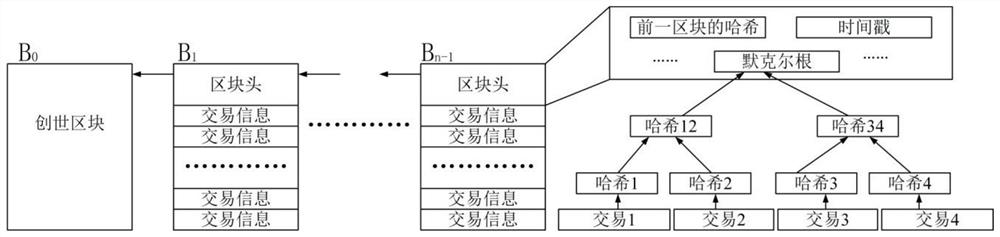
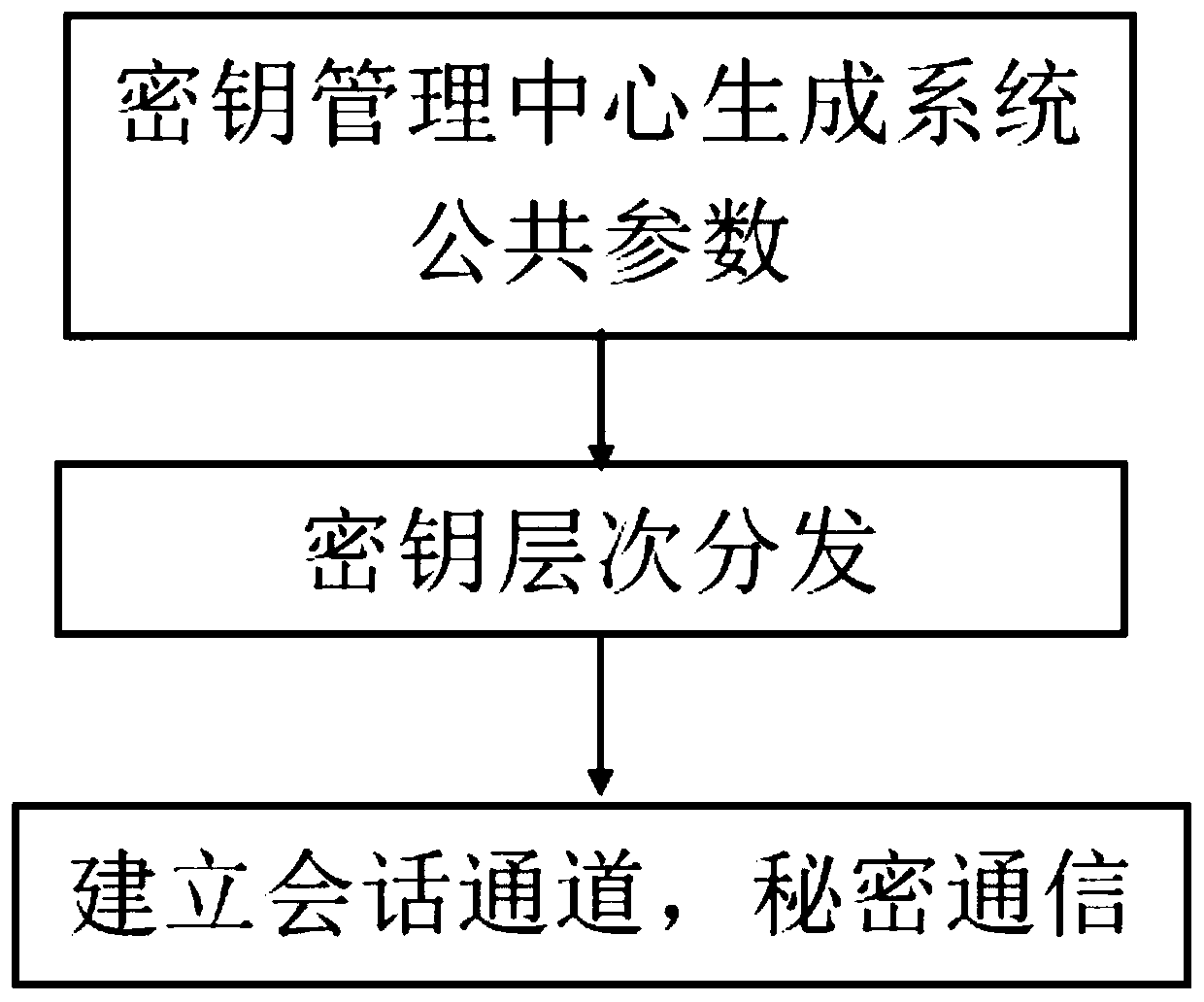
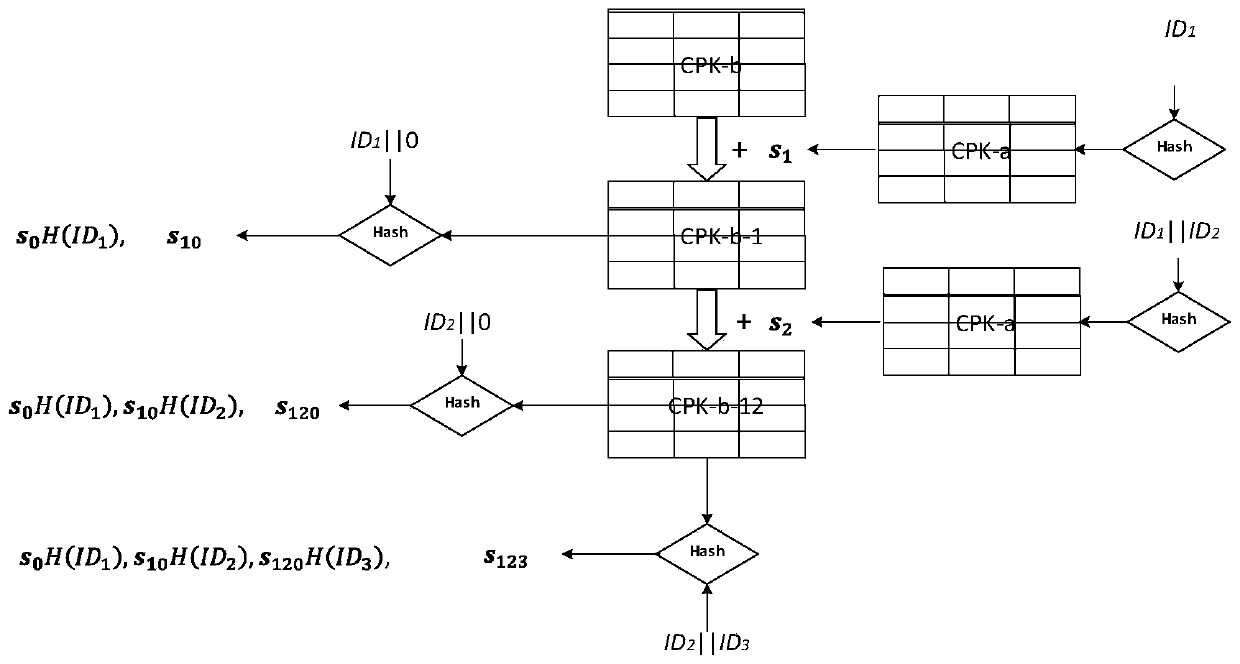
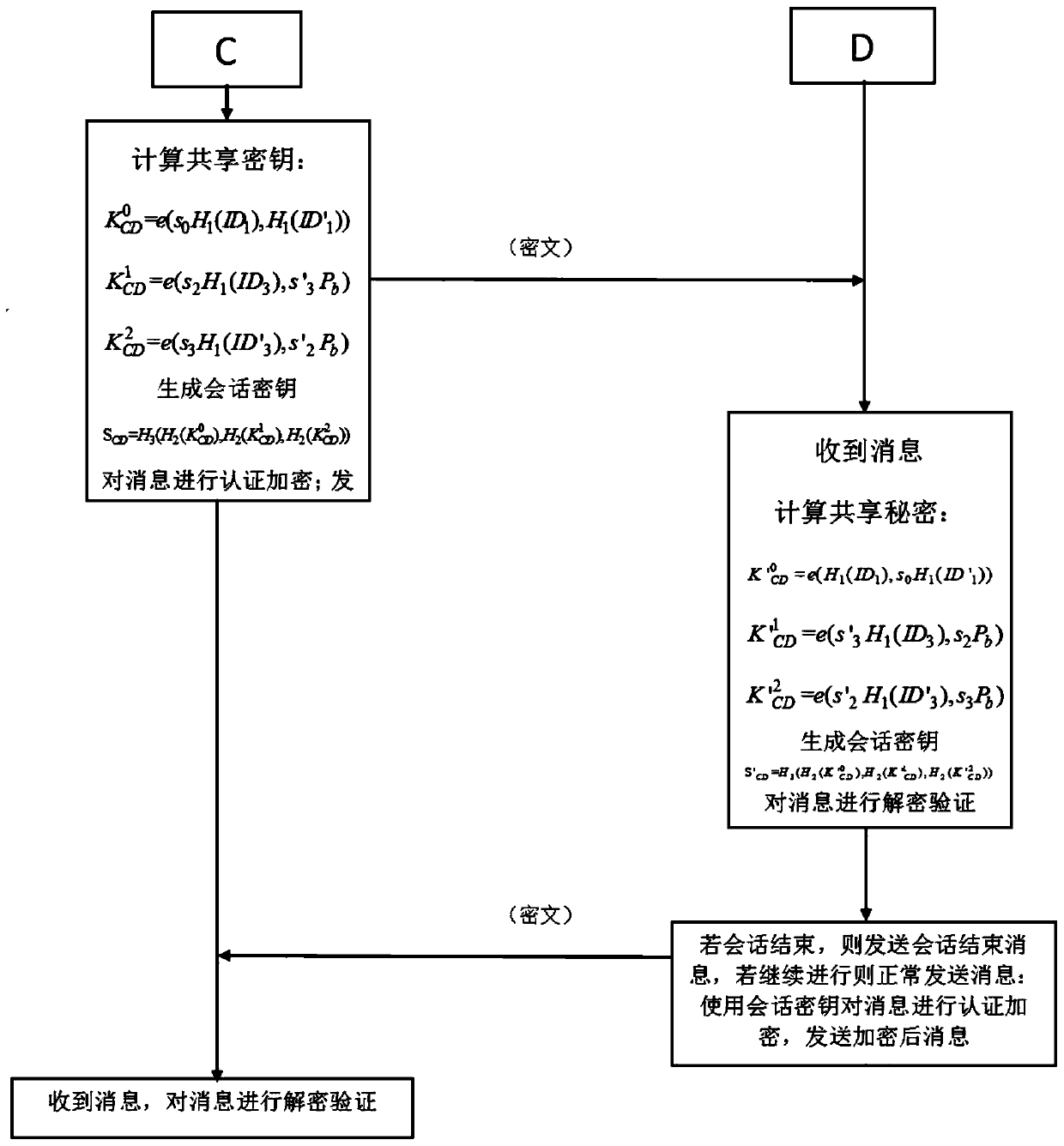
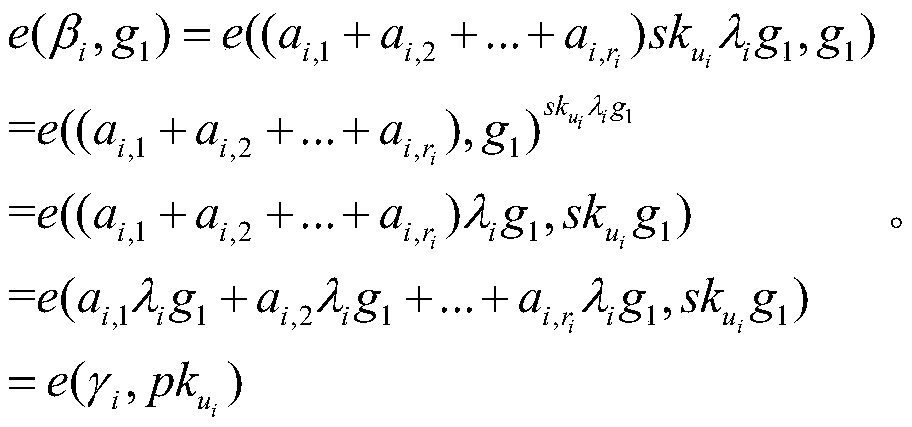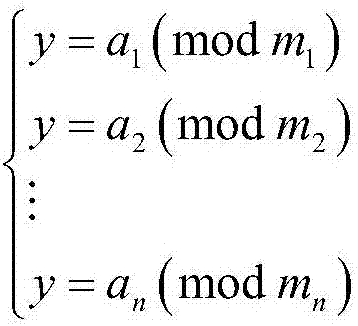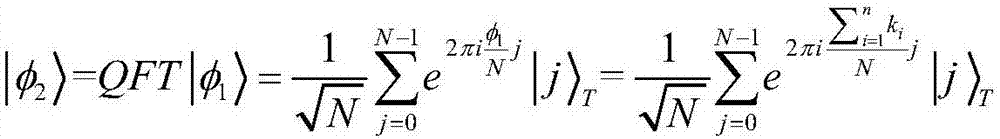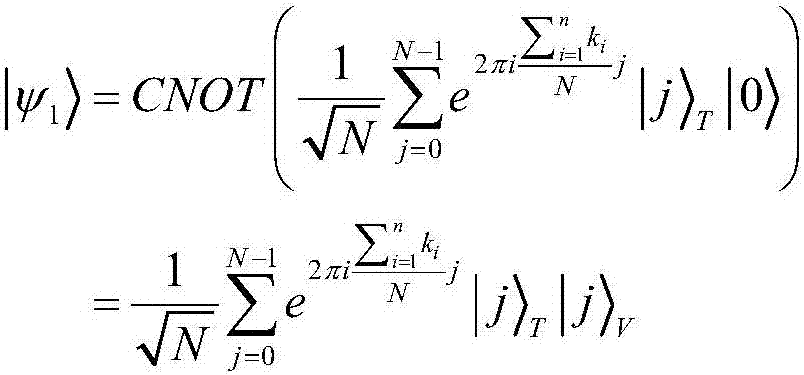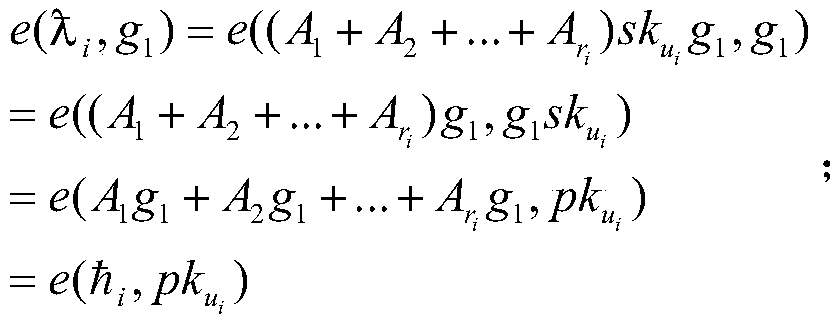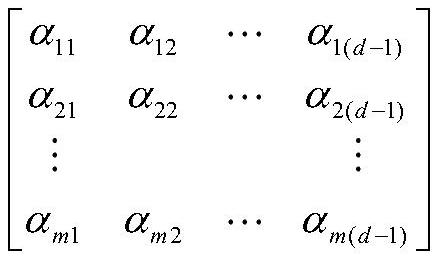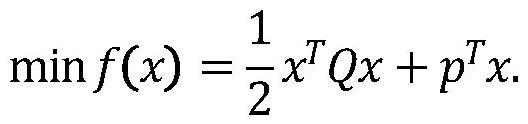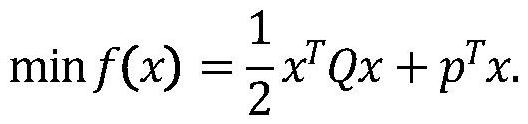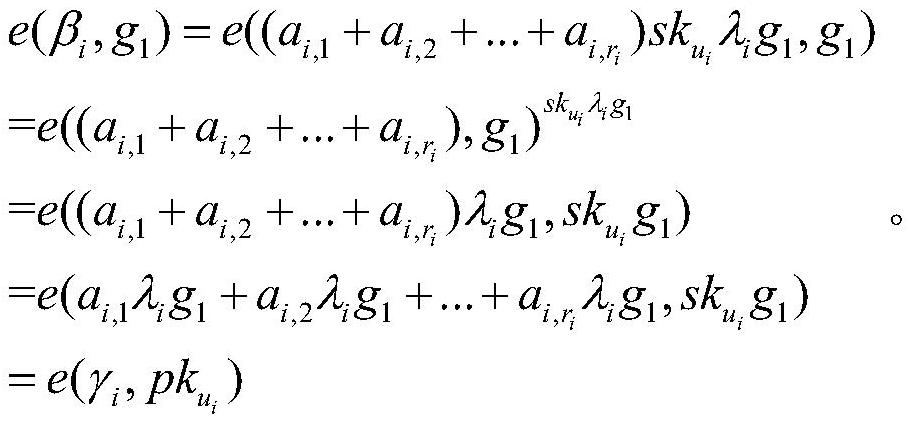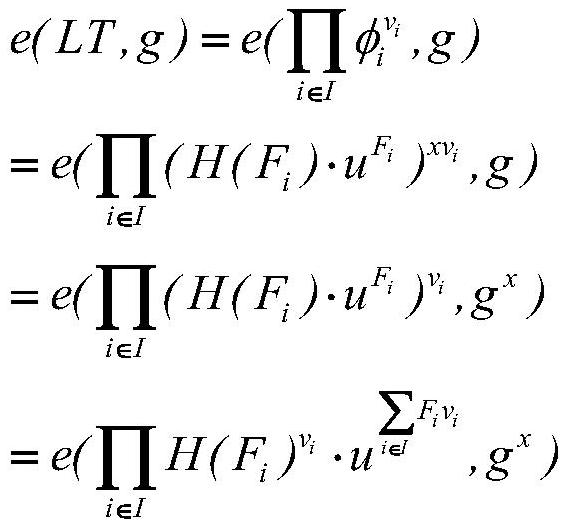Patents
Literature
49results about How to "Avoid Collusion Attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Blockchain-based safety excitation method and system in crowd sensing application
ActiveCN108055119AAvoid Collusion AttacksAvoid safety hazardsCryptographic attack countermeasuresThird partySensing applications
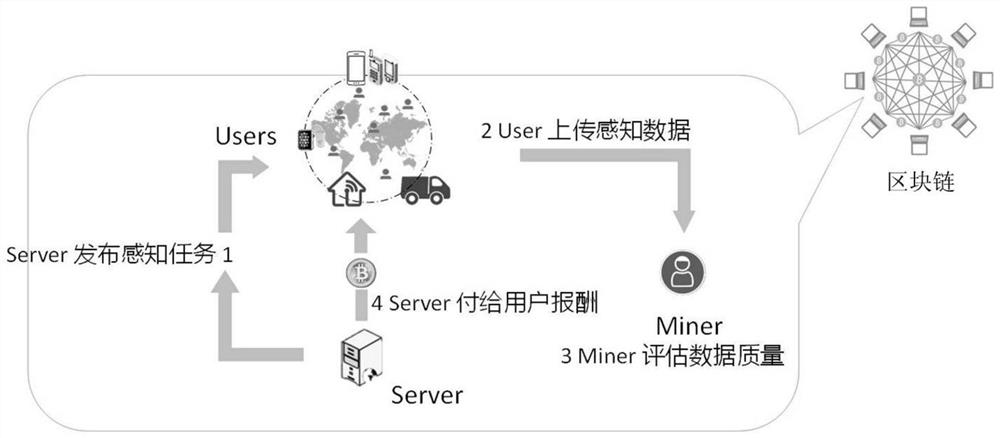
The invention relates to a blockchain-based safety excitation method and system in a crowd sensing application. In the method, a user side and a server side, as both transaction parties of a blockchain, carry out transaction. The method comprises the following steps that: 1, a server releases a perception task to the user side; 2, after executing and completing the perception task, the user side uploads perception data to the server; 3, a miner in the blockchain verifies quality of the perception data and sends the quality of the perception data to the server; and 4, the server pays the remuneration to the user side according to the quality of the perception data. Further, after obtaining the quality of the perception data, the miner quantifies an effective contribution of the quality of the perception data by utilizing a mutual information principle and sends the effective contribution to the server, and then the server gives the corresponding remuneration to the user side according to the effective contribution. According to the invention, safety excitation in the crowd sensing application is implemented by adopting a distributed architecture of blockchain safety, a collusion attack initiated by a perception platform can be effectively prevented, and potential safety hazards which a credible third party faces are overcome.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
