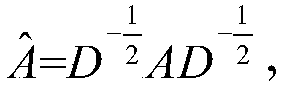Patents
Literature
265 results about "Hide node" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
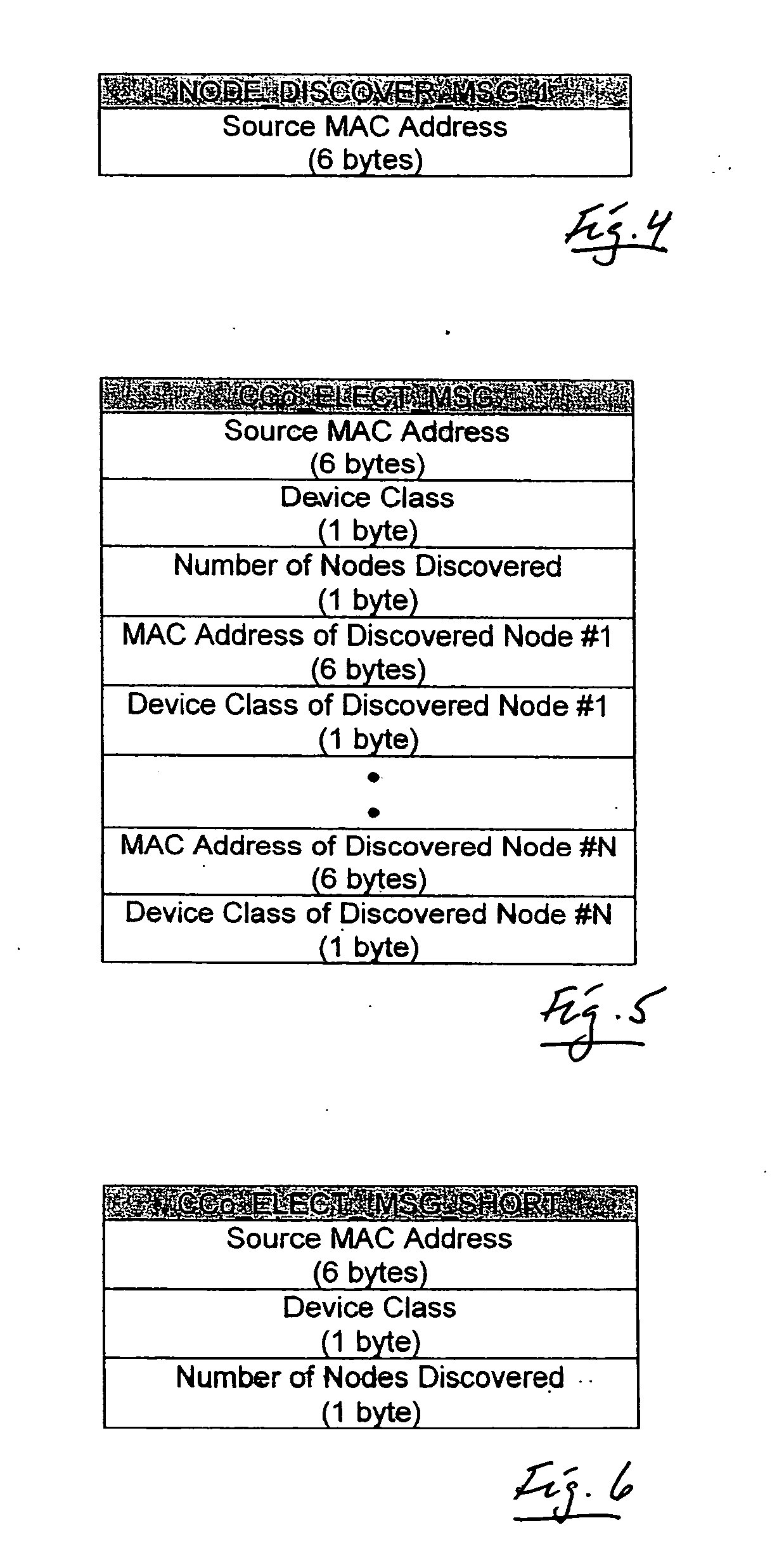
Method and system for setting routing path considering hidden node and carrier sense interference, and recording medium thereof
ActiveUS8300538B2Improve routing performanceImprove network performanceError preventionFrequency-division multiplex detailsHidden node problemCarrier signal
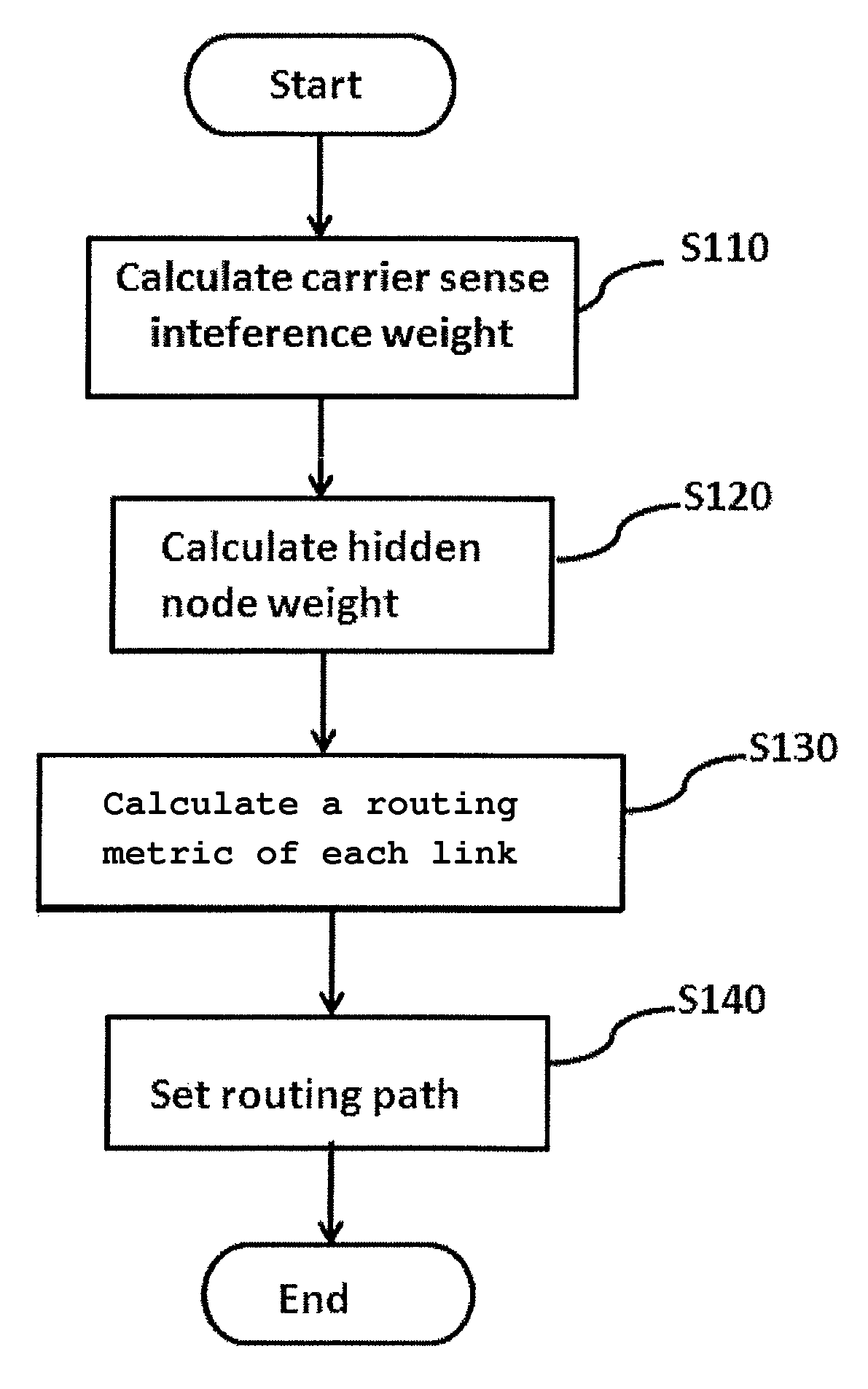
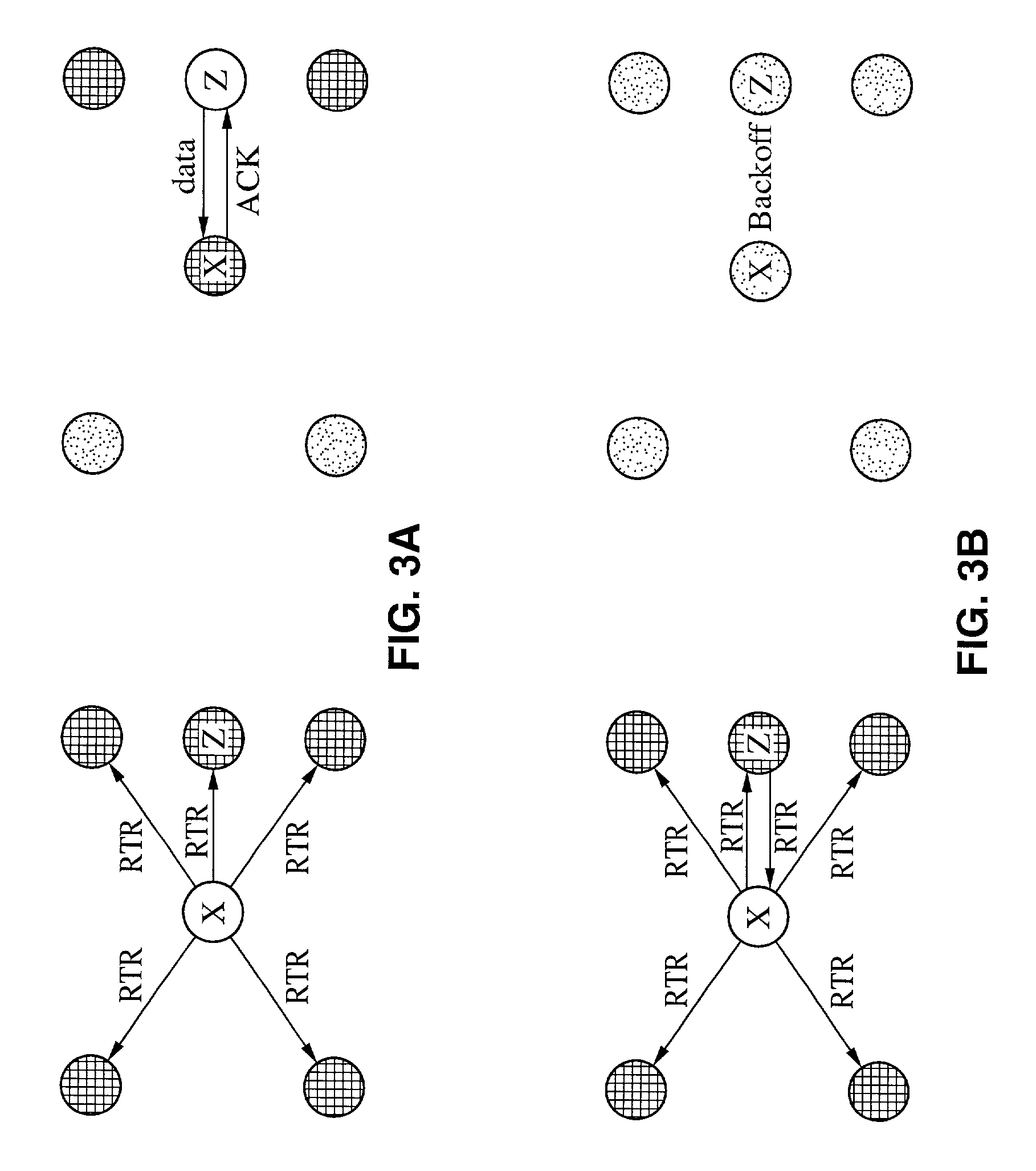
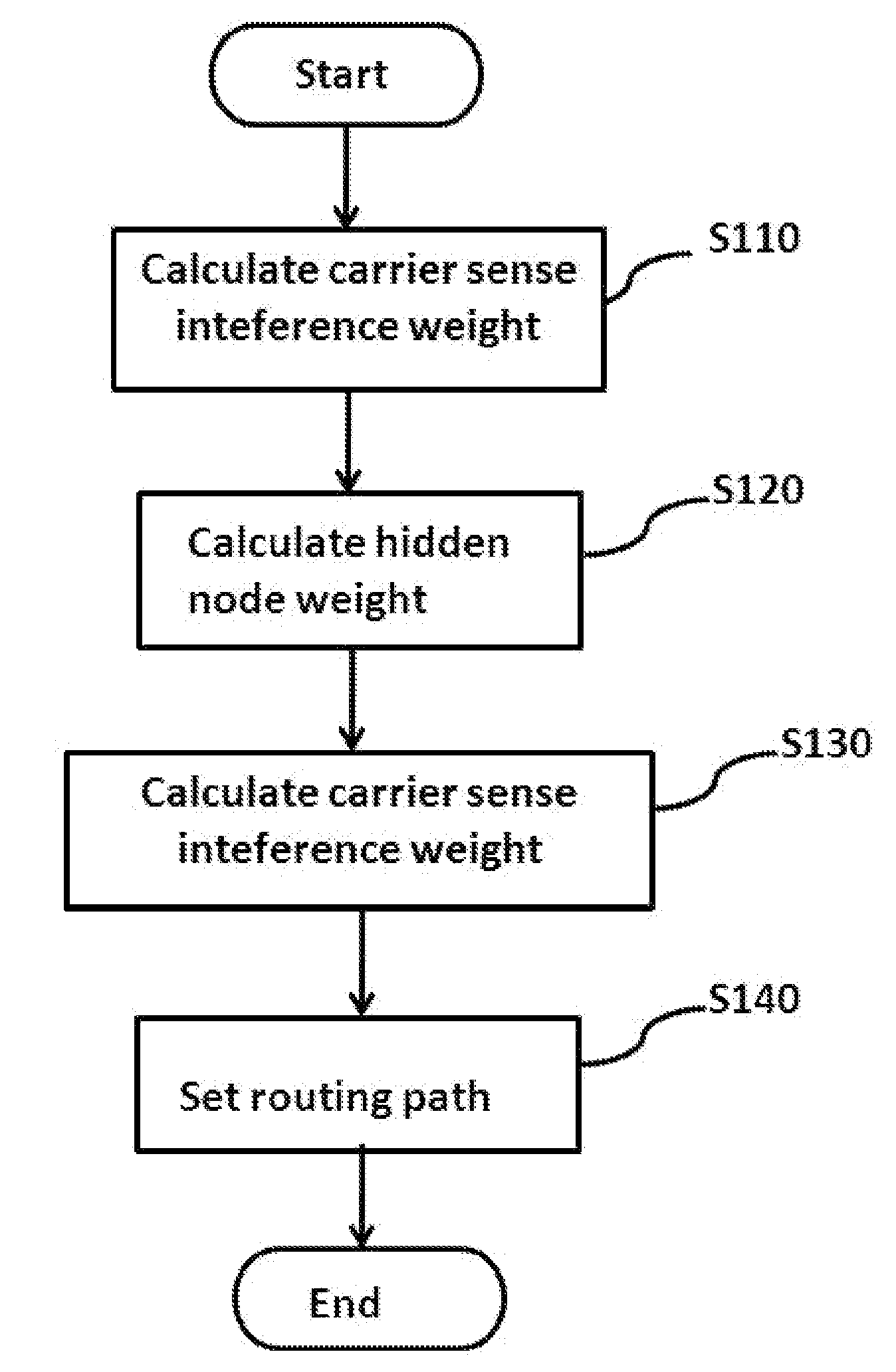
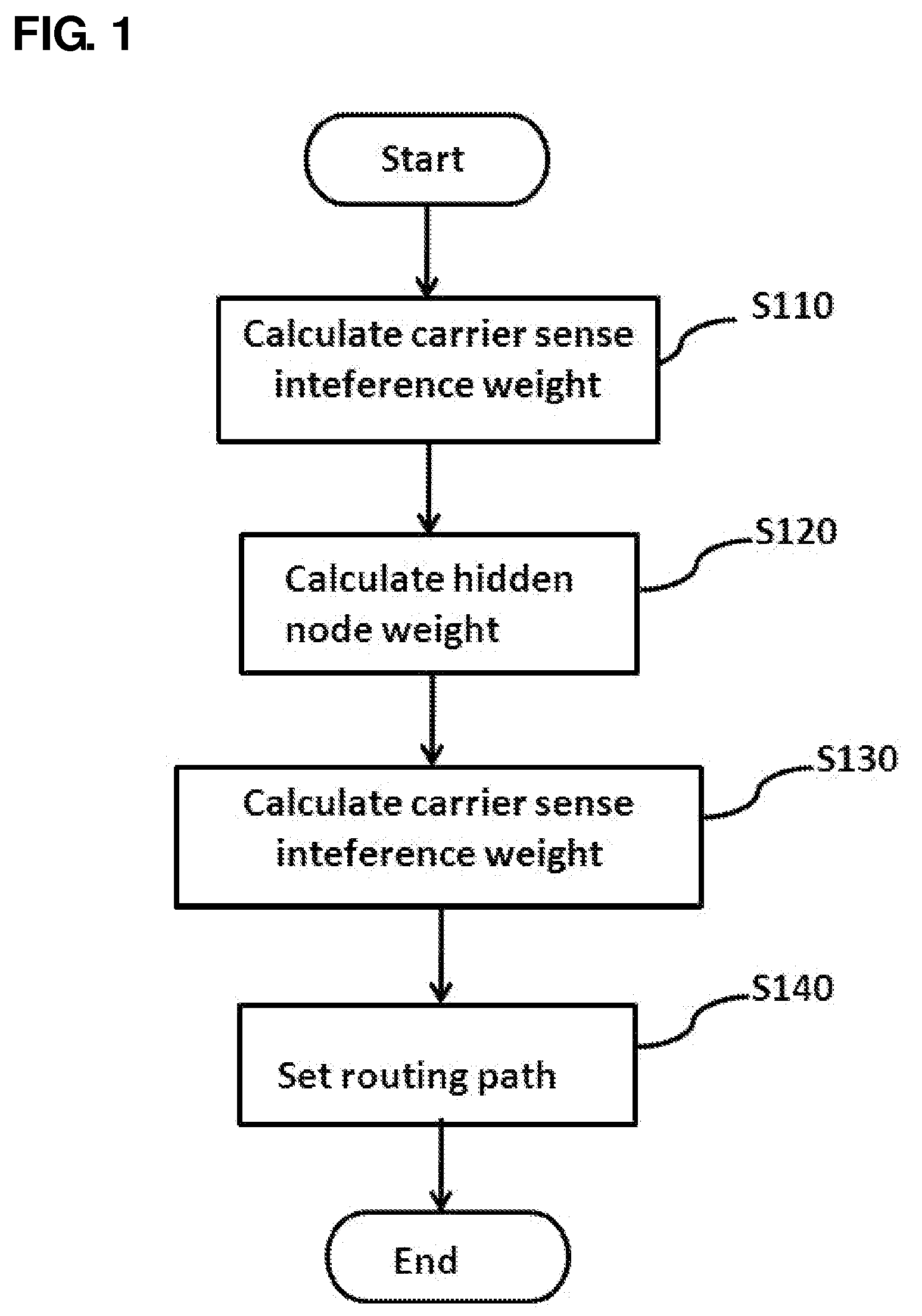
A method of setting a routing path for transmitting a packet from a source node to a destination node in a wireless multi-hop network including plural nodes and plural links for connecting two nodes with each other. The method includes calculating carrier sense interference weights representing carrier sense interference related to the respective links and combining the carrier sense interference weights of the links included in at least one specific path connecting the source node with the destination node. The method further includes calculating hidden node weights representing hidden node problems related to the respective links and accumulating the hidden node weights of the links included in the path. The method further includes calculating a metric value for the specific path by combining the carrier sense interference weights and the hidden node weights, and determining the specific path with the least metric value as the routing path.
Owner:KOREA ADVANCED INST OF SCI & TECH
Distributed network organization and topology discovery in ad-hoc network
InactiveUS20050174950A1Reduce collisionImprove throughputData switching by path configurationNetwork topologyDistributed computing
A distributed network method for self-organizing a group of nodes into a bi-directional communication network where initially there is no central coordinator in the prospective network environment. The method involves engaging in the process of determining internodal communication capabilities en route to creating a network topology table, and then using that table as a guide (a) selecting, by nodal election, an appropriate central coordinator, and (b) establishing proxy nodes which enable full network bi-directional communication between all nodes, including otherwise communicatively-compromised hidden nodes.
