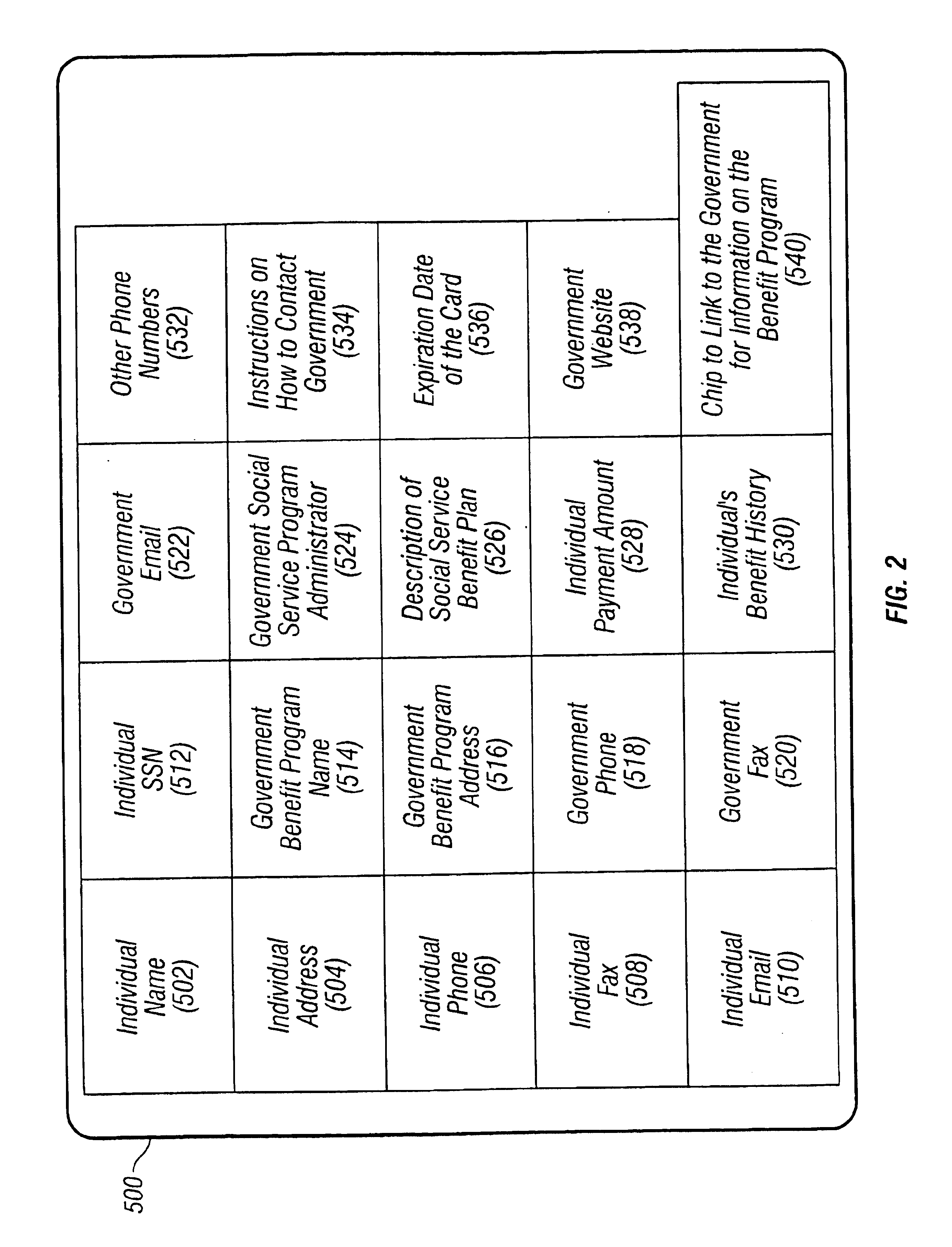
Patents
Literature
135results about How to "Reduce fraud" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
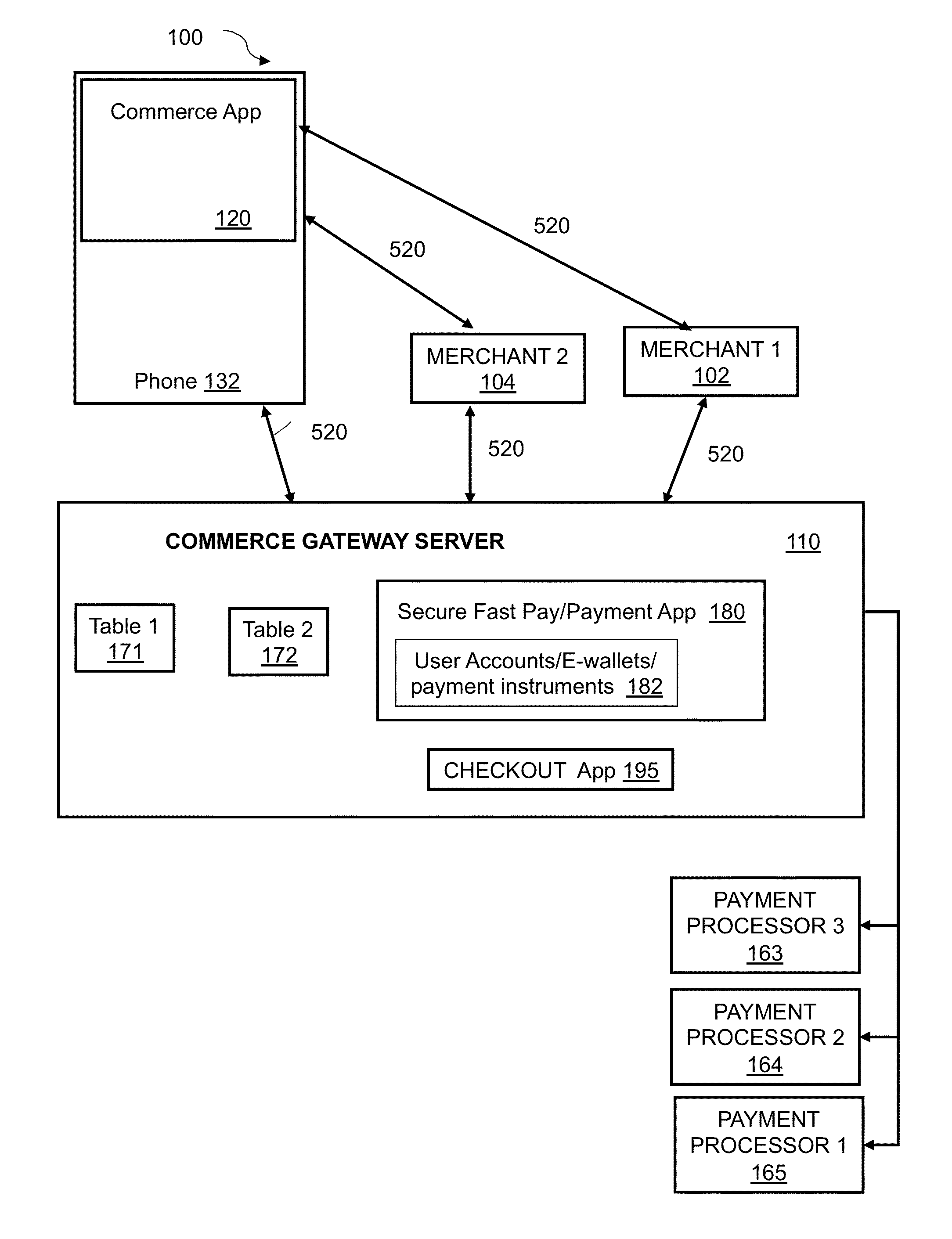
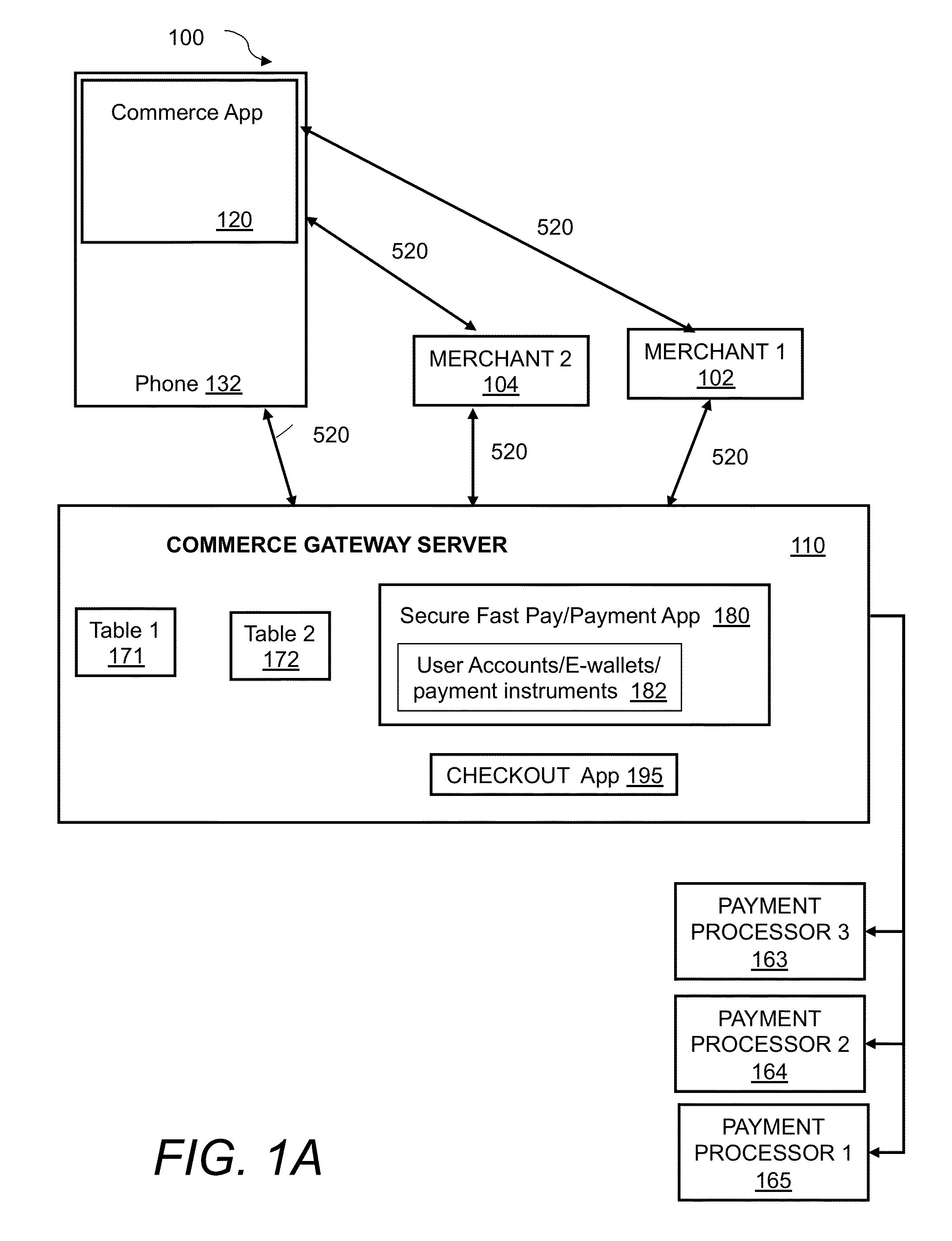
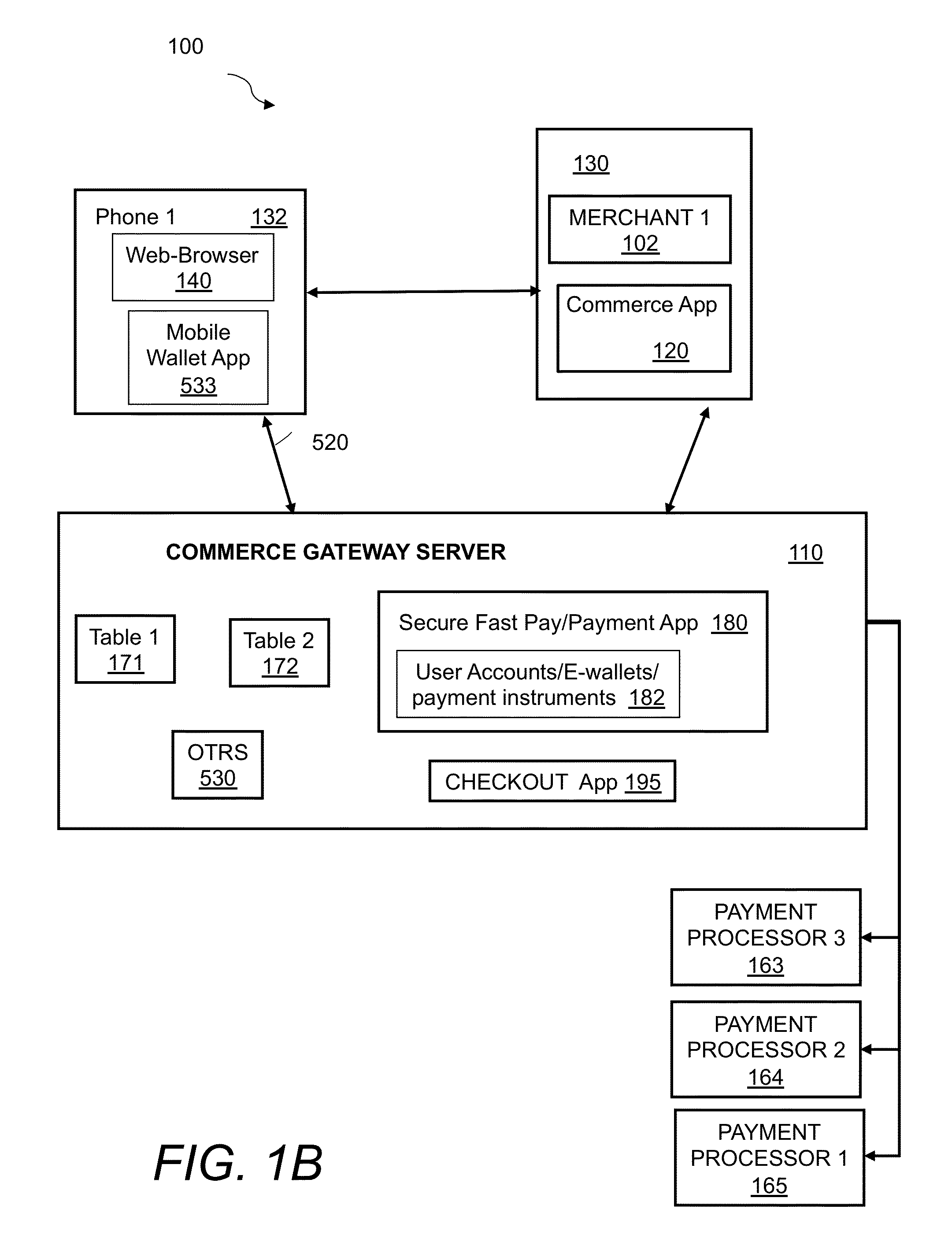
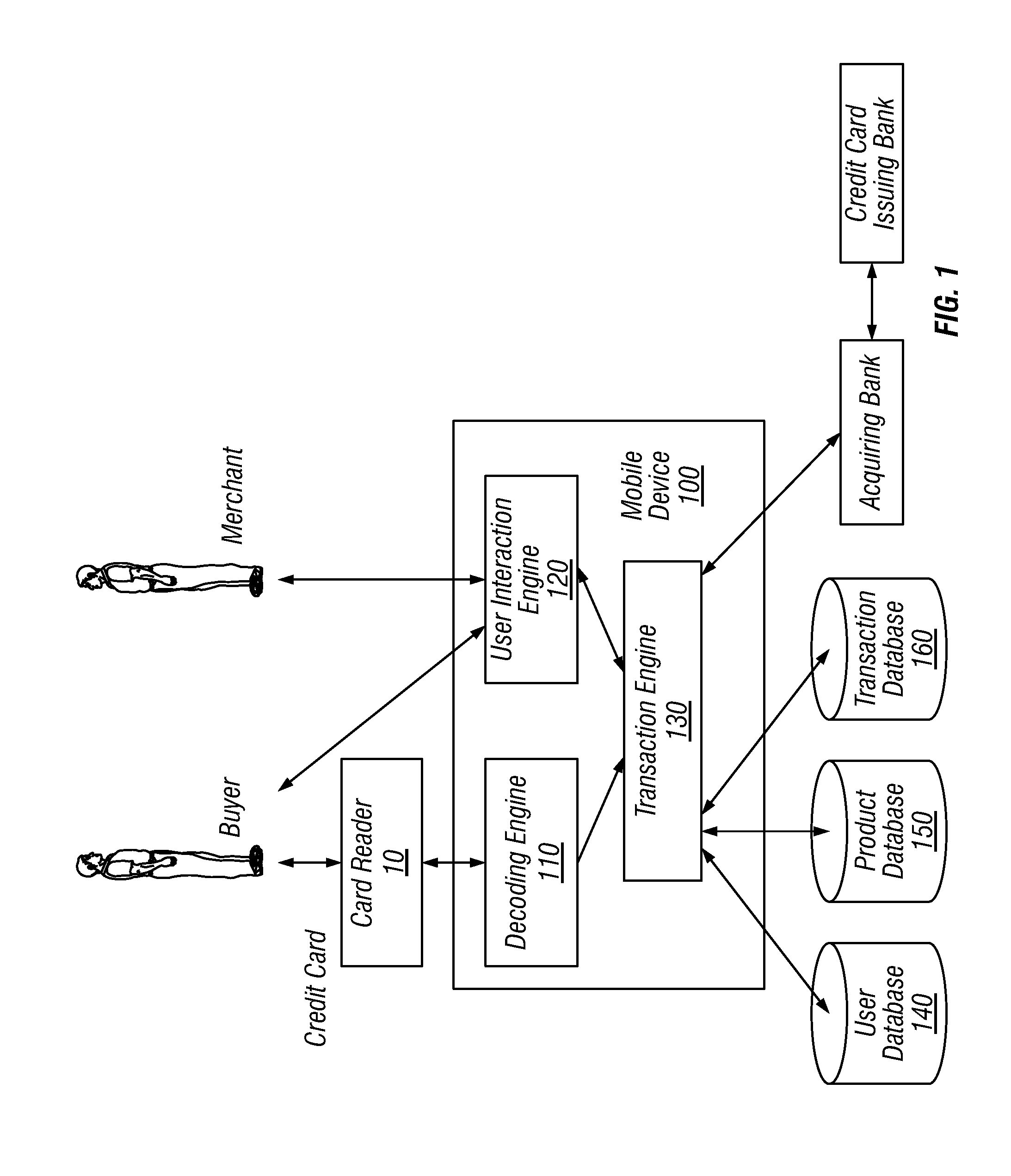
System and method for incorporating one-time tokens, coupons, and reward systems into merchant point of sale checkout systems
ActiveUS20130054336A1Convenient checkout experienceMore dataHand manipulated computer devicesDiscounts/incentivesPaymentReward system
A method for incorporating one-time-tokens, coupon and reward systems in conjunction with merchants' POS checkout systems in the physical or virtual environments includes providing a consumer computing device comprising an electronic wallet application, providing a One-time Token Redemption System(OTRS) and user electronic wallet accounts, logging into a user electronic wallet account through the electronic wallet application, sending a request for a one-time token valid for a specified time interval and then forwarding the request for the one-time token to the OTRS and upon approval sending the requested one-time token from the OTRS to the electronic wallet application. Next, presenting and entering the one-time token into a merchant point of sale checkout system within the specified time interval via the consumer computing device, sending the entered one-time token to a checkout application, and then processing payment via a secure payment application.
