCharacter and pattern recognitionNODALAlgorithm
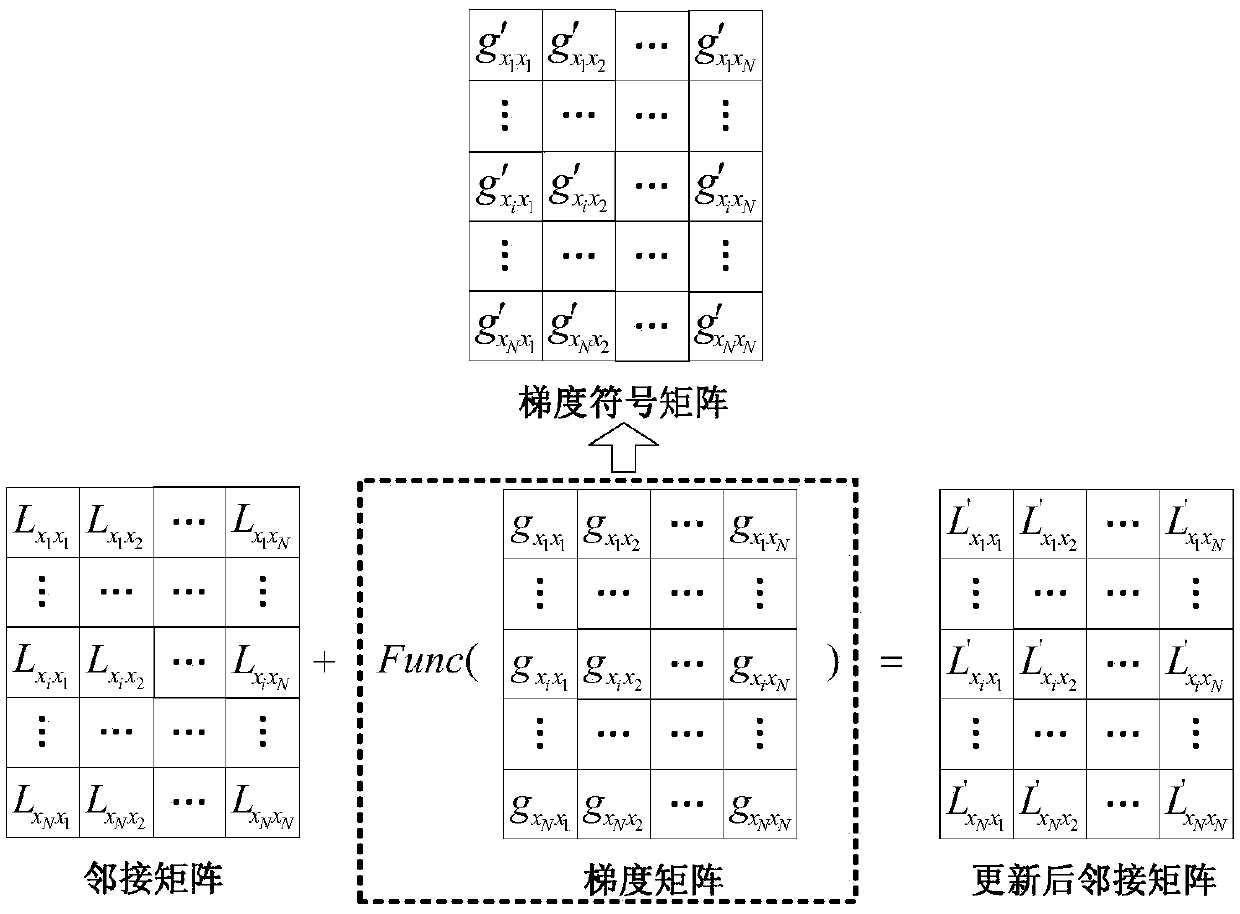
The invention discloses a graph convolutional network gradient-based node information hiding method. The method comprises the steps of (1) constructing a network graph, constructing an adjacent matrixaccording to a connected edge set corresponding to the network graph, and preprocessing the adjacent matrix; (2) constructing and training a graph convolutional network model, and determining final weight information of the graph convolutional network model; (3) according to the final weight information, building an objective function based on a goal of ensuring non-target node classification tobe accurate as far as possible and enabling target node classification to be wrong, and calculating a connected edge gradient matrix corresponding to the adjacent matrix by utilizing the objective function; (4) according to a set gradient threshold, symbolizing the connected edge gradient matrix to obtain a connected edge gradient symbol matrix; and (5) updating the adjacent matrix by utilizing the connected edge gradient symbol matrix to hide node information. According to the method, the target node information of a network can be hidden under the condition of slightly changing the structureof the network as far as possible.
Owner:ZHEJIANG UNIV OF TECH
On-line evaluating method of urban network max power supply capability
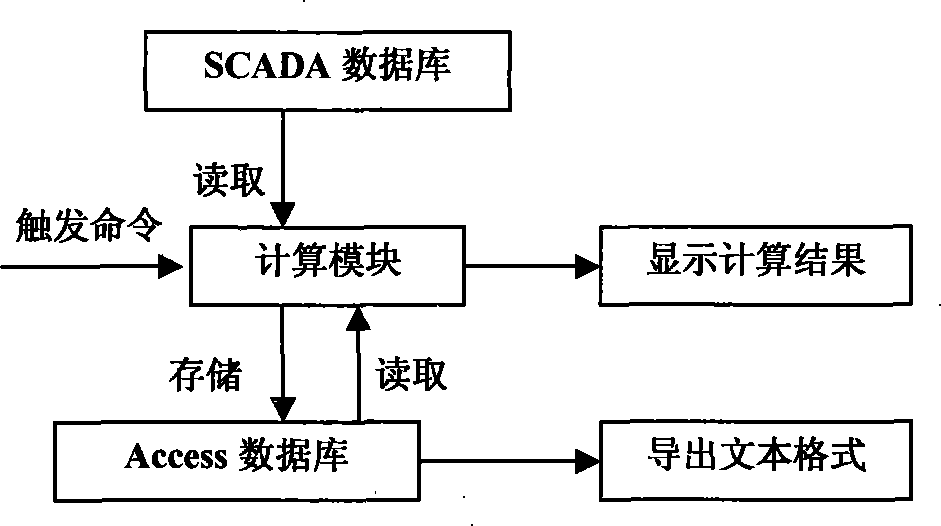
ActiveCN101252280AData processing applicationsSystems intergating technologiesPower system schedulingCalculation error
The invention relates to an online evaluation approach to evaluate the maximum power supply capacity of urban power network, belonging to the technical field of advanced application of electric power system dispatching. The method employs data base connection modes(ADO and ODBC), reads the relative network topology and network nodes in EMS and analyses the topology of the urban power network by means of an adjacency matrix to build up a model for calculating the maximum power supply capacity of the urban power network; the model is a linear programming model based on DC power flow and takes the maximum load of the network as the target function, and power balance, rated capacities of the branch lines and power restriction of the nodes as the constraint condition. In the program, the linear programming is worked out through improved simplex method and error analysis is carried out to the result. The model has the advantages of big calculation speed and small calculation error as for light load network and is suitable for power networks that require repeated optimization and adjustment. Results from a great amount of calculation with the program show that the method is of efficacy and applicability.
Owner:KUNMING UNIV OF SCI & TECH
Path planning determining method based on cladogram topological road network construction
The invention discloses a path planning determining method based on cladogram topological road network construction, which comprises the steps of: obtaining city complete road network data, constructing a road network full-connected graph G expressing original geographic information by applying an adjacent topological cladogram; classifying and dividing the road network full-connected graph G into a Y-type road network topological cladogram; obtaining the minimal branching tree comprising all target nodes; and eliminating invalid branching nodes by adopting a branching delimiting searching strategy for the minimal branching tree comprising all target nodes in a road planning problem, reducing incidence matrix dimensionality and obtaining a planning result. The invention has the advantagesof optimizing algorithm complexity of the road planning process and improving road planning efficiency.
Owner:ZHEJIANG UNIV OF TECH
Adjacency matrix-based graph feature extraction system, graph classification system and methods
PendingCN108062551AReduce computational complexitySmall amount of calculationCharacter and pattern recognitionKnowledge representationComputation complexityFeature extraction
The present invention provides an adjacency matrix-based graph feature extraction system, an adjacency matrix-based graph feature extraction picture classification system and corresponding methods. According to the systems and methods, connection information elements in an adjacency matrix corresponding to a graph are concentrated at a specific diagonal region of the adjacency matrix, and non-connection information elements are reduced in advance; a filtering matrix is used to extract the subgraph structure of the graph along a diagonal direction; a stack convolutional neural network is used to extract a larger subgraph structure; and therefore, computational complexity and computational quantity are greatly reduced, the restrictions of computational complexity and the restrictions of window size can be eliminated; and a large multi-vertex subgraph structure and the deep features of implicit correlation structures from vertices and edges can be captured through a small window, and theaccuracy and speed of graph classification can be improved.