Owner:SHARP LAB OF AMERICA INC
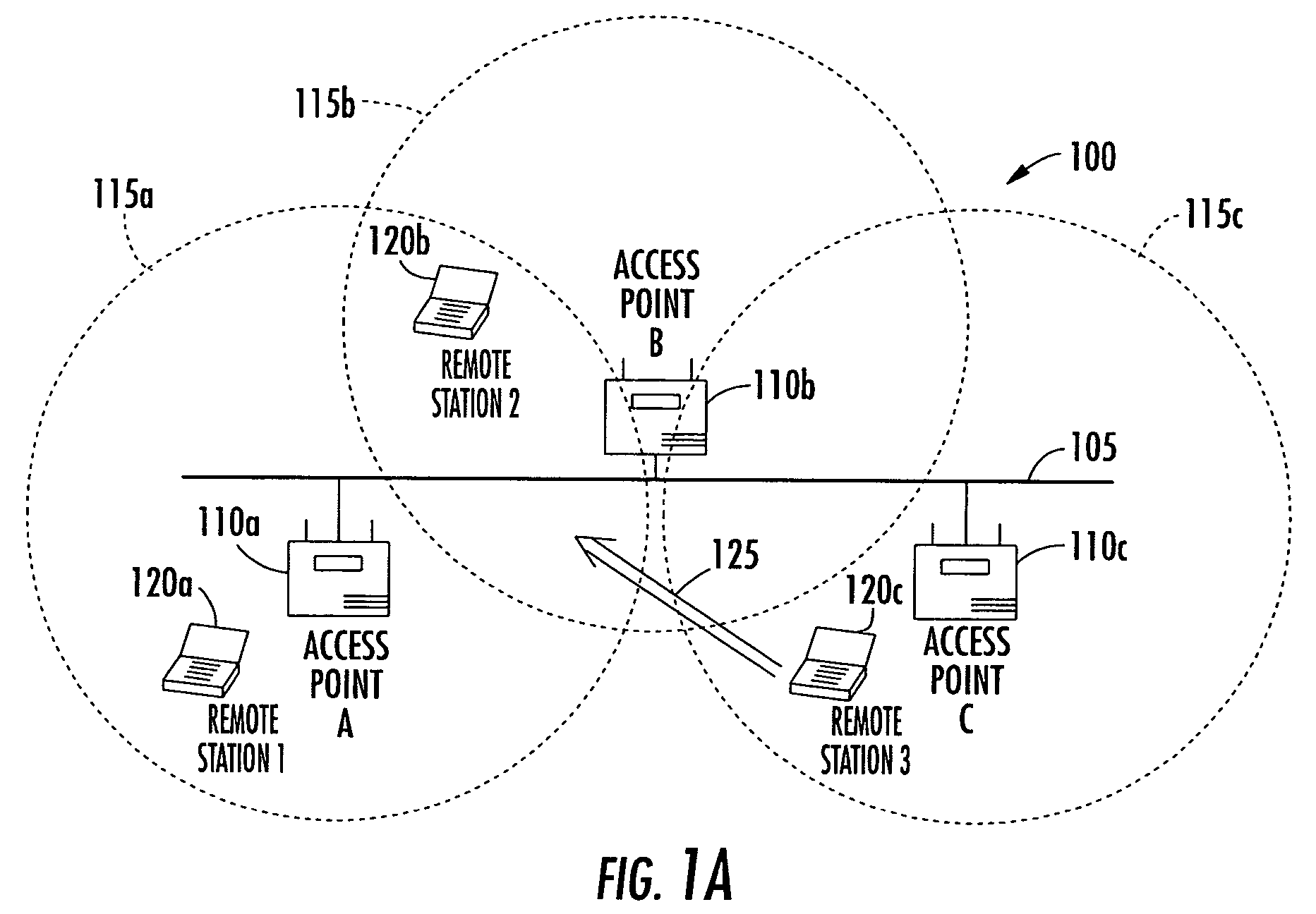
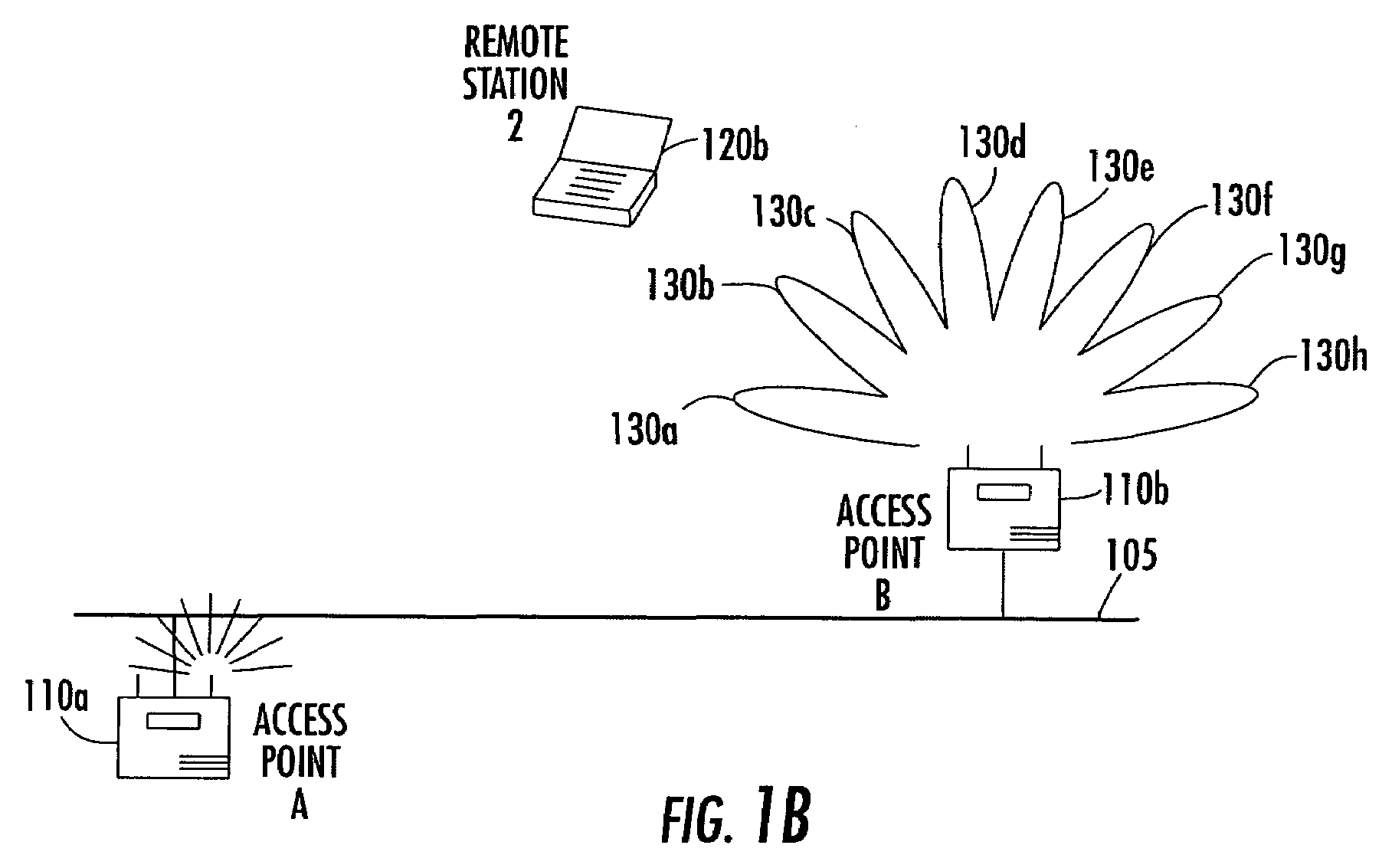
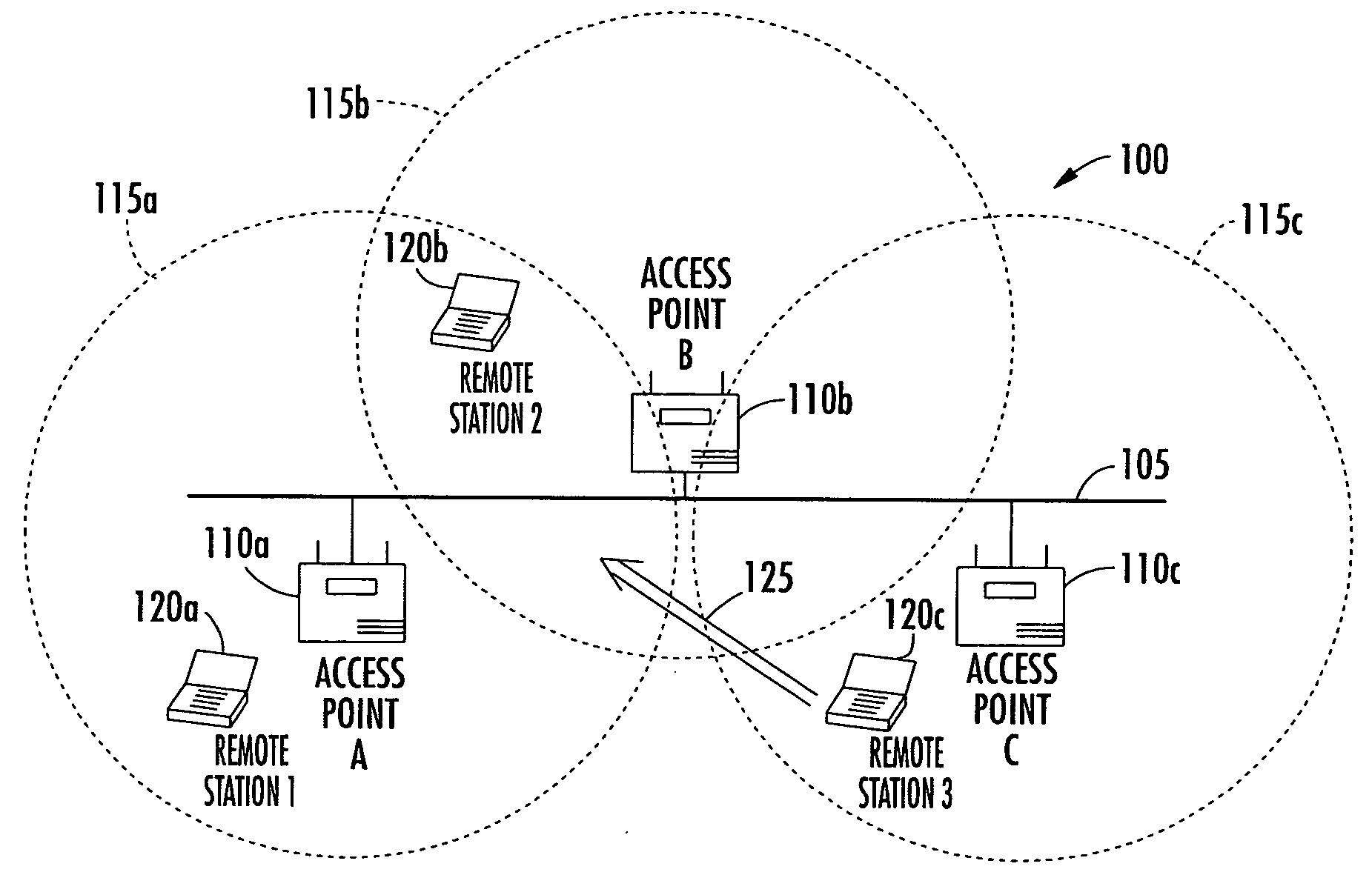
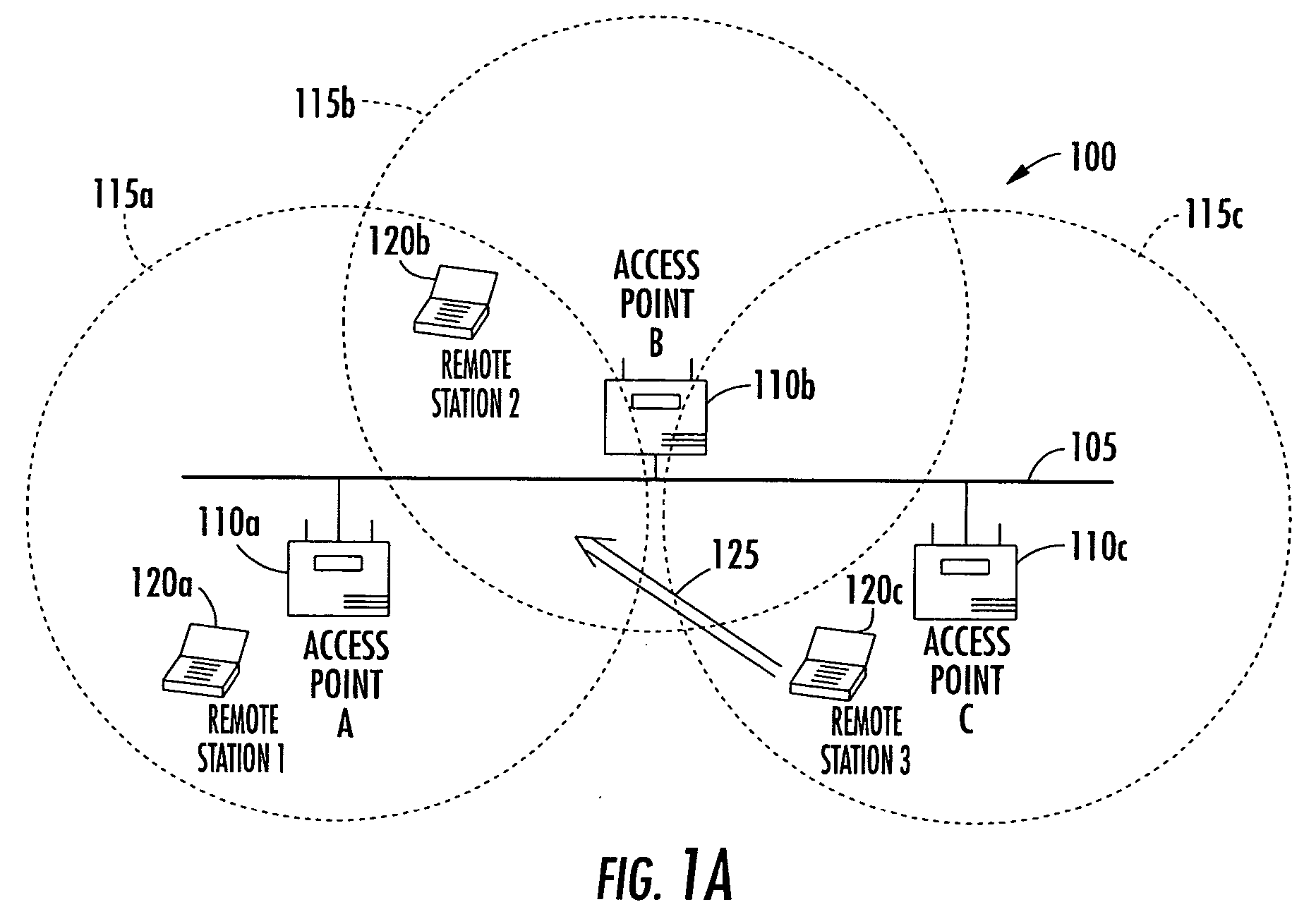
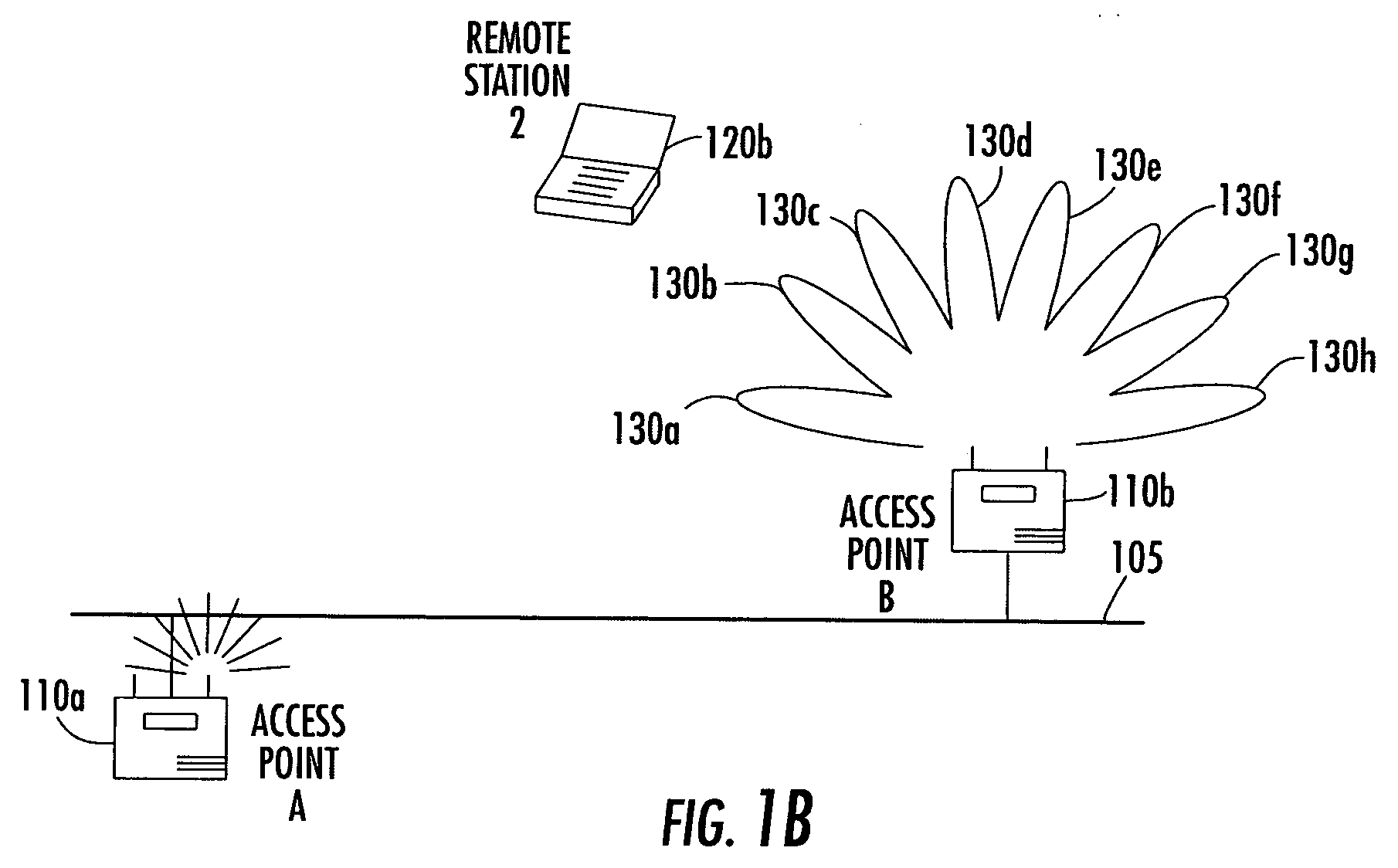
Antenna steering and hidden node recognition for an access point
InactiveUS7103386B2Facilitate communicationImprove throughputSpatial transmit diversitySubstation equipmentSignal qualityTelecommunications
A method for operating an access point in a wireless local area network (WLAN) is provided. The access point includes a directional antenna for communicating with a plurality of remote stations, and the directional antenna includes a plurality of antenna patterns. The method includes creating an antenna database by associating between the access point and each remote station a respective measured signal quality corresponding to the plurality of antenna patterns. The respective measured signal qualities are determined by the access point based upon communications with each remote station. The method further includes determining for each remote station a preferred antenna pattern based upon the antenna database, and selecting a remote station and the corresponding preferred antenna pattern to communicate with. It is also determined based upon the antenna database and prior to communicating with the selected remote station, if any non-selected remote stations have the potential of not being aware when such communications actually occurs.
Owner:IPR LICENSING INC
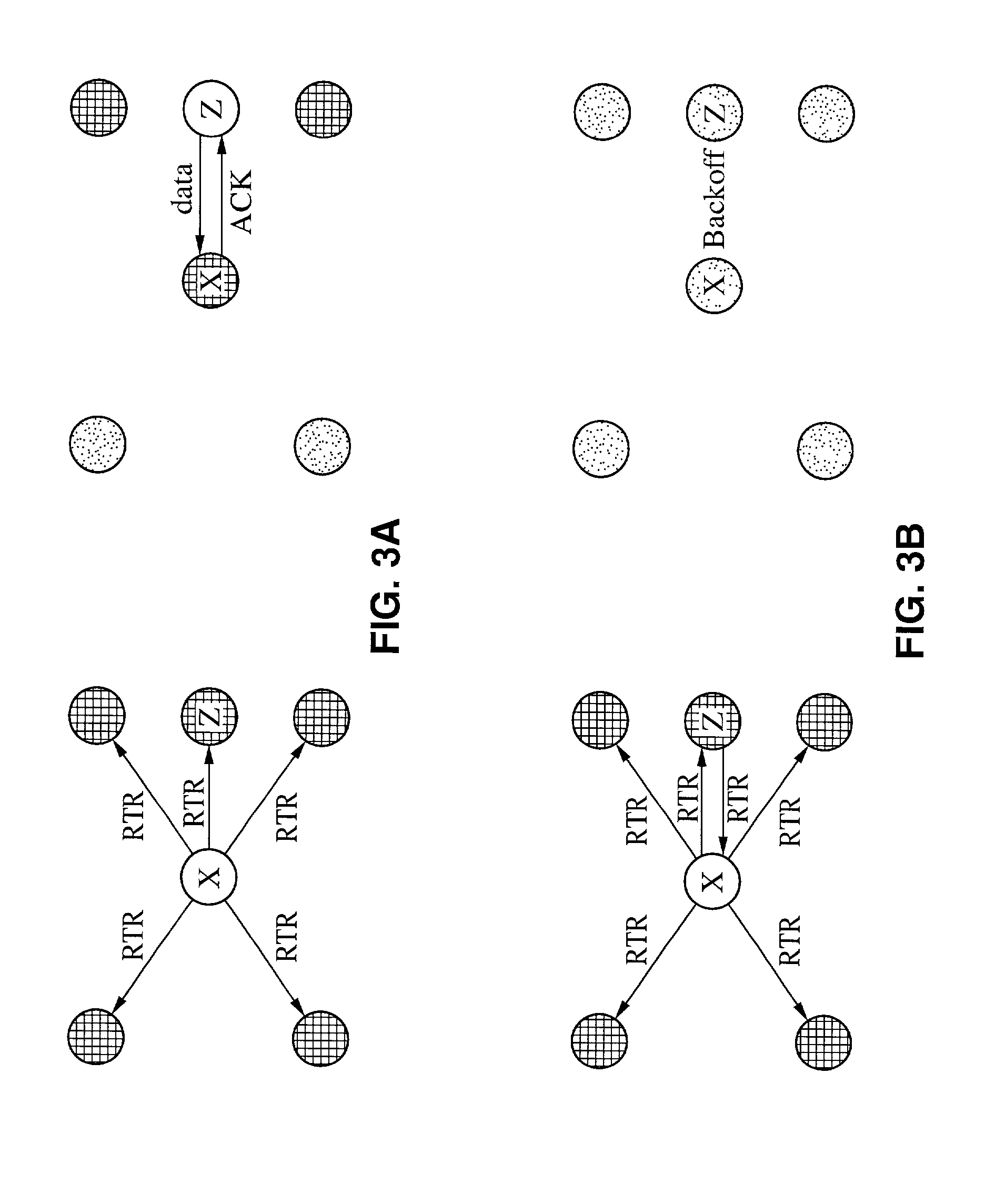
Multi-hop wireless mesh network medium access control protocol
ActiveUS20070147322A1RemissionImprove reliabilityPower managementNetwork topologiesClear to sendWireless mesh network
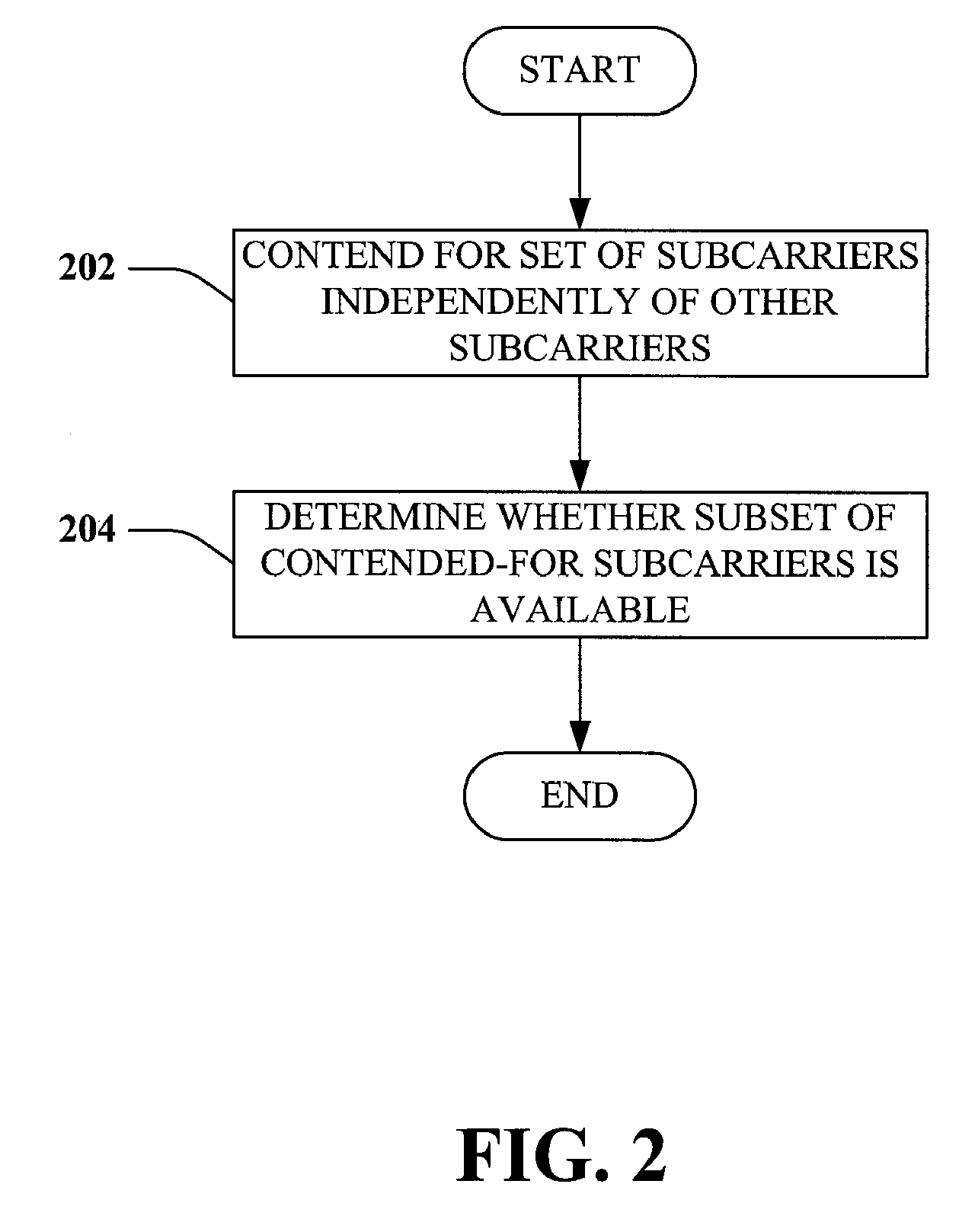
Systems and methodologies are described that facilitate mitigating a hidden node condition in a wireless mesh network wherein nodes utilize a request-to-send / clear-to-send (RTS / CTS) protocol in conjunction with an asynchronous hybrid automatic repeat request protocol. For instance, a node may contend for a set of subcarriers by sending an RTS signal over the desired subcarriers, and may receive a CTS signal over the contended subcarriers, wherein the CTS signal indicates which subcarriers the node may transmit data over. If another node has won the contention for a particular subcarrier, requesting node may adjust a power level at which it transmits an RTS or a data packet in order to permit the requesting node to utilize the subcarrier without interfering with the winning node.
Owner:QUALCOMM INC
Antenna steering and hidden node recognition for an access point
InactiveUS20050075142A1Facilitate communicationImprove throughputSpatial transmit diversitySubstation equipmentTelecommunicationsSignal quality
A method for operating an access point in a wireless local area network (WLAN) is provided. The access point includes a directional antenna for communicating with a plurality of remote stations, and the directional antenna includes a plurality of antenna patterns. The method includes creating an antenna database by associating between the access point and each remote station a respective measured signal quality corresponding to the plurality of antenna patterns. The respective measured signal qualities are determined by the access point based upon communications with each remote station. The method further includes determining for each remote station a preferred antenna pattern based upon the antenna database, and selecting a remote station and the corresponding preferred antenna pattern to communicate with. It is also determined based upon the antenna database and prior to communicating with the selected remote station, if any non-selected remote stations have the potential of not being aware when such communications actually occurs.