Owner:INGENICO INC
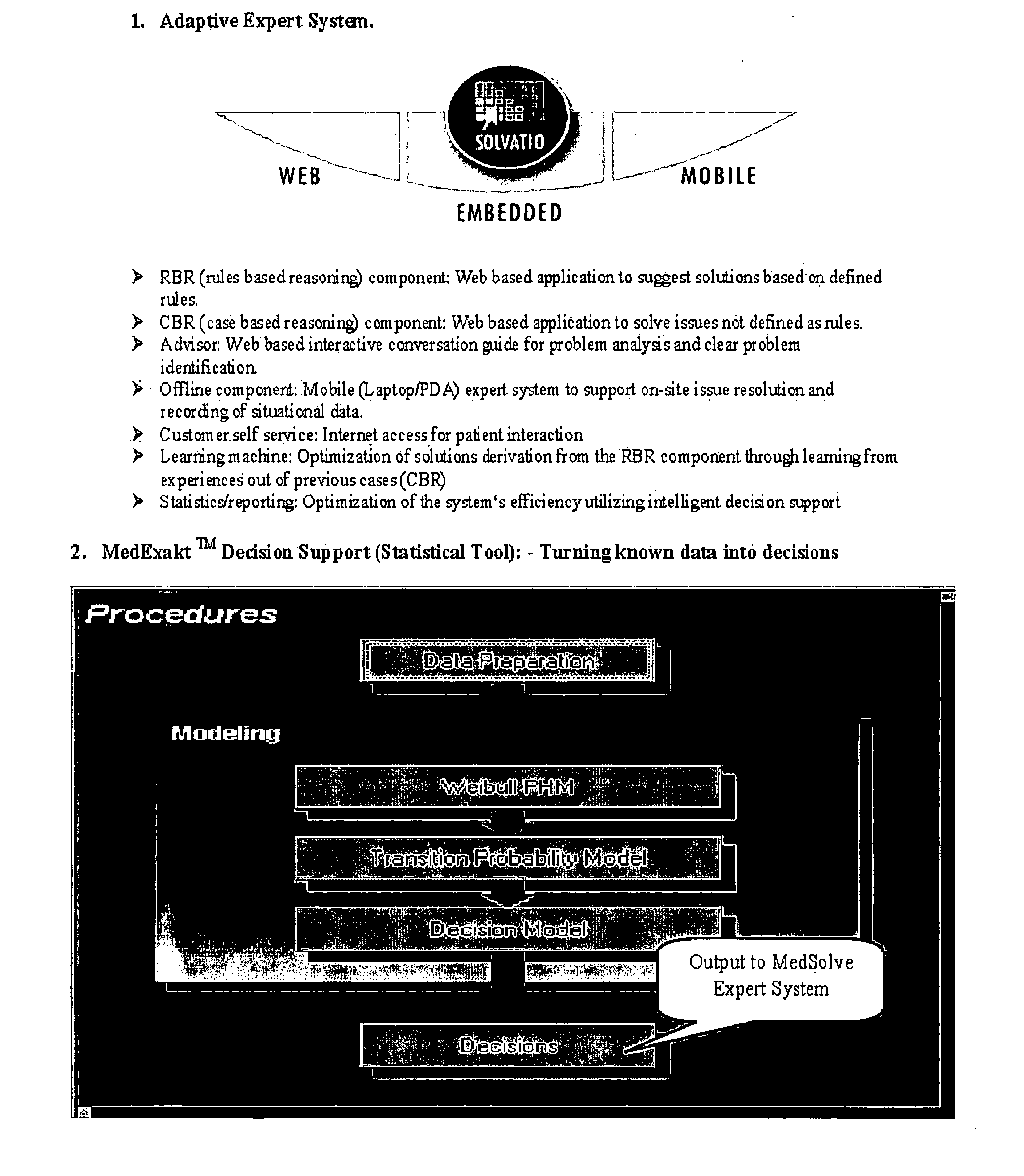
Portable medical information system
InactiveUS20060173712A1Negates needGenerate revenueMedical data miningMedical automated diagnosisComputerized systemSmart card
A computerized system for monitoring and maintaining the health of a person comprising the steps of (a) obtaining parameter data from the patient and inputting the parameter data into a computer database; (b) analyzing the parameter data using a computerized statistical modeling technique module and a computerized adaptive expert system shell for the prediction of a health event in the lifetime of the patient; (c) using the analyzed data to developed a health maintenance schedule for the patient, and (d) embedding and / or linking such data onto a microprocessor powered smart card.
Owner:JOUBERT DIRK
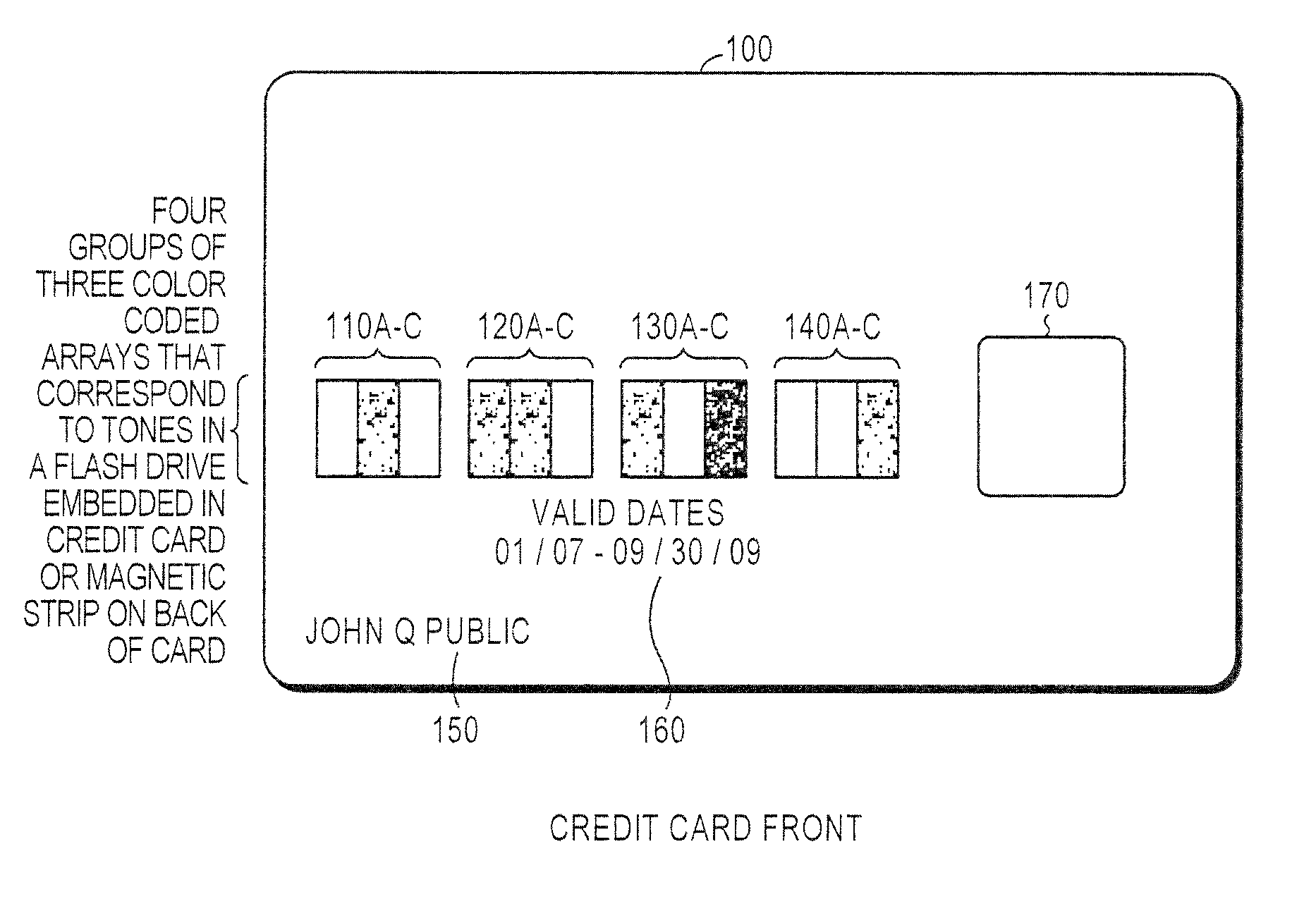
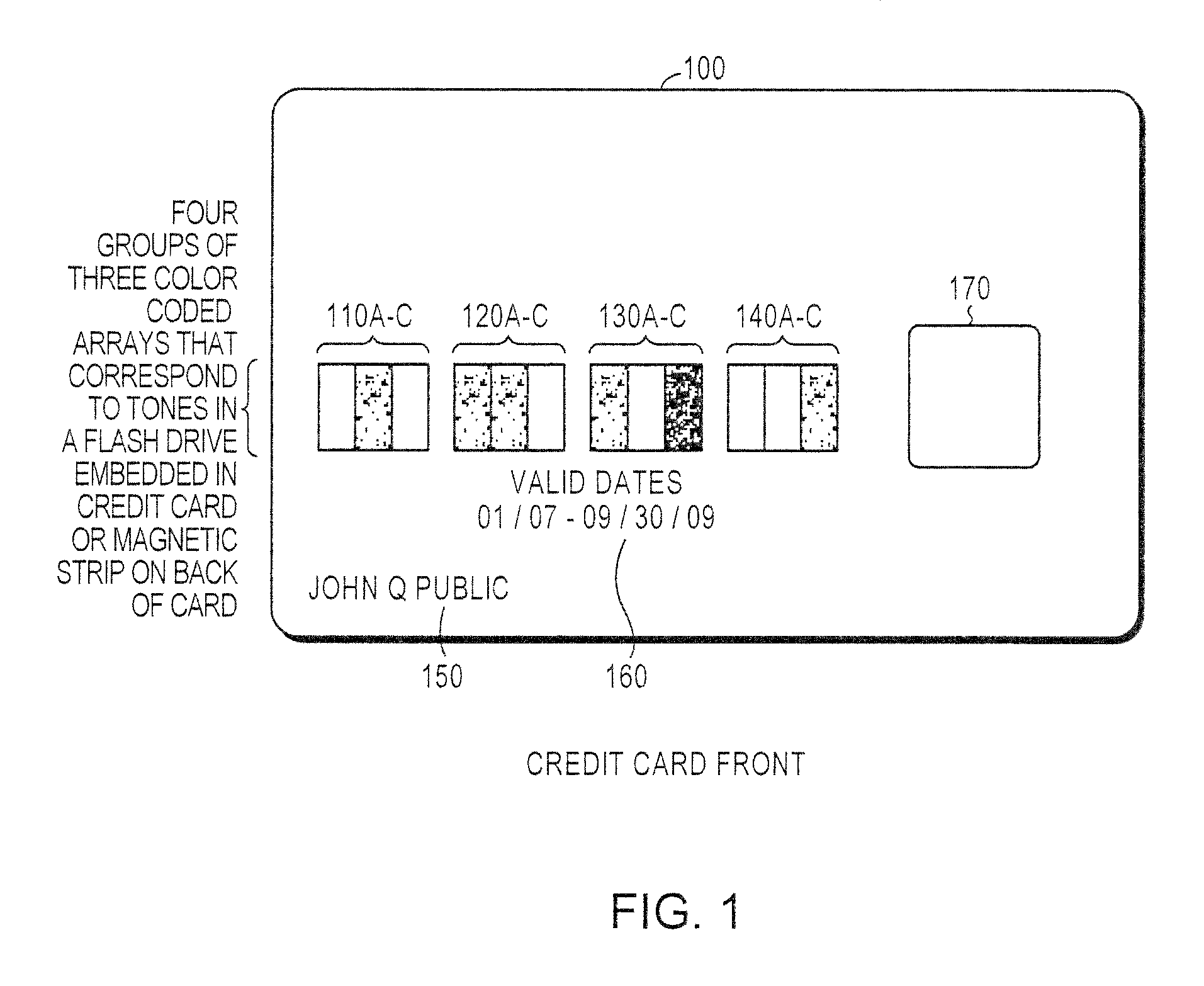
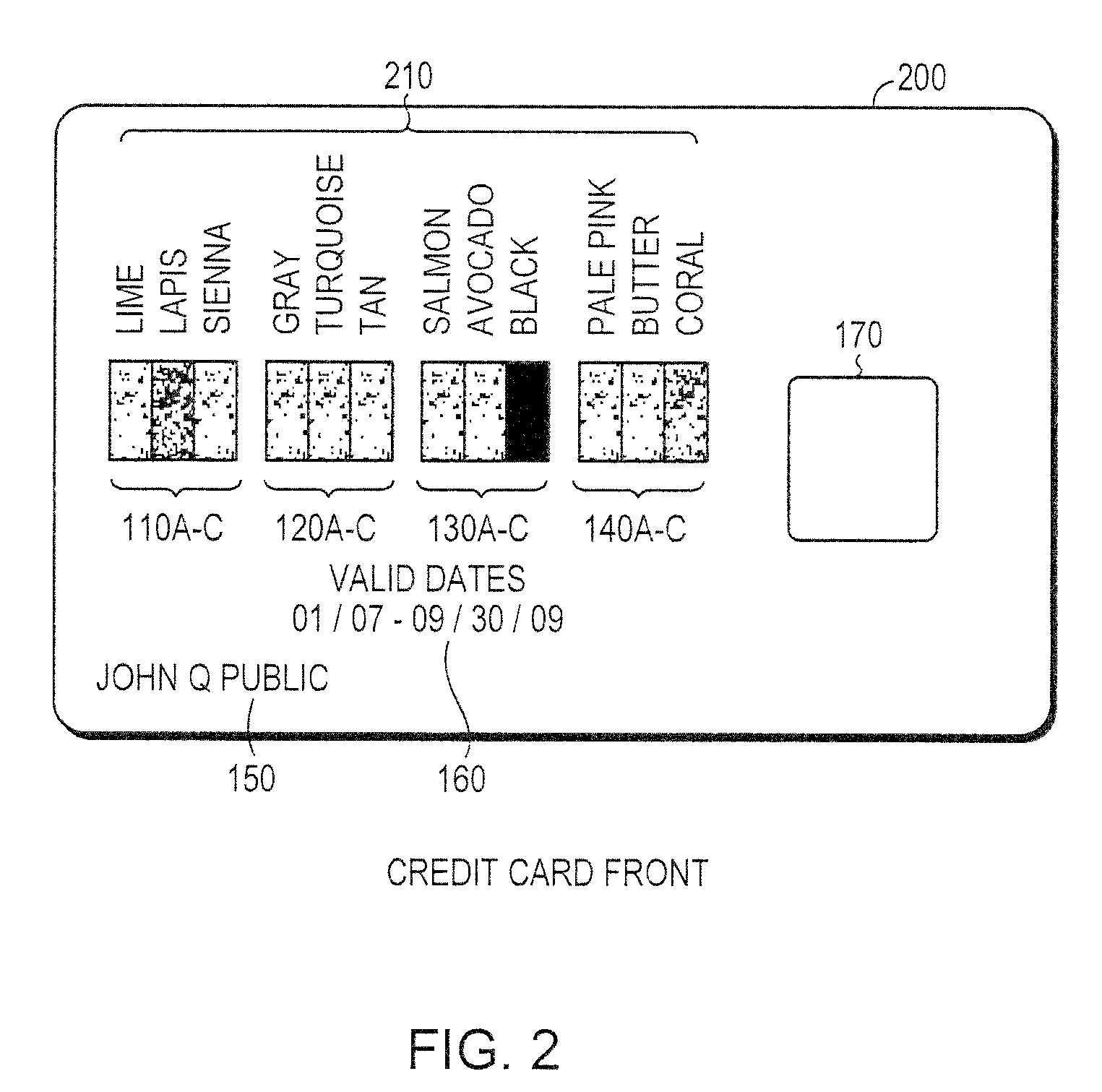
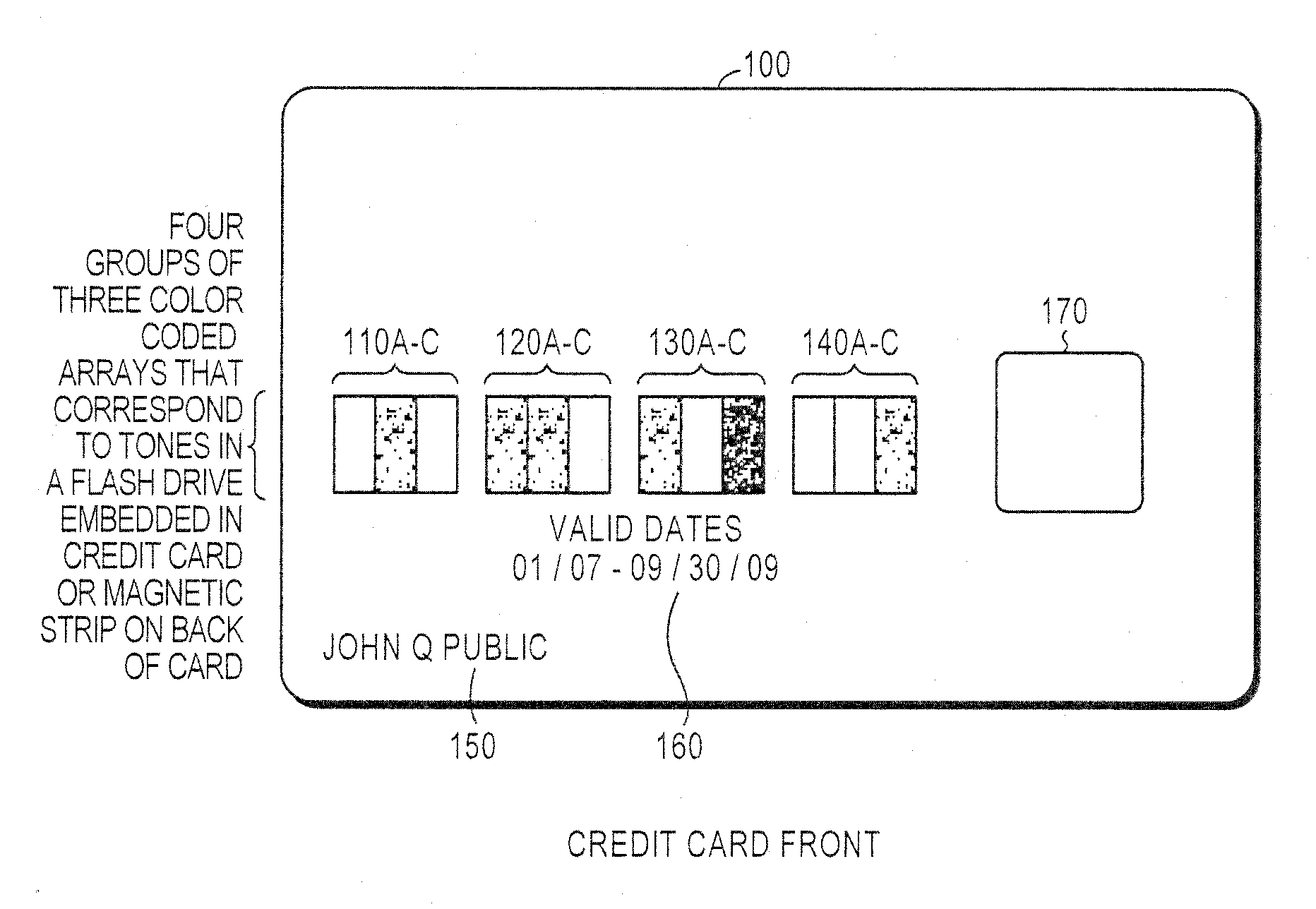
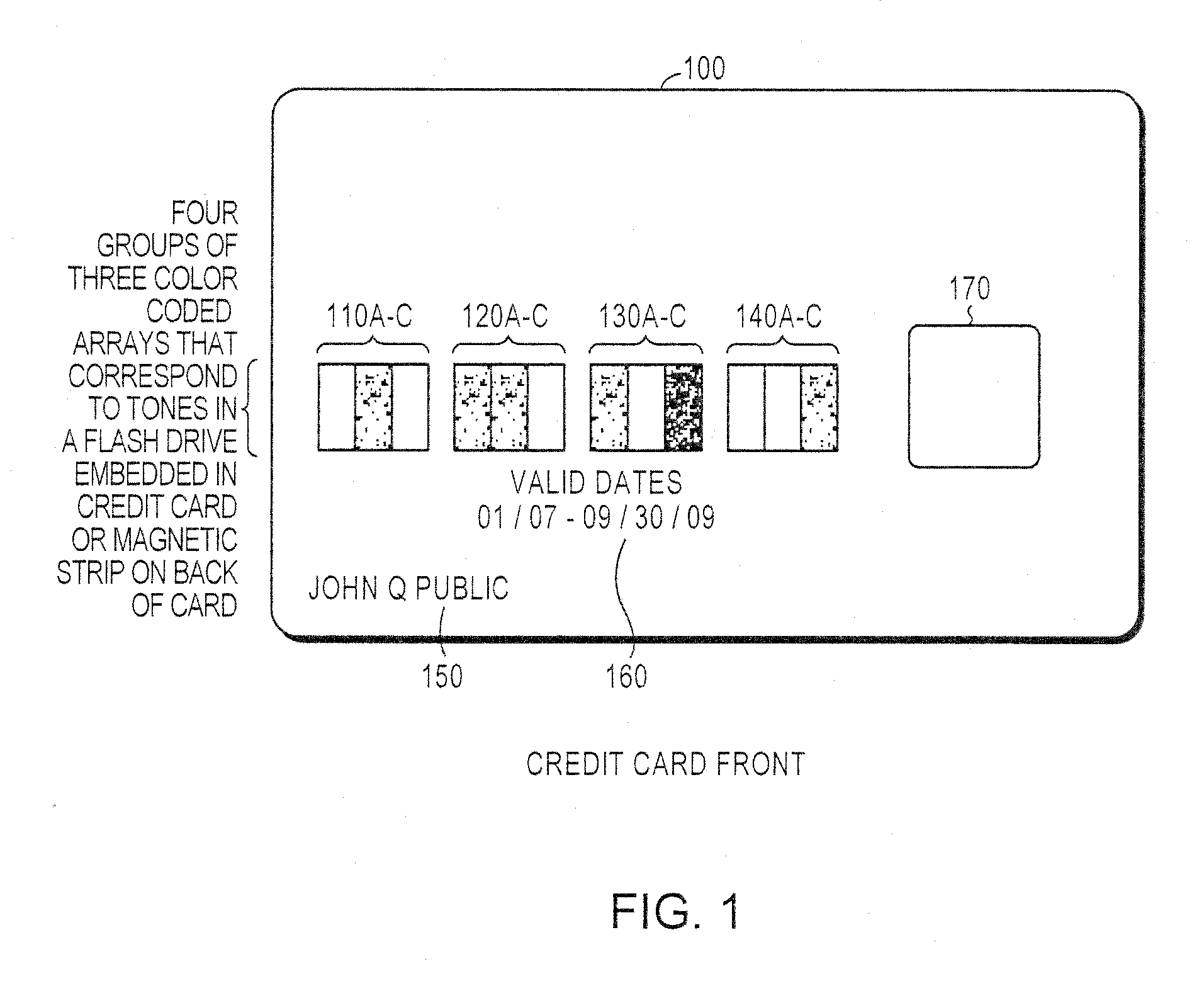
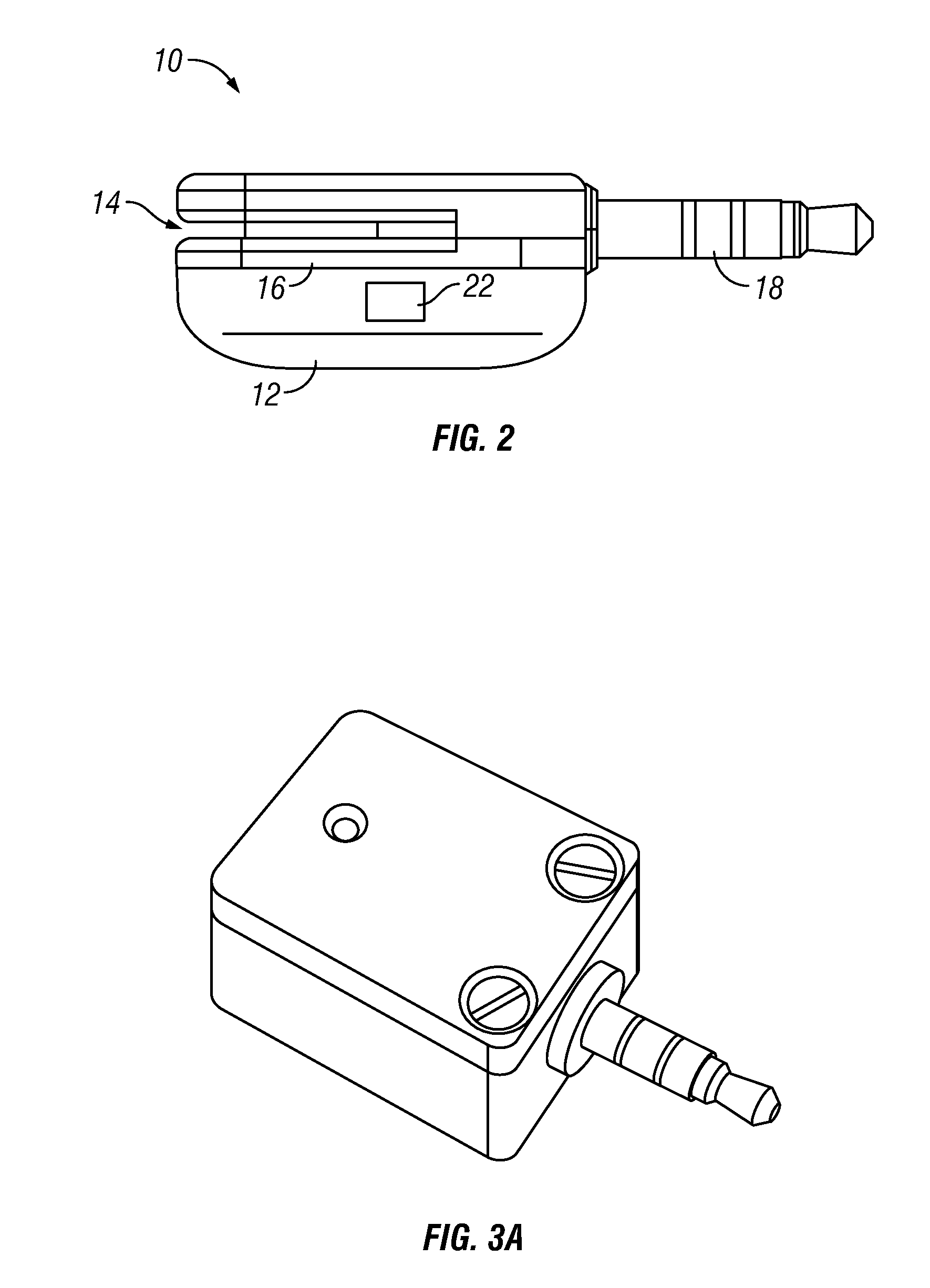
Secured transaction using color coded account identifiers
InactiveUS7896238B2Reduce fraudReduce piracyComplete banking machinesFinanceSecured transactionDatabase
A method and system provides coded access to a transactional or other type of system by acquiring account identification data corresponding to a combination of a plurality of colors. The account identification data is transmitted to, for example, a remote server to correlate the account identification data against an account database to evaluate corresponding account information. Based on the account information, access to the transactional or other type of system may be controlled.
