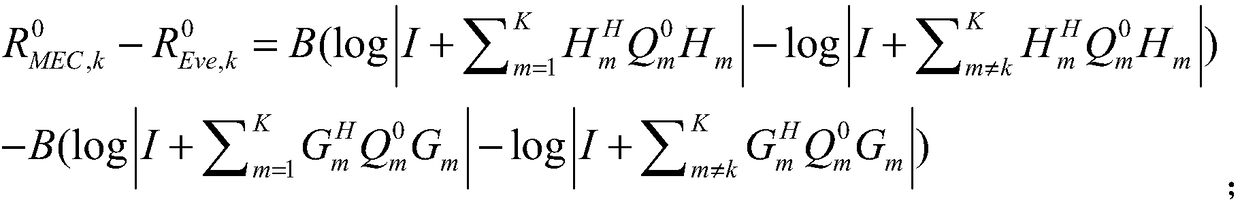Patents
Literature
248results about How to "Guaranteed safe transmission" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
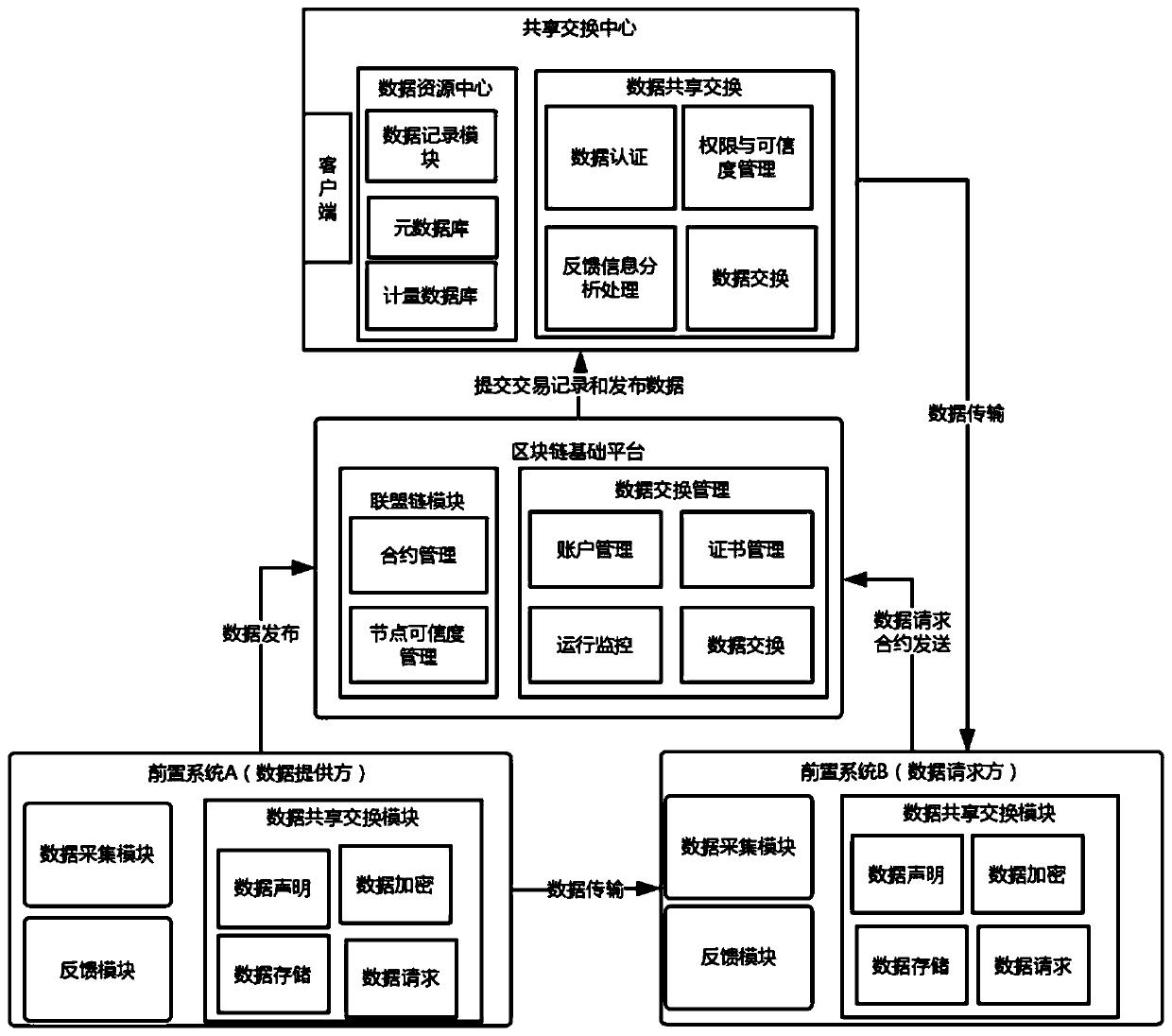
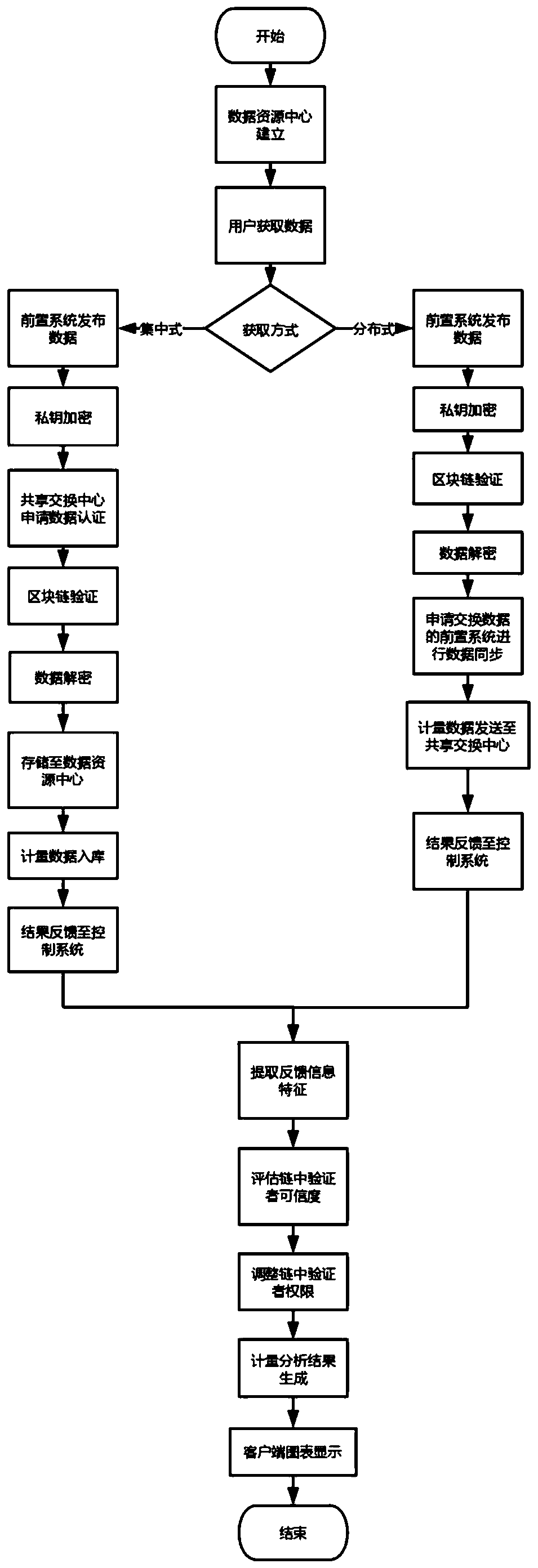
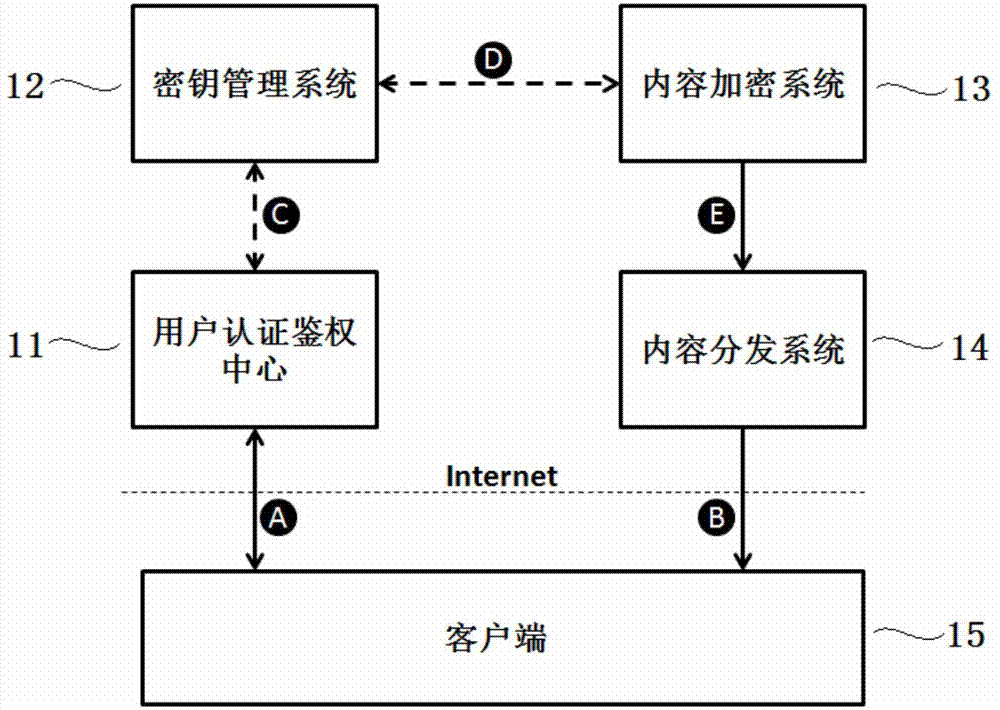
A data sharing exchange system and method based on a block chain
ActiveCN109729168AComply with shared exchange requirementsEasy to modifyUser identity/authority verificationDigital data protectionEnd systemControl system
The invention discloses a data sharing exchange system and method based on a block chain. The system comprises a data sharing exchange center, a front-end system and a block chain basic platform. Thedata sharing exchange center comprises a data sharing exchange control system, a data resource center and a client; The front-end system comprises a data acquisition system, a shared exchange module and a feedback module; The block chain basic platform comprises an alliance chain module and a data sharing exchange management module, the alliance chain module is responsible for intelligent contractand verifying credibility configuration of nodes, the intelligent contract generated in the data sharing exchange process is verified, and the data sharing exchange center communicates with the front-end systems in an alliance chain mode. According to the invention, the credit problem and the incentive problem of data sharing exchange in a multi-party participation environment are solved, the security and the reliability are ensured, the enthusiasm of a user for publishing and updating the sharing exchange data is promoted, and meanwhile, the guiding effect on user decision can be realized.
Owner:浙江成功软件开发有限公司
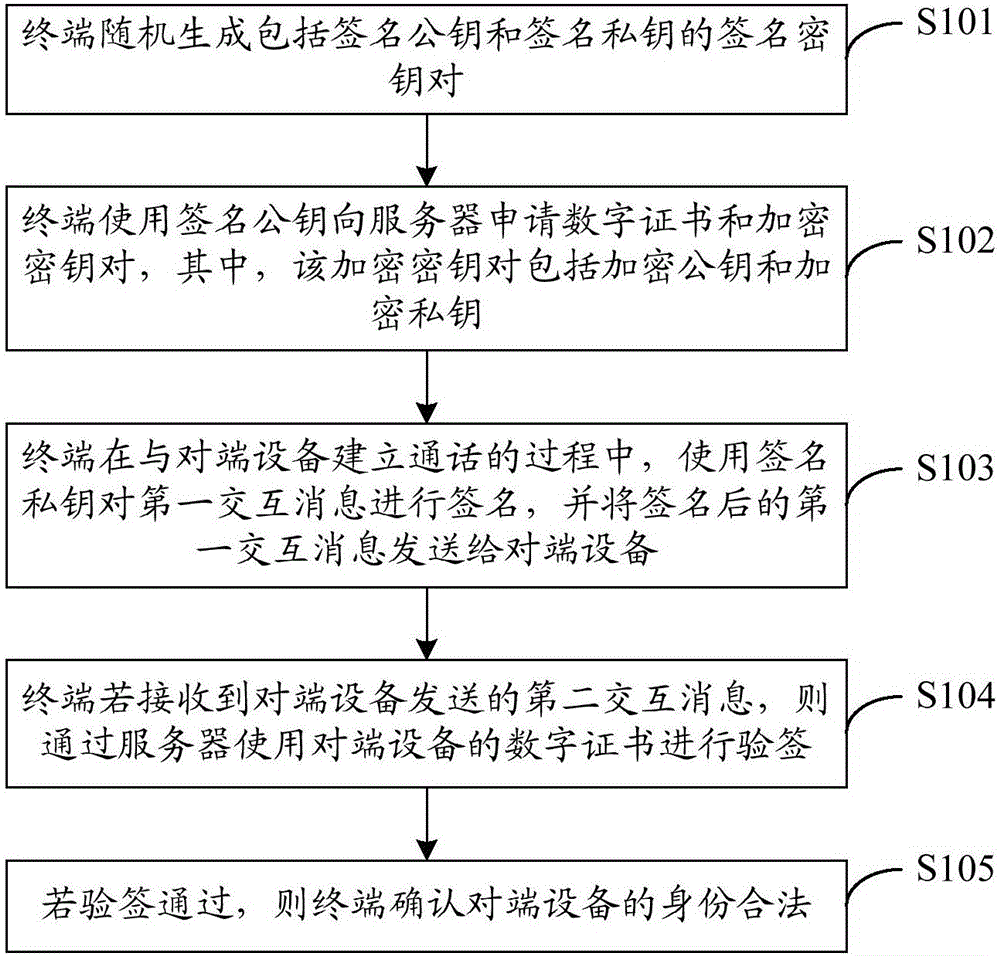
Identity authentication method and system
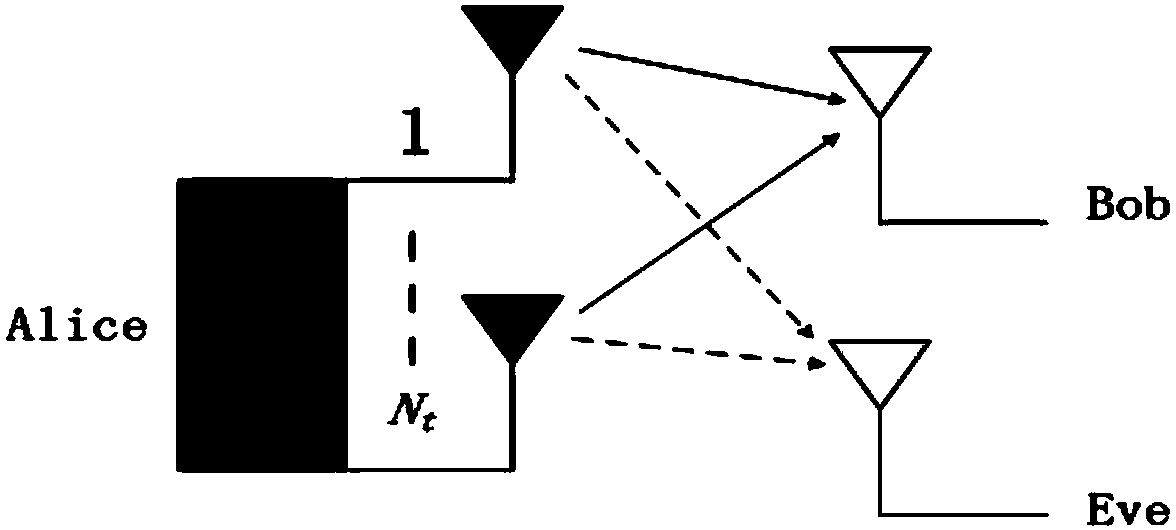
ActiveCN106453330AAvoid attackGuaranteed safe transmissionTransmissionSecure transmissionTerminal equipment
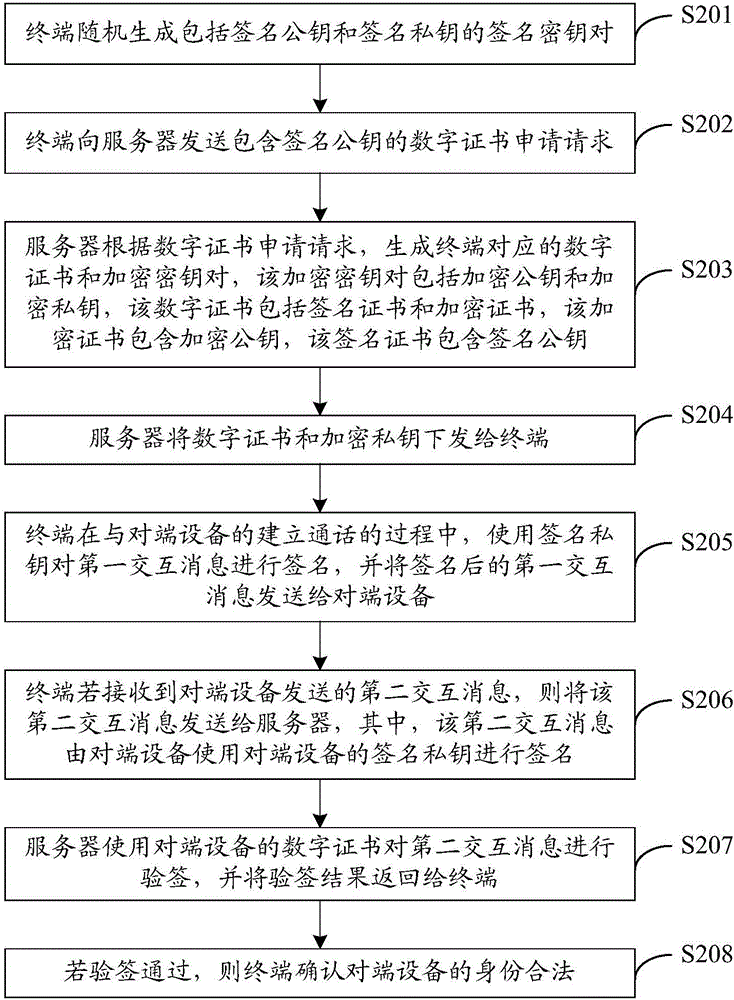
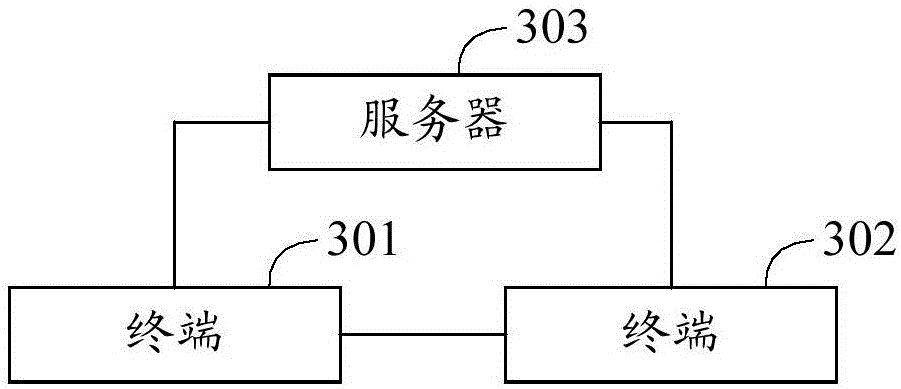
The embodiment of the invention discloses an identity authentication method and system, and the method comprises the steps that a terminal randomly generates a signature secret key pair comprising a signature public key and a signature secret key; the terminal uses the signature public key to apply for a digital certificate and an encryption secret key pair from a server; the terminal carries out the signature of a first interaction message in a process of building communication with opposite terminal equipment through the signature secret key, and enables the first interaction message after signature to be transmitted to the opposite terminal equipment; the terminal carries out the signature of the digital certificate of the terminal equipment through the server if the terminal receives a second interaction message sent by the opposite terminal equipment; and the terminal confirms the valid identity of the opposite terminal equipment if the signature verification is passed. According to the embodiment of the invention, the method can carry out the verification of the validity of the identities of two communication sides of intelligent terminals through the valid generation and transmission of the digital certificate and the combination with the server to complete the signature and signature verification processes, and guarantees the safe transmission of communication contents.
Owner:SHENZHEN TRANSSION HLDG CO LTD
Cloud resource access control method based on dynamic cross-domain security token
InactiveCN102984252AImprove protectionEnsure safetyKey distribution for secure communicationUser identity/authority verificationCloud resourcesAuthentication
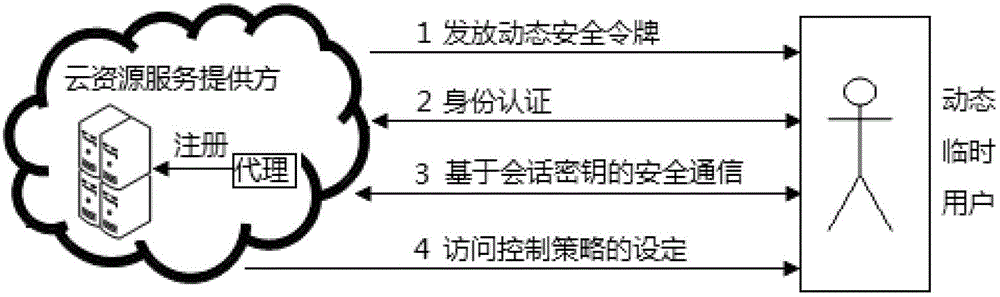
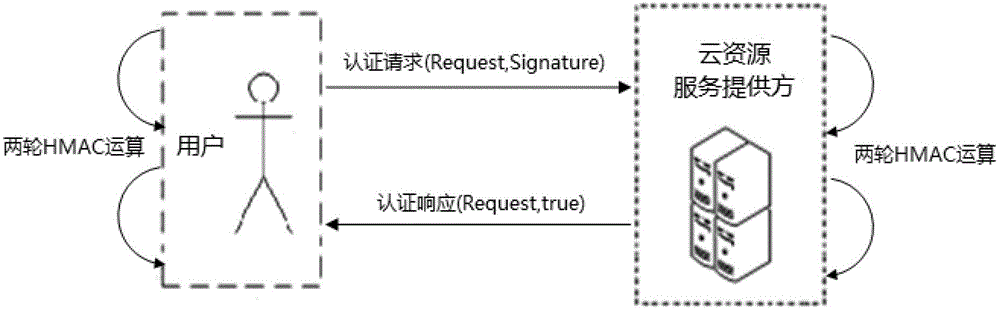
The invention discloses a cloud resource access control method based on a dynamic cross-domain security token. The method includes that 1) an access agent is preset on a cloud resource service providing party and requests a dynamic security token for each dynamic temporary user to the cloud resource providing party; 2) the cloud resource providing party generates the dynamic security token, sets the access strategy and transmits the strategy to the dynamic temporary users; 3) a sharing secrete key is respectively set between each dynamic temporary user and the cloud resource providing party; 4) the dynamic temporary users conduct signing on the access request through the sharing secrete key and transmit the authentication request news to the cloud resource providing party; and 5) the cloud resource providing party conducts signing on the authentication request news through the sharing secrete key, authentication passes if signatures are identical, the access strategy of the dynamic security token and the access agent is judged, and the access request of the dynamic temporary users is responded according to judgment results. The method achieves the high-efficiency cross-domain authentication mechanism and is high in judgment efficiency.
