Data sharing method, device and system, client and storage medium
A data sharing and client-side technology, applied in the field of cloud computing security, can solve problems such as user information leakage and affecting data sharing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
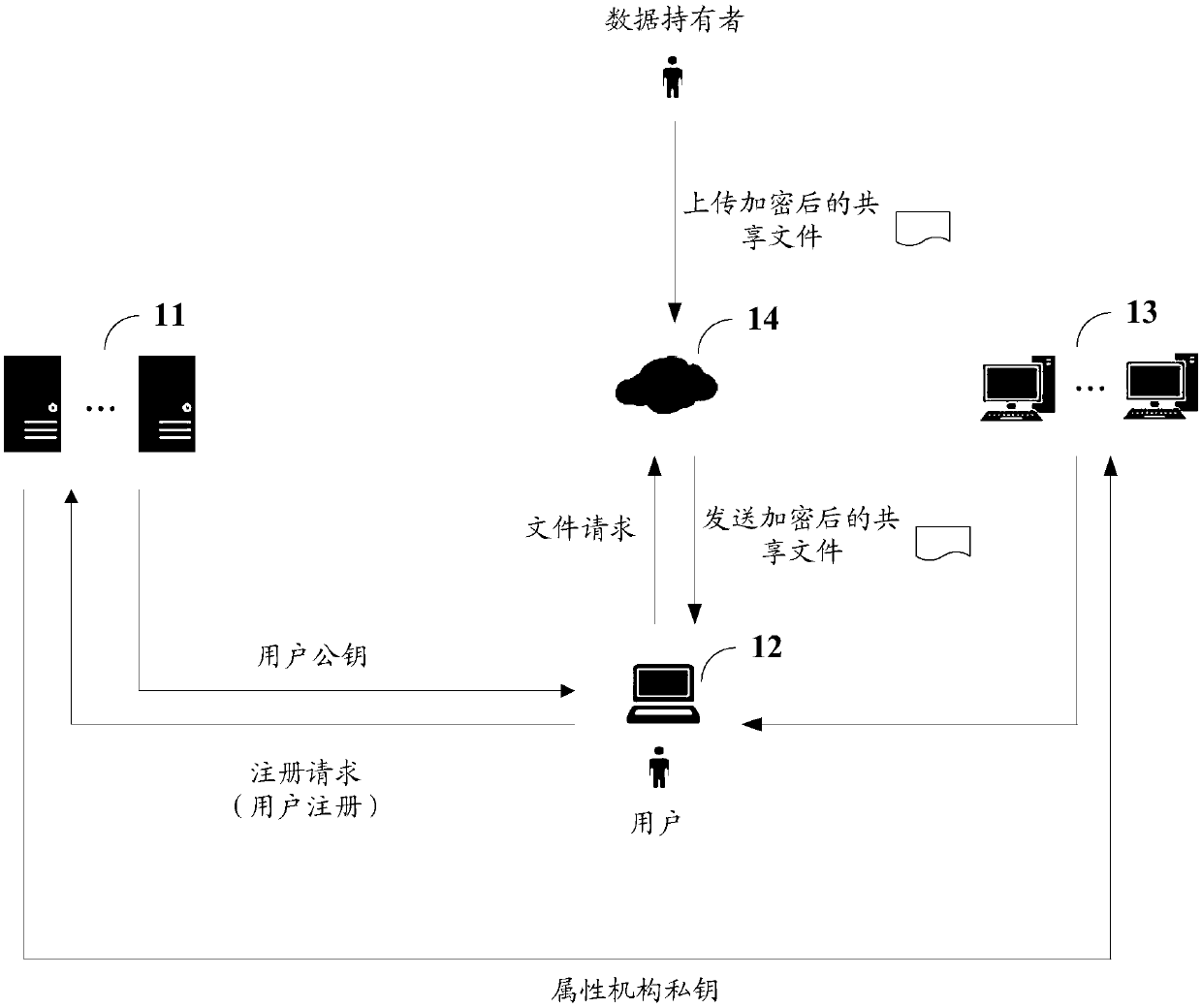
[0042] figure 1 A schematic structural diagram of a data sharing system provided by an embodiment of the present invention, including at least two CA11, client 12, at least two AA13 and cloud server 14:
[0043] The client 12 is configured to send a registration request to any target CA11 of the at least two CA11s, wherein the registration request includes an attribute set of the user of the client 12;
[0044] The target CA11 is used to receive the registration request sent by the client 12, generate the user public key of the user according to the attribute set and the preset random algorithm, and send the user public key to the Client 12;
[0045] The client 12 is further configured to receive the user public key sent by the target CA11, and send the user public key and attribute set to the at least two AA13;
[0046] The at least two AAs13 are used to receive the user public key and attribute set sent by the client 12, and according to the private key corresponding to ea...
