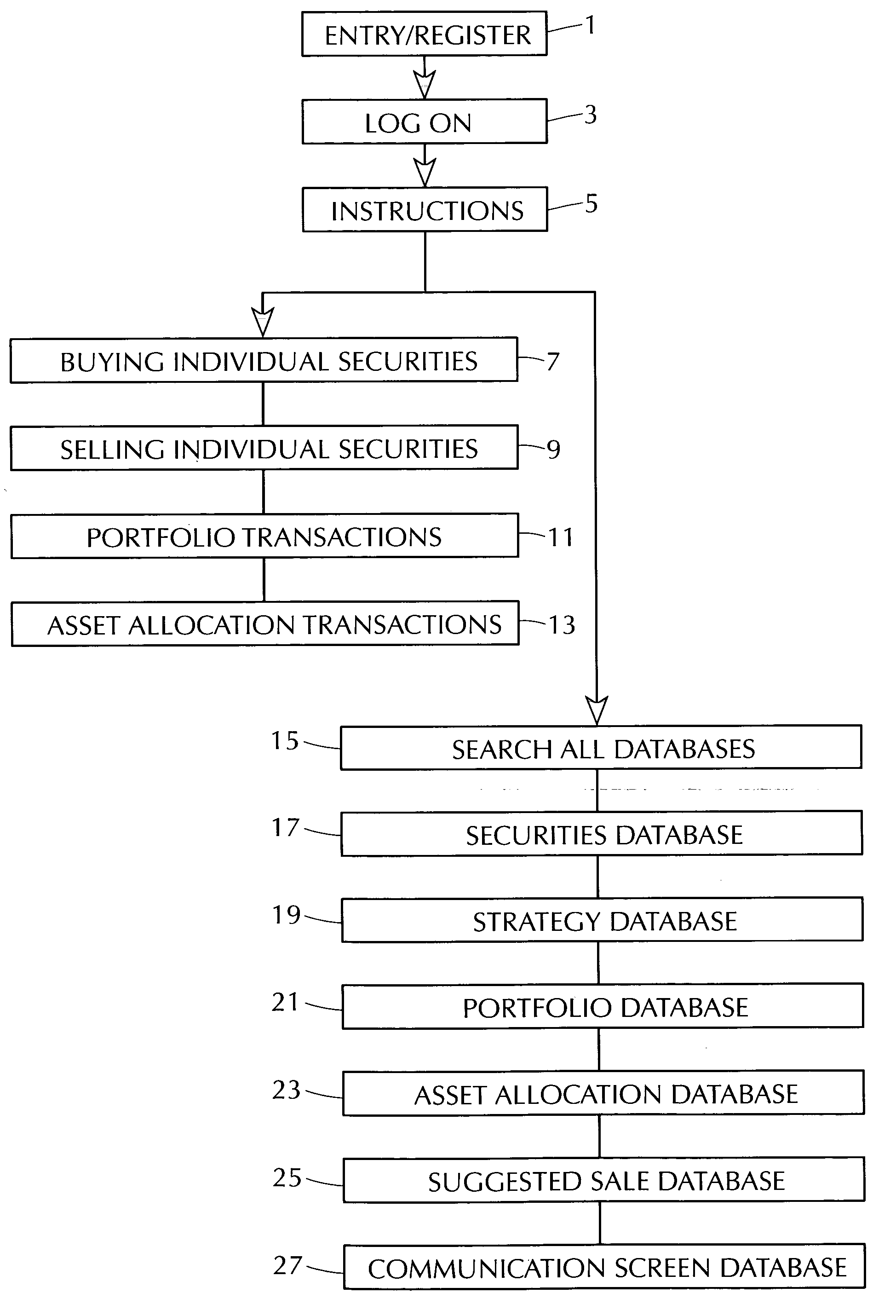
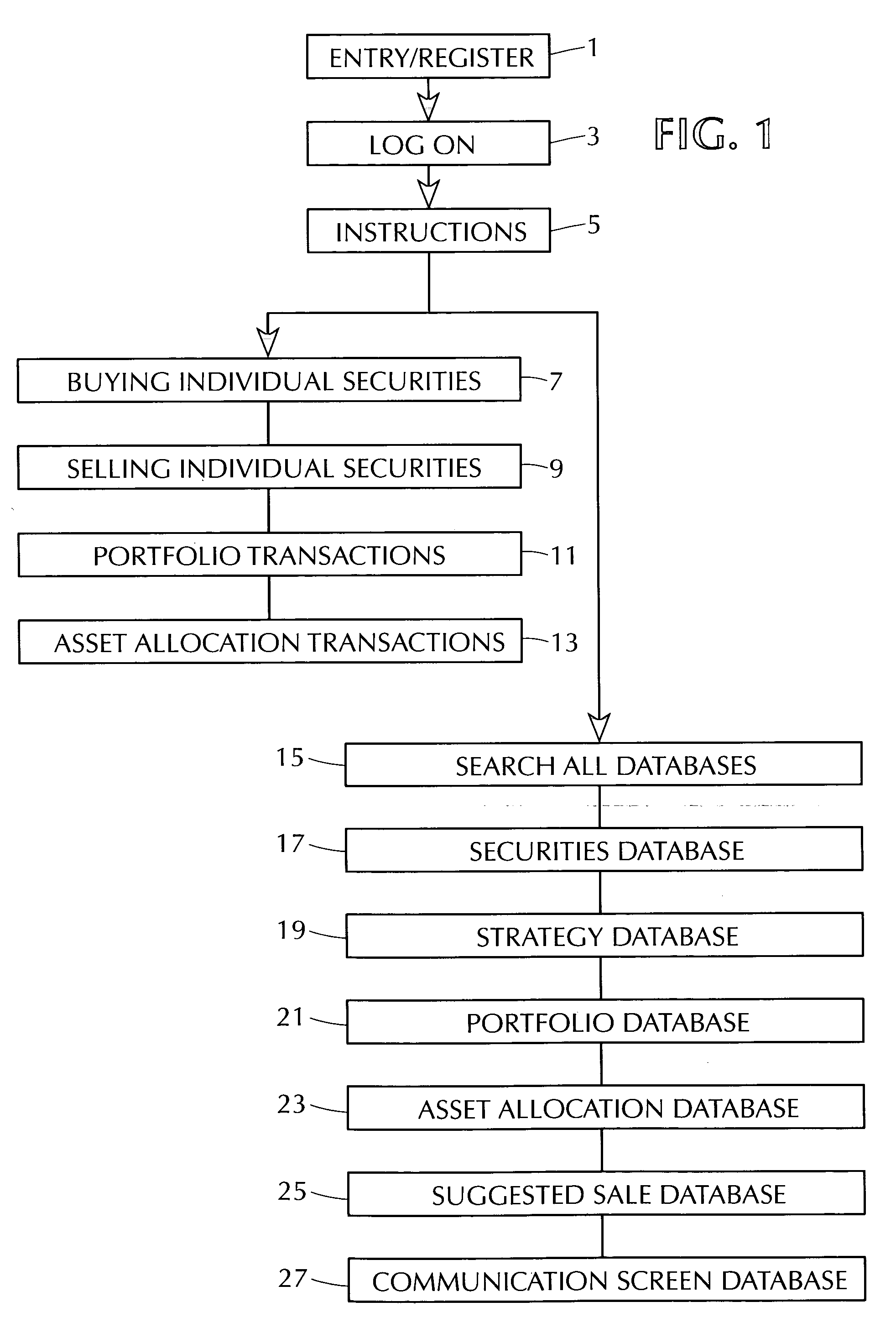
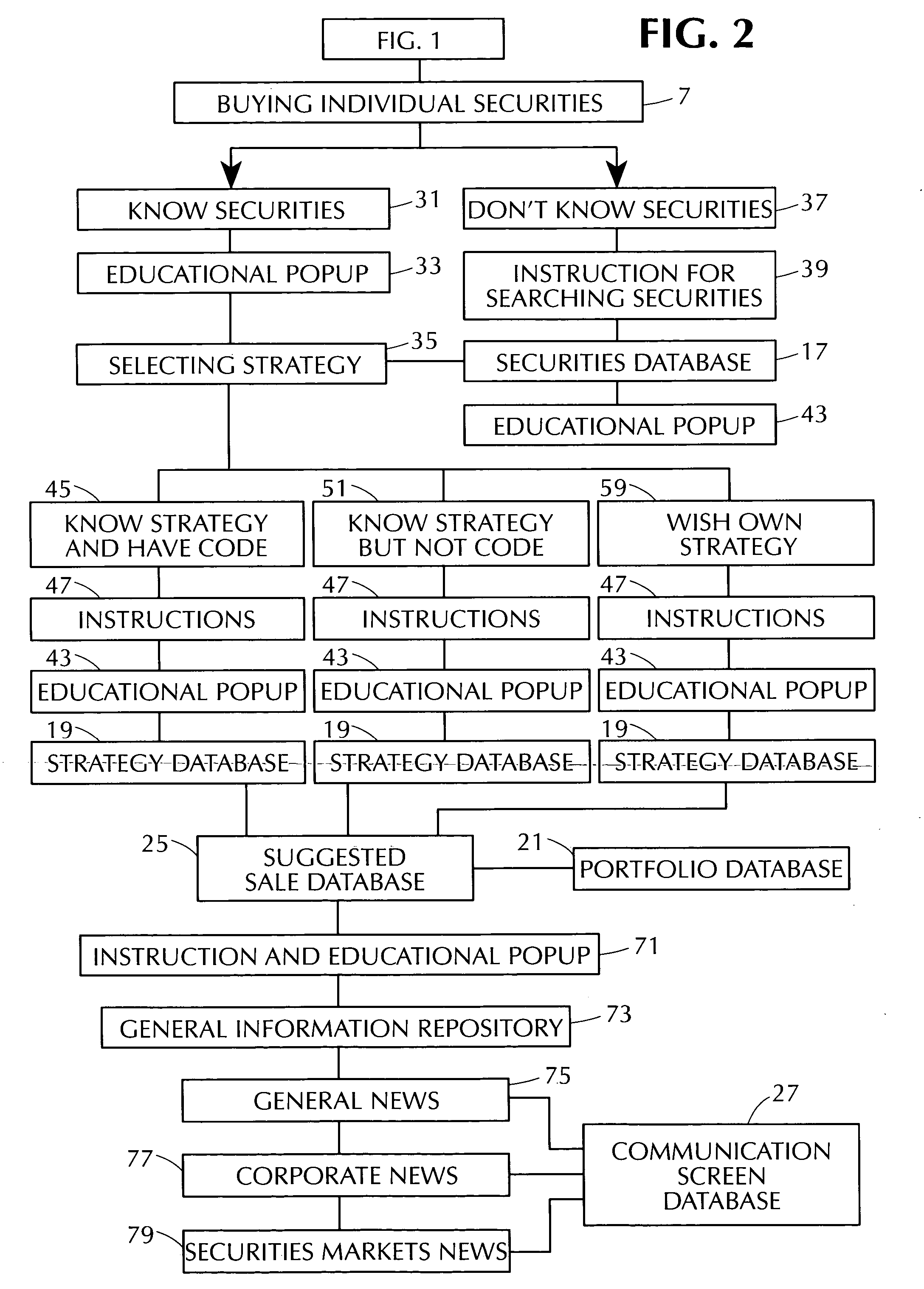
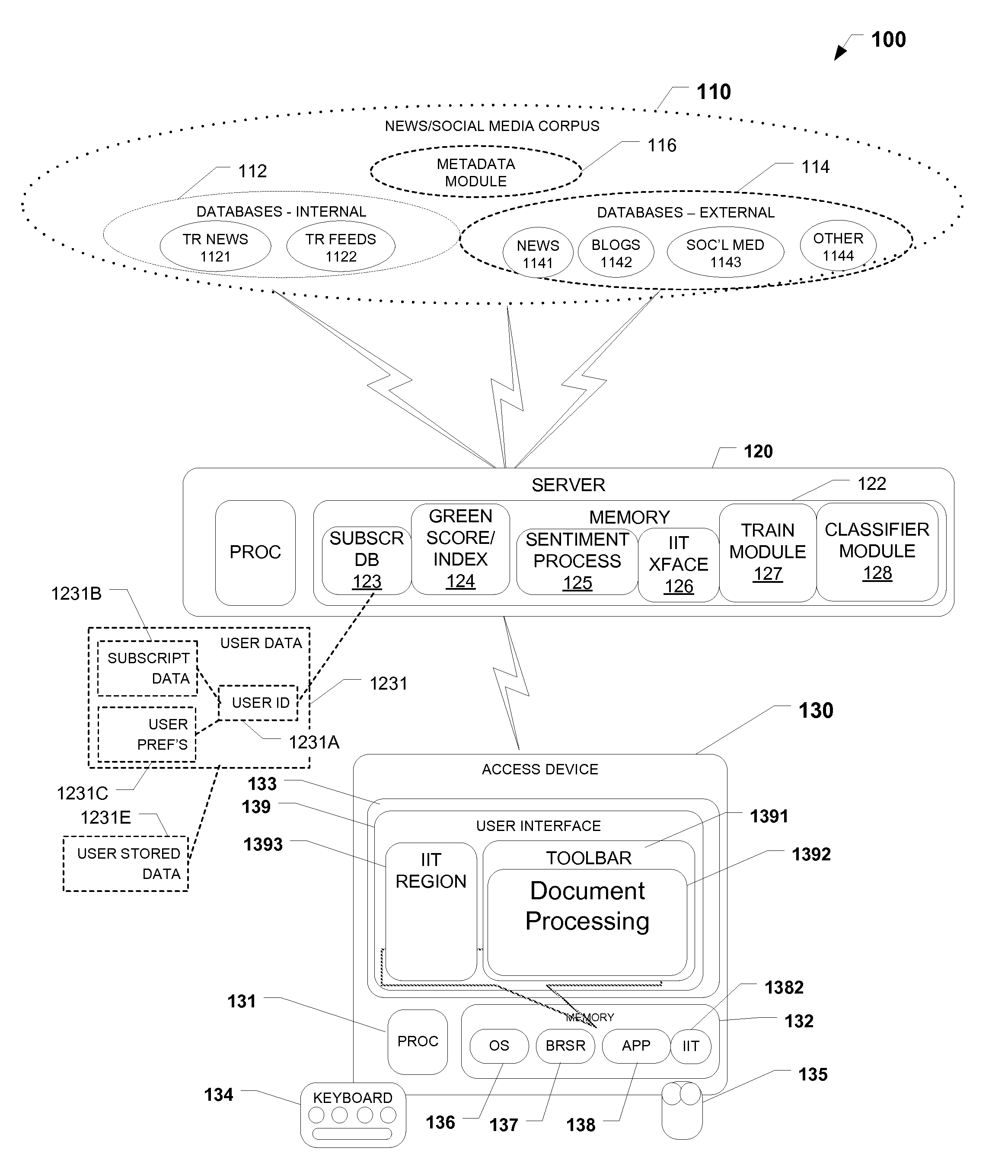
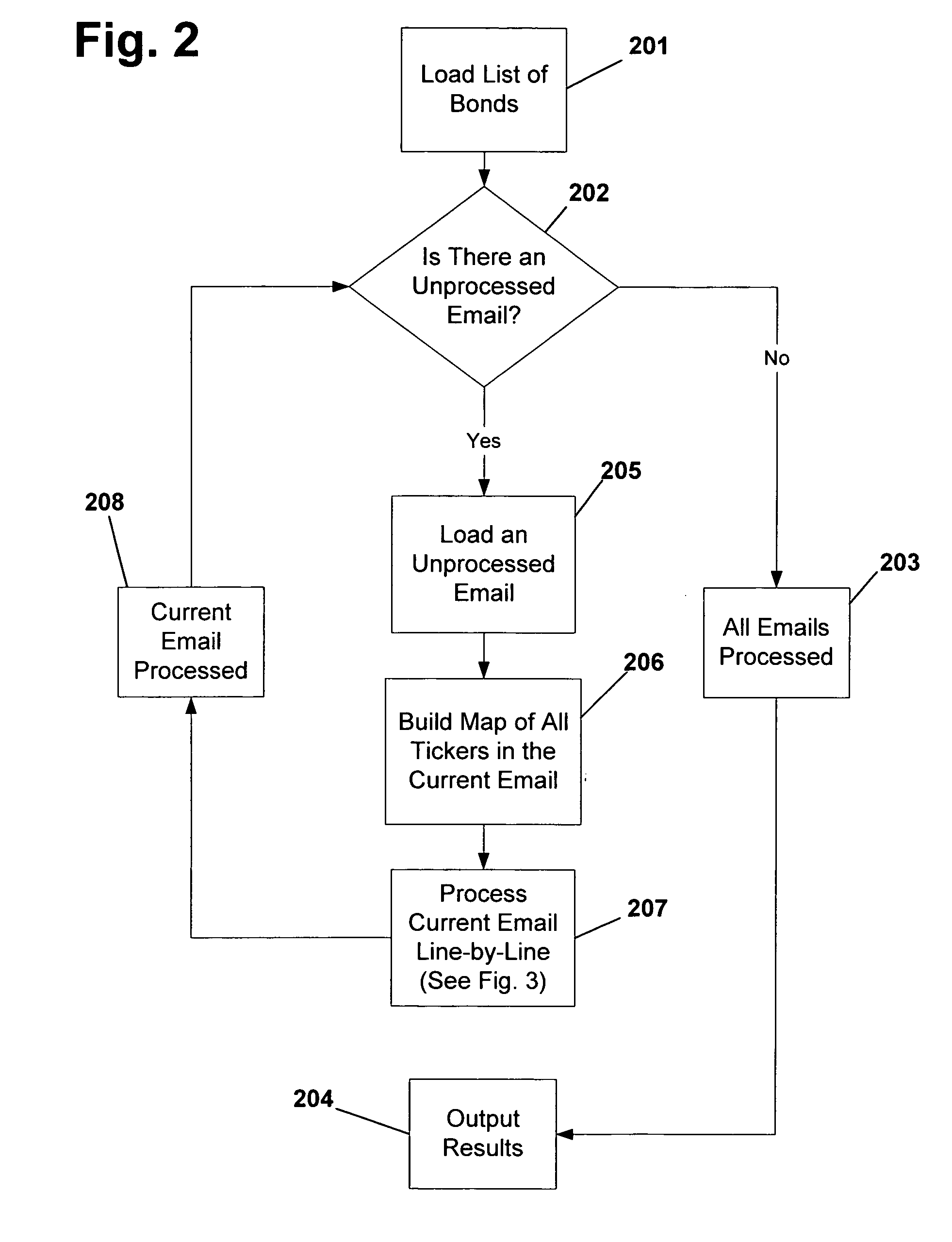
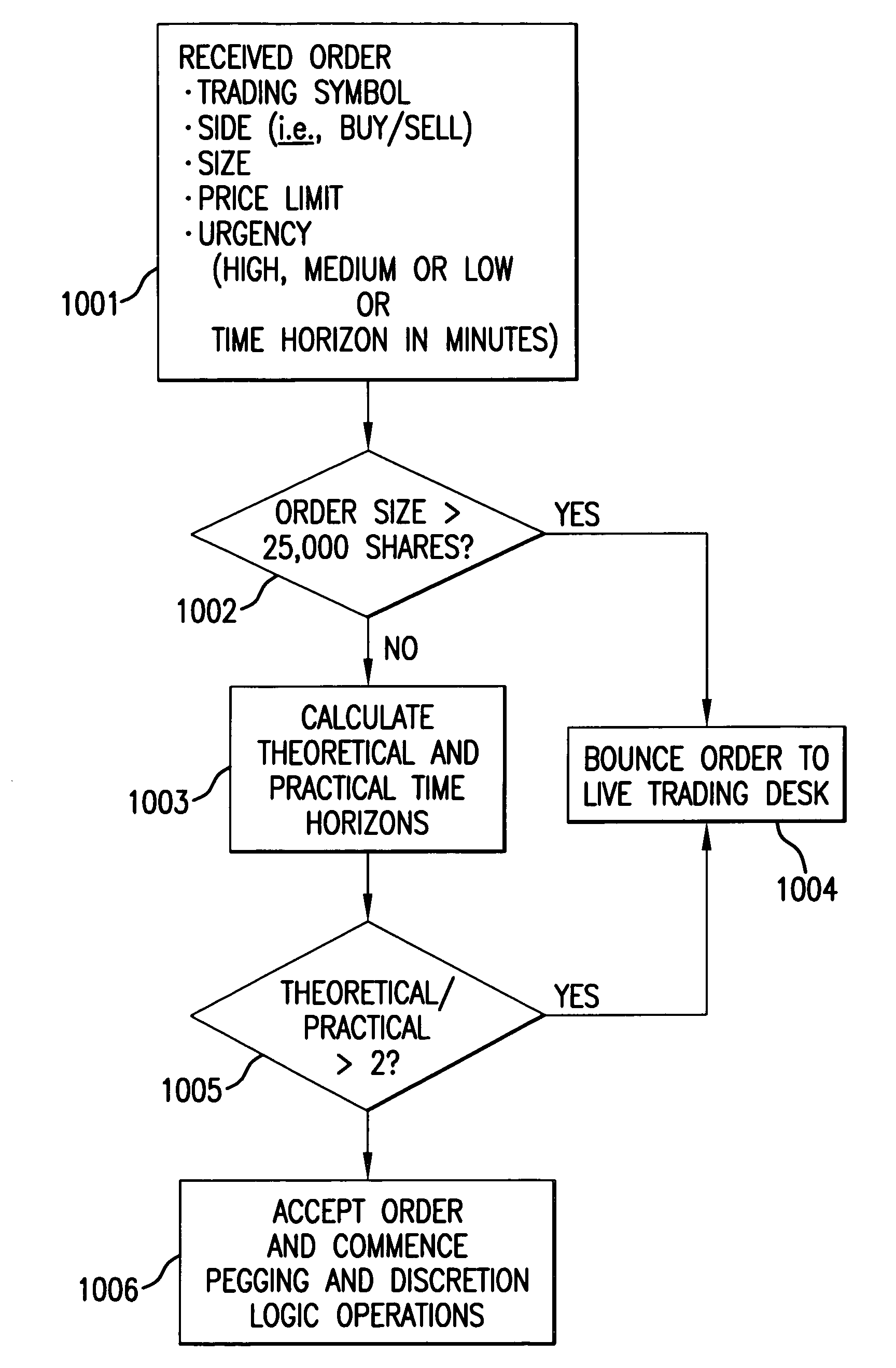
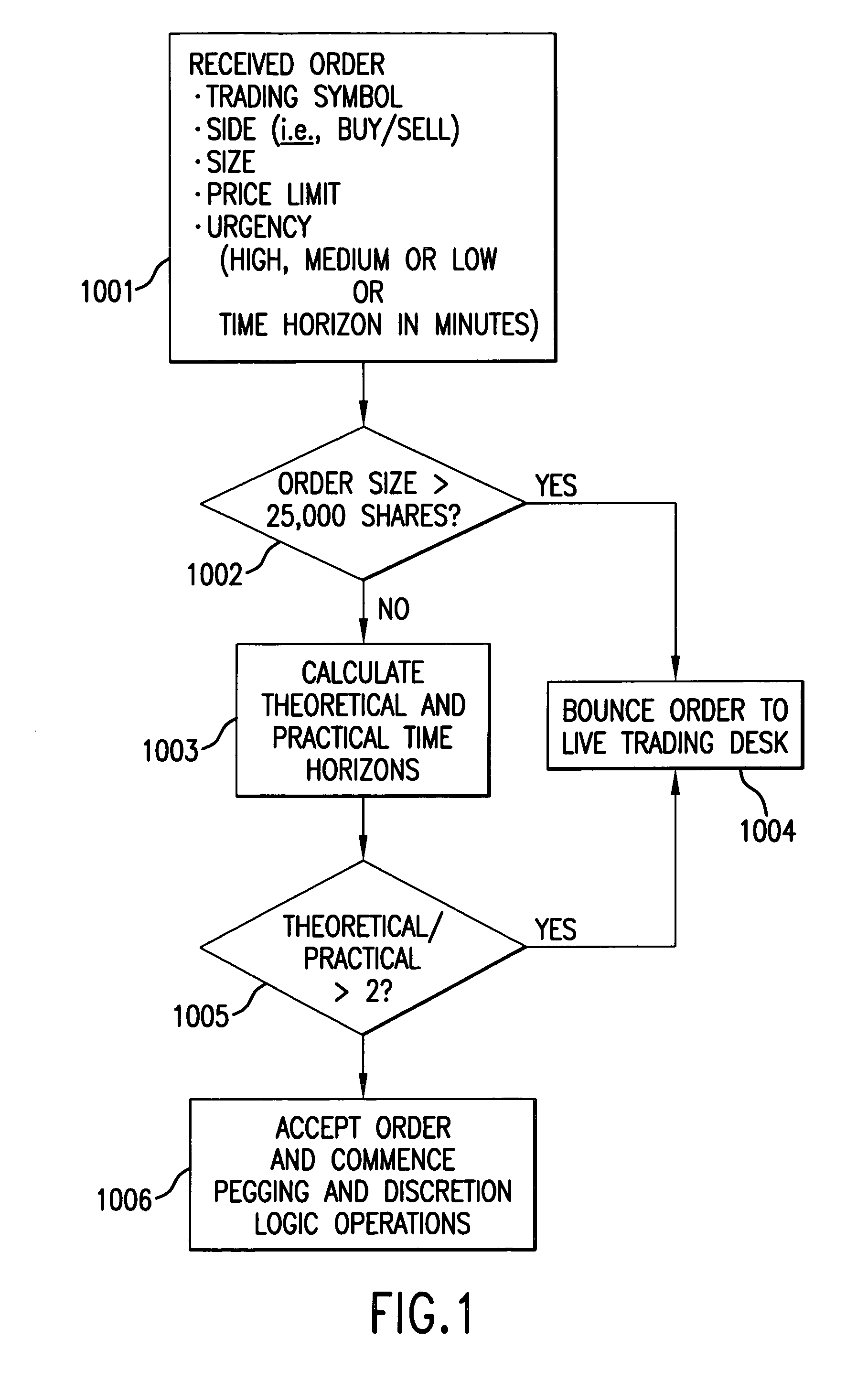
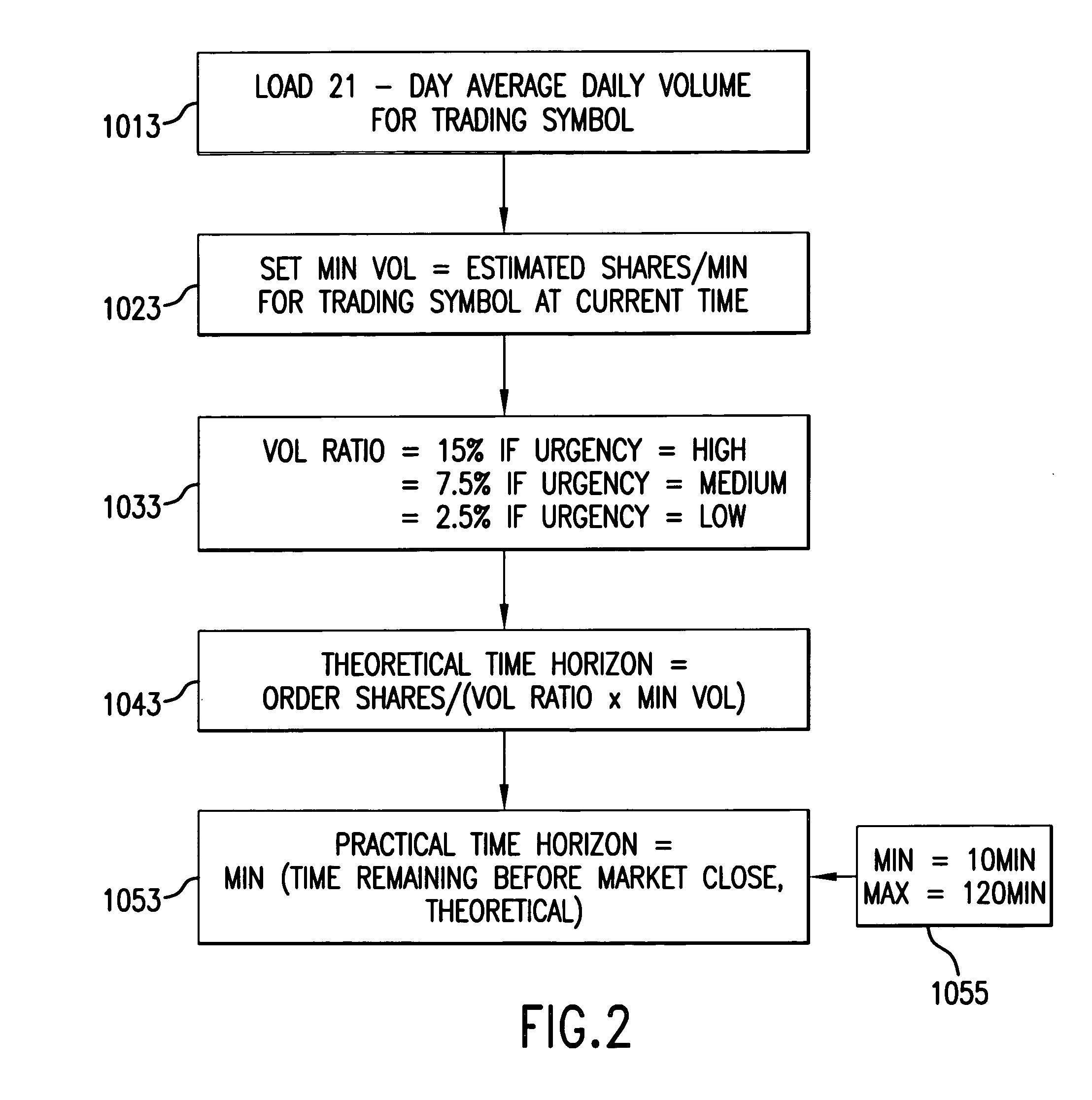
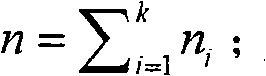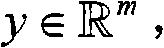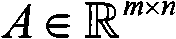Patents
Literature
207 results about "Financial security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Securities aid
A computer-implemented method and system for a systematic trading of financial securities consistent with investment strategies which in turn inherently dictates the time to sell such securities. A method utilizing a computer system for inputting investment portfolio parameters pertaining to a security of interest and interactively utilizing the computer to output investment and performance information, providing the user with general securities trading informational popups and a screening of financial information for securities to be tailored to particular strategies.