Owner:INST OF INFORMATION ENG CAS
Image encryption method based on block scrambling and state conversion
ActiveCN112422268AGuaranteed safe transmissionSuitable for encryptionEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsAlgorithmSecure transmission
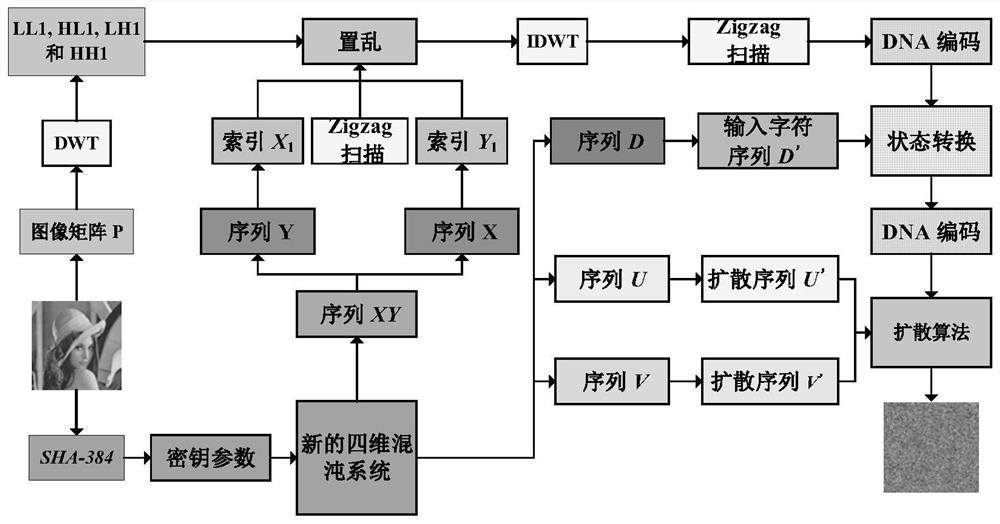
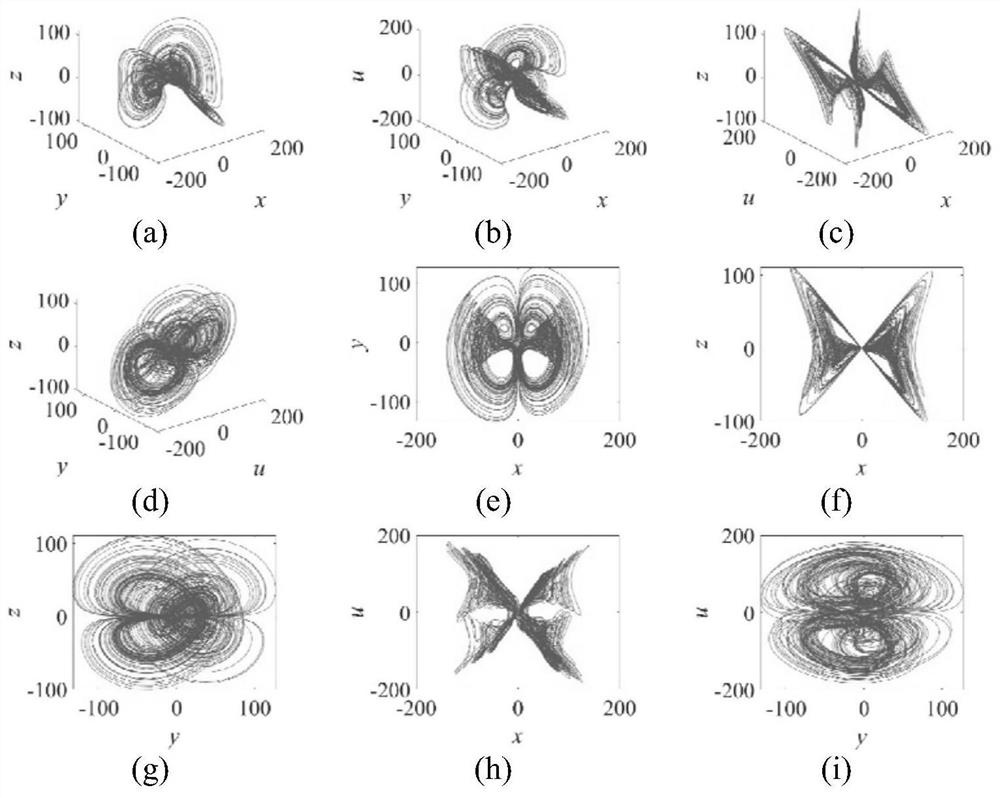
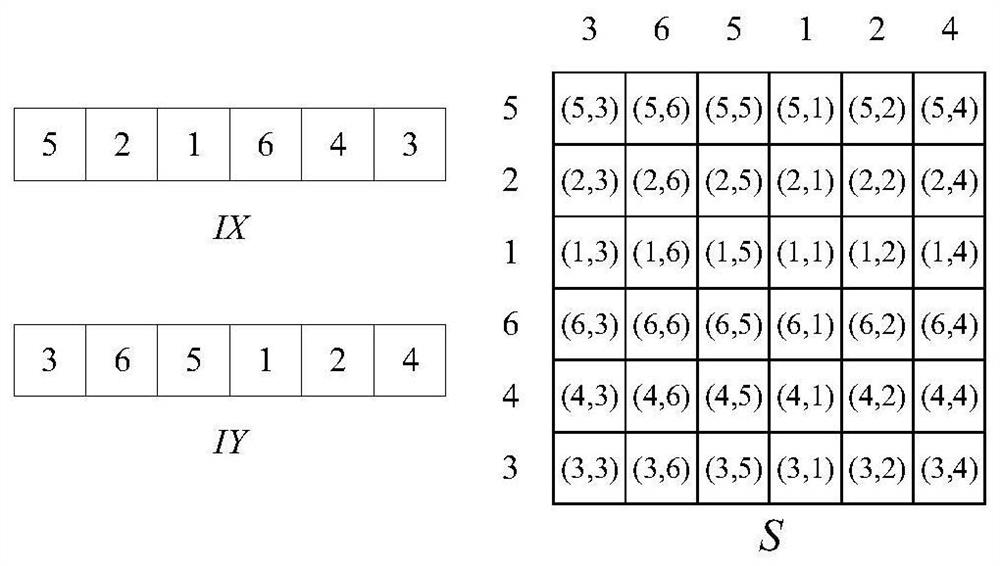
The invention provides an image encryption method based on block scrambling and state conversion, and the method comprises the steps: carrying out the processing of an image matrix through a secret key generation system, generating an initial iteration parameter, inputting the initial iteration parameter into a four-wing 4D chaotic system, and carrying out the iteration to generate four chaotic sequences; intercepting the chaotic sequence and performing descending sort to obtain row and column scrambling vectors to generate a scrambling matrix; scrambling the scrambling matrix by using a scanning curve; scrambling the image matrix by using the scrambled matrix to obtain a pixel scrambling matrix, and performing DNA encoding and chaotic sequence input on the pixel scrambling matrix to determine a finite state automaton to obtain a state conversion sequence; performing DNA decoding on the state conversion sequence to obtain a state conversion sequence; and diffusing the state transitionsequence E by using the chaotic sequence to obtain an encrypted image. The scrambling method can effectively break the correlation of adjacent pixels, can resist various attacks, is high in safety, ensures safe transmission of images, and is very suitable for image encryption.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
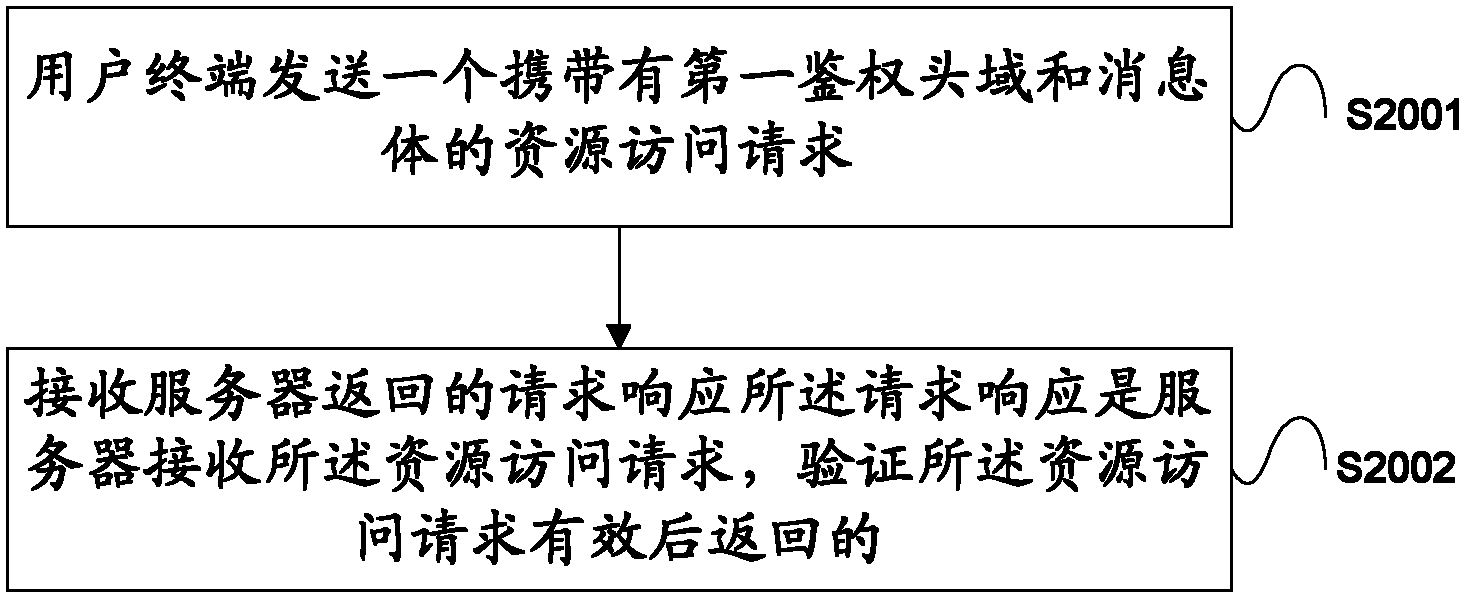
Method, device and system of transmitting data safely
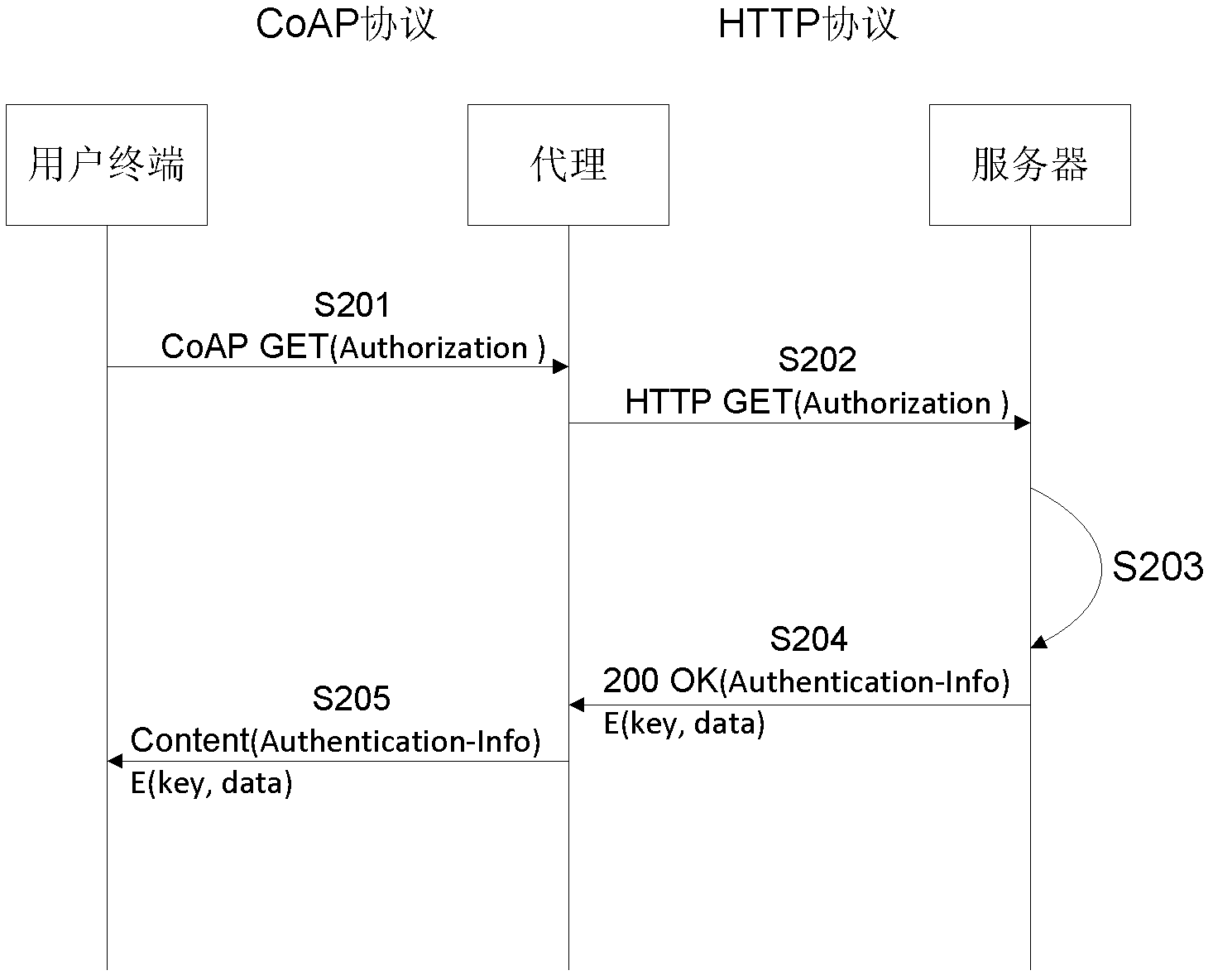
InactiveCN103166931AEnsure safetyGuaranteed safe transmissionKey distribution for secure communicationSecurity arrangementCOAP protocolPassword
The invention provides a method, a device and a system of transmitting data safely. The method of transmitting data safely is characterized by comprising that a user terminal sends a resource access request carrying a first authentication request header field to a server, wherein the first authentication request header field comprises user identification and server identification; a request response returned by the server is received, the request response comprises a second authentication request header field and a message body, and the second authentication request header field carries a third integrity summery; and after the server receives the resource access request, the third integrity summery is further obtained by calculation, wherein the calculation is carried out by using a third a message digest algorithm according to a user password and message contents and by using, and the message body carries the message contents encrypted by a shared key. The user password is obtained from the storage area of the server according to the user identification carried by the resource access request. The machine-to-machine (M2M) transmission based on a constrained application protocol (CoAP) is enabled to be carried out safely and reliably.
Owner:HUAWEI TECH CO LTD
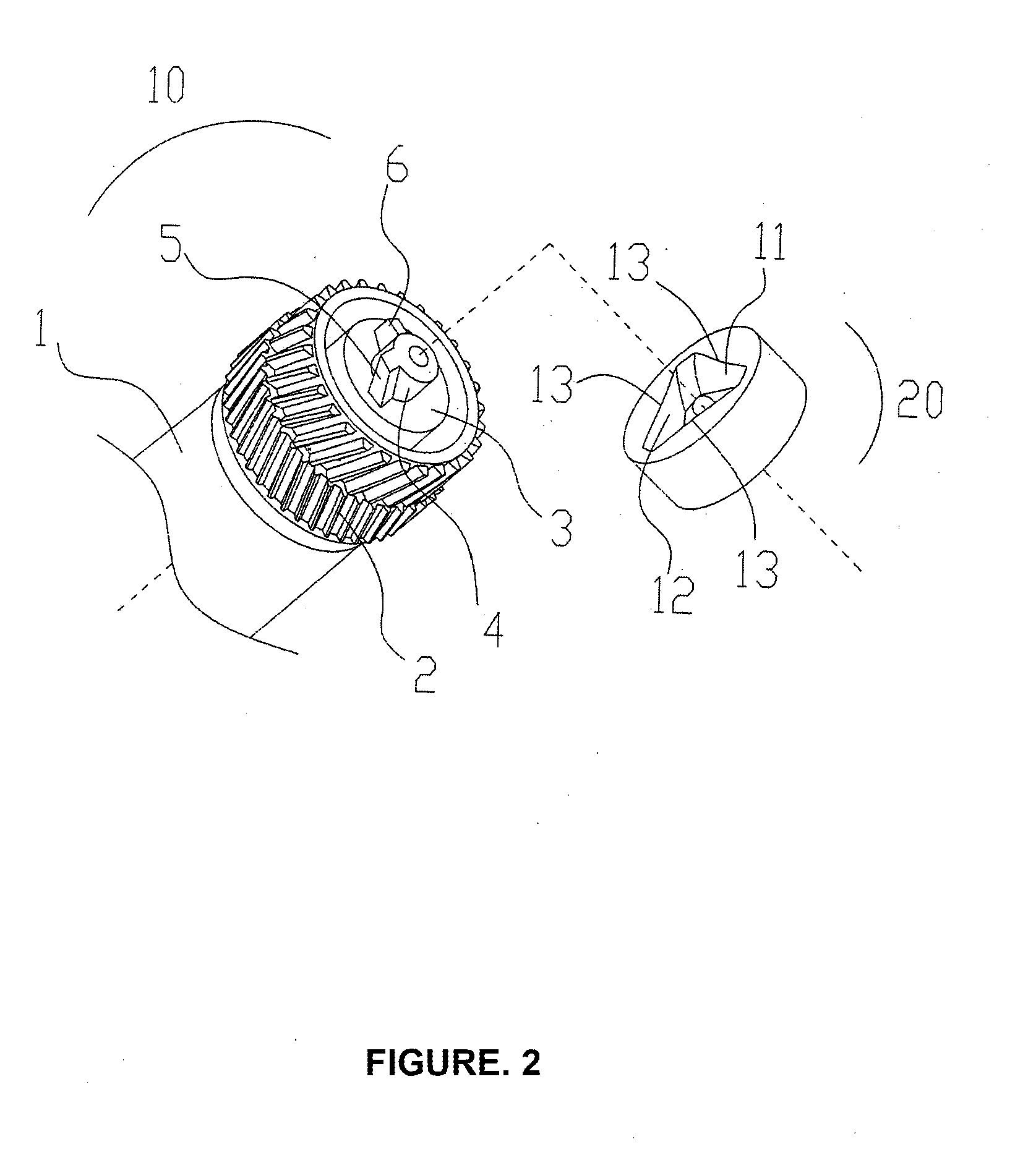
Process cartridge
InactiveUS20120257906A1Effective and continuous transmissionSimple configurationYielding couplingElectrographic process apparatusEngineeringImaging equipment
The present invention relates to a process cartridge, comprising a photosensitive drum driving component in conjunction with an image forming apparatus driving head, wherein said image forming apparatus driving head includes a twisted recess and said photosensitive drum driving component includes a drum gear provided at an end of a photosensitive drum and connected to the photosensitive drum, a drum shaft outwardly projected in an axis direction from an end of the drum gear for rotatably supporting said photosensitive drum during operation and a boss outwardly projected from an end surface of the drum shaft. A first teeth and a second teeth in a radial direction of the boss are provided on a side wall of said boss, wherein said first teeth is engaged with a twisted-section of the twisted recess in said image forming apparatus and said second teeth is engaged with an end surface edge of other twisted-sections of the twisted recess in said image forming apparatus. Thereby, the process cartridge according to this invention ensures an effectively and continuously transmitted driving force and contains a simple prepared photosensitive drum driving head, which will be less damaged even during long time operation.