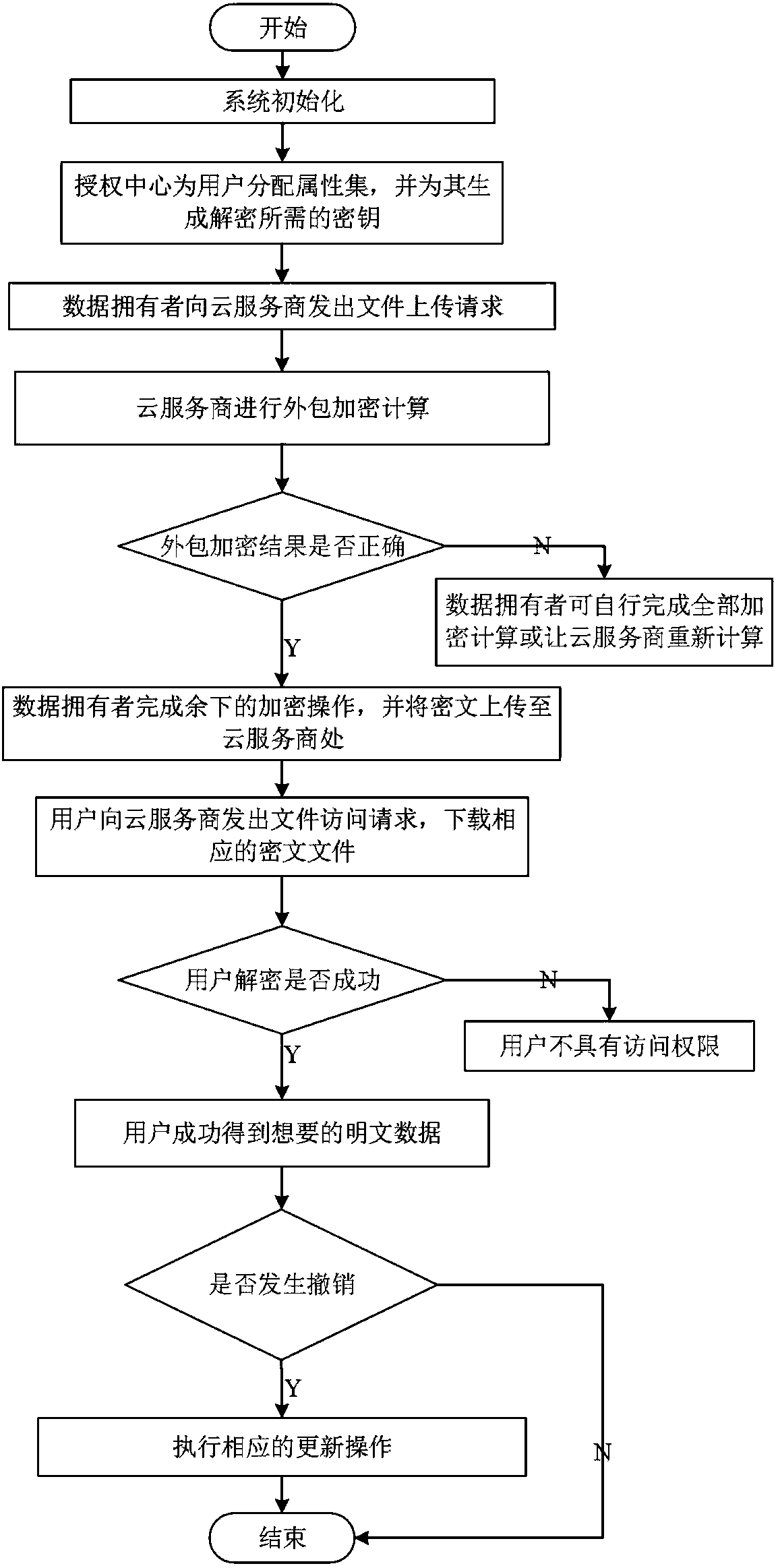
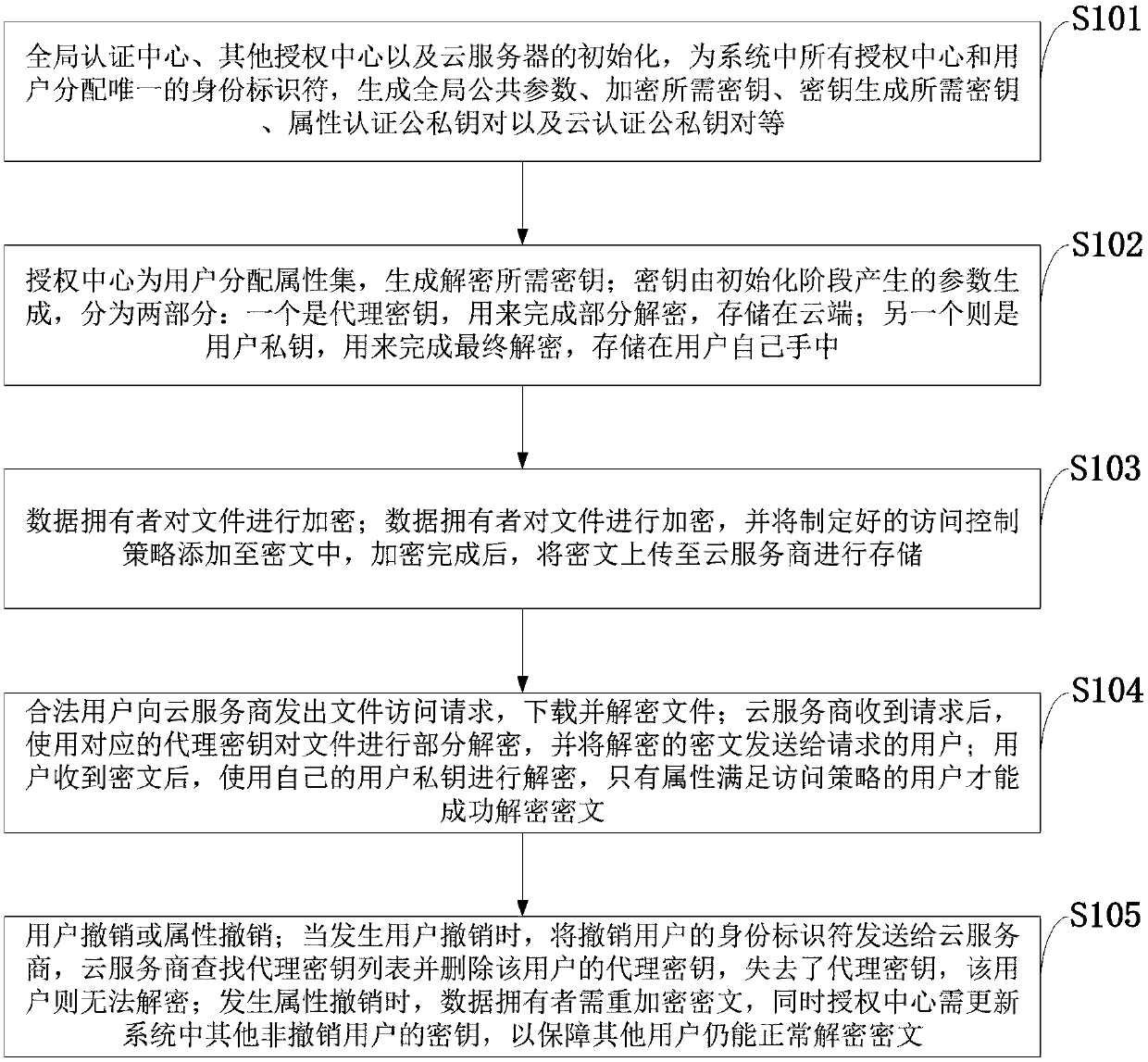
Cancellation-supported outsourcing verifiable multi-authorization center access control method, and cloud server
ActiveCN108390876ARich domainImprove efficiencyKey distribution for secure communicationUser PrivilegeCloud storage
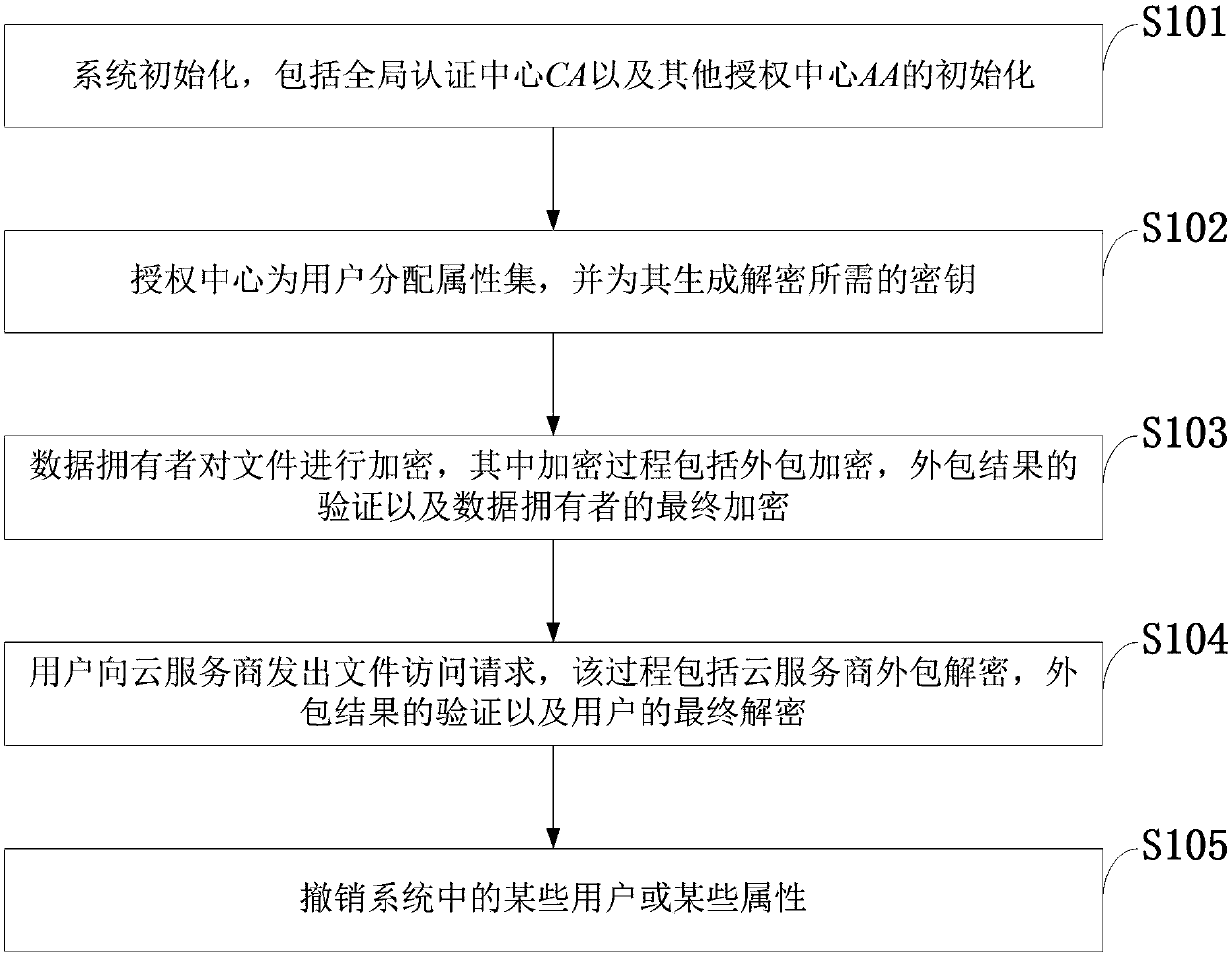
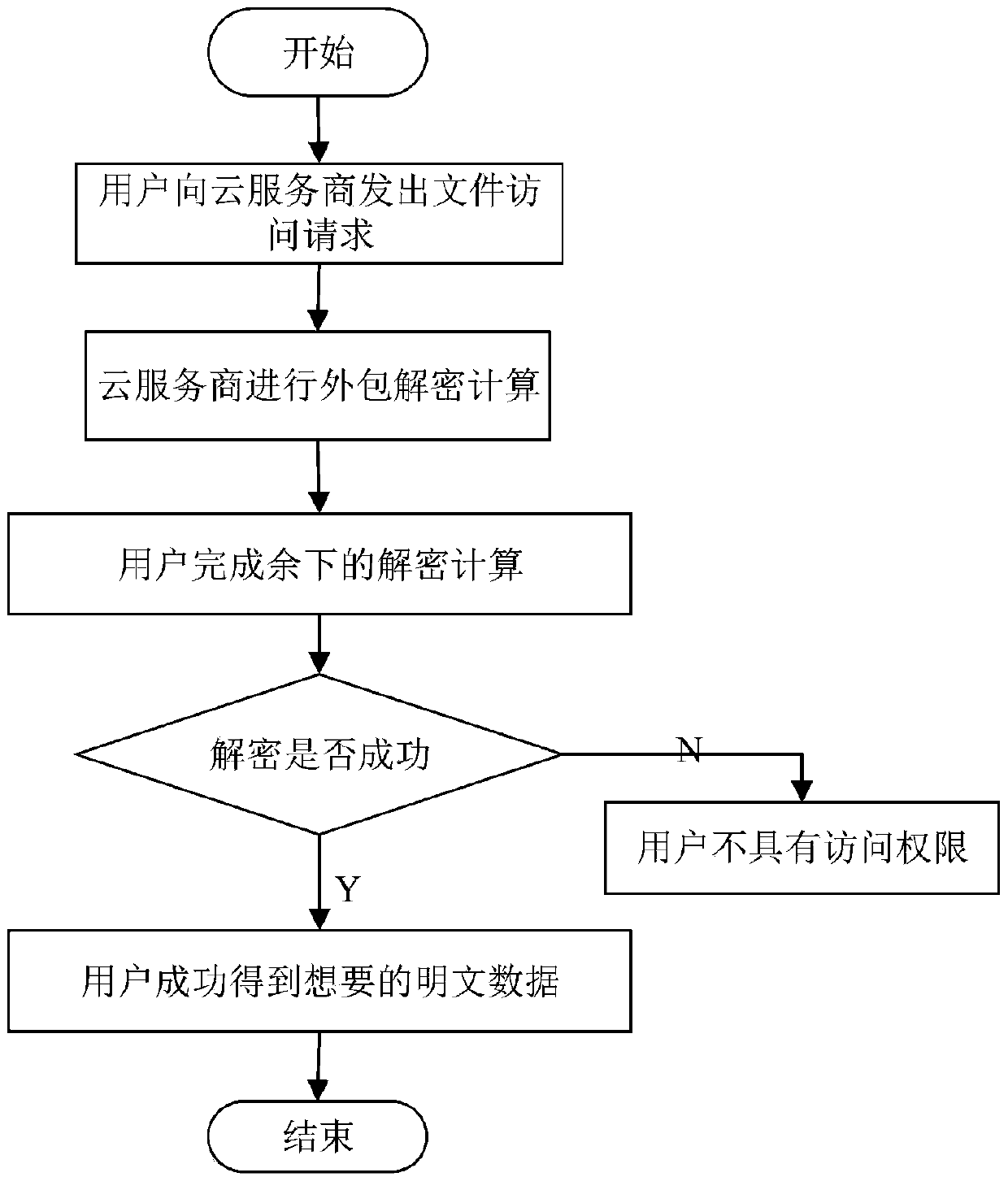
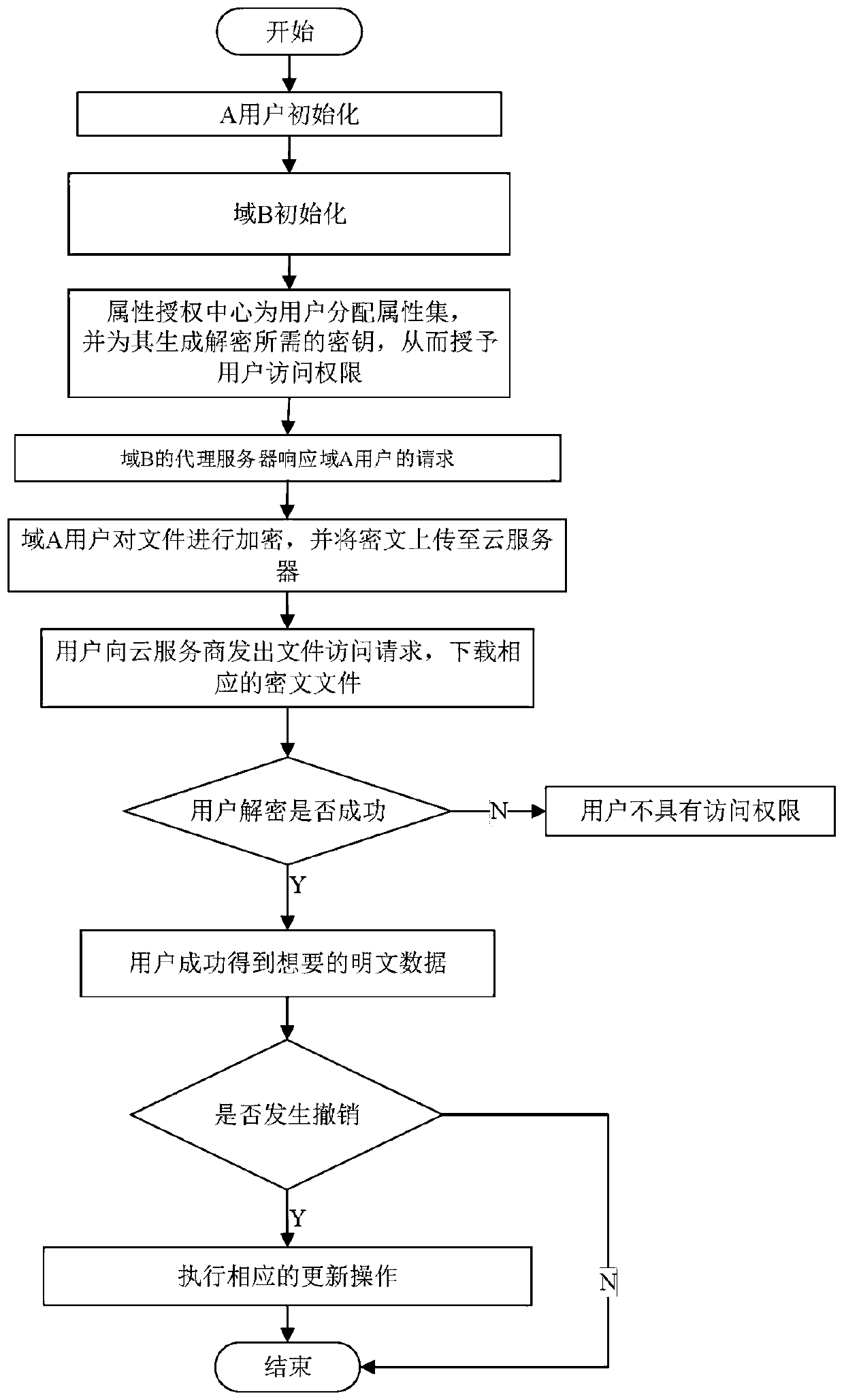
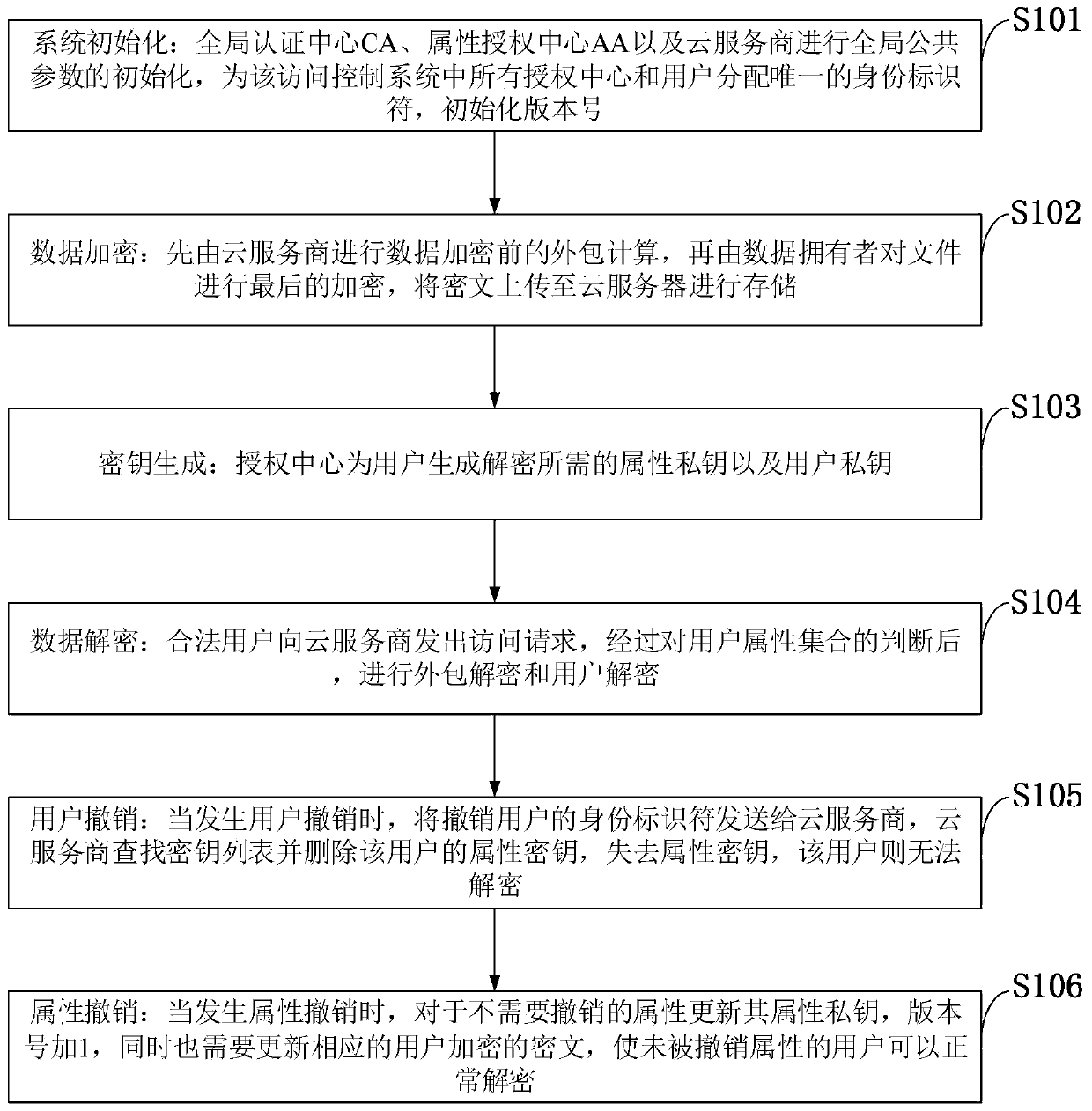
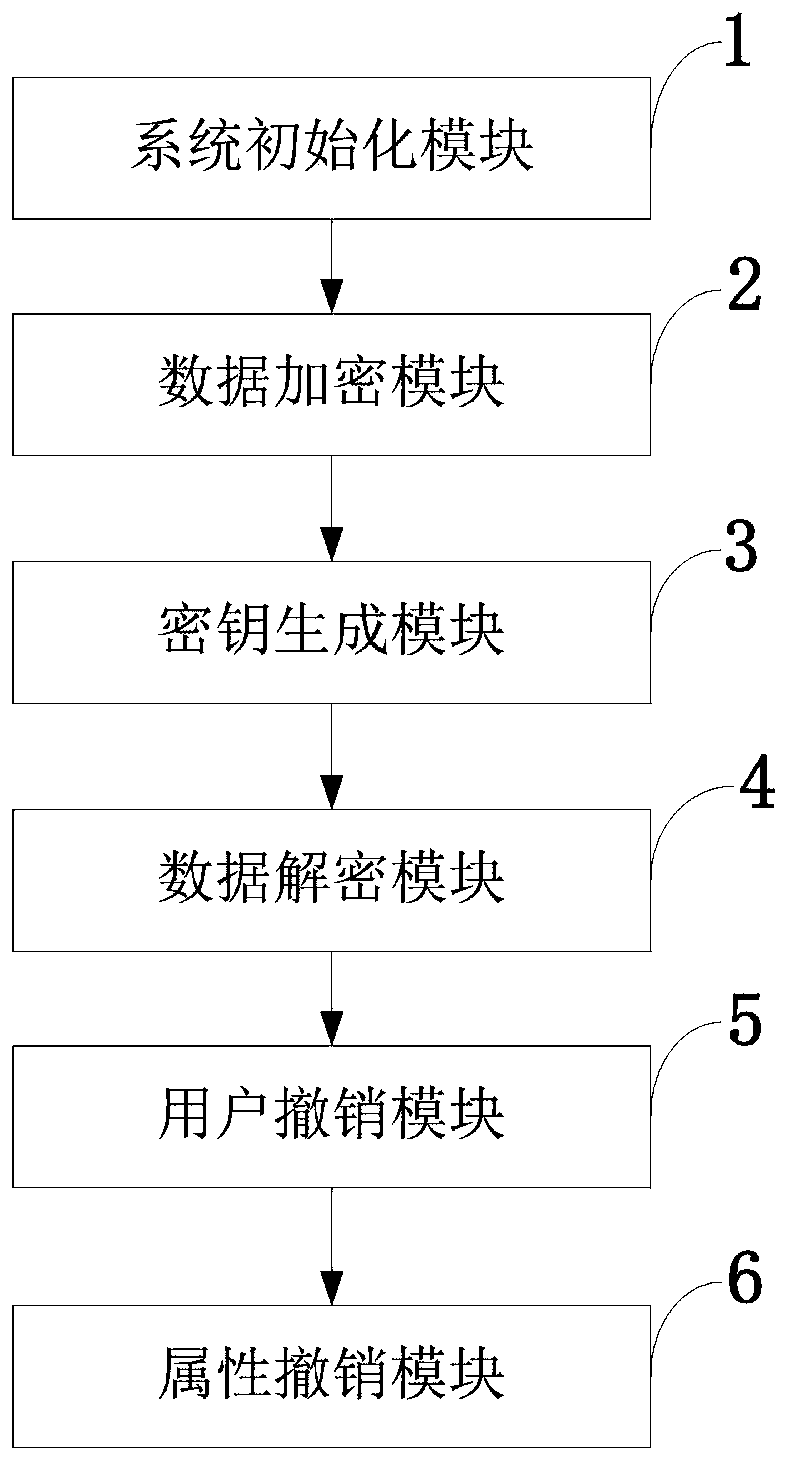
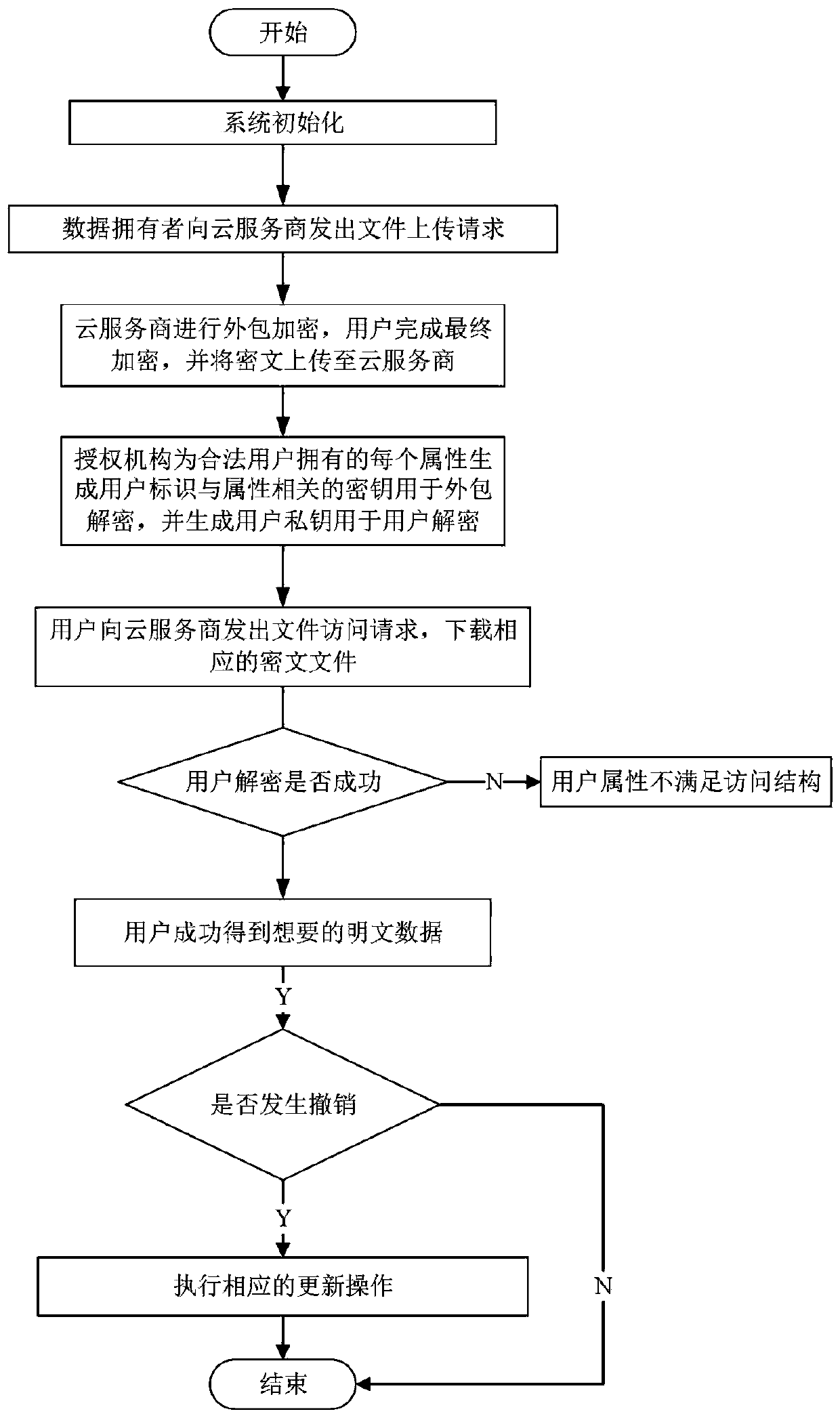
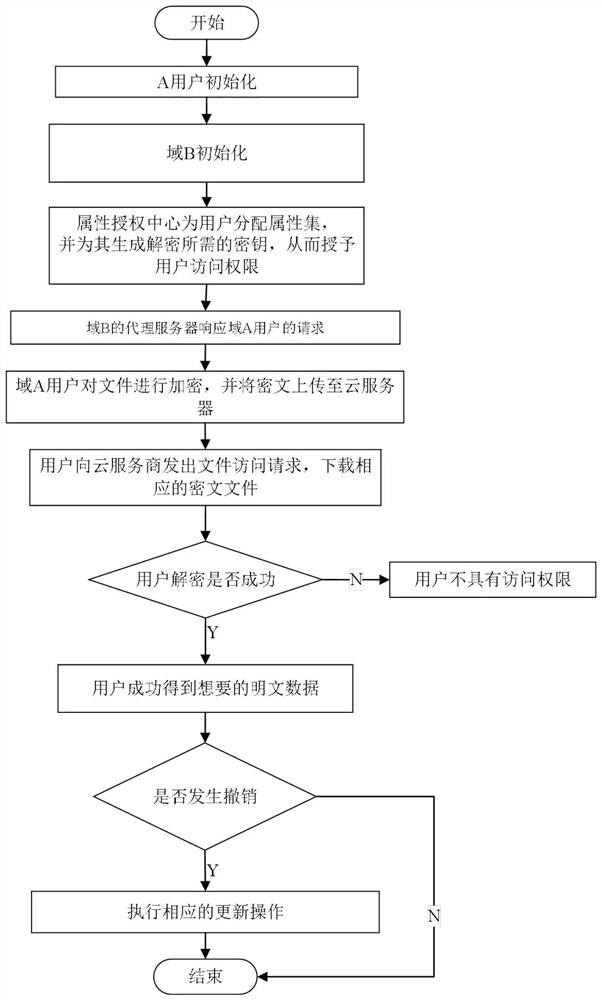
The invention belongs to the technical field characterized by a protocol, and discloses a cancellation-supported outsourcing verifiable multi-authorization center access control method, and a cloud server. The method comprises the following steps: system initialization, including the initialization of a global authentication center and other authorization centers; allocating an attribute set for auser by the authorization centers, and generating a secret key needed by decryption for the user; encrypting a file by a data owner, wherein the encryption process comprises outsourcing encryption, the verification of an outsourcing result and the final encryption of the data owner; issuing a file access request to a cloud service provider by the user, wherein the process includes cloud service provider outsourcing decryption, the verification of the outsourcing result, and the final decryption of the user; and cancelling some users or some attributes in a system. The cancellation-supported outsourcing verifiable multi-authorization center access control method provided by the invention has the advantages of being high in system access efficiency, low in computation overhead, capable of supporting dynamic user authority management and the like, and can be used for guaranteeing the privacy data safety of the user in cloud storage, reducing the computation overhead of the user and dynamically managing the authority of the user in the system.