Owner:WEINREB EARL J
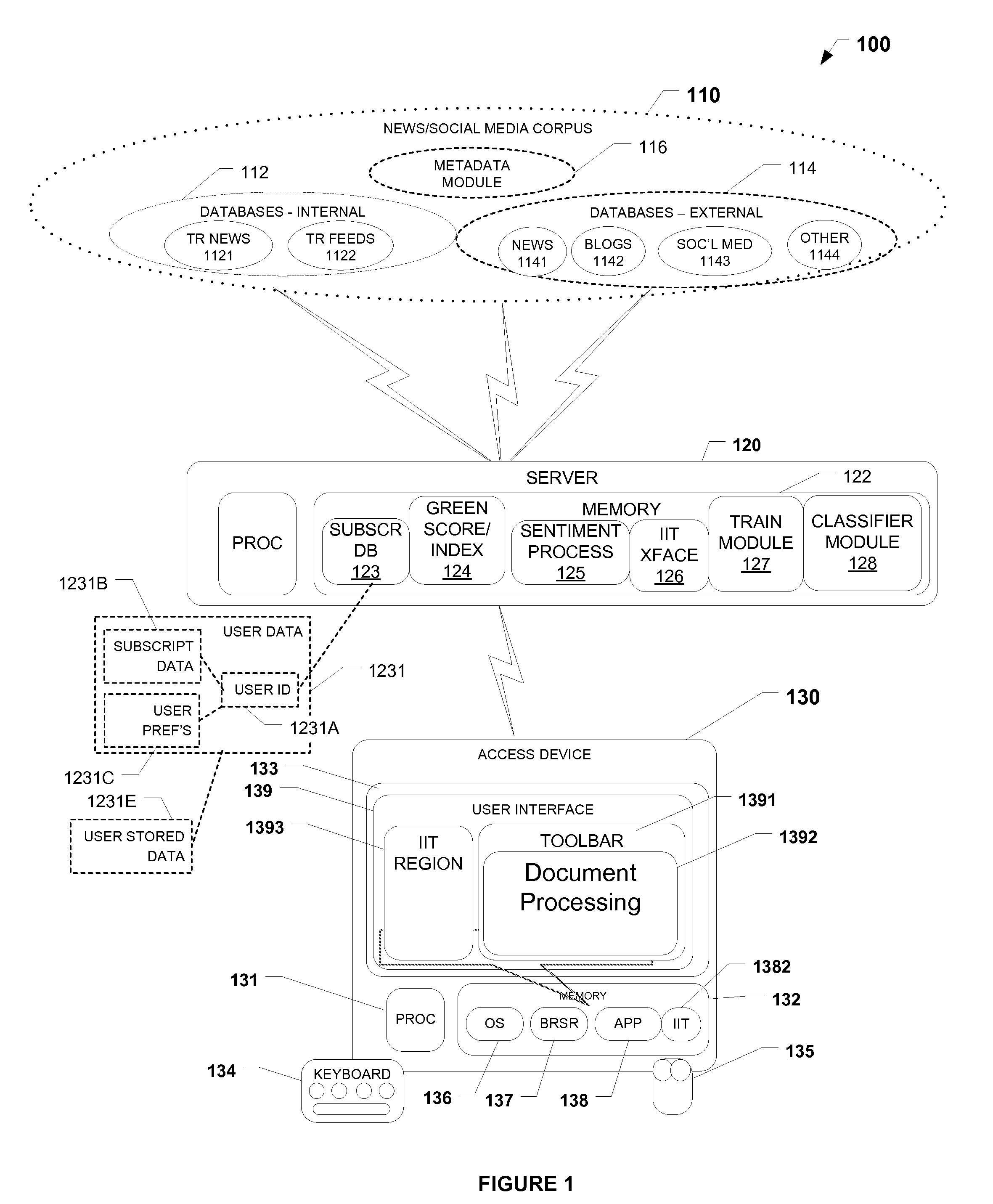
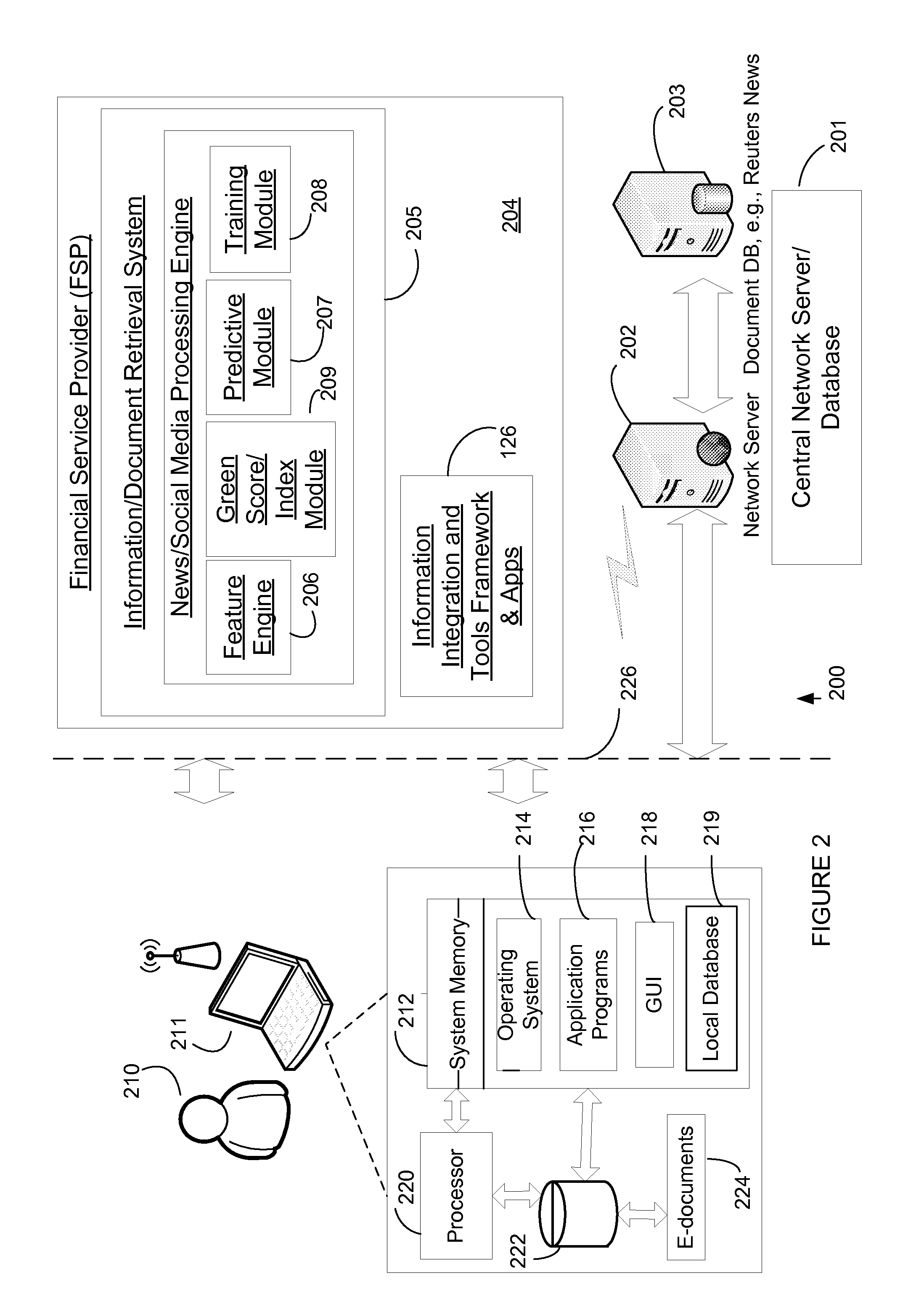
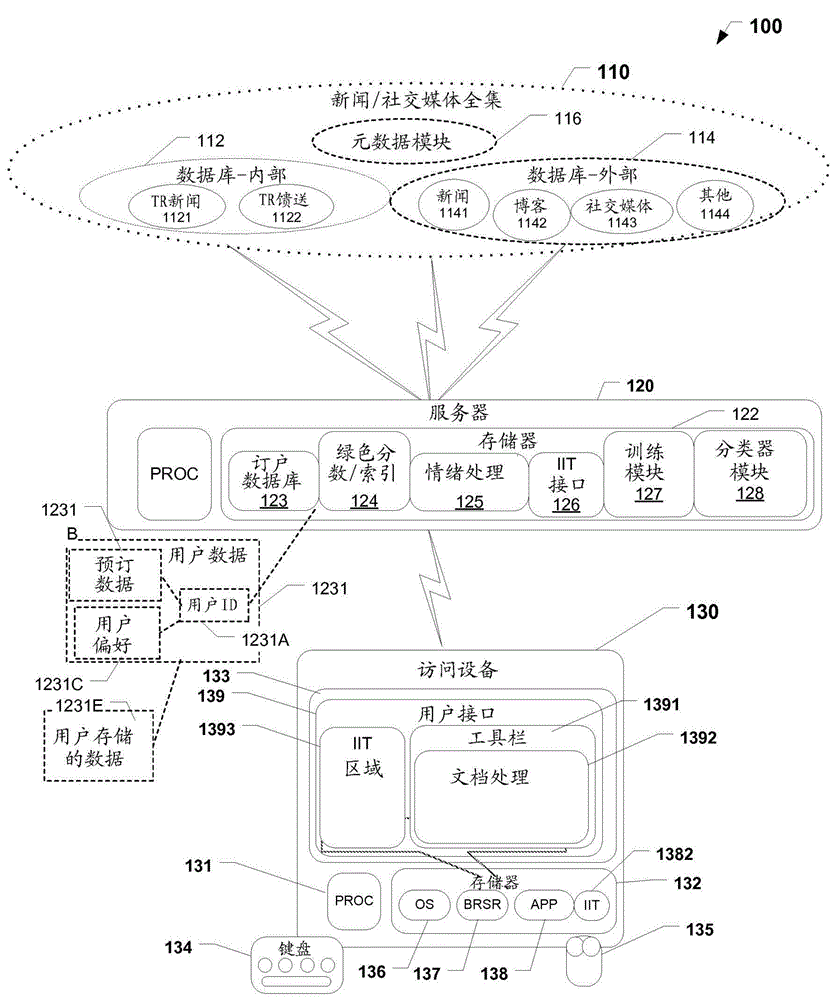
Methods and systems for generating corporate green score using social media sourced data and sentiment analysis
PendingUS20120316916A1Effects of social media are increasingly profoundIncrease contentFinanceMarketingSocial mediaFinancial security
The present invention provides a News / Media Analytics System (NMAS) adapted to automatically process and “read” news stories and content from blogs, twitter, and other social media sources, represented by news / media corpus, in as close to real-time as possible. Quantitative analysis, techniques or mathematics, such as green scoring / composite module and sentiment processing module are processed to arrive at green scores, green certification, and / or model the value of financial securities, including generating a green score, green compliance certification, and a composite environmental or green index. The NMAS automatically processes news stories, filings, new / social media and other content and applies one or more models against the content to determine green scoring and / or anticipate behavior of stock price and other investment vehicles. The NMAS leverages traditional and, especially, social media resources to provide a sentiment-based solution for scoring the “greenness” of companies.
Owner:REFINITIV US ORG LLC
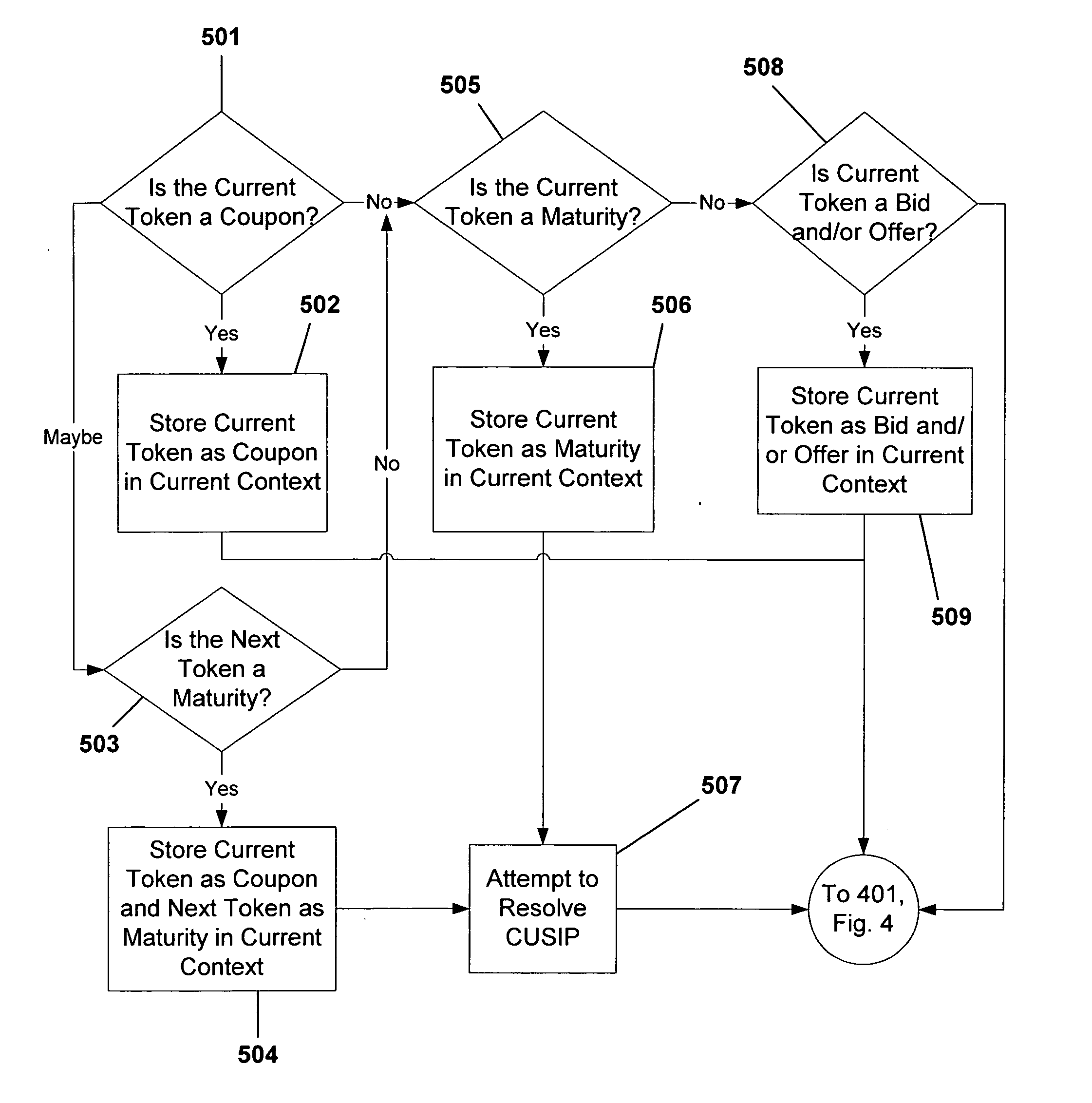
System and method for processing partially unstructured data
ActiveUS20050086170A1More informationFinanceComputer security arrangementsFinancial securityUnstructured data
A system and method for processing partially unstructured data relating to a financial security. The system and method resolve first- and second-identifying data from the partially unstructured data and determine whether a security is defined by the first-identifying data and the second-identifying data. Additionally, the system and method resolve trade information relating to the security identifier from the partially unstructured data. If a security is defined by the resolved identifying data, a security identifier representing the defined security, along with the trade information relating to the defined security, are output.
Owner:JPMORGAN CHASE BANK NA
Dynamic aggressive/passive pegged trading
A computer-implemented system and method for executing trades of financial securities according to a combination passive / aggressive trading strategy that reliably executes trades of lists of securities or blocks of a single security within a desired time frame while taking advantage of dynamic market movement to realize price improvement for the trade within the desired time frame. A passive trading agent executes trades at advantageous prices by floating portions of the order at the bid or ask to maximize exposure to the inside market and attract market orders. An aggressive agent opportunistically takes liquidity as it arises, setting discretionary prices in accordance with historical trading data of the specified security.
Owner:ITG SOFTWARE SOLUTIONS INC
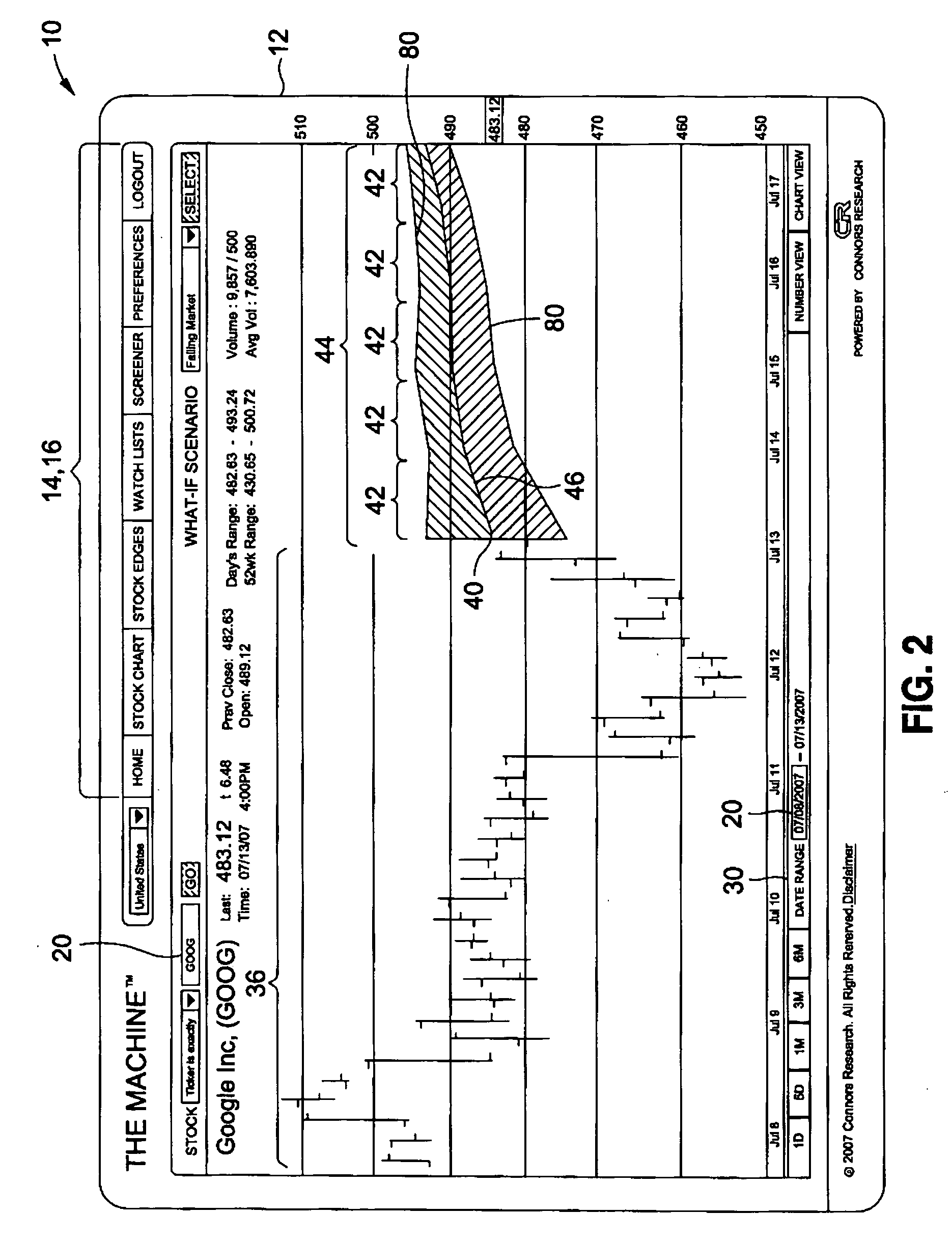
Method of presenting predictive data of financial securities
A method of presenting past, present, and predictive data of a stock comprises the steps of displaying historical data of the stock on a user interface and displaying the current price of the stock on the user interface. The method further includes displaying limit prices of the stock including incrementally greater and lesser values expressed as a percentage of the target price of the stock. The method further includes displaying predictive data for the current price wherein the predictive data includes an edge expressed as an increase or decrease in the current price predicted to occur at the end of a hold period. The predictive data further includes a numerical expression of the probability that the predicted edge will occur at the end of the hold period.
Owner:CONNORS RES +1
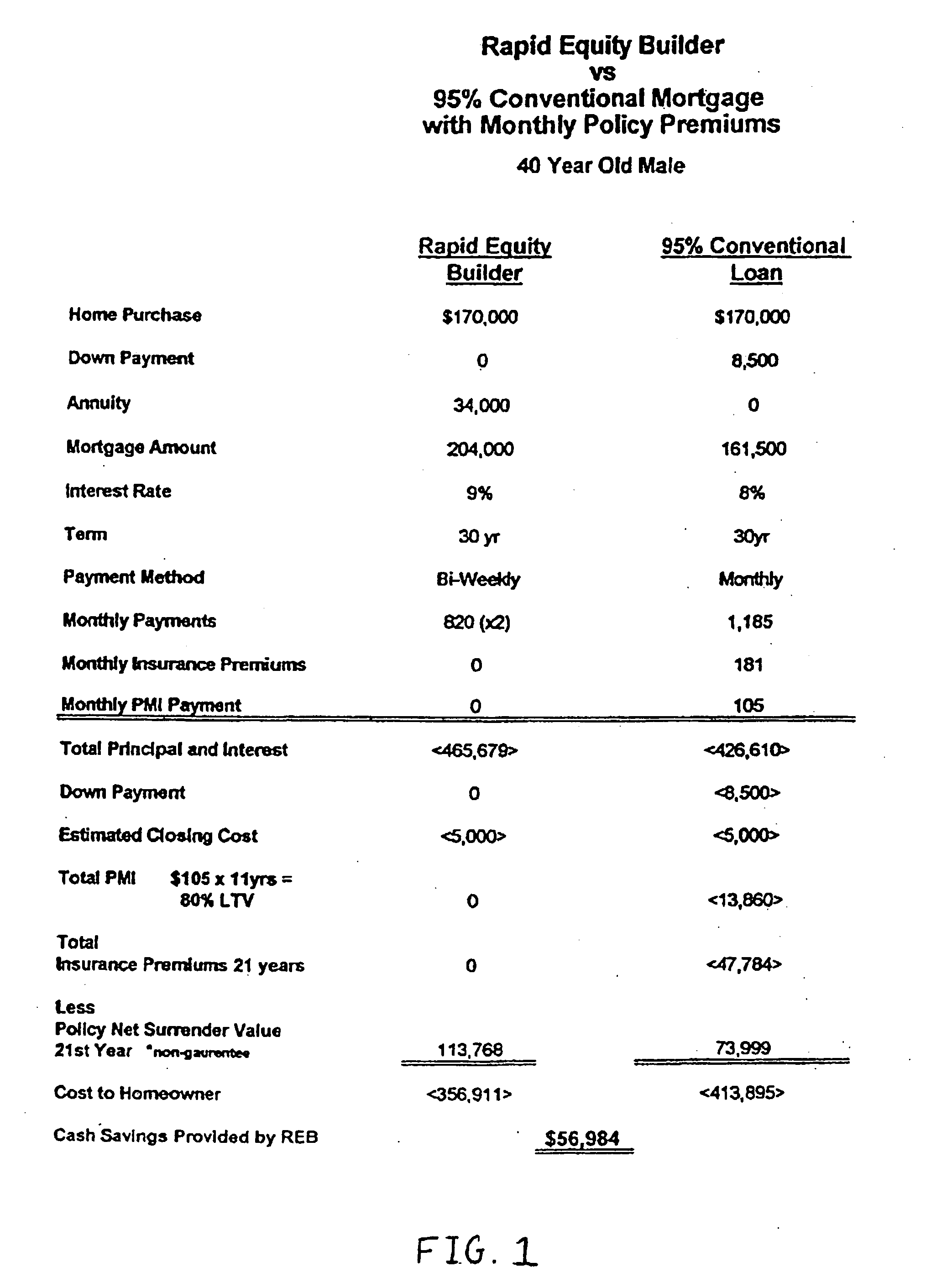
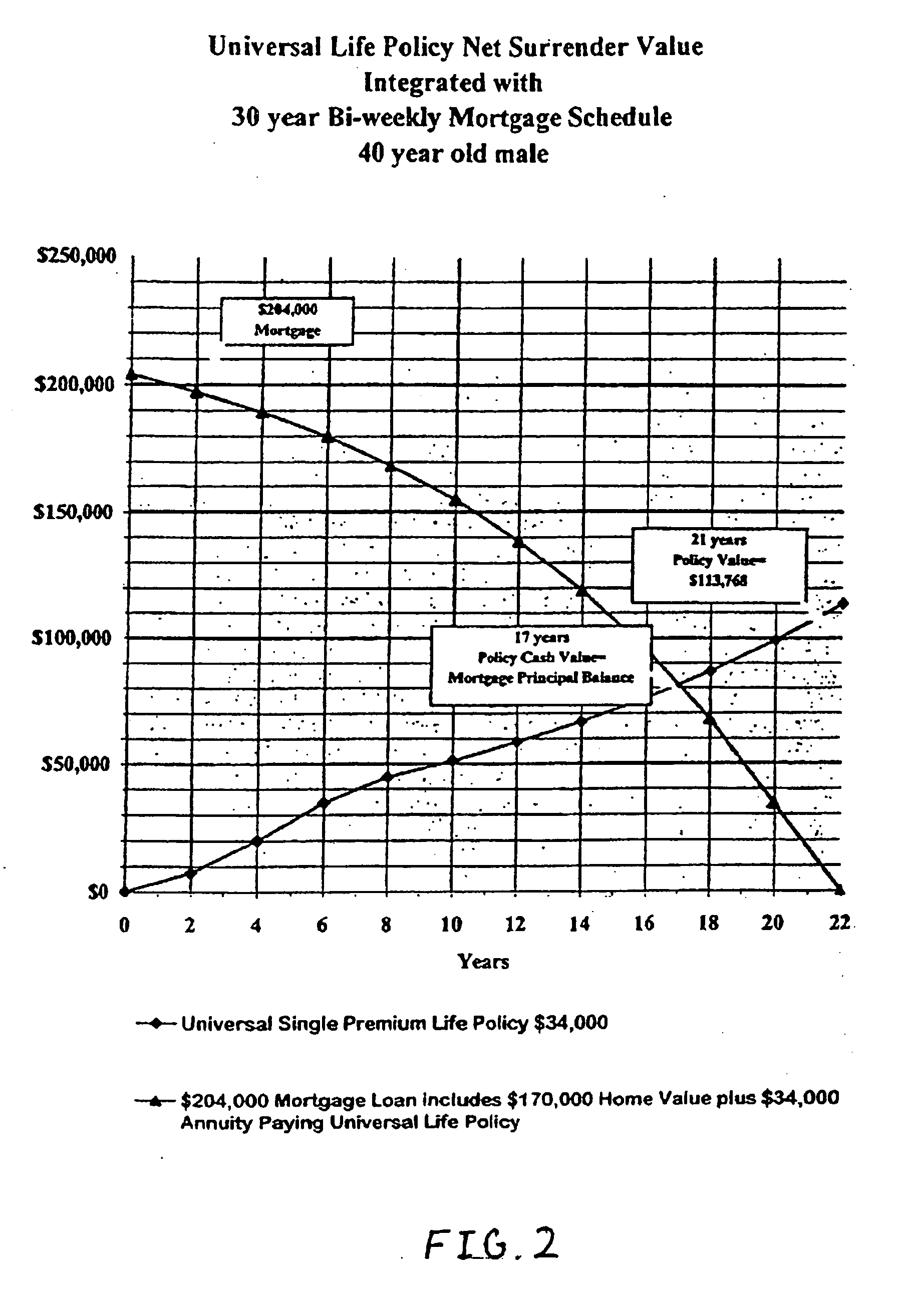
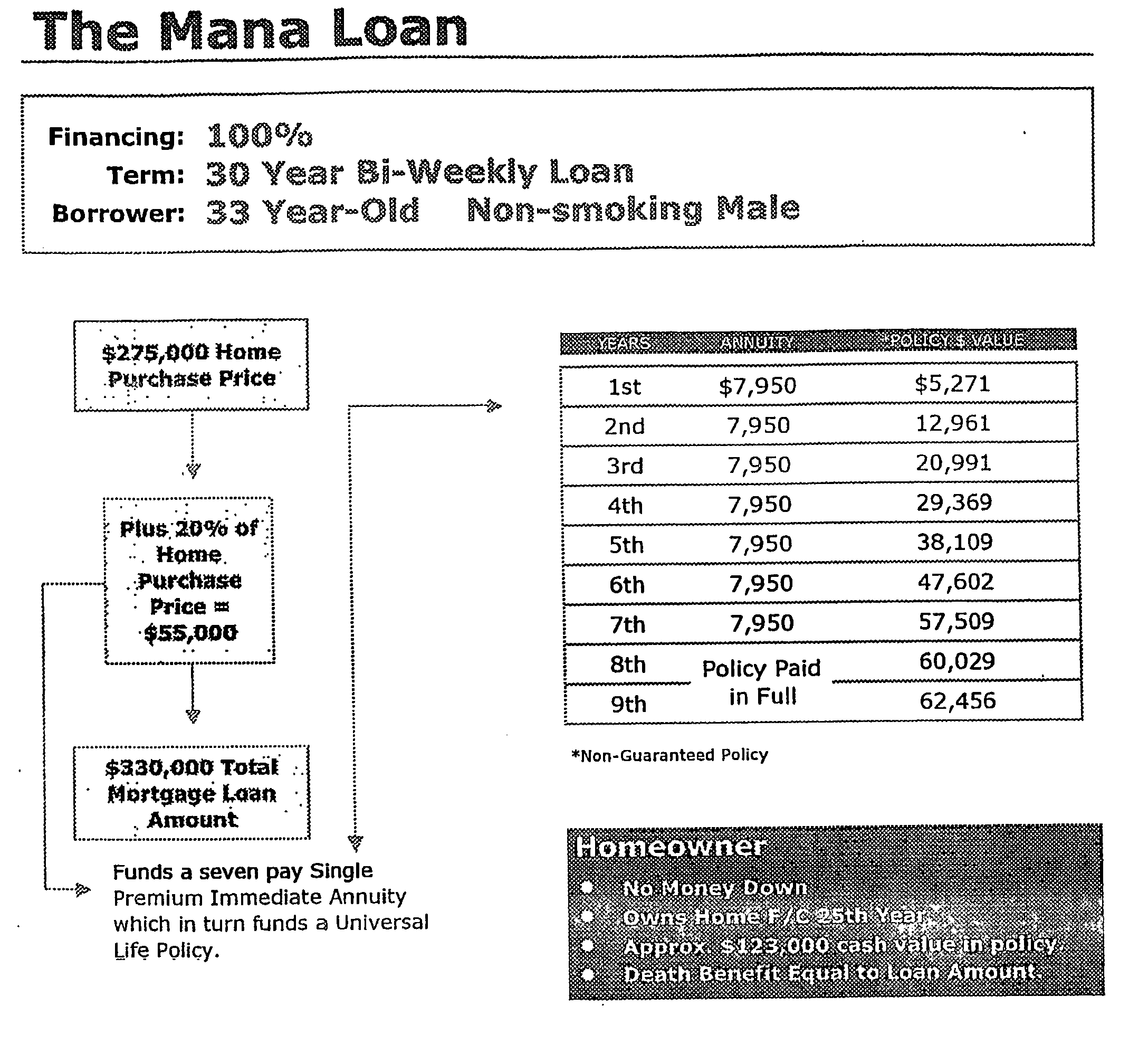
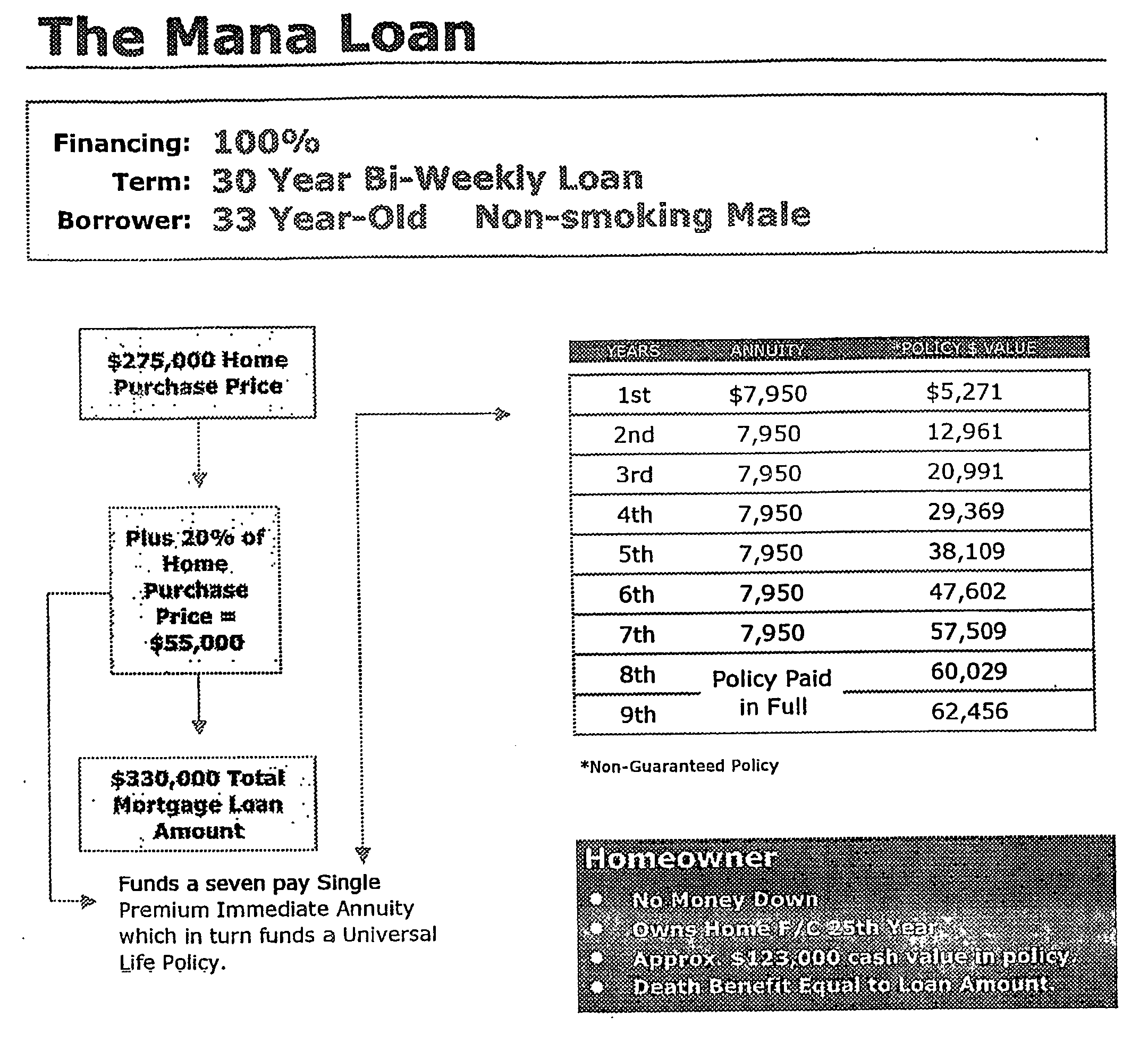
Mortage financing system
InactiveUS20050246267A1Reduce riskCreates financially healthy borrowersFinanceSpecial data processing applicationsPaymentFinancial security
The present invention is a method for providing mortgage financing to a borrower while additionally creating the opportunity for the borrower to invest in their long and short-term financial security. In real estate purchase, a mortgage is extended for greater than the real estate purchase price. The surplus amount is applied against at least one investment vehicle, so that after the periodic payments are completed, the borrower has equity in real estate and an interest in at least one investment vehicle. The investment vehicle provides security for the mortgage.
