Cloud resource access control method based on dynamic cross-domain security token
A dynamic security and security token technology, applied in the field of access control in information security, can solve the problems of not considering the session key, the secure transmission of confidential information cannot be guaranteed, and the signature authentication process is complicated, so as to strengthen protection and ensure security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be described in detail below through specific embodiments and in conjunction with the accompanying drawings.
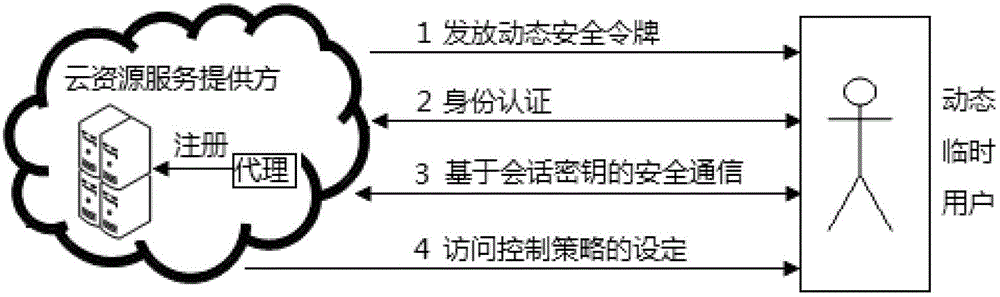
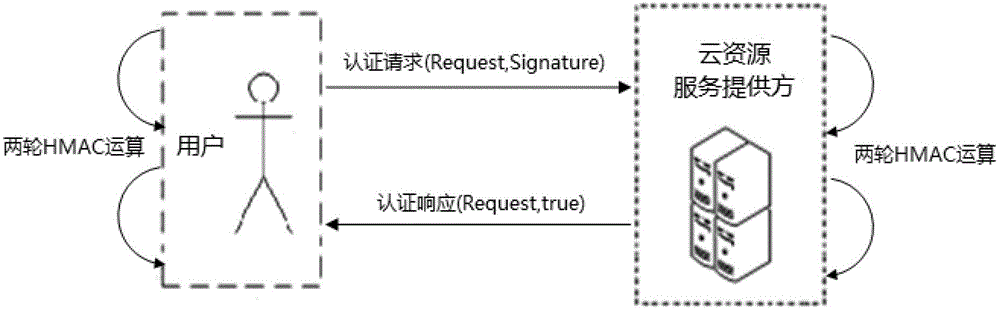
[0024] attached figure 1 The overall framework for the implementation of the program mainly includes the following contents.
[0025] 1. Identity management based on dynamic security tokens
[0026] With the emergence of cloud computing technology, its cross-domain and heterogeneous characteristics make the original resource sharing mode change to resource consumption mode. Among cloud resource consumers, there are not only a large number of users who use cloud resources for a long time, but also some dynamic temporary users who occasionally access cloud resources. For long-term users, accounts can be established for them at cloud resource service providers. Each account has its own billing for cloud resources, and we refer to these long-term users as ordinary cloud resource users.
[0027] For users who occasionally access cloud ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com