NOMA mobile edge computing system construction method with anti-eavesdropping capability
A technology of edge computing and construction method, which is applied in the field of construction of secure NOMA mobile edge computing system, can solve the problem of whether it is difficult and unrealistic to detect eavesdroppers, achieve low latency, ensure safe transmission, and improve spectral efficiency. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings.
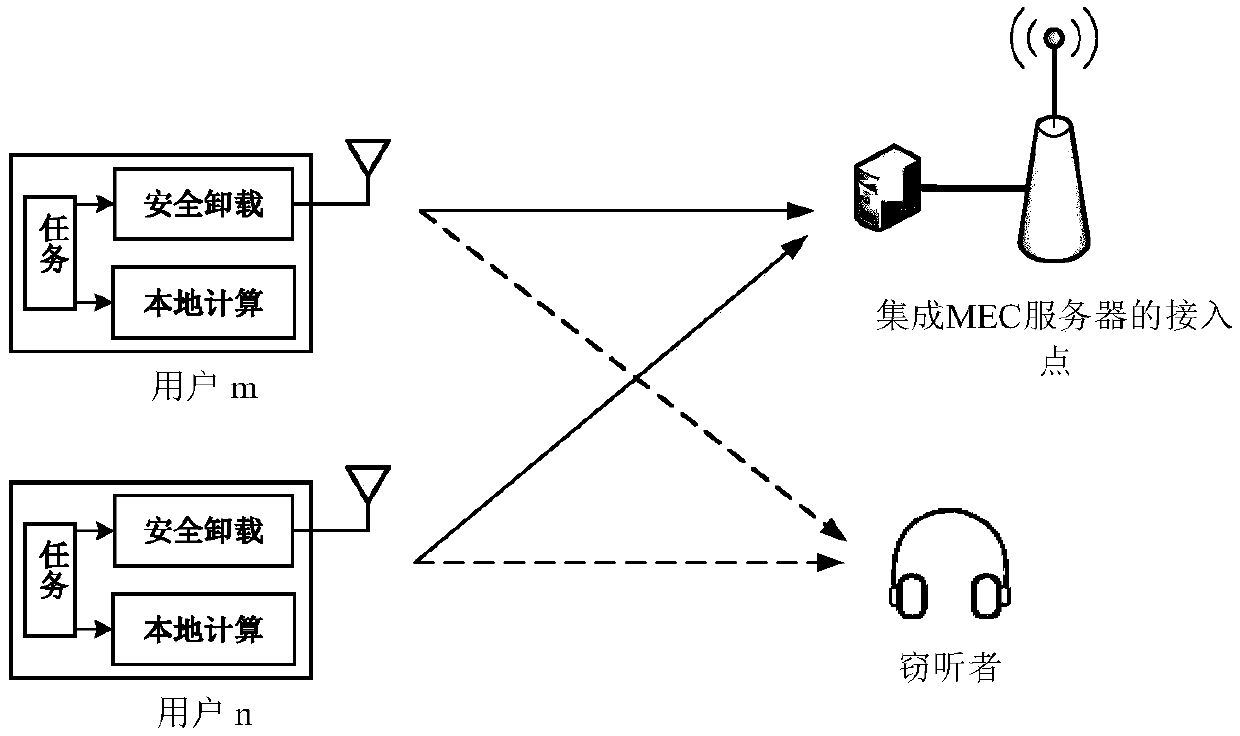
[0043] In the absence of eavesdropper channel state information, a reasonable way to enhance confidentiality is to use all available resources to guarantee a certain degree of service quality, such as high reliability and low delay of transmission, etc. The invention proposes that under the condition of not knowing the channel state information of the eavesdropper, the user introduces a measure irrelevant to the eavesdropper's channel state information to quantify the user's anti-eavesdropping ability through secret coding, so as to achieve information security transmission. refer to figure 1 , a kind of secure NOMA mobile edge computing system with anti-eavesdropping capability is provided in the embodiment, and the construction of the system includes the following steps:
[0044] Step 1: In the described system, consider the case where ther...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com