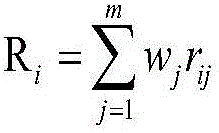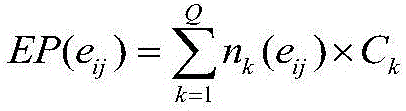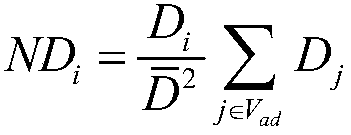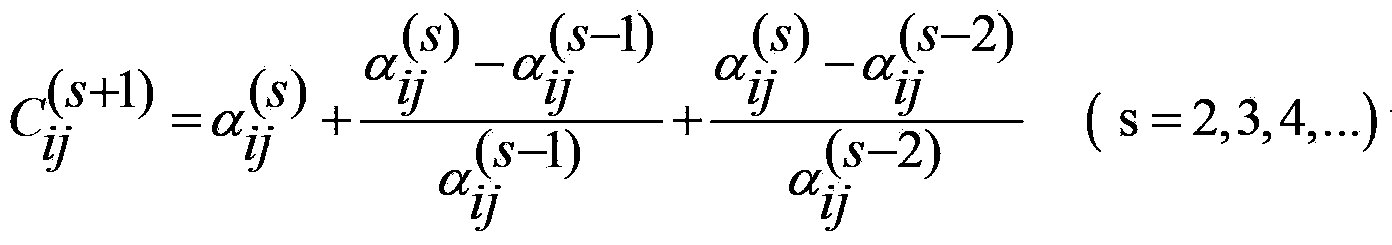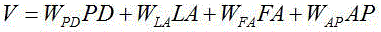Patents
Literature
143 results about "Vulnerability index" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
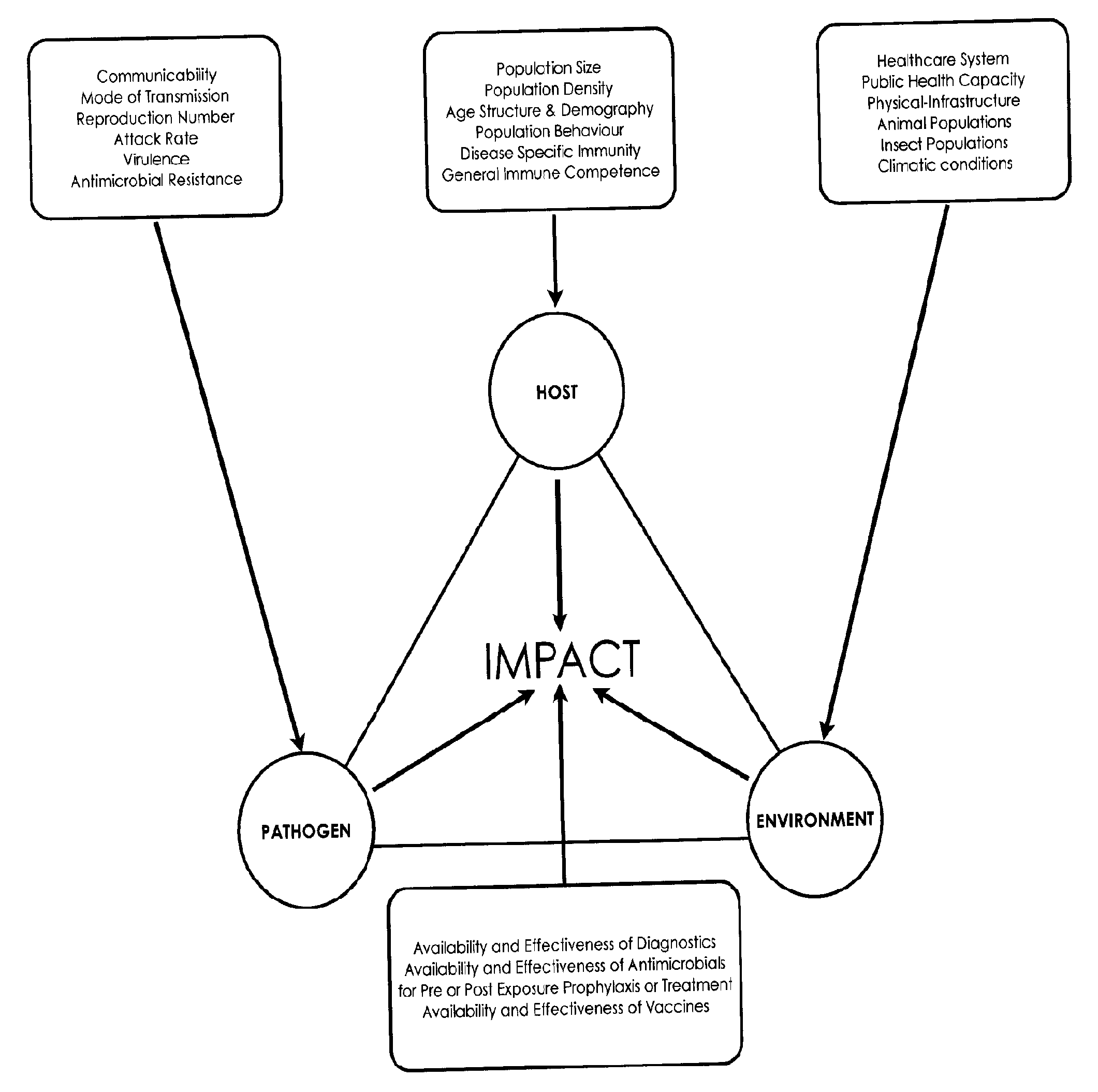
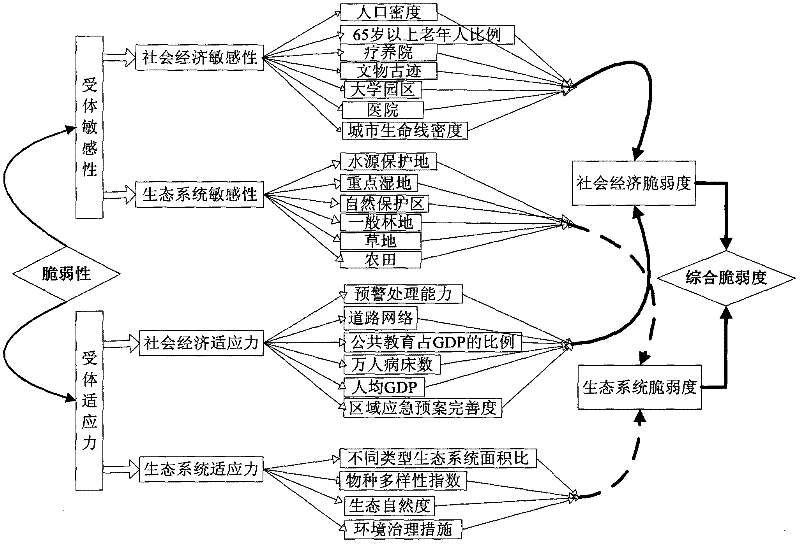
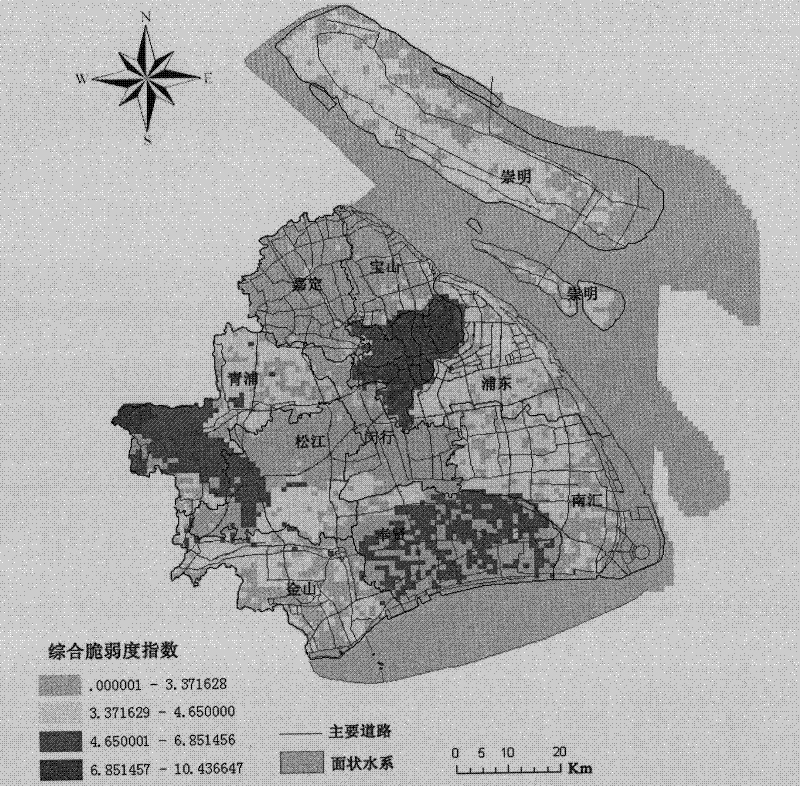
A vulnerability index is a measure of the exposure of a population to some hazard. Typically, the index is a composite of multiple quantitative indicators that via some formula, delivers a single numerical result. Through such an index "diverse issues can be combined into a standardised framework...making comparisons possible". For instance, indicators from the physical sciences can be combined with social, medical and even psychological variables to evaluate potential complications for disaster planning.
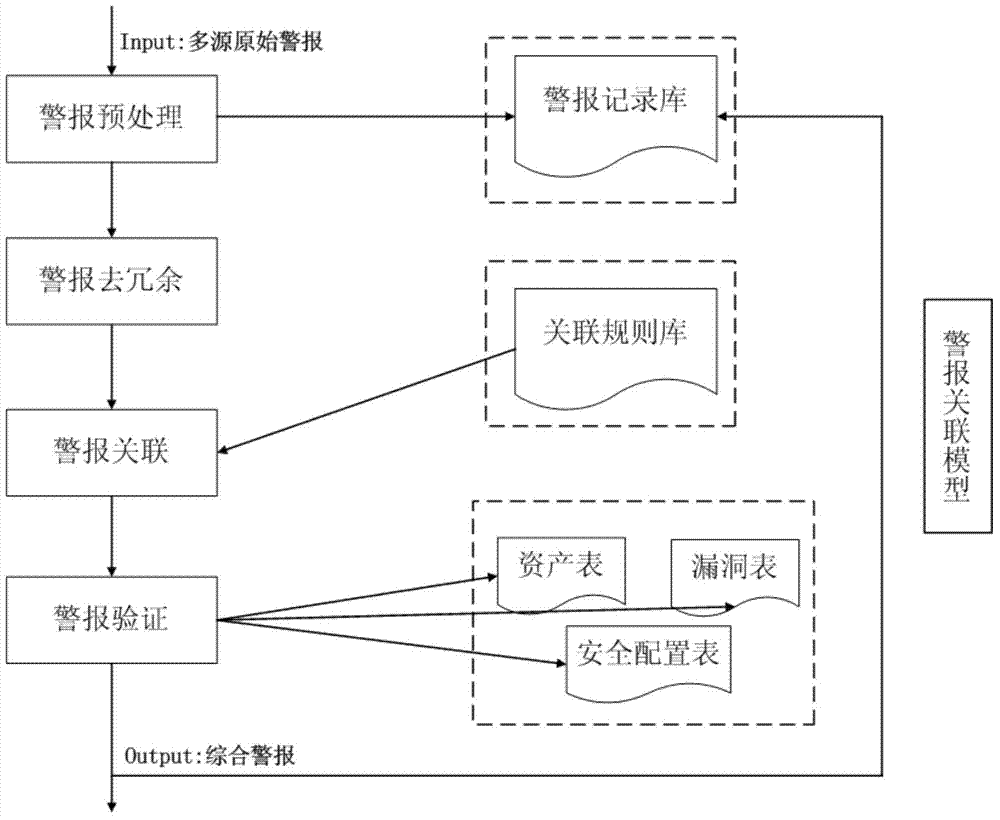
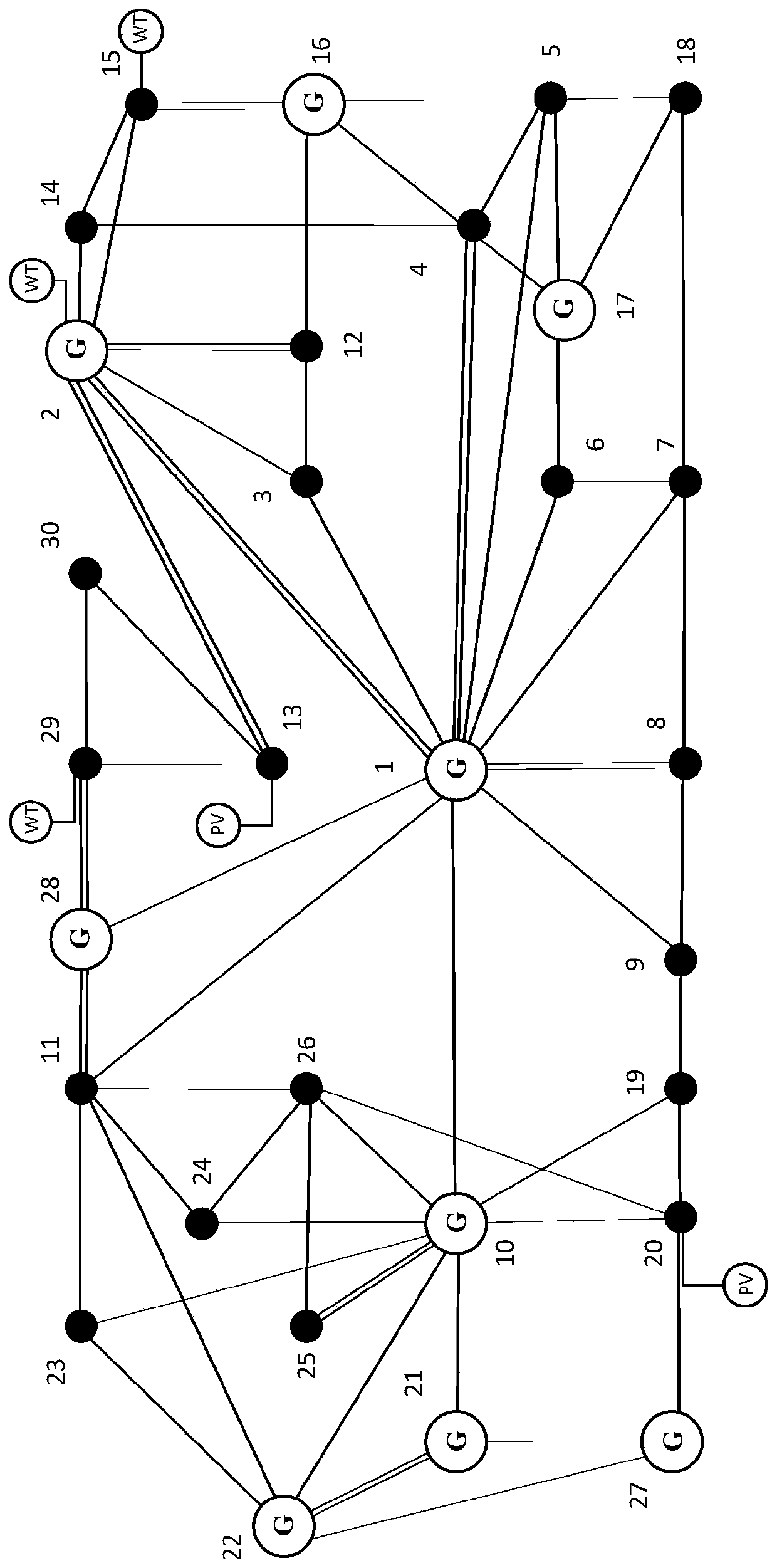
Security risk assessment method and apparatus
InactiveCN103716177AEffective positioningAchieve positioningData switching networksRisk indicatorRisk index
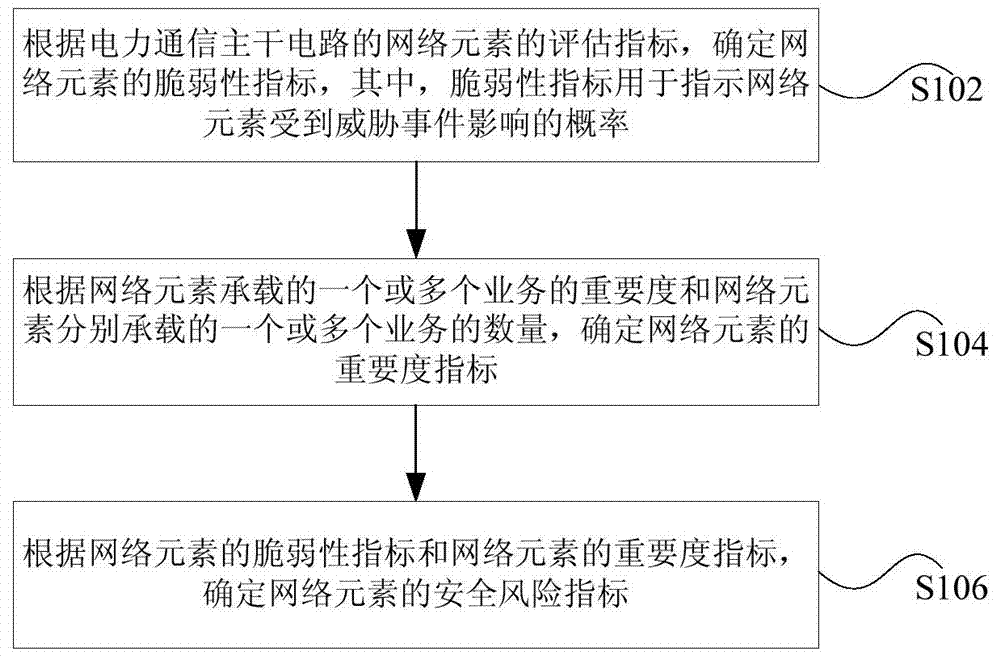
The invention discloses a security risk assessment method and apparatus. The method comprises determining a vulnerability index of a network element based on an evaluation index of the network element of an electric power communication main trunk circuit, wherein the vulnerability index is used for indicating the probability that the network element is affected by a threat event; determining an importance index of the network element based on the importance of one or more services borne by the network element and the number of one or more services respectively borne by the network element; and determining a security risk index of the network element based on the vulnerability index and importance index of the network element. According to the invention, the problem in the prior art that an electric power communication main trunk circuit system-based integral evaluation mode has difficulty in effectively locating the network element which is easy to have security risks is solved, so that the security risk assessment of the network element in the electric power communication main trunk circuit is realized and the effective locating of the network element which is easy to have security risks is facilitated.
