Patents
Literature
93results about How to "Reduce the risk of attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
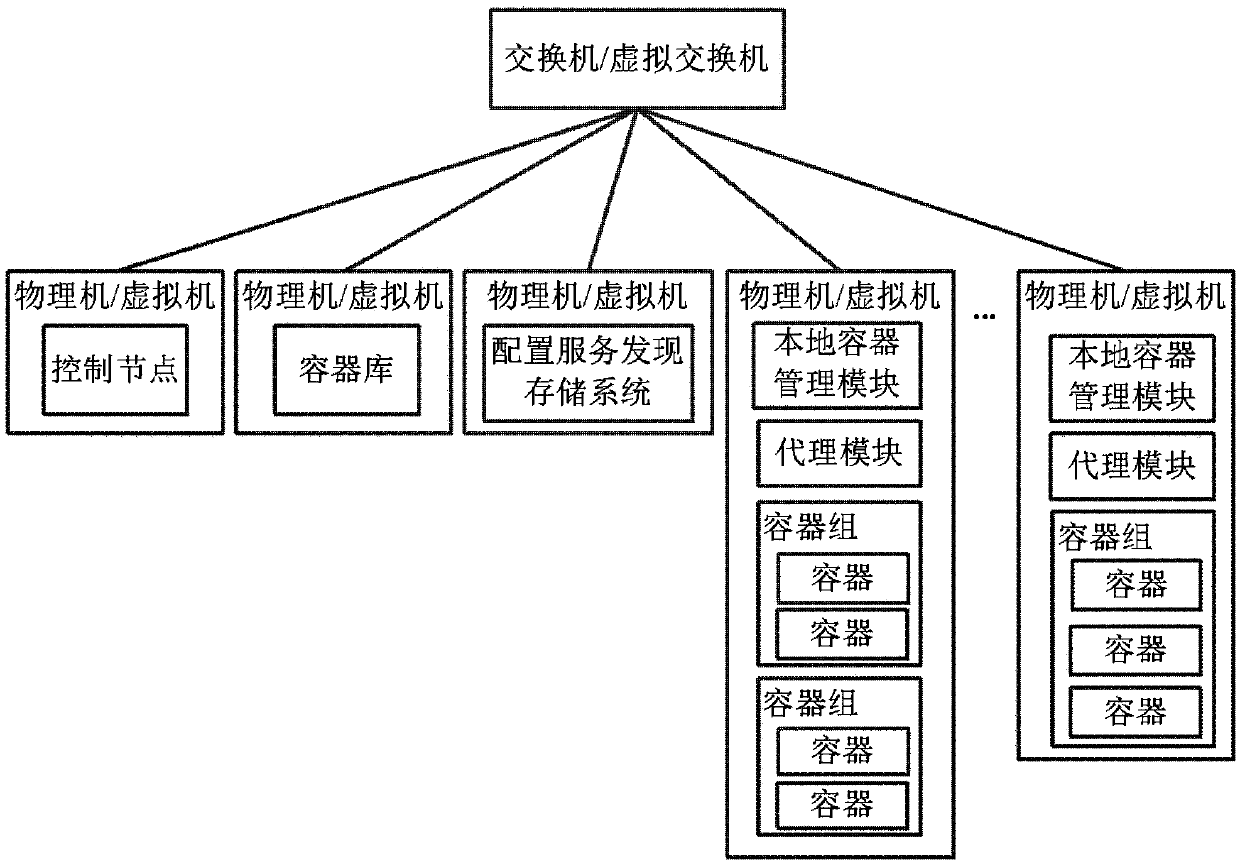
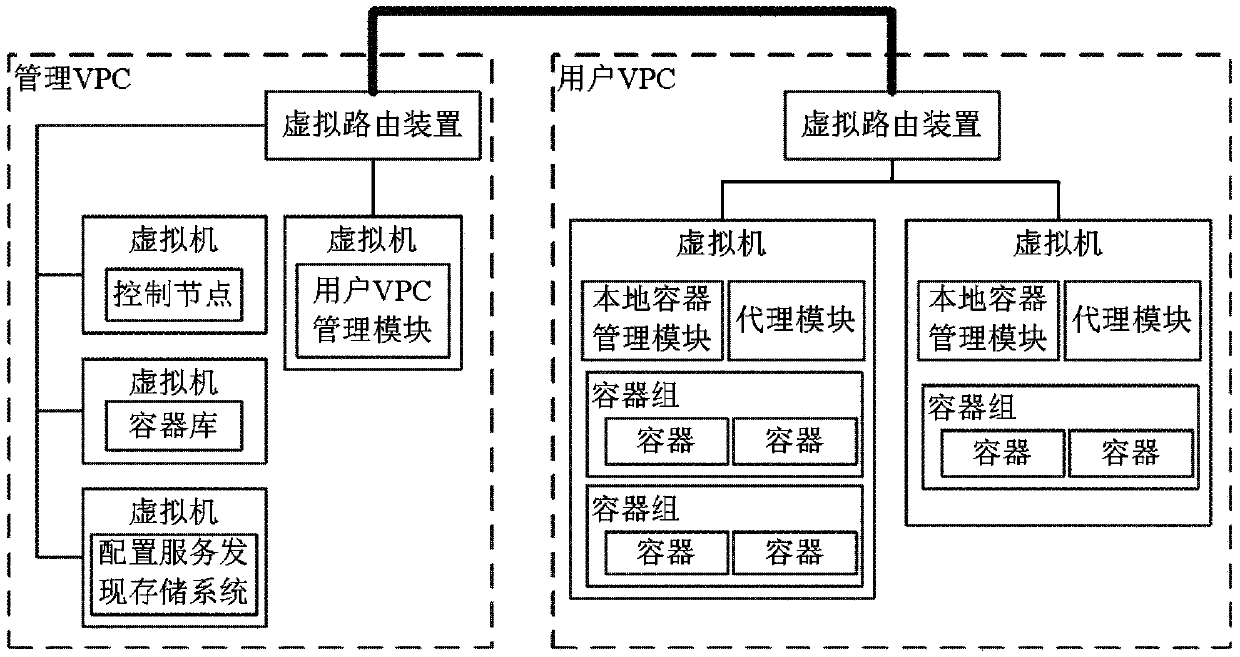
Docker implementing system and communication method thereof
ActiveCN105376303AReduce the risk of attackImprove system securityNetworks interconnectionSoftware simulation/interpretation/emulationMessage passingSystem safety
The invention provides a Docker implementing system and a communication method thereof. The Docker implementing system comprises a management VPC and a user VPC. Each VPC comprises a virtual routing device and a virtual machine. The management VPC comprises a VPC management module, a control node, a container database, and a configuration service discovery storage system. The virtual machine of the user VPC is provided with a local container management module, a proxy module, and containers. The containers are used for storing the application of a user. A safe tunnel is provided between the virtual routing device of the management VPC and the virtual routing device of the user VPC. The control node sends messages to the virtual machine of the user VPC via the safe tunnel between the virtual routing device of the management VPC and the virtual routing device of the user VPC. The virtual machine of the user VPC transmits the messages to the local container management module of the virtual machine of the user VPC. The Docker implementing system may reduce a risk that the application of the user is attacked by other users and improve system security.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
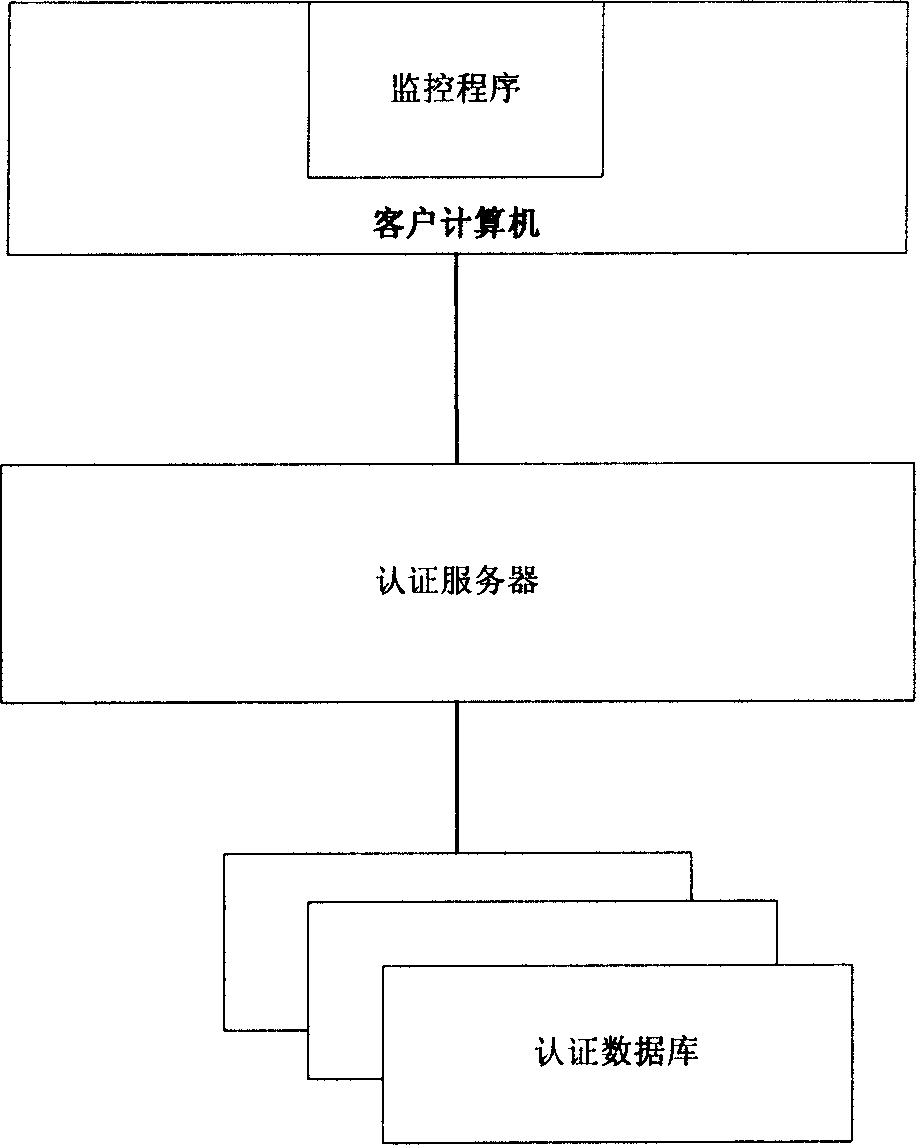
Computer safety protective method based on software identity identifying technology
InactiveCN1900941AMeet safety requirementsStop runningPlatform integrity maintainanceProtection mechanismAuthentication server
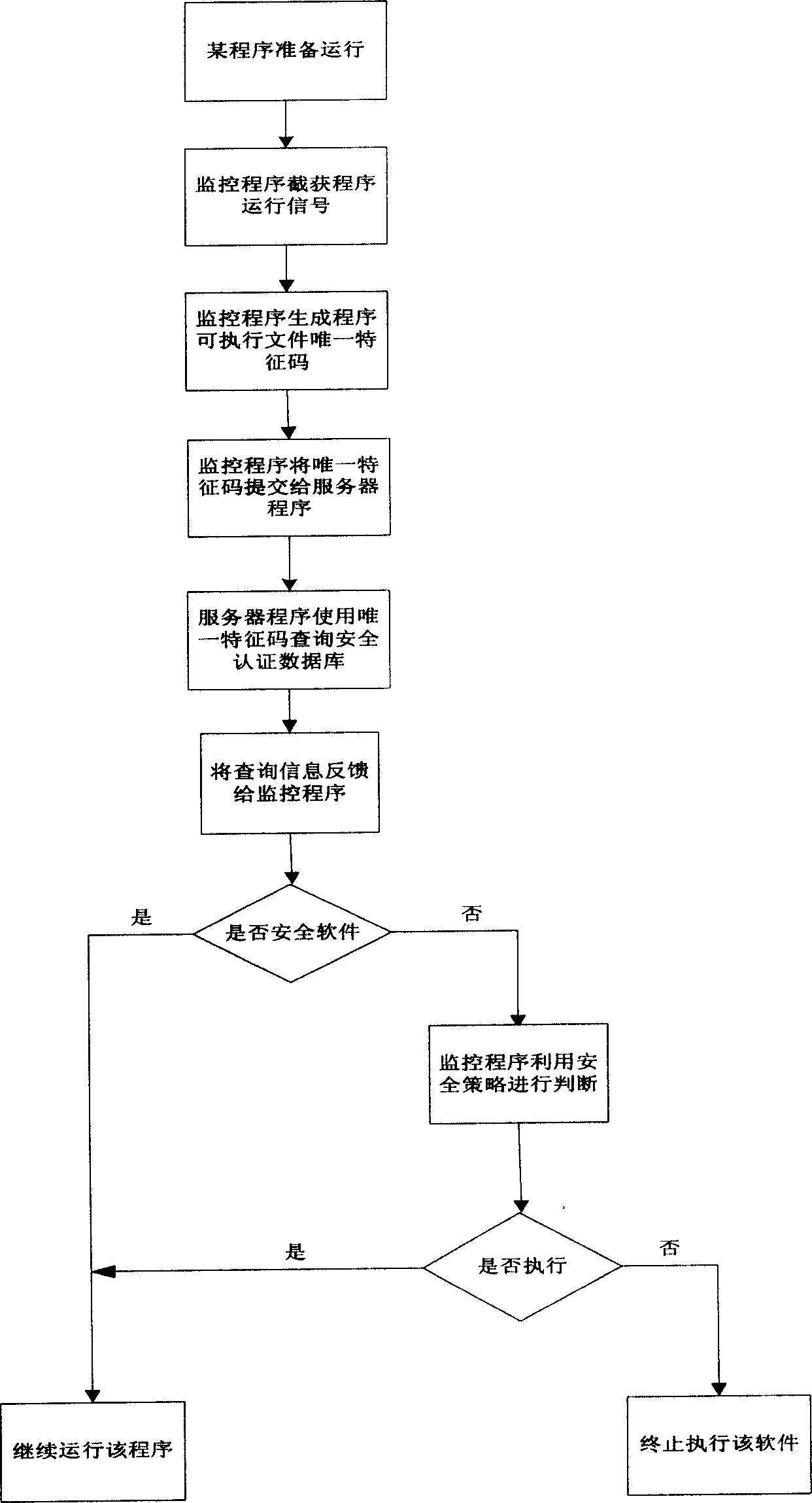
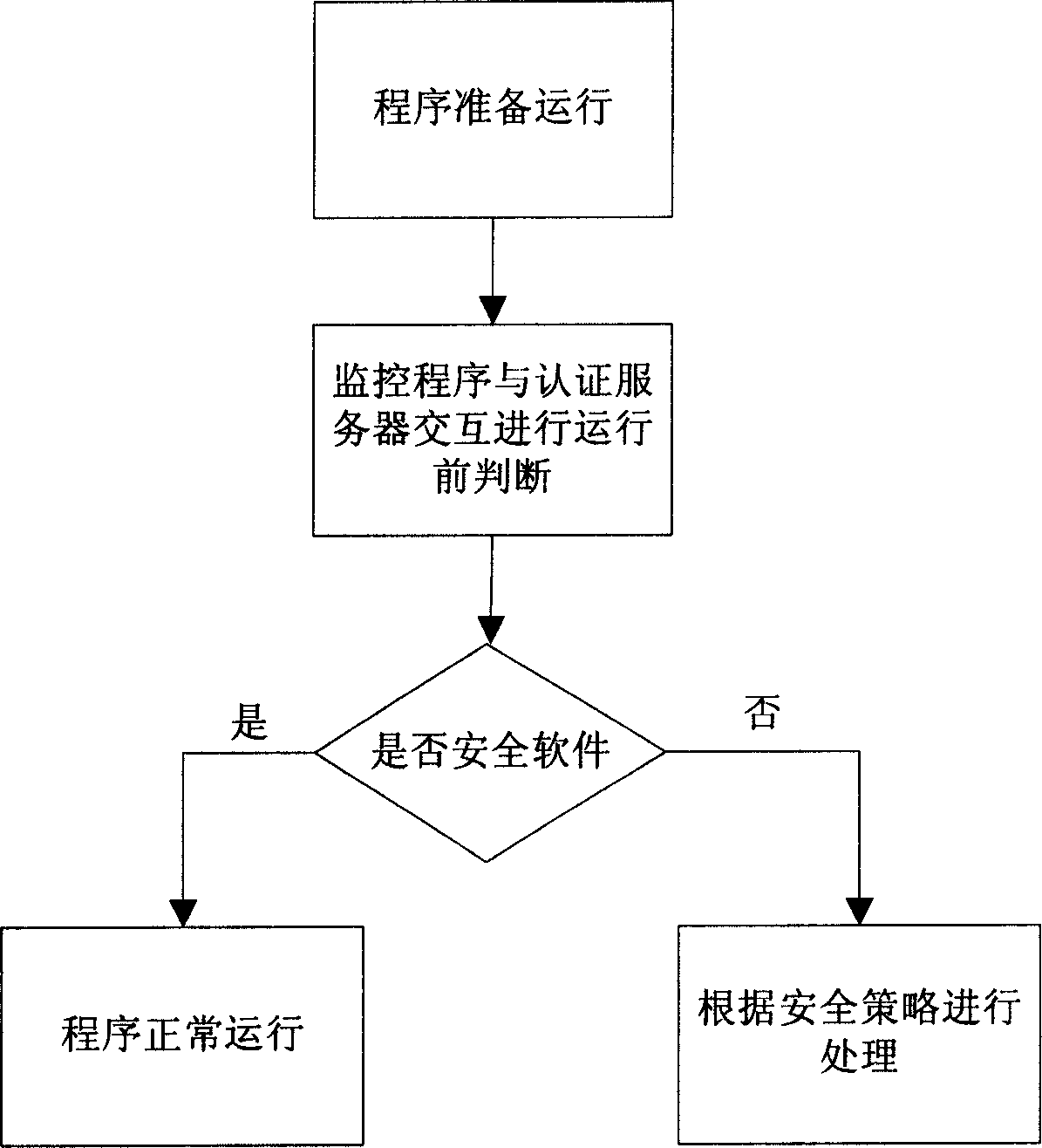
The present invention relates to computer security technology, and is a client end computer security protecting mechanism established around the certificating server based on software identity certification. The present invention includes: 1. establishing security certificating database with the unique flag code as ID; 2. establishing certificating server for providing software security certificating function with the security certificating database as kernel; 3. establishing security policy for limiting the software running in the client end; 4. monitoring the client end computer and extracting the unique ID and submitting it to the certificating server before starting the executable file; 5. inquiring the security certificating database with the certificating server and feeding back the corresponding security information to the client end computer; and 6. the client end computer judging whether to execute the software. Compared with traditional antivirus method, the present invention has more wide protection.
Owner:傅玉生
Dynamically and smoothly expandable data acquisition system and method
ActiveCN103532975ASelf-describingImplement self-describing data accessUser identity/authority verificationData switching networksData acquisitionComputer terminal
The invention discloses a dynamically and smoothly expandable data acquisition system and method. The dynamically and smoothly expandable data acquisition system comprises a central data acquisition system and a data acquisition terminal, wherein the central data acquisition system comprises a gateway routing node, a data acquisition man aging node, data acquisition nodes, a security authenticating node, an acquired data storing node, a monitoring node, a time synchronizing service node, a security certificate storing node, a log managing node and a log storing node; the central data acquisition system communicates with the data acquisition terminal through a communication network; the data acquisition terminal transmits acquired device data to the data acquisition node, submits a data acquisition application form to the gateway routing node, acquires a node routing information form according to data fed back by the gateway routing node, and initiates a business report block transmission request to each data acquisition node for encrypted transmission of the data. According to the invention, the problems that the existing data acquisition system is high in expansion cost, poor in expansion capability and high in security risk under new application requirements are solved.
Owner:STATE GRID INTELLIGENCE TECH CO LTD
Authentication server, method and system for bidirectional authentication in mesh network
InactiveCN101222331ADecreased trustReduce the risk of attackUser identity/authority verificationData switching by path configurationAuthentication serverSecurity level
The invention relates to a bi-directional certification method for a certification server and a mesh network and a system thereof, belonging to the communication technical field; the certification server comprises a trust degree distribution module, a node state detecting module, a trust degree lowering / deprivation module and a trust degree management module, wherein the trust degree distributionmodule is used to determinate the security level of the node according to the received information of the node which requires to be certificated, and generates the trust degree time stamp after successful certification, and time stamp is sent to the node which requires to be certificated together with the signature algorithm mark after the signature; the node state detecting module is used to detect if nodes are attacked; the trust degree lowering / deprivation module is used to receive the break information or lower / deprive the trust degree of the node which is attacked; the rust degree management module is sued to store the user identity information of nodes in the Mesh network, which is successfully certificated, and the trust degree, the signatures and time stamps which are approved by the AS. The invention realizes that all nodes in the mesh network can choose correlation nodes based on the trust degree; moreover, the invention also realizes the bi-directional certification by verifying the trust degree signatures fed back from the correlation nodes at one time.