Owner:IPR LICENSING INC
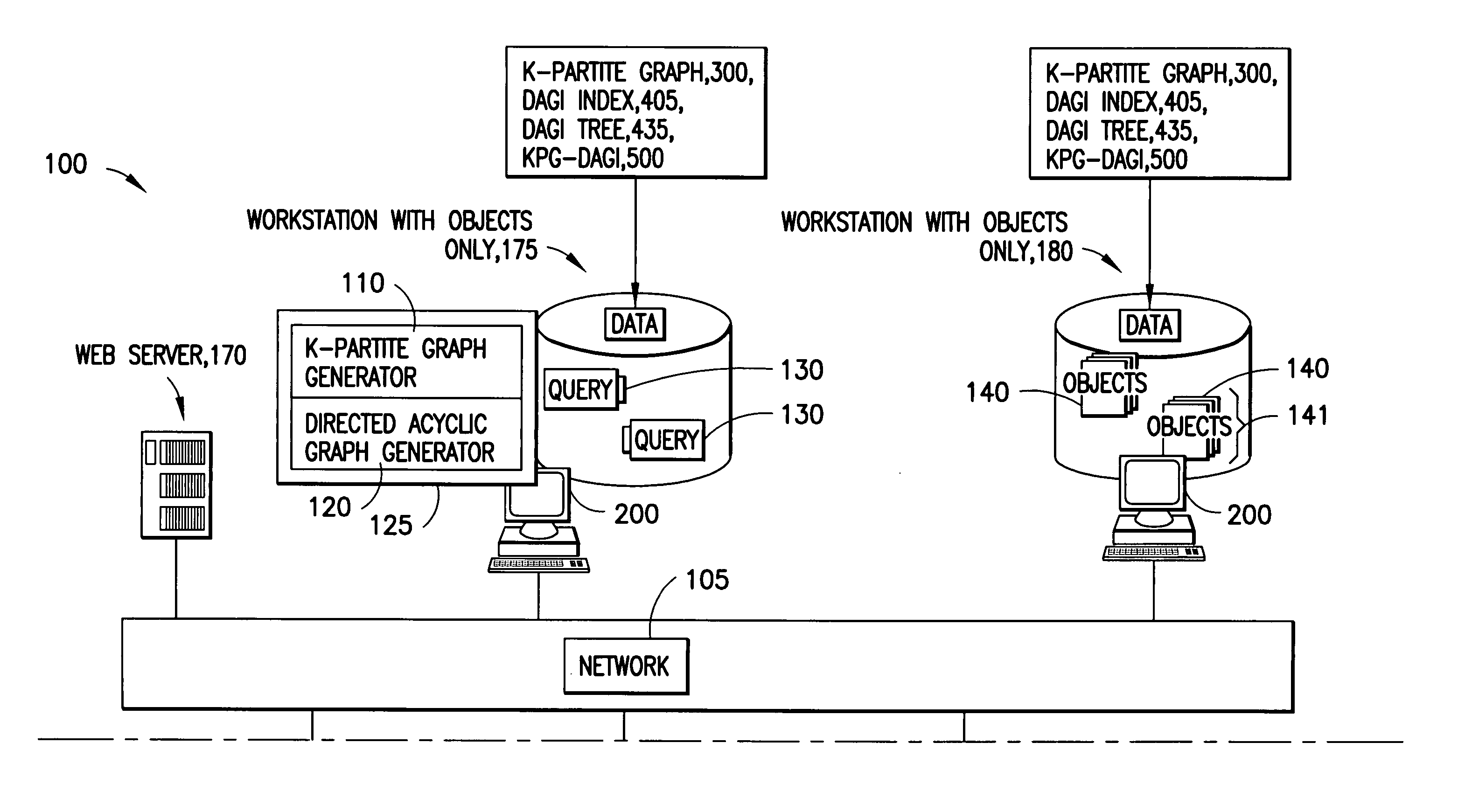
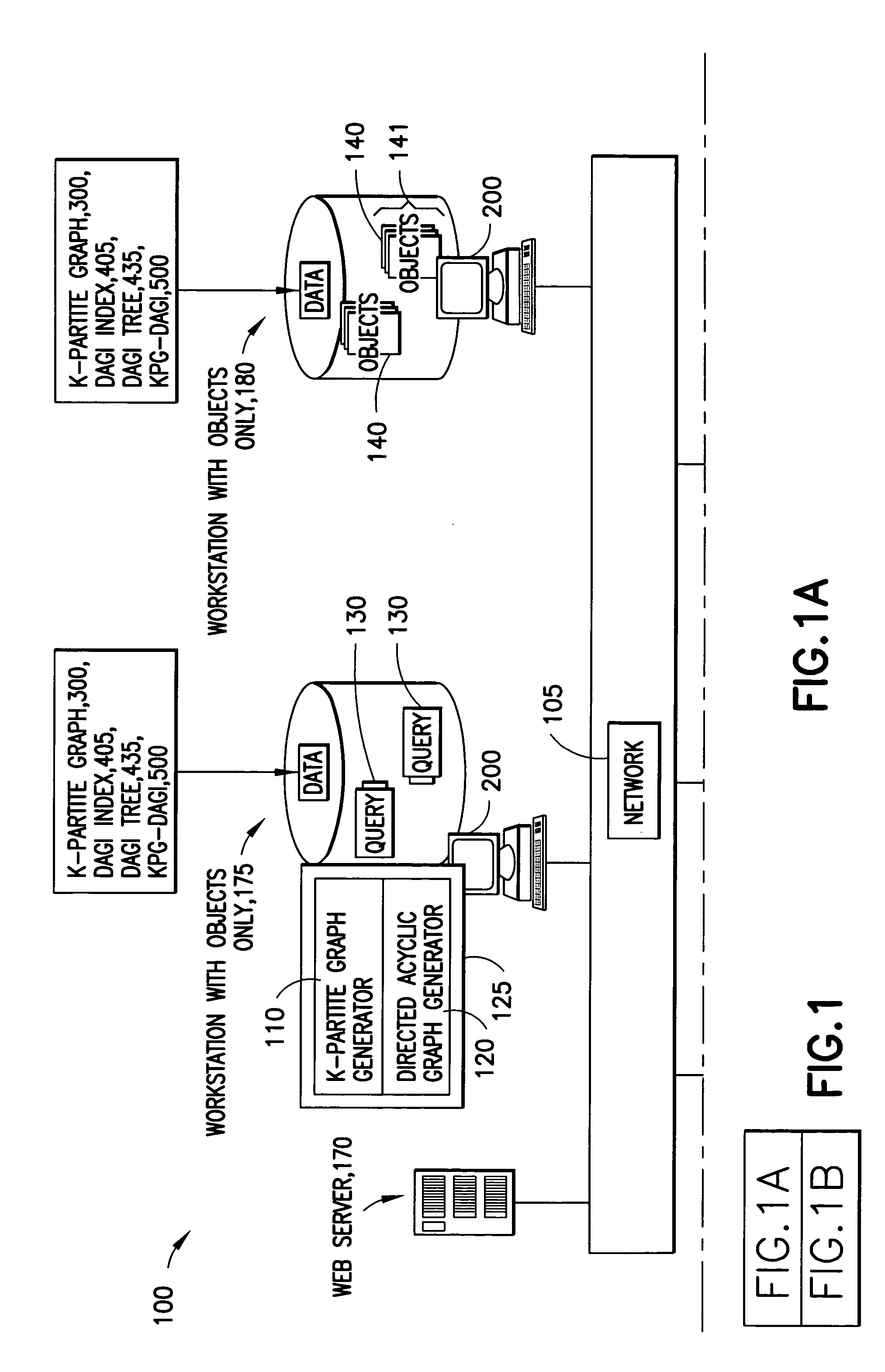
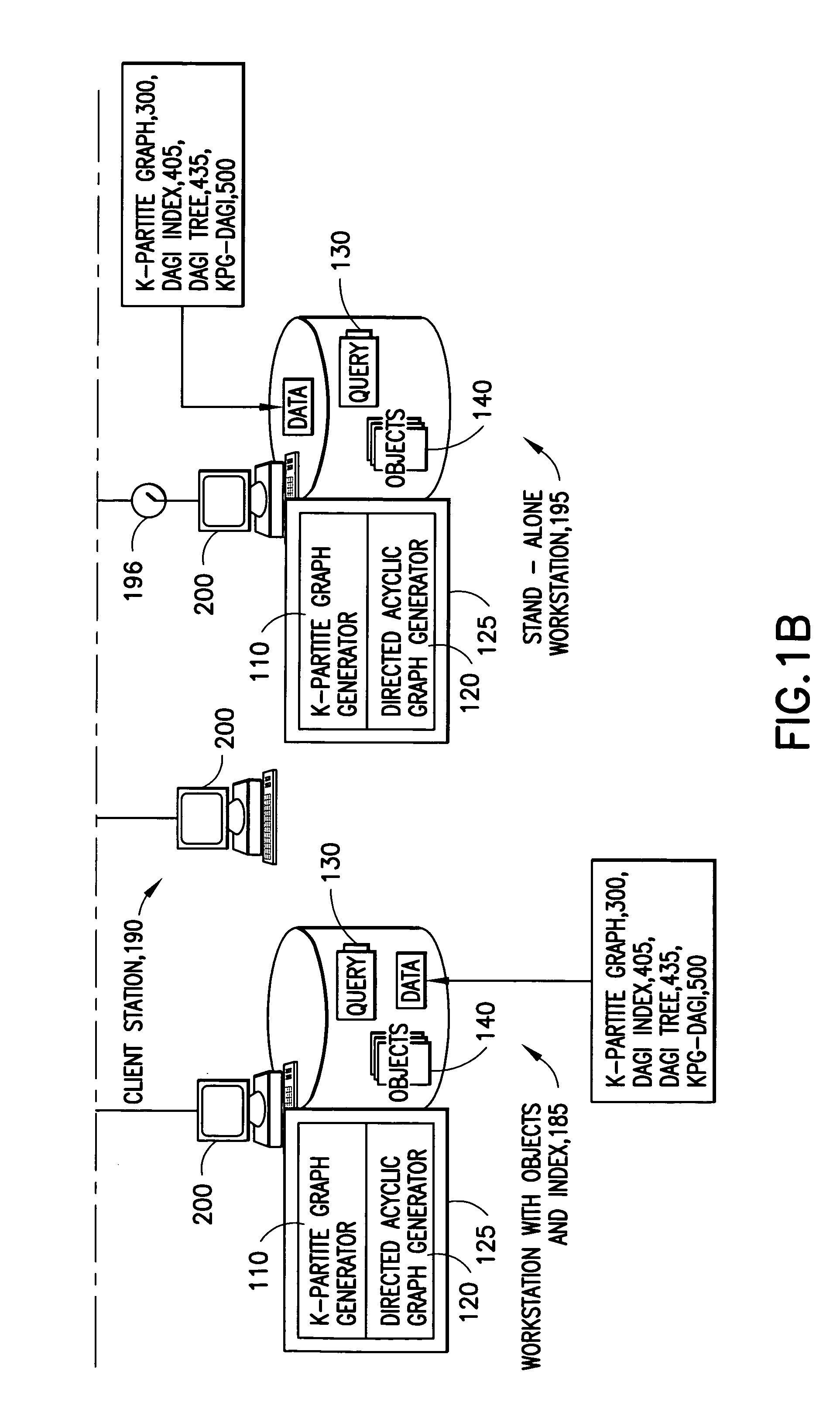
System and method for simplifying and manipulating k-partite graphs
InactiveUS20050038533A1High frequencySampled-variable control systemsData processing applicationsTheoretical computer scienceMultiple category
The system has a collection of a plurality of objects. Each object defines a node in a k-partite graph, such that, the nodes can e divided into a number of mutually exclusive sets such that all of the nodes are in exactly one of the sets; further edges occur only between nodes in different sets; The system also has a simplification process that aggregates one or more of the nodes into one or more categories and identifies a category node corresponding to each category. The category node inherits the mode and the edges of all the nodes in the respective category. Further, the system contains Directed Acyclic Graphs Indices (DAGIs) whose nodes may have a 1-1 mapping with the nodes in the k-partite graph. These indices can be used to aggregate and hide nodes in the k-partite graph. Aggregation occurs by selecting one or more non-leaf nodes in the DAGI and aggregating all descendent nodes. Hiding occurs by selecting some set of DAGI nodes, thus selecting some corresponding set of nodes in the k-partite graph, and requesting this set of nodes be hidden which effectively removes them from further consideration until they are restored by explicit request.
Owner:IBM CORP
Receiver-initiated multiple access for AD-HOC networks (RIMA)
ActiveUS20020080768A1Improve efficiencyReduce control overheadNetwork traffic/resource managementTransmission control/equalisingCarrier signalDual purpose
Receiver-initiated collision avoidance methods for use in ad-hoc wireless networks in which carrier sensing is available. A number of protocol variants are described including RIMA-SP (simple polling), RIMA-DP (dual-purpose polling), and RIMA-BP (broadcast polling). These handshake methods according to the invention are capable of correctly avoiding collisions within a network that contains hidden nodes, and the RIMA-DP protocol provides higher performance levels than attainable with existing handshaking protocols within the ad-hoc wireless networks. The use of dual-purpose polling allows a control packet to be sent which has alternative functions, such as requesting data from the polled node, if available, and if not available then providing a transmission request from the polling node to send data to the polled node.
Owner:RGT UNIV OF CALIFORNIA
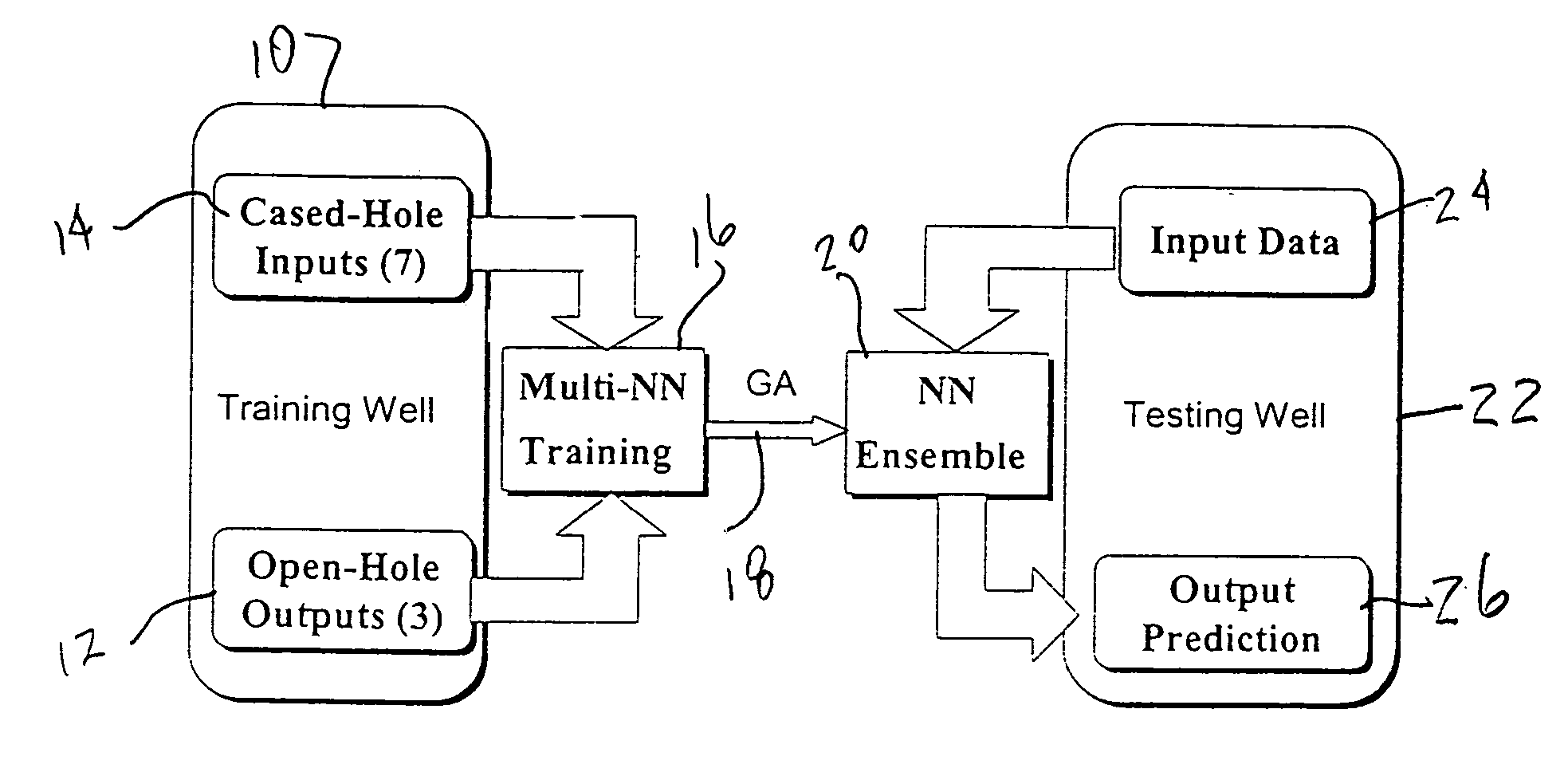
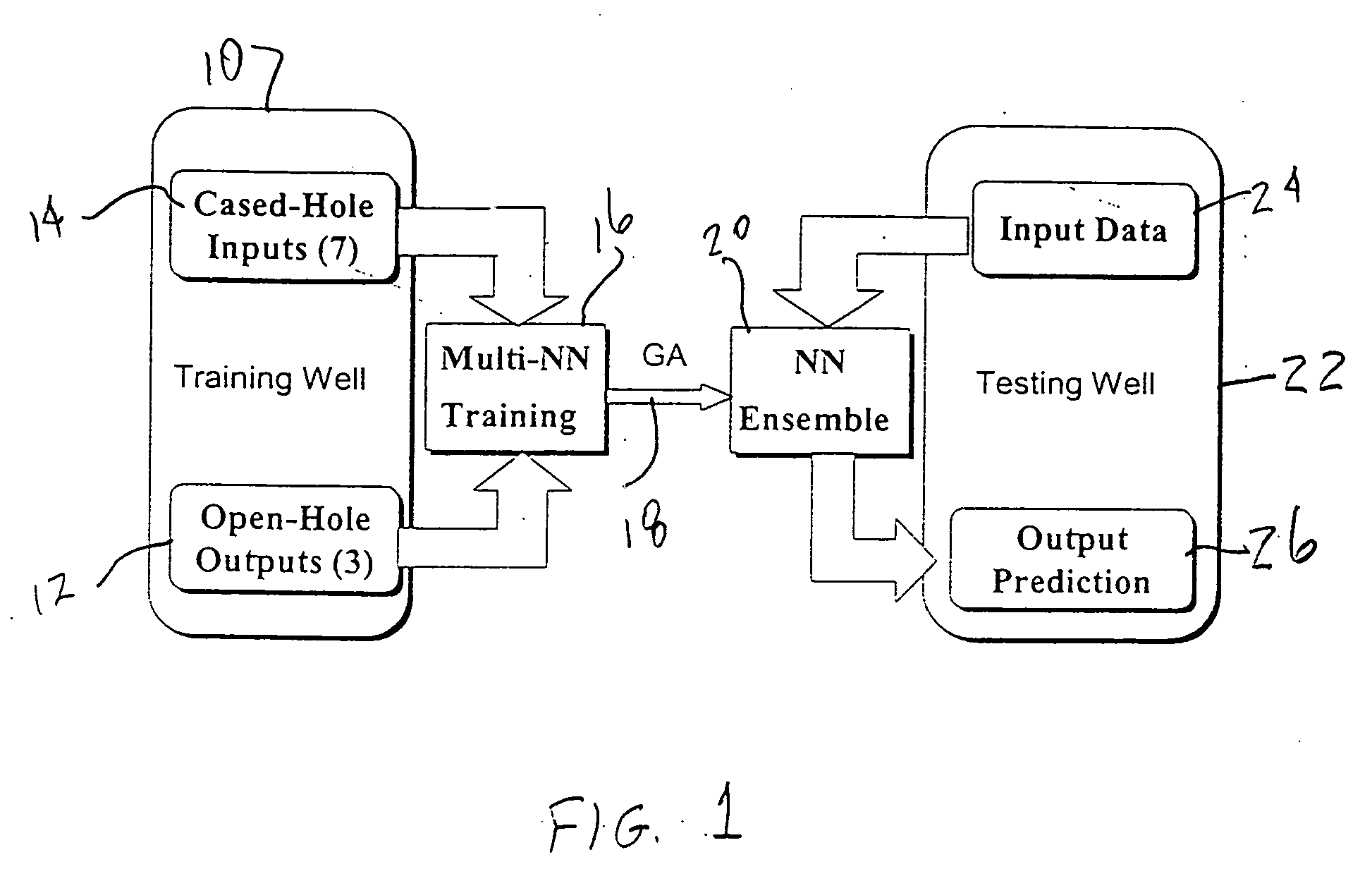
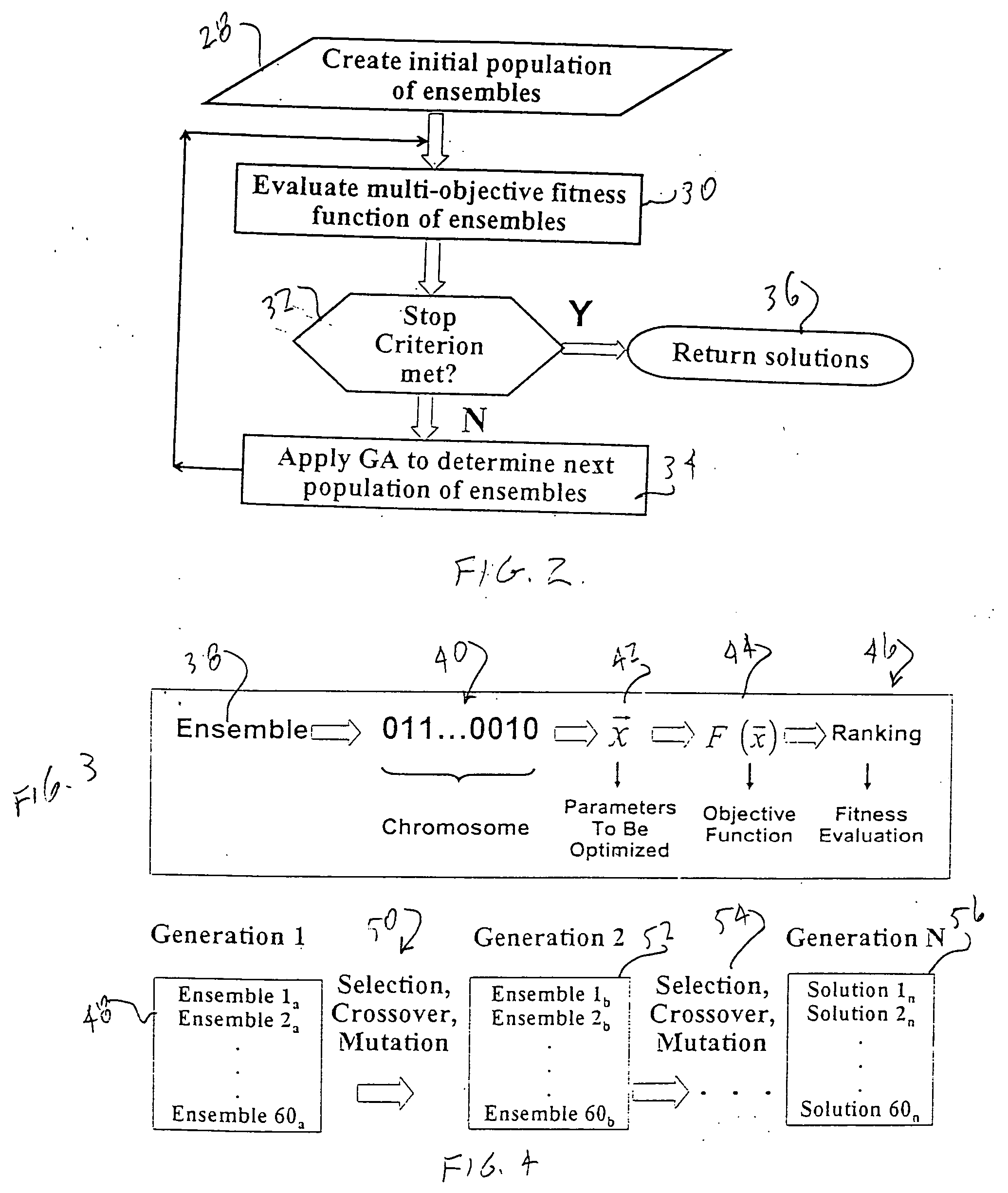
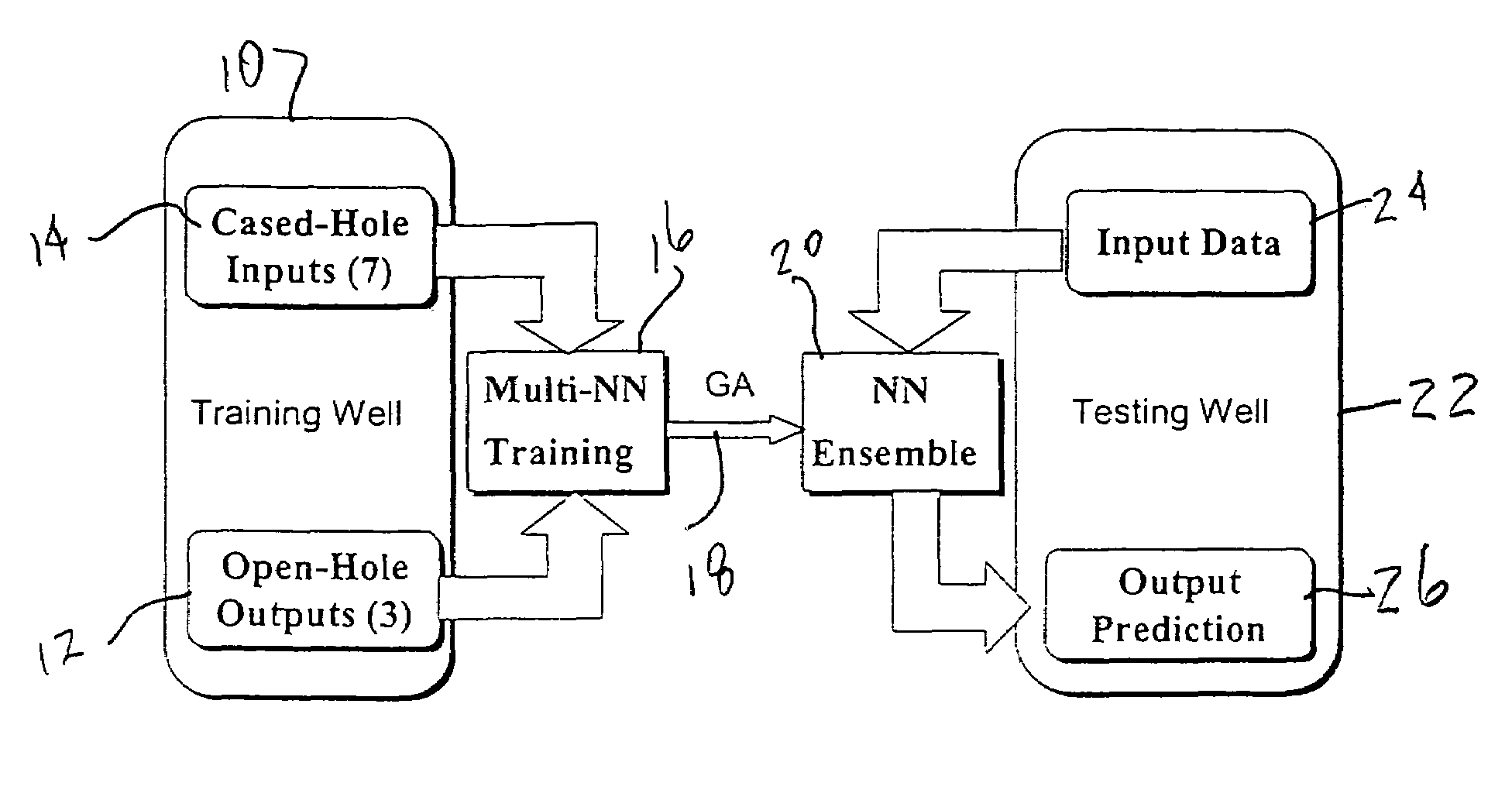
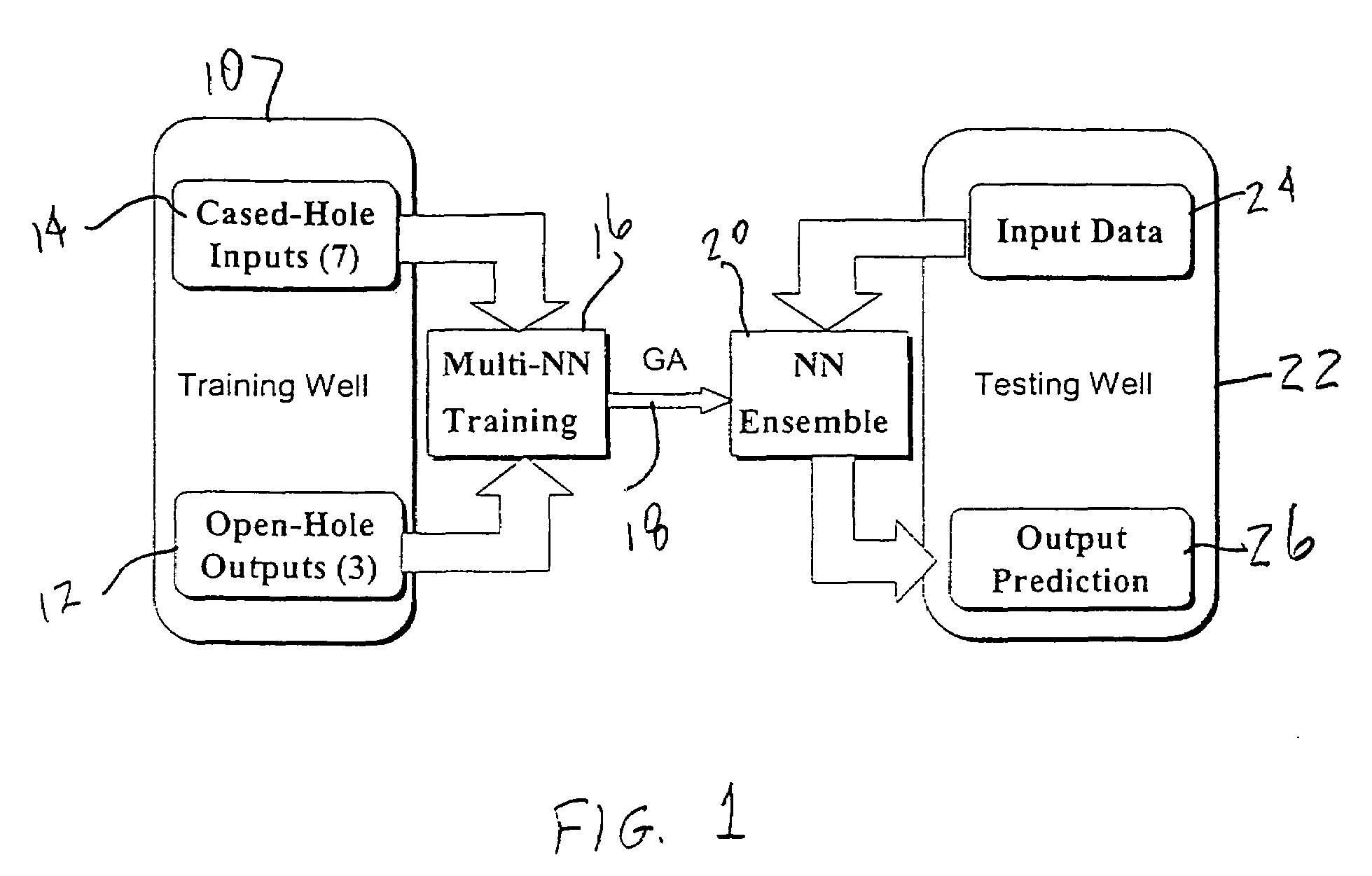
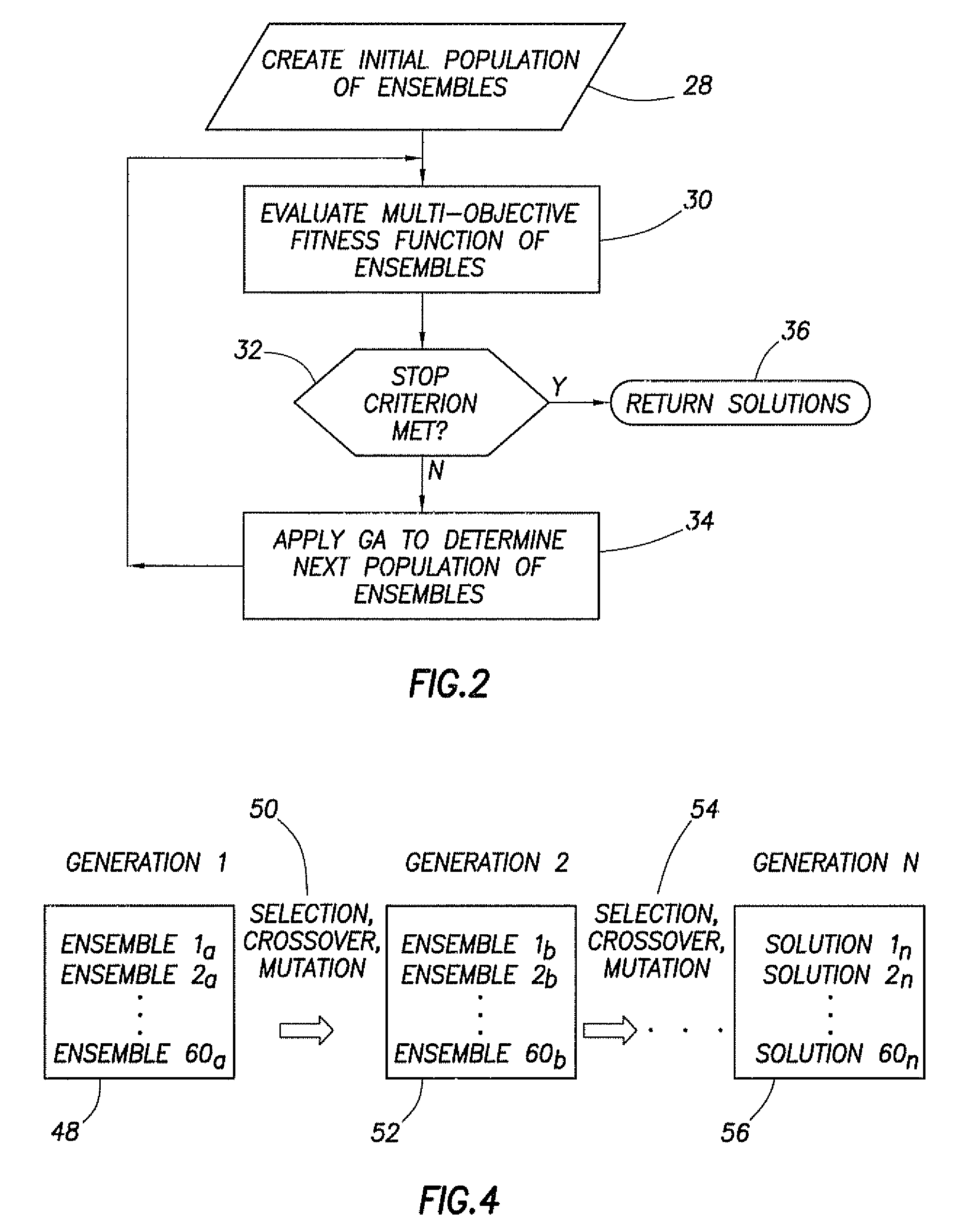
Genetic algorithm based selection of neural network ensemble for processing well logging data
ActiveUS20050246297A1Improve generalization abilityElectric/magnetic detection for well-loggingDigital computer detailsNegative errorNerve network
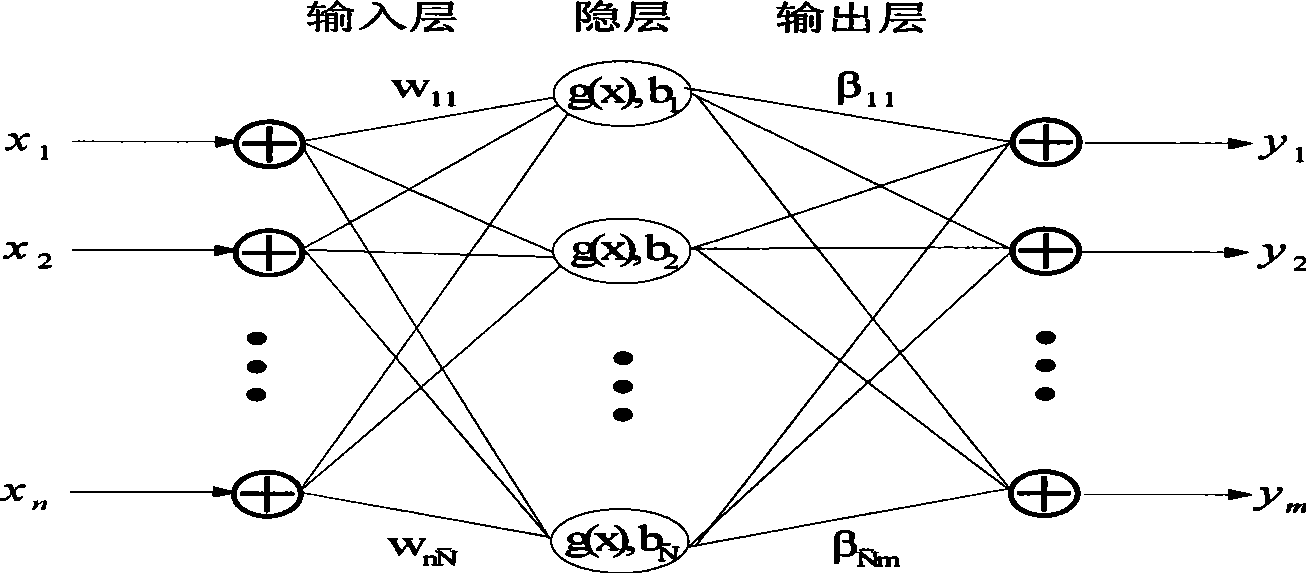
A system and method for generating a neural network ensemble. Conventional algorithms are used to train a number of neural networks having error diversity, for example by having a different number of hidden nodes in each network. A genetic algorithm having a multi-objective fitness function is used to select one or more ensembles. The fitness function includes a negative error correlation objective to insure diversity among the ensemble members. A genetic algorithm may be used to select weighting factors for the multi-objective function. In one application, a trained model may be used to produce synthetic open hole logs in response to inputs of cased hole log data.
