Client based on biometric feature recognition and working method thereof
A biometric data and client-side technology, applied in the field of information security, can solve problems such as user information security threats, achieve the effect of improving security and reducing the risk of being attacked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
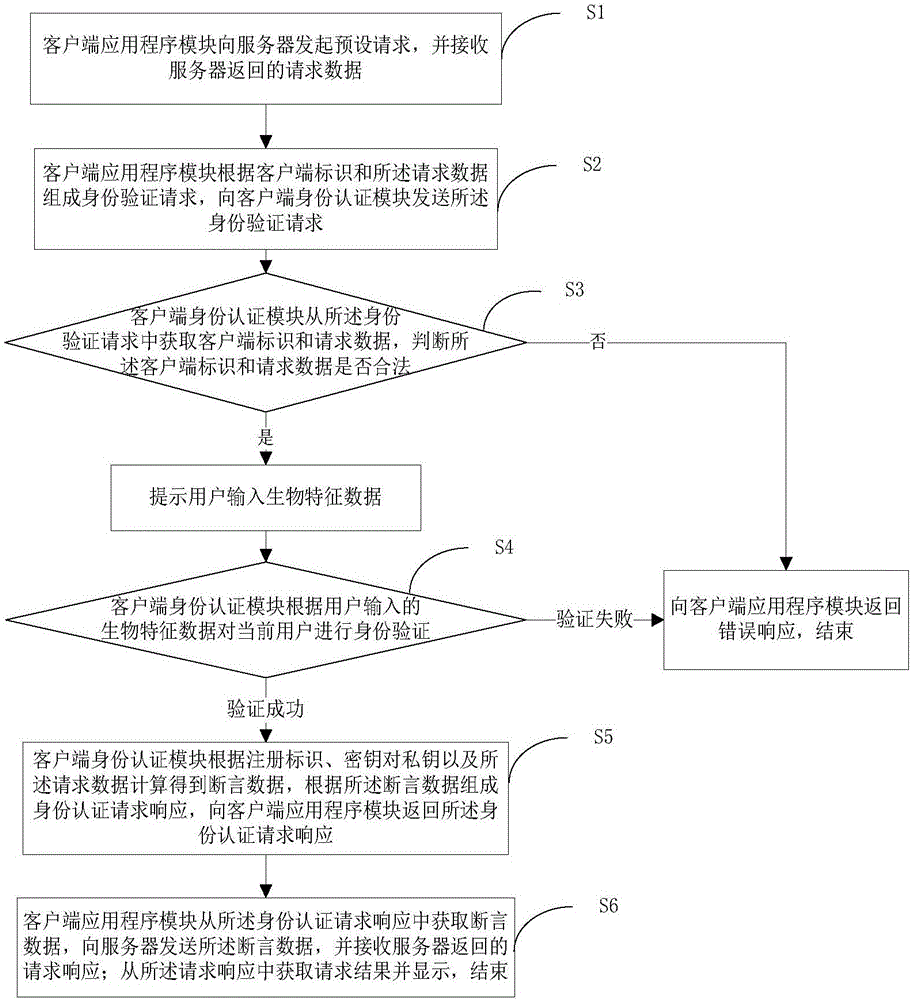
[0035] This embodiment provides a client working method based on biometric identification, wherein the client includes a client application program module and a client identity authentication module, and its working method is specifically as follows: figure 1 shown, including the following steps:
[0036] Step S1: The client application module initiates a preset request to the server, and receives the request data returned by the server;
[0037] Specifically, the preset request may be a registration request, an authentication / transaction request;
[0038] When the preset request is a registration request, the request data is specifically registration data, and the registration data includes an application ID, a user name parameter, a challenge value parameter and an authentication policy parameter;
[0039] When the preset request is an authentication request, the request data is specifically authentication data, and the authentication data includes an application ID, a chal...