Owner:NICHOLS EVELYN
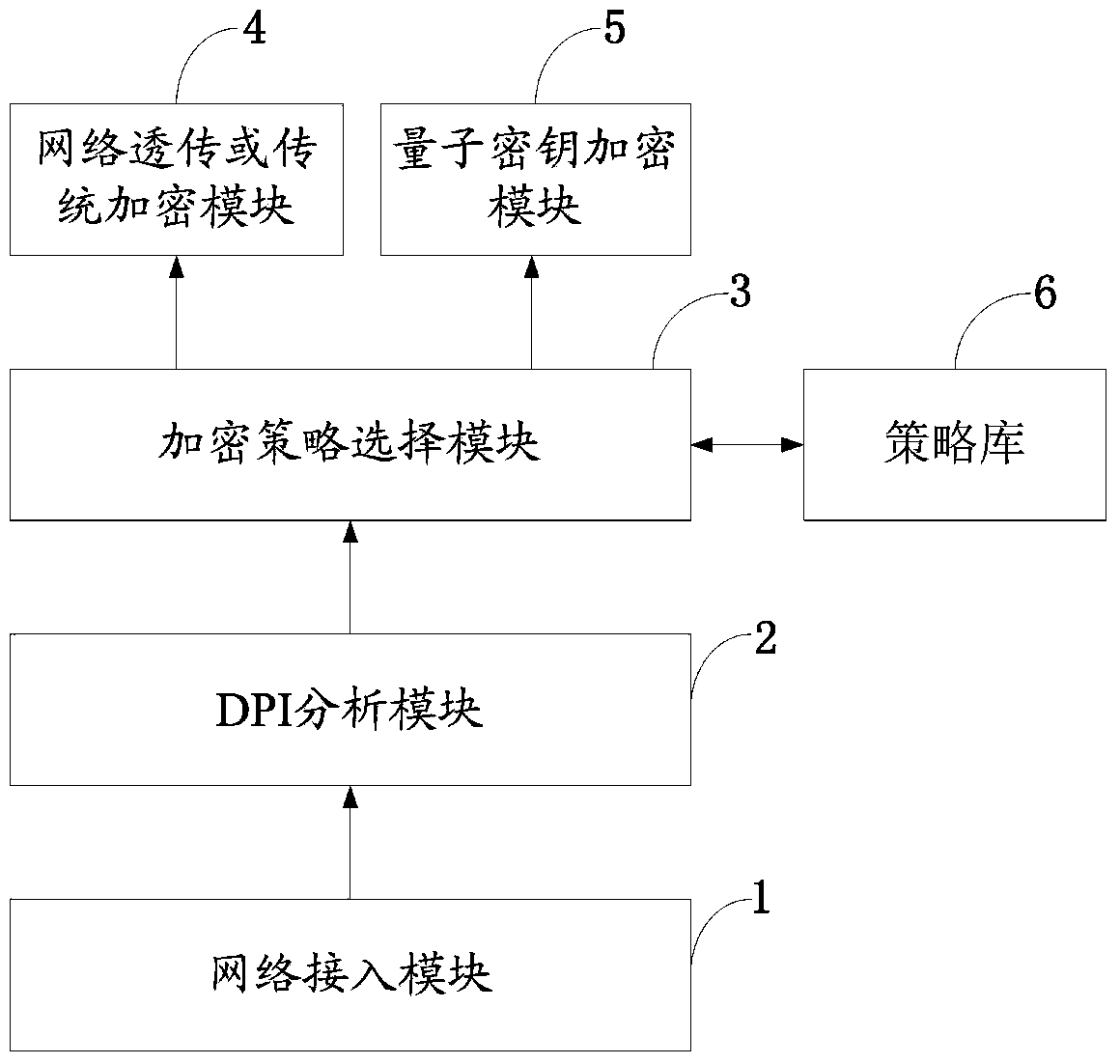
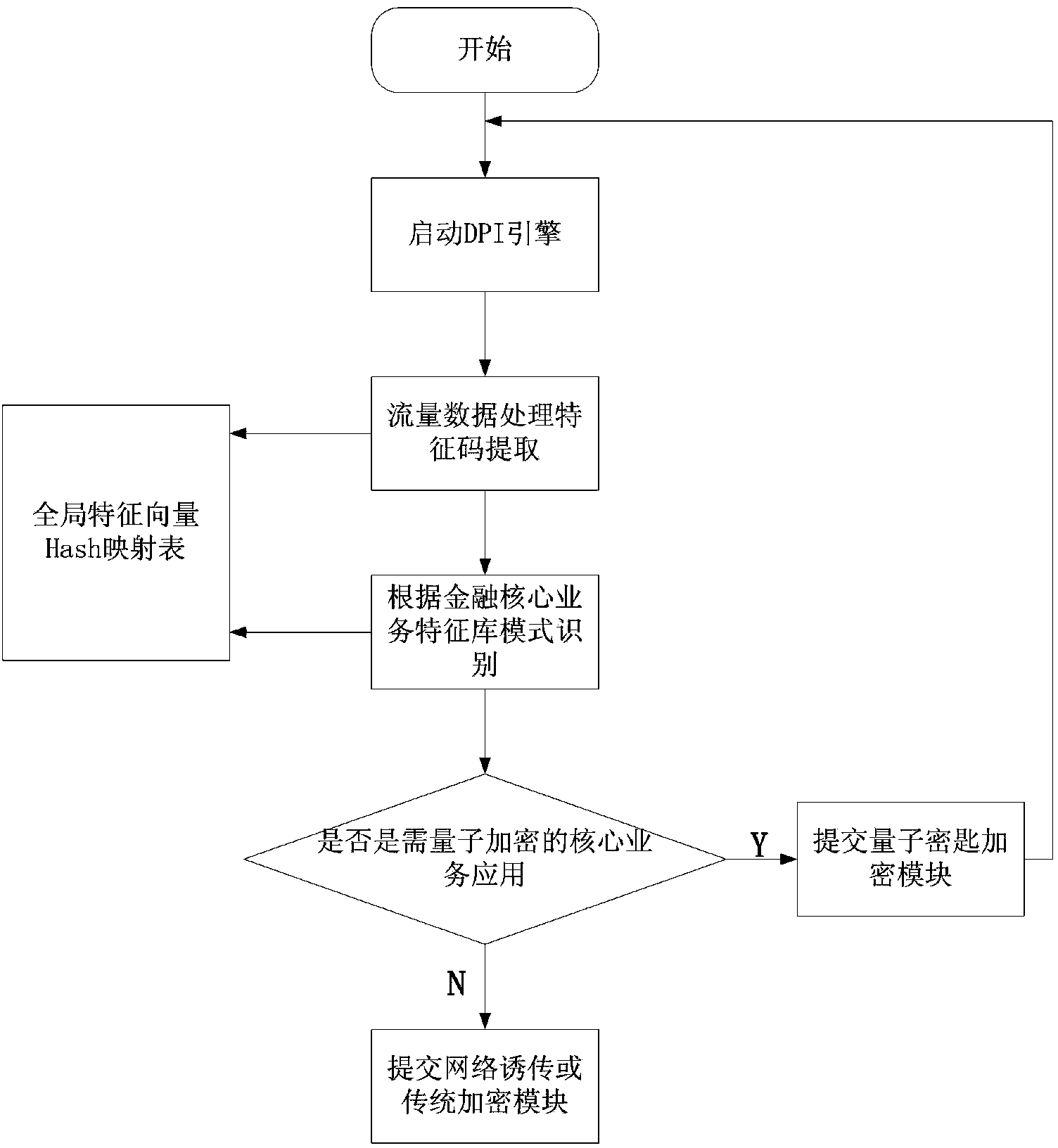
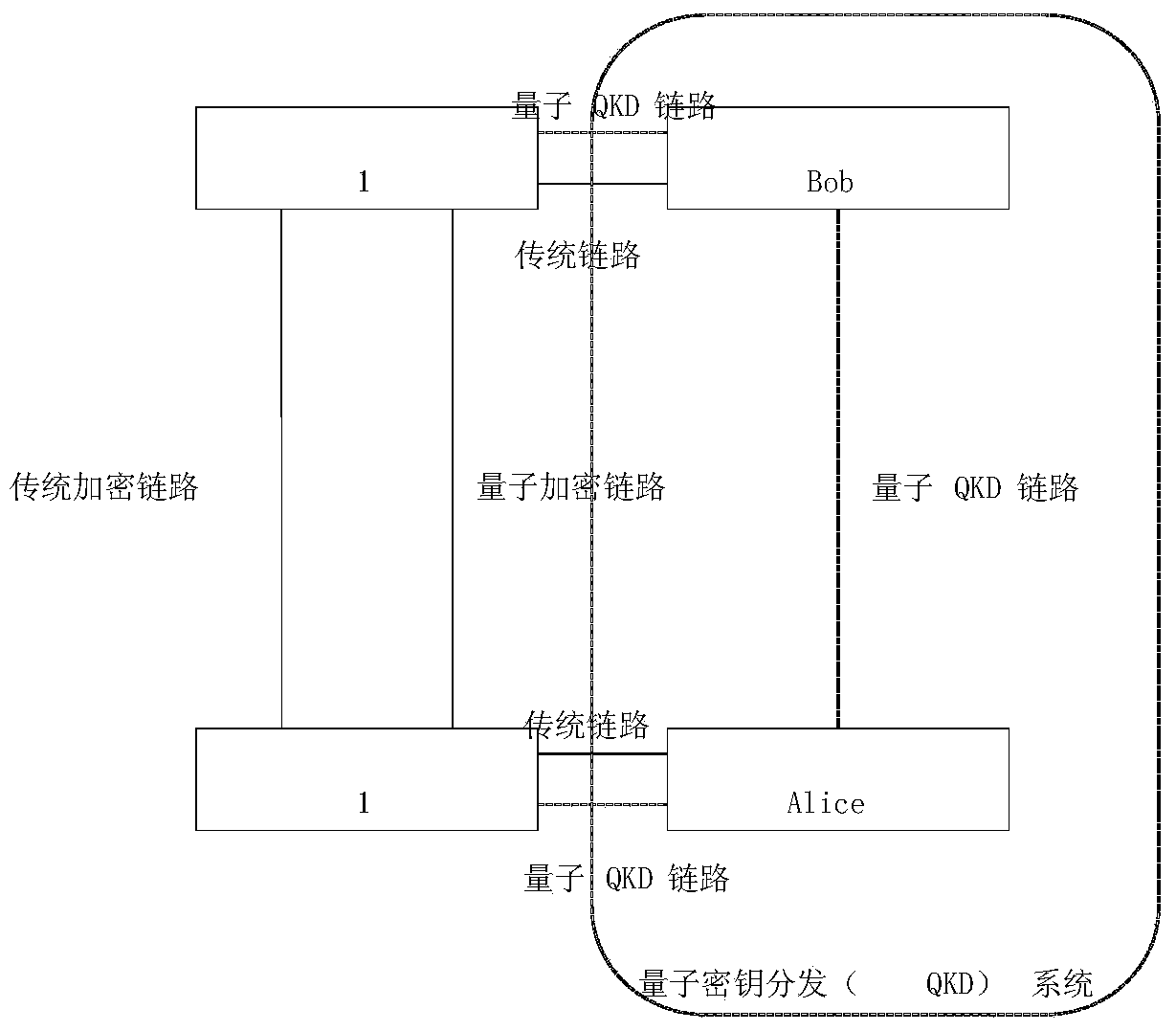
Quantum secret communication gateway system for financial security network
InactiveCN103916239ATaking into account the transmission efficiencyRealization of Quantum Secure CommunicationKey distribution for secure communicationNetwork connectionsService flowData stream
The invention discloses a quantum secret communication gateway system for a financial security network. A DPI analysis module of the system conducts application layer analysis on network data streams so as to recognize service types of various applications and submit the service types to an encryption strategy selection module; the encryption strategy selection module conducts quantum key encryption or traditional key encryption or selection transparent transmission according to the priority on services of different levels on the basis of strategies; a network transparent transmission or traditional key encryption module conducts transparent transmission without encryption or conducts encryption through a traditional encryption algorithm based on algorithm safety; a quantum key encryption module conducts quantum encryption transmission. The quantum secret communication gateway system realizes distinguishing and identifying of core service flow of the financial security network, conducts hierarchical encryption on different types of service flow, selects a key distribution encryption or traditional encryption mode according to encryption strategies, realizes quantum secret communication of the core service flow of the financial security network, and gives consideration to the transmission efficiency of financial network services.
Owner:CHANGCHUN UNIV
Method for managing a financial security
A financial security product and method for managing a financial security, such as a variable annuity, which enables financial service providers to deduct the fees, costs and expenses associated with managing the financial security product. In a preferred embodiment, the method enables financial service providers to provide optional benefits to investors of a financial security without the need for maintaining separate unit prices for each potential combination of optional benefits. The method comprises periodically declaring a dividend with respect to the financial security and deducting at least a portion of the fees associated with managing the financial security from the declared dividend. The amount of the fees can vary depending upon the number of optional benefits, if any, selected to be provided with the financial security by the investor. In a preferred embodiment, any remaining dividend after the fees have been deducted is reinvested into the financial security.In a preferred embodiment, the process for declaring the dividend, assessing and deducting the management fees, reinvesting the remainder of the dividend and determining the new value of the financial security is accomplished using a series of calculations via an automated system such as a computer program.
Owner:SE2
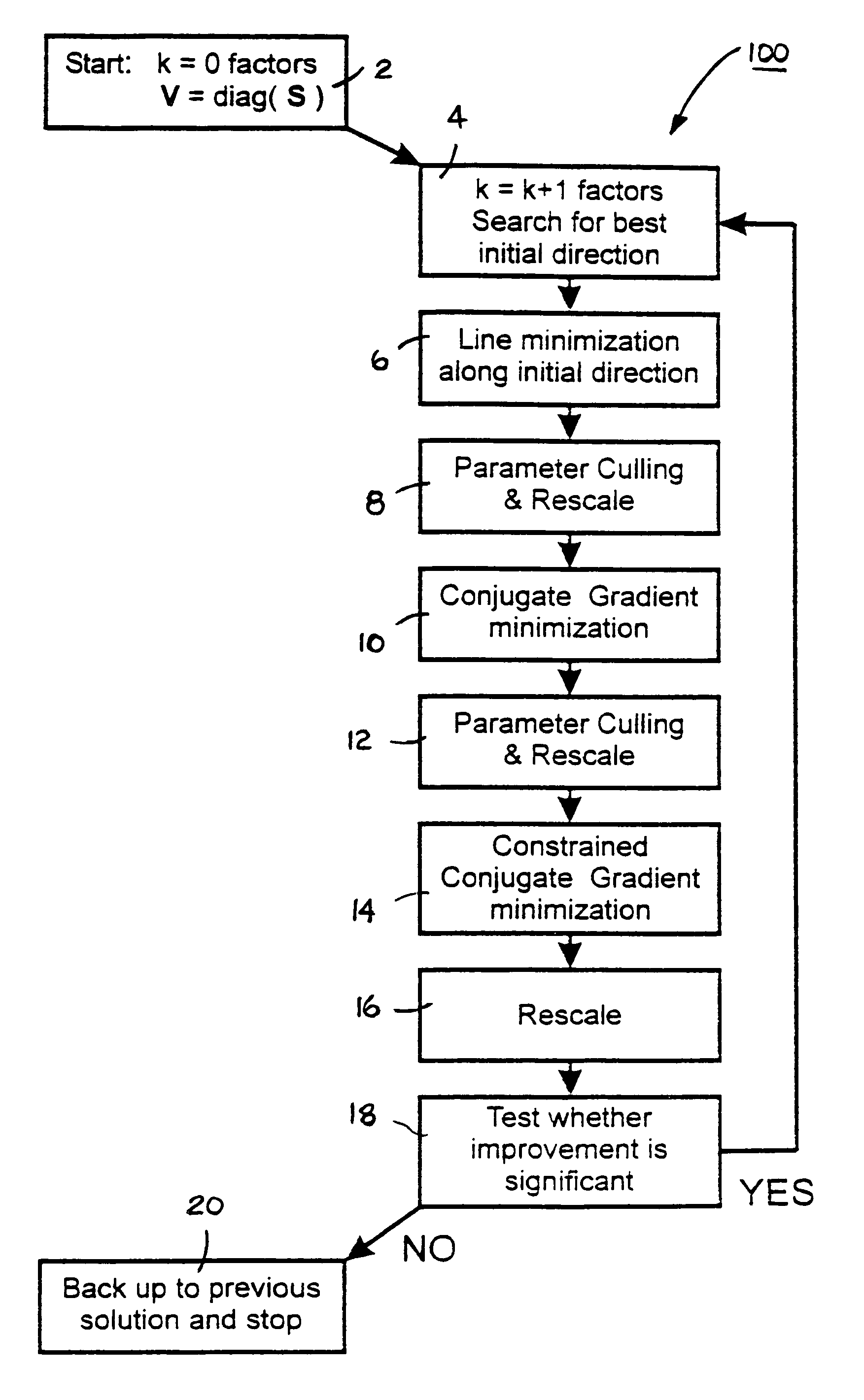
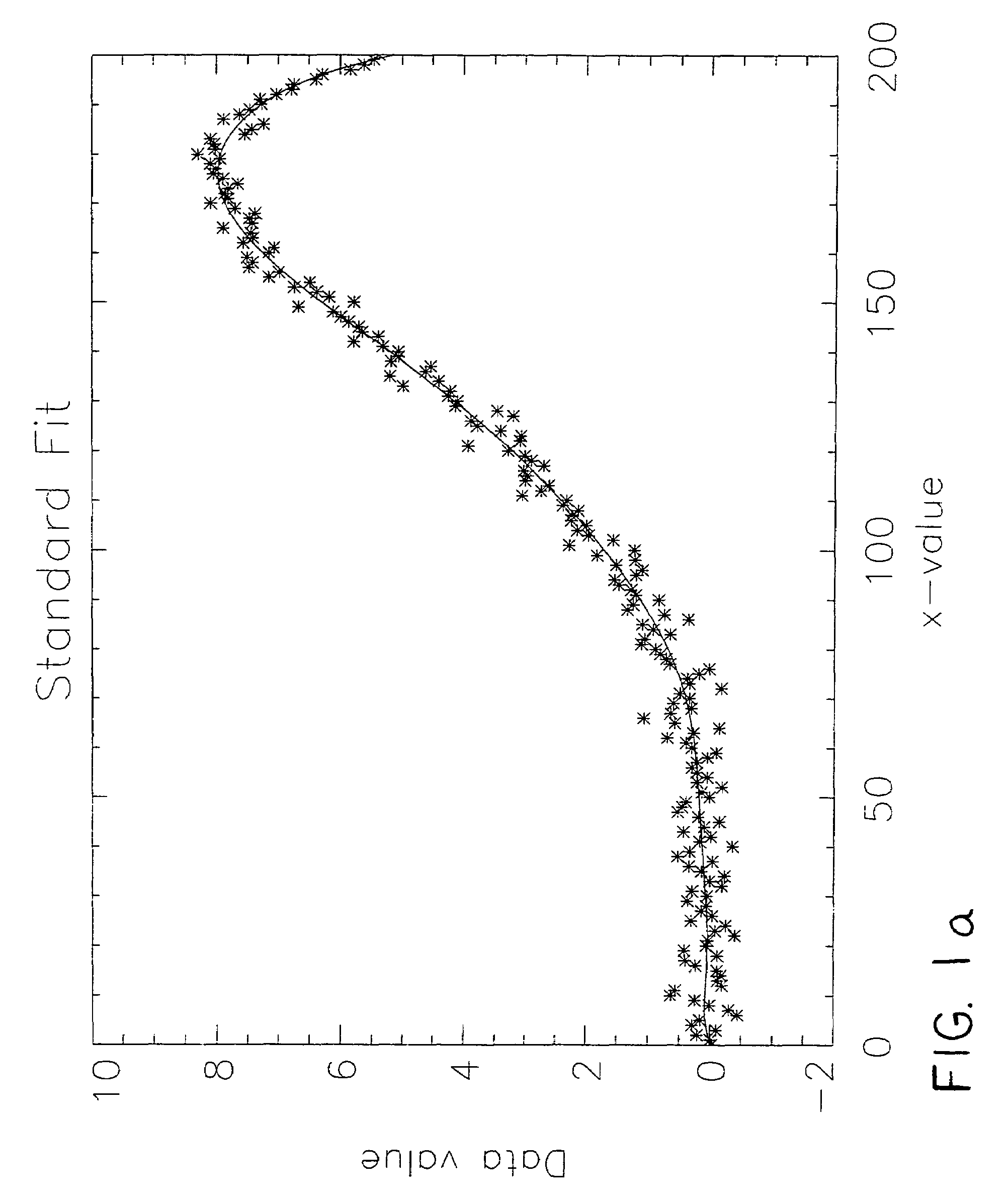
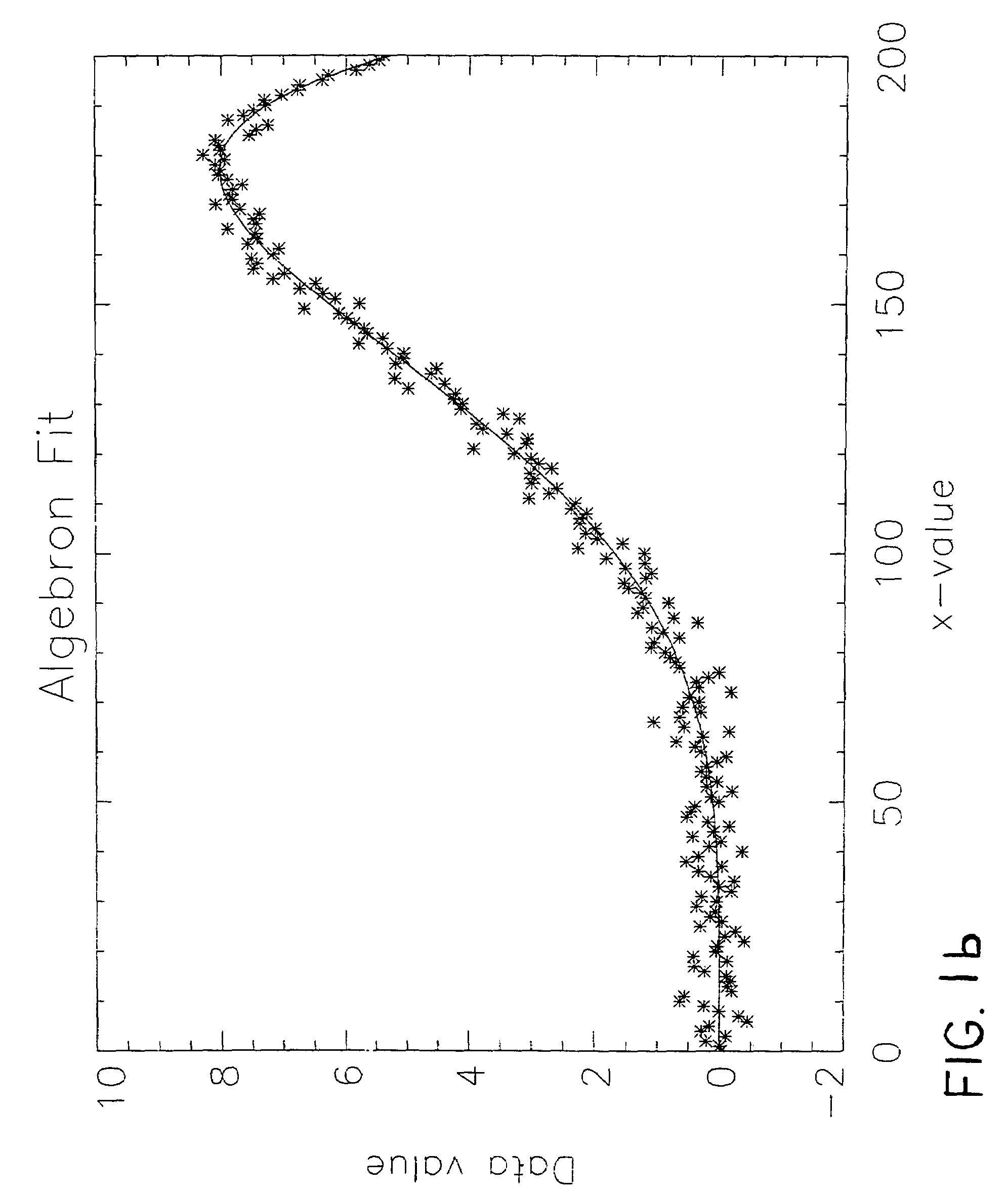
System and method for prediction of behavior in financial systems
InactiveUS7328182B1Minimize complexityAccurate measurementFinanceComplex mathematical operationsRound complexityFinancial security
A computer-based system and method are provided to determine the minimum number of factors required to account for input data by seeking an approximate minimum complexity model. In an exemplary embodiment, covariance in the daily returns of financial securities is estimated by generating a positive-definite estimate of the elements of a covariance matrix consistent with the input data. Complexity of the covariance matrix is minimized by assuming that the number of independent parameters is likely to be much smaller than the number of elements in the covariance matrix. Each variable is described as a linear combination of independent factors and a part that fluctuates independently. The simplest model for the covariance matrix is selected so that it fits the data to within a specified level as determined by the selected goodness-of-fit criterion.
