Neural network distribution encryption and anti-collusion attack method thereof
A technology of neural network and encryption method, applied in the field of neural network distribution encryption and anti-collision attack, can solve the problems of unrealistic and weak practicability, and achieve the effect of preventing collusion attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
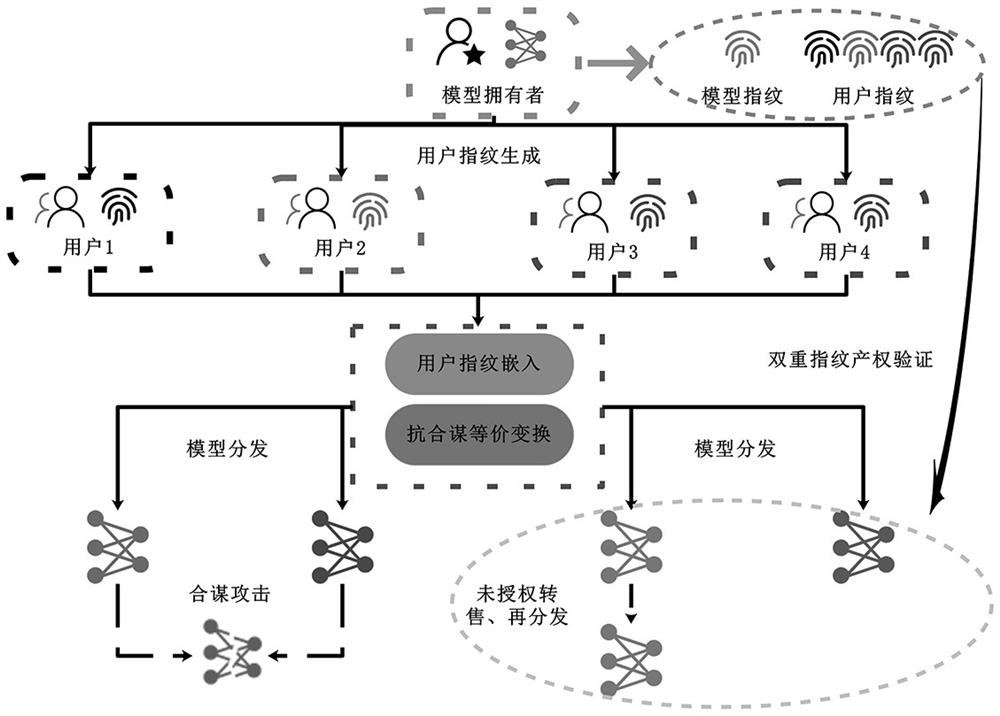
[0085] see figure 1 , the basic structure design of the neural network distribution and property rights protection framework of collusion security, according to its execution elements, this embodiment proposes a neural network distribution scheme of collusion security and property rights security in a black box scenario, which mainly includes two parties: a neural network Network model owner, multiple users to be distributed.
[0086] The specific implementation steps are as follows:
[0087] (1) According to the needs of the system, the owner of the neural network model first uses the adversarial sample generation algorithm to extract n adversarial samples and label pairs on the source model as a set of model fingerprint information.
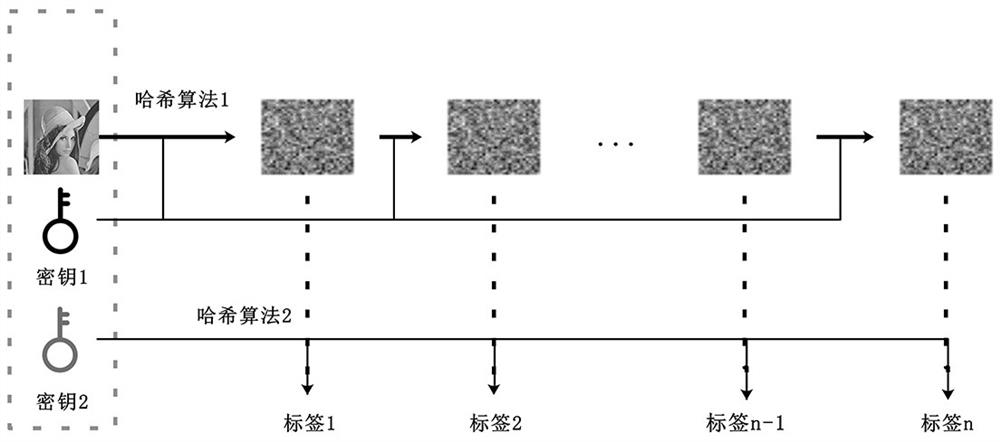
[0088] (2) The model owner generates a relevant key for each user to be distributed, and then generates a series of sample label pairs different from the original data set through the key, as a unique set of users that is different from other ...
Embodiment 2
[0093] Assuming that the neural network model to be distributed or sold has extremely high commercial value, the neural network distribution and property rights protection framework designed in this embodiment can provide property rights tracking and verification through the dual fingerprint verification mechanism, and resist types such as collusion attacks, reverse attacks, Malicious model stealing attacks such as fingerprint removal.
[0094] In the first example, the basic structure required for the neural network distribution and property rights protection scheme against collusion attacks is briefly described, and then this embodiment will further describe the specific implementation details on the basis of the first example. The special features are as follows:
[0095] (1) Model fingerprint extraction of the source model
[0096] Adversarial examples are transferable, i.e. adversarial examples from one model are usually applicable to another model. Therefore, adversari...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com