Secure financial terminal firmware programming method and financial terminal
A financial terminal and security firmware technology, applied in the direction of program loading/starting, program control devices, etc., can solve the problems of security firmware code errors or misjudgments, security problems, and re-establishment of security environment, so as to avoid potential security risks and improve security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
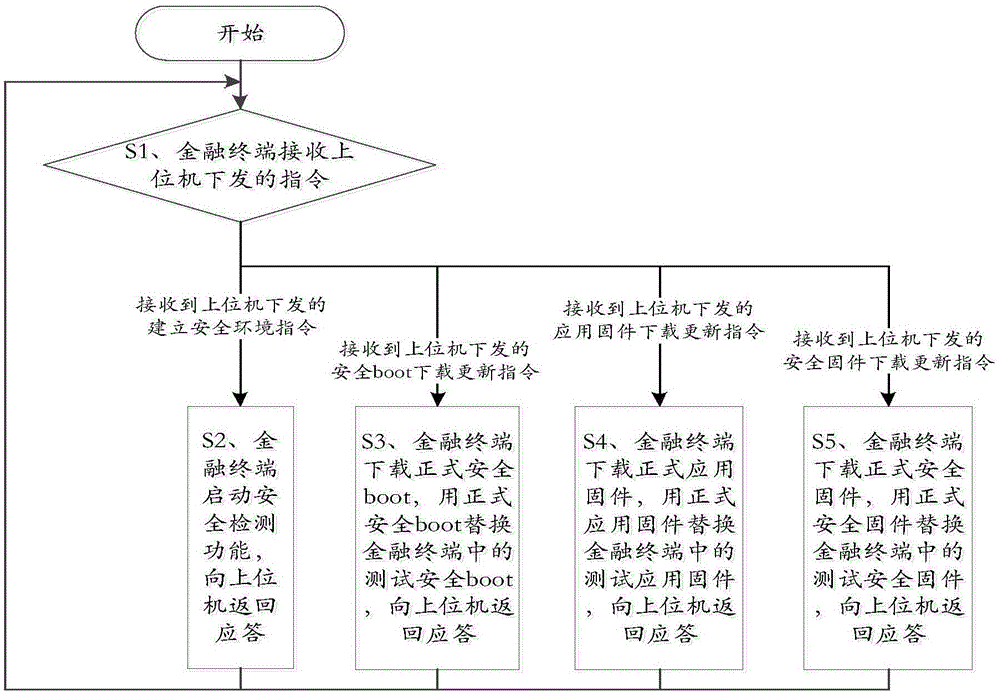
[0055] This embodiment provides a safe financial terminal firmware programming method, such as figure 1 shown, including:
[0056] Step S1. The financial terminal receives the instruction issued by the host computer. When receiving the instruction to establish a safe environment issued by the host computer, execute step S2. When receiving the secure boot download update instruction issued by the host computer, execute step S3. When receiving Step S4 is executed when the application firmware download and update instruction issued by the host computer is received, and step S5 is executed when the secure firmware download update instruction issued by the host computer is received;
[0057] Specifically, in this embodiment, the host computer encapsulates the instruction to be sent into a standard CCID communication instruction and sends it to the financial terminal.