Owner:HUAWEI TECH CO LTD
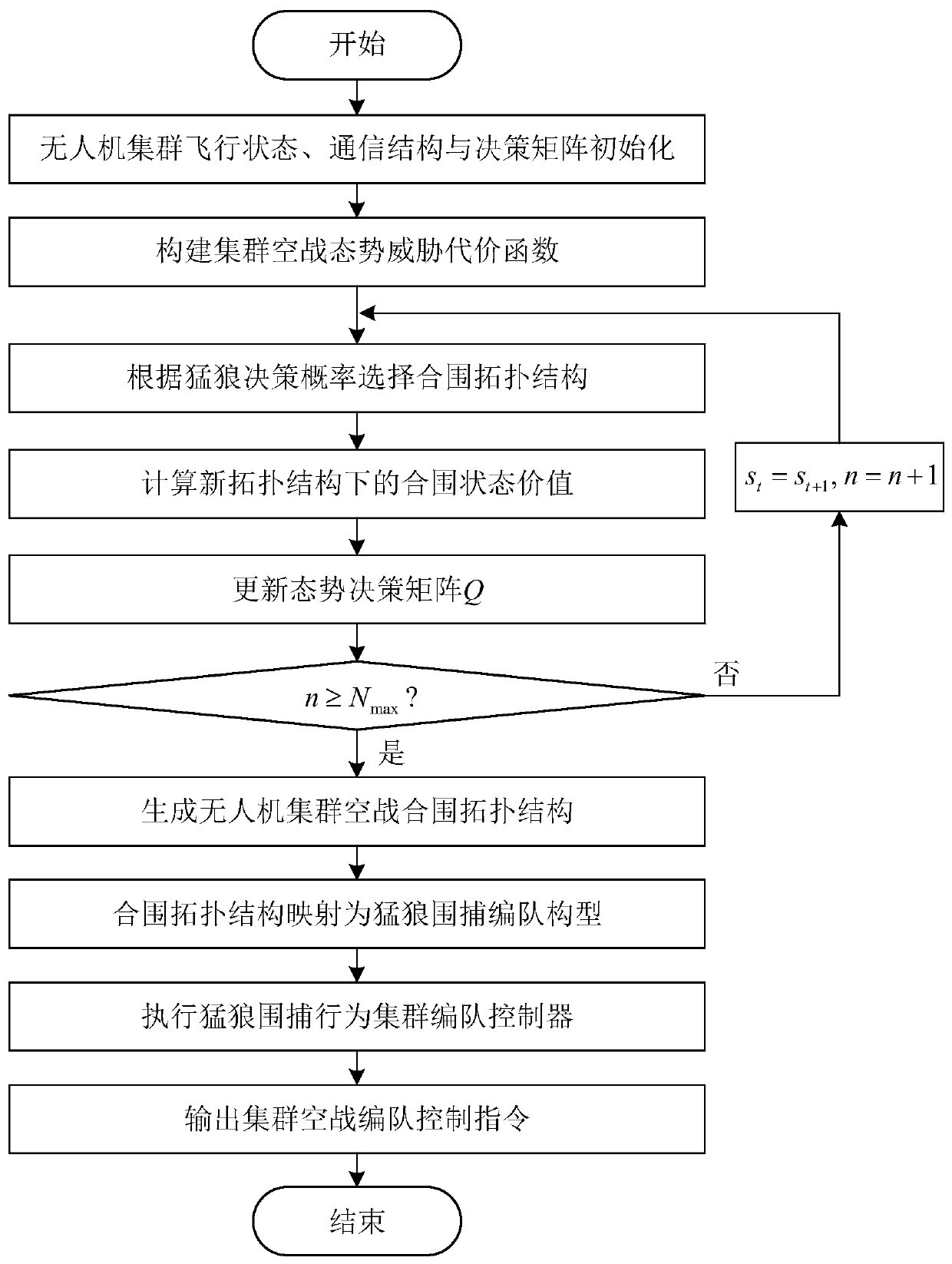
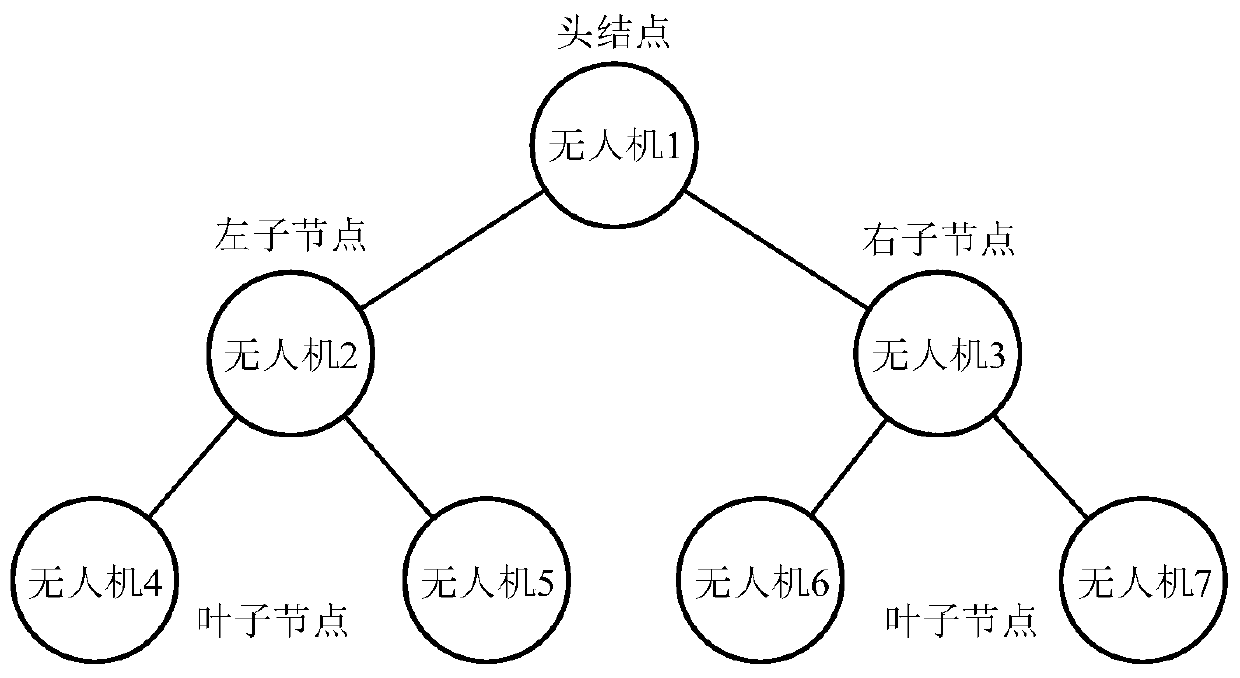
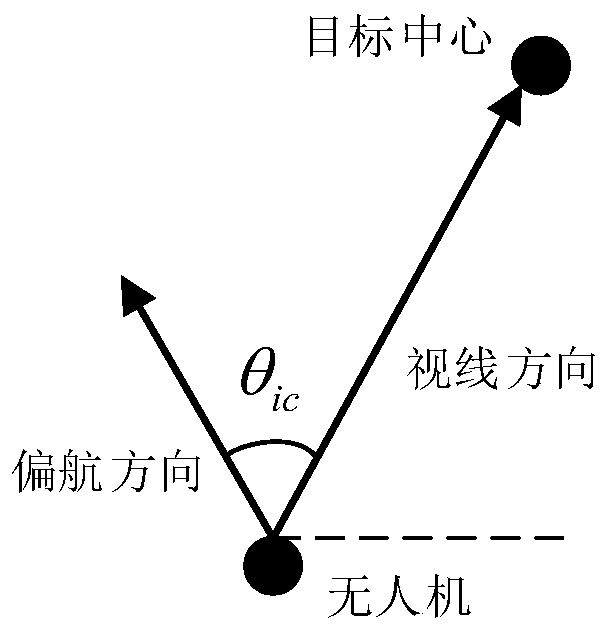
Unmanned aerial vehicle cluster air combat method based on wolf roundup behavior
ActiveCN110069076AReduce the risk of attackGuaranteed stabilityPosition/course control in three dimensionsConsistency controlUncrewed vehicle
The invention discloses an unmanned aerial vehicle cluster air combat method based on a wolf roundup behavior. The method comprises the steps that first, an unmanned aerial vehicle cluster air combatis initialized; second, cluster air combat situation threat cost is constructed; third, an unmanned aerial vehicle cluster air combat encirclement topological structure is determined by use of wolf situation learning; fourth, the encirclement topological structure is mapped into a wolf roundup formation configuration; fifth, unmanned aerial vehicle formation encirclement control is performed basedon the wolf roundup configuration; and sixth, a cluster air combat formation control instruction is output. The method can support a dynamically-changing air combat environment, an attack rick of anunmanned aerial vehicle cluster is effectively lowered, and optimal overcome effectiveness is achieved; and meanwhile, the stability of an attack formation, the consistency of attack behaviors and a high target damage probability are guaranteed, and dynamic decision, consistency control and other difficulties in cluster control are overcome.
Owner:BEIHANG UNIV
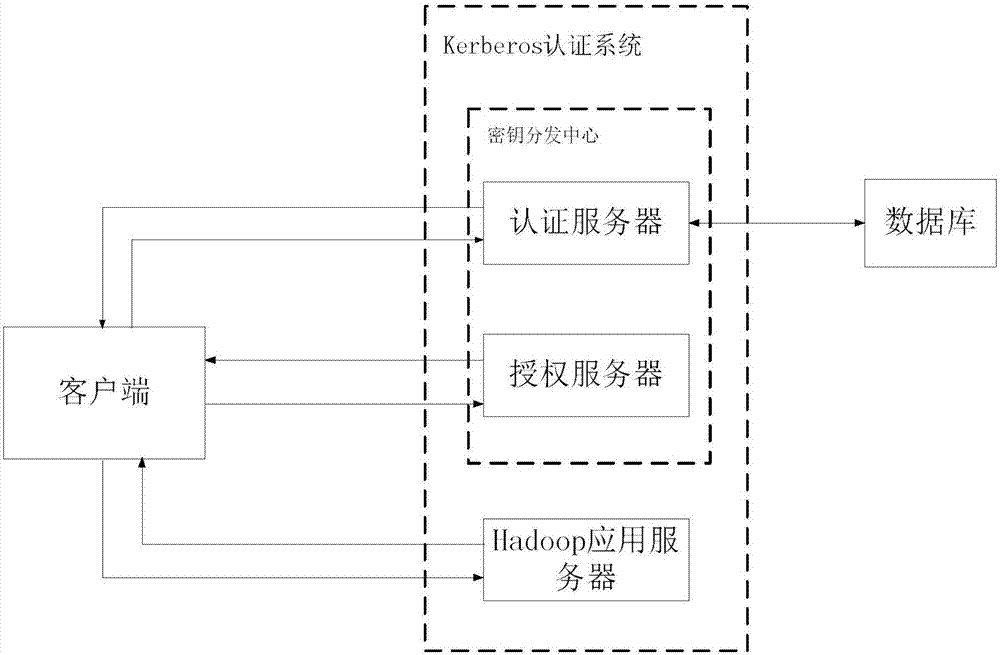
Identity authentication method for Hadoop cluster
ActiveCN107257334AImprove securityReduce risk pointsUser identity/authority verificationPlaintextAuthentication server
The invention discloses an identity authentication method for a Hadoop cluster. The method comprises the following steps: step one, a client sends a request to an authentication server to request for the ticket granting, the request is sent to the authentication server in a plaintext way, the request message comprises a user name, an authorization server name, a valid survival period, the first random number and a user located Kerberos field user information; step two, after receiving the request message of the client, the authentication server firstly finds a key of the user in a local database according to the user name, if the finding is successful, the authentication is continued. By adopting an authentication mode based on the PKI, the command of the user is unnecessary to save on the KDC, the risk point of the system is reduced, and the security of the Hadoop cluster identity authentication is greatly improved.
Owner:NO 32 RES INST OF CHINA ELECTRONICS TECH GRP
Cloud terminal identity authentication method and system
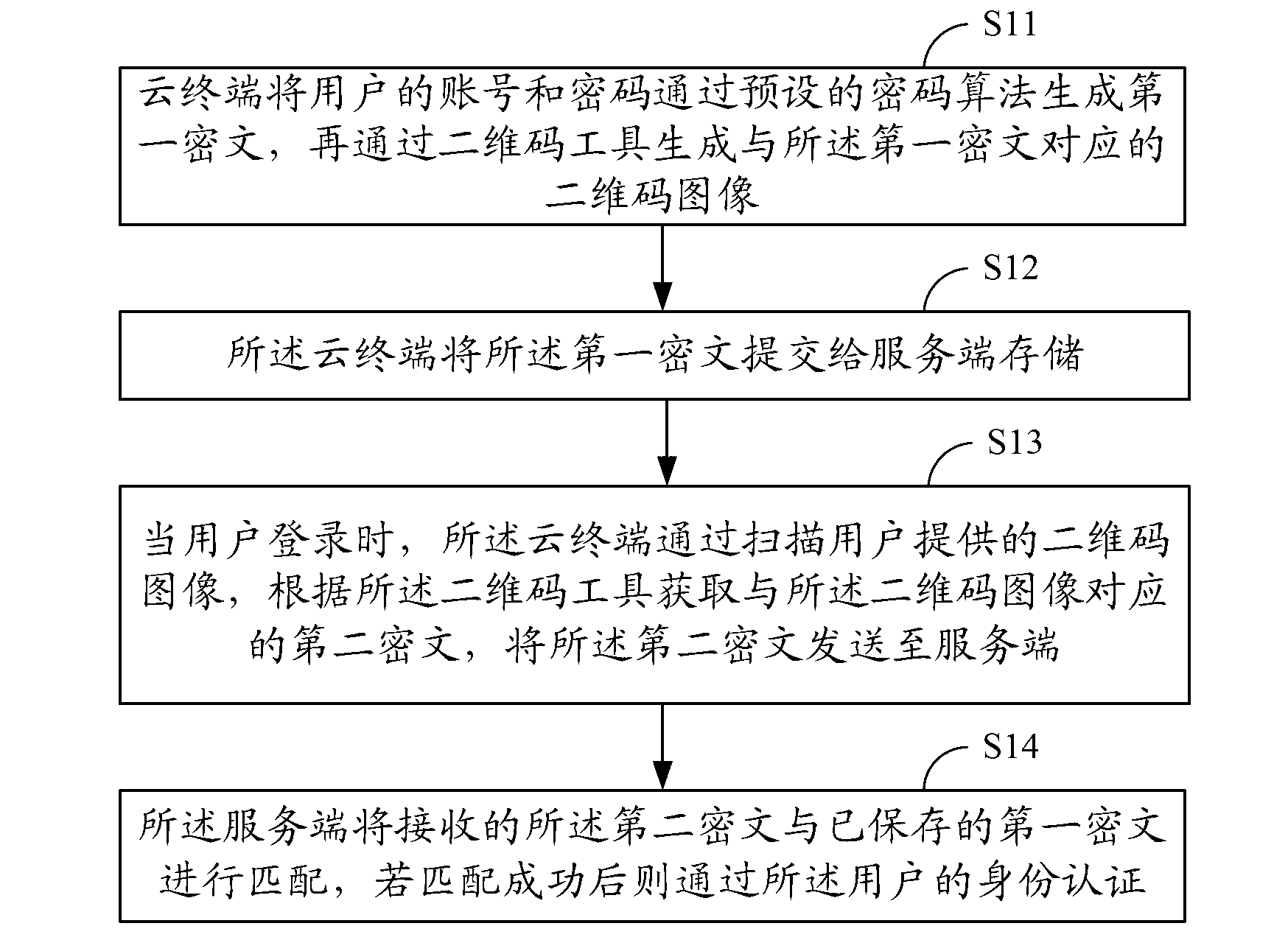
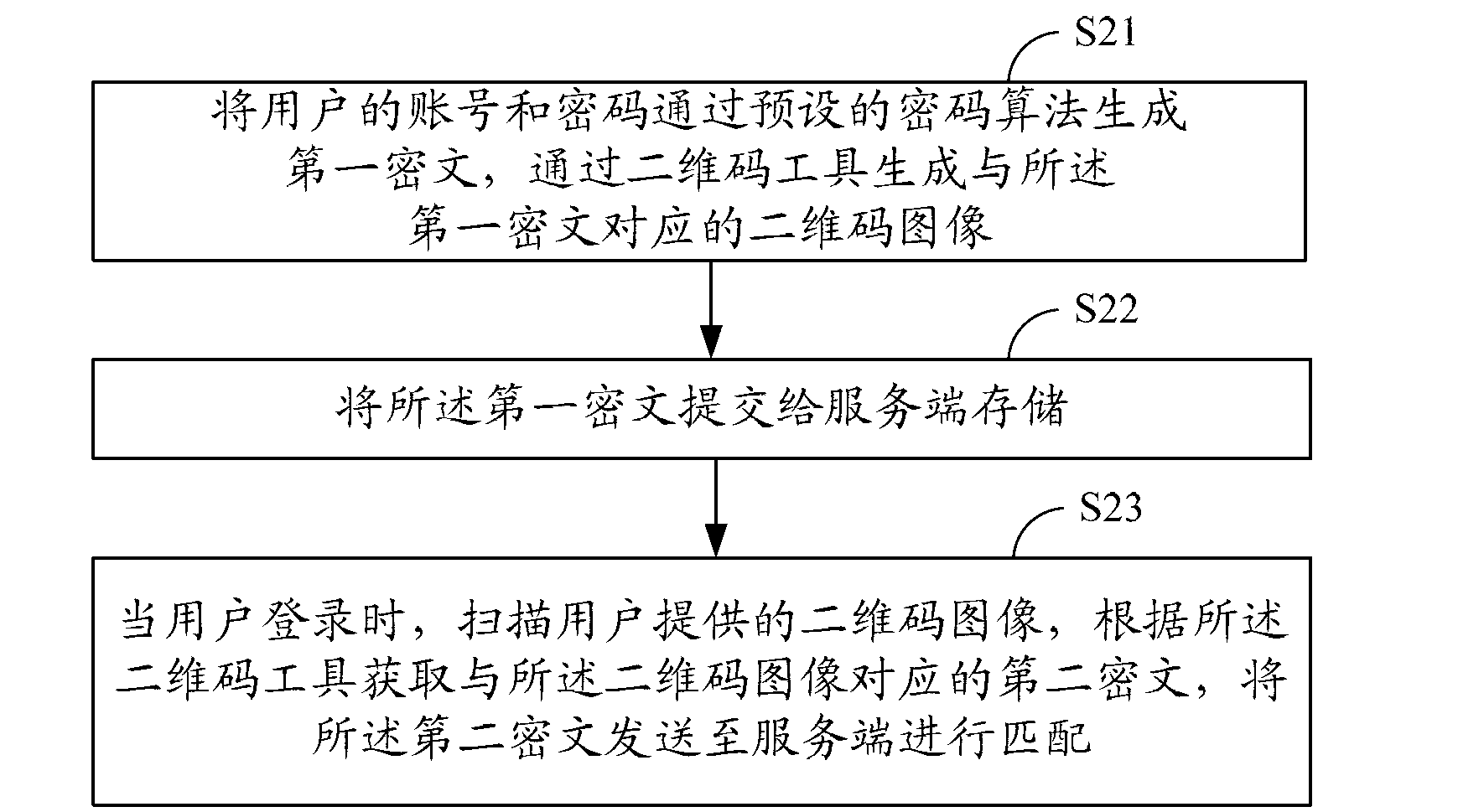
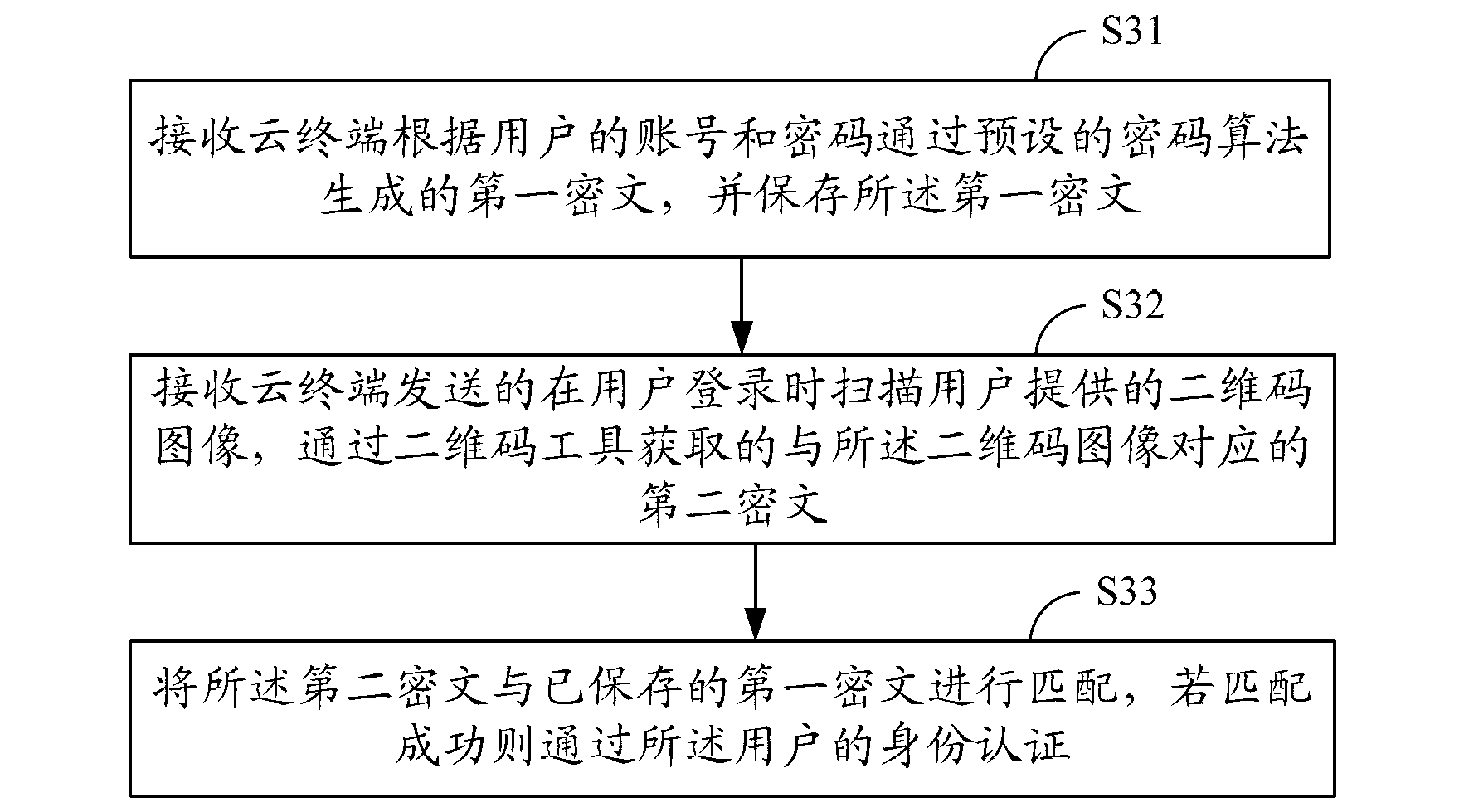
InactiveCN103067371AReduce the risk of attackImprove securityUser identity/authority verificationComputer hardwareCiphertext
The invention provides a cloud terminal identity authentication method. The cloud terminal identity authentication method includes that an account and a password of a user are converted to a first cipher text through a preset password algorithm and then converted to a two-dimensional code image corresponding to the first cipher text through a two-dimensional code tool; a cloud terminal submits the first cipher text to a server-side to store; when the user logins, the cloud terminal scans the two-dimensional code image provided by the user and obtains a second cipher text corresponding to the two-dimensional code image through the two-dimensional code tool, and the second cipher text is sent to the server-side; and the second cipher text received by the server-side is matched with the stored first cipher, and if the second cipher text received by the server-side is successfully matched with the stored first cipher, an identity authentication of the user is passed. The invention further provides a corresponding cloud terminal identity authentication system. The cloud terminal identity authentication method and the corresponding cloud terminal identity authentication system can improve the safety performance of the cloud terminal identity authentication, and the risk that user information is disclosed is greatly lowered.