Owner:HALLIBURTON ENERGY SERVICES INC
Model training method and device and text intention recognition method and device
ActiveCN107943860AGood at discoveringImprove generalization abilityCharacter and pattern recognitionSpecial data processing applicationsMulti dimensionalMachine learning
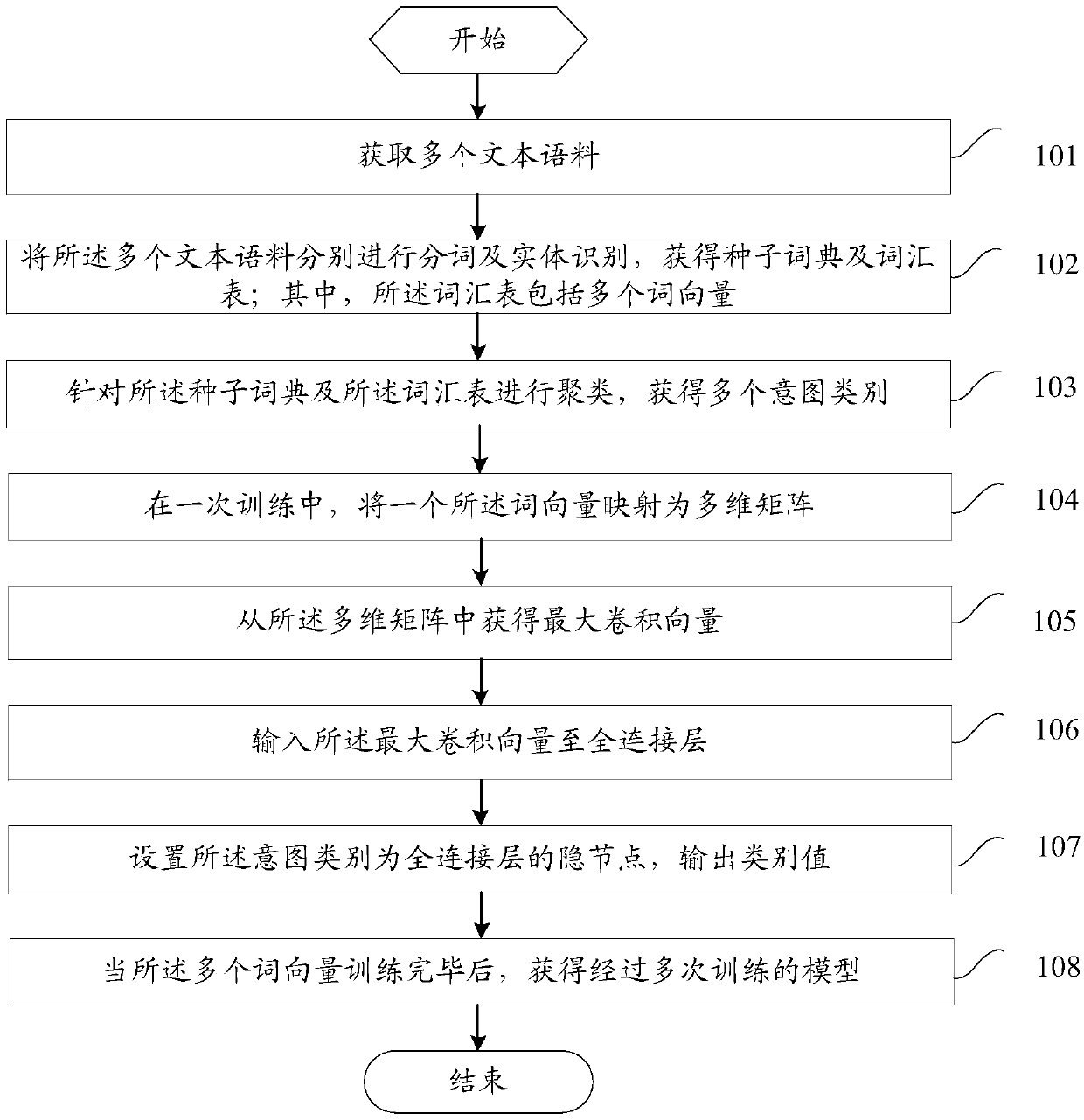
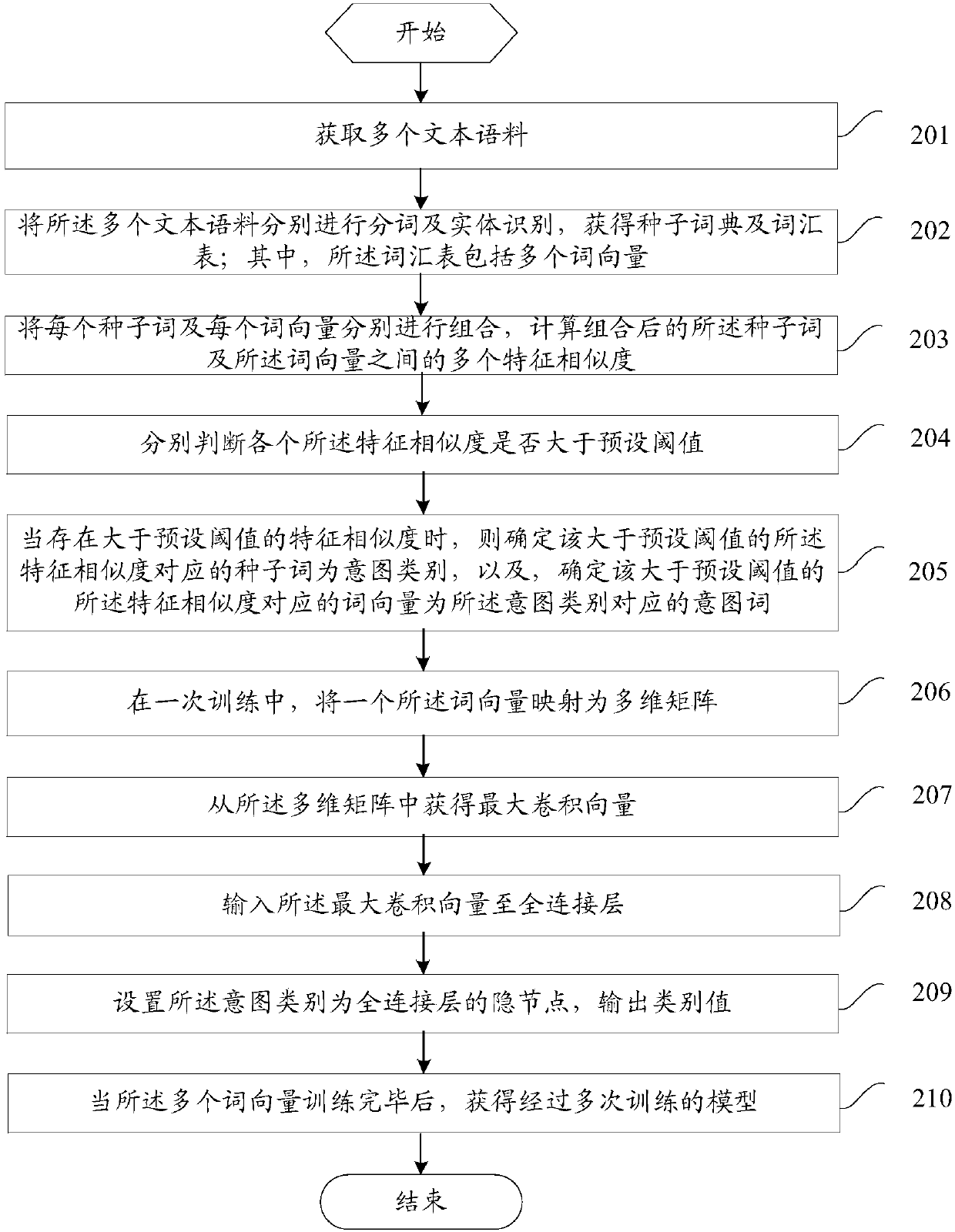
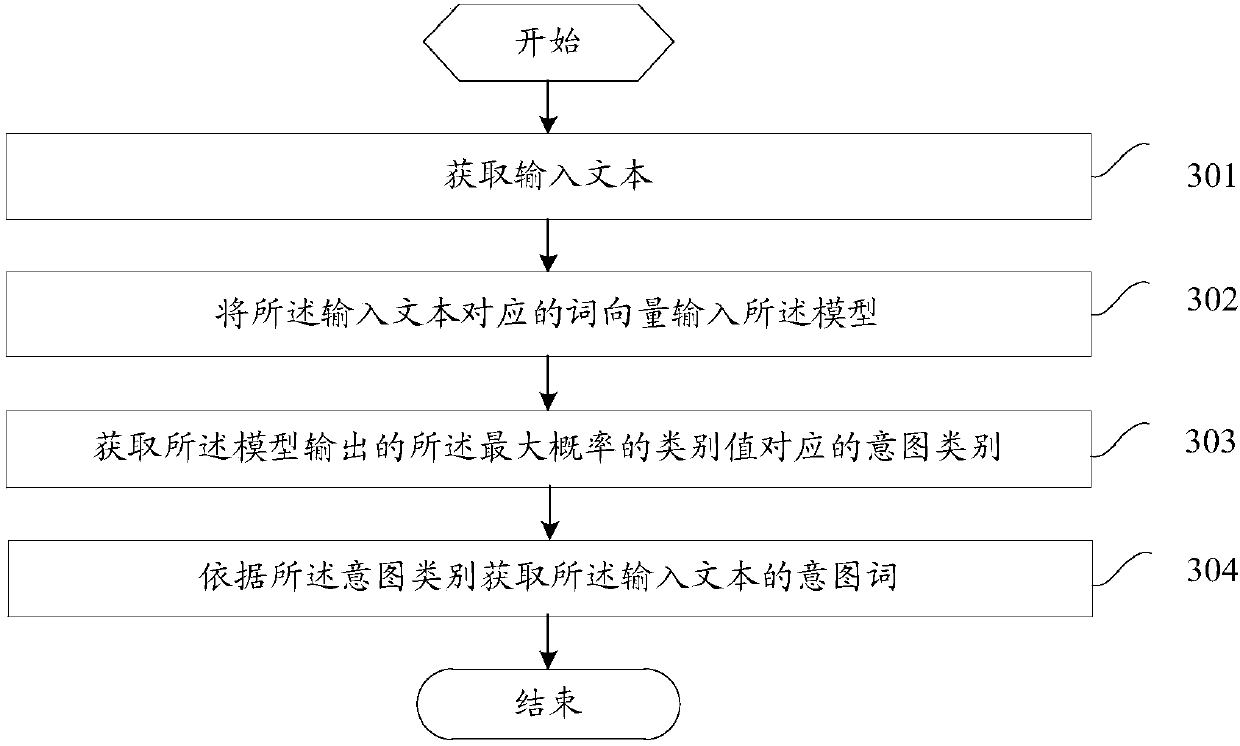
Embodiments of the invention provide a model training method and device and a text intention recognition method and device. The model training method comprises the following steps of: obtaining a plurality of text corpuses; respectively carrying out word segmentation and entity recognition on the plurality of text corpuses so as to obtain a seed dictionary and a vocabulary; clustering the seed dictionary and the vocabulary to obtain a plurality of intention categories; in a training, mapping a word vector into a multi-dimensional matrix; obtaining a maximum convolution vector from the multi-dimensional matrix; inputting the maximum convolution vector to a full connection layer; setting the intention categories as hidden nodes of the full connection layer and outputting category values; andwhen the training of a plurality of word vectors is finished, obtaining a model which is repeatedly trained. The invention discloses a word vector-based intention category determination method whichis good at discovering new intention categories when being compared traditional artificial setting and enumerating method; and by adoption of the trained model, the text intention recognition rate ishigher.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
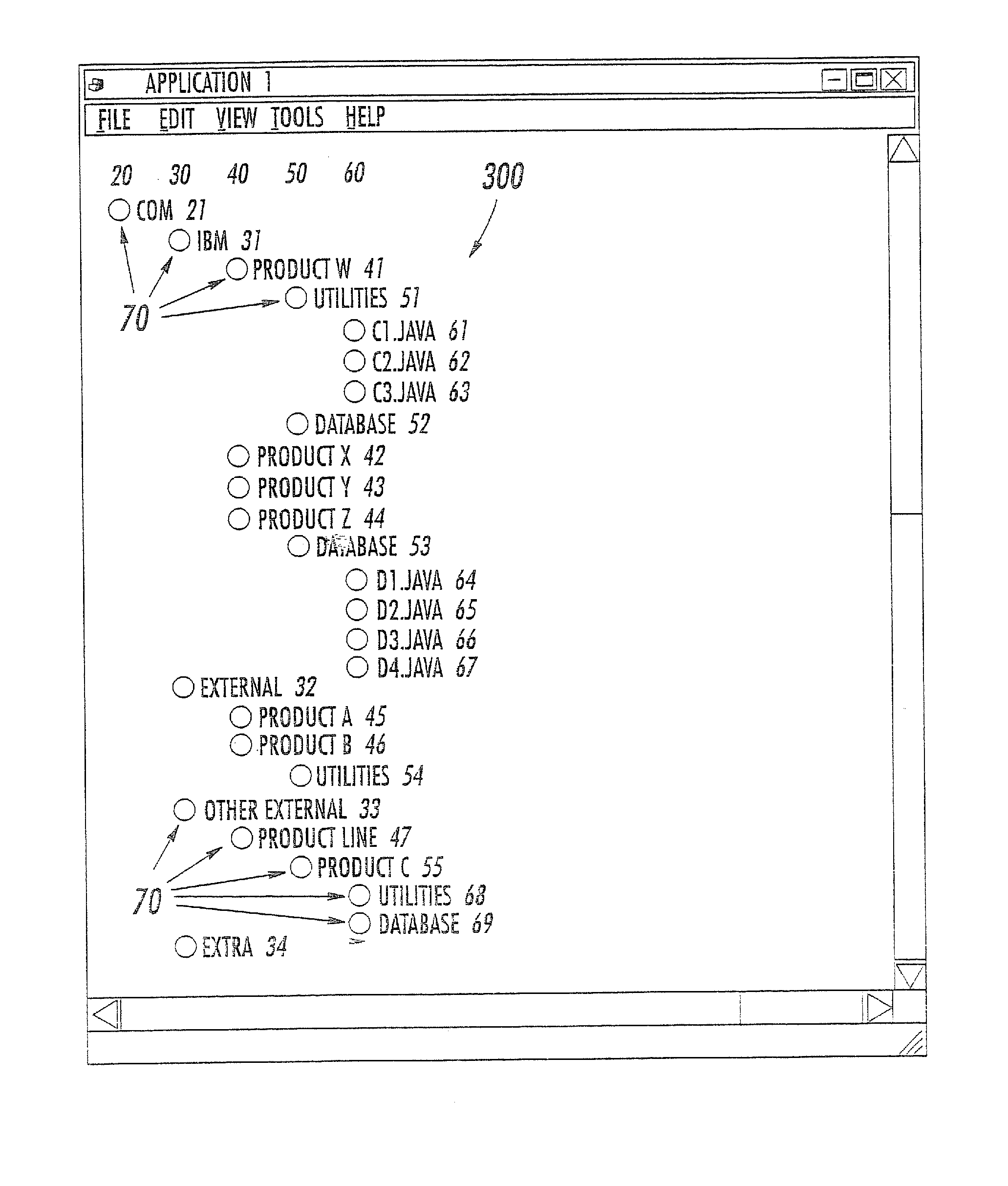
Methods, systems and computer program products for controlling tree diagram graphical user interfaces and/or for partially collapsing tree diagrams
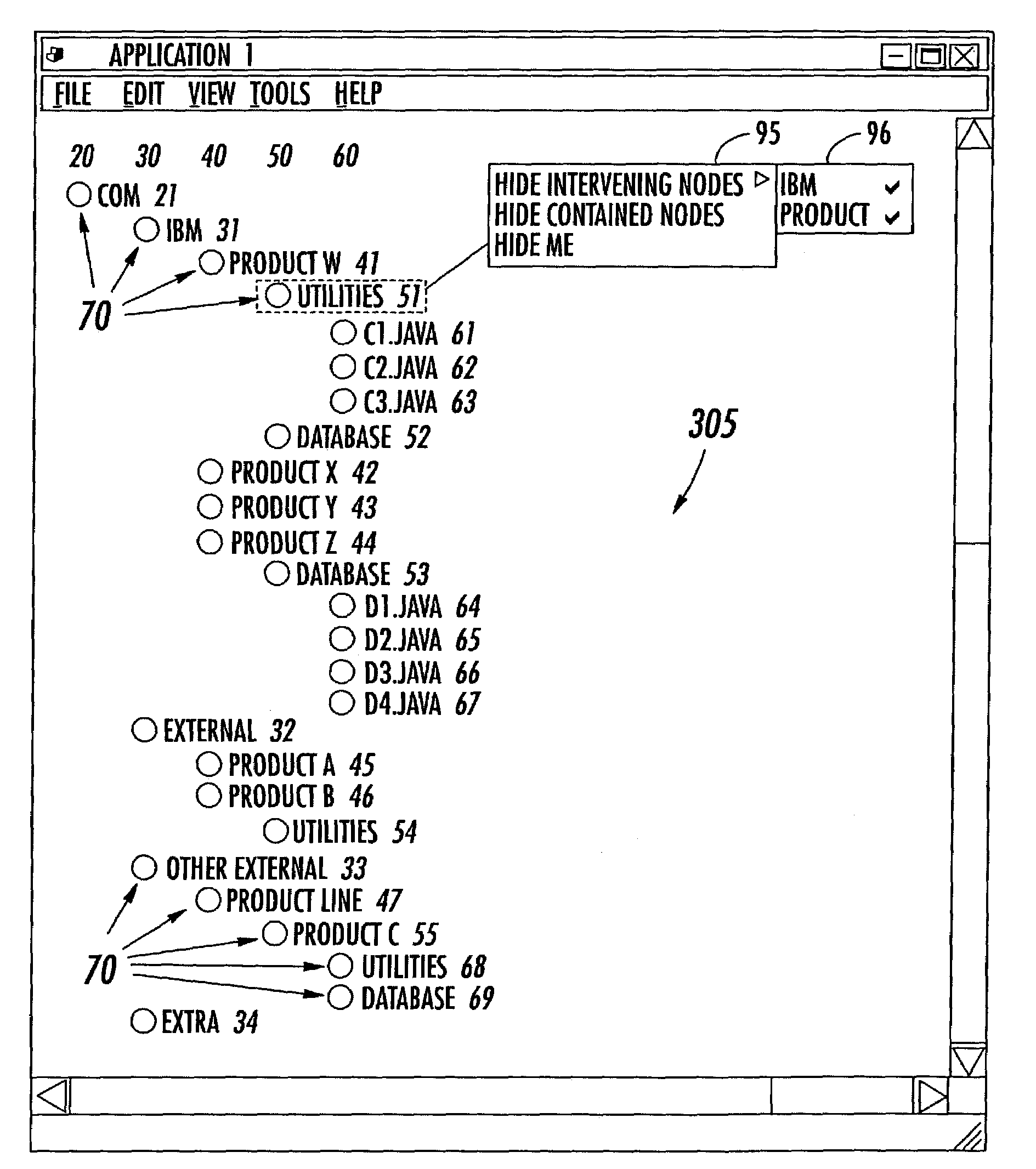
Methods for selectively displaying portions of a hierarchical data set on an electronic display comprise the steps of displaying at least a portion of the hierarchical data set on an electronic display in a tree diagram format. Input may then be obtained from a user to identify one or more displayed nodes in the tree diagram that are to be hidden and / or one or more hidden nodes in the tree diagram that are to be displayed. Based on this input, at least one node in the tree diagram is partially collapsed and / or at least one node in the tree diagram may be partially expanded so as to display the hidden nodes identified by the user and so as to hide the displayed nodes identified by the user.