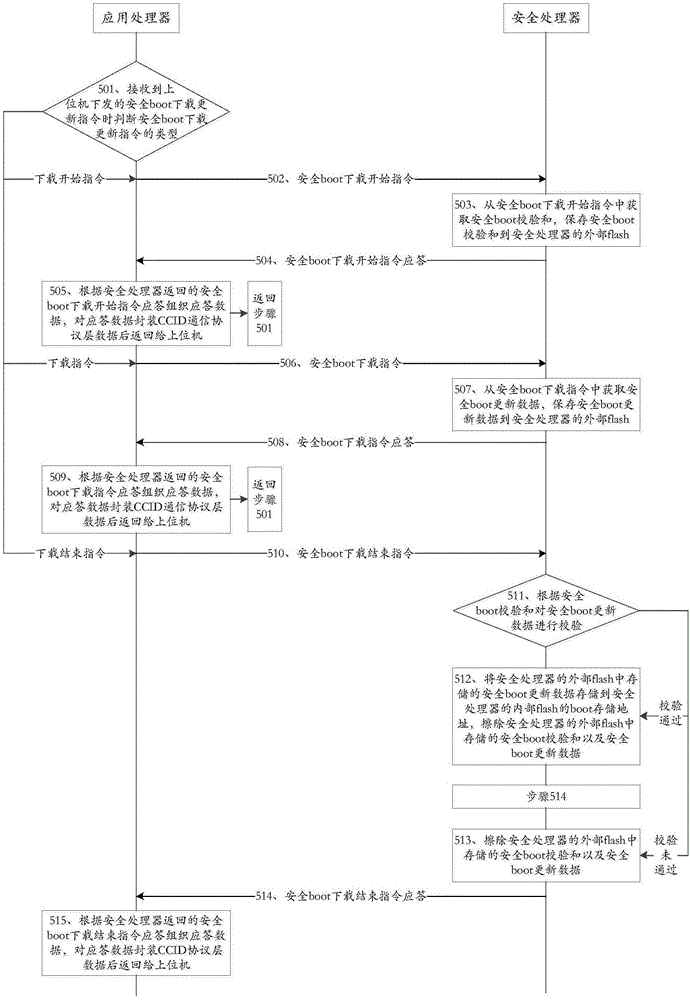
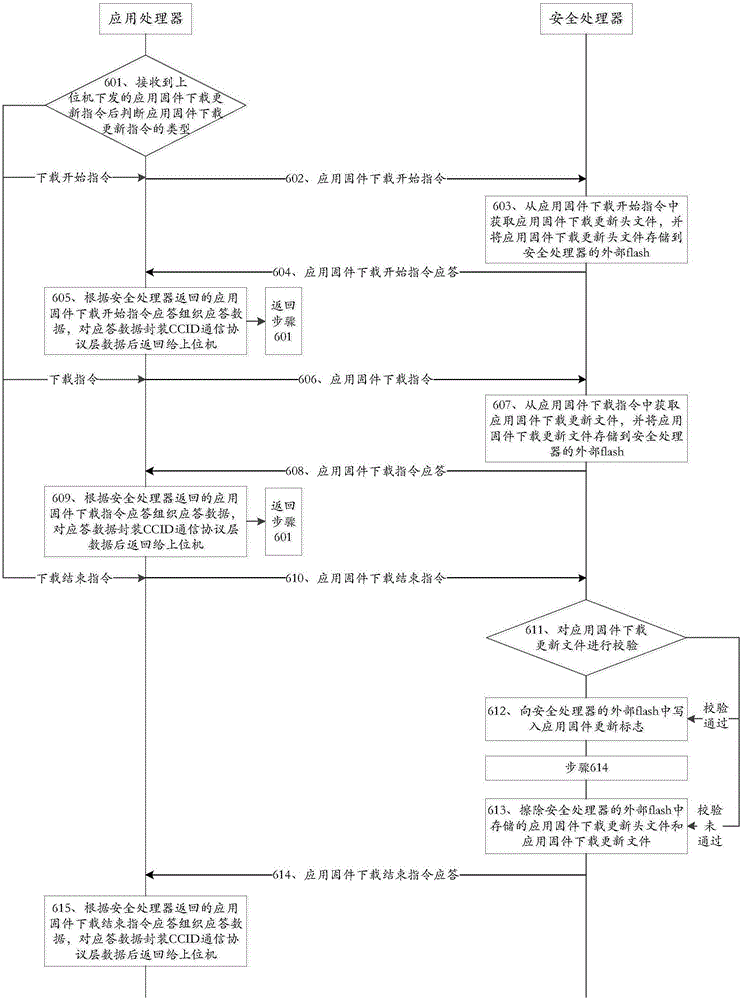
[0058] Step S2, the financial terminal starts the safety detection function, returns a response to the upper comp...
Embodiment 2
[0225] This embodiment provides a financial terminal, such as Figure 7 As shown, it specifically includes: a communication module 11, a safe environment establishment module 12, a storage module 13, a safe boot download and update module 14, an application firmware download and update module 15 and a secure firmware download and update module 16, and the specific functions of the above modules are as follows:
[0226] The communication module 11 is used to receive the instructions for establishing a safe environment, the download and update instructions for safe boot, the download and update instructions for application firmware, and the download and update instructions for secure firmware issued by the host computer; 14. When the application firmware download and update module 15 and the secure firmware download and update module 16 are finished running, a response is returned to the upper computer;
[0227] The safe environment establishment module 12 is used for starting t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com