Owner:XYLON LLC
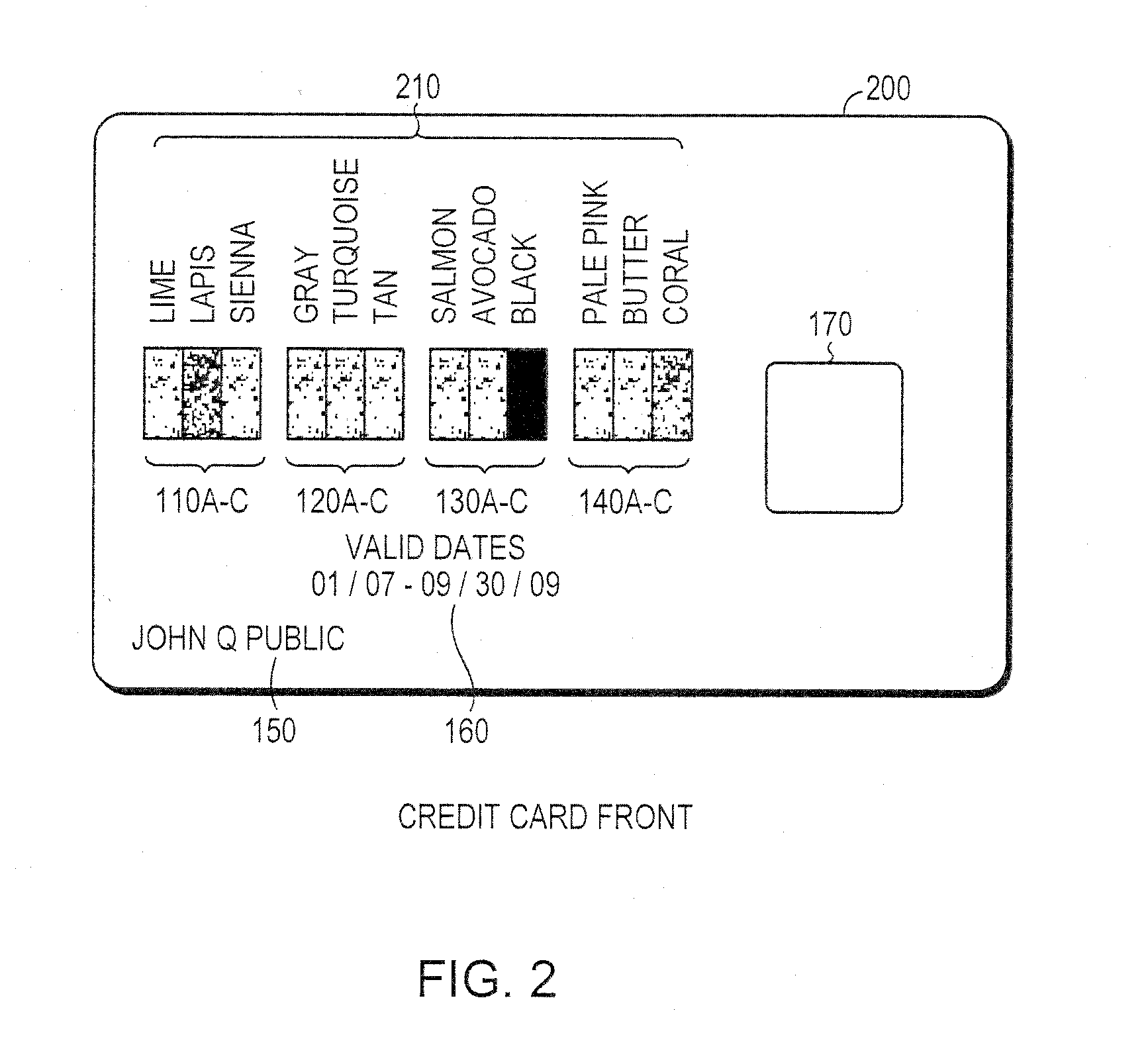
System and method for controlling secured transaction using color coded account identifiers
InactiveUS20080245861A1Low costHigh degree of accuracyComplete banking machinesFinanceSecured transactionDatabase
A method and system provides coded access to a transactional or other type of system by acquiring account identification data corresponding to a combination of a plurality of colors. The account identification data is transmitted to, for example, a remote server to correlate the account identification data against an account database to evaluate corresponding account information. Based on the account information, access to the transactional or other type of system may be controlled.
Owner:XYLON LLC
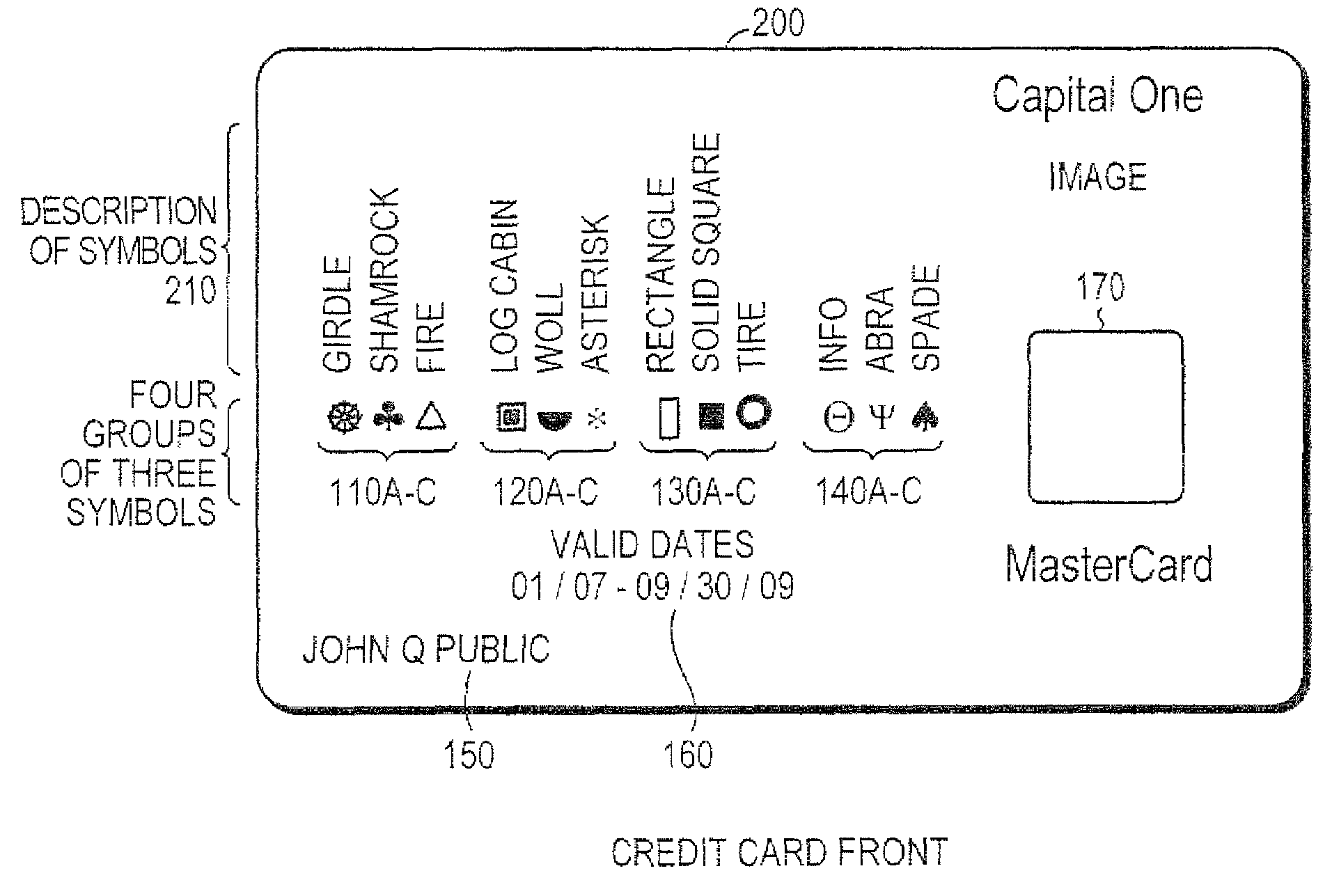
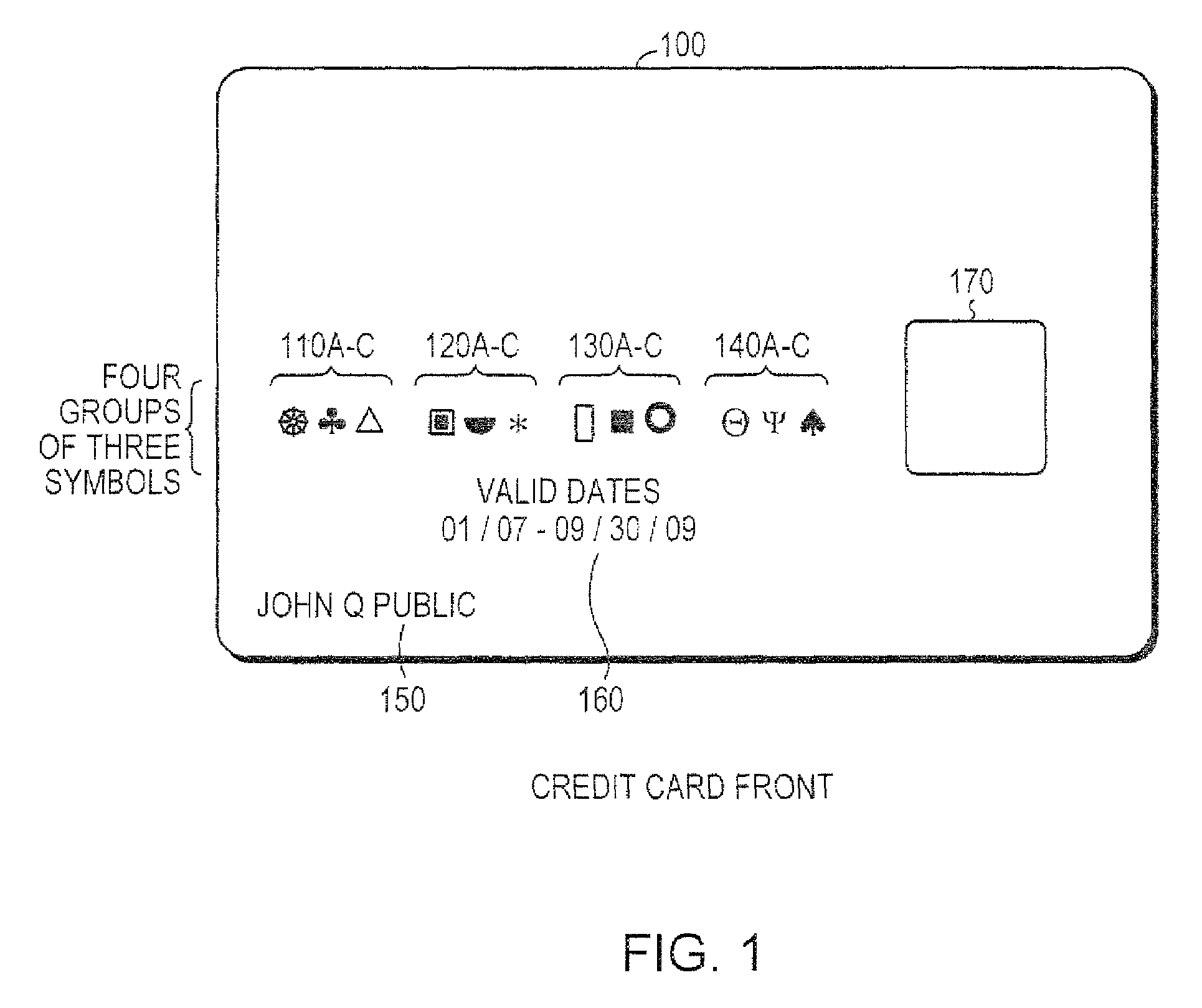
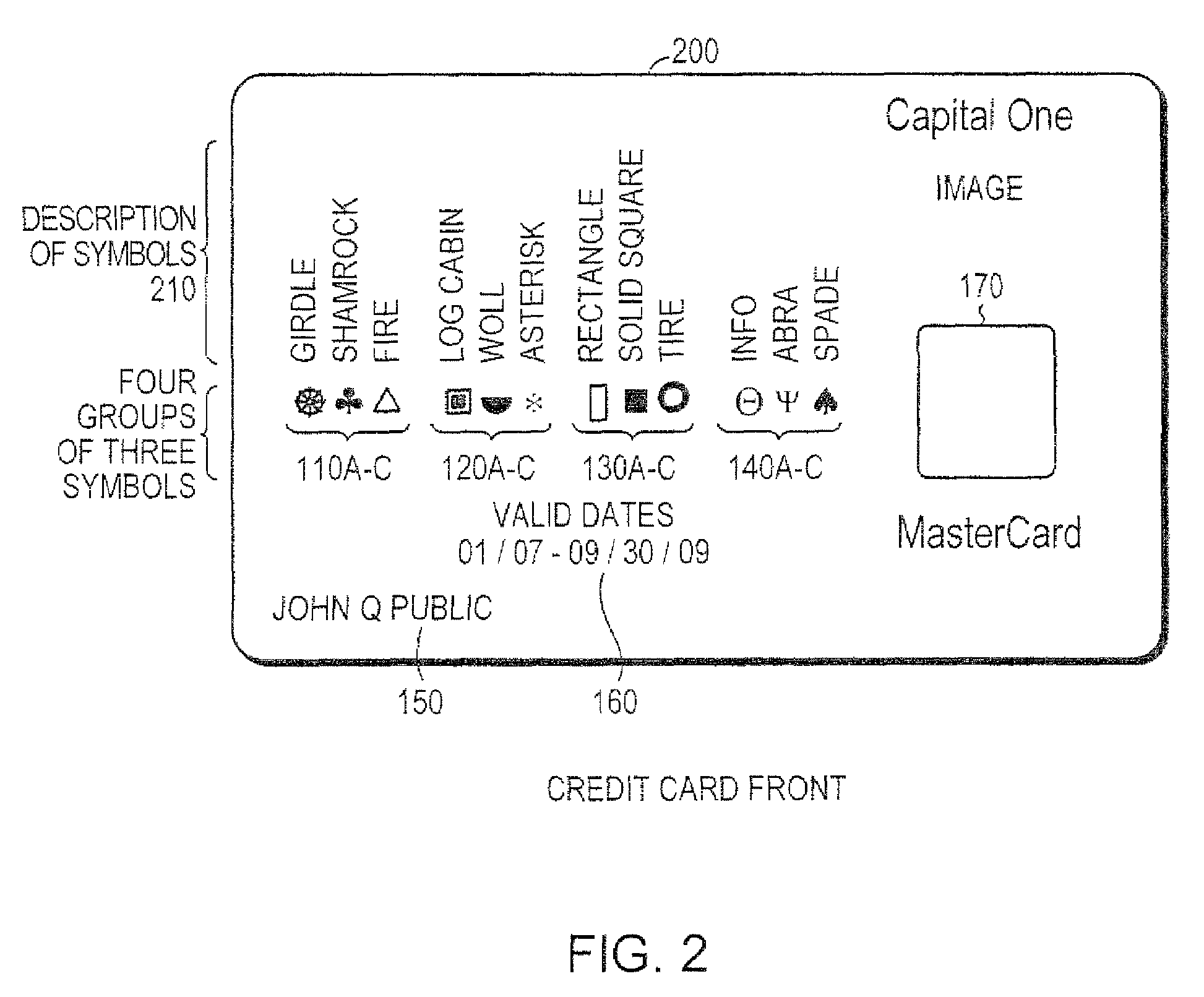
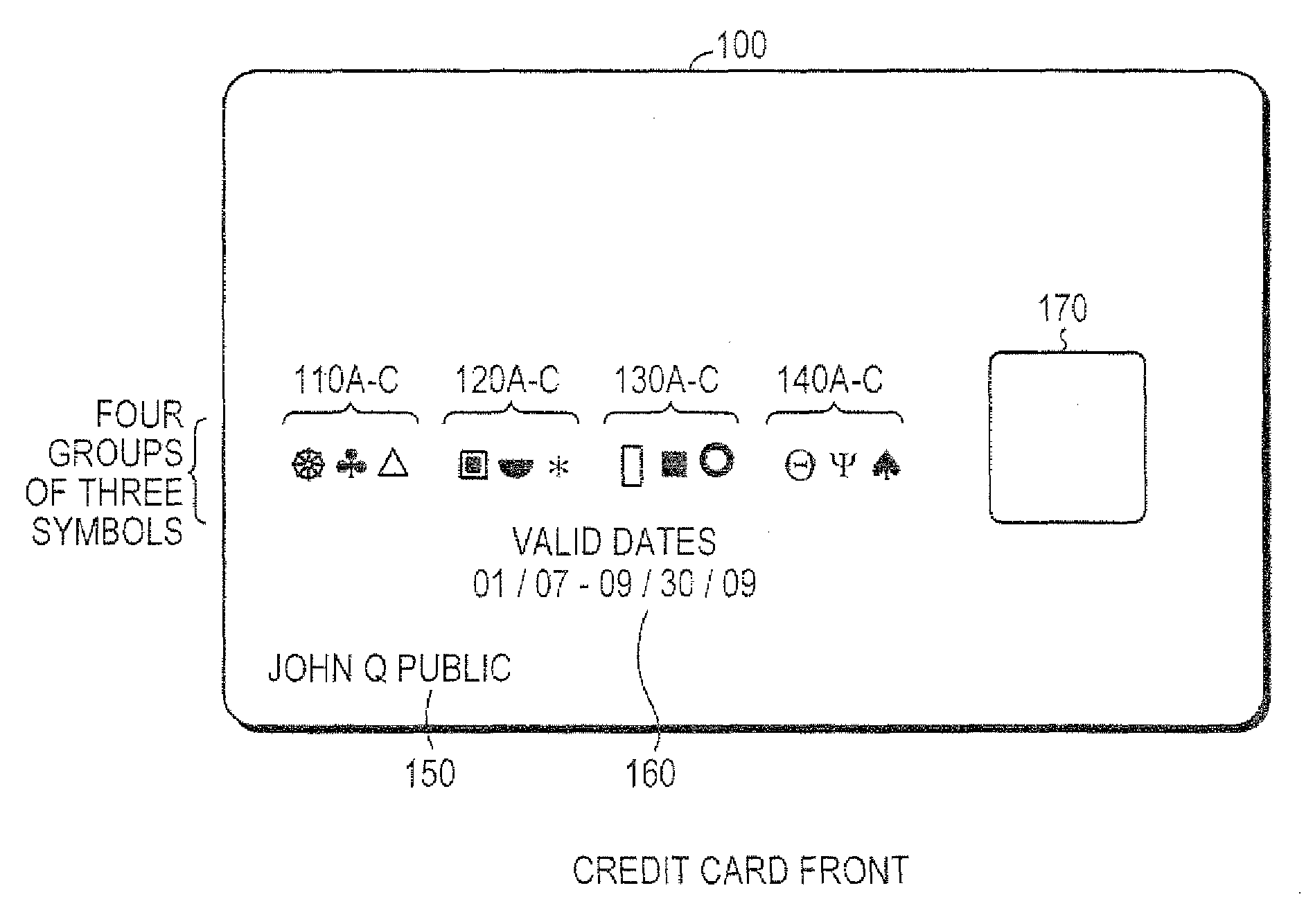
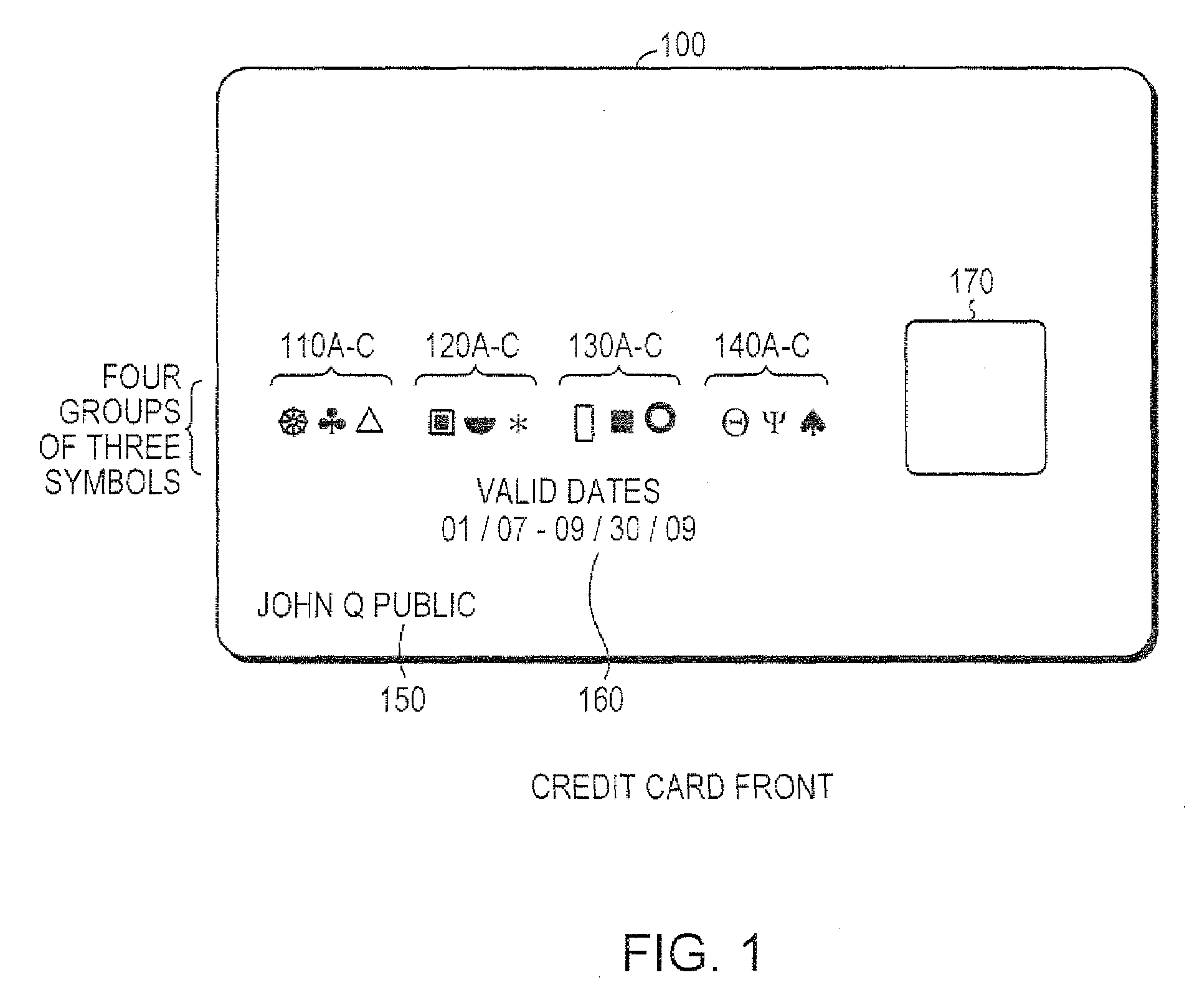
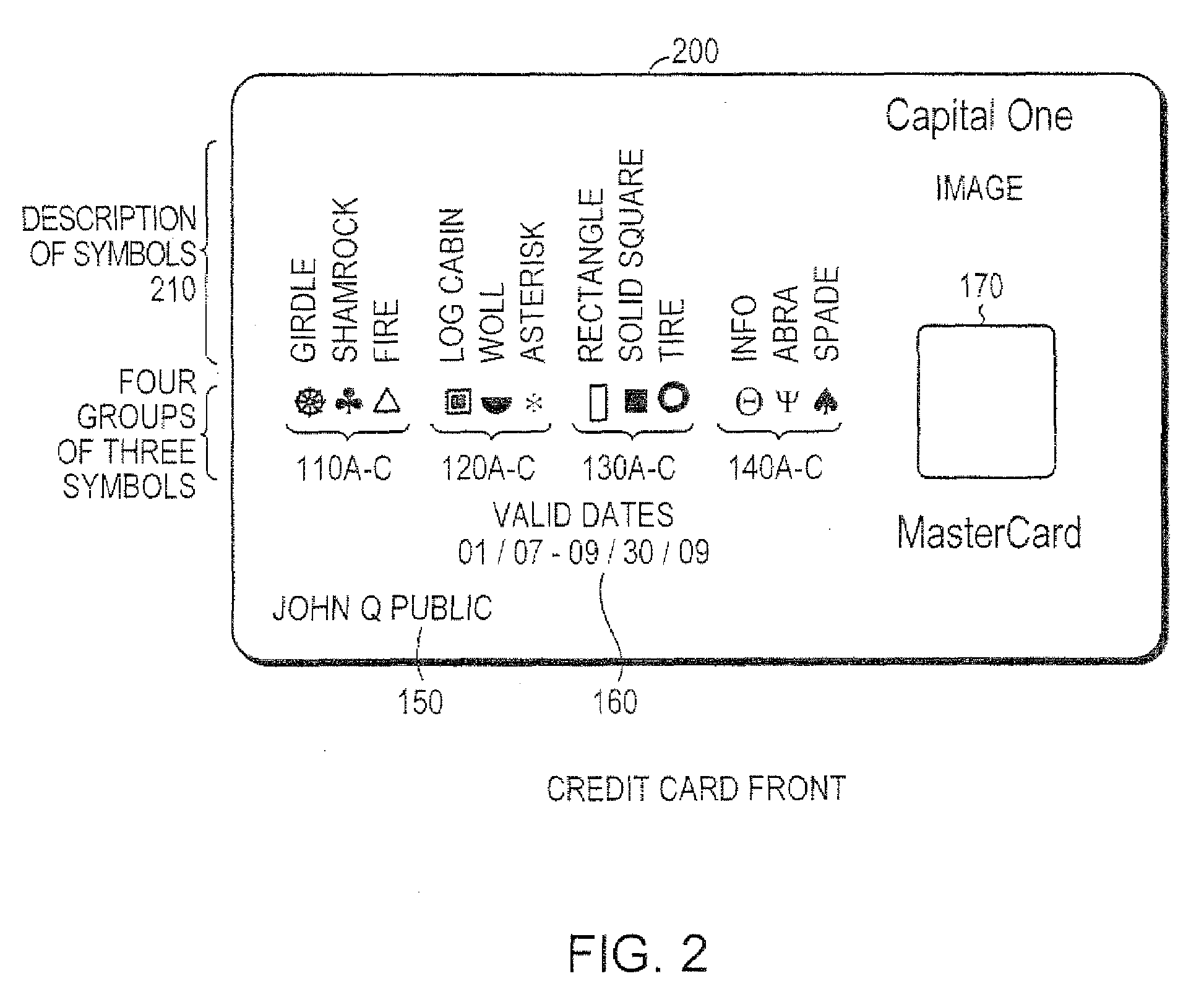
System and method for controlling secured transaction using directionally coded account identifiers
A control method and system provides coded access to a system by acquiring account identification data corresponding to a combination of a plurality of symbols. The account identification data is transmitted, for example to a remote server, to correlate the account identification data against an account database to evaluate corresponding account information. Based on the account information, access to the system may be controlled.