Owner:ZHEJIANG UNIV
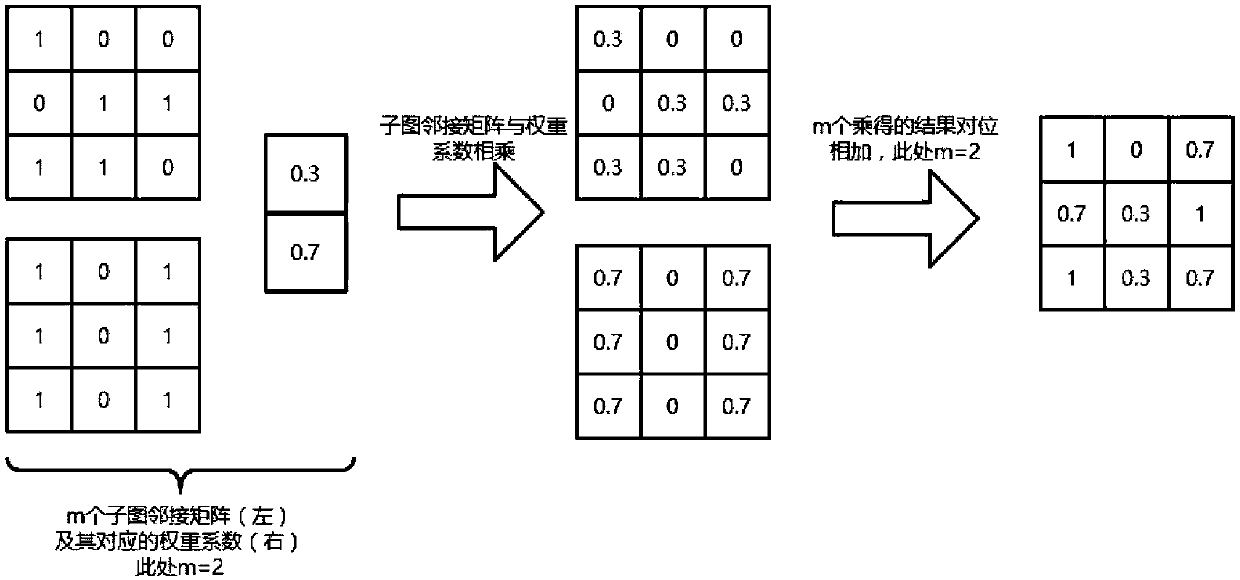
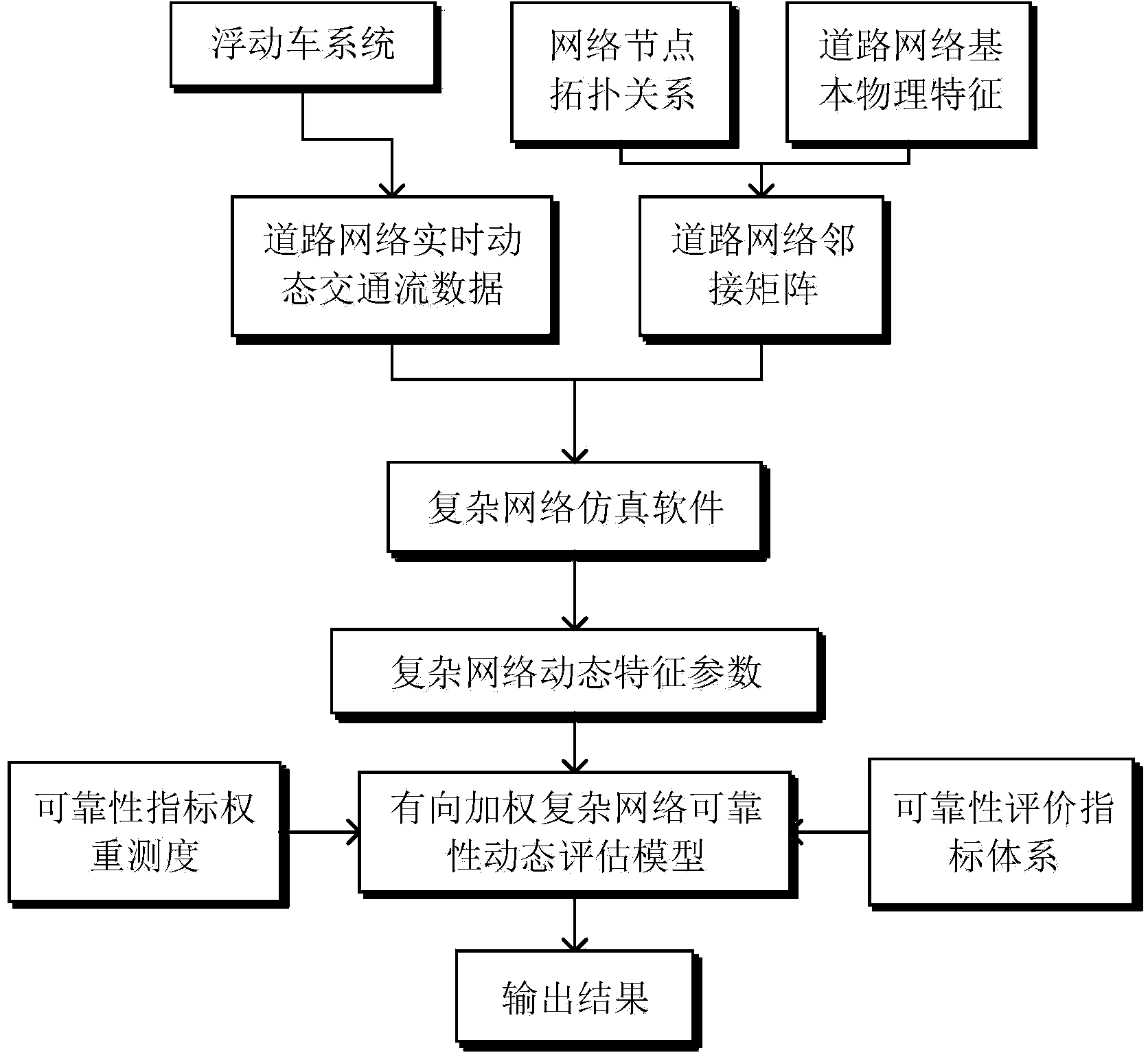
Reliability evaluation method of urban road network based on data of floating vehicles
InactiveCN104392094AAvoid reliability pitfallsAchieve the purpose of evaluationDetection of traffic movementSpecial data processing applicationsRoad networksTraffic flow
The invention discloses a reliability evaluation method of an urban road network based on data of floating vehicles. The method comprises the following steps of applying the data of the floating vehicles, and combining with a geological information system technique to obtain traffic flow data of the road network; using the traffic flow data as road section weights, and combining with an adjacent matrix of the road network to generate a directed weighting complicated road network file; applying complicated network simulation software to output complicated network feature parameters corresponding to different moments of the road network, and finally building a reliability evaluation model of the directed weighting road network; substituting the outputted complicated network feature parameters to calculate, so as to obtain a final reliability evaluation value. The method has the advantages that the data of the floating vehicles and a complex network theory are combined to evaluate the reliability of the urban road network from a macro perspective, the traffic flow features of dots, lines and planes of the road network are integrally researched, the defect of the reliability evaluation of the road network from a micro dynamics perspective is effectively overcome, and the reliability evaluation of the urban road network is more perfect.
Owner:BEIHANG UNIV
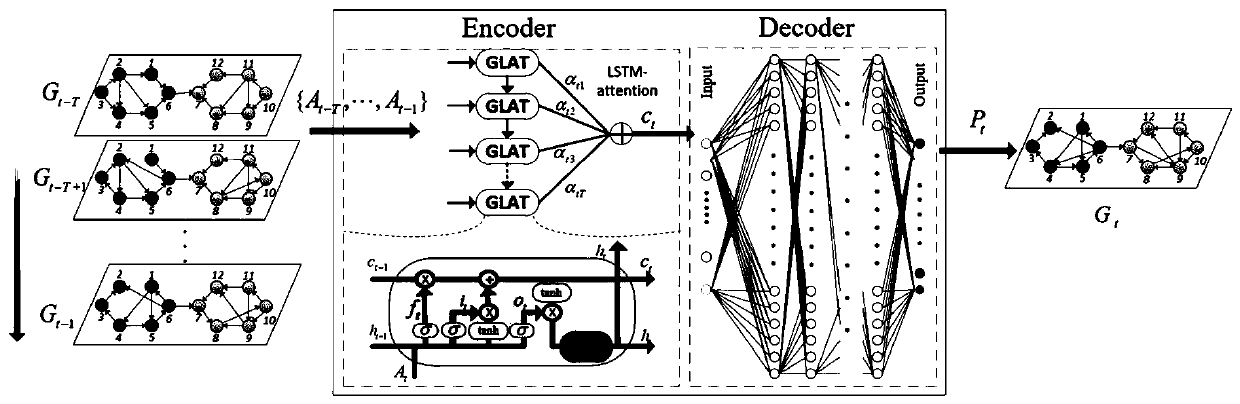
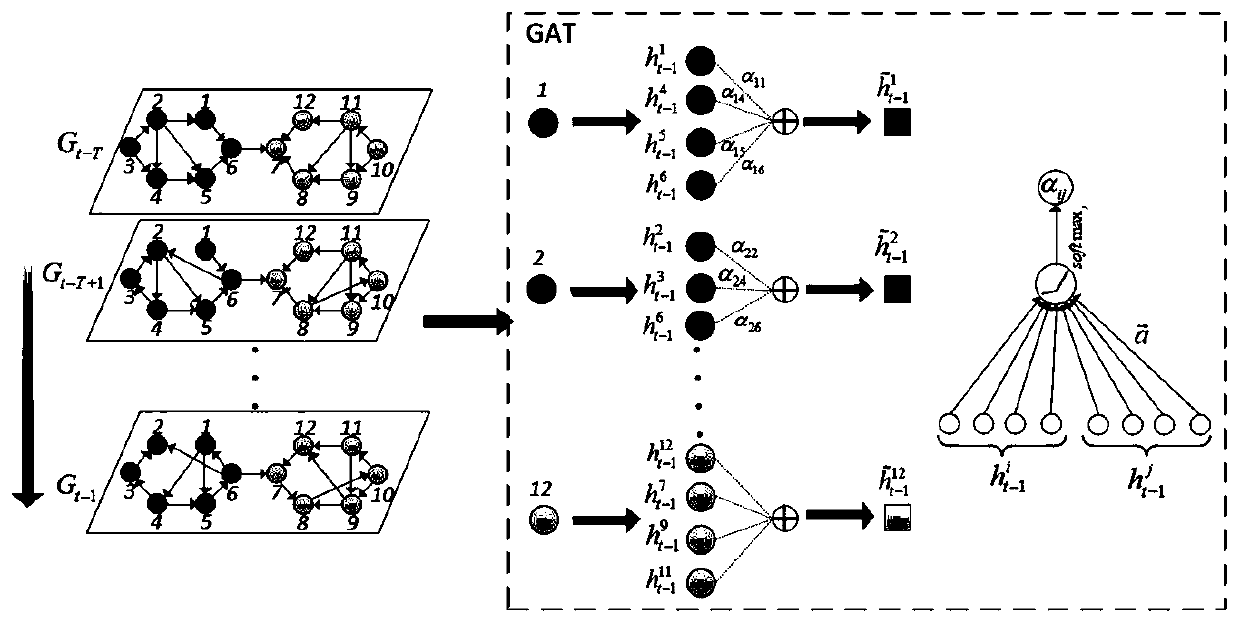
Dynamic link prediction method based on space-time attention deep model
The invention discloses a dynamic link prediction method for a space-time attention deep model, and the method comprises the following steps: taking an adjacent matrix A corresponding to a dynamic network as an input, and the dynamic network comprises a social network, a communication network, a scientific cooperation network or a social security network; extracting a hidden layer vector {ht-T,..., ht-1} from the hidden layer vectors {ht-T,..., ht-1} by means of an LSTM-attention model, calculating a context vector at according to the hidden layer vectors {ht-T,..., ht-1} at T moments, and inputting the context vector at the T moments into a decoder as a space-time feature vector; and decoding the input time feature vector at by adopting a decoder, and outputting a probability matrix whichis obtained by decoding and is used for representing whether a link exists between the nodes or not, thereby realizing the prediction of the dynamic link. According to the dynamic link prediction method, link prediction of the end-to-end dynamic network is realized by extracting the spatial and temporal characteristics of the dynamic network.