Owner:STATE GRID CORP OF CHINA +2
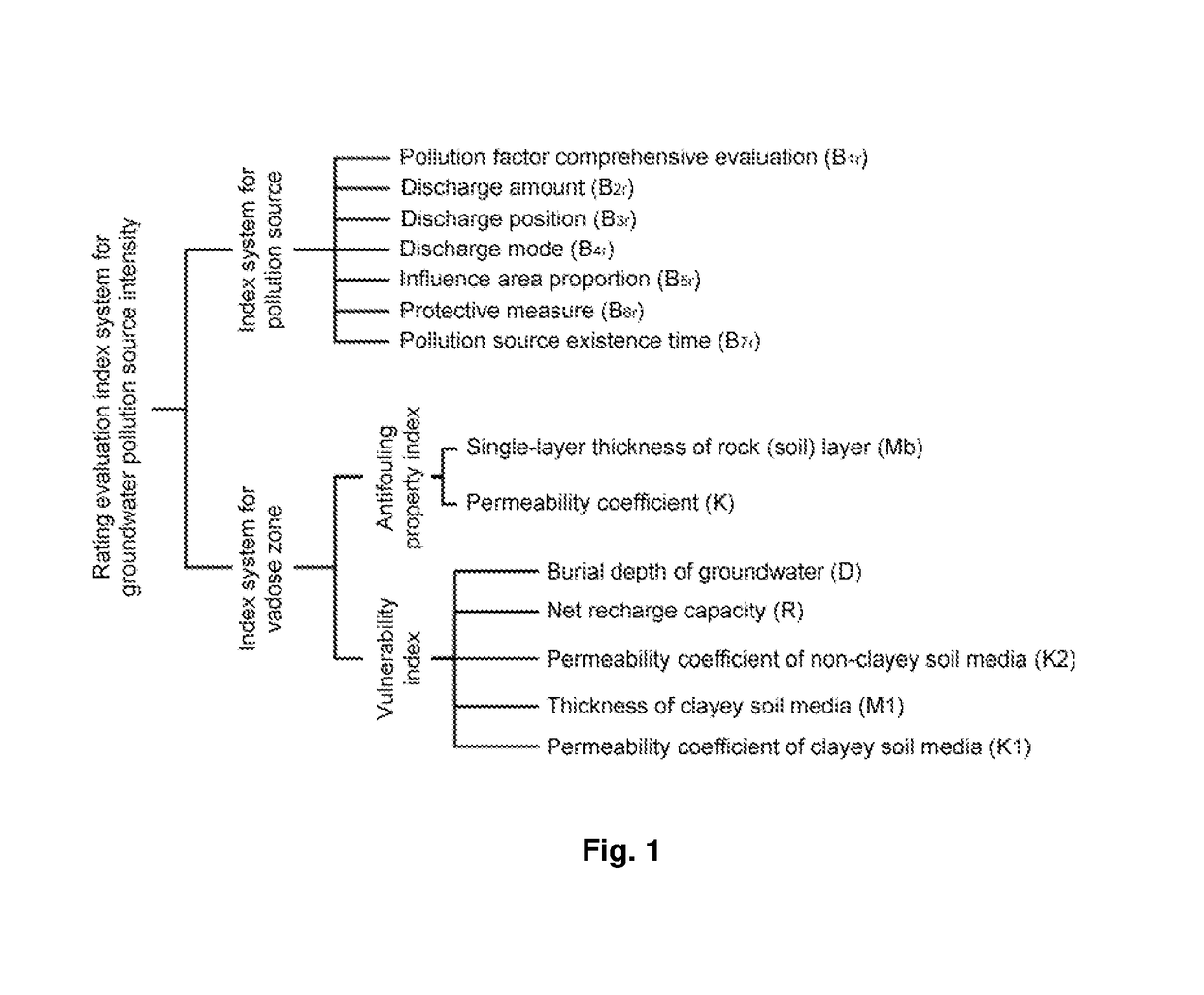
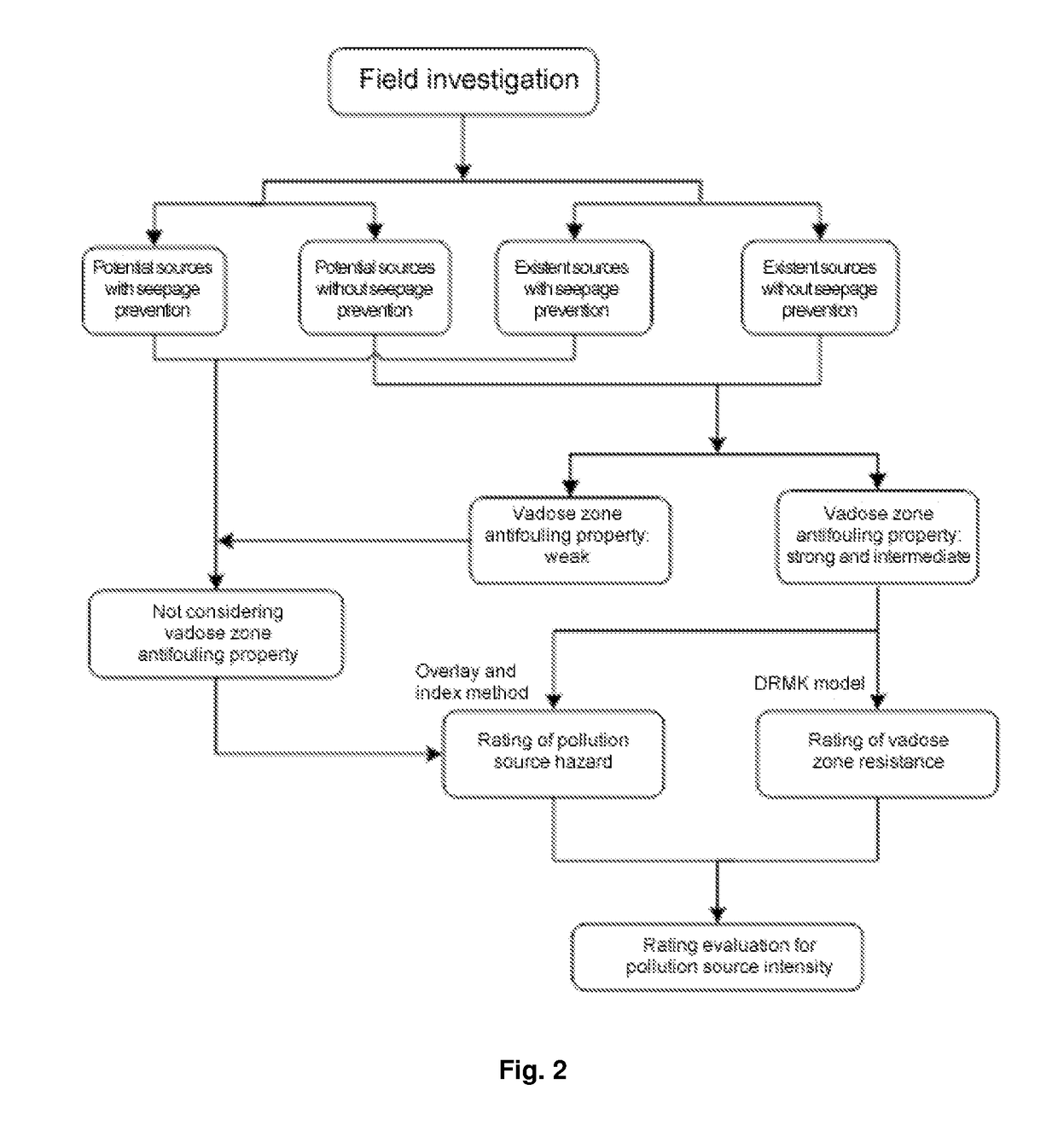
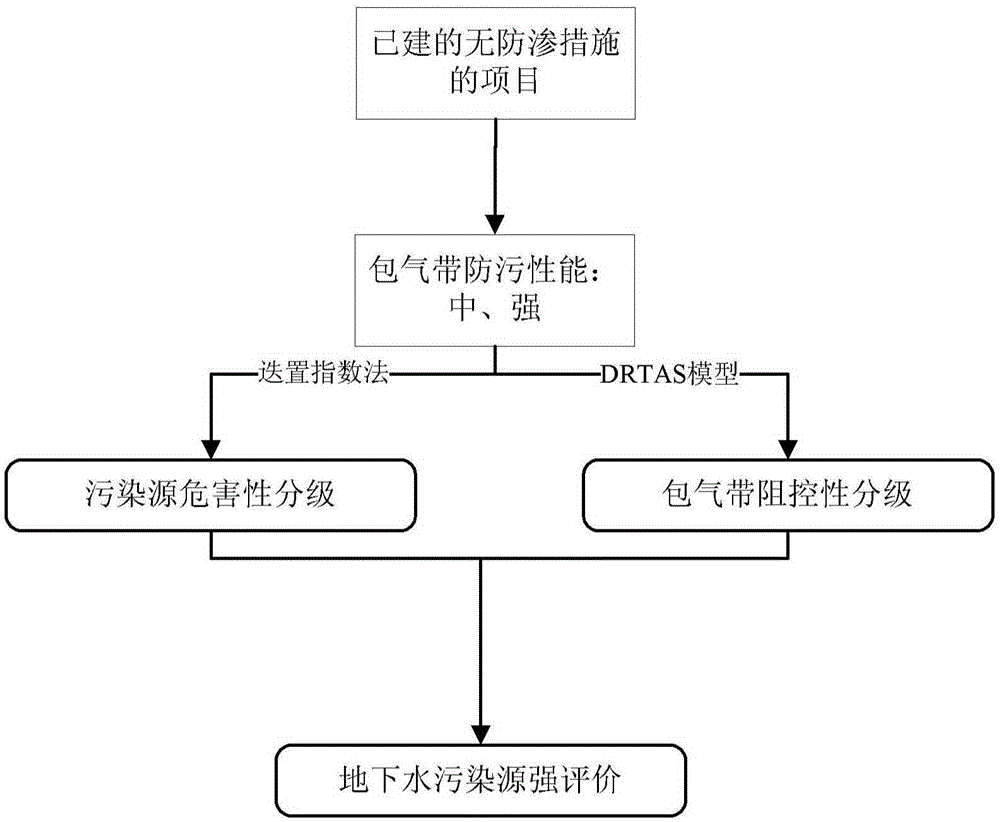
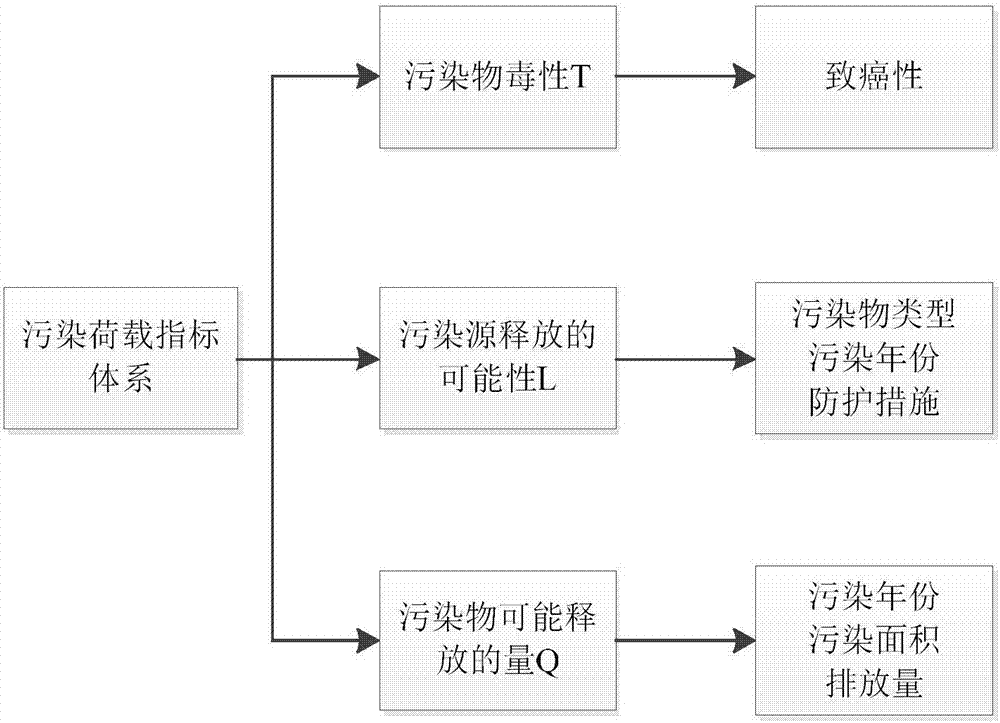
Rating evaluation method for groundwater pollution source intensity
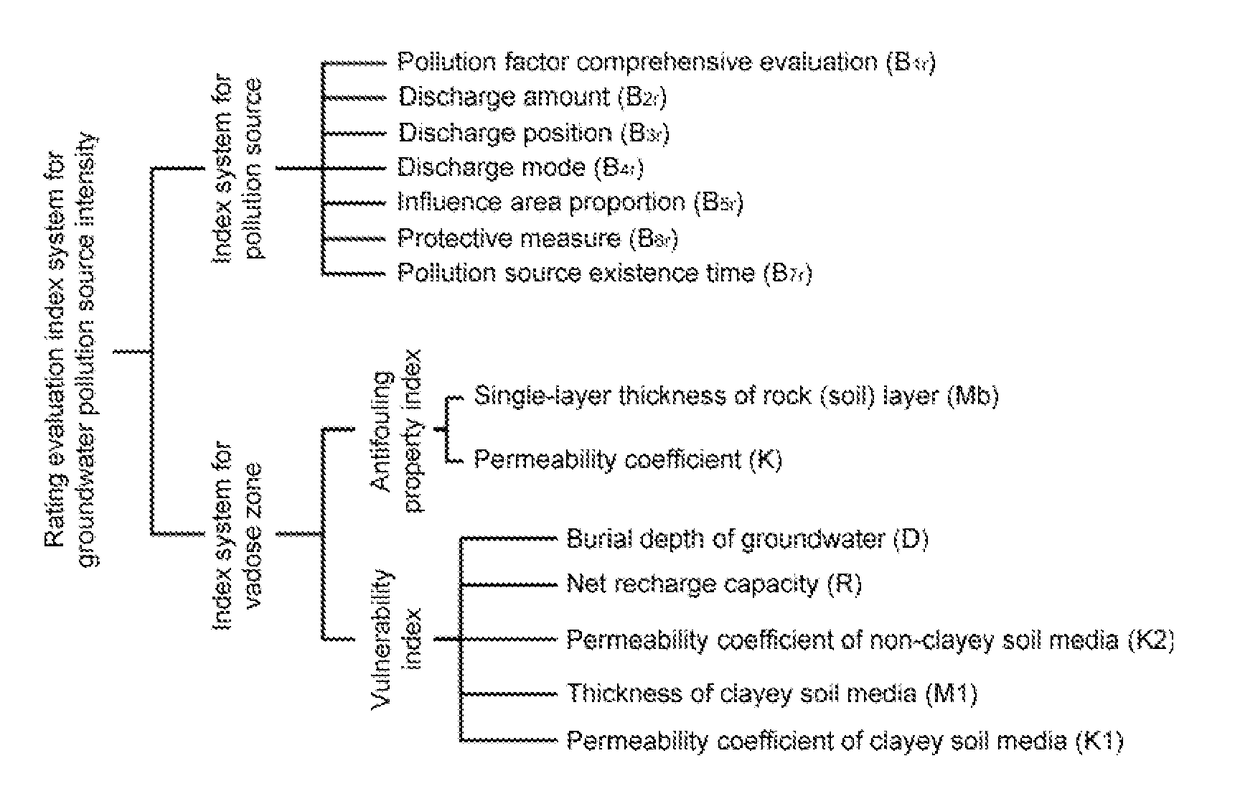
A rating evaluation method for groundwater pollution source intensity, including: determining pollution source characteristic indices, and weights and scores thereof, according to the type, the discharge mode, the existence time, and the like of a groundwater pollution source; determining an vadose zone antifouling property index and an vadose zone vulnerability index and scores thereof according to vadose zone characteristics; determining a rating evaluation index system for groundwater pollution sources by combining the pollution source characteristic indices with the vadose zone antifouling property index and the vadose zone vulnerability index; and establishing a rating evaluation method for groundwater pollution source intensity and evaluating the groundwater pollution source intensity. The evaluation method comprehensively considers pollution source characteristics and vadose zone characteristics to accurately reflect source intensities of groundwater pollutants and protect groundwater, and may provide a scientific basis to allow for more scientific and rational protection and management of groundwater.
Owner:CHINESE RES ACAD OF ENVIRONMENTAL SCI
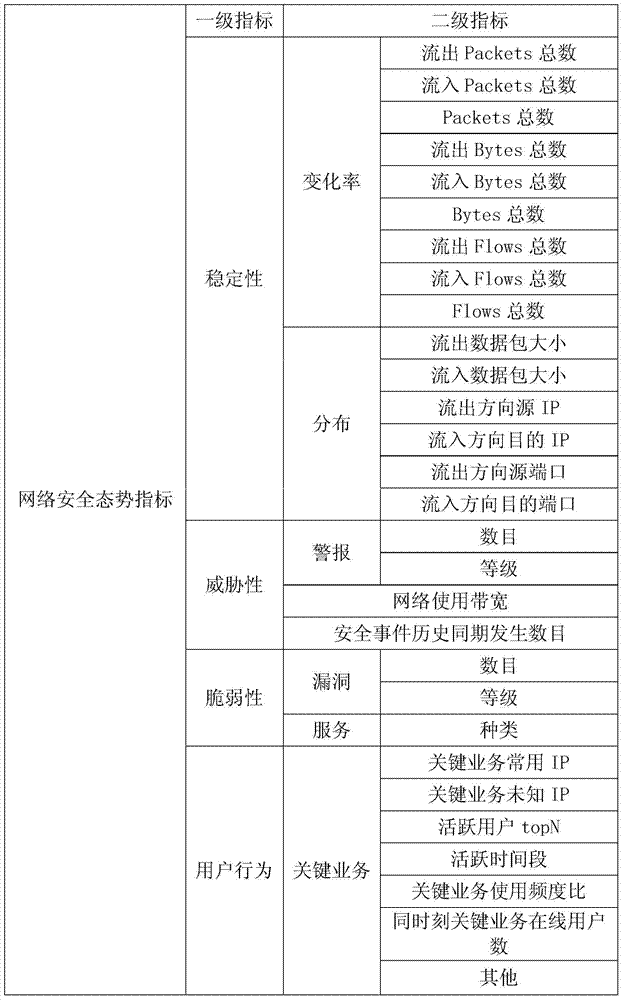
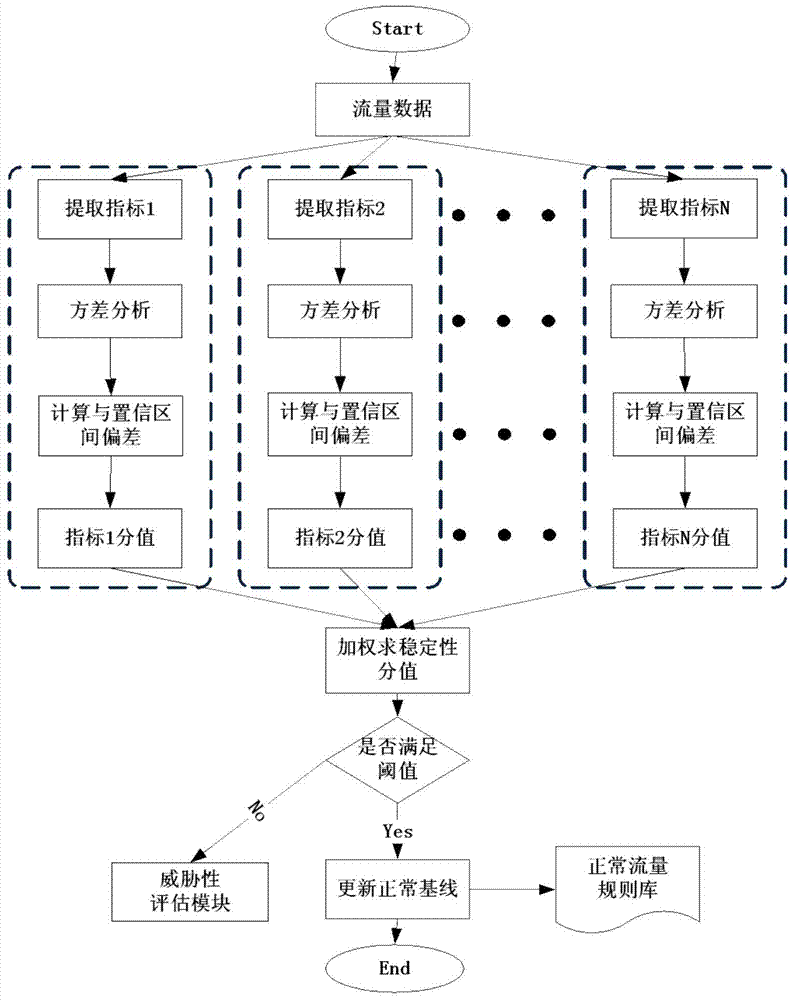
Network security situation awareness method and system
ActiveCN103581186AStability RefinementEasy to implementData switching networksStability indexVulnerability index
The invention relates to a network security situation awareness method and system. The network security situation awareness method comprises the steps that key elements capable of being used for describing the network security situation are extracted, including network flow stability, threatening, vulnerability and user behaviors, second-level index score calculation and first-level index score calculation are carried out on the extracted key elements, first-level index scores include a network flow stability index score SS, a threatening index score TS, a vulnerability index score VS and a user behavior index score US, and finally the value of the entire network security situation is calculated by utilizing the weighted sum. The network security situation awareness method and system aim to establish comprehensive network security situation awareness indexes and improve the effectiveness and the real-time performance of the network security situation awareness.