Owner:GCI SCI & TECH
Industrial access control method and device
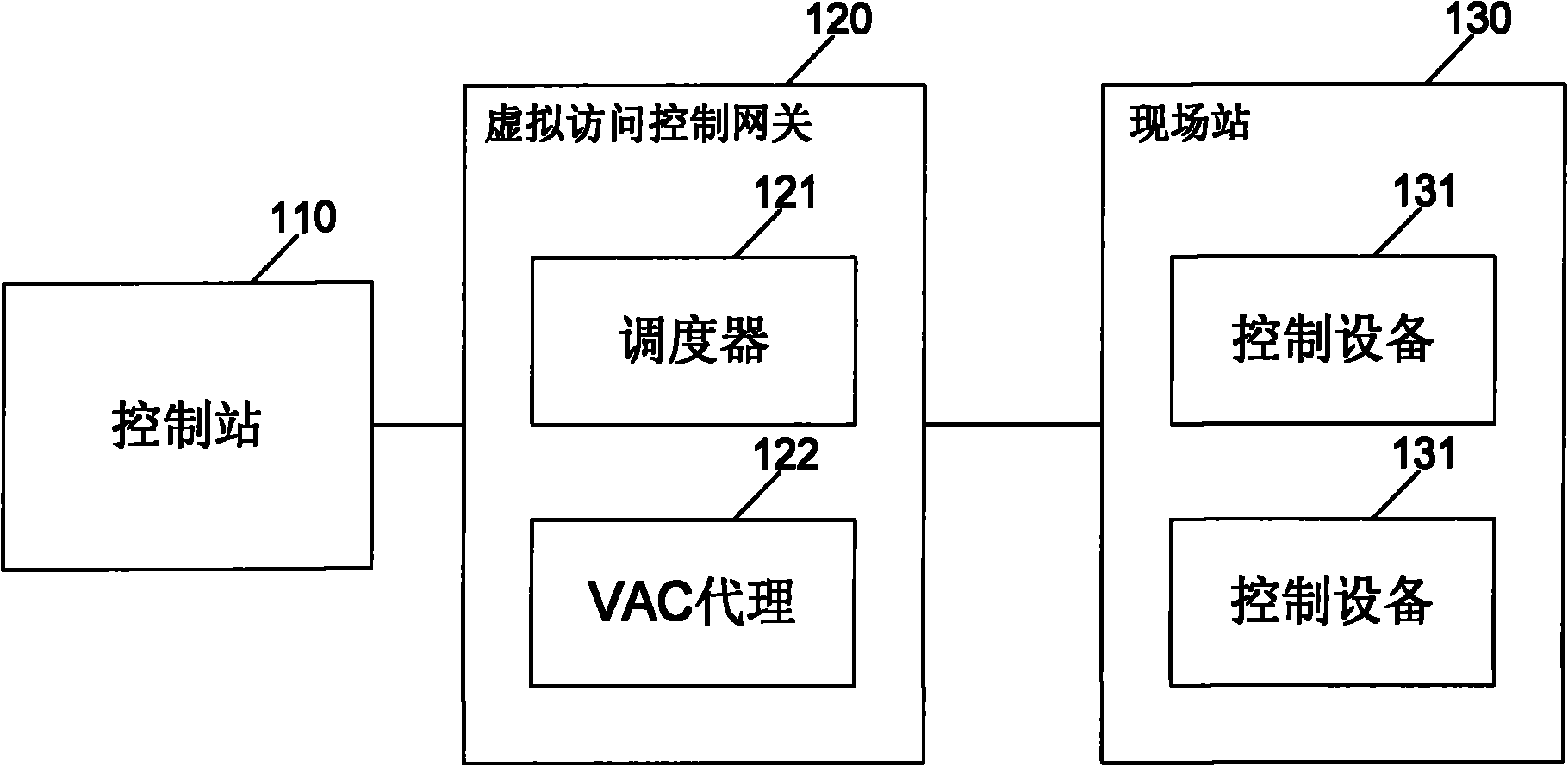
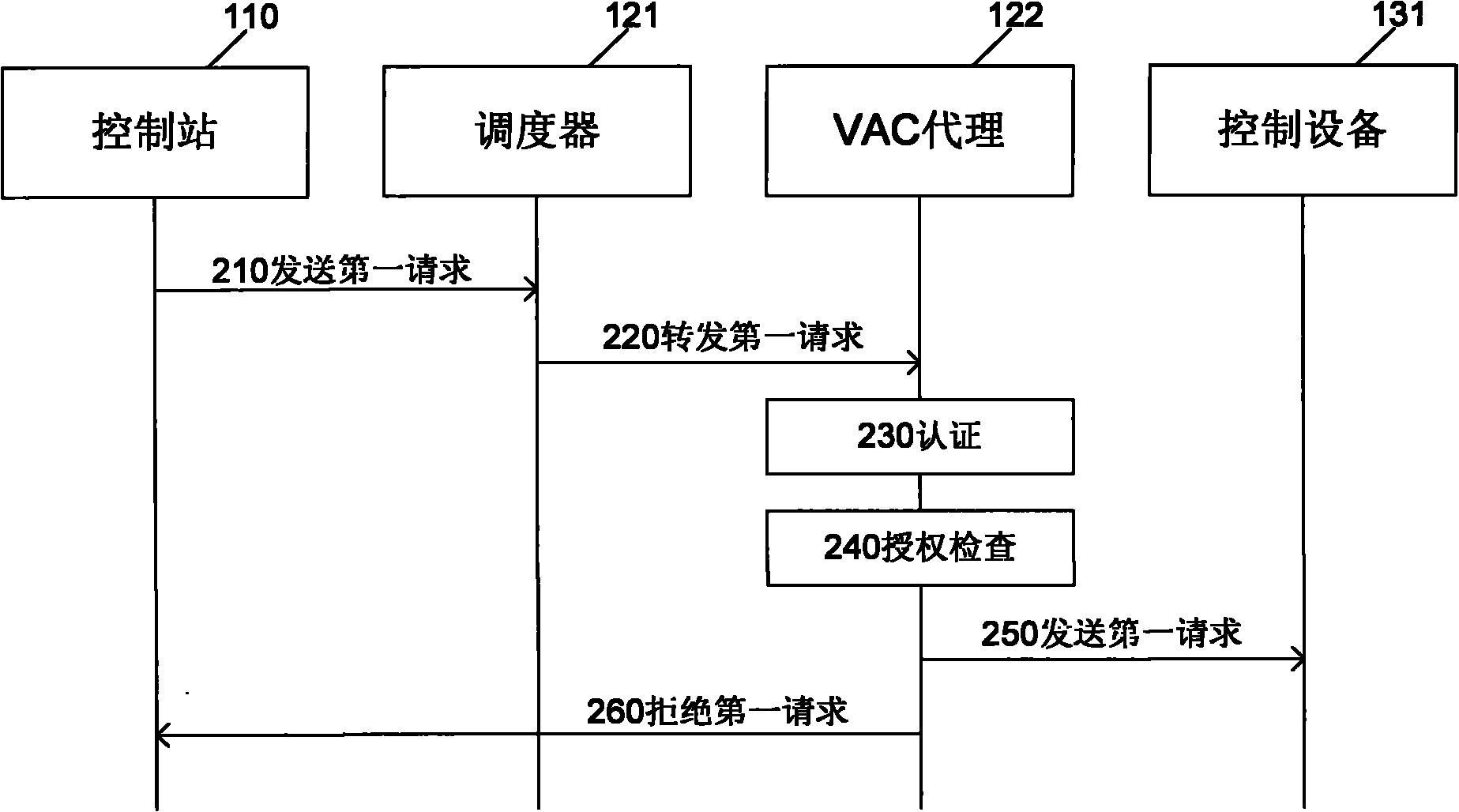
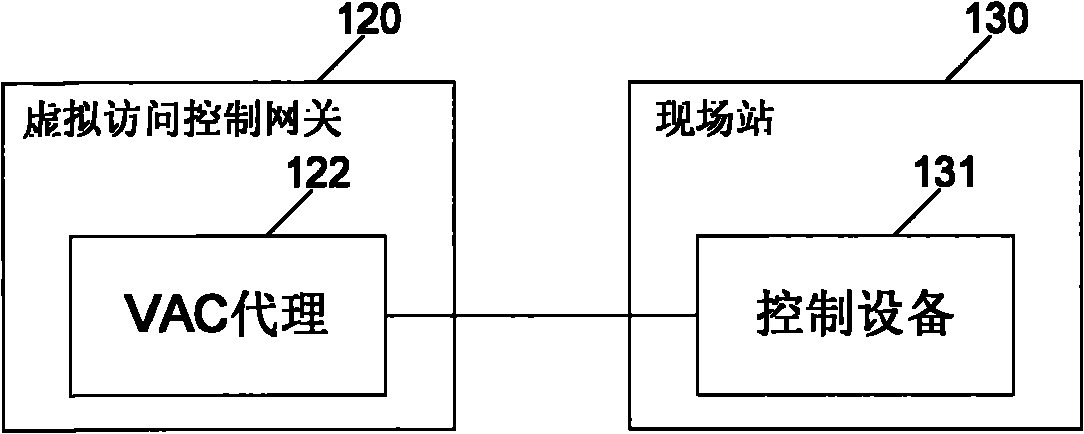
InactiveCN102377740AReduce the risk of attackProtection securityNetwork connectionsTarget controlAuthorization
The invention relates to an industrial access control method. The method comprises the following steps: a virtual access control gateway receives a first request sent by a control station, wherein the first request is used for requesting to operate target control equipment or is used for requesting to access the target control equipment; after the first request is received, the virtual access control gateway authenticates the control station in accordance with an authorization strategy; if the authorization passes, the virtual access control gateway carries out authorization check operation in accordance with authorization rules; if the authorization check passes, the virtual access control gateway sends a second request to the target control equipment, wherein the second request is used for requesting to operate the target control equipment. The invention also relates to an industrial access control device and a virtual access control gateway. The method, the device and the equipment disclosed by the invention have the capability of reducing the risk of suffering network attack of an industrial control system, have no need to transform the traditional systems, and can be used for a heritage industrial control system.
Owner:SIEMENS AG
Network security protection method, device and storage medium
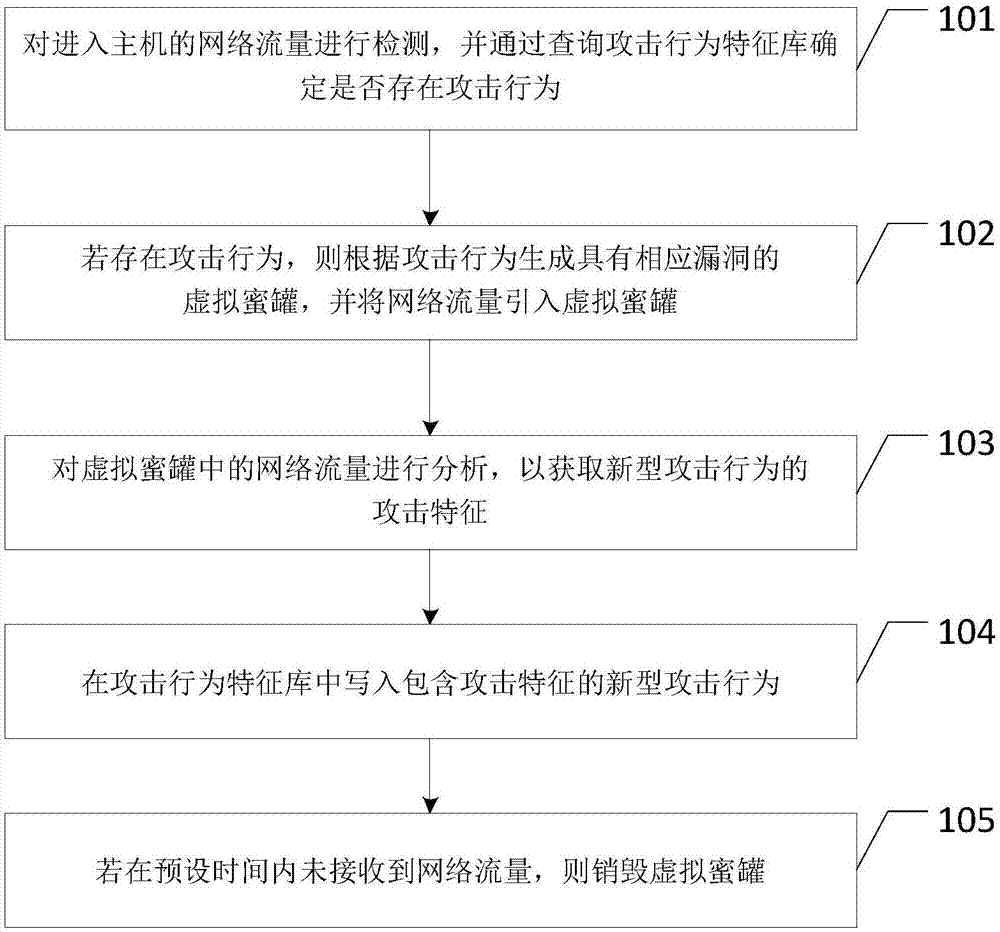
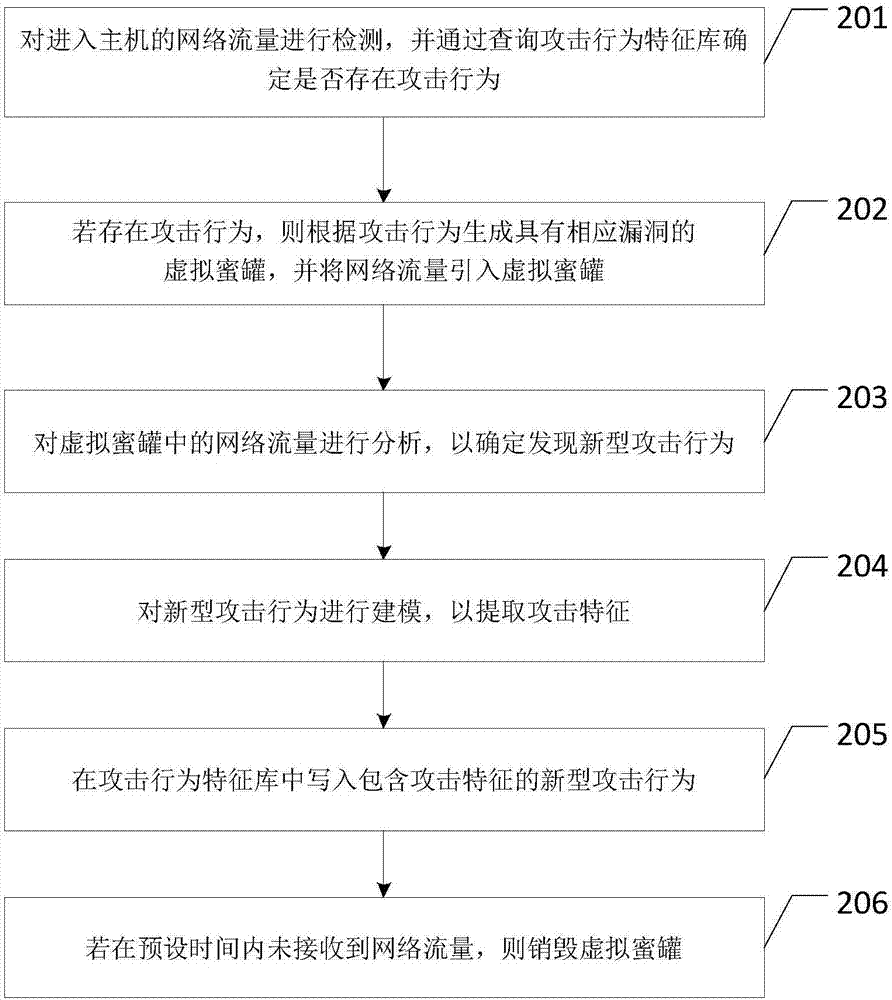
ActiveCN107426242AMitigate the risk of attackReduce the risk of attackTransmissionTraffic volumeFeature based
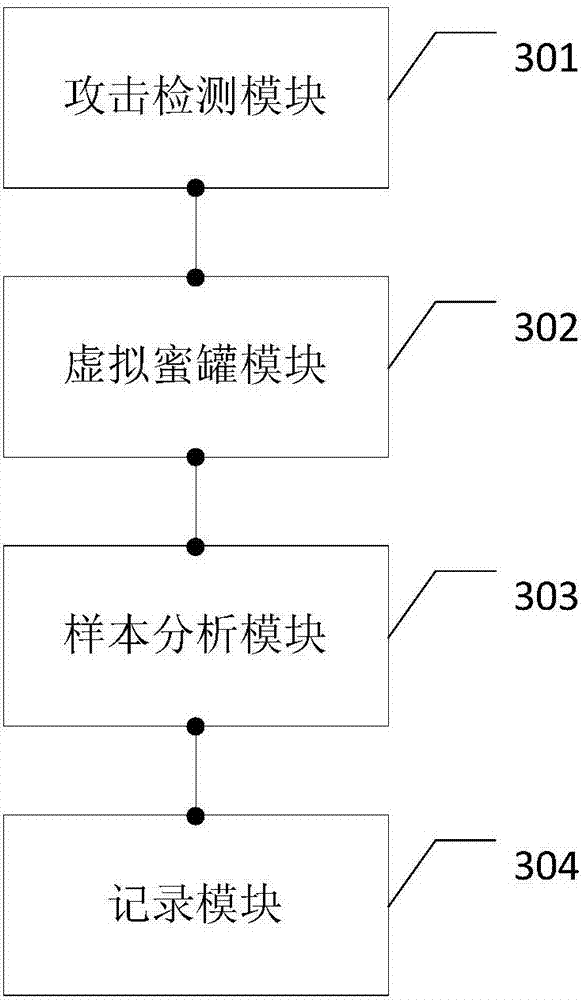
The embodiment of the invention discloses a network security protection method, a device and storage medium. Various attacks can be effectively intercepted, and the risk that a business system is attacked is relieved. The method disclosed by the embodiment of the invention comprises the following steps: detecting network traffic entering a host, and determining whether an attack behavior is existent by querying an attack behavior feature base; if the attack behavior is existent, generating a virtual honeypot with a corresponding loophole according to the attack behavior, and importing the network traffic into the virtual honeypot; analyzing the network traffic in the virtual honeypot to acquire the attack feature of the novel attack behavior; writing the novel attack behavior containing the attack feature in the attack behavior feature base; if the network traffic is unreceived within the preset time, destroying the virtual honeypot.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
Pseudo AP detection method based on RSSI
InactiveCN105472621AShorten detection timeImprove timelinessSecurity arrangementNetwork attackEmbedded system
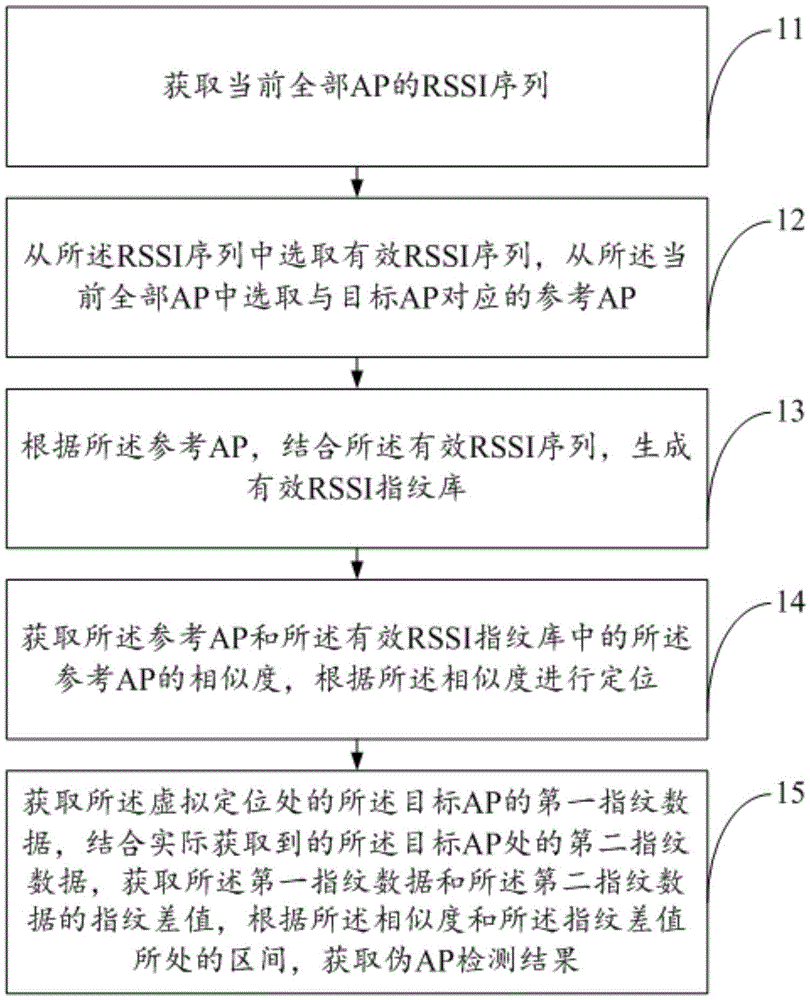
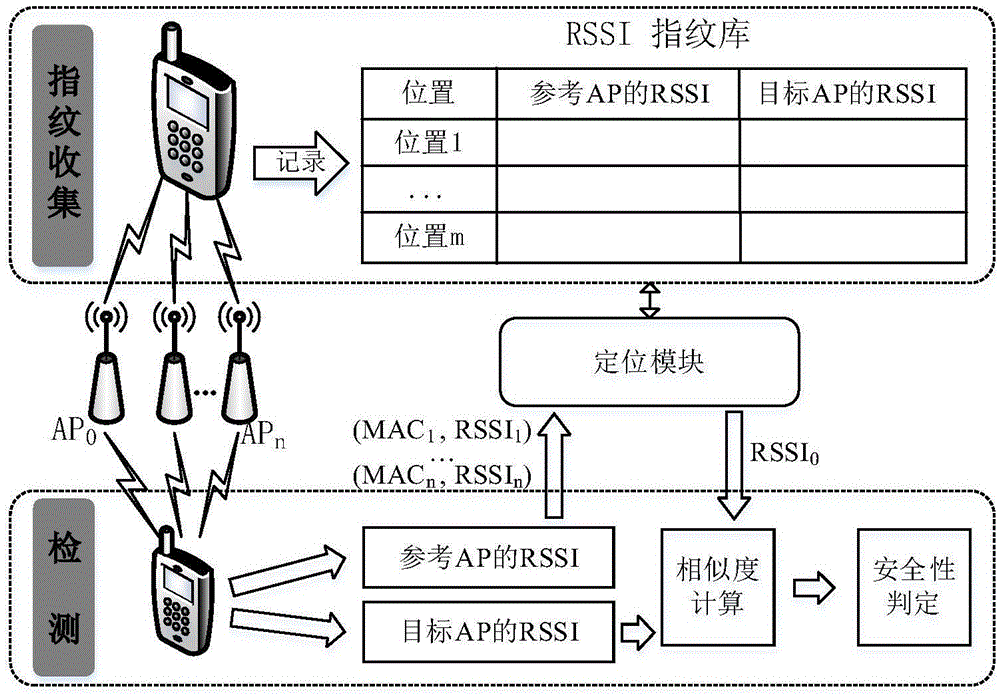
The invention discloses a pseudo AP detection method based on an RSSI, and belongs to the field of wireless network safety. The method comprises the steps: obtaining the RSSI sequences of all current APs; selecting the effective RSSI sequence from the RSSI sequences; selecting a reference AP, corresponding to a target AP, from all current Aps; generating an effective RSSI fingerprint library according to the obtained reference AP through combining with the effective RSSI sequence, thereby obtaining the similarity of the reference AP with the reference AP in the effective RSSI fingerprint library; carrying out positioning according to the similarity; obtaining the first fingerprint data of the target AP at a virtual positioning place, obtaining a fingerprint difference between the first fingerprint data and second fingerprint data through combining with the actually obtained second fingerprint data at the target AP, and obtaining a pseudo AP detection result according to the similarity and the section where the fingerprint difference is located. The method can shorten the detection time in the prior art, improves the timeliness of detection, does not need the connection with a suspicious AP in a detection process, and reduces the risks of network attack.