Owner:ZHEJIANG UNIV OF TECH
Discovery method of complex network community
InactiveCN102073700ASave storage spaceIncrease computing speedSpecial data processing applicationsAlgorithmComputation process
The invention discloses a discovery method of a complex network community. The discovery method comprises the following steps of: 1, establishing adjacency matrix representation of a network which is required to be analyzed; 2, determining the value of an initial partition point; 3, calculating the degree of each node in the network; 4, selecting K points with the highest node degrees as initial partition points; 5, selecting a specific needed partition point; and 6, giving a last community discovery result by using a computer according to the last partition point obtained in the step 5. The invention provides a partition-point-based discovery method for processing a complex network community for the computer. Through the method, the technical problem that a large-scale complex network cannot be processed by using the computer in the prior art is solved, a large amount of computer storage space can be saved in a calculation process, system resource occupied by calculation is reduced, and operation speed and efficiency of the computer are improved; simultaneously, a downward decomposition method and an upward polymerization method are unified.
Owner:ZHEJIANG UNIV
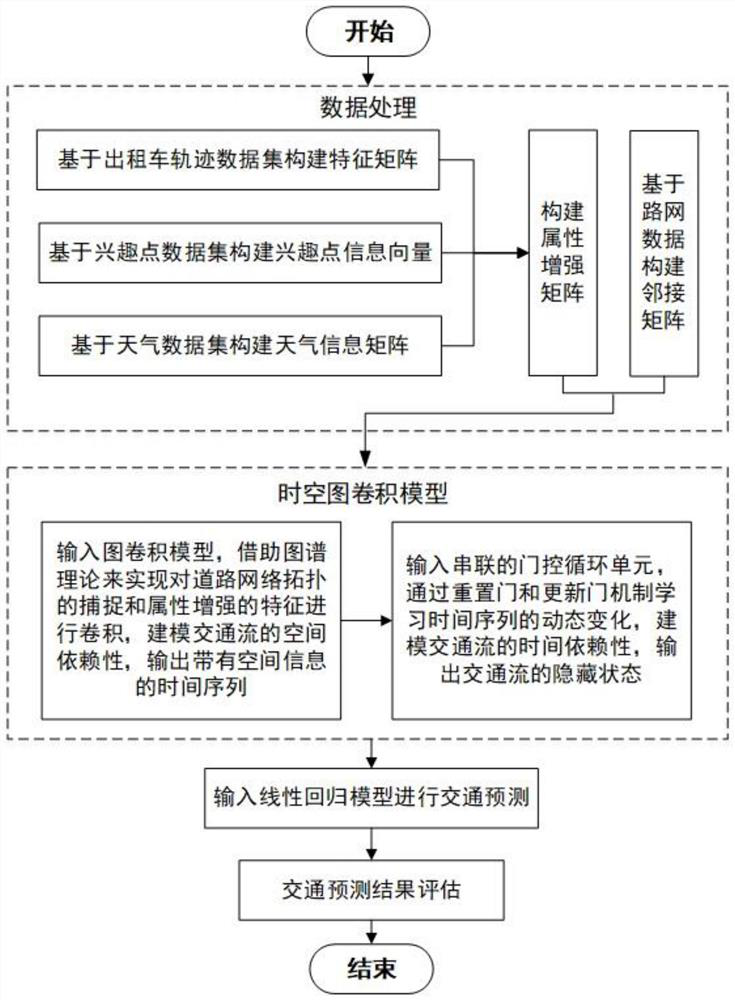
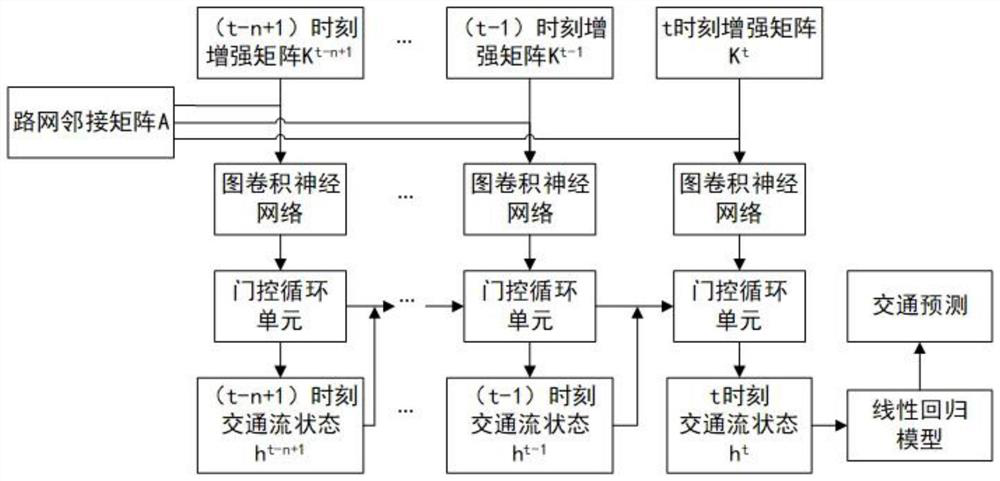
Traffic prediction method of spatio-temporal diagram convolution model based on attribute enhancement
ActiveCN112216108AOvercome the defect of not being able to integrate multi-source dataAccurate traffic forecastDetection of traffic movementForecastingTraffic predictionAlgorithm
The invention discloses a traffic prediction method of a spatio-temporal graph convolution model based on attribute enhancement. The method comprises the following steps: constructing an adjacent matrix A based on road network data; constructing an attribute enhancement matrix Kt = [Xt, p, Bt] at the moment t based on the feature matrix X, the interest point information vector p and the weather information matrix B; inputting the attribute enhancement matrixes of the n historical moments and the adjacent matrix of the road network into a spatio-temporal diagram convolution model for learning and training, calculating a traffic flow hidden state, and obtaining a traffic prediction value. According to the method of the invention, on the basis of spatial features when a spatio-temporal diagram convolution model is used for modeling, multi-source fragmented city data are fused to capture the relationship between external factors influencing traffic and traffic flow, the perception of the spatio-temporal diagram convolution model on the external influence factors is enhanced, and therefore, more efficient and accurate traffic prediction can be realized.
Owner:CENT SOUTH UNIV
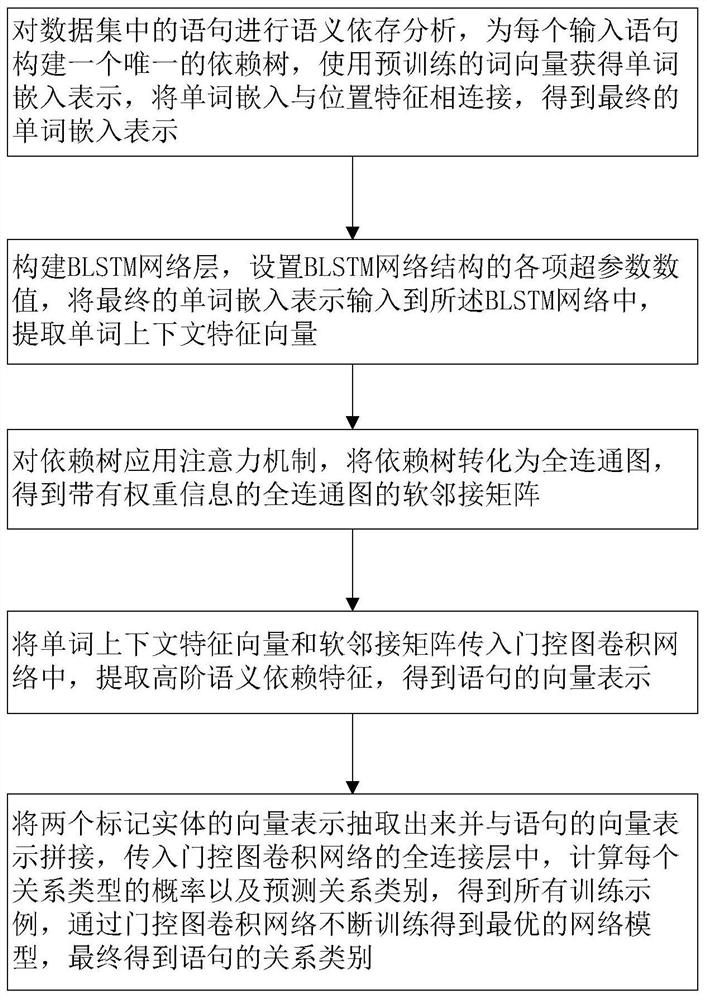
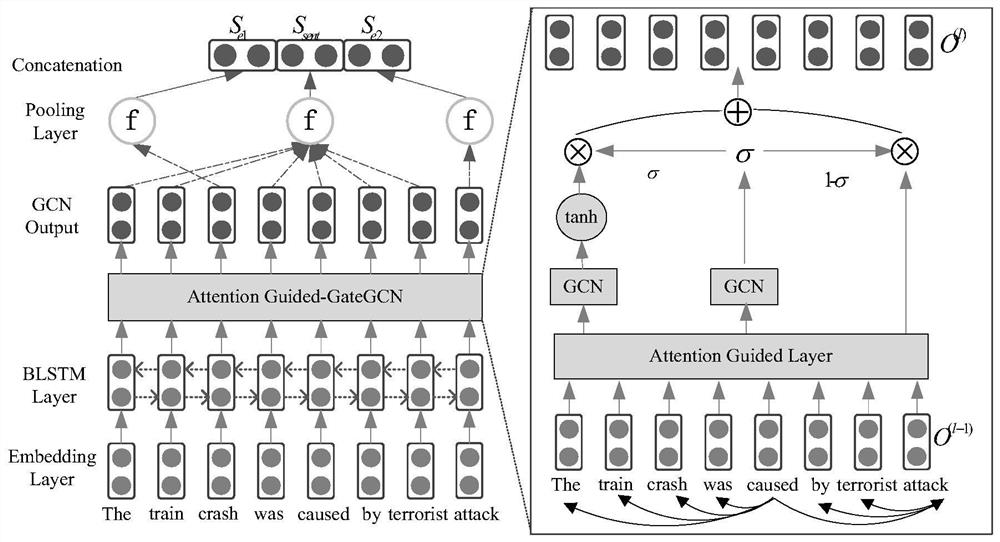
Relation extraction method and system based on attention cycle gated graph convolutional network
PendingCN111985245AImprove the extraction effectAvoid lossSemantic analysisNeural architecturesFeature vectorAlgorithm
The invention relates to a relation extraction method and system based on an attention cycle gated graph convolutional network, and the method comprises the steps of carrying out the semantic dependency analysis of a statement, enabling word embedding to be connected with a position feature, and obtaining a final word embedding representation; constructing a BLSTM network layer, and extracting a word context feature vector; applying an attention mechanism to the dependency tree to obtain a soft adjacency matrix of a fully connected graph with weight information; transmitting the word context feature vector and the soft adjacency matrix into a gated graph convolutional network, and extracting a high-order semantic dependence feature to obtain vector representation of a statement; and extracting vector representations of the two marked entities, splicing the extracted vector representations of the two marked entities with the vector representation of the statement, transmitting the spliced vector representation of the statement into a full connection layer of the gated graph convolutional network, calculating the probability of each relationship type and predicting the relationship type, and finally obtaining the relationship type of the statement. According to the invention, key information loss is avoided, and the relationship extraction performance is improved.
