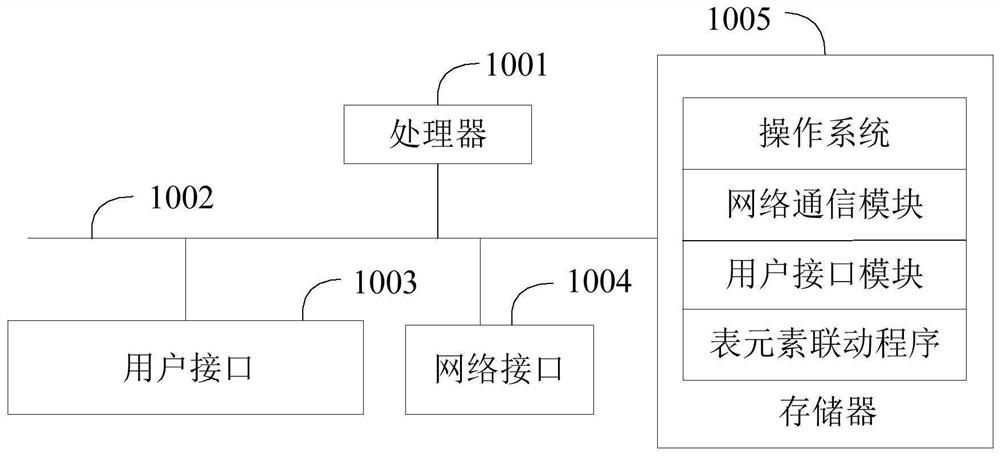
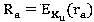Patents
Literature
81results about How to "Reduce the risk of being attacked" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
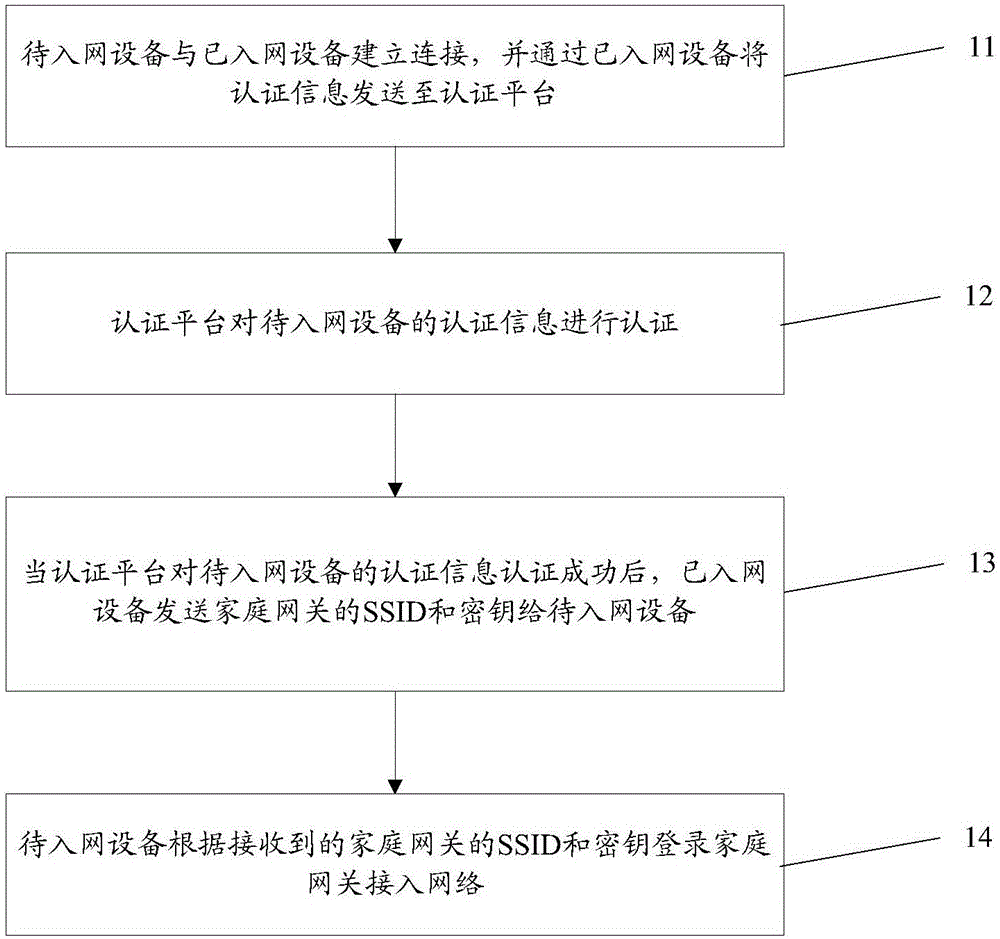
Patent Type
Patent Status
Application Year
Inventor
Automatic WIFI accessing method and system of device
ActiveCN105101206AReduce the risk of being attackedUser-friendlySecurity arrangementSmart deviceThe Internet
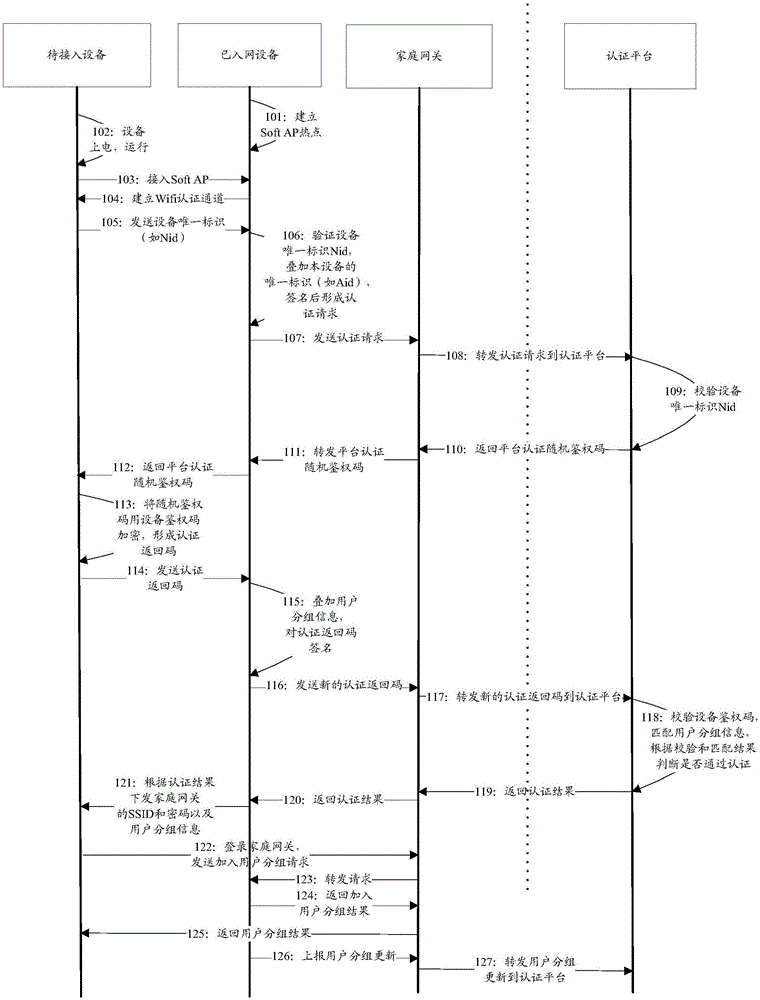
The invention discloses an automatic WIFI accessing method and system of a device. The method comprises: a device waiting for accessing to the Internet establishes connection with a device already accessing to the Internet and sends authentication information to an authentication platform via the device already accessing to the Internet, wherein the device already accessing to the Internet is already authenticated via the authentication platform and already logs in a home gateway; the authentication platform authenticates the authentication information of the device already accessing to the Internet; when the authentication platform succeeds in authenticating the authentication information of the device already accessing to the Internet, the device already accessing to the Internet sends a service set identification (SSID) and a key of the home gateway to the device waiting for accessing to the Internet; and the device waiting for accessing to the Internet logs in the home gateway according to the received SSID and key of the home gateway and then accesses to the Internet. The automatic WIFI accessing method and system of the device are capable of reducing the risk that an intelligent device is attacked in the process of automatically accessing to the Internet, and reducing user intervention.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Mimicry defense judgment method and system based on partial homomorphic encryption algorithm
ActiveCN110995409APrivacy protectionImprove securityCommunication with homomorphic encryptionCiphertextConfidentiality
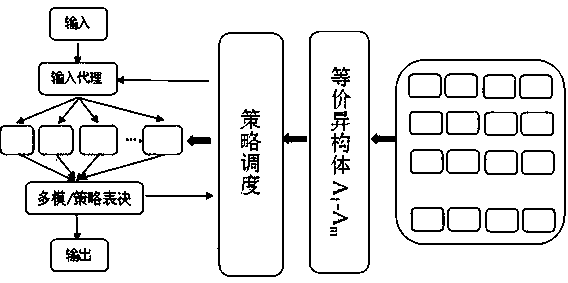
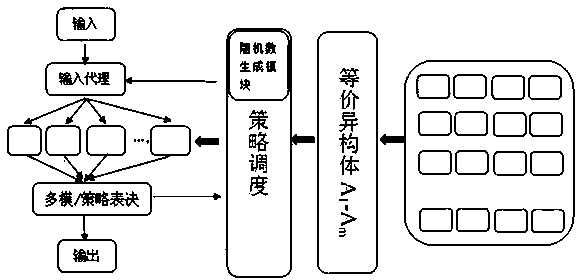
The invention discloses a mimicry defense judgment method and system based on a partial homomorphic encryption algorithm. In the judgment method, a random number and an encryption key are distributedfor a heterogeneous execution body, a ciphertext is outputted through an execution module, a judgment object is a ciphertext obtained through employing an agreed algorithm for an execution result, anda feedback system which is convenient to check and is good in confidentiality is arranged. The system comprises a strategy scheduling module, an execution module, a multimode and strategy voting module, an isomer set and the like, the strategy scheduling module is provided with a random number generation module, and the execution module is provided with a homomorphic encryption module. Accordingto the method and the system, replay attacks and the like on the judgment mode in the multimode / strategy voting system can be reduced or avoided, and the purposes of protecting user privacy, preventing data leakage and improving the safety and stability of the whole mimicry defense system are achieved.
Owner:NANJING REDMATRIX NETWORK SECURITY TECH R & D INST
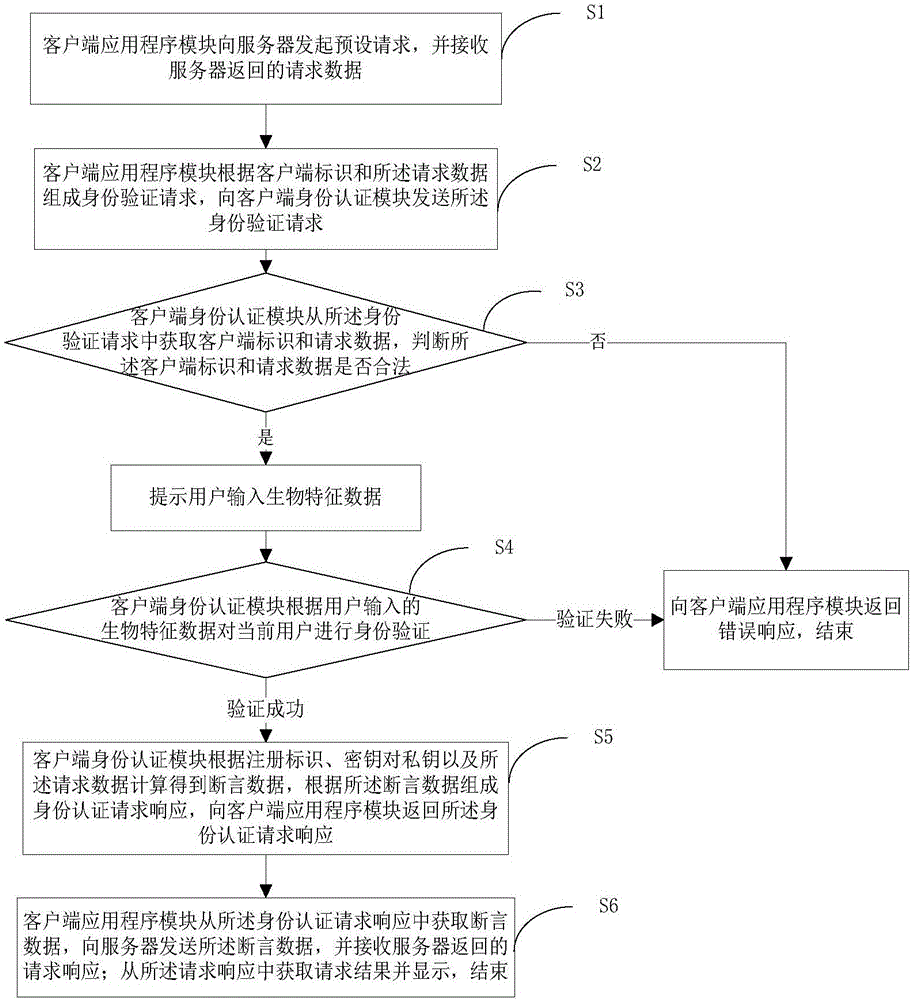
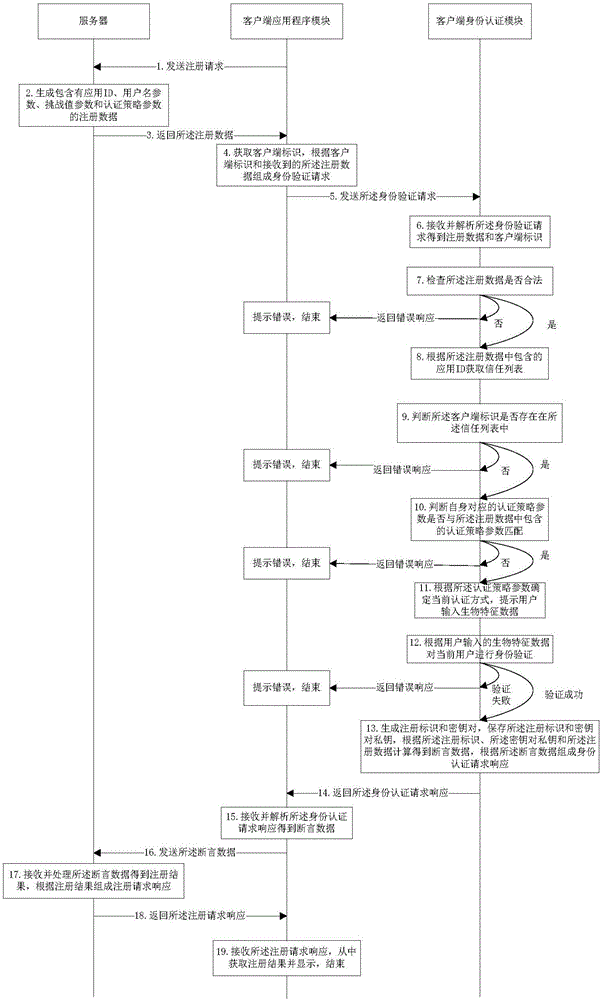
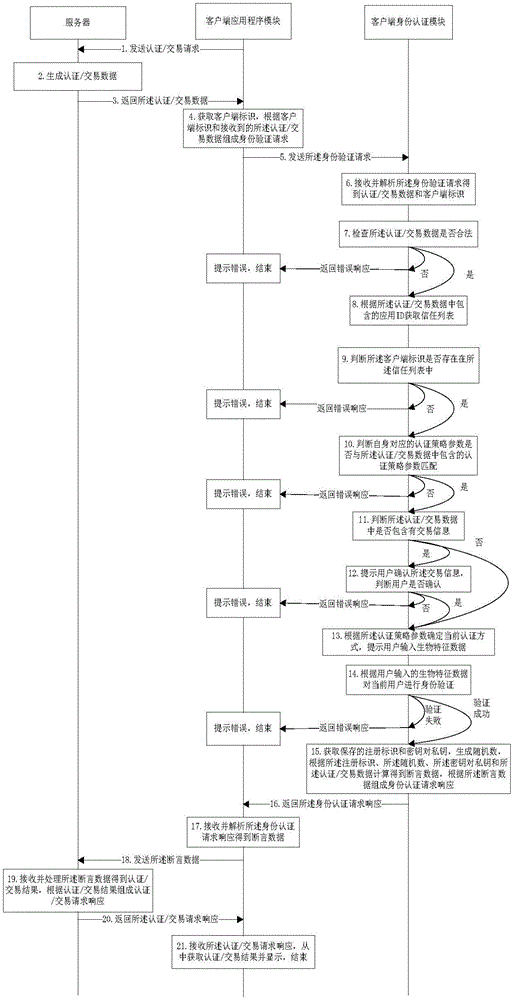
Client based on biometric feature recognition and working method thereof
InactiveCN106549973AImprove securityReduce the risk of being attackedTransmissionUser inputWorking set
The invention discloses a client based on biometric feature recognition and a working method thereof, and belongs to the field of information security. The client comprises a client application program module and a client identity authentication module, wherein the client application program module generates an identity authentication request according to a client identifier and request data acquired from a server, and sends the identity authentication request to the client identity authentication module; the client identity authentication module reminds the user to input biometric feature data for authentication after the condition that the client identifier and the request data are legal is determined, works out assertion data according to a registration identifier, a secret key and a private key if the authentication is successful, the assertion data is sent to the server via the client application program module, and the client identity authentication module receives and displays a request result returned by the server. According to the client provided by the invention, authentication of the biometric feature information of the user is completed in the client identity authentication module, the risk that the biometric feature information of the user is attacked is reduced, and user online register and login security are improved.