Owner:JIANGXI YIBO E TECH CO LTD
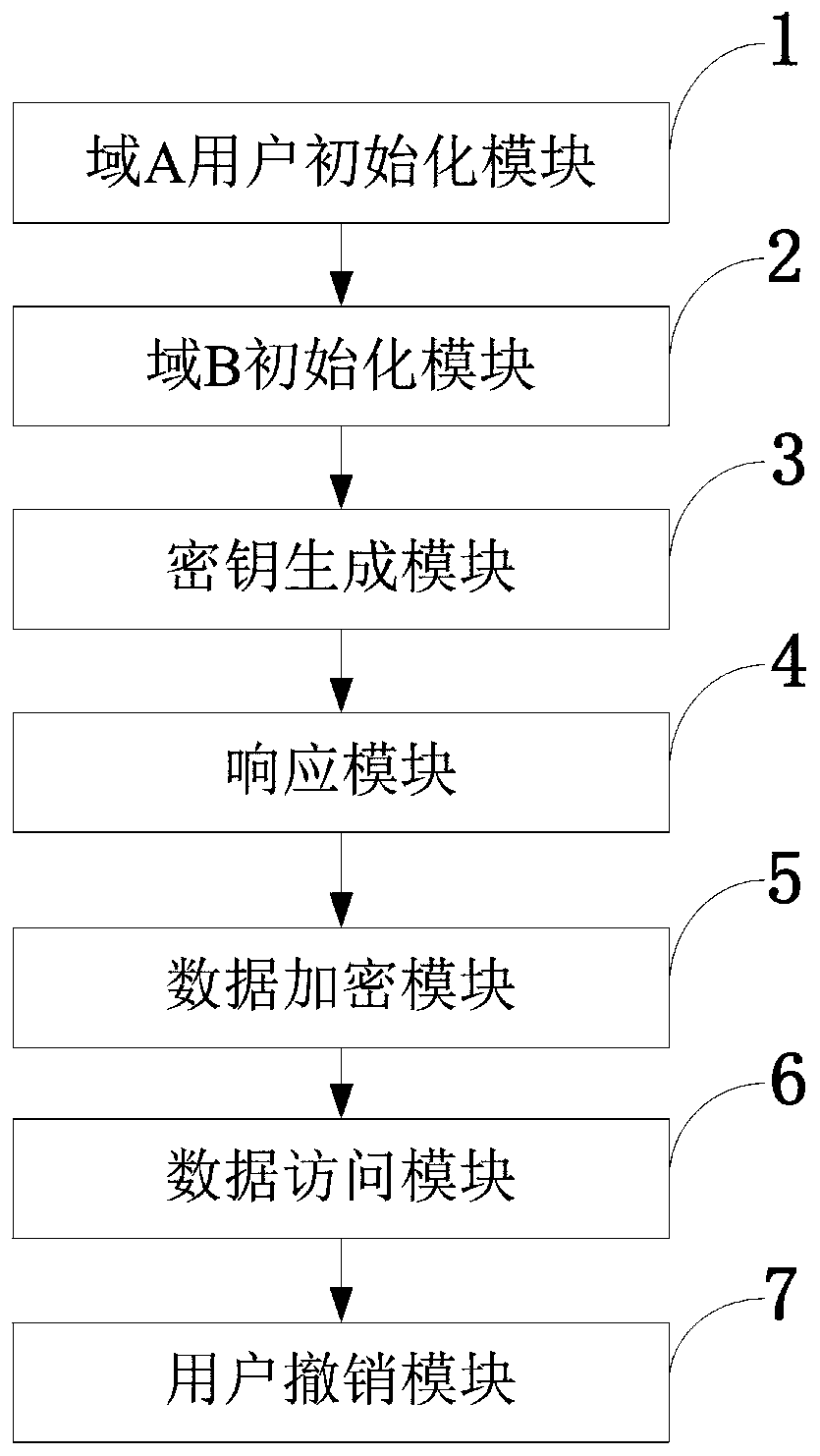
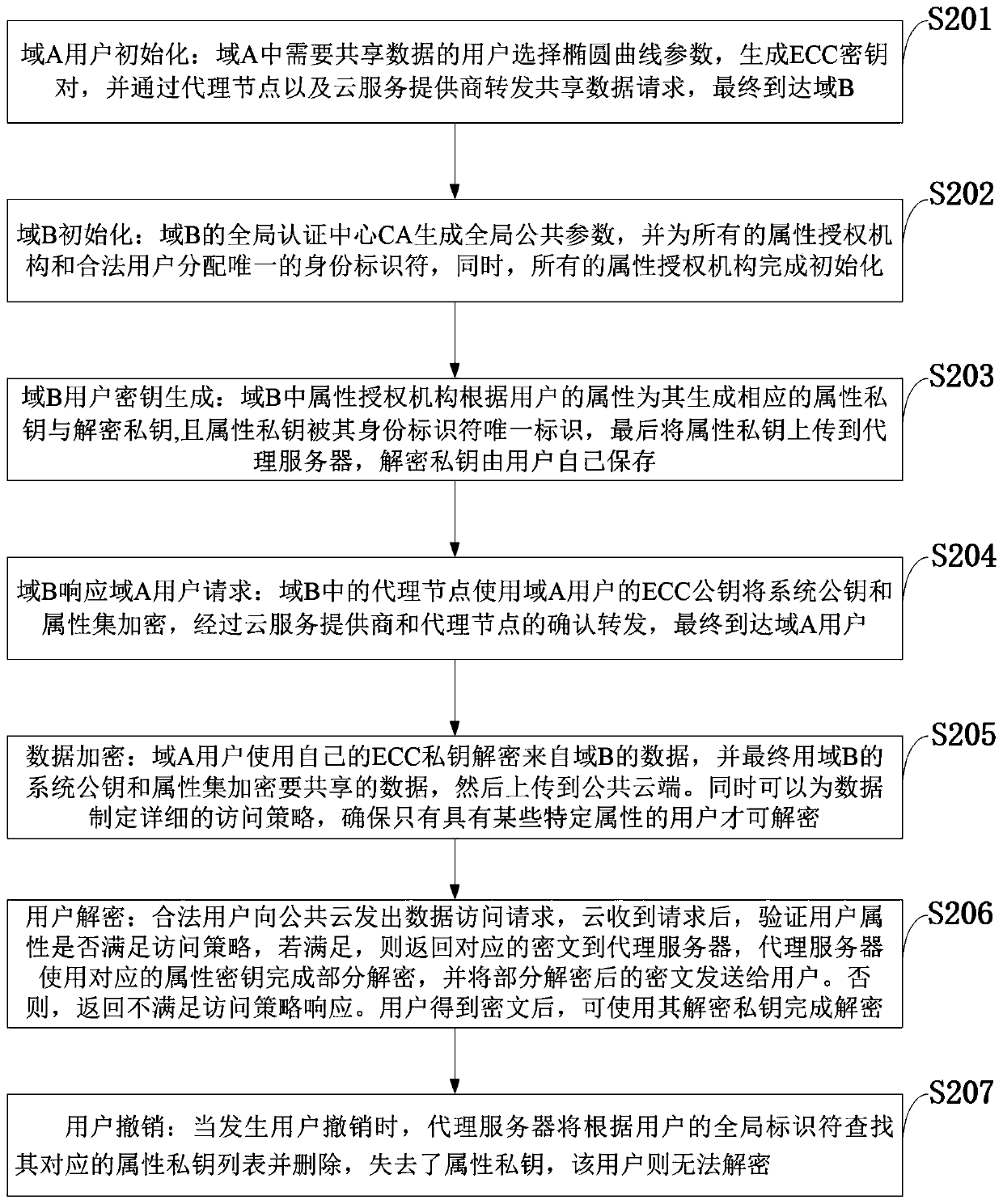
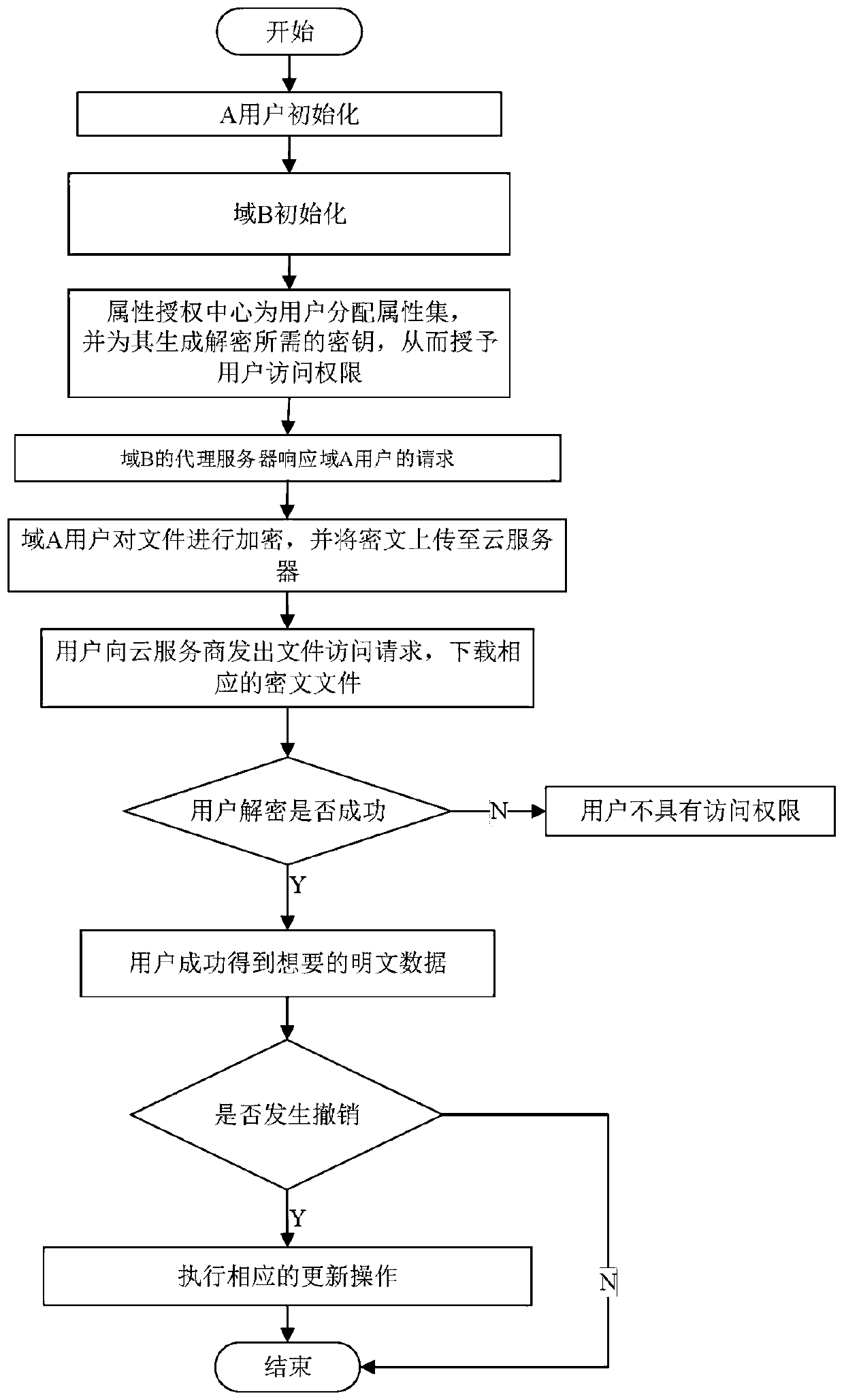
Access control system and method supporting cross-domain data sharing and wireless communication system
ActiveCN110636500AGuaranteed safe transmissionImprove securityPublic key for secure communicationSecurity arrangementKey sizeCommunications system
The invention belongs to the technical field of wireless communication networks, and discloses an access control system and method supporting cross-domain data sharing, and a wireless communication system. Users needing to share data in a domain A select elliptic curve parameters to generate ECC key pairs; a global authentication center CA of the domain B generates a global public parameter; the proxy node in the domain B encrypts the system public key and the attribute set by using the ECC public key of the domain A user; the domain A user decrypts the data from the domain B by using the ECCprivate key of the domain A user and uploads the data to the public cloud; the legal user sends a file access request to the public cloud; and when user revocation occurs, the proxy server searches acorresponding attribute private key list according to the global identifier of the user and deletes the attribute private key list. The method is high in safety under the condition of the same secretkey length. The method gives full play to the characteristic of strong computing power of agent nodes, completes the preprocessing of some data, helps a user to carry out partial decryption, and improves the decryption efficiency of the user.
Owner:XIDIAN UNIV
Method for encrypting data of an access virtual private network (VPN)
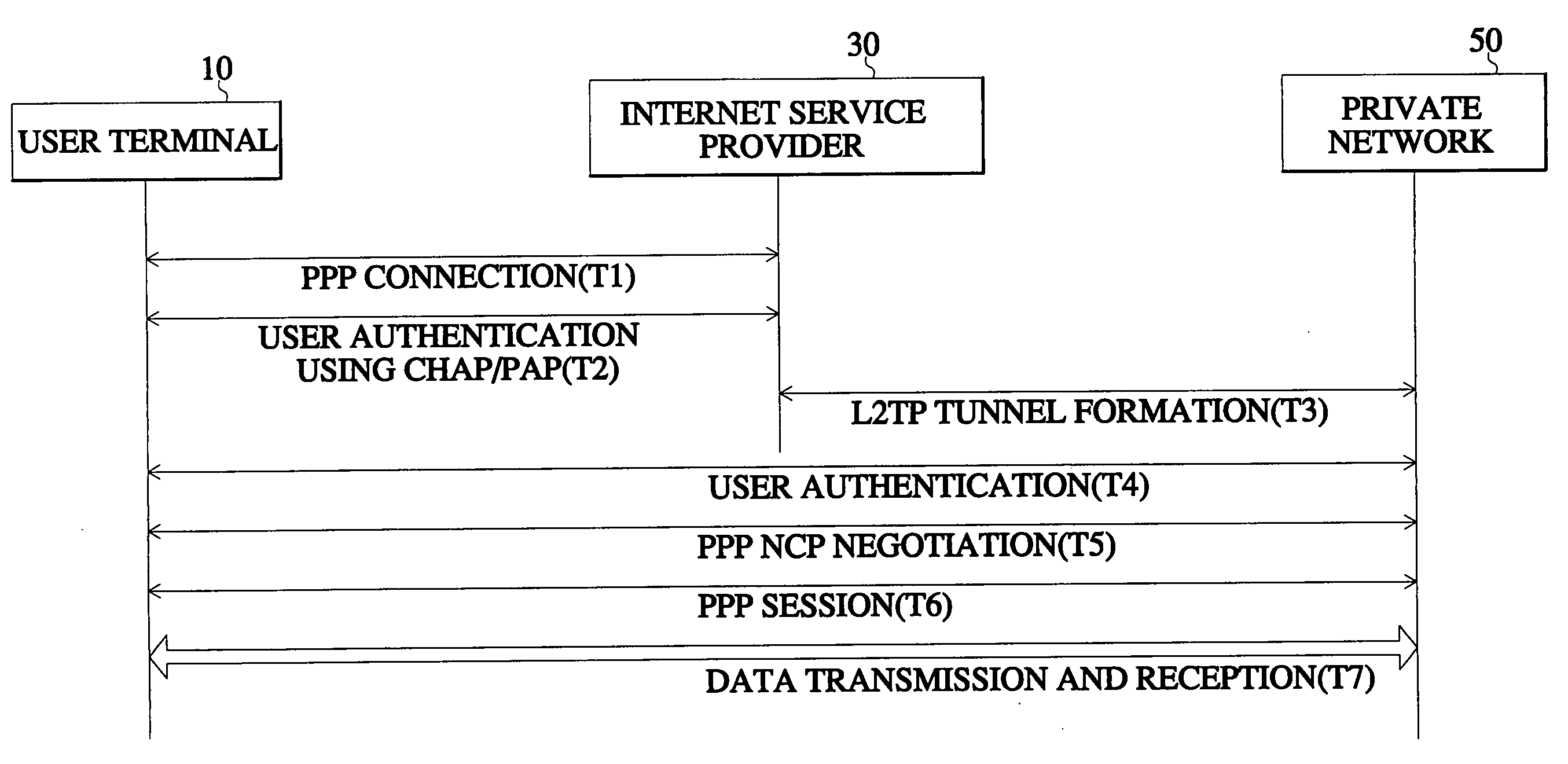
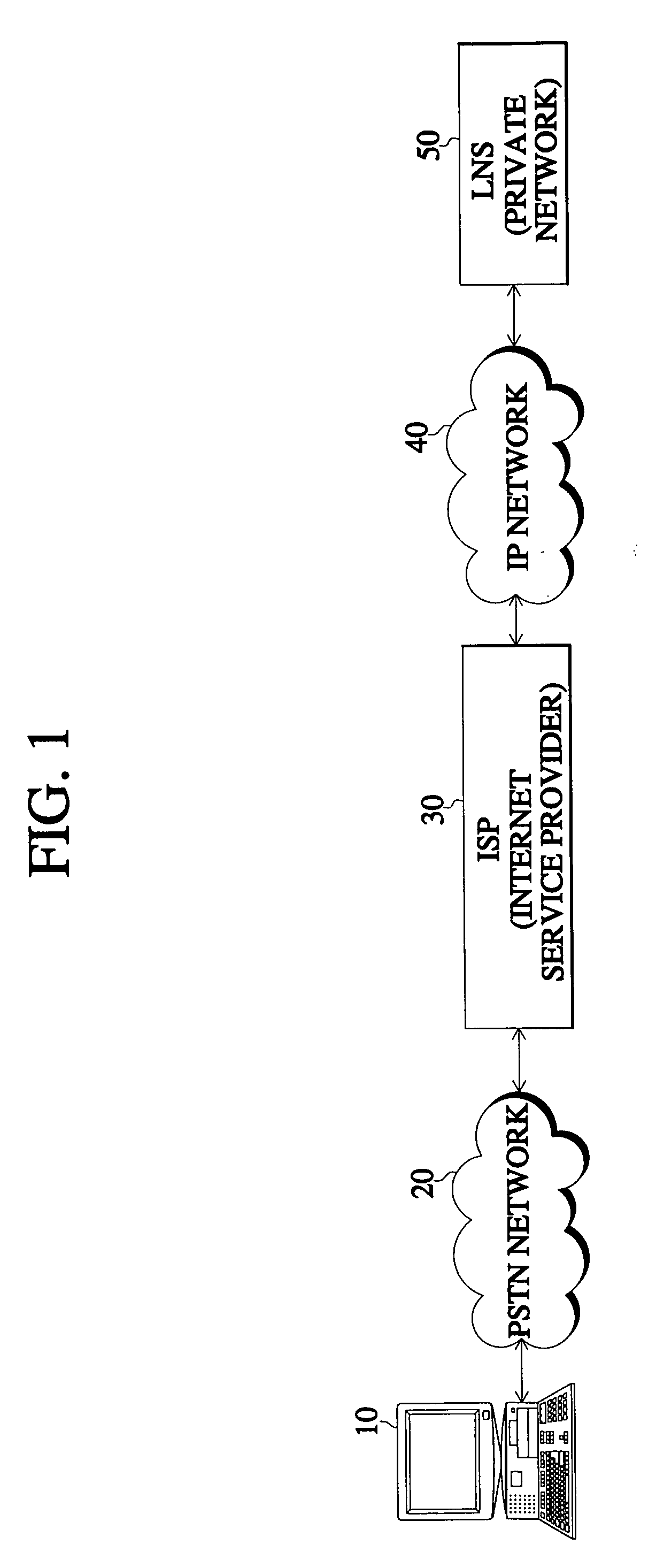
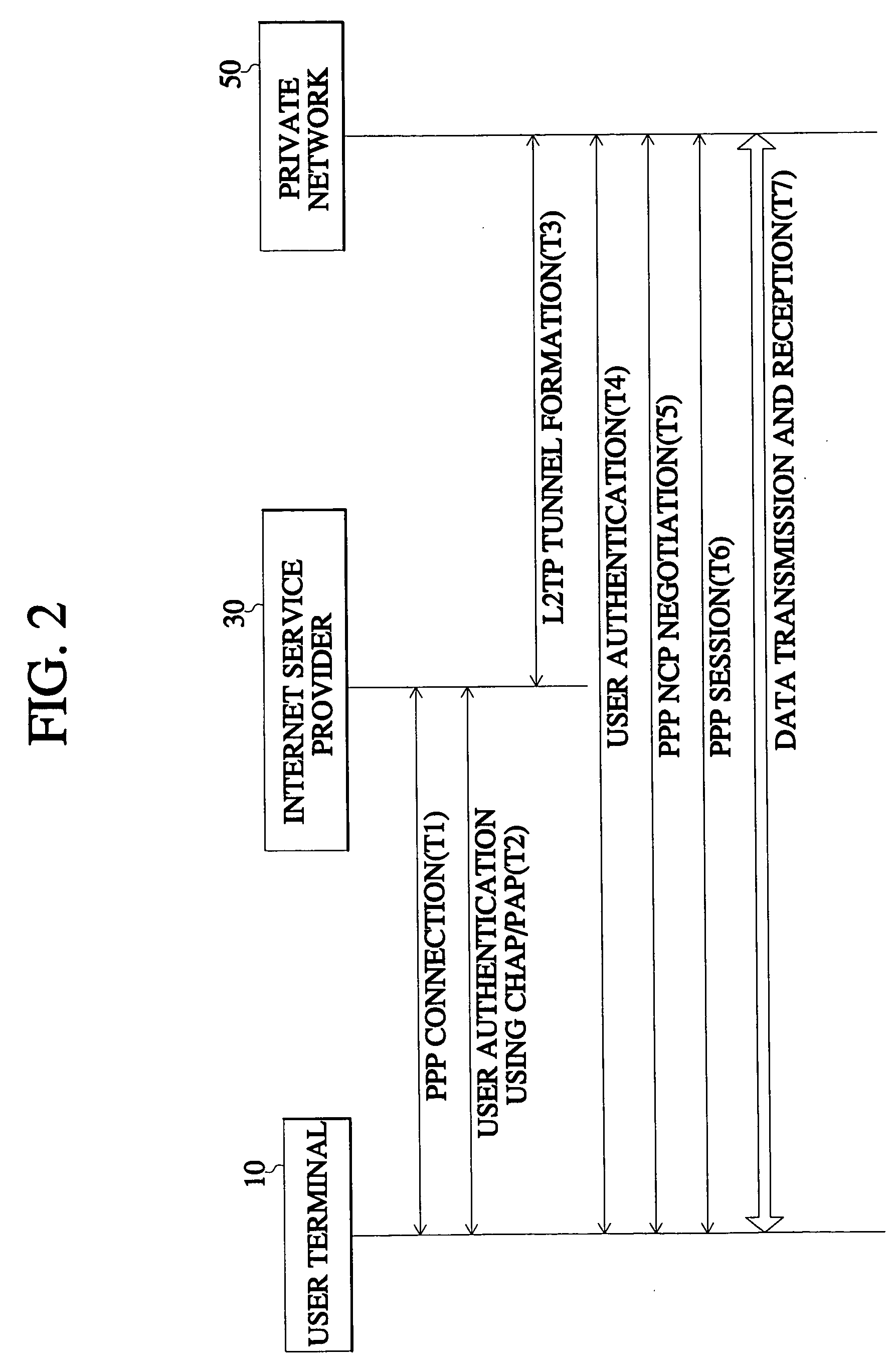
InactiveUS20040168049A1Safe receptionGuaranteed safe transmissionData taking preventionMultiple digital computer combinationsData compressionSecure communication
In a method for encrypting data in an access virtual private network (VPN), a subscriber performs a data encrypting step for data security upon accessing the private network of his company. In this method, access is set up in a dead step according to an access attempt signal by a user. A link control protocol (LCP) negotiation is performed with regard to a mutual authentication method, maximum number of reception bytes, and whether to perform data compression. When the LCP negotiation determines that mutual authentication and data encryption are necessary, the authenticating step is performed first, and mutual authentication is performed by use of a challenge handshake authentication protocol / password authentication protocol (CHAP / PAP). If the authentication is normally completed, the data encryption is performed. Therefore, data encryption is performed together with user authentication so that data is not easily exposed and communication with guaranteed security is performed.