Owner:JIANGNAN UNIV
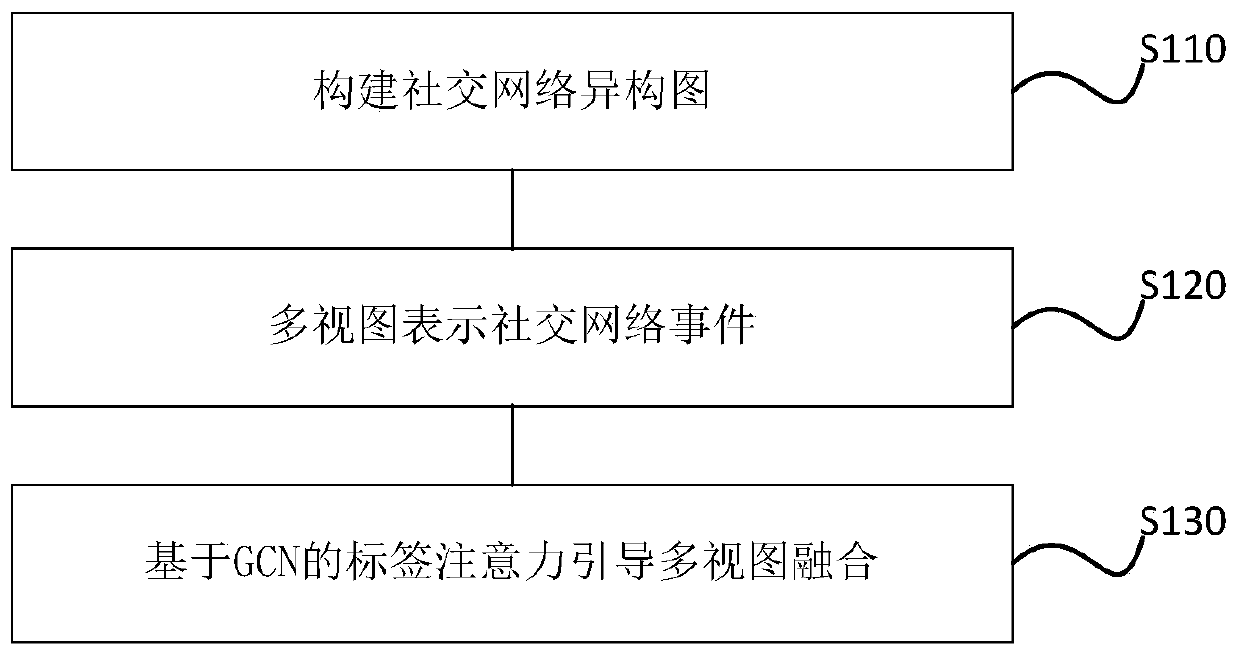
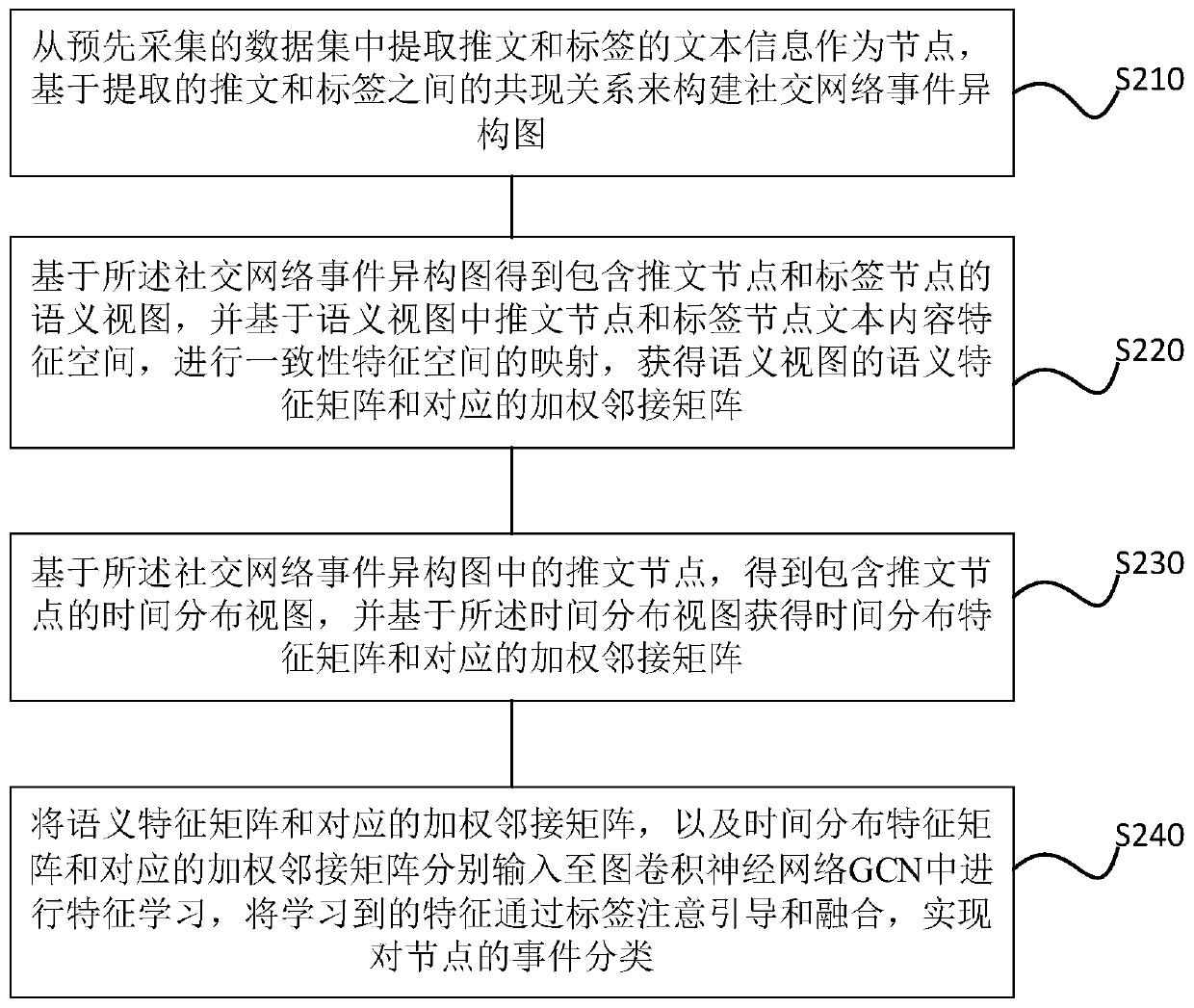
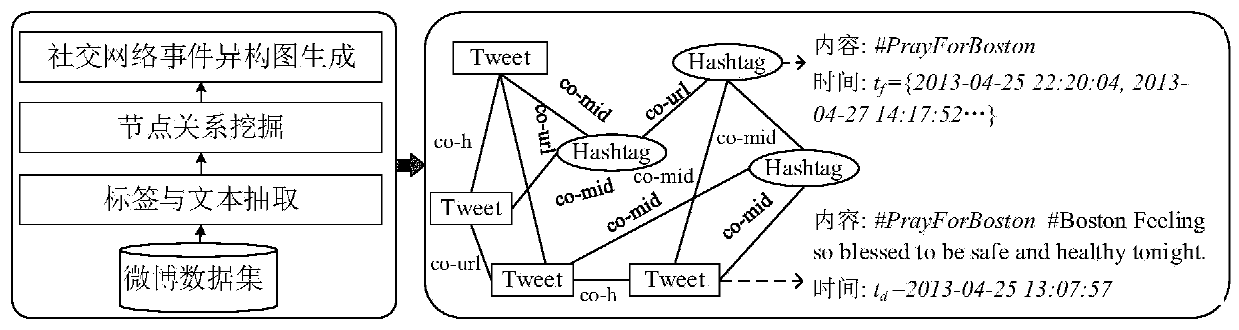
Social network event detection method and device
ActiveCN111598710AAccurate detectionData processing applicationsNeural architecturesData setTheoretical computer science
The invention provides a social network event detection method and device, and the method comprises the steps: taking a push text and a label extracted from a data set as nodes, and constructing a social network event heterogeneous graph; constructing a semantic view based on text contents of a push text and a label in the heterogeneous graph, and obtaining a feature matrix and a weighted adjacency matrix of the semantic view; constructing a time distribution view based on the push-texts in the heterogeneous graph and the time of the push-texts, and obtaining a feature matrix and a weighted adjacency matrix of the time distribution view; inputting the feature matrix and the weighted adjacency matrix of the semantic view , and the feature matrix and the weighted adjacency matrix of the timedistribution view into the GCN; and in combination with an attention mechanism, guiding feature fusion of the semantic view and the time distribution view by adopting a label, generating an attentiondistribution probability of the text semantic view and the time distribution view under a given label, obtaining a probability that each node in the heterogeneous graph belongs to an event in the data set, and realizing prediction of the nodes. According to the social network event detection method provided by the embodiment of the invention, the detection effect of the social network event is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
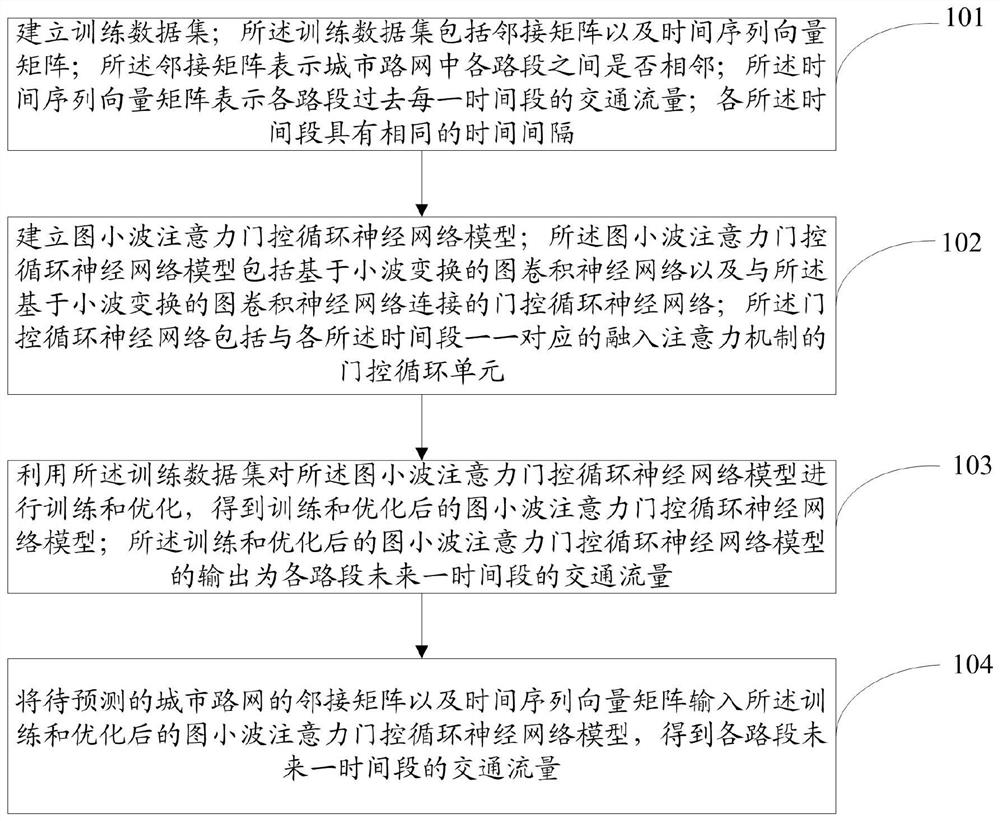
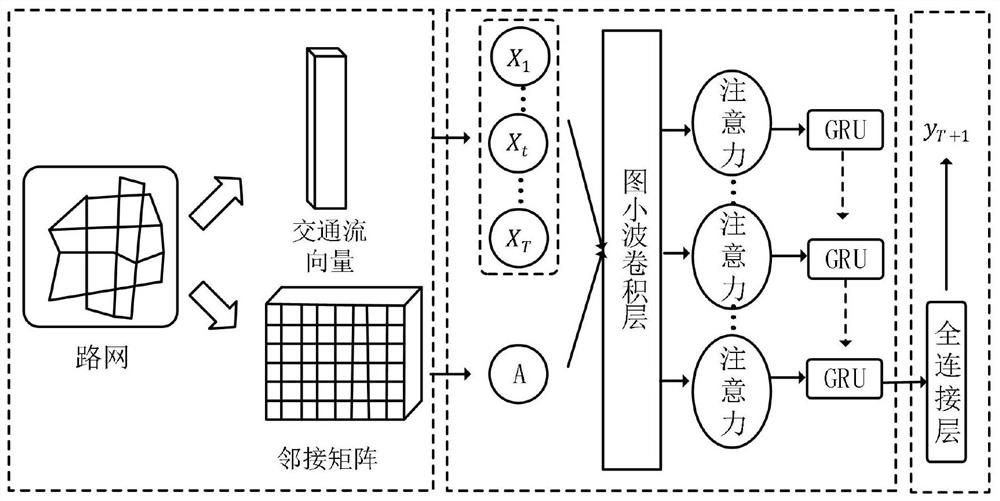
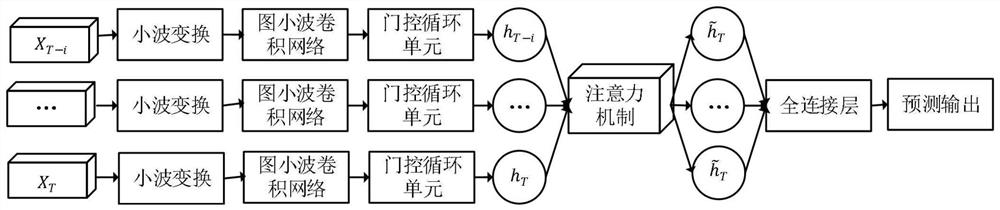
Traffic flow prediction method and system for urban road network
The invention discloses a traffic flow prediction method and system for an urban road network, and relates to the technical field of intelligent transportation, and the method comprises the steps: building a training data set comprising an adjacent matrix and a time sequence vector matrix; establishing a graph wavelet attention gating recurrent neural network model; wherein the model comprises a graph convolutional neural network based on wavelet transform and