Owner:FEITIAN TECHNOLOGIES
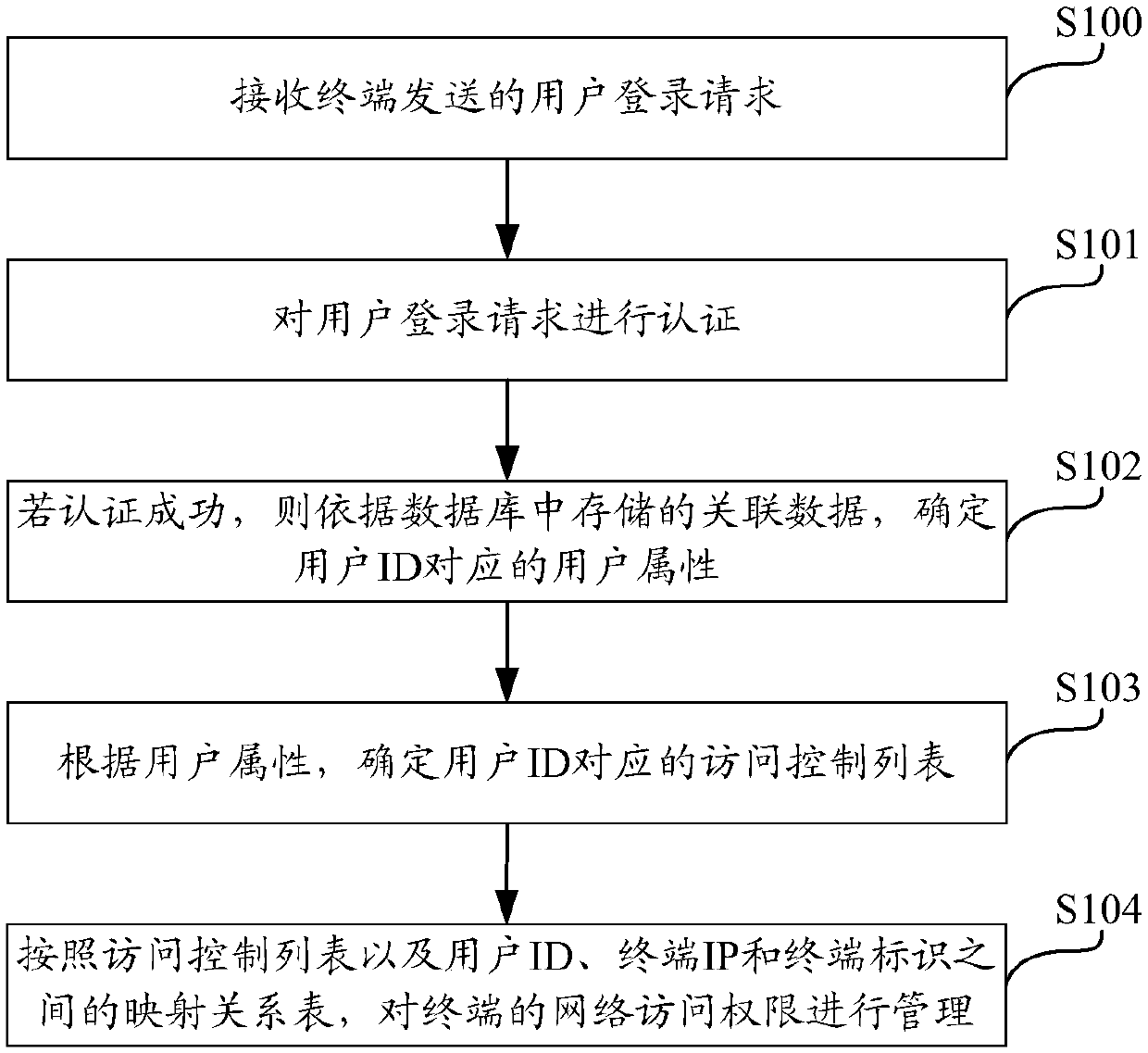
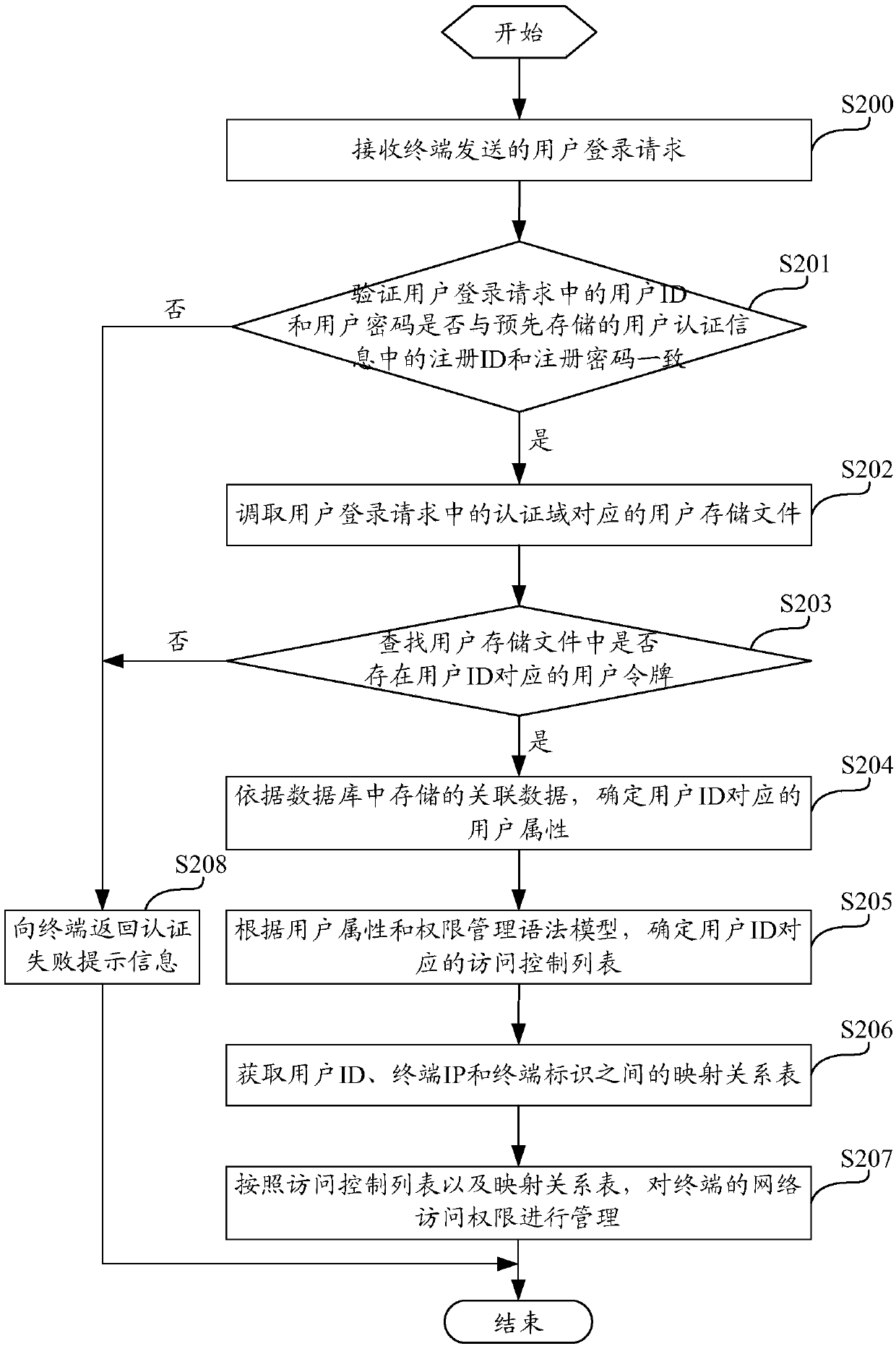
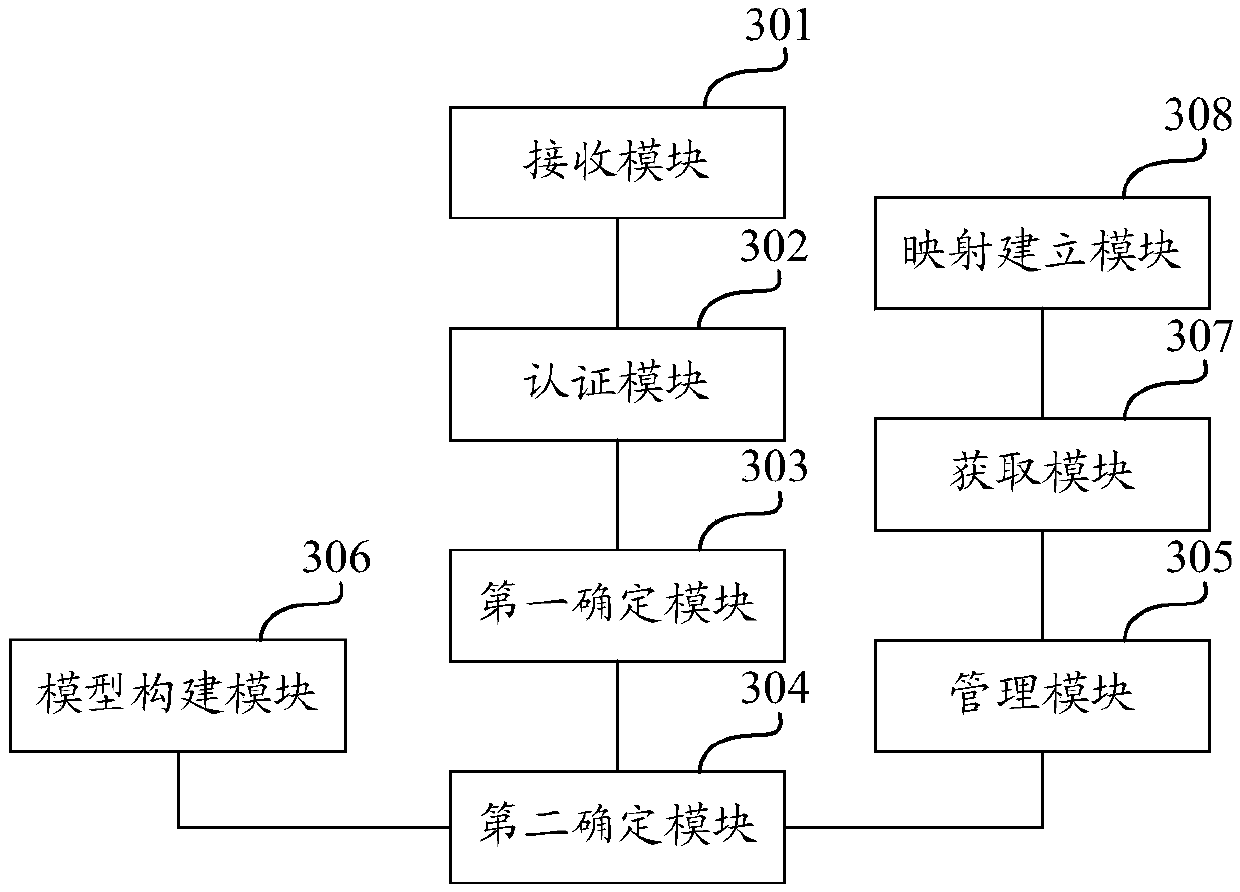
Network access authority management method and device and computing equipment
The invention discloses a network access authority management method and device, computing equipment and a computer storage medium, and the method comprises the steps: receiving a user login request transmitted by a terminal; authenticating the user login request, and if the authentication is successful, determining a user attribute corresponding to a user ID according to associated data stored ina database; determining an access control list corresponding to the user ID according to the user attribute; and managing the network access authority of the terminal according to the access controllist and a mapping relationship table among the user ID, a terminal IP and a terminal identifier. According to the technical scheme of the invention, fine-grained network access authority management is realized, the network access authority of the terminal can be conveniently managed according to the access control list and the mapping relation table, diversified authority management requirementsare well met, network attack resistance is facilitated, and the risk that a resource server is attacked is reduced.
Owner:BEIJING QIHOO TECH CO LTD
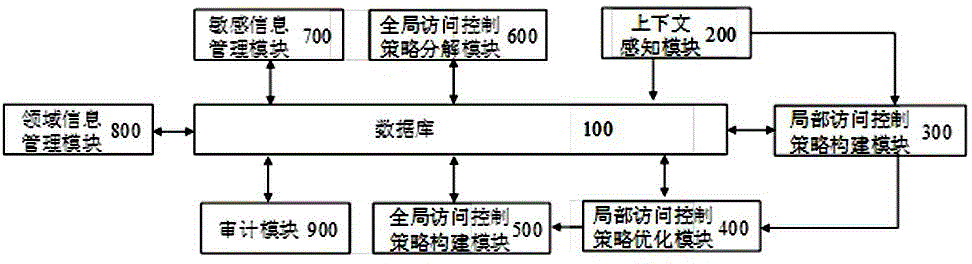
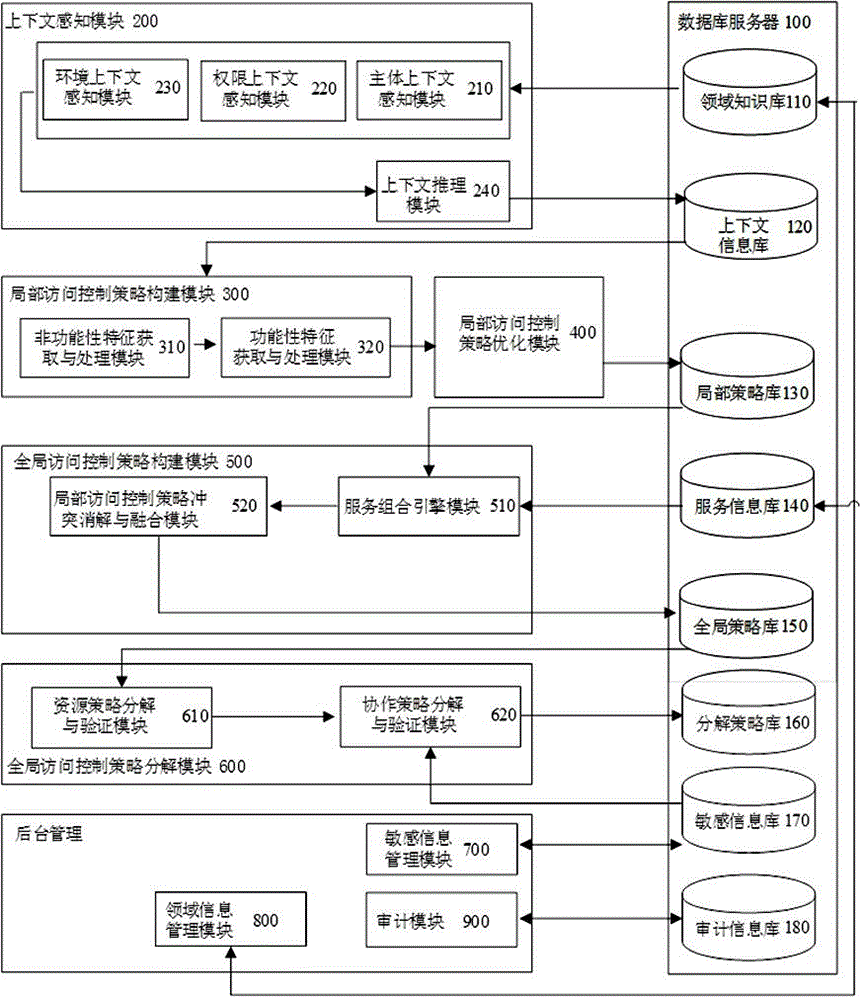
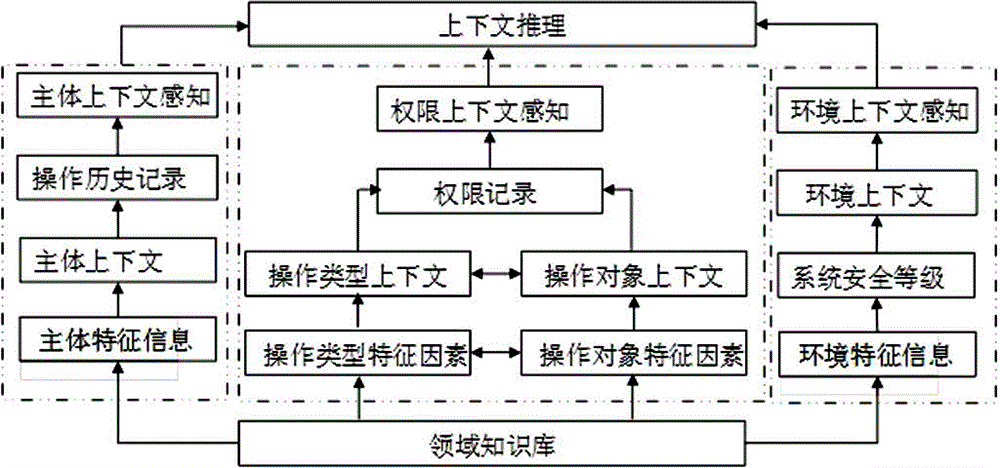
System for establishing access control policies in private cloud environment
InactiveCN104580163AGuaranteed autonomyGuaranteed compatibilityTransmissionExtensibilityComposite services
The invention provides a system for establishing access control policies in a private cloud environment. The system comprises a database (100), a context-sensing module (200), a local access control policy establishing module (300), a local access control policy optimizing module (400), a global access control policy establishing module (500), a global access control policy decomposing module (600), a sensitive information management module (700), a field information management module (800) and an auditing module (900). The system dynamically establishes the local access control policy in the private cloud environment, so that the established policy can meet requirements on dynamism and adaptivity of the private cloud environment; the system also realizes establishment and decomposition of a global access control policy which describes a composite service security requirement, so that the aim of avoiding leakage of sensitive information in the access control policy of a collaboration-participating service provider is achieved. The system has the characteristics of high security, high executing efficiency and high expandability.
Owner:NANYANG NORMAL UNIV
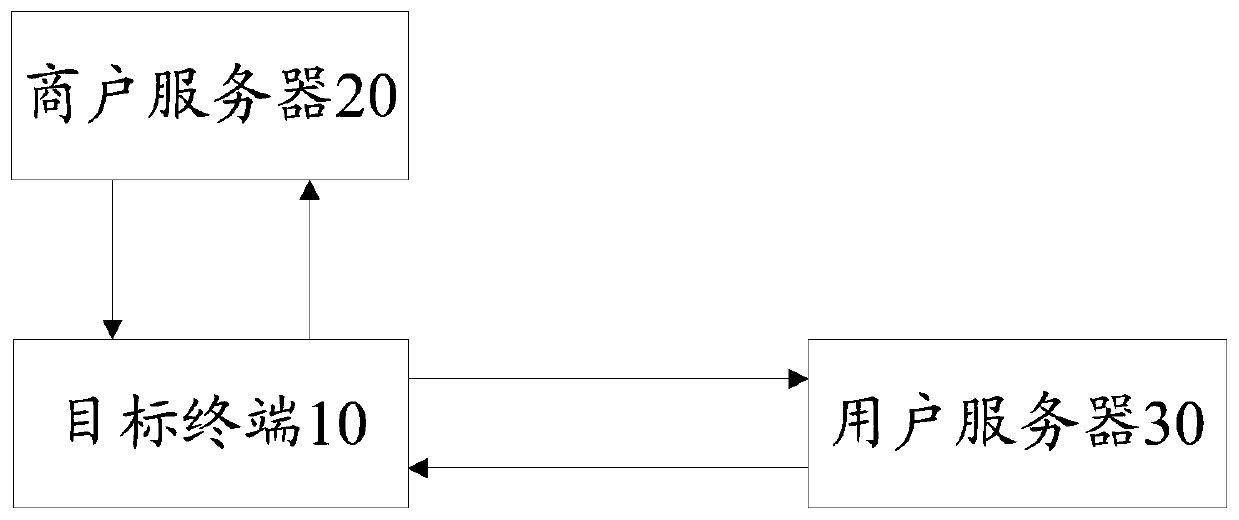
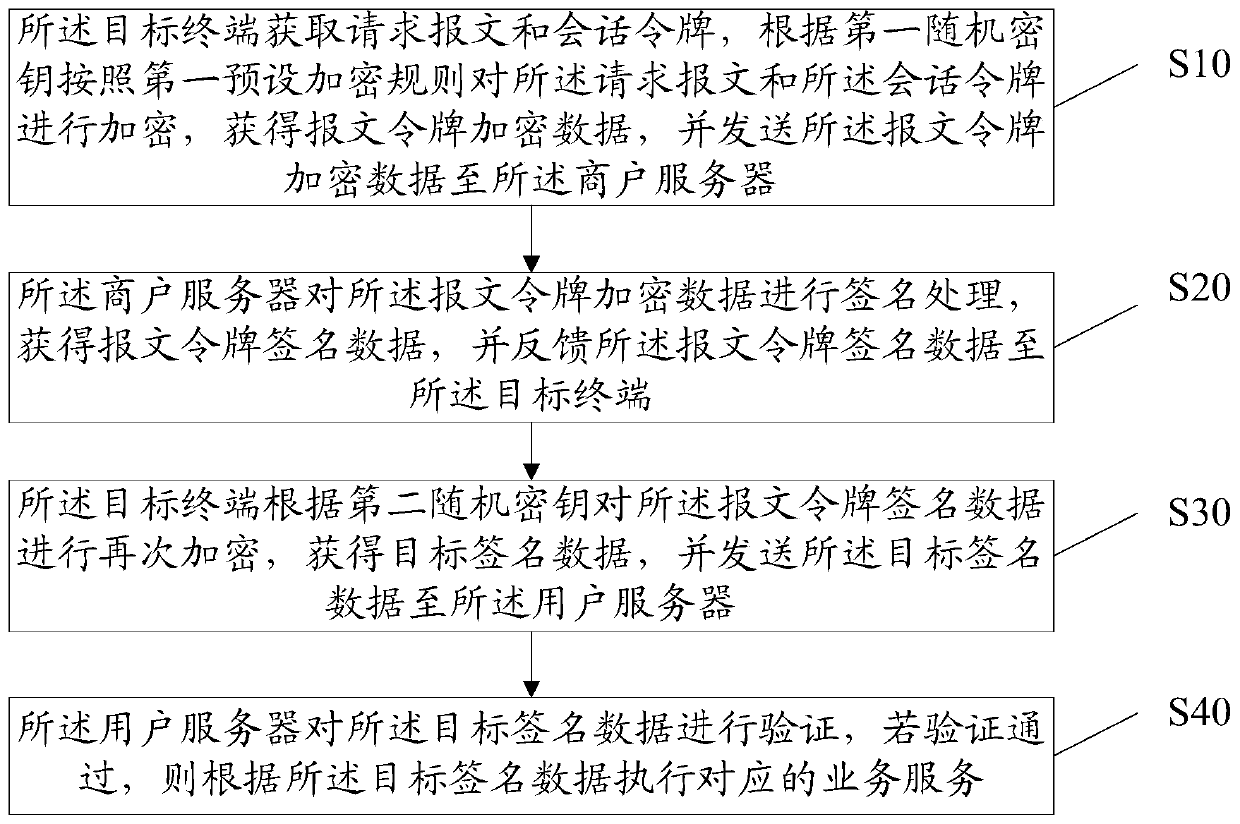
Application-based service security system and method
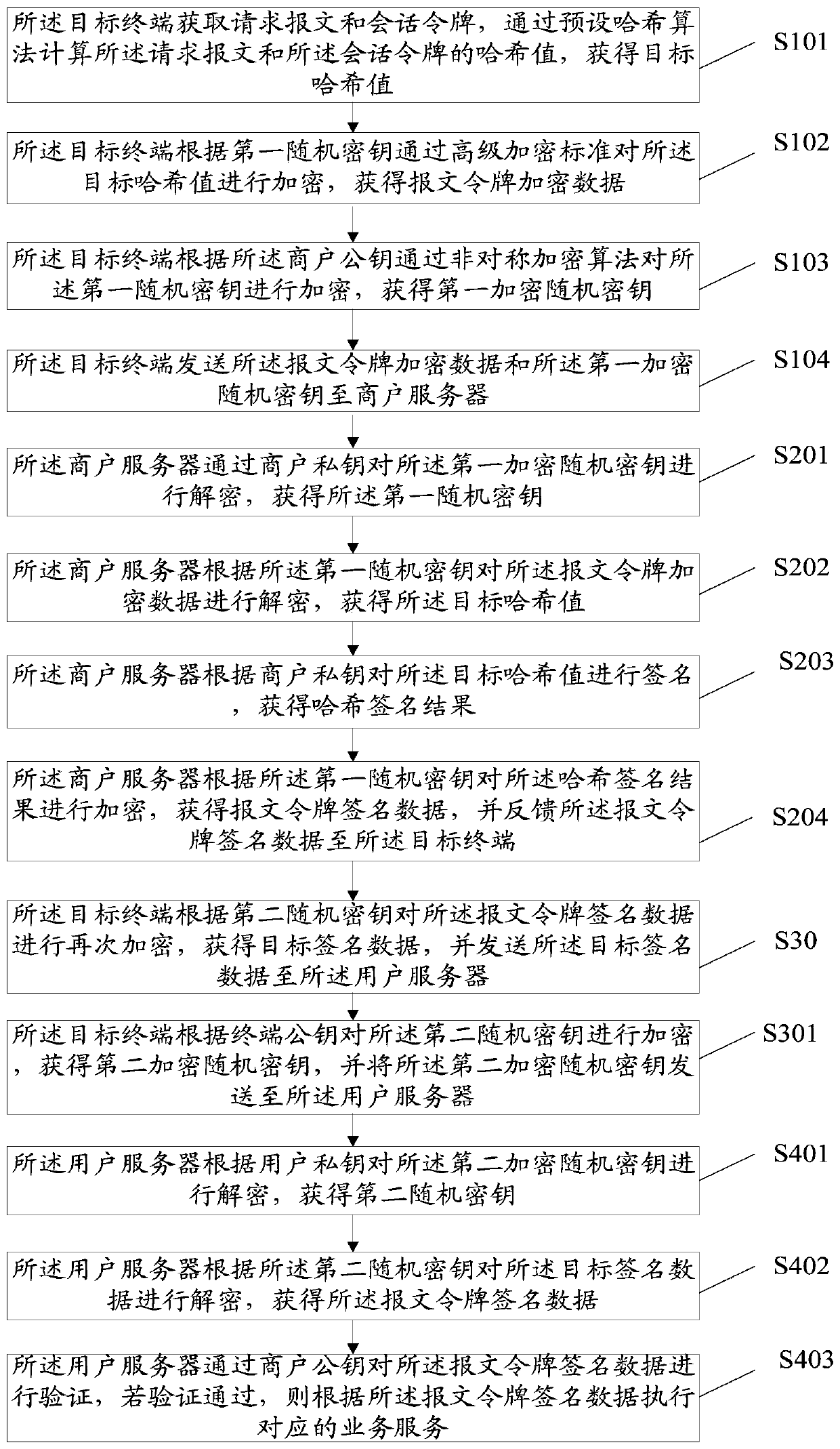
InactiveCN110290102AReduce risk of leakageReduce theftUser identity/authority verificationComputer terminalTarget signature
The invention discloses an application-based service security system and method. In the system, a target terminal is used for acquiring a request message and a session token, encrypting the request message and the session token according to a first random key and a first preset encryption rule to obtain message token encrypted data, and sending the message token encrypted data to a merchant server; a merchant server is used for carrying out signature processing on the message token encrypted data, obtaining message token signature data and feeding back the message token signature data to the target terminal; a target terminal is also used for encrypting the message token signature data again according to the second random key to obtain target signature data and sending the target signature data to the user server; and a user server is used for verifying the target signature data, and executing the corresponding business service according to the target signature data if the verification is passed. Based on the information security, the data interaction security is improved by encrypting the message, authenticating the identity and signing the data.