Owner:PIXON
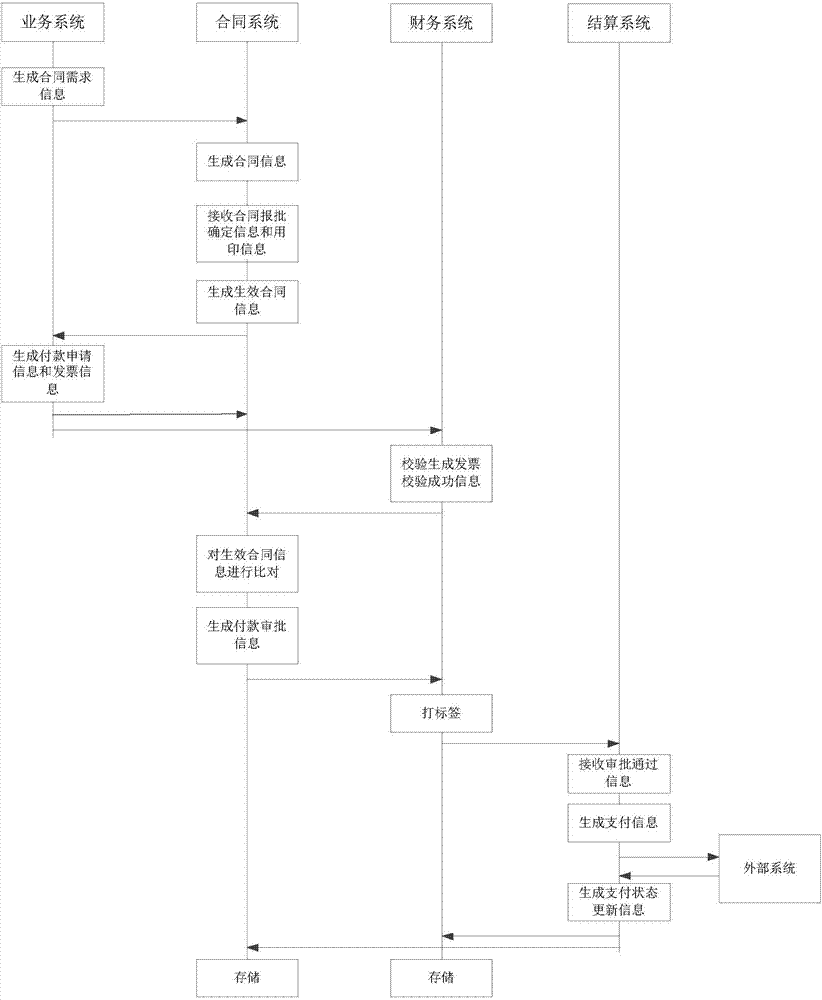
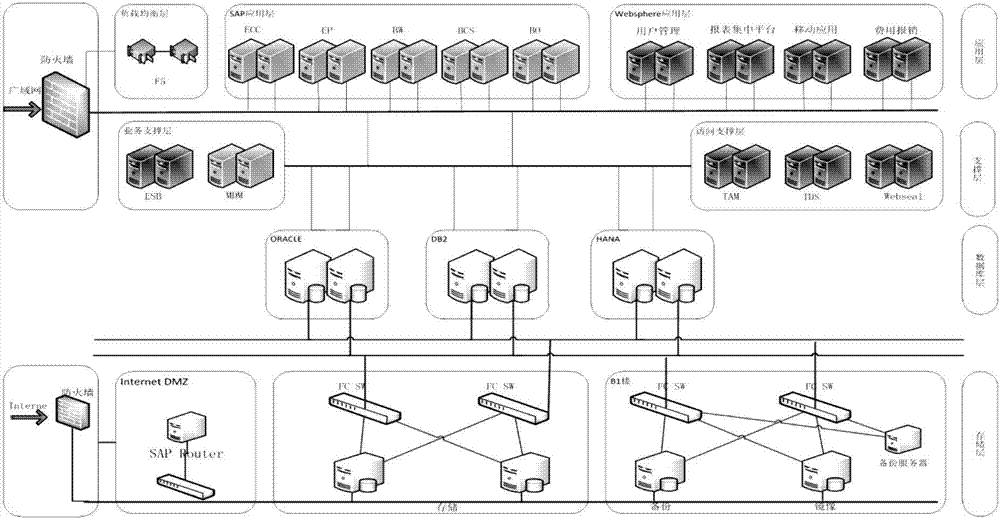
Business-finance-integrated heterogeneous ERP system
PendingCN107067233AOptimize and determine the entire business process of operation and managementReduce business riskFinancePayment protocolsPaymentBusiness enterprise
The invention relates to a business-finance-integrated heterogeneous ERP system. The business-finance-integrated heterogeneous ERP system comprises a storage layer system, a database layer system connected to the storage layer system, a support layer system connected to the database layer system, and an application layer system connected to the database layer system and the support layer system; the support layer system comprises an enterprise service bus system and a master data management system; and the application layer system comprises a business system, a contract system, a finance system and a settlement system. The business-finance-integrated heterogeneous ERP system realizes integration of heterogeneous ERP platform data and flow configuration and has good flexibility and stability. The business-finance-integrated heterogeneous ERP system firstly brings forward and establishes a form of taking a contract whole life cycle as a main line, realizes business and finance safe payment integrated management mode of diversified enterprises or groups, optimizes and determines a whole business flow of enterprise operation management and reduces operational risks of enterprises.
Owner:中国华电集团有限公司 +1
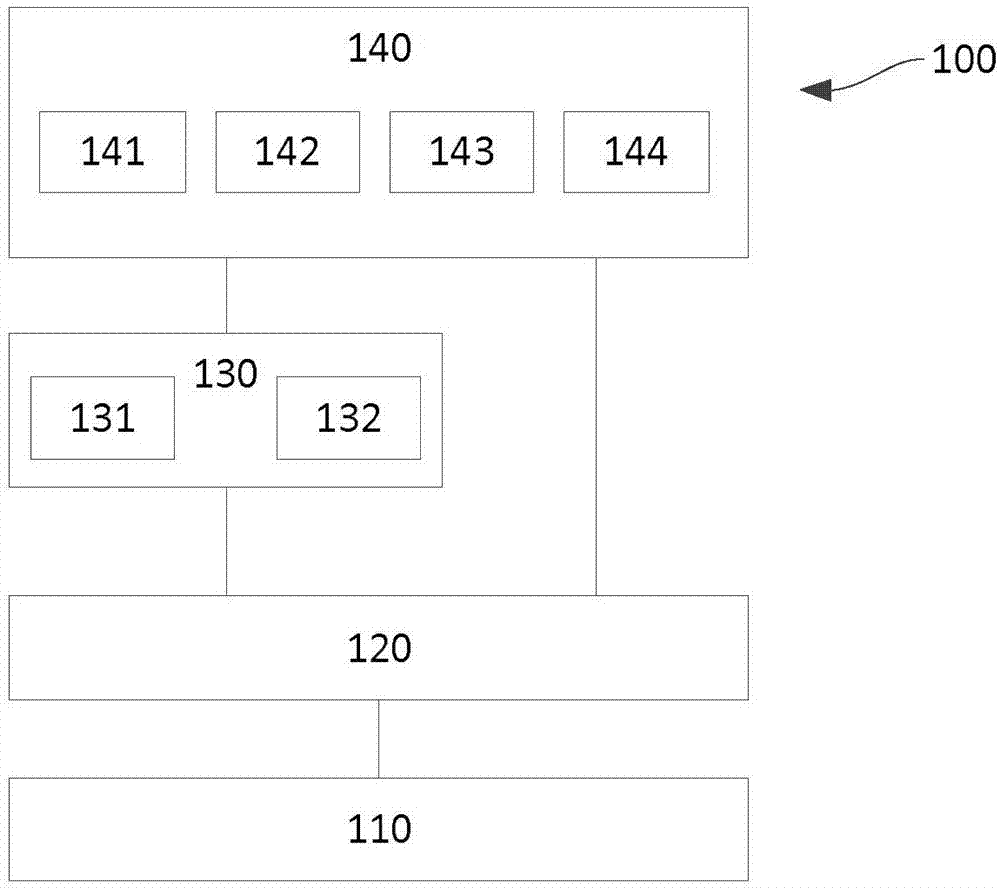
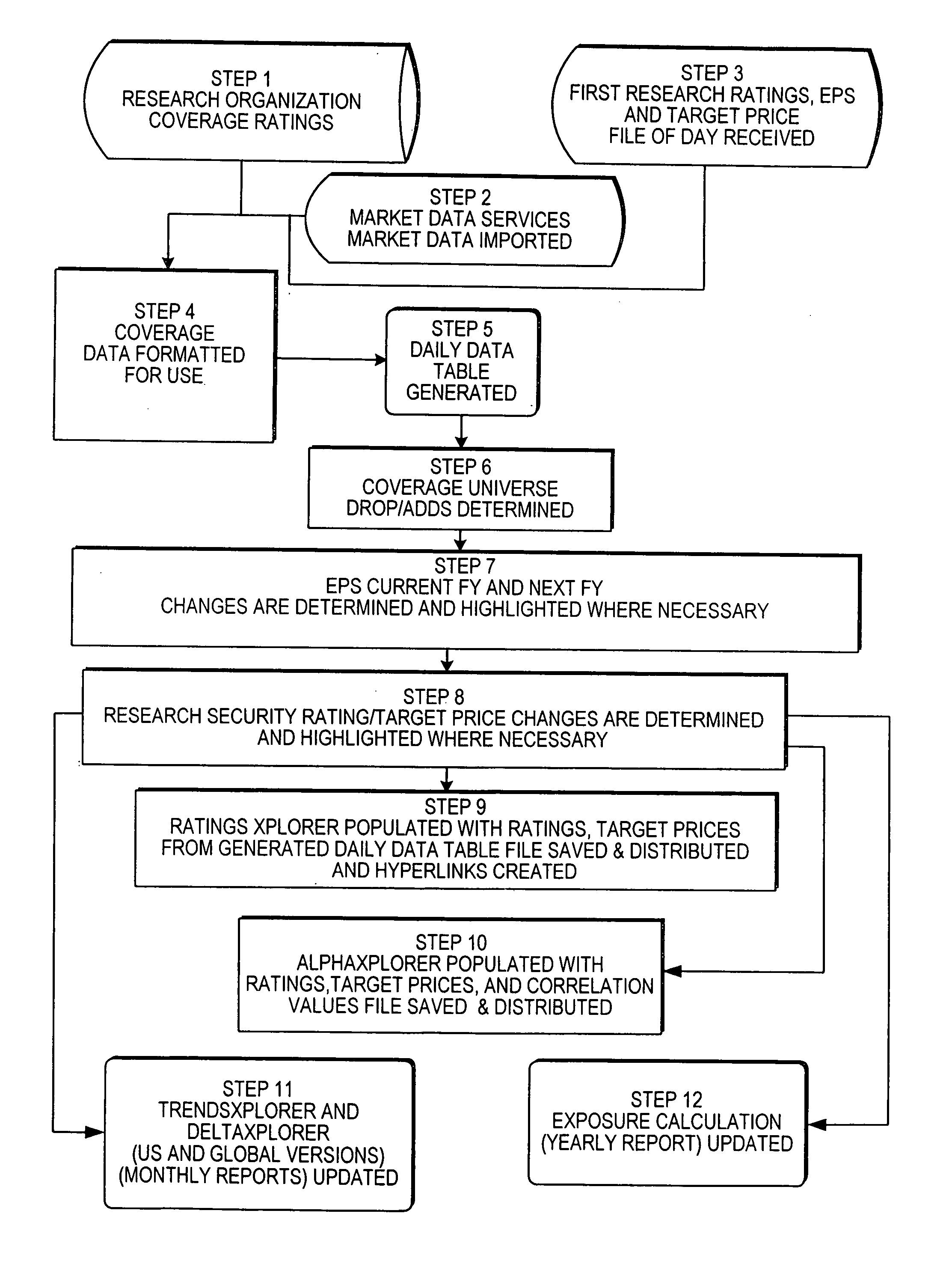
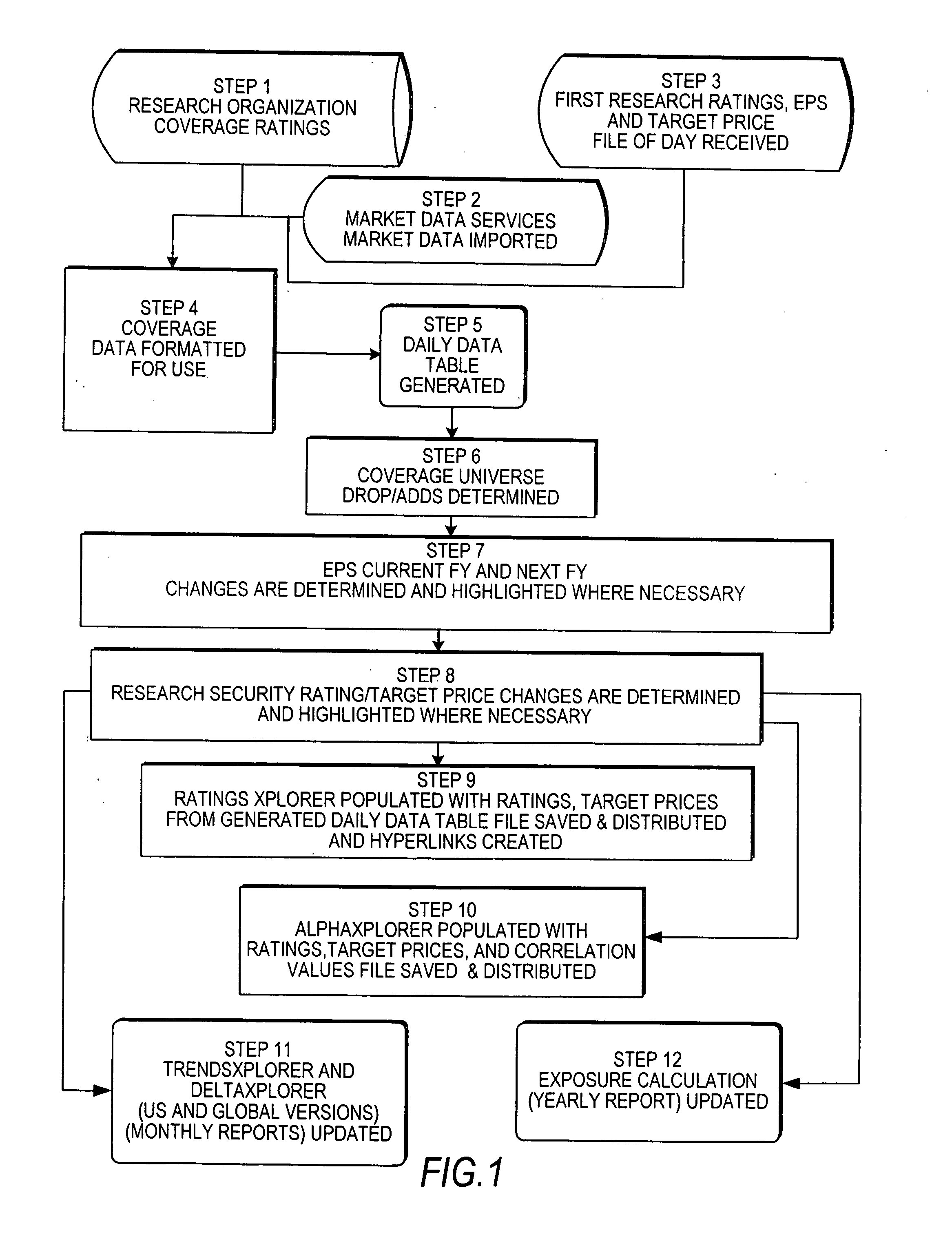
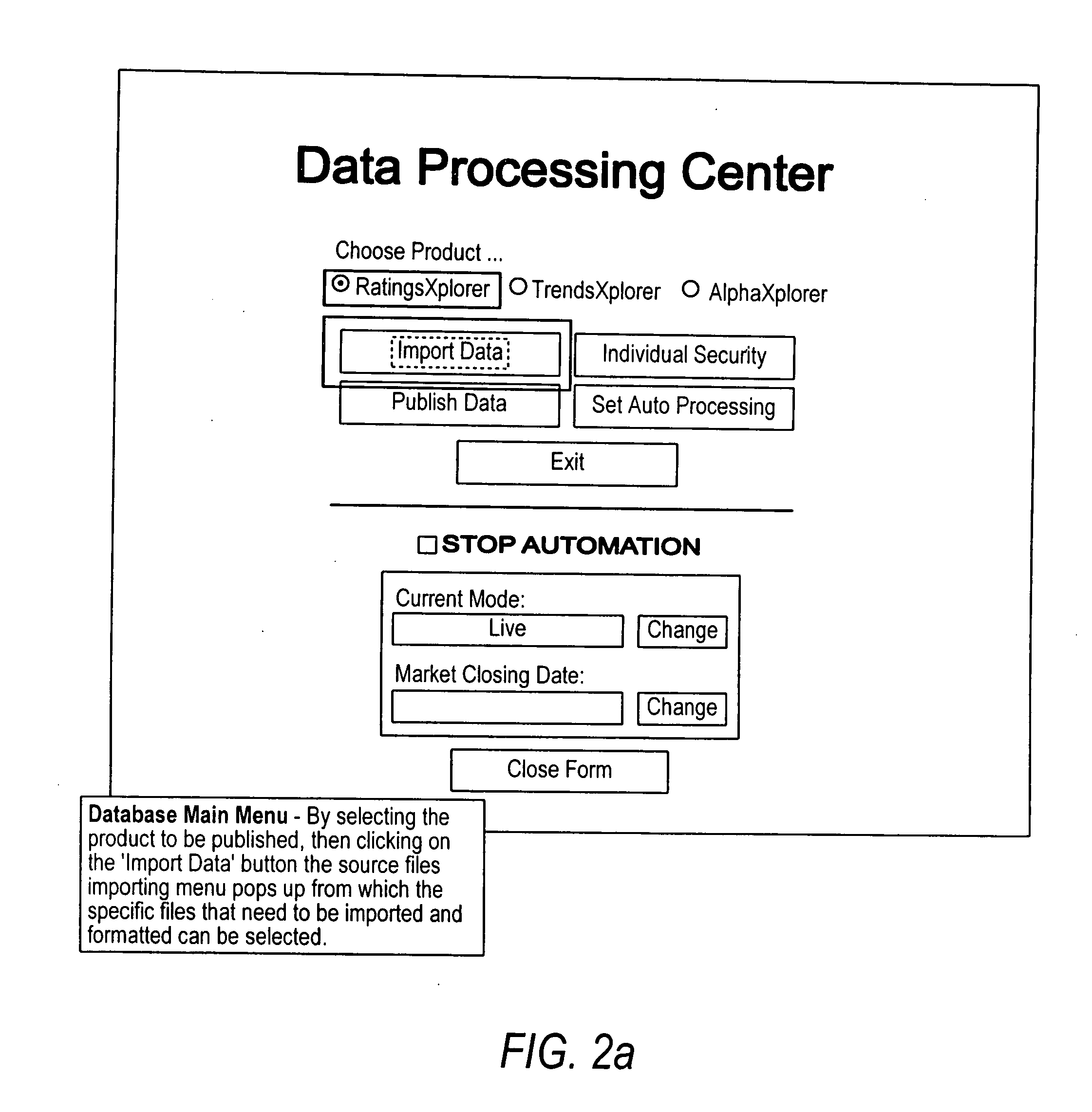
Computer-aided financial security analysis system and method
ActiveUS20070016502A1FinanceAutomatic call-answering/message-recording/conversation-recordingFinancial securityComputer aid
A computer-aided financial analysis system and method provides research analytical capabilities for modeling financial security holdings that include the capability to conduct multi-dimensional dynamic searches across fundamental research, technical research, market data and exposure to exogenous economic and market factors. The capability to isolate securities most susceptible to market movements and overlay available research analyses on top of this view and to view exposure to directional change in any exogenous economic and market factor on an individual security or portfolio of securities in a real-time, intuitive manner via charts, tables and / or heat maps is also provided.
Owner:JPMORGAN CHASE BANK NA
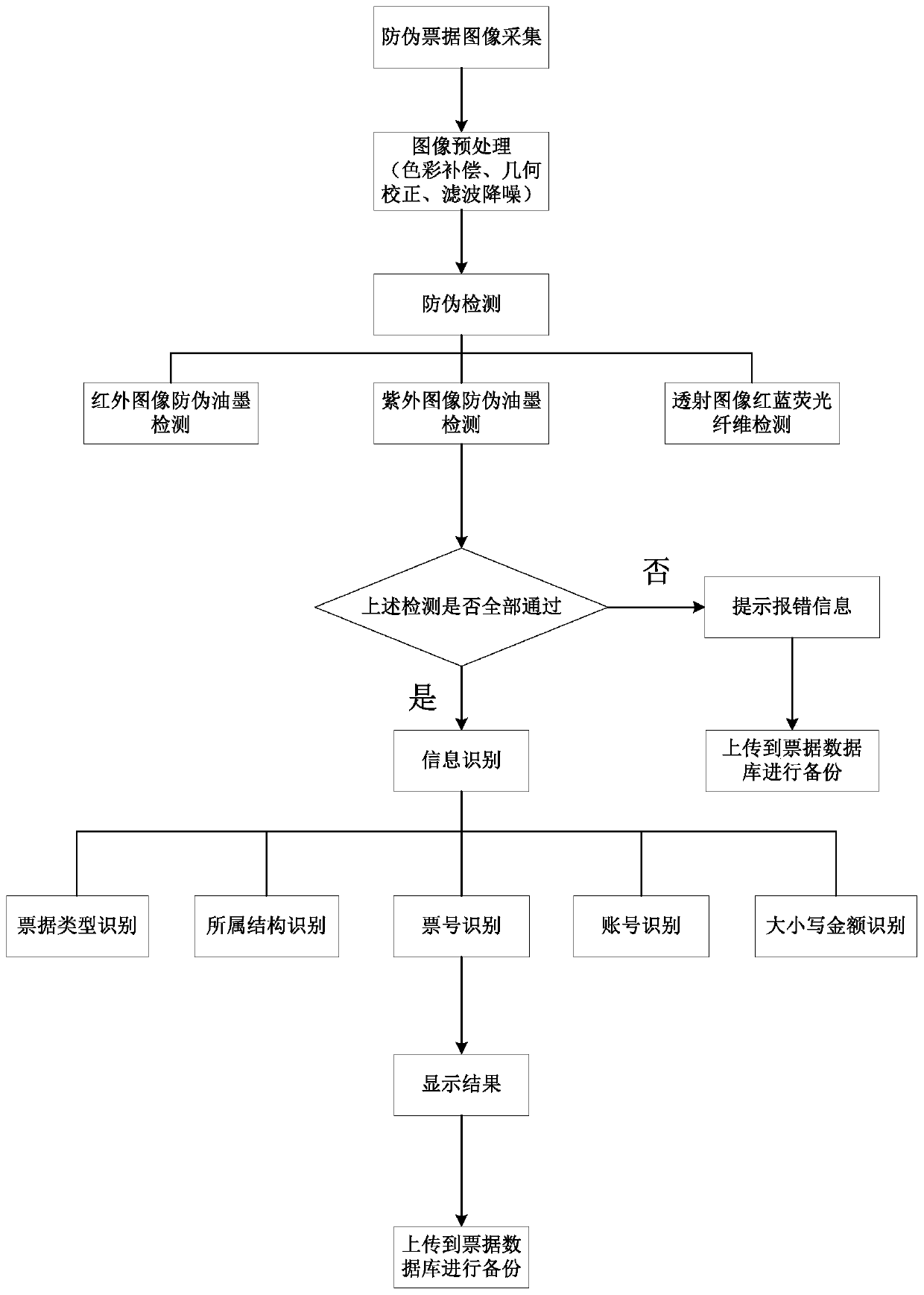
Anti-counterfeiting bill authentic identification system and method based on multispectral images
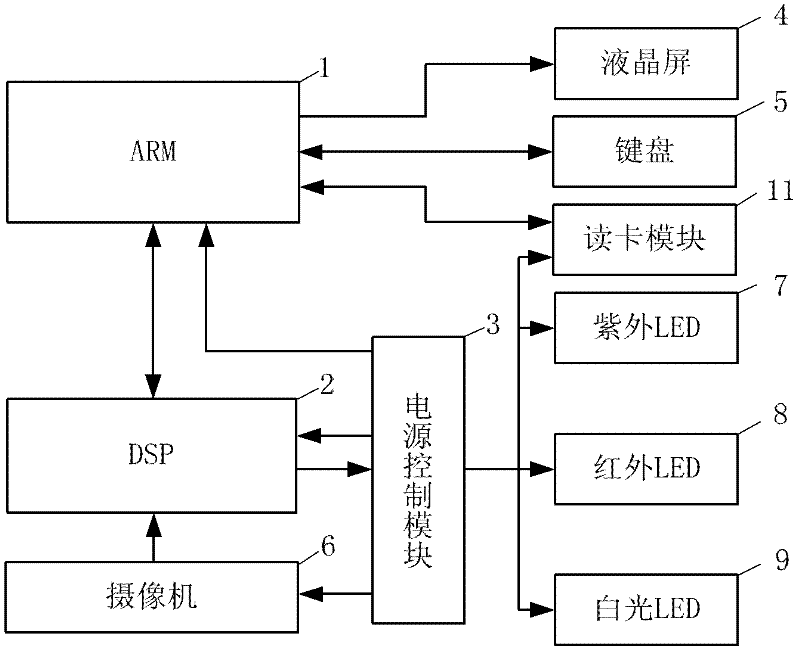
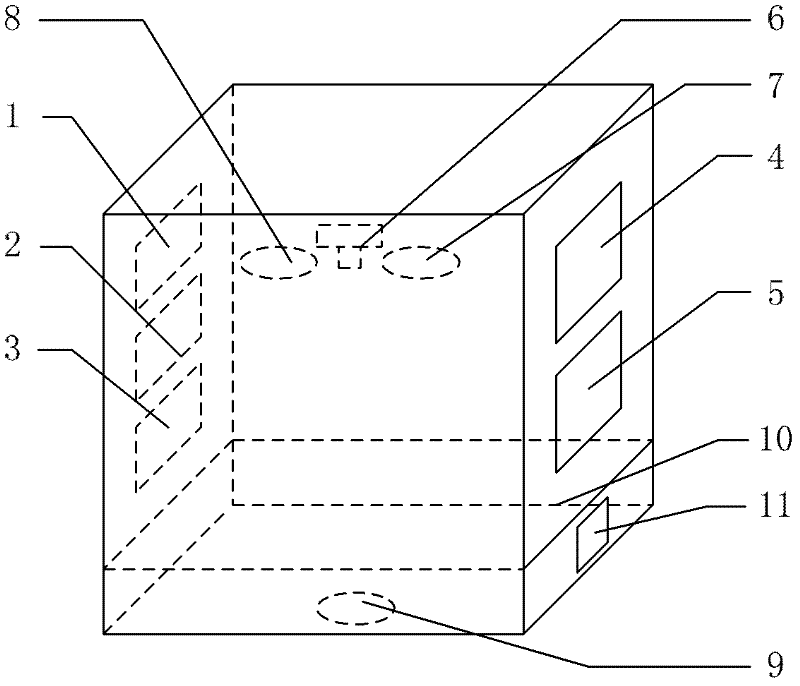
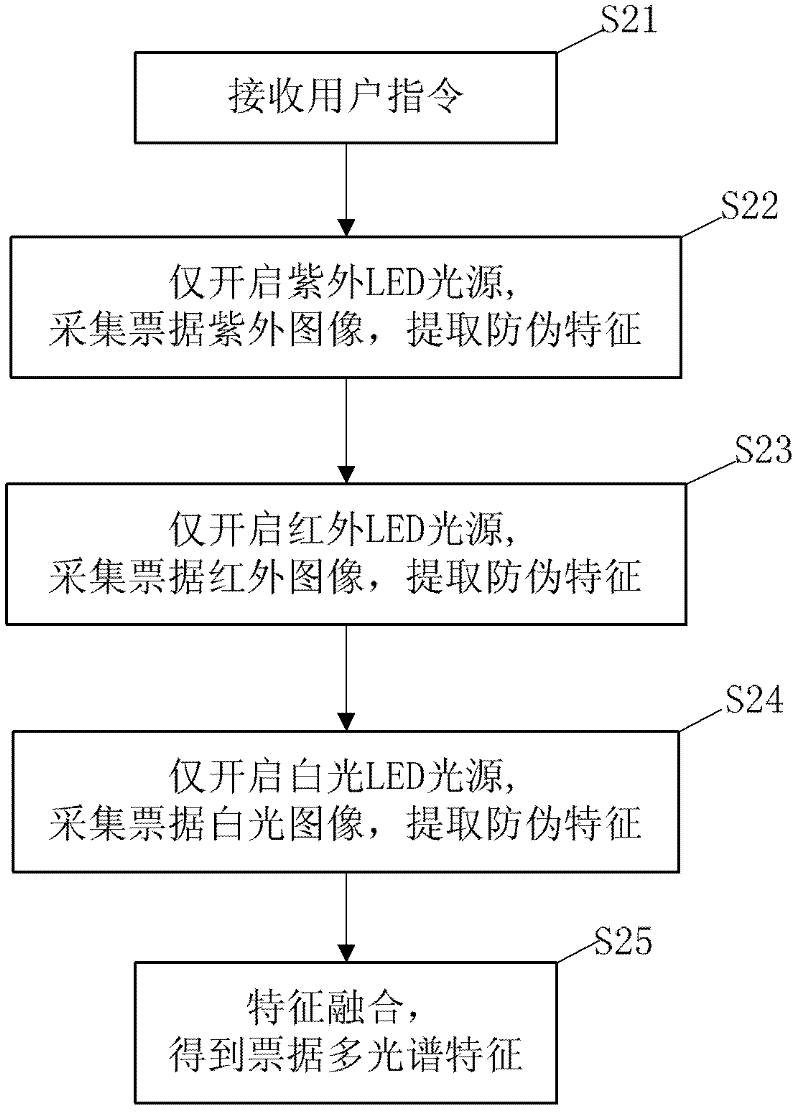
ActiveCN110598699AImprove accuracyImprove reliabilityPaper-money testing devicesCharacter and pattern recognitionColor compensationFinancial security
The invention belongs to the technical field of financial security authentic identification and identification, and discloses an anti-counterfeiting bill authentic identification system and method based on multispectral image. The method comprises the steps: carrying out the image collection of an anti-counterfeiting bill through an image collection module, and obtaining anti-counterfeiting bill images under different spectrums; preprocessing the acquired bill images, wherein preprocessing includes color compensation, geometric correction, filtering and noise reduction; extracting anti-counterfeiting features from the infrared and ultraviolet images, and fusing multiple features to judge the authenticity of the anti-counterfeiting bill; and detecting a text area on the white light image, and recognizing bill face text information, wherein the bill face text information comprises bill types, affiliated organizations, bill numbers, accounts and money amounts. According to the invention,bill authentic identification is carried out by using a multi-mode multi-feature fusion mode, so that the authentic identification accuracy and reliability are improved; and the detail information ofthe anti-counterfeiting mark can be captured, and accurate matching of the feature points is achieved. Moreover, the matching speed is high, and the requirement of real-time performance of online detection can be met.