Owner:NORTHWEST UNIV(CN)
Network video monitoring system and method for automatically assigning cameras in the same
InactiveUS20150138365A1Load balancingAvoid failureTelevision system detailsClosed circuit television systemsVideo monitoringVideo recording
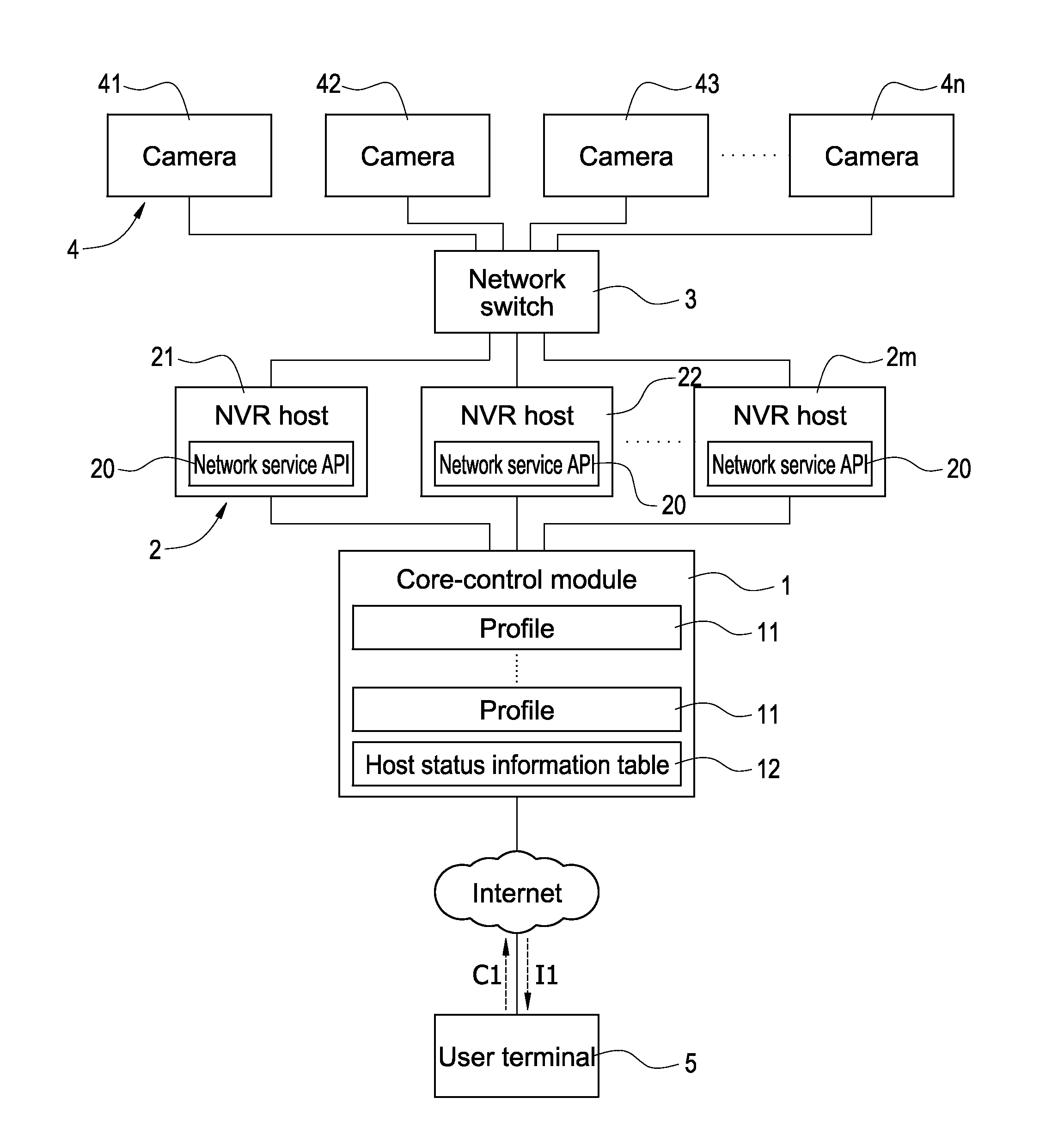
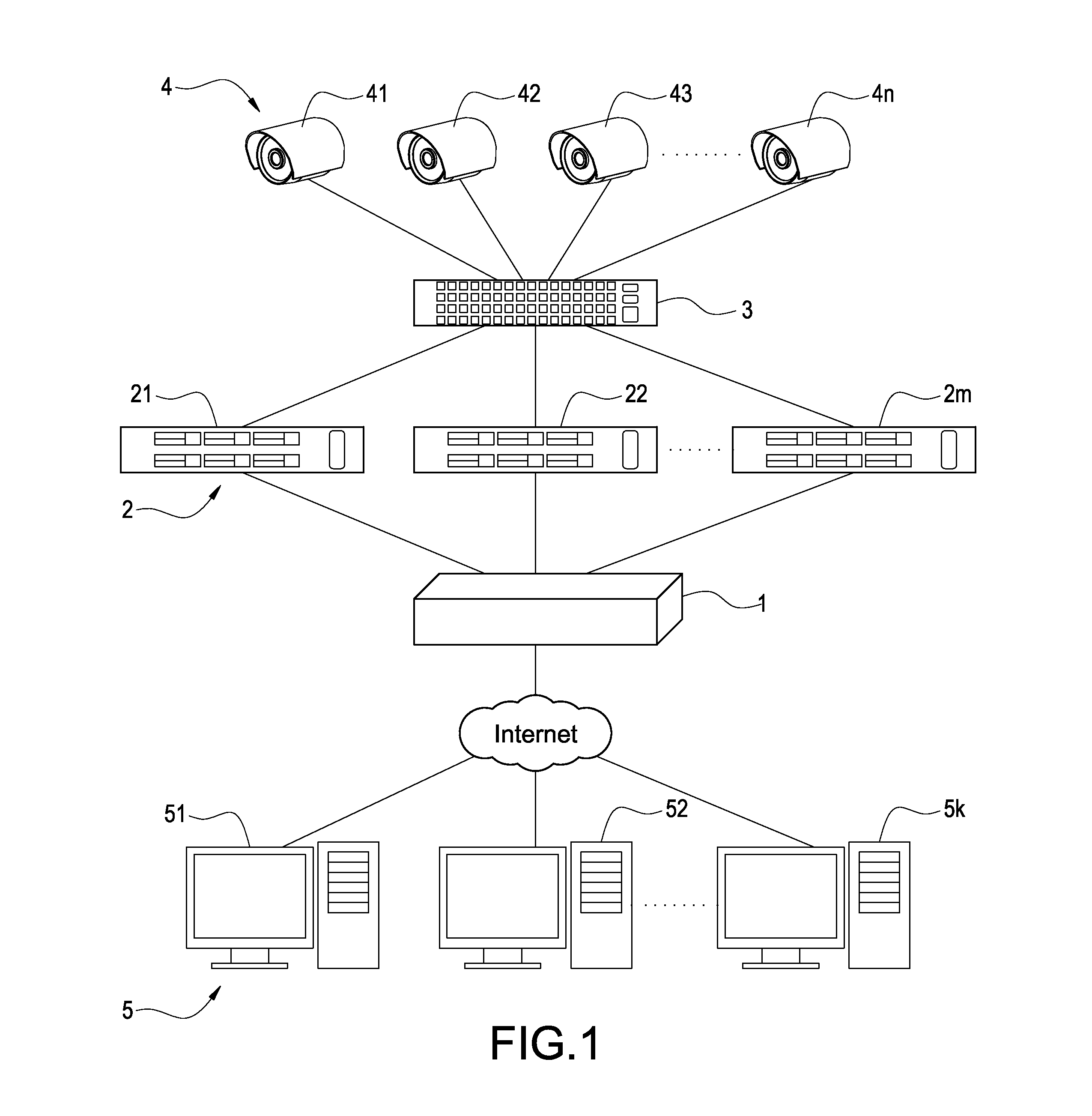
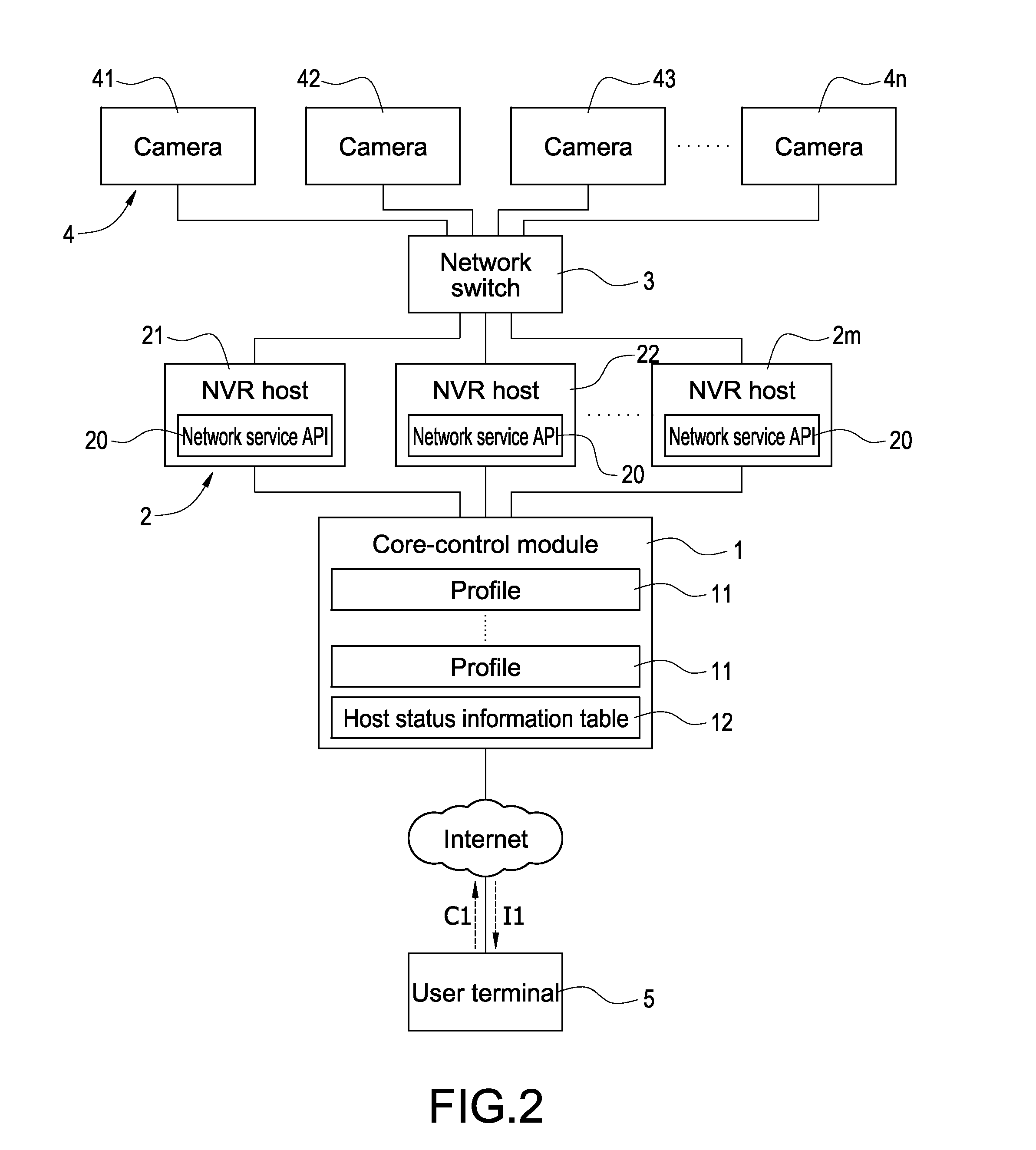
A network video monitoring system includes a core-control module, a plurality of network video recording (NVR) hosts, and a plurality of cameras. The core-control module assigns the cameras to the NVR hosts respectively for controlling the camera by the NVR hosts according to status of each NVR host. In this application, the core-control module obtains the status of each NVR host periodicity for determining if the NVR hosts are over loading or failed, and re-assigns the cameras automatically for the overloaded or malfunctioned NVR hosts. The application rescues the NVR hosts from the over loading problem, and prevents the termination of the monitoring action of the cameras when one of the NVR host malfunctions.
Owner:DELTA ELECTRONICS INC
Intelligent distribution terminal security protection method based on asymmetric digital signature authentication
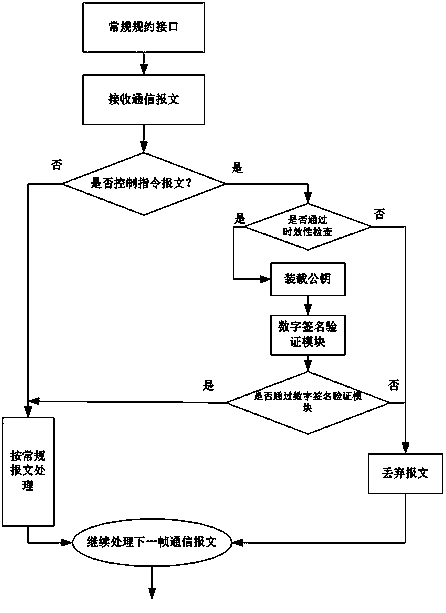
InactiveCN103368742AGuaranteed operational safetyReduce the risk of attackCircuit arrangementsUser identity/authority verificationTimestampDigital signature
The invention discloses an intelligent distribution terminal security protection method based on asymmetric digital signature authentication. According to the actual characteristics of an intelligent distribution terminal, asymmetric digital signature authentication is realized on the distribution terminal; and the authentication of a digital signature technology can be realized by making small changes on the conventional communication protocols of the conventional distribution automation system without redefining a new communication protocol, namely the authentication of the digital signature technology can be realized by adding a digital signature section and a timestamp security information section of a sending party on the basis of the original standard protocol communication message section. The compatibility with the protocol before renovation is guaranteed, the renovation cost is low, and the method is easy to implement in engineering project construction, so that the risk of the distribution automation system from public network attack is reduced, and the operation security of the distribution automation system is guaranteed; and therefore the method has a good application prospect.
Owner:NANJING NARI GROUP CORP +1
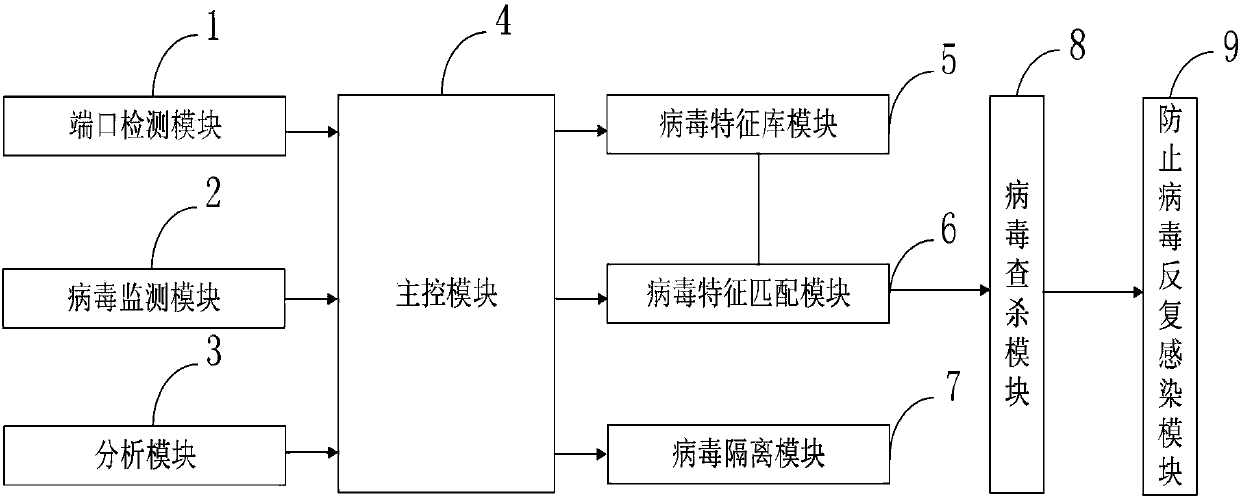
Novel computer network virus defensive system
InactiveCN107612933AEliminate regeneration abilityImprove success efficiencyTransmissionRecurrent viral infectionsBotnet
The invention belongs to the technical field of network virus defense, and discloses a novel computer network virus defensive system. The network virus defensive system comprises an end detection module, a virus monitoring module, an analysis module, a main control module, a virus feature library module, a virus feature matching module, a virus isolation module, a virus searching and killing module, and a repeated-virus-infection-prevention module. The end detection module, the virus monitoring module and the analysis module are connected with the main control module through a circuit line separately; the main control module is connected with the virus feature library module, the virus feature matching module and the virus isolation module separately through the circuit line separately. Through the repeated-virus-infection-prevention module, the regenerating capability of viruses can be eradicated; through the analysis module, botnet viruses or target attack viruses which are targetedaiming at virus attacking objects can be analyzed, searched and killed, and therefore compared with general antivirus software, the novel computer network virus defensive system is more targeted.
Owner:LINGNAN INST OF TECH
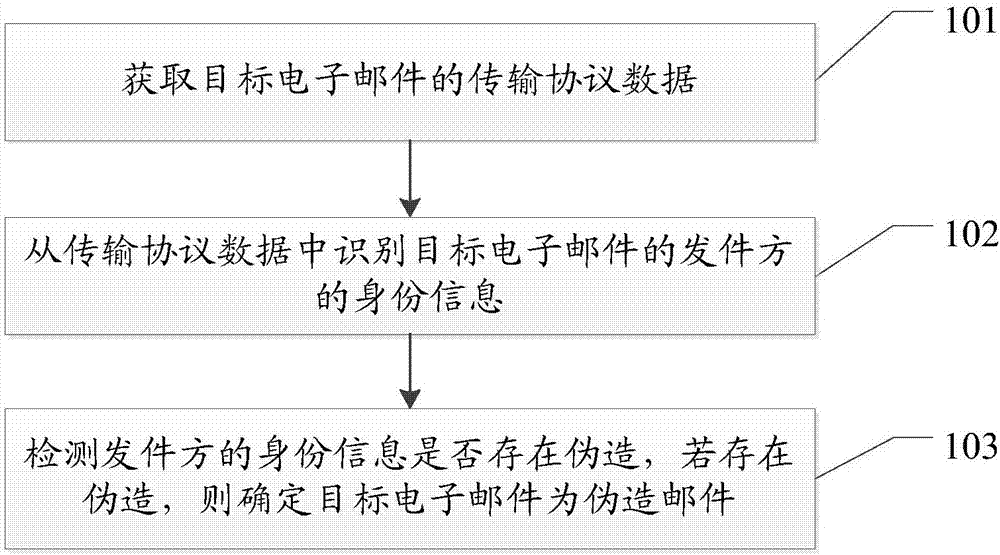
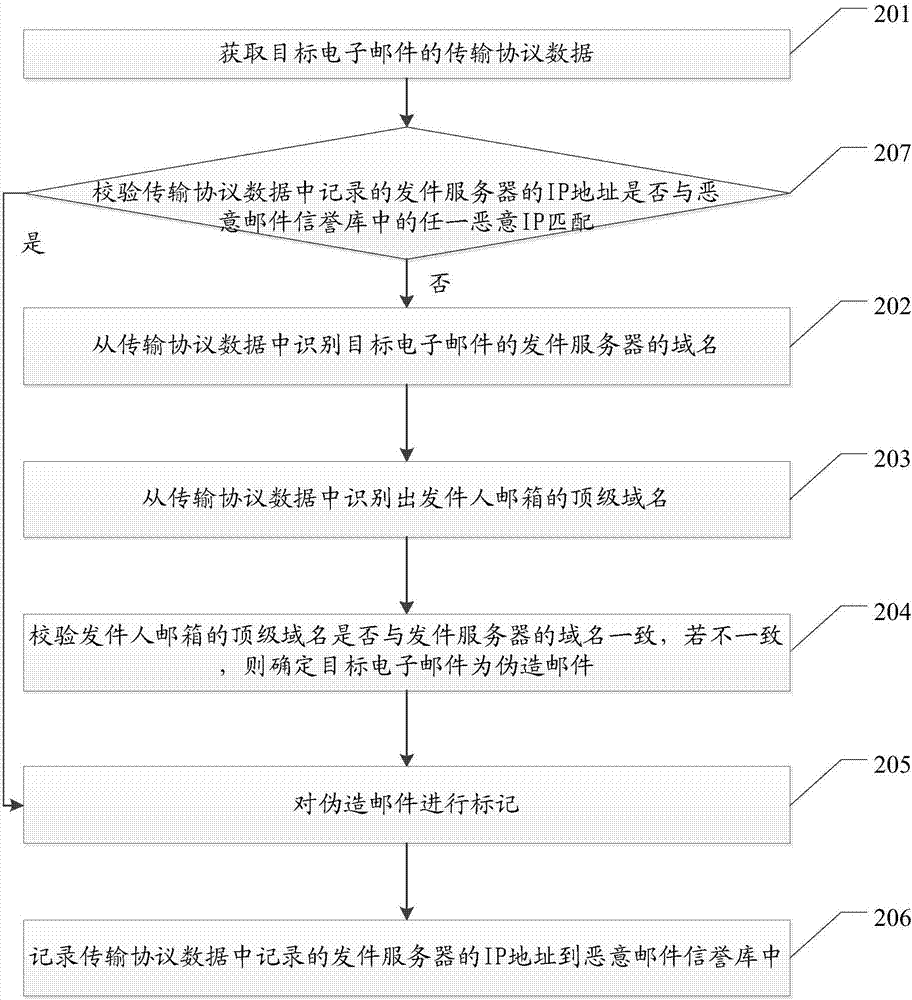
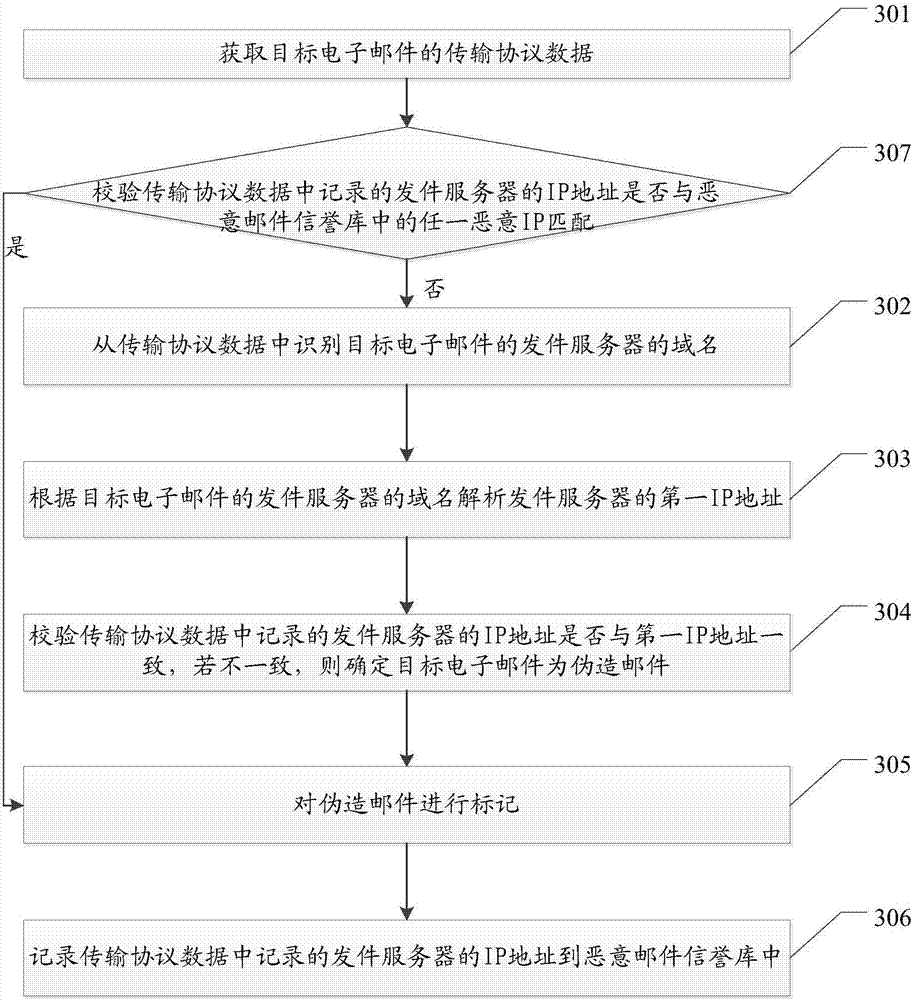
Method and system for forged mail detection
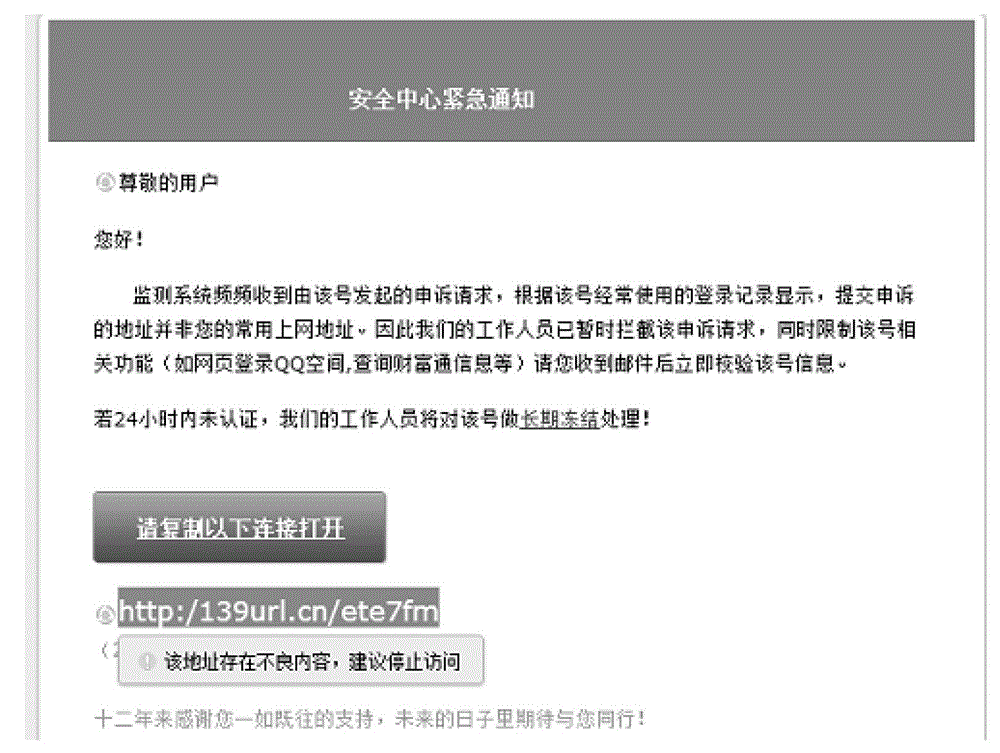
InactiveCN106992926AReduce the risk of attackData switching networksTransmission protocolInternet privacy
Embodiments of the invention disclose a method and a system for forged mail detection for detecting and identifying forged mails and reducing the risk of e-mails being maliciously attacked. The method comprises: obtaining transmission protocol data of a target e-mail; identifying the identity information of a sender of the target e-mail from the transmission protocol data; and detecting whether the identity information of the sender is forged, and if there is a forgery, determining that the target e-mail is a forged mail.