Owner:武汉众邦银行股份有限公司
Key negotiation method and electronic device
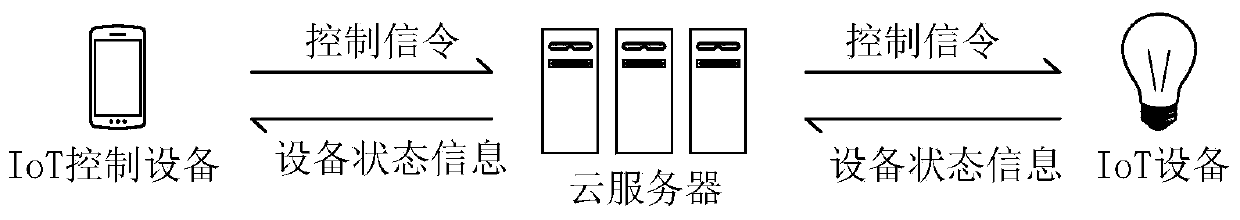
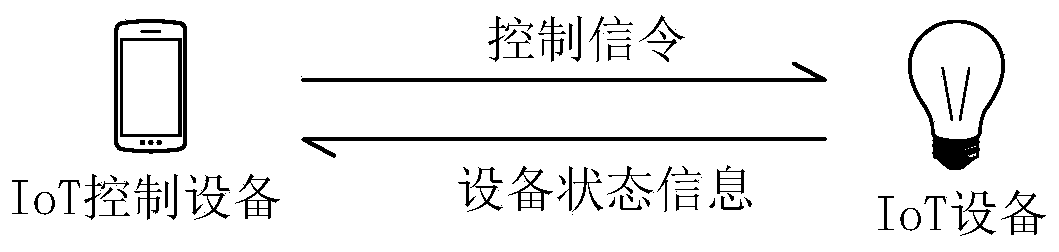
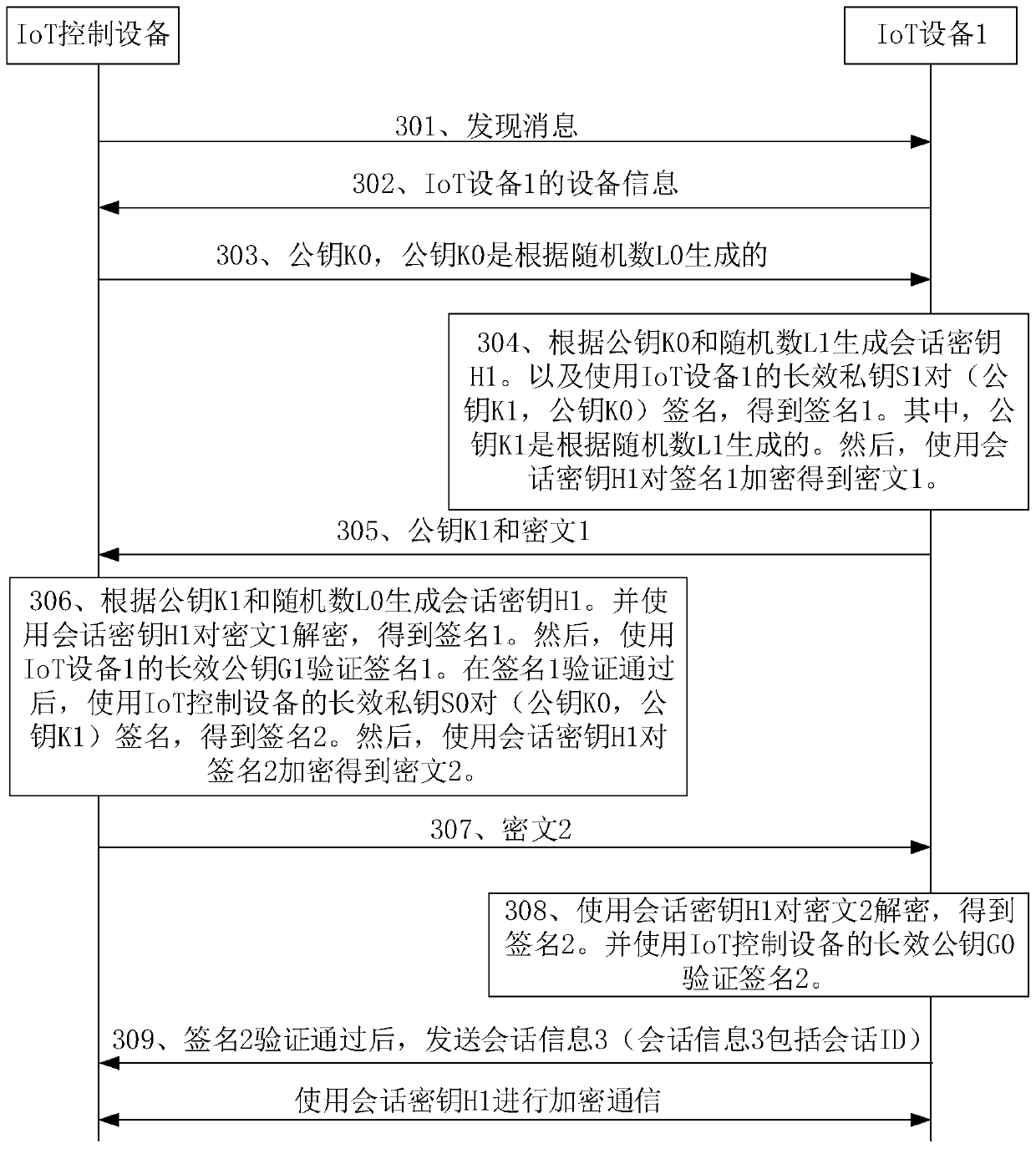
ActiveCN110933672AImprove efficiencyReduce the number of interactionsKey distribution for secure communicationSecurity arrangementCiphertextEngineering
The invention discloses a key negotiation method and an electronic device, and relates to the technical field of communication. Specifically, the method comprises the following steps: an IoT control device multicasting a discovery message carrying a first public key in a first local area network, and sending a second ciphertext to a first IoT device after receiving a first ciphertext and a secondpublic key; after receiving the third ciphertext from the first IoT device, the IoT control device decrypting the third ciphertext according to the first session key to obtain a second signature and second session information; verifying the second signature based on the long-acting public key of the first IoT device; and after the second signature is successfully verified, performing encrypted communication with the first IoT device based on the first session key. According to the technical scheme, the IoT control device carries the first public key in the discovery message, so that the STS negotiation process is fused into the discovery process, the number of times of message interaction between the IoT device and the IoT control device is reduced, and the efficiency of obtaining the session key is improved.
Owner:HUAWEI TECH CO LTD
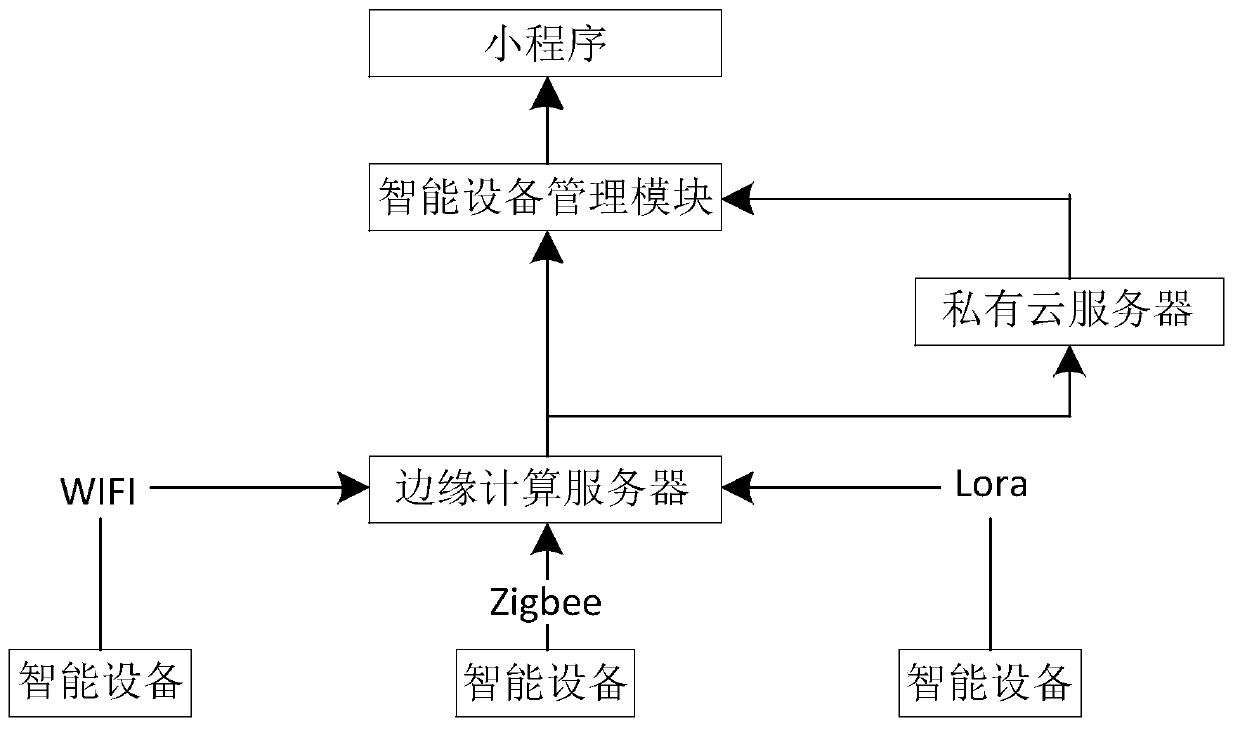
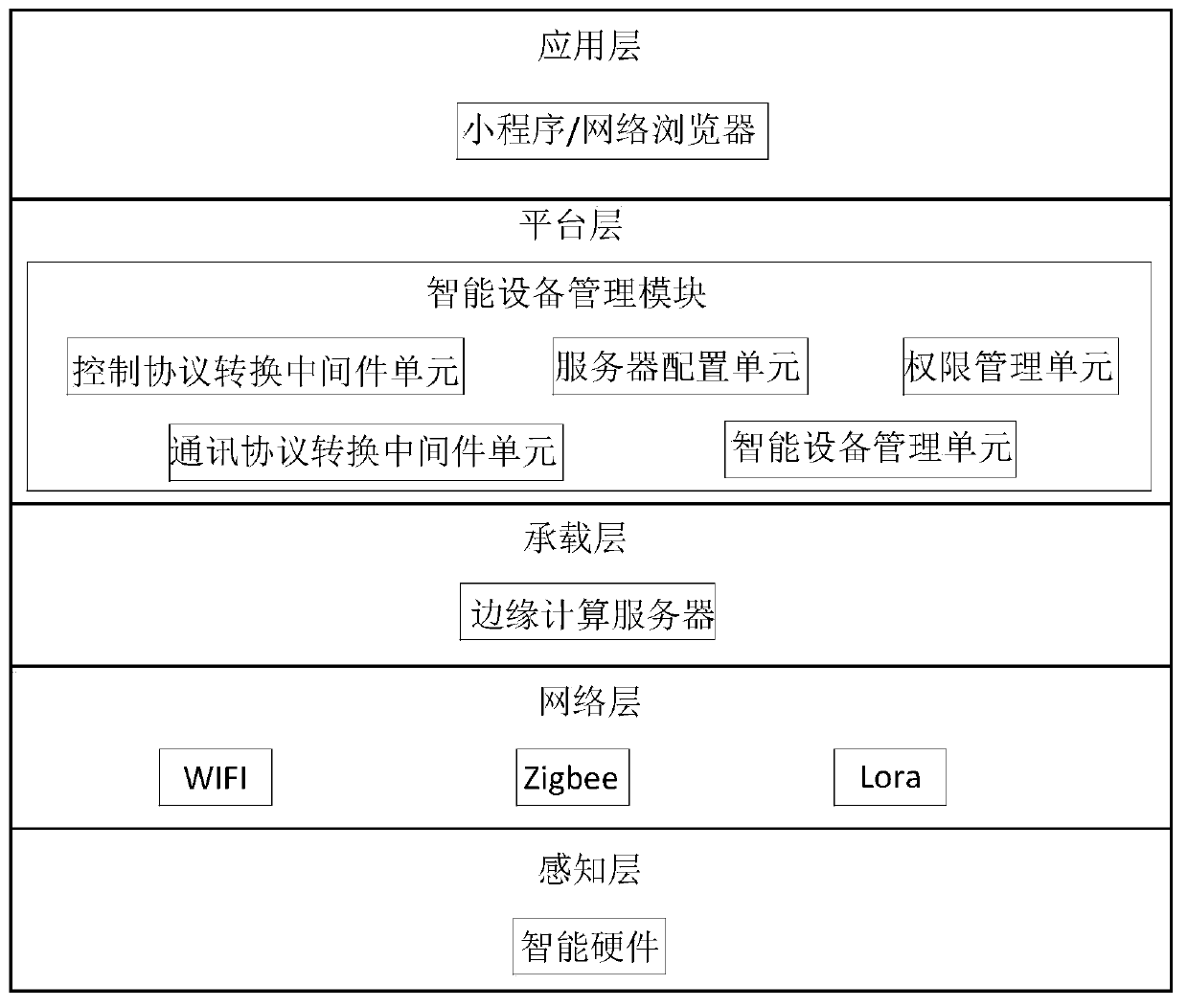
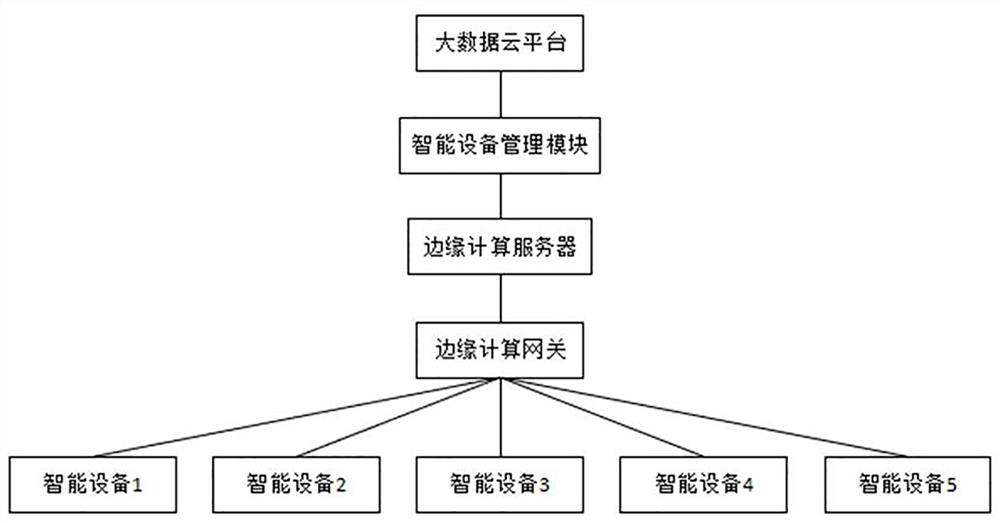
An intelligent equipment management system based on an Internet of Things edge computing server
InactiveCN109743401AReduce the risk of being attackedImprove management abilityData switching by path configurationWeb browserEdge computing
The embodiment of the invention discloses an intelligent equipment management system based on an Internet of Things edge computing server. The intelligent equipment management system comprises a sensing layer, a network layer, a bearing layer, a platform layer and an application layer; the sensing layer is in communication connection with the bearing layer through the network layer; the bearing layer comprises an edge computing server; the platform layer comprises an intelligent equipment management module; wherein the edge computing server is directly connected with the intelligent device management module through a multicast technology or through a private cloud, the application layer is a web browser or a mini program, the application layer is in network connection with the intelligentdevice management module, and a user performs interaction and management on an intelligent device through the application layer. The problem that existing enterprise operation data cannot be privatized and locally deployed is solved.
Owner:南京我在智能科技有限公司
Identity verification method and device, computer equipment and storage medium
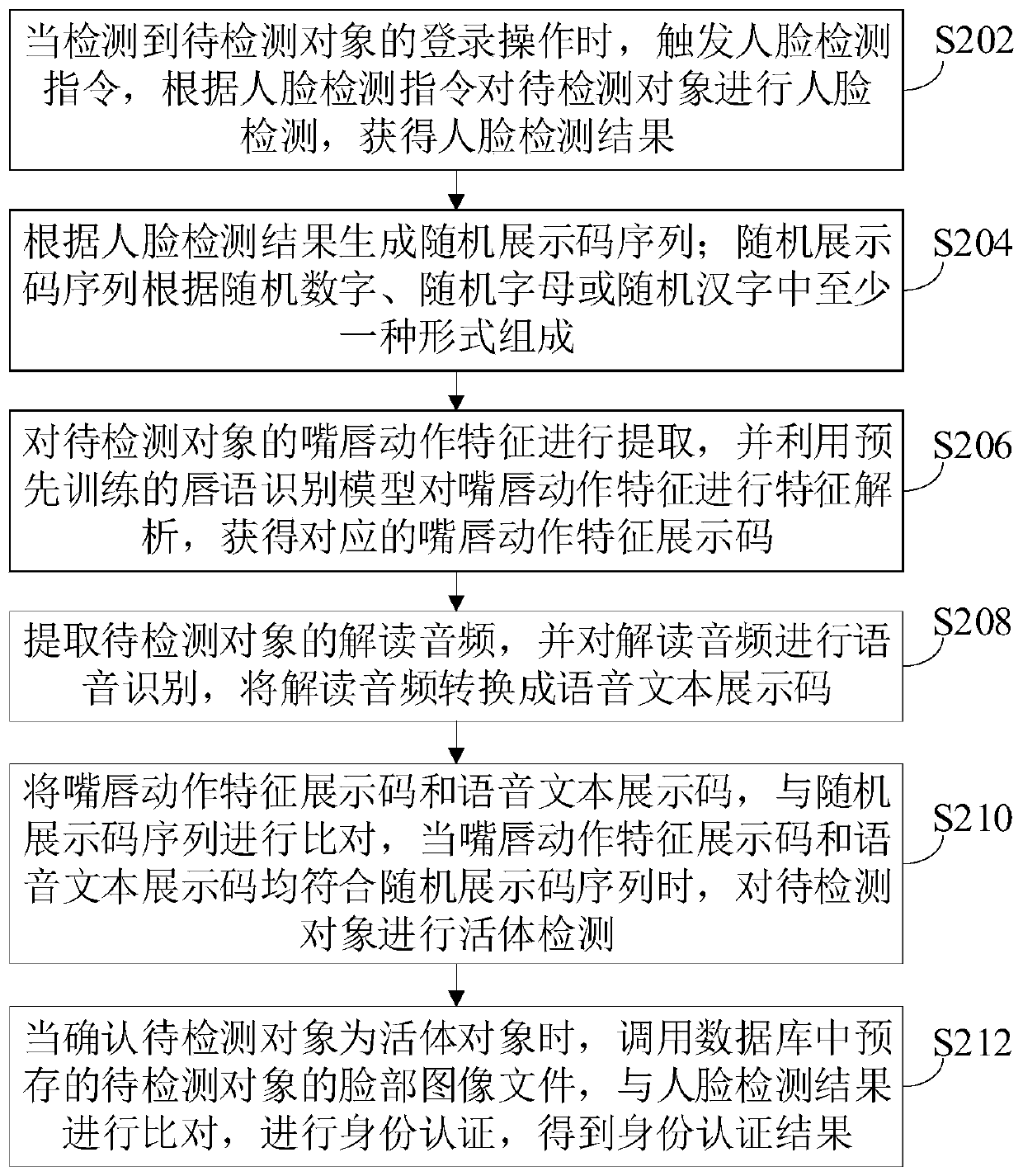
PendingCN110955874AReduce the risk of being attackedImprove reliabilityDigital data authenticationFace detectionText display
The invention relates to an identity authentication method and device based on a password technology, computer equipment and a storage medium. The method comprises the following steps: performing facedetection on a to-be-detected object to obtain a face detection result, and generating a random display code sequence according to the face detection result; extracting lip action features of the to-be-detected object, and performing feature analysis on the lip action features by utilizing the lip language recognition model to obtain a lip action feature display code; extracting interpretation audios of the to-be-detected object, converting the interpretation audios into voice text display codes, comparing the lip action feature display codes and the voice text display codes with the random display code sequence, and performing living body detection on the to-be-detected object when the lip action feature display codes and the voice text display codes conform to the random display code sequence; when living body detection is passed, comparing the face image file of the to-be-detected object with the face detection result to obtain an identity authentication result. According to the method, face, lip language and voice recognition is combined, and the reliability and safety of identity authentication are enhanced.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Internet asset exposure information checking method
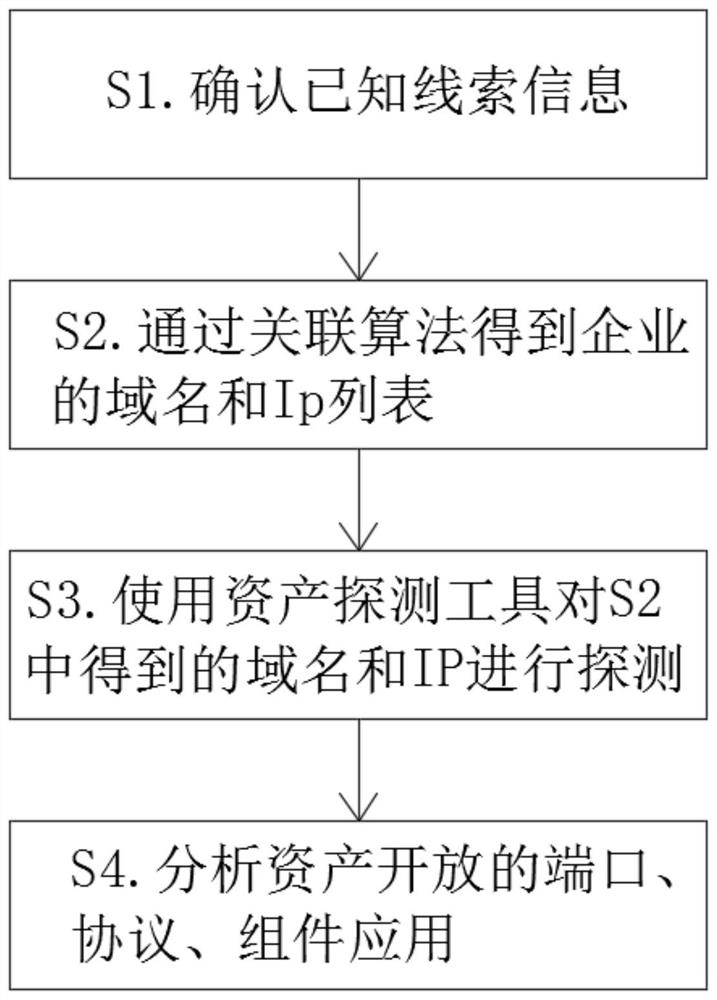
PendingCN112926942AComprehensive exposure screeningReduce notificationFinanceOffice automationDomain nameInternal management
The invention discloses an internet asset exposure information checking method. The method comprises the following steps: S1, confirming known clue information; s2, obtaining a domain name and an Ip list of an enterprise through an association algorithm; s3, detecting the domain name and the IP obtained in the S2 by using an asset detection tool; and S4, analyzing ports, protocols and component applications of asset opening. The enterprise domain name and Ip list are obtained through association algorithms such as certificates, sub-domain name blasting, flow analysis, ICP information, domain name registration information, enterprise names, app, WeChat applets and the like, then the domain names and the IPs are detected by using an asset detection tool, open ports, protocols and component applications of assets are analyzed, comprehensive exposure surface investigation is carried out on enterprise internet assets. The method can converge the attack surface, reduce the attacked risk, improve the internal management of an enterprise, reduce the notification of a supervised unit, and lay a foundation for the subsequent safety risk assessment and monitoring.