Owner:HUAZHONG UNIV OF SCI & TECH
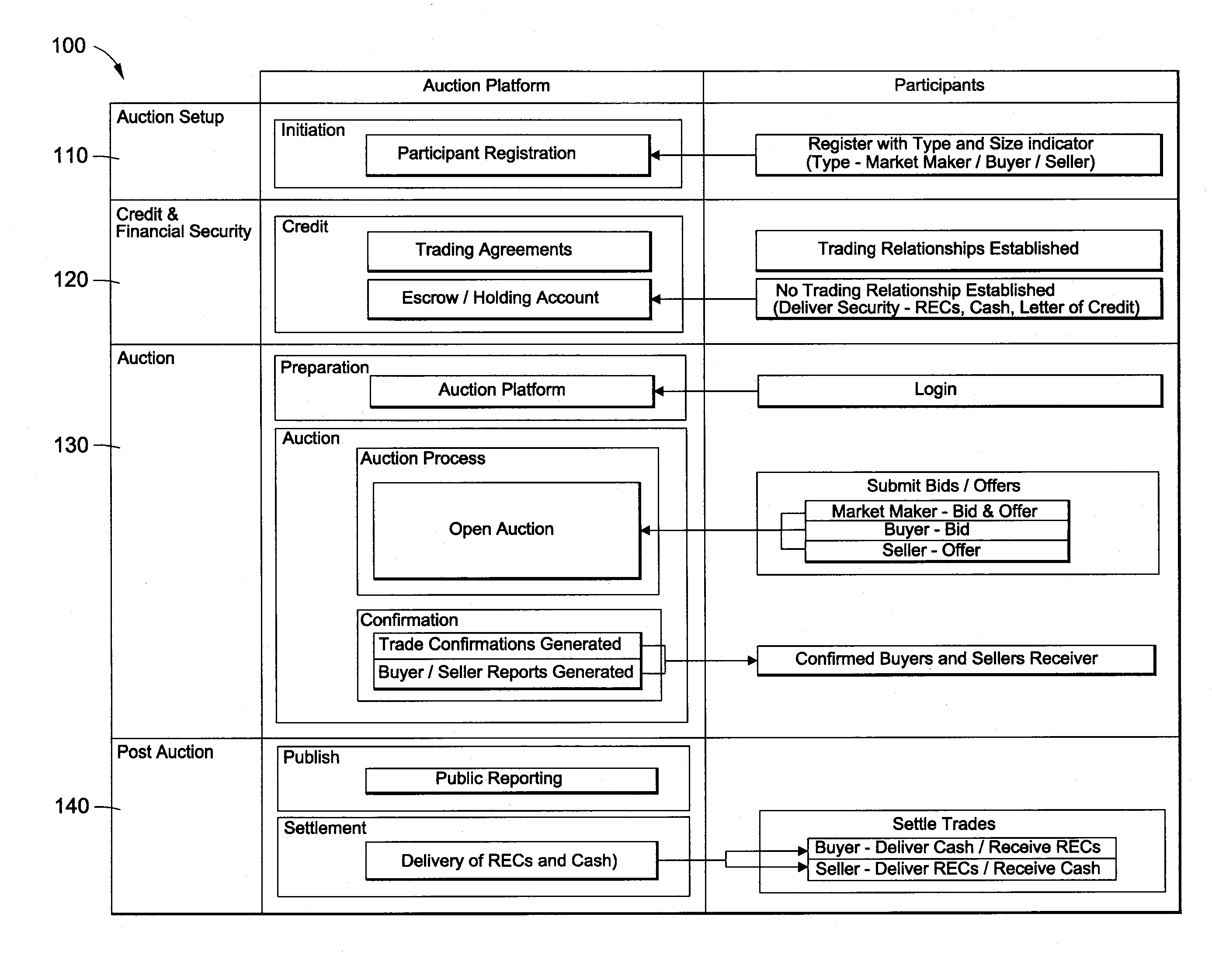
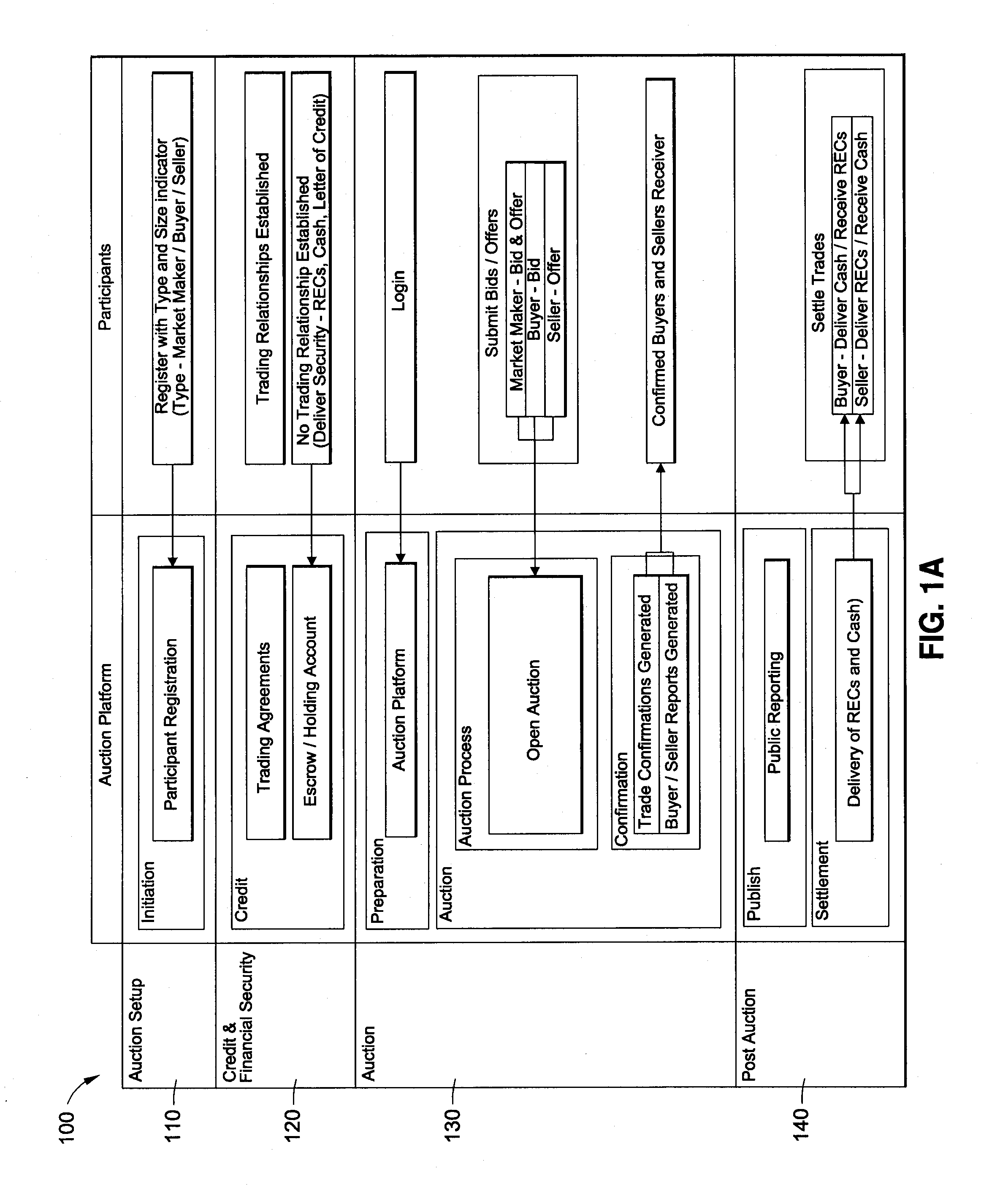
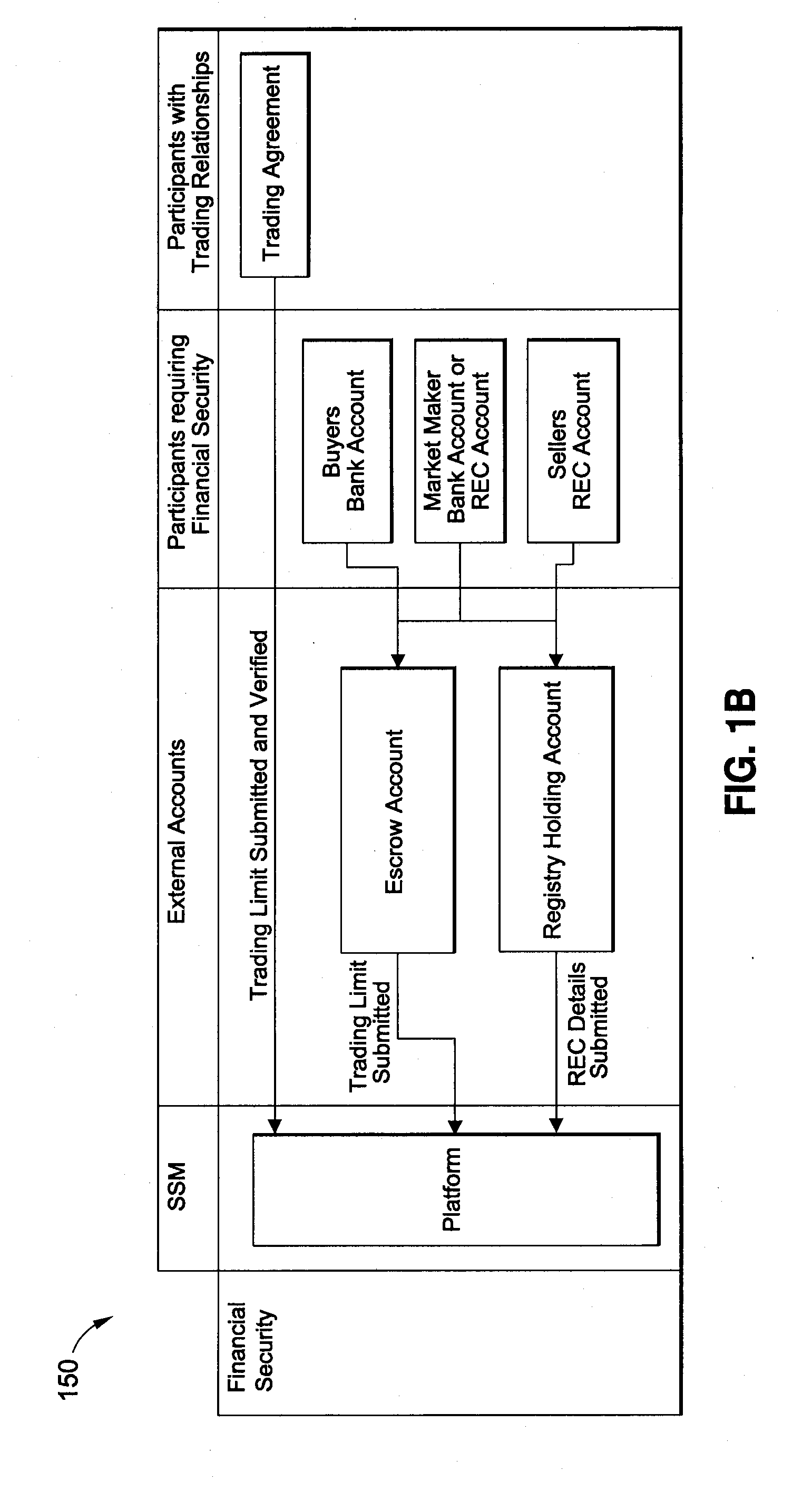
System and Method for Auctioning Environmental Commodities
An institutionally-focused, neutral auction platform is provided that may be utilized for both the primary and secondary trading of environmental commodities and instruments. The auction platform may perform an on-boarding process for auction participants. Thereafter, the auction platform initiates an auction event, in response to a request by an auctioner, based on an identified block of environmental commodities. The auction platform may also receive an indication of financial security from one or more of the auction participants. A winning bidder may then be selected based on auctioner-defined parameters. In certain embodiments, the auction platform may also perform a settlement function for the auctioner and winning bidder relating to the delivery of, and payment for, the identified block of environmental commodities. Various other services and processes may also be provided by the auction platform.
Owner:SKYSTREAM MARKETAB
Computerized system and method for optimizing after-tax proceeds involving options
InactiveUS7047217B1Accurately determineReduce inhibitionFinancePayment architectureTime rangeElectronic form
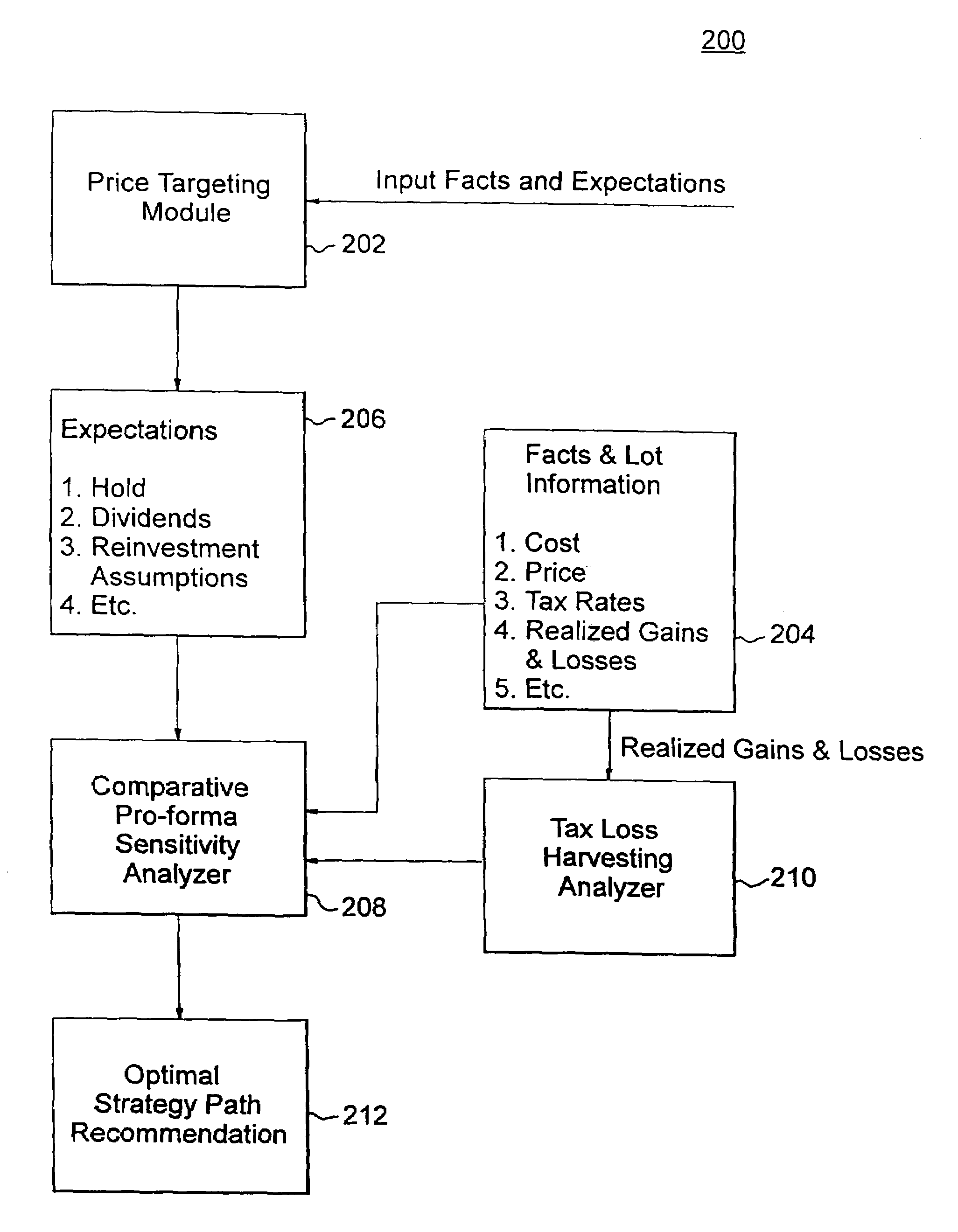
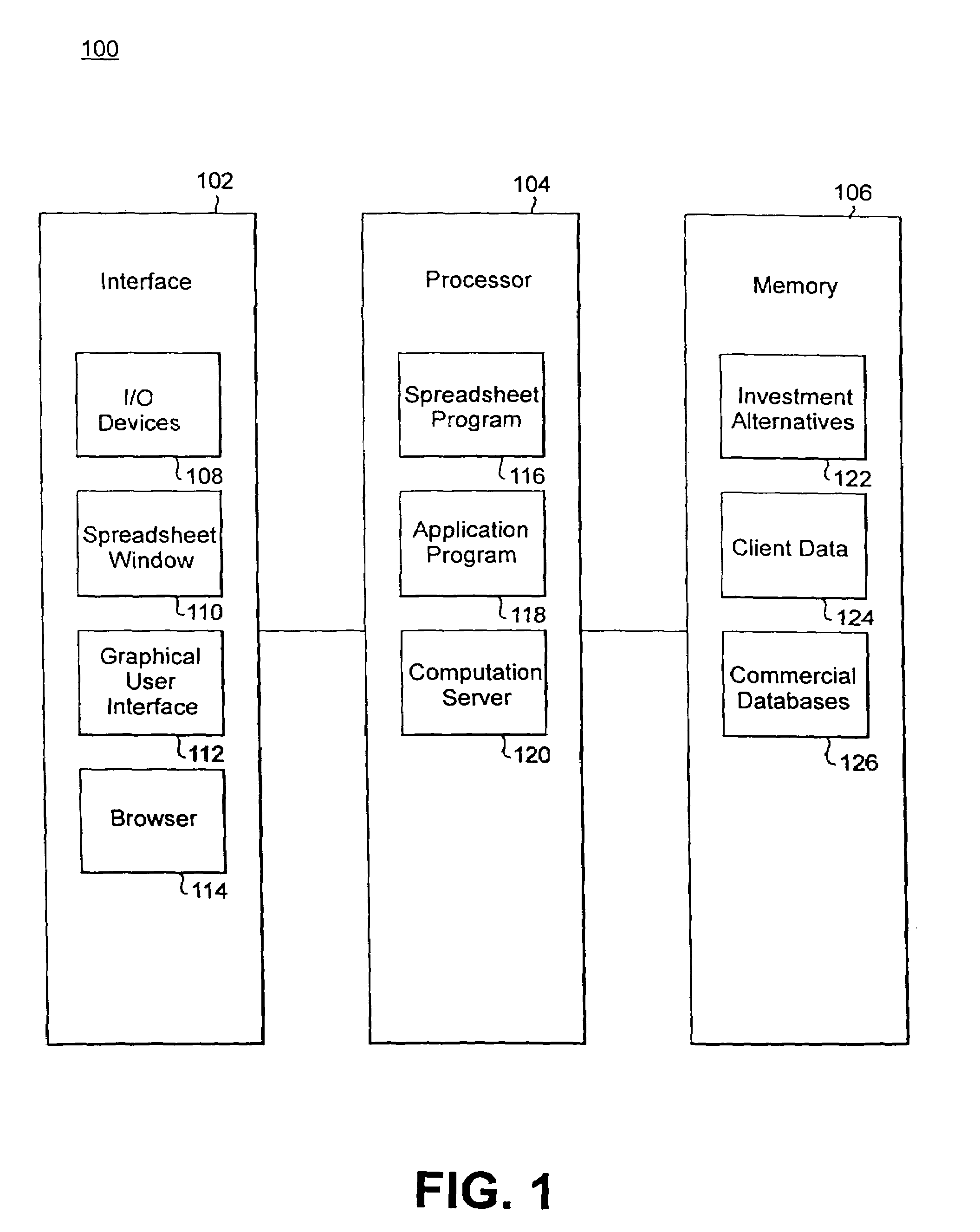
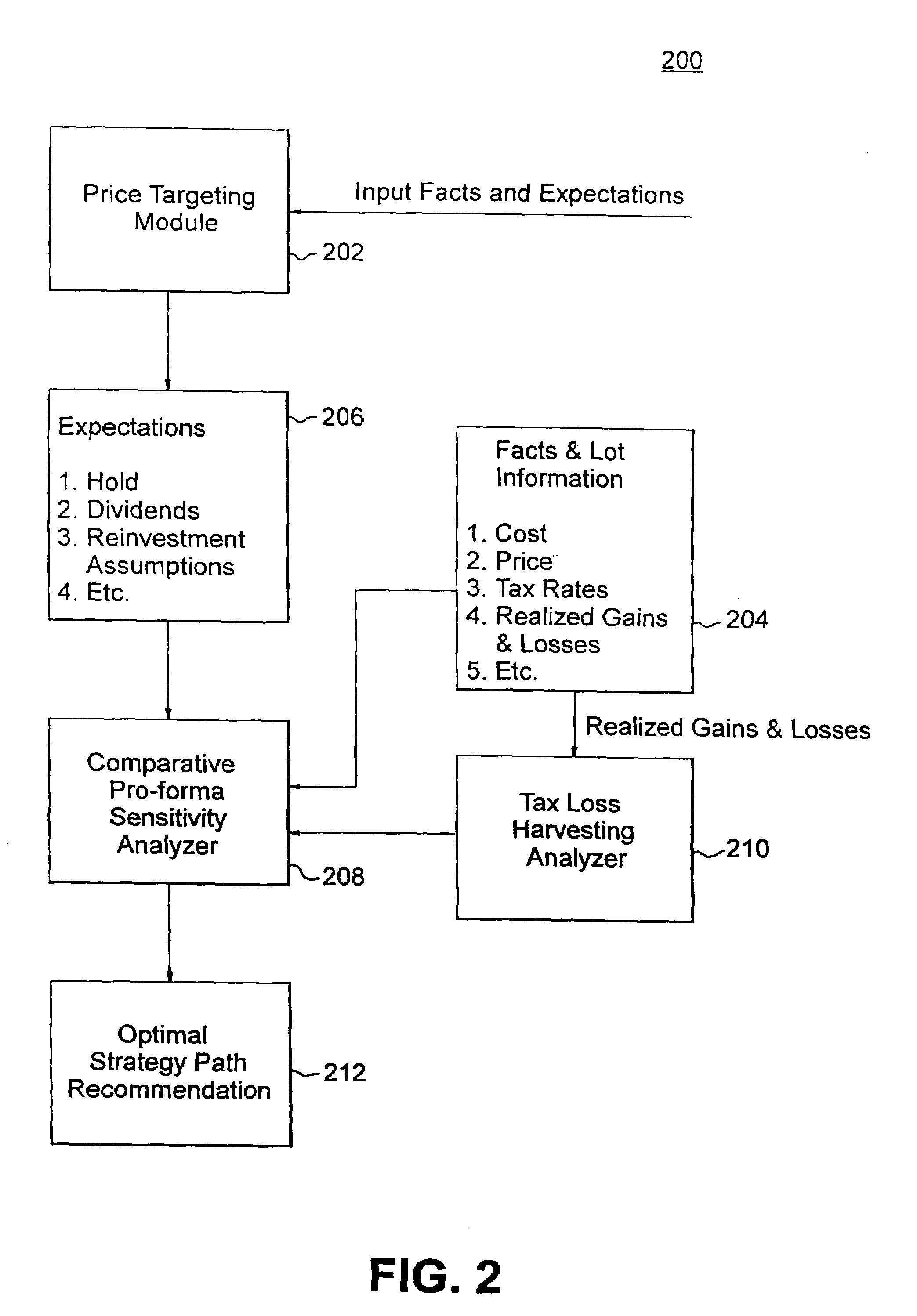
A computerized system and method process financial securities and instruments, including options, derivatives, and bonds, to accurately determine and optimize the after-tax proceeds an investor could expect to have at the end of a holding period for each of a set of investment strategies and determines an optimal strategy for maximizing such after-tax proceeds. The computerized system and method receive tax and investment data, user-customized investment expectations, and financial adviser-based investment expectations at a processor; perform tax loss harvesting analysis on the user-customized investment expectations and the financial adviser-based investment expectations over a dynamic taxation time range using a predetermined software program; perform comparative pro-form a tax sensitivity analysis of the tax and investment data and the analyzed investment expectations using the predetermined software program; and determine and output an optimal after-tax investment strategy path from a plurality of investment strategy paths over the dynamic taxation time range using the predetermined software program to optimize the after-tax proceeds from the plurality of investment strategies. The predetermined software program may include a spreadsheet program.
Owner:BARNARD J GOTTSTEIN REVOCABLE LIVING TRUST +1
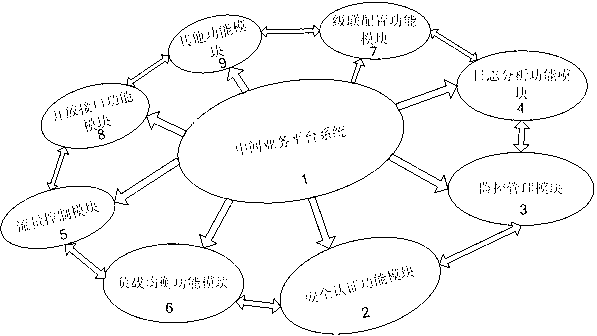
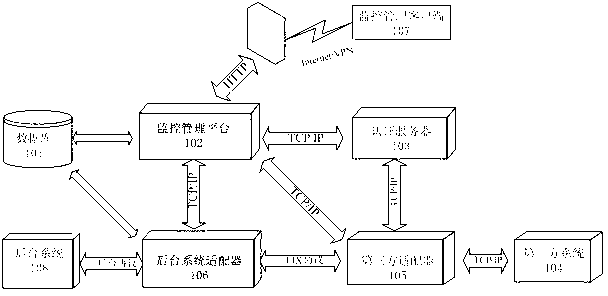
Intermediate business platform system used for financial securities industry
The invention relates to an intermediate business platform system used for the financial securities industry. The intermediate business platform system comprises a main intermediate business access platform frame, a monitoring and management subsystem module, an authentication service module, a Fix engine subsystem module and a third-party system access client end, a background system adapter module and a monitoring / management client end module, wherein the main intermediate business access platform frame is used for loading the modules, coordinating the communication among the modules, and transmitting third-party interface protocols of securityies companies; the authentication service module is an authentication subsystem; the monitoring and management subsystem module can monitor the transaction situation of the Fix engine subsystem module, and encode / decode policy configuration, and the background system adapter and the third-party system access the access authority of the client end; and the Fix engine subsystem module and the third-party system access client end carry out information exchange through the Fix engine subsystem module. The intermediate business platform system can realize the separation of an internal securities foreground system and an internal securities background system, and efficiently carry out the data exchange among systems.