Owner:SHANGHAI YINGLIAN SOMATOSENSORY INTELLIGENT TECH CO LTD
Security emergency processing method and system based on analytic hierarchy process
ActiveCN106960269AShorten the emergency response cycleInhibited DiffusionResourcesRisk levelCountermeasure
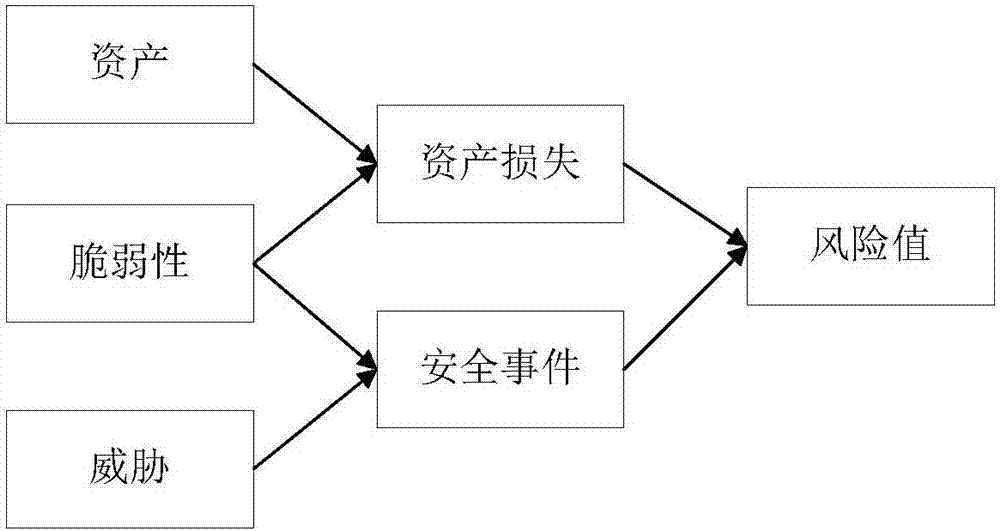
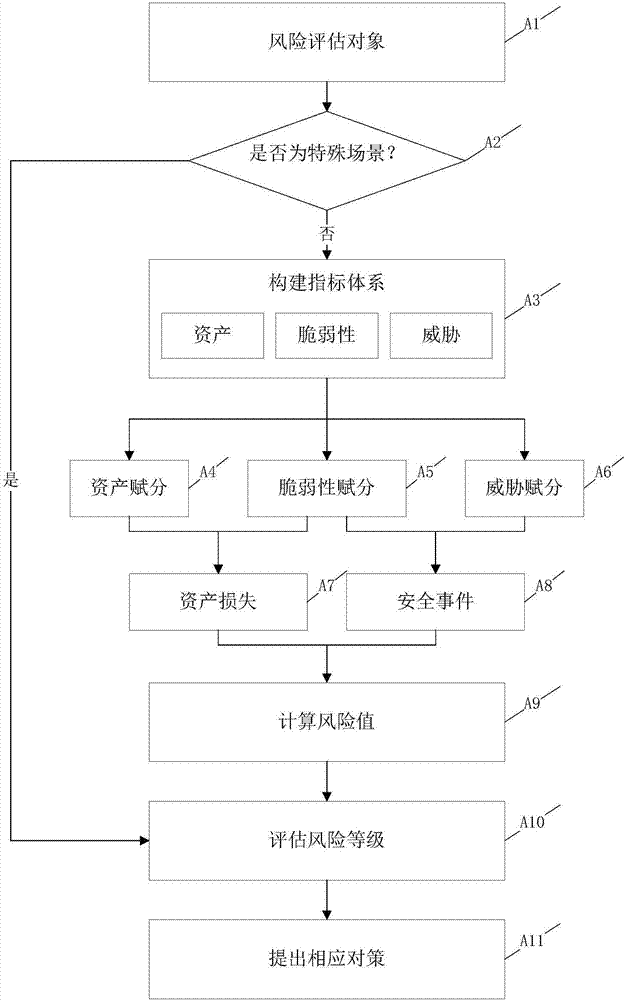
The invention belongs to the information security technology field and more particularly, to a security emergency processing method and system based on analytic hierarchy process. The method comprises the following steps: S1) determining a risk evaluation object; S2) determining whether the risk evaluation object is located in a special scene or not; if the risk evaluation object is, then, switching to the step 5; otherwise, constructing an index system featuring the asset, the vulnerability and the threat; S3) assigning a score to the asset index; using the analytic hierarchy process to assign scores to the vulnerability index and the threat index; calculating the scores of asset loss and the security event and obtaining the corresponding risk values; S4) according to the risk values, dividing the security levels; and S5) proposing different processing policies according to the different risk levels. According to the invention, the method and the system integrate the security risks of the asset importance, the vulnerability degree and the threat and then, further, quantify and divide them into different levels, which effectively shortens the emergency processing cycle of a security event, contains the spreading of the security risk and raises the overall security emergency efficiency.
Owner:ZHEJIANG PONSHINE INFORMATION TECH CO LTD
Water quality model based regional environment risk assessment method
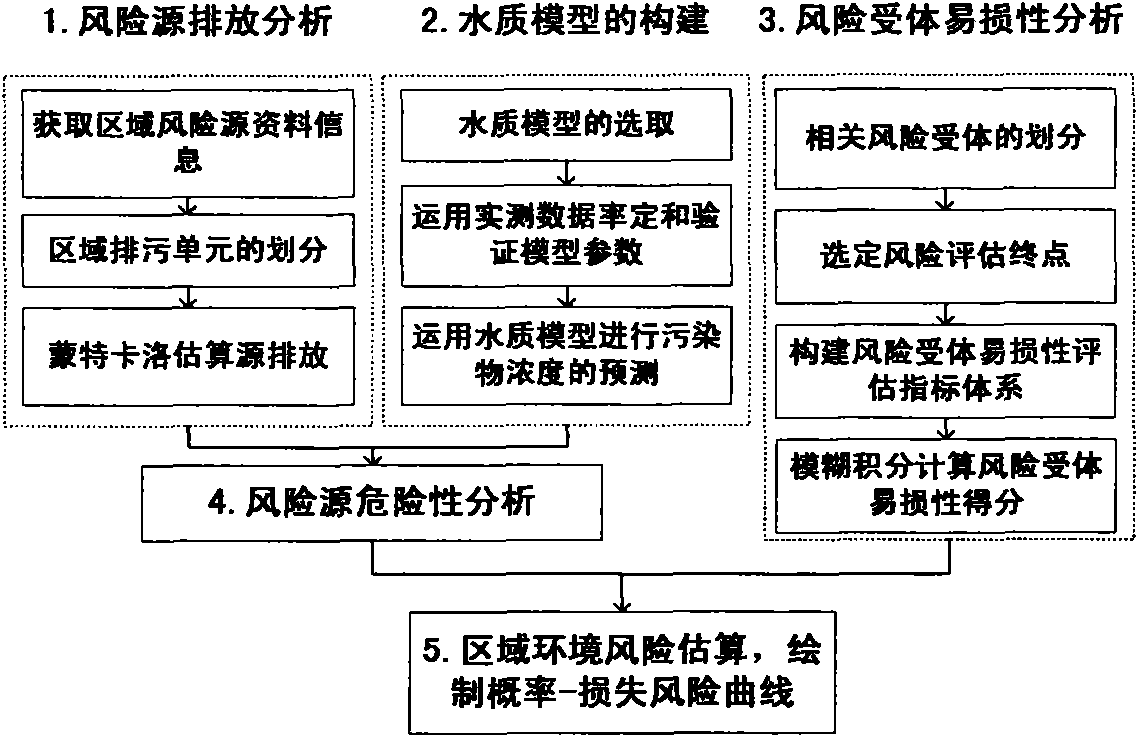
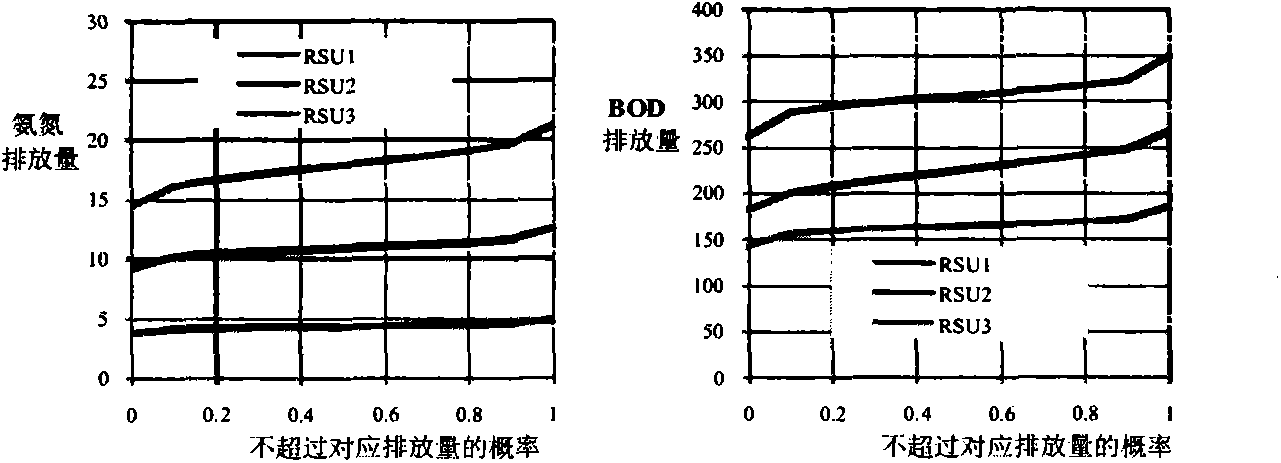
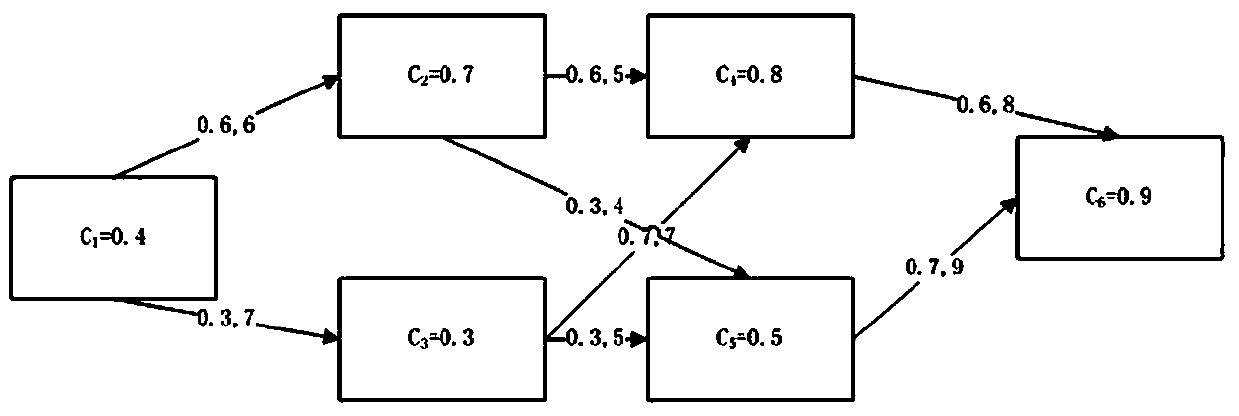
The invention provides a water quality model based regional environment risk assessment method. The water quality model based regional environment risk assessment method includes five steps of establishing a regional environment risk source information database, and utilizing a Monte Carlo algorithm to simulate discharge of risk source pollutants; selecting a water quality model, and constructing a water quality model which meets characteristics of an assessment region source intensity water quality response relationship; calculating vulnerability indexes of risk receptors by using a fuzzy integral method with the risk assessment goal of influence on water ecology, human health and social economy; utilizing the water quality model to predict the distribution of regional pollutant concentration under all possible source intensity situations, and analyzing dangerousness of risk sources; characterizing regional environment risks with a risk curve under the synthesis of dangerousness of the risk sources and vulnerability indexes of the receptors. According to the risk curve, regional environment risk assessment can be performed, high-risk regions, and key risk sources and vulnerary receptors are identified, so that a reference is provided for planning a targeted region risk prevention and control scheme.
Owner:NANJING UNIV
Network security evaluation device based on attack graph adjacent matrix
The invention provides a network security evaluation device based on an attack graph adjacent matrix. The network security evaluation device comprises an information collection device, an atom attack graph generation device, a matrix calculation device, a network safety analyzing device and a result appearing device, wherein the information collection device is used for collecting all information in a network; the atom attack graph generation device is used for generating an initial atom attack graph between a main engine pair needed for carrying out subsequent analysis on network safety; the matrix calculation device is used for converting the generated atom attack graph into the corresponding adjacent matrix and is also used for calculating a corresponding iteration matrix of the adjacent matrix through setting iteration times; the network safety analyzing device is used for obtaining information including a key main engine, a key path and the like on the basis of the finally-generated iteration matrix; the result appearing device is used for visually appearing the found key main engine and key path and a network vulnerability index. The network security evaluation device disclosed by the invention is high in efficiency and is suitable for large-scale and high-speed networks. The network security evaluation device can improve the instantaneity of evaluating a target network. The evaluation accuracy rate is high, and the key path and the key main engine can be accurately recognized. The visualization degree is high so that the network security evaluation device is convenient for a manager to check, analyze and maintain.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Assessment method for vulnerability of smart distribution network based on dynamic probability trend
ActiveCN102930175AImprove self-healing abilityData processing applicationsSpecial data processing applicationsRisk theoryVulnerability index
The invention relates to an assessment method for vulnerability of a smart distribution network based on a dynamic probability trend. The assessment method comprises the following steps: adopting a basic function and a random function to form probability distribution for node injection power of the smart distribution network; computing probability distribution for busbar voltage and line power according to Gram-Charlier stage number and semi invariant; utilizing a piecewise function to compute harm severity index caused by voltage, current and power on the smart distribution network; and then computing to output the vulnerability index of the smart distribution network. According to the invention, the method based on risk theory adopts the dynamic probability trend method to access the vulnerability, and enables a self-healing control scheme of the smart distribution network to adapt to change of load and operating environment of the smart distribution network, so that the smart distribution network can operate safely, reliably and economically.
Owner:HOHAI UNIV +2
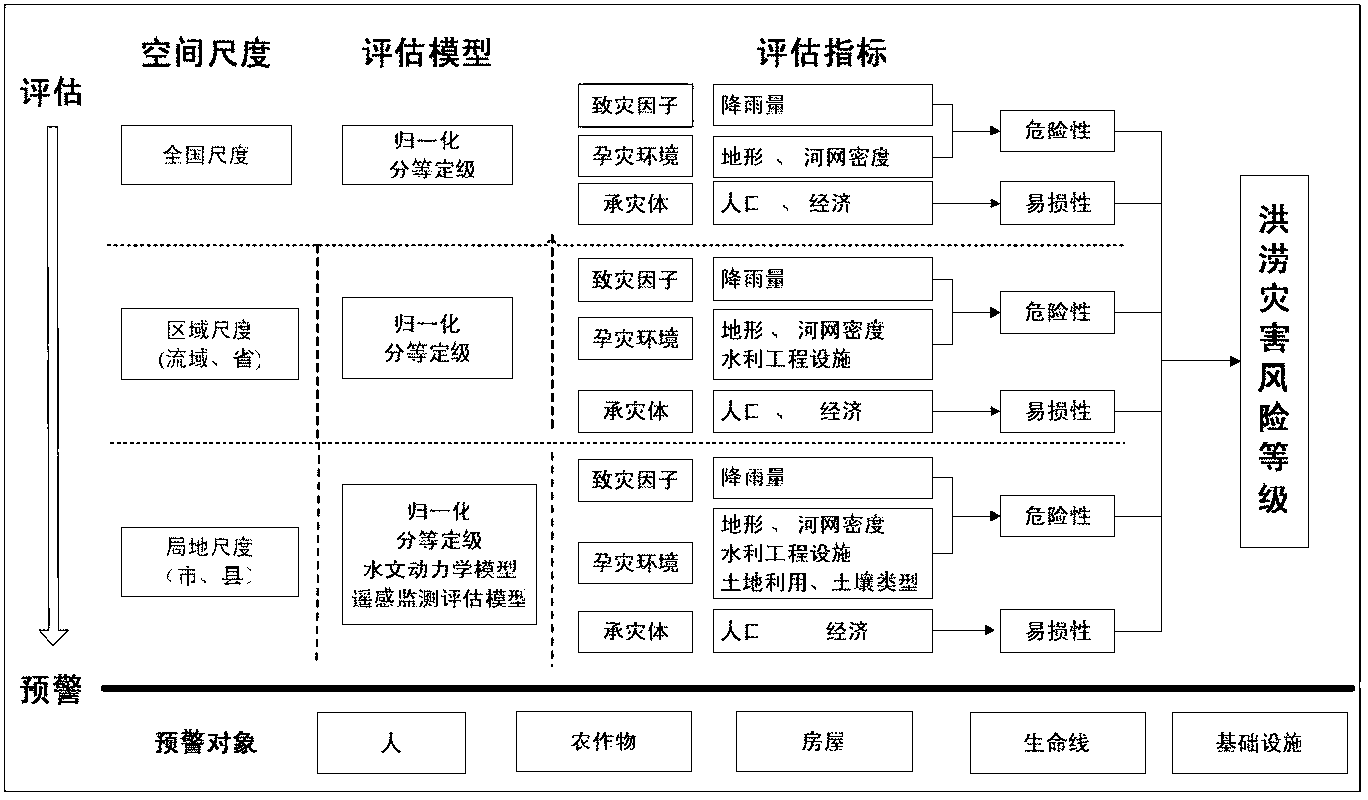
Method and device for grading flood risk
InactiveCN103218522AIncrease the frequency of monitoringSpecial data processing applicationsRisk levelTerrain
The invention provides a method for grading flood risk according to a plurality of space scales. Under each space scale, the method comprises the following steps of: S1, calculating a flood risk index by taking a precipitation amount index, a river-lake index and a terrain index as risk evaluating factors of flood; S2, calculating a vulnerability index after calculating vulnerability evaluating factors of the flood by taking a population density index and an economic GDP (Gross Domestic Product) density index as evaluating factors; and S3, generating a flood risk index by synthesizing the risk index and the vulnerability index, and further grading the flood risk index to generate a flood risk level. The method is implemented in a sequence from larger space scales to smaller space scales. Due to the adoption of the method for grading the flood risk, areas with social and economic damages possibly caused by flood disaster phenomena and risk levels can be analyzed on different space scales, and the monitoring frequency of highly-risky areas is increased.