Owner:XIDIAN UNIV
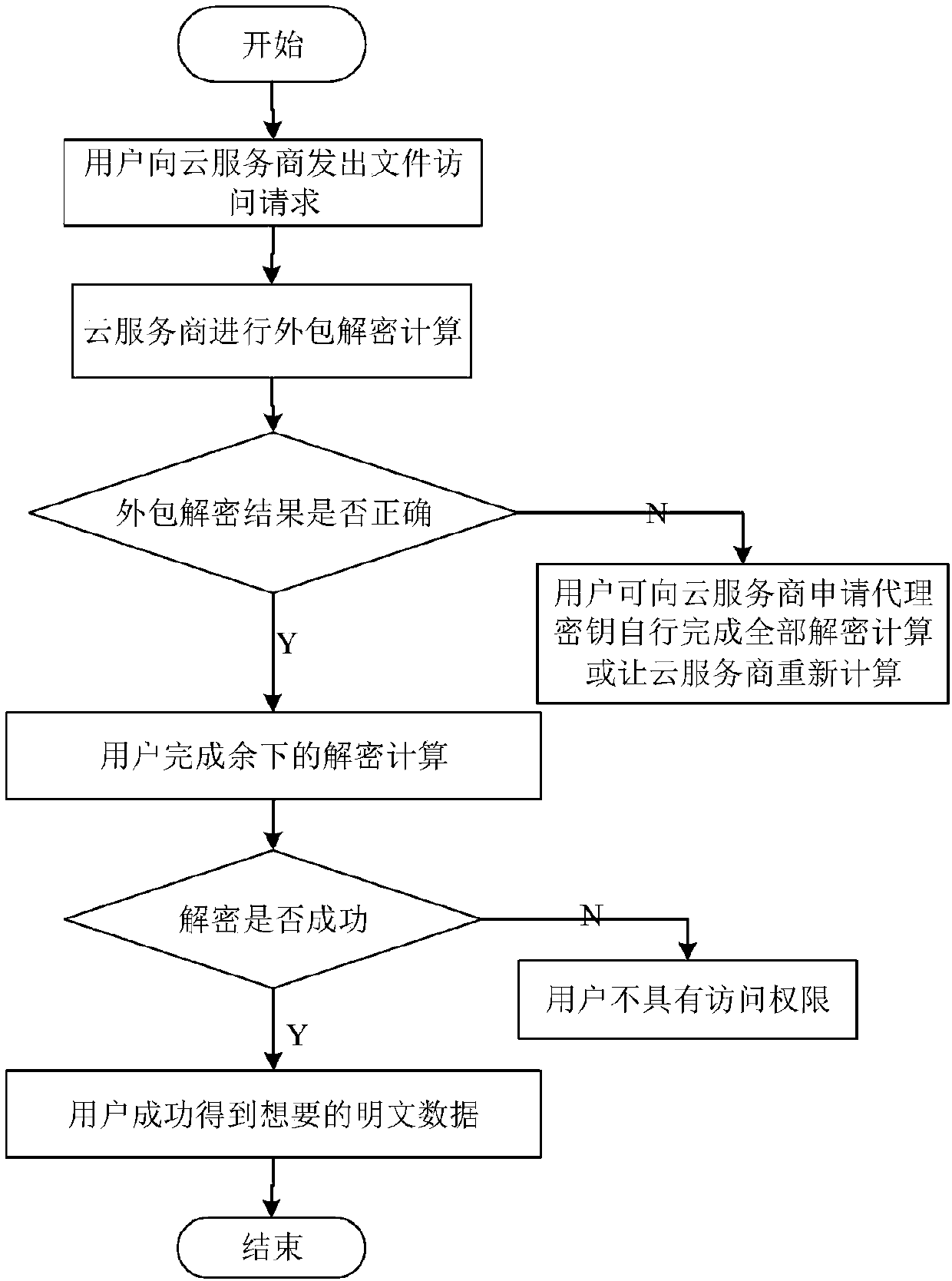
Agent-based revocable multi-authorization center access control method and cloud storage system
ActiveCN108810004ARich domainAvoid Collusion AttacksKey distribution for secure communicationUser PrivilegeData information
The invention belongs to the technical field of wireless communication networks, and discloses an agent-based revocable multi-authorization center access control method and a cloud storage system. Themethod comprises the steps that system initialization is conducted, wherein initialization of a global authentication center CA and other authorization centers AA and initialization of a cloud serverare included; the authorization centers AA allocate attribute sets to users and generate keys needed for decryption for the users; a data owner encrypts a file; the users send file access requests toa cloud service provider, wherein the process comprises outsourcing decryption of the cloud service provider and final decryption of the users; and some users or some attributes in the system are revoked. The method has the advantages of being high in system efficiency, supporting dynamic user permission management and the like and can be used for ensuring the privacy data security of the users in the data information system, reducing the computing overhead of the users and dynamically managing the permissions of the users in the system.
Owner:XIDIAN UNIV
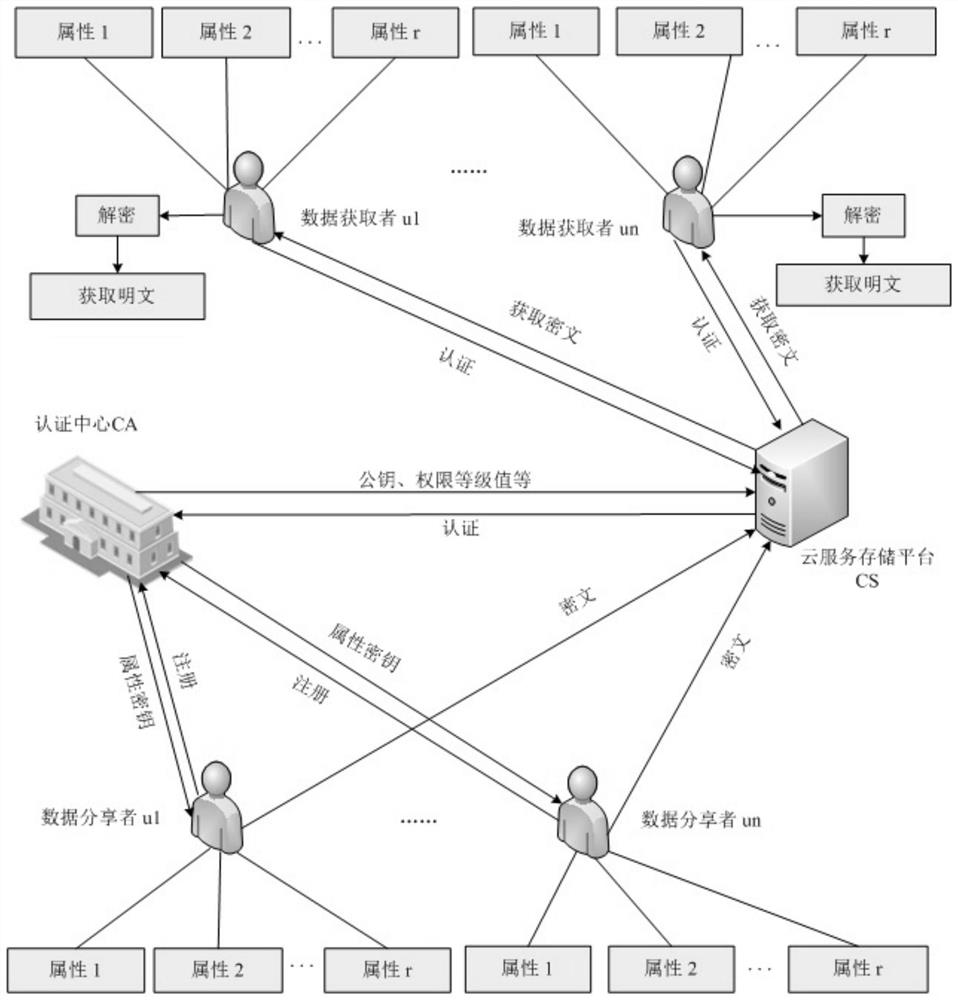
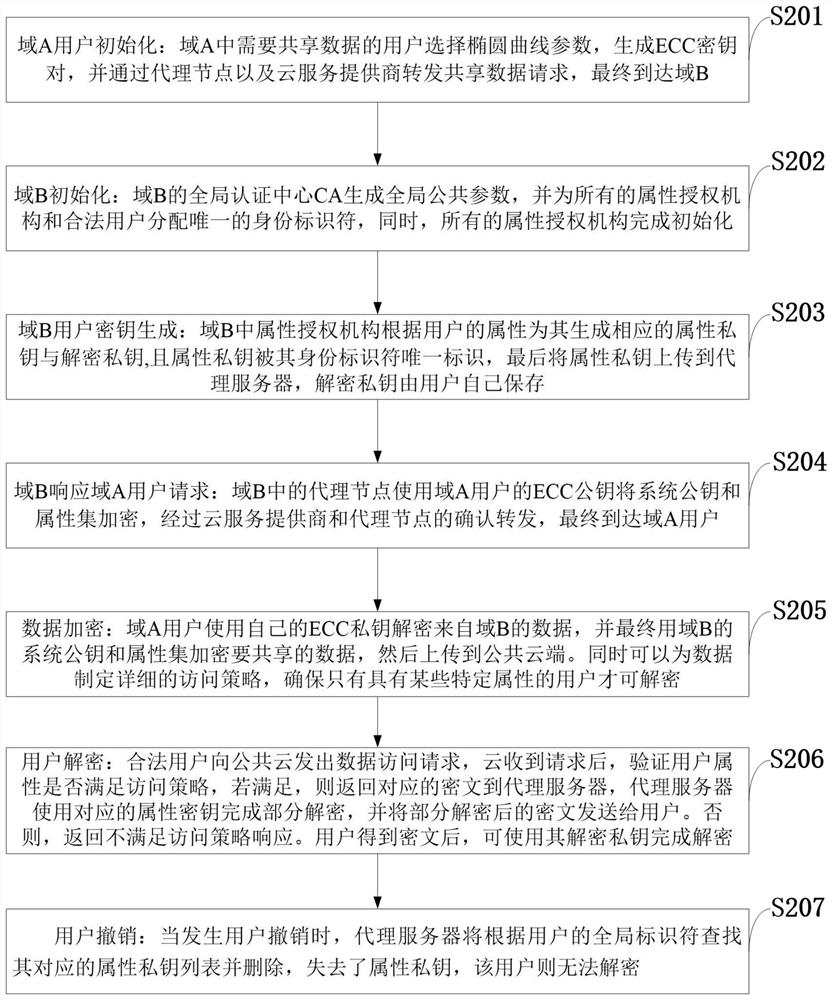
Access control system and method supporting cross-domain data sharing and wireless communication system
ActiveCN110636500AGuaranteed safe transmissionImprove securityPublic key for secure communicationSecurity arrangementKey sizeCommunications system
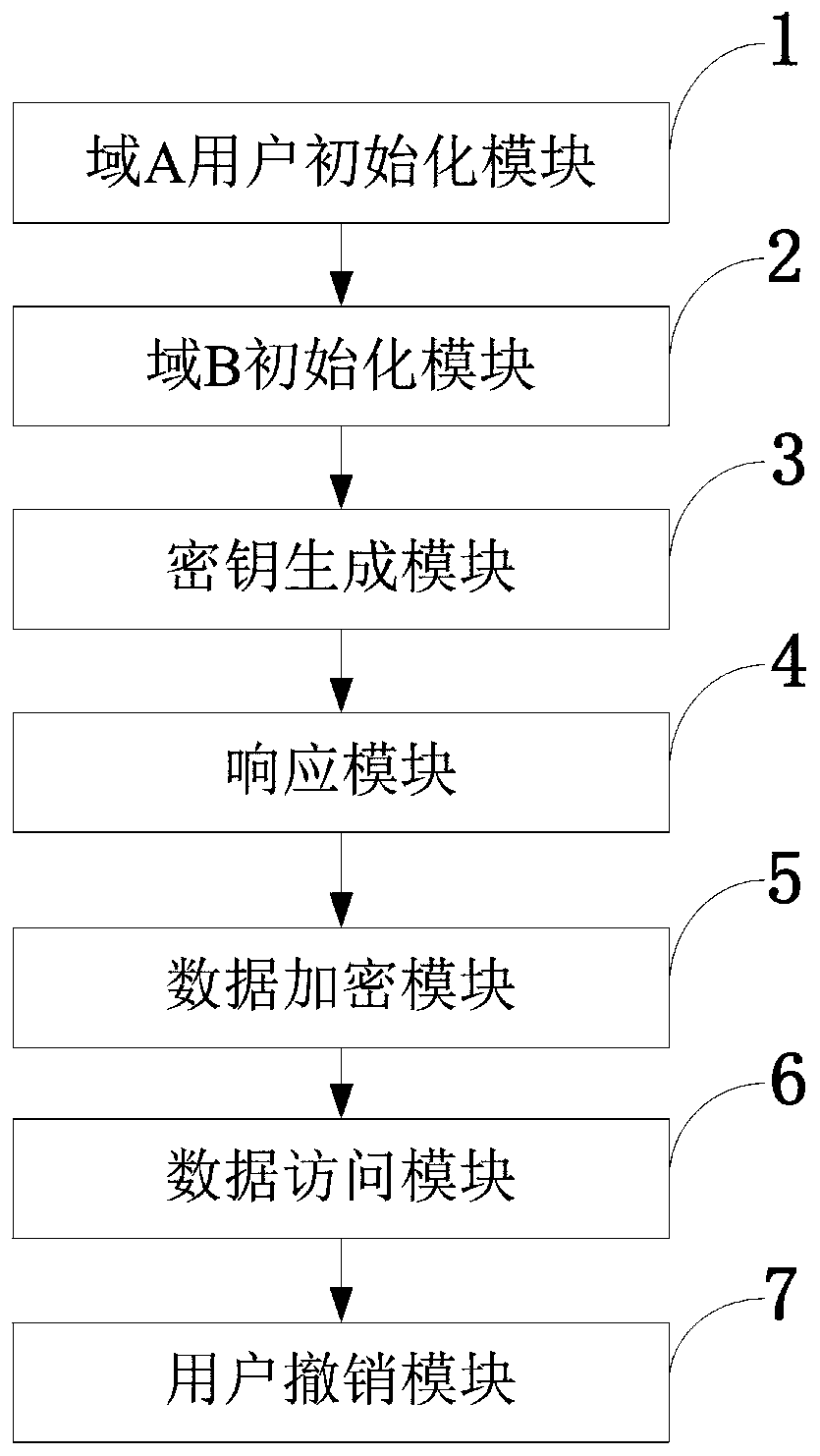
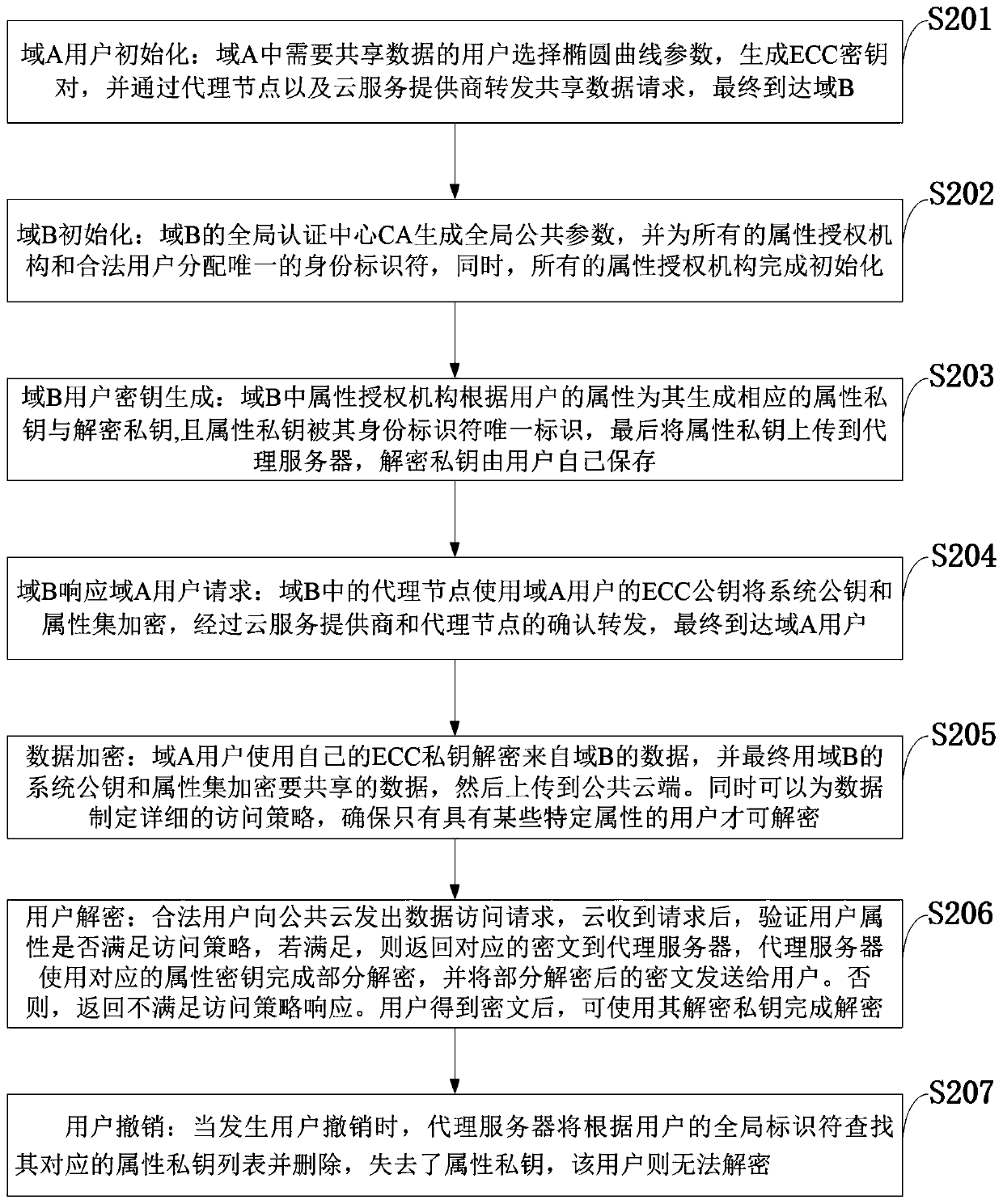
The invention belongs to the technical field of wireless communication networks, and discloses an access control system and method supporting cross-domain data sharing, and a wireless communication system. Users needing to share data in a domain A select elliptic curve parameters to generate ECC key pairs; a global authentication center CA of the domain B generates a global public parameter; the proxy node in the domain B encrypts the system public key and the attribute set by using the ECC public key of the domain A user; the domain A user decrypts the data from the domain B by using the ECCprivate key of the domain A user and uploads the data to the public cloud; the legal user sends a file access request to the public cloud; and when user revocation occurs, the proxy server searches acorresponding attribute private key list according to the global identifier of the user and deletes the attribute private key list. The method is high in safety under the condition of the same secretkey length. The method gives full play to the characteristic of strong computing power of agent nodes, completes the preprocessing of some data, helps a user to carry out partial decryption, and improves the decryption efficiency of the user.