a gating recurrent neural network connected with the graph convolutional neural network; the gating recurrent neural network comprisesgating recurrent units which are in one-to-one correspondence with the time periods and are integrated into the attention mechanism; training and optimizing the graph wavelet attention gating recurrent neural network model by using the training data set; and inputting the adjacency matrix of the urban road network to be predicted and the time sequence vector matrix into the trained and optimized graph wavelet attention gating recurrent neural network model to obtain the traffic flow of each road section in a future time period. The method and the system disclosed by the invention can accurately predict the traffic flow.
Owner:CHANGCHUN UNIV OF SCI & TECH
Method for carrying out community detection on heterogeneous social network on basis of clustering algorithm
InactiveCN103810288AImprove accuracyData processing applicationsWebsite content managementCluster algorithmCommunity structure
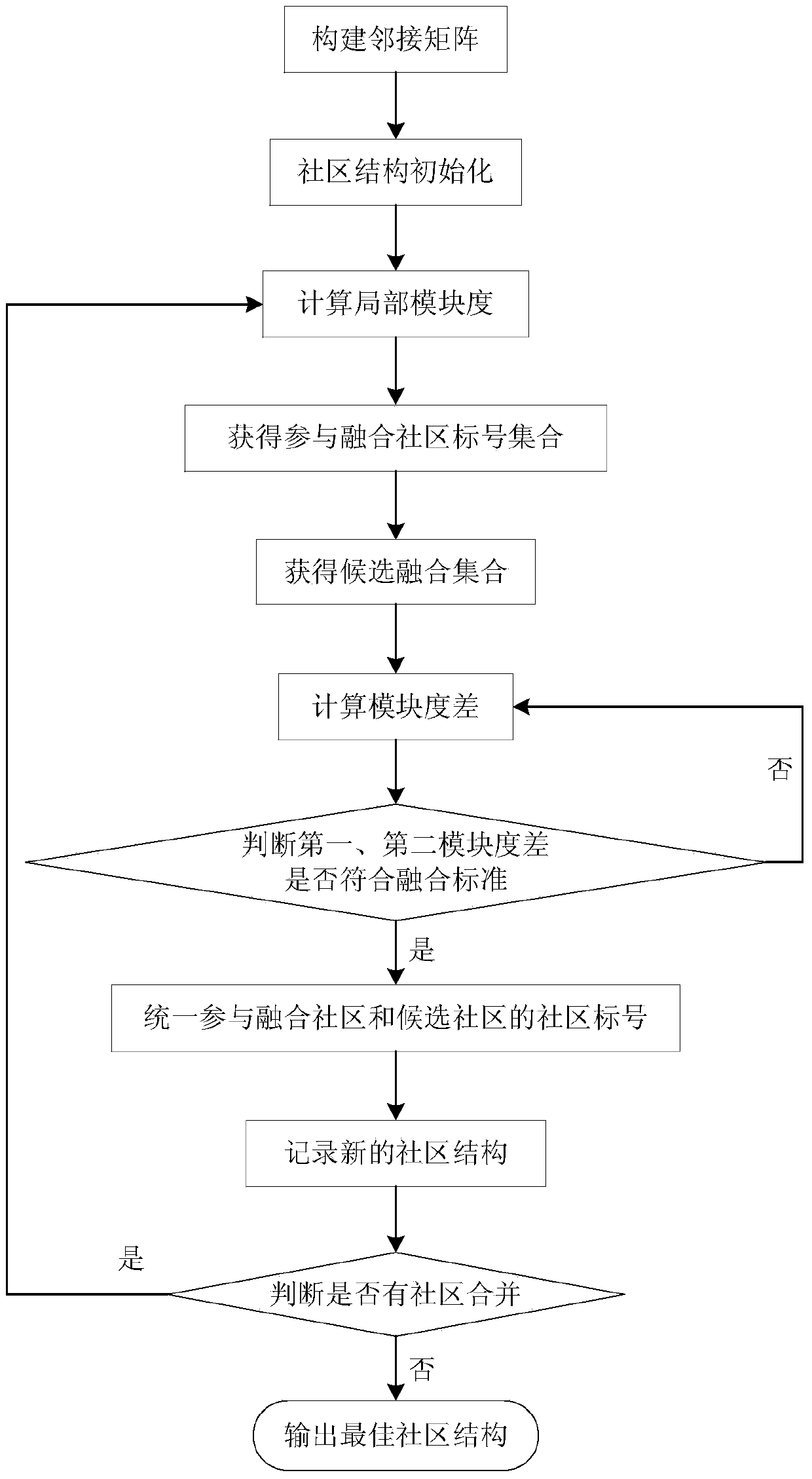
Provided is a method for carrying out community detection on a heterogeneous social network on the basis of a clustering algorithm. The method comprises the steps that an adjacent matrix is built; the community structure is initialized; the local modularity is calculated; a set of mark numbers of communities participating in fusion is obtained; candidate fusion sets are obtained; differences of the modularity are calculated; whether the first modularity difference and the second modularity difference meet the fusion standard or not, if yes, the mark numbers of the communities participating in fusion and the mark numbers of candidate communities are unified, and if not, the step of calculation of the local modularity is executed again; a new community structure is recorded; if community merging does not exist in the current cycle, the optimal community structure is output. According to the method for carrying out community detection on the heterogeneous social network on the basis of the clustering algorithm, due to the fact that the clustering method, the similarity vector method and the local modularity method are adopted, the methods can be effectively applied to community detection of the heterogeneous social network, and accuracy of the detection result of the heterogeneous network community structure is improved.
