Identity authentication method and system
An identity authentication and certificate technology, applied in the field of identity authentication methods and systems, can solve problems such as user security risks, vulnerability to man-in-the-middle attacks, key information theft, etc., and achieve the effect of avoiding security risks, preventing man-in-the-middle attacks, and ensuring secure transmission.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
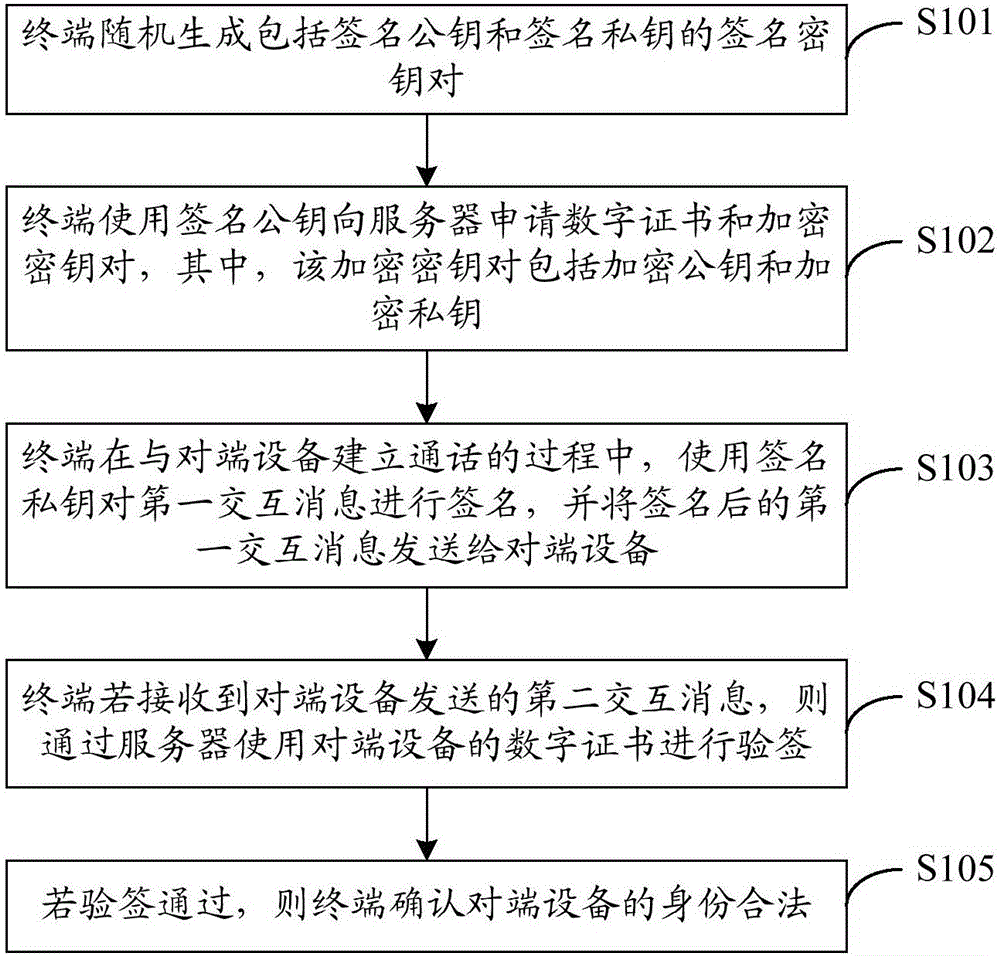
[0037] see figure 1 , figure 1 It is a schematic flow chart of an identity authentication method provided in Embodiment 1 of the present invention. The execution subject of this embodiment includes a terminal and a server, where the terminal may be a smart phone or other smart terminal. figure 1 The shown identity authentication method may include the following steps:
[0038] S101. The terminal randomly generates a signature key pair including a signature public key and a signature private key.
[0039] Specifically, the signature key pair randomly generated by the terminal is used for performing a digital signature and verifying the digital signature.
[0040] S102. The terminal uses the signature public key to apply for a digital certificate and an encryption key pair from the server, where the encryption key pair includes an encryption public key and an encryption private key.
[0041] Specifically, the server includes a certificate authority (Certificate Authority, CA)...