Owner:MIN OF CIVIL AFFAIRS NAT DISASTER REDUCTION CENT
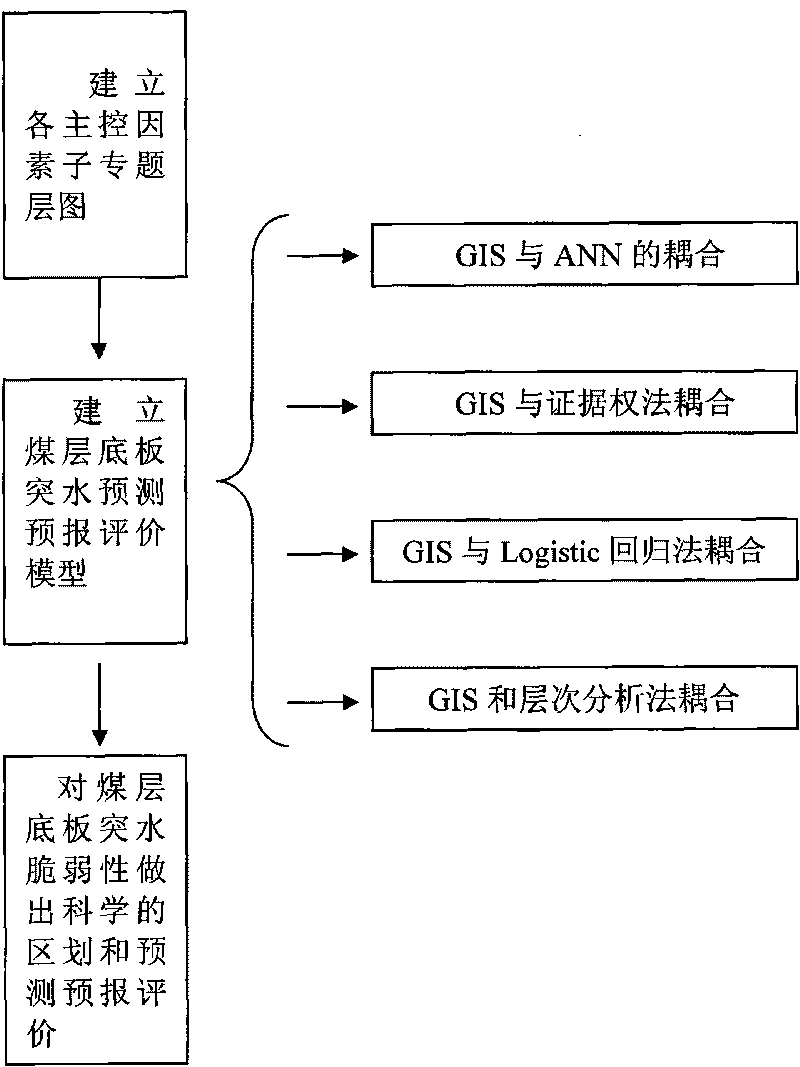
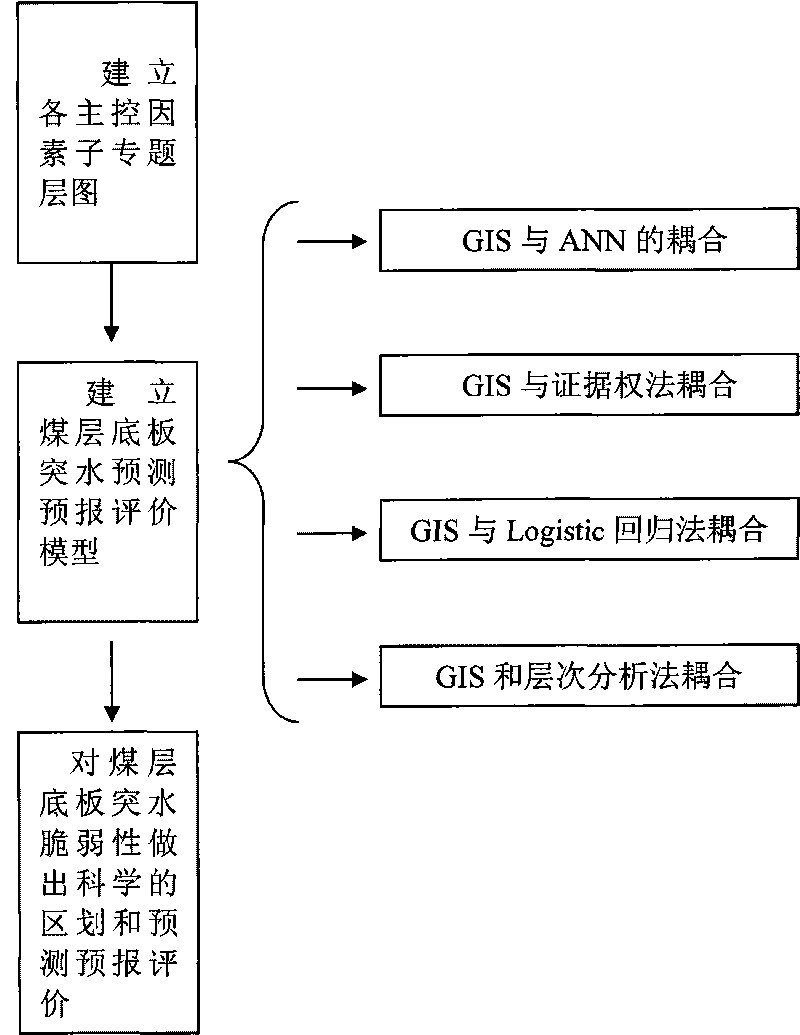
Novel practical method frangibility index method for evaluating seam floor water inrush
InactiveCN101699451ASolve the difficult problem of water inrush prediction and evaluationSpecial data processing applicationsMaterial defectCoupling
The invention relates to a frangibility index method for evaluating seam floor water inrush, which comprises the following steps: determining main control factors of the seam floor water inrush by taking GIS as an operating platform based on a multi-source information fusion theory, and establishing a sub-subject layer diagram for each main control factor through data acquisition, analysis and processing; determining the 'contribution' or the 'weight' of each main control factor to a complex water inrush process and establishing a forecast evaluation model for the seam floor water inrush through the inversion identification or the learning training of the model by applying a multi-source geoscience data composite superposition principle and adopting a modern linear or non-linear mathematical method; and reasonably determining a subarea threshold value of the water inrush frangibility according to the analysis of a frequency histogram of water inrush frangibility indexes calculated by each unit in a research area and finally making a scientific division and a forecast evaluation on the seam floor water inrush frangibility. The method well overcomes the difficulty of the forecast evaluation on the seam floor water inrush, breaks through the restriction by significant deficiencies that the conventional water inrush coefficient method for the seam floor water inrush evaluation can only consider two control factors and has no influence 'weight' concept and the like, and adopts the GIS and the modern non-linear mathematical coupling method to truly depict the non-linear dynamic process of the seam floor water inrush which is controlled by a plurality of factors and has a very complicated formation mechanism.
Owner:CHINA UNIV OF MINING & TECH (BEIJING)
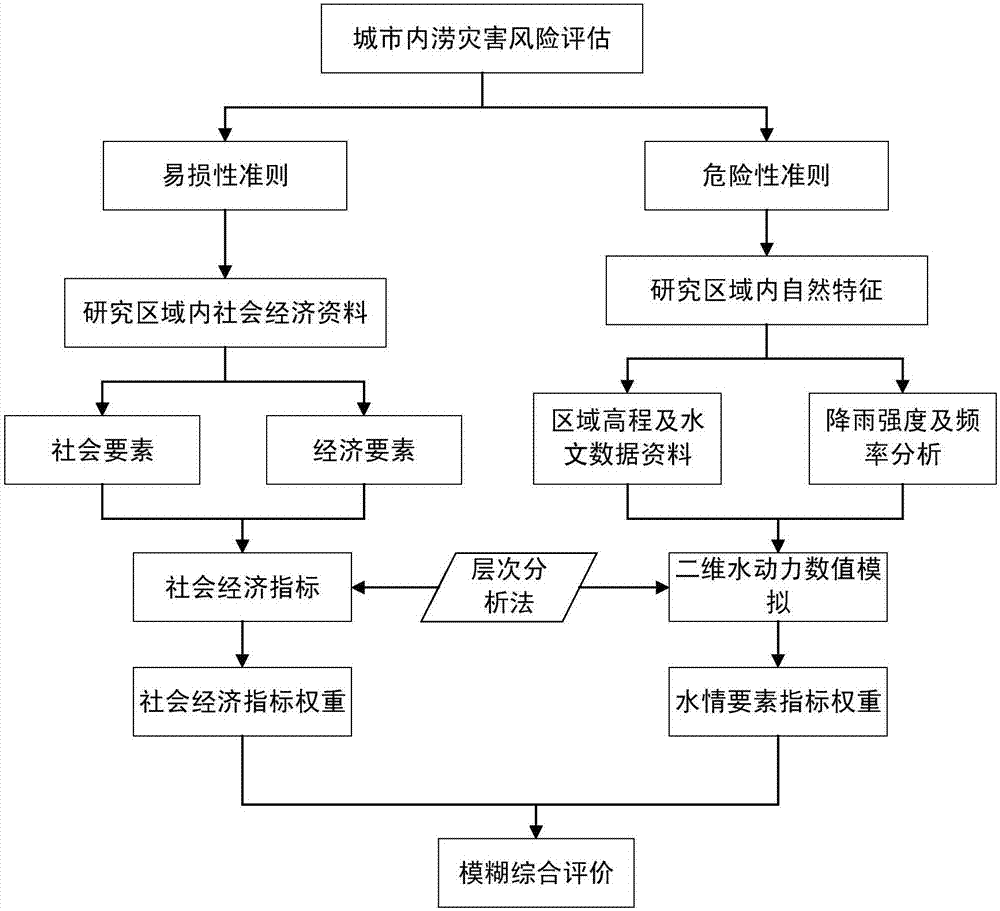
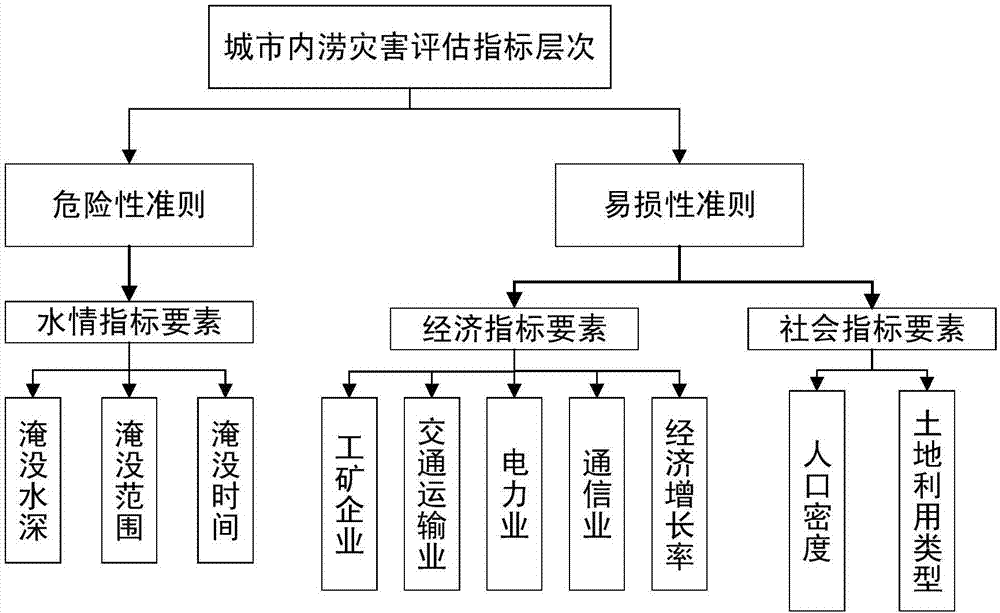
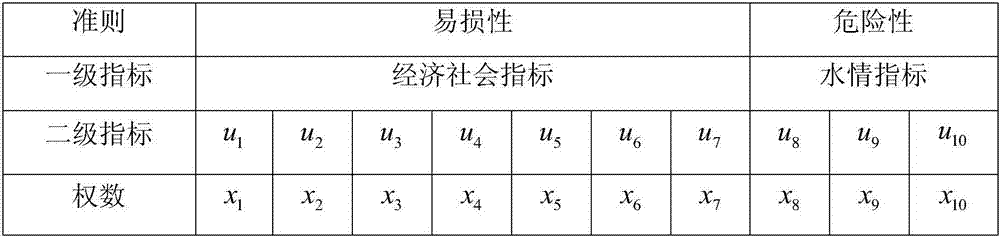
Urban inland flooding hazard risk evaluation method
The invention discloses a method for assessing the risk of urban waterlogging disasters, comprising the following steps: S1: distinguishing and determining the vulnerability index of urban waterlogging disasters; S2: determining the risk indicators of urban waterlogging disasters; S3: establishing a city based on a fuzzy evaluation method Waterlogging disaster risk assessment model; S4: Apply the assessment model obtained in step S3 to assess the urban waterlogging disaster, and determine the degree of danger and risk level of the disaster. The evaluation result of the invention is closer to the actual situation, can be widely applied to disaster management, disaster early warning, emergency rescue and the like, and has important significance for urban disaster prevention and mitigation.
Owner:SOUTHEAST UNIV
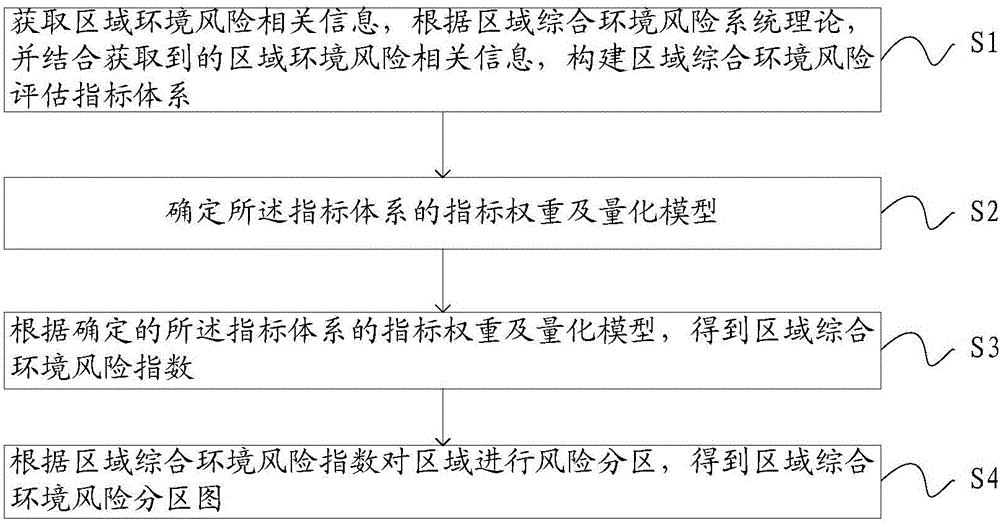
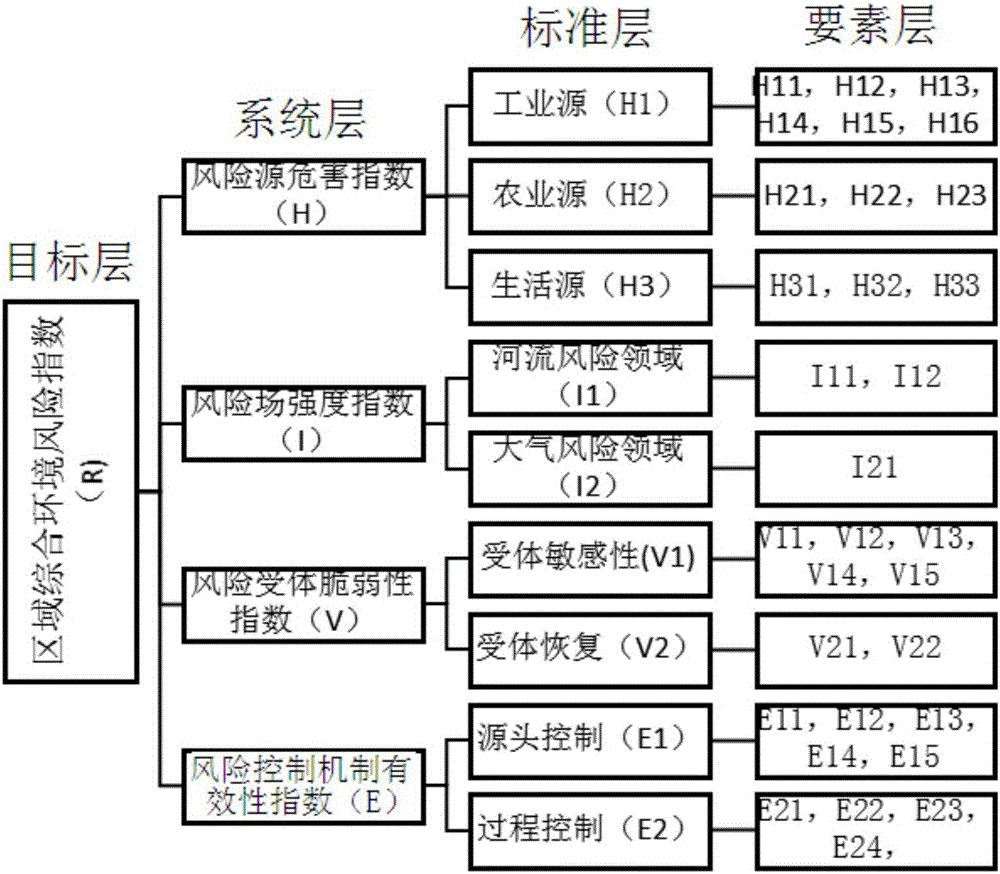
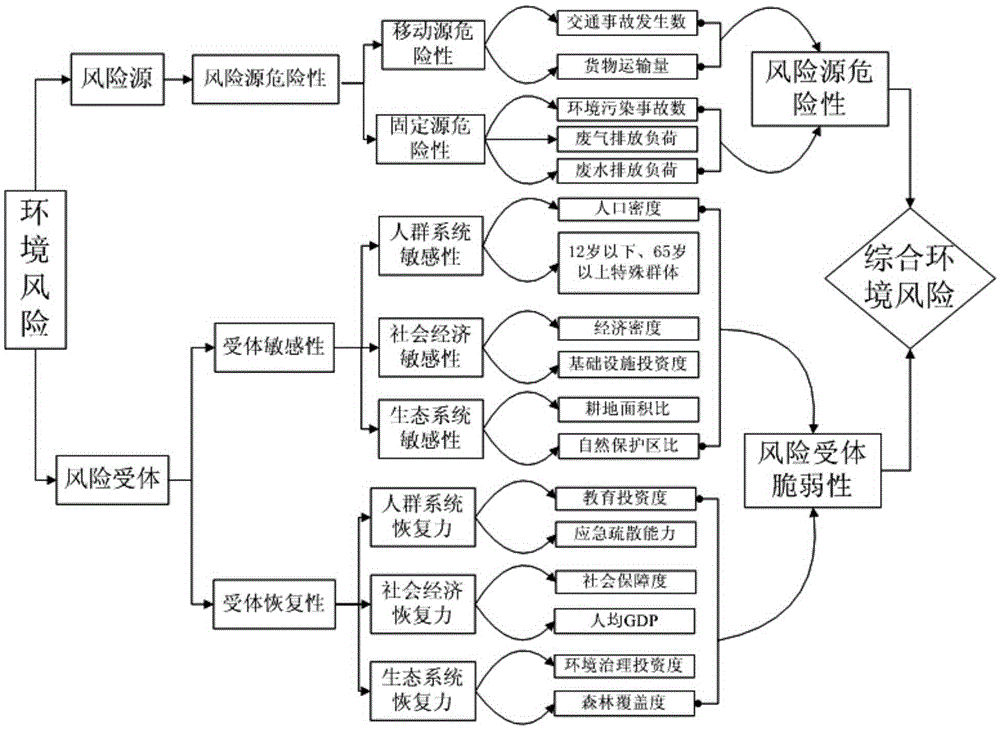
Area integrated environment risk evaluation and portioning method
The invention provides an area integrated environment risk evaluation and portioning method, for reflecting the environment risk status of an area. The method comprises the following steps: obtaining area environment risk correlation information, and according to an area integrated environment risk system theory, through combination with the obtained area environment risk correlation information, constructing an area integrated environment risk evaluation index system, wherein the index system comprises a risk source harm index, a risk field intensity index, a risk acceptor vulnerability index and a risk control mechanism validity index; determining an index weight and quantification model of the index system; according to the determined index weight and quantification model of the index system, obtaining an area integrated environment risk index; and according to the area integrated environment risk index, performing risk partitioning on the area so as to obtain an area integrated environment risk partitioning graph. The method provided by the invention is applied to the field of environment science and environment risks.