Owner:北京华顺信安信息技术有限公司
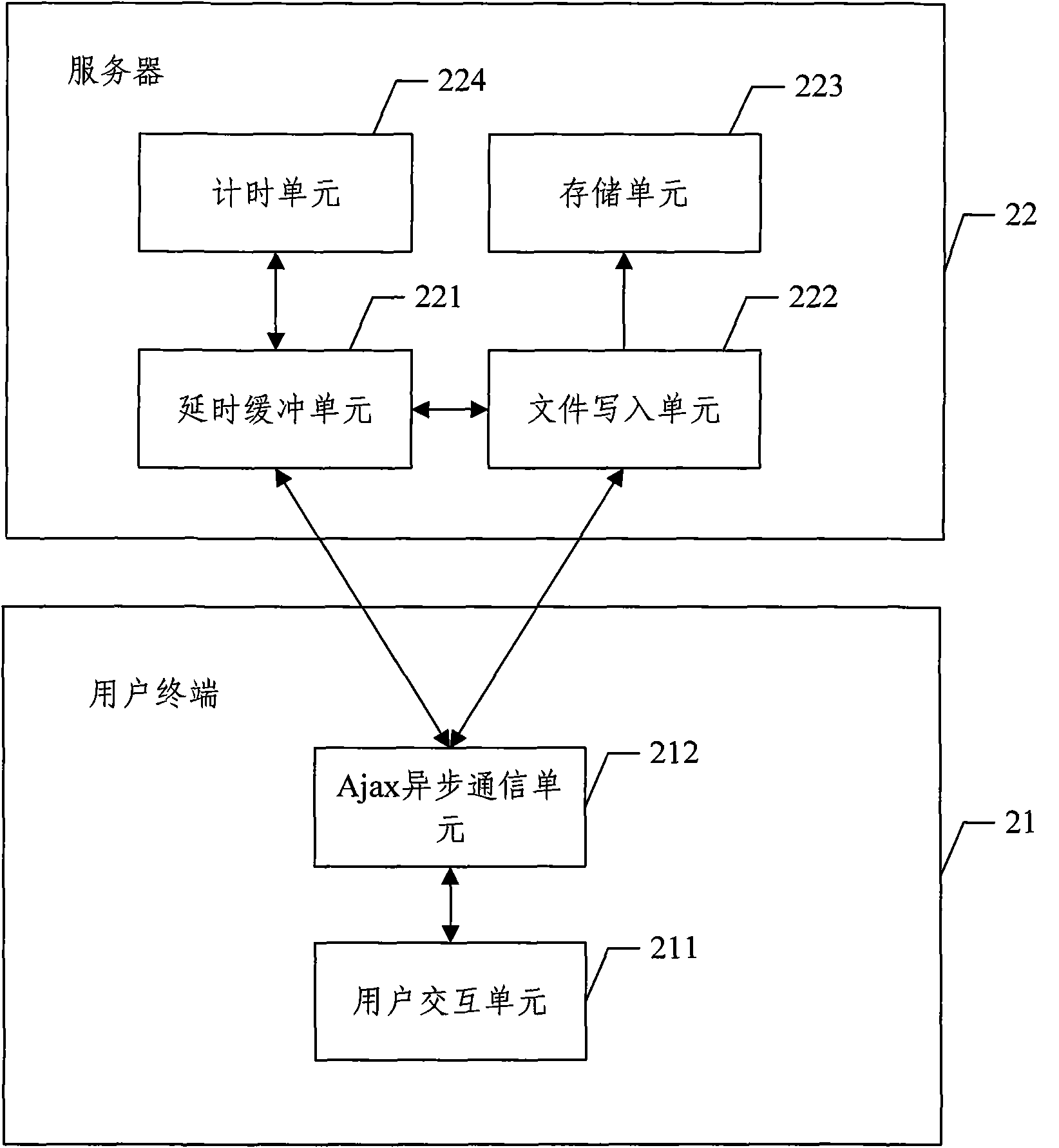
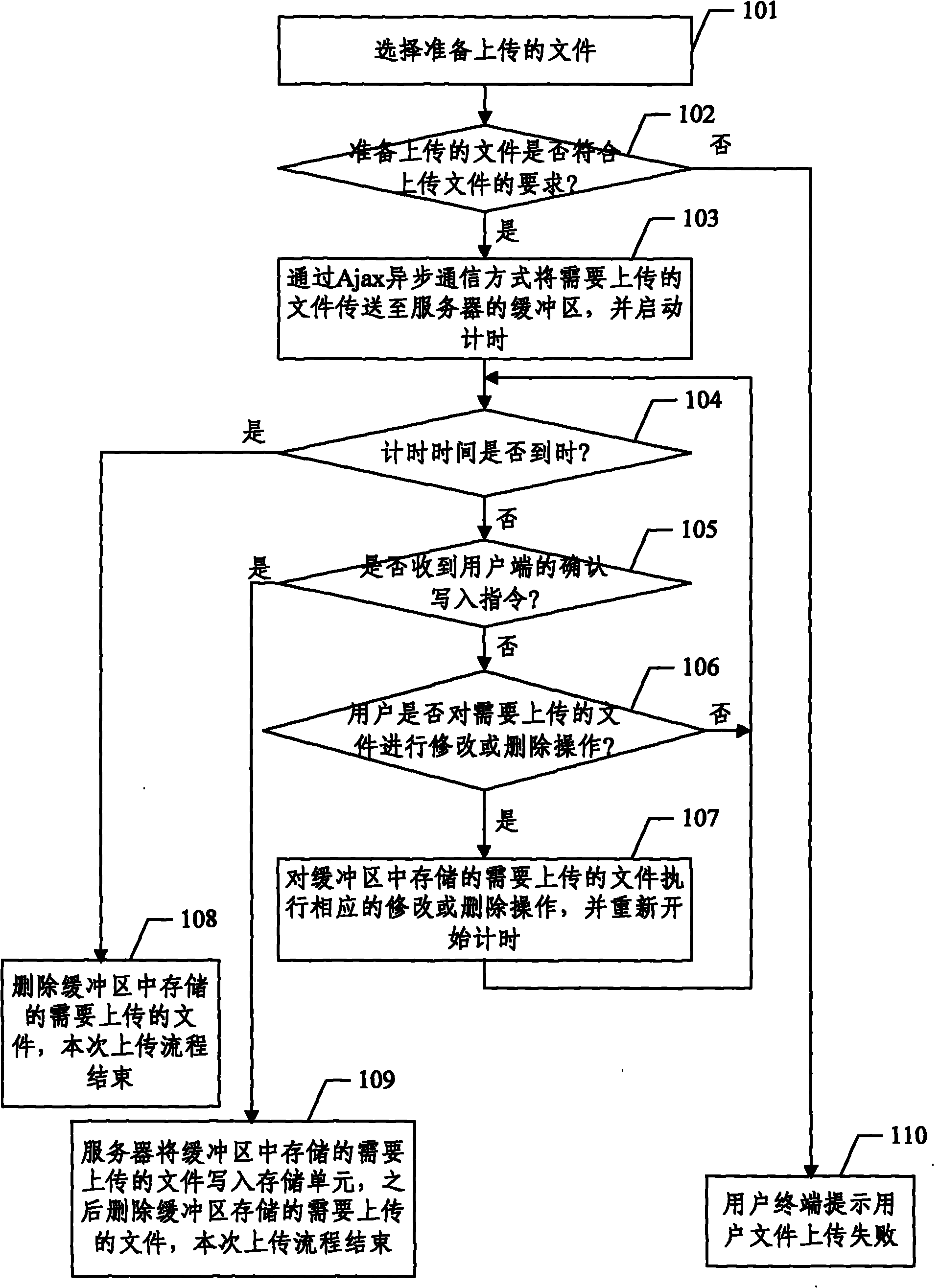
File uploading device based on asynchronous javascript and xml (Ajax) technology
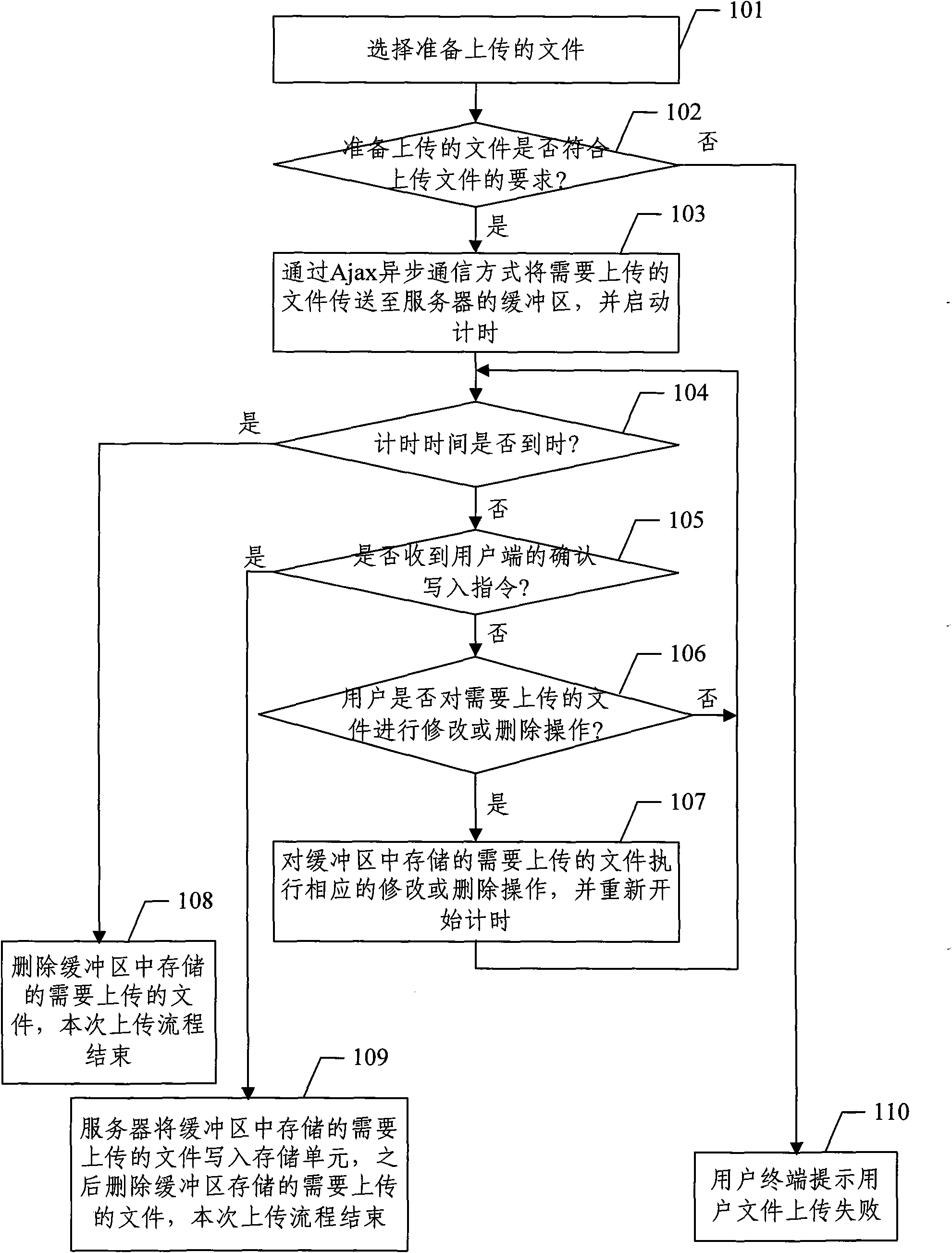
The invention discloses a file uploading device based on asynchronous javascript and xml (Ajax) technology, which comprises the processes that a user terminal is used for confirming a file needing unloading which is transmitted to a server through the user terminal in Ajax asynchronous communication mode, the server receives confirmed writing-in instruction transmitted by the user terminal and writes the file needing unloading stored in a buffer zone into a storage unit, and then the file needing unloading stored in the server is deleted.
Owner:北京市崇文区信息化工作办公室 +1
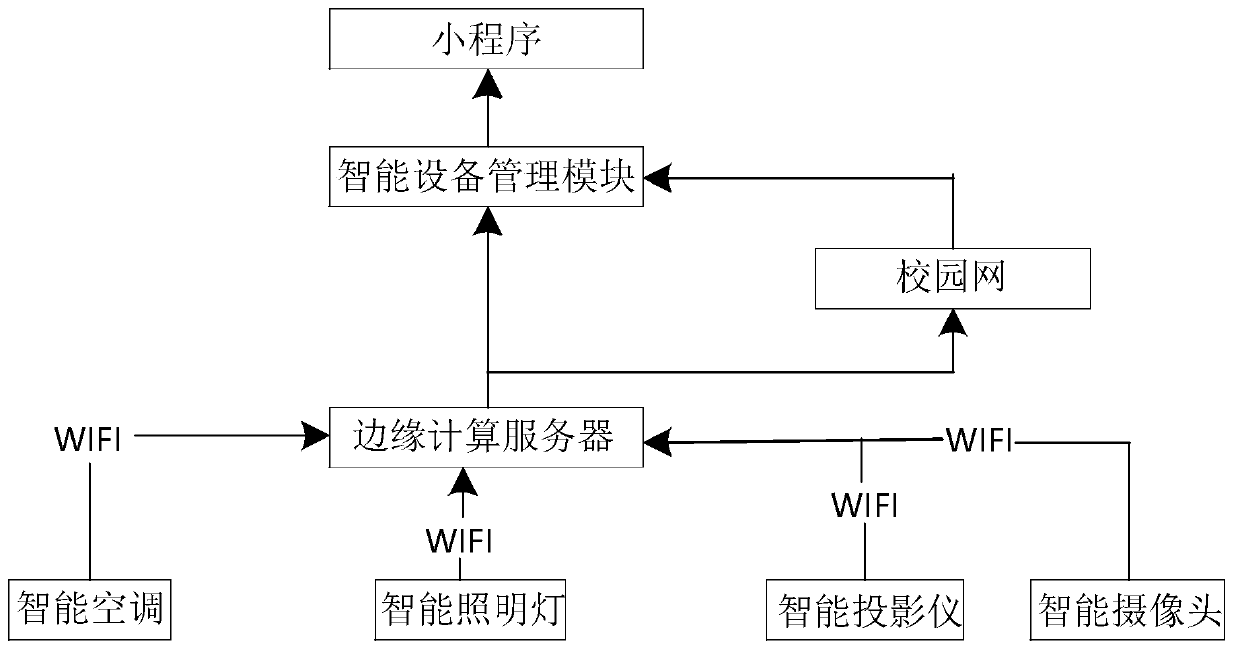
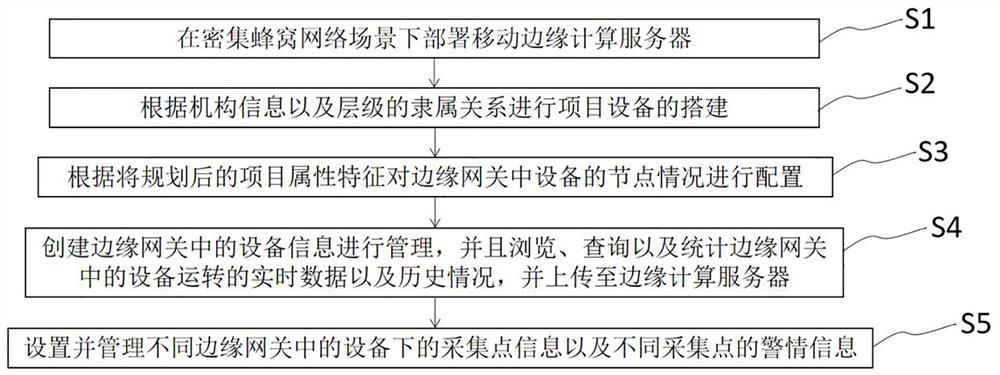
Intelligent equipment management system and method based on edge computing
PendingCN113741282AReduce the risk of being attackedRealize centralized controlProgramme controlComputer controlEdge serverEdge computing
The invention discloses an intelligent equipment management system and method based on edge computing, and relates to the technical field of intelligent equipment management. The system comprises intelligent equipment, an edge computing gateway, an edge computing server, an intelligent equipment management module and a big data cloud platform; the edge server is used for collecting data and state information sent by the intelligent equipment and processing and operating the data; and the intelligent equipment management module is used for managing the edge computing server, monitoring terminal intelligent equipment in batches, issuing an instruction, receiving an alarm in real time and querying historical data. According to the invention, the edge computing server analyzes and processes the data of the intelligent equipment, the edge computing server establishes connection with the intelligent equipment management module through the private cloud, centralized control of the intelligent equipment is realized, data localization is realized, and the risk that the server is attacked is reduced in the environment of the private cloud server.
Owner:山东恒远智能科技有限公司
Method and device for realizing network security communication, and equipment
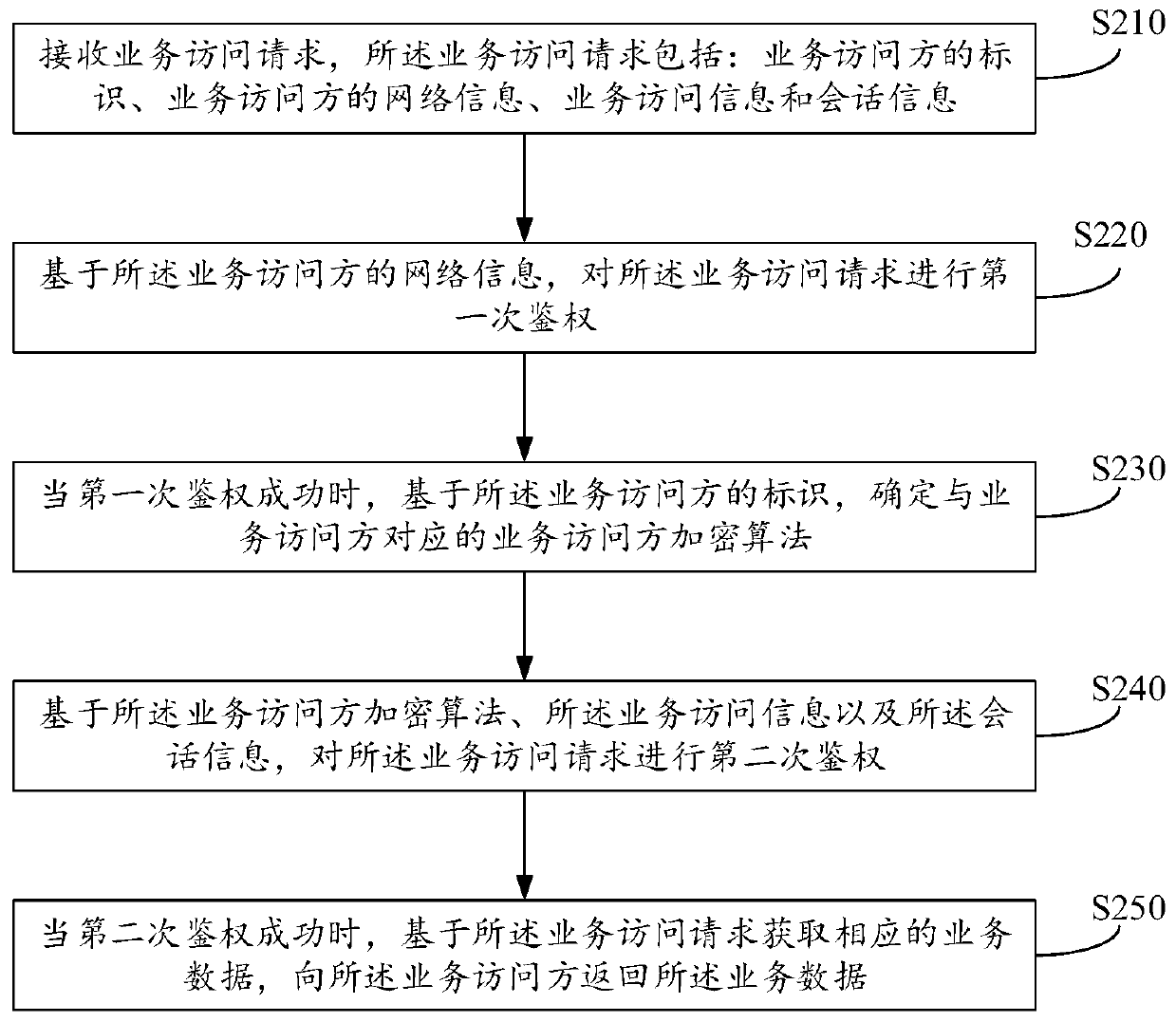
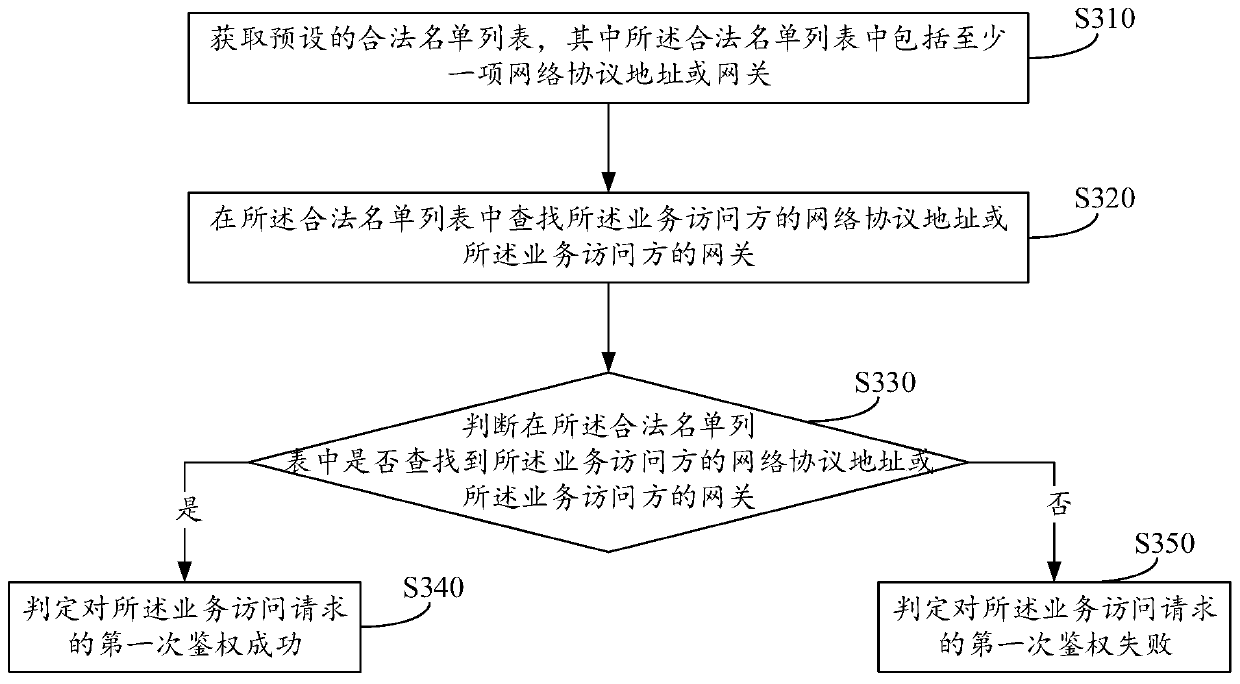
ActiveCN110719265AImprove safety and efficiencyReduce the risk of being attackedTransmissionSecure communicationService system
The invention relates to a method and device for realizing network security communication, and equipment. The method comprises the steps: receiving a service access request which comprises the identification of a service access side, the network information of the service access side, the service access information and the session information; performing first authentication on the service accessrequest based on the network information of the service access party; when the first authentication succeeds, determining a service access party encryption algorithm corresponding to the service access party based on the identifier of the service access party; performing second authentication on the service access request based on the service access party encryption algorithm, the service access information and the session information; and when the second authentication succeeds, obtaining corresponding service data based on the service access request, and returning the service data to the service access party. According to the invention, the security of the system and background data can be improved, and the risk that the service system is attacked is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Distributed software distribution method
ActiveCN106713483AReduce backbone network load and master server loadImprove distribution speed and efficiencyTransmissionClient-sideDistribution method
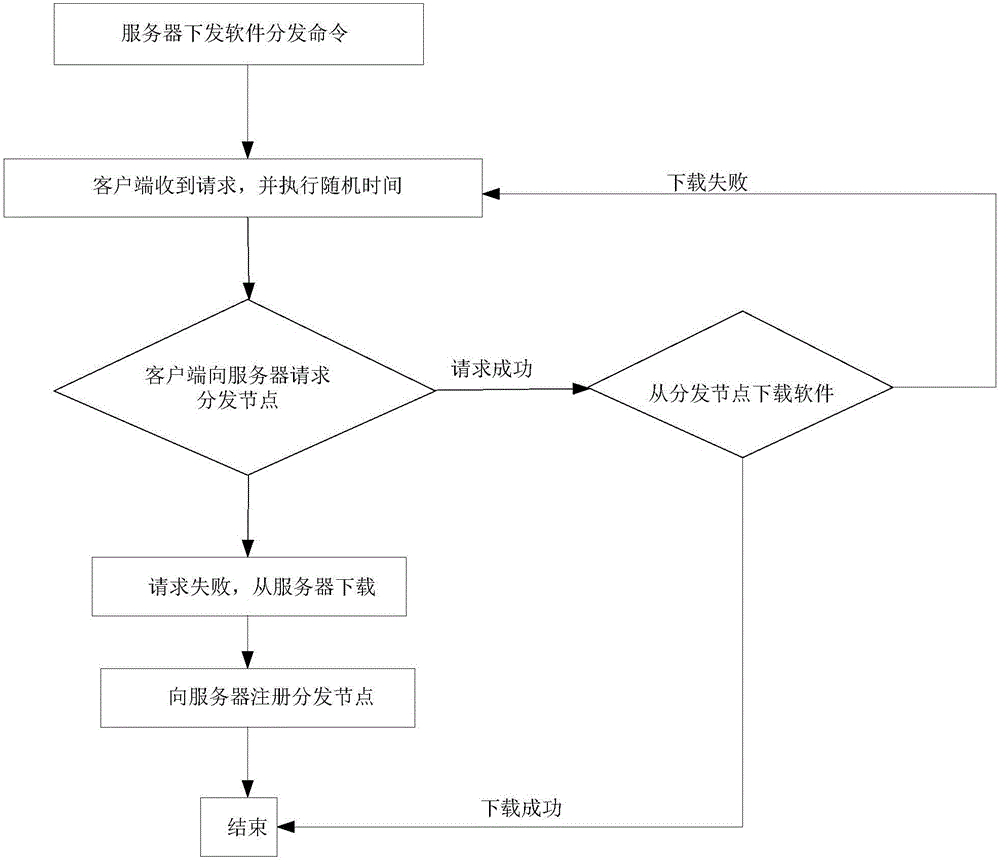
The invention provides a distributed software distribution method, comprising the following steps: a server issues software distribution commands to all clients, wherein the software distribution commands contain random time; after reaching the random time, the client requests a distribution node from the server; the client of which the random time is 0 directly downloads the software from the server, opens a download port after completing the download, and registers as the distribution node to the server; if the request for the distribution node succeeds, the client can download the required software from the distribution node; if the request for the distribution node fails or times out, the client will download the software from the server; and the server sends the distribution node to the client after receiving the register of the distribution node. According to the distributed software distribution method provided by the invention, the client in the network is fully used to ensure that the load of the backbone network and the primary server can be reduced, and the distribution speed and efficiency can be increased; and meanwhile, as the opening time of the distribution node is limited, the attack risk of terminals can be reduced.