Owner:XIDIAN UNIV
Pedestrian intention recognition based on graph convolution
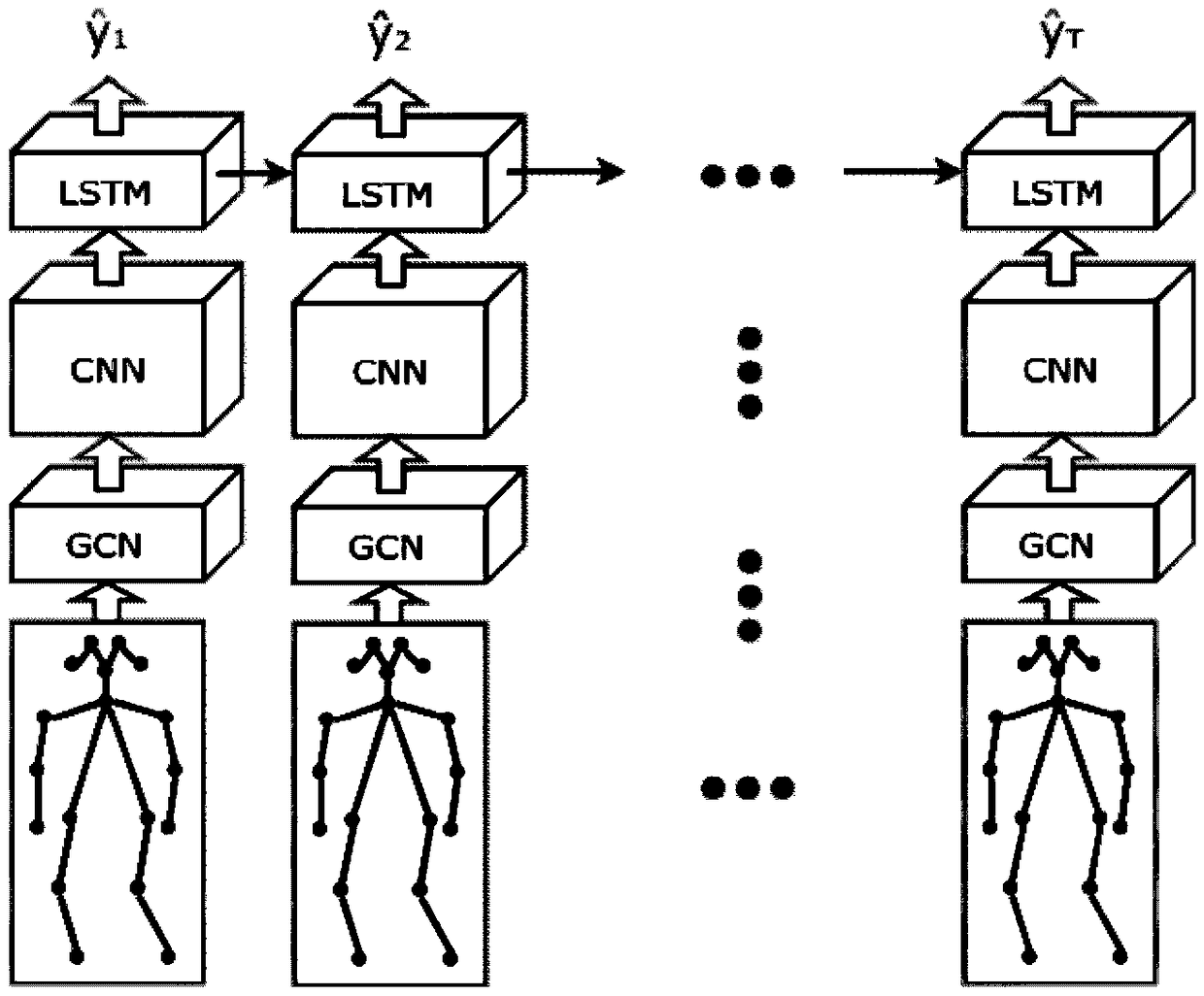
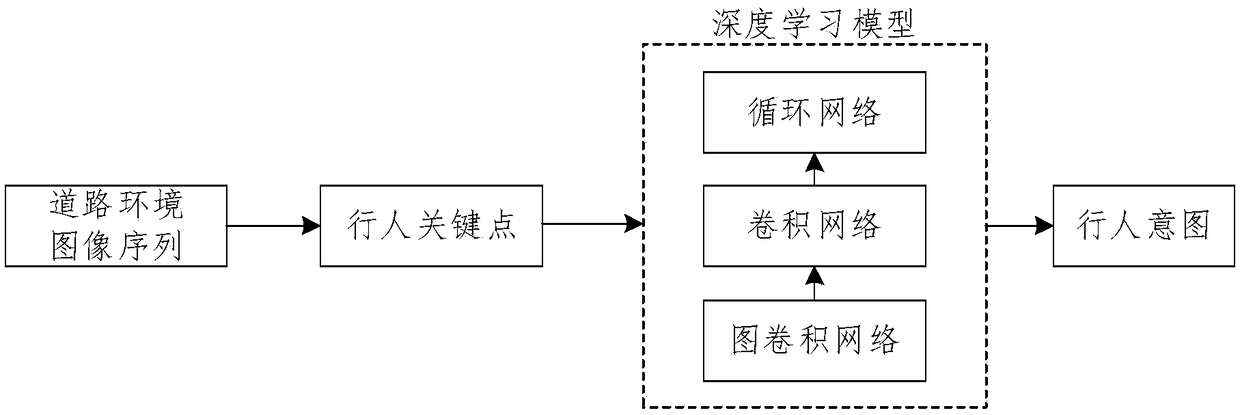
ActiveCN109117701AProtection securityImprove understandingCharacter and pattern recognitionHuman bodyData set
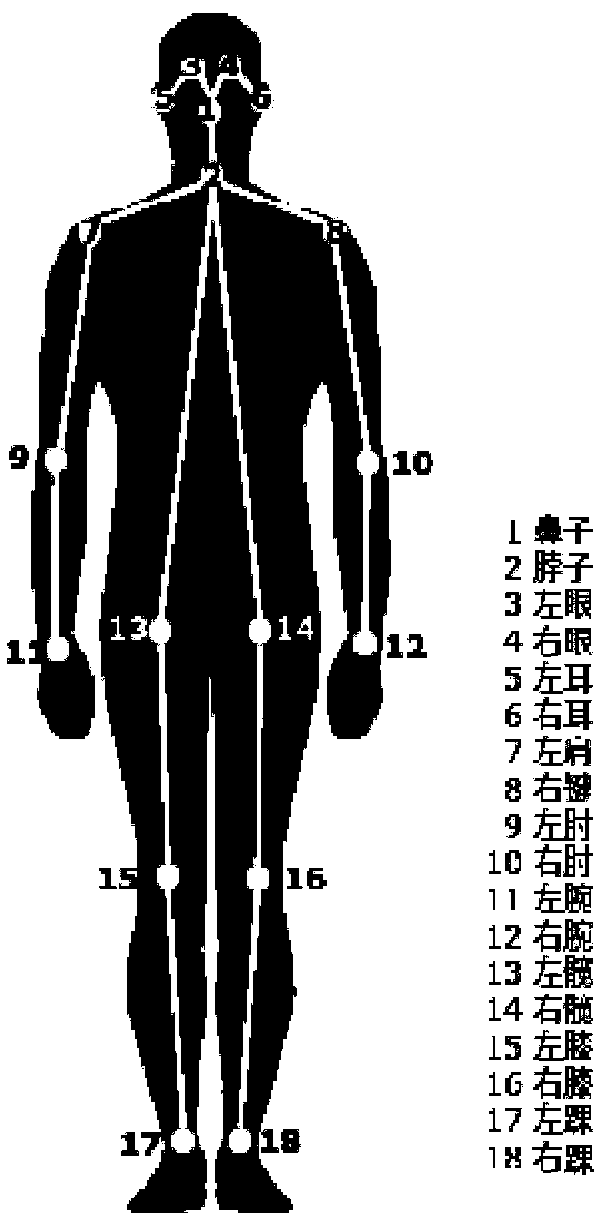
The invention relates to a pedestrian intention recognition method based on graph convolution. The video image of road environment is captured by a forward-looking camera system mounted on a vehicle.Pedestrian detection and pedestrian human key points extraction are carried out on the image, and the adjacency matrix is constructed to represent the connection information of pedestrian human key points based on graph theory. The bottom feature is extracted from coordinate information and adjacency matrix representation of key points by graph convolution algorithm, and the bottom feature is extracted and time series analyzed by depth convolution neural network and depth loop neural network. Based on the data set of pedestrian intention constructed by manual labeling method, the parameters ofthe model are optimized to realize the classification and recognition of pedestrian intention. The invention effectively utilizes the high-level semantic feature of the key point information of the pedestrian human body, so that the automobile advanced driving assistance system has the ability to understand the pedestrian behavior intention.
