Safety communication system
A secure communication and security technology, applied in the Internet field, can solve problems such as hindering informatization and weak authentication mechanisms, and achieve the effects of reducing risks, improving security and reliability, and ensuring safe transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
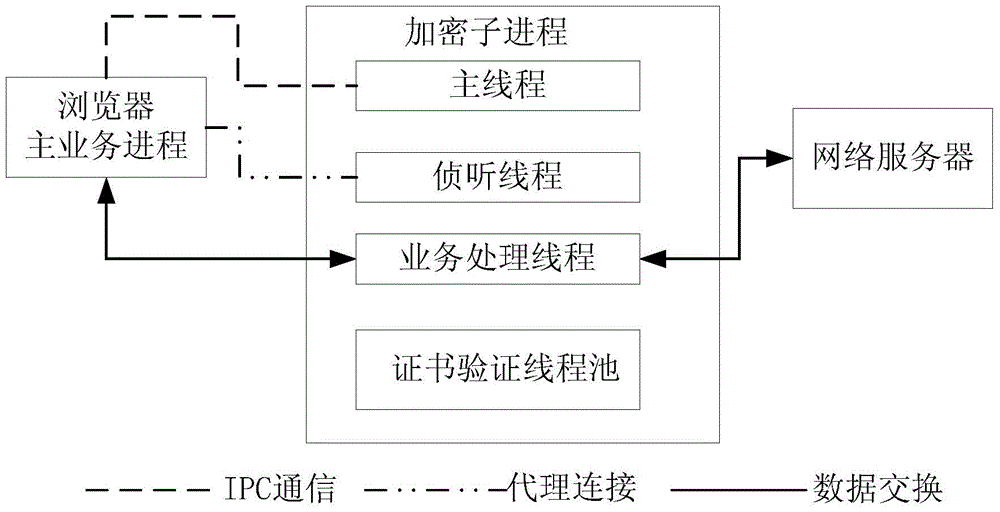
[0019] refer to figure 1 , which shows a flow chart of the steps of an implementation method embodiment of a secure browser according to an embodiment of the present invention, which may specifically include the following steps:
[0020] Step 102, start an encryption sub-process in the browser client to communicate with the browser main business process, wherein the encryption sub-process is used as a connection agent to realize the conversion from the first encryption channel to the second encryption channel, and the data Forward.
[0021] For some websites, such as banking websites, Alipay websites and other websites that involve financial services, encrypted data transmission needs to be carried out through a security-oriented HTTP (HTTP-Hypertext transfer protocol) channel, but sometimes the main business process of the browser Different encryption protocols or algorithms are used with the web server, so that the two cannot communicate directly, and cannot access the web ...
Embodiment 2
[0034] On the basis of the above embodiments, this embodiment continues to discuss the implementation method of the secure browser.
[0035] refer to figure 2 , which shows a flow chart of the steps of an implementation method embodiment of a secure browser according to an embodiment of the present invention, which may specifically include the following steps:
[0036] Step 202, start an encryption sub-process in the browser client to communicate with the browser main business process, wherein the encryption sub-process is used as a connection agent to realize the conversion from the first encryption channel to the second encryption channel, and the data Forward.
[0037] In this embodiment, the encryption sub-process that starts communication with the browser main business process in the browser client can be automatically started by the browser. Specifically, when the browser main business process fails to communicate with the network server, the browser automatically The...
Embodiment 3
[0125] On the basis of the above embodiments, this embodiment also discloses a secure communication system.
[0126] refer to Figure 5 , shows a structural block diagram of an embodiment of a secure communication system according to an embodiment of the present invention.
[0127] refer to Figure 6 , shows a structural block diagram of a secure browser device in an embodiment of a secure communication system according to an embodiment of the present invention.
[0128] The secure communication system includes: a secure browser device 504 and a network server 502 .
[0129] Wherein, the network server 502 is configured to establish an encrypted connection communication with the secure browser device; and perform service data interaction with the secure browser device through a second encrypted channel after the encrypted connection communication is successfully established.
[0130] The secure browser device 504 includes: a browser main service process module 50402 and an ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com