Owner:XIDIAN UNIV
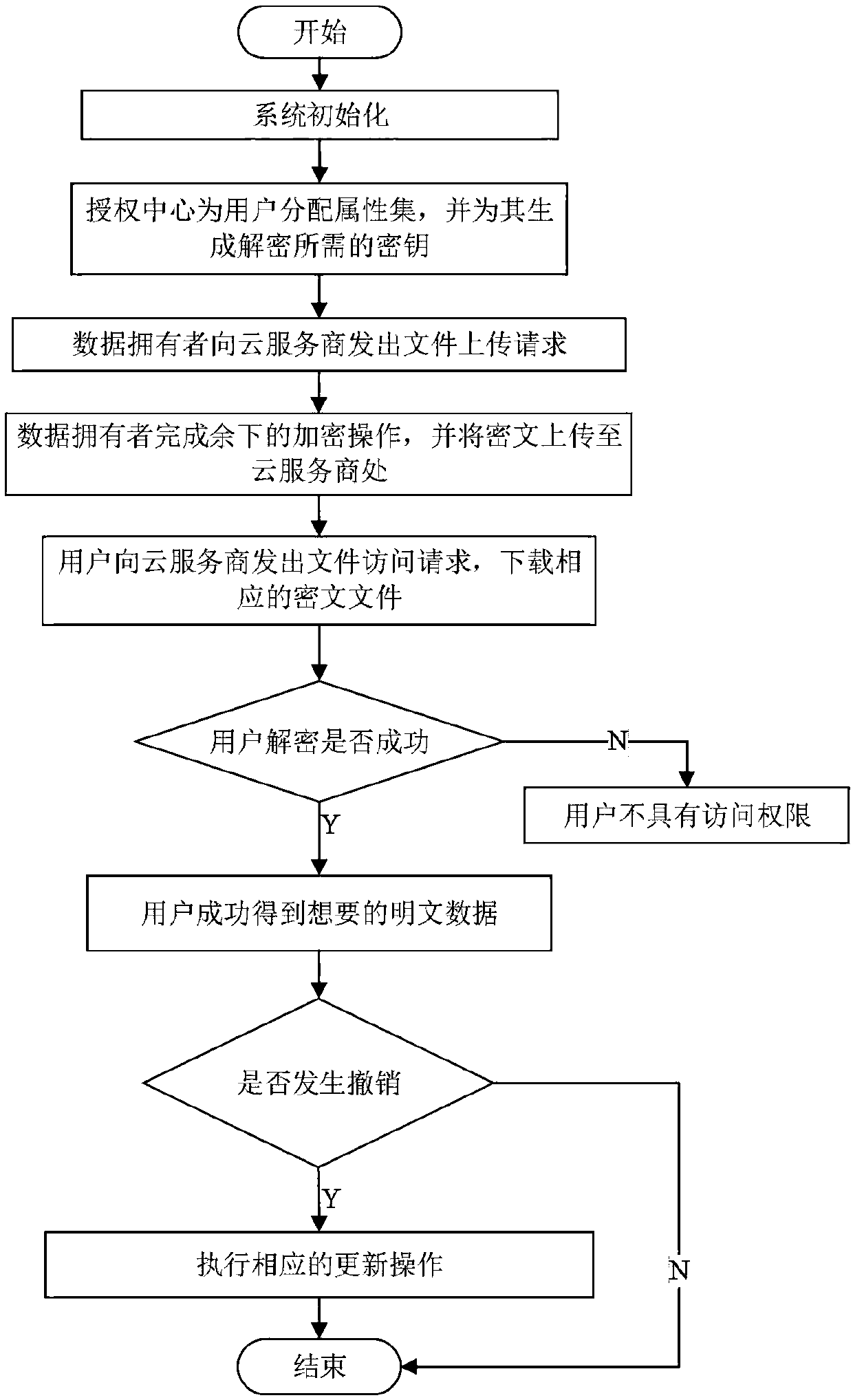
Multi-authorization center access control method and system and cloud storage system
InactiveCN110602063ALighten the computational burdenAvoid Collusion AttacksTransmissionUser PrivilegeCloud storage system
The invention belongs to the technical field of information security, and discloses a multi-authorization center access control method and system and a cloud storage system, and the method comprises the steps: system initialization: initializing a global authentication center CA and an attribute authorization center AA; data encryption: outsourcing encryption and user encryption performed by a cloud service provider; key generation: an attribute authorization center AA allocates an attribute private key related to the attribute and a user decryption key to the user; the user sends a file access request to the cloud service provider, and the process comprises outsourcing decryption of the cloud service provider and final decryption of the user; some users in the system are revoked; certainattributes in the system are revoked. The method has the advantages of high system efficiency, reduction of user computing burden, support of multiple authorization centers, dynamic change of user permission and the like, and can be used in a cloud storage system to guarantee the data privacy security of users, reduce the computing overhead of the users and improve the system efficiency.
Owner:XIDIAN UNIV
Verifiable matrix multiplication security outsourcing calculation method and system
InactiveCN106775576ATightness is not brokenReduce computing pressureComputation using non-contact making devicesTransmissionMatrix multiplicationCalculation methods
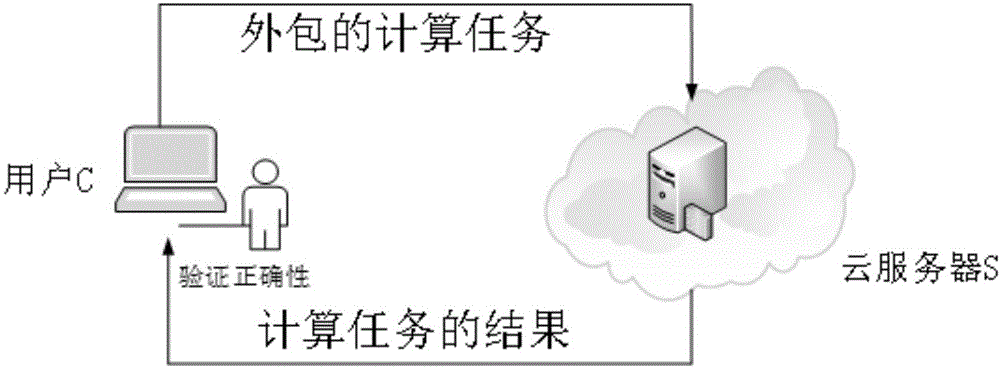
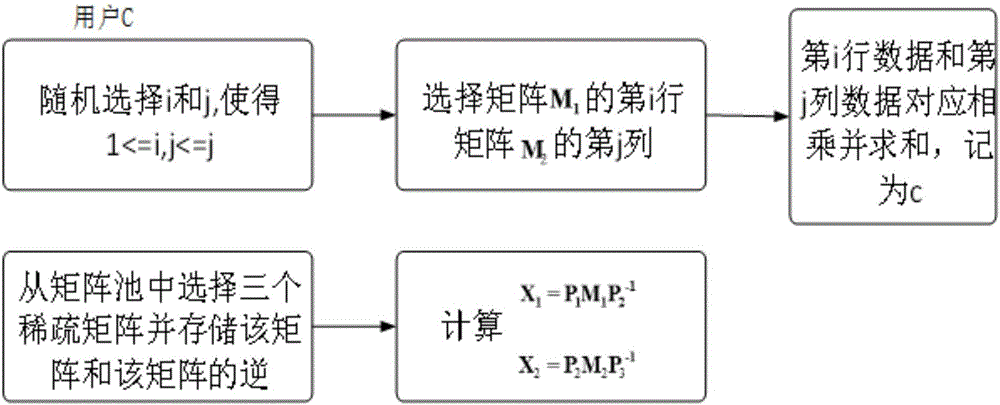
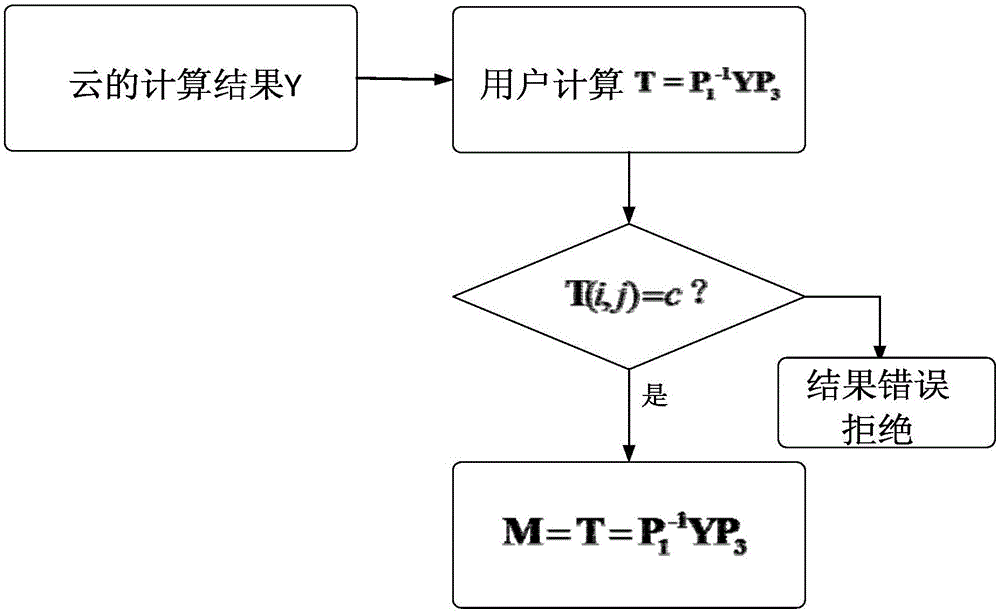
The invention provides a verifiable matrix multiplication security outsourcing calculation method. The calculation method comprises the following steps: firstly, outsourcing of a user: namely rendering outsourcing of an own consumed time matrix multiplication calculation operation to a cloud server by the user; secondly, calculation of the cloud server: namely, carrying out matrix multiplication calculation by utilizing an own powerful computing resource by the cloud server after receiving a matrix and an operation, and returning a calculation result to the user after the calculation is completed; and thirdly, user restoring and verification: namely receiving the calculation result returned by virtue of cloud by the user, and verifying correctness of the result. In the method provided by the invention, calculation data uploaded to the cloud by the user are subjected to preprocessing calculation, so that privacy of user data is protected; when the cloud returns the result to the user, the user can efficiently verify the correctness of the result, and an error result is prevented from being returned to the user by virtue of the cloud and undetected.
Owner:QINGDAO UNIV
Cloud auditing method with lightweight user dynamic revocation and data dynamic update
ActiveCN107566118AImprove dynamic update efficiencyAvoid Collusion AttacksKey distribution for secure communicationThird partyData integrity
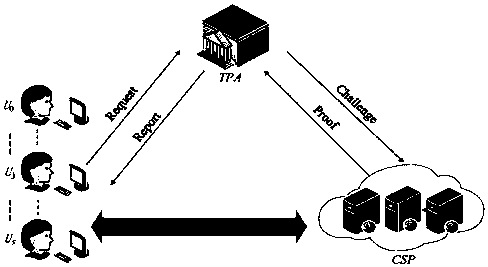
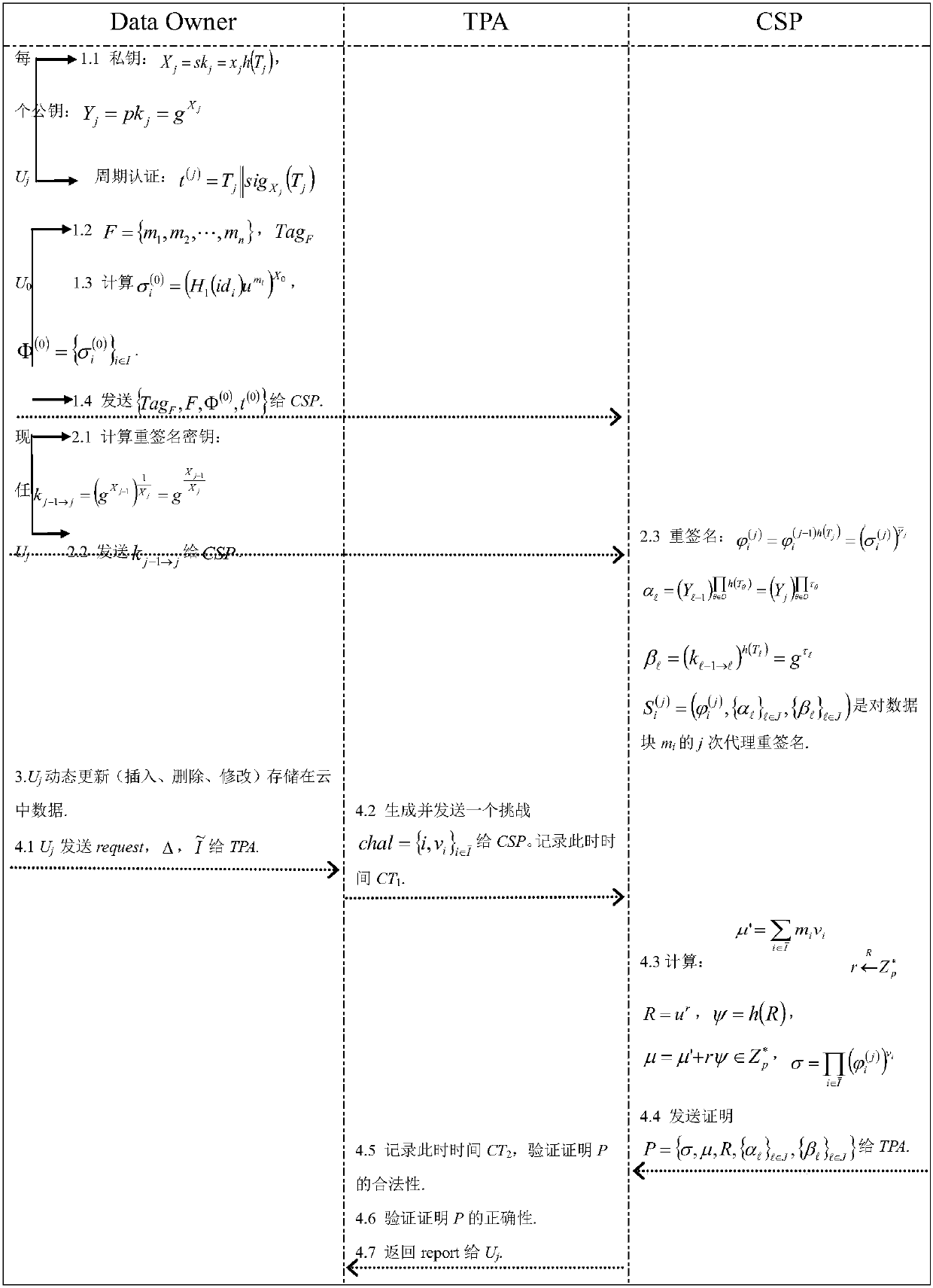
The invention discloses a cloud auditing method with lightweight user dynamic revocation and data dynamic update. First of all, a user can implement efficient dynamic revocation (including replacementof public and private keys), and in a user revocation stage, multiple one-way proxy re-signature technologies are adopted, and a new user only needs to compute a re-signature key and does not need todownload a data re-signature from a cloud end and then upload to the cloud end; then, the data can be guaranteed to be updated (inserted, deleted and modified) dynamically in real time, and by introducing a virtual index to identity recognition codes of data blocks, when the data are updated dynamically, only the identity recognition codes of the updated data blocks change and the identity recognition codes of the rest data blocks remain unchanged; and at last, in a re-signature stage, a cloud server performs re-signature instead of a new appointed user, and in an auditing stage, a third party auditing center performs verification on integrity of the data stored at the cloud end instead of a current user; the computation overhead of a terminal user and the communication overhead of a system are greatly relieved; and the cloud auditing method is efficient and secure.
Owner:趣橙(上海)信息技术有限公司
Identity-based traceable ring signature authentication protocol
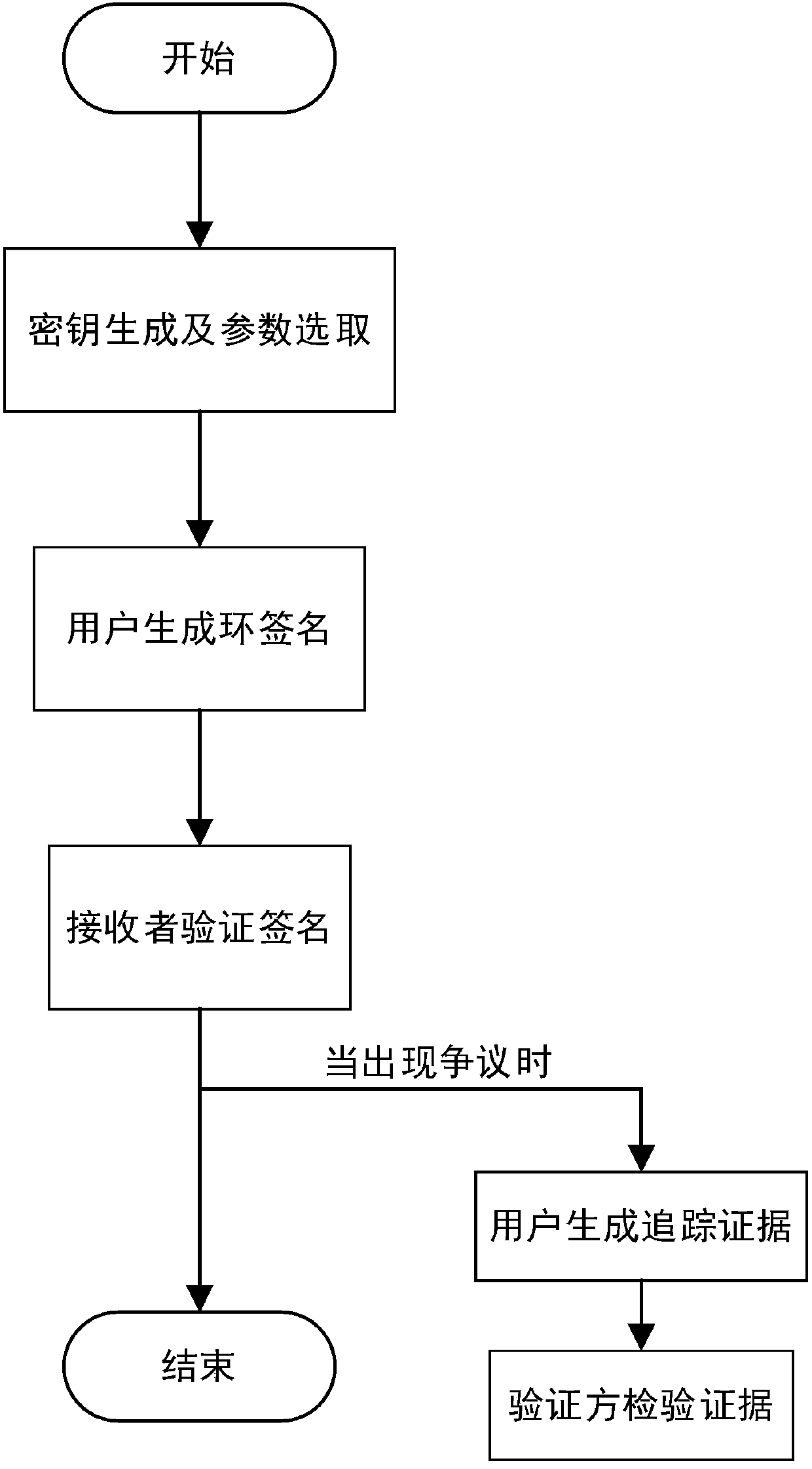
ActiveCN107835082AEnsure safetyImprove applicabilityUser identity/authority verificationSignature of knowledgeKey generation
The invention discloses an identity-based traceable ring signature authentication protocol, comprising the steps of I, initializing a system, to be specific, generating a secret key and selecting parameters; II, generating and verifying a signature, to be specific, allowing a user to generate a ring signature, and allowing a receiver to verify validity of the signature; III, generating and verifying tracing evidence, to be specific, allowing the user to generate tracing evidence, and allowing a verifier to verify legality of the evidence. The identity-based traceable ring signature authentication protocol has the advantages that a signer can be effectively traced at the premise of implementing authentication security, and collusion attack can be resisted; since a signature of fixed lengthis generated based on a collision-resistant accumulator and signature of knowledge and the length is not proportional to the number of ring members, communication cost is effectively reduced.