Owner:SUZHOU INDAL PARK LINKAGE SOFTWARE
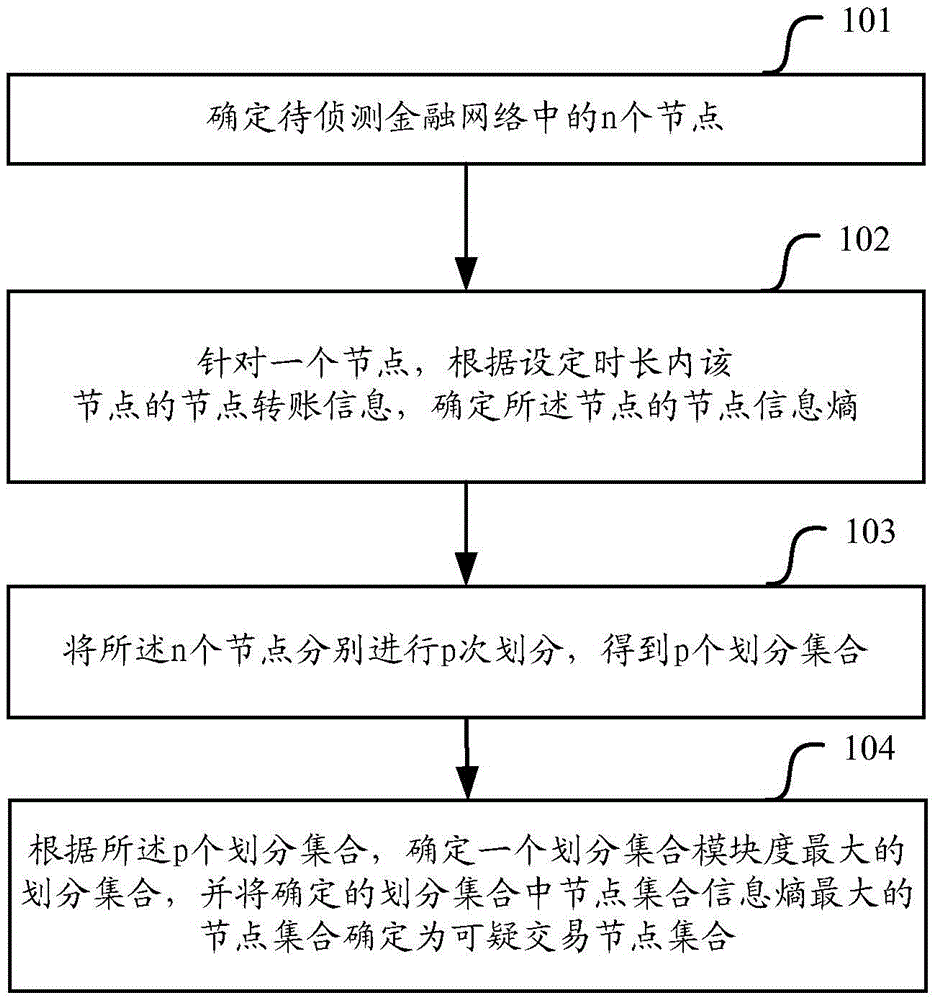
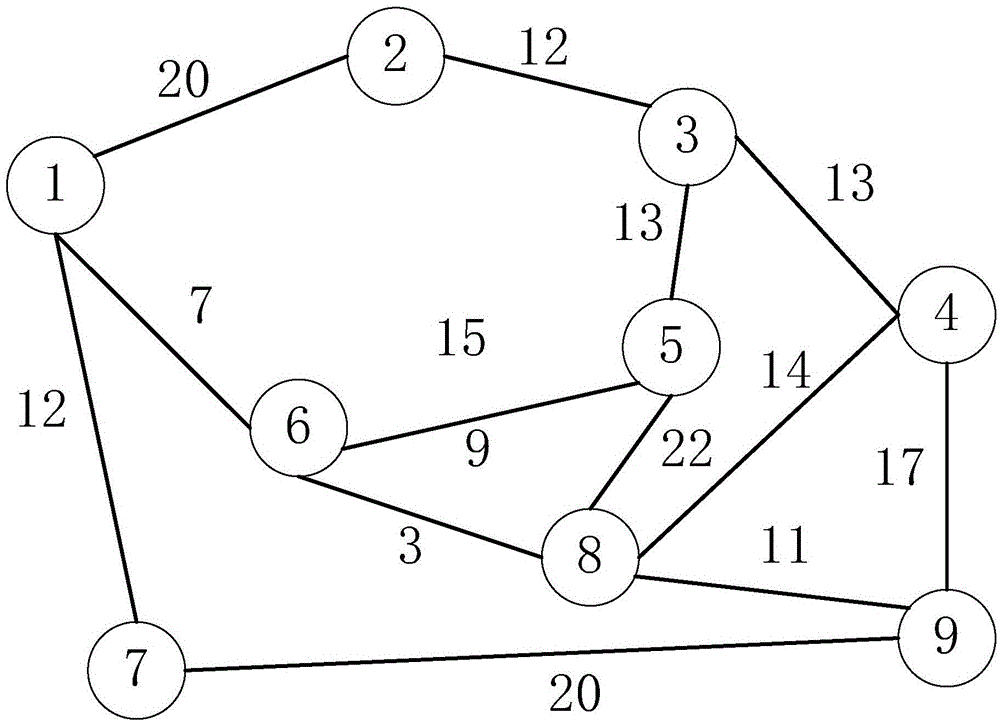
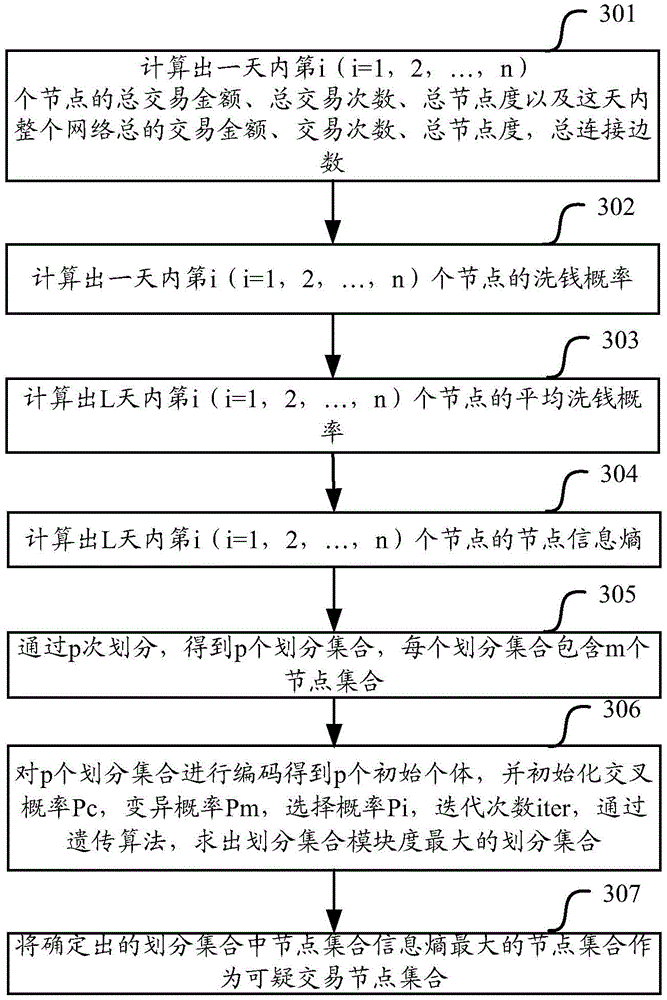
Suspected transaction node set detection method and device
The invention relates to the technical field of financial security, and particularly relates to a suspected transaction node set detection method and device, aiming to solve the technical problems that the accuracy and the efficiency are low and abnormal transaction communities with good concealment are difficult to be found when suspected money laundering communities in financial network are detected in the prior art. The method includes that for the n nodes in the financial network, the n nodes are divided for p times to obtain p divided sets, and a divided set with the largest divided set modularity is obtained based on the p divided sets, and the node set with the largest node set information entropy in the divided set is regarded as a suspected transaction node set. According to the method, the relevance between the nodes and the relation of the nodes in a network topology between the nodes are fully considered, so that the suspected transaction node set in the financial network can be accurately and reliably determined, and the suspected transaction node set can be a community which allows transaction.
Owner:CHINA UNIONPAY
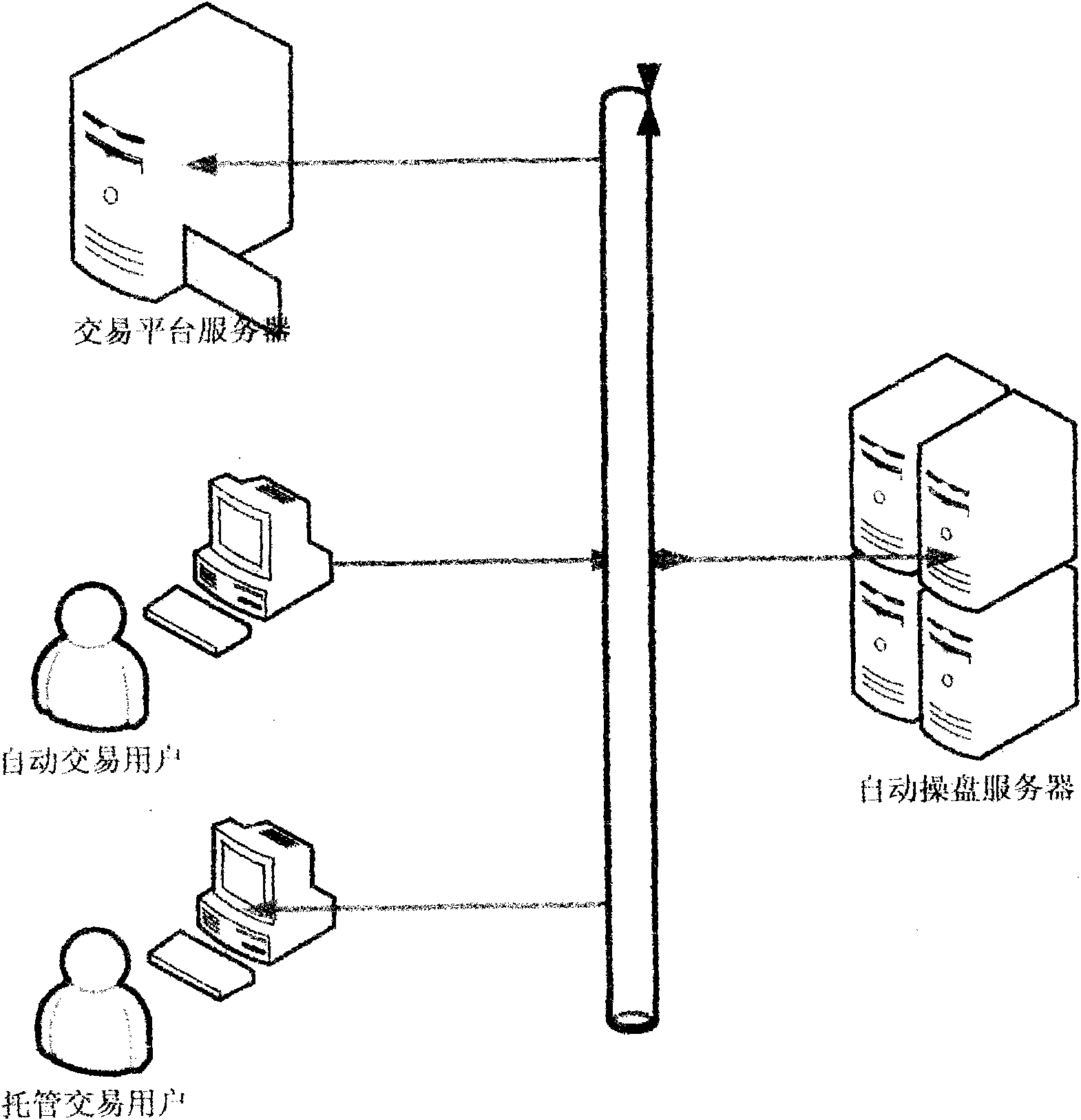
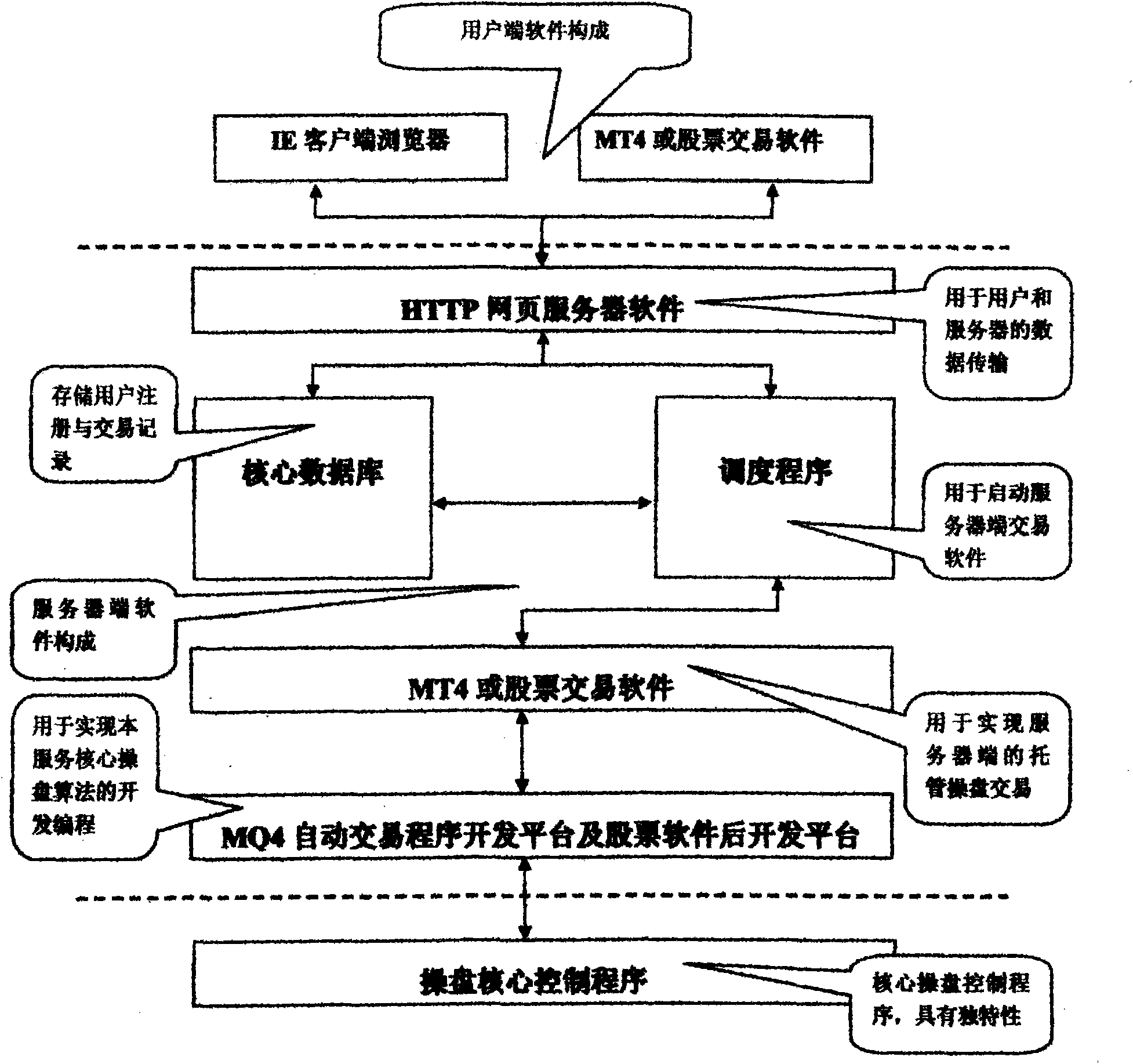
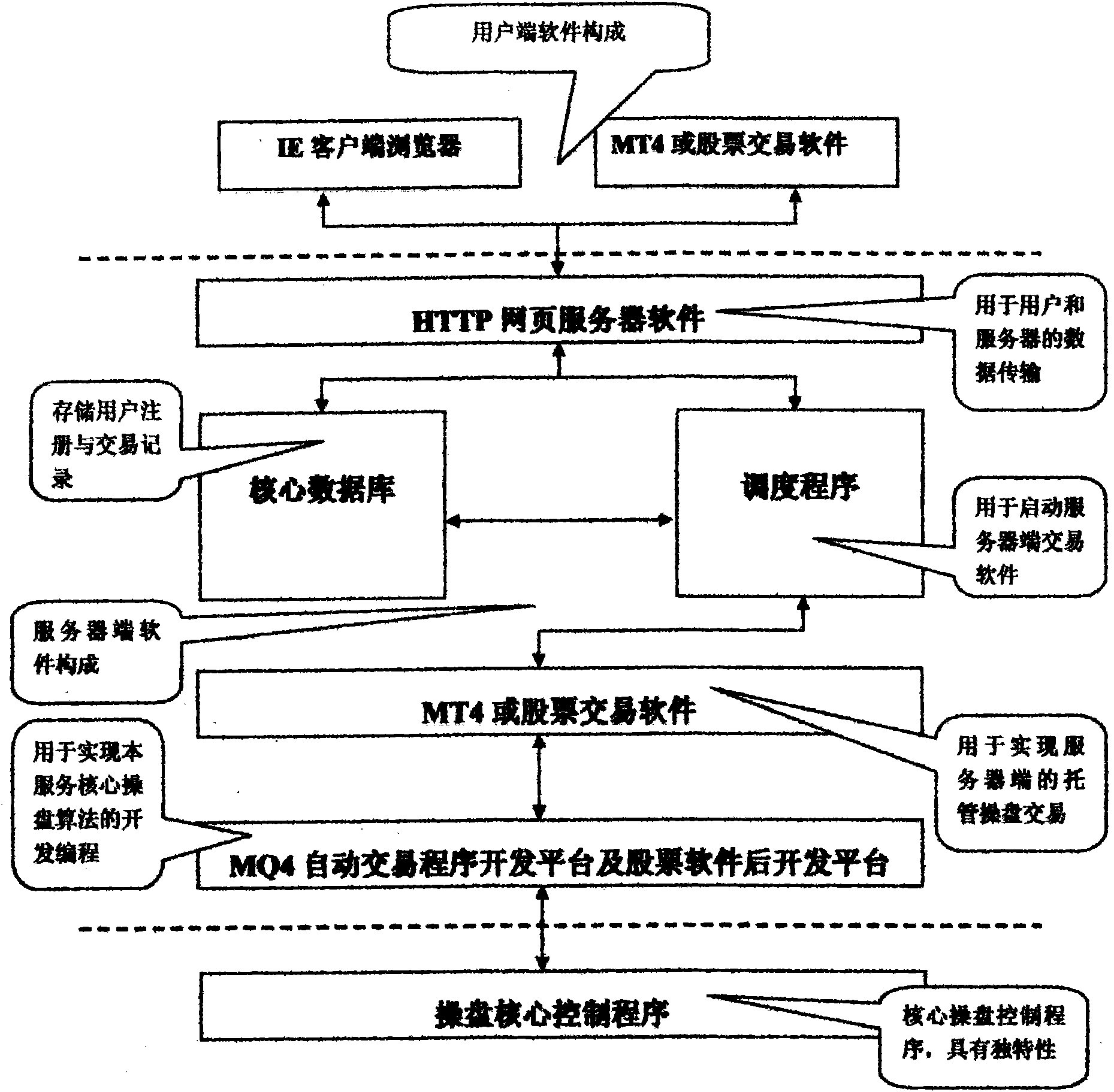
Fully-automatic stock operation server
The invention relates to a fully-automatic stock operation server, belongs to the field of computer server, and aims to realize automated stock operation with a high success rate and stable profit. The fully-automatic stock operation server consists of an IE client browser, an MT4 or stock trading software, HTTP web server software, a core database, a scheduling program, an MQ4 intelligent trading program developing platform, a stock software background developing platform, and a stock operation core control program. The fully-automatic stock operation server has the advantages of automatic stock operation, capability of overcoming subjective and emotional errors of artificial market analysis and stock operation, high success ratio, high stability and high profit; the core stock operation algorithm of the system is tested by long-term historical data and real-time data, which proves that stock operation profit success ratio is over 90 percent, the profit curve straightly rises, the annual investment return is over 50 percent, and the fully-automatic stock operation server is suitable to be used by people engaged in investment and market analysis of financial security.
Owner:帅亿
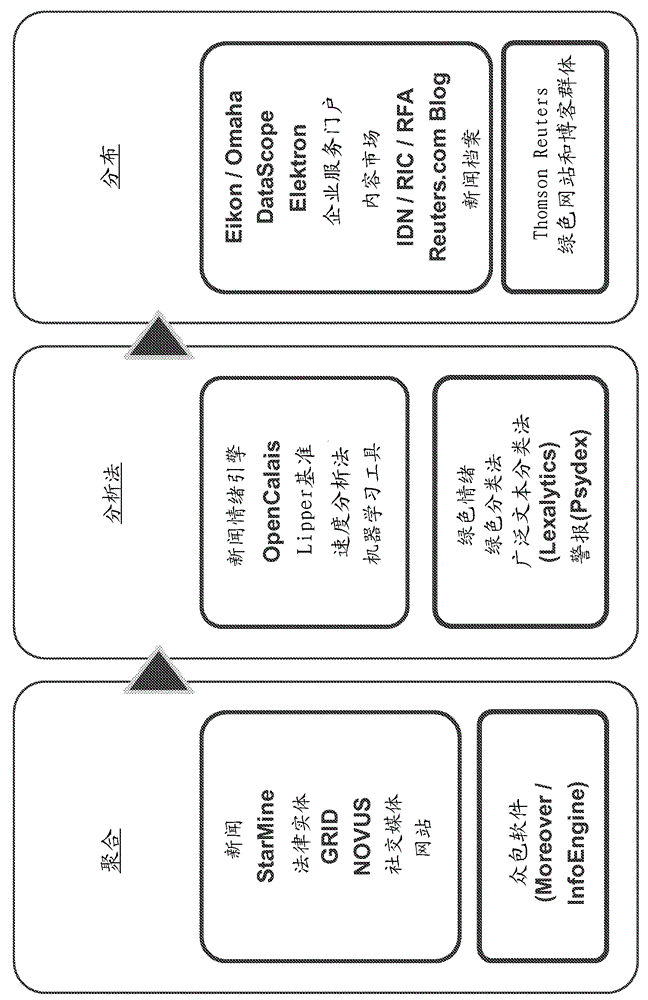
Methods and systems for generating composite index using social media sourced data and sentiment analysis
ActiveCN104995650AAccelerate market share penetrationDevelop Emotional DefenseFinanceSemantic analysisSocial mediaFinancial security
The present invention provides a News / Media Analytics System (NMAS) adapted to automatically process and read news stories and content from blogs, twitter, and other social media sources, represented by news / media corpus, in as close to real-time as possible. Quantitative analysis, techniques or mathematics, such as green scoring / composite module and sentiment processing module are processed to arrive at green scores, green certification, and / or model the value of financial securities, including generating a composite environmental or green index. The NMAS automatically processes news stories, filings, new / social media and other content and applies one or more models against the content to determine green scoring and / or anticipate behavior of stock price and other investment vehicles. The NMAS leverages traditional and, especially, social media resources to provide a sentiment-based solution that expands the scope of conventional tools for creating a socially aware composite index.