Owner:KIOBA PROCESSING LLC
System and method for controlling secured transaction using directionally coded account identifiers
InactiveUS20080245855A1Low costHigh degree of accuracyOther printing matterFinanceSecured transactionDatabase
A control method and system provides coded access to a system by acquiring account identification data corresponding to a combination of a plurality of symbols. The account identification data is transmitted, for example to a remote server, to correlate the account identification data against an account database to evaluate corresponding account information. Based on the account information, access to the system may be controlled.
Owner:KIOBA PROCESSING LLC
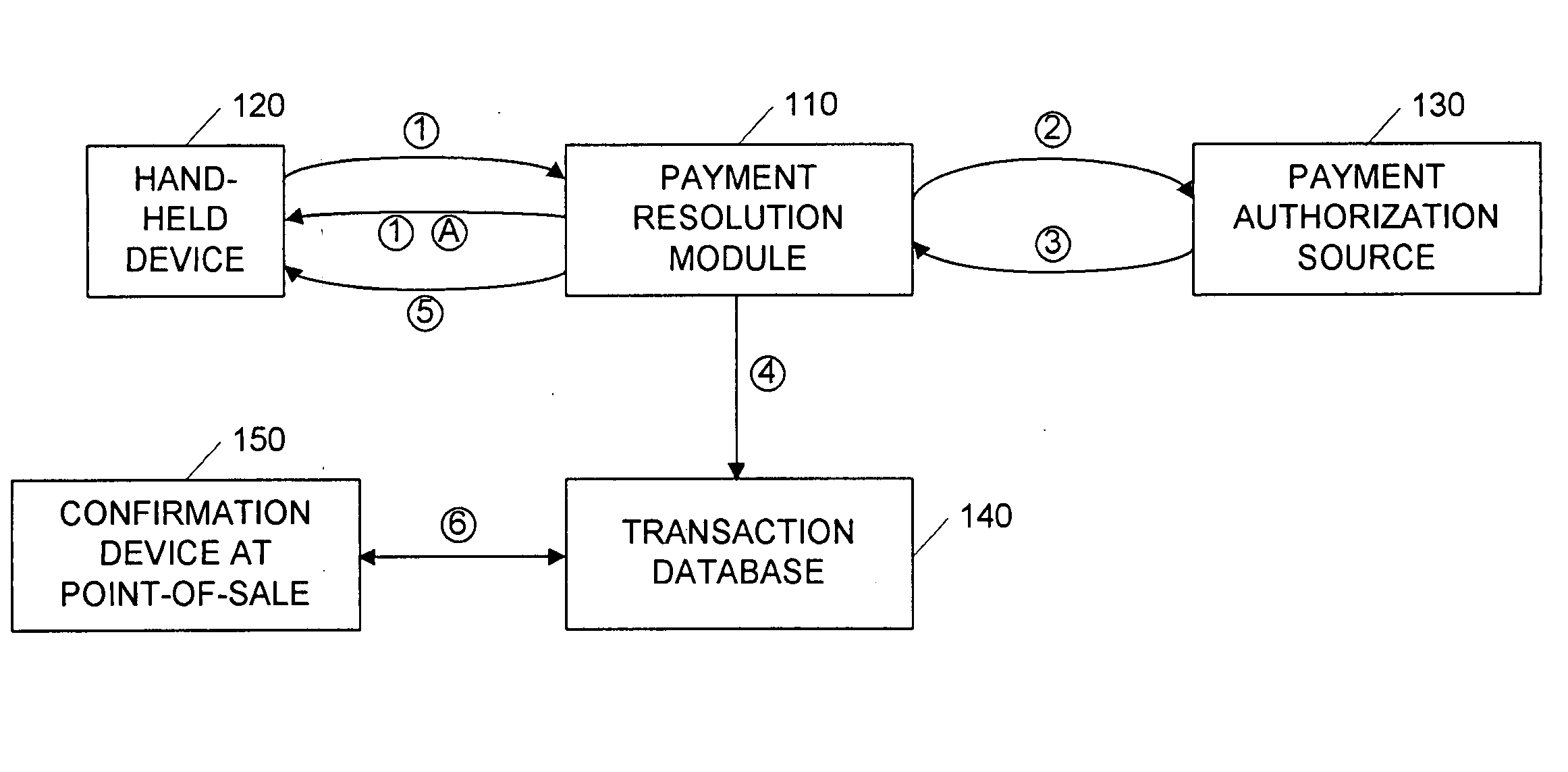
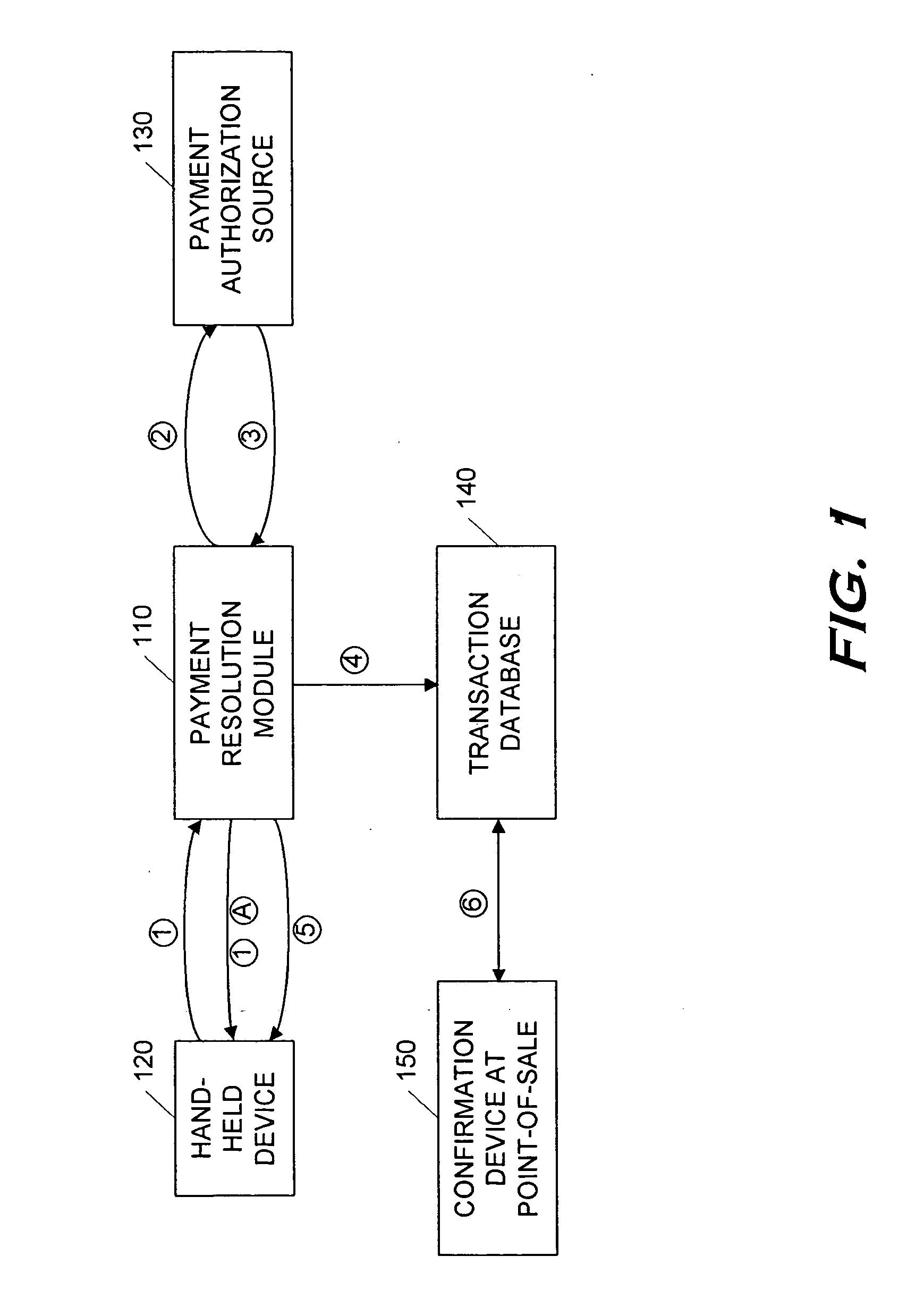
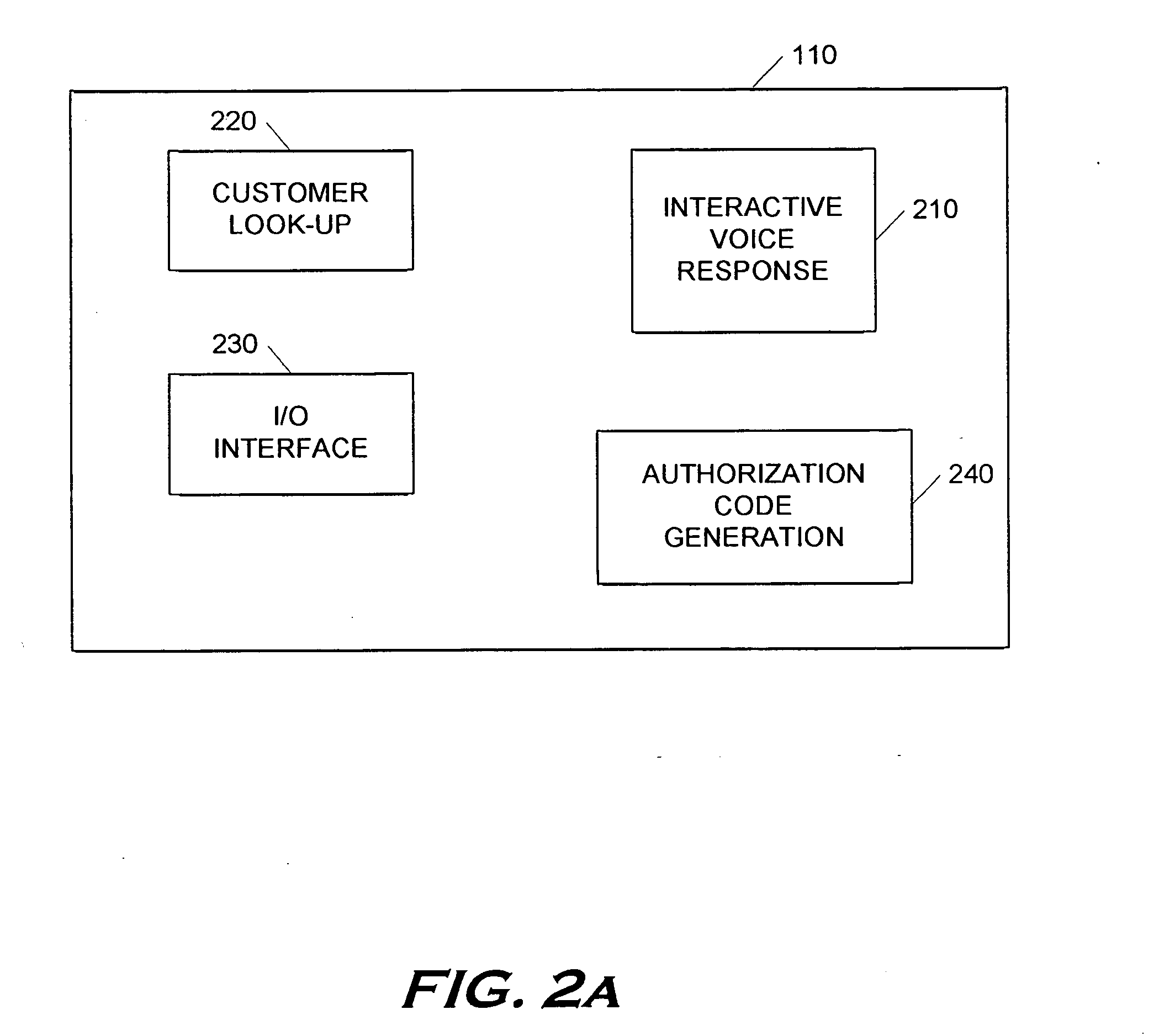
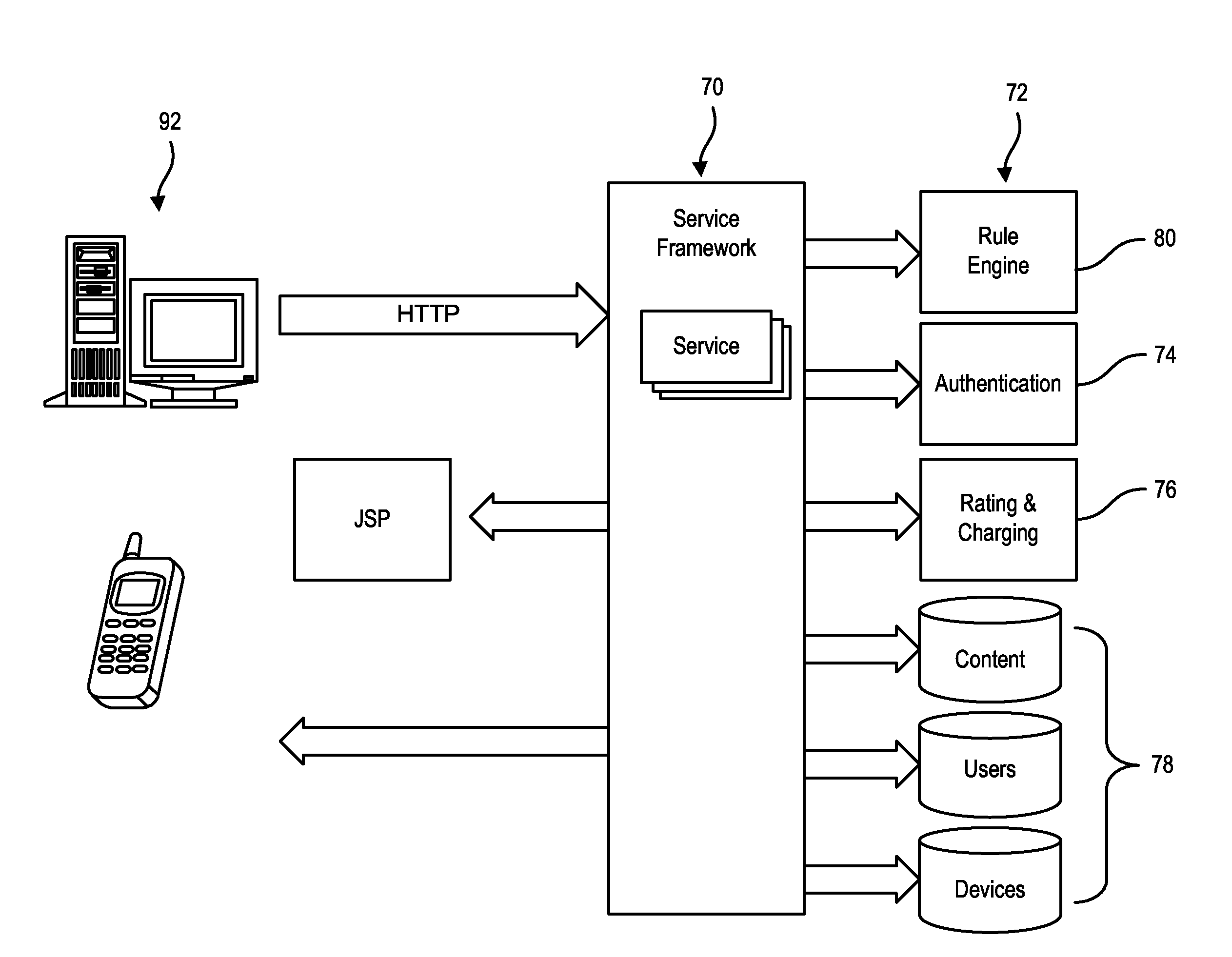
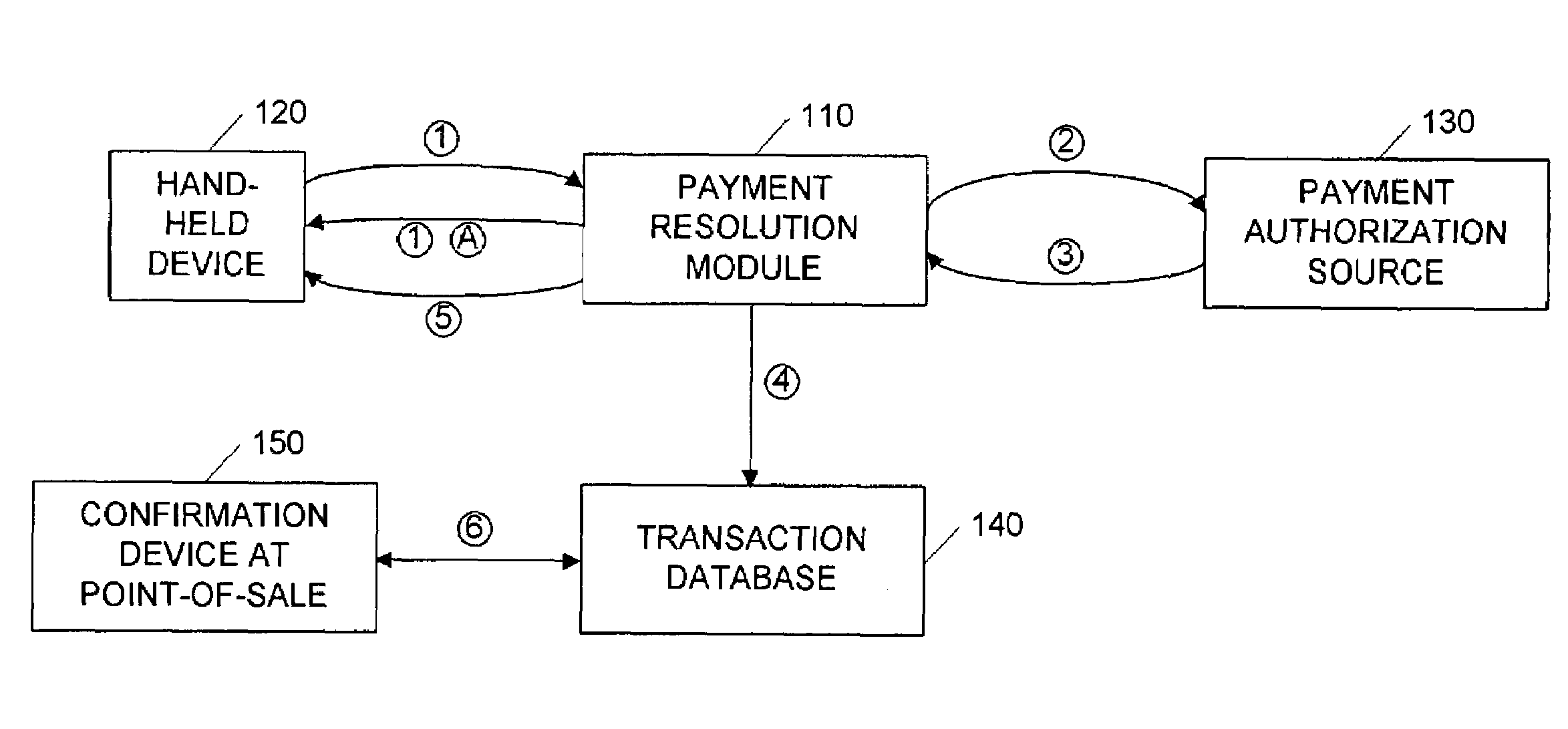
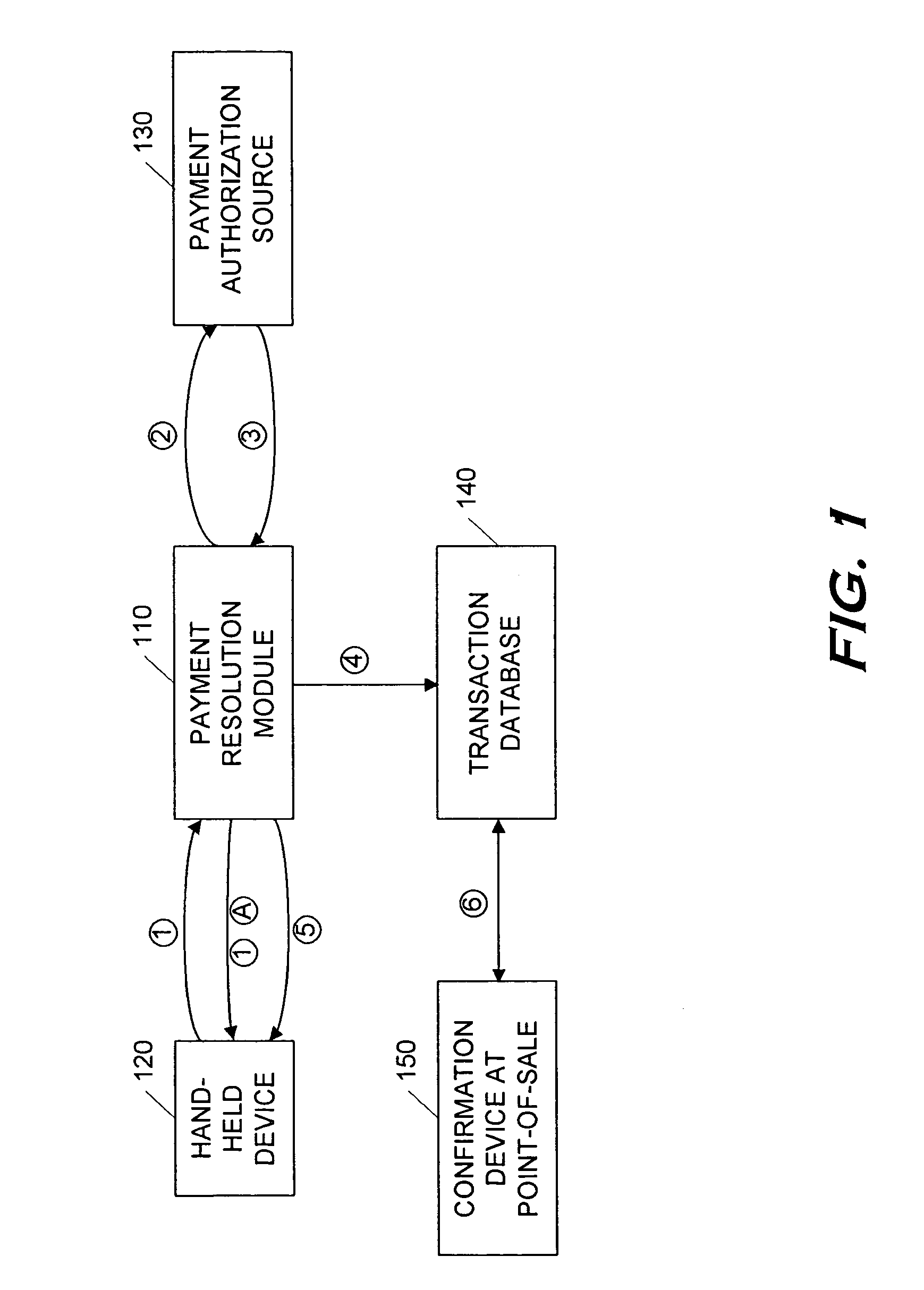
Point-of-sale billing via hand-held devices
InactiveUS20050109838A1Reduce fraudComplete banking machinesFinancePaymentPersonal identification number
A payment resolution module is configured to communicate with hand-held devices (such as mobile phones, PDA's, or computers) to allow purchase of products using the hand-held devices, without requiring the user of the hand-held device to enter payment