Method and system for achieving secret key generation and protection through cloud and terminal three-power separation
A technology of key generation and separation of powers, applied in the field of information security, can solve the problem that it is difficult for users to establish trust in SaaS service providers, and achieve the effect of reducing the risk of being attacked, improving security, and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
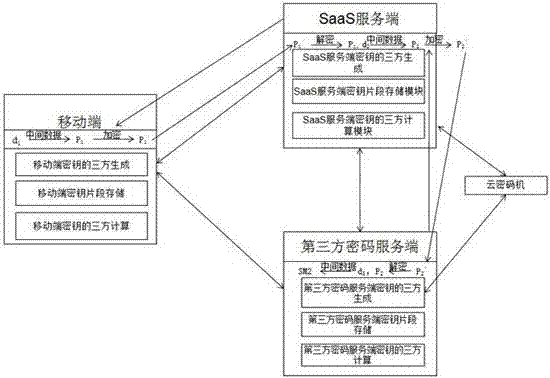
[0052] A method for key generation and protection realized by the separation of three rights in the cloud plus terminal of the present invention uses the mobile terminal, the SaaS server and the third-party password server to jointly generate a user key, and when used, the three parties jointly calculate and maintain independence And mutually restrict and cooperate with each other to improve the overall security of the user key; including the following steps:
[0053] (1) Key generation process: the mobile terminal, the SaaS server and the third-party password server jointly generate a key SM2;
[0054] (2) Key storage process: The key fragment of the mobile terminal is comprehensively protected by multiple means of TEE / SE, binding device hardware, fingerprint / face biometrics, password and APP reinforcement, SaaS server and third-party password server Use the cloud cipher machine to securely store their respective key fragments;
[0055] (3) Key usage process: After the user ...
Embodiment 2
[0057] A method for key generation and protection realized by the separation of three rights in the cloud plus terminal of the present invention uses the mobile terminal, the SaaS server and the third-party password server to jointly generate a user key, and the three parties jointly calculate when using it, and each remains independent And mutually restrict and cooperate with each other to improve the overall security of the user key; including the following steps:
[0058] (1) Key generation process: The mobile terminal, SaaS server and third-party password server jointly generate a key SM2; as attached figure 2 shown, including the following steps:
[0059] ①. The mobile terminal generates a random number d1, d1 = MobileGenRand(); calculates the intermediate data p1 from the random number d1, p1 = Encode(d1); encrypts p1 with the public key or certificate of the SaaS server, and obtains p1', p1' = Encrypt (p1, SaaSPubKey); and send p1' to the SaaS server;
[0060] ②. The...
Embodiment 3
[0083] as attached figure 1 As shown, a kind of cloud-plus-terminal separation of three rights of the present invention realizes key generation and protection system, including mobile terminal, SaaS server end, third-party password server end and cloud cipher machine; mobile terminal is used for mobile terminal key fragment production, safe storage and use; the SaaS server is used for the generation, safe storage and use of the key fragment of the SaaS server, and provides an API for its use; the third-party password server is used for the key fragment of the third-party password server Generation, safe storage and use; the cloud cipher machine is used for SaaS server and third-party cipher server random number generation, encryption and decryption of key fragments.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com