Owner:IBM CORP
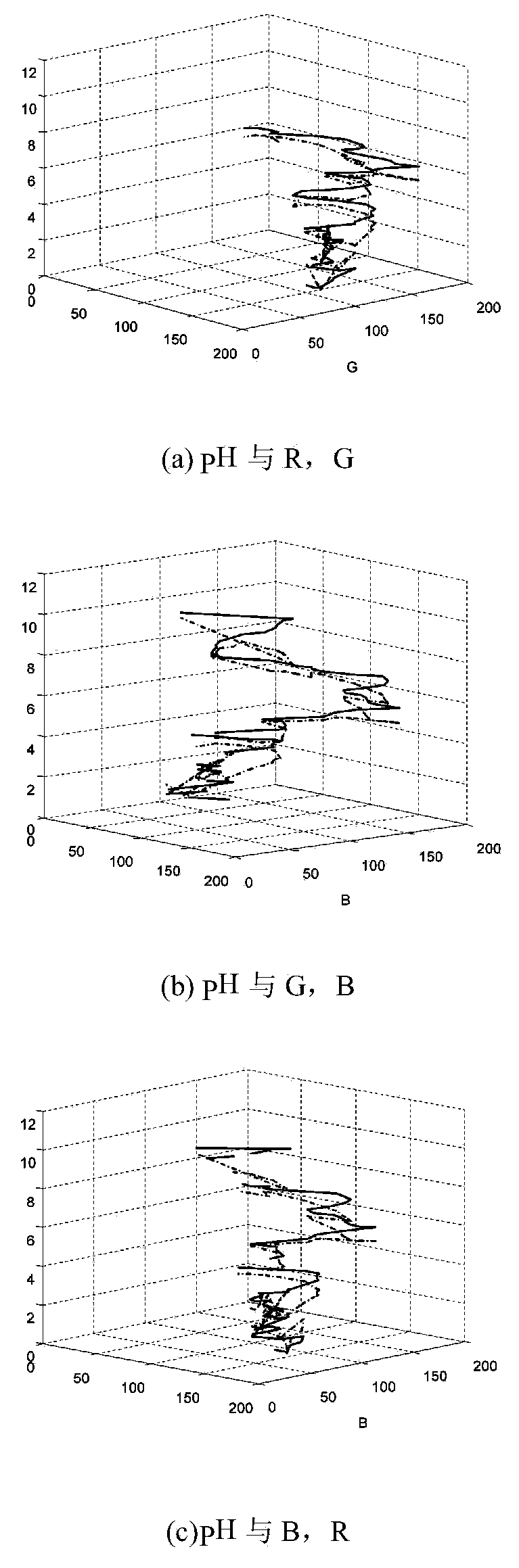
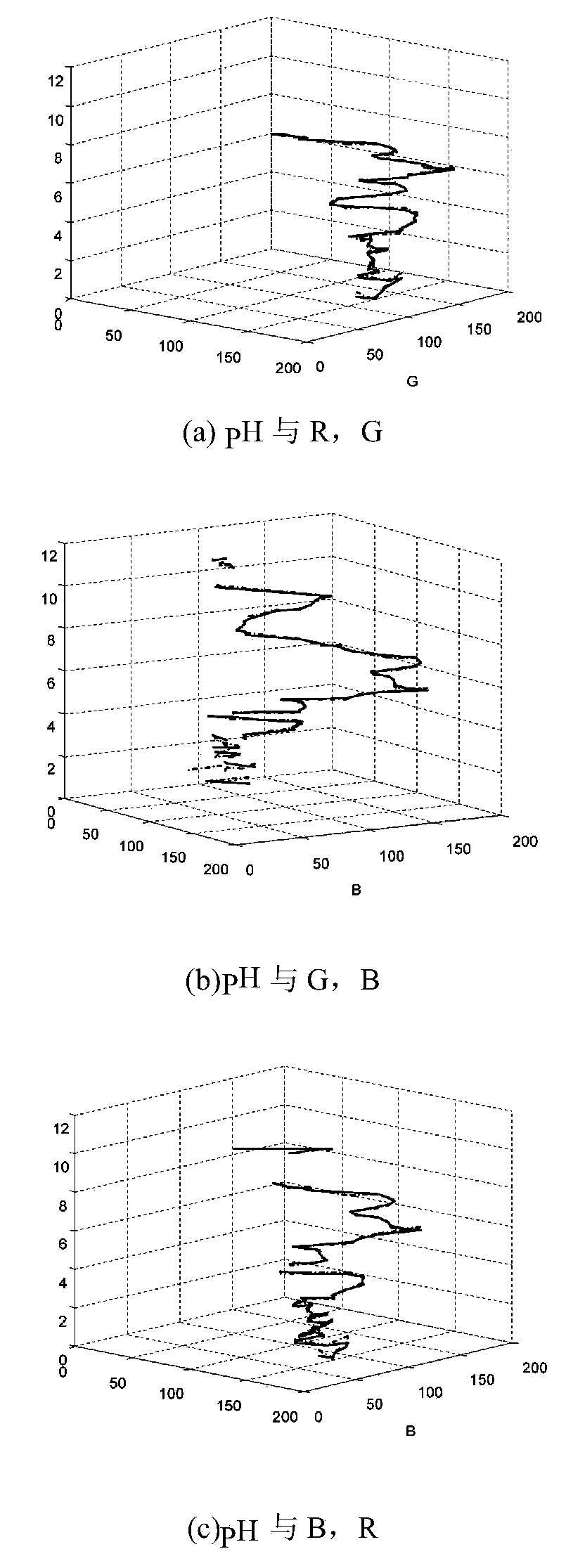
PH (potential of hydrogen) value predicting method of BP (back propagation) neutral network based on simulated annealing optimization
InactiveCN104700153AAvoid randomnessFast convergenceForecastingNeural learning methodsHydrogenOptimal weight
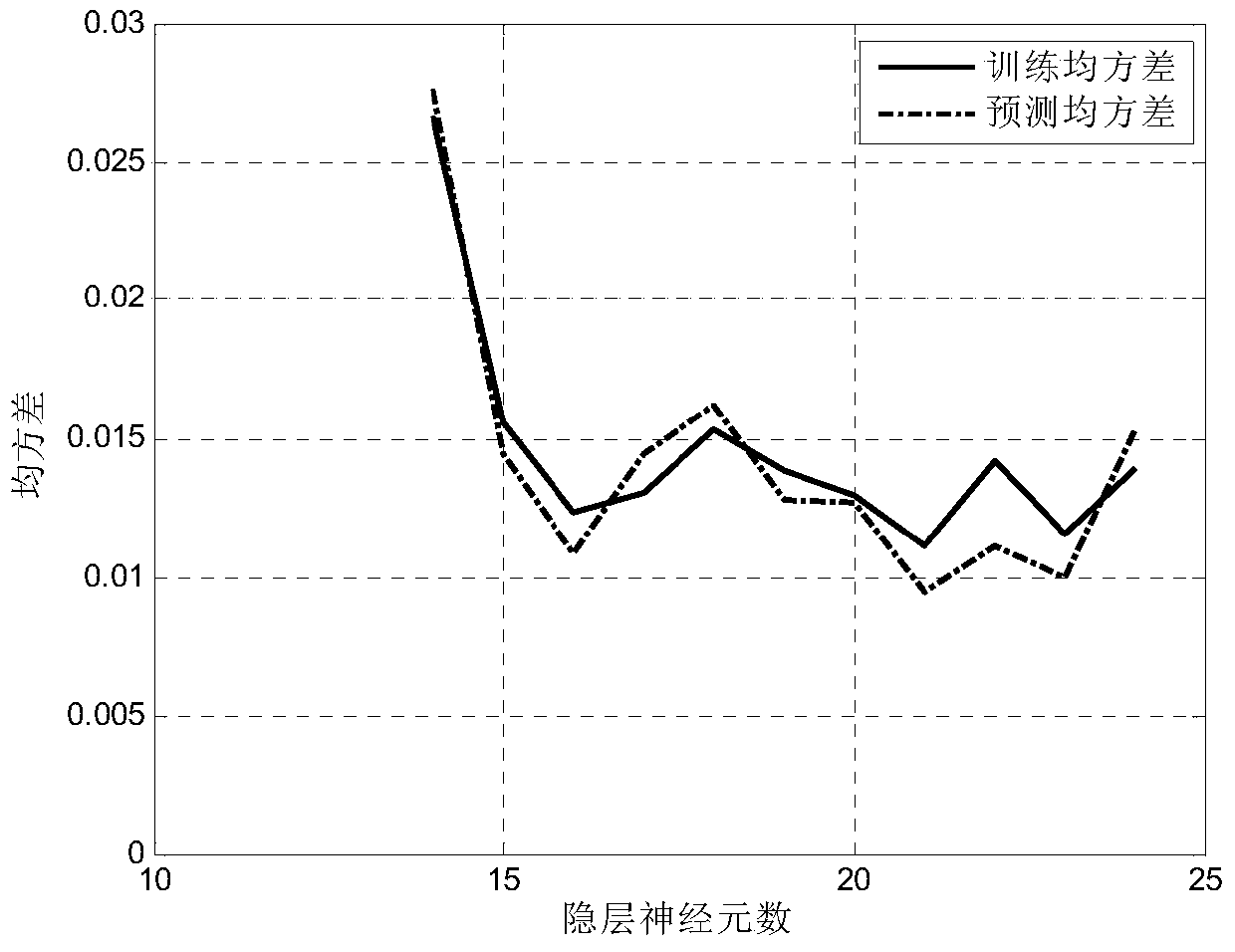
The invention discloses a pH (potential of hydrogen) value predicting method of a BP (back propagation) neutral network based on a simulated annealing (SA) algorithm optimization. The pH value predicting method comprises the following steps: step one, selecting a sample according to a sample selecting strategy and inputting; step two, according to the BP theorem, determining the structure of the BP neutral network; step three, according to a network training strategy, applying the simulated annealing algorithm to optimize the BP network weight parameter; training the BP network by using the input sample, and determining the optimal weight and optimal hidden node number of the BP network; step four, according to the well trained BP neutral network, structuring a predicting model of the pH value. The pH value predicting method overcomes the randomness of the BP network in terms of weight selection, improves the rate of convergence and study ability of the BP neutral network. Besides, the method optimizes the selection of the training sample and the network hidden neutral element number, and improves the generalization ability of the BP neutral network. Moreover, the pH value predicting method is high in predicting accuracy of pH value and good in nonlinear fitting ability.
Owner:JIANGNAN UNIV
Devices, softwares and methods for rescheduling multi-party sessions upon premature termination of session
InactiveUS7330877B2Readily apparentConnection managementData switching by path configurationHidden node problemTime efficient
Devices, softwares and methods reschedule multi-party sessions upon premature termination of a wireless communication session. Upon sensing a premature termination, an access point transmits a rescheduling frame. All sessions are advanced in time, which saves time in the end, without leaving quiet times. In addition, the invention avoids a hidden node problem.
Owner:SHARP KK
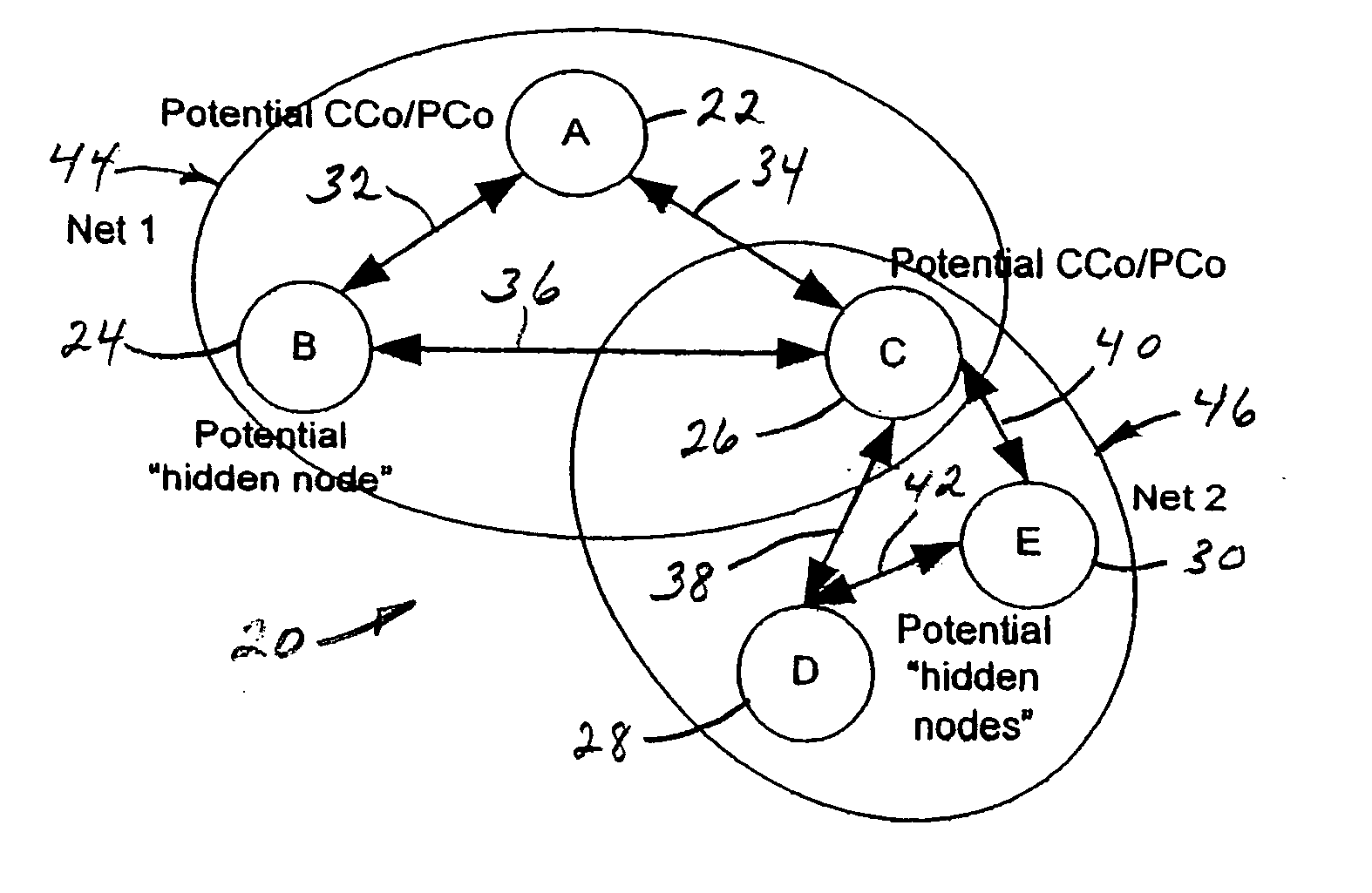
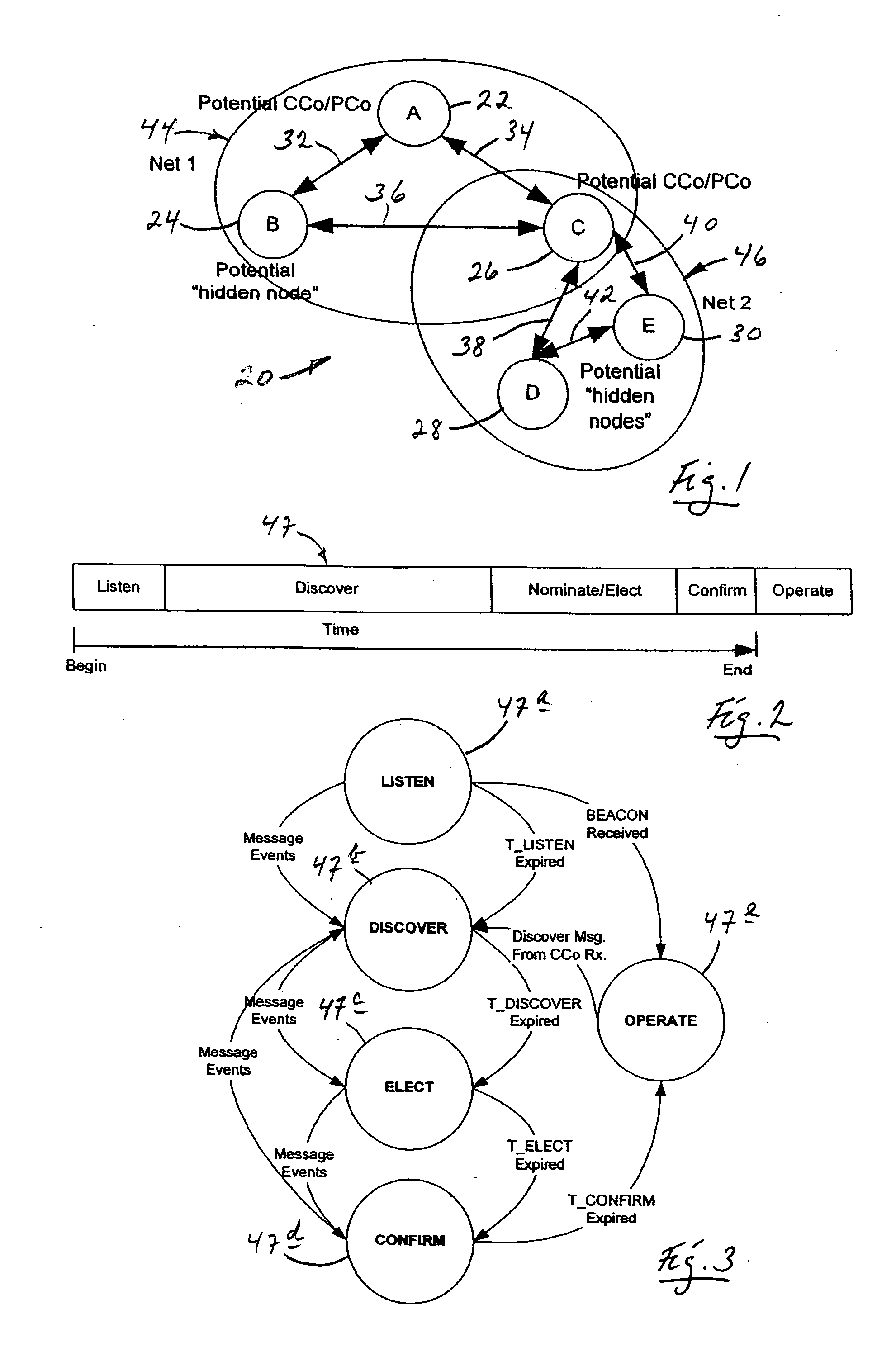
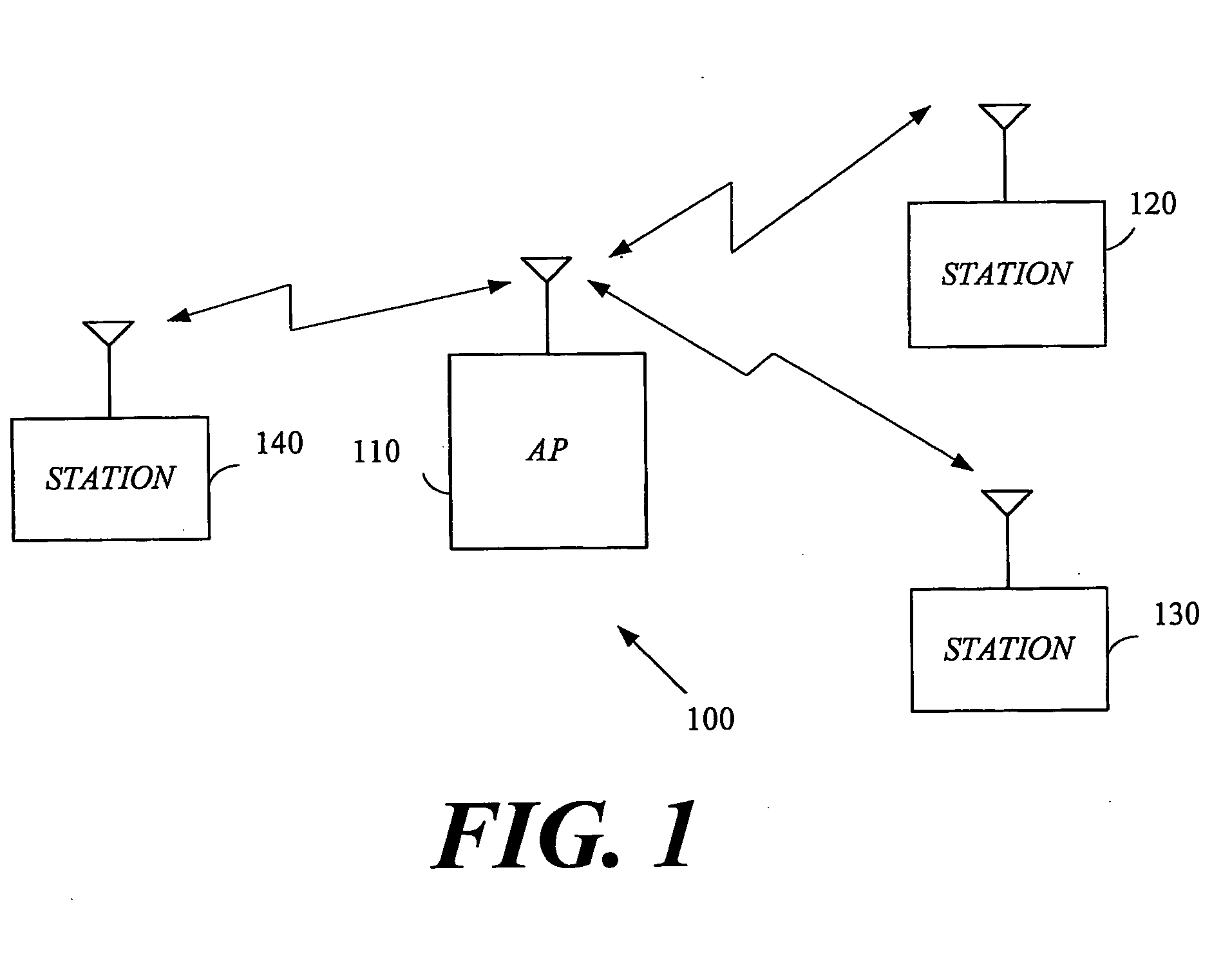
System and method for identifying potential hidden node problems in multi-hop wireless ad-hoc networks for the purpose of avoiding such potentially problem nodes in route selection
InactiveUS7200149B1Effective and efficient identificationHigh degreeNetwork topologiesBroadcast transmission systemsHidden node problemAd hoc communication
A system and method for identifying potential hidden node problems in a multi-hop wireless ad-hoc communication network, such as an 802.11 network. The system and method evaluates the relationship between the neighbors of each respective node to identify nodes of a wireless ad-hoc communication network whose capabilities of receiving data packets can be adversely affected by hidden node problems in order to avoid selecting paths containing those potentially problem nodes for routing data packets. Specifically, for each node, the system and method generates a node metric identifying the relationship between the neighbors of a node. Each node can then transmit its respective metric with its routing advertisement data, so that other nodes can assess the degree of potential hidden node problem that may be experienced by that node, and can choose to avoid using that potentially problem node for routing data packets to other nodes.
Owner:ARRIS ENTERPRISES LLC
Method for forecasting electric power system short-term load based on method for improving uttermost learning machine
InactiveCN101414366AImprove forecast accuracyImprove the speed of predictionNeural learning methodsNODALLearning machine
The invention discloses a power system short-term load forecasting method based on improving extreme learning machine (IELM) methods, which adopts an extreme learning machine (ELM) as the basic structure of a forecasting model and is an iteration-analysis learning algorithm which puts forward BFGS (Broyden, Fletcher, Goldfarb, Shanno) simulated Newton's method to give optimization, training and adjustment to network left metrics and analyze to get right metric parameters. The invention establishes the short-term load forecasting model based on improving extreme learning machine (IELM) method, puts forward extreme learning machine network reference hidden node concepts, trains the equidimensional extreme learning machine networks which have the same numbers of hidden nodes and samples, orderly clusters module values of equidimensional network right metrics vector, finds out a plurality of corresponding module value break points, and regards the break points as the reference hidden nodes of predicting networks. The method of the invention is also greatly improved in the aspect of prediction precision and speed.
