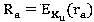Mimicry defense judgment method and system based on partial homomorphic encryption algorithm
A technology of homomorphic encryption and adjudication method, which is applied in the field of information security, can solve the problems of inconvenient and quick search of executive bodies, execution bodies cannot be completely heterogeneous, and high equipment performance requirements, so as to reduce the risk of being attacked and reduce attack sensitivity high probability and high safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The following further clarifies the present invention with reference to the drawings and specific embodiments. It should be understood that these embodiments are only used to illustrate the present invention and not to limit the scope of the present invention.
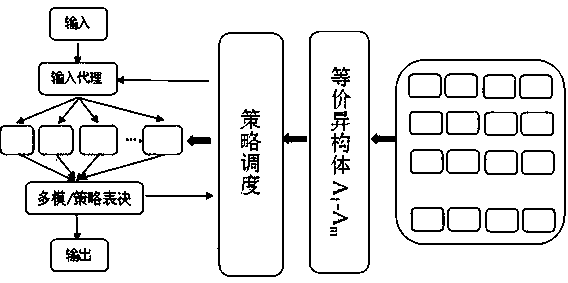
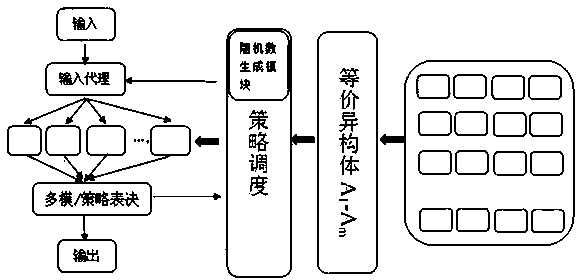
[0033] In the mimic defense ruling system based on partial homomorphic encryption of the present invention, a homomorphic encryption module is added to the execution module, that is, a homomorphic encryption module and figure 1 The execution body in the executor is combined to form a new execution body; the strategy scheduling module only needs to add a random number generation module, and there is no need to change the hardware of the original system, which is convenient for upgrading the existing system.
[0034] The method of the present invention includes the following steps:
[0035] Step (1.1). After the task is input to the mimic defense system, the strategy scheduling module selects a certain amount of heterogen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com