Owner:SAMSUNG ELECTRONICS CO LTD
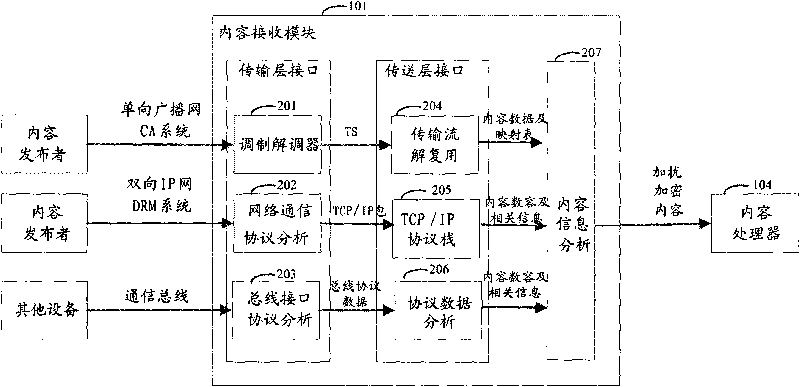
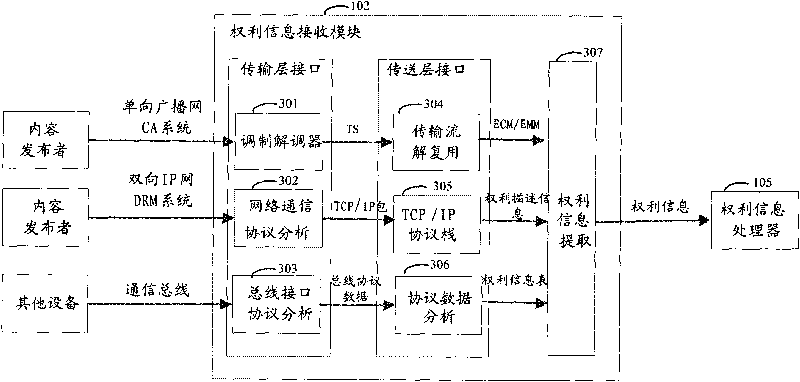
Terminal equipment for realizing content protection and transmission method thereof
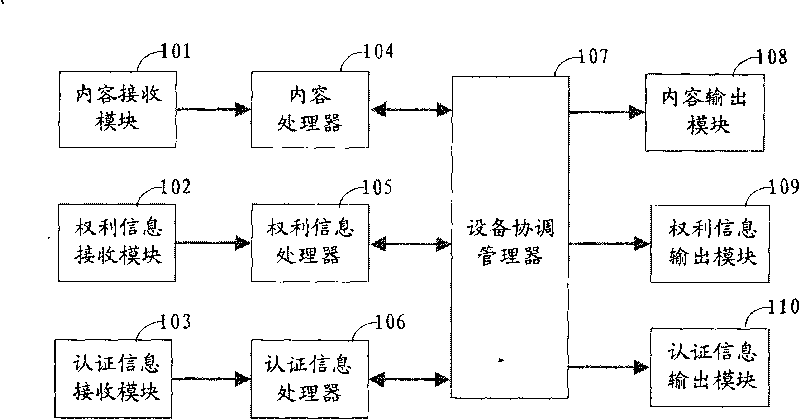
ActiveCN101719910AProtect normal transmissionGuaranteed safe transmissionKey distribution for secure communicationTerminal equipmentInformation processor
The invention discloses terminal equipment for realizing content protection, which receives first authentication information, first right information and content data from the network side or other terminal devices. An authentication information processor generates second authentication information of the terminal equipment and calculates the first authentication information and the second authentication information to obtain a first shared session key; a right information processor uses the first shared session key to decrypt first right information; a content processor uses the first shared session key for decryption to obtain content data and uses the content data according to the right information; and during transmitting data, the authentication information processor determines the legality of opposite equipment and obtains a second shared session key; and the right information processor generates second right information, encrypts the second right information and the content data by using the second shared session key and transmits the encrypted second right information and the encrypted content data. The invention also discloses a transmission method for realizing content protection. By applying the terminal equipment and the transmission method, the protection and the transmission of the content of a family digital network can be realized.
Owner:UNITEND TECH +1
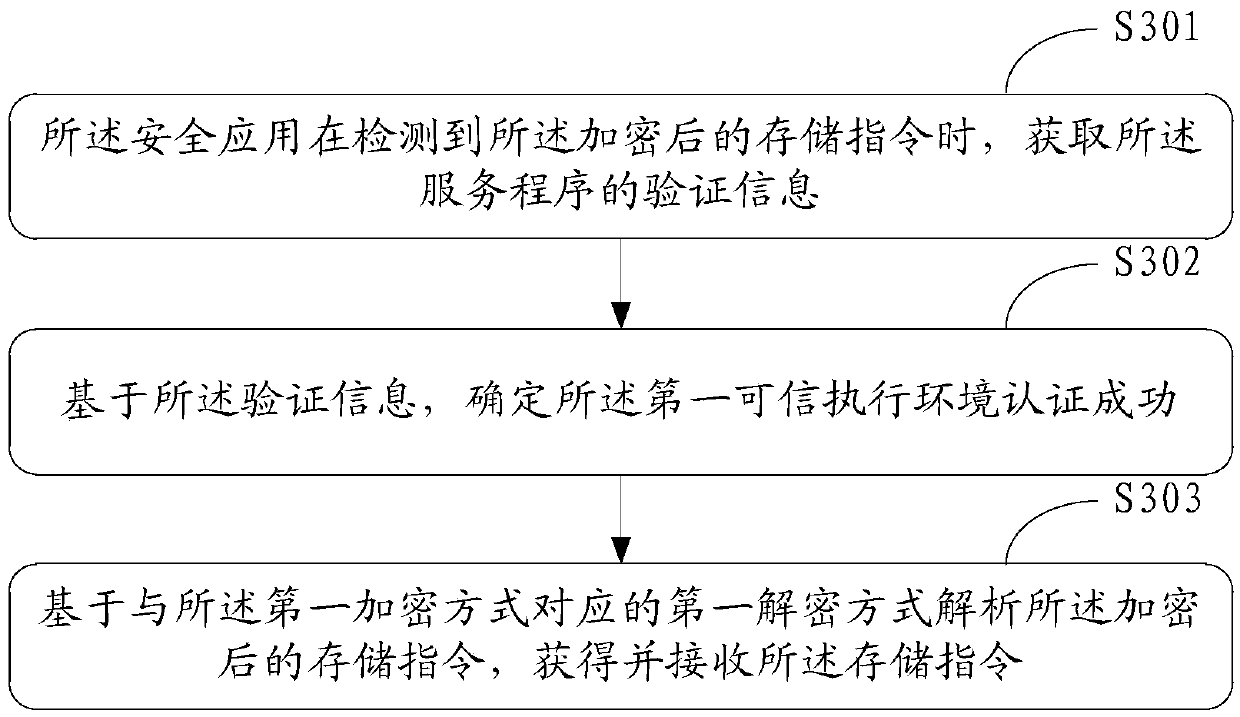
Method for secure storage of data and electronic equipment
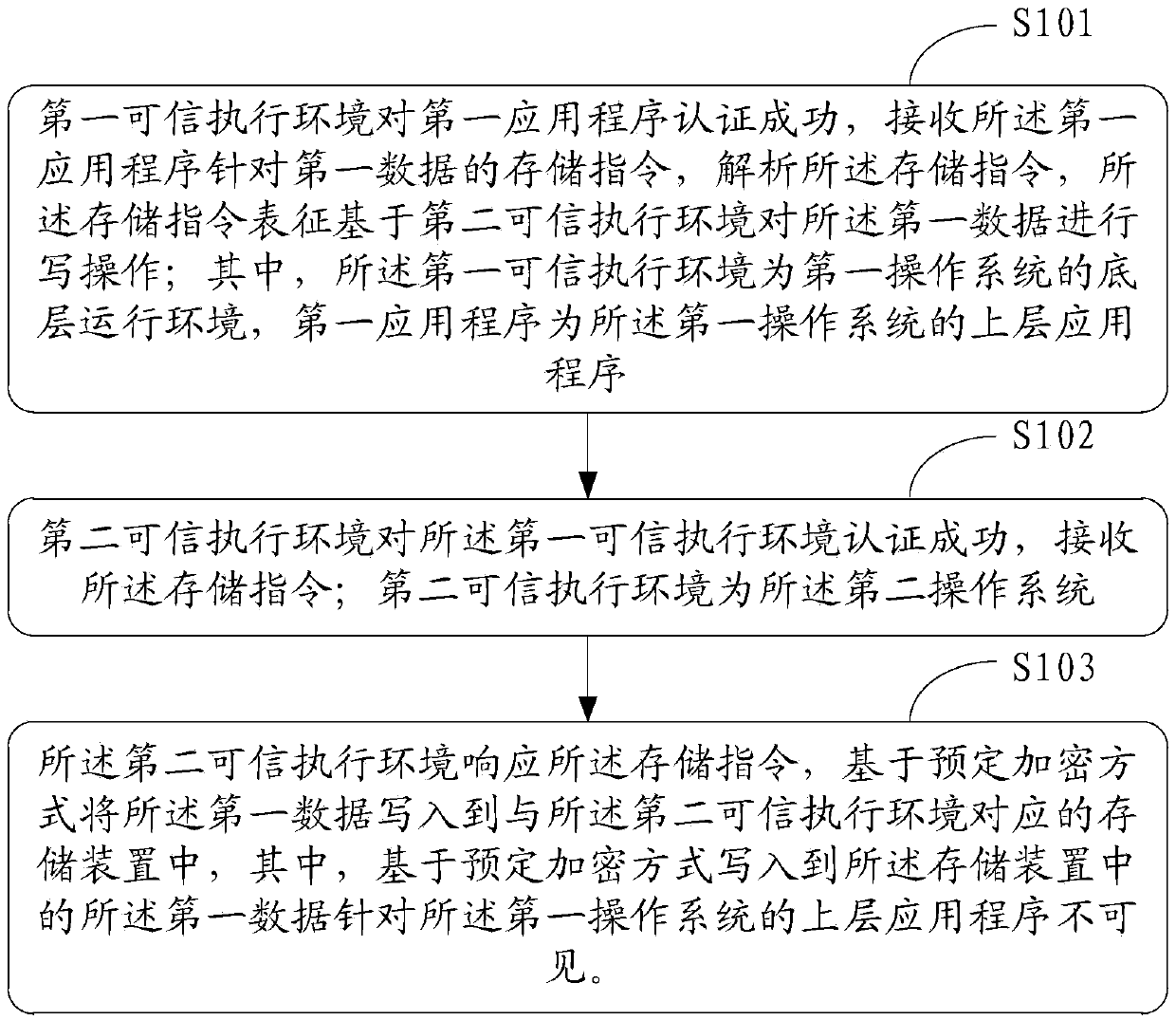
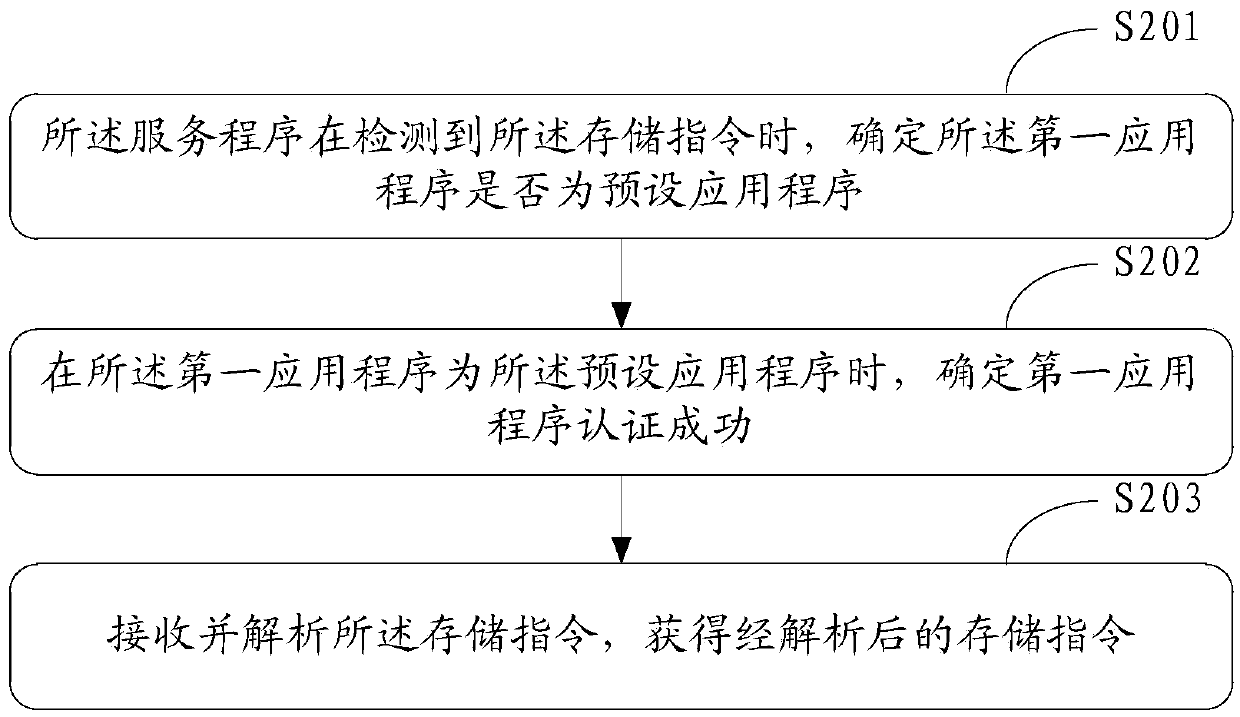
InactiveCN105512576AEnsure communication securityEnsure safetyInternal/peripheral component protectionDigital data authenticationOperational systemApplication software
The invention discloses a method for secure storage of data and electronic equipment. The method comprises steps as follows: a first credible execution environment authenticates a first application successfully, receives a storage instruction of the first application for first data and analyzes the storage instruction, and the storage instruction represents to perform write operation on the first data on the basis of a second credible execution environment; the second credible execution environment authenticates the first credible execution environment successfully and receives the storage instruction; the second credible execution environment is a second operation system; the second credible execution environment responds to the storage instruction and writes the first data in a storage device corresponding to the second credible execution environment in a preset encryption mode, and the first data written in the storage device in the preset encryption mode are invisible to an upper-layer application of a first operation system.
Owner:LENOVO (BEIJING) CO LTD
Power transmission device and power transmission control method
ActiveUS20140253052A1Guaranteed normal transmissionReduces voltage suppliedBatteries circuit arrangementsElectric powerElectric power transmissionPower circuits
Power transmission device that causes a power supply circuit to supply a first voltage to a first active electrode when power transmission is performed, causes the power supply circuit to supply a second voltage that is lower than the first voltage to the first active electrode and causes power reception device detection means to perform frequency sweeping at a first time interval until the power reception device is mounted, or causes the power supply circuit to supply a third voltage that is lower than the first voltage to the first active electrode and causes the power reception device detection means to perform frequency sweeping at a second time interval that is longer than the first time interval until the power reception device is removed.
Owner:MURATA MFG CO LTD
Data transmission method, device and system
ActiveCN102932349AGuaranteed normal transmissionRealize transmissionKey distribution for secure communicationObfuscationComputer terminal
The invention discloses a data transmission method and a device which are applied to a first terminal. The method includes obtaining a second encryption key of a second terminal; obfuscating data to be sent up to obtain obfuscated data according to a preset obfuscation rule; encrypting the obfuscated data as a sequence by using the second encryption key to obtain encrypted data; and sending the encrypted data as serial data to the second terminal through a physical connecting link. The invention further discloses a data transmission method and a device which are applied to the second terminal. The method includes obtaining the second encryption key of the second terminal; obtaining encrypted data sent by the first terminal through the physical connecting link; decrypting the encrypted data by using the second encryption key to obtain decrypted data; and reducing the decrypted data according to a preset anti-obfuscation rule to obtain restoring data.
Owner:SOUTHWEST JIAOTONG UNIV +1
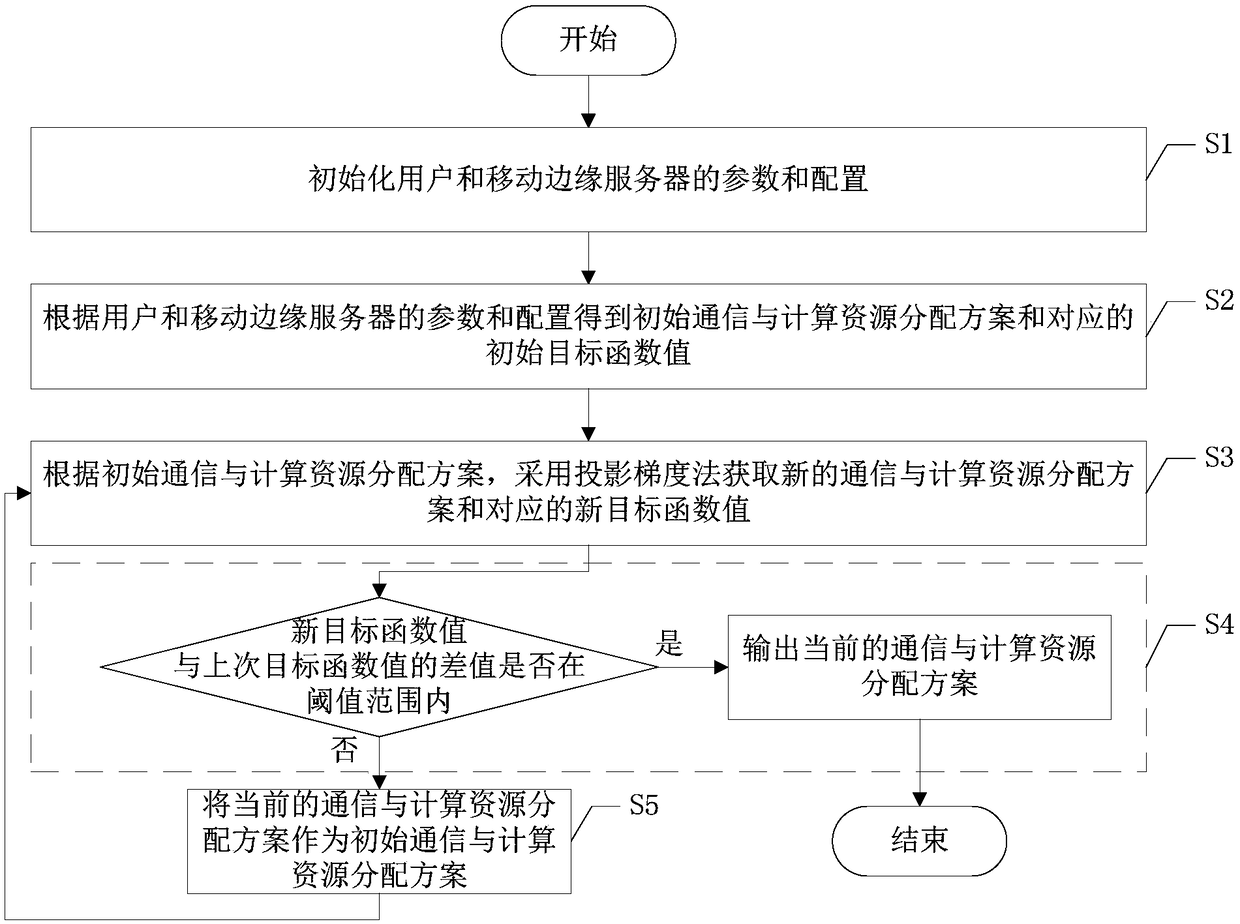
A resource optimization method for safe calculation unloading in mobile edge computing network
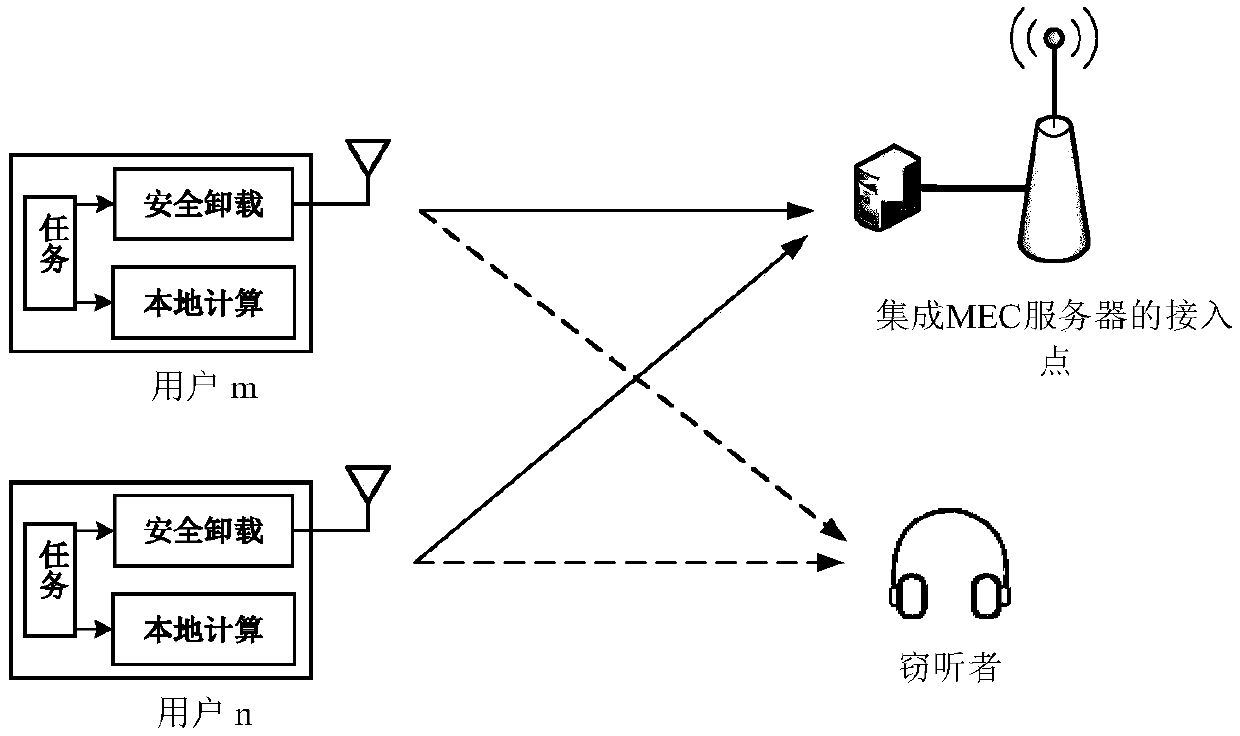
ActiveCN109167787ASmall task delayImprove real-time performanceProgram initiation/switchingTransmissionQos quality of serviceEdge server
The invention discloses a resource optimization method for safe calculation unloading in a mobile edge computing network, which comprises the following steps: S1, initializing parameters and configurations of a user and a mobile edge server; S2, obtaining an initial communication and computing resource allocation scheme and a corresponding initial objective function value; S3, according to that initial communication and computing resource allocation scheme, a projection gradient method is adopted to obtain a new communication and computing resource allocation scheme and correspond new objective function values; S4, judging whether that difference between the new objective function value and the last objective function value is within the threshold value range, and if so, outputting a current communication and calculation resource allocation scheme and terminating optimization; Otherwise proceeding to step S5; S5, taking the current communication and computing resource allocation schemeas the initial communication and computing resource allocation scheme, and returning to step S3. The method considers the scene of eavesdropper in the system, improves the security of the system, realizes the minimum delay, and improves the service quality.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
NOMA mobile edge computing system construction method with anti-eavesdropping capability
ActiveCN109548013AGuaranteed safe transmissionImprove spectral efficiencyPower managementNetwork traffic/resource managementEavesdroppingSystem construction
The invention discloses an NOMA mobile edge computing system construction method with anti-eavesdropping capability. In the case that there is an eavesdropper and the channel state information of theeavesdropper is unknown, a user introduces a metric independent of the channel state information of the eavesdropper through secret coding to quantify the anti-eavesdropping ability of the user. Two users simultaneously send respective partial tasks to nearby access points equipped with mobile edge computing servers through NOMA uplinks in a resource block sharing manner and perform fast processing, thereby actively assisting the execution of computing tasks of mobile users, and ensuring the fast execution of the computing tasks with low delay tolerance and high complexity of mobile clients. The NOMA mobile edge computing system construction method disclosed by the invention has the advantages of ensuring secure transmission of information through the anti-eavesdropping ability when the channel state information of the eavesdropper is unknown. According to the NOMA mobile edge computing system construction method disclosed by the invention, a class of interrupt events based on probabilistic analysis is also defined to measure the communication performance of the system and to evaluate the impact of transmitting power and unloading tasks on the system performance.