Owner:SANGFOR TECH INC
Full-automatic pet cleaning machine and cleaning method
InactiveCN105210912AReduce stressReduce tensionGrooming devicesProgrammable logic controllerWarm water
The invention discloses a full-automatic pet cleaning machine and a cleaning method. The cleaning machine comprises a machine body internally provided with a constant temperature water tank, a force pump, a three-dimensional cleaning box and a drying device. A PLC (programmable logic controller) is arranged on the machine body and is connected to a computer. The cleaning method comprises steps of (1) storing warm water, (2) cleaning a pet and (3) drying the pet. A one-channel two-way alternative valve and two pipes are employed in the full-automatic pet cleaning machine, wherein water are discharged through the two pipes, so that a phenomenon that the pet feels compressed and nervous, and is prone to restlessness due to water curtains densely distributed around can be alleviated, the pet can be cleaned all-dimensionally through the water in two channels, and the pet can be quite clean. The cleaning machine is easy to operate, the computer can automatically work out a cleaning mode, the cleaning and drying can be completed for about 30 minutes, a whole process is carried out in the cleaning box and without the aid of a worker, manpower cost and labor cost are greatly saved, and risks that the worker is attacked by the pet are reduced.
Owner:CHANGSHU SHUANGSHI ENVIRONMENT PROTECTION EQUIP CO LTD
Hardware trojan resistant integrated circuit design method and system
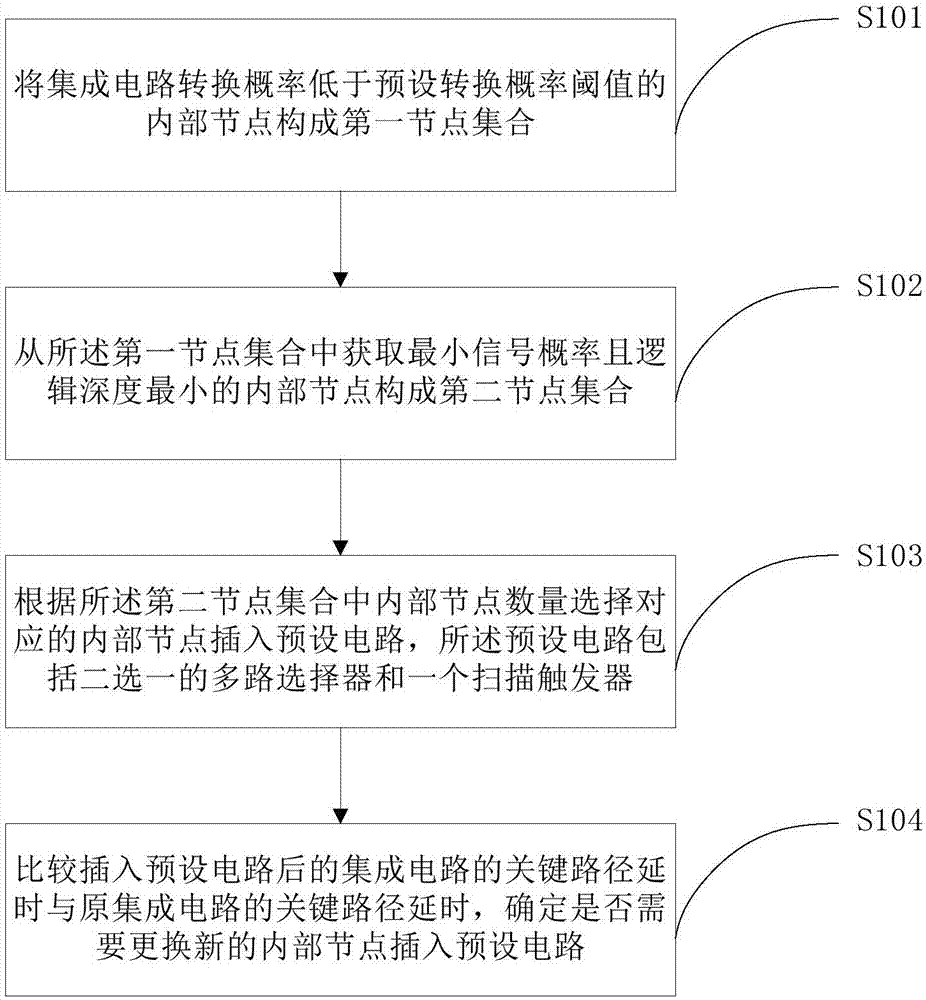
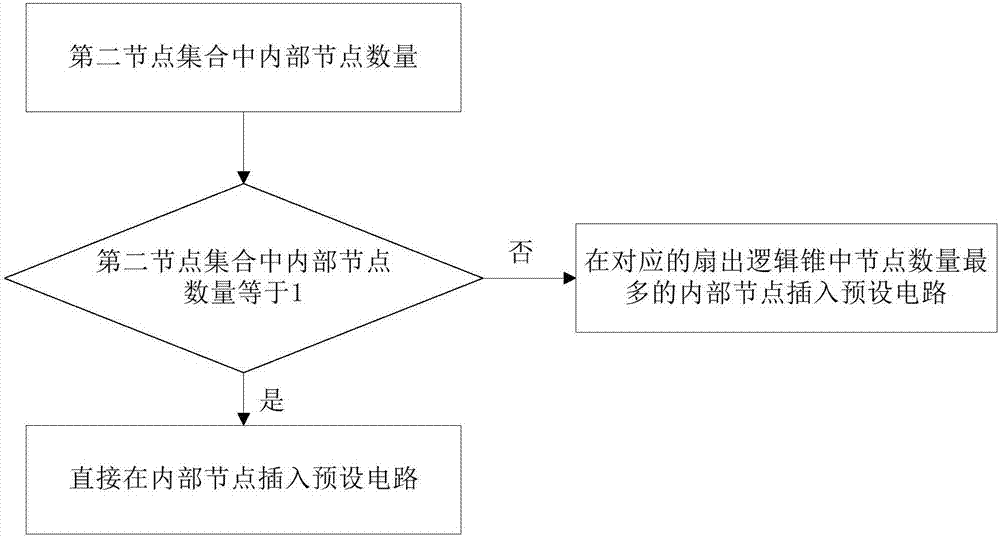
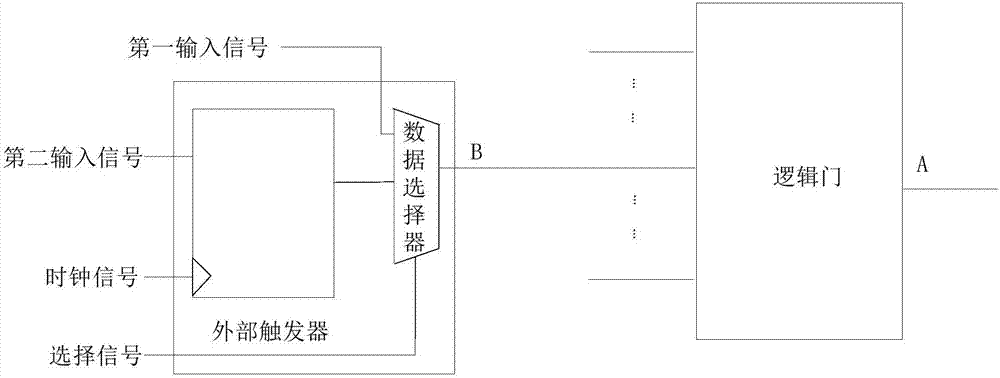
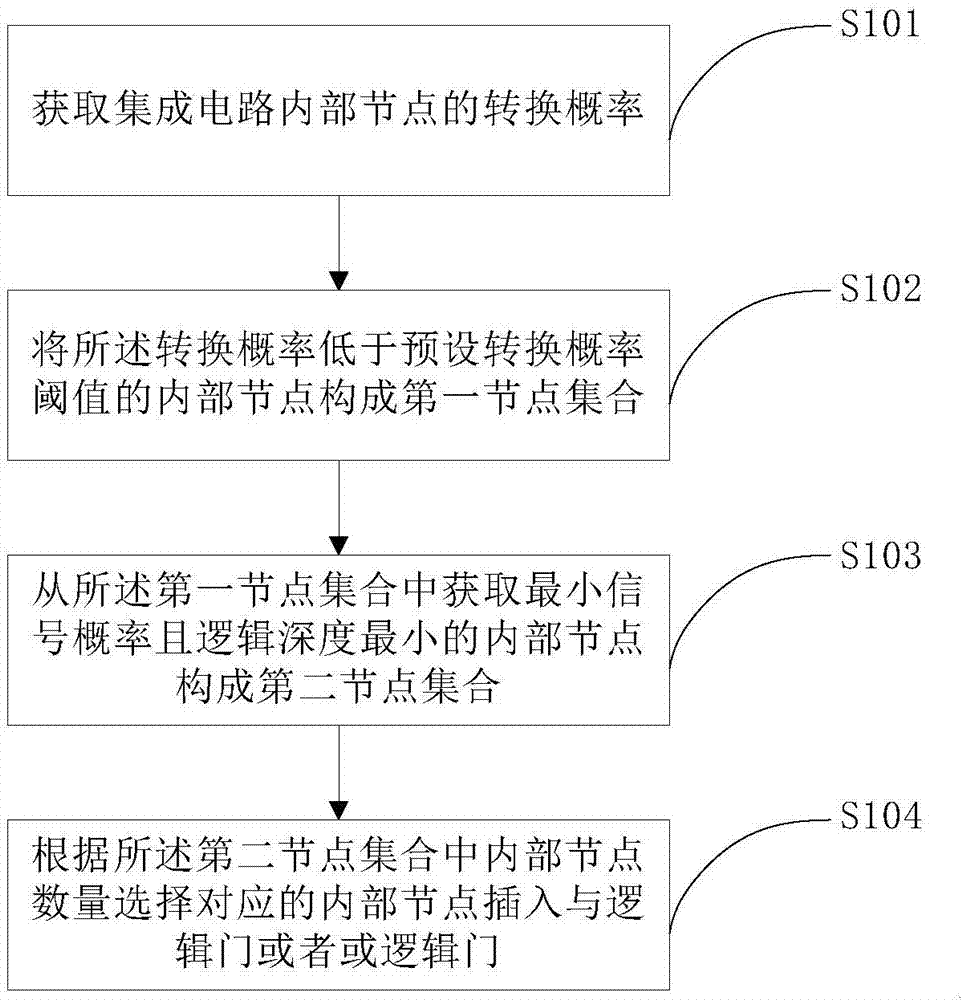
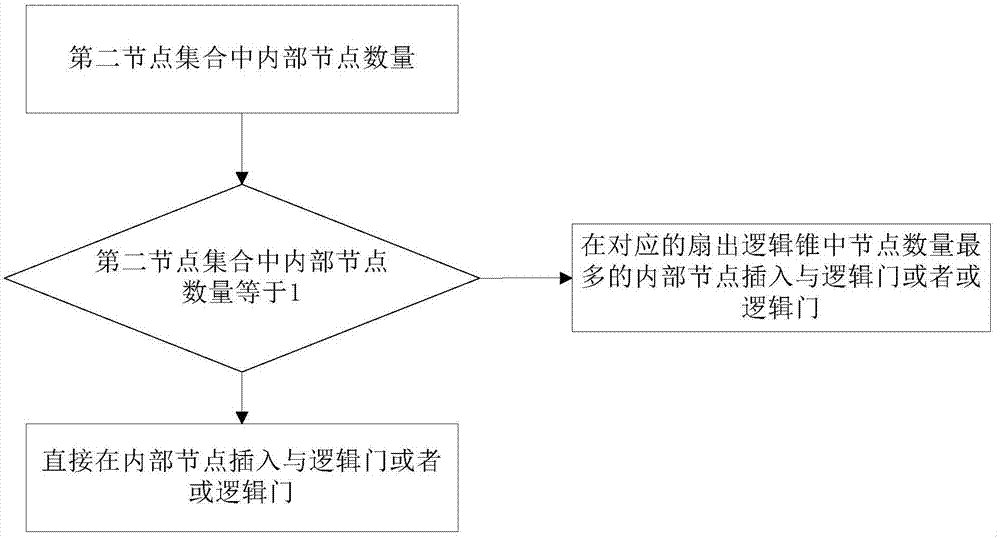
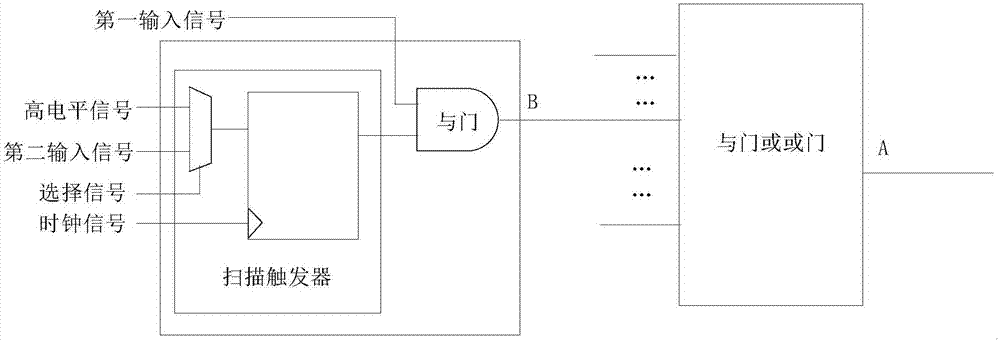
InactiveCN107239620AHigh activation rateReduce the risk of attackInternal/peripheral component protectionSpecial data processing applicationsMultiplexerHardware Trojan
The embodiment of the invention discloses a hardware trojan resistant integrated circuit design method and system. The hardware trojan resistant integrated circuit design method comprises the steps that internal nodes with integrated circuit conversion probability lower than a preset conversion probability threshold value form a first node set; the internal nodes having the lowest signal probability and smallest logic depth in the first node set are selected to form a second node set; according to the number of the internal nodes in the second node set, corresponding internal nods are selected to be inserted into a preset circuit, wherein the preset circuit comprises a one-from-two multiplexer and one scanning trigger; when the key path delay of an integrated circuit after preset circuit insertion is compared with the key path delay of an original integrated circuit, whether new internal nodes are needed for replacement and need to be inserted into the preset circuit or not is determined. After the corresponding internal nods are selected to be inserted into the preset circuit, the node conversion probability is improved, the activated probability is improved when hardware trojan selecting nodes are inserted, so that hardware trojans cannot find appropriate insertion nodes to be inserted into the integrated circuit, the risk that the integrated circuit is attached by hardware trojans is reduced.
Owner:SOUTHWEST JIAOTONG UNIV +1
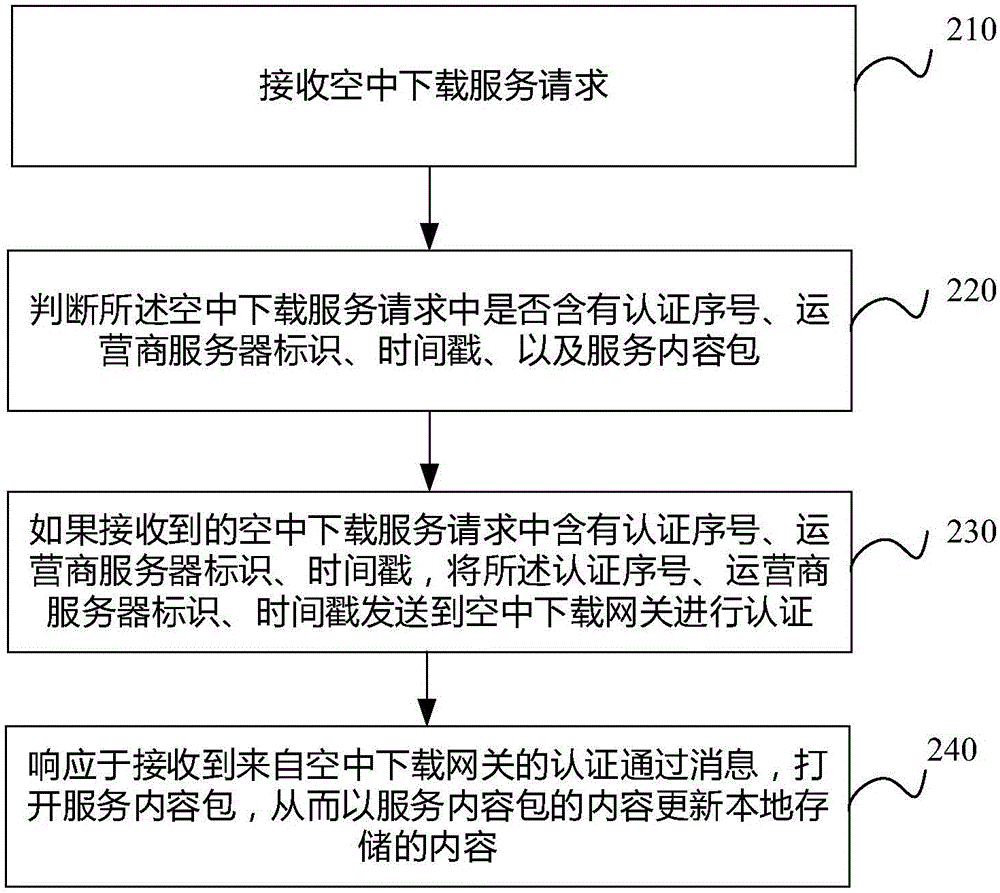
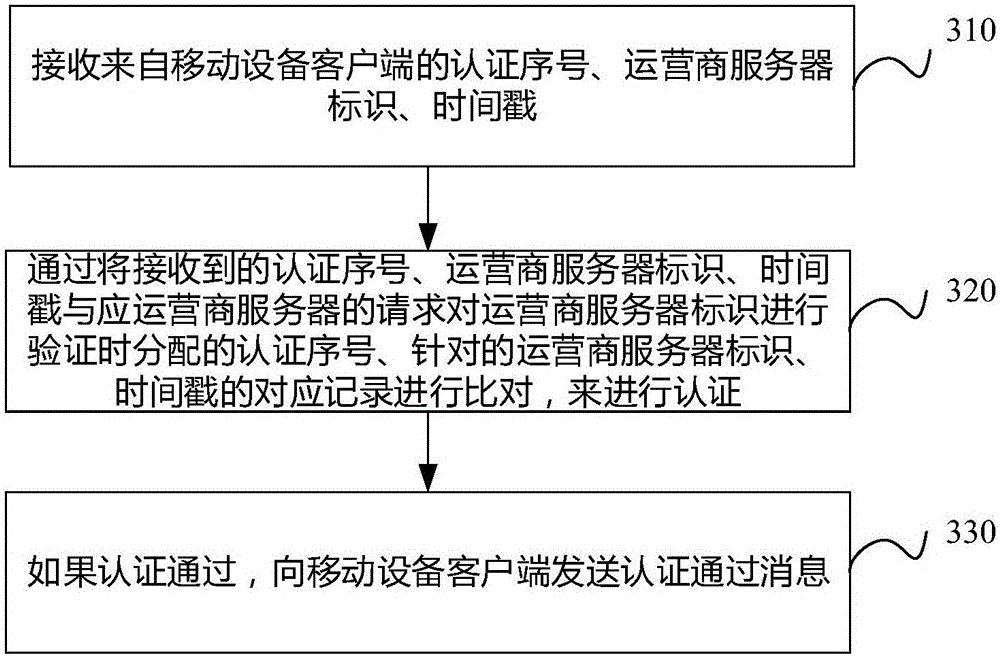
Over-the-air (OTA) method and device with risk control function and equipment
ActiveCN106535168AReduce the risk of attackImprove securitySecurity arrangementNetwork data managementRisk ControlTimestamp
The invention discloses an over-the-air (OTA) method and device with a risk control function and equipment. The method comprises the following steps: receiving an OTA service request; judging whether the OTA service request includes an authentication serial number, an operator server identifier, a timestamp and a service content package or not; if the received OTA service request includes the authentication serial number, the operator server identifier and the timestamp, transmitting the authentication serial number, the operator server identifier and the timestamp to an OTA gateway in order to compare with corresponding records of an authentication serial number, a specific operator server identifier and a timestamp which are allocated by the OTA gateway to authenticate the operator server identifier at the request of an operator server for authentication; and opening the service content package in response to an authentication pass message received from the OTA gateway in order to update locally-stored content according to content of the service content package. Through adoption of the OTA method and device with the risk control function and the equipment, the security of the OTA method is enhanced.