Owner:FINANCIAL & RISK ORG LTD
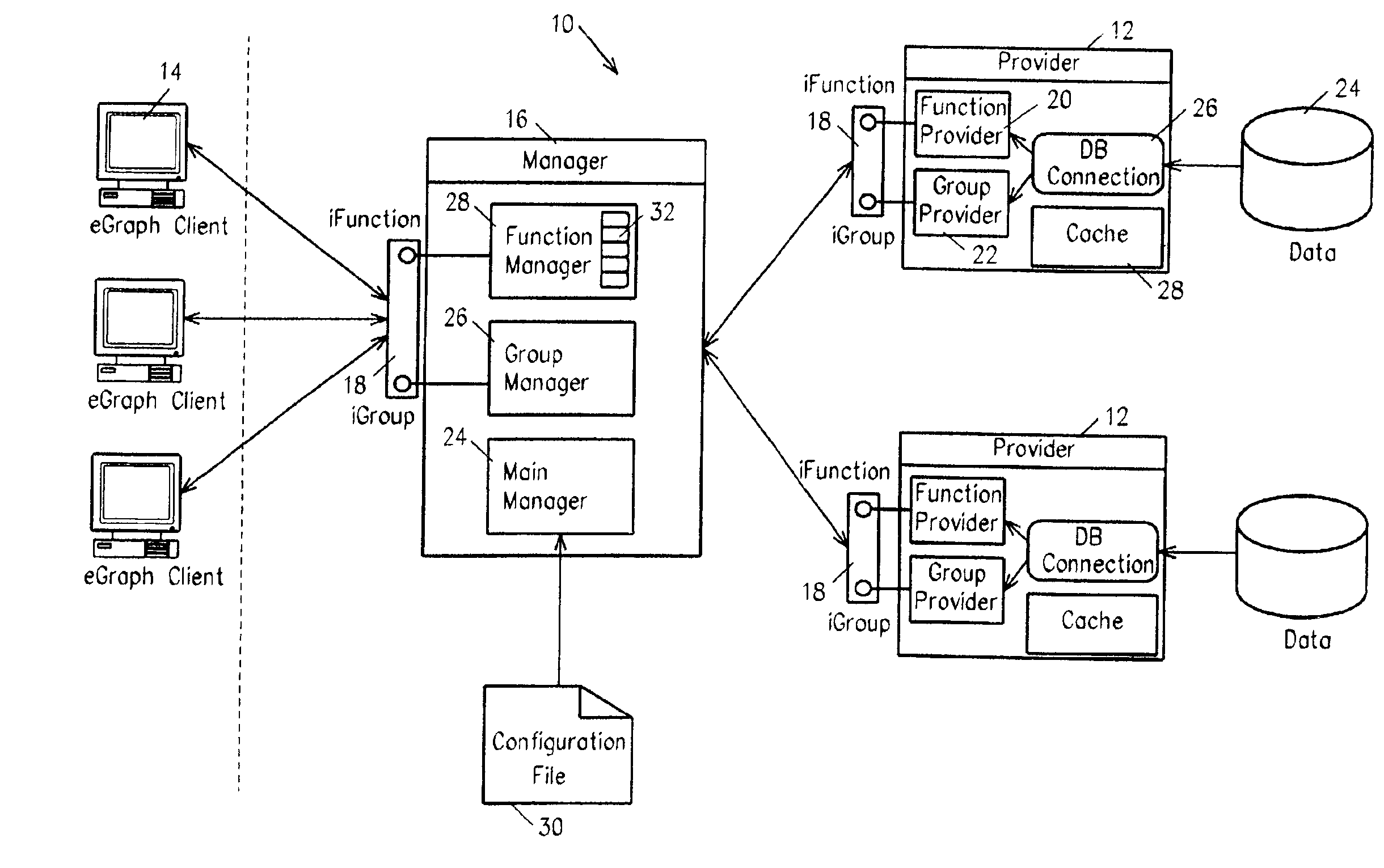
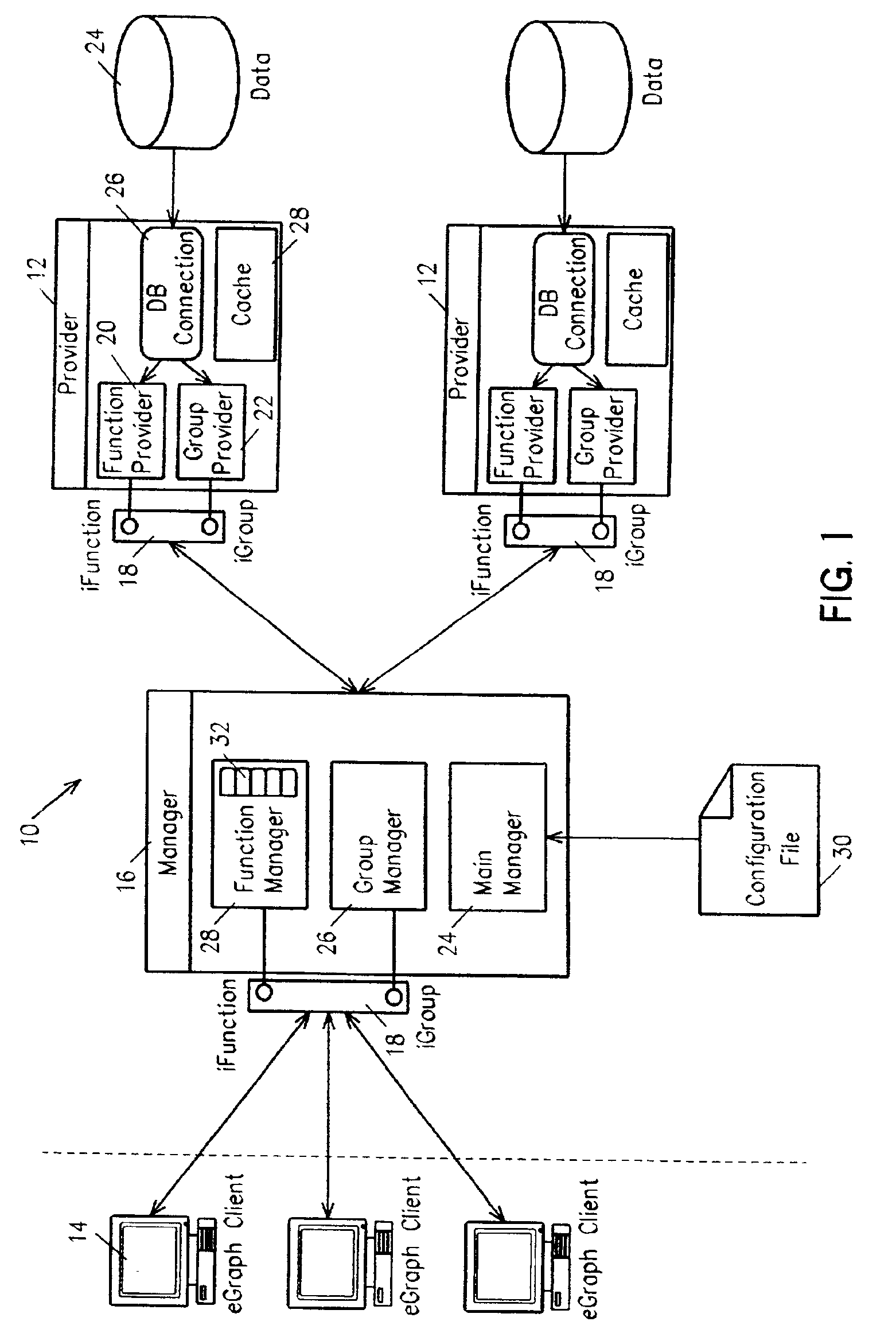
Method and system for providing distributed functionaltiy and data analysis system utilizing same
InactiveUS6968355B2Increase capacityDynamic ResponseData processing applicationsResource allocationGraphicsSpecific function
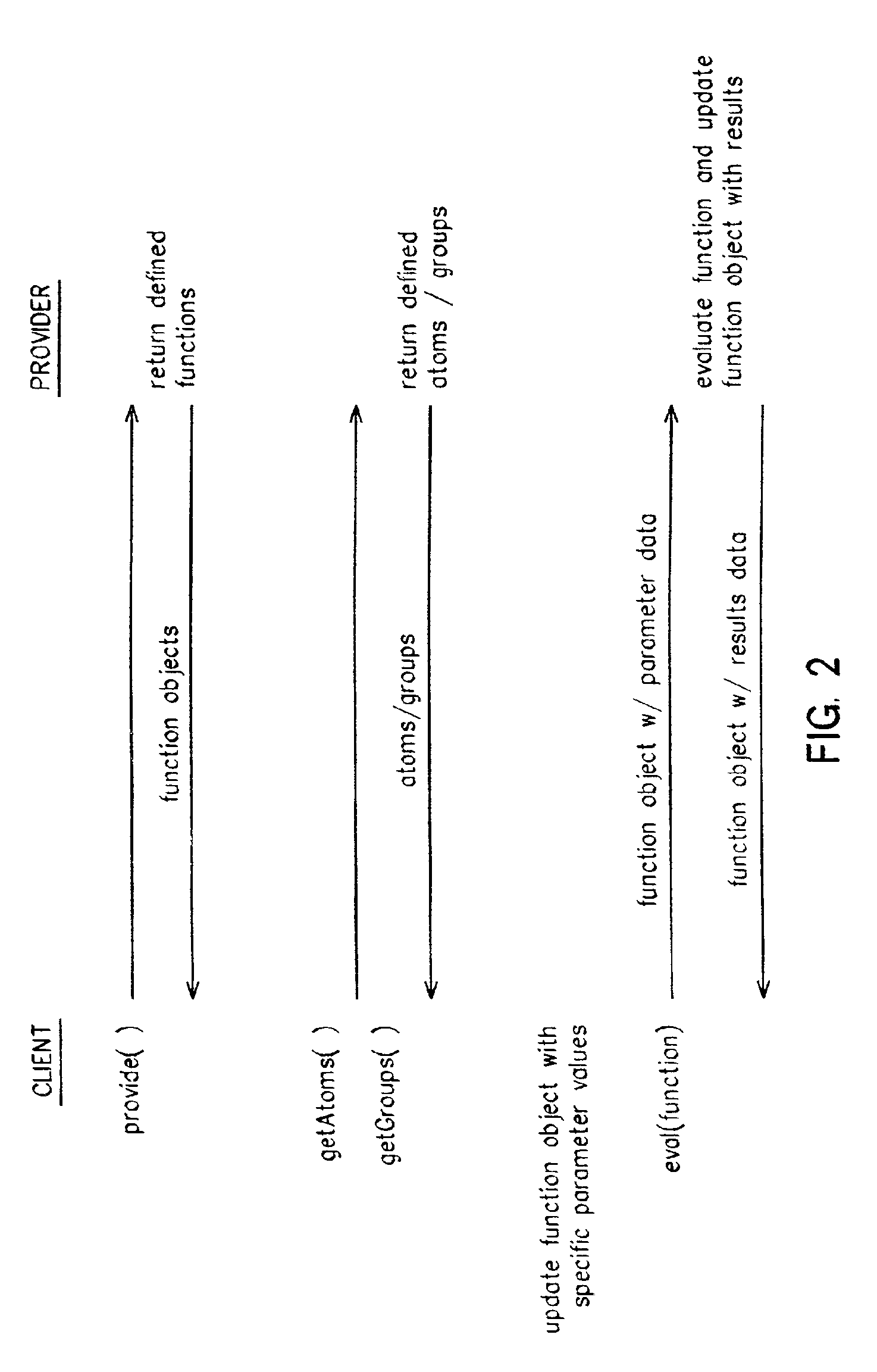
Methods and systems for providing distributed functionality to a plurality of clients comprise the use of more provider servers which publish function objects to clients upon request. Each function object corresponds to a function that is supported by the provider server or a connected downstream provider server. Group definition can also be published by the provider server. The client software is dynamically responsive to the functions which are available from the provider servers and permit a user of the client to select specific functions from the set of available functions for execution. Functions can be executed by modifying the function object to include specific parameter values and sending it to a provider server. Results of function evaluation can be returned in a further modified function object. In a particular implementation, the functions return financial information about specified financial securities and the client graphically displays the returned data.
Owner:UBS BUSINESS SOLUTIONS AG
Financial security authentication based mobile Internet intelligent payment terminal and payment system
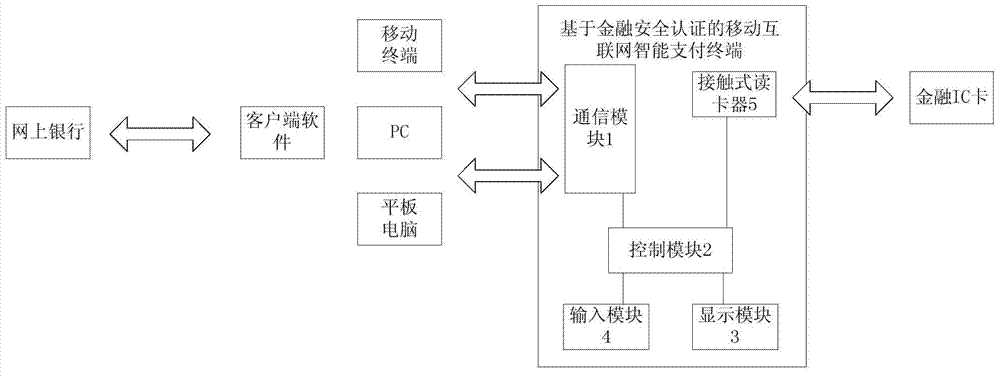
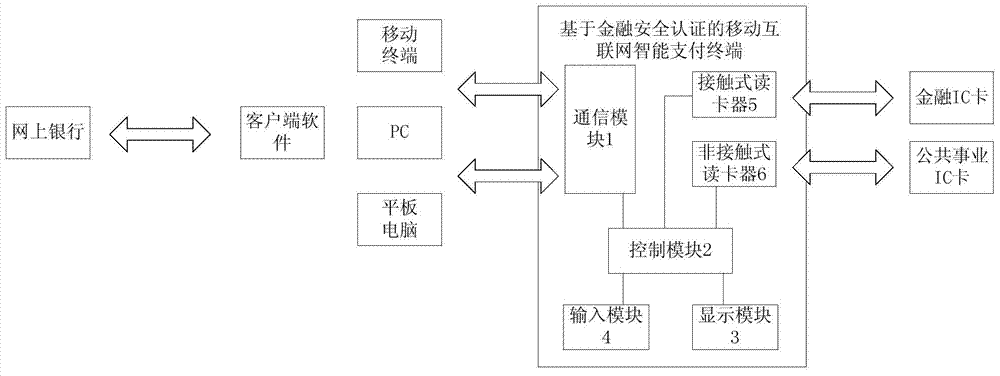
The invention provides a financial security authentication based mobile Internet intelligent payment terminal. The financial security authentication based mobile Internet intelligent payment terminal comprises a communication module, a control module, a display module, an input module and a contact type card reader; the communication module is used for receiving the identity authentication information and the transaction information from a financial IC (Integrated Circuit) card of a client; the control module is used for receiving and storing the identity authentication information and the transaction information of the financial IC card; the display module is used for receiving and displaying the identity authentication information and the transaction information of the financial IC card and prompting a user whether the authorization confirmation needs to be performed or not; the input module is used for receiving an authorization instruction or a transaction cancelling instruction of the user and forwarding the authorization instruction or the transaction cancelling instruction to the control module; the contact type card reader is used for calling the financial IC card according to a digital signature instruction to perform the digital signature on the transaction information, reporting a transaction message after the signature to an Internet bank for verification and achieving the payment after the verification succeeds. According to the financial security authentication based mobile Internet intelligent payment terminal and payment system, the man-machine interactive way is adopted, the identity authentication and the transaction signature are provided, the meanwhile the Internet bank based mobile payment business model is provided.
Owner:BEIJING JINKELIANXIN DATA TECH CO LTD
Identity authentication method for realizing two-dimensional code safety payment
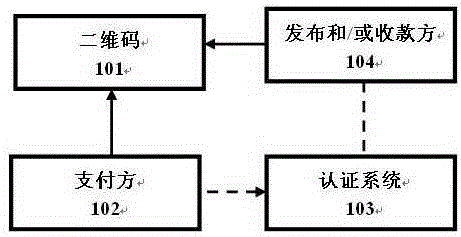
InactiveCN105243539AEnsure safetySafe Payment GuaranteeProtocol authorisationPaymentFinancial security
The invention relates to an identity authentication method for realizing two-dimensional code safety payment. According to the method, identity authentication codes of a payee or a two-dimensional code releaser are loaded in a two-dimensional code, and therefore, when two-dimensional code payment is carried out, a system performs identity authentication on the payee, the two-dimensional code releaser and a payer in advance, and substantial payment business operation can be allowed to be carried out only when relevant authentication is successful. With the method of the invention adopted, the real identity information of each side can be fully displayed as much as possible, and the payer side can be assisted to further confirm whether the real identity information of the payee is consistent with the information mastered before, and whether the payer side is the true owner of a payment account can be also confirmed, and therefore, financial security of users can be guaranteed. According to the method, a safety payment threshold is established at a front end, and effective prevention of account compromised payment or illegal payment can be established at a back end, and the identity of the payer can be further authenticated, and illegal transfer through using compromised accounts can be prevented, and safety protection for the payment of the users can be implemented in a multi-aspect manner.
Owner:CHONGQING ZHITAO INFORMATION TECH CENT
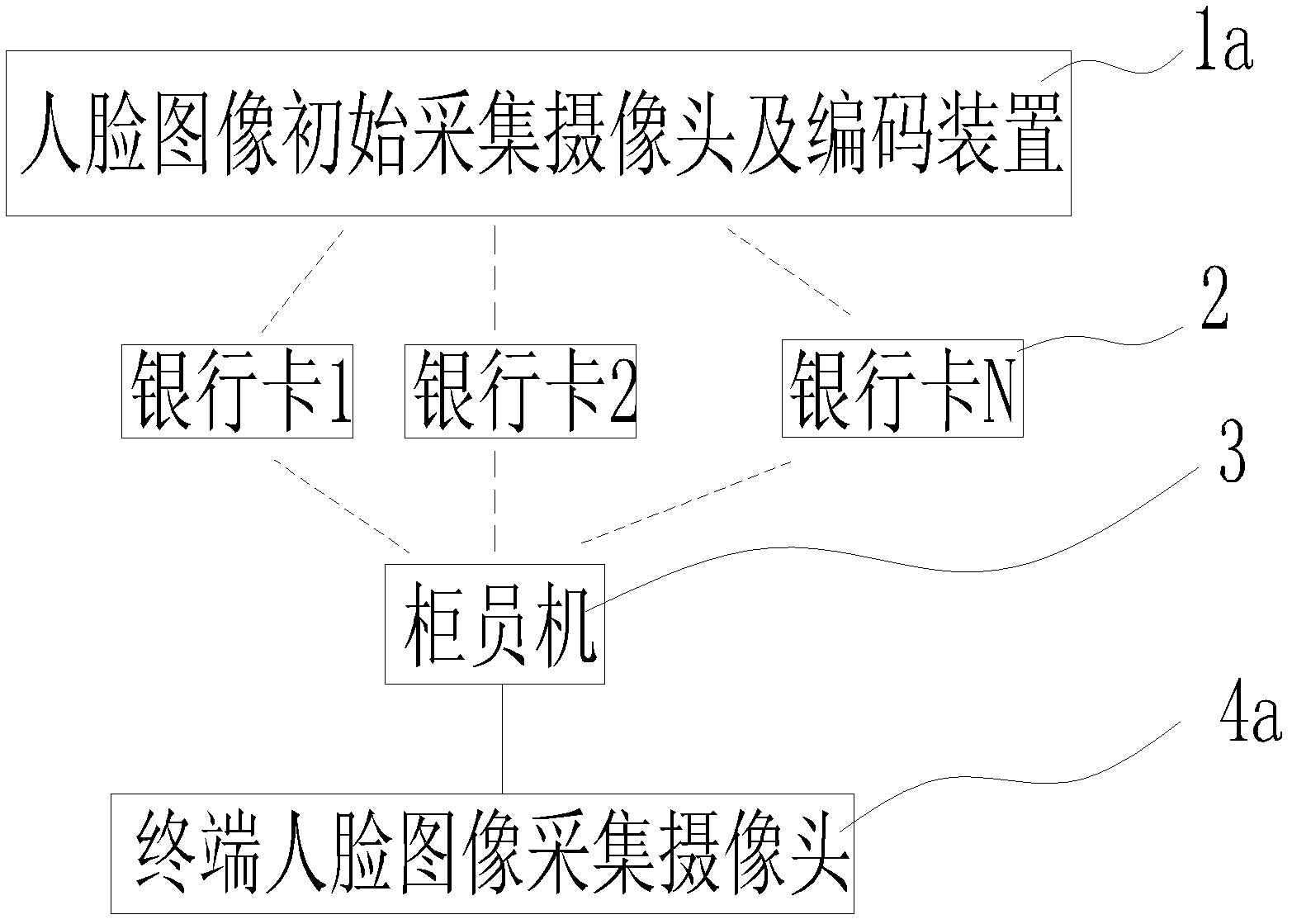
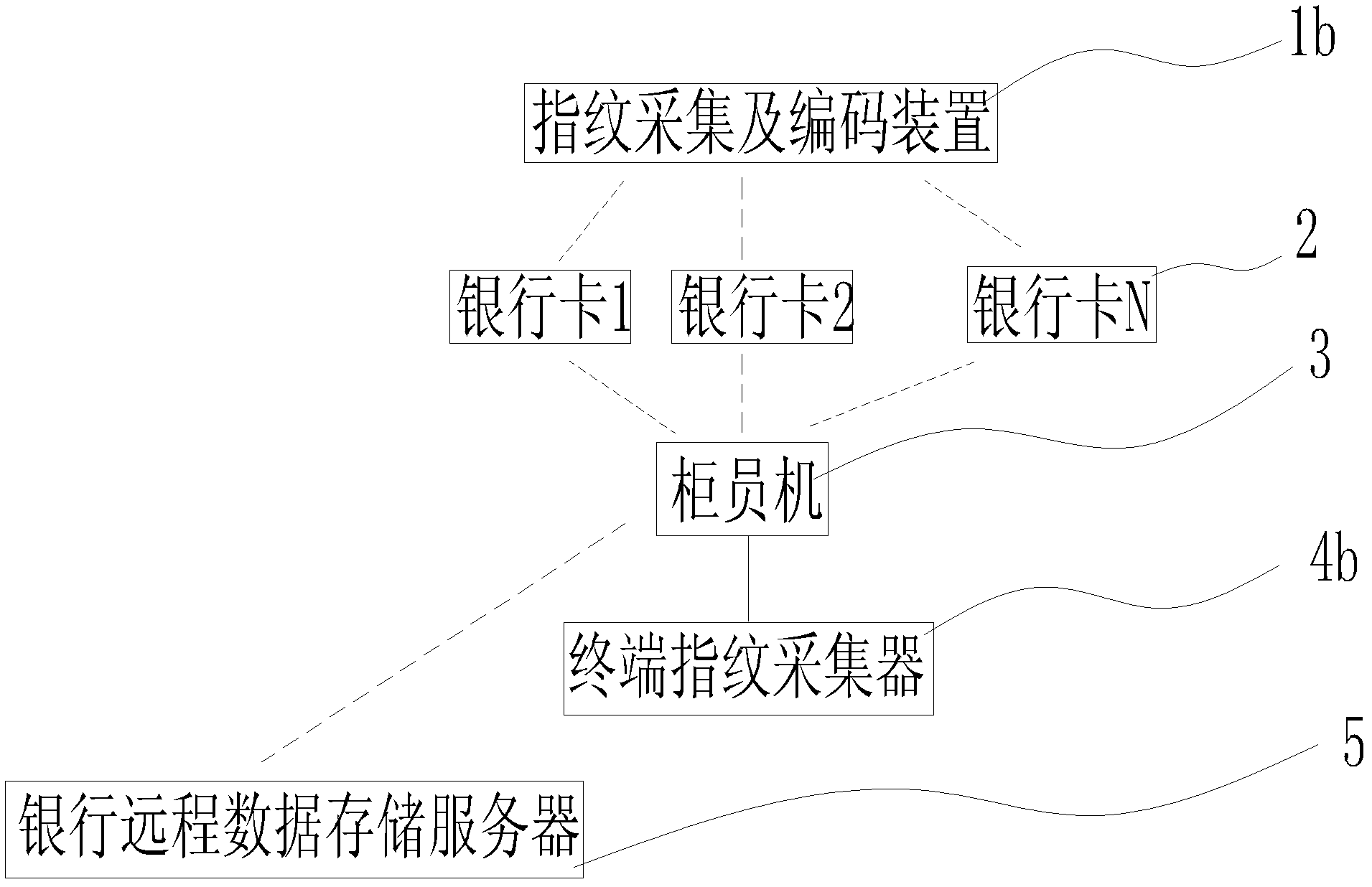
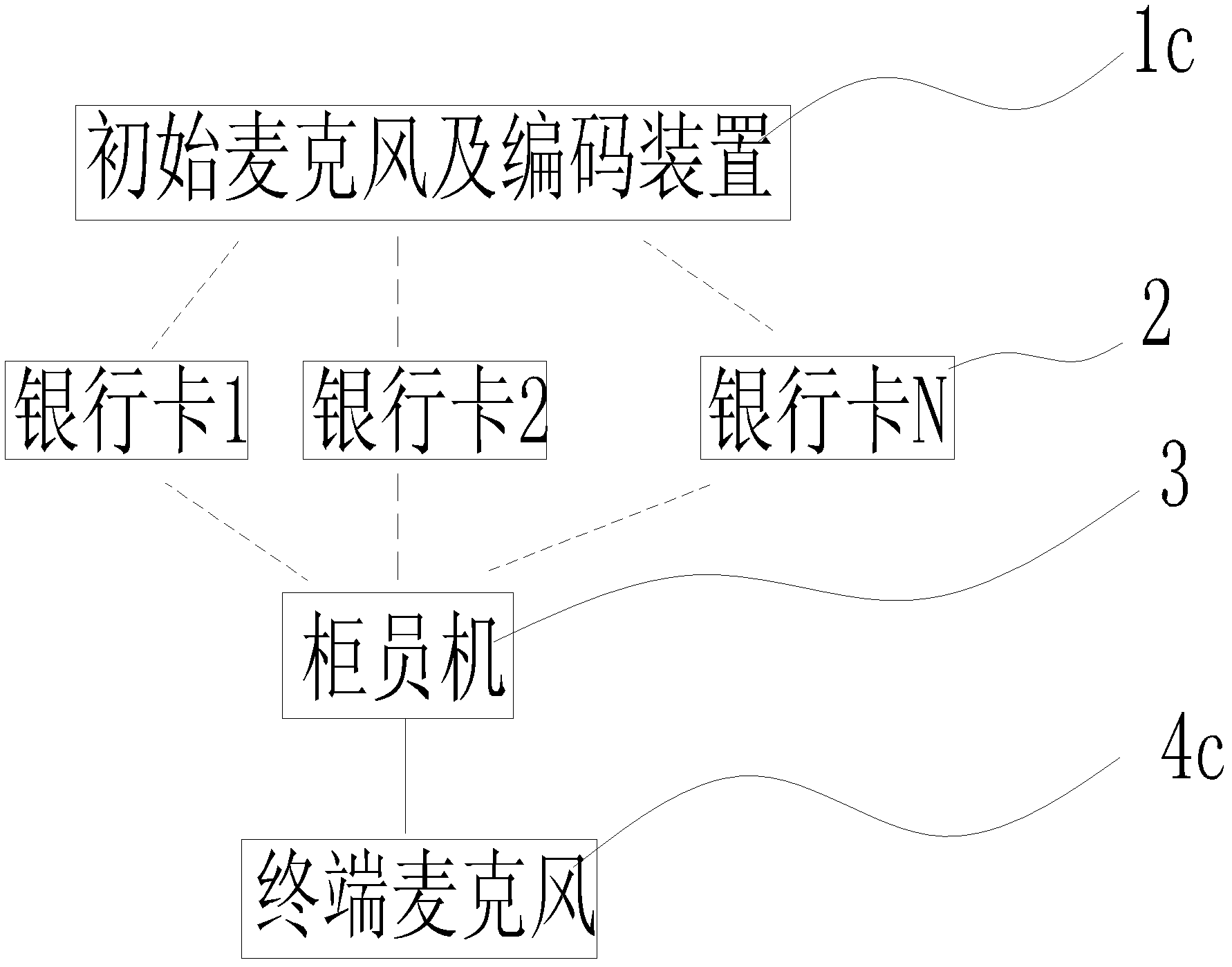
Bank card security system based on human body biological information code and operation method thereof
InactiveCN102915594AGuarantee property securityGuarantee personal safetyComplete banking machinesCoded identity card or credit card actuationHuman bodyElectricity
The invention relates to a bank card system, and discloses a bank card security system based on a human body biological information code. The system comprises at least one biological information initial acquiring and encoding device, at least one bank card used for storing a special human body biological information code, at least one bank card reader device and a terminal biological information acquiring device electrically connected with the bank card reader device. The invention further discloses an operation method comprising the following steps: (1) acquiring and encoding biological information; (2) manufacturing the bank card with the human body biological information code; and (3) identifying people and the card. The advantage that the bank card can be both identified according to a password and human bodies is provided, so that the security of a bank card identification system is comprehensively enhanced; property and personal safety of a card holder can be furthest guaranteed; and the financial security and the social stability are maintained.
Owner:SHENZHEN TRIUMPHANT HI TECH CO LTD
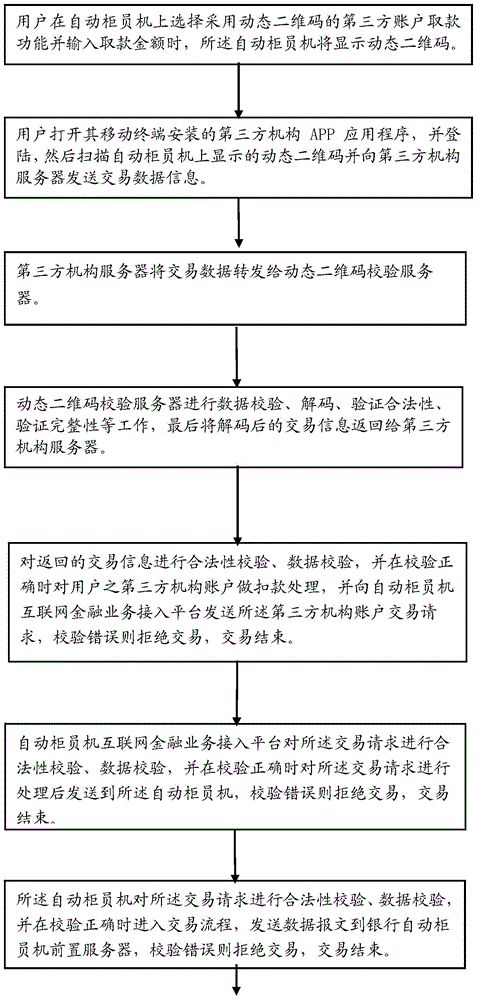
Third-party account ATM (automatic teller machine) withdrawing method and system based on dynamic two-dimension codes
InactiveCN104599408AEnsure safetyEnsure financial securityComplete banking machinesPayment protocolsThird partyData information
The invention relates to the technical field of encoding and decoding two-dimension codes, in particular to a third-party account ATM (automatic teller machine) withdrawing method based on dynamic two-dimension codes. The method comprises the following steps that a user can choose a third-party organization no-card withdrawing function of the dynamic two-dimension codes on an ATM, the ATM can display dynamic two-dimension code images, the user can log in third-party organization APP application programs to scan the dynamic two-dimension codes and send transaction data information to a third-party organization server, the third-party organization server can transmit the transaction data to a dynamic two-dimension code checking server, the dynamic two-dimension data checking server can check data and finally returns the transaction information to the third-party organization server, and the third-party organization server can check the legality of the transaction information and then checks the transaction information again. When the transaction information is not legal, transaction is refused and finishes. Compared with an existing static two-dimension code withdrawing program, a dynamic two-dimension code checking technique utilizes a more complex security mechanism to guarantee financial security of the user.