Owner:NANJING UNIV OF POSTS & TELECOMM
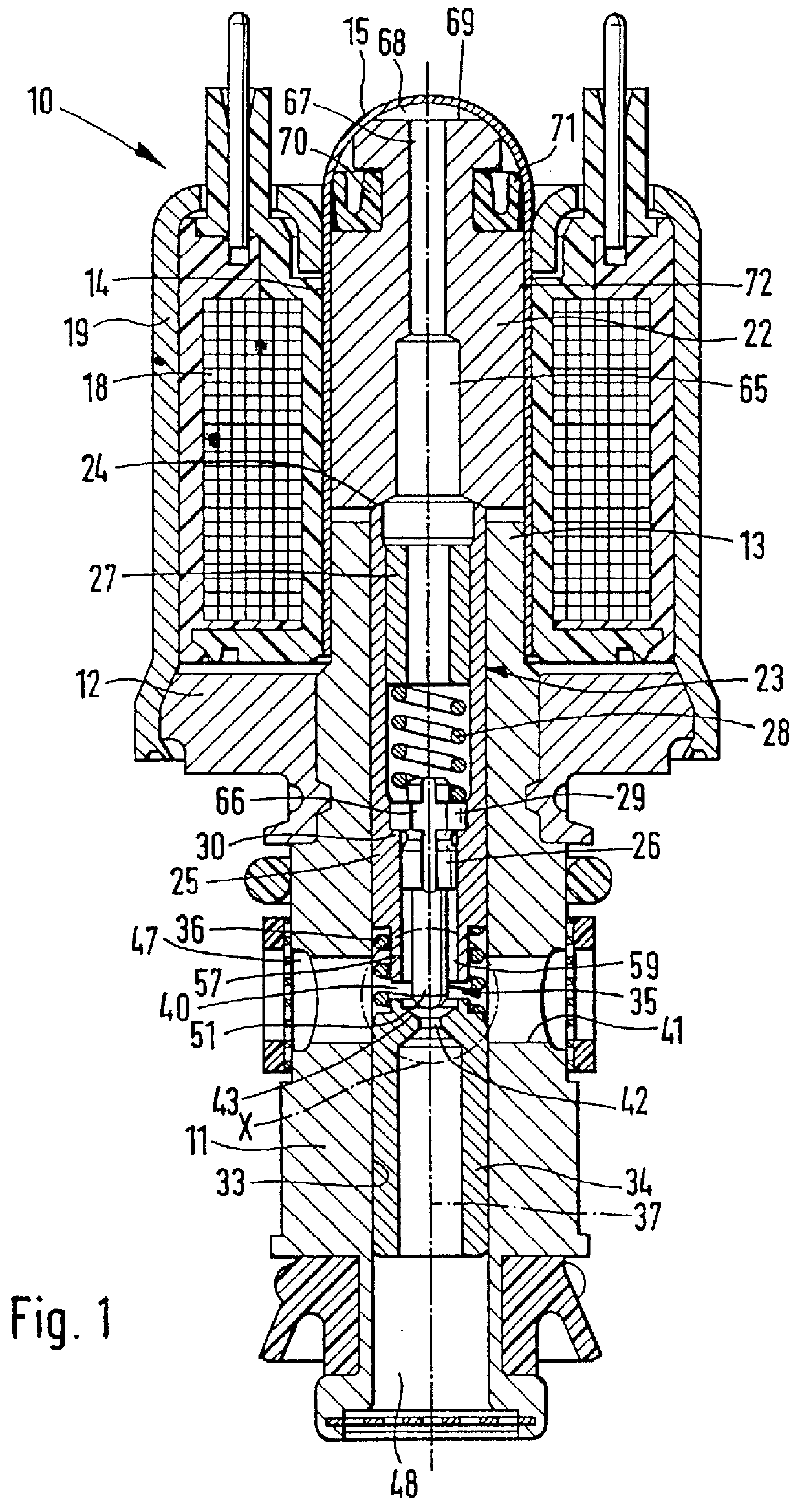
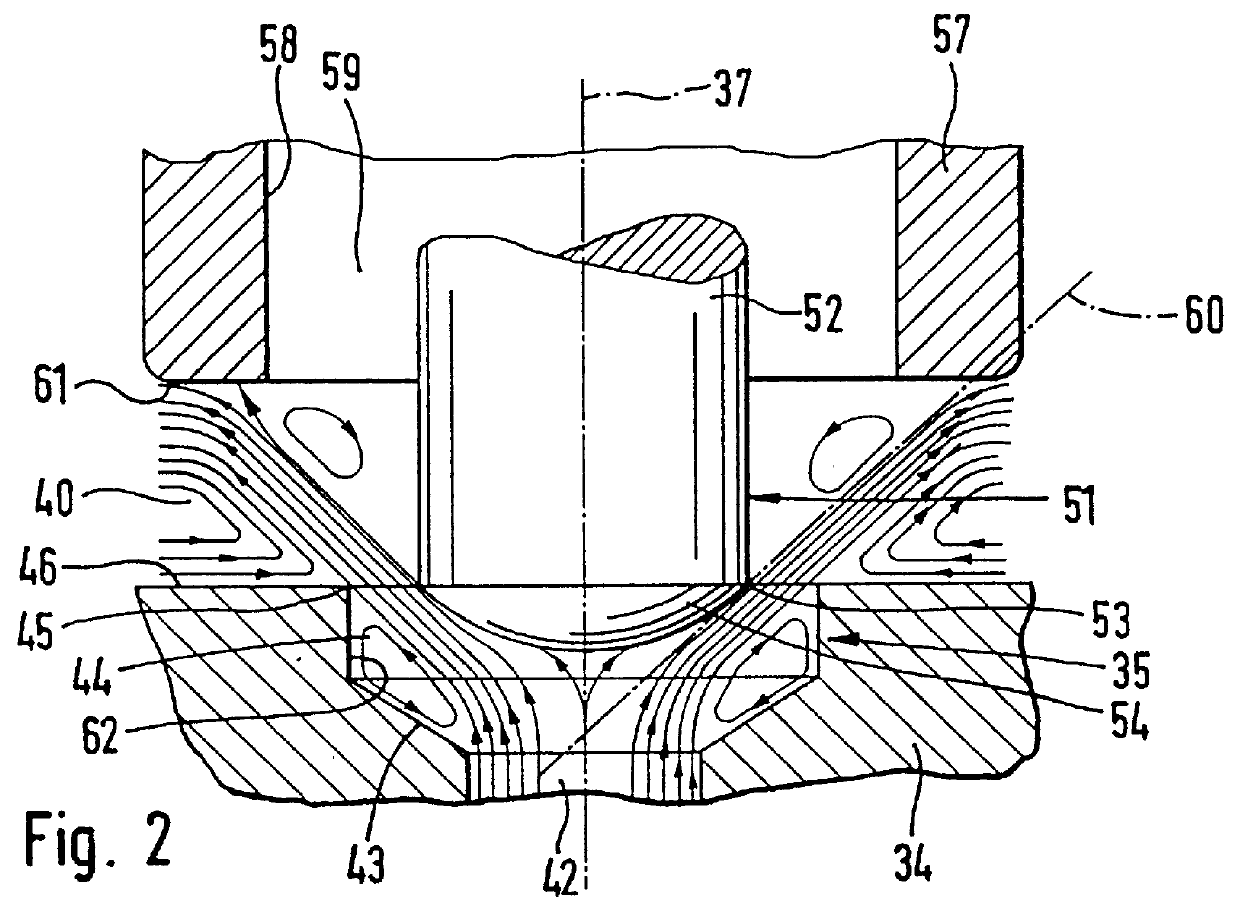
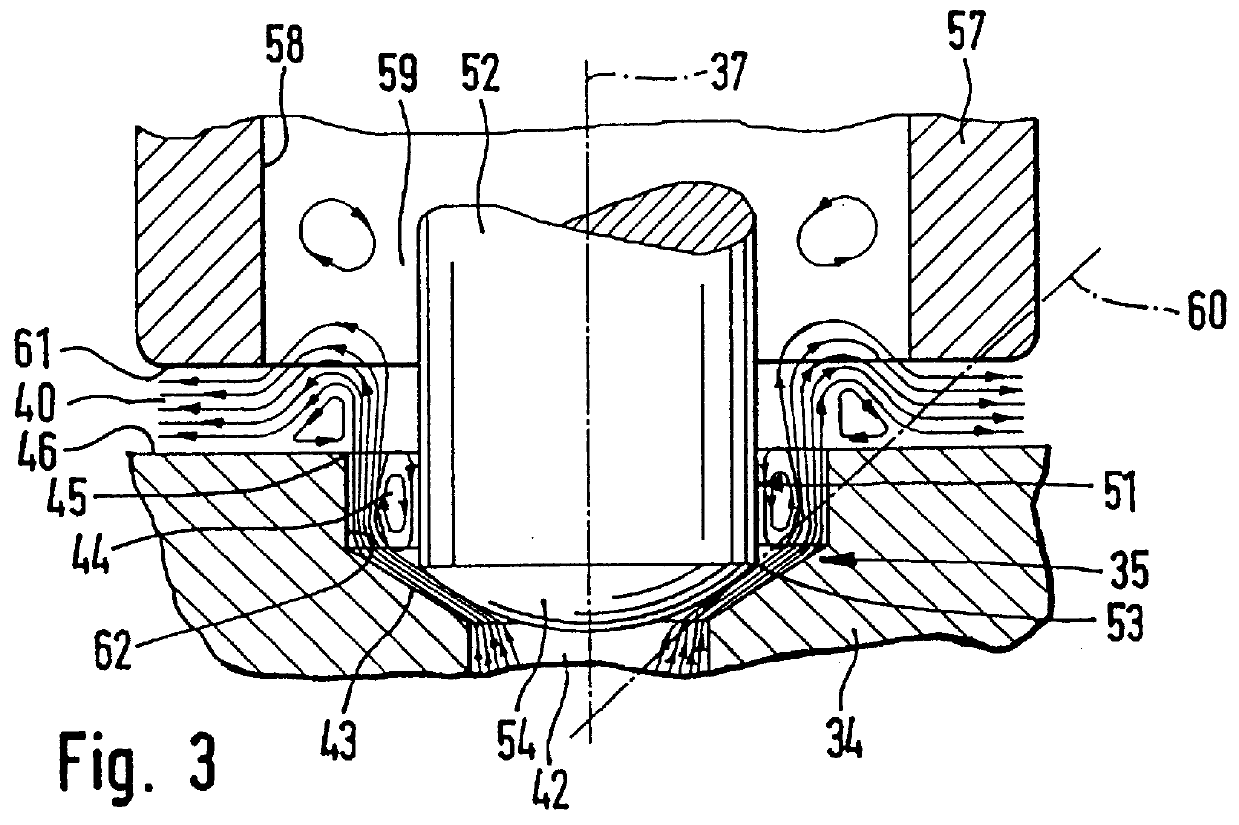
Magnet valve with pressure limitation for slip-controlled motor vehicle brake systems
InactiveUS6086164AGuaranteed safe transmissionSealing is not affectedOperating means/releasing devices for valvesValve members for absorbing fluid energyLow noiseMobile vehicle
PCT No. PCT / DE95 / 01386 Sec. 371 Date Apr. 28, 1997 Sec. 102(e) Date Apr. 28, 1997 PCT Filed Oct. 10, 1995 PCT Pub. No. WO96 / 13414 PCT Pub. Date May 9, 1996A magnet valve with low noise upon shutoff from the pressure limiting function. The magnet valve has a two-part valve tappet, whose inner valve tappet part has the closing member of a seat valve. The closing member is circumferentially engaged in spaced-apart fashion, forming a gap space, by a tubular portion of the outer valve tappet part. From the gap space, a pressure fluid conduit leads to a control chamber, which is located between the face end, remote from the seat valve, of a magnet armature that cooperates with the valve tappet, and a valve dome. Upon shutoff of the magnet valve, the seat valve changes from its closing position to a partly open position, in which dynamic pressure in the gap space becomes operative and is transmitted through the pressure fluid conduit into the control chamber. The hydraulic force that is operative there on the magnet armature acts counter to the opening forces of the magnet valve and slows down its opening motion. Because of the thus-throttled flow of pressure fluid through the seat valve, a pressure surge is averted. The magnet valve can be used in slip-controlled motor vehicle brake systems.
Owner:ROBERT BOSCH GMBH
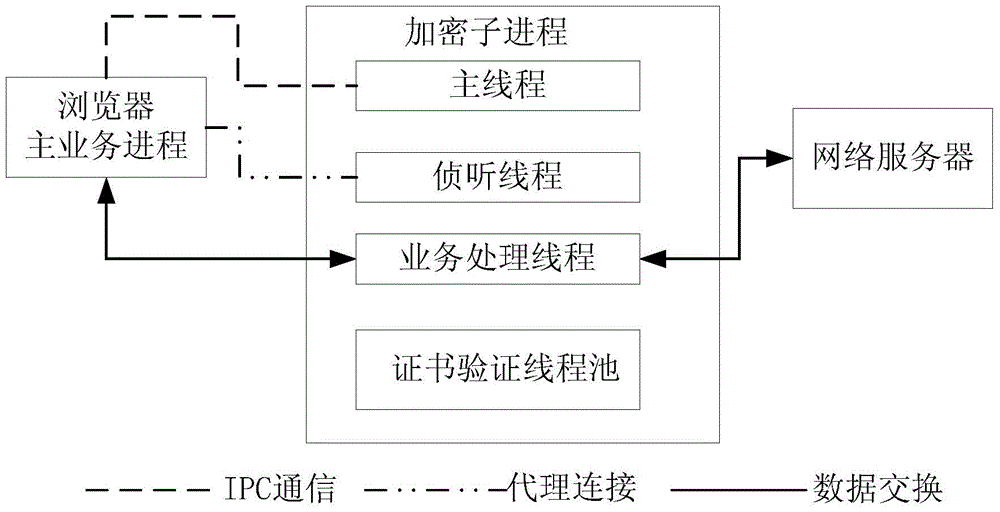
Safety communication system
InactiveCN104580189AGuaranteed safe transmissionReduce riskSecuring communicationSecure communicationData transmission
The invention provides a safety communication system. The system comprises a safety browser device and a network server. The safety browser device comprises a browser main service process module and an encryption subprocess module, wherein an encryption subprocess of the encryption subprocess module serves as a connecting agency to achieve conversion from a first encryption channel to a second encryption channel and data forwarding, encryption connection communication is established through the encryption subprocess module and the network server, safety transmission of service data is guaranteed, the risk of service data leakage can be reduced, and the safety and reliability of service data transmission are improved.
Owner:BEIJING QIHOO TECH CO LTD +1
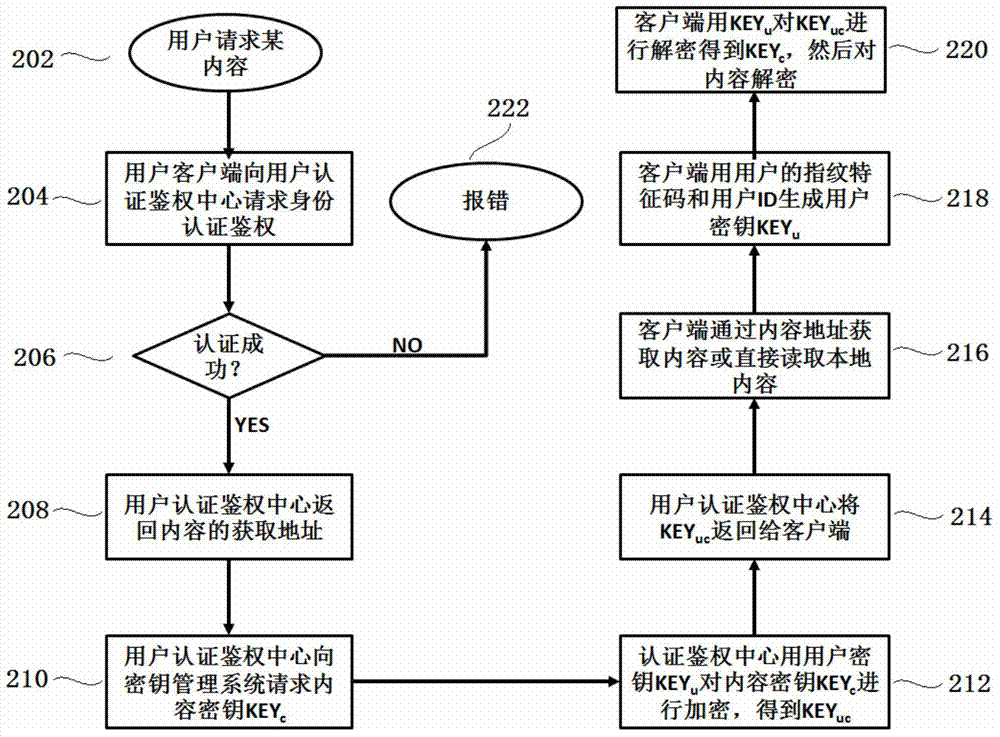
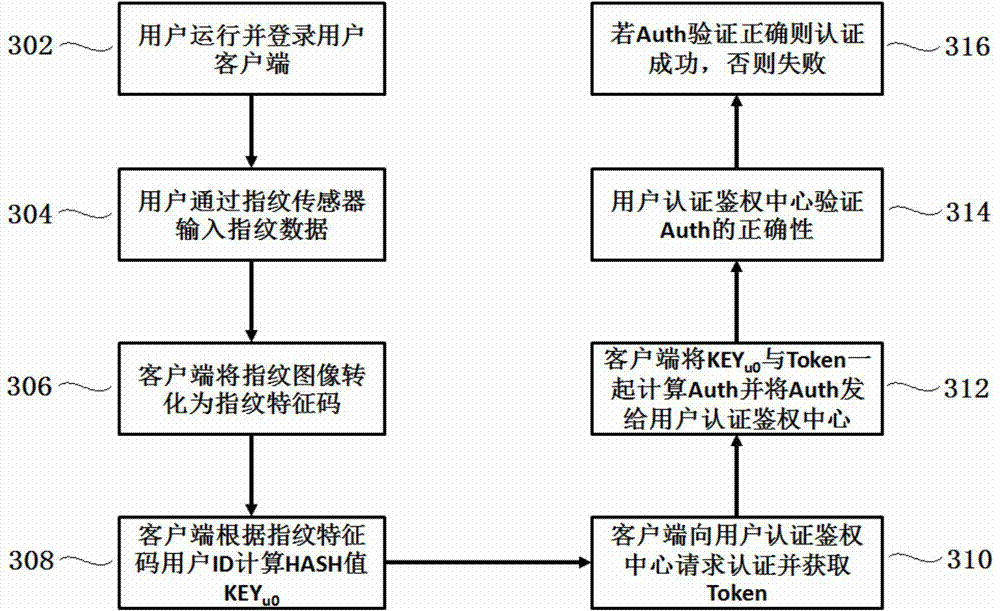
Digital right management method and system
InactiveCN104283686AEnsure safetyGuaranteed safe transmissionUser identity/authority verificationProgram/content distribution protectionSecure transmissionClient-side
The invention discloses a digital right management method and system. The digital right management method includes the steps that the digital right management system responds to a content request of a user at a client side under the condition that the response conditions are met, a user secret key at least containing pre-recorded fingerprint feature information of the user is used for carrying out encryption on a content secret key corresponding to the requested content to form an encrypted secret key; the encrypted secret key is returned to the client side, the client side uses the user secret key for decrypting the encrypted secret key to obtain the content secret key, and therefore the client side can use the content secret key to decrypt the requested content. The digital right management system uses the user secret key based on fingerprint features to encrypt the content secret key to form the encrypted secret key, and the content secret key is obtained only by decrypting the encrypted secret key through the user secret key based on the fingerprint features at the client side. Thus, safe transmission of the content secret key is guaranteed, and safety of content protection is further improved.