Owner:HOHAI UNIV
Book resource access control method based on ciphertext attribute authentication and threshold function
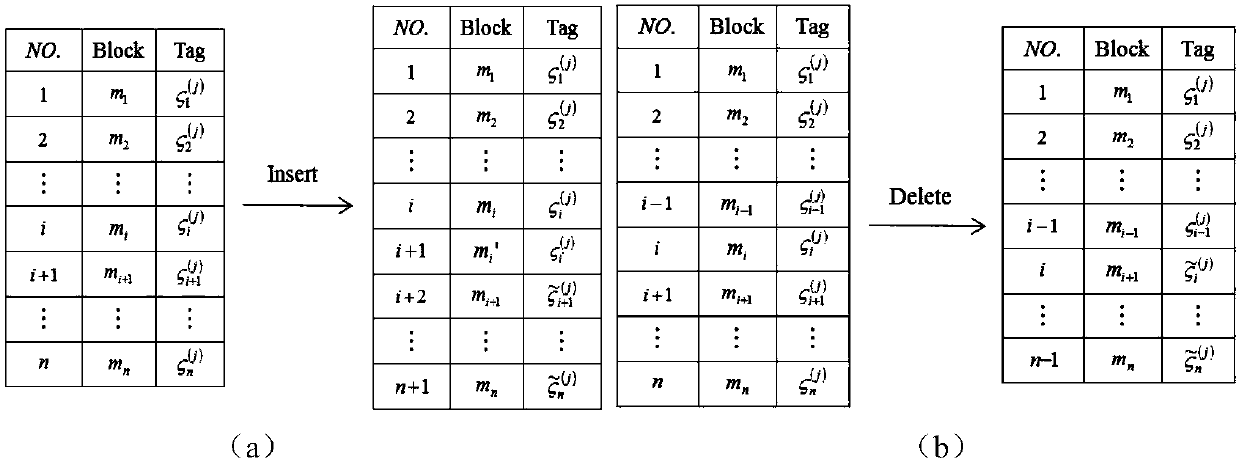
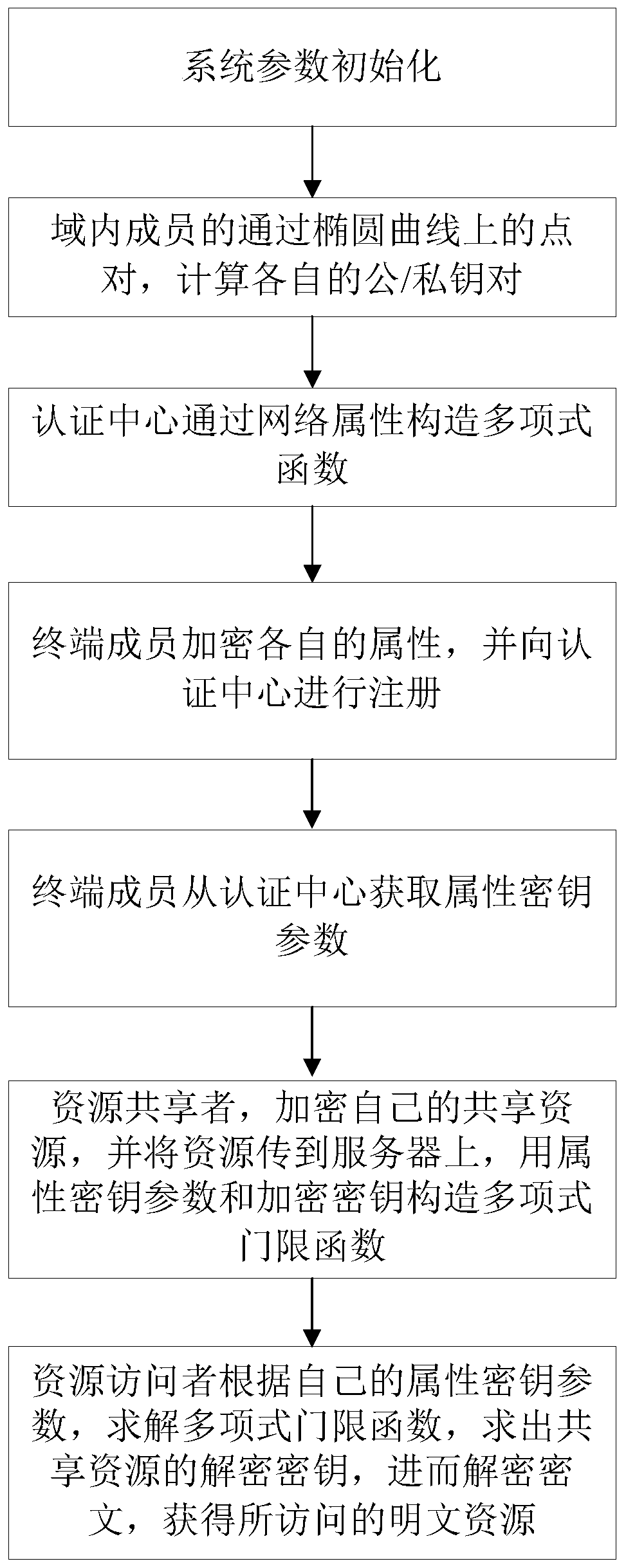
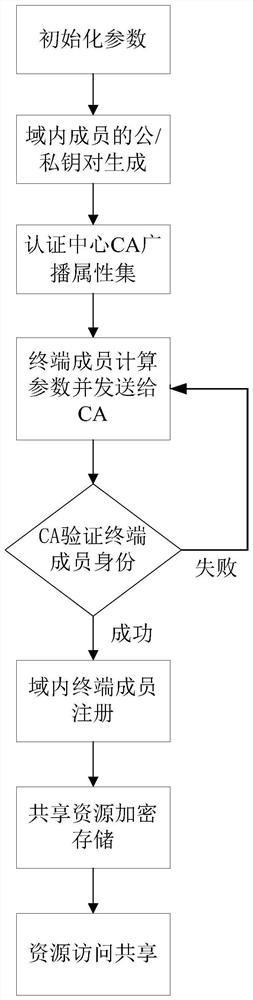
ActiveCN110912897AReduce computational and communication overheadAvoid Collusion AttacksPublic key for secure communicationInformation resourceThreshold function
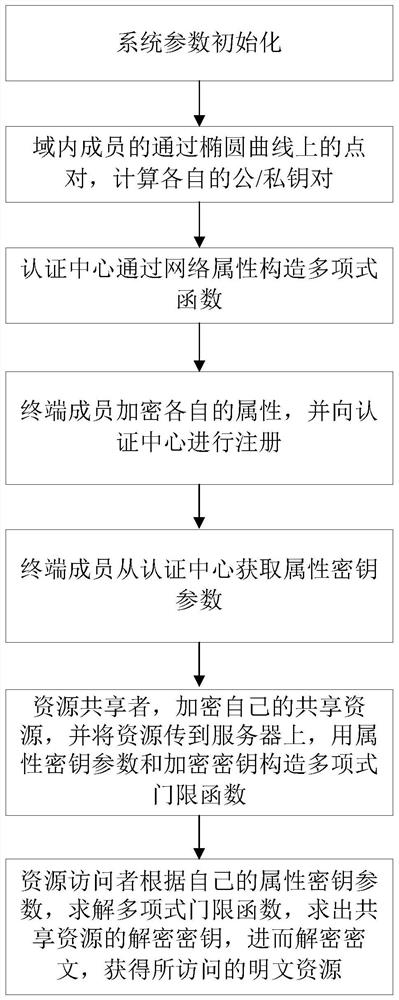
The invention provides a book resource access control method based on ciphertext attribute authentication and a threshold function. The book resource access control method comprises the following steps that an authentication center and terminal members generate respective public / private key pairs; the terminal members interact with the authentication center to perform attribute authentication to obtain permission level values, and each terminal member sends the public key and the permission level value to the authentication center, and sends the public key and the permission level value to thecloud service platform after verification; the terminal member calculates an encryption key and a decryption key, encrypts the shared resource information into a ciphertext and uploads the ciphertextto the cloud service platform; and the terminal member determines a ciphertext resource to be checked according to the ciphertext, the cloud service platform verifies the identity of the ciphertext resource and opens an access link of the ciphertext resource, and the terminal member downloads the ciphertext for decryption. Personal privacy is protected by adopting a ciphertext attribute authentication technology, access permission is controlled by setting a threshold function to guarantee the safety of resource sharing, and collusion attack is prevented by adopting identity and permission dual authentication, so that information resource sharing in the Internet of Things is more flexible, efficient and practical.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
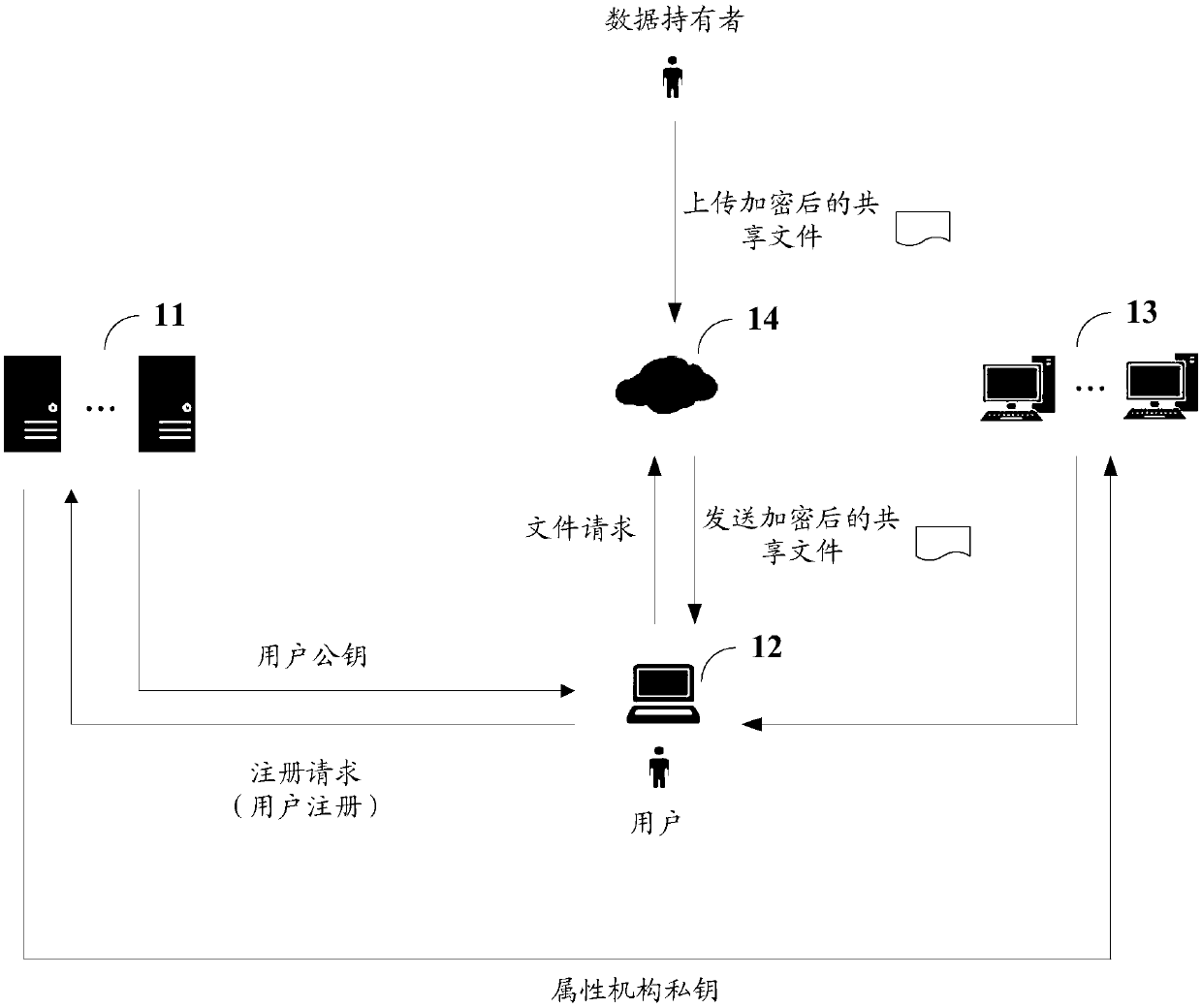
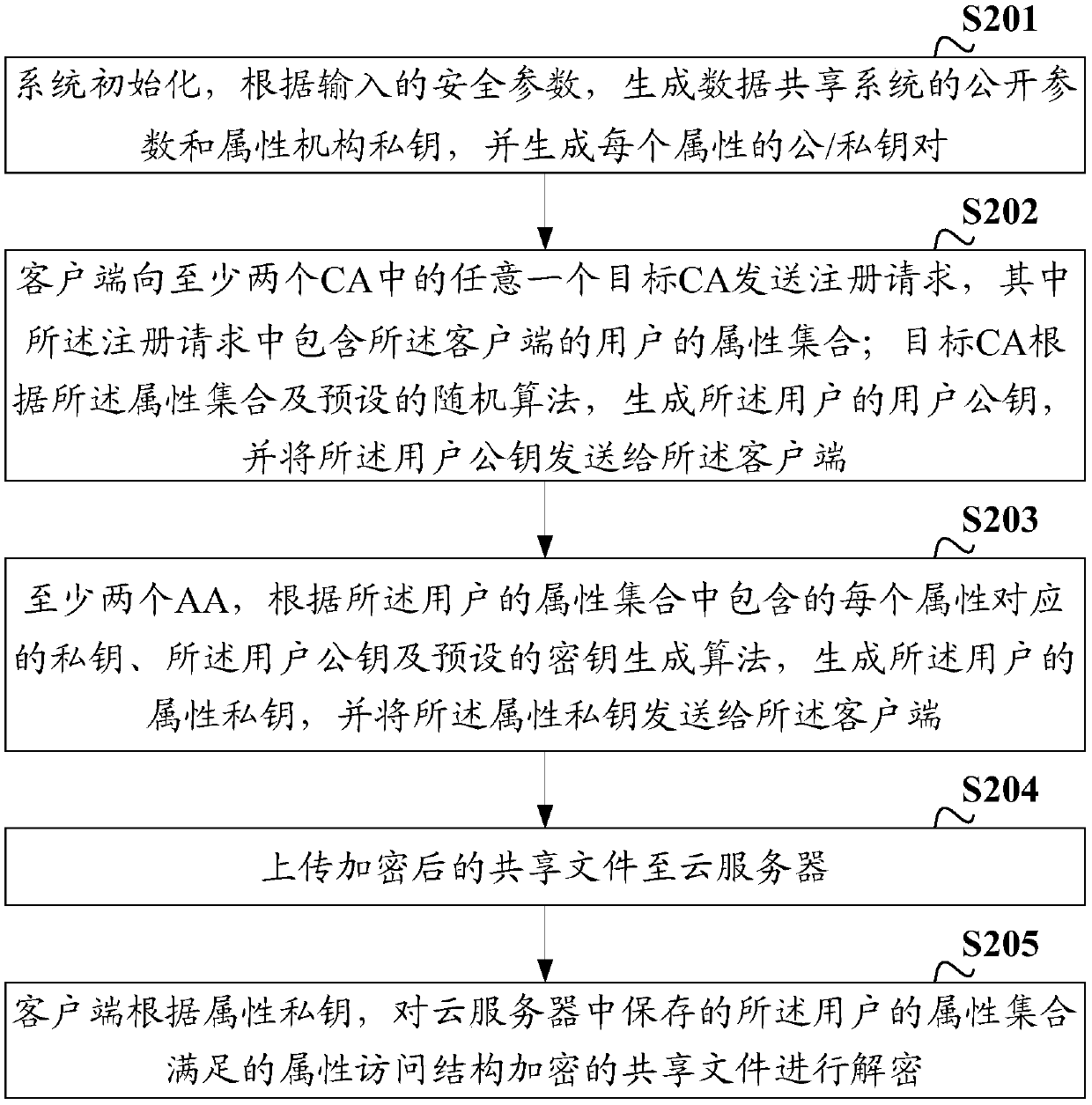
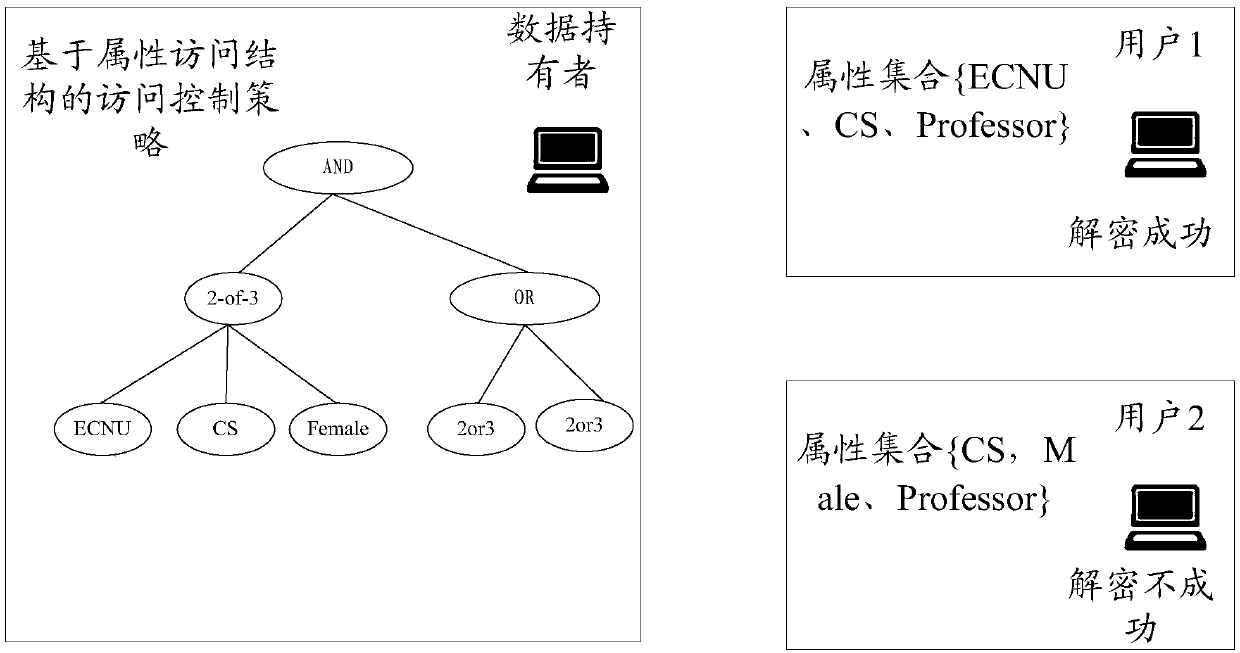
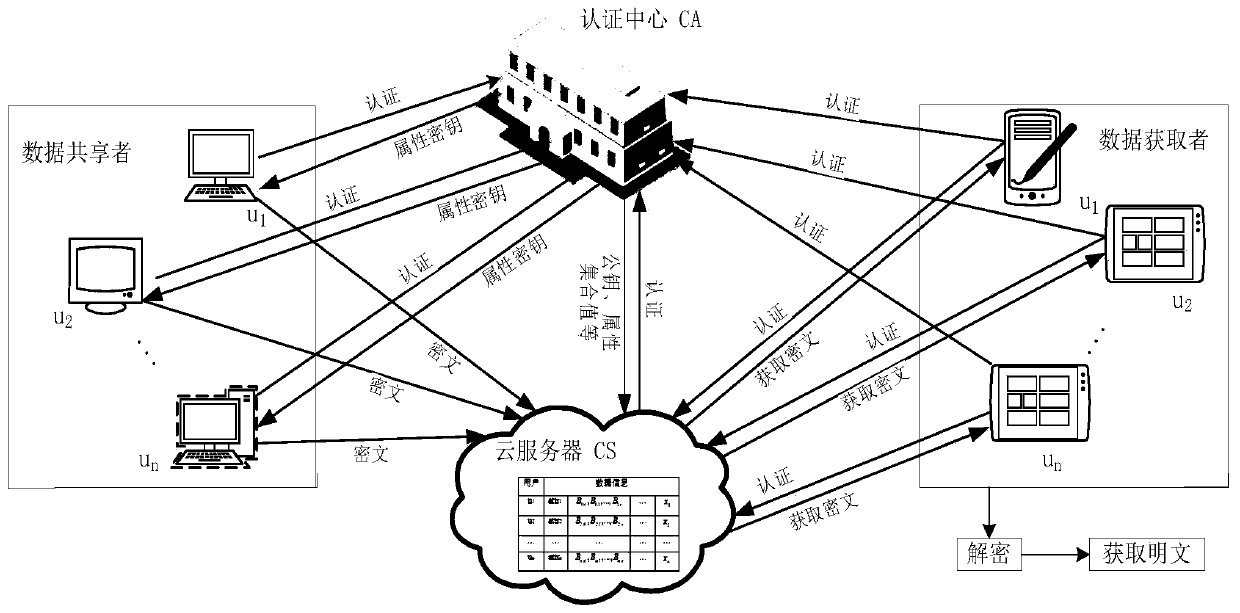
Data sharing method, device and system, client and storage medium
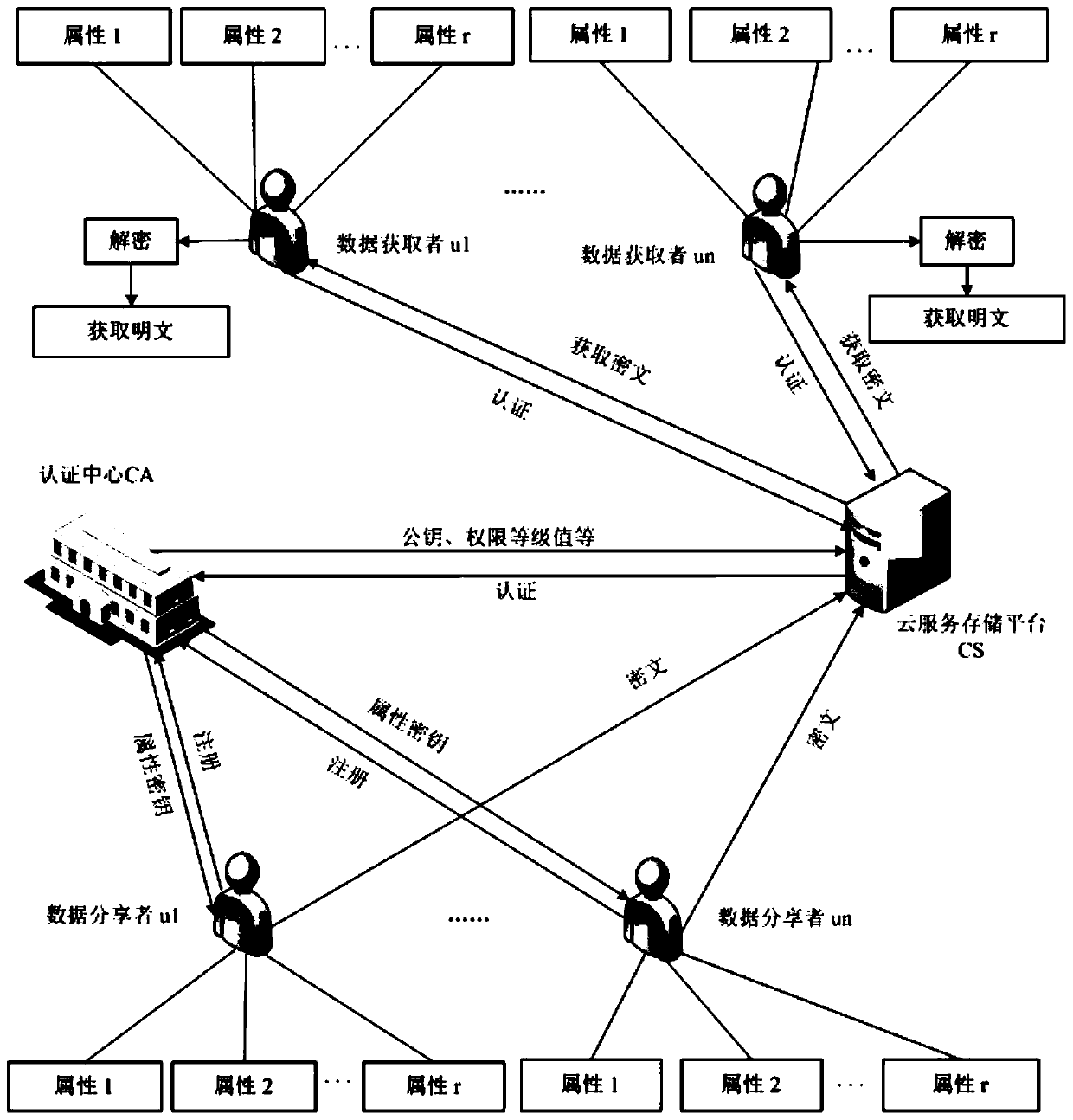
ActiveCN111163036AImprove securityImprove practicalityKey distribution for secure communicationAccess structureStochastic algorithms
The invention discloses a data sharing method, device and system, a client and a storage medium. The system comprises at least two CAs, the client, at least two AAs and a cloud server, wherein the client is used for sending a registration request to any target CA in the at least two CAs, wherein the registration request comprises an attribute set of a user of the client; the target CA is used forgenerating a user public key of the user according to the attribute set and a preset random algorithm; the client is also used for sending the user public key and the attribute set to the at least twoAAs; the at least two AAs are used for generating an attribute private key of the user according to the private key corresponding to each attribute contained in the attribute set, the user public keyand a preset key generation algorithm; and the client is also used for decrypting a shared file which is encrypted by adopting an attribute access structure satisfied by the attribute set of the userand stored in the cloud server according to the attribute private key. The system is used for improving the safety and practicability of data sharing.