Owner:BEIJING BANGCLE TECH CO LTD
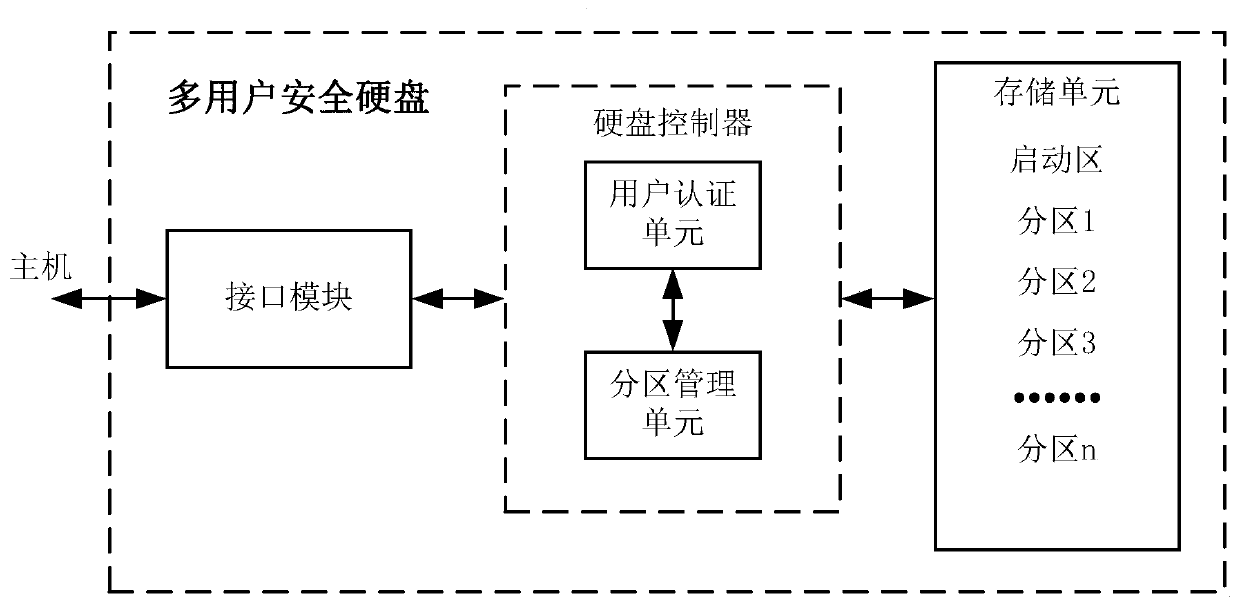
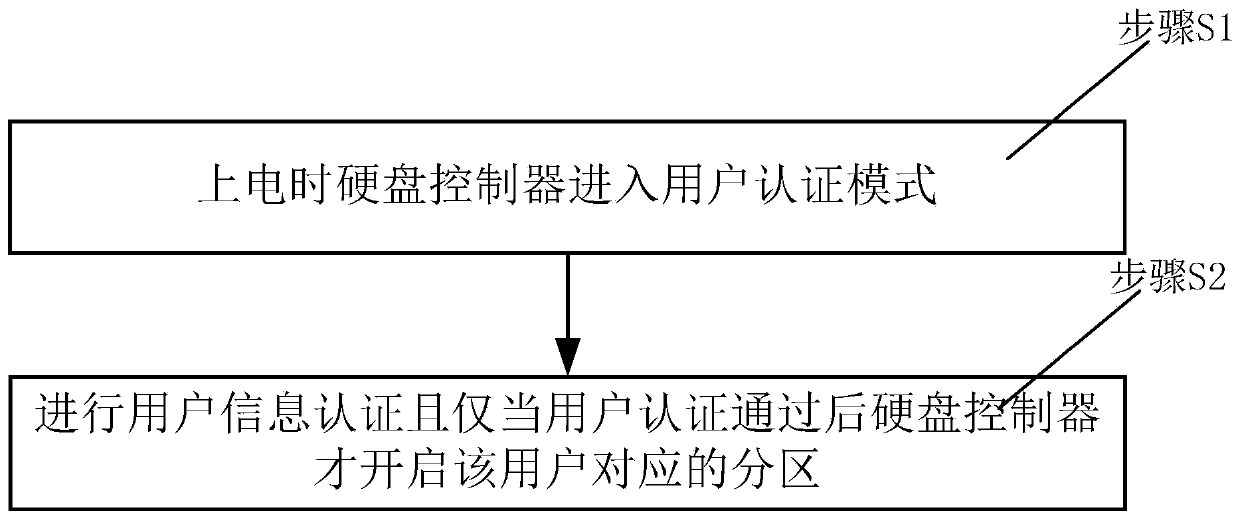
A multi-user security hard disk and a control method thereof
InactiveCN109711206AReduce the risk of attackEasy to operate independentlyInternal/peripheral component protectionManagement unitDisk controller
The invention discloses a multi-user security hard disk and a control method thereof, the multi-user security hard disk at least comprises an interface module, a hard disk controller and a storage unit, and the interface module is used for carrying out data communication with a host; the storage unit opens up a plurality of independent partitions for multi-user data storage; the hard disk controller is connected with the interface module and the storage unit, is used for controlling the work of the storage unit according to an instruction of the host, and at least comprises a user authentication unit and a partition management unit, and the user authentication unit is used for carrying out user information authentication and sending authentication result information to the partition management unit; and the partition management unit is used for managing the corresponding partition of the storage unit according to the authenticated user information, so that the hard disk controller canonly perform read-write operation on the partition. Compared with the prior art, the physical isolation of each user data storage area is realized through the bottom chip of the storage equipment, sothat the data security performance is greatly improved.
Owner:SAGE MICROELECTRONICS CORP
History-based downgraded network identification
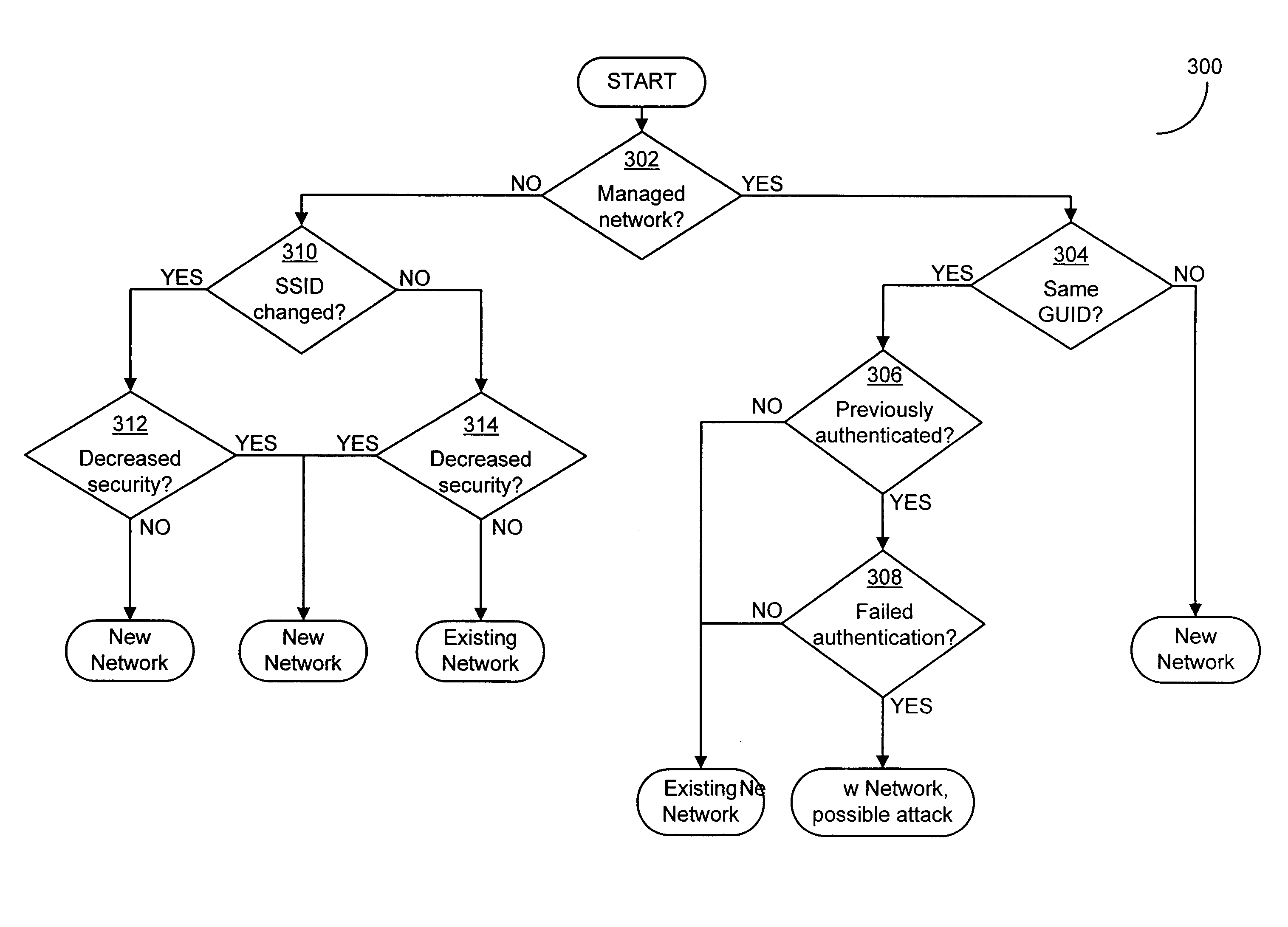
ActiveUS8769639B2Improve securityReduce the risk of attackDigital data processing detailsUser identity/authority verificationLower riskClient-side
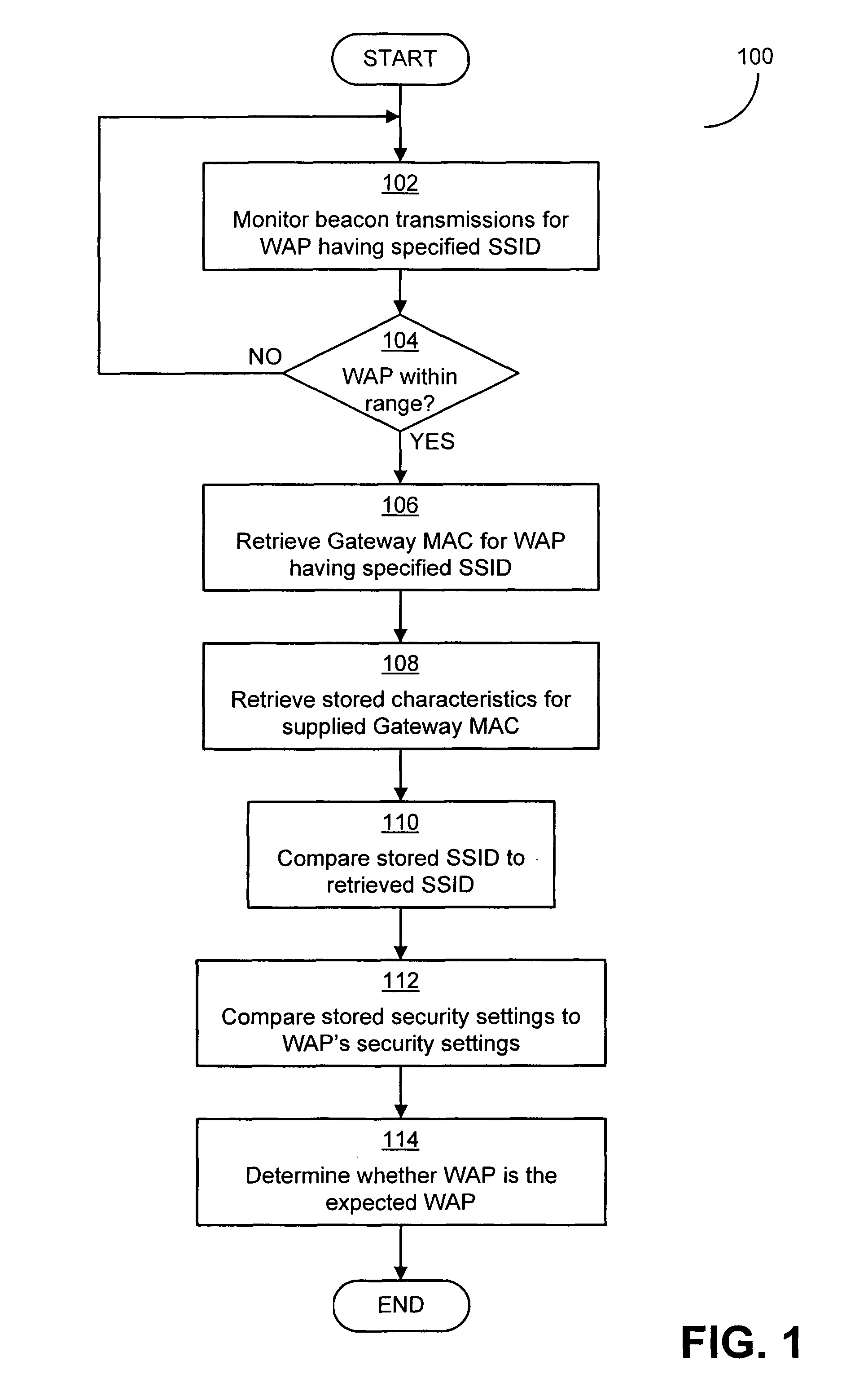
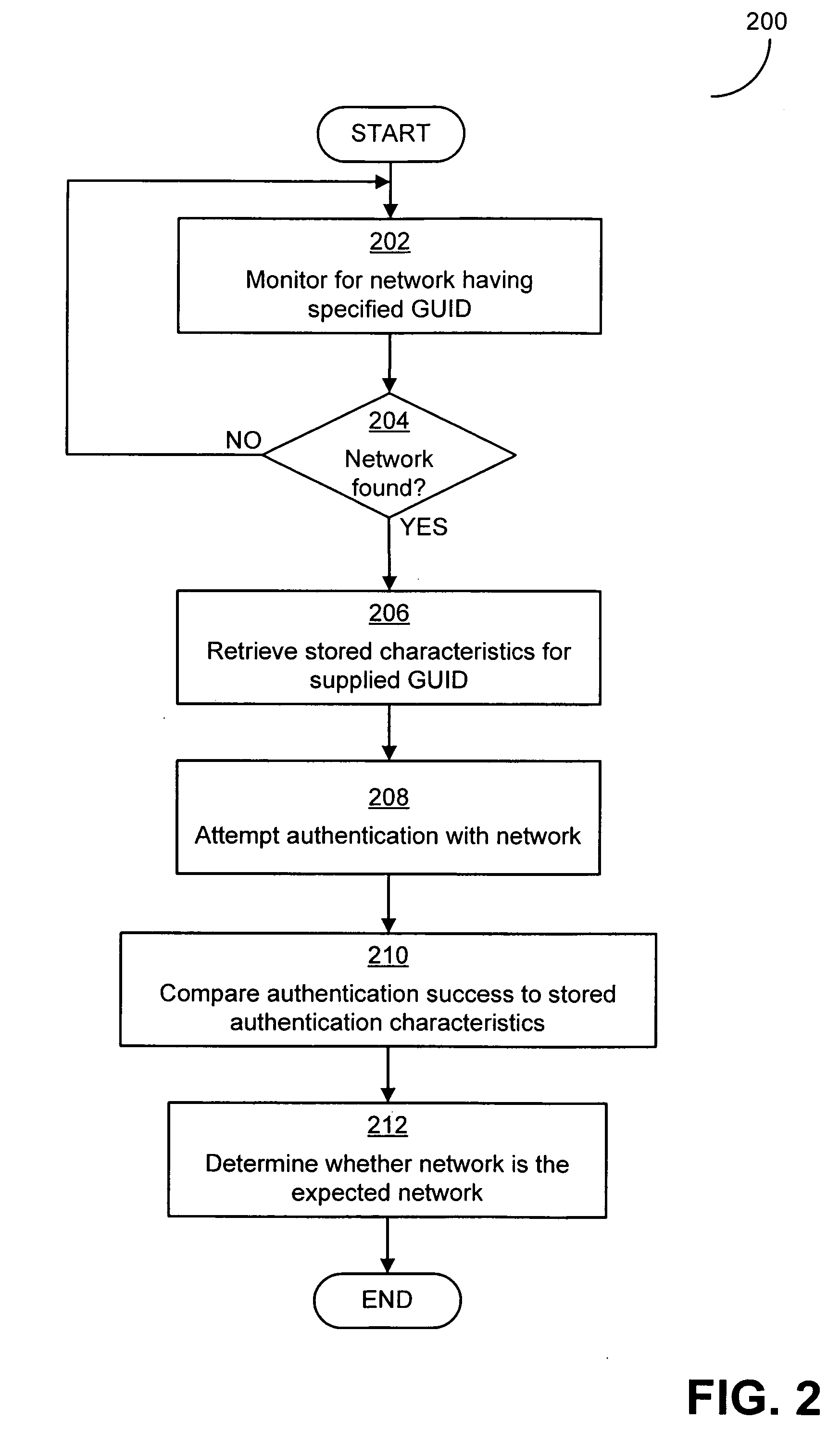
Some embodiments of the invention are directed to increasing security and lowering risk of attack in connecting automatically to networks by enabling client devices to verify the identity of the networks by, for example, confirming the identity of networks and network components such as wireless access points. In some embodiments, a client device may maintain a data store of characteristics of a network—including, for example, characteristics of a wireless access point or other portion of the network and / or characteristics of a connection previously established with the wireless access point and / or network. Stored characteristics may include characteristics other than those minimally necessary to identify a wireless access point and / or wireless network. The stored characteristics may be compared to known good characteristics of a network (including characteristics of a wireless access point or other portion of the wireless network) prior to connection to the network to determine whether the characteristics match.
Owner:MICROSOFT TECH LICENSING LLC
Router with infrared detection equipment
The invention discloses a router with infrared detection equipment. The router comprises a router main body and further comprises the infrared detection equipment, wherein the infrared detection equipment comprises a base, a connecting plate and an infrared sensor; the base is connected with the router main body; the bottom end of the connecting plate is connected with the base; and the infrared sensor is connected with the top of the connecting plate. The router with the infrared detection equipment disclosed by the invention has the advantages that: the infrared detection equipment is arranged and a power supply of the router is automatically switched off after a user leaves away for a period of time, so that the danger of attacking the router is greatly reduced; and meanwhile, when the user is close to the router, the power supply is automatically switched on, so that the use is very convenient.
Owner:SUZHOU XINRUILA PHOTOELECTRIC TECH
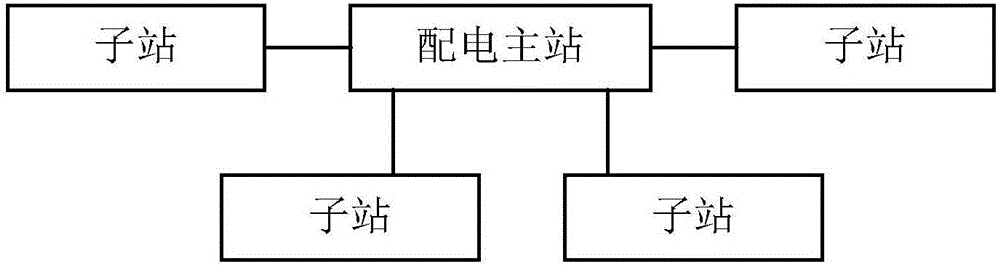
Power distribution safety protection monitoring system
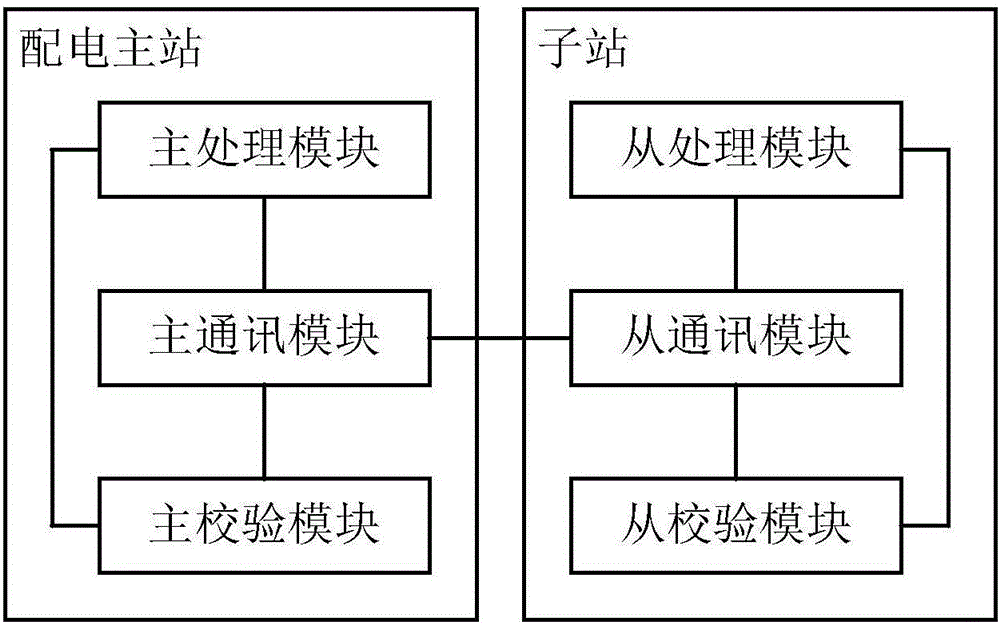
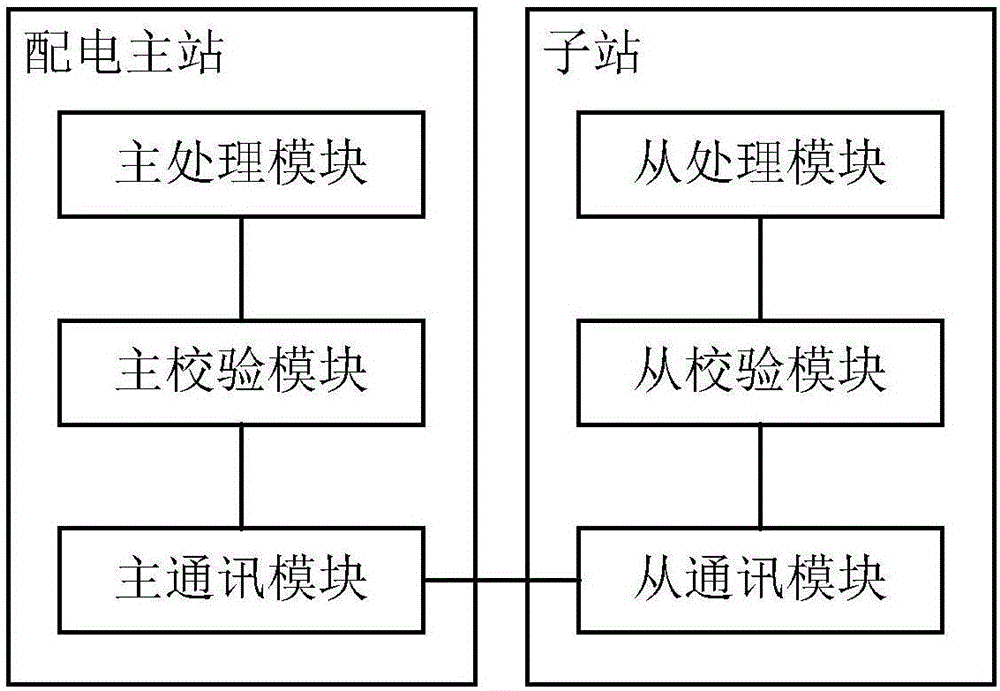
ActiveCN106549502AReduce the risk of attackSafe and stable operationCircuit arrangementsInformation technology support systemMaster stationMonitoring system
The invention discloses a power distribution safety protection monitoring system, which comprises a power distribution master station and a plurality of substations. The power distribution master station is provided with a master processing module, a master check module and a master communication module. Each substation is provided with a slave processing module, a slave check module and a slave communication module. The master communication module is in communication connection with the slave communication modules; the master communication module and the slave communication modules are used for communication data two-way transmission; the master check module is connected with the master processing module and the master communication module, and is used for checking substation identity information in the communication data received by the master communication module, and after the check passes, the master processing module carries out processing on substation control information in the communication data; and the slave check modules are connected with the slave processing modules and the slave communication modules. The new power distribution safety protection monitoring system can improve power distribution safety protection in both-way communication.
Owner:ELECTRIC POWER SCI RES INST OF GUIZHOU POWER GRID CO LTD
Design method and system for anti-hardware Trojan horse chip
InactiveCN107016223AHigh activation rateReduce the risk of attackCAD circuit designSpecial data processing applicationsComputer hardwareHardware Trojan
The embodiment of the invention discloses a design method and system for an anti-hardware Trojan horse chip. The method comprises the following steps of: acquiring the conversion probability of internal nodes of an integrated circuit; forming a first node set by internal nodes, the conversion probability of which is smaller than a predetermined conversion probability threshold value; acquiring the minimal signal probability from the first node set and forming a second node set by the internal nodes, the logic depths of which are the smallest; and selecting corresponding internal nodes according to the quantity of the internal nodes in the second node set, and inserting the internal nodes into an and logic gate or an or logic gate. After the selected corresponding internal nodes are inserted into the and logic gate or the or logic gate, the conversion probability of corresponding nodes is increased, and the corresponding conversion probability of the whole integrated circuit is also increased, so that when the hardware Trojan horse selects nodes to insert, the probability that the hardware Trojan is activated is increased, so that the hardware Trojan horse cannot find proper insertion points to be inserted into the integrated circuit, and therefore, the risk that the integrated circuit is attached by the hardware Trojan horse is reduced.