Owner:BEIJING NORMAL UNIVERSITY
Power communication network vulnerability evaluation and routing optimization method
ActiveCN106789190AImprove accuracyComprehensive performance of the size of the vulnerabilityData switching networksVulnerability factorVulnerability evaluation
The invention relates to a power communication network vulnerability evaluation and routing optimization method, and belongs to the technical field of power communications. The method comprises the following steps: modeling a network topology of a power communication network, and defining the power communication network as a weighted undirected network; establishing a vulnerability evaluation model of a node and a side according to a topology vulnerability factor, a business vulnerability factor and an equipment vulnerability influencing the vulnerability of the node and the side, and evaluating the vulnerability of the power communication network according to the vulnerability evaluation model. The factors influencing the vulnerability of the node and the side are summarized as three factors of topology vulnerability, the business vulnerability and the equipment vulnerability, and a comprehensive vulnerability index is obtained according to the relation of above mentioned three factors, thereby comprehensively displaying the vulnerability size of the node and the side, and improving the vulnerability evaluation accuracy of the power communication network.
Owner:STATE GRID HENAN INFORMATION & TELECOMM CO +1
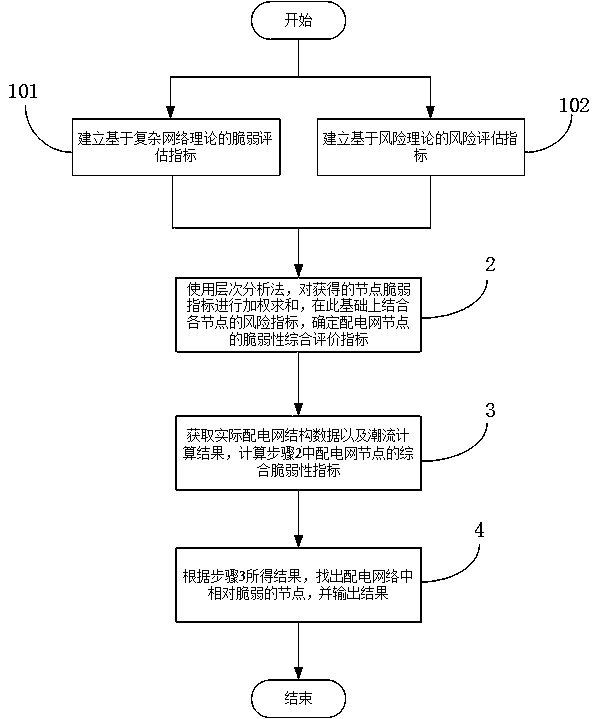
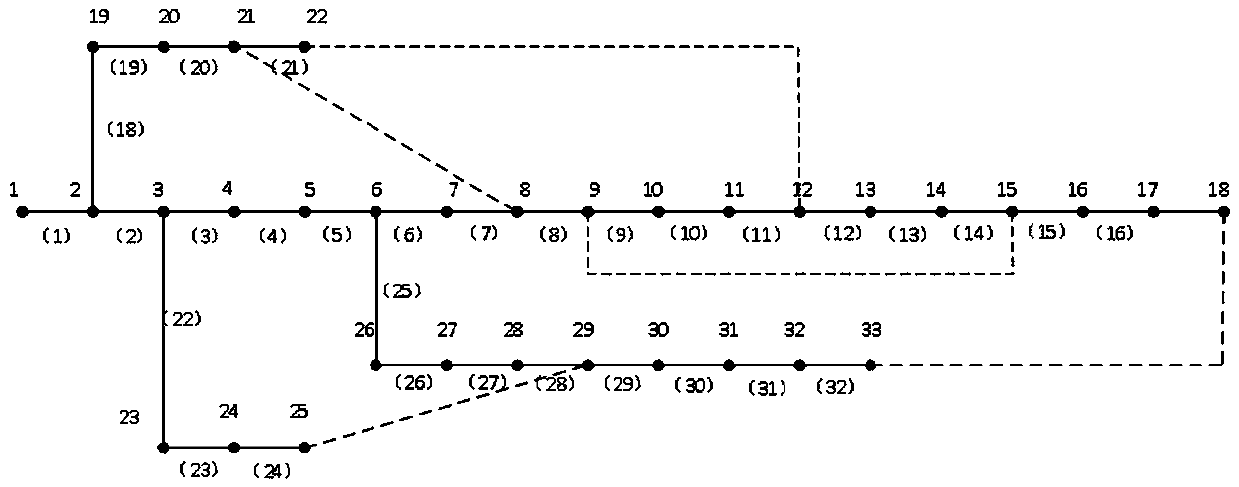
Identification method of vulnerable nodes of distribution network
PendingCN107871216AEffectively identify vulnerable nodesFind vulnerable nodesResourcesRisk theoryRisk evaluation
The invention discloses an identification method of vulnerable nodes of a distribution network. The method includes the following steps: (1) establishing vulnerability evaluation indexes based on complex network theory, and a risk evaluation index based on risk theory; (2) using a hierarchical analysis method to carry out weighted summation on the vulnerability evaluation indexes of the distribution network and comprehensively analyze the vulnerability indexes and the risk index, and establishing a comprehensive estimation index of node vulnerability of the distribution network; (3) acquiringstructure data of the distribution network and a power flow calculation result, and calculating the comprehensive estimation index of the distribution network; and (4) outputting the relatively vulnerable nodes of the distribution network. The comprehensive estimation index has the following advantages that: the complex network theory and the risk theory are adopted, a structure of the distribution network is taken into account, fault risks are taken into account, and the identification problem of the vulnerable nodes in the distribution network is comprehensively solved.
Owner:HUIZHOU POWER SUPPLY BUREAU OF GUANGDONG POWER GRID CO LTD
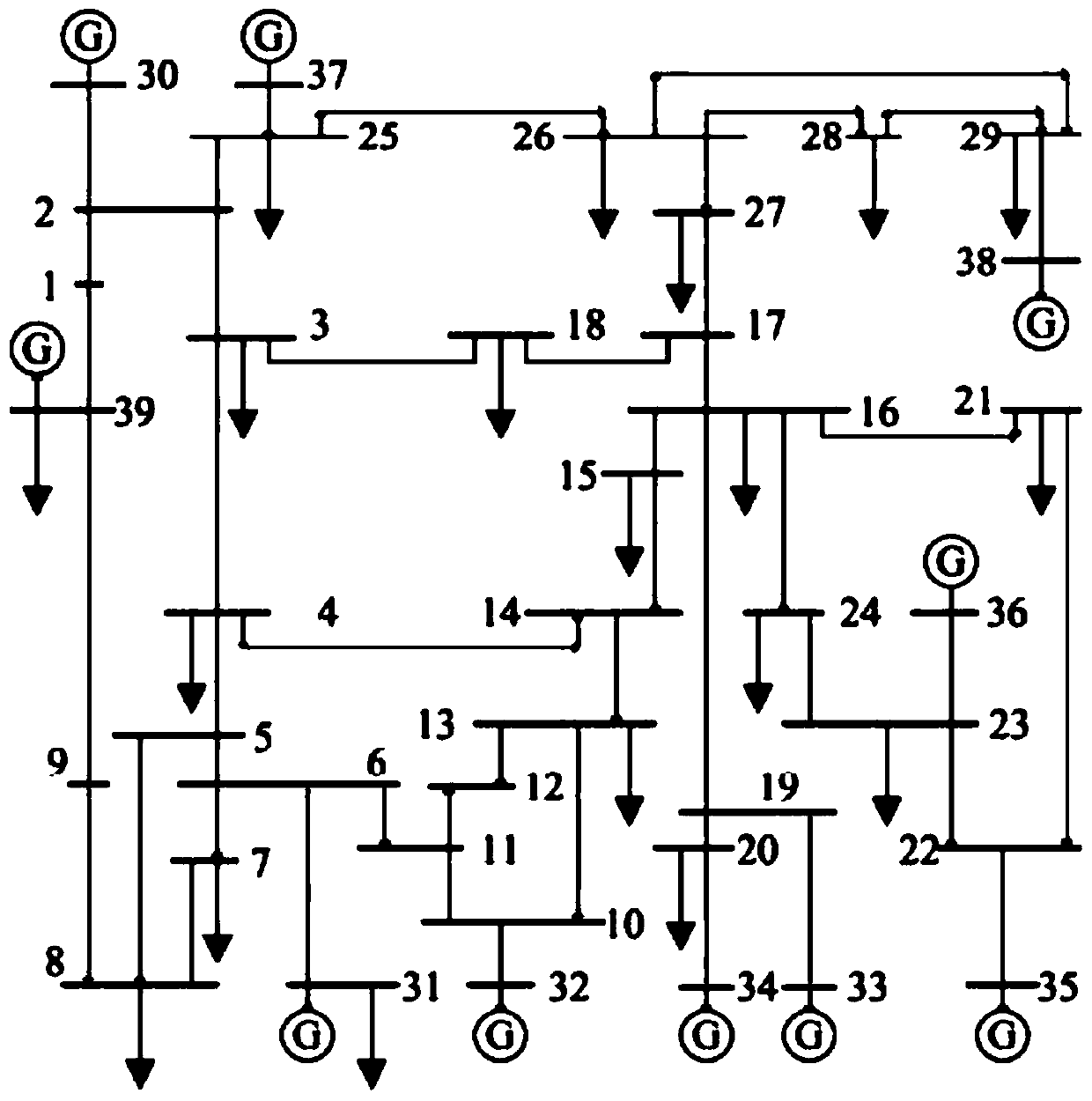
Power grid node comprehensive vulnerability index calculation method based on network analytic hierarchy process
The invention particularly relates to a power grid node comprehensive vulnerability index calculation method based on a network analytic hierarchy process. The method aims to solve the problem that node structure vulnerability and node state vulnerability are not independent, the node structure vulnerability and node state vulnerability are connected with each other, but a common analytic hierarchy process theoretically requires that the node structure vulnerability and node state vulnerability s are independent of each other, in practical application, the evaluation result of the vulnerability is unreasonable; therefore, the method is based on a network analytic hierarchy process, in the aspect of expert decision making, the mutual relation between the node structure vulnerability and thenode state vulnerability assessment result is considered; the obtained weight is more accurate; and on the other hand, an entropy weight method is utilized to reflect an objective weight value to correct the power grid node structure vulnerability and node state vulnerability weight obtained by the network analytic hierarchy process, so that a comprehensive vulnerability evaluation result of eachnode of the power grid is obtained through calculation, and sorting is carried out to judge weak links existing in the power grid. The method can meet the requirement of power grid node comprehensivevulnerability assessment under the large power grid interconnection background.
Owner:YUNNAN POWER GRID
Warning System For Infectious Diseases And Method Therefor
A computer implemented method for predicting the local area impact of the spread of global infectious diseases including the steps of providing on a computer readable medium a global pathogen risk factors database having data stored therein related to local area vulnerability of a group of human pathogens across a plurality of areas, providing on a computer readable medium a global pathogen activity database having data stored therein related to the activity of the group of human pathogens in said plurality of geographies, providing on a computer readable medium a global transport database having data stored therein related to travel patterns in and / or between the plurality of areas, processing by a computer system data on each of the global pathogen risk factors database, the global pathogen activity database and the global transport database to generate a pathogen vulnerability index, a pathogen activity index and a transportability index, and processing by the computer system each of the pathogen vulnerability index, the pathogen activity index and the transportability index to generate a risk indicator indicative of the local area impact of individual global infectious diseases.
Owner:BLUEDOT INC
Power system cascading failure mode prediction method
Owner:ELECTRIC POWER SCHEDULING CONTROL CENT OF GUIZHOU POWER GRID CO LTD +1
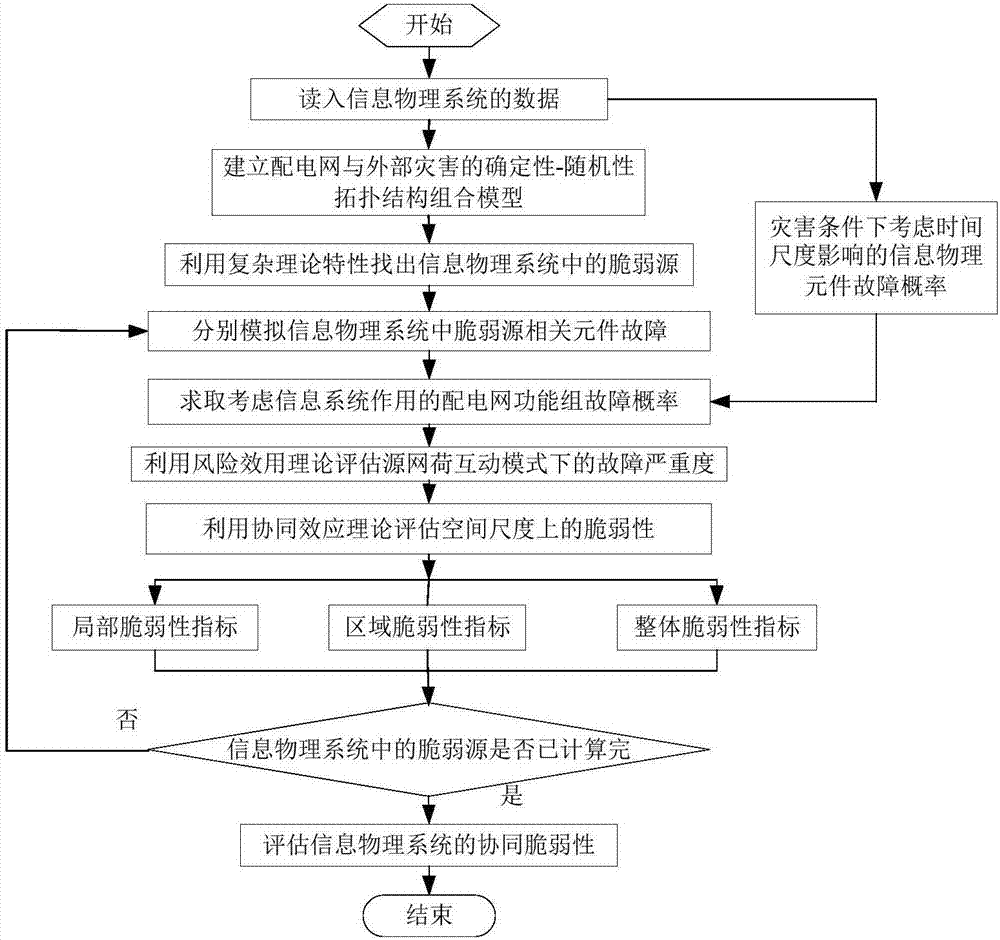
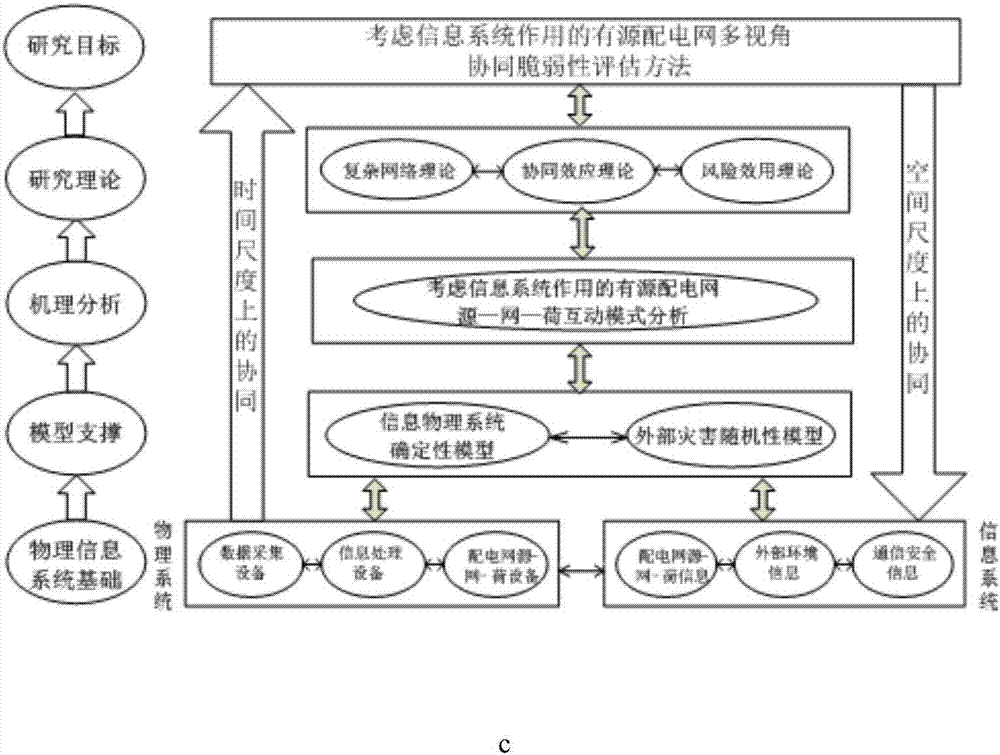
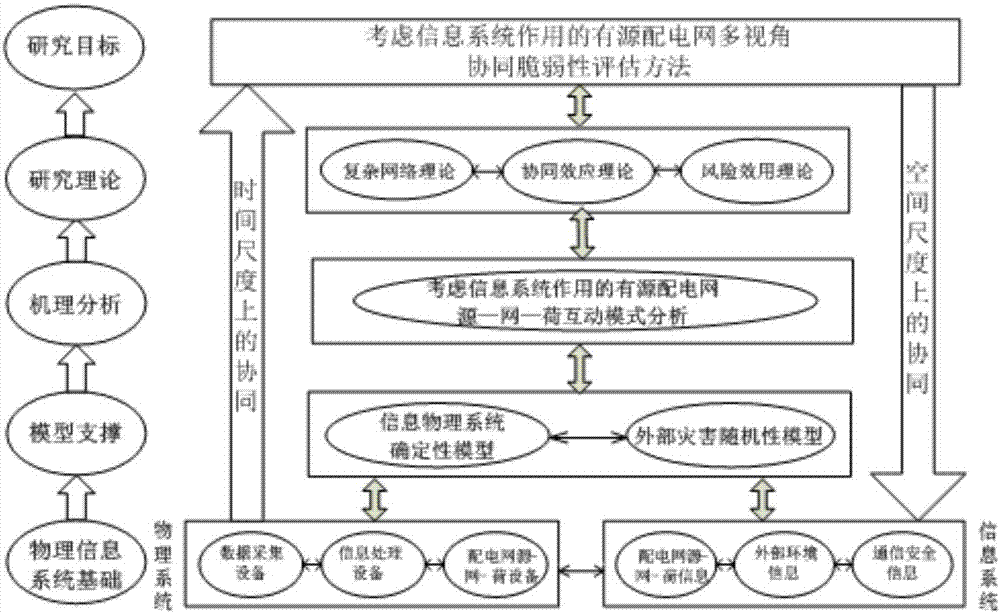
Active distribution network multi-view collaborative vulnerability assessment method considering effects of information system
ActiveCN107220775AComplies with operating conditionsAccurate predictionResourcesPhysical systemIndex system
The invention provides an active distribution network multi-view collaborative vulnerability assessment method considering effects of an information system, which comprises the steps of firstly building a definiteness-randomness topology structure model in allusion to the occurrence randomness of an external disaster of a distribution network; determining the multi-time-scale collaborative influencing information / physical component failure probability under a disaster condition based on system panoramic information; then building an active distribution network function group failure probability model considering effects of the information system; performing assessment on various operating states and grid structures of an active distribution network under a source network load interaction mode, building an active distribution network and information system integrated vulnerability assessment system under the source network load interaction mode, and assessing the collaborative vulnerability between the distribution network structure and the operating stage and between a physical system and the information system at the same time; and finally building a local collaborative vulnerability index system, a regional collaborative vulnerability index system and a global collaborative vulnerability index system on the space scale, and assessing the vulnerability of the active distribution network more comprehensively and more specifically.