Owner:CHINA MOBILE SUZHOU SOFTWARE TECH CO LTD +1
Reputation data processing method based on anonymous network and machine learning
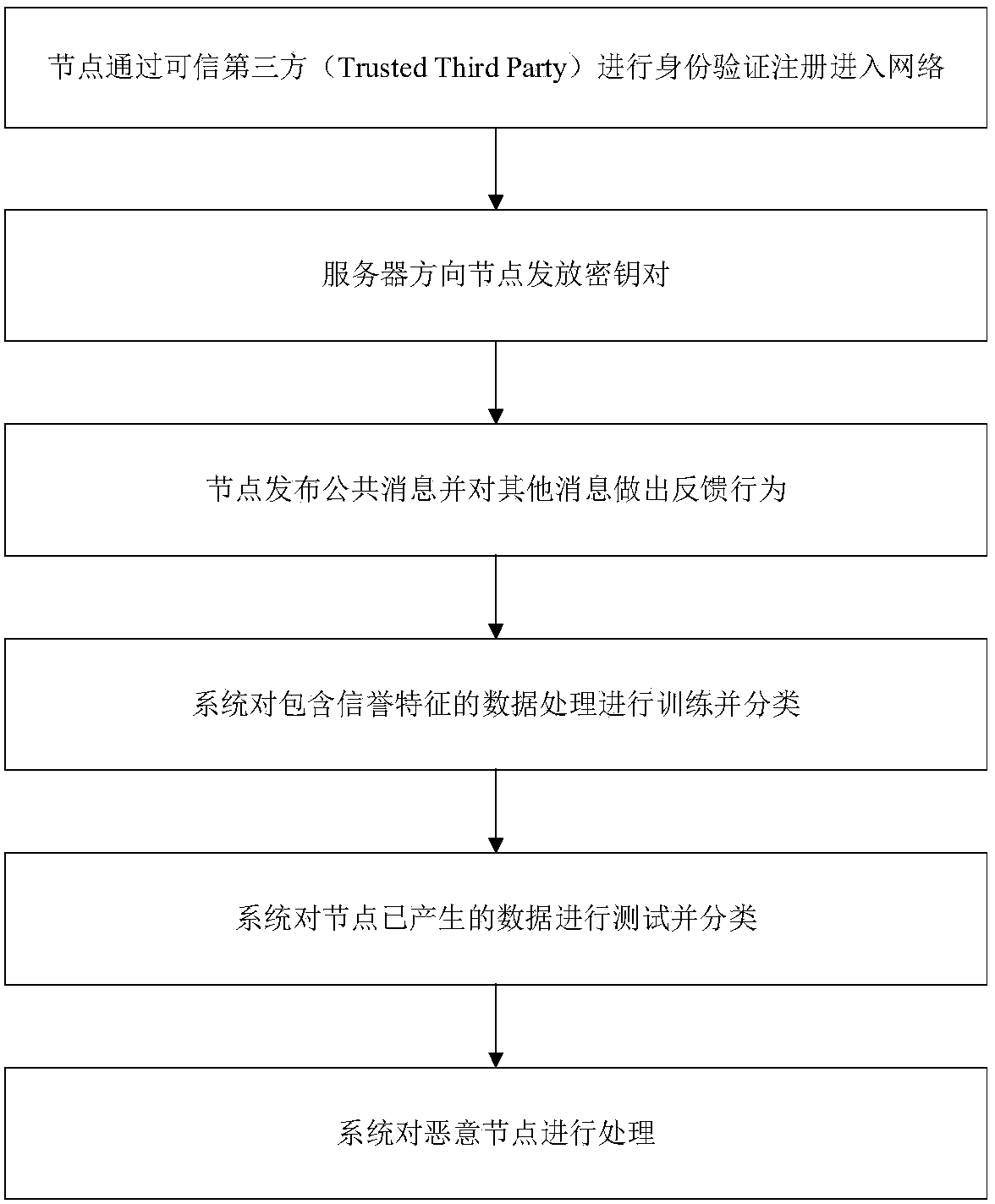
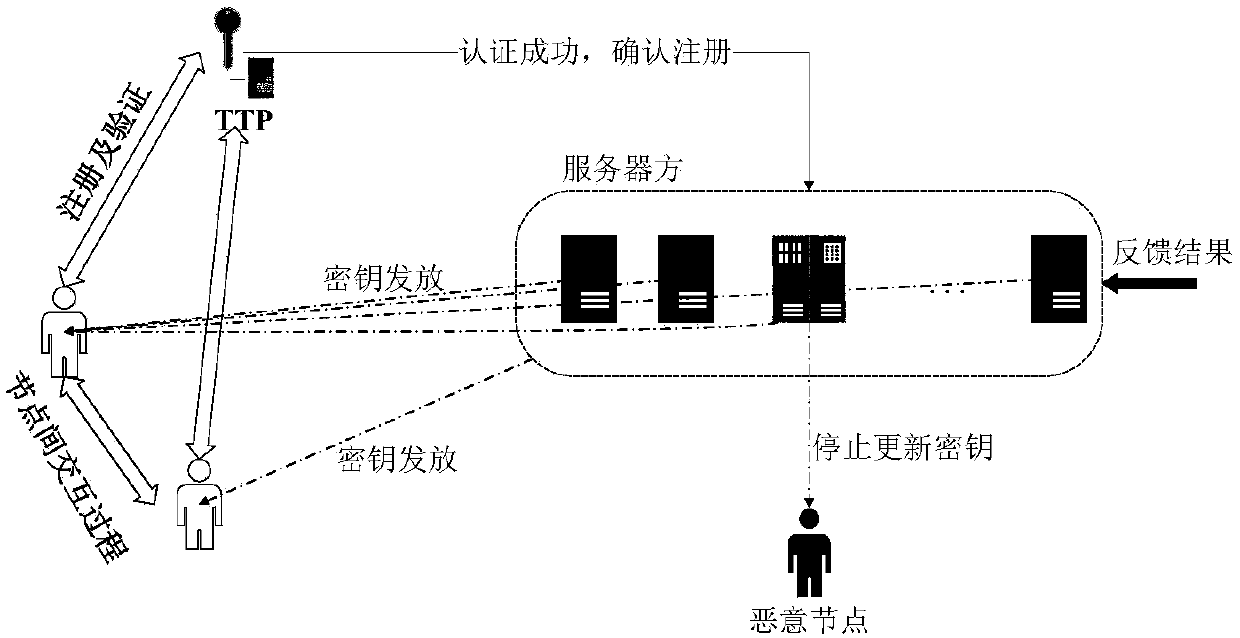
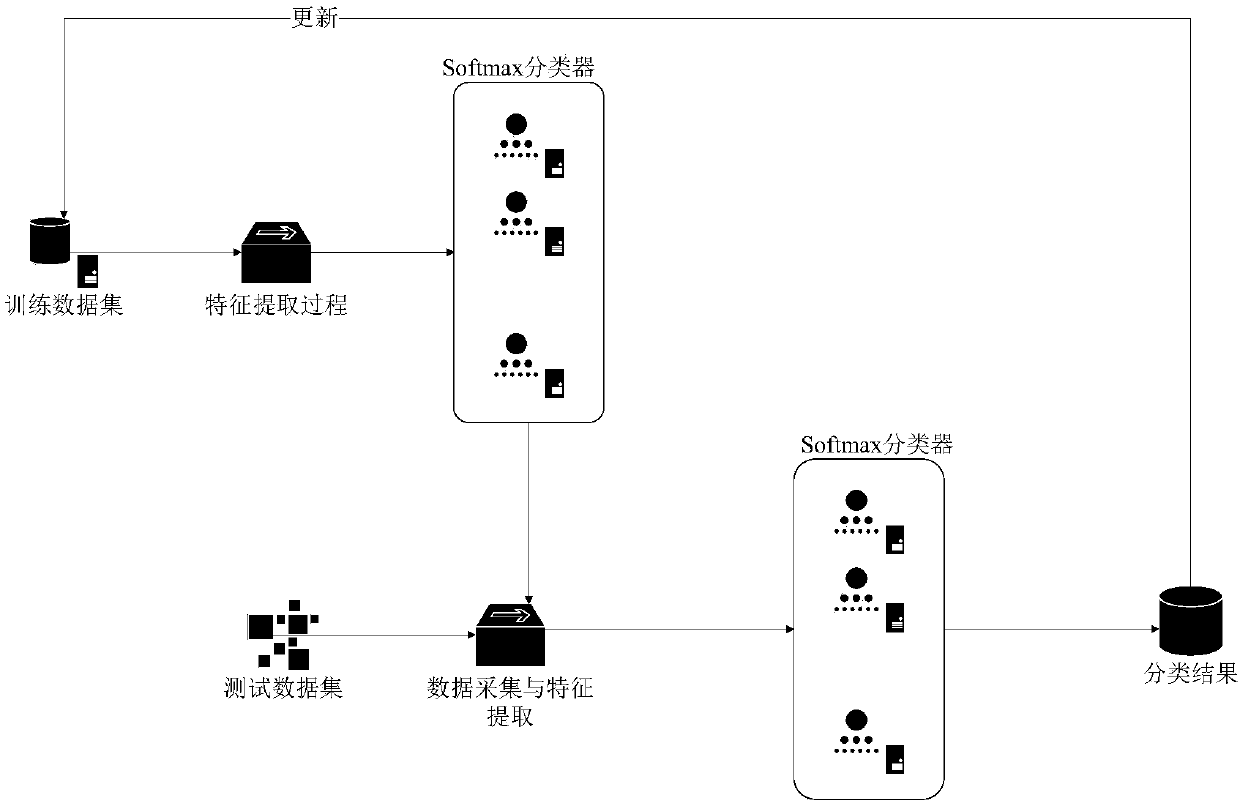
InactiveCN110166415AAvoid Collusion AttacksMeet the conditional anonymity requestBuying/selling/leasing transactionsMachine learningPrivacy protectionTrusted third party
The invention provides a reputation data processing method based on an anonymous network and machine learning. The reputation data processing method is used for solving the problems of privacy protection and attack resistance in the prior art. Implementation steps are as follows: implementation steps are as follows: the a node carries out identity authentication and registration through the trusted third party to enter the network; and the a server issues a key pair to the node, the node issues a public message and makes a feedback behavior to other messages, the system trains and classifies data containing reputation characteristics, the system tests and classifies the data generated by the node, and the system processes malicious nodes. According to the method, Tthe evaluated identity, the registered identity and the real identity are separated through an appropriate encryption mechanism, so that the real identity of the user is difficult to track, the problem of privacy protection is solved, and meanwhile, a machine learning mechanism is applied to classify and process reputation data, so that network attacks possibly suffered by a reputation system are effectively resisted.
Owner:XIDIAN UNIV
Internet of Things data security sharing method based on privacy protection
ActiveCN112165472AReduce calculationReduce communication overheadKey distribution for secure communicationUser identity/authority verificationInformation resourceAttack
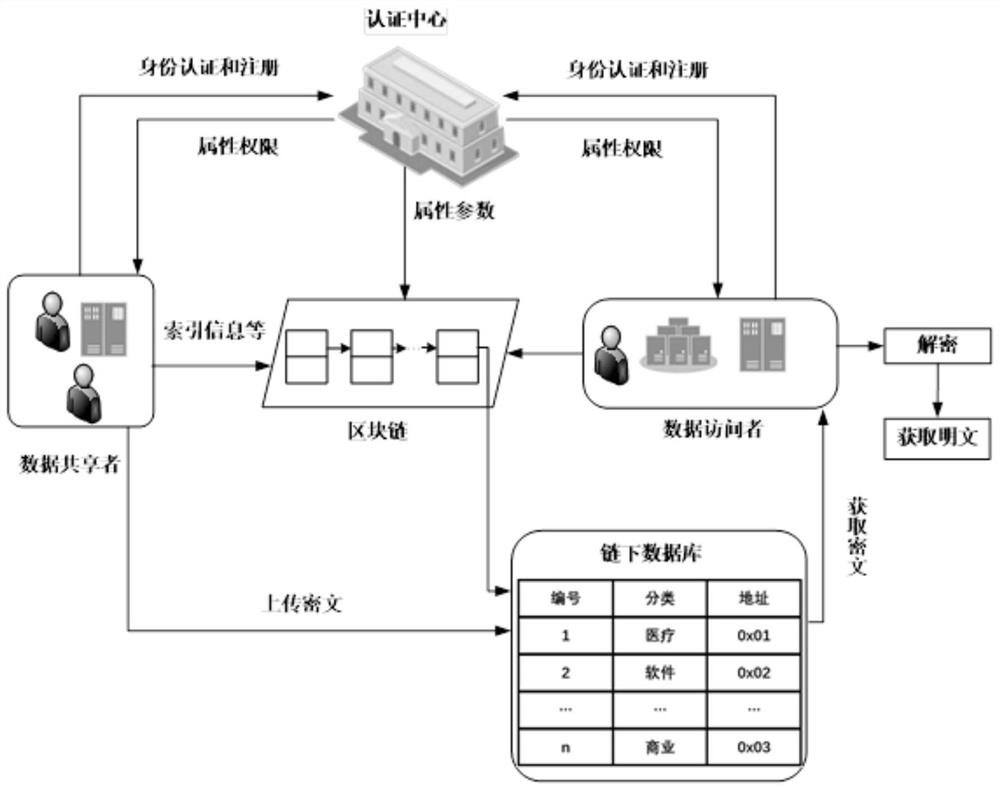
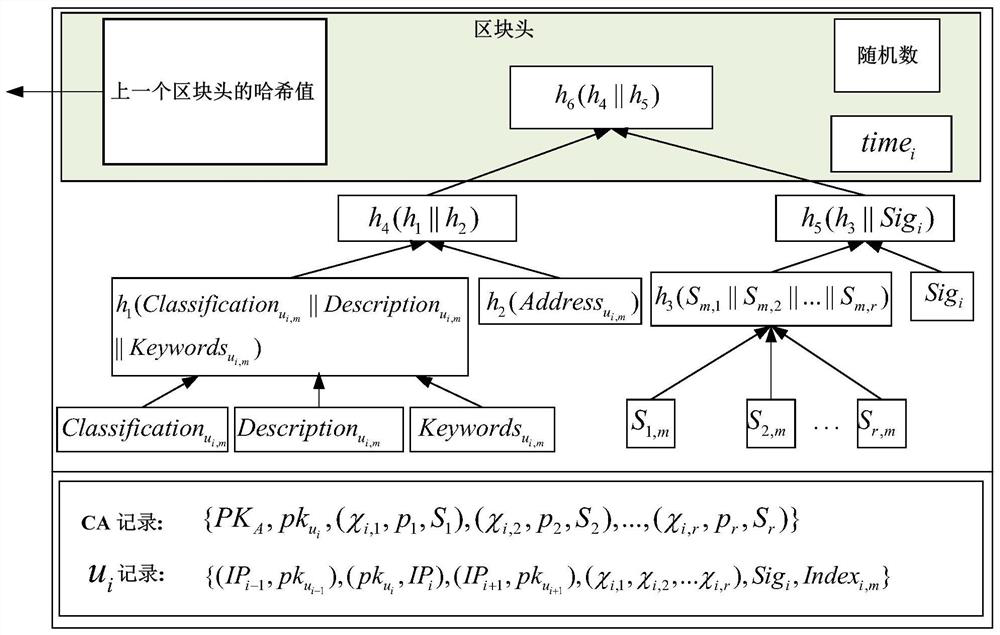
The invention provides an Internet of Things data security sharing method based on privacy protection. The method comprises the following steps: initializing protocol parameters in an information sharing network domain; registering a terminal member; enabling the terminal member to acquire own attribute authority parameters, calculating encryption keys according to the Chinese remainder theorem, encrypting shared information resources and storing the encrypted information resources in an off-chain database; calculating intermediate parameters required for storing the information resources, generating index information of the shared ciphertext and packaging the index information in a block, and so on, enabling each terminal member to store related information of the ciphertext in the blockto generate a block chain; and accessing and sharing the ciphertext. Identity and attribute parameter matching dual authentication is adopted to prevent collusion attacks and protect personal privacy,an attribute matching access control strategy is combined with a block chain technology to guarantee the safety of shared resource information, the storage burden is reduced, information resource sharing in the industrial Internet of Things is more flexible, efficient and practical, and the method has important field research significance and commercial application value.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Mobile quantum voting method based on Chinese remainder theorem
ActiveCN108010178APrevent secondary voting attacksReduce consumptionVoting apparatusChinese remainder theoremQuantum state
The invention discloses a mobile quantum voting method based on Chinese remainder theorem, which is characterized in that a supervisor, a teller and a plurality of voters exist. A quantum state is prepared by the supervisor, moreover, the quantum state is divided into two, one part of quantum bits are sent to the voters to serve as quantum votes, and the other part of the quantum bits are sent tothe teller to serve as vote-checking certificates; each voter performs voting operation on the same quantum vote, the quantum votes are sent to the teller for counting and verification after all voting operations are complete, and ultimately, voting results of all the voters are obtained. The objective of the invention is to solve the problem that conventional mobile voting cannot resist secondaryvoting attacks of dishonest voters and the problem that excessive quantum resource is consumed by conventional distributive voting, and the security of voting operation is enhanced.
Owner:ANHUI UNIVERSITY
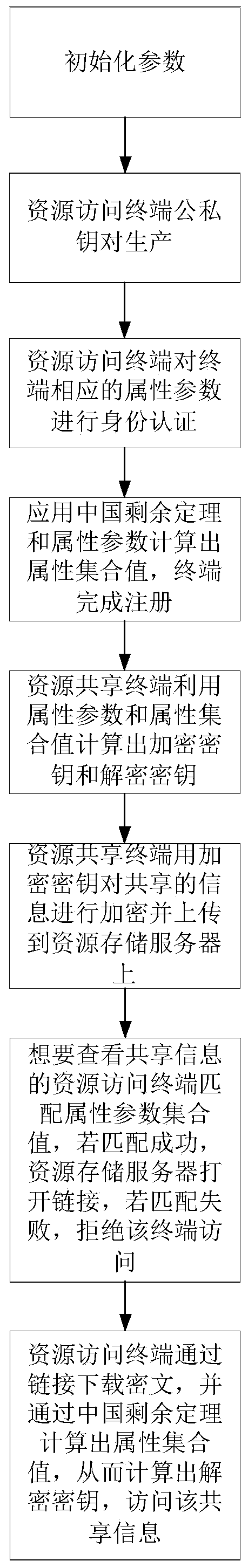
Book resource access control method based on Chinese remainder theorem
ActiveCN111447058AAvoid Collusion AttacksEnsure safetyKey distribution for secure communicationCiphertextChinese remainder theorem
The invention provides a book resource access control method based on the Chinese remainder theorem. The book resource access control method comprises the steps that a book resource authentication center and a resource access terminal generate respective public and private key pairs; the resource access terminals interact with the book resource authentication center to perform attribute identity authentication, and each resource access terminal sends attribute parameters to the book resource authentication center, verifies the attribute parameters and sends the attribute parameters to the resource storage platform; the resource access terminal encrypts the shared resource information into a ciphertext and uploads the ciphertext to the resource storage platform; and the resource access terminal determines a ciphertext resource to be checked according to the ciphertext, the resource storage platform verifies the identity of the ciphertext resource and opens an access link of the ciphertext resource, and the resource access terminal downloads the ciphertext for decryption. Personal privacy is protected by adopting ciphertext attribute authentication, access permission is set by applying an attribute matching access control strategy to guarantee safety of resource sharing, collusion attacks are prevented by adopting identity and attribute permission dual authentication, and book resource sharing in the Internet of Things is more flexible, efficient and practical.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
High-security quantum multi-party privacy summation method
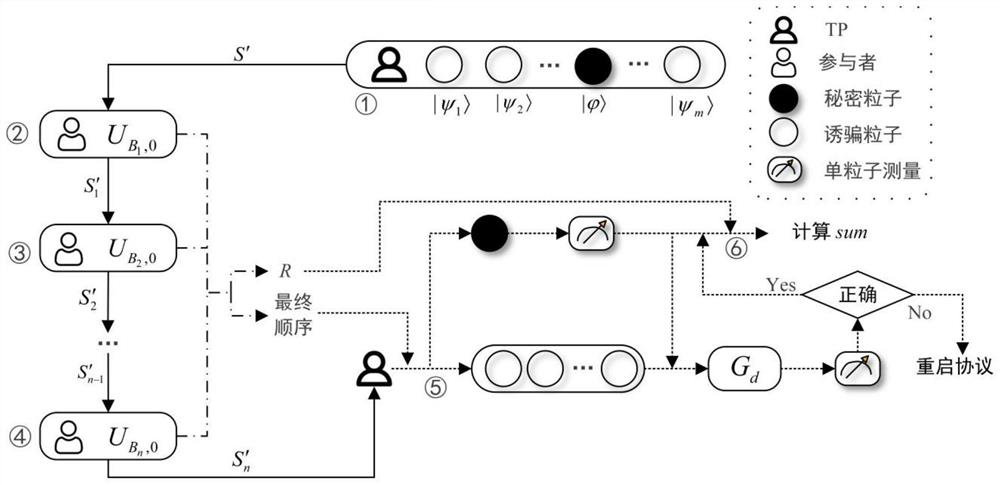
ActiveCN112887034ALow computing power requirementsReduce consumption of resourcesKey distribution for secure communicationPhotonic quantum communicationCommunications securityThird party
The invention relates to the technical field of quantum communication security, in particular to a high-security quantum multi-party privacy summation method, which comprises the following steps that: a third party TP constructs a transmission sequence S' according to a coefficient matrix and a single quantum state, and sends the S' to a participant Bob1 through a quantum channel; the Bob1 executes unitary transformation and particle reordering operation on the received transmission sequence S' to obtain a new transmission sequence S1', sending the S1' to the next participant Bob2; after the Bob2 receives the transmission sequence S1', executing the same operation as the Bob1 and transmitting the operation to the next participant, and sequentially transmitting the transmission sequence in the participants until the last participant Bobn executes unitary transformation and particle reordering on the received transmission sequence to obtain a new transmission sequence S'n and transmitting the new transmission sequence S'n back to the TP; and the TP executing eavesdropping detection on the S'n, if the quantum channel has an eavesdropper, restarting the method, otherwise, requesting the participant to calculate the sum of all random numbers, and the TP calculating the summation value of the privacy of the participant. The method has higher security while effectively reducing resource consumption and communication consumption.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Group key management method base spherical surface in N dimension
InactiveCN101488849AReduce storageSmall amount of calculationKey distribution for secure communicationInformation quantityComputer science
The invention discloses a cluster cryptographic key management method based on N-dimensional spherical surface, after initializing, when a new user enters, the cluster manager receives the user and edits a number for the new user, when the user exits, the cluster manager deletes secret information of the exiting user, if the user enters and exits simultaneously, the secret information of the exiting user can be deleted, the new user is received, the cluster manager receives the user and edits a number for the new user, and the secret information of the new user can be received simultaneously, the, the cluster manager selects mapping parameters and maps each user in the cluster and secret information per se into points in the space respectively; the center of the spherical surface composed of points is solved, and the center and the mapping parameters are disclosed, the editing number of the exiting user also can be disclosed; the user in the cluster can solve the corresponding space point based on the editing number per se further to solve the cluster cryptographic key. The invention can effectively reduce the user storage information, the calculation amount, the information quantity when the cryptographic key is updated, and can keep independence with each other between cryptographic keys.