Embodiment 2
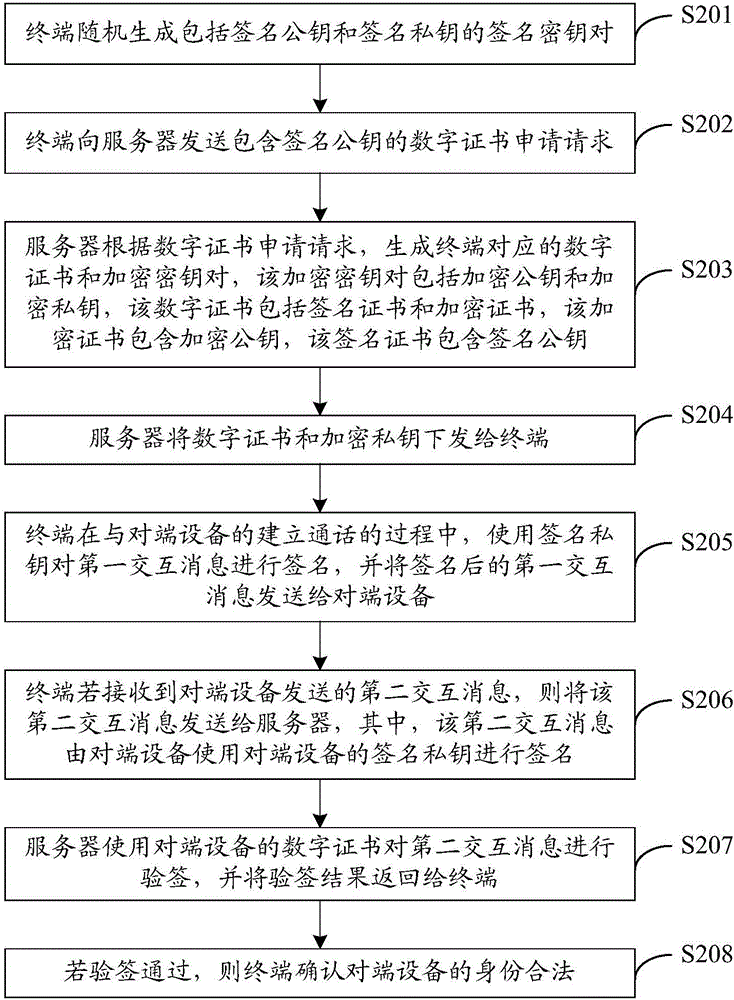
[0058] see figure 2 , figure 2 It is a schematic flow chart of an identity authentication method provided in Embodiment 2 of the present invention. The execution subject of this embodiment includes a terminal and a server, wherein the terminal may be a smart phone or other smart terminal. figure 2 The shown identity authentication method may include the following steps:
[0059] S201. The terminal randomly generates a signature key pair including a signature public key and a signature private key.
[0060] Specifically, the signature key pair randomly generated by the terminal is used for performing a digital signature and verifying the digital signature.
[0061] S202. The terminal sends a digital certificate application request including the signature public key to the server.
[0062] Specifically, the server includes a CA function, which can implement functions such as issuing certificates, authenticating certificates, and managing issued certificates. The terminal ...
Embodiment 3
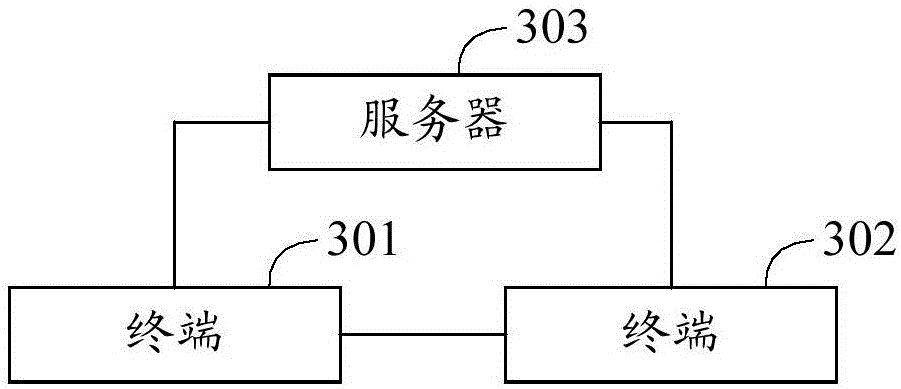
[0102] see Figure 4 , Figure 4 It is a schematic block diagram of an identity authentication system provided by Embodiment 3 of the present invention. For ease of description, only parts related to the embodiments of the present invention are shown. Figure 4 The example identity authentication system 300 may be the execution subject of the identity authentication method provided in the first embodiment. Figure 4 The example identity authentication system 300 mainly includes a terminal 31 and a server 32, and the details are as follows:
[0103] Terminal 31 includes:
[0104] A key generating unit 311, configured to randomly generate a signature key pair comprising a signature public key and a signature private key;
[0105] A certificate application unit 312, configured to use the signature public key generated by the key generation unit 311 to apply to the server for a digital certificate and an encryption key pair, wherein the encryption key pair includes an encrypti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com