Owner:NORTHEASTERN UNIV
Method for comprehensively evaluating regional abrupt environmental pollution accident risk
The invention discloses a method for comprehensively evaluating a regional abrupt environmental pollution accident risk. The method comprises the following steps: building a multilayer evaluation index system for the regional environmental pollution accident risk; building a risk source dangerousness quantitative model, a receptor sensitivity quantitative model and a restoring force quantitative model by using an objective weighting method, and acquiring risk source dangerousness indexes, receptor sensitivity indexes and restoring force indexes of different study units in a study region; building an environmental risk receptor vulnerability evaluation concept model and a regional abrupt environmental pollution accident comprehensive risk evaluation concept model, and calculating an environmental risk receptor vulnerability index and a regional environmental pollution accident comprehensive risk index according to the concept models, the risk source dangerousness indexes, the receptor sensitivity indexes and the restoring force indexes; and hierarchically clustering comprehensive environmental risk profiles of evaluation units. Through adoption of the method, a scientific theoretical foundation is laid for regional environmental risk comprehensive management, industrial distribution adjustment and optimization, accident emergency and the like. The method has the advantages of high efficiency, low cost, high accuracy and the like.
Owner:HENAN POLYTECHNIC UNIV
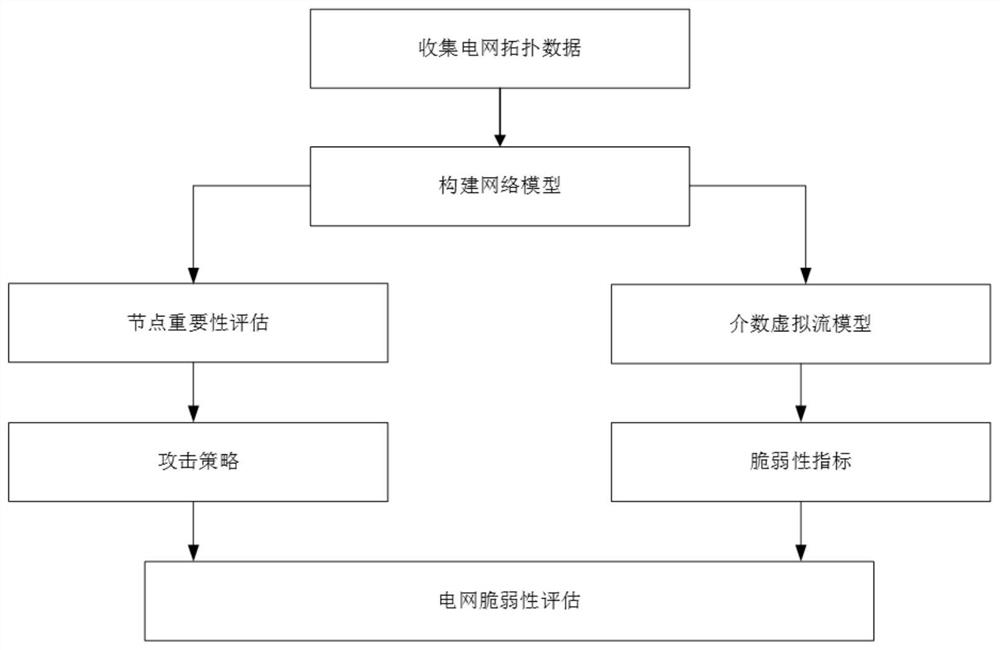
Power network vulnerability evaluation method based on multiple attack strategies
InactiveCN111950153AFacilitate identificationFeatures at the functional levelDesign optimisation/simulationResourcesElectric power systemAttack
The invention discloses a power system vulnerability evaluation method based on multiple attack strategies. The method comprises the following steps: 1) constructing a power grid model; 2) evaluatingthe importance of nodes in the network from four aspects of node degree, betweenness, local centrality and node fault loss, and completing the formulation of an attack strategy according to the importance of the network nodes; 3) establishing a betweenness virtual flow model to simulate a cascade fault propagation process in a power system; and 4) establishing a vulnerability index based on the betweenness virtual flow model, simulating a network attack by adopting a plurality of attack strategies, and evaluating the vulnerability of the IEEE300 power system network according to the change ofthe vulnerability index. Aiming at the vulnerability of the power network under the condition of various attack strategies, the betweenness virtual flow model and the various attack strategies are established to analyze the performance change of the power grid under the cascade failure. The importance of nodes in a power network can be identified, and decision support is provided for maintenance work of power system managers and power system fault prevention of designers.
Owner:XUZHOU NORMAL UNIVERSITY
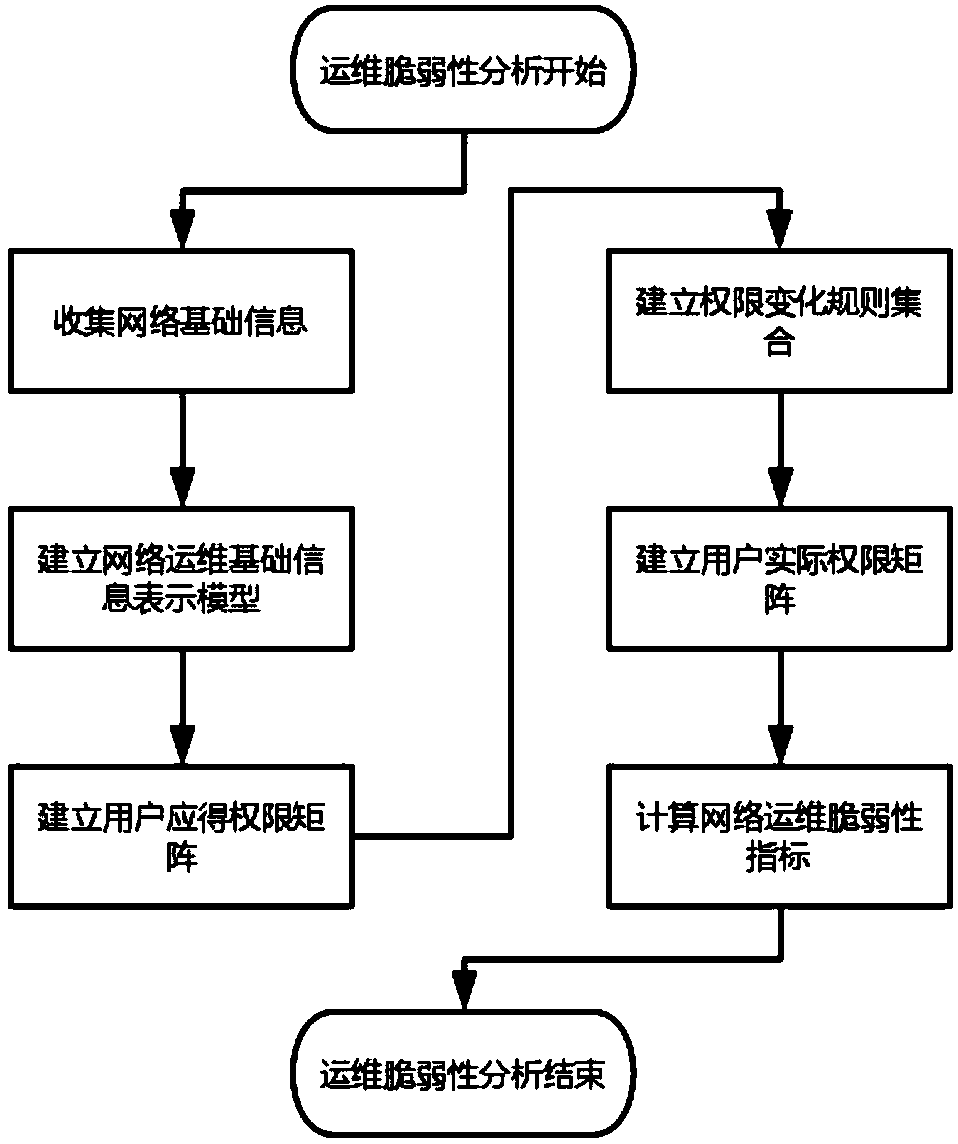
Network operation and maintenance vulnerability analysis method
ActiveCN109302310AUncover security gapsVulnerability analysis results are concrete and realData switching networksInformation representationAnalysis method
The invention discloses a network operation and maintenance vulnerability analysis method. The method comprises the following steps: step 1, collecting network basic information; step 2, establishinga network operation and maintenance basic information representation model; step 3, establishing a user deserved permission matrix; step 4, establishing a permission change rule set; step 5, establishing a user actual permission matrix; and step 6, calculating a network operation and maintenance vulnerability index. According to the network operation and maintenance vulnerability analysis method disclosed by the invention, the vulnerability additionally introduced to a network in a network operation and maintenance activity is focused on discovering a security gap between the specific implementation of the network and a network planning design; when the network operation and maintenance vulnerability is discovered, the information in the traditional network domain is not only used, and a large amount of semantic information in a physical domain and an information domain are also used, so that a vulnerability analysis result is more specific and true; and the difference between the actual permission and the deserved permission of each user in a target network is used as the measurement of the network vulnerability, and the impact of the current network operation and maintenance activity on the network vulnerability is focused on.
Owner:ARMY ENG UNIV OF PLA
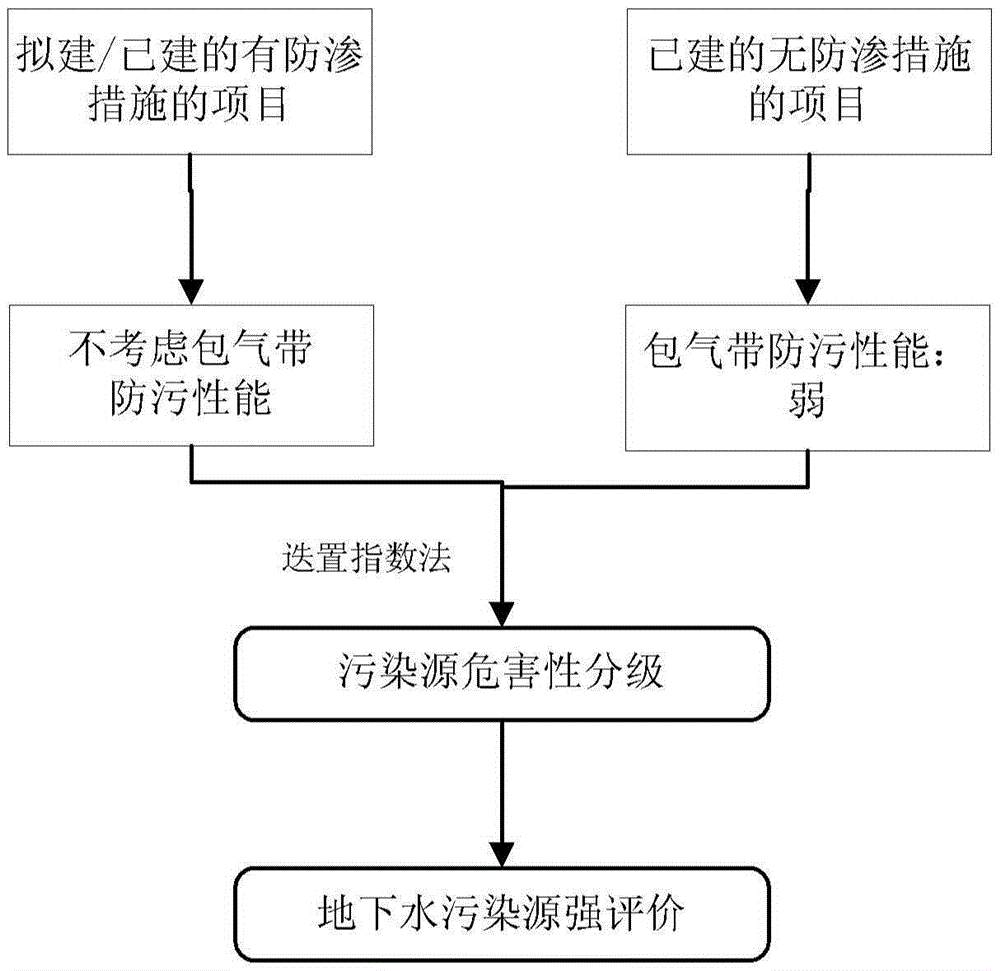
Groundwater pollution source strength evaluation method
InactiveCN105427013AScientific and reasonable protectionScientific and reasonable managementTechnology managementResourcesWater sourceVadose zone
Provided is a groundwater pollution source strength evaluation method. The method includes: determining the classified condition of an evaluation site with the combination of the hydrogeological condition around the site according to the construction condition of an industrial site and the implementation condition of seepage prevention measures; dividing the protection grade of vadose zones into three grades of "strong", "medium", and "weak" according to the classified condition of the industrial site, and the thickness and the permeability coefficient of the vadose zones; determining vulnerability indexes and scores of the vadose zones by employing a DRTAS model with the combination of characteristics of the vadose zones, and determining the resistance control classification of the vadose zones according to the protection grade and the vulnerability scores of the vadose zones; determining characteristic indexes of a pollution source and weights thereof by employing overlay and index methods with the combination of characteristics of the pollution source, thereby performing classification of harmfulness of the pollution source; and establishing a groundwater source strength classification evaluation method according to classification matrix coupling, and evaluating the groundwater pollution source strength of the industrial site. According to the method, the groundwater pollution source strength of the industrial site can be accurately evaluated, and scientific basis is provided for the protection and management of groundwater.
Owner:CHINESE RES ACAD OF ENVIRONMENTAL SCI
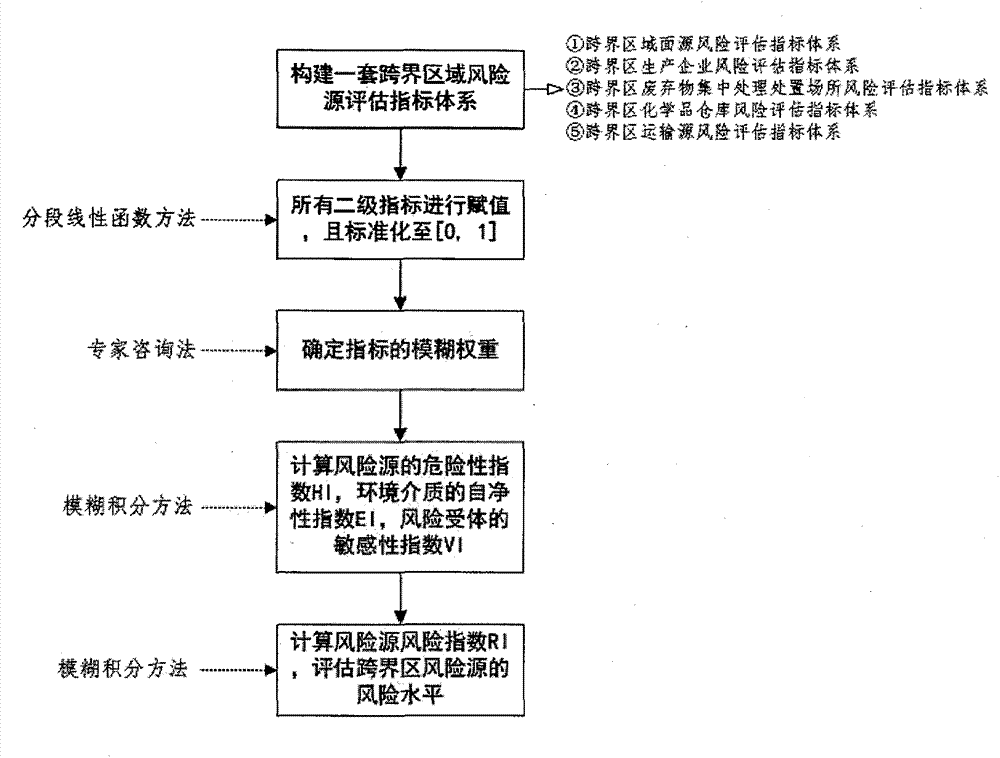
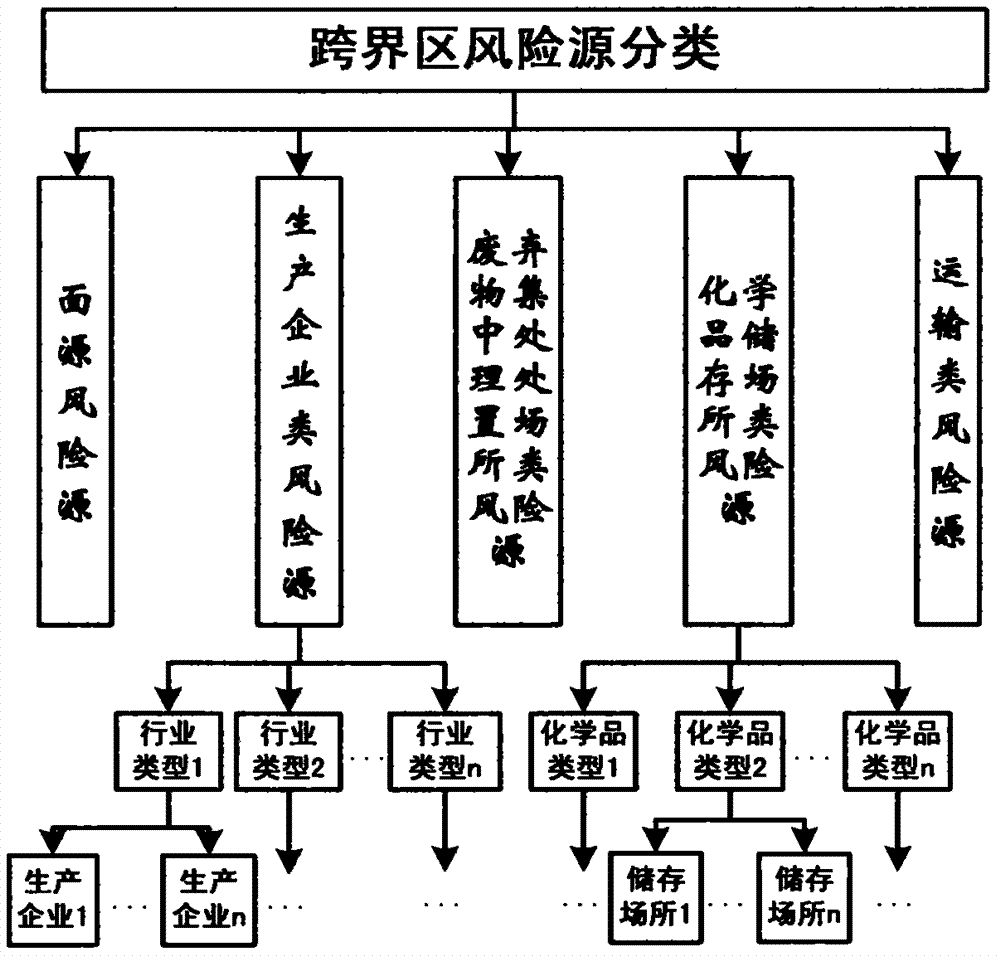
Water environmental risk source risk representing method in drainage basin transboundary region
The invention provides a water environmental risk source risk representing method in a drainage basin transboundary region. The method is used for evaluating the risk level of a risk source of the drainage basin transboundary region. The risk source of the transboundary region is divided into five categories including a surface source, production enterprises, a centralized treatment place of waste, a chemical storing site and transportation. The method includes the fives steps that first, a risk source risk index system of the transboundary region is constructed, the risk index systems of the five categories of risk sources respectively comprise three first-level indexes and a plurality of second-level indexes, the numbers of the second-level indexes in the risk index systems are different, and the indexes comprise three risk levels of the high risk level, the middle risk level and the low risk level; an information database of the risk sources of the transboundary region is established, values are assigned to all the second-level indexes, and the values of the all the second-level indexes are standardized to [0,1]; then, fuzzy weights of the indexes are determined; next, a fuzzy integration method is adopted for respectively calculating the risk indexes of the risk sources, the self-purification index of environmental mediums, and the vulnerability index of risk receiving bodies; finally, the risk indexes of the risk sources are calculated through the fuzzy integration method so that the risk levels of the risk sources can be represented.