Embodiment 2
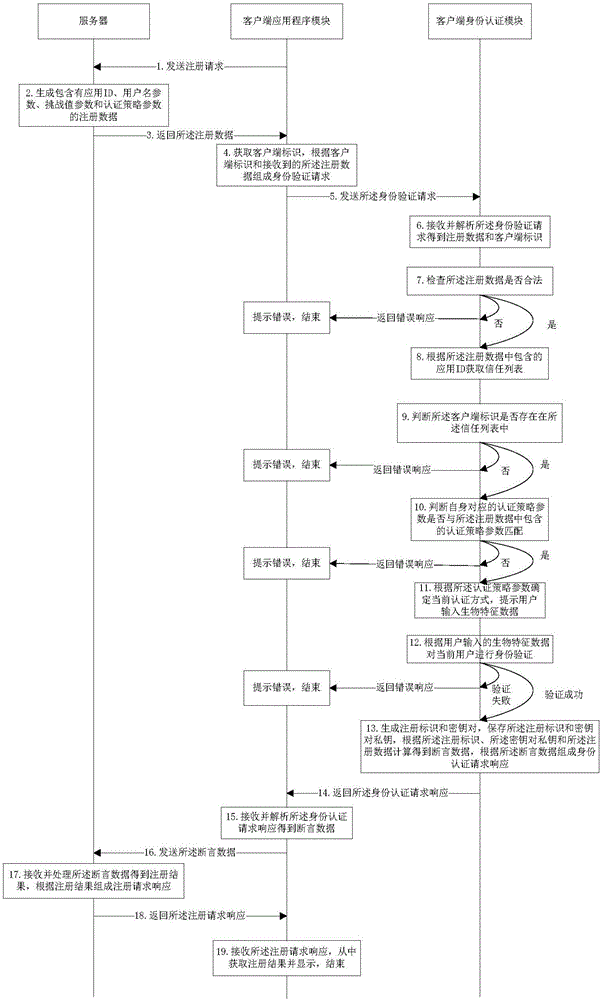
[0052] Embodiment 2 of the present invention provides a registration method based on biometric identification, which is suitable for a system composed of a server and a client, wherein the client includes a client application module and a client identity authentication module, such as figure 2 As shown, when the user initiates a registration operation to the client application module, the following steps are performed:
[0053] Step 1: The client application module sends a registration request to the server;
[0054] For example, the registration request sent is as follows:
[0055] {"userName":"test","method":"registStart","uafResponse":""}.
[0056] Step 2: The server generates registration data including application ID, user name parameters, challenge value parameters and authentication policy parameters;
[0057] For example, the generated registration data is as follows:
[0058] [{"header":{"upv":{"major":1,"minor":0},"op":"Reg","appID":"https: / / uafmagdc.cloudentify....
Embodiment 3
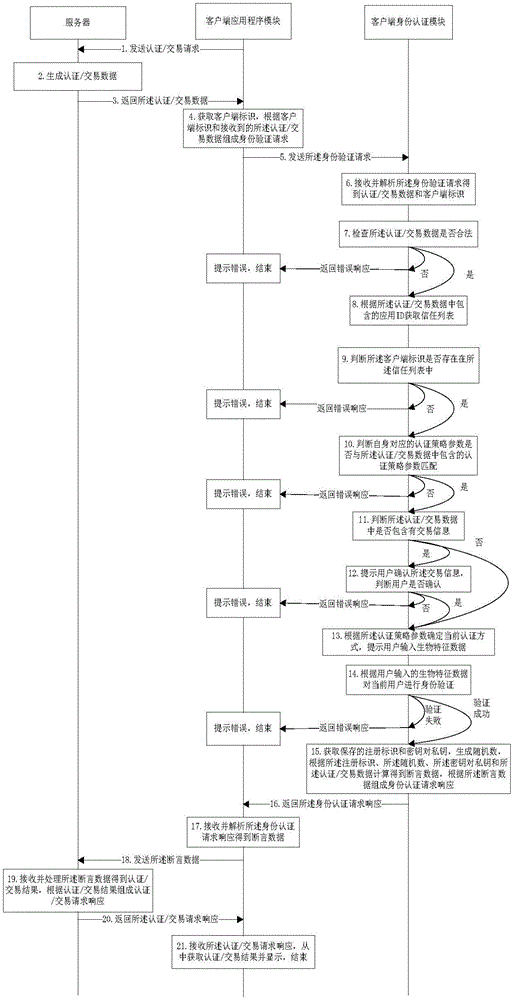
[0111] Embodiment 3 of the present invention provides an authentication / transaction method based on biometric identification, which is suitable for a system composed of a server and a client, wherein the client includes a client application module and a client identity authentication module, such as image 3 As shown, when the user initiates an authentication / transaction operation to the client application module, the following steps are performed:
[0112] Step 1: The client application module sends an authentication / transaction request to the server;
[0113] Step 2: The server generates authentication / transaction data;
[0114] Step 3: the server returns the authentication / transaction data to the client application module;
[0115] Step 4: The client application module obtains the client ID, and composes an identity verification request according to the client ID and the received authentication / transaction data;
[0116] Step 5: the client application module sends the ident...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com