Owner:宁波汉达信息科技有限公司 +1
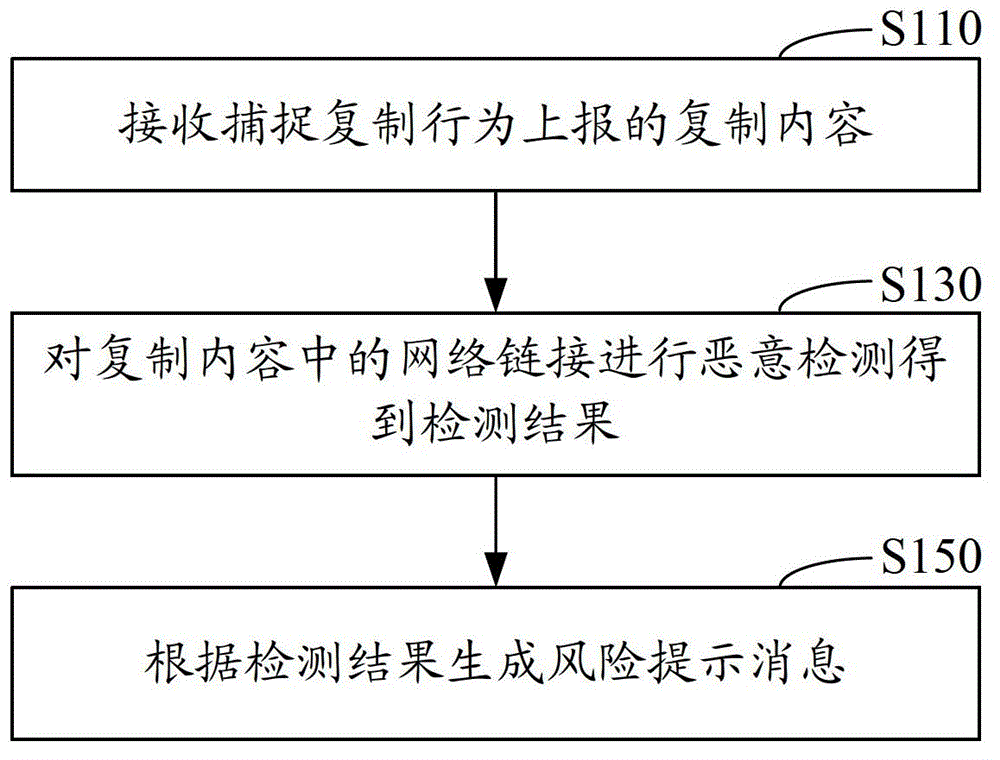
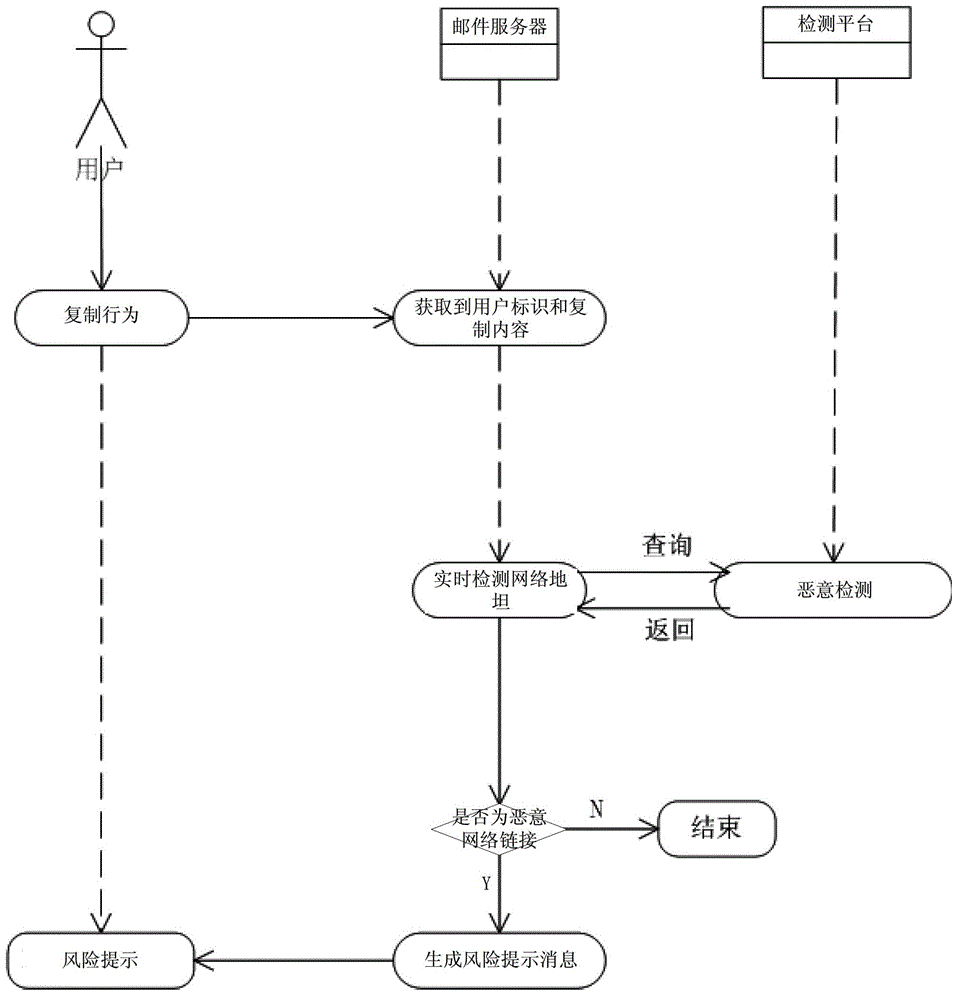
Network link detection method and system
A method and system for detecting network link are disclosed. The method includes: receiving copy content by capturing a copy behavior; performing malware detection on network link in the copy content to obtain a detection result; generating a risk warning message according to the detection result. The system includes: a receiving module, configured to receive copy content by capturing a copy behavior; a detecting module, configured to perform malware detection on network link in the copy content to obtain a detection result; a message generating module, configured to generate a risk warning message according to the detection result. The method and system can reduce the attack risk of malicious network link.
Owner:TENCENT TECH (SHENZHEN) CO LTD
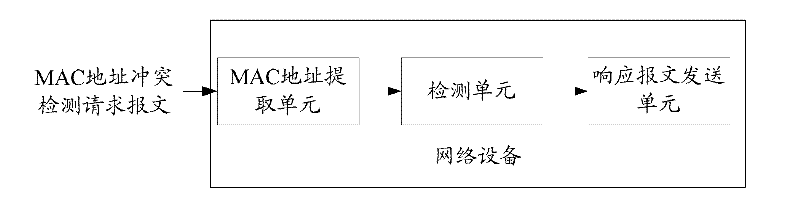
Medium/media access control address conflict detection method, device and system
ActiveCN102333134AAvoid conflict situationsEasy accessData switching networksMulticast addressNetwork attack
The invention provides a medium / media access control (MAC) address conflict detection method, which comprises that: before accessing a network, local network equipment transmits a MAC address conflict detection request message to a destination multicast address, wherein the request message carries a current MAC address of the network equipment; destination network equipment receiving the request message extracts the MAC address from the message request, detects the MAC address, and when judging that the extracted MAC address is the same as own MAC address, transmits a MAC address conflict detection response message to a requesting multicast address; and the local network equipment receiving the response message generates a new MAC address. The invention also discloses a MAC address conflict detection device and a MAC address conflict detection system. By the method, the device and the system, the occurrence of MAC address conflicts can be effectively avoided, the network equipment can be ensured to access the network normally, normal network service can be provided for a user, and risks in network attacks can be reduced.
Owner:ZTE CORP
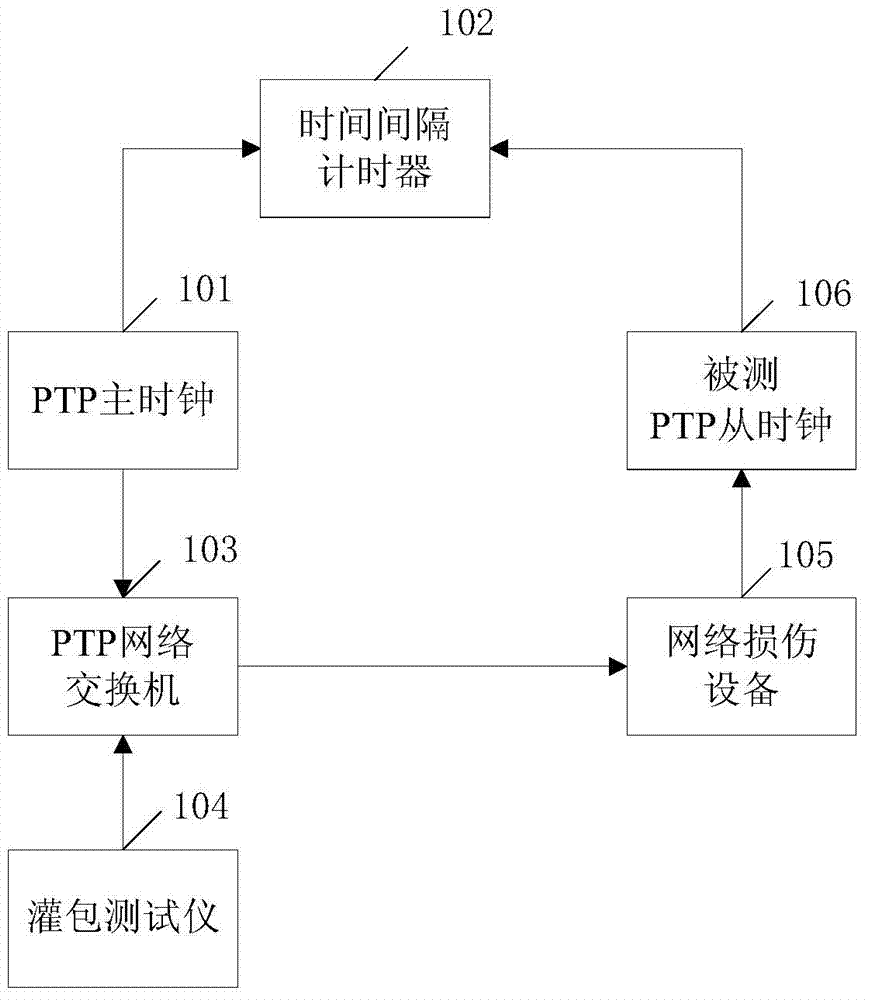
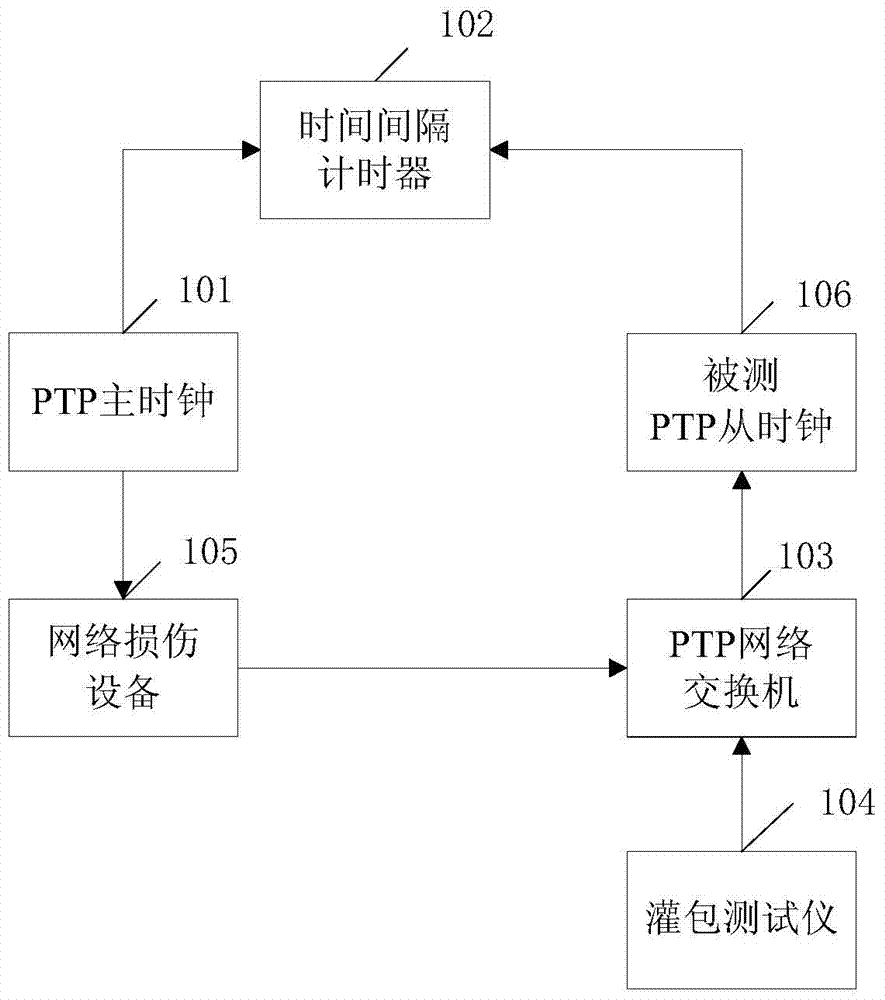
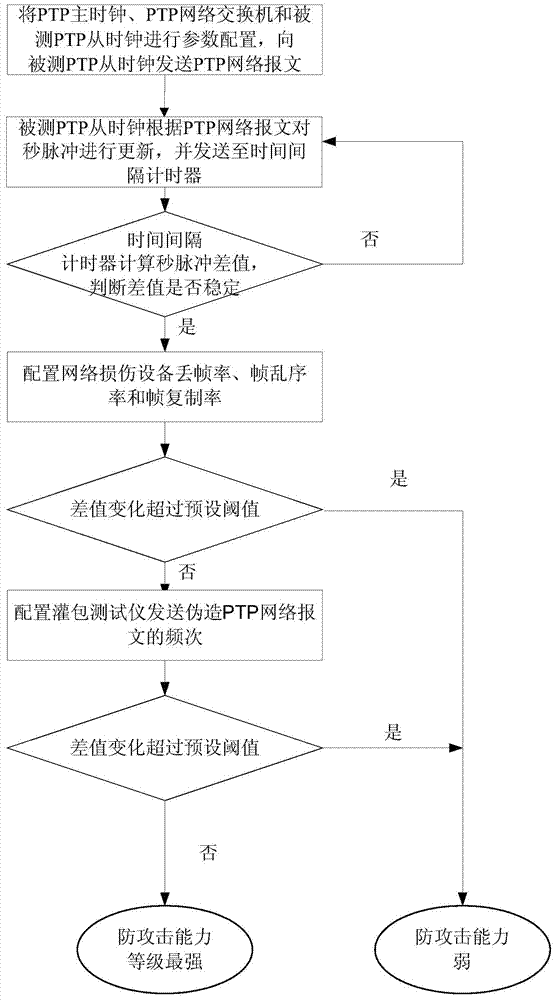
Attack testing method and system of precision time synchronization protocol (PTP) clock
InactiveCN104852827AComprehensive testing methodsReduce the risk of attackData switching networksReal-time computingTime synchronization
The present invention discloses an attack testing system of a precision time synchronization protocol (PTP) clock. The system comprises a PTP main clock connected with an interval timer and a PTP network switch; a bagging tester connected with the PTP network switch, the PTP network switch also being connected with a network damage device; the network damage device also connected with an under-test PTP slave clock; and the under-test PTP slave clock also connected with the interval timer, wherein the interval timer is used for receiving and calculating a difference value between pulses per second sent by the PTP main clock and pulses per second sent by the under-test PTP slave clock, and determining the anti-attack capability of the under-test PTP slave clock according to the difference value. Another attack testing system of a PTP clock and an attack testing method of the PTP clock are also provided. With adoption of the system and the method provided by the present invention, the anti-attack capability of the PTP clock can be tested and judged, the PTP clocks can be improved by researchers according to test results, and under attack risks are reduced.
Owner:STATE GRID ELECTRIC POWER RES INST +1
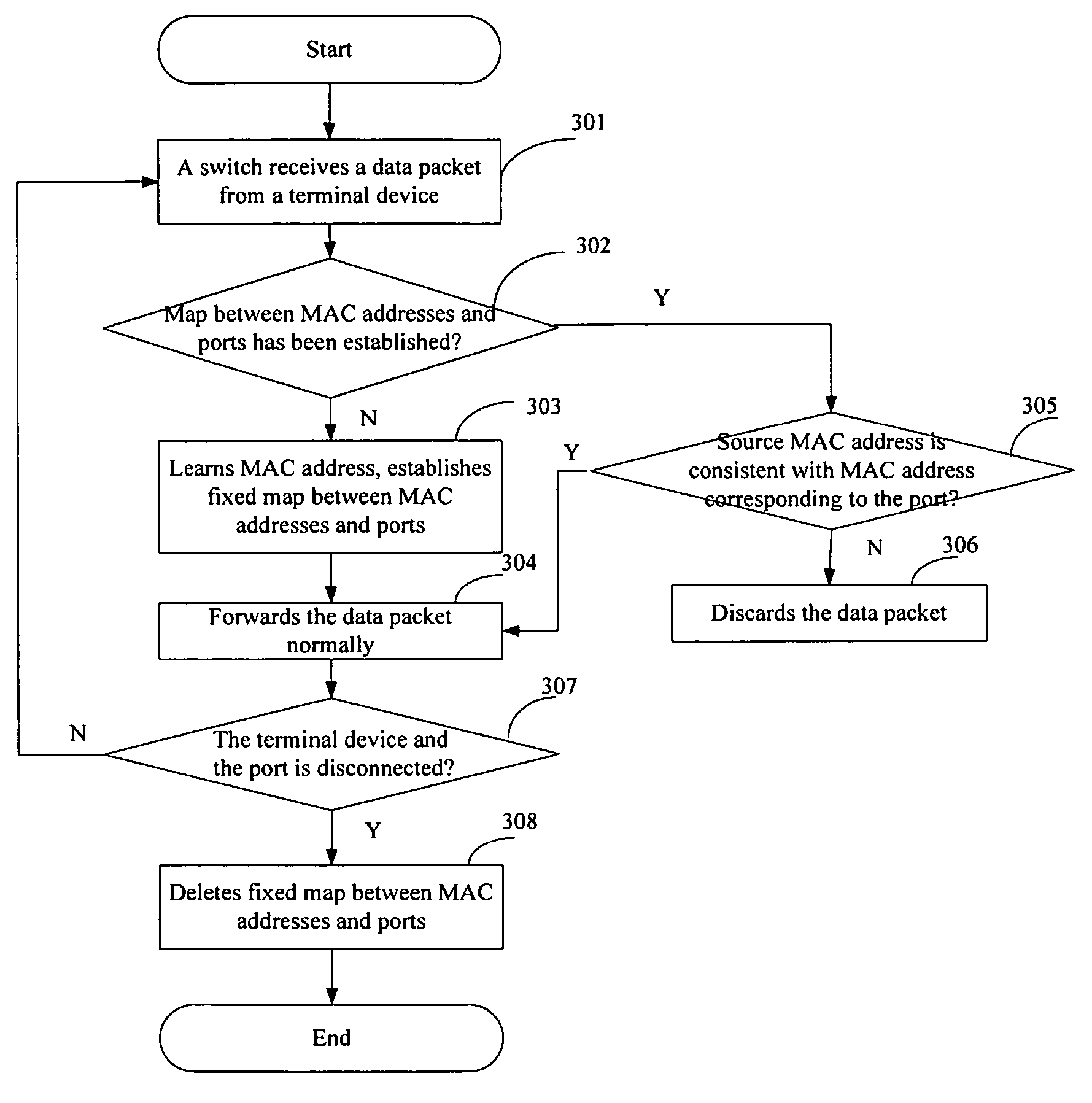
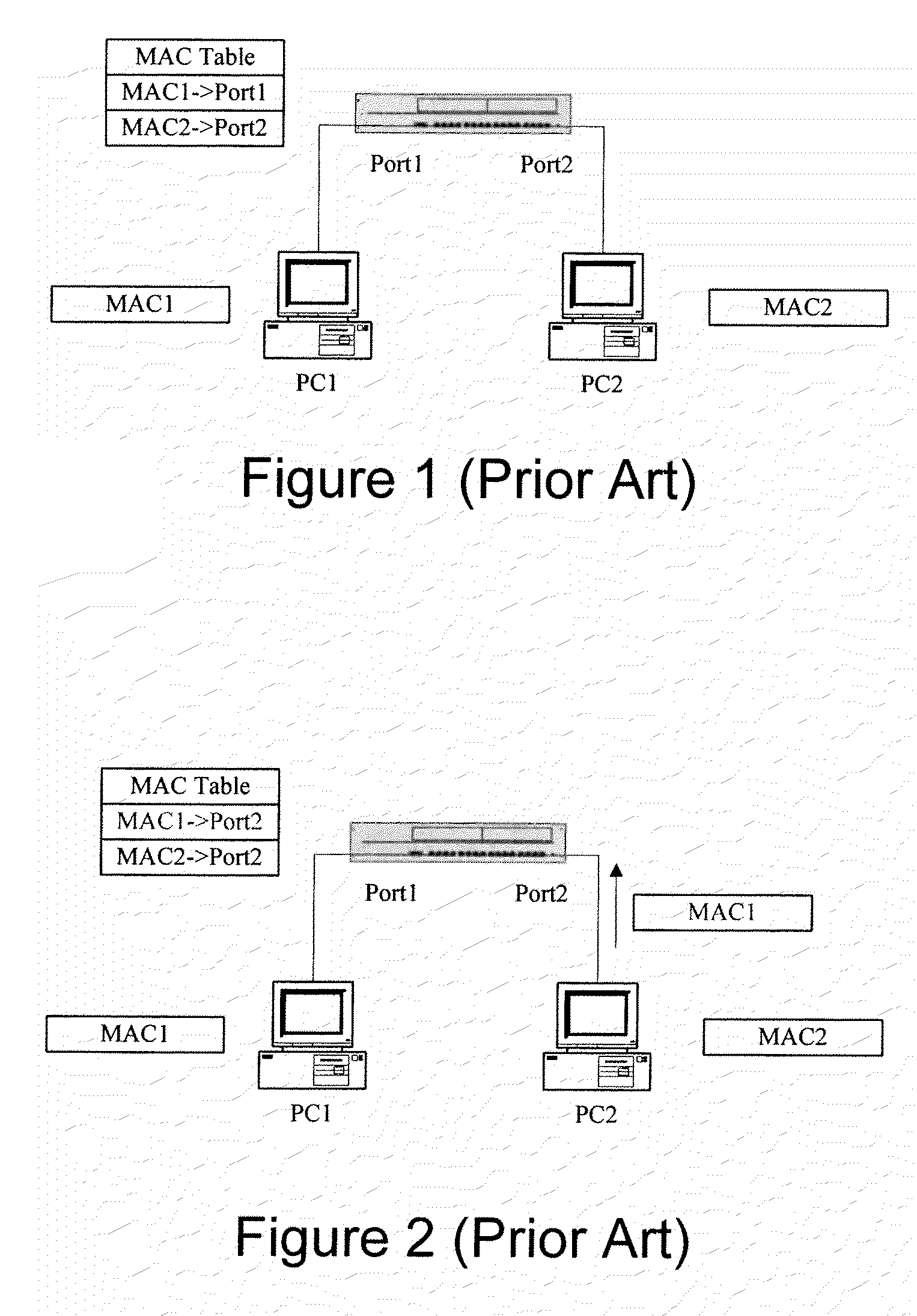
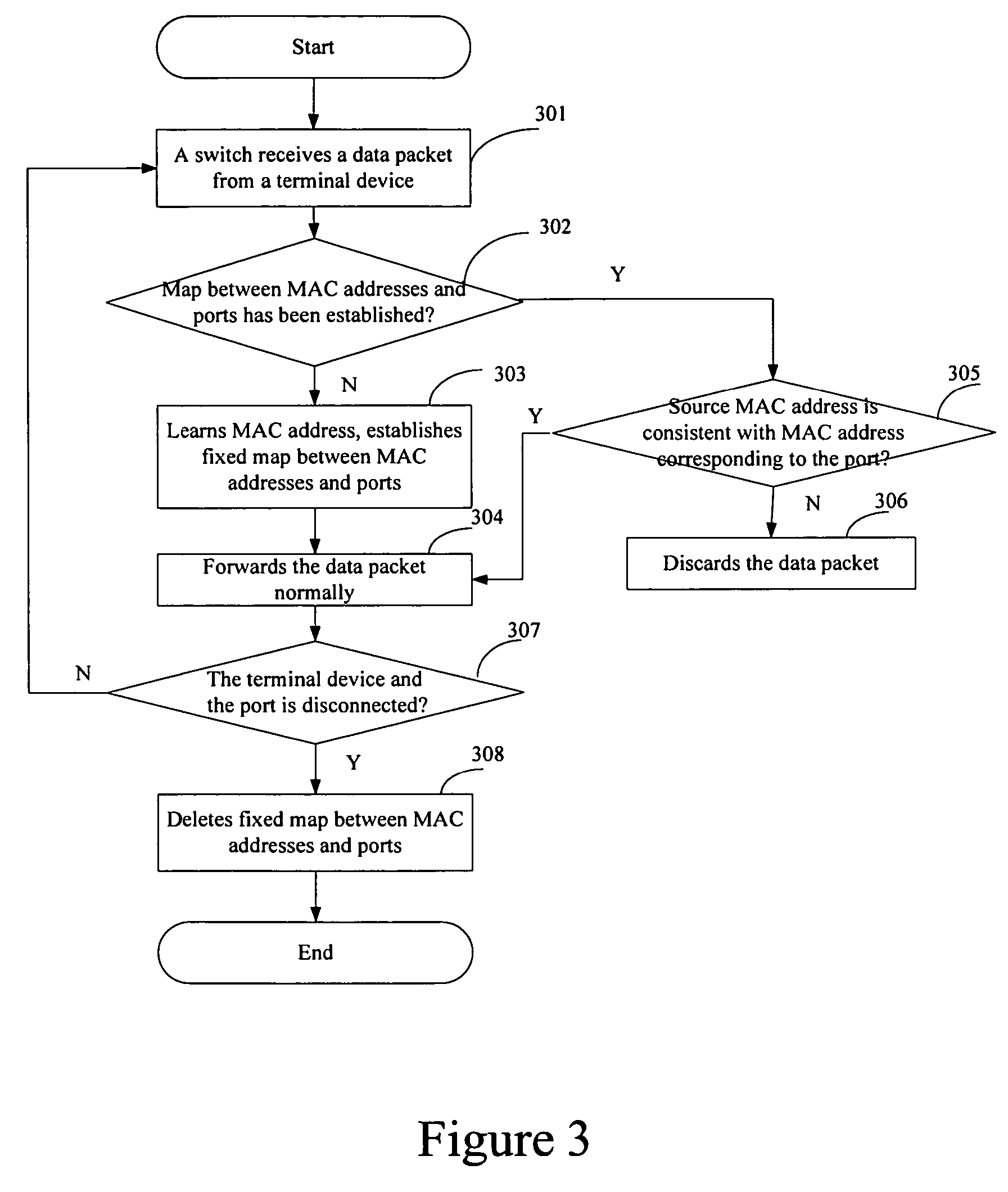
Method for preventing Ethernet from being attacked
ActiveUS7720069B2Improve maintenance efficiencyReduce maintenance costsMemory loss protectionError detection/correctionNetwork packetTerminal equipment
A method for preventing Ethernet from being attacked is provided. The method comprises the steps as follows: after detecting a new connection between a port and a terminal device and receiving a data packet from the terminal device, an Ethernet communication device establishing and storing a fixed map between the port and a hardware address of the terminal device, then forwarding the data packet according to the fixed map; after detecting a disconnection between the port and the terminal device, the Ethernet communication device deleting the fixed map.