Owner:NANJING UNIV
A Vulnerability Assessment Method for Regional Environmental Risk Receptors
InactiveCN102270325AComprehensive evaluationEvaluation is scientific and comprehensiveInstrumentsFragilityEnvironment of Albania
Owner:BEIJING NORMAL UNIVERSITY
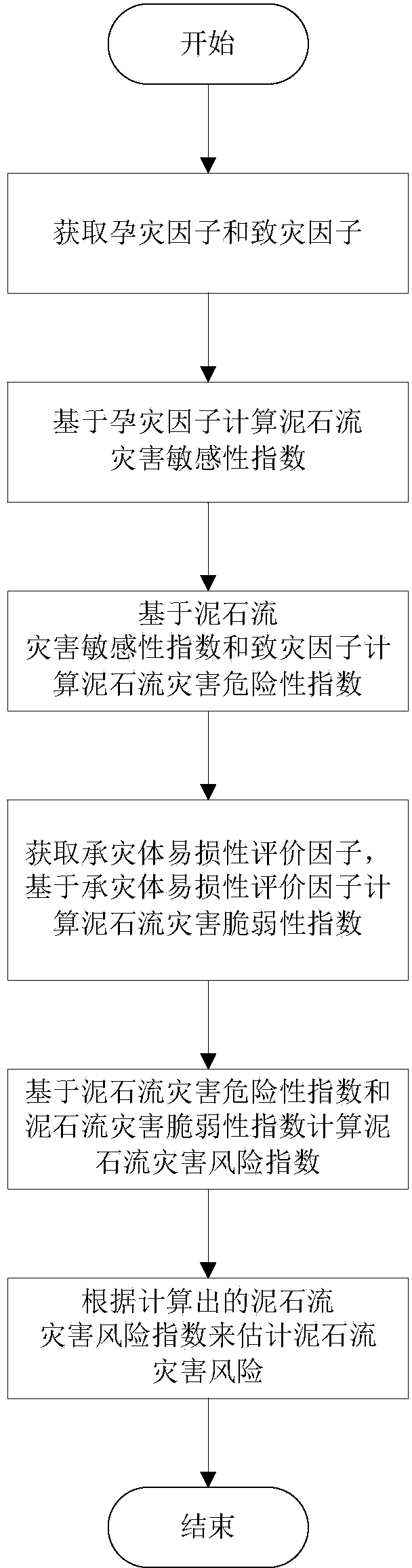
Area debris flow disaster risk estimation method
The invention discloses an area debris flow disaster risk estimation method. The method includes the following steps that at least one disaster pregnancy factor and at least one disaster causing factor for at least one debris flow disaster point in an interesting area are obtained from different data sources; a debris flow disaster sensibility index is calculated based on the disaster pregnancy factor; a debris flow disaster dangerousness index is calculated based on the debris flow disaster sensibility index and the disaster causing factor; at least one disaster bearing body vulnerability assessment factor is obtained, and a debris flow disaster vulnerability index is calculated based on the disaster bearing body vulnerability assessment factor; a debris flow disaster risk index is calculated based on the debris flow disaster dangerousness index and the debris flow disaster vulnerability index; debris flow disaster risks are estimated according to the calculated debris flow disaster risk index.
Owner:MIN OF CIVIL AFFAIRS NAT DISASTER REDUCTION CENT
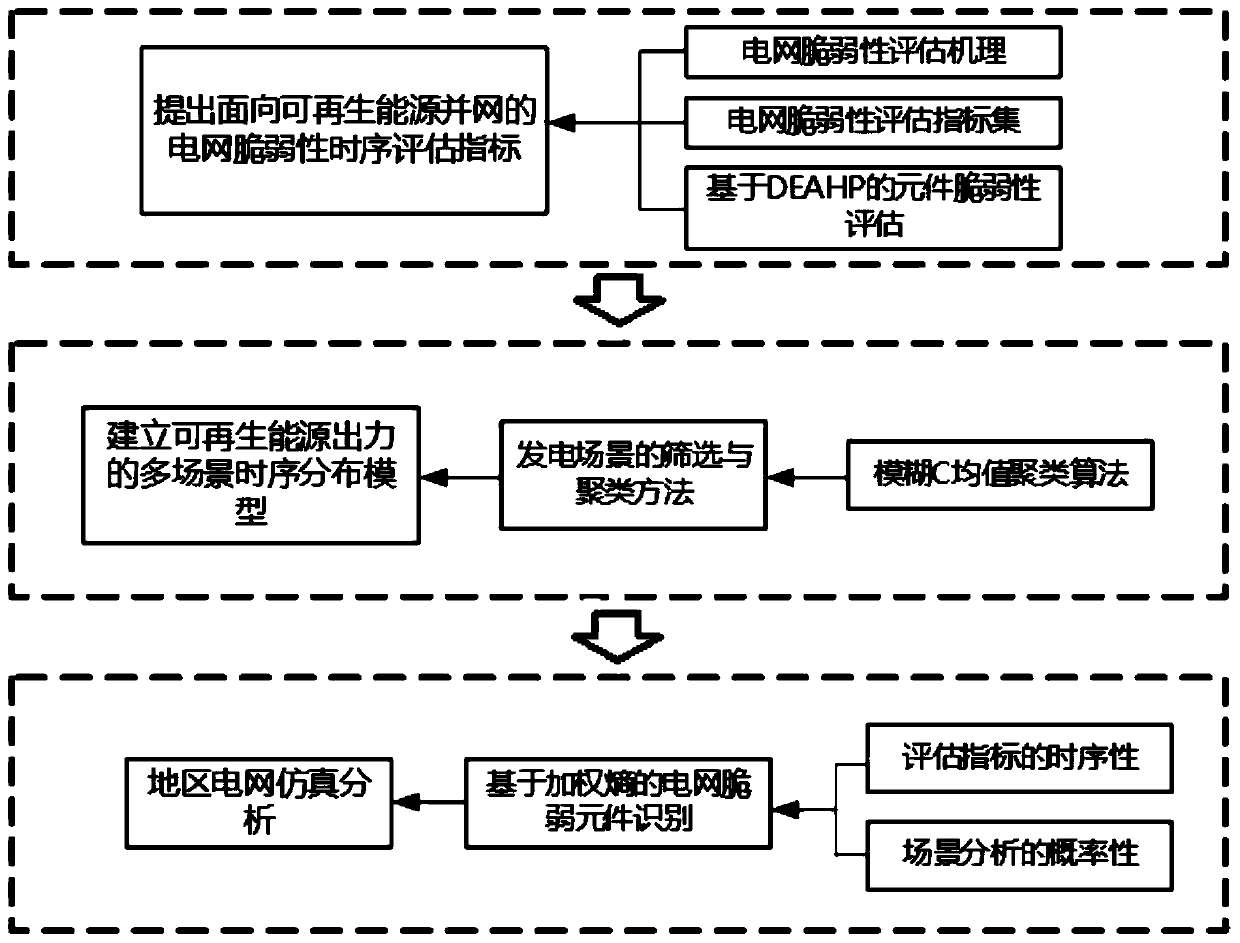
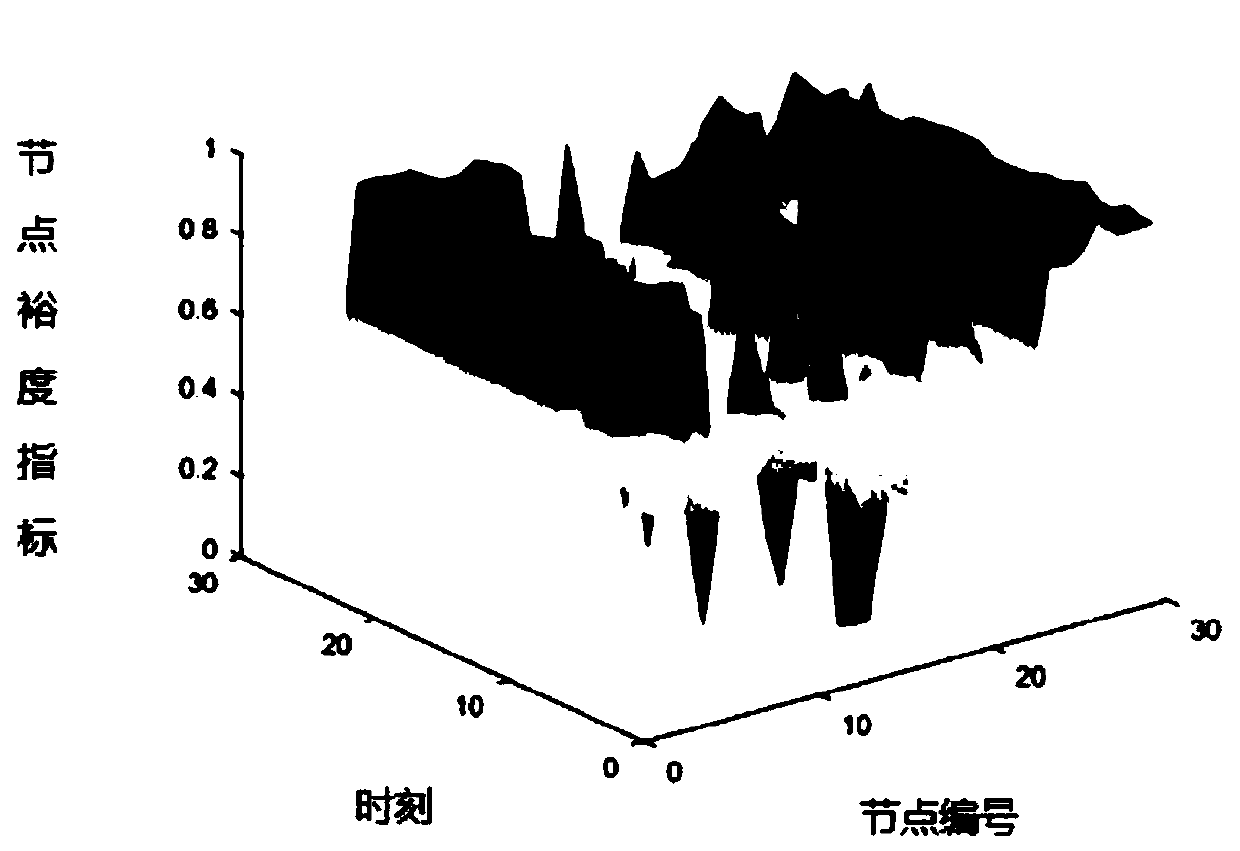
Power grid vulnerability evaluation method under high-proportion renewable energy source access
ActiveCN110705879AAchieve classification reductionIn line with the actual operationCharacter and pattern recognitionTechnology managementCluster algorithmEvaluation result
The invention discloses a power grid vulnerability evaluation method under high-proportion renewable energy access, and the method comprises the steps: carrying out the clustering of high-proportion renewable energy output data of a target region power grid through employing a fuzzy C-means clustering algorithm through employing a multi-scene technology, and obtaining a multi-scene time sequence distribution model of high-proportion renewable energy output; evaluating element vulnerability by using a DEAHP-based vulnerability index system in each typical scene to obtain a vulnerability time sequence evaluation index changing along with renewable energy output change, so that the fluctuation degree and the real-time operation condition of node vulnerability characteristics are reflected. The idea of weighted entropy is introduced, and the static evaluation model of each time section is linearly weighted and aggregated by using a time sequence weighting vector so as to comprehensively consider the fluctuation characteristics and the equilibrium degree of node vulnerability under all typical time sequence scenes. The combination of typical scene probabilistic and vulnerability evaluation time sequence is realized, and the vulnerability of each node in the network is evaluated statically, dynamically and comprehensively, so that the evaluation result better conforms to the actual operation of the power grid.
