Network security evaluation device based on attack graph adjacent matrix
A technology of network security assessment and adjacency matrix, which is applied to electrical components, transmission systems, etc., can solve the problems of not being able to identify key hosts on critical paths, not being able to generate attacking network nodes, etc., and achieve easy viewing, fast calculation speed, and strong real-time performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0065] Embodiment of information collection device
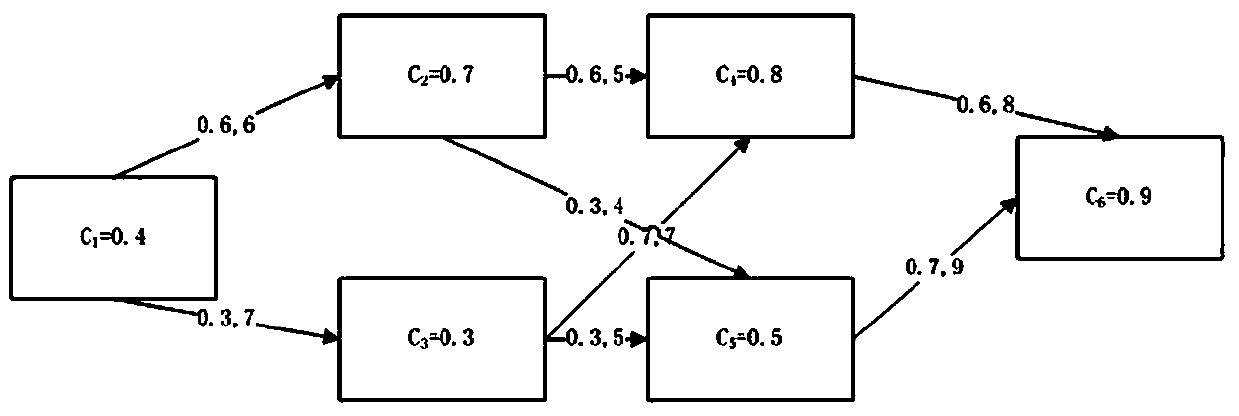
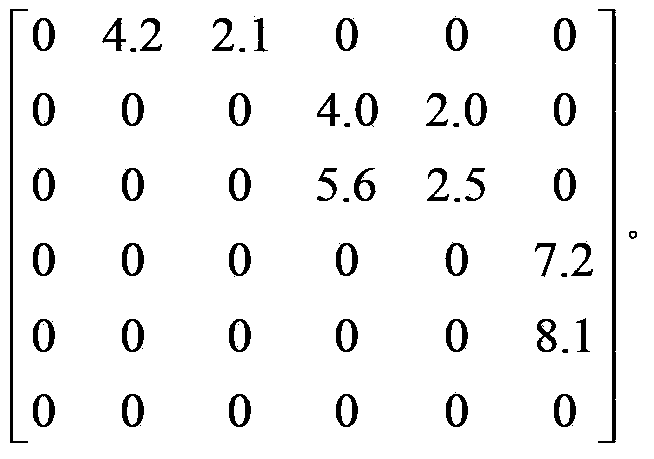
[0066] The connection mode of each host in the network can be obtained from the network topology diagram. Usually, a network is divided into several different areas separated by firewalls or routers, and the hosts in each area are interconnected. If you do not know the network topology map, use various routing search algorithms and related protocols including: DNS, ICMP, SNMP, RIP, OSPF, operating system and architecture-related protocols to obtain the routing information of each device in the entire network, and then use The obtained information automatically generates the required topology diagram. Use scanning tools or network management software to obtain network device and host configuration information. Since the host needs to provide services and must open its own port, there is a possibility of being attacked remotely. At the same time, the host itself is also vulnerable. Therefore, it is necessary to obtain the vu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com