Owner:ATMU INFORMATION TECH
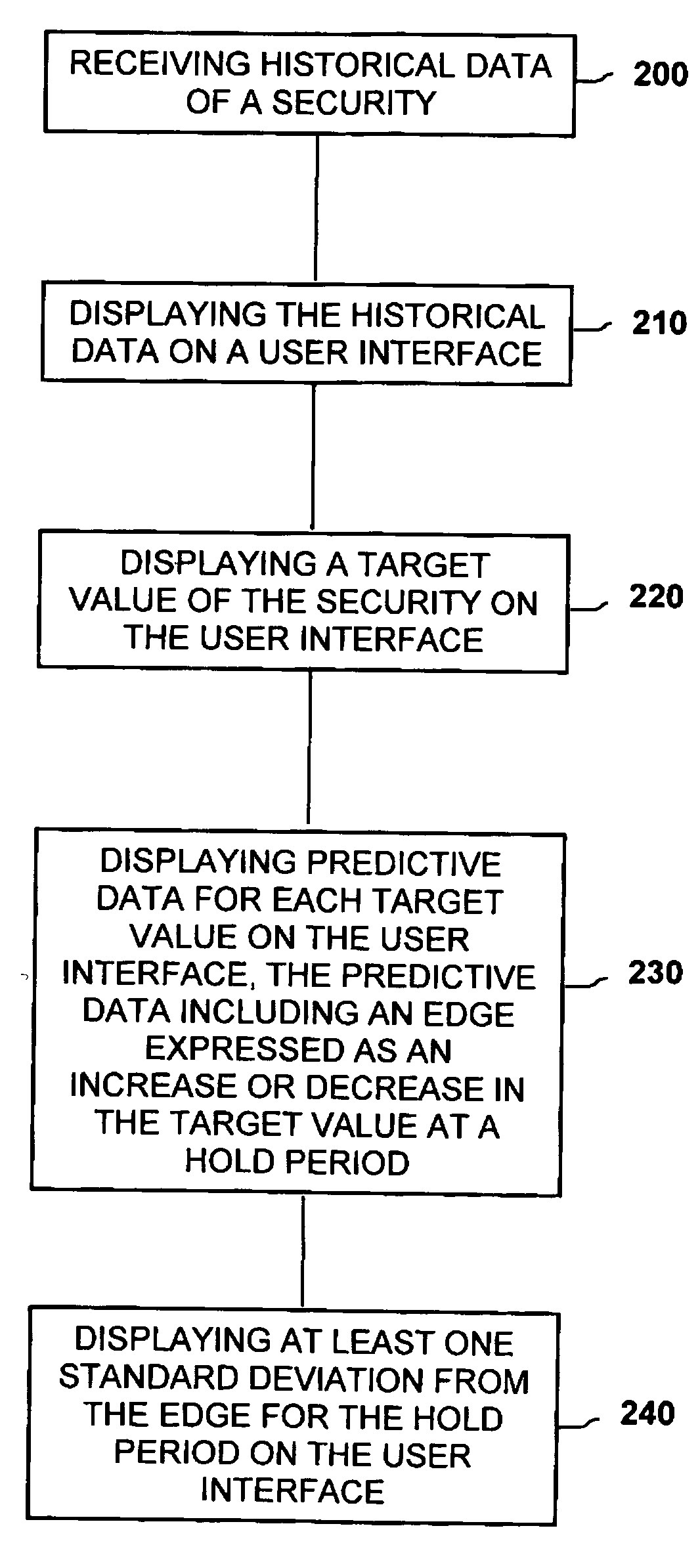
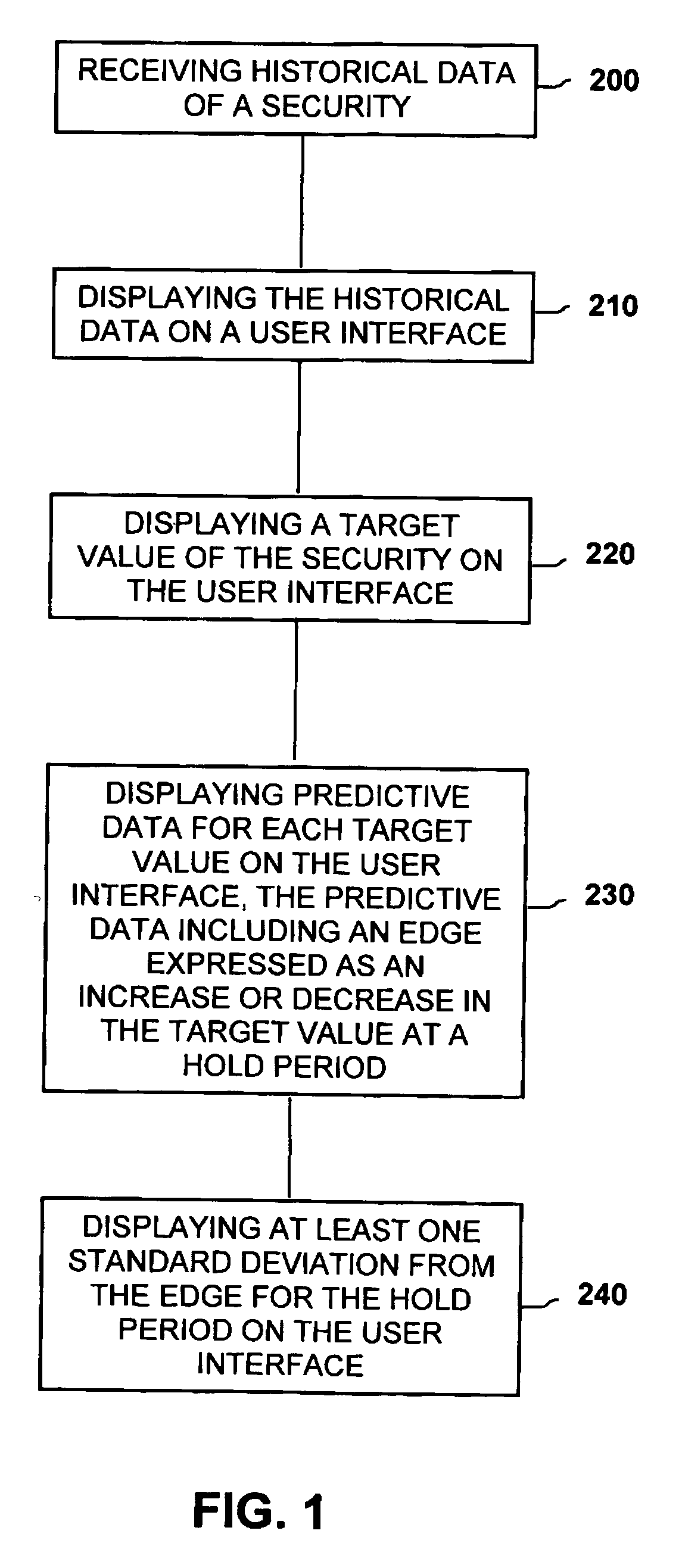
Method of presenting predictive data including standard deviation of financial securities
A method of presenting historical and predictive data of a security comprises the steps of displaying the historical data of the security on a user interface. The method further includes displaying a target value of the security. The method may also include displaying incrementally greater and lesser values expressed as a percentage of the target value of the security. The method further includes displaying predictive data for the current price wherein the predictive data includes an edge expressed as an increase or decrease in the current price predicted to occur at the end of a hold period. The method further includes displaying at least one standard deviation from the edge for the hold period on the user interface.
Owner:CONNORS RES +1
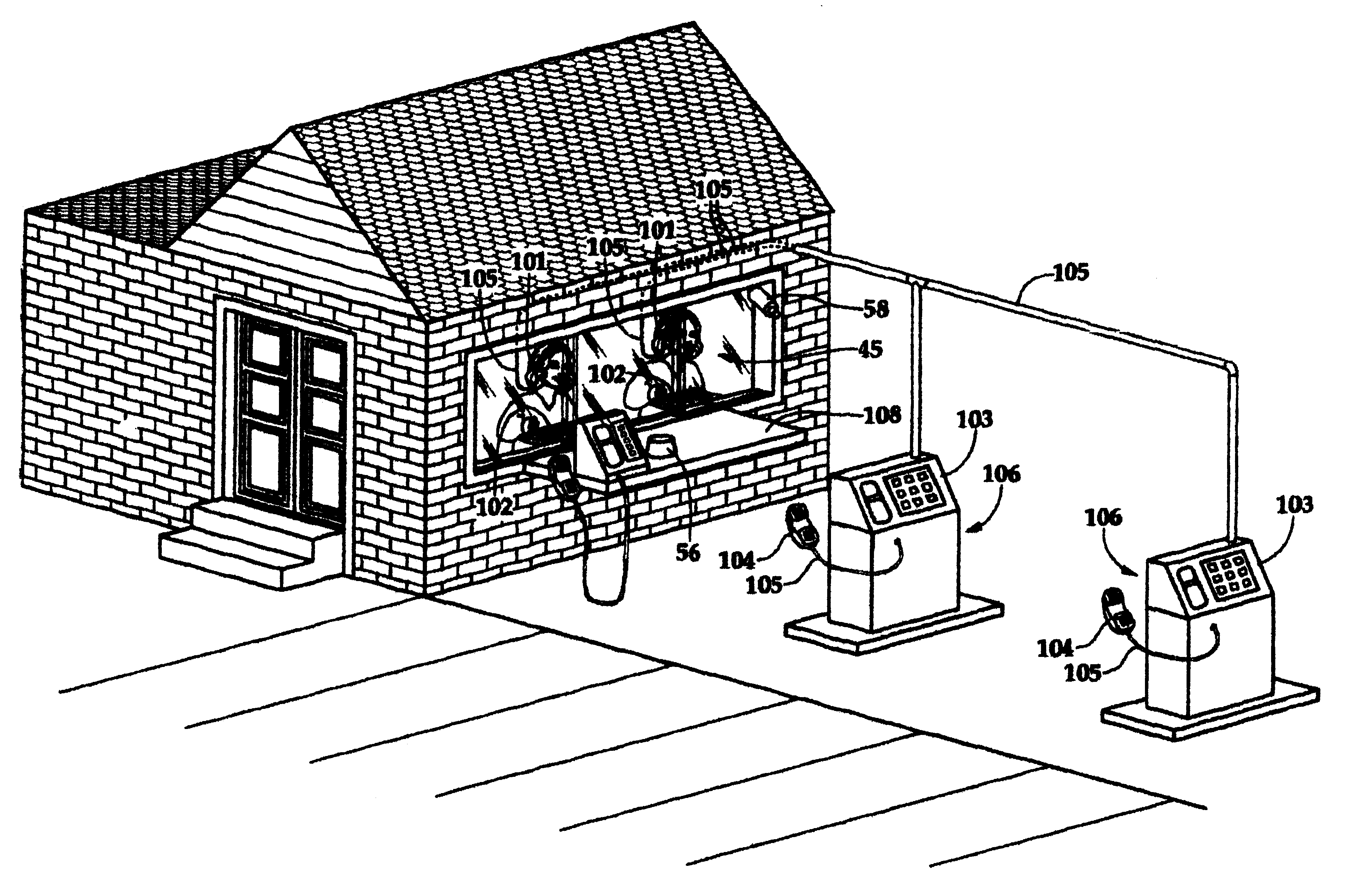
Lobby banking financial security transaction chamber
InactiveUS6655302B1Improve security levelLip reading of customer's financial transaction is also eliminatedComplete banking machinesSafety transaction partitionBank tellerFinancial security
A primary communication channel for drive-in customers performing financial transactions with bank teller while customers are in their cars from the drive-through lanes. This telecommunication system is a conduit secured line telephone receiver for each separate lane and is interconnected with corresponding headsets. The total design prevents cross-talk, amplified overhead conversations to other customers in their cars or to persons walking perimeter of drive-through banking areas. Each customer is provided with a complete primary communication channel for financial transactions Preventions of customers being identified as potential victims of financial exploitations through car tag associations with amplified conversations. Improved apprehension of person attempting to rob bank from bank teller's transaction window of drive-in area.
Owner:ROSS JUANDE
Secure financial terminal firmware programming method and financial terminal
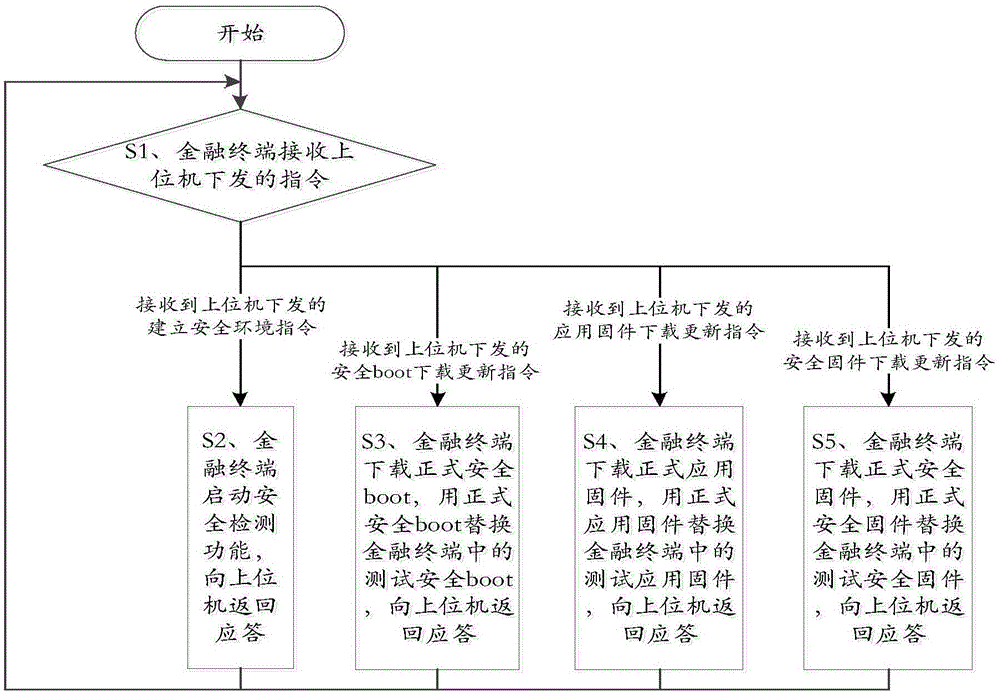
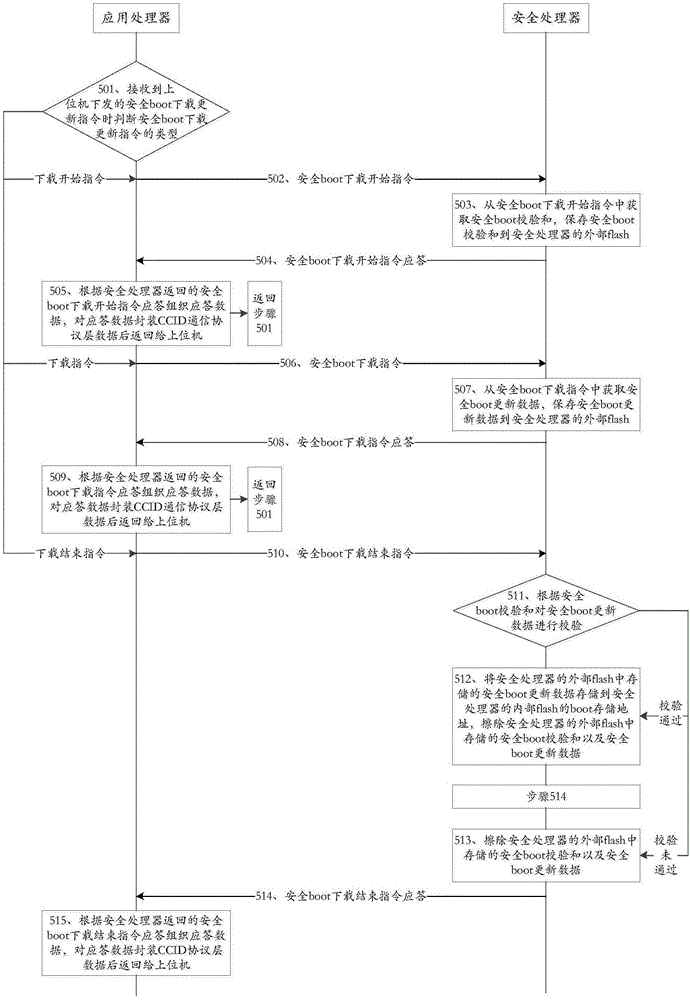
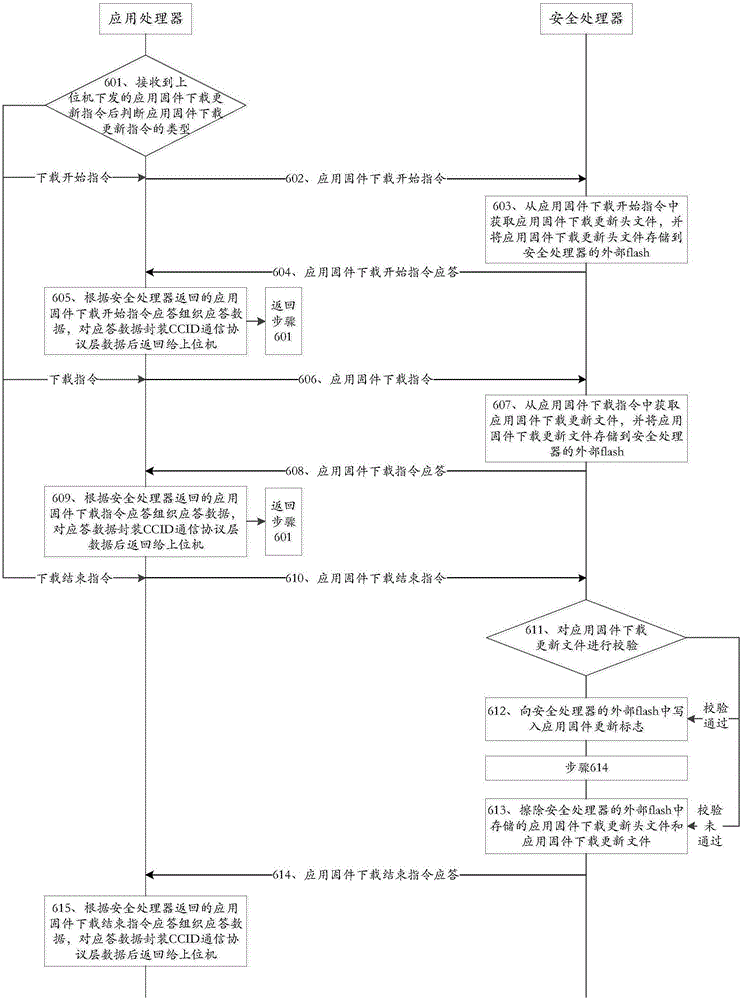
ActiveCN105159707AAvoid safety hazardsImprove securityProgram loading/initiatingFinancial securityProgramming method
The present invention discloses a secure financial terminal firmware programming method and a financial terminal and belongs to the field of financial security. The method comprises: the financial terminal, according to instructions issued by an upper computer, completes establishment of a security environment, downloading and update of a secure boot, downloading and update of application firmware and downloading and update of secure firmware. The financial terminal comprises a communication module, a security environment establishment module, a secure boot downloading and updating module, an application firmware downloading and updating module and a secure firmware downloading and updating module. The secure financial terminal firmware programming method and the financial terminal have the beneficial effects that potential safety hazards of an existing financial terminal firmware programming method can be avoided and safety of a financial terminal product can be improved.
Owner:FEITIAN TECHNOLOGIES
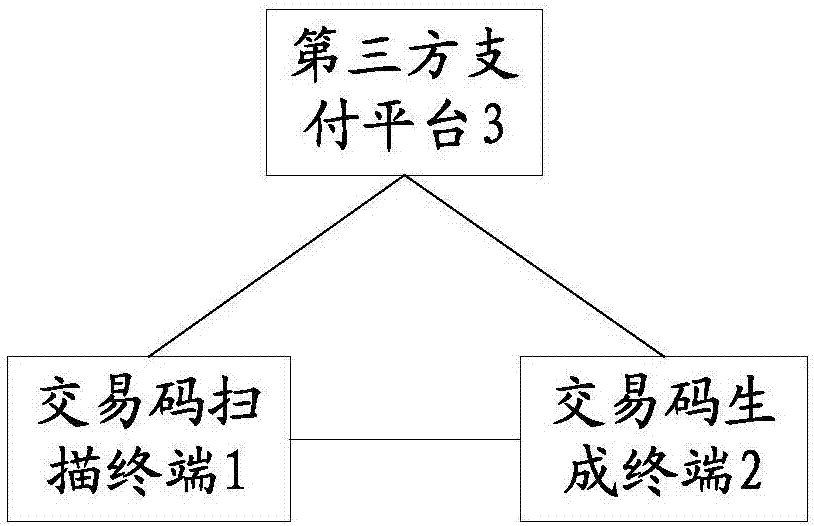
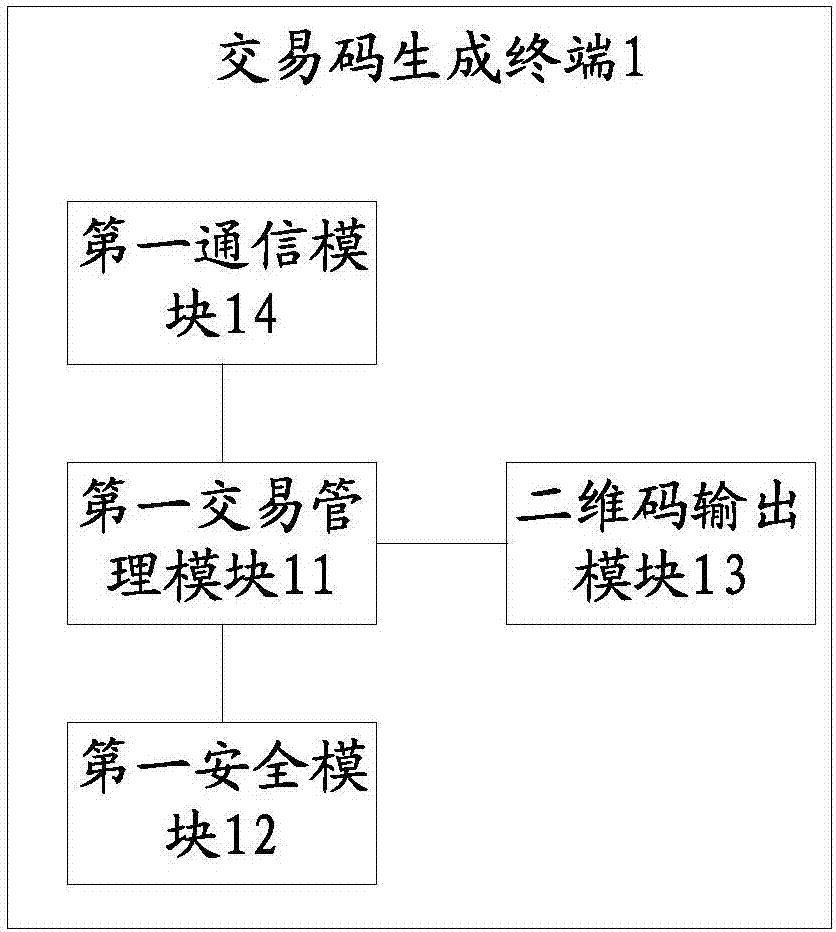
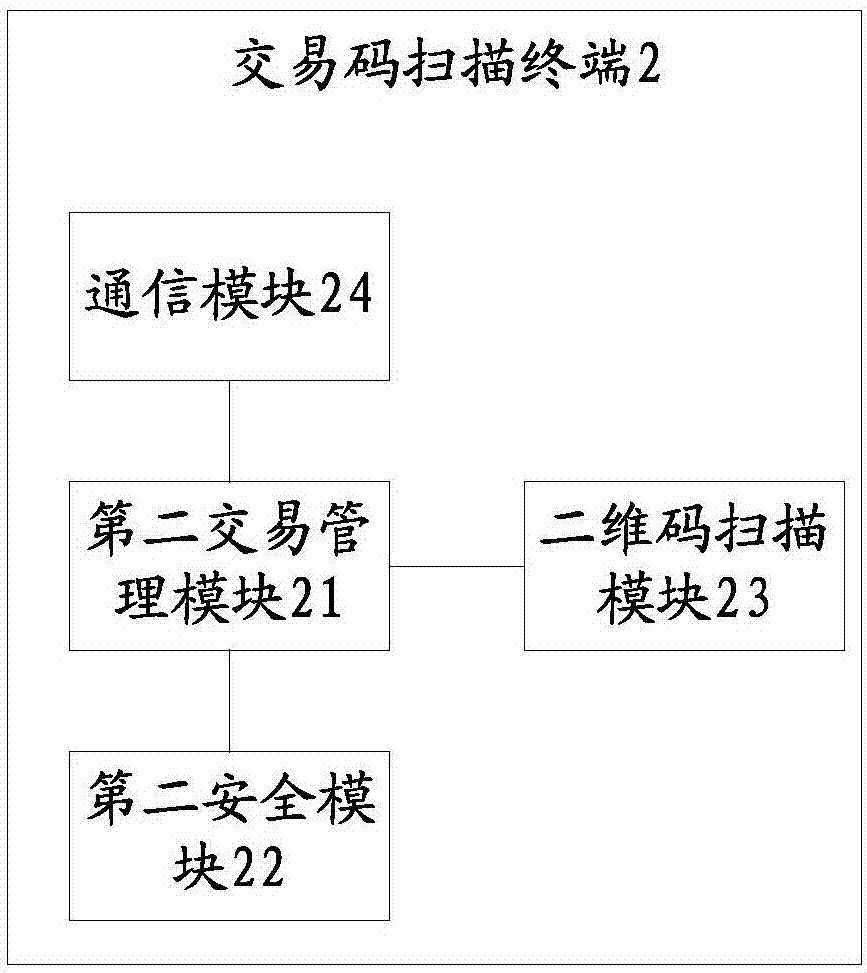
Transaction code generation terminal, transaction code scanning terminal and transaction code generation and transaction method
PendingCN107194695AEnsure safetyImprove satisfactionProtocol authorisationPayments involving neutral partyPaymentThird party
The invention provides a transaction code generation terminal, a transaction code scanning terminal and a transaction code generation and transaction method. According to the method, security modules acquired from a credible third party are arranged on at least one of the transaction code generation terminal and the transaction code scanning terminal, wherein all the arranged security modules are financial security management hardware chips; and in a transaction process, digital signing can be performed on a transaction request through the security modules, and a subsequent transaction processing process cannot be performed unless a payment platform corresponding to the credible third party authenticates corresponding digital signatures. That is to say, both parties in a transaction utilize the security chips to perform digital signing, so that two-dimensional code payment has the security of POS payment and the convenience of mobile two-dimensional code payment at the same time, the risk and the potential safety hazard in the transaction process are lowered as much as possible, and the satisfaction of user experience is improved.
Owner:NATIONZ TECH INC
Face recognition method based on kernel nearest subspace
InactiveCN101916369AHave non-linear featuresPreserve globalityCharacter and pattern recognitionDimensionality reductionCharacteristic space
The invention discloses a face recognition method based on kernel nearest subspace, mainly solving the problem that the non-linear characteristics of the data can not be subjected to linear expression in the existing methods. The method comprises the following steps: (1) mapping the training sample matrixes and the testing samples to the non-linear characteristic space by Mercer kernel experience, then carrying out dimension reduction and normalization on the mapped samples and then extracting each class of training samples undergoing dimension reduction; (2) solving the sample reconstruction coefficient between the normalized testing samples and each class of training sample matrixes and reconstructing the original testing samples; and (3) obtaining the residual errors between various classes of reconstructed samples and the original testing samples and taking the class of the subscript corresponding to the minimum in the residual errors as the class of the testing samples. The method improves the precision in face recognition application, simultaneously expands the application range to the low-dimensional samples so as to further have universality and can be used for supervision and protection of public security, information security and financial security.
Owner:XIDIAN UNIV
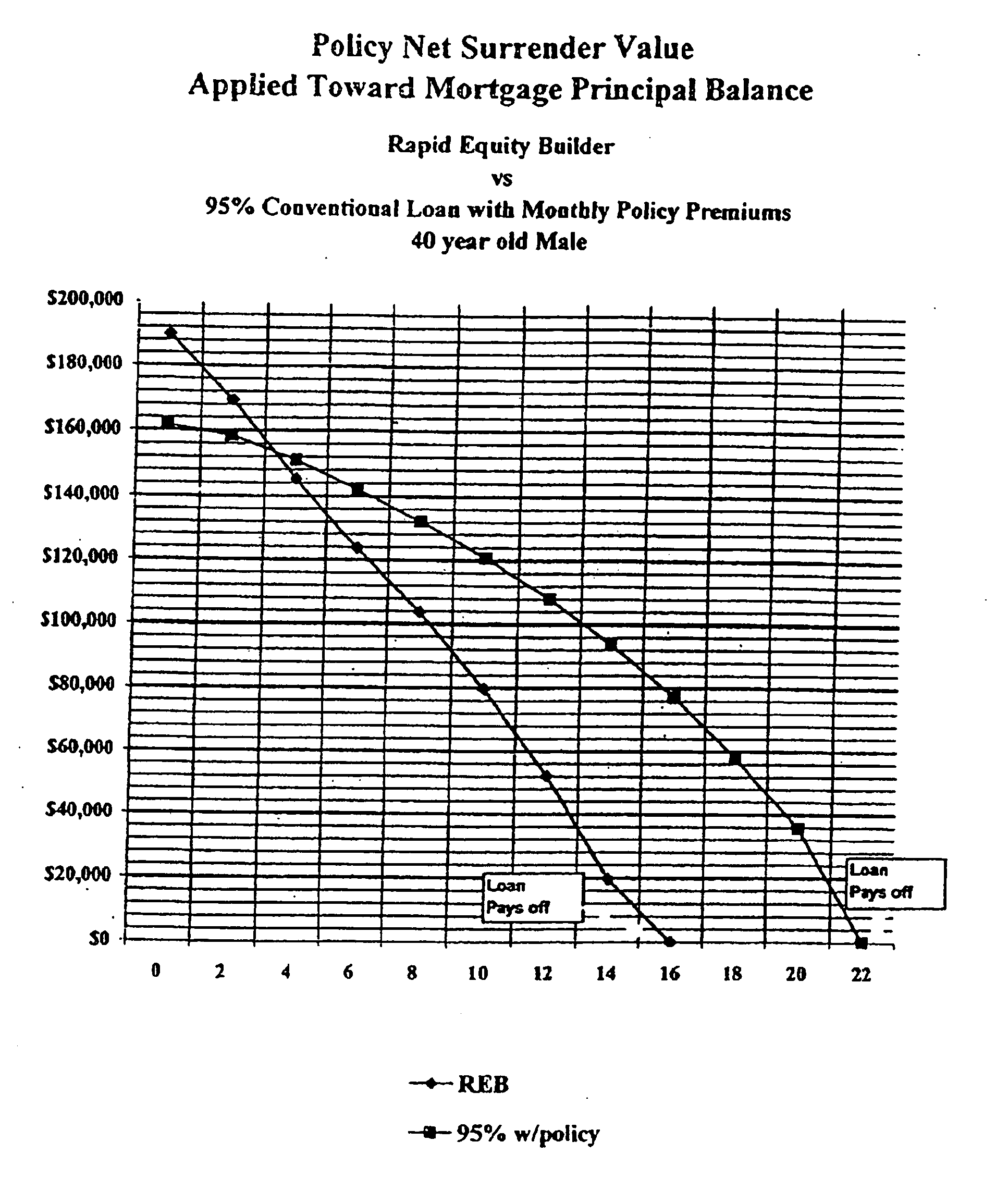
Mortgage financing system
InactiveUS20060149663A1Reduce riskCreates financially healthy borrowersFinancePaymentFinancial security
The present invention is a method for providing mortgage financing to a borrower while additionally creating the opportunity for the borrower to invest in their long and short-term financial security. In real estate purchase, a mortgage is extended for greater than the real estate purchase price. The surplus amount is applied against at least one investment vehicle, so that after the periodic payments are completed, the borrower has equity in real estate and an interest in at least one investment vehicle. The investment vehicle provides security for the mortgage.
Owner:NICHOLS EVELYN
Note intelligent identifier and note anti-counterfeiting method based on multispectral characteristic
InactiveCN102568079ACurb counterfeitingAvoid false detectionPaper-money testing devicesFinancial securityTwo step
The invention discloses a note intelligent identifier and a note anti-counterfeiting method based on a multispectral characteristic. The note intelligent identifier comprises a reading and writing module and an electronic tag, wherein the electronic tag is used for storing the multispectral characteristic or reading the multispectral characteristic from the electronic tag. The multispectral characteristic of a note is extracted and then is compared with the multispectral characteristic stored in the electronic tag to identify the note. The note anti-counterfeiting method is implemented through the note intelligent identifier and comprises two steps of storing the multispectral characteristic in the electronic tag when the note is signed, and identifying the note with the note intelligent identifier when the note is exchanged. Identification processing and anti-counterfeiting processing for the note are performed by the note intelligent identifier and the note anti-counterfeiting method, and the acquired multispectral characteristic is stored in the electronic tag and transmitted by the electronic tag. The identifier can be used conveniently, simply, quickly and safely and has great significance for the national financial security.
Owner:中钞实业有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com