Owner:SOUTH CHINA UNIV OF TECH
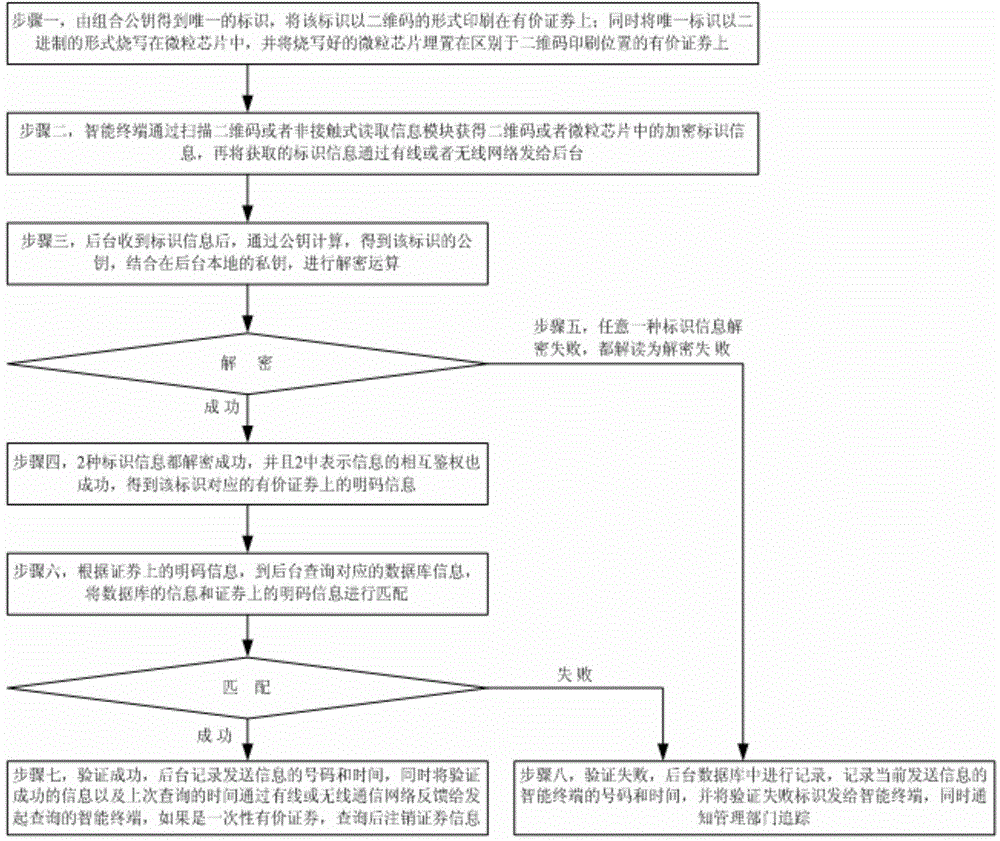
Fast and effective anti-fake identifying method
ActiveCN104091191ALow costPlay anti-counterfeiting effectPaper-money testing devicesRecord carriers used with machinesRead throughSecurity information
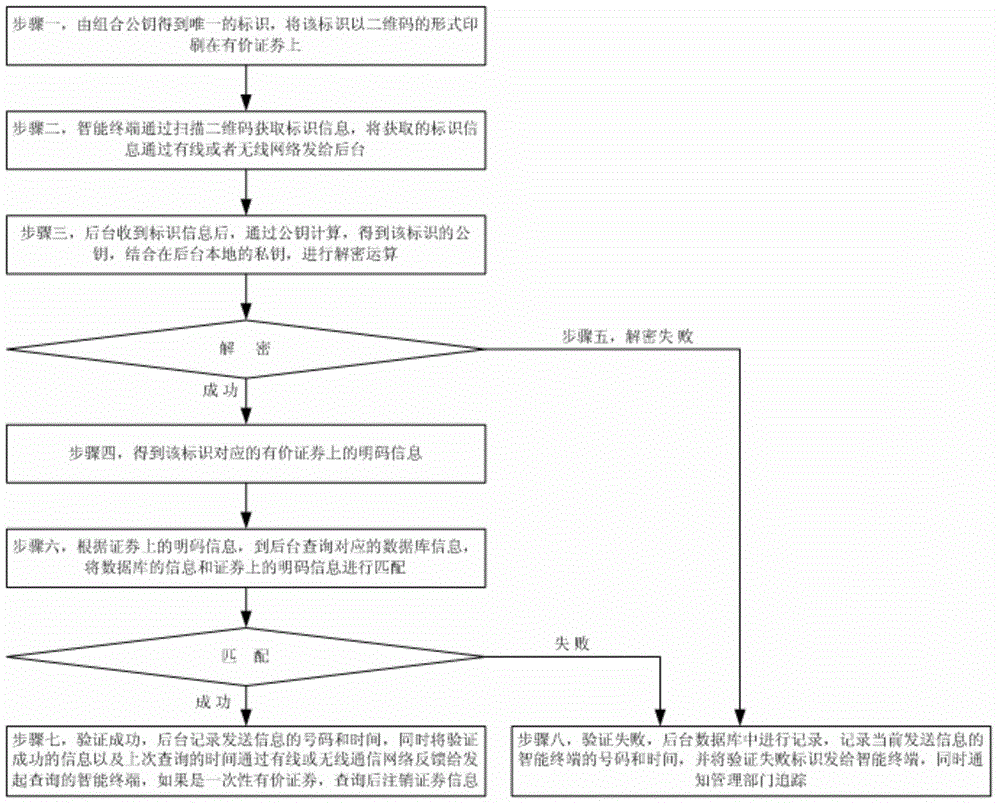
The invention belongs to the technical field of anti-fake identifying, and provides a fast and effective anti-fake identifying method. The anti-fake identifying method includes the following steps that unique identity is obtained through combined public keys and is printed on negotiable securities in a two-dimension code mode; an intelligent terminal scans two-dimension codes to obtain identity information and then sends the identity information to a background through a communication network; public keys of the identity are obtained through public key calculation, and private keys are combined for decryption calculation; if decryption succeeds, plain code information can be obtained; the plain code information is matched with inquiring database information of the background; if the information is matched, it is shown that verification succeeds, the background records and feeds the records back to the intelligent terminal, and if the negotiable securities are disposable, security information is cancelled; if the information is not matched, or decryption fails, it is shown that verification fails, the background performs recording and notifies an administrative department of tracing. The negotiable securities can be read through an intelligent mobile phone, the identity information is matched and encrypted, and the anti-fake identifying advantage is achieved effectively and fast.
Owner:上海象形通讯科技股份有限公司
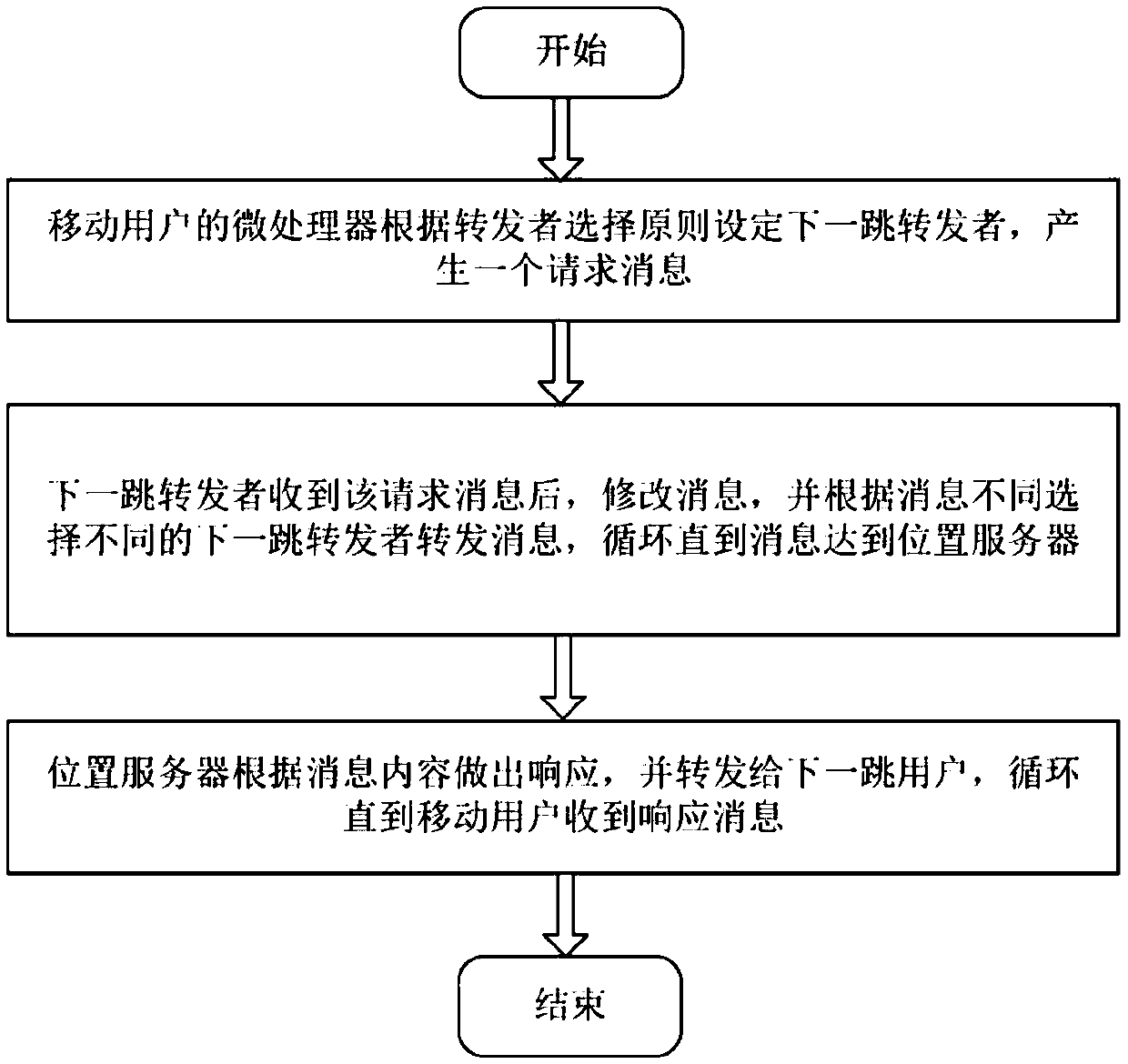
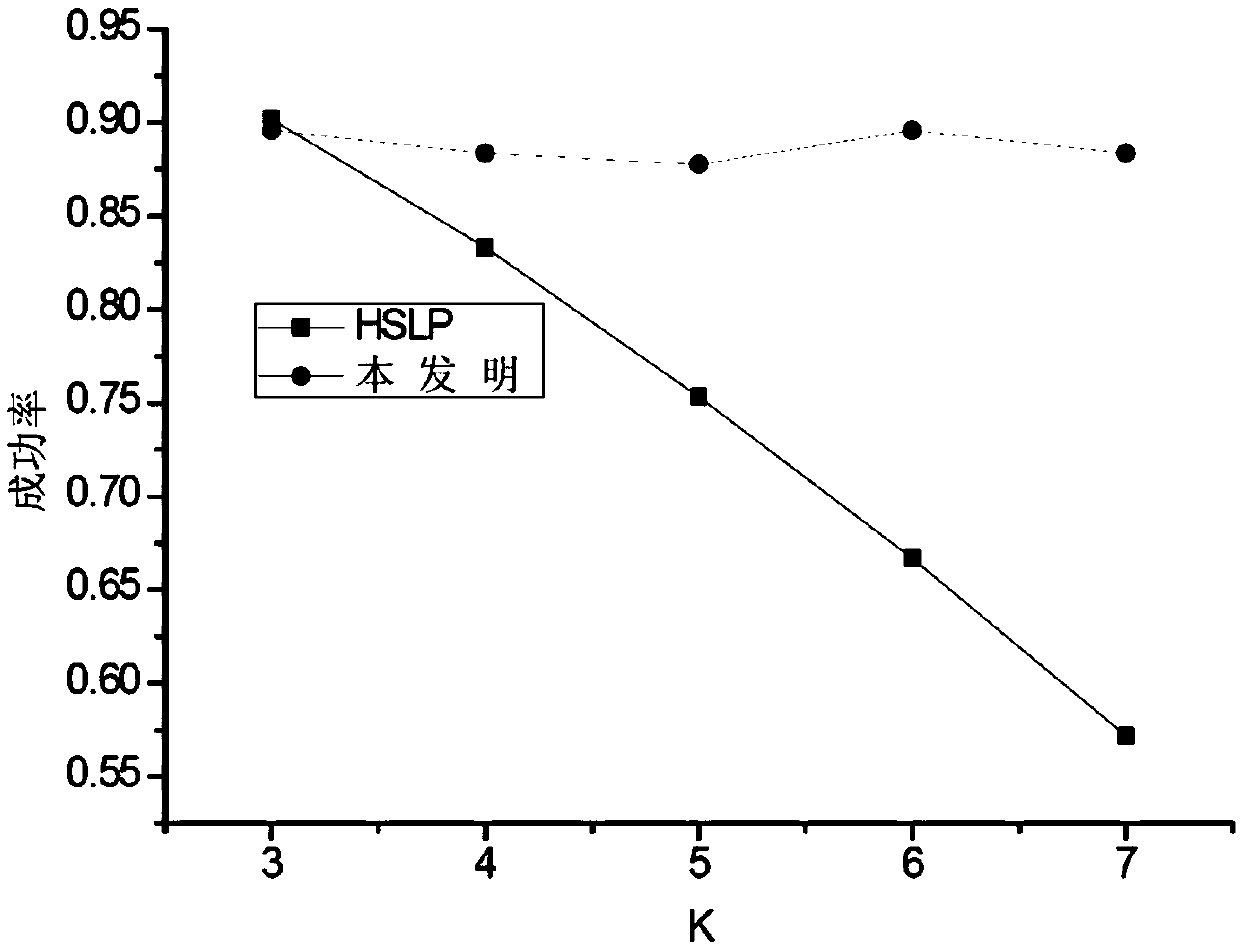
Friend forwarding based location privacy protection method of vehicle-mounted social network
ActiveCN108900977AProtection positionProtect identity privacyParticular environment based servicesServices signallingPrivacy protectionSocial network
The invention discloses a friend forwarding based location privacy protection method of a vehicle-mounted social network. In the location privacy protection method of the vehicle-mounted social network, a location inquiry request massage, which is submitted to a location service, by a mobile subscriber can reach a location server through friend forwarding, and inquiry information fed back by the location server is acquired, so that the location privacy of the mobile subscriber is protected and the success rate of enabling the request massage to reach the server is improved. The friend forwarding based location privacy protection method of the vehicle-mounted social network has the following beneficial effects that (1) a friend forwarding mechanism is adopted to prevent malicious attackersto do collusion attacks, and the location privacy protection intensity of the mobile subscriber is improved; (2) the message reaching success rate of the mobile subscriber can be maintained to be 0.9or more, and the requirements of the subscriber on location service business can be met.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Verifiable constrained quadratic programming safety outsourcing calculation method and system
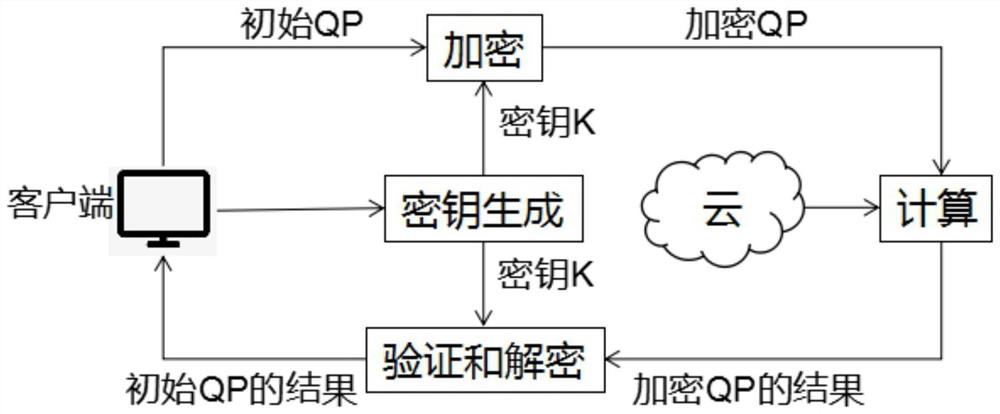
InactiveCN113271293APrivacy protectionSolve difficult problems that cannot be solved by quadratic programmingKey distribution for secure communicationOutsourcing computationCalculation methods
The invention relates to a verifiable constrained quadratic programming safe outsourcing calculation method and system.The client side can outsourcing calculation which cannot be conducted locally to a cloud server for calculation so as to reduce the calculation cost of a user, and the outsourcing process comprises the steps that firstly, the client side initializes setting, encrypts tasks needing outsourcing and sends the tasks needing outsourcing to the cloud server; then, the cloud server receives the task, performs calculation according to requirements, and returns a corresponding result to the client; and finally, the client verifies the correctness of the returned result, if the result is correct, the required original task result is obtained through decryption, otherwise, the result is refused to be accepted, and the cloud server is required to recalculate. According to the method provided by the invention, the client can solve the difficult problem which cannot be solved due to local resource limitation on the premise of protecting own data privacy. Meanwhile, the malicious behavior of the cloud server can be resisted.
Owner:SHANGHAI UNIV
Spatial point set data privacy protection matching method based on similarity binning
ActiveCN111460513AImprove privacy protectionHigh precision adjustabilityDigital data protectionData privacy protectionDegree of similarity
The invention provides a spatial point set data privacy protection matching method based on similarity binning. The method comprises the following steps: grouping point set data range union sets at equal intervals, agreeing data grouping parameters, carrying out space division on original point set data, and obtaining grouping numbers of the point set data based on matching of the point set data and a division space; performing equal-interval binning on the similarity between the point set data and the reference value, calculating the similarity between the attribute value and the reference value, and performing binning on all similarity values by adopting an equal-interval division technology to further obtain binning combinations of all the point set data; and based on matching calculation of the point set data grouping combination number and the sub-box combination number, obtaining an identification number of the point set data according to the grouping number and the sub-box combination number of the point set data, further obtaining a matching point pair of the point set data according to the identification number, and finally exchanging the corresponding point set data according to the matched point pair. The method has the advantages of high privacy protection and precision adjustability.
Owner:NANJING UNIV OF POSTS & TELECOMM
A Method of Multiple Combination Keys
InactiveCN102299794AAvoid Collusion AttacksGood for loss reportingKey distribution for secure communicationUser identity/authority verificationGroup keyPrinciple of orthogonal design
The invention belongs to the field of network information security, and the invention discloses a method of multiple combined keys based on the CPK authentication system: by grouping user IDs, a key matrix for each group of IDs is generated at the same time, and rules are formulated to make each group of IDs The value range is smaller than the rank of the combined key mapping matrix, so as to avoid the risk of collusion to crack, and at the same time, the group keys of multiple groups of IDs are compounded again to obtain the user's key, so that the available key space reaches a sufficient number; according to the key The principle of segmentation is to combine and store the private key matrix of the group ID, so as to resist external and internal attacks on the private key matrix; to add the version number of the ID, so that the ID certificate and key can be updated without changing the user ID.
Owner:北京聚宝网络科技有限公司
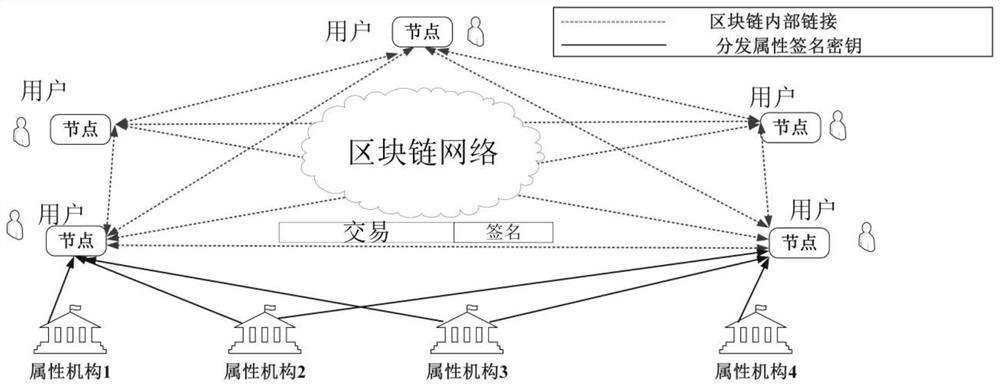
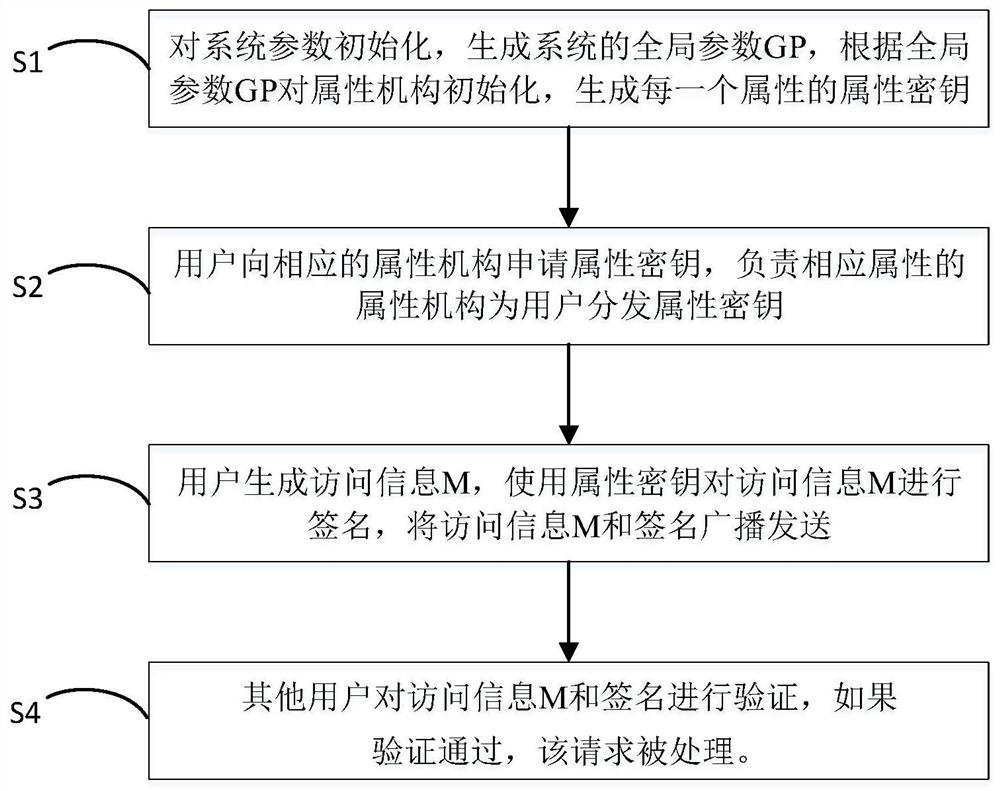
Anonymous identity management and verification method supporting dynamic change of user attributes
PendingCN113656826APrivacy protectionAvoid Collusion AttacksDigital data protectionDigital data authenticationTheoretical computer scienceEngineering
The invention discloses an anonymous identity management and verification method supporting dynamic change of user attributes, which belongs to the field of block chains and mainly comprises four steps of system initialization, generation and updating of an attribute signature key, signature generation and signature verification. According to the method, the problems in the prior art can be effectively solved, management and verification of the user identity can be realized under the condition that the user identity is not leaked, and the process does not depend on a central trust mechanism, so that the method is well suitable for a distributed scene.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
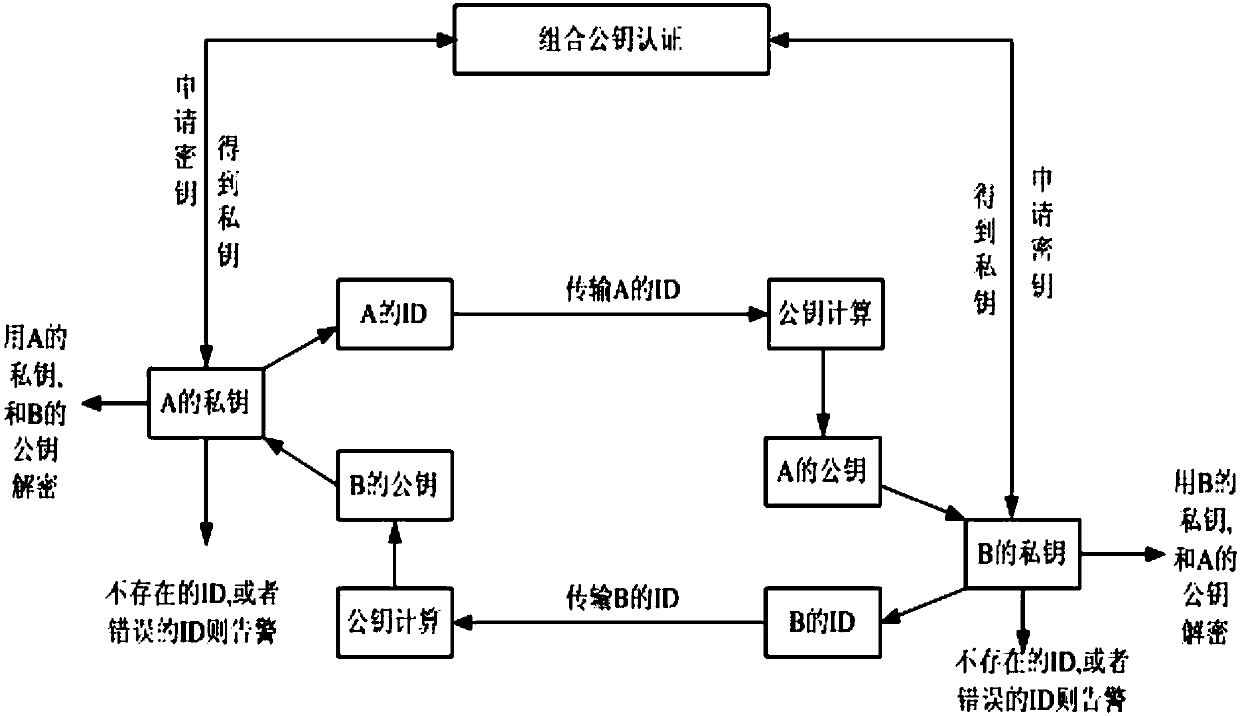
Pair-based combined hierarchical non-interactive key negotiation method
ActiveCN111010269AEnd-to-end securityAchieve end-to-end securityKey distribution for secure communicationEngineeringKey distribution
The invention discloses a pair-based combined hierarchical non-interactive key negotiation method. The method comprises an overall scheme design and a negotiation algorithm design. The method specifically comprises the following steps: S1, registering: the PKG generates system parameters, and generates and distributes corresponding private keys for the first layer of nodes in the domain; S2, intermediate node key distribution: each intermediate node obtains its exclusive CPK private key table from the PKG distribution; S3, extracting of node keys: each intermediate node generates a CPK key component by using the own CPK private key table, and the CPK key component is combined with the hierarchical identity key to form an own node key; S4, establishing of initialization of a session channel, initiating of a communication party and completing of calculation of a session key; S5, formal communication between two parties: a receiving party calculates the session key and decrypts the communication content. The two parties can directly establish an encryption channel without additional communication for key agreement. Public key sharing is achieved through the CPK tables, and the leaf nodes only need to store the two CPK public key tables and do not need to interact with the other communication party in advance to obtain public key information of the nodes.