information for each transaction. The user of the hand-held device may be identified as the owner of the device either by having the option to enter a personal identification code, or by using a biometric to identify himself, for example. Accordingly, only an authorized user of the hand-held device may use the hand-held device to purchase products. After the payment resolution module receives authorization for payment, an authorization code is transmitted to the mobile device. The user may be required to present the authorization code at the point of sale, such as by entering the code into a computing device at the point-of-sale, prior to completion of the transaction.
Owner:XILIDEV
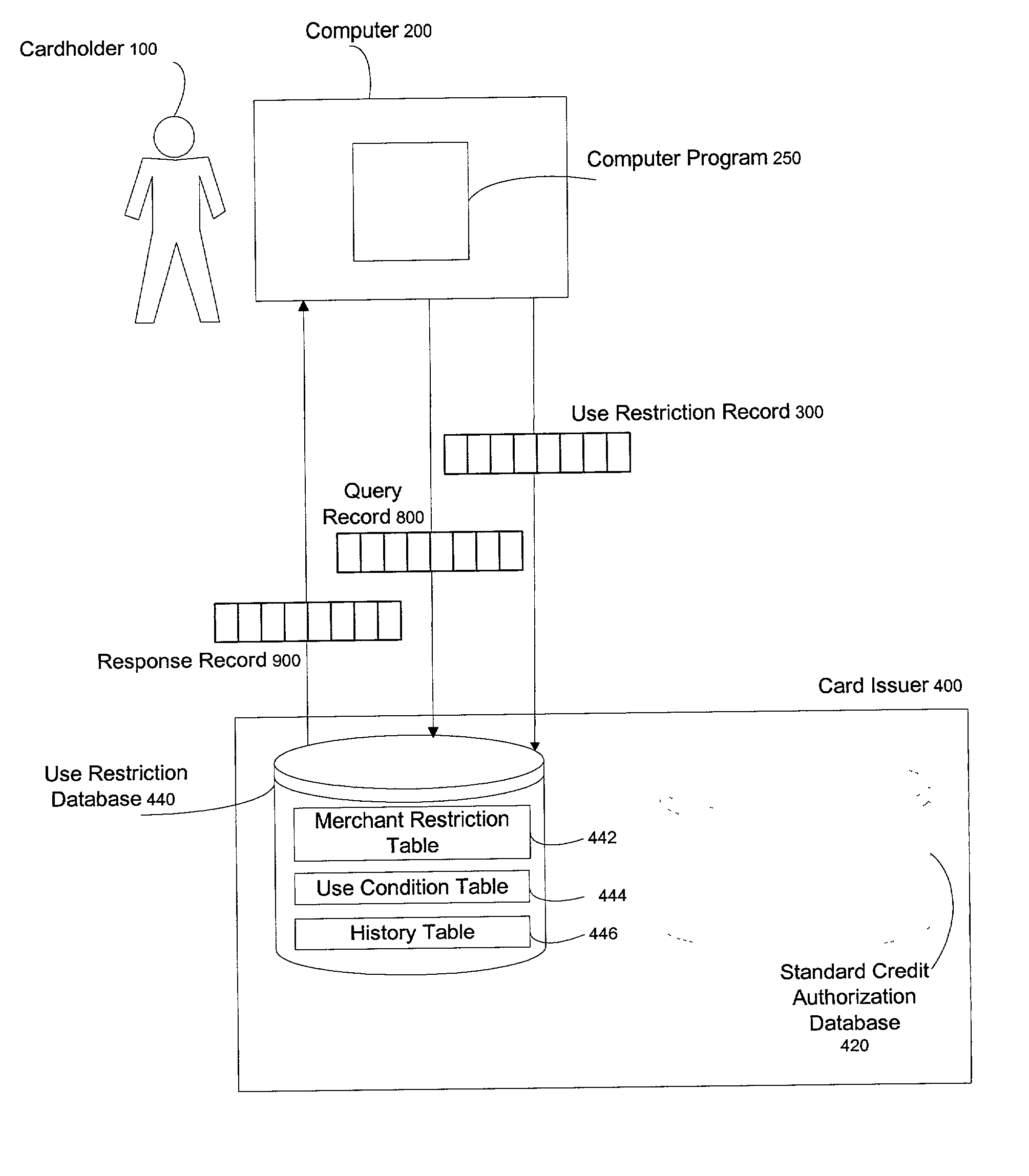
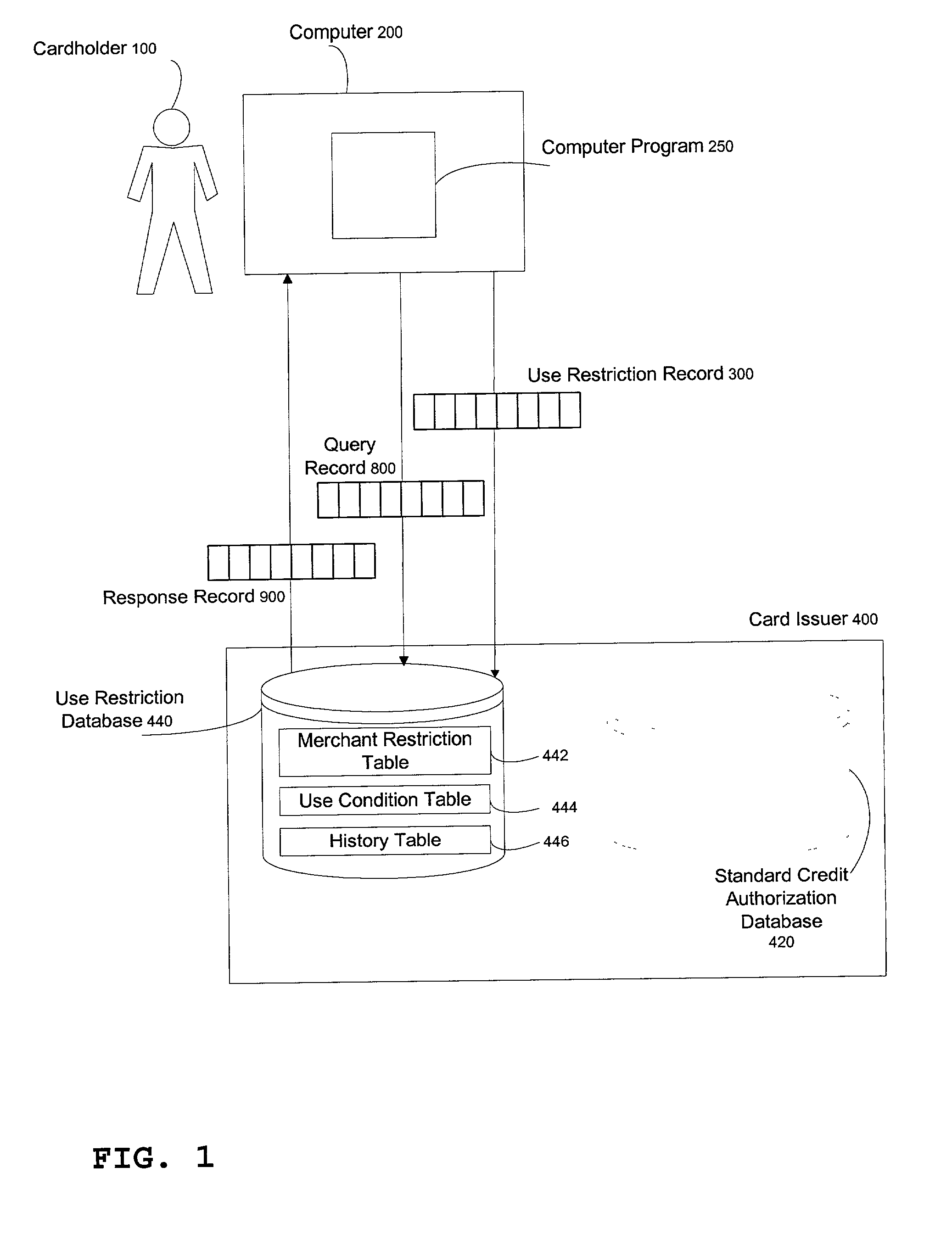
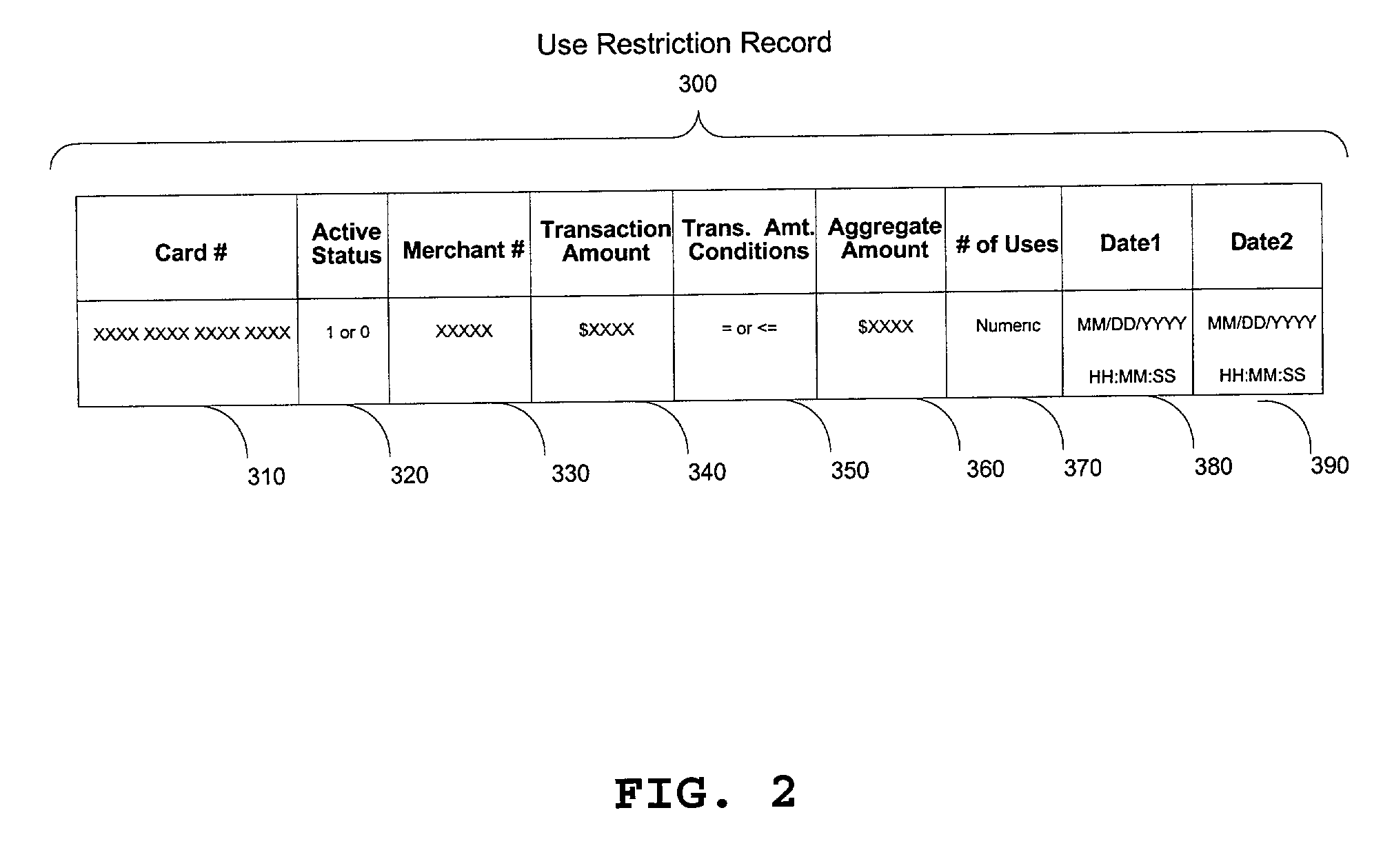
Method for cardholder to place use restrictions on credit card at will
InactiveUS20020169720A1Opportunities decreaseConfidenceFinanceSpecial data processing applicationsCredit cardWeb application
A method for cardholders to communicate restrictions on card usability in terms of time, amount, number of charges, and merchants to card issuers though dedicated applications on wireless PDA, cell phone, desktop applications, or Web applications, repeatedly and at will, and for card issuers to evaluate future transactions in terms of these restrictions and authorize or decline those transactions based on the results of those evaluations.