Owner:BEIJING KINGSOFT SECURITY MANAGEMENT SYST TECH CO LTD
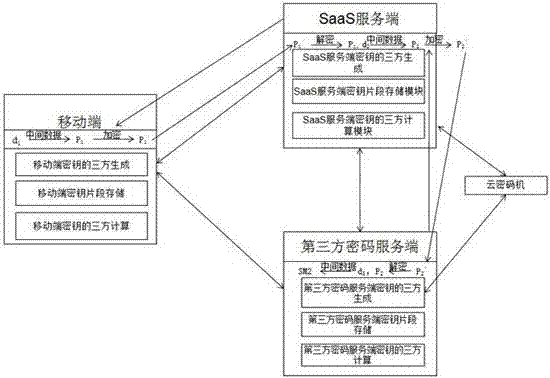
Method and system for achieving secret key generation and protection through cloud and terminal three-power separation
ActiveCN107342862AImprove securityReduce the risk of being attackedKey distribution for secure communicationThird partyPassword
The invention discloses a method and system for achieving the secret key generation and protection through cloud and terminal three-power separation, and belongs to the technical field of information safety. The invention aims at solving a technical problem that how to improve the safety of a secret key of a user. The employed technical scheme is that the method comprises the steps: enabling a mobile terminal, an SaaS service side and a third password service side to jointly form a secret key SM2; enabling the mobile terminal, the SaaS service side and the third password service side to respectively store the respective secret key segments; enabling the mobile terminal, the SaaS service side and the third password service side to respectively calculate the data according to the secret key segments after a user completes the certification at the mobile terminal, carrying out the secondary calculation of a calculation result, and forming a final result. The system comprises the mobile terminal, the SaaS service side, the third password service side and a cloud password machine.
Owner:北京信任度科技有限公司
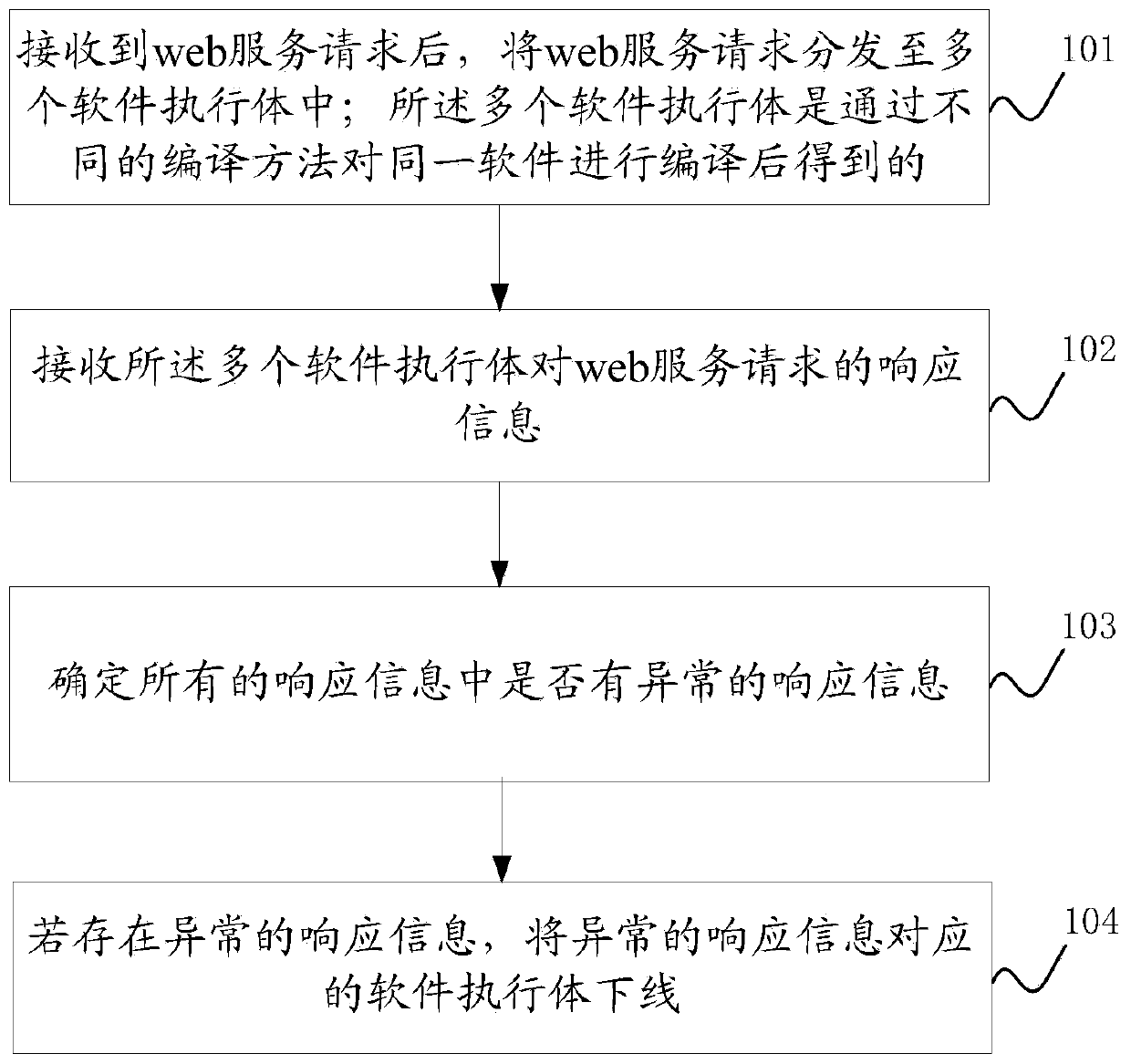
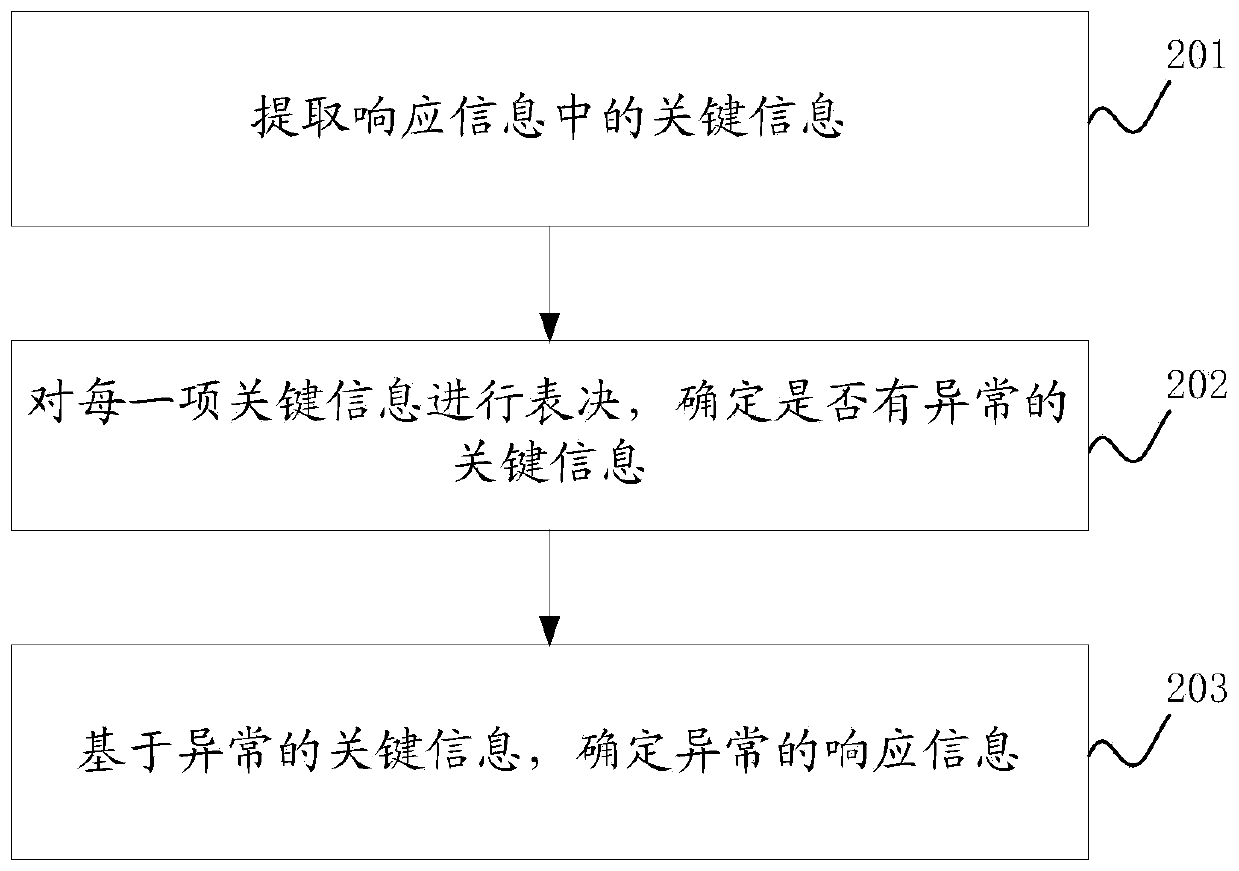
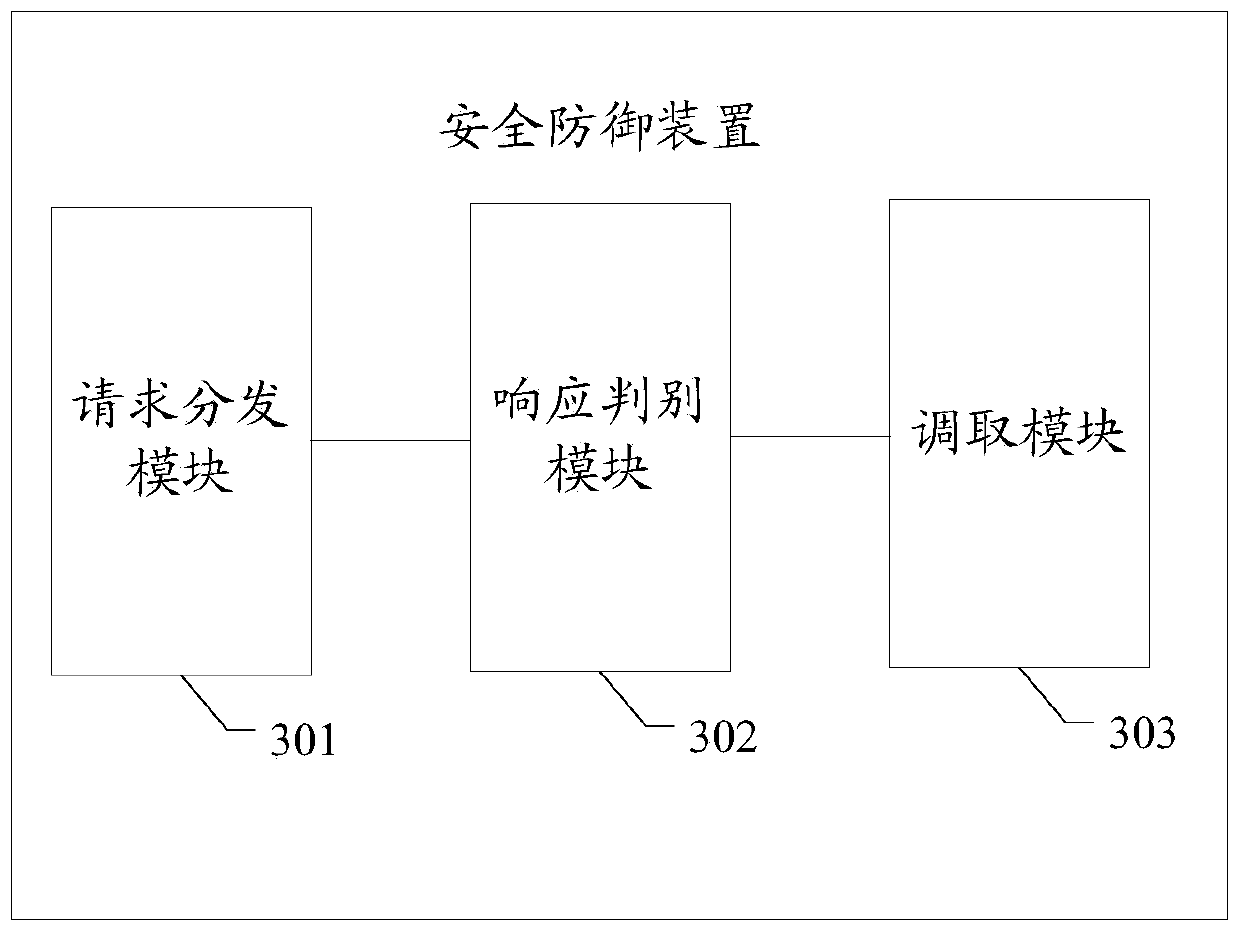
Security defense method and device
InactiveCN110784475AReduce the risk of being attackedReduce the risk of attackTransmissionWeb serviceAttack
The embodiment of the invention discloses a security defense method and device. The method comprises the following steps: distributing a web service request to a plurality of software executors, wherein the plurality of software executors are obtained by compiling the same software in different compiling modes, analyzing the response information to determine whether abnormal response information is contained or not, and offline the software executor corresponding to the abnormal response information under the condition that the abnormal response information is contained. Therefore, the functions of the software executors obtained through different compiling modes are the same, but structures are different, in this way, attacks on a certain software execution body are greatly reduced; the risk that other execution bodies of the software or execution bodies of other versions of the software are attacked is avoided, and the risk that the software is attacked is greatly reduced by selecting the abnormal response information even if the software execution body which is possibly attacked is discovered and the software execution body is offline in time.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
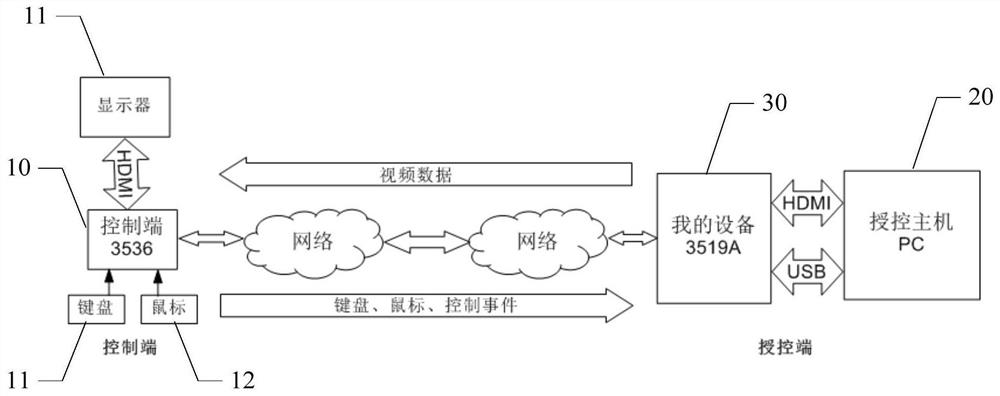
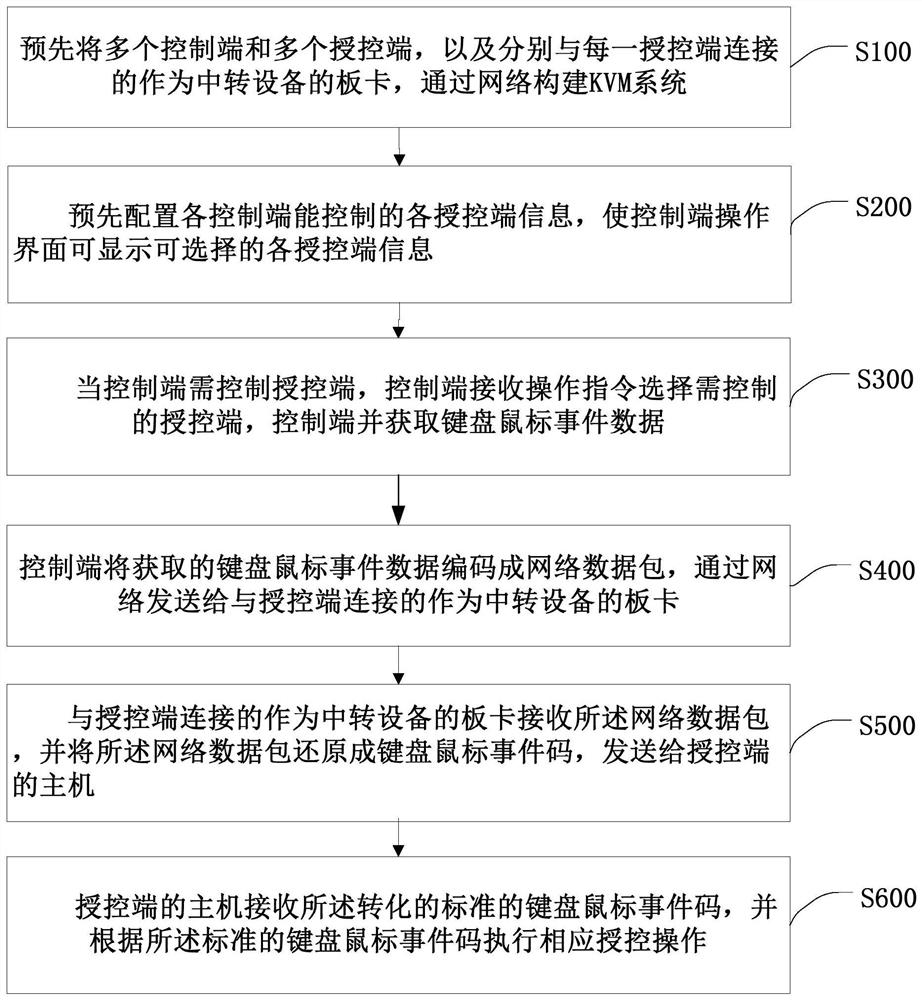
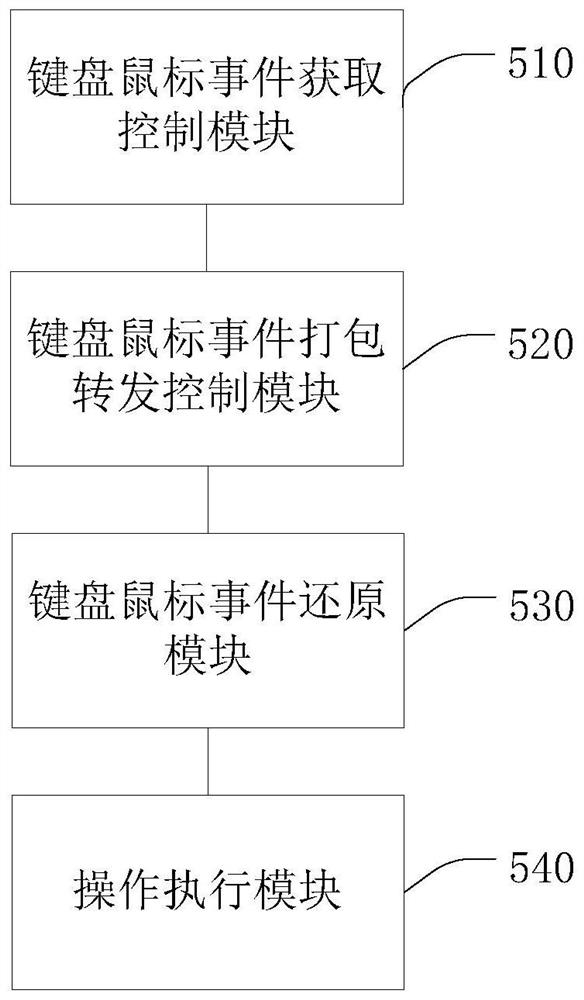
Network forwarding keyboard mouse code processing method, device and system
InactiveCN112462961ASolve the problem of needing to install specific driversReduce the risk of being attackedTransmissionDigital output to display deviceData packNetwork packet
The invention discloses a network forwarding keyboard and mouse code processing method, device and system, and the method comprises the steps: enabling a control end to receive an operation instruction when the control end needs to control a controlled end, selecting the control end and the controlled end which need to be controlled, and obtaining keyboard and mouse event data; enabling the control end to encode the acquired keyboard and mouse event data into a network data packet, and sending the network data packet to a board card connected with the controlled end and used as transfer equipment through a network; receiving the network data packet by a board card which is connected with the controlled end and serves as transfer equipment, decoding and restoring the network data packet into a keyboard and mouse event code, and sending the keyboard and mouse event code to a host of the controlled end; and enabling the host of the controlled end to receive the converted standard keyboardand mouse event code, and executing corresponding control operation according to the standard keyboard and mouse event code. The USB keyboard and the mouse are forwarded through the network, the standard keyboard and the standard mouse can operate different computers and be controlled by the different computers through the network, safety is improved, and convenience is brought to use of a user.
