Method, device and system of transmitting data safely
A technology of secure transmission and data, applied in the field of communication, can solve the problems that CoAP message conversion cannot be realized at the same time, CaAP protocol cannot be transmitted normally, and there is no guarantee of separate protection of CoAP protocol and HTTP protocol conversion information and message body transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In the embodiment of the method for obtaining resources provided by the present invention, the implementation process is specifically as follows:
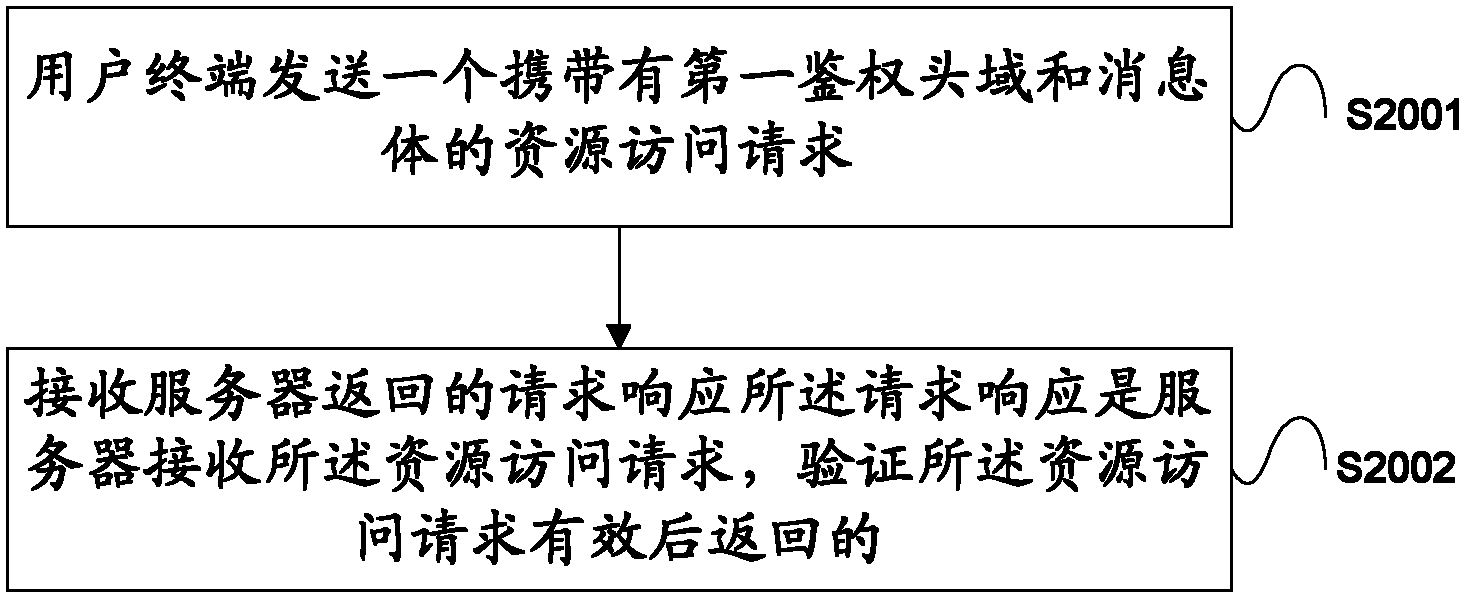
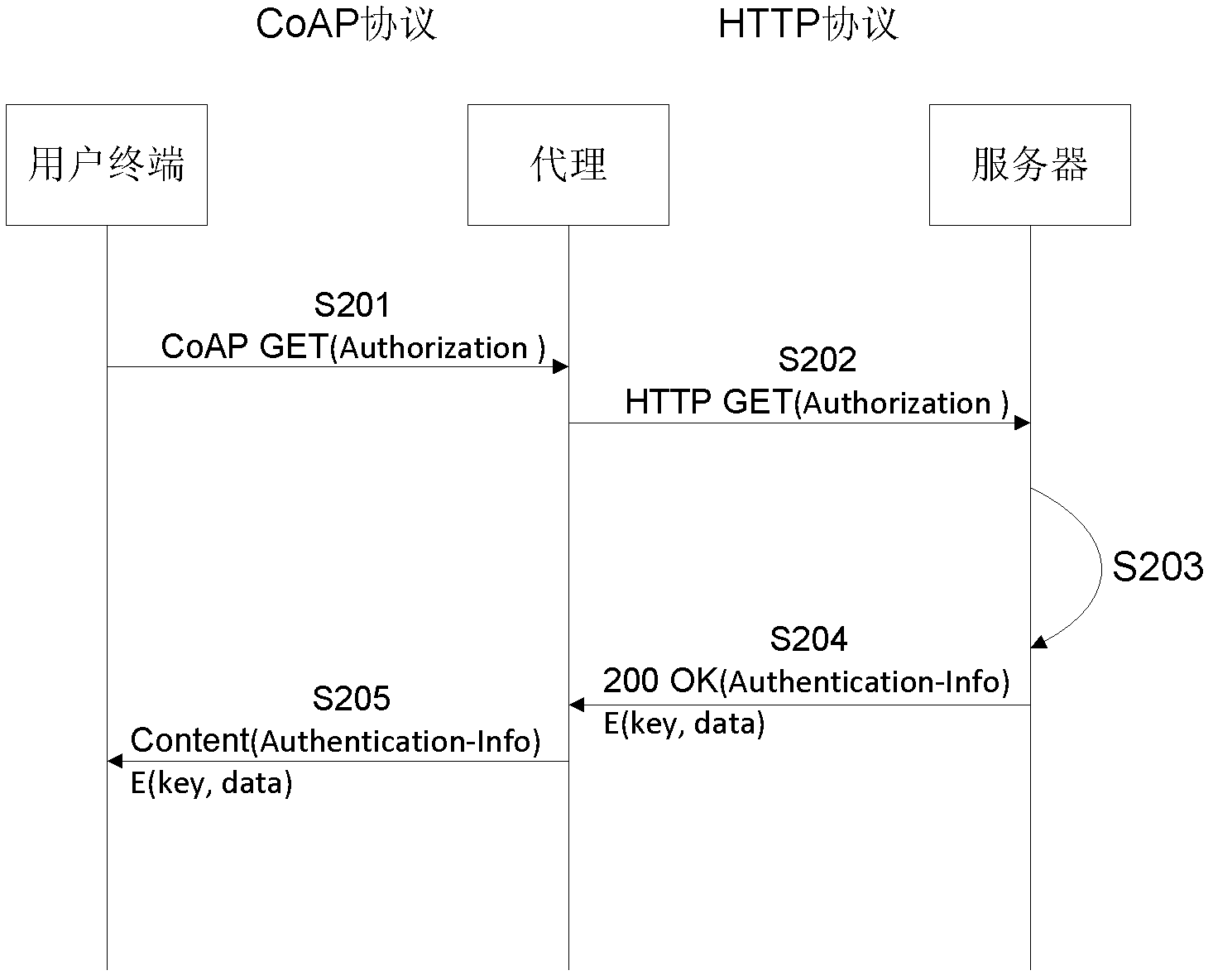
[0048] S1001. The user terminal sends a resource access request carrying the first authentication header to the server.
[0049] Further, the first authentication header field may further include a first digest calculation parameter, and the first digest calculation parameter includes the user identification and the server identification, and also includes a random identification, a resource access path, and a negotiation key One or a combination of several of the parameters; the resource access request sent by the user terminal may further include calculating the first message digest algorithm according to one or more combinations of the user password and the first digest calculation parameter. Complete summary
[0050] The random identification is temporarily generated by the user terminal every time a resource access request me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com