Unmanned aerial vehicle GNSS deception detection method based on flight path
A technology of unmanned aerial vehicle and track, applied in the field of information security, can solve the problems of inaccurate magnetic heading, increasing the risk of being attacked, reducing the feasibility of detection, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] Embodiments of the present invention will be further described below in conjunction with the accompanying drawings, and the present invention includes but not limited to the following embodiments.
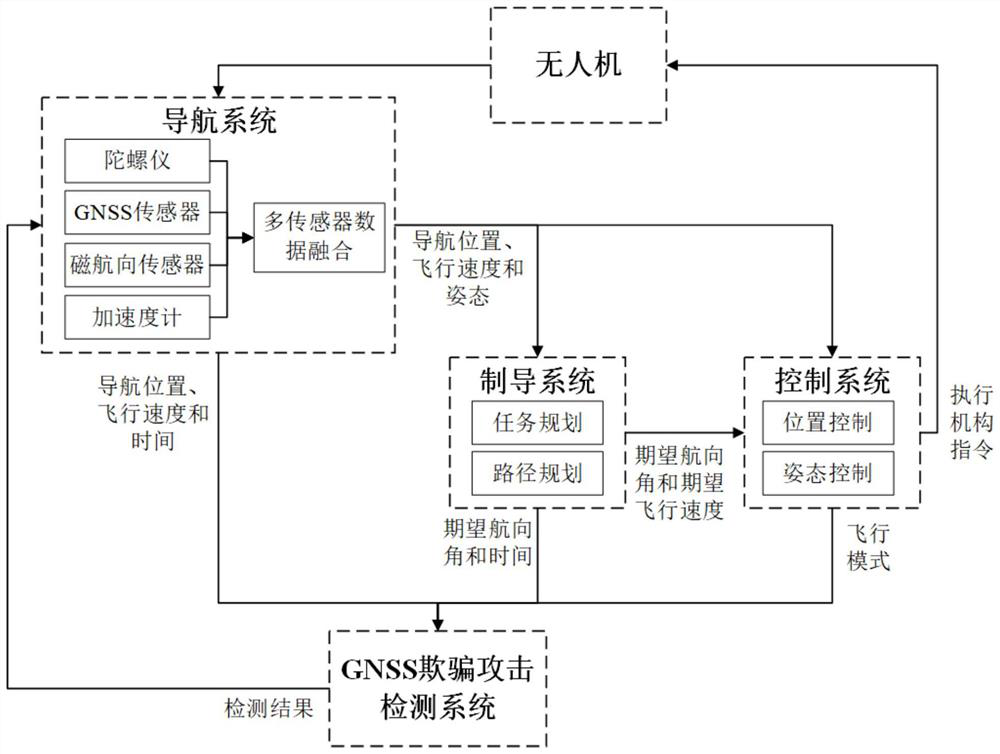
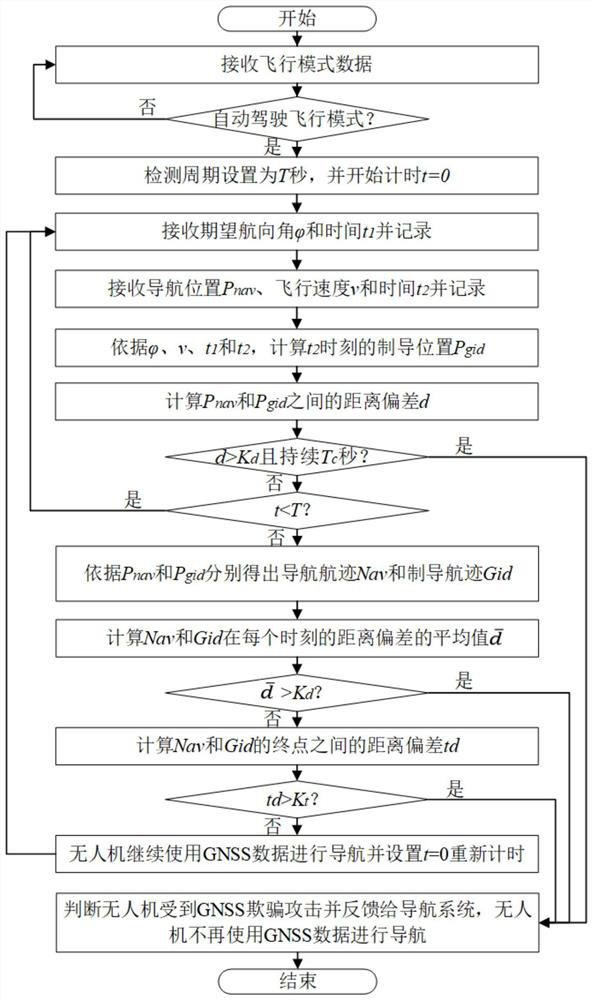
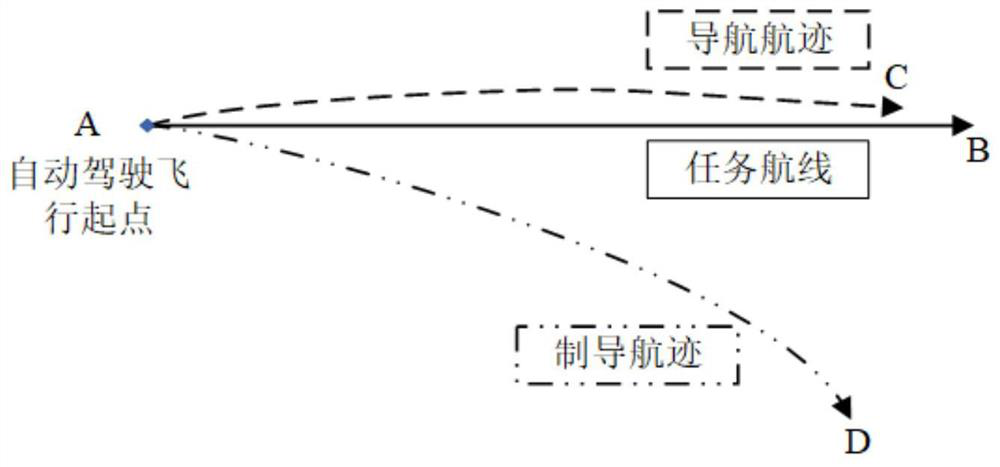
[0040] refer to figure 1, UAV GNSS spoofing detection system, including navigation system, guidance system, control system, GNSS spoofing attack detection system and UAV body. Among them, the navigation system includes gyroscopes, magnetic heading sensors, GNSS sensors, accelerometers and multi-sensor data fusion modules; the guidance system includes mission planning and path planning modules; the control system includes position control and attitude control modules. The navigation system is connected with the guidance system and the control system respectively; the navigation system is connected with the GNSS spoofing attack detection system in two directions; the guidance system is connected with the control system and the GNSS spoofing attack detection system respectively...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com