Owner:SOUTHEAST UNIV
Traffic light control method based on heuristic deep Q network
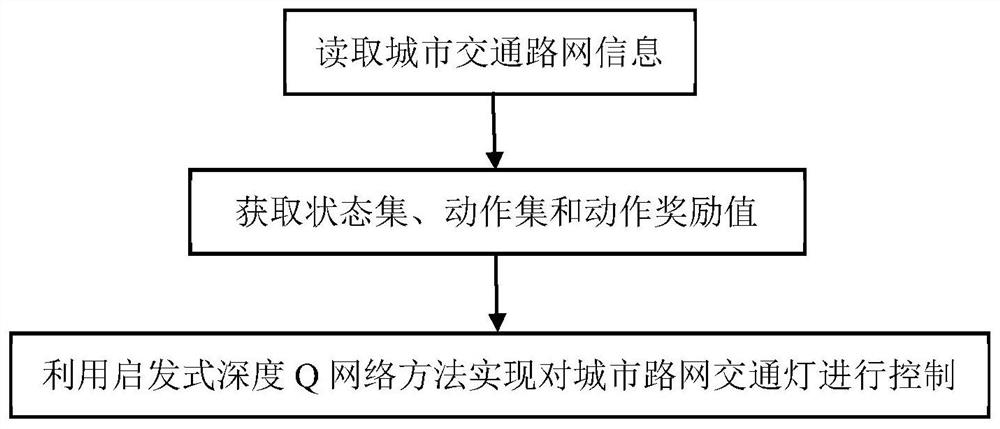
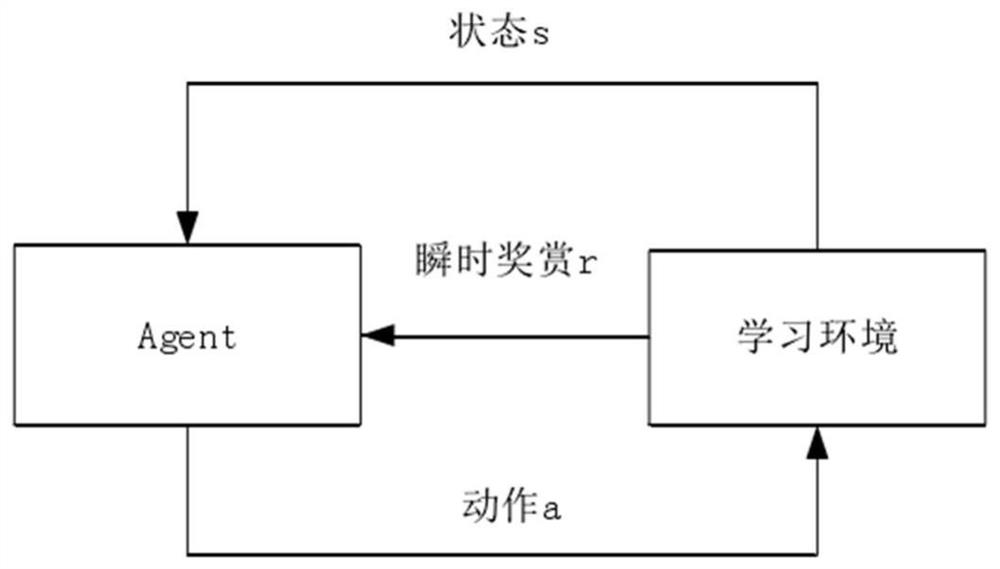
ActiveCN111696370AAvoid correlationConvincing training resultsControlling traffic signalsCharacter and pattern recognitionTraffic signalTraffic network
The invention discloses a multi-intersection traffic signal control method based on heuristic deep Q learning, and mainly solves problems of correlation of training data, incapability of rapid convergence of a traffic light control strategy and low control efficiency in an existing method. The method comprises steps that the urban traffic network information is read, a vehicle traffic state set ofeach intersection is established, and the read urban traffic network information is converted into an adjacent matrix to be stored; a state set, an action set and an action reward value of each intersection are acquired from a vehicle traffic state set of each intersection; according to the state set, the action set, the action reward value and the adjacency matrix, a heuristic deep Q network method is used for continuously executing actions according to the state of each intersection to obtain rewards and then to the next state, and urban road network traffic lights are controlled. The method can improve control efficiency of intersection traffic signal lamps, improves performance of the multi-intersection traffic signal controller, can be used for urban traffic management, and reduces the urban traffic congestion.
Owner:XIDIAN UNIV
City road network link prediction method, system and storage medium
ActiveCN108108854AAvoid the problem of slow updatePrevent overfittingDetection of traffic movementForecastingAlgorithmRoad networks
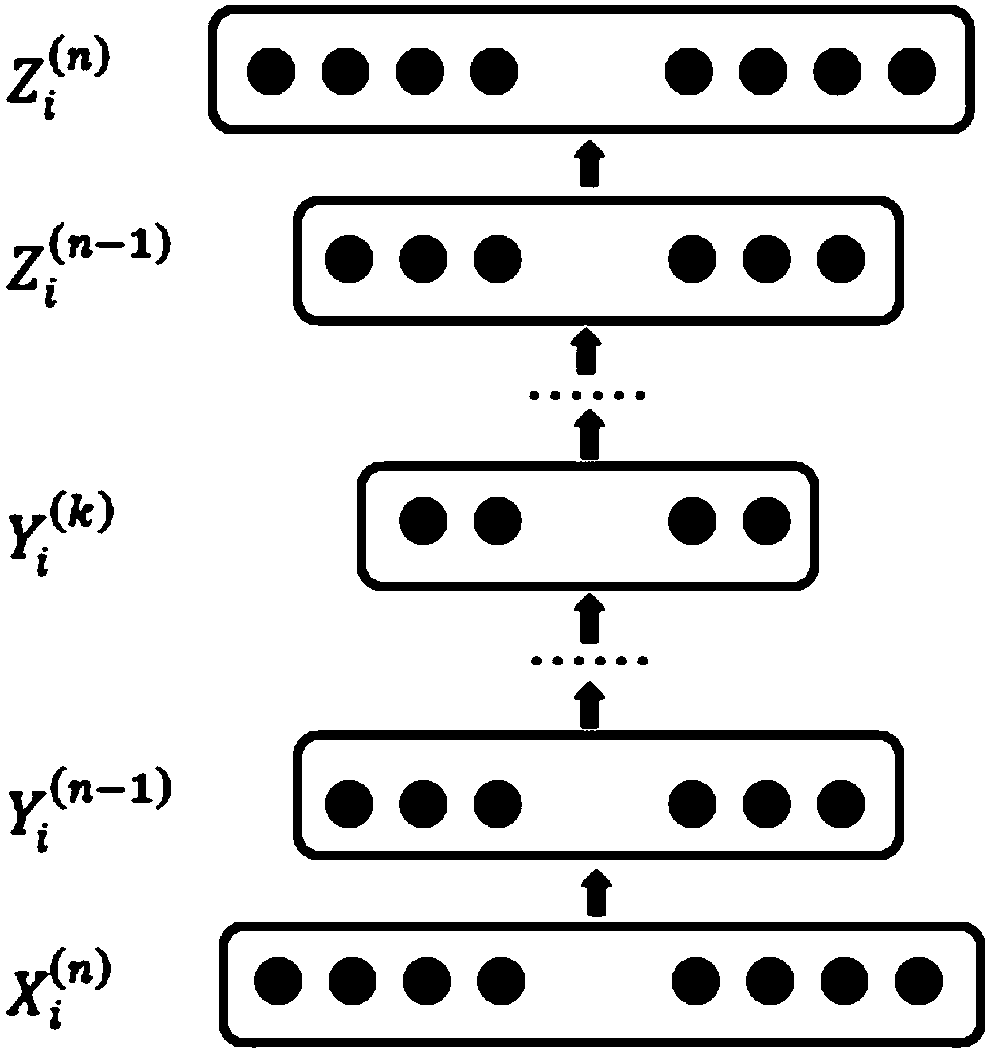
The invention relates to the city traffic technical field, and discloses a city road network link prediction method, system and a storage medium, thus improving the road network link prediction accuracy, and improving the data processing efficiency; the method comprises the following steps: building a road network adjacent matrix; obtaining a Katz similarity matrix according to the adjacent matrix; normalizing the Katz similarity matrix and using a multilayer non-linear automatic encoder to carry out network symptom learning, thus obtaining a network symptom vector; using the network symptom vector to decode and reconstruct the adjacent matrix, and using the reconstructed the adjacent matrix to carry out link prediction.