Owner:XI AN JIAOTONG UNIV
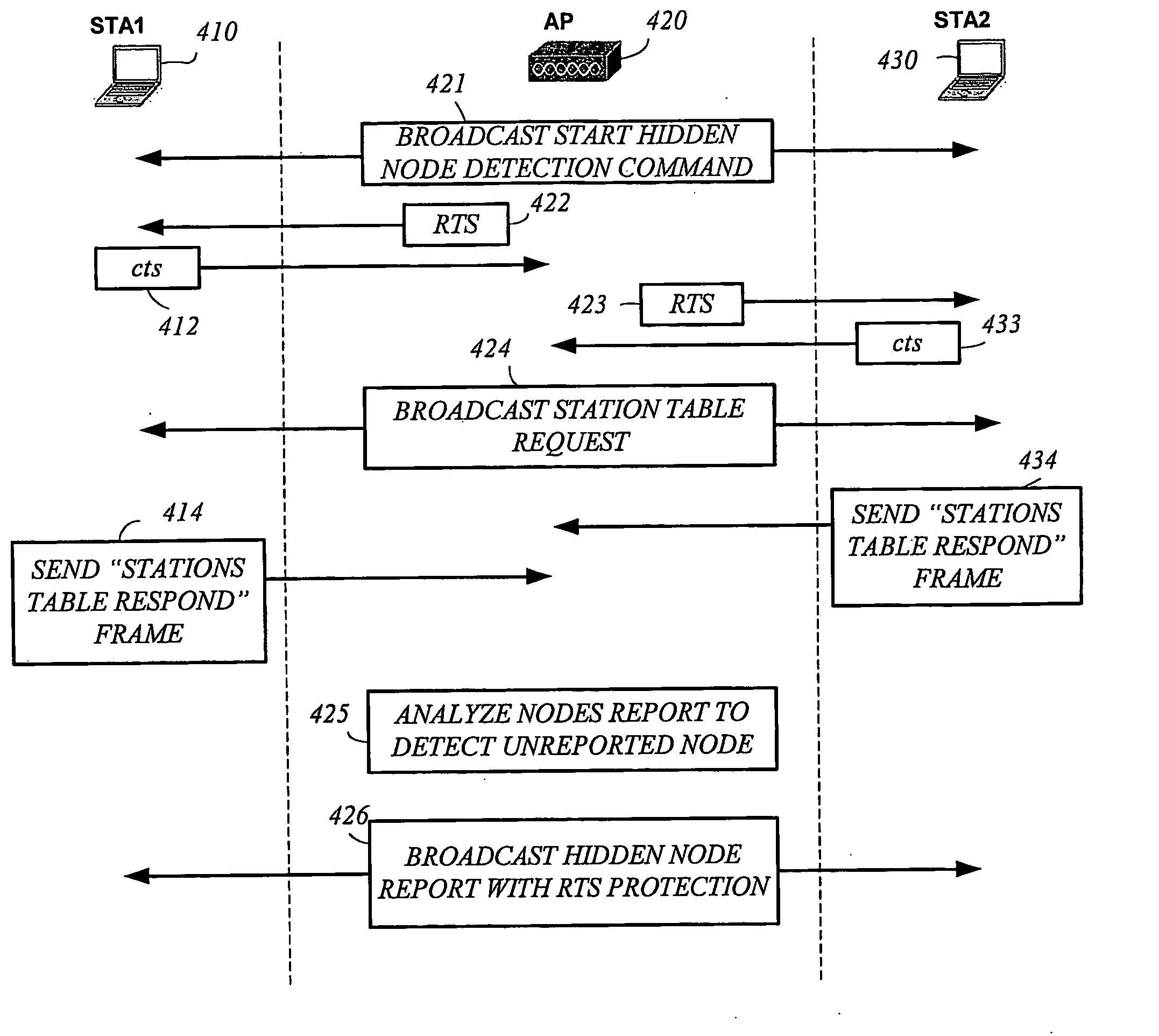
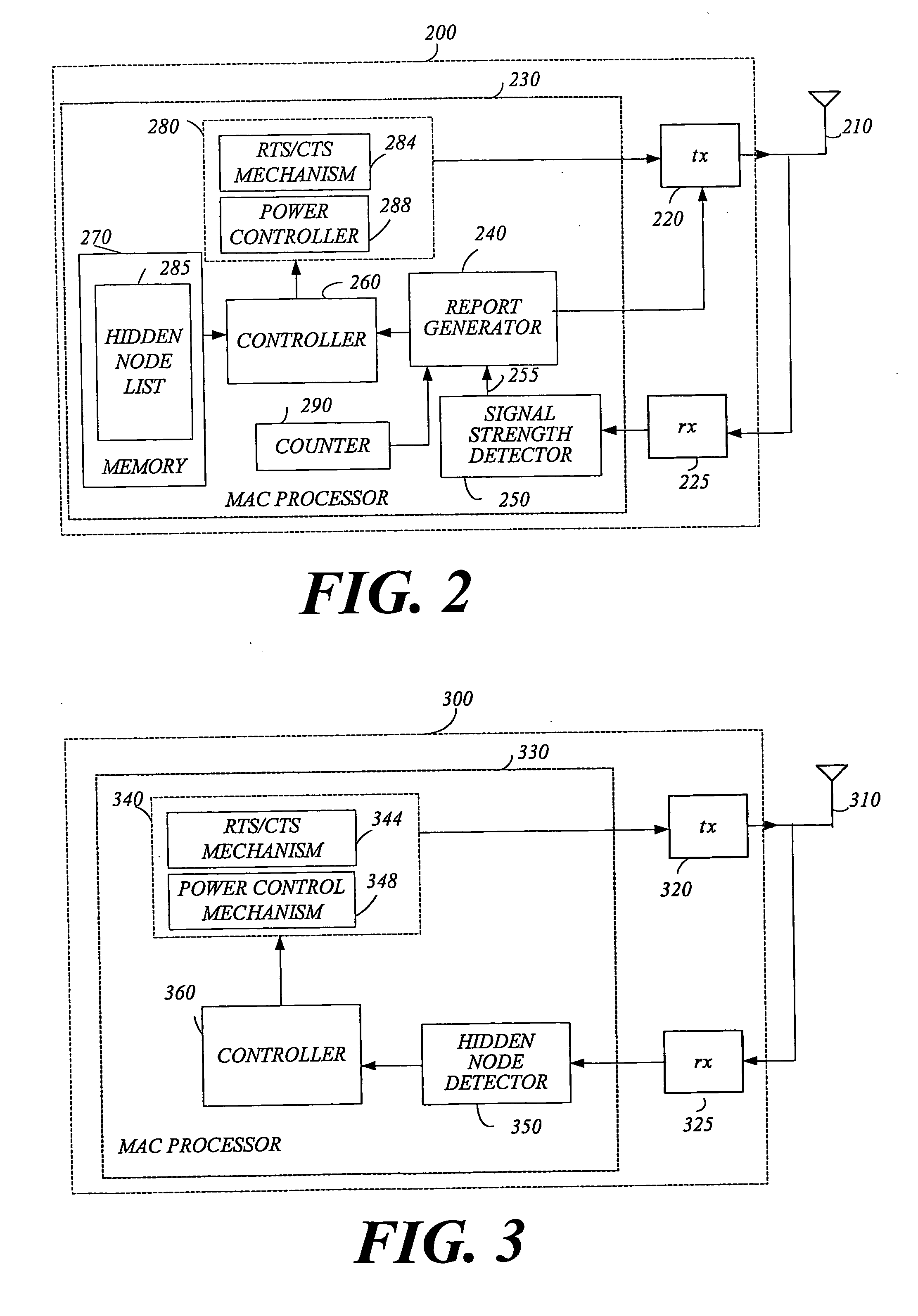
Method and apparatus to provide hidden node protection
InactiveUS20050213601A1Network topologiesRadio/inductive link selection arrangementsComputer networkProtection mechanism
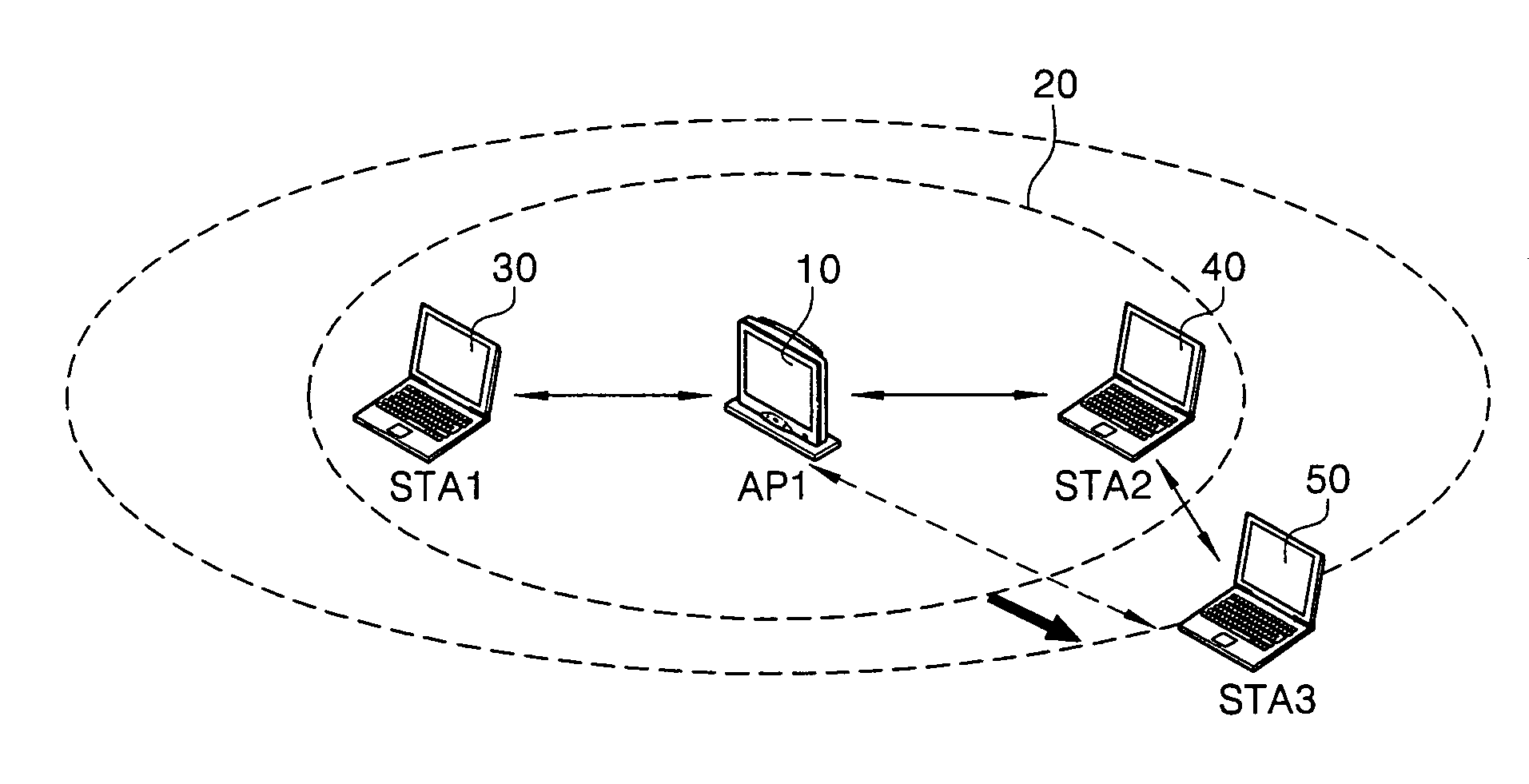
Briefly, a method and apparatus that may detect hidden nodes in BSS based on a hidden node report that may be generated in an access point based on nodes reports received from stations of the BSS. The access point may enable and / or disable a hidden node protection mechanism and / or may control the transmit power of the stations.
Owner:INTEL CORP
Crowd abnormity detection and positioning system and method based on time recurrent neural network
InactiveCN104636751AHigh detection efficiencyImprove real-time performanceBiological neural network modelsCharacter and pattern recognitionNODALCrowds
The invention discloses a crowd abnormity detection and positioning system and a crowd abnormity detection and positioning method based on a time recurrent neural network. The method comprises the steps of carrying out gridding division on a scene on the basis of preprocessing acquired sample data, and dividing a video fragment consisting of n frames into a plurality of time-space blocks; then constructing a multi-scale optical flow histogram and Gabor wavelet texture features in each time-space block; vectoring and combining the features in the multiple time-space blocks, finding out a relation between a space dimension and a time dimension by taking the video fragment as a time sequence through respectively using hidden nodes and feedback nodes of the time recurrent neural network, and training a time recurrent neural network model capable of detecting a long dependency relation; finally detecting and positioning a crowd abnormity by the model. The method is higher in instantaneity and accuracy, and can detect abnormities activated by a small quantity of individuals or a large quantity of individuals.
Owner:GUANGDONG UNIV OF TECH
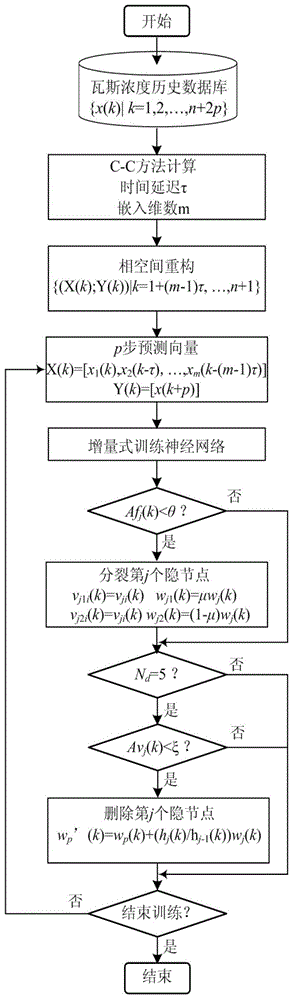
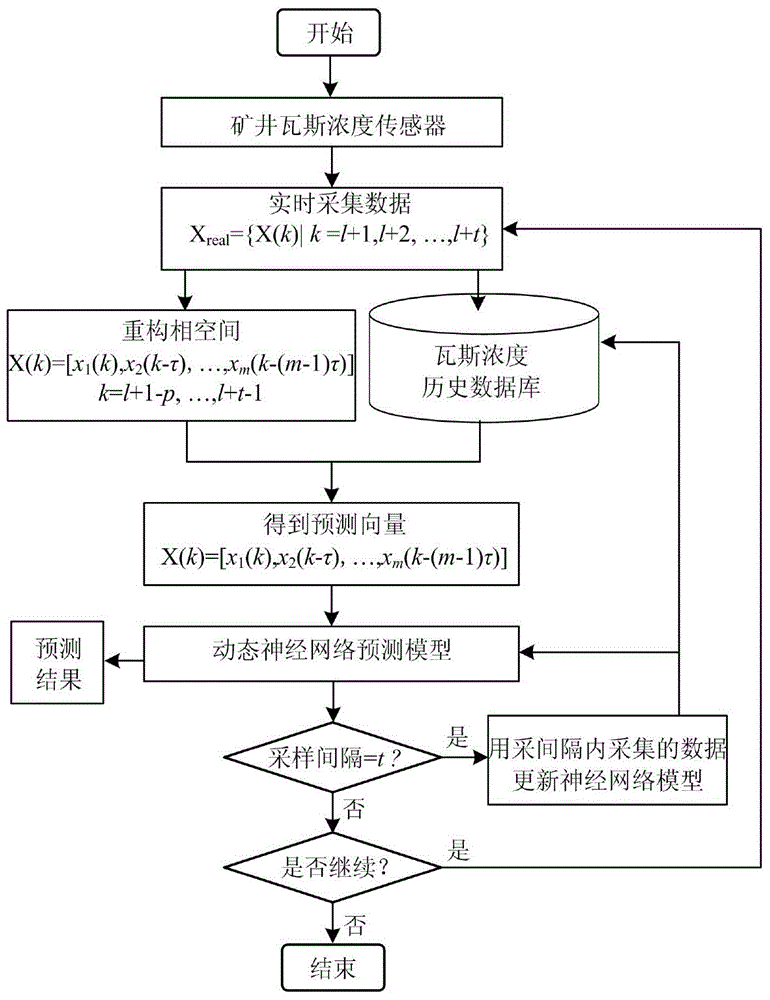
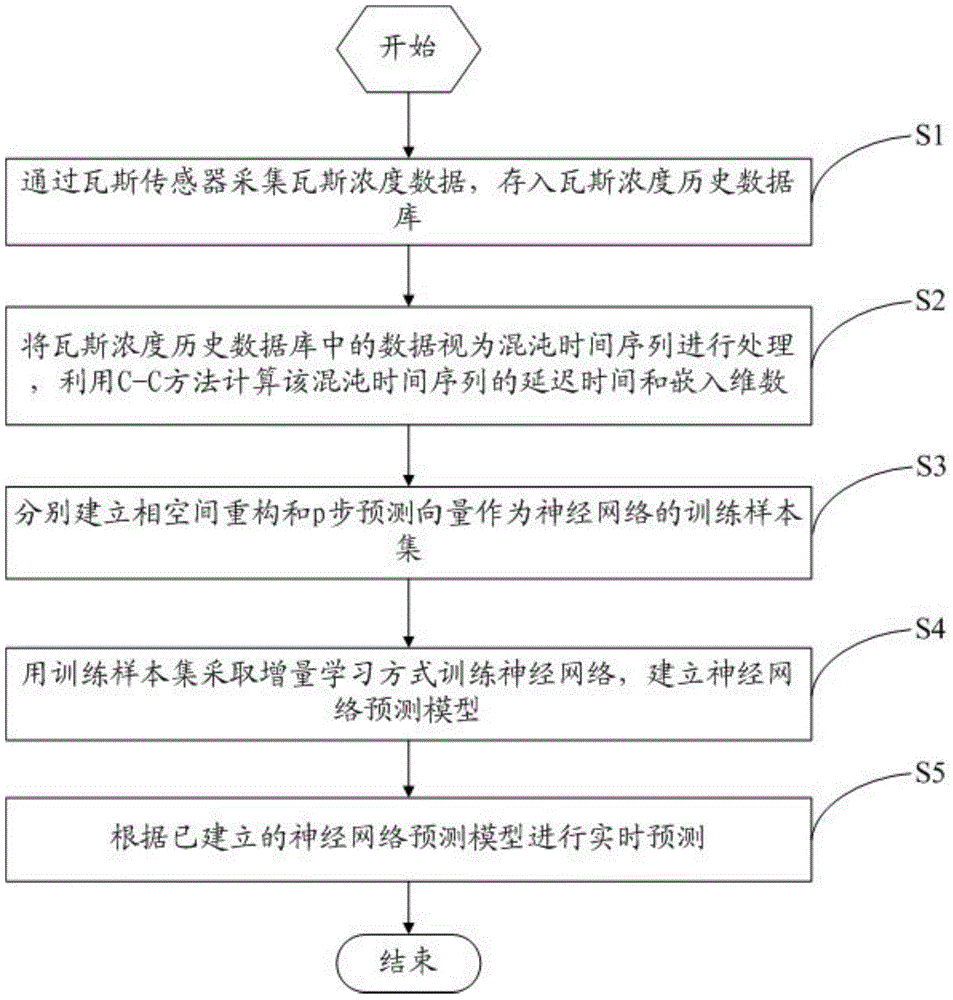
Gas concentration real-time prediction method based on dynamic neural network
InactiveCN104156422AImprove real-time performanceImprove stabilityMining devicesForecastingEngineeringArtificial intelligence
The invention provides a gas concentration real-time prediction method based on a dynamic neural network. Firstly, the neural network is trained by means of data in a mine gas concentration historical database, activeness of hidden nodes of the network and learning ability of each hidden node are dynamically judged in the network training process, splitting and deletion of the hidden nodes of the network are achieved, and a network preliminary prediction model is built; secondly, mine gas concentration information is continuously collected in real time and input into the prediction model of the neutral network to predict the change tendency of gas concentration in the future, and the network is trained timely through predicted real-time data according to the first-in first-out queue sequence to update a neutral network structure in real time, so that the neutral network structure can be adjusted according to real-time work conditions to improve gas concentration real-time prediction precision. According to the method, the neural network structure can be adjusted timely on line according to the real-time gas concentration data, so that gas concentration prediction precision is improved, and the technical requirements of a mine gas concentration information management system are met.
Owner:LIAONING TECHNICAL UNIVERSITY
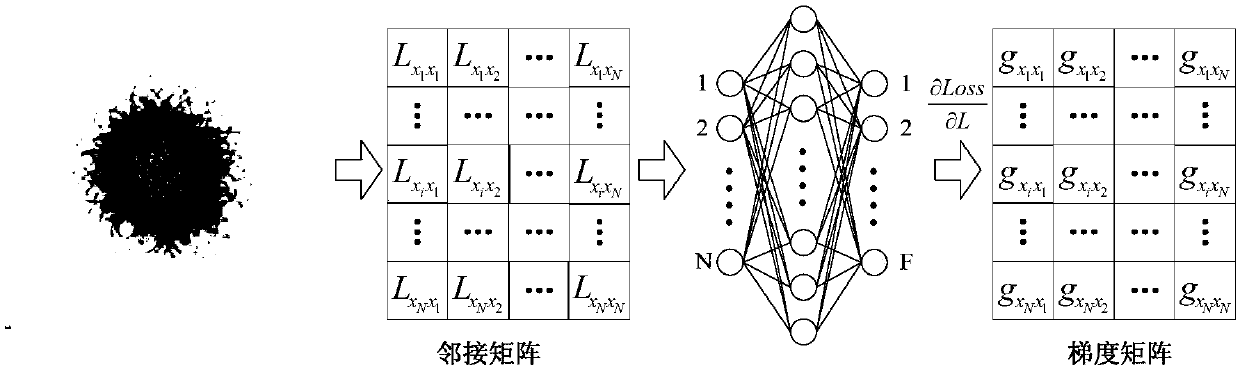
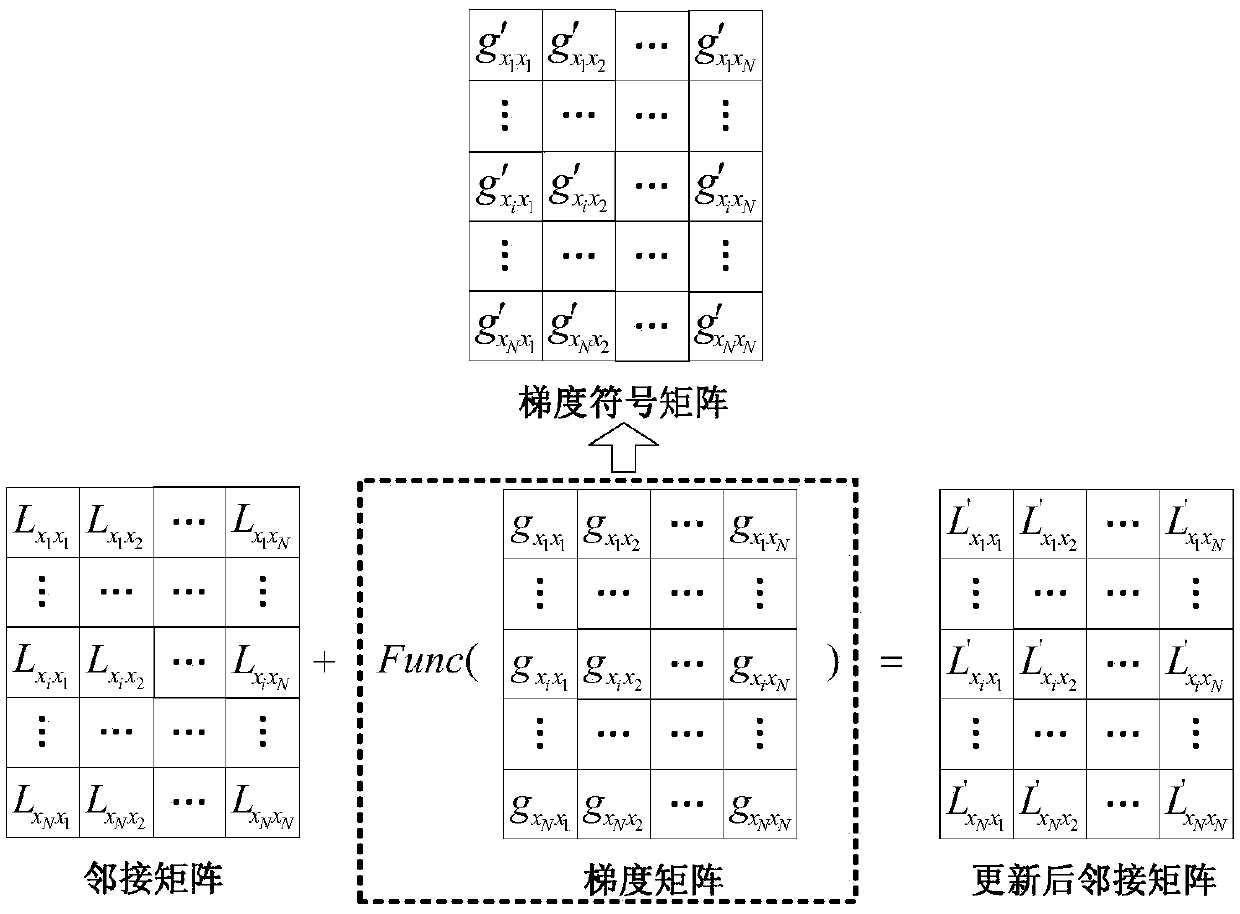
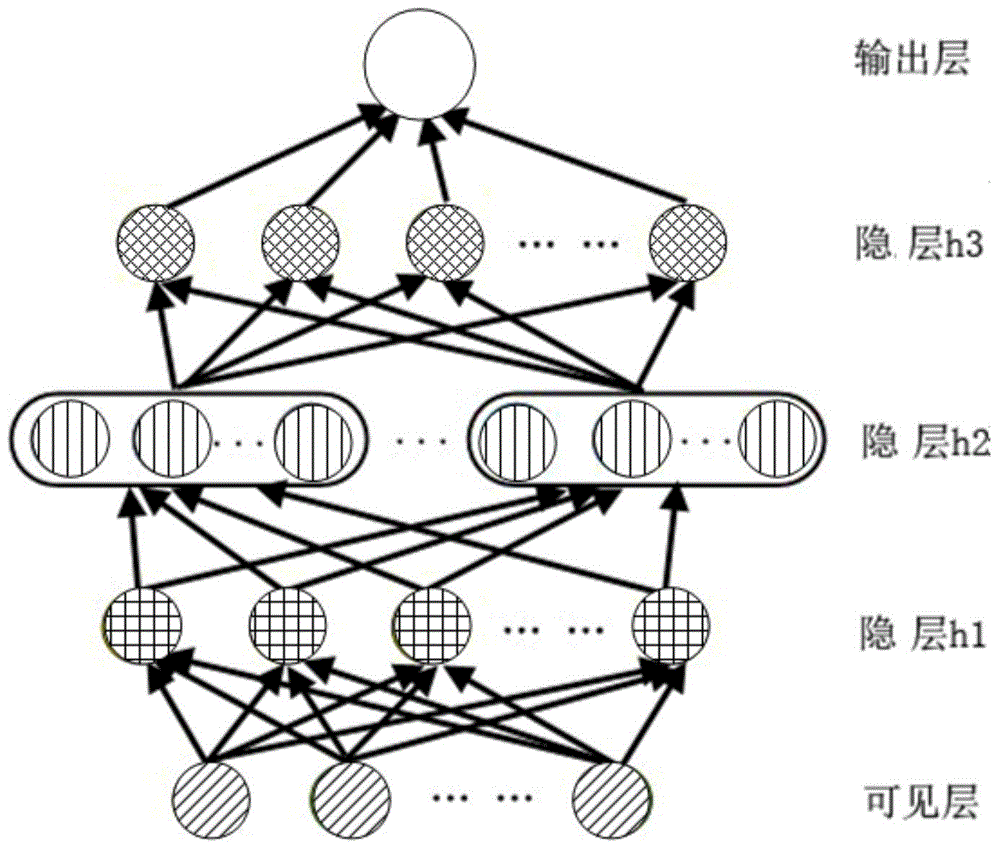
Graph convolutional network gradient-based node information hiding method
PendingCN108648095AAccurate classificationAchieve hiddenData processing applicationsCharacter and pattern recognitionNODALAlgorithm
The invention discloses a graph convolutional network gradient-based node information hiding method. The method comprises the steps of (1) constructing a network graph, constructing an adjacent matrixaccording to a connected edge set corresponding to the network graph, and preprocessing the adjacent matrix; (2) constructing and training a graph convolutional network model, and determining final weight information of the graph convolutional network model; (3) according to the final weight information, building an objective function based on a goal of ensuring non-target node classification tobe accurate as far as possible and enabling target node classification to be wrong, and calculating a connected edge gradient matrix corresponding to the adjacent matrix by utilizing the objective function; (4) according to a set gradient threshold, symbolizing the connected edge gradient matrix to obtain a connected edge gradient symbol matrix; and (5) updating the adjacent matrix by utilizing the connected edge gradient symbol matrix to hide node information. According to the method, the target node information of a network can be hidden under the condition of slightly changing the structureof the network as far as possible.
Owner:ZHEJIANG UNIV OF TECH
Receiver-initiated multiple access for ad-hoc networks (RIMA)
ActiveUS6996074B2Improve efficiencyOvercome problemsNetwork traffic/resource managementTransmission control/equalisingCarrier signalDual purpose
Receiver-initiated collision avoidance methods for use in ad-hoc wireless networks in which carrier sensing is available. A number of protocol variants are described including RIMA-SP (simple polling), RIMA-DP (dual-purpose polling), and RIMA-BP (broadcast polling). These handshake methods according to the invention are capable of correctly avoiding collisions within a network that contains hidden nodes, and the RIMA-DP protocol provides higher performance levels than attainable with existing handshaking protocols within the ad-hoc wireless networks. The use of dual-purpose polling allows a control packet to be sent which has alternative functions, such as requesting data from the polled node, if available, and if not available then providing a transmission request from the polling node to send data to the polled node.
Owner:RGT UNIV OF CALIFORNIA
Method and system for setting routing path considering hidden node and carrier sense interference, and recording medium thereof
ActiveUS20110075578A1Improve network performanceReduce network overheadError preventionFrequency-division multiplex detailsHidden node problemWireless mesh network
Disclosed are a method and a system for setting a routing path in consideration of hidden nodes and carrier sense interference.The method of setting a routing path for transmitting a packet from a source node to a destination node in a wireless multi-hop network consisting of plural nodes and plural links for connecting two nodes with each other, comprises: calculating carrier sense interference weights representing carrier sense interference related to the respective links and combining the carrier sense interference weights of the links included in at least one specific path connecting the source node with the destination node; calculating hidden node weights representing hidden node problems related to the respective links and accumulating the hidden node weights of the links included in the path; and calculating a metric value for the specific path by combining the carrier sense interference weights and the hidden node weights, and determining the specific path with the least metric value as the routing path.Accordingly, in the multi-channel multi-radio wireless mesh network, the path with minimized hidden node problem and carrier sense interference can be selected to improve network performance
Owner:KOREA ADVANCED INST OF SCI & TECH
System and method for controlling transmission power in wireless local area network
InactiveUS7570969B2Limit transmission powerPower managementNetwork topologiesTelecommunicationsLink margin
Disclosed are a system and method for controlling transmission power in a wireless local area network (WLAN), and more particularly, a system and method for controlling transmission power in a WLAN that are capable of providing a WLAN service to terminals outside a service area by controlling the transmission power in the WLAN. Thus, link margin data of a station positioned at a hidden node of the WLAN is received from another station positioned in a service area, and the received link margin data is compared with preset link margin data for control of the transmission power in the WLAN.