Owner:SHENZHEN MPR TECH CO LTD
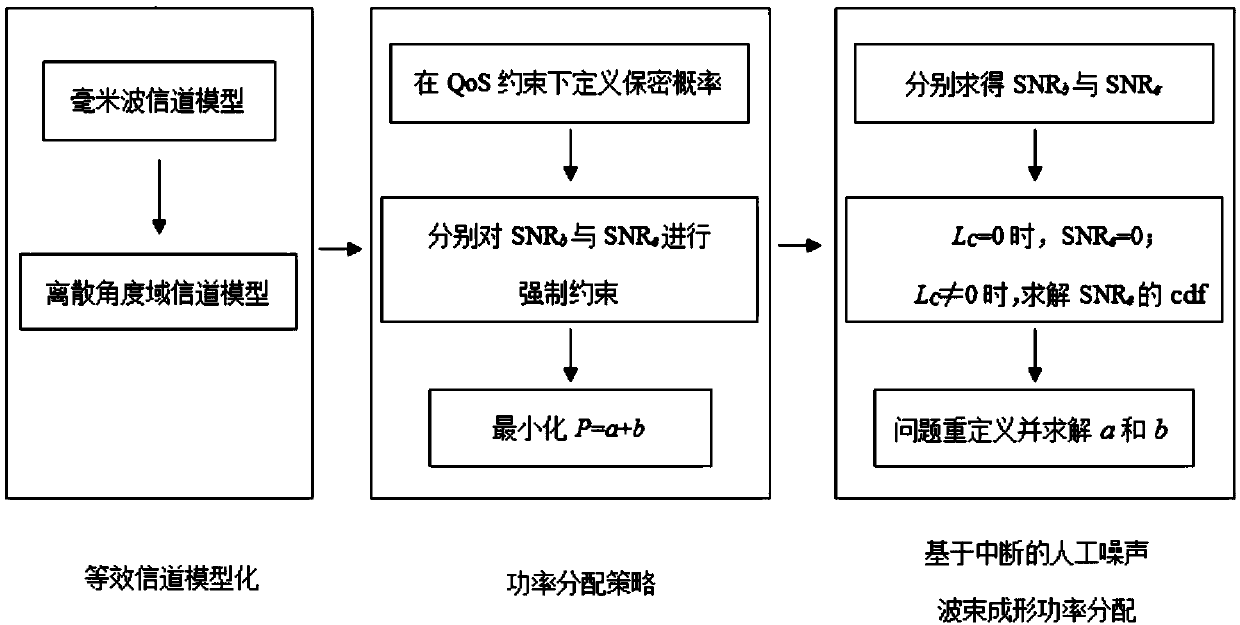
Method of security probability-based power allocation in millimeter wave system
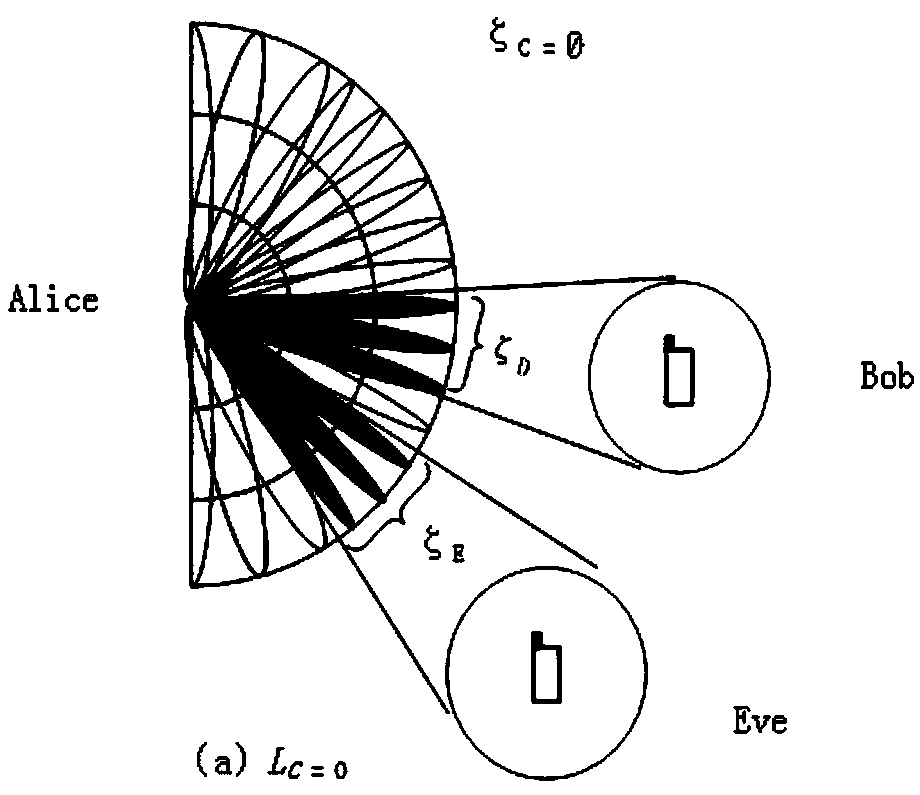
InactiveCN109547135AImprove privacyImprove confidentialityTransmission monitoringHigh level techniquesSignal-to-noise ratio (imaging)Quality of service
The invention discloses a method of security probability-based power allocation in a millimeter wave system. The method comprises the following steps: S1, an equivalent channel modeling step, whereina millimeter wave channel model is established, and thus a discrete angular domain channel model is obtained; S2, a power allocation strategy defining step, wherein a minimum value of a receiving signal-to-noise ratio of a legal direction is forcibly restricted, an upper boundary of a receiving signal-to-noise ratio of an eavesdropping direction is limited at the same time an allocation strategy of total transmission power is formulated, and an effect that target security probability meets constraints of quality-of-service demand is guaranteed; and S3, a power allocation step, wherein artificial noise beamforming power allocation based on interruption is carried out, and performance evaluation is carried out on a final allocation result. The invention provides the power allocation method with a data protection function, privacy and confidentiality of data in a wireless communication process can be effectively improved, established security probability is achieved, normalized safety throughput is increased, and system complexity is reduced.
Owner:NANJING UNIV OF POSTS & TELECOMM
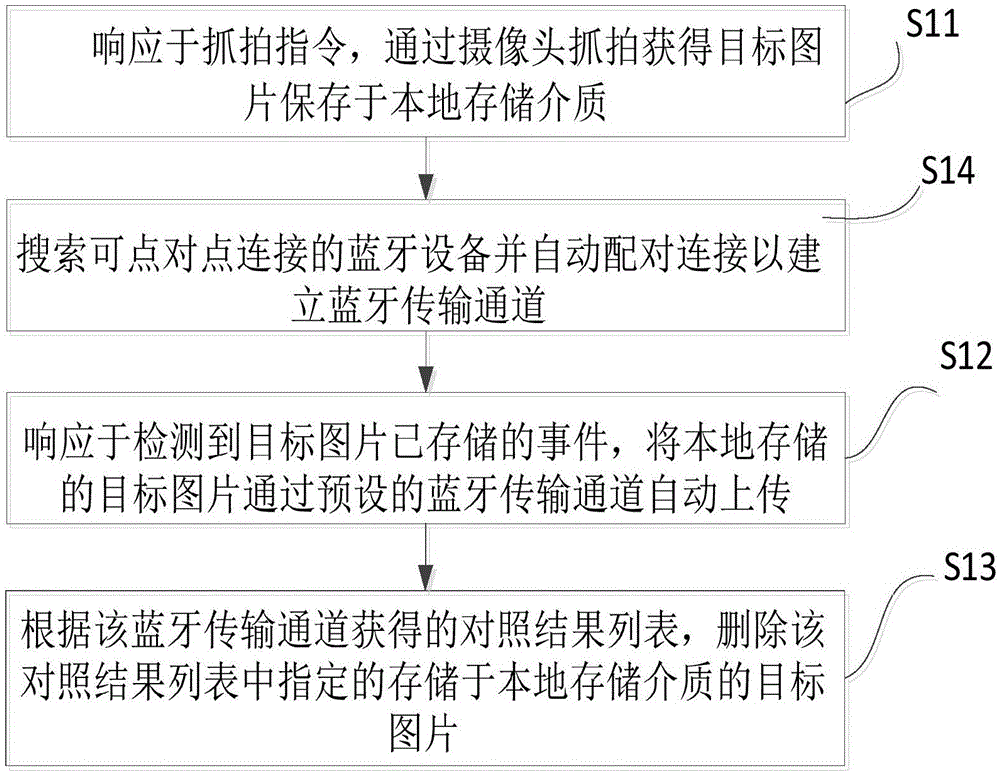
Picture transmission control system, and security protection and transmission method of each related end
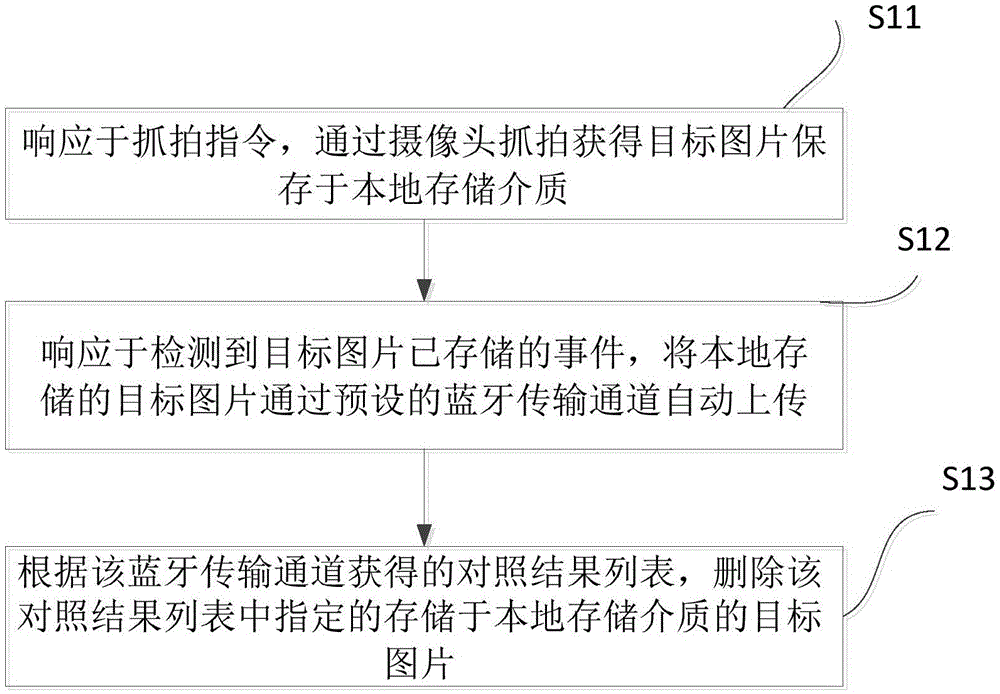
ActiveCN105100249AAvoid lossGuaranteed safe transferRegistering/indicating working of vehiclesWireless commuication servicesControl systemTime transfer
The invention relates to the technical field of picture transmission of an intelligent terminal, and brings forward a tachograph picture transmission control method. The method comprises the following steps: a tachograph obtains an object picture in response to a user snapshot instruction and storing the object picture to a local storage medium; the tachograph automatically uploading the object picture to a mobile terminal through a first channel; at the same time, the mobile terminal automatically uploading the object picture automatically obtained from the first channel to a cloud end through a second channel; and the tachograph, according to a comparison result list which is obtained from the first channel and is fed back by the mobile terminal, deleting an object picture, specified to be stored in the local storage medium, in the comparison result list. The invention also relates to a picture security protection and transmission method and a corresponding terminal. According to the invention, security protection and automatic real-time transfer of picture files are realized, and picture loss generated when pictures are stored at a tachograph end and are covered due to a limited storage capacity is avoided.
Owner:BEIJING QIHOO TECH CO LTD
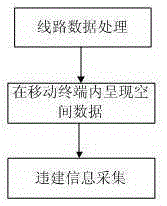
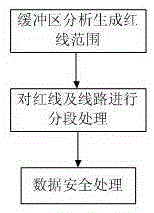
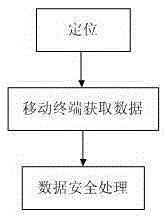
Unapproved construction information high precision acquisition method based on mobile terminal
InactiveCN106709837ARaise the spotlightRealize secure transmissionData processing applicationsData displaySecure transmission
The invention discloses an unapproved construction information high precision acquisition method based on a mobile terminal, and relates to the information acquisition technology field. The unapproved construction information high precision acquisition method comprises steps: processing of line data, spatial data displayed in the mobile terminal, and acquisition of unapproved construction information. The unapproved construction information high precision acquisition method is advantageous in that a method of acquiring, integrating, and pushing information for location awareness in different environments is used to effectively support integration of audio and video information, image information, position information, and attribute information by taking place name and address data as a basis, and the multidirectional comprehensive acquisition and collection of the unapproved construction information is realized; during the data acquisition, automatic acquisition is carried out, and range value precision is high, and a range value is precise to a centimeter level, and therefore the high precision position locating and the acquisition of the related data are realized; before the data pushing, the safety of the data is guaranteed by adopting an information encryption pushing strategy based on the position and a mobile terminal data strategy, and therefore safe transmission of a line and red line data during a mobile inspection process is realized, and the currency of the unapproved construction data acquisition is improved.
Owner:星际空间(天津)科技发展有限公司
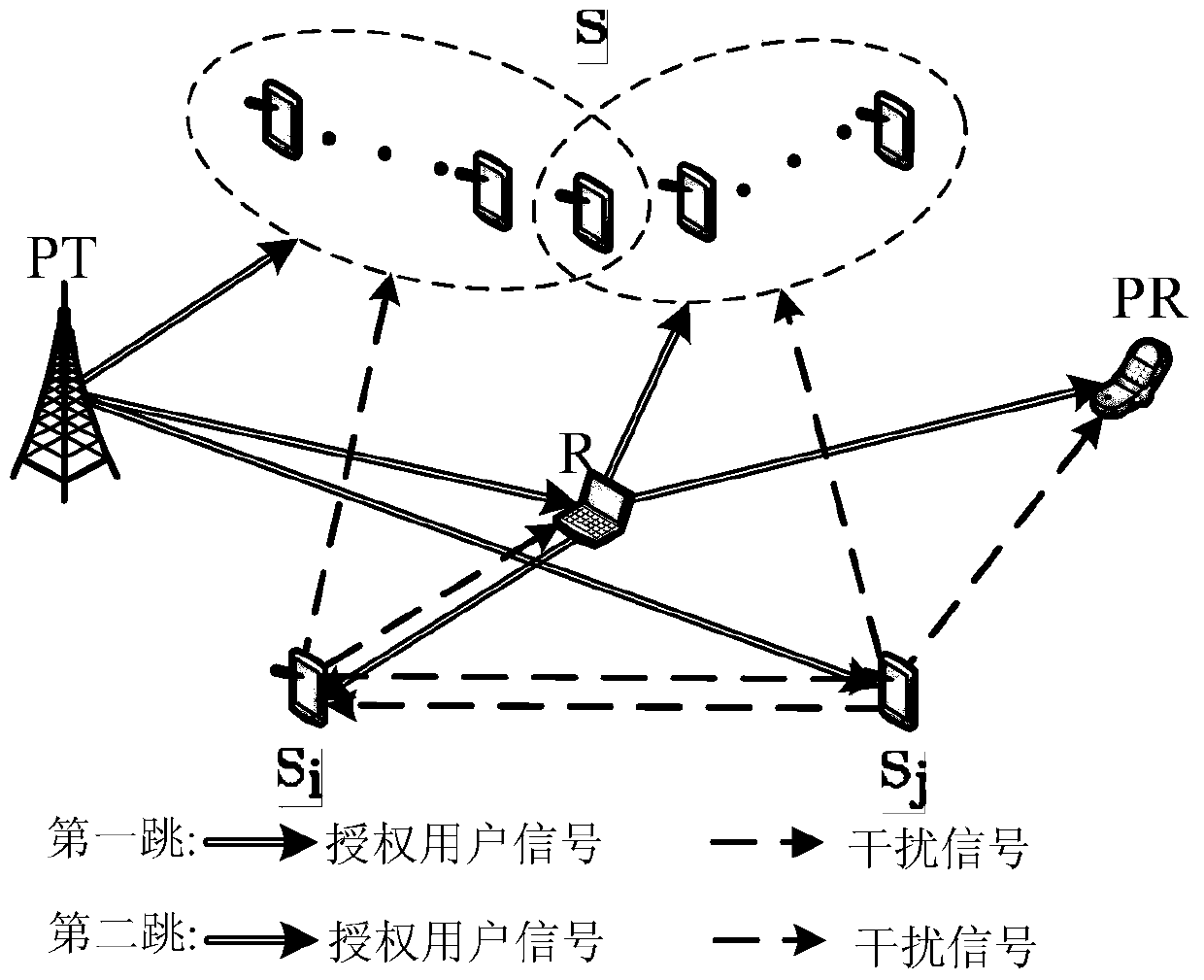
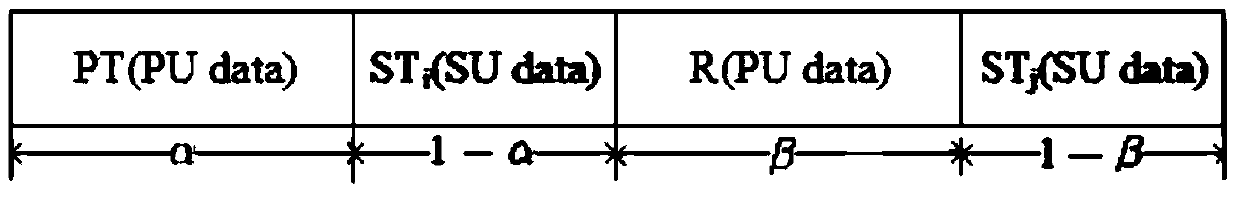
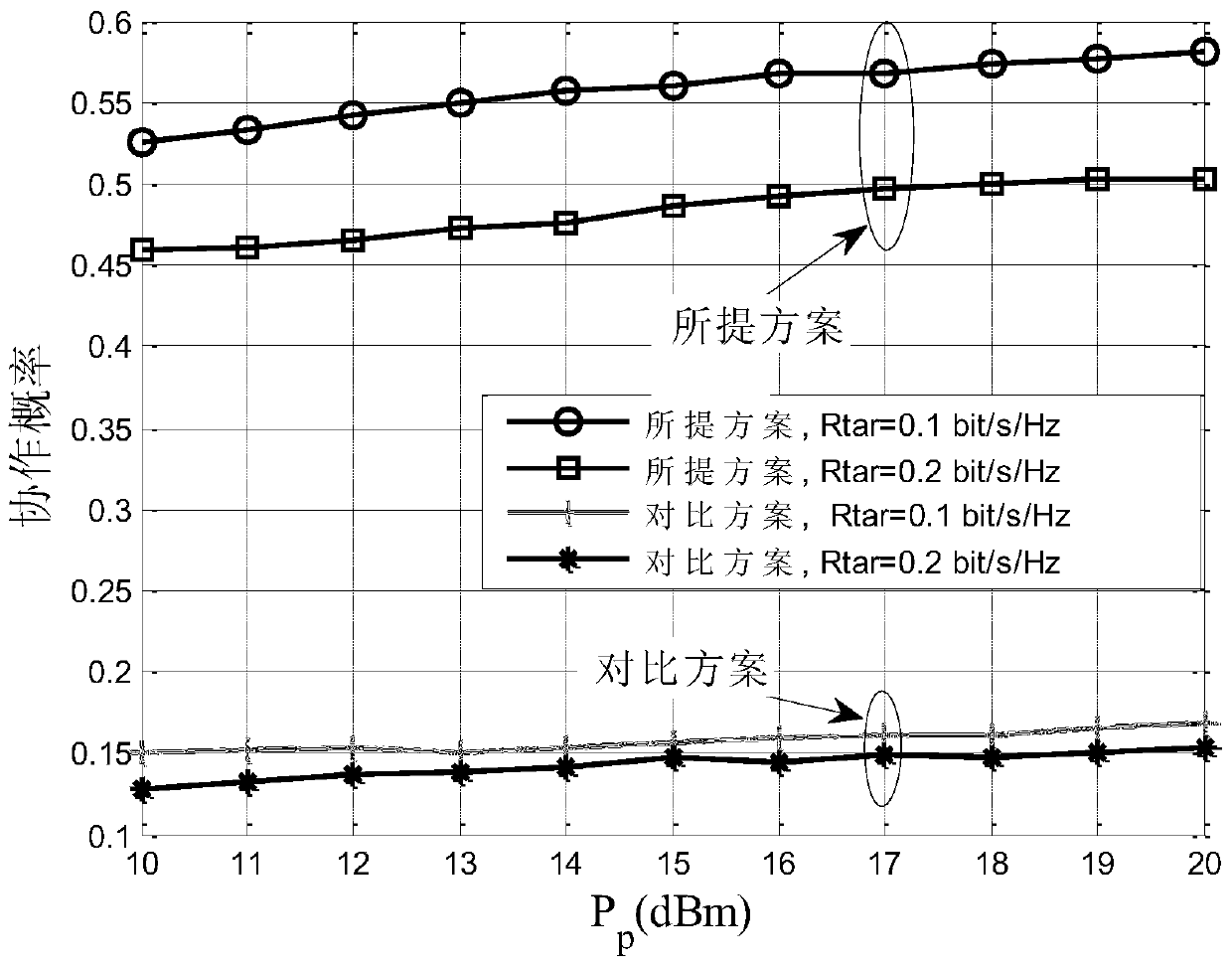
Secure transmission method based on non-trusted cognitive user collaboration interference
ActiveCN104918239AGuaranteed safe transmissionEnsure safetySecurity arrangementCognitive userSecure transmission
The invention discloses a secure transmission method based on non-trusted cognitive user collaboration interference, which belongs to the technical field of wireless communication. The secure transmission method adopts a time-division scheme, and is divided into two phases. The two phases respectively correspond to first hop transmission and second hop transmission of an authorized user. At each transmission phase, the authorized user occupies part of time slots for transmitting authorization information and selecting one cognitive user to generate interference information for assisting his secure transmission; and the rest of the time slots at the phase is allocated to the cognitive user for use. According to the secure transmission method based on non-trusted cognitive user collaboration interference, two cooperative cognitive users are selected optimally, and transmission time slots are allocated to the users for maximizing transmission speed of the cognitive users while ensuring security of the authorized user; and the simulation results indicate that the secure transmission method can improve secure outage performance of the authorized user and average transmission speed of the cognitive user when compared with the traditional single cognitive user collaborative scheme.