Owner:SHENZHEN SKYWORTH QUNXIN SECURITY TECH
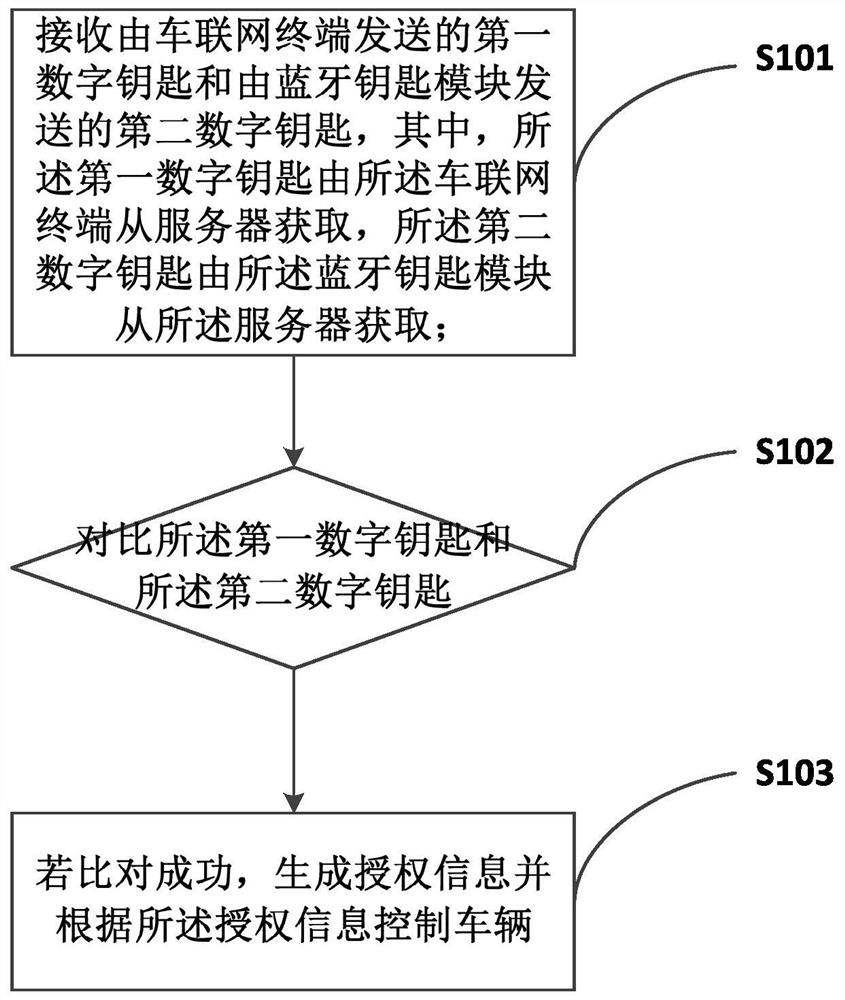
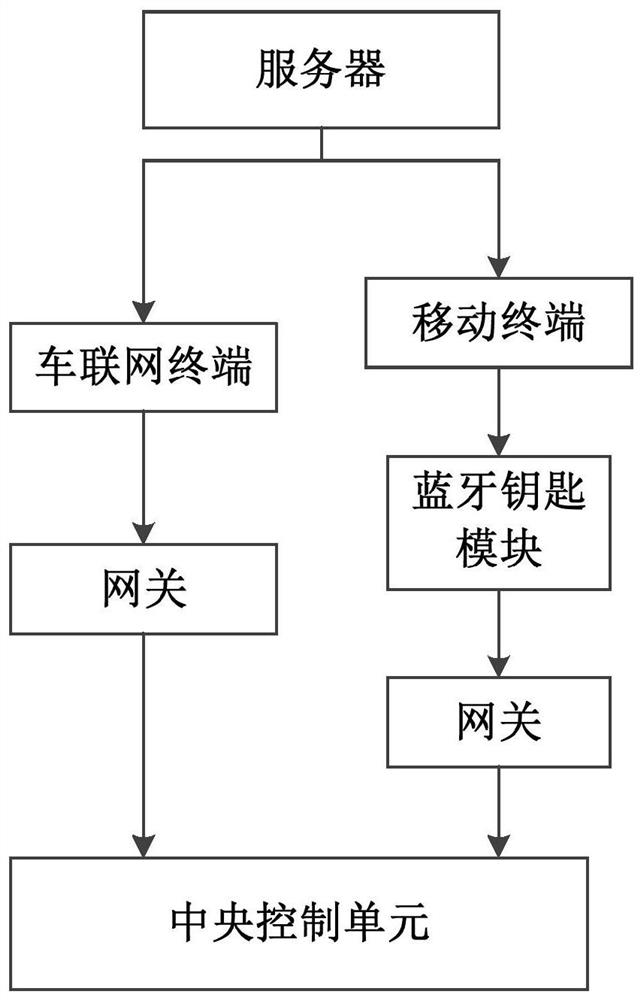
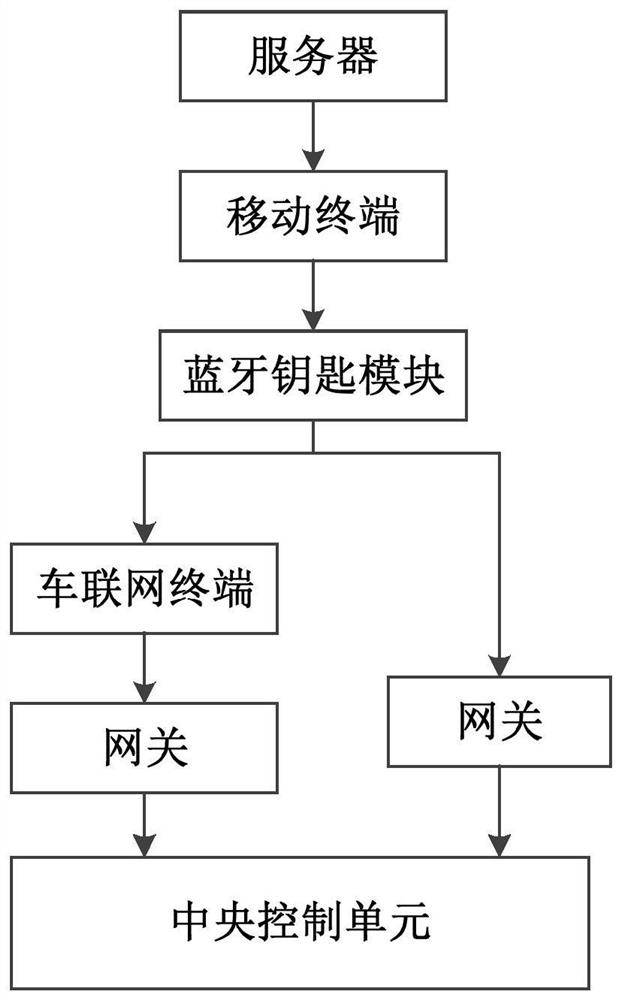
Authorization method, device and system of vehicle Bluetooth key and storage medium
InactiveCN112440935AImprove security levelReduce the risk of being attackedAnti-theft devicesInformation controlThe Internet
The invention provides an authorization method, device and system of a vehicle Bluetooth key and a storage medium, and relates to the technical field of vehicles. The authorization method of the vehicle Bluetooth key comprises the steps that a first digital key sent by an Internet of Vehicles terminal and a second digital key sent by a Bluetooth key module are received, wherein the first digital key is obtained from a server by the Internet of Vehicles terminal, and the second digital key is obtained from the server by the Bluetooth key module; the first digital key is compared with the seconddigital key; and if comparison succeeds, authorization information is generated, and the vehicle is controlled according to the authorization information. By the adoption of the method, different digital key information is transmitted through the two independent channels, finally, the two pieces of digital key information are compared, the whole process is conducted through the Internet of Vehicles terminal, the Bluetooth key module and a central control unit, and the safety level is higher.
Owner:NINGBO GEELY AUTOMOBILE RES & DEV CO LTD +1
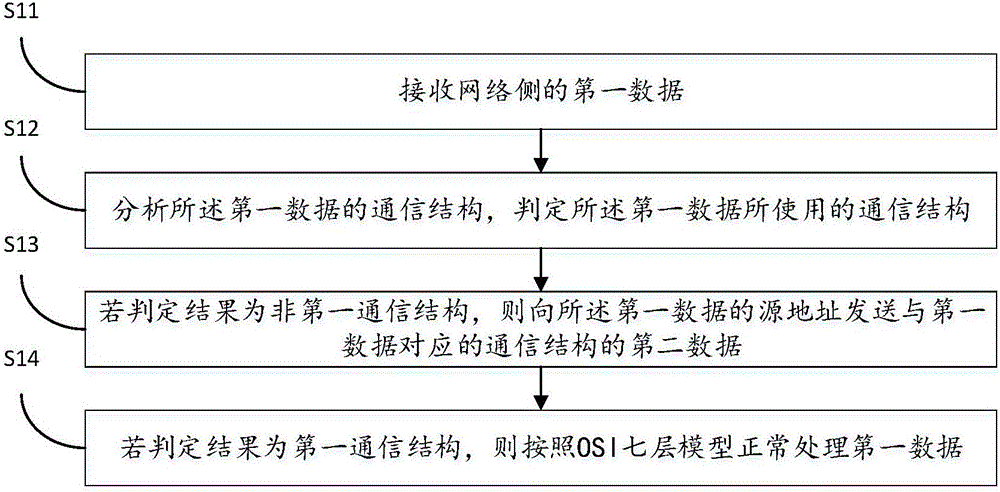
Computing equipment and equipment communication method
InactiveCN106385417AEnsure network securityEnsure equipment securityTransmissionPrivate networkStructure of Management Information
The invention discloses computing equipment and an equipment communication method. The method comprises the steps: receiving first data transmitted by second computing equipment at a network side; analyzing the communication structure of the first data, transmitting second data, corresponding to the first data, of a communication structure to the second computing equipment if the communication structure of the first data is not a first communication structure, wherein the second data is used for indicating the second computing equipment to transmit the data of the first communication structure. Through a reverse authentication mechanism, the method achieves the 'first verification, second connection' network access management, avoids the attack risks caused by the first connection, and guarantees the network safety and equipment safety of a private network. Moreover, the method employs a no-response strategy, reduces the attack risks, and further guarantees the network safety and equipment safety of the private network.
Owner:ANTAIOS (BEIJING) INFORMATION TECH
Service request message data processing method and device
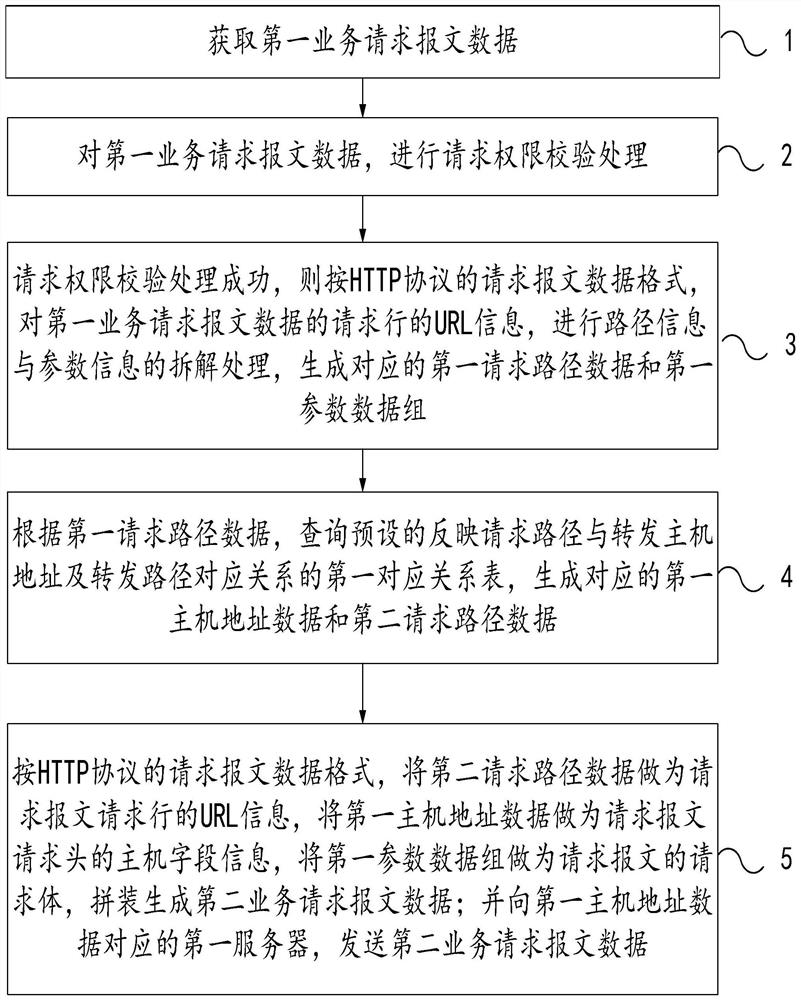
ActiveCN112769863AReduce the risk of being attackedReduce overheadUser identity/authority verificationSpecial data processing applicationsPathPingData set
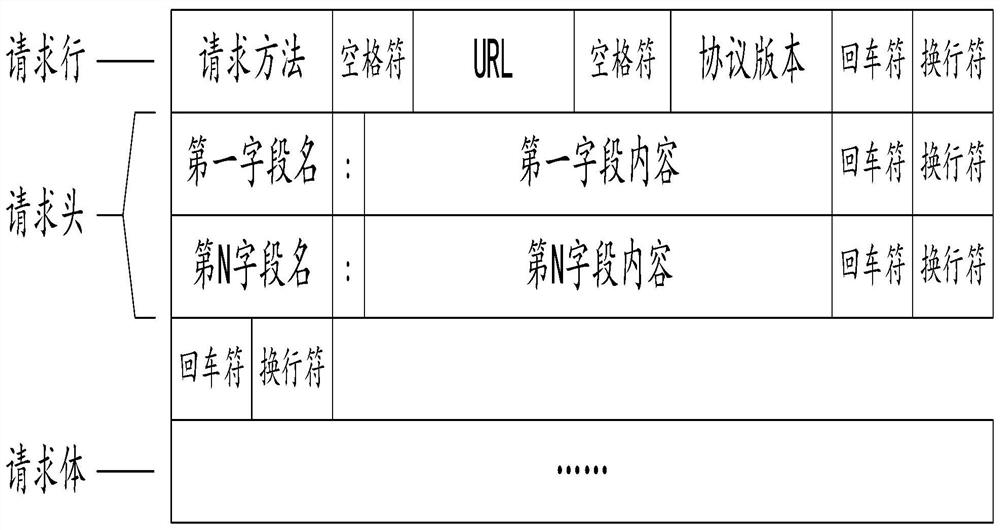
The embodiment of the invention relates to a service request message data processing method and device. The method comprises the following steps: acquiring first service request message data; performing request permission verification processing on the first service request message data; if verification succeeds, disassembling the first service request message data according to a request message data format of a hypertext transfer protocol to generate corresponding first request path data and a first parameter data set; querying a first corresponding relation table according to the first request path data, and generating corresponding first host address data and second request path data; and splicing and generating second service request message data according to a hypertext transfer protocol, and sending the second service request message data to a first server corresponding to the first host address data. The service with the function of method is deployed at the interface position of the application system and the public network, so that the attack risk can be reduced, and the software and hardware overhead of the sub-service for processing the service request can be reduced.
Owner:广东树米科技有限公司
Table element linkage method, device and equipment and computer readable storage medium
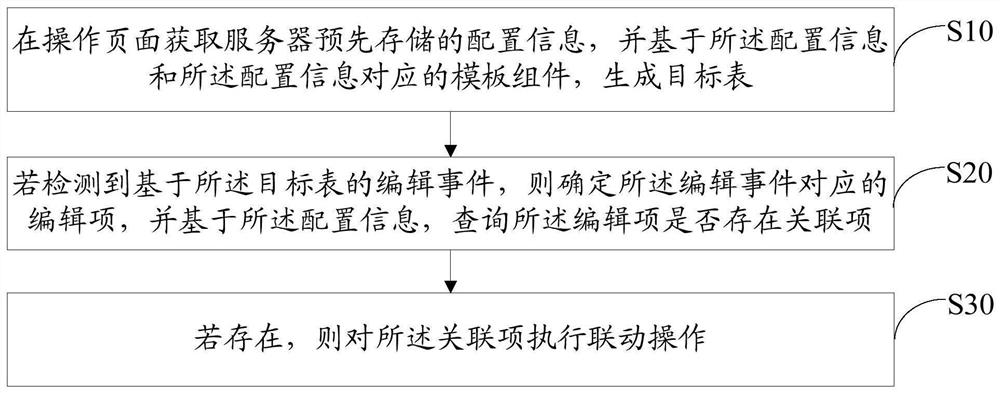
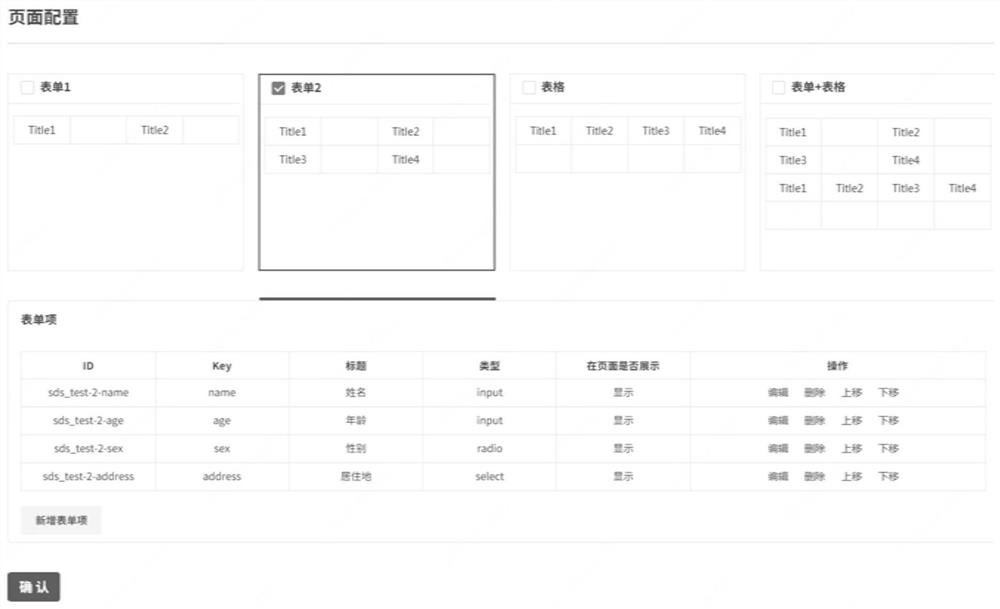
PendingCN112631591AReduce the risk of being attackedEasy maintenanceFinanceSoftware engineeringProgramming languageDatabase
The invention discloses a table element linkage method which comprises the following steps: acquiring configuration information pre-stored by a server on an operation page, and generating a target table based on the configuration information and a template component corresponding to the configuration information; if an editing event based on the target table is detected, determining an editing item corresponding to the editing event, and querying whether the editing item has an associated item or not based on the configuration information; and if so, executing a linkage operation on the associated item. The invention further discloses a table element linkage device and equipment and a computer readable storage medium. According to the method, the configuration information indicating the linkage relationship is transmitted to the server side for storage in the preset standard format, coding is not needed, the risk that codes are attacked is reduced, the target table is rapidly generated through the template assembly, and the target table is more flexible and easy to maintain.