Owner:SAMSUNG ELECTRONICS CO LTD
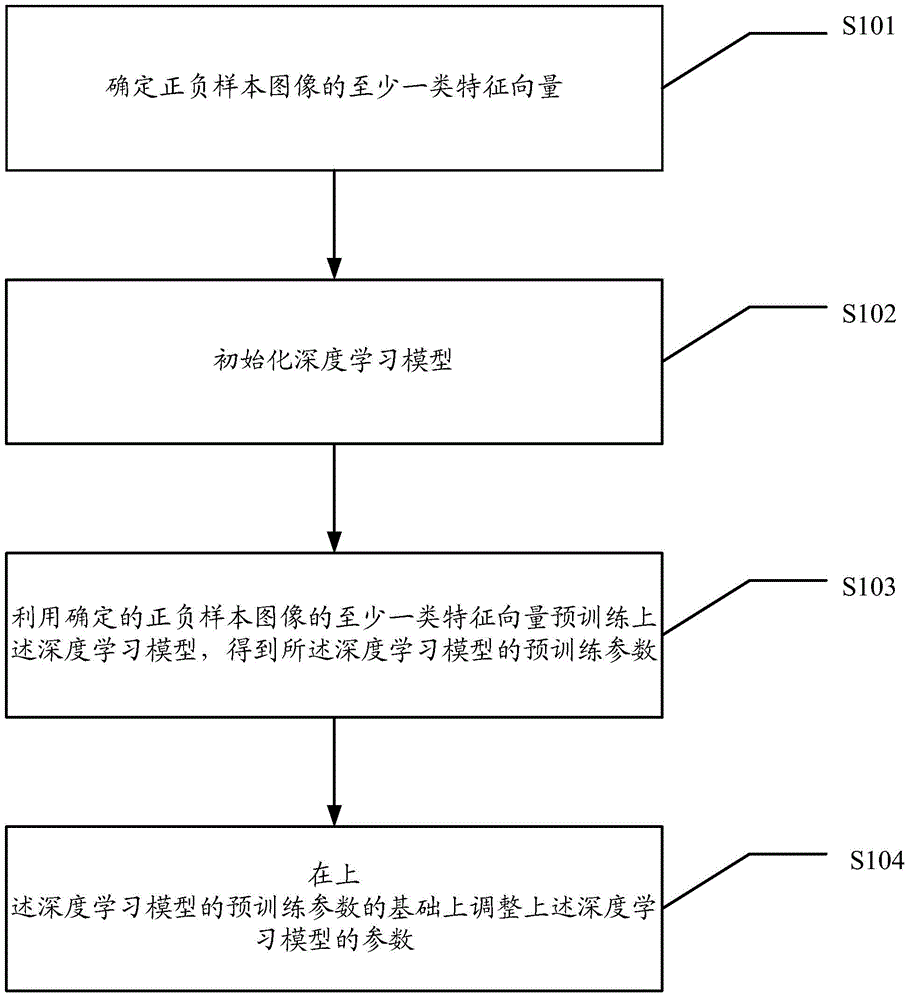
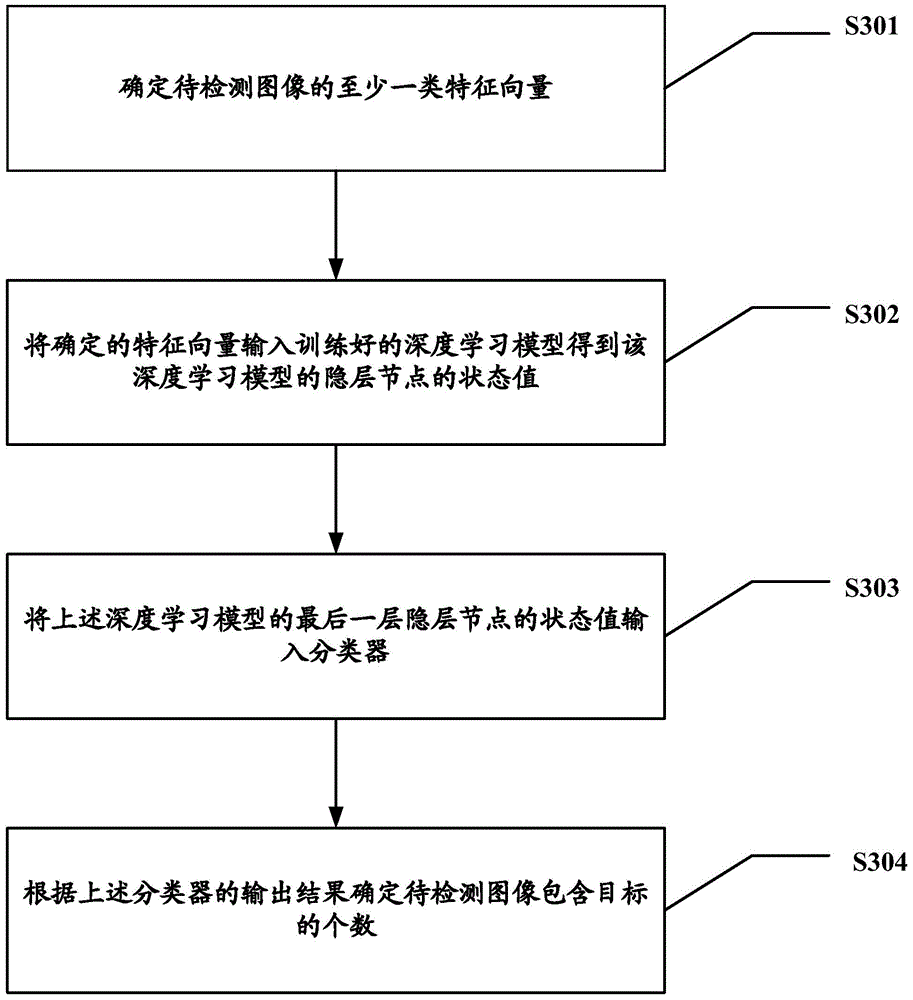
Target detection method and device
The embodiment of the invention provides a target detection method and device. The target detection method and device are used for solving the problem that according to an existing pedestrian detecting method, the detection precision is low when multiple targets are detected. The target detection method comprises the steps that at least one type of feather vectors of an image to be detected are determined, the determined feature vectors are input into a trained deep learning model so that the state values of hidden nodes of the deep learning model can be obtained, the state value of the last hidden node of the deep learning model is input into a classifier, and the number of targets contained in the image to be detected is determined according to an output result of the classifier.
Owner:CHINA SECURITY & FIRE TECH GRP +1
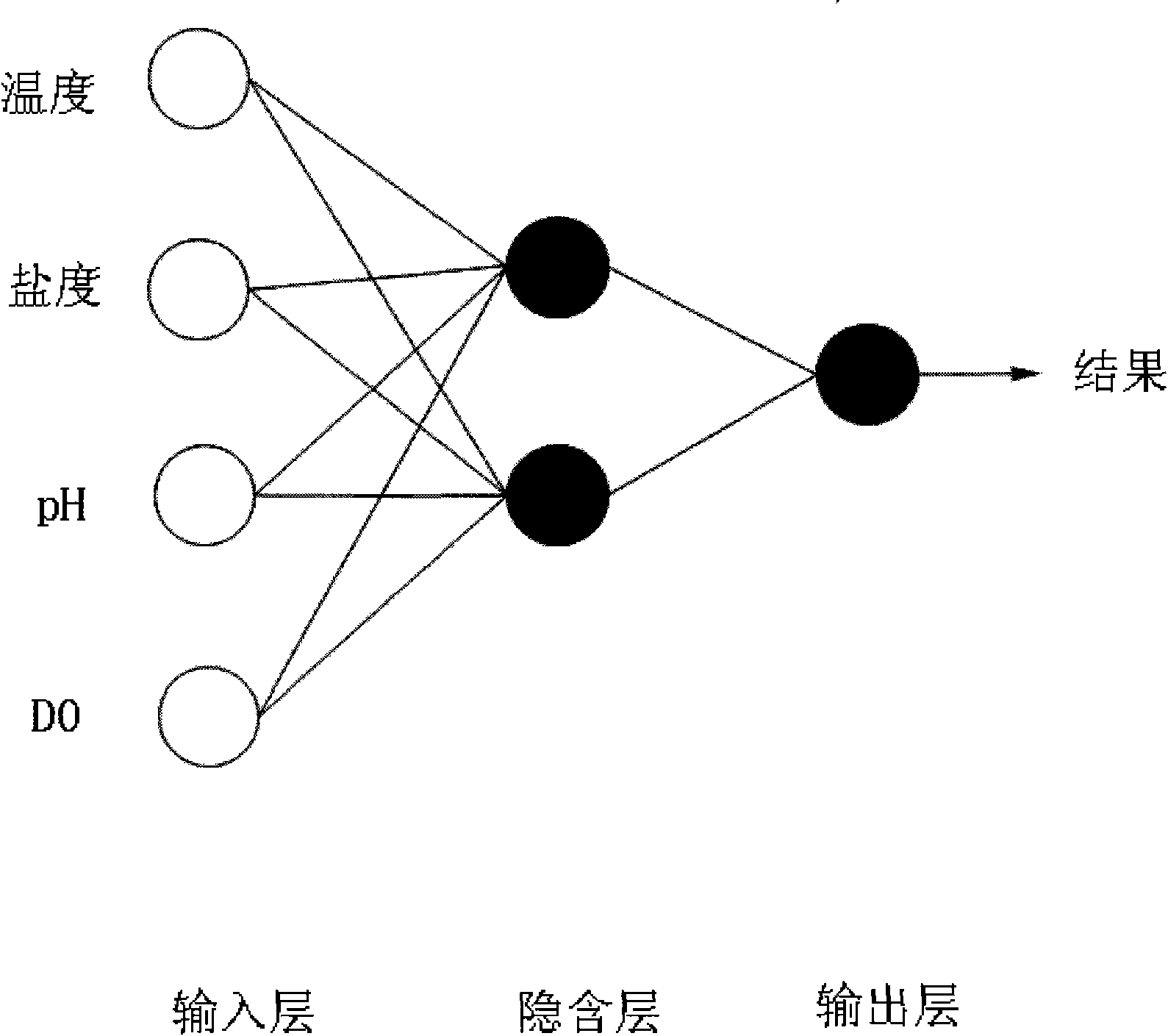
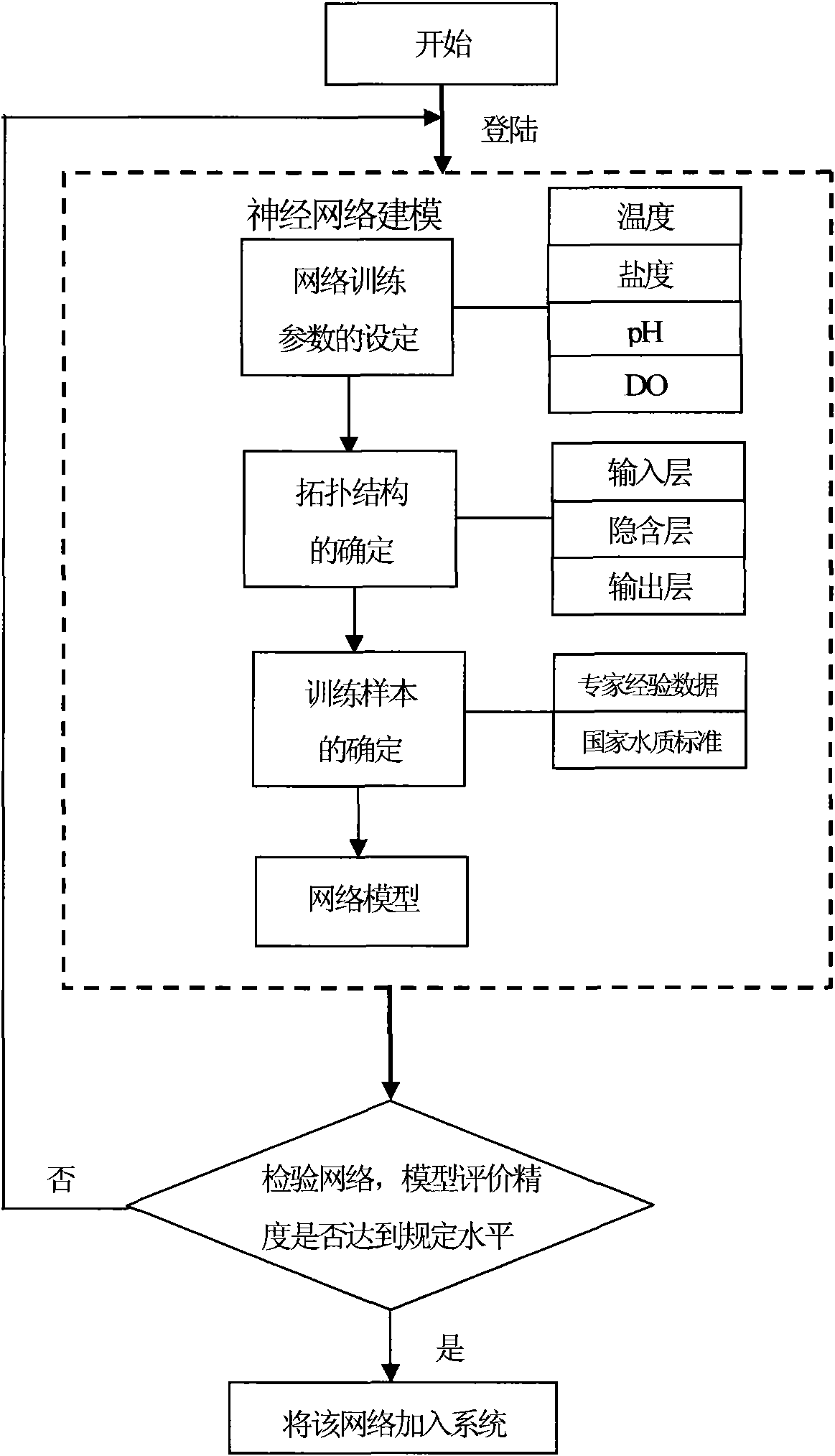
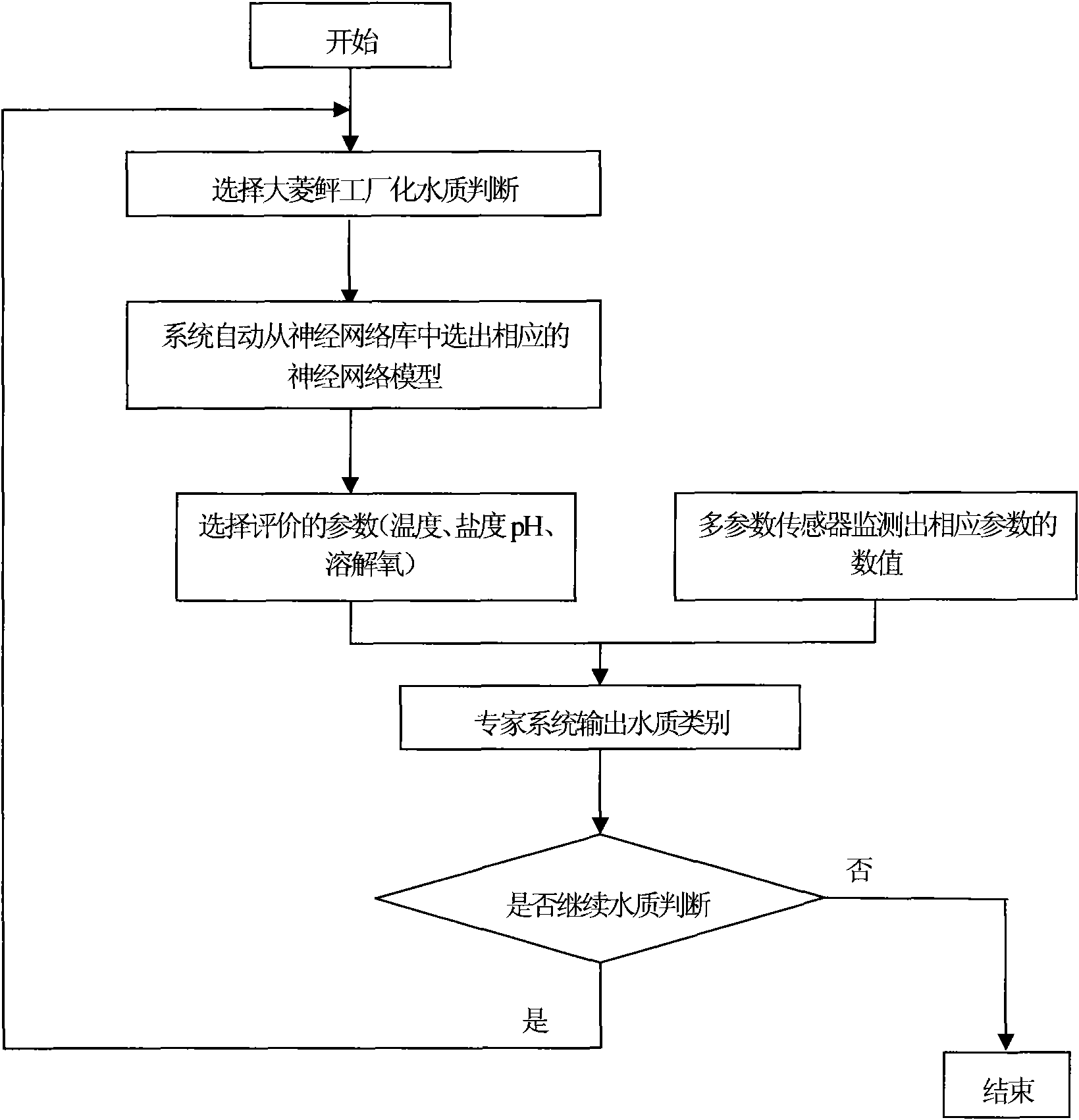
Construction method of fuzzy neural network expert system for water quality assessment in turbot culture
InactiveCN101793887AAvoid influenceAdaptive strongBiological neural network modelsTesting waterNODALSensitive index
The invention relates to a construction method of a fuzzy neural network expert system for the water quality assessment in turbot culture, which comprises neural network modeling and network model testing. The method is characterized in that the neural network modeling comprises the following steps of: setting network training parameters, wherein sensitive indexes of the growth of turbots after three-tiered classification, which include four expert data of temperature, salinity, pH and dissolved oxygen, are used as input parameters; determining the network topology: constructing a three-layer neural network by using the input layers of four input nodes, the hidden layers of two hidden nodes and the output layer of one output node; and determining training samples. The network model testing comprises the steps of: leading in tested samples and assessing the network model. The invention combines the neural network, the fuzzy system and the on-line monitoring system for the water quality assessment in industrial turbot culture for the first time, avoids the operations such as manual setting and the like in the traditional assessment method, and overcomes the influence of human factors and the like on the assessment in the traditional turbot water quality assessment.
Owner:YELLOW SEA FISHERIES RES INST CHINESE ACAD OF FISHERIES SCI
Methods, Systems and Computer Program Products for Controlling Tree Diagram Graphical User Interfaces and/or For Partially Collapsing Tree Diagrams
InactiveUS20070198930A1Execution for user interfacesInput/output processes for data processingGraphicsData set
Methods for selectively displaying portions of a hierarchical data set on an electronic display comprise the steps of displaying at least a portion of the hierarchical data set on an electronic display in a tree diagram format. Input may then be obtained from a user to identify one or more displayed nodes in the tree diagram that are to be hidden and / or one or more hidden nodes in the tree diagram that are to be displayed. Based on this input, at least one node in the tree diagram is partially collapsed and / or at least one node in the tree diagram may be partially expanded so as to display the hidden nodes identified by the user and so as to hide the displayed nodes identified by the user.
Owner:INT BUSINESS MASCH CORP
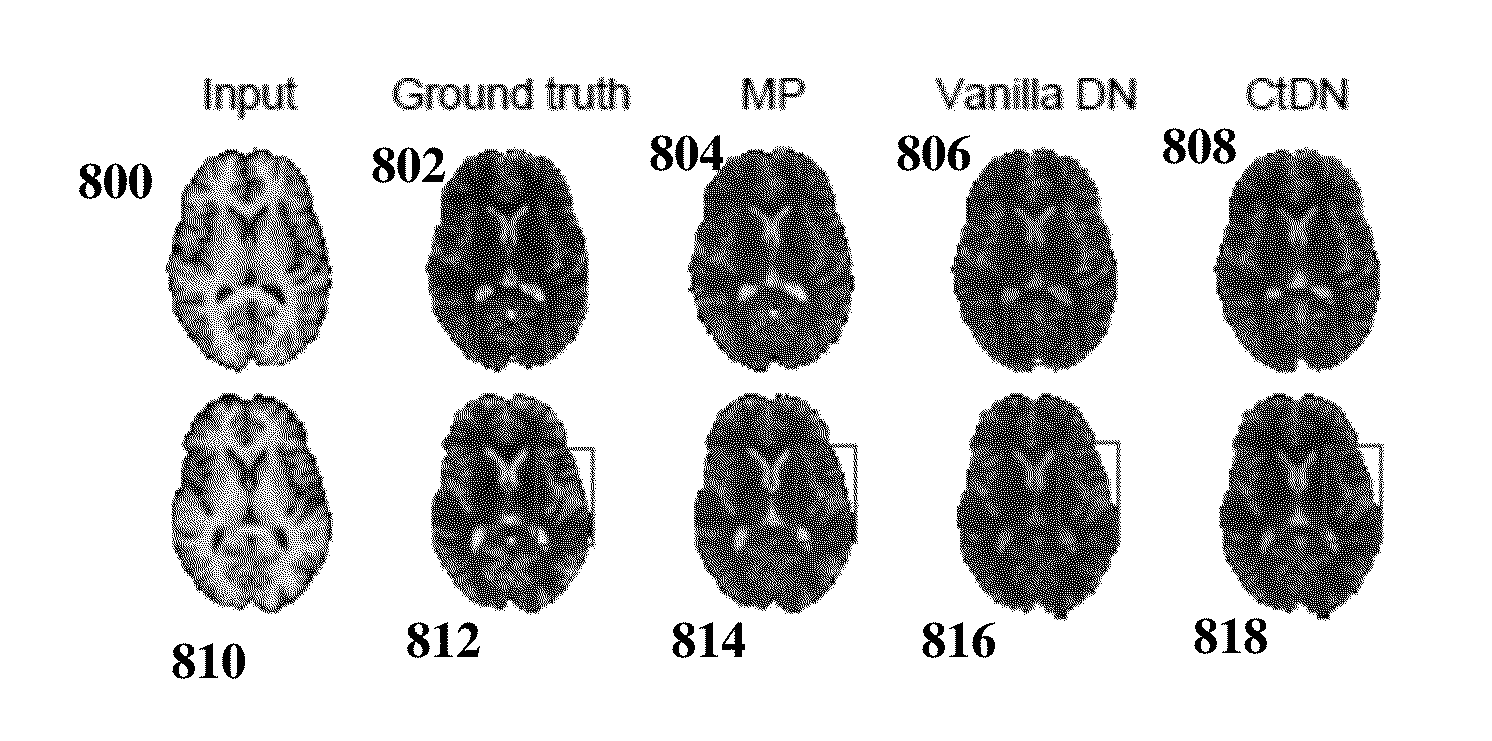
Method and system for cross-domain synthesis of medical images using contextual deep network
A method and apparatus for cross-domain medical image synthesis is disclosed. A source domain medical image is received. A synthesized target domain medical image is generated using a trained contextual deep network (CtDN) to predict intensities of voxels of the target domain medical image based on intensities and contextual information of voxels in the source domain medical image. The contextual deep network is a multi-layer network in which hidden nodes of at least one layer of the contextual deep network are modeled as products of intensity responses and contextual response.
Owner:SIEMENS HEALTHCARE GMBH
Genetic algorithm based selection of neural network ensemble for processing well logging data
ActiveUS7280987B2Improve generalization abilityElectric/magnetic detection for well-loggingDigital computer detailsNegative errorNerve network
A system and method for generating a neural network ensemble. Conventional algorithms are used to train a number of neural networks having error diversity, for example by having a different number of hidden nodes in each network. A genetic algorithm having a multi-objective fitness function is used to select one or more ensembles. The fitness function includes a negative error correlation objective to insure diversity among the ensemble members. A genetic algorithm may be used to select weighting factors for the multi-objective function. In one application, a trained model may be used to produce synthetic open hole logs in response to inputs of cased hole log data.
Owner:HALLIBURTON ENERGY SERVICES INC
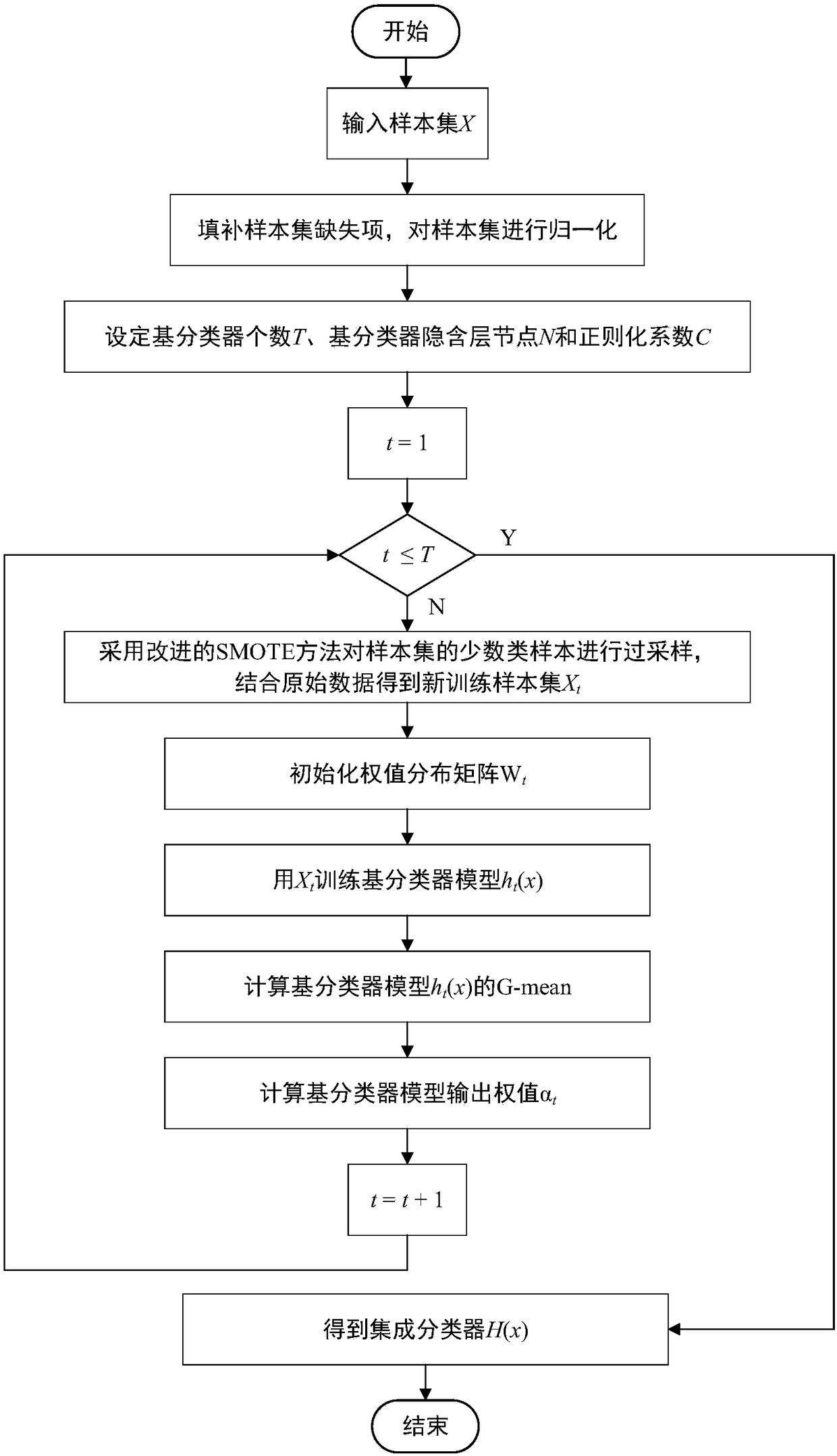
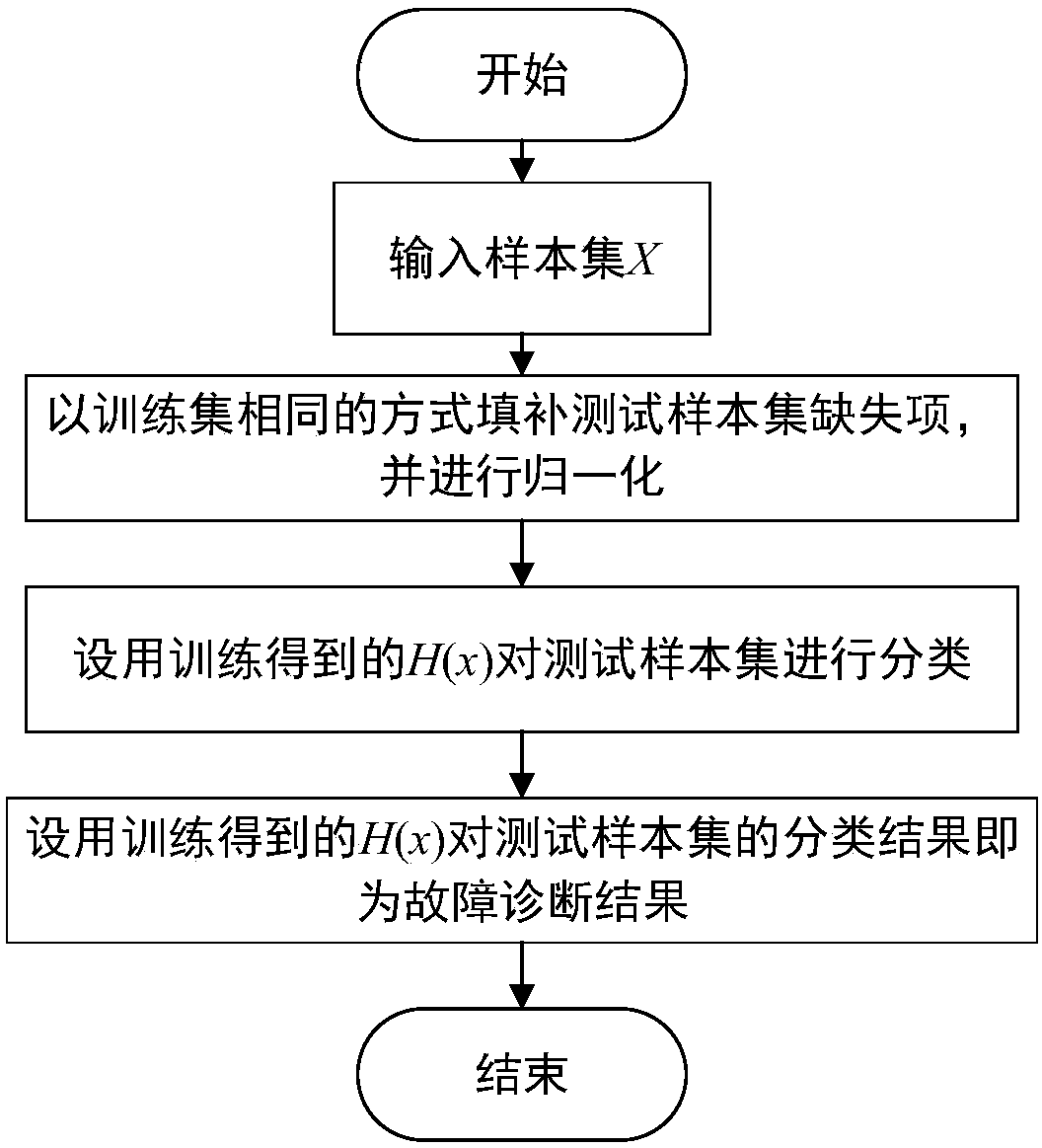
SMOTE_Bagging integrated sewage treatment fault diagnosis method based on weighted extreme learning machine
ActiveCN108228716AImprove stabilityReduce biasData processing applicationsRelational databasesDiagnosis methodsSewage
The invention discloses an SMOTE_Bagging integrated sewage treatment fault diagnosis method based on a weighted extreme learning machine, the method comprises the following steps that (1) the defect items of samples with incomplete attributes in sewage data are supplemented with an averaging method and normalized to be in an interval of [0,1]; (2) the number of base classifiers and the optimal parameters of hidden nodes of the base classifiers are set; (3) independent oversampling is performed to the training sample corresponding to each base classifier with an improved SMOTE algorithm aimingat each base classifier, and the base classifiers are trained; (4) the output weight of each classifier is determined on the basis of a G-mean method; (5) integration is performed to all base classifiers after training, and a final integration classifier is obtained. According to the SMOTE_Bagging integrated sewage treatment fault diagnosis method based on the weighted extreme learning machine, the diversity among the base classifiers is improved while the unbalancedness of sewage data is effectively reduced, the classification accuracy of sewage treatment fault classes is improved, and further the whole performance of fault diagnosis in the sewage treatment process is effectively improved.