Owner:WILSON PHILLIP C +1
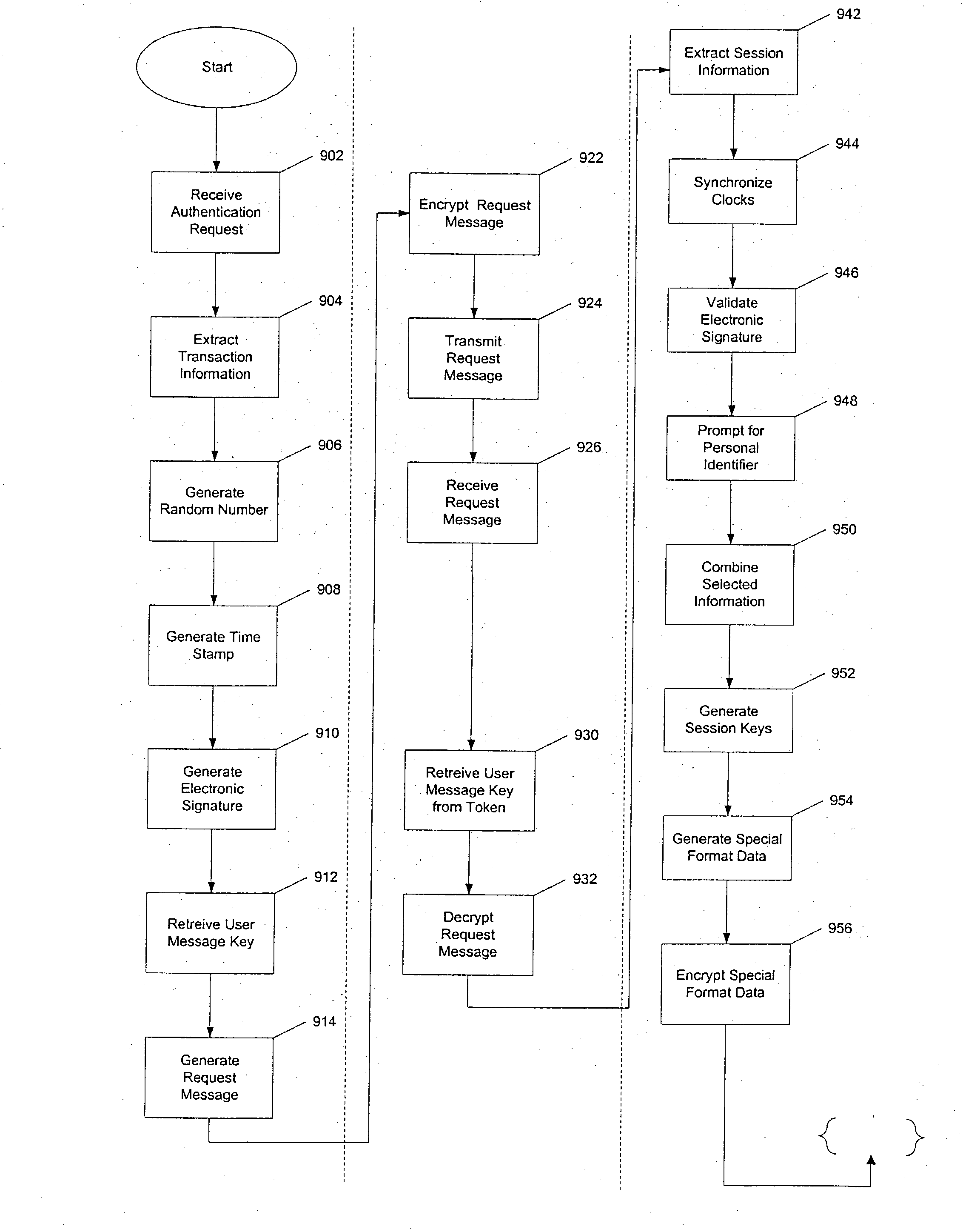
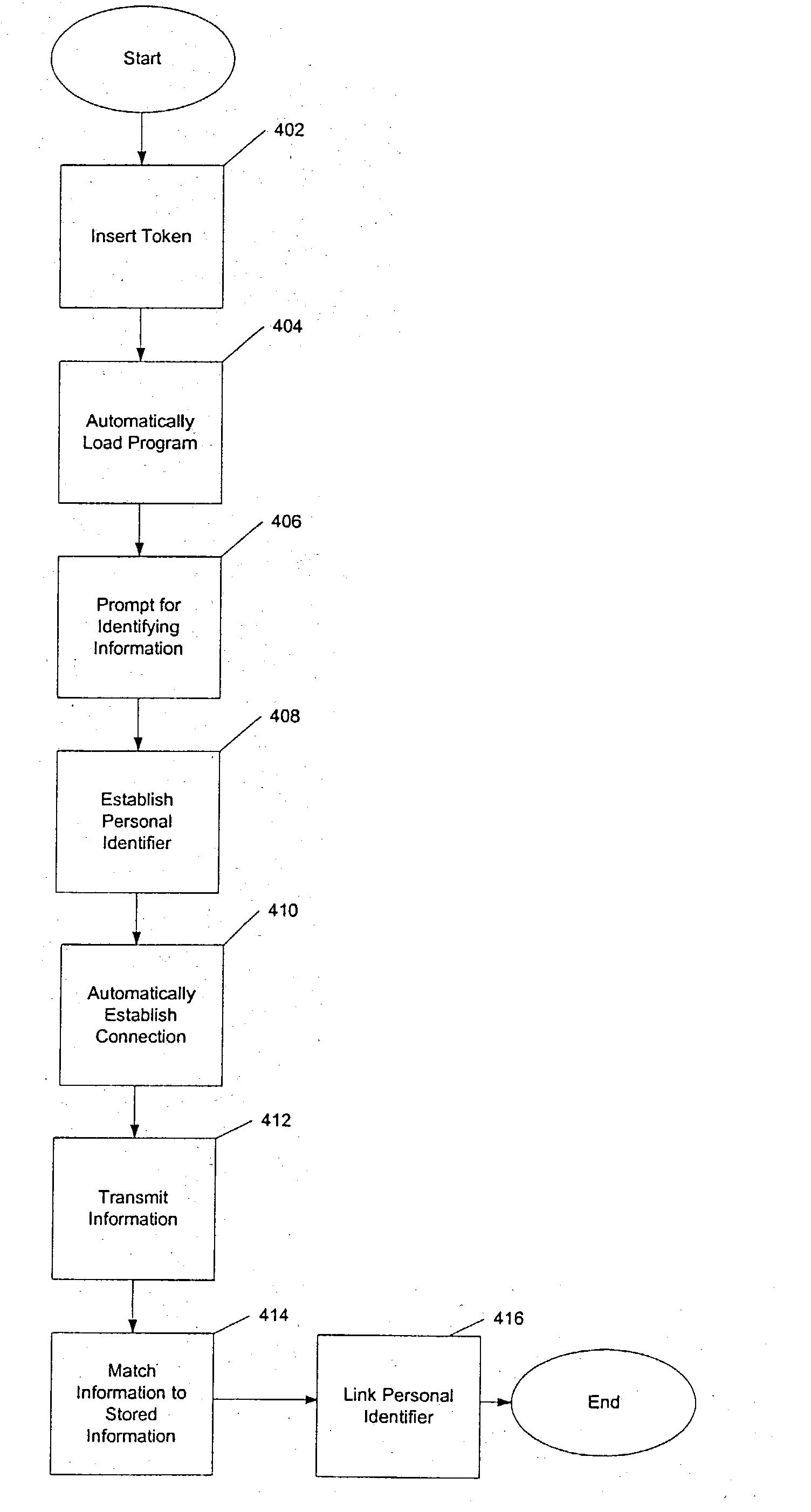
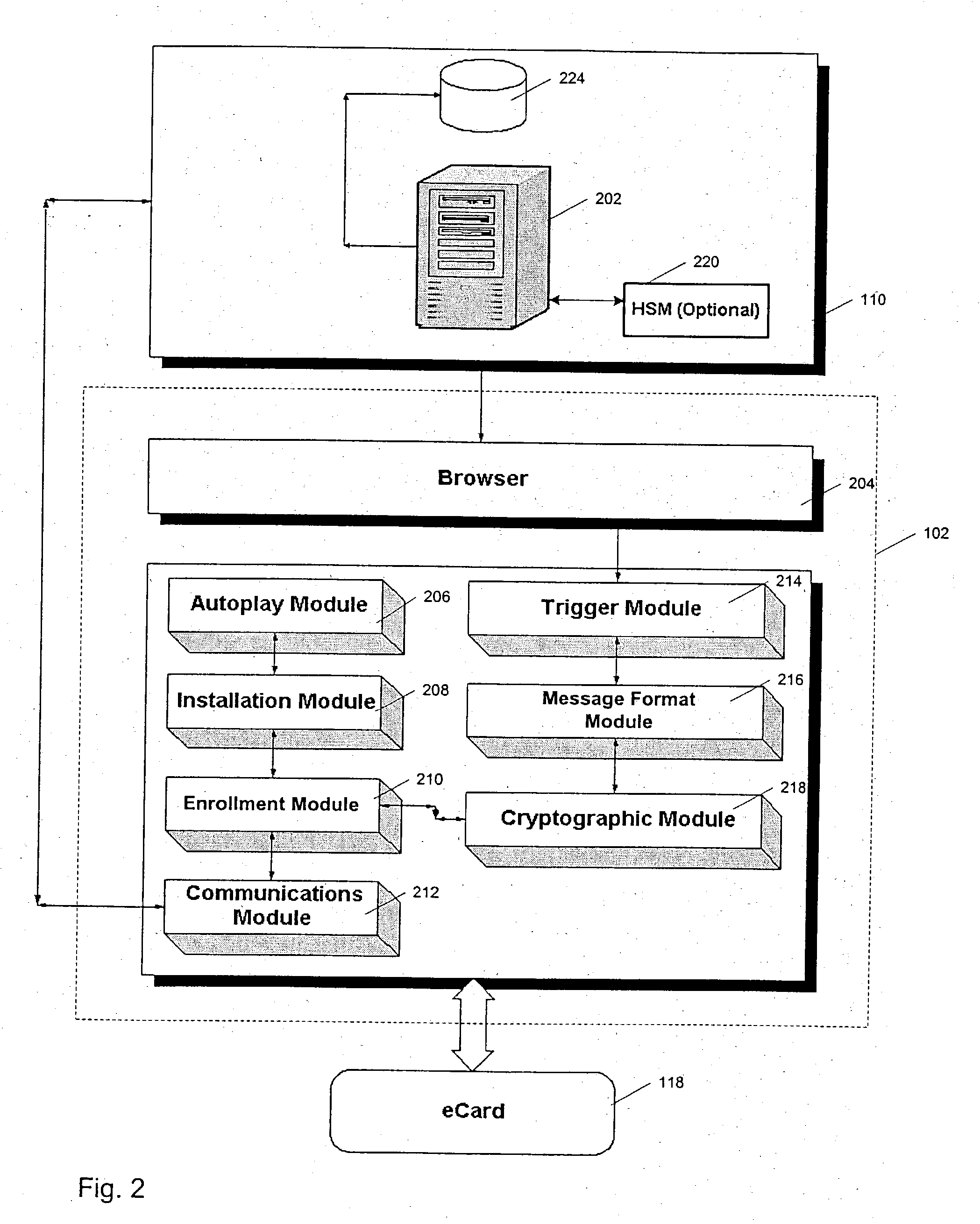
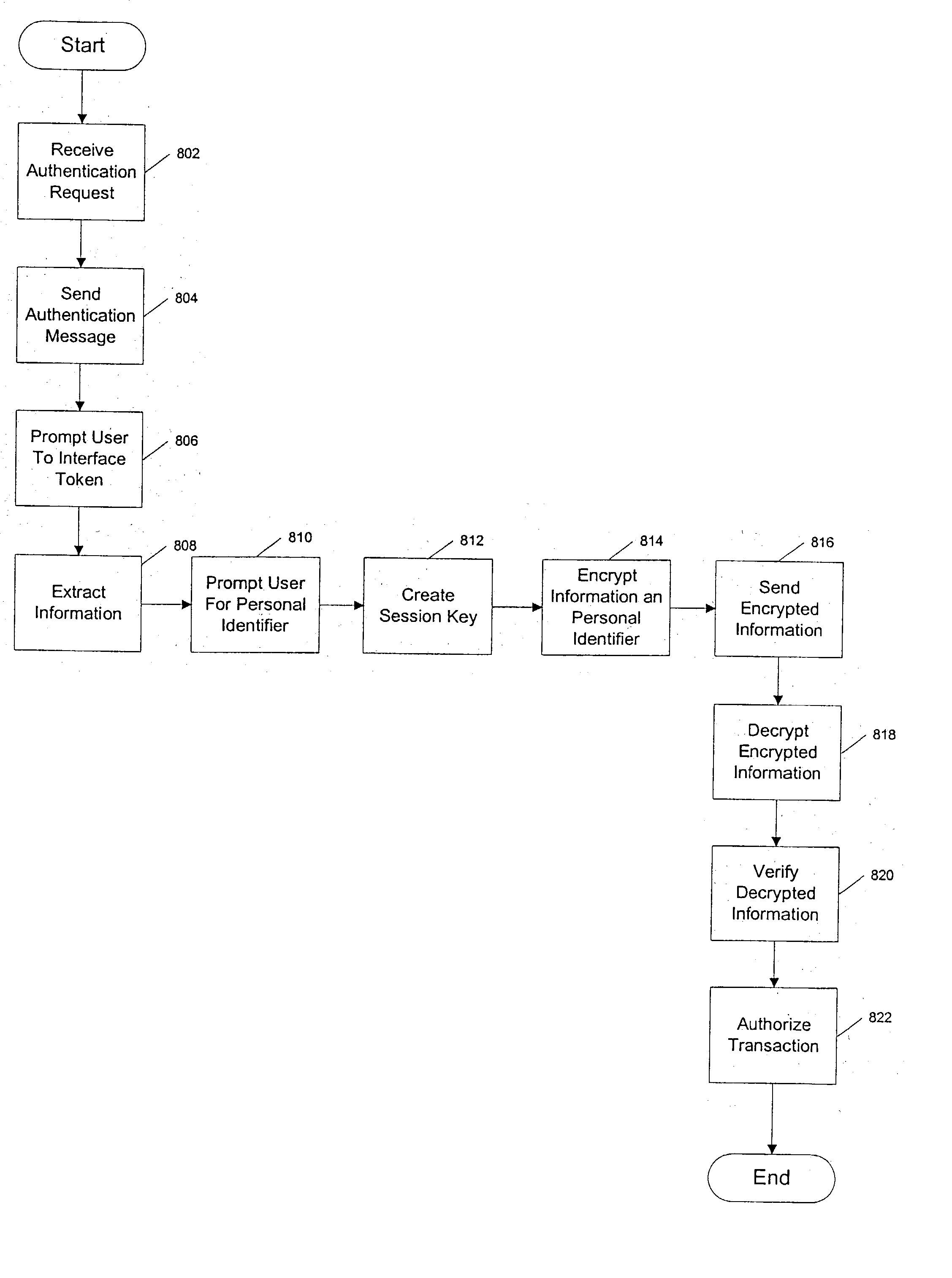
Systems and methods for enrolling a token in an online authentication program
InactiveUS20050033703A1Improve reliabilityReduce fraudFinanceDigital data processing detailsInternet privacyAuthentication
An online transaction system configured to implement authentication methods that allow for strong multi-factor authentication in online environments. The authentication methods can be combined with strong security methods to further ensure that the authentication process is secure. Further, the strong multy-factor authentication can be implemented with zero adoption dependencies through the implementation of automated enrollment methods.