Owner:CENT SOUTH UNIV
Intelligent traffic system flow short-term prediction method and system based on divergence convolution and GAT
ActiveCN111899510AInsufficient improvementUniversalDetection of traffic movementCharacter and pattern recognitionStreaming dataStatistical correlation
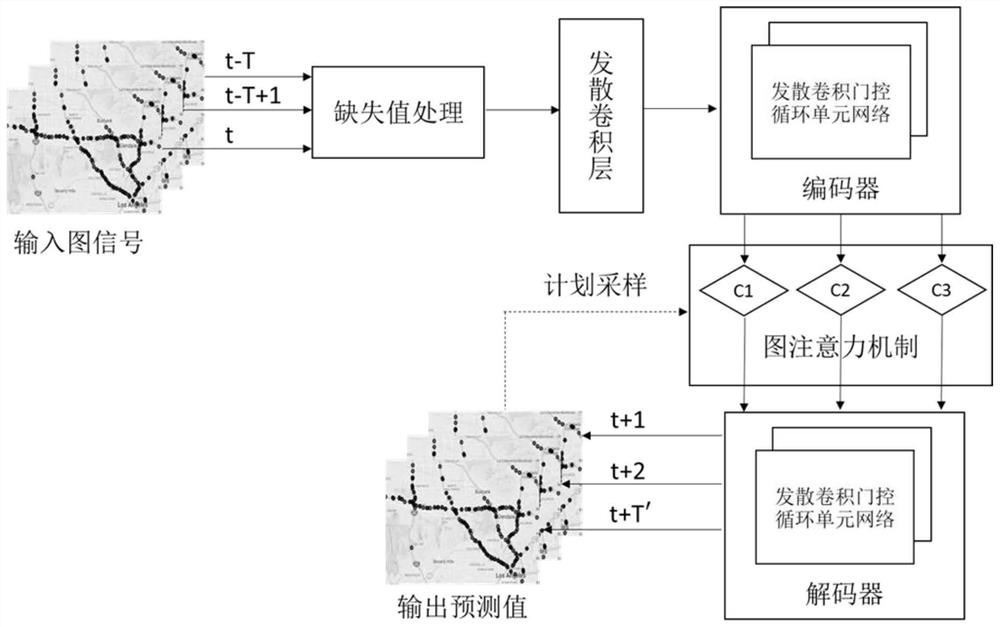
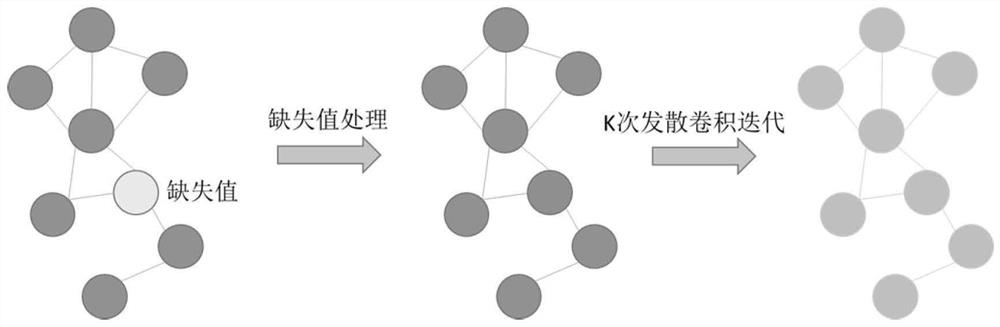
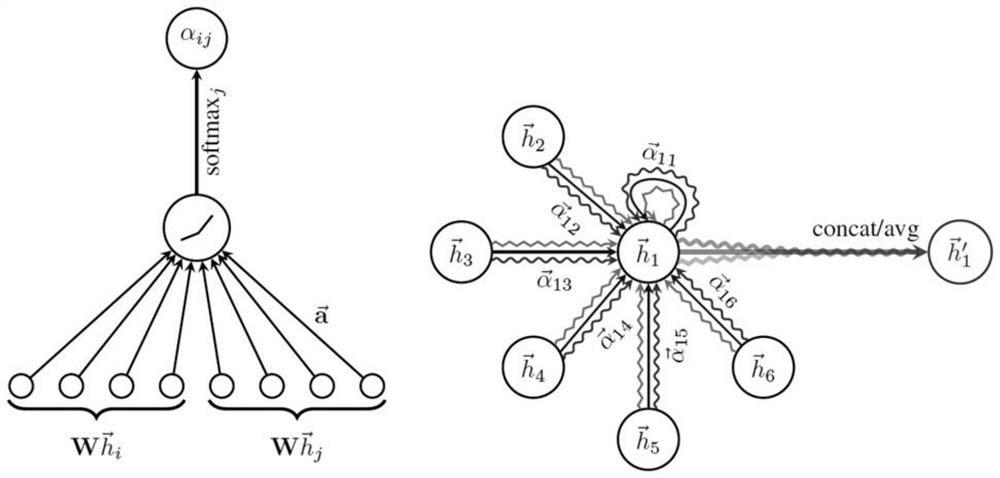
The invention discloses an intelligent traffic system flow short-term prediction method and system based on divergence convolution and GAT. Missing values in the traffic flow data set are complementedthrough a statistical correlation method such as a historical average value method, the distance between every two nodes is calculated, a Gaussian kernel with a threshold value is used for establishing an adjacency matrix representing the node adjacency degree, a divergence convolution layer is used for fully extracting spatial and temporal features of traffic flow data, and then, the extracted features are predicted through a coder-decoder program with planned sampling based on a graph attention mechanism and a divergence convolution gating cycle unit network. According to the method, the problem of data missing can be effectively improved, the prediction precision and the operation efficiency are remarkably improved, and particularly, the short-time prediction effect is better.
Owner:NANJING INST OF TECH
Fast generation method for wireless cell coverage distribution
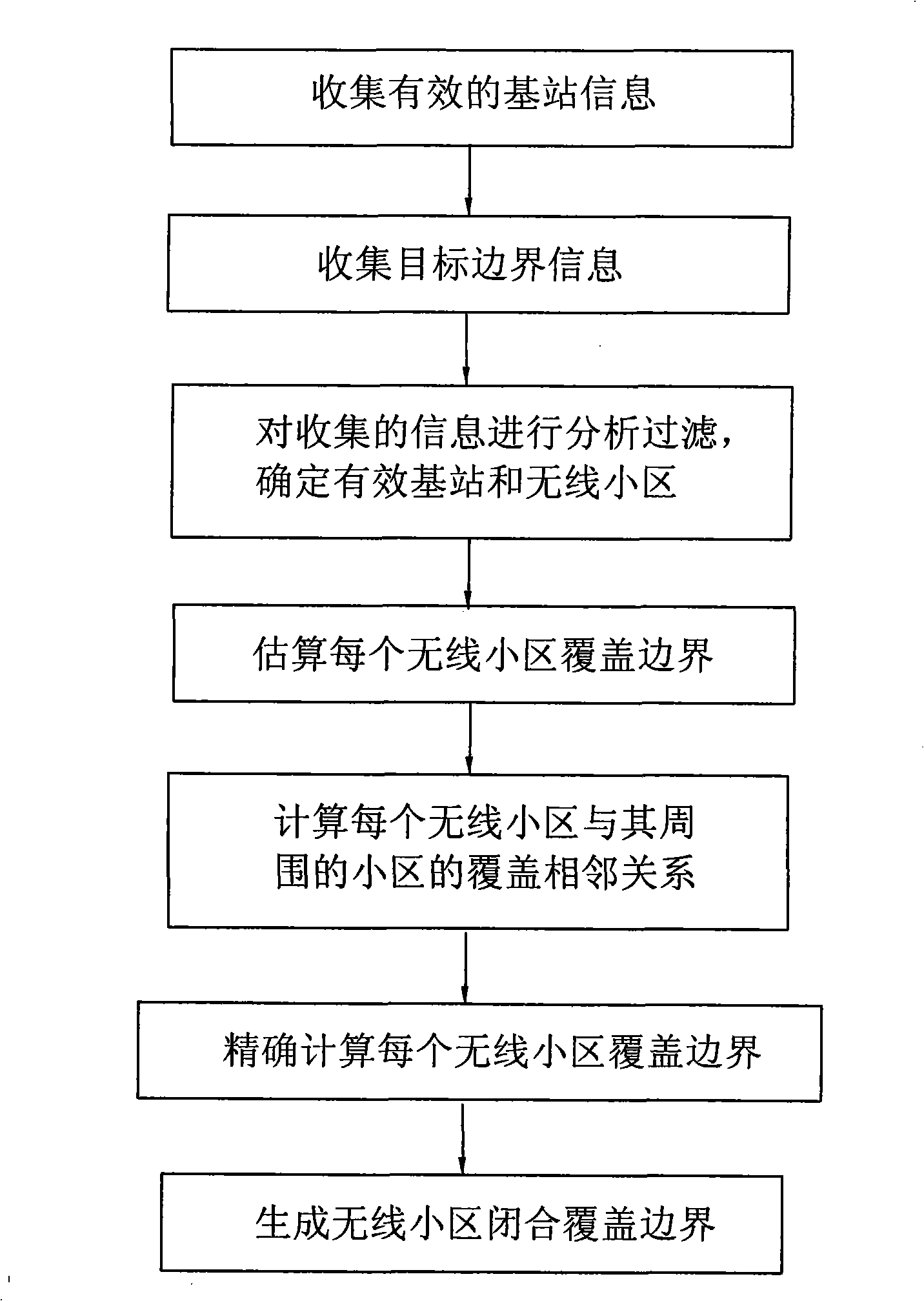
ActiveCN101541013AIgnoring factors that cover less influentialEfficiently obtainedNetwork planningLongitudeAdjacency relation
The invention belongs to a fast generation method for wireless cell coverage distribution in the field of mobile communication. The method is realized through the following steps: collecting effective base-station information; collecting target-boundary information; analyzing and filtering the collected information so as to determine effective base stations and wireless cells; estimating the regional coverage of each wireless cell, finishing and outputting the estimated regional coverage of each wireless cell in a coordinate mode; calculating the coverage adjacency relation between each wireless cell and the surrounding wireless cells thereof according to the estimated regional coverage of each wireless cell, and generating an adjacency matrix of base-station adjacency relation; adopting smoothing algorithm to accurately calculate the coverage boundaries of the wireless cells; and generating a wireless-cell closed coverage boundary with continuous coordinate points taking latitude and longitude as a unit. The method is simple to realize, can fast and effectively generate multilevel actual coverage-distribution fitting graphs of wireless cells, base stations, base-station controllers and mobile switches, and can be widely applied to GIS application analysis, mobile network optimization and other fields.
Owner:CHINA MOBILE COMM CORP TIANJIN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com