Owner:NAT UNIV OF DEFENSE TECH
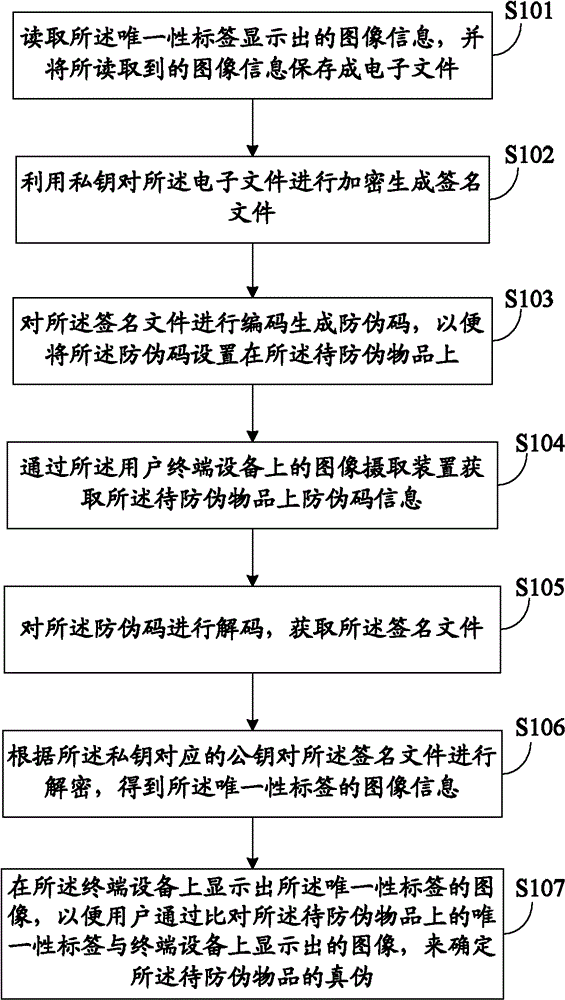
Object anti-counterfeiting method and system
InactiveCN102201100BNon-reproducibleIncrease the difficulty of copyingUser identity/authority verificationSensing by electromagnetic radiationSignature fileTerminal equipment
The invention discloses an object anti-counterfeiting method and system. The method comprises the following steps of: firstly, setting a label on an object to be anti-counterfeited, wherein the label is provided with uniqueness; reading image information displayed by the uniqueness label when anti-counterfeiting verification is carried out, and encrypting the label by utilizing a private key to generate a signature file; encoding the signature file to generate an anti-counterfeiting code so as to set the anti-counterfeiting code on the object to be anti-counterfeited; obtaining anti-counterfeiting information on the object to be anti-counterfeited through an image capturing device on a user terminal device when the truth and false of the object to be anti-counterfeited need to be verified; decoding the anti-counterfeiting code to obtain the signature file; and decrypting the signature file according to public key information corresponding to the private key to obtain and display the image information of the uniqueness label. By adopting the object anti-counterfeiting method and system, the anti-counterfeiting effect can be improved.
Owner:朱清明 +1
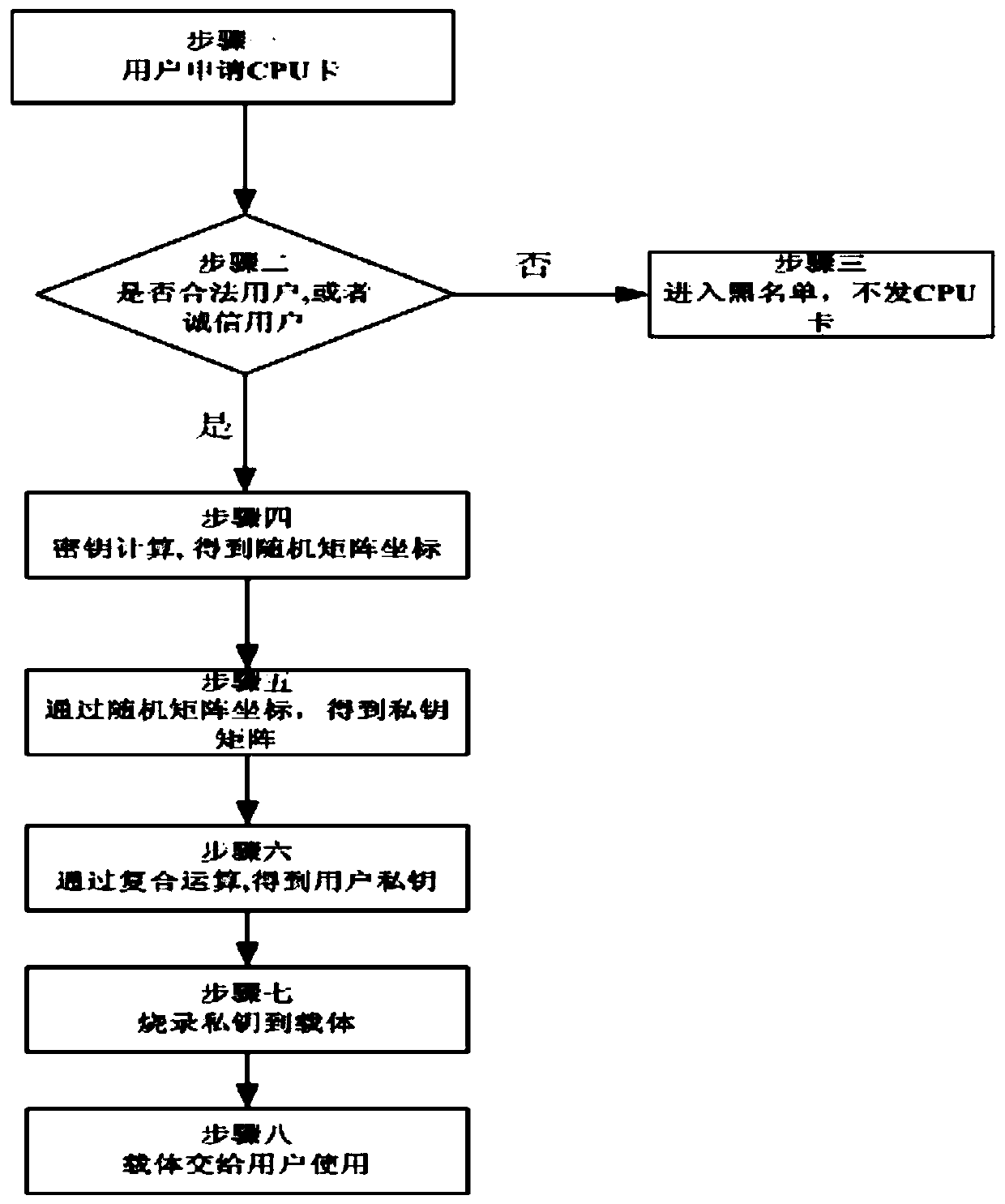
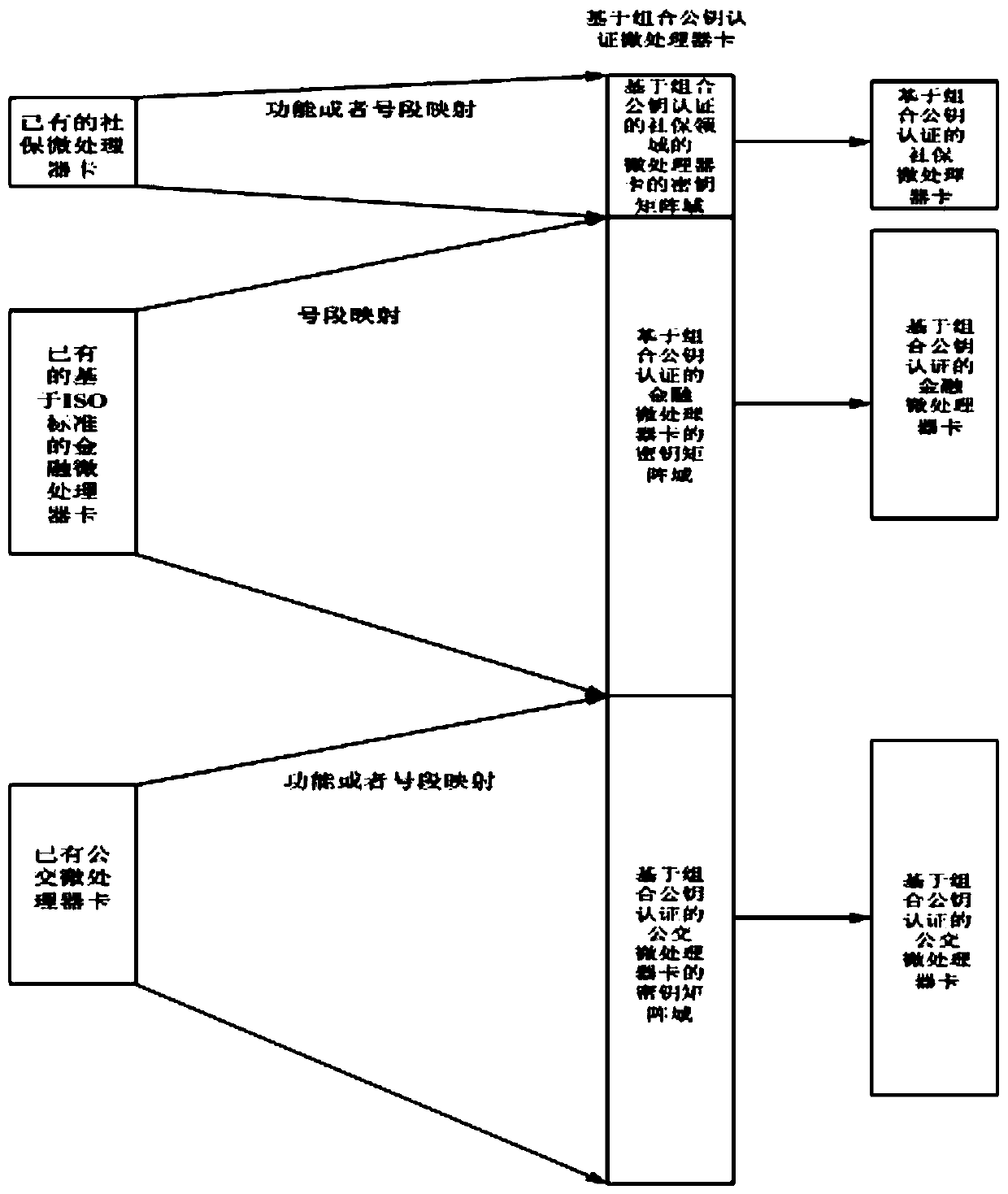
Method based on combined public key authentication microprocessor card cloud management system
ActiveCN104065488BTransmission does not involveRealize associationPublic key for secure communicationUser identity/authority verificationPublic key authenticationIdentity recognition
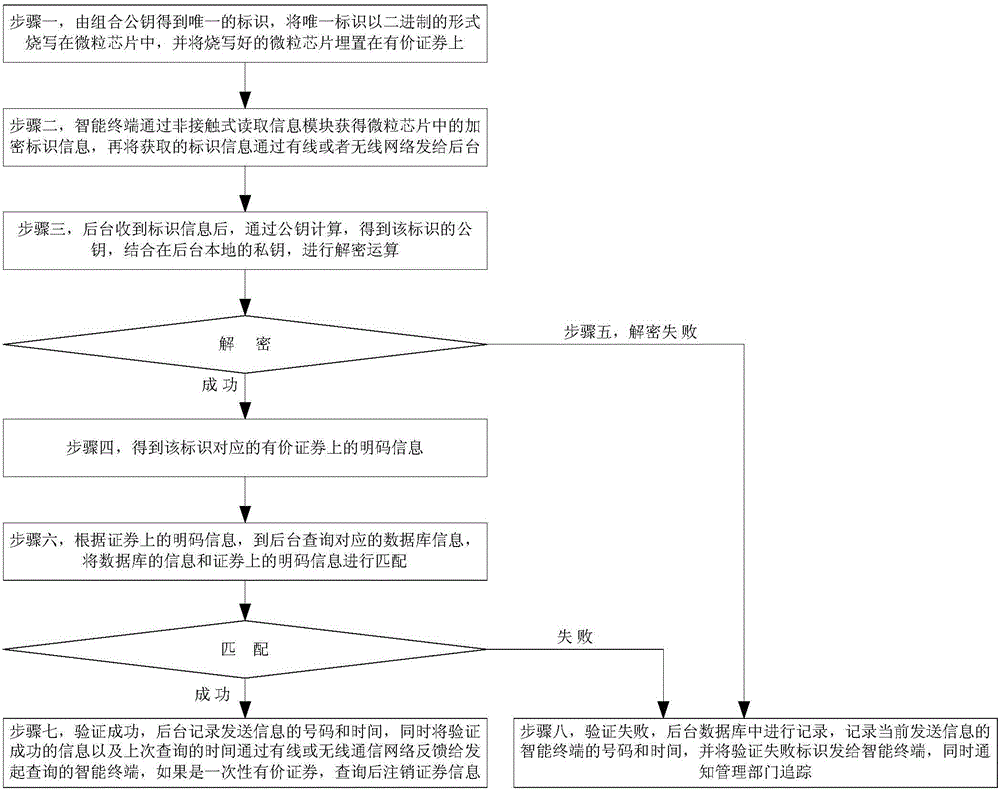
The invention belongs to a microprocessor card cloud management system, and provides a method based on a combined public key authentication microprocessor card cloud management system, comprising the following steps: a user applies for a microprocessor CPU card, collects the user's identification information, and completes the identification identification; to further determine whether the user is a legal user or an honest user; to enter the blacklist, the CPU card will not be issued; to enter the key calculation process, the user will obtain a random matrix coordinate sequence; further obtain the private key matrix, and save it in the secret The key matrix storage center; perform compound operations to obtain the user's identity private key; bind the pseudo-random sequence with the identity private key, and solidify it on the private key carrier; finally, hand over the private key carrier carrying the identity private key to user. The invention has the characteristics of no key transmission, high security, one card with multiple functions, new CPU card and old CPU card can be compatible and docked, use efficiency is improved, and it is beneficial to large-scale popularization and use.
Owner:上海象形通讯科技股份有限公司
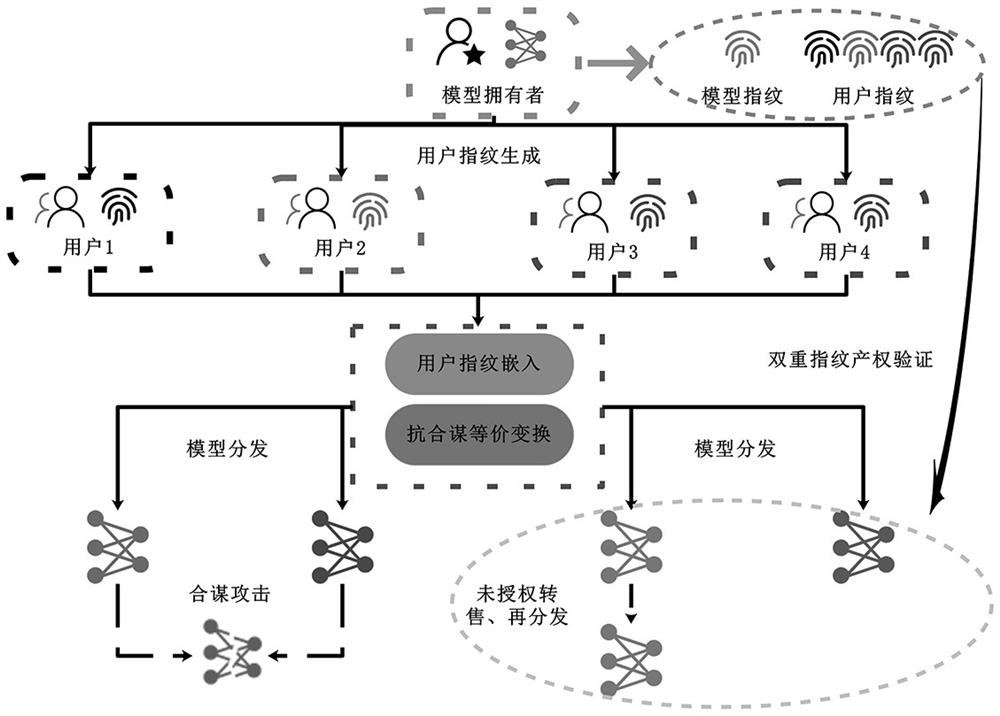
Neural network distribution encryption and anti-collusion attack method thereof
PendingCN114880642AAvoid Collusion AttacksVerified and reliableDigital data protectionDigital data authenticationPattern recognitionAlgorithm
According to the neural network distribution encryption and collusion attack resisting method, a user fingerprint is constructed based on a neural network black box watermark technology, and a model fingerprint of a source model is extracted based on an adversarial sample technology, so that a dual fingerprint verification technology is provided for a neural network model; and a property right tracing and tracking function from coarse granularity to fine granularity is provided by adopting a dual fingerprint verification technology. In addition, two anti-collusion equivalent transformation technologies based on a neural network structure are provided, and active defense against collusion attacks is achieved.
Owner:薇链信息技术有限公司
A blockchain-based security incentive method and system in crowd sensing applications
ActiveCN108055119BAvoid Collusion AttacksAvoid safety hazardsCryptographic attack countermeasuresSensing dataThird party
The invention relates to a block chain-based security incentive method and system in a crowd sensing application. In this method, the client and the server conduct transactions as the transaction parties of the block chain, including the following steps: 1) the server issues a sensing task to the client; 2) after the client executes and completes the sensing task, uploads the sensing data to the server; 3) ) The miners in the blockchain verify the quality of the perceived data and send it to the server; 4) The server pays the client according to the quality of the perceived data. Further, after obtaining the quality of the perceived data, the miners use the principle of mutual information to quantify the effective contribution of the perceived data quality, and send it to the server, and then the server gives the client corresponding rewards according to the effective contribution. The present invention adopts a secure distributed architecture of the block chain to realize security incentives in the application of group intelligence sensing, which can effectively prevent collusion attacks initiated by the sensing platform, and overcome the security risks faced by trusted third parties.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
Book resource access control method based on ciphertext attribute authentication and threshold function
ActiveCN110912897BEnsure safetyGuaranteed leak resistancePublic key for secure communicationView basedCiphertext
The present invention proposes a book resource access control method based on ciphertext attribute authentication and threshold function. The steps are as follows: the authentication center and terminal members generate their own public / private key pairs; the terminal members interact with the authentication center to perform attribute authentication to obtain authority Level value, each terminal member sends the public key and authority level value to the certification center, and sends it to the cloud service platform after verification; the terminal member calculates the encryption key and decryption key and encrypts the shared resource information into ciphertext and uploads it to the cloud Service platform: terminal members determine the ciphertext resources they want to view according to the ciphertext, the cloud service platform verifies their identities and opens the access link of the ciphertext resources, and terminal members download the ciphertext for decryption. The invention adopts ciphertext attribute authentication technology to protect personal privacy, sets threshold function to control access authority to ensure the security of resource sharing, and adopts double authentication of identity and authority to prevent collusion attacks, making information resource sharing in the Internet of Things more flexible, efficient and practical.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Access control system and method supporting cross-domain data sharing, and wireless communication system
ActiveCN110636500BGuaranteed safe transmissionImprove securityPublic key for secure communicationSecurity arrangementKey sizeCommunications system
The invention belongs to the technical field of wireless communication networks, and discloses an access control system and method supporting cross-domain data sharing, and a wireless communication system. Users in domain A who need to share data select elliptic curve parameters to generate ECC key pairs; domain B The global certification center CA of the global certification center CA generates global public parameters; the proxy node in domain B uses the ECC public key of domain A user to encrypt the system public key and attribute set; domain A user uses its own ECC private key to decrypt the data from domain B, upload to the public cloud; the legitimate user sends a file access request to the public cloud; when the user revokes, the proxy server will search for the corresponding attribute private key list according to the user's global identifier and delete it. The present invention has high security under the condition of equal key length. Give full play to the characteristics of strong computing power of proxy nodes, complete some data preprocessing work, and help users partially decrypt, improving user decryption efficiency.
Owner:XIDIAN UNIV
A data integrity audit protocol based on Hyperledger
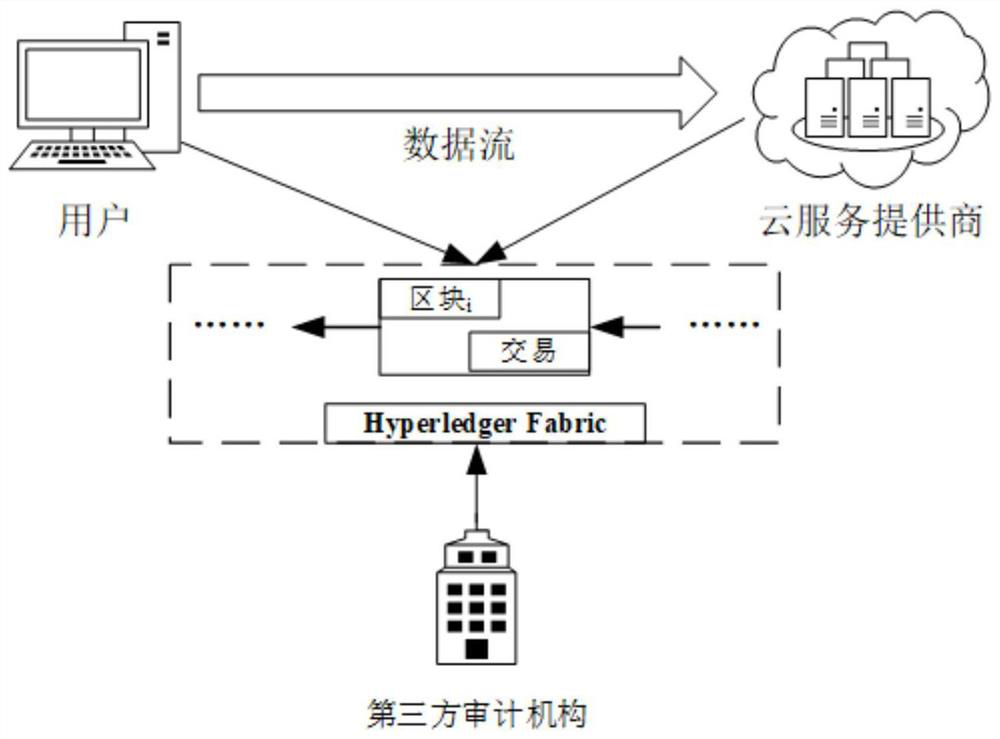
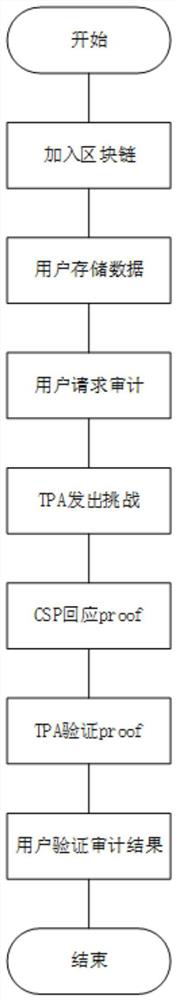
ActiveCN113315740BRealize privacy protectionAchieving Trusted RecordsPublic key for secure communicationThird partyData integrity
The present invention relates to the technical field of information security, in particular to a data integrity audit protocol based on Hyperledger, which realizes data privacy protection during the data integrity audit process by using bilinear pairing technology, and uses Hyperledger Fabric This blockchain technology realizes the credible record of the interactive data of all parties during the data integrity audit process, thereby realizing the traceability function; by using the anonymity function that comes with Hyperledger Fabric, the data integrity audit process is realized. Privacy protection of the identities of all parties; through the use of commitment technology, the temporary concealment and final disclosure of the identities of third-party audit agencies and cloud service providers during the data integrity audit process is realized, and the self-regulatory function is realized; including the following stages: Registration phase, preparation phase, storage phase and audit phase.
Owner:东北大学秦皇岛分校
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com