Owner:U S ENCODE CORP
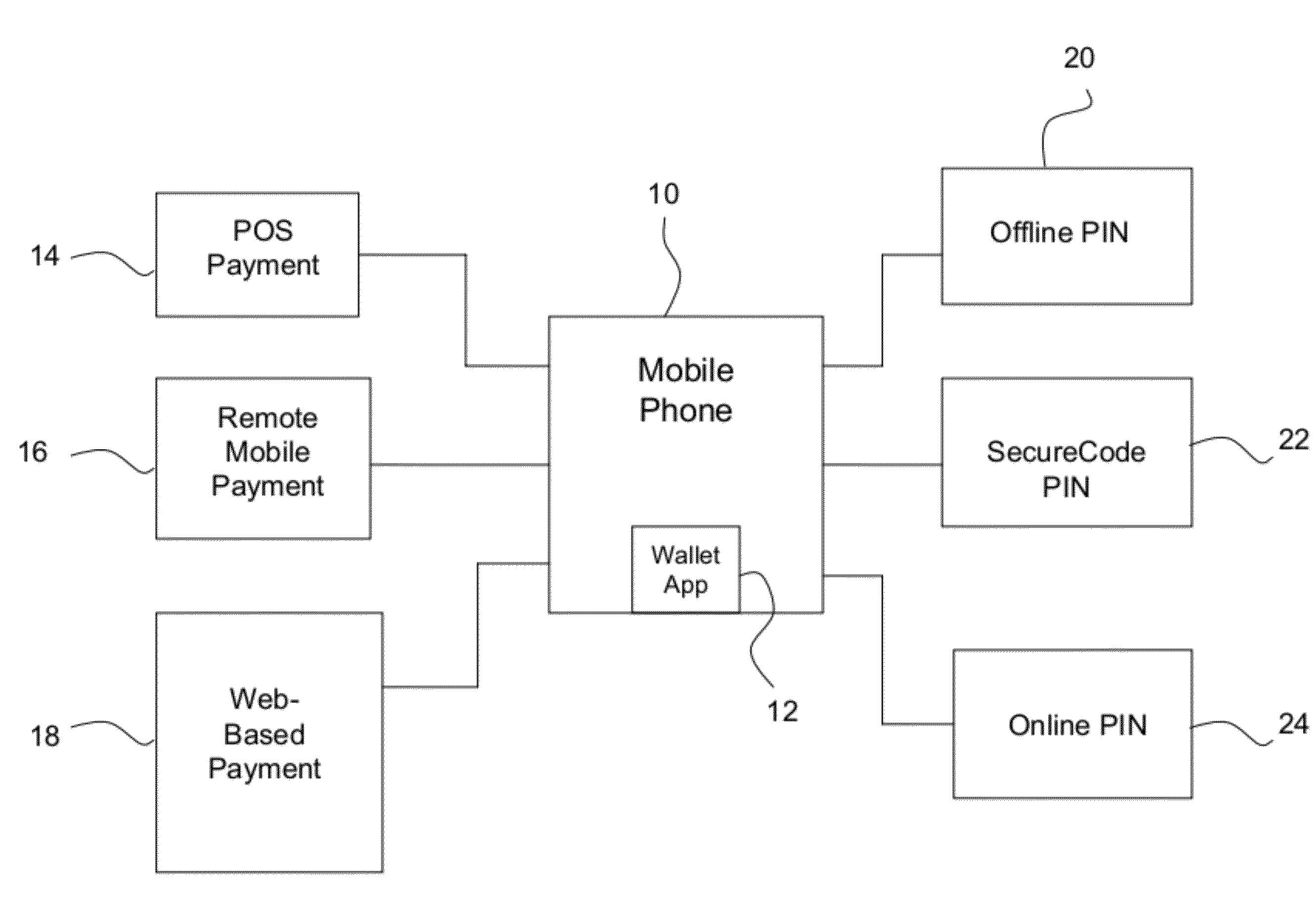
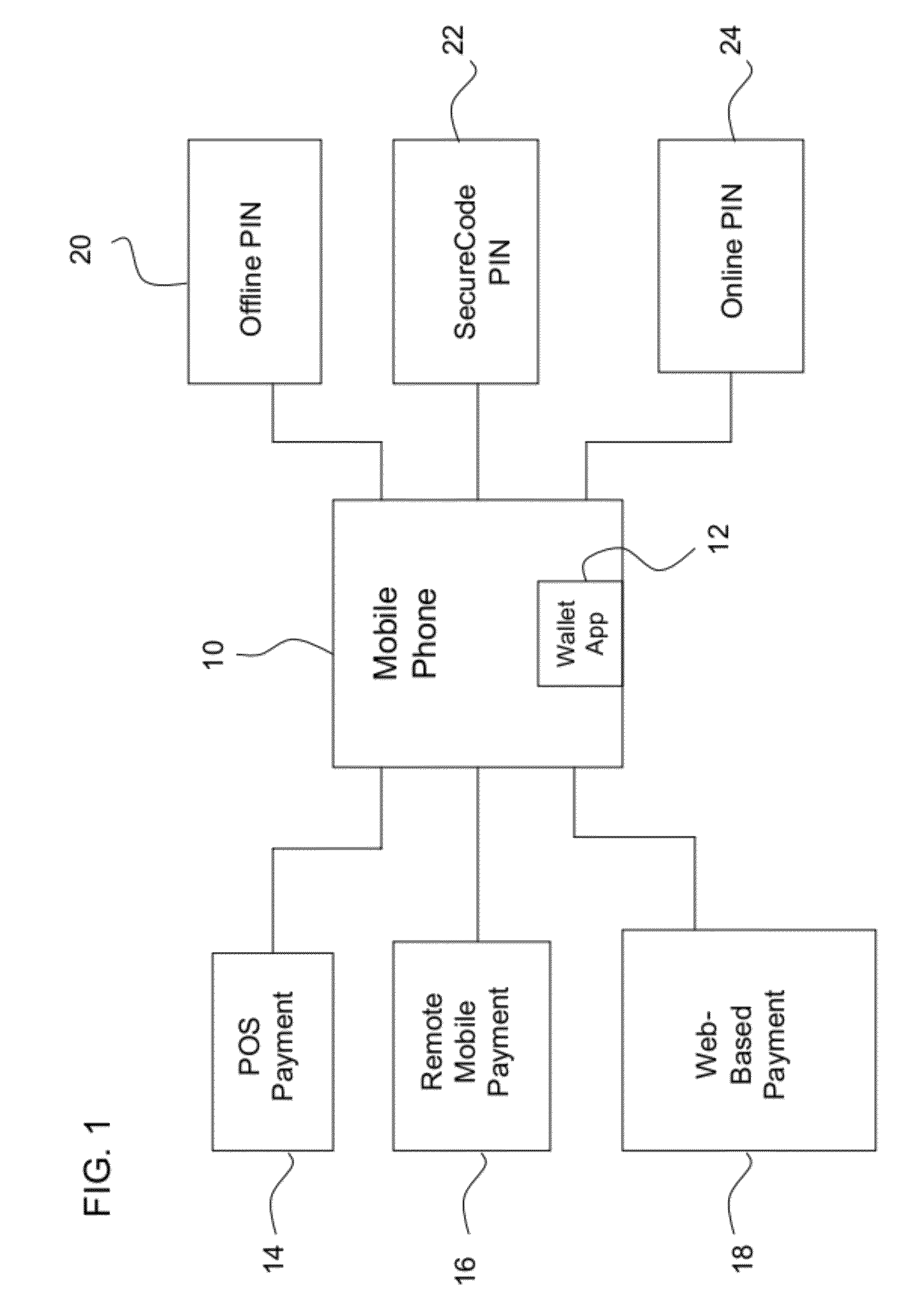
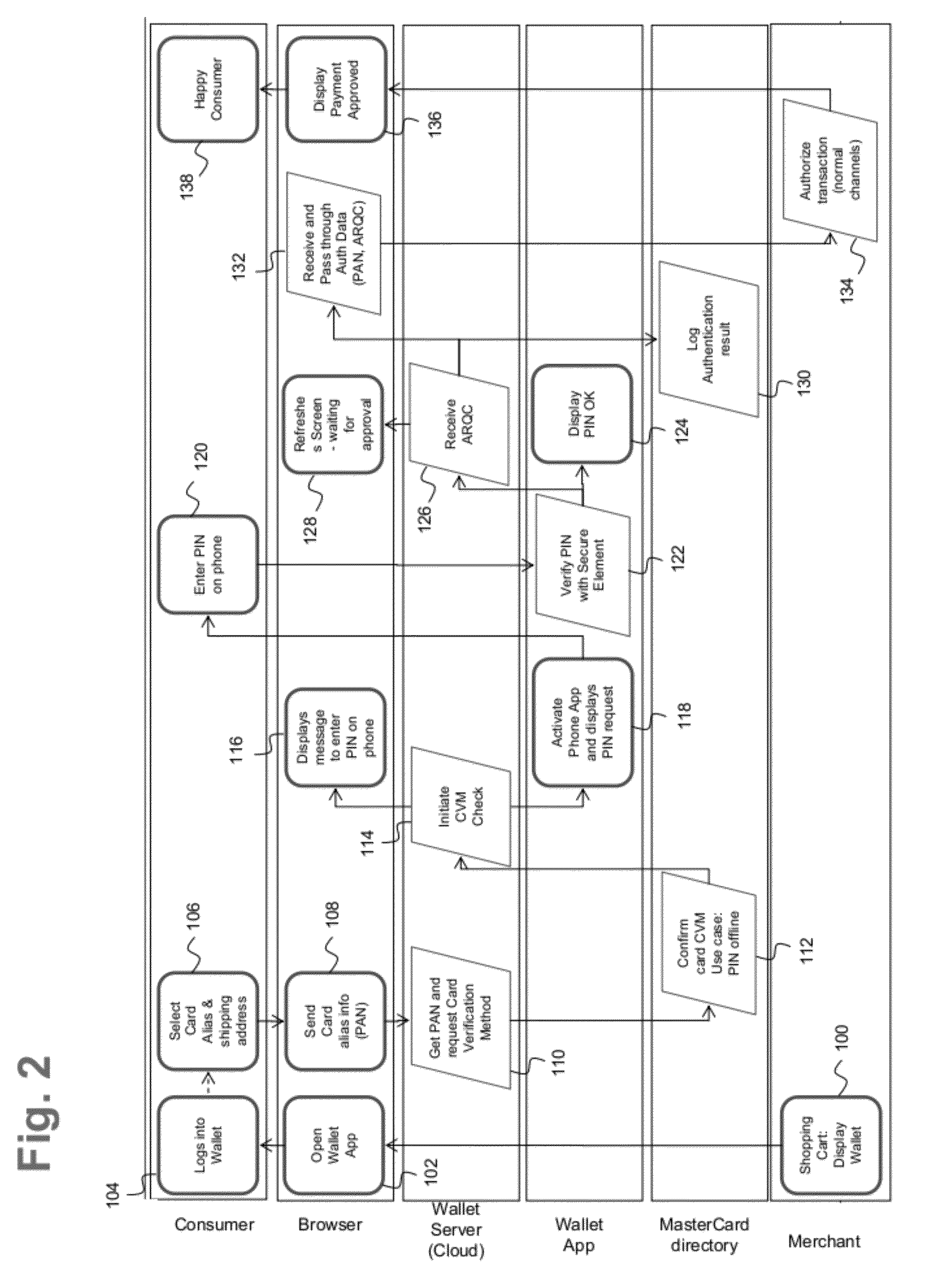
Multi-commerce channel wallet for authenticated transactions
InactiveUS20120143752A1Low implementation requirementsCommunication securityFinanceTransmissionFinancial transactionMobile payment
A phone-based electronic wallet providing authenticated transactions across multiple channels of commerce. The electronic wallet may be used for point-of-sale payments, remote mobile payments and / or web-based payments, and may use authentication tools such as offline PINs, SecureCode PINs and / or online PINs.
Owner:MASTERCARD INT INC
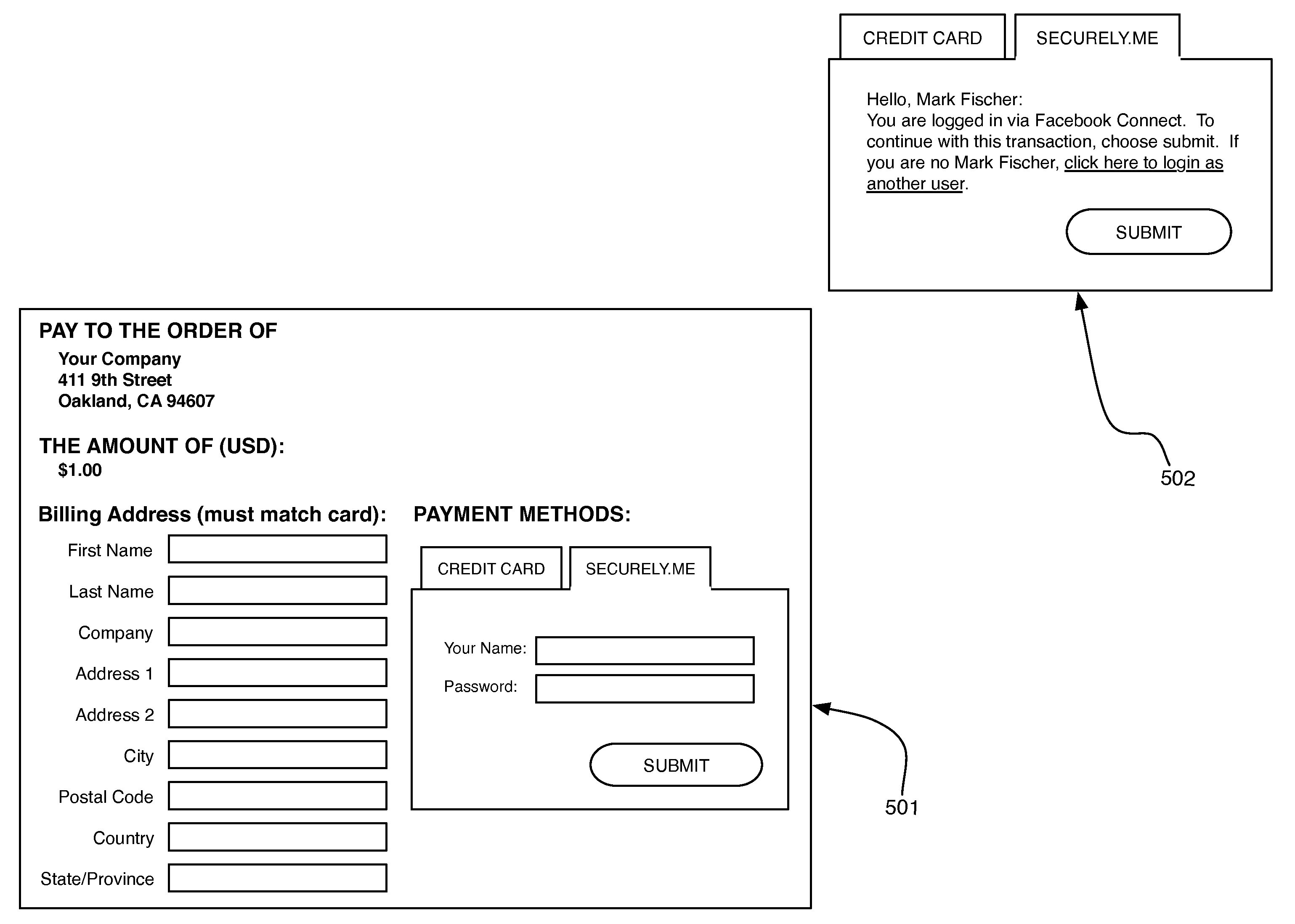
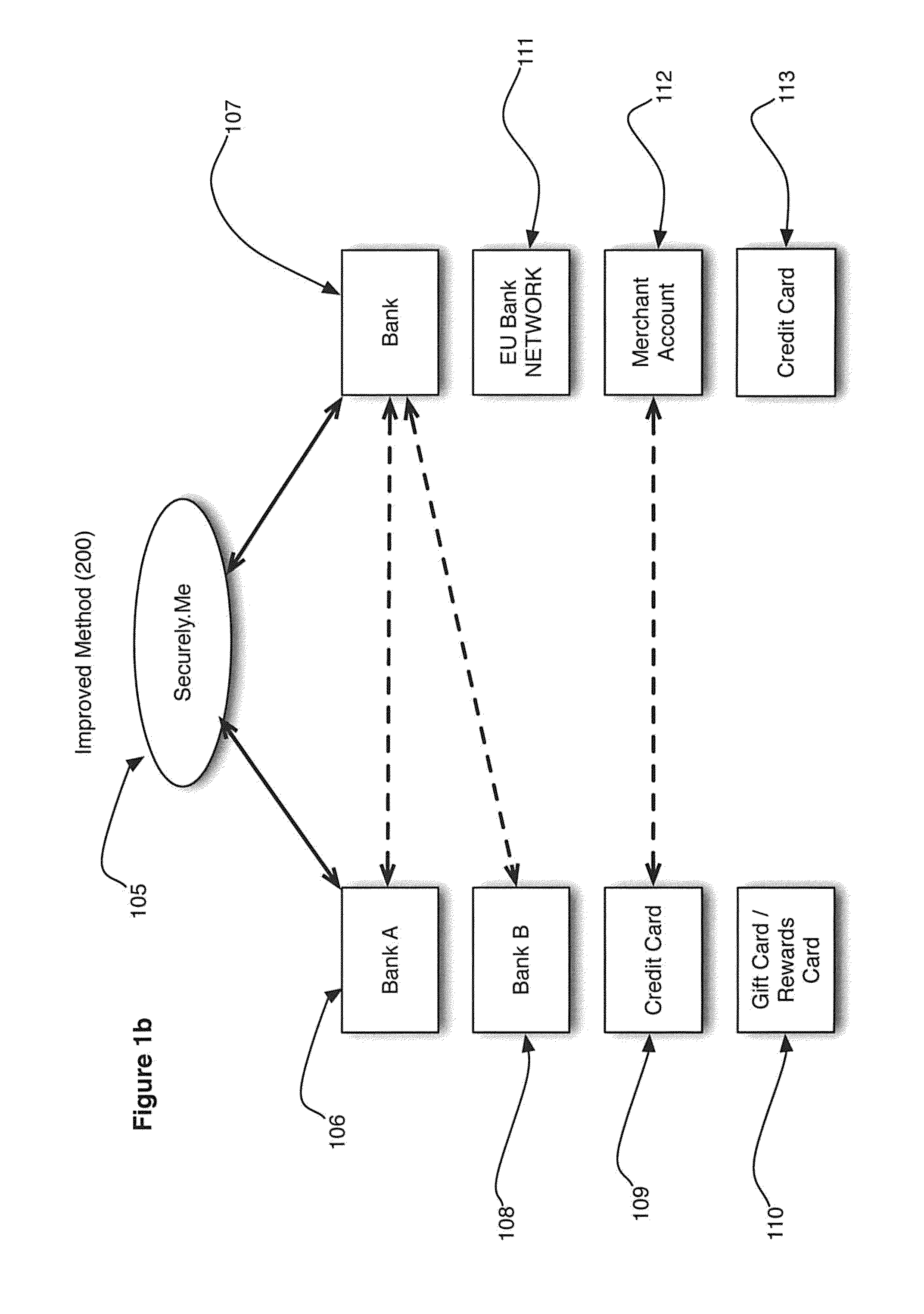
System and Method for Enhancing Electronic Transactions
InactiveUS20120179558A1Reduce fraudLow costFinanceBuying/selling/leasing transactionsMachine learningFinancial transaction
A system and method that enables a consumer or merchant to configure their own respective requirements for using and accessing one or more financial accounts in connection with a financial transaction between a consumer and a merchant. Requirements can include any number of factors including the credit profile of the user, the size of the transaction, the location of the merchant or user, the device used by the user or merchant to perform the transaction. Once requirements have been met for at least one financial account, permitting the completion of a financial transaction using one or more of the financial accounts that have had its requirements met.
Owner:FISCHER MARK NOYES
Single platform system for multiple jurisdiction lotteries and social media
ActiveUS20160104346A1Reduce fraudPlastic/resin/waxes insulatorsBoard gamesSocial mediaCommunications system
A wireless communications system includes a computer system run on a single platform on which different lottery games for different jurisdictions are supported and run from the single platform. The single platform is configured to be in communication with one or more social media sites. Computer executable instructions, when executed by at least one network processor in a workflow server residing in a mobile communications network, implements components that include: a workflow module of sets of workflow instructions for processing different types of lottery game packets from different jurisdictions. A deep packet inspection module inspects a received lottery game packet and provides information about the lottery game packet to the workflow module. The workflow module coordinates processing of the received lottery game packets using selected ones of selectable communication function modules based on the information about the lottery game packet provided by the deep lottery game packet inspection module.
Owner:LOTTERY NOW INC
Point-of-sale billing via hand-held devices
InactiveUS7273168B2Reduce fraudComplete banking machinesFinancePaymentPersonal identification number
A payment resolution module is configured to communicate with hand-held devices (such as mobile phones, PDA's, or computers) to allow purchase of products using the hand-held devices, without requiring the user of the hand-held device to enter payment information for each transaction. The user of the hand-held device may be identified as the owner of the device either by having the option to enter a personal identification code, or by using a biometric to identify himself, for example. Accordingly, only an authorized user of the hand-held device may use the hand-held device to purchase products. After the payment resolution module receives authorization for payment, an authorization code is transmitted to the mobile device. The user may be required to present the authorization code at the point of sale, such as by entering the code into a computing device at the point-of-sale, prior to completion of the transaction.