Owner:WEBANK (CHINA)
Unmanned aerial vehicle GNSS deception detection method based on flight path
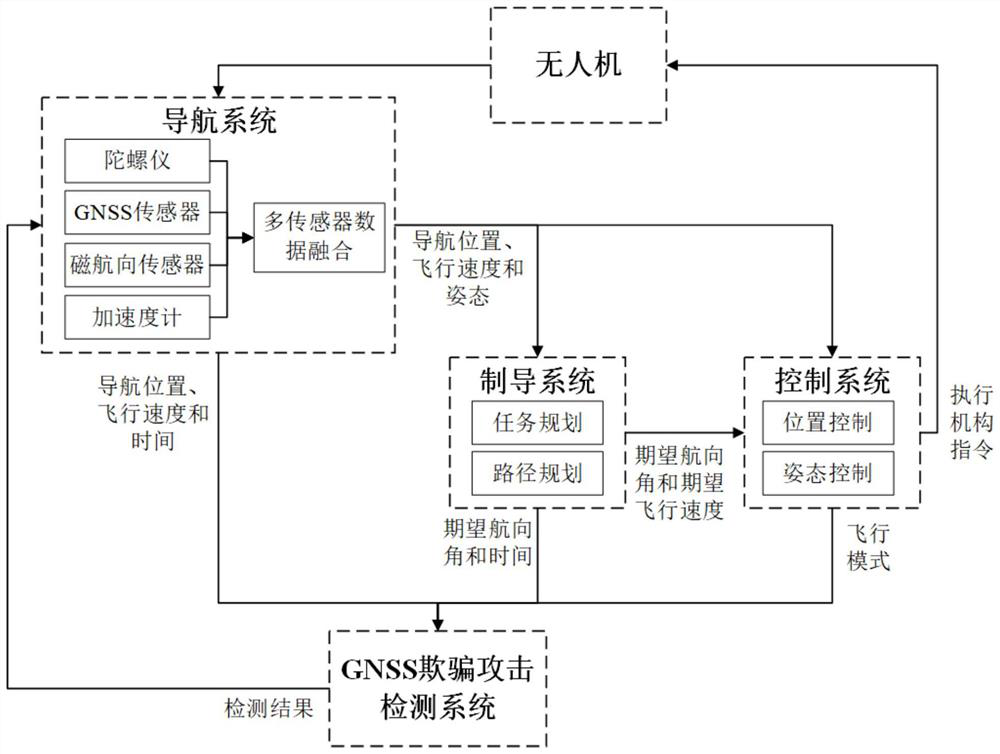
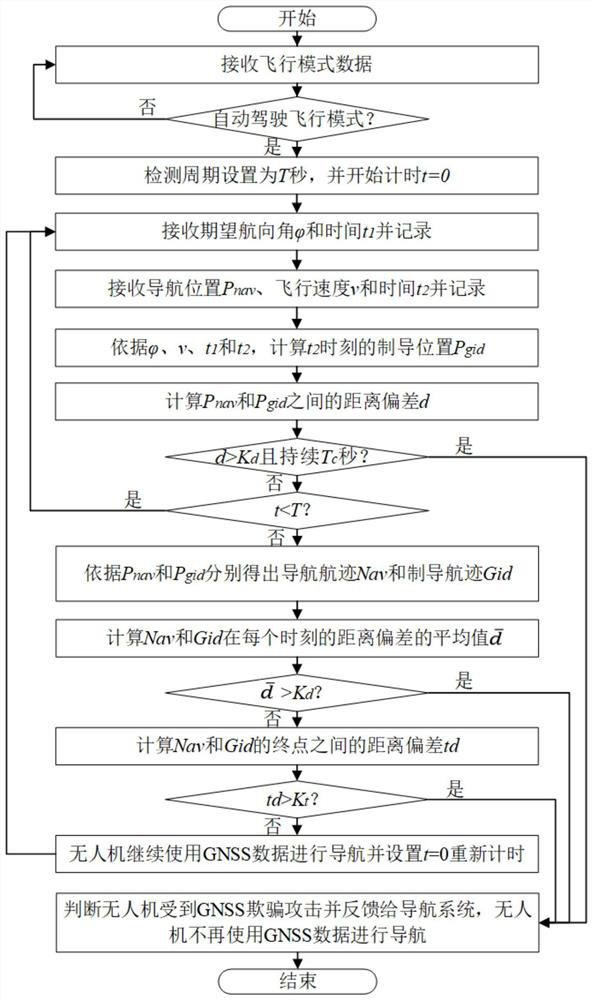
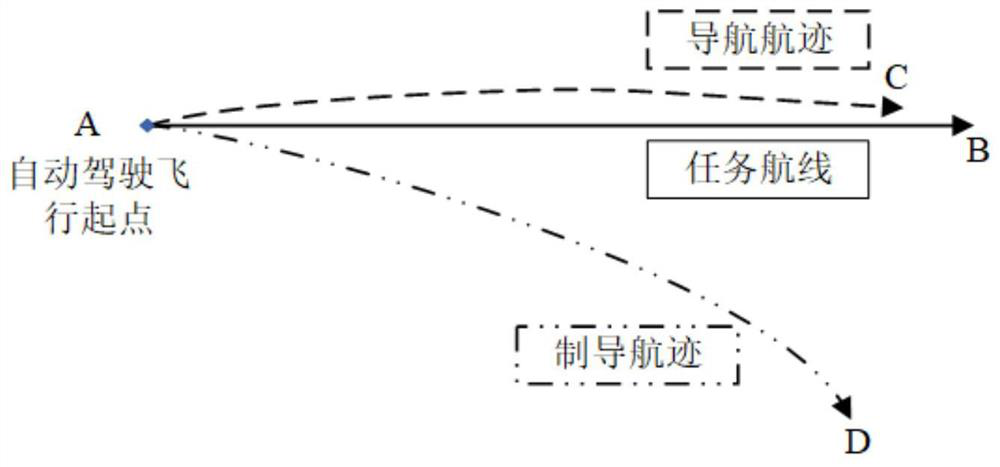
ActiveCN112859013AReal-time spoofing attackSpoofing attacks will notWave based measurement systemsInternal combustion piston enginesGuidance systemSimulation
The invention discloses an unmanned aerial vehicle GNSS deception detection method based on a flight path, and mainly solves problems that an attack risk is increased due to the change of a task flight path and the interference is easily caused due to the dependence on a sensor in the prior art. According to the scheme, a guidance position is calculated by means of an expected course angle obtained by a guidance system and a flight speed and a navigation position obtained by a navigation system; a navigation track and a guidance track are obtained according to the two positions; whether the distance deviation between the navigation position and the guidance position is continuously larger than a threshold value or not is judged, whether the average value of the distance deviation between the two tracks is larger than the threshold value or not is judged, and whether the distance deviation between the two track end points is larger than the threshold value or not is judged, if so, the unmanned aerial vehicle is determined to be subjected to spoofing attack, and the unmanned aerial vehicle does not use GNSS data any more and finishes detection; otherwise,the data is continuously used to realize cyclic detection of the unmanned aerial vehicle. According to the invention, the risk that the unmanned aerial vehicle is subjected to spoofing attacks is reduced, the safety of an unmanned aerial vehicle system is enhanced, and the method can be used for detecting external attacks of the unmanned aerial vehicle system.
Owner:XIDIAN UNIV
Project management platform based on fuzzy comprehensive evaluation algorithm and dynamic feedback mechanism
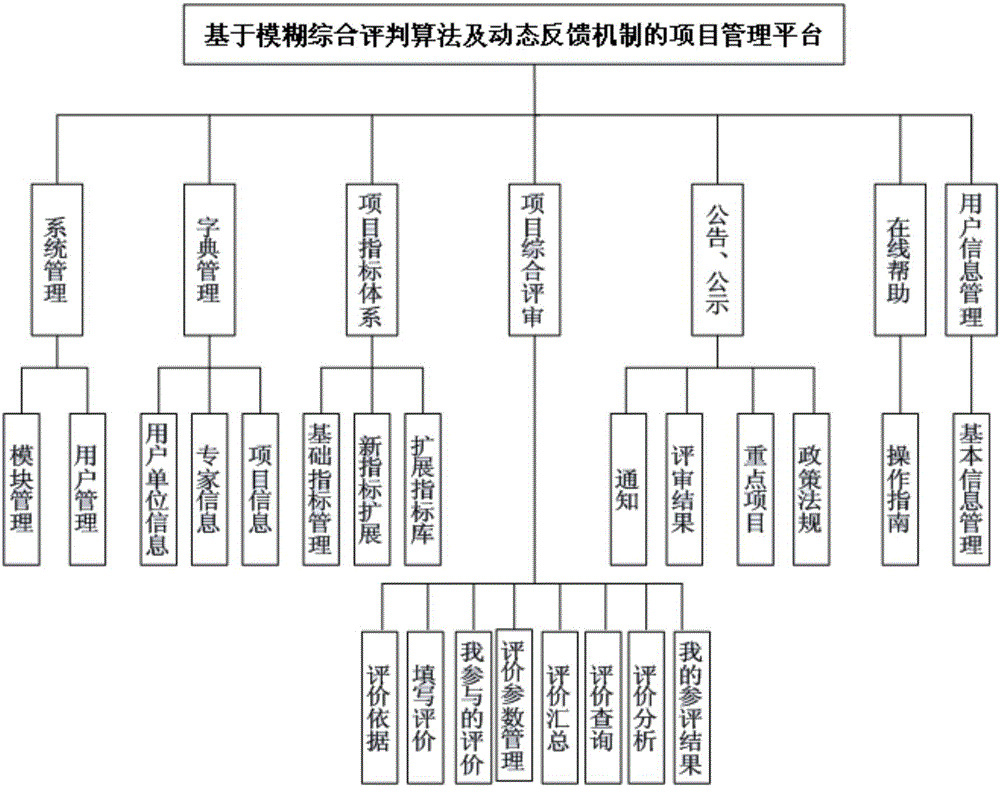
InactiveCN106485468AReduce the risk of being attackedOffice automationResourcesResearch ObjectSystems management
The invention discloses a project management platform based on a fuzzy comprehensive evaluation algorithm and a dynamic feedback mechanism. The project management platform is composed of seven modules, namely a system management module, a dictionary management module, a project index system module, a project comprehensive evaluation module, a public announcement module, an online helping module and a user information management module. According to the project management platform, related functional departments of Tibet Rikaze municipal government are used as researching objects. For settling problems of the departments in a project application process and a project management process, the invention provides the project management platform based on the fuzzy comprehensive evaluation algorithm and the dynamic feedback mechanism. Through the platform of the invention, project application, project evaluation, dynamic management and dynamic updating can be performed in time in an online manner. The project management platform further has advantages of changing a traditional working mode, improving department project application level and project management level, promoting development of Tibet, and realizing a good application prospect.
Owner:TIANJIN UNIV
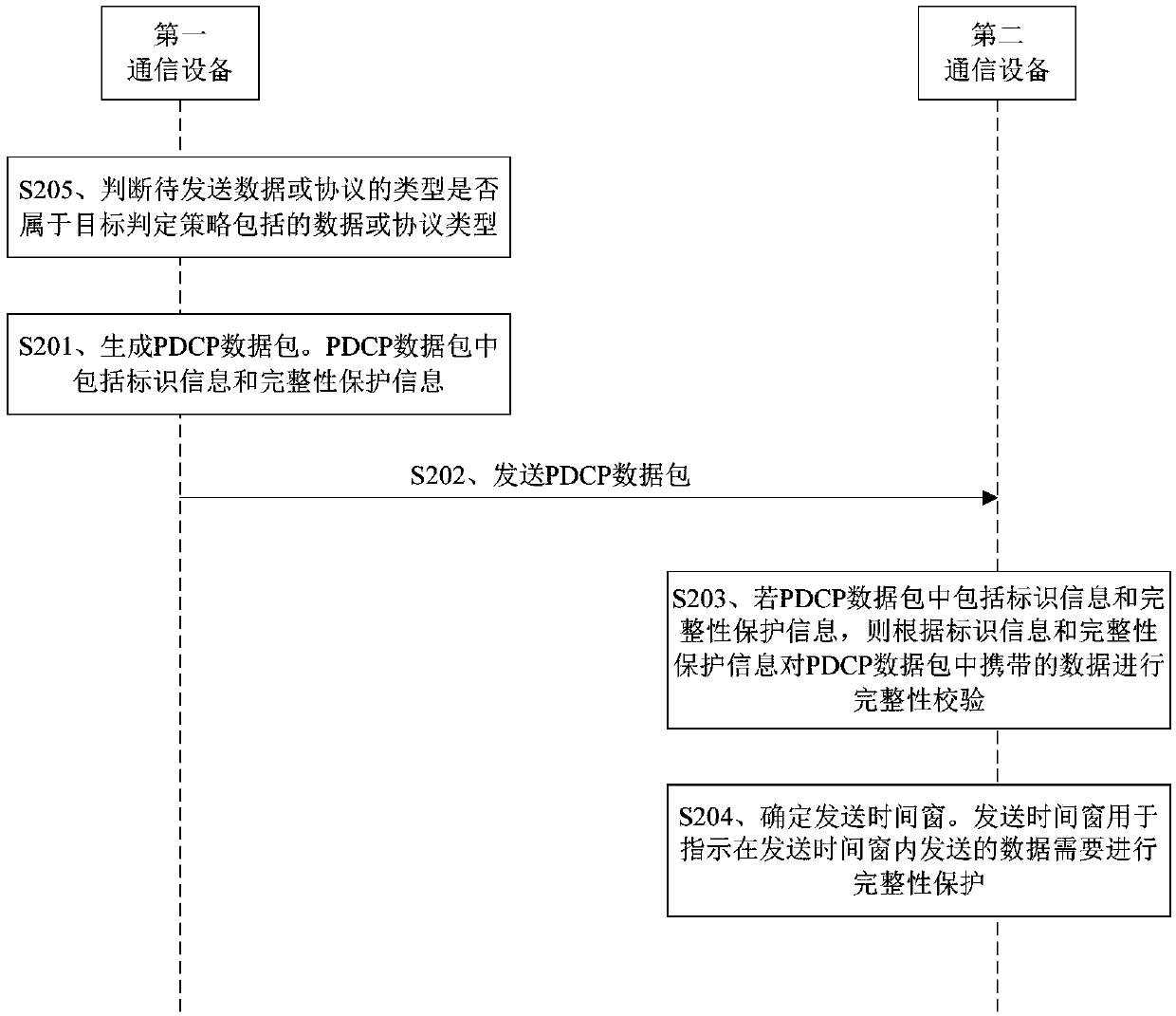
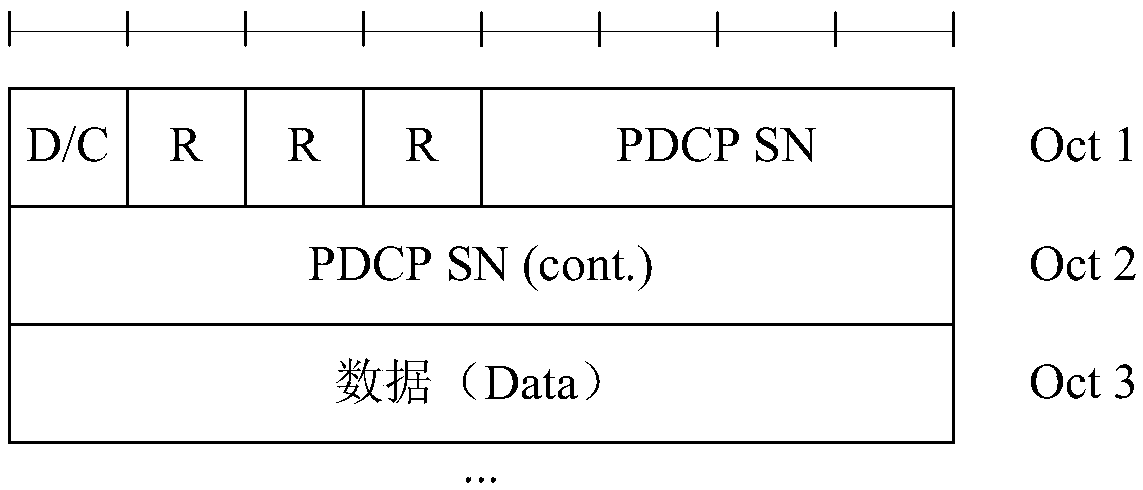
Data transmission method and device
ActiveCN110830421AReduce the risk of being attackedImprove securityWireless network protocolsTransmissionData transmissionComputer security
The embodiment of the invention provides a data transmission method and device. The data transmission method comprises the steps of generating a PDCP data packet by performing integrity protection onto-be-sent data, wherein the PDCP data packet comprises identification information and integrity protection information, and the identification information is at least used for indicating that integrity protection is carried out on data carried in the PDCP data packet, and the integrity protection information is used for carrying out integrity verification on the data carried in the PDCP data packet; and sending the PDCP data packet. According to the data transmission method provided by the embodiment of the invention, integrity protection is performed on the data carried in the PDCP data packet, and indication is performed through the identification information, so that the security of data transmission is improved.
Owner:HUAWEI TECH CO LTD
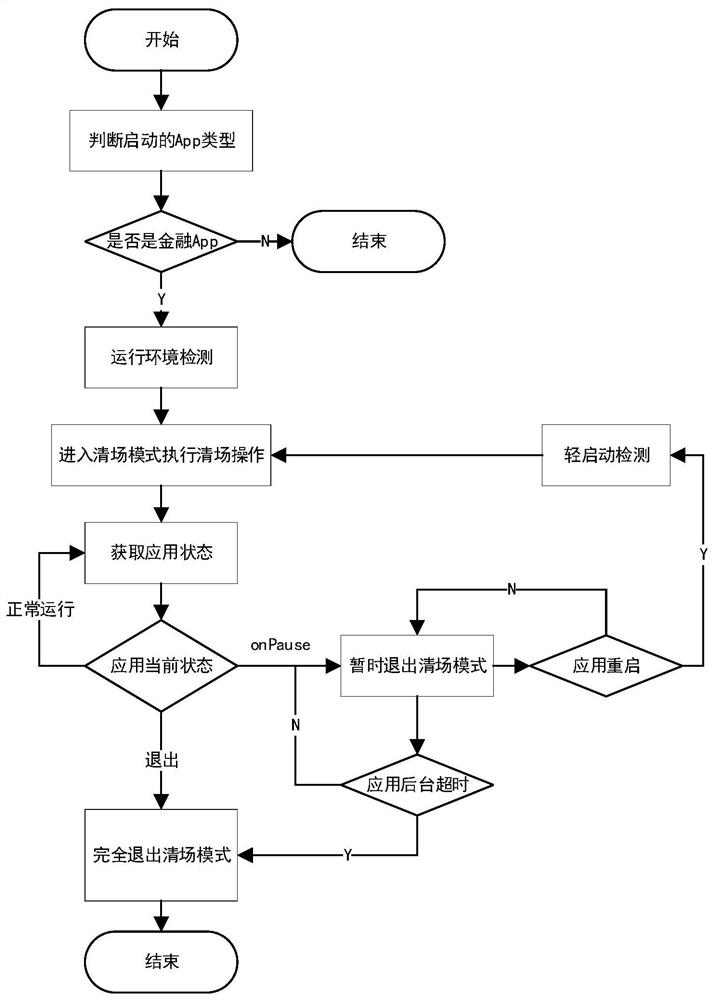
Method for ensuring safety of local operating environment of financial App
PendingCN111814180AEasy to useEnsure safetyDigital data protectionPayment protocolsAttackFinancial security
The invention discloses a method for ensuring the security of a local operating environment of a financial App, which is characterized by comprising the following steps of: A, judging whether a started App is the financial App or not, and if so, detecting the operating environment; b, entering a site cleaning mode and executing site cleaning operation; c, executing different site clearing operations according to the state of the application, such as temporarily quitting a site clearing mode, restarting the site clearing mode, clearing a background financial App and the like; and D, completelyquitting the site cleaning mode. According to the method, the state of the App is monitored, the financial App is matched according to the package name of the App, and the site clearing strategy is started; when the financial App is started, the operation environment is detected, and the site clearing operation is executed, so that the financial App operates in the site clearing mode, and the useof the financial App and the safety of financial transactions are ensured. By using the System Server, an external interface is not exposed, and the attack difficulty of the method is improved. Therefore, the method has the advantages that the security of the local operation environment of the financial App is improved, the attacked risk is reduced, and the financial security is protected.
Owner:中天掌金(北京)科技有限公司
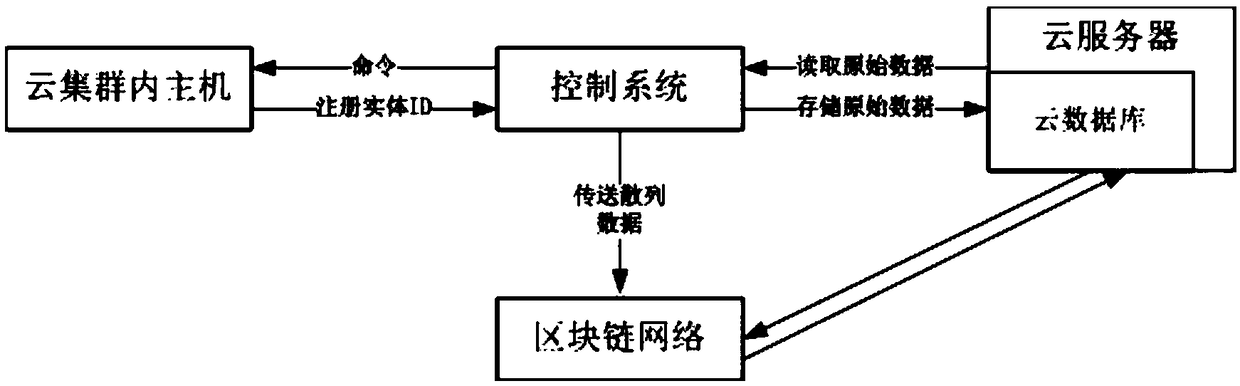
Trusted cloud task scheduling system and auditing method
InactiveCN109327498AAdd audit functionReduce the risk of being attackedEncryption apparatus with shift registers/memoriesUser identity/authority verificationControl systemData information
The invention discloses a trusted cloud task scheduling system, comprising a cloud cluster, a control system, a cloud database and a blockchain network. On the basis of a cloud cluster architecture, the system combines a blockchain network technology and uses the blockchain network to record hashes of cloud task scheduling information; the system can combine cloud scheduling with the blockchain technology, and increases an audit function; and the system can record the scheduling condition of cloud tasks within a cloud platform, provide trusted data information and reduce the risk of being attacked.
Owner:XIAN UNIV OF TECH
Cross-network transmission system and method for individual soldier
PendingCN113949523ARealize cross-network transmissionGuaranteed relativityKey distribution for secure communicationEngineeringSerial code
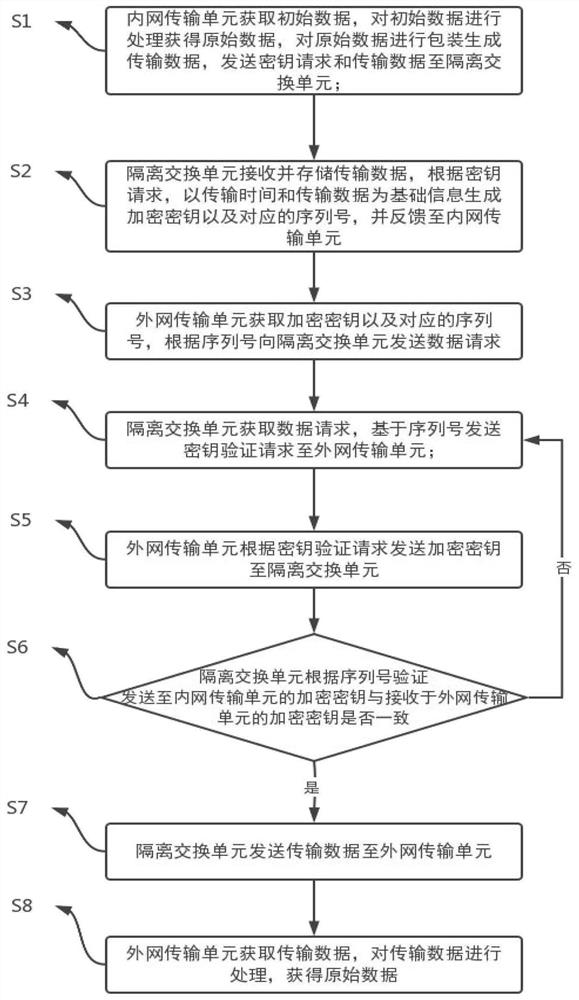
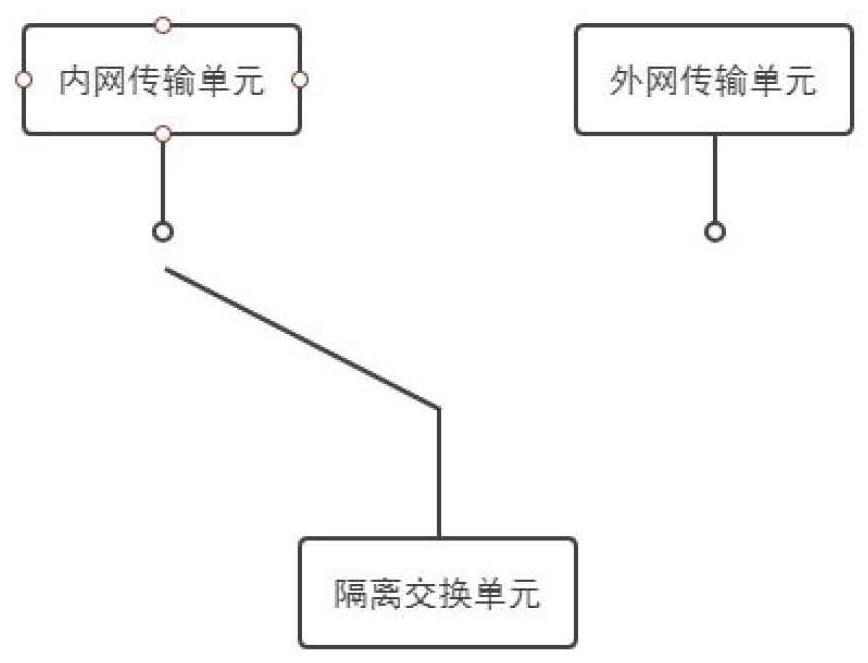
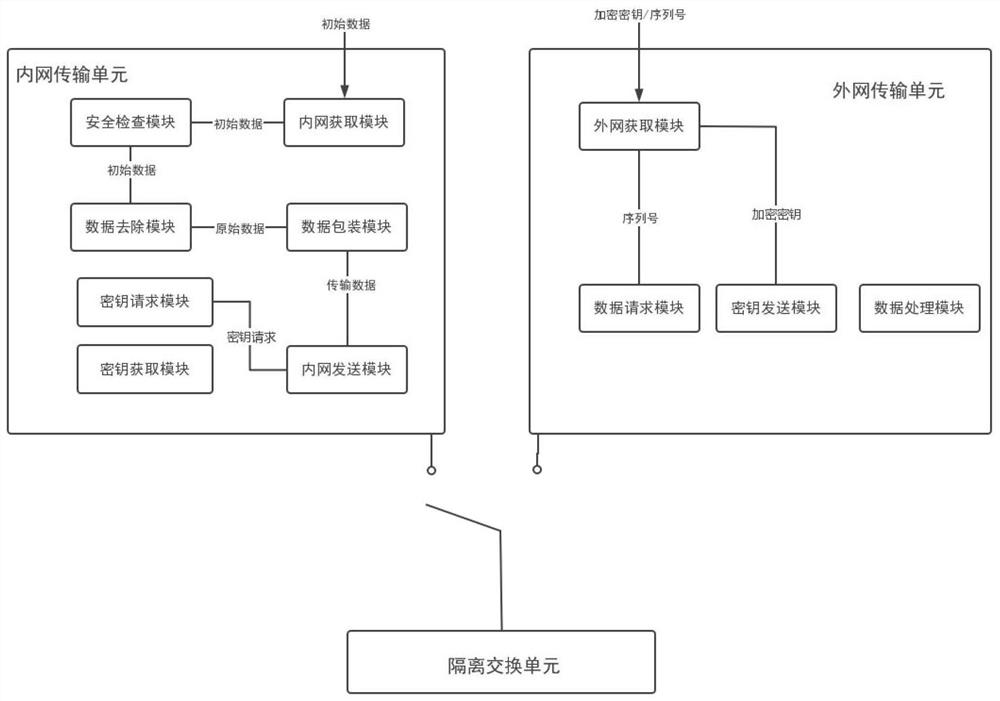
The invention relates to a cross-network transmission system and method used by an individual soldier. A secret key request and transmission data are sent to an isolation exchange unit through an intranet transmission unit; the isolation exchange unit generates an encryption key and a corresponding serial number and feeds back the encryption key and the corresponding serial number to the intranet transmission unit; an external network transmission unit obtains the encryption key and the corresponding serial number, and sends a data request to the isolation exchange unit according to the serial number; the isolation exchange unit sends a key verification request to the external network transmission unit based on the serial number; the external network transmission unit sends the encryption key to the isolation exchange unit; the isolation exchange unit verifies whether the encryption key sent to the intranet transmission unit is consistent with the encryption key received from the extranet transmission unit or not according to the serial number, and if yes, transmission data is sent to the extranet transmission unit; and the external network transmission unit obtains transmission data. In the invention, the cross-network transmission of the file is realized through the isolation exchange unit, and the encryption cross-network transmission between individuals is realized through the encryption key.