Embodiment 2
[0065] In order to facilitate the dynamic addition and deletion of attributes and enhance the practicability of the data sharing system, such as Figure 4 As shown, the system also includes: an attribute control server 15;
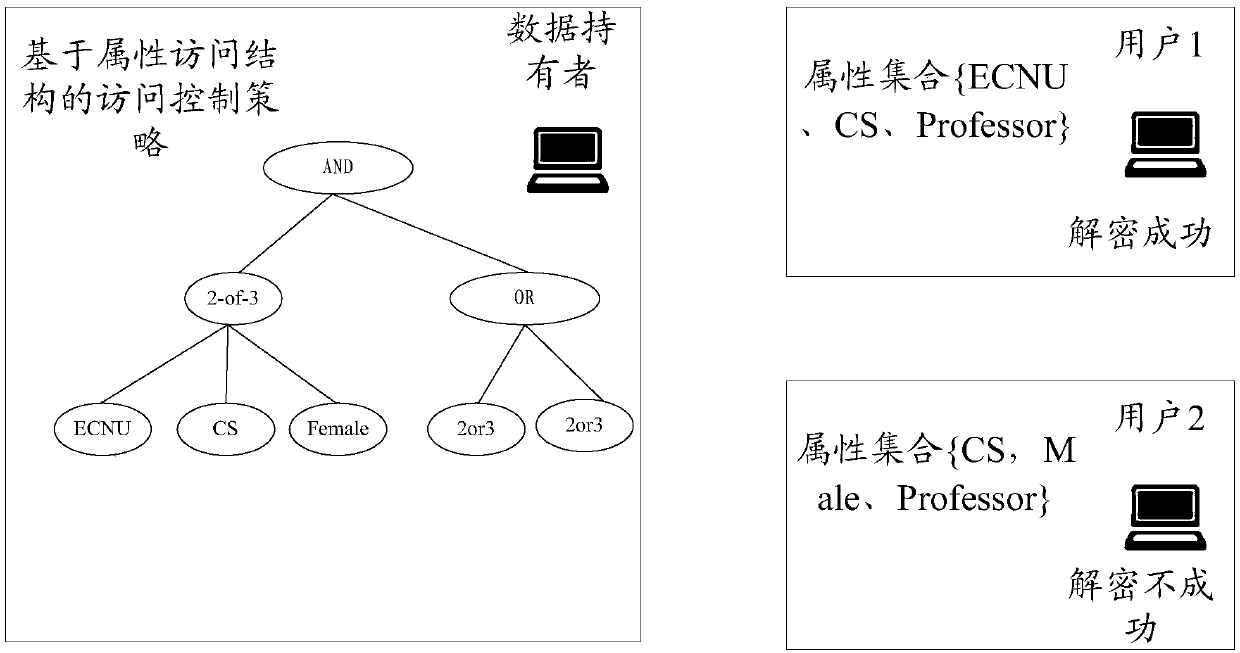
[0066] The attribute control server 15 is further configured to receive a first update request for adding a first attribute; determine a first target category corresponding to the first attribute according to a pre-saved attribute-category comparison table, and identify the at least two Whether there is a first target AA13 that manages the attributes corresponding to the first target category in each AA13; if yes, add the first attribute to the first target AA13; if not, create and manage the first target category The first target AA13 of the corresponding attribute, and add the first attribute to the first target AA13.
[0067] The attribute control server 15 is further configured to receive a second update request for deleting a second attribute, determ...