Owner:XILIDEV
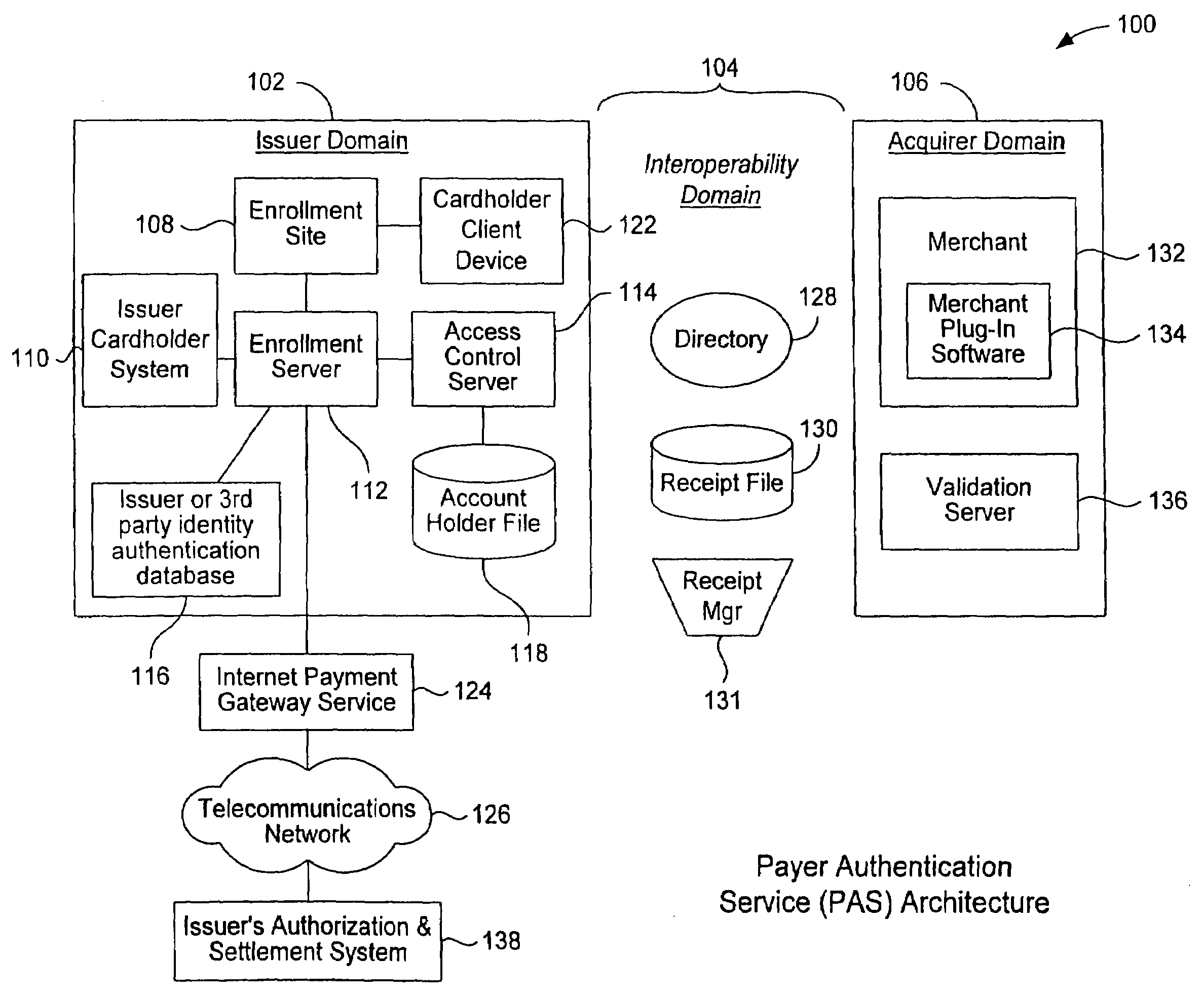
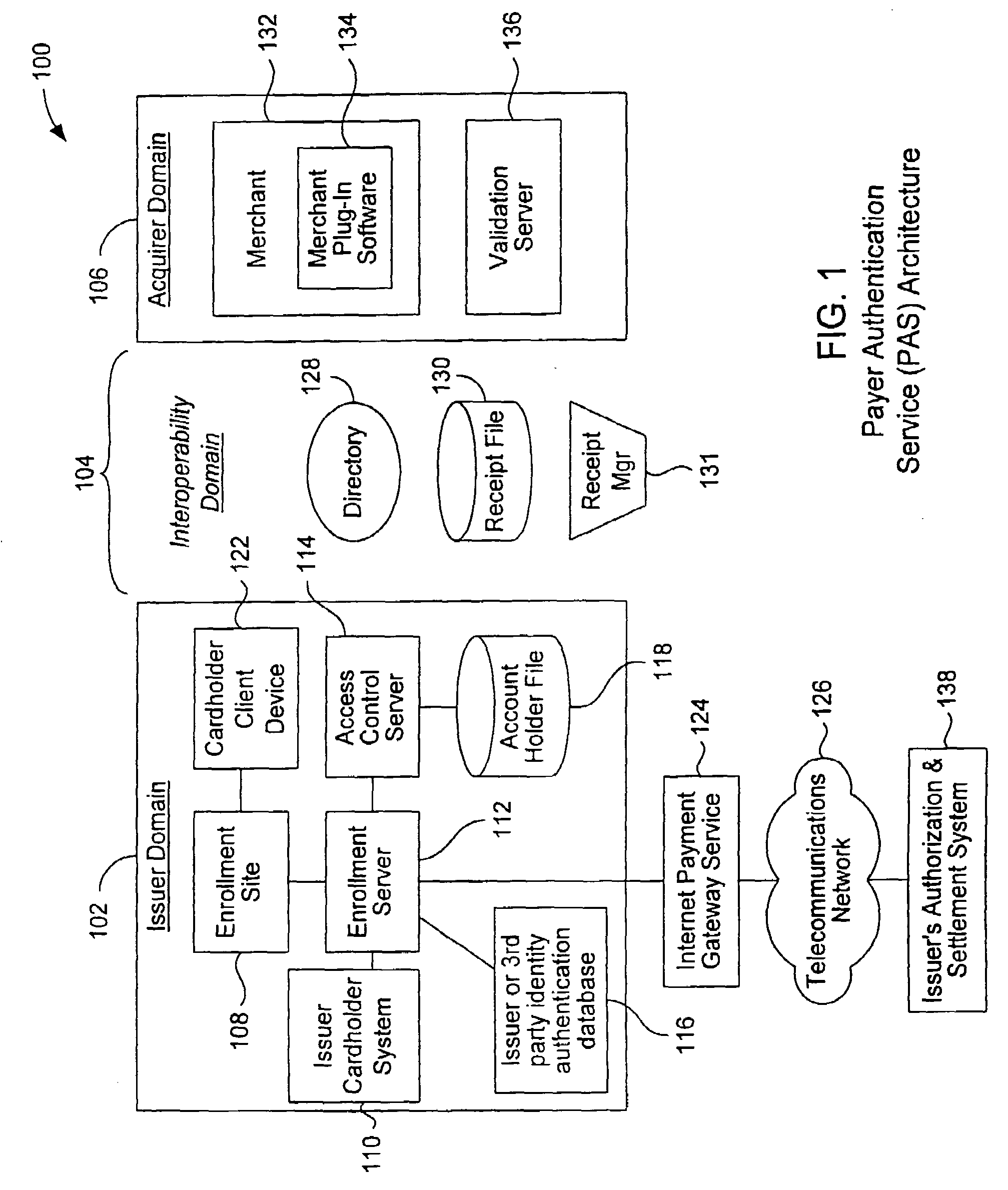
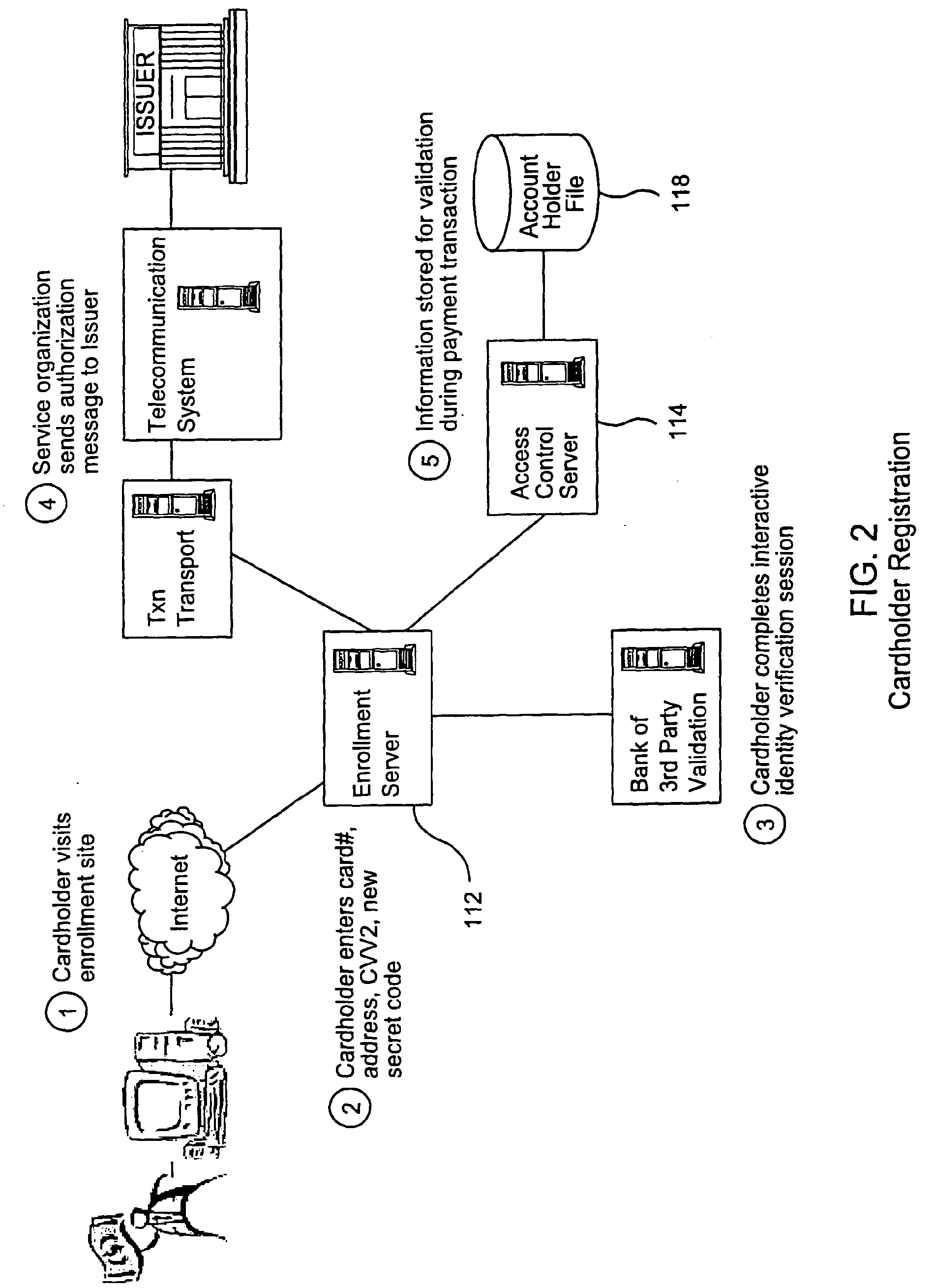
Online payer authentication service
InactiveUS20080301056A1Reduce chargebacksReduce fraudUser identity/authority verificationCo-operative working arrangementsPaymentInternet Authentication Service
A payment authentication service authenticates the identity of a payer during online transactions. The authentication service of the present invention allows a card issuer to verify a cardholder's identity using a variety of authentication methods, such as the use of passwords. Also, the only system participant requiring a certificate is the issuing financial institution. One embodiment of the invention for authenticating the identity of a cardholder during an online transaction involves querying an access control server to determine if a cardholder is enrolled in the payment authentication service, requests a password from the cardholder, verifies the password, and notifies a merchant whether the cardholder's authenticity has been verified. In another aspect of the invention, a chip card and the authentication service independently generate cryptograms that must match in order for the service to verify that the correct chip card is being used by the cardholder.
Owner:WELLER KEVIN D +6
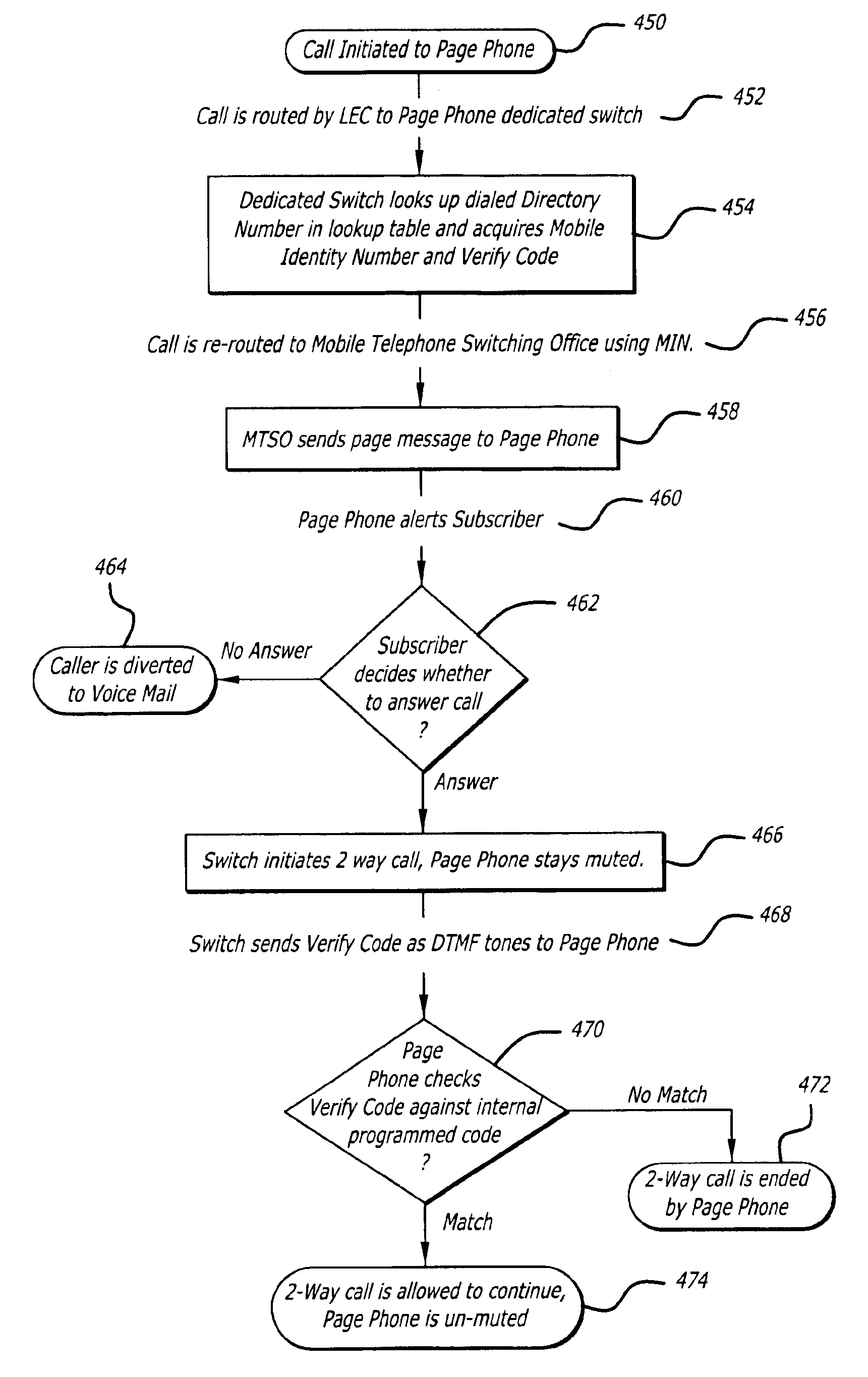
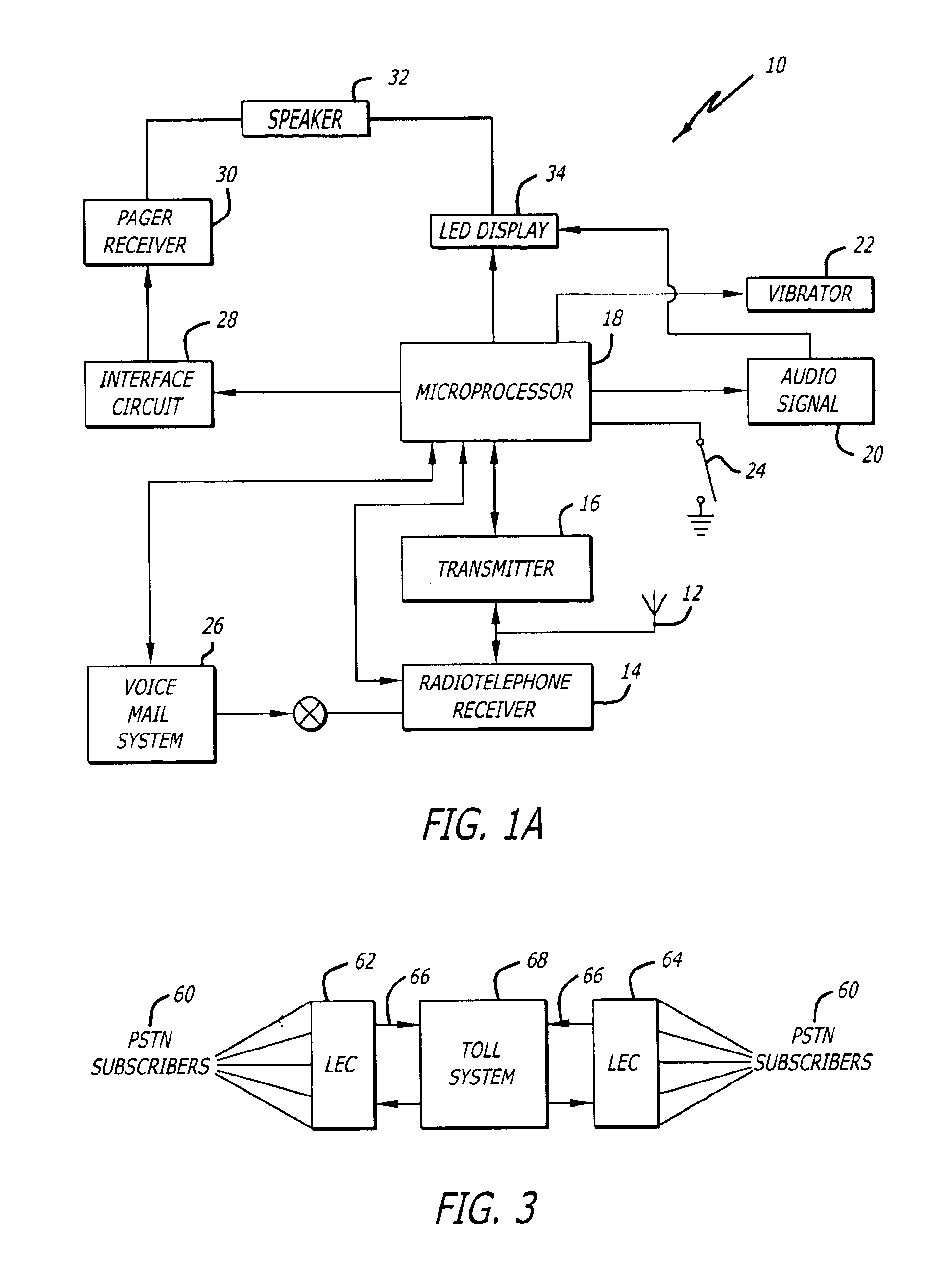
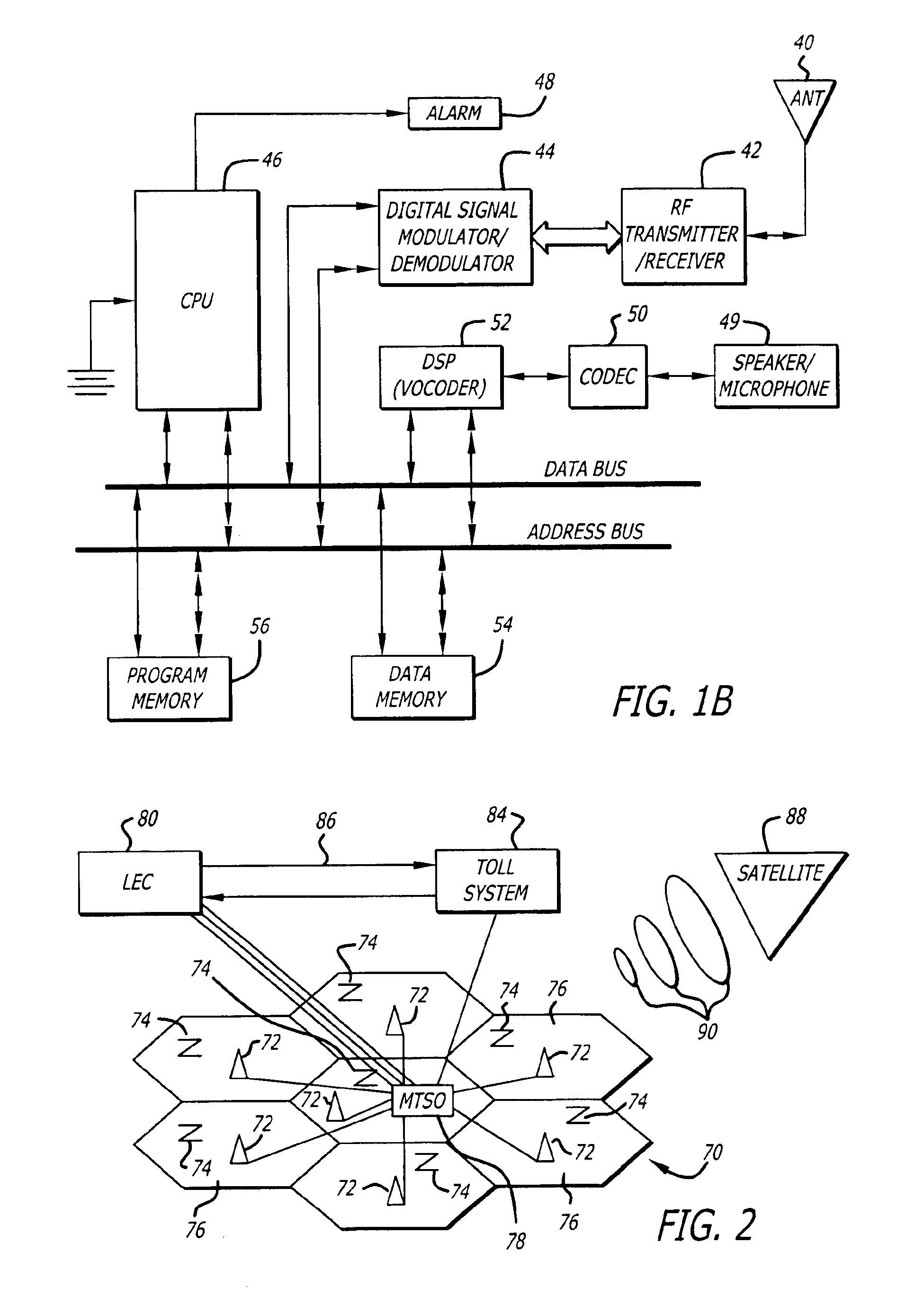
