Method for secure storage of data and electronic equipment
A technology for safe data storage and electronic equipment, applied in the electronic field, can solve problems such as insecure data storage, and achieve the effect of ensuring communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
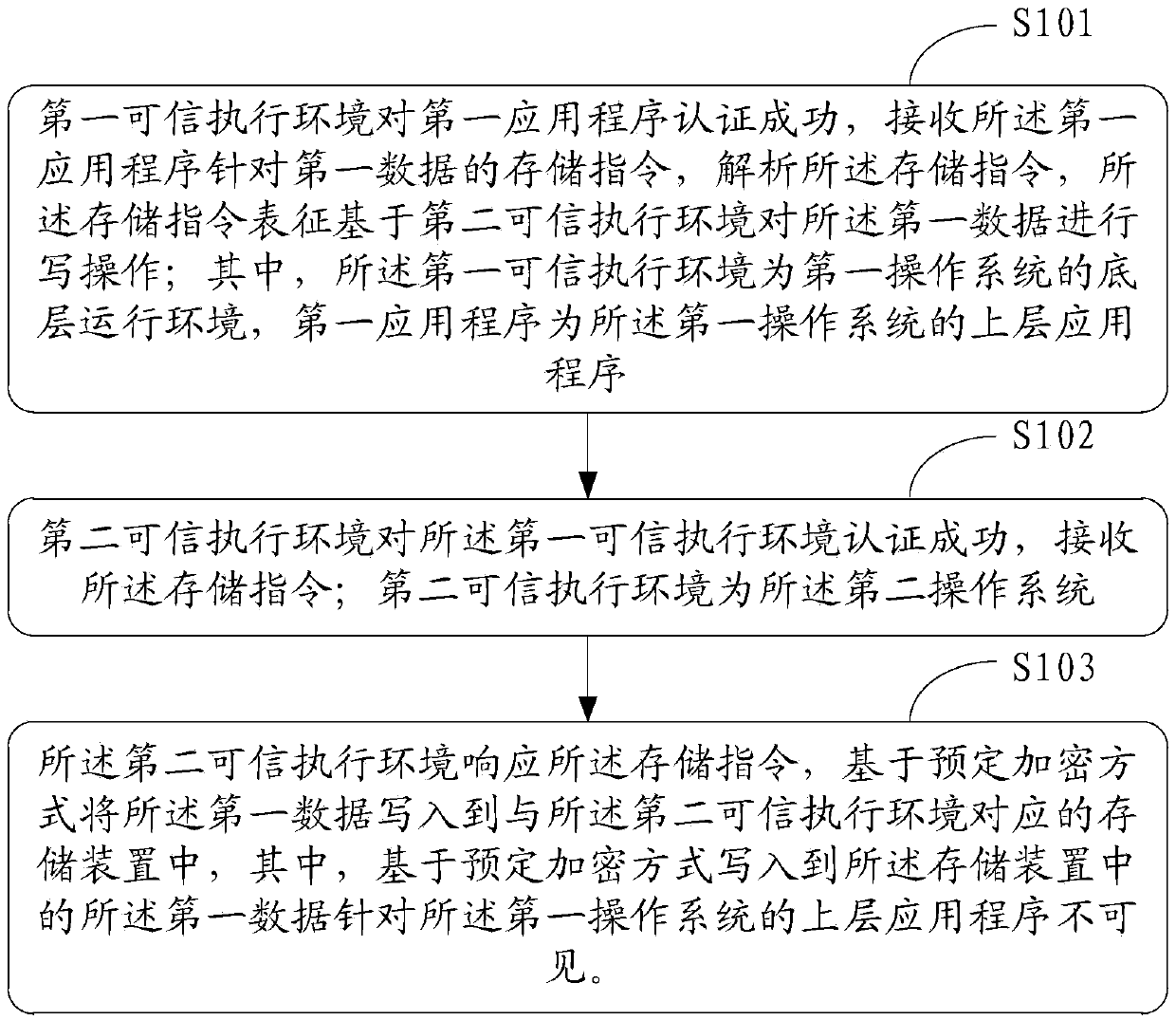
[0087] Please refer to figure 1 , which is a flowchart of a method for securely storing data provided in Embodiment 1 of the present application, the method includes:
[0088] S101: The first trusted execution environment authenticates the first application program successfully, receives the storage instruction of the first application program for the first data, and parses the storage instruction, and the storage instruction is based on the second trusted execution environment. The first data is written; wherein, the first trusted execution environment is the underlying operating environment of the first operating system, and the first application is an upper-layer application of the first operating system;
[0089] S102: The second trusted execution environment successfully authenticates the first trusted execution environment, and receives the storage instruction; the second trusted execution environment is the second operating system;
[0090] S103: In response to the sto...
Embodiment 2
[0129] Based on the same inventive concept as in Embodiment 1 of this application, Embodiment 2 of this application provides an electronic device, please refer to Figure 6 ,include:
[0130] housing 10;
[0131] The memory 20 is arranged in the casing 10, wherein the memory includes a first storage device and a second storage device, and the first storage device is used for storing the first system file corresponding to the first operating system and the first system file corresponding to the first operating system. an application program file corresponding to the application program, the second storage device is used to store a second system file corresponding to the second operating system;
[0132] a processor 30, arranged in the housing 10, configured to receive a storage instruction of the first application program for the first data when the first trusted execution environment successfully authenticates the first application program, and parse the storage instruction, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com