Owner:XI AN JIAOTONG UNIV
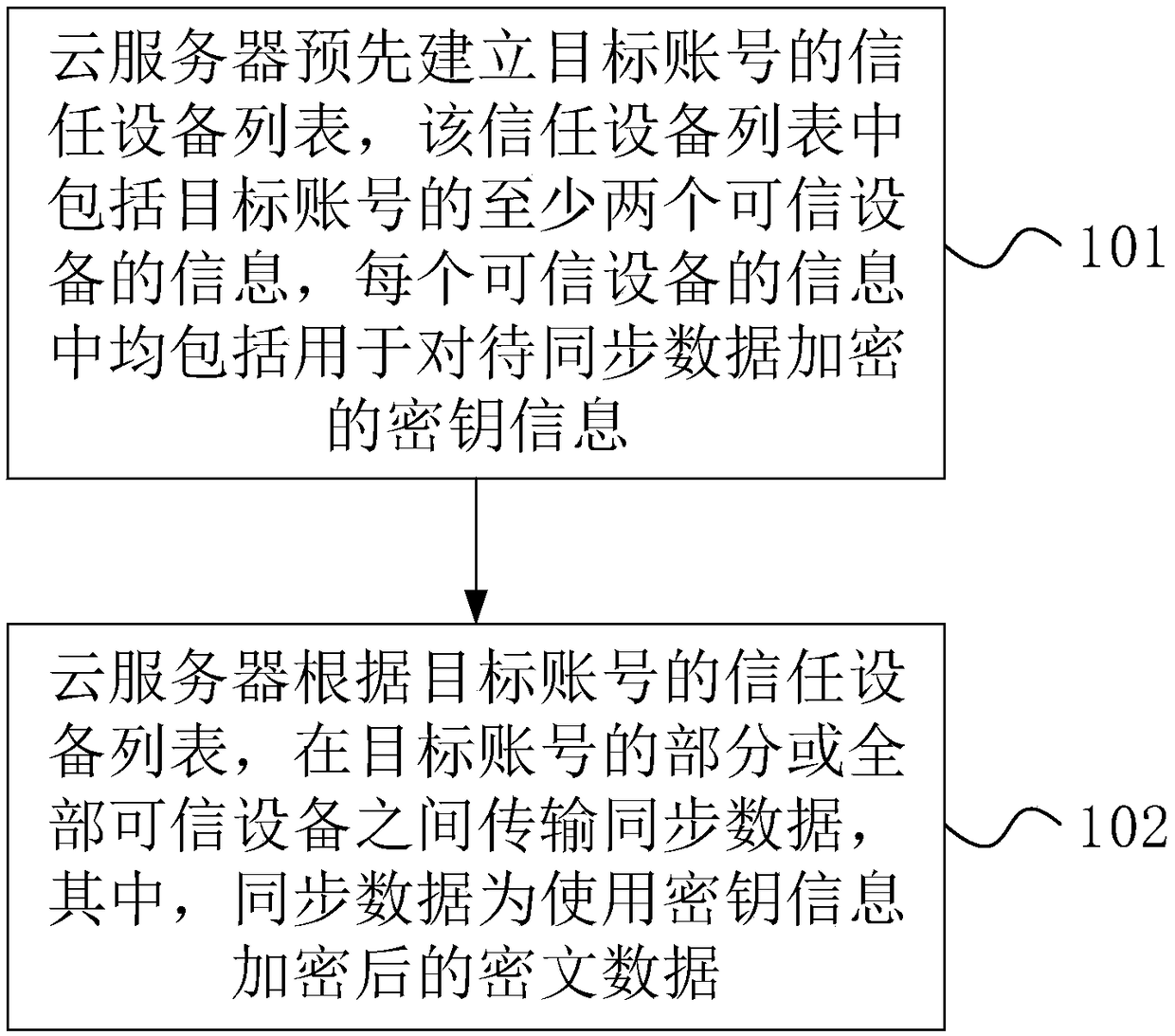
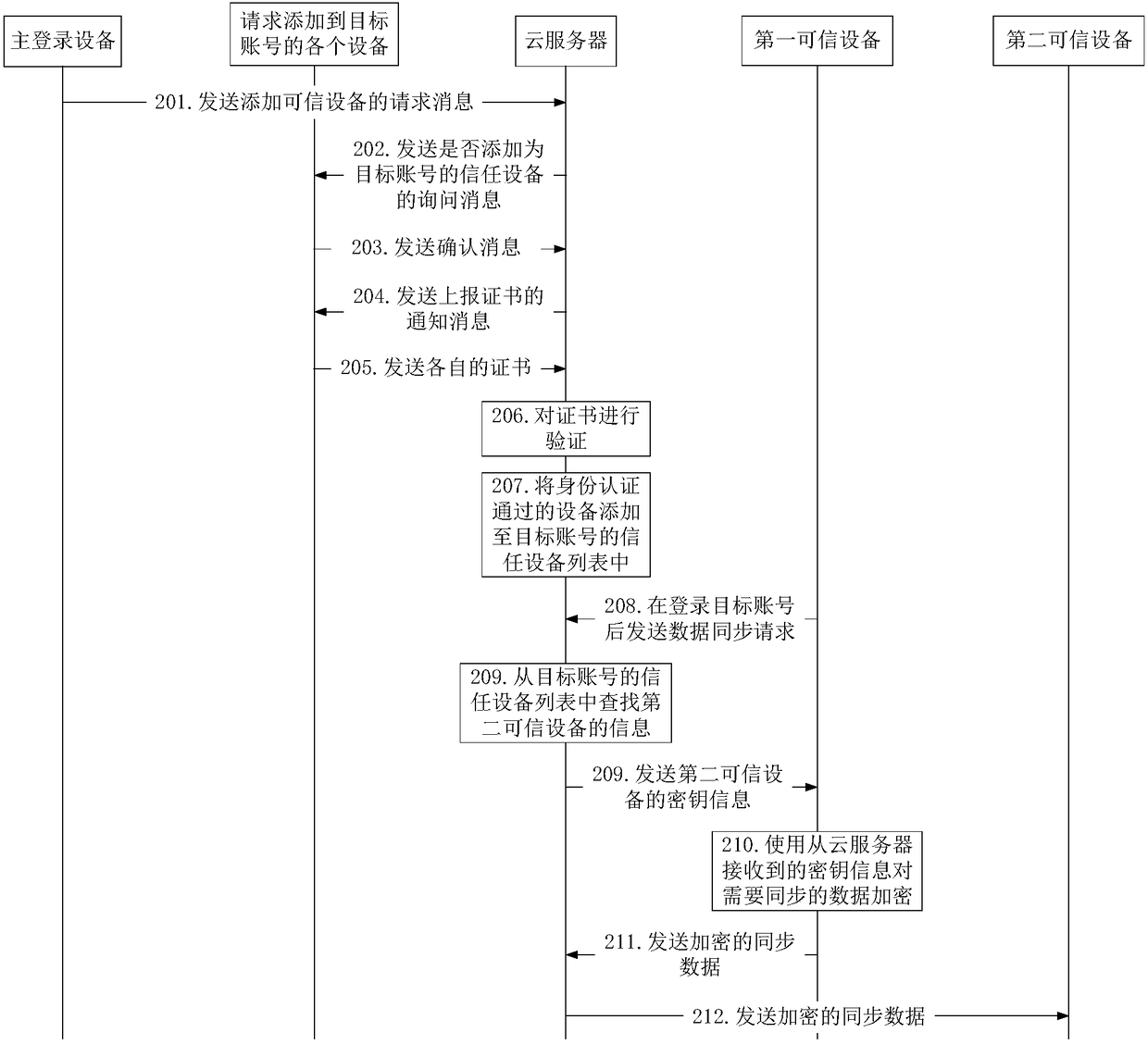
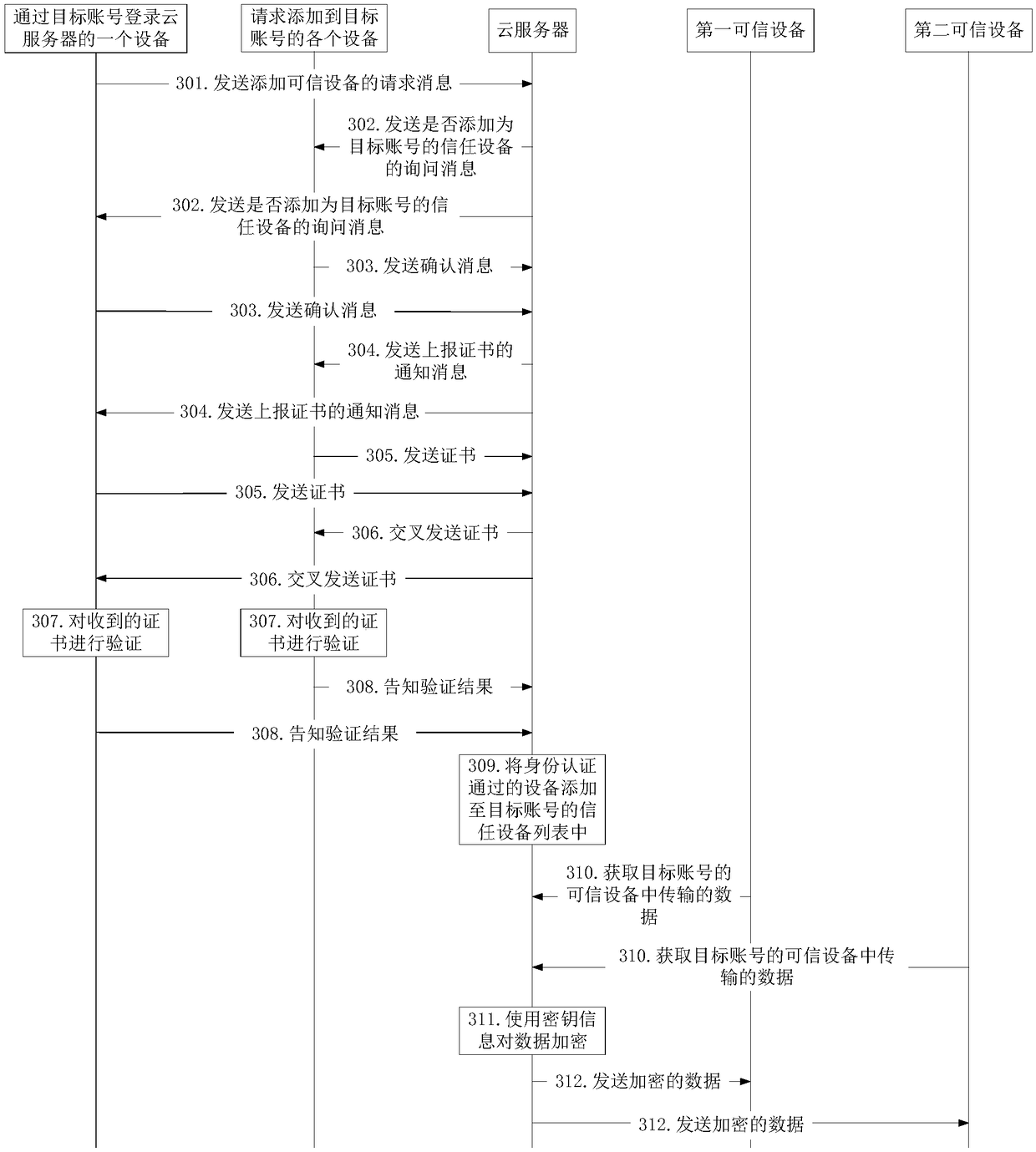
Method for synchronizing data between equipment via cloud and cloud server
ActiveCN108134789APrevent leakageGuaranteed safe transmissionTransmissionData synchronizationSecure transmission
The embodiment of the invention discloses a method for synchronizing data between equipment via cloud and a cloud server. The method for synchronizing data between equipment via the cloud provided bythe embodiment of the invention comprises the steps as follows: the cloud server pre-builds a trusted equipment list of a target account, wherein the trusted equipment list comprises information of atleast two pieces of trusted equipment of the target account, and the information of each piece of trusted equipment comprises key information used for encrypting data to be synchronized; the cloud server transmits synchronous data between the part of or all trusted equipment of the target account according to the trusted equipment list of the target account, wherein the synchronous data is ciphertext data encrypted by using the key information. According to the method and the cloud server provided by the embodiment of the invention, the information leakage caused by capturing of the data is avoided, and the secure transmission of the data is ensured.
Owner:BEIJING SENSESHIELD TECH
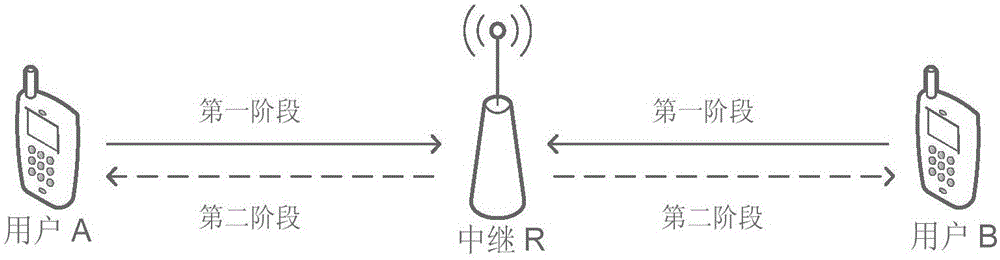
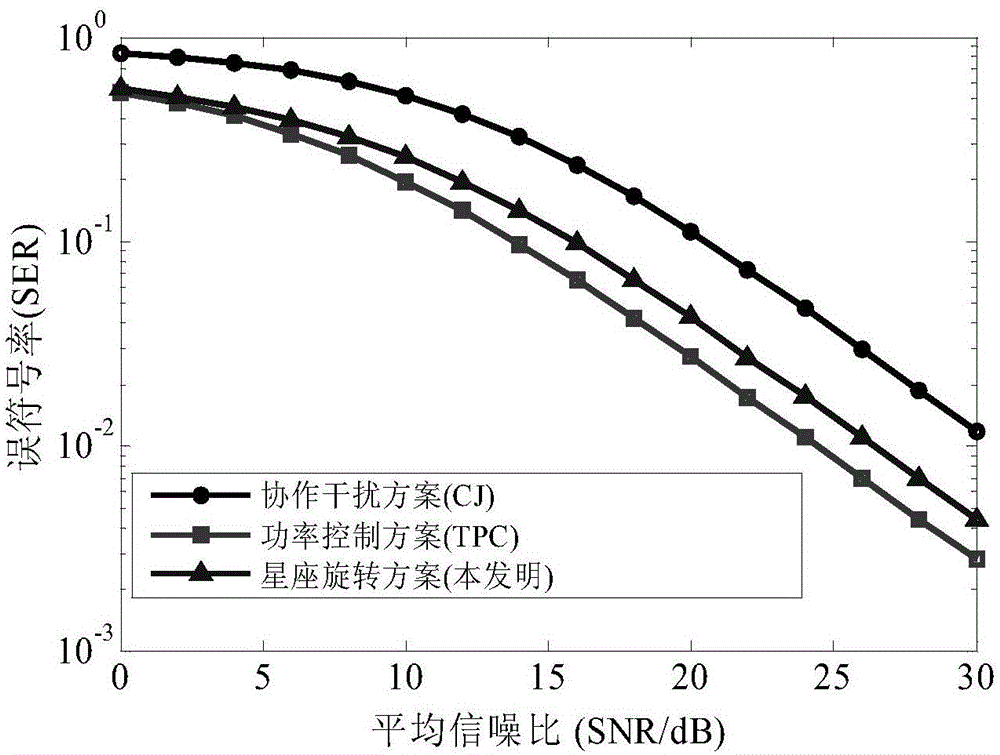
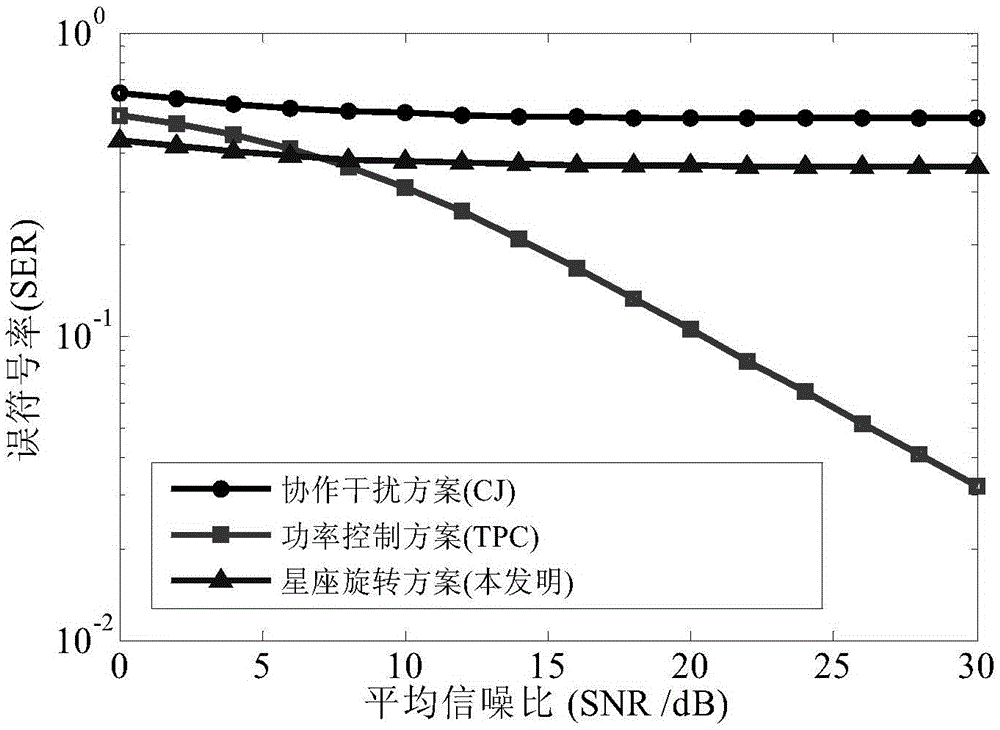
Constellation rotation assisted wireless physical layer secure transmission method in two-way relay system
ActiveCN105163310AIncrease the difficulty of eavesdroppingGuaranteed safe transmissionRadio transmissionSecurity arrangementVIT signalsConstellation
The invention discloses a constellation rotation assisted wireless physical layer secure transmission method in a two-way relay system. The constellation rotation assisted wireless physical layer secure transmission method comprises: 1) channel information is established, a user node A and a user node B select symbols carrying information from a rotated constellation, inject manual noise to construct a composite signal, carry out phase pre-compensation on the composite signal according to the estimated channel information to obtain a composite signal SA to be sent by the user node A and a composite signal SB to be sent by the user node B, and meanwhile respectively send the composite signal SA to be sent and the composite signal SB to be sent at transmitting power P; 2) a relay receives the signals sent by the user node A and the user node B to obtain a mixed signal yB; 3) the relay amplifies the obtained mixed signal and broadcasts the mixed signal to the user node A and the user node B; and 4) the user node A and the user node B detect the mixed signal. The constellation rotation assisted wireless physical layer secure transmission method disclosed by the invention can be used for effectively resisting the eavesdropping behavior of incredible relays.
Owner:XI AN JIAOTONG UNIV
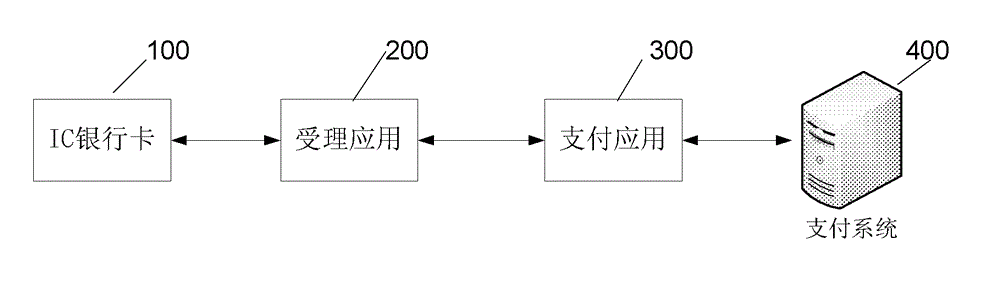
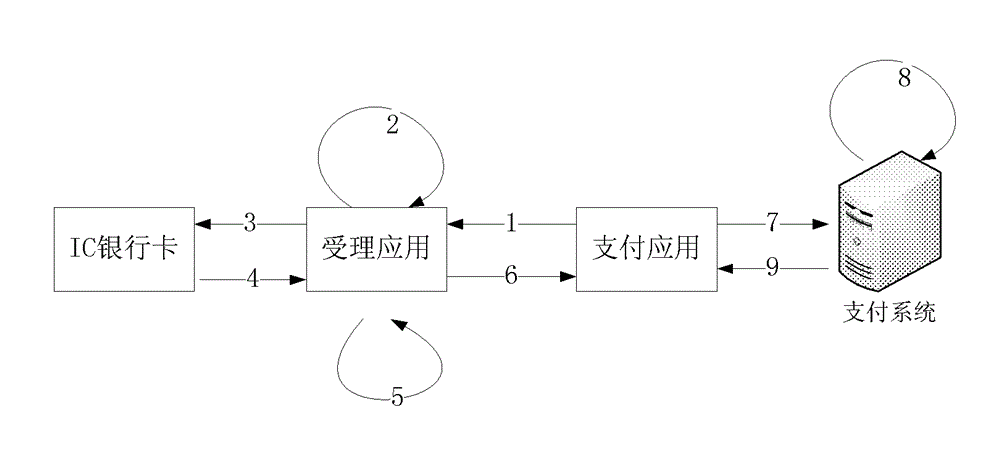
Online payment method and online payment system based on IC bank card
The invention relates to an online payment method and online payment system based on an IC bank card. The online payment method based on the IC bank card comprises a binding activating step and a payment step. The payment step comprises: a first sub step that a payment application initiates a dynamic token generating request to an accepting application; a second sub step that the accepting application verifies whether the dynamic token generating request is valid and initiates a dynamic token acquiring request to the IC bank card if yes; a third sub step that the IC bank card generates dynamic token abstract data according to the dynamic token acquiring request and returns the dynamic token abstract data to the accepting application; a fourth sub step that the accepting application generates a dynamic token according to the acquired dynamic token abstract data and returns the dynamic token to the payment application; a fifth sub step that the payment application transmits a payment request including the dynamic token to a payment system; and six sub step that the payment system authenticates the payment request and completes payment if authentication succeeds.