Owner:HUAWEI TECH CO LTD
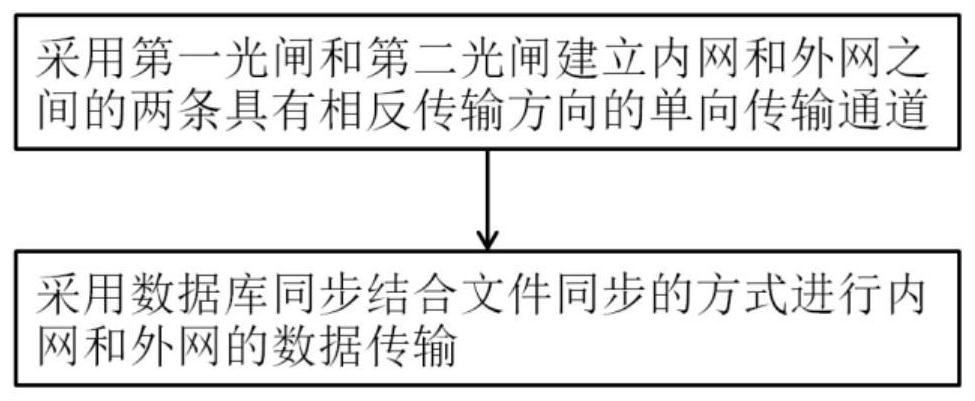
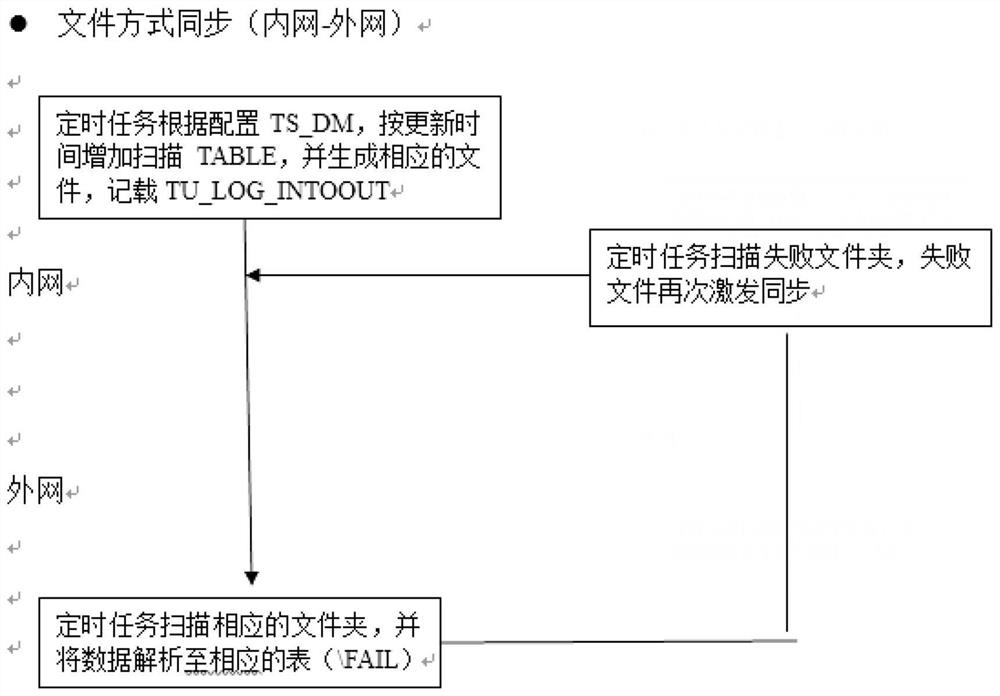
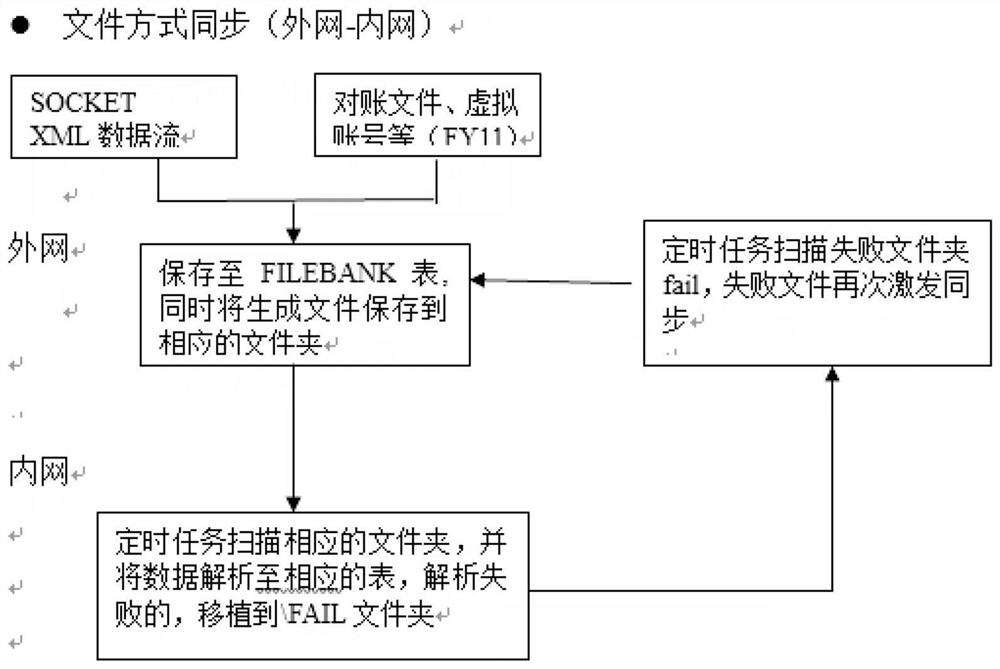
Safe transmission method and system suitable for financial information
ActiveCN111865969AFix security issuesEffective protectionDatabase distribution/replicationTransmissionFile synchronizationSecure transmission
The invention discloses a safe transmission method suitable for financial information, which comprises the following steps of: establishing two unidirectional transmission channels with opposite transmission directions between an intranet and an extranet by adopting a first optical shutter and a second optical shutter, and transmitting data of the intranet and the extranet by adopting a mode of combining database synchronization with file synchronization. According to the invention, one-way transmission of data between the intranet and the extranet can be ensured by adopting the two optical gates for one-way transmission; and then, the secure transmission of the intranet data and the extranet data is realized by adopting a file synchronization and database synchronization mode, so that thesecurity problem of data transmission in the financial industry is successfully solved, the user information is effectively protected, and a corresponding basis is provided for social stability.
Owner:江苏润易联信息技术有限公司
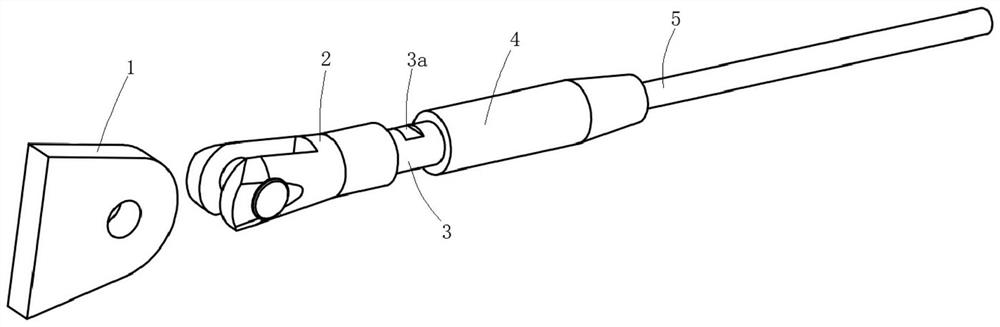
Cable tensioning device
ActiveCN108360820BReduce the risk of attackEnsure safetyBridge structural detailsBuilding material handlingRemote controlControl theory
The invention relates to the field of inhaul cable pre-stressed structure construction devices, in particular to an inhaul cable tensioning device. In the prior art, the inhaul cable tensioning construction adopts manual construction through a wrench, the labor intensity is high, the construction is dangerous and cannot be constructed in extreme environment. The invention provides the inhaul cabletensioning device. The inhaul cable tensioning device comprises a node plate, a fork ear anchorage device, a connecting nut and a connecting anchorage device which are connected in sequence. The nodeplate is used for connecting with a connecting inhaul cable or a building, the fork ear anchorage device is connected with the node plate through a pin shaft, and the connecting anchorage device is internally connected with an inhaul cable; and the inhaul cable tensioning device further comprises a power device, the input end of the power device is used for connecting with a remote control deviceto realize the purpose of remotely controlling the rotation of the connecting nut, and the output end of the power device is connected with the connecting nut and used for driving the connecting nutto rotate. Compared with the prior art, the inhaul cable tensioning device has the advantages of low labor intensity, suitability for extreme environments, and safe use.
Owner:北京奇力建通工程技术有限公司
IPoE roaming session control method
ActiveCN108712411AFlexible customizationReduce the risk of attackTransmissionNetwork data managementTelecommunicationsSession control
The invention discloses a IPoE roaming session control method. The IPoE roaming session control method comprises the steps such as a corresponding strategy is matched from the roaming control strategies when one side of a BRAS receives a traffic or on-line trigger request with the same IP as an existing session. The beneficial effect of the IPoE roaming session control method is that operators cancustomize the roaming strategies flexibly according to the needs of users.
Owner:NANJING INST OF RAILWAY TECH
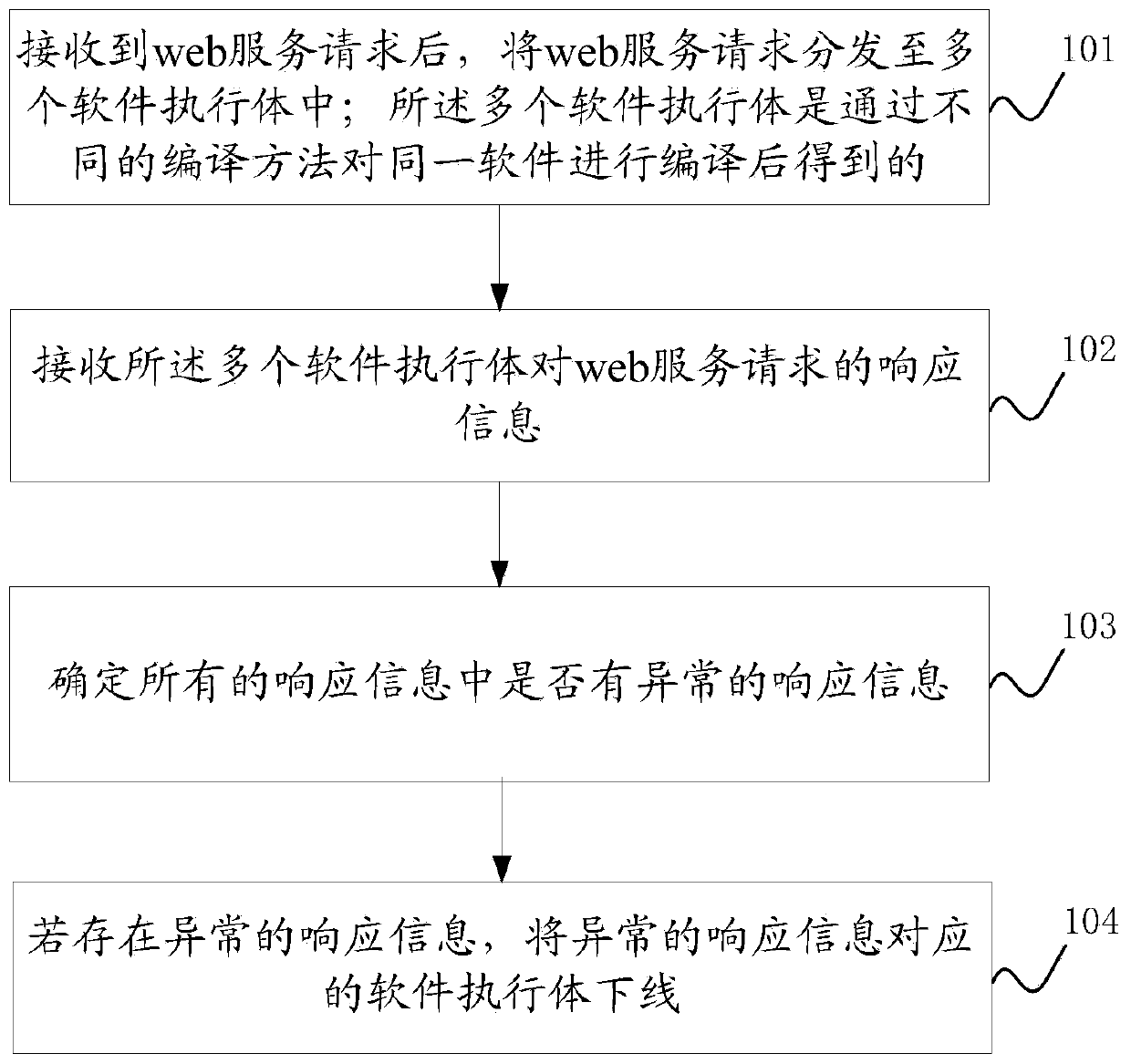
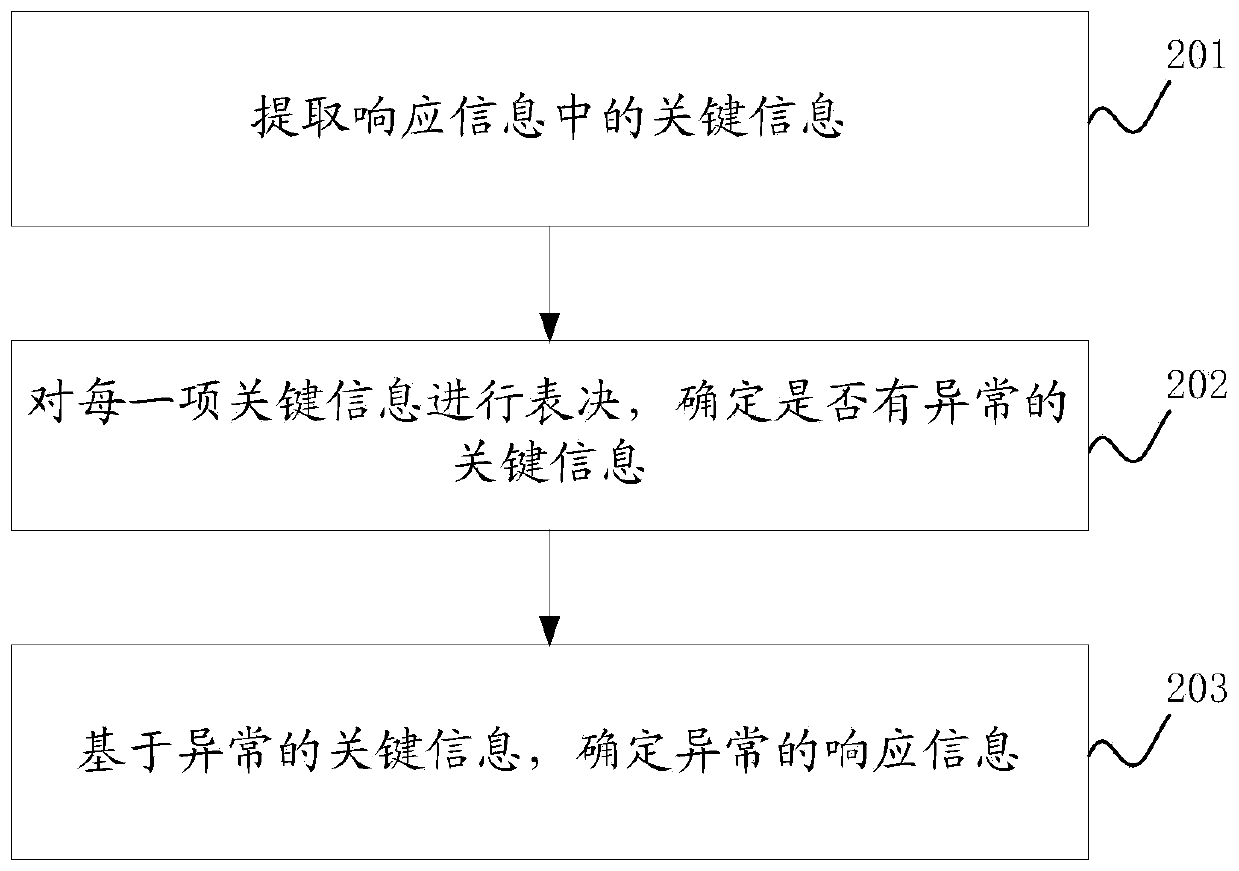
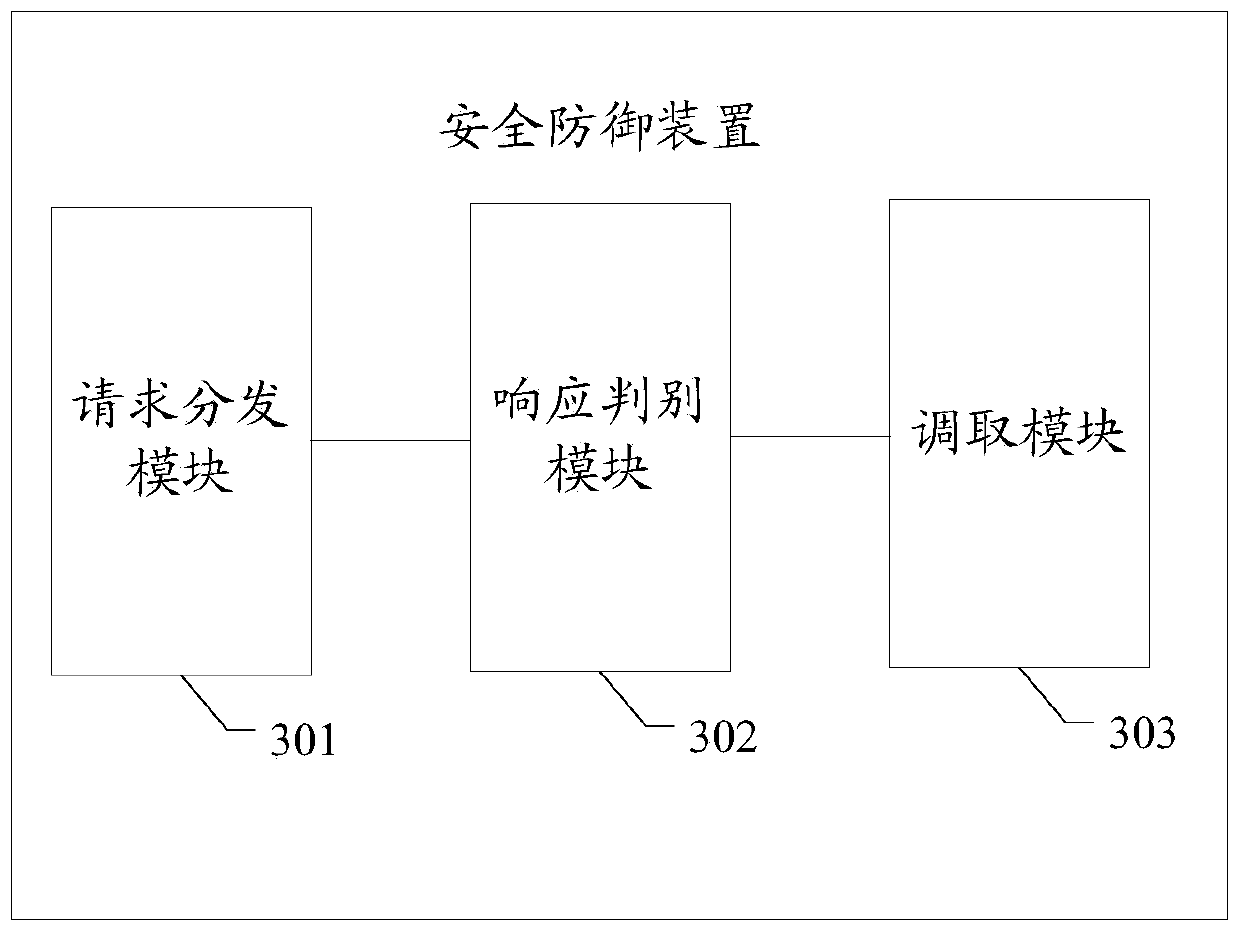
Security defense method and device
InactiveCN110784475AReduce the risk of being attackedReduce the risk of attackTransmissionWeb serviceAttack
The embodiment of the invention discloses a security defense method and device. The method comprises the following steps: distributing a web service request to a plurality of software executors, wherein the plurality of software executors are obtained by compiling the same software in different compiling modes, analyzing the response information to determine whether abnormal response information is contained or not, and offline the software executor corresponding to the abnormal response information under the condition that the abnormal response information is contained. Therefore, the functions of the software executors obtained through different compiling modes are the same, but structures are different, in this way, attacks on a certain software execution body are greatly reduced; the risk that other execution bodies of the software or execution bodies of other versions of the software are attacked is avoided, and the risk that the software is attacked is greatly reduced by selecting the abnormal response information even if the software execution body which is possibly attacked is discovered and the software execution body is offline in time.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com