Owner:ELECTRIC POWER RES INST OF STATE GRID ANHUI ELECTRIC POWER +1
Integrity verification calculation method and system based on operation spanning tree state machine
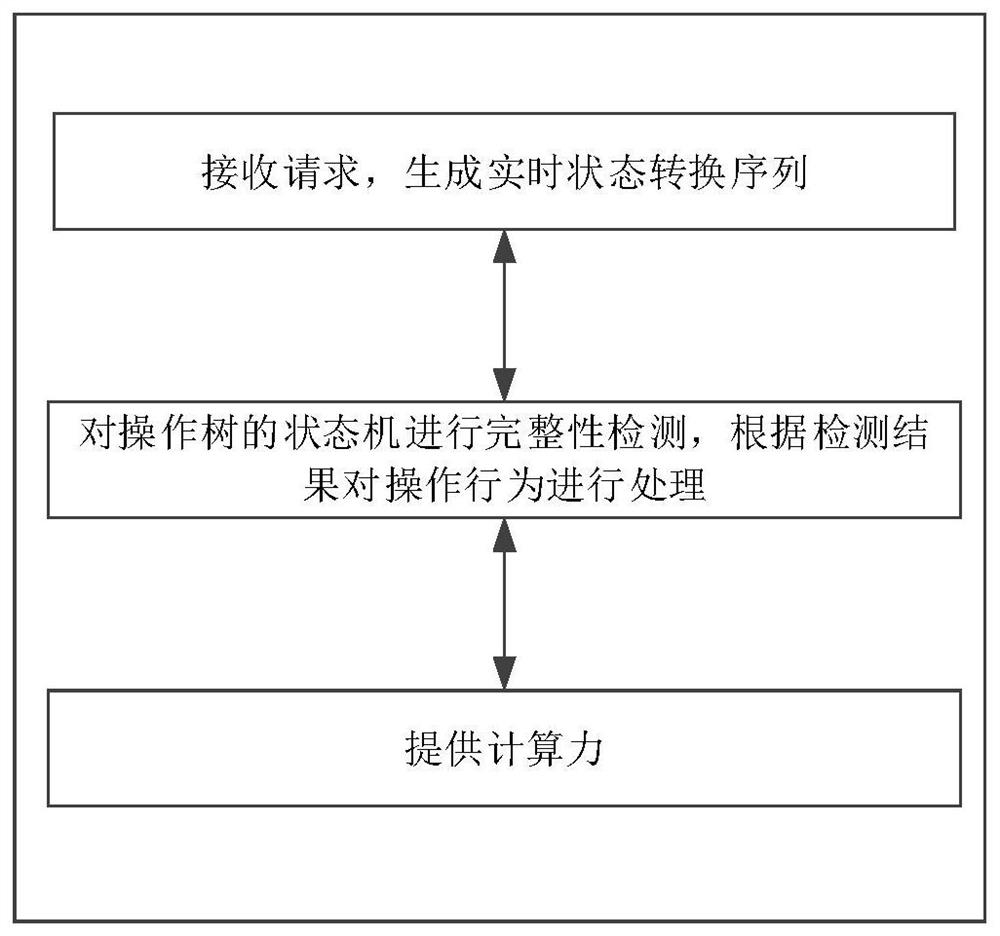
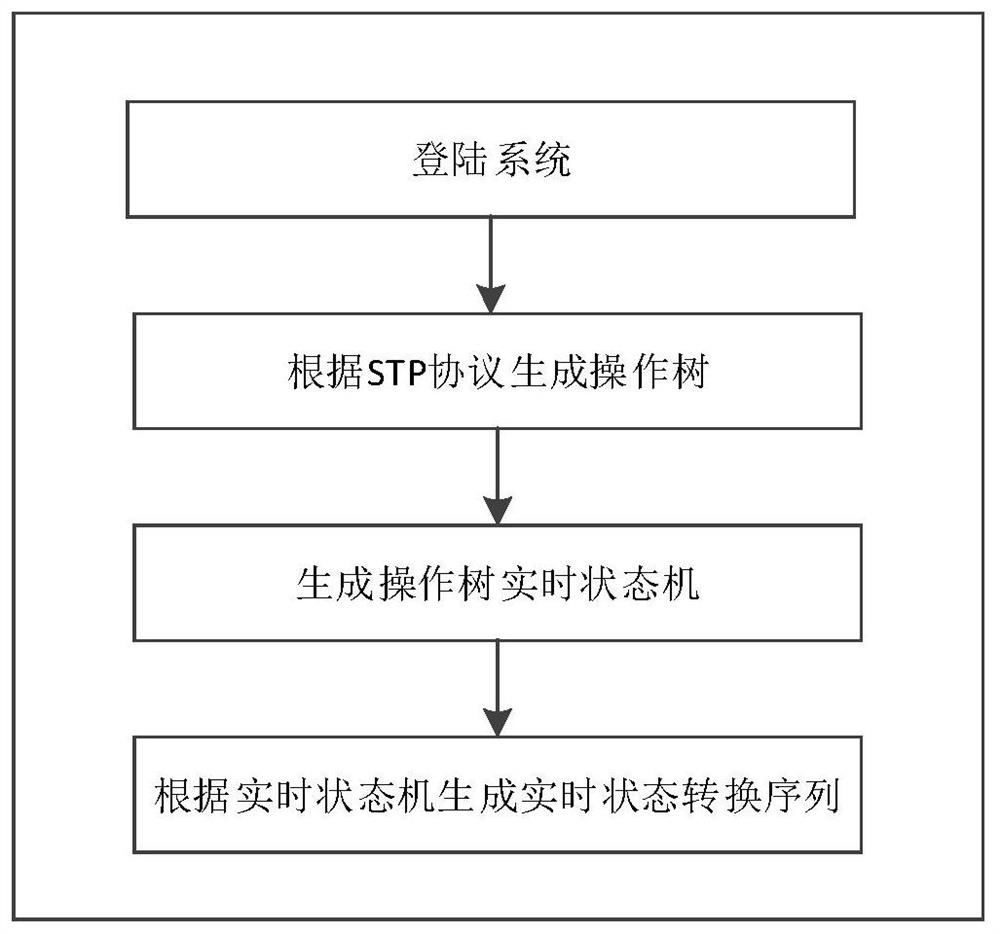
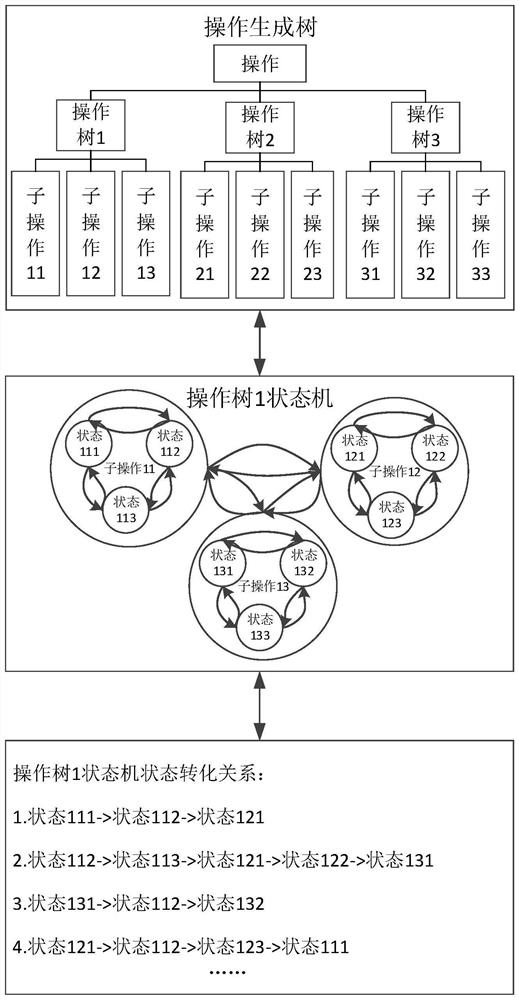
ActiveCN112437070AReduce the risk of being attackedEnsure computing securityPlatform integrity maintainanceTransmissionCloud detectionComputing systems
The invention discloses an integrity verification calculation system and method based on an operation spanning tree state machine, and the method comprises: an operation tree generation step: receiving a business request, generating an operation tree, and forming a state machine according to each state of the operation tree and a conversion condition of the operation tree; a fireproof cloud detection filtering step: carrying out integrity detection on a state machine of the operation tree, and filtering operation behaviors according to a detection result; and a brain-like computing step: providing computing power for the operation tree generation step and the fireproof cloud detection filtering step. The user operation behavior is converted into the operation tree state machine for integrity detection, bidirectional detection and comprehensive detection can be achieved, the risk that a service system is attacked is reduced, the behavior of a legal user has safety and non-repudiation, and the strong computing power provided based on brain-like computing can ensure the security, stability and high efficiency of the computing of the business system when massive users access in parallel.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
Traceable access control method based on double block chains
PendingCN114826652APrevent tamperingEasy to findKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEngineeringBlockchain
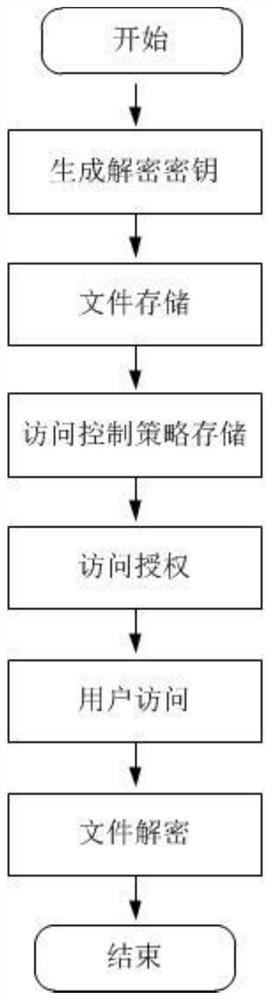
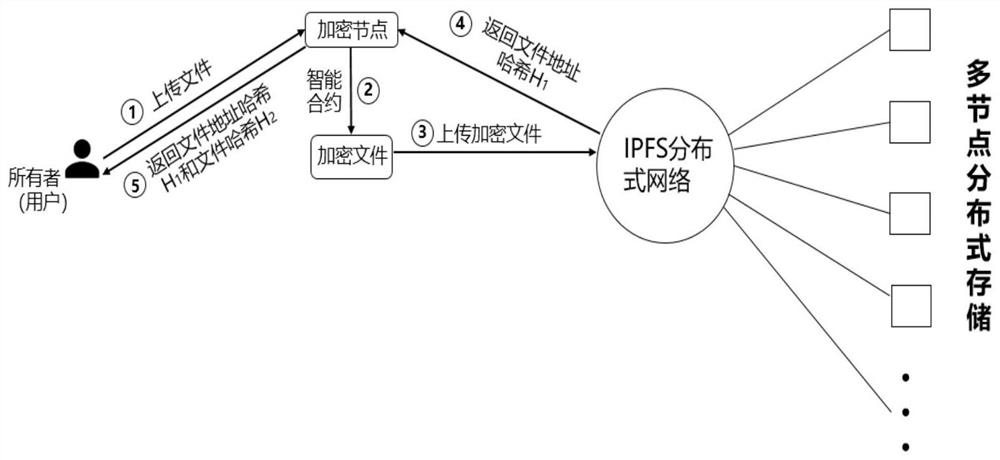
The invention discloses a traceable access control method based on double block chains, and the method comprises the steps: generating a decryption key, storing a file, storing an access control strategy, carrying out access authorization, carrying out user access, carrying out file decryption, and enabling an initial user to provide own attribute information for registration, thereby obtaining the decryption key; the uploaded file is encrypted and then stored in the IPFS, an intelligent access strategy of attributes is set according to the file, and the file can be accessed only when the intelligent strategy is met; and the accessed file also needs to be decrypted by a decryption key during registration, and when the file is tampered, the access process is checked to search for illegal users, so that more accurate equipment traceability is achieved. According to the method, the unpaired CP-ABE algorithm is adopted to encrypt the uploaded file, and the simple scalar multiplication in the elliptic curve encryption is utilized to replace bilinear pairing, so that the file encryption efficiency is improved; the IPFS is used for storing file data, the risk that a database is attacked is reduced, and the files are prevented from being lost and tampered.
Owner:NANJING UNIV OF POSTS & TELECOMM
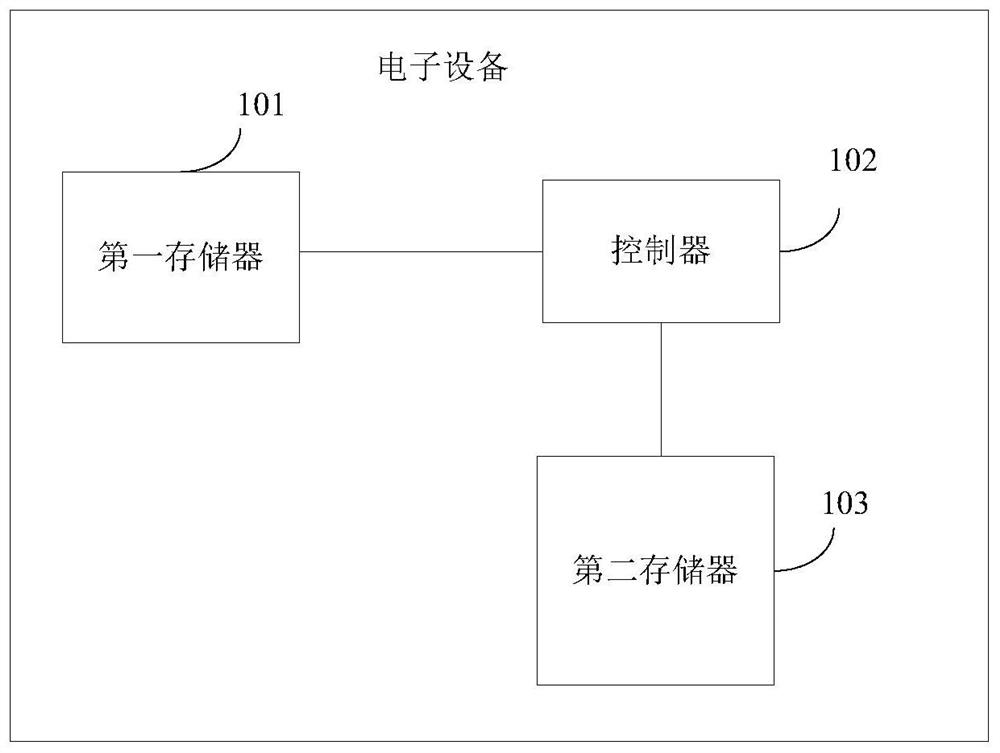
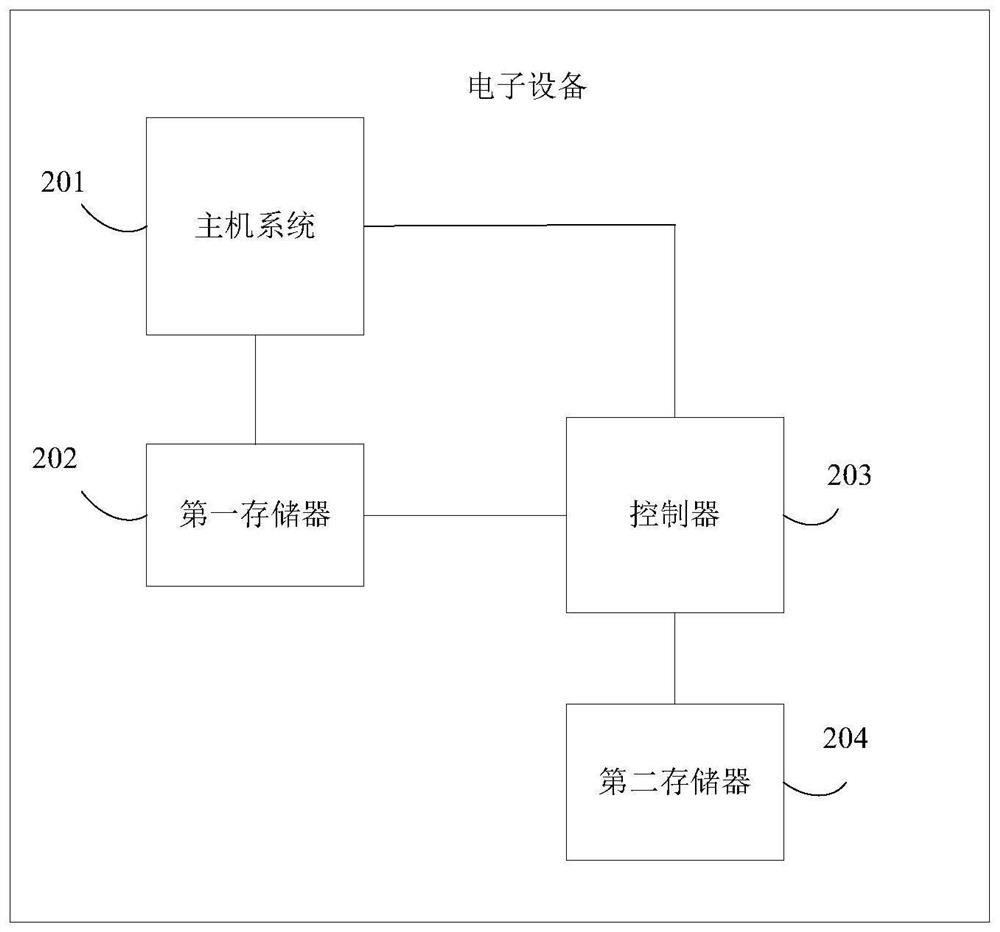
Control method and electronic equipment
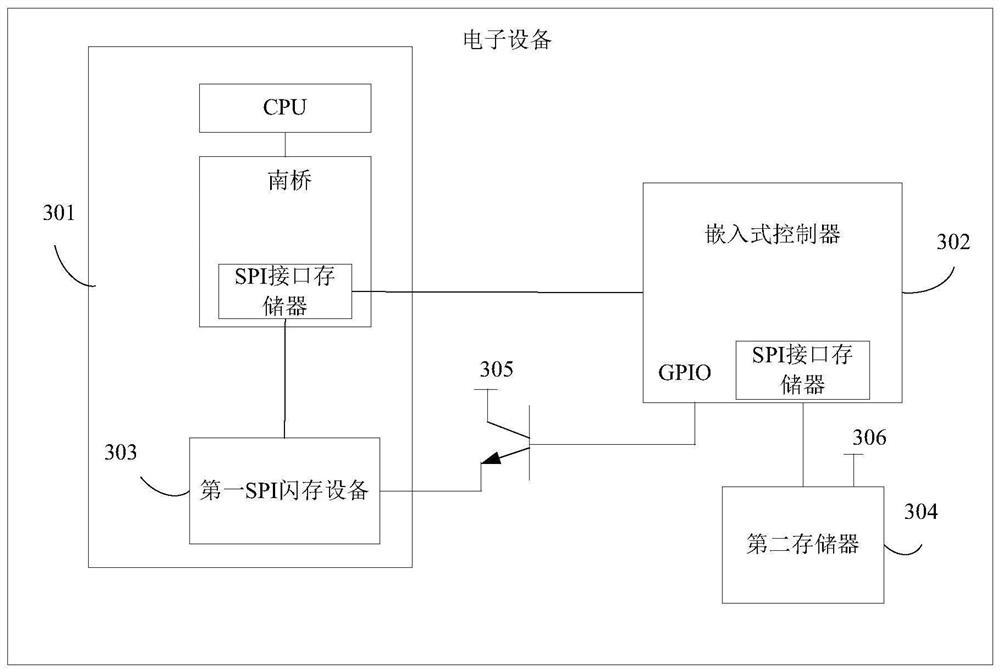
PendingCN113051576AReduce stepsReduce the risk of being attackedDetecting faulty hardware by power-on testBootstrappingAttackControl engineering
The invention provides a control method and electronic equipment. The electronic equipment comprises a controller; a first memory connected with the controller and at least storing a guide system; a second memory which is connected with the controller and is used for storing update data of the boot system; wherein after the electronic equipment completes power-on self-test, the controller controls the first memory to be in an inaccessible state and controls the second memory to be in an accessible state. According to the scheme of the invention, illegal attacks suffered by the guidance system can be reduced.
Owner:LENOVO (BEIJING) LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com