Owner:BINZHOU POWER SUPPLY COMPANY OF STATE GRID SHANDONG ELECTRIC POWER
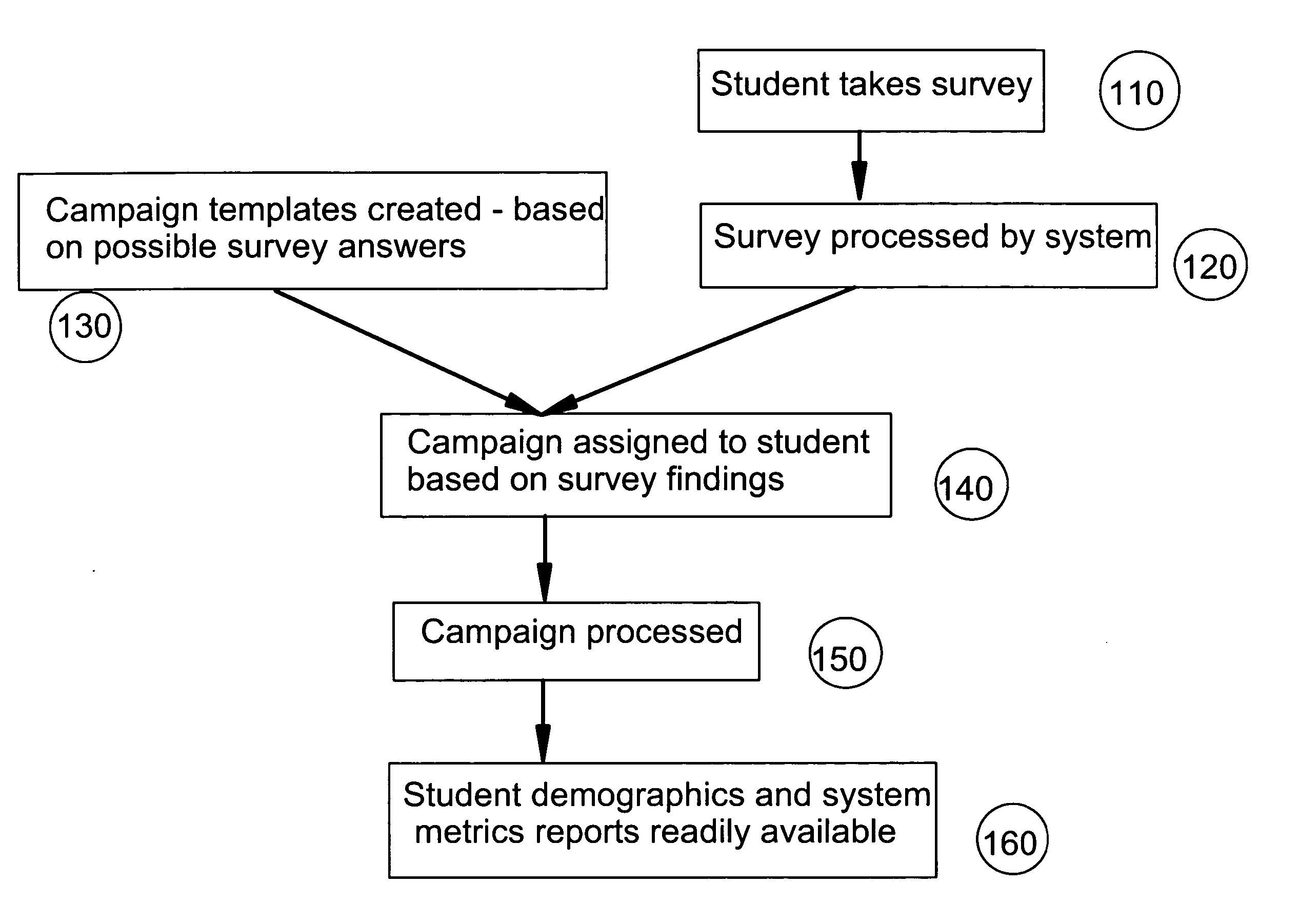
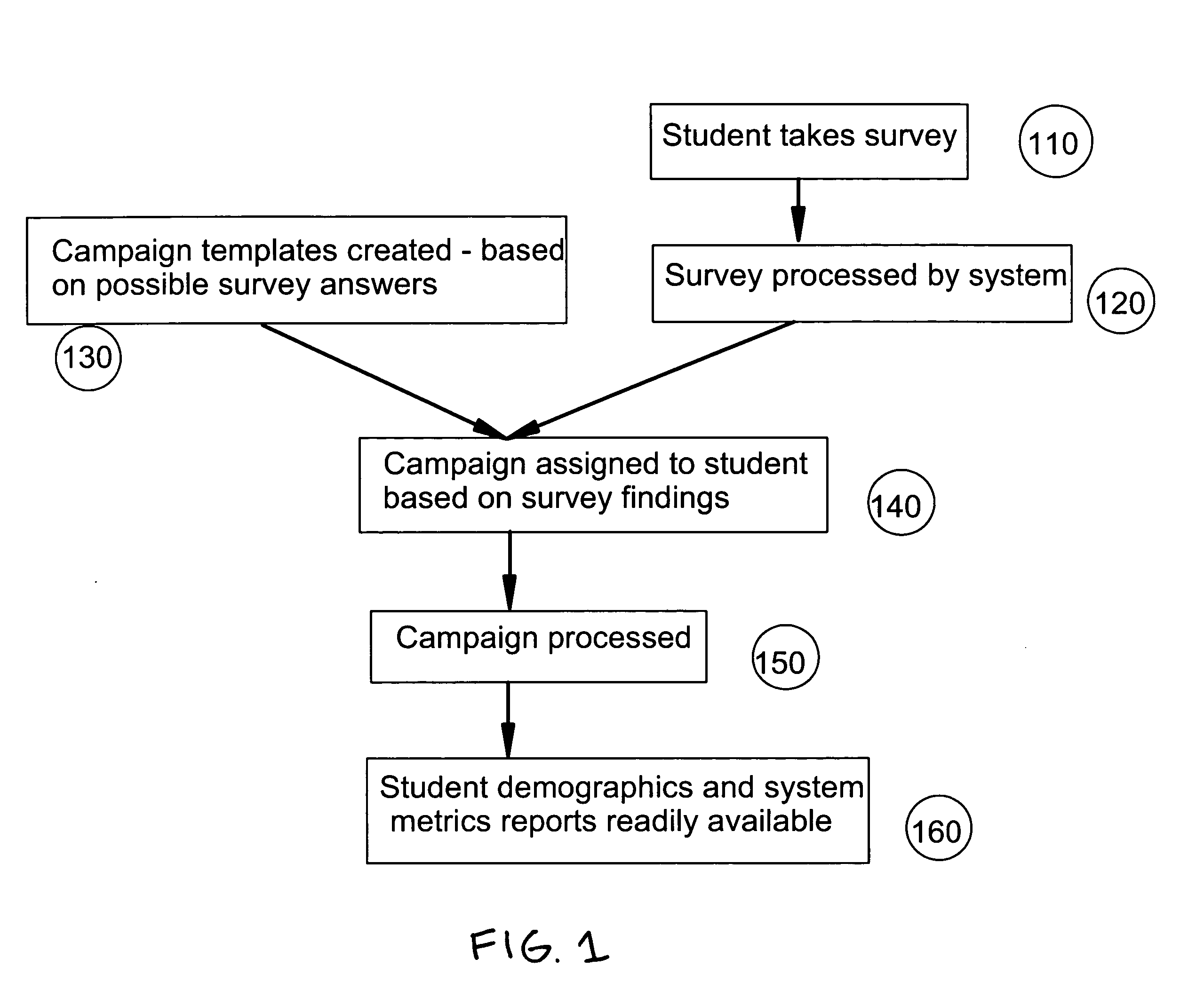
Individualized retention plans for students
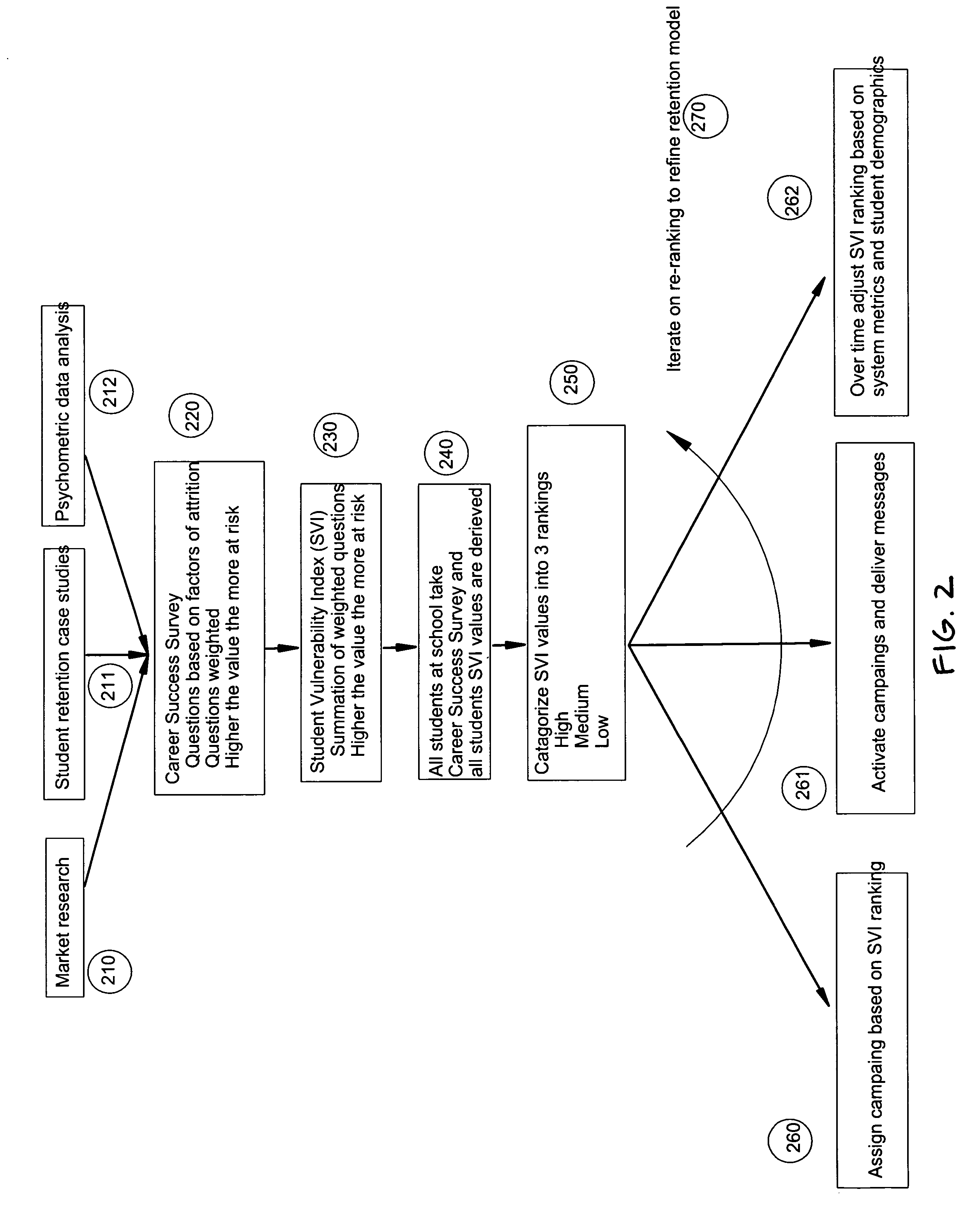
Developing and executing individualized retention plans for students. A career success survey is provided to a student, and the survey includes queries used to derive a student vulnerability index. A completed version of the career success survey with answers to the queries is received from the student, and an communication plan is assigned to the student based the completed career success survey (student vulnerability index). The dynamically assigned communication plan delivers messages to the student at periodic times in an effort to increase the likelihood of retaining the student or otherwise attempt to prevent the student from dropping out of an educational institution. The messages can include e-mail, mail, and telephone messages, and they can be sent at particular times during the student's enrollment at the educational institution. The content of the messages are personalized to the student based upon a number of criteria such as age, major, gender, identified needs, student vulnerability index, or any other criteria gathered by the system from the career success survey. The system also provides the basis of a student retention methodology for school administrators, faculty and staff by providing an environment for all concerted to better understand who the at risk students are, how to best help the at risk students, and a reporting system indicating improvement in student retention.
Owner:ECOLLEGE COM
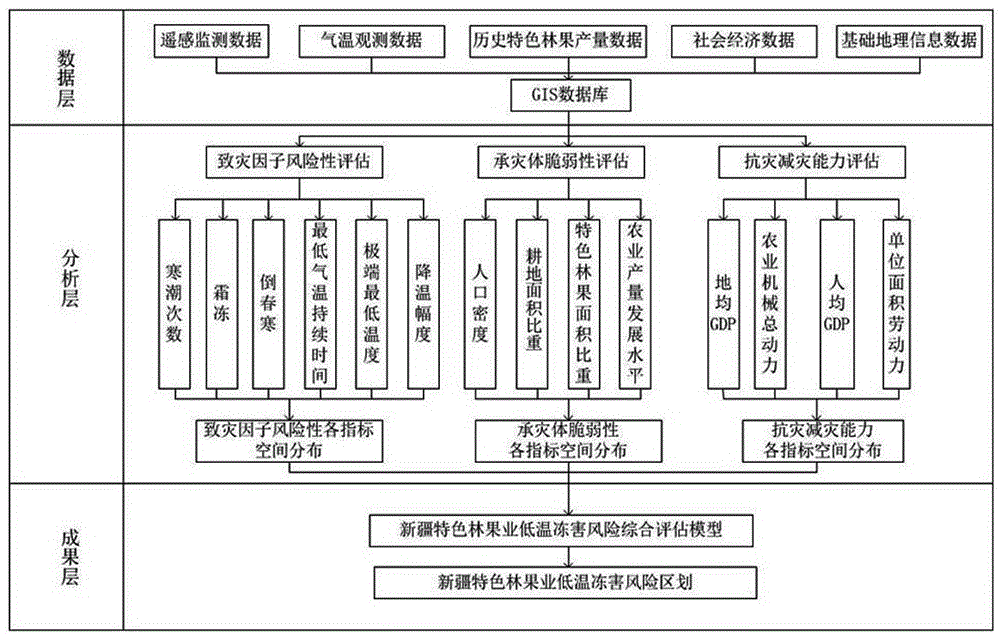
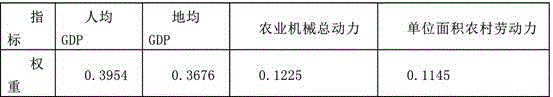
Fruit industry low temperature frost damage risk acquiring method
The invention discloses a fruit industry low temperature frost damage risk acquiring method. The method mainly comprises the steps that a data collector acquires the temperature data and the geographic information data of a specific forest fruit planting area, and sends the data to the receiving platform of each place through a wireless data transmission module for storing; the receiving platform of each place sends the received data to the GIS server of a data application central apparatus room; a server GIS database carries out processing to acquire disaster-inducing factor risk index data, hazard-affected body vulnerability index data and disaster resistance and alleviation index data; according to the spatial distribution data of the disaster-inducing factor risk index data, the spatial distribution data of the hazard-affected body vulnerability index data and the spatial distribution data of the disaster resistance and alleviation ability index data, a low temperature frost damage comprehensive risk assessment model is established; and fruit industry low temperature frost damage risk division is carried out. The defects of unreasonable design, incomprehensive comprehensive consideration factor and inaccurate risk early warning of the fruit industry low temperature frost damage risk acquiring method in the prior art are overcome.
Owner:新疆林科院园林绿化研究所
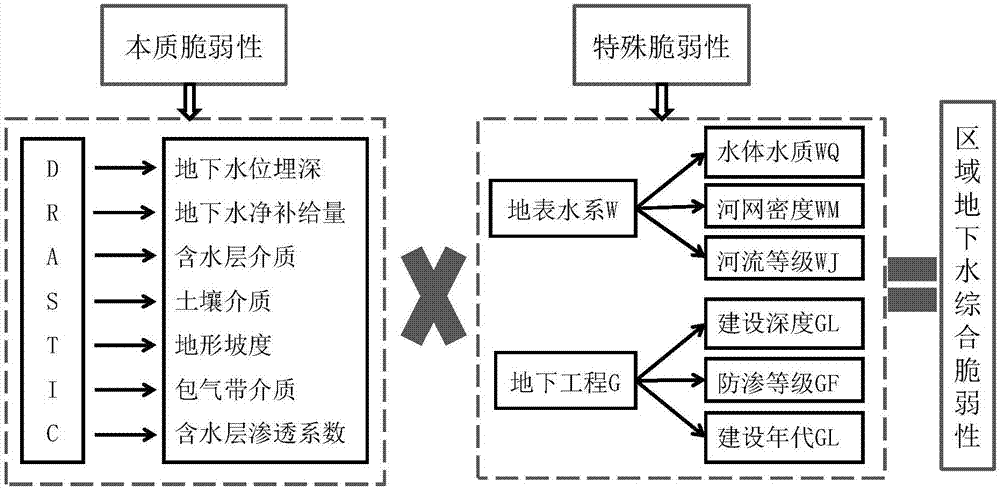
Method for optimizing groundwater special vulnerability evaluation model
The present invention provides a method for optimizing a groundwater special vulnerability evaluation model. According to the technical scheme of the invention, the evaluation model is optimized respectively in four aspects, namely the establishment of an index system, the assignment of index grades, the determination of weights, and the grading method selection of vulnerability indexes. Therefore, the subjectivity of the evaluation model based on the overlay and index method is effectively reduced. The method comprises the steps of determining groundwater special vulnerability influence factors; selecting typical indexes out of the influence factors to establish an index system; according to the characteristic value of each index in a research area, dividing the grade of each index and assigning a value to each grade; determining the weight of each index through studying the specific pollutant concentration at a sampling point in the research area and the correlation degree among the values of all indexes; constructing a groundwater special vulnerability evaluation model, and forming groundwater special vulnerability sub-areas through different grading methods respectively; and determining an optimal groundwater special vulnerability map through the contrastive analysis of the grade difference method. The method is applicable to the field of groundwater pollution prevention and control management.
Owner:CHINESE RES ACAD OF ENVIRONMENTAL SCI
Method and system for assessing underground water vulnerability and pollution risks in plain river network area
The invention provides a method and system for assessing underground water vulnerability and pollution risks in a plain river network area. The system comprises an index data input module, a grading module, an underground water pollution risk computation module and a display module, wherein the index data input module is used to input various types of index data; the grading module is used to pre-store grading data of underground water pollution risk grades, grading data of pollution source loads, and grading data of underground water environment essential vulnerability indexes; the underground water pollution risk computation module is used to compute an underground water pollution risk prevention and control value according to the various types of index data and compute a risk grade of the area corresponding to the underground water pollution risk prevention and control value in combination with the grading data of the underground water pollution risk grades in the grading module; and the display module is used to edit computation results of the underground water pollution risk computation module into pictures for display in combination with GIS data. The system is characterized in that the new vulnerability computation method is used; direct display is achieved effectively in combination with GIS information; and practicability is greatly enhanced.
Owner:SHANGHAI ACADEMY OF ENVIRONMENTAL SCIENCES
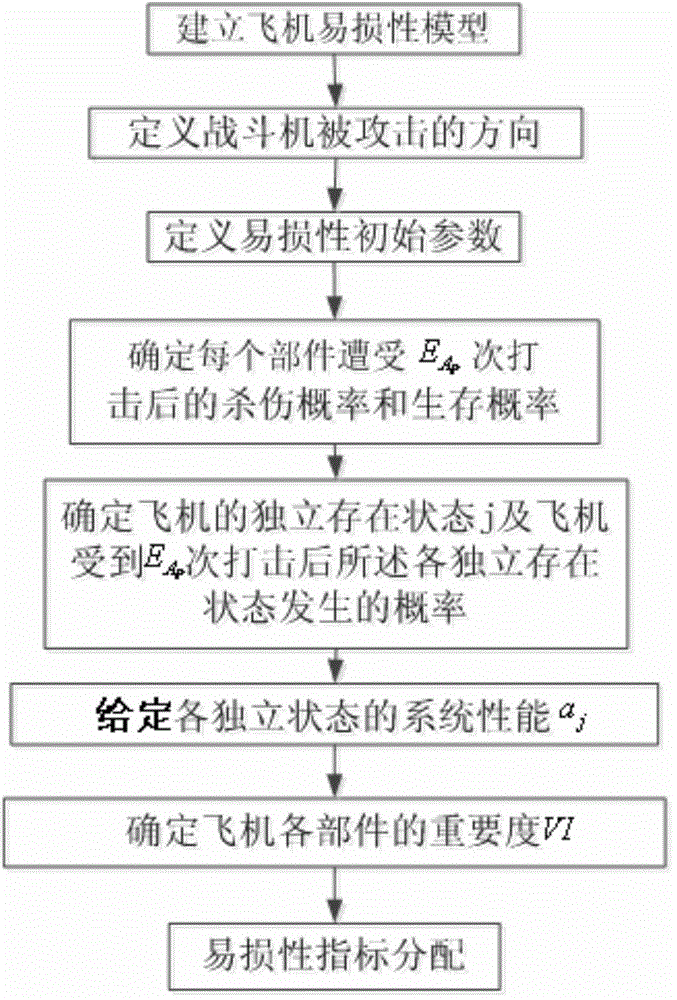
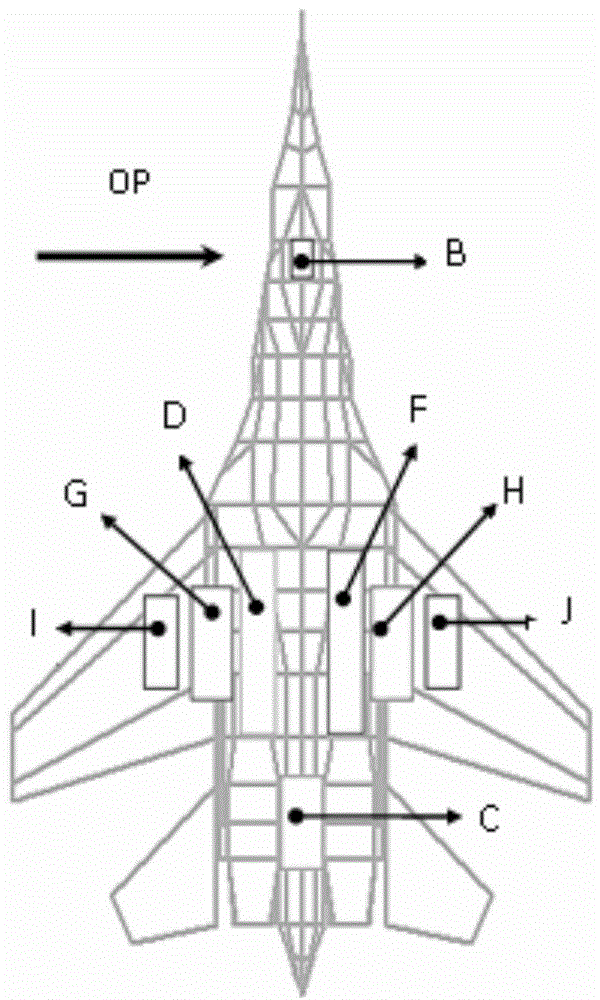
Method for distributing vulnerability index of combat aircraft system
ActiveCN104820778AImprove survivabilityReduce vulnerabilitySpecial data processing applicationsSurvivabilitySurvival probability
A method for distributing a vulnerability index of a combat aircraft system, comprising the steps as follows: determining a vulnerability initial parameter under a condition that menace and attack are determined through establishing a certain type fighter vulnerability model, then determining the times of the attack suffered by an aircraft, and the killing probability and the survival probability of each attacked component, determining the self-existent state of the aircraft and attacked probability of each state, substituting the obtained data into computational formulas of a comprehensive importance degree and a Griffith importance degree to obtain the comprehensive importance degree and the Griffith importance degree computational of each component, finally distributing the vulnerability of the whole aircraft by using a vulnerability index distribution method to obtain the vulnerability of each component. The method of the invention can be used for reducing the vulnerability of the component with large vulnerability after obtaining the vulnerability distributed to each component to reduce the vulnerability, thereby increasing the aircraft survivability.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com