Owner:SOUTH CHINA UNIV OF TECH
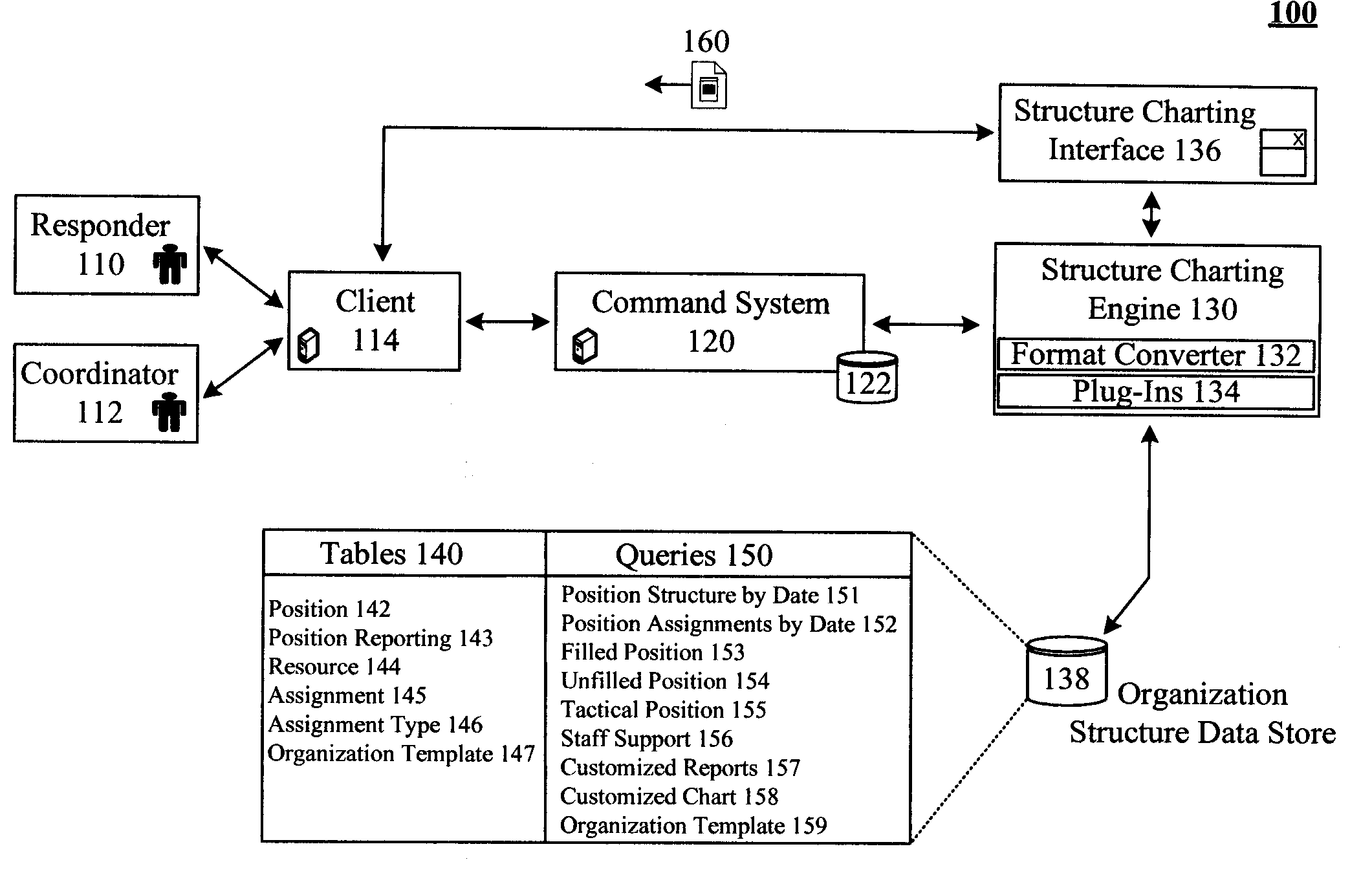
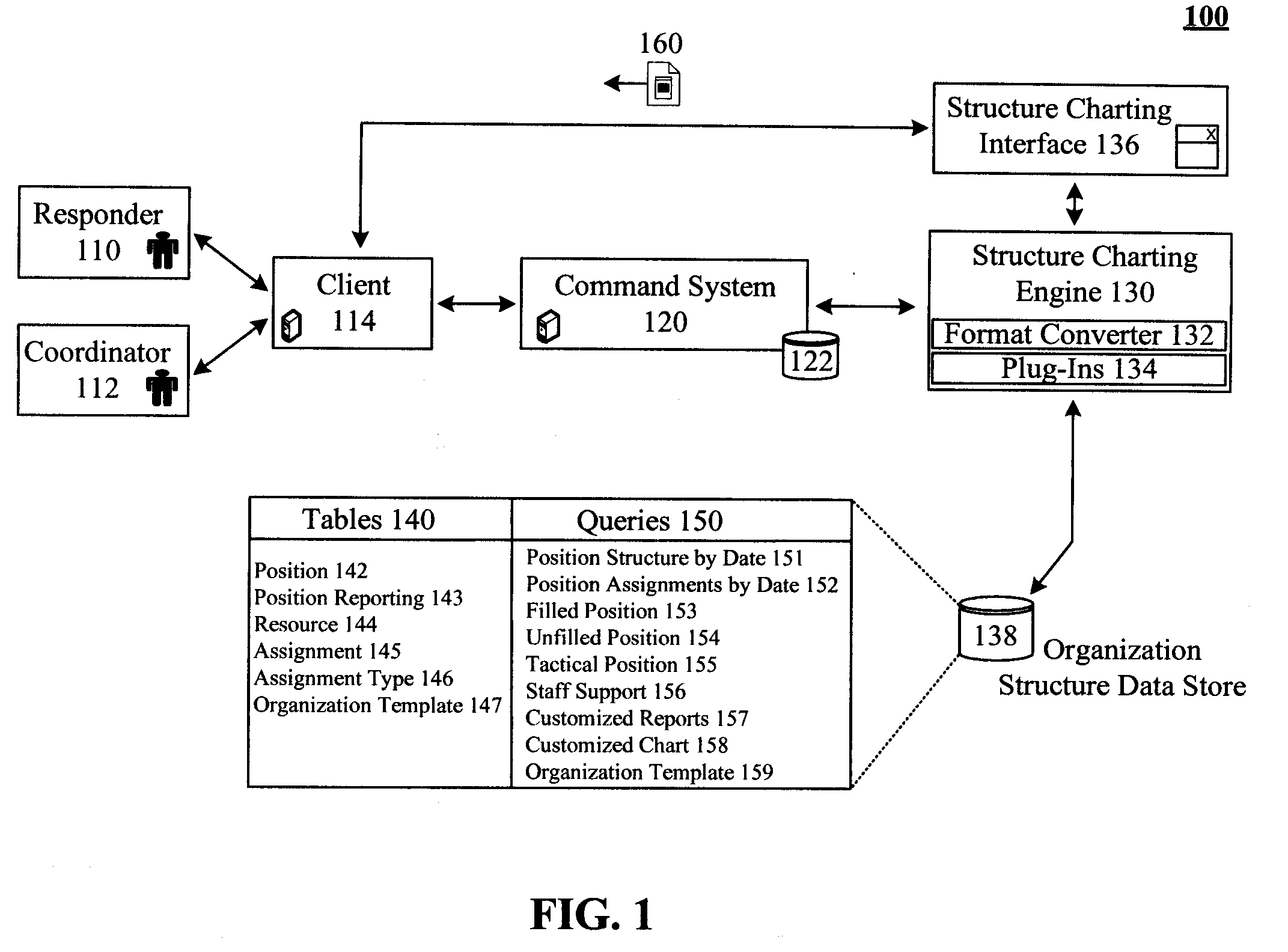
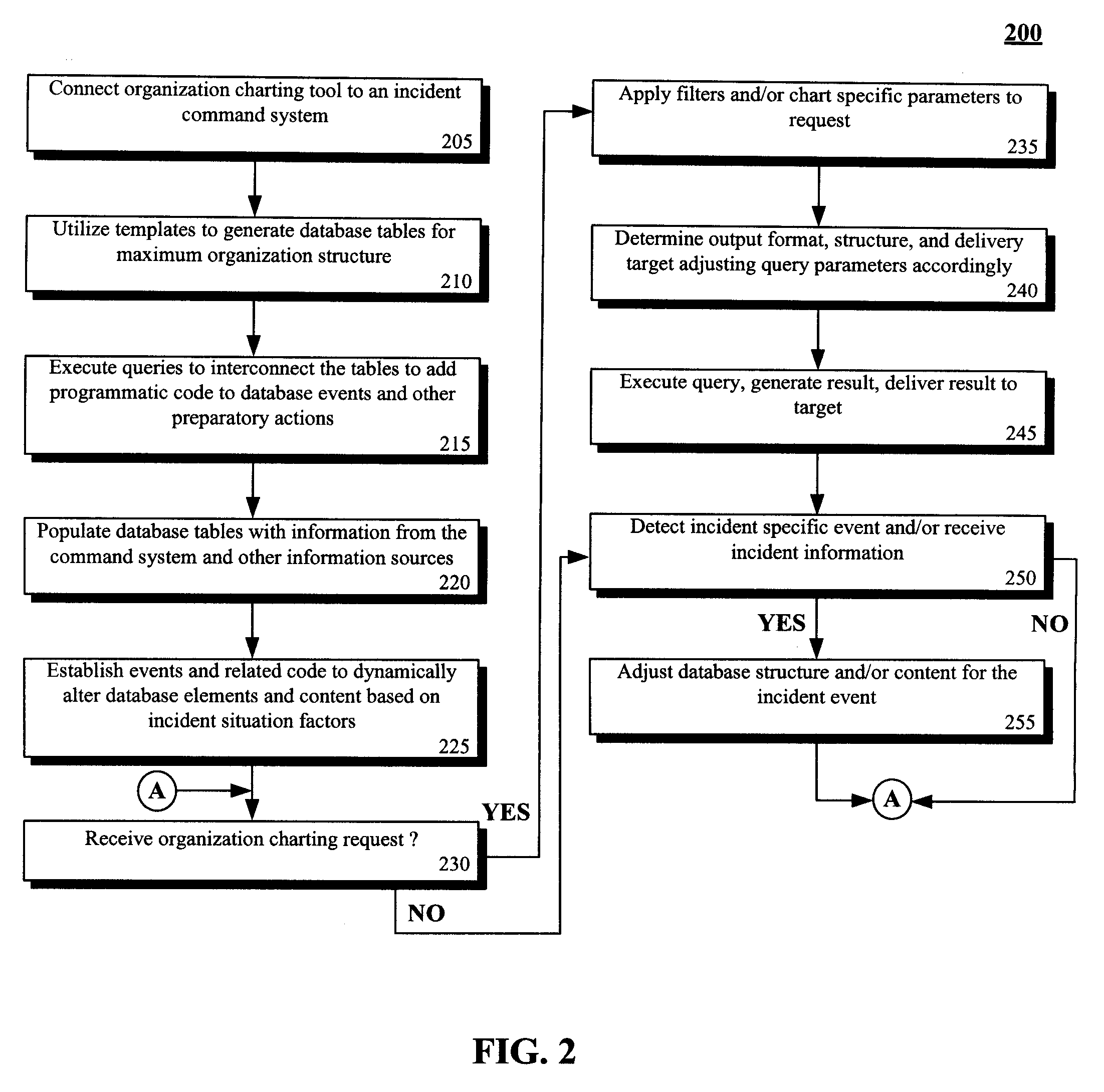
Storing and depicting organizations that are subject to dynamic event driven restructuring
ActiveUS20080300952A1Efficient storageEfficient managementMultiprogramming arrangementsResourcesApplication softwareComputer science
The present invention discloses a solution for storing and depicting complex non-contiguous organizations that are subject to situation-based restructuring. Different views for organization charts of the organization can be generated, where the generated organization charts are collapsed to a minimal view which automatically hides at least a portion of the organization positions in accordance with a desired view. For example, a view showing only filled positions will hide unfilled positions, collapsing intermediate nodes of a shown hierarchy so that child nodes of a hidden node are directly connected to the parent node of the hidden node. A set of indexed database tables can be used to efficiently store details of the organization. The indexed tables can store positions, assignment, and position reporting details in separate 3NF tables. The solution can be integrated to a commercial off-the-shelf command management system and / or to a commercial off-the-shelf front-end charting application.
Owner:IBM CORP
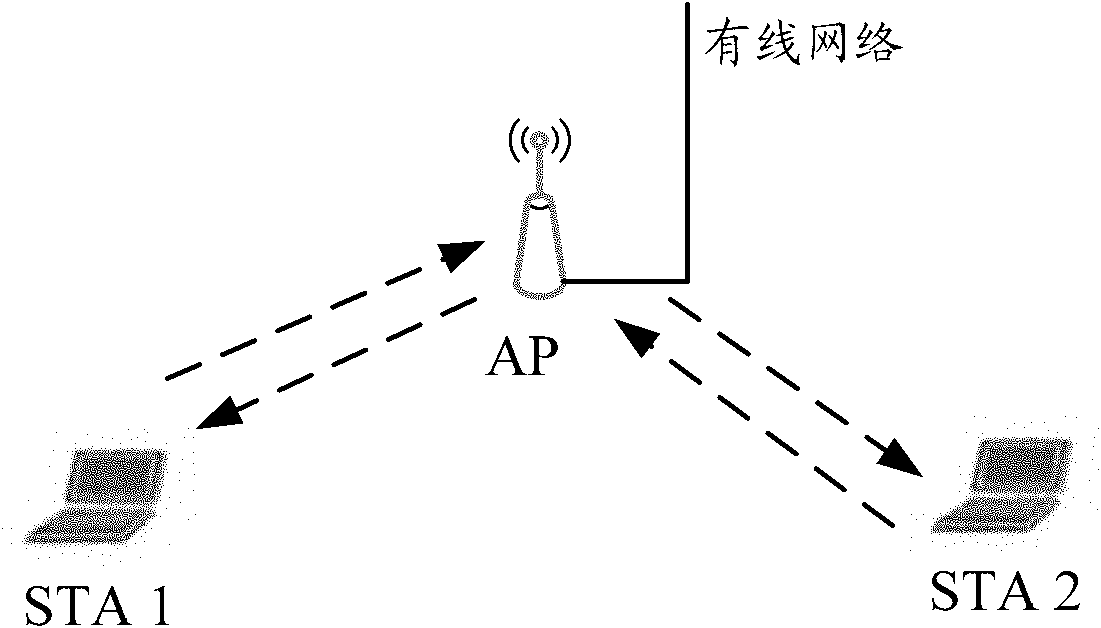
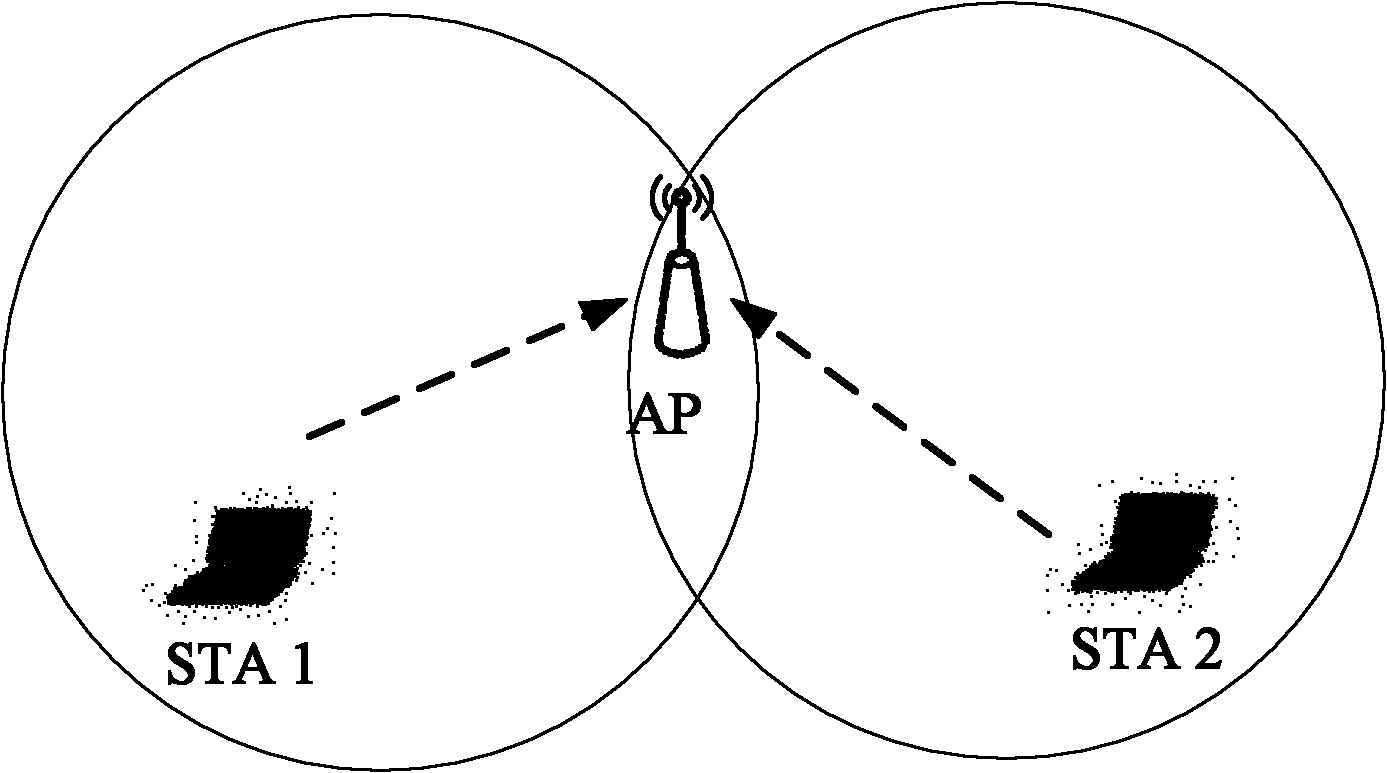
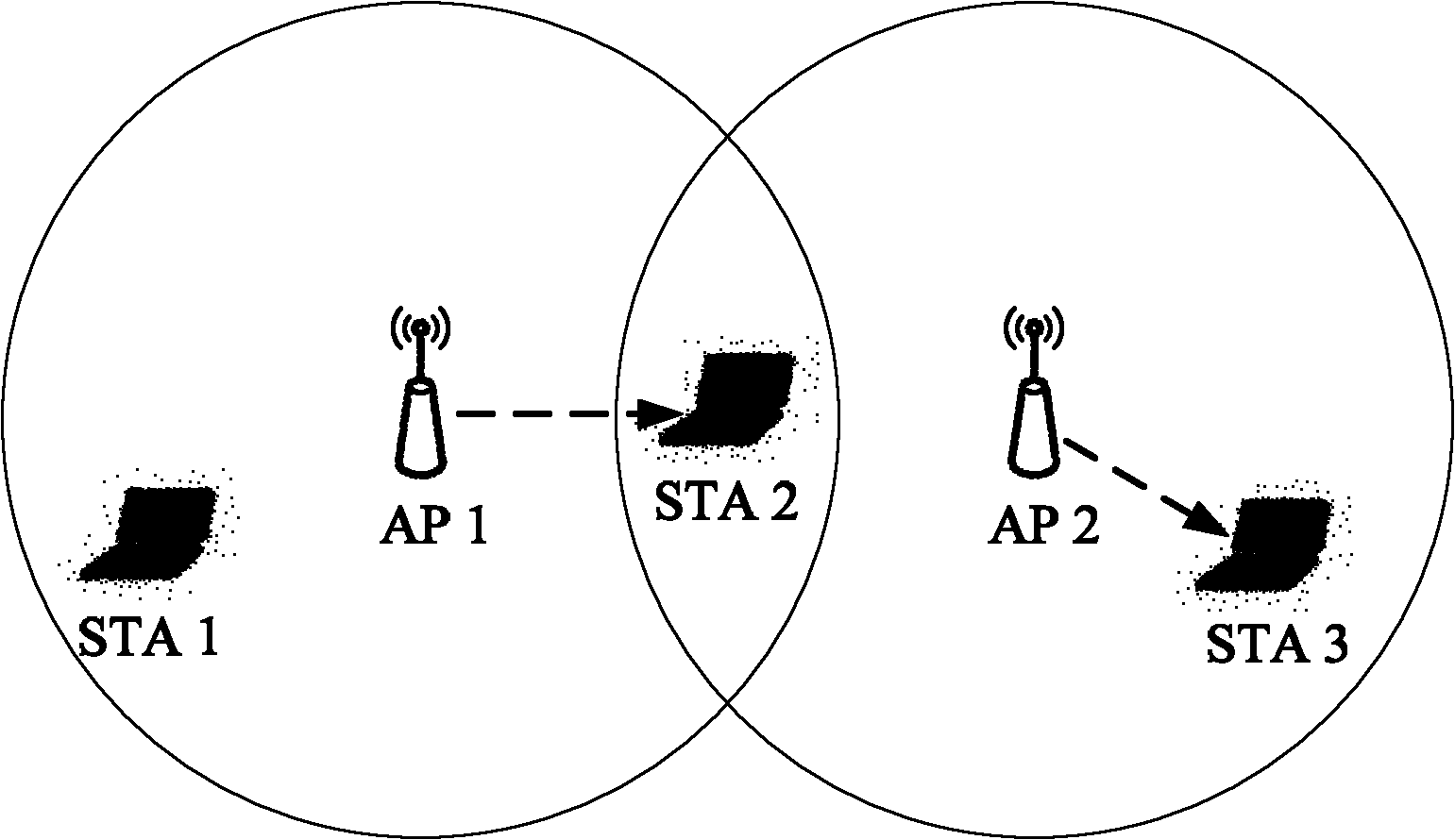
Hidden node detection method and equipment
InactiveCN102045745AImprove running qualityThe method is simple and accurateWireless communicationComputer scienceReal-time computing
The invention provides a hidden node detection method and equipment. The method comprises the steps of monitoring a signal of a station (STA) in a medium according to a received monitoring instruction, wherein the signal contains the node identification of the station which transmits the signal; if the node identification represents an isolation node of the node, judging whether the station is located in the overlapped coverage area of the node and the isolation node; and if yes, determining the isolation node to be a hidden node of the node. The node comprises a monitoring module, a judging module and a determining module. A node controller comprises a transceiving module, a judging module and a determining module. The scheme provided by the invention realizes accurate positioning of an access point (AP) belonging to the hidden node without changing the STA station.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Wireless Mesh network self-adapting routing method based on throughput performance
ActiveCN101296180AImpact of reduced throughputNetwork connectionsWireless communicationWireless mesh networkPacket loss
The invention discloses a wireless Mesh network self-adapting routing method based on throughput performance. Each node maintains a link quality database according to the packet loss ratio of probe packets by broadcasting the probe packets outwards and receiving the probe packets sent by neighbor nodes; a hidden node is introduced to the occupied weight and calculation of throughput; a database records the link quality information between the node and the neighbor nodes thereof and a metric value is used for expression; the metric value is used for calculating the quality of each specific route. A route request is flooded into the whole network as required, and a router having an optimal metric value is taken as an optimal router to be recorded by each node. By broadcasting gateway information, a gateway node maintains the knowability and accessibility in the whole wireless Mesh network, namely, the active trace of an egress router by all nodes. The method solves the problem of performance degradation caused by the insufficient consideration about the hidden node.
Owner:SHANGHAI MAXTROPY DATA TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com