Owner:CHINA UNIONPAY
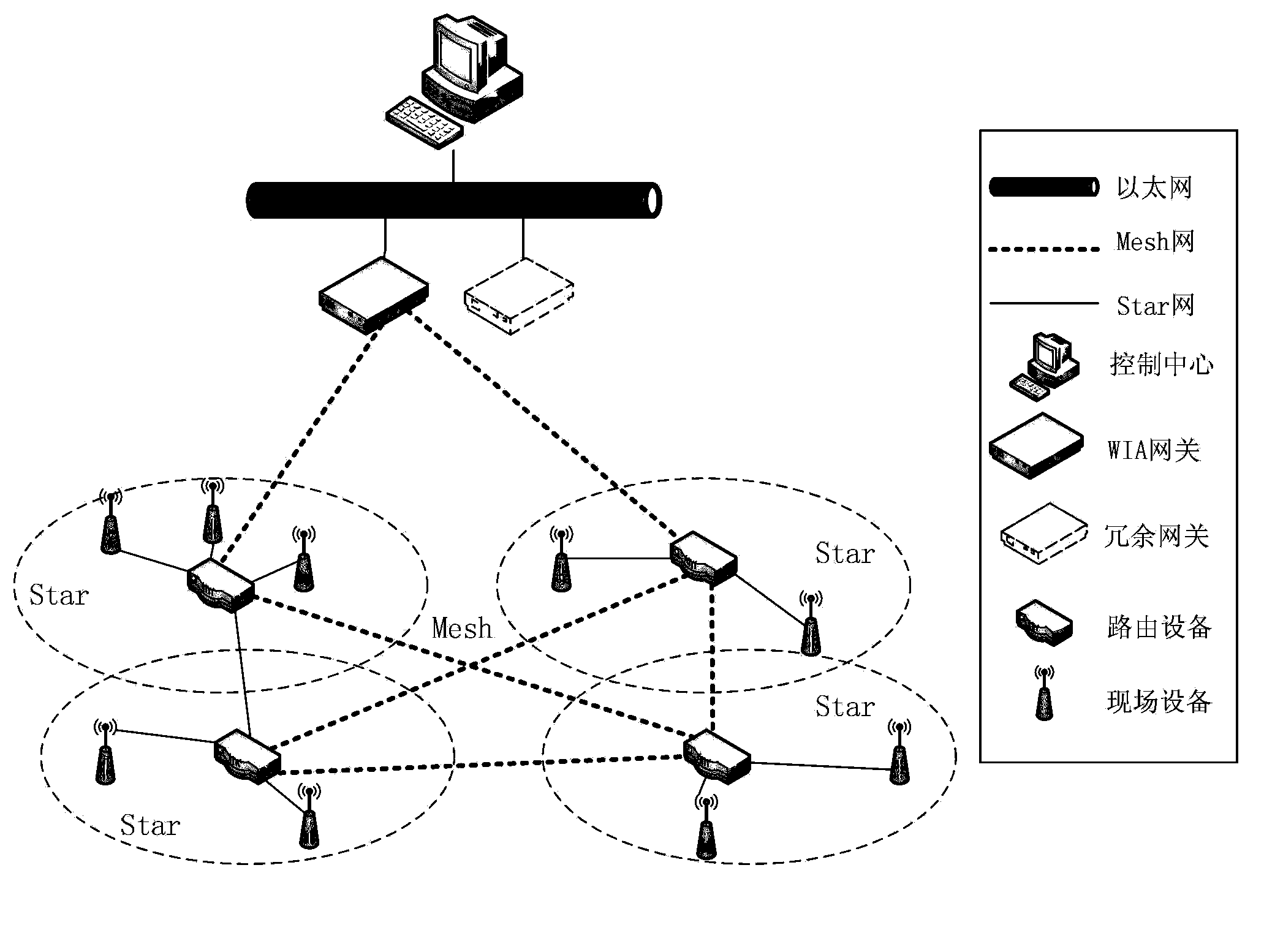
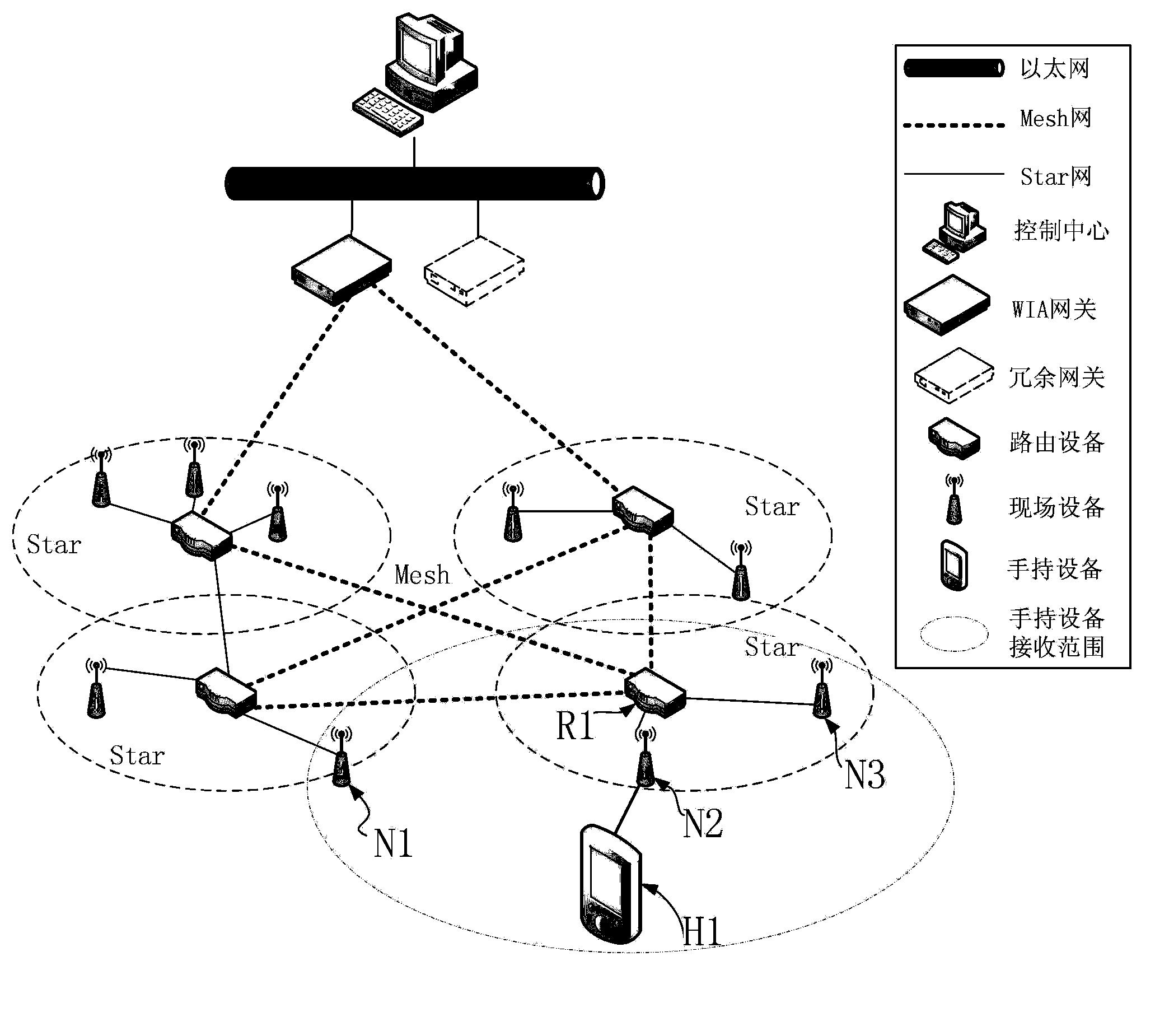
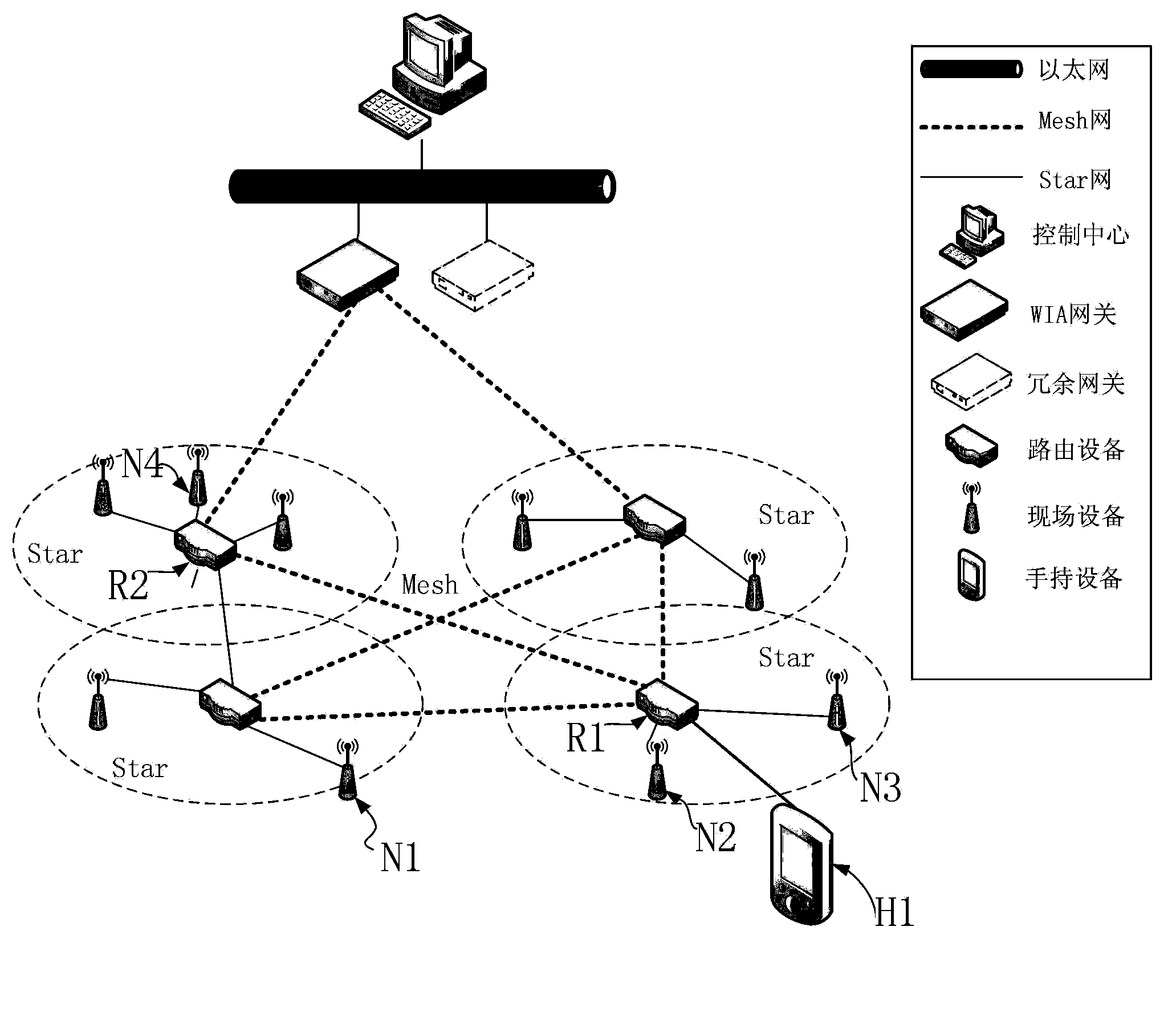
Multi-level encryption and authentication type WIA-PA network handheld device communication method
ActiveCN103888940AFast encryptionReduce power consumptionSecurity arrangementHigh level techniquesField deviceEncryption
The invention relates to a high-safety multi-level encryption and authentication type WIA-PA network handheld device communication method. The WIA-PA network includes a gateway, a routing device and a field device. The handheld device can be in safe communication with devices in the WIA-PA network in two ways. In the first way, point-to-point communication is established between the handheld device and the devices in the WIA-PA network, and encryption is performed in the link layer. In the second way, the handheld device is joined into the WIA-PA network, and the handheld device is in communication with the devices in the WIA-PA network through the multi-level encryption technology after the handheld device is joined into the WIA-PA network. Through the combination of the two ways, the safety can be ensured, and at the same time, communication is fast established between the handheld device and the devices in the network, and advantages of low power consumption, fast speed and less network performance influences can be realized.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
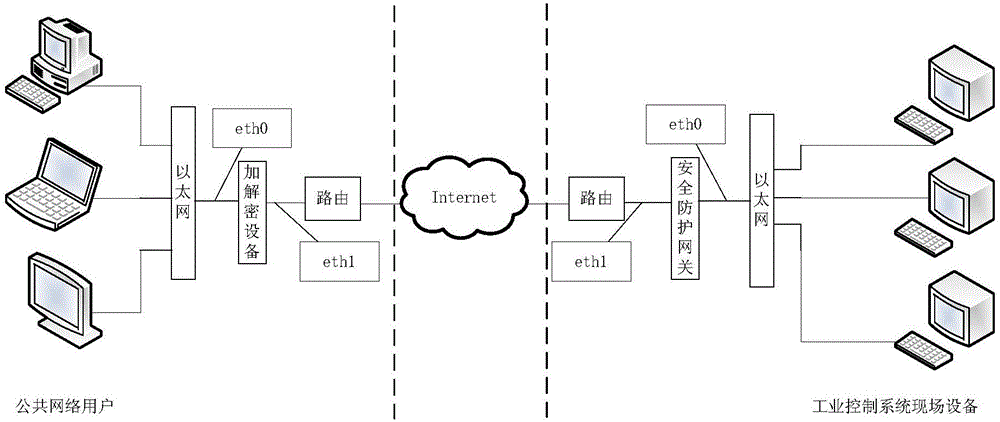
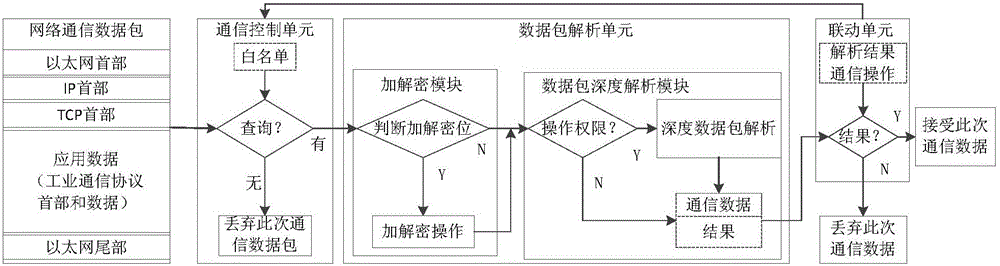
Safe protective gateway and system for modern industrial control system network communication
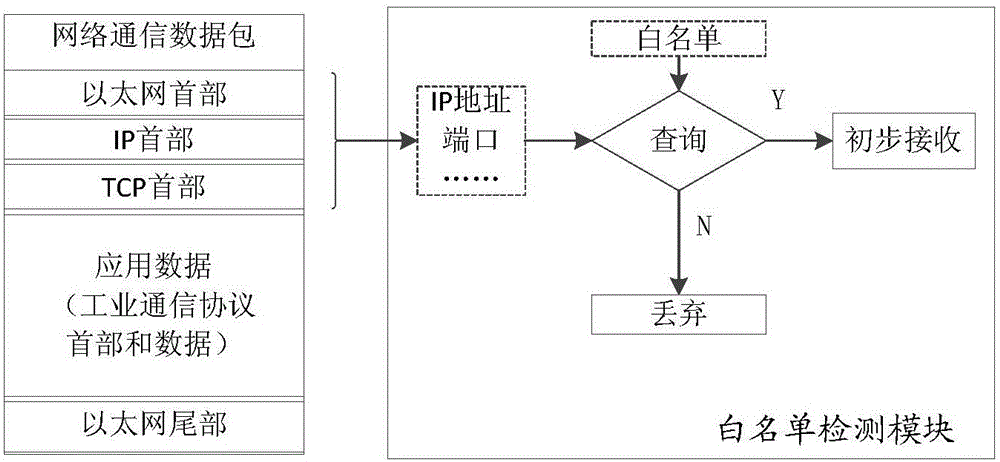
ActiveCN105072025AGuaranteed safe transmissionImprove automatic defense capabilitiesNetwork connectionsCommunications securityNetwork packet
The invention provides a safe protective gateway and system for modern industrial control system network communication, which can guarantee safe communication between users and field devices in a public network. The gateway comprises a communication control unit, a data package analysis unit and a linkage unit. The communication control unit is used for basic communication control and control of communication between the users and the field devices according to a command sent from the linkage unit. The data package analysis unit is used for performing selective encryption and decryption and selective deep analysis on a received communication data package. The linkage unit is used for sending a command whether to refuse subsequent communication requests of the user to the communication control unit according to an analysis result, and determining whether to send the analyzed communication data package to a target field device. The safe protective gateway and system are applicable to the technical field of communication.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
Thermal lodging type low-aging-speed cable
ActiveCN111710462ANot easy to frostbiteImprove cooling effectClimate change adaptationInsulated cablesInsulation layerThermal break
The invention discloses a thermal lodging type cable with a low aging speed, and belongs to the fields of cable. According to the thermal lodging type low-aging-speed cable, at a low temperature, opposite heat insulation sheets form a circle of independent heat insulation layer in an outer protection layer so as to effectively avoid external low temperature from being conducted into a wire core layer while a self-lodging rod is not in contact with the surface of the wall-attached heat insulation layer so as to effectively reduce heat exchange inside and outside the cable, so that the cable iseffectively prevented from being frostbitten at a low temperature; at a high temperature, the opposite heat insulation sheets are propped open after being heated, and a double-end embedded heat conduction rod can be communicated with a sheath layer and the wall-attached heat insulation layer so as to continuously dissipate the heat generated by the cable from inside to outside while the self-lodging rod falls down and is attached to the surface of the wall-attached heat insulation layer, so that the heat dissipation performance of the cable is effectively improved; and the heat dissipation andheat insulation performance of the cable can be automatically adjusted at different use temperatures, so that the aging speed is remarkably reduced, the service life is prolonged, and potential safety hazards are reduced.
Owner:湖南湘联电缆有限公司
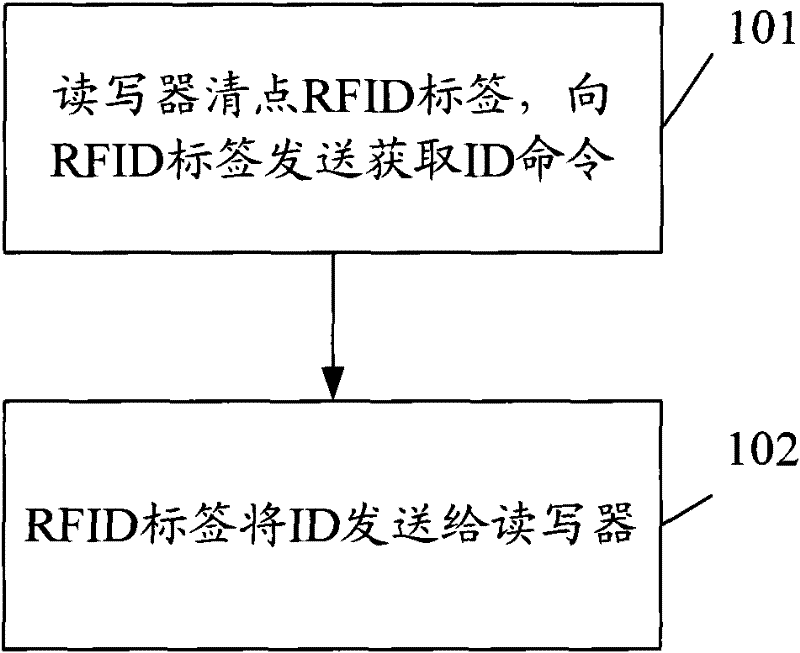
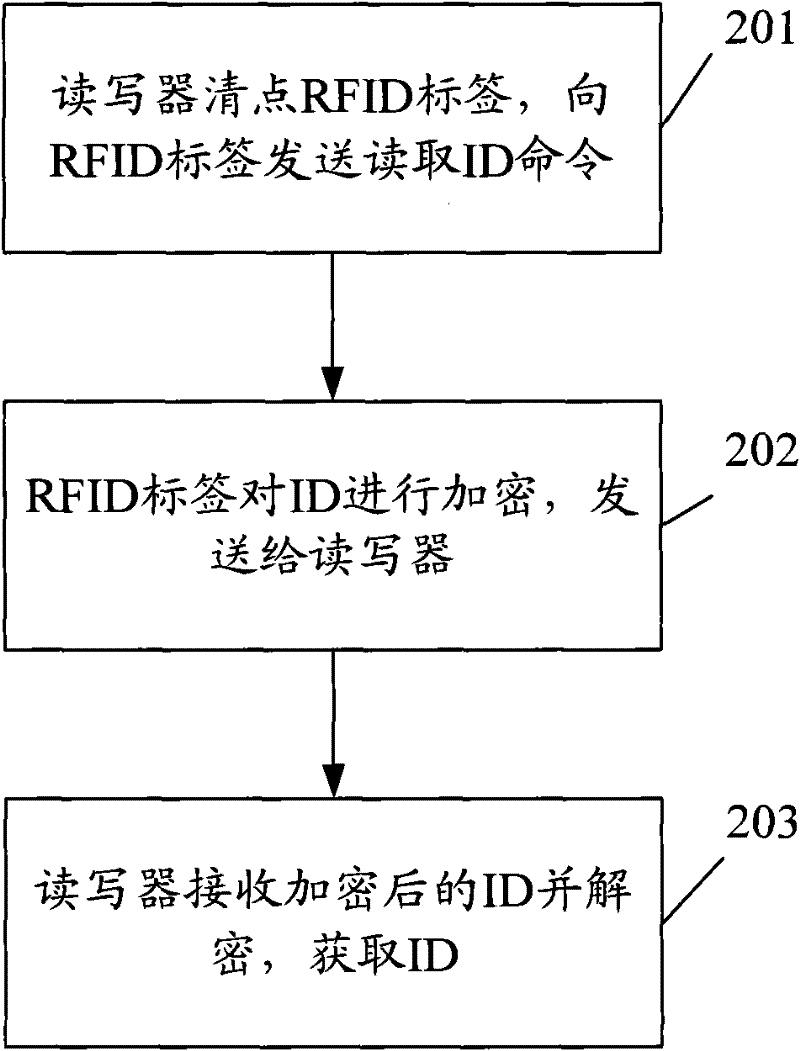
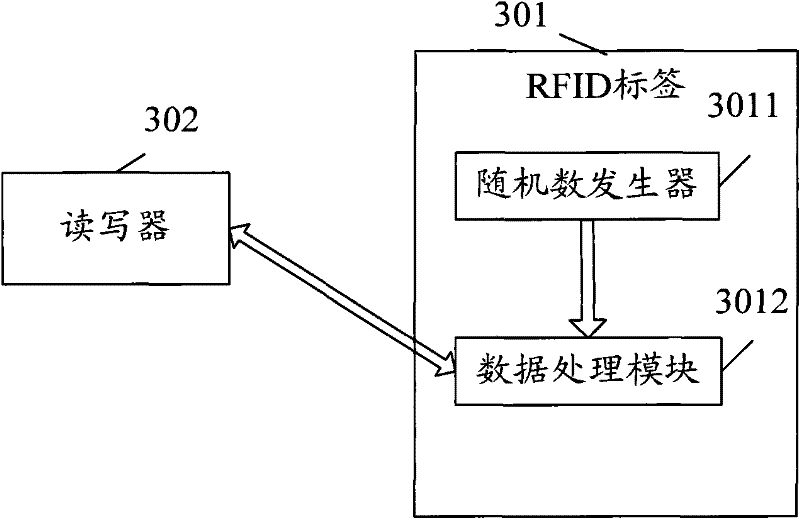
RFID (radio frequency identification) tag identification method
InactiveCN102479334AImprove securityGuaranteed safe transmissionCo-operative working arrangementsRadio frequencyComputer science
The invention discloses an RFID (radio frequency identification) tag identification method. The method comprises the following steps: a reader checking an RFID tag; the RFID tag generating a random number and transmitting the random number to the reader; the reader transmitting a unique identification (ID) code reading command including the random number to the RFID tag; and the RFID tag encrypting ID according to the random number and a preset encryption algorithm, and transmitting the encrypted ID to the reader. The invention also discloses an RFID tag identification system. The method and the system provided by the invention can enhance ID identification security and ensure safe transmission of RFID tag data, thereby facilitating development of RFID technique.
Owner:TIANJIN ZHONGXING SOFTWARE
Software-defined Internet of Things network topology data transmission security management method and system
ActiveCN112565230AReduce control overheadGuaranteed safe transmissionKey distribution for secure communicationUser identity/authority verificationGlobal topologyTopology information
The invention provides a software-defined Internet of Things network topology data transmission security management method and system, and the method comprises the steps: deploying common nodes and aggregation nodes at Internet of Things network nodes, and enabling the nodes to communicate with each other; performing encryption algorithm configuration on common nodes and aggregation nodes; each adjacent node performing bidirectional identity authentication and key agreement, and each node recording credible nodes passing authentication around itself and suspicious nodes failing to be authenticated; periodically executing topology discovery, collecting topology information of common nodes by the aggregation nodes, forwarding messages of trusted nodes among the aggregation nodes, establishing a trusted path, and constructing a global topology view; sequentially forwarding and aggregating the topology state messages according to the determined trusted path; and determining newly added nodes and malicious nodes based on the global topology view, broadcasting, and updating the network topology structure of the Internet of Things. According to the invention, the security and reliabilityof data transmission can be effectively improved.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +1
Authorized user safe transmission oriented power distribution method in cognitive wireless network
ActiveCN105959939AGuaranteed safe transmissionIncrease transfer rateTransmission monitoringSecurity arrangementTransmission delayTransmission rate
The invention discloses an authorized user safe transmission oriented power distribution method in a cognitive wireless network. The system has four states according to a channel occupation state and a perception result. The transmission rate of a cognitive user and the safe transmission rate and the safe outage probability thereof of the authorized user are computed under each state. Under the constraint of the safe outage probability of the authorized user, the average transmission rate of the cognitive user is maximized so as to obtain the power distribution under each system state. Compared with the comparison scheme, the purposed scheme can guarantee the safe transmission of the authorized user while improving the transmission rate of the cognitive user.
Owner:XI AN JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com