Embodiment 3
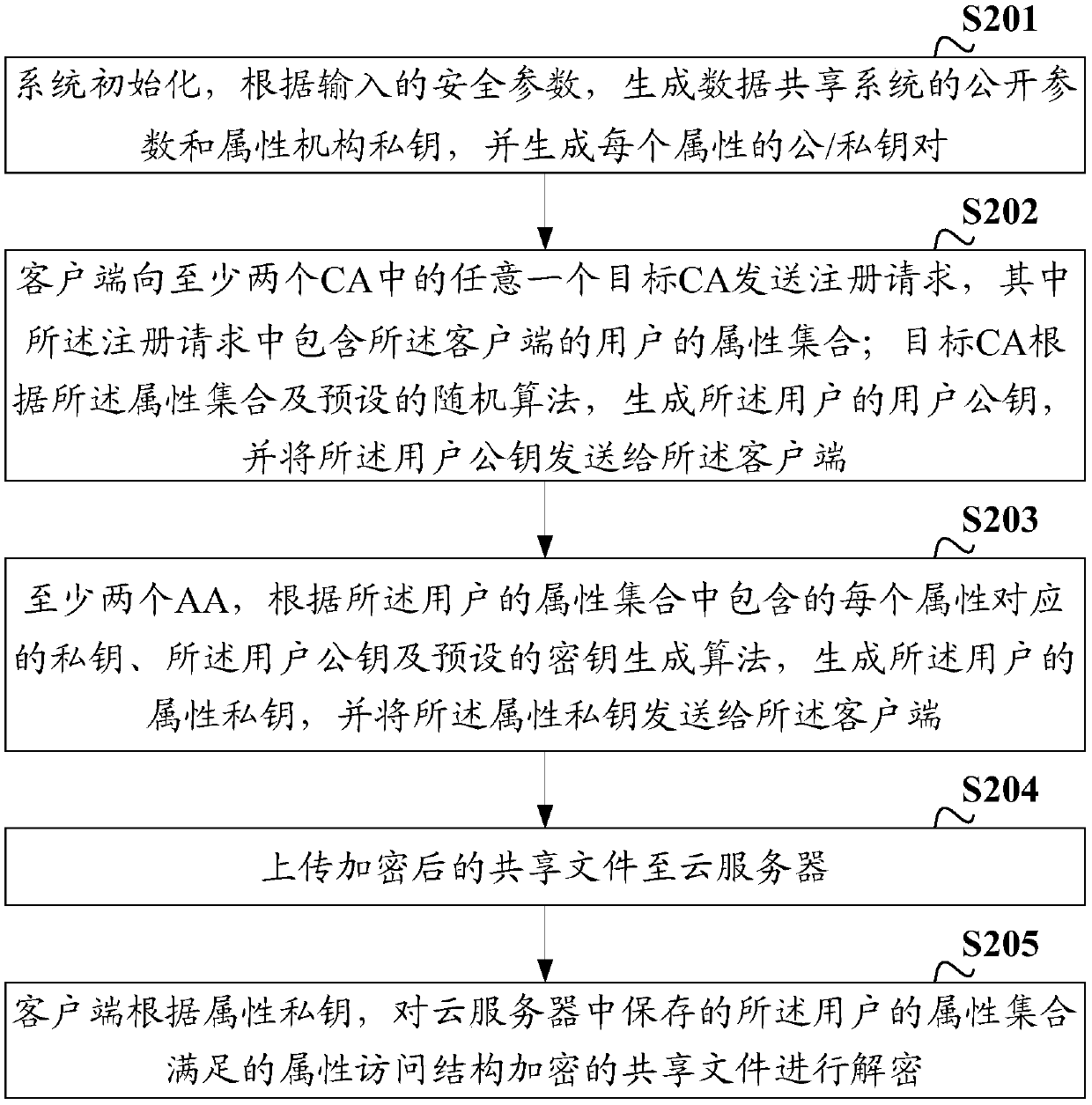
[0074] Based on the above examples, such as Figure 5 As shown, the embodiment of the present application provides a data sharing method, and the specific steps include:
[0075] S501: Send a registration request to any target CA among the at least two certificate authority CAs in the data sharing system, wherein the registration request includes an attribute set of the user of the client, so that the target CA according to the attribute set and a preset random algorithm to generate the user public key of the user.
[0076] S502: Send the user public key and the attribute set to at least two attribute agencies AA of the data sharing system, so that the at least two AAs can use the private key corresponding to each attribute included in the user attribute set, the The user public key and the preset key generation algorithm are used to generate the attribute private key of the user.
[0077] S503: According to the attribute private key, decrypt the shared file stored in the cl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com