Secure transmission method based on non-trusted cognitive user collaboration interference
A technology of cognitive user and secure transmission, applied in the field of wireless communication, can solve the problem of cognitive network security, not trustworthy, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The present invention will be further described in detail below in conjunction with specific embodiments, which are explanations of the present invention rather than limitations.
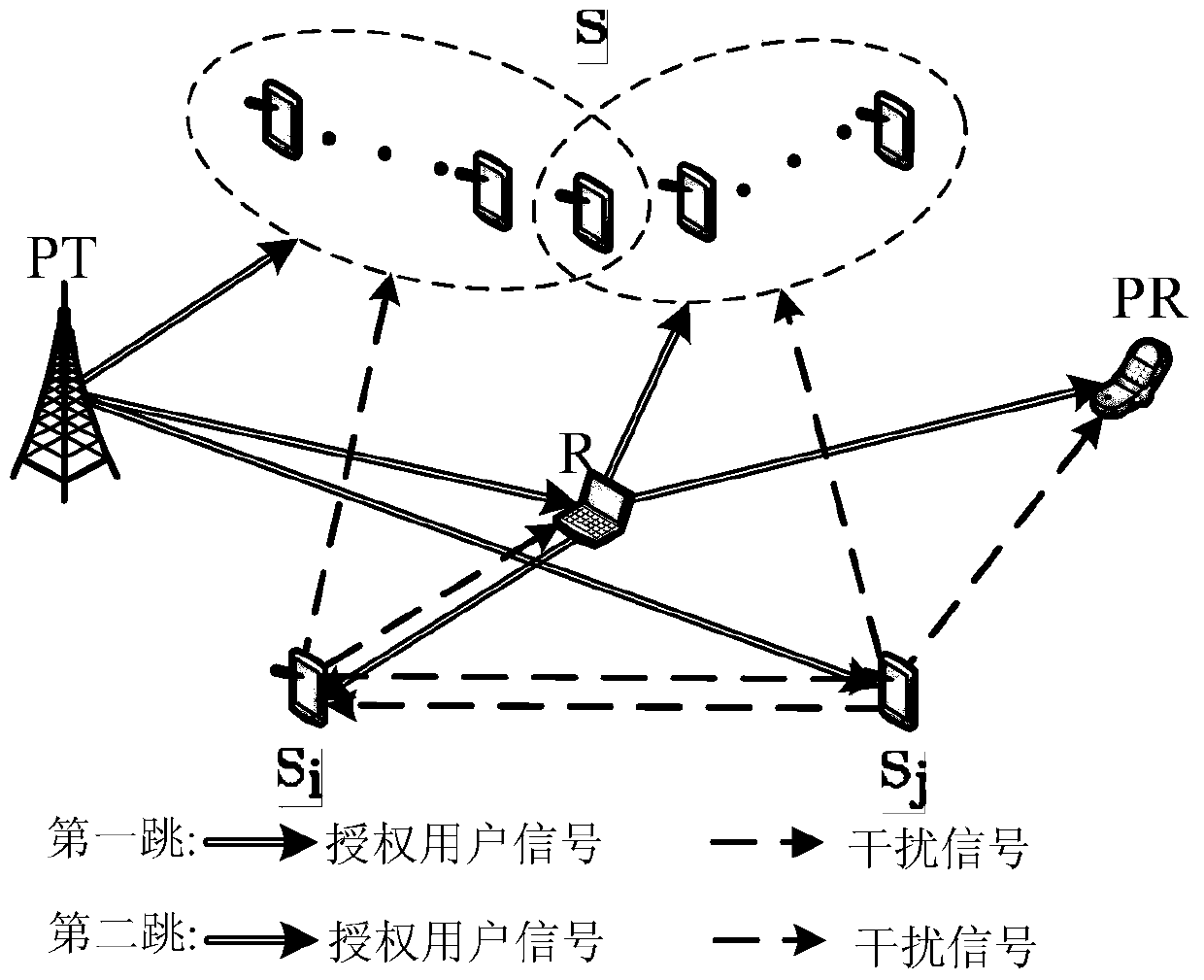
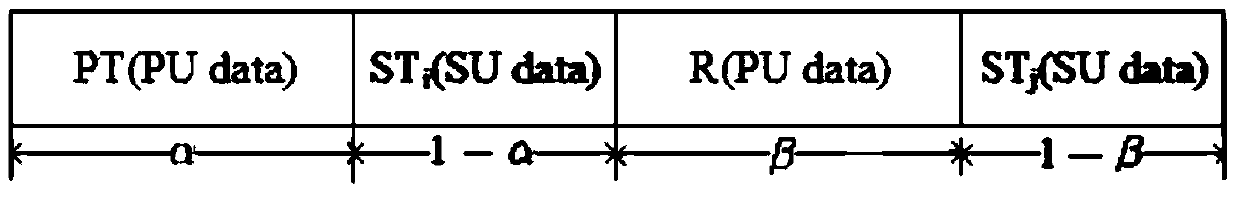
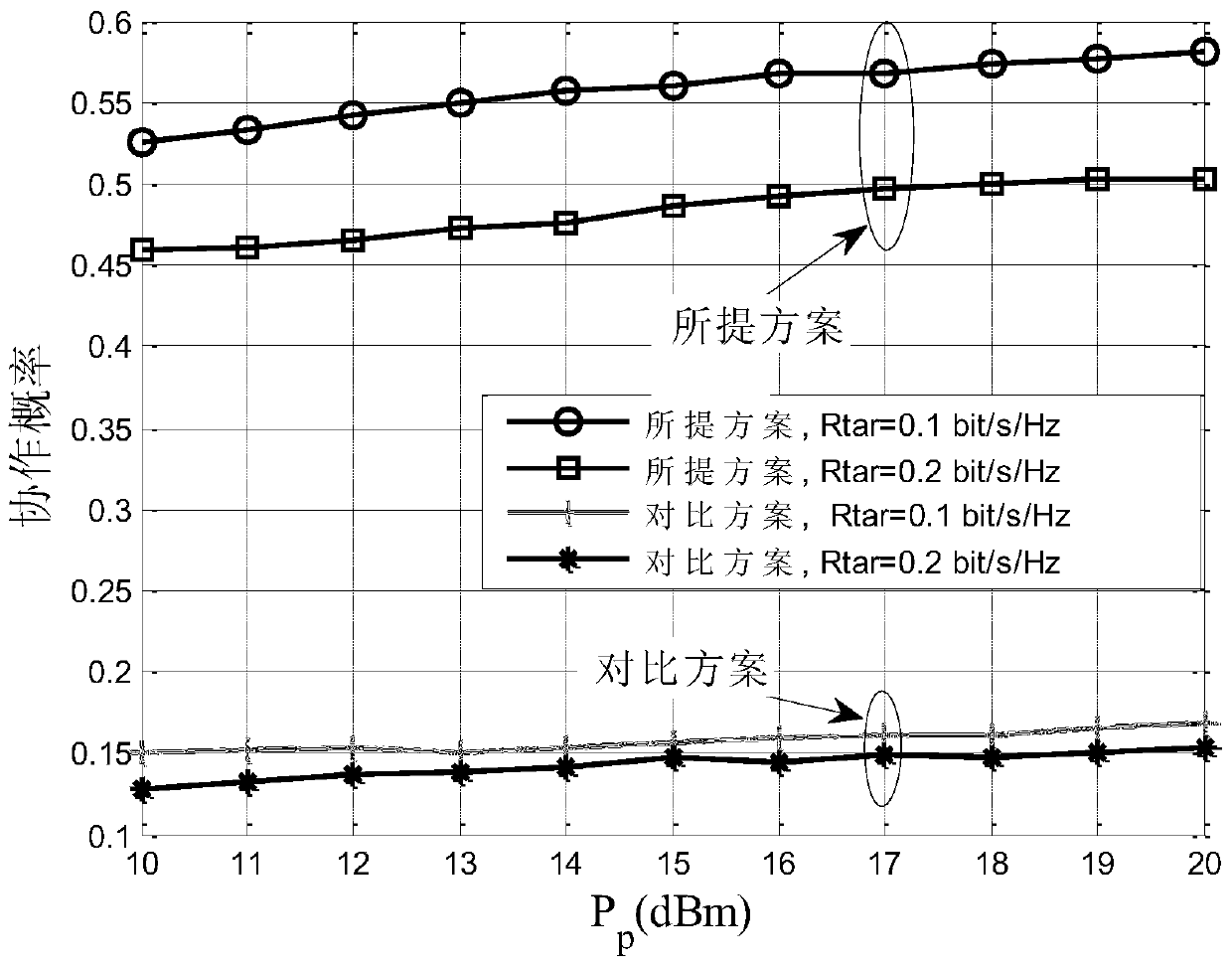
[0061] Since the access environment of the authorized network is open, it faces the problem of eavesdropping by cognitive users. At the same time, since cognitive users do not have authorized spectrum, it needs to assist authorized users to securely transmit to obtain spectrum opportunities. Cooperative jamming is a very effective security transmission scheme, which can reduce the eavesdropping rate of eavesdropping links, thereby increasing the security capacity of authorized users. Therefore, in the present invention, we use cognitive user cooperative interference to assist authorized users to transmit securely, thereby ensuring secure transmission of authorized users, and cooperative cognitive users can obtain certain spectrum opportunities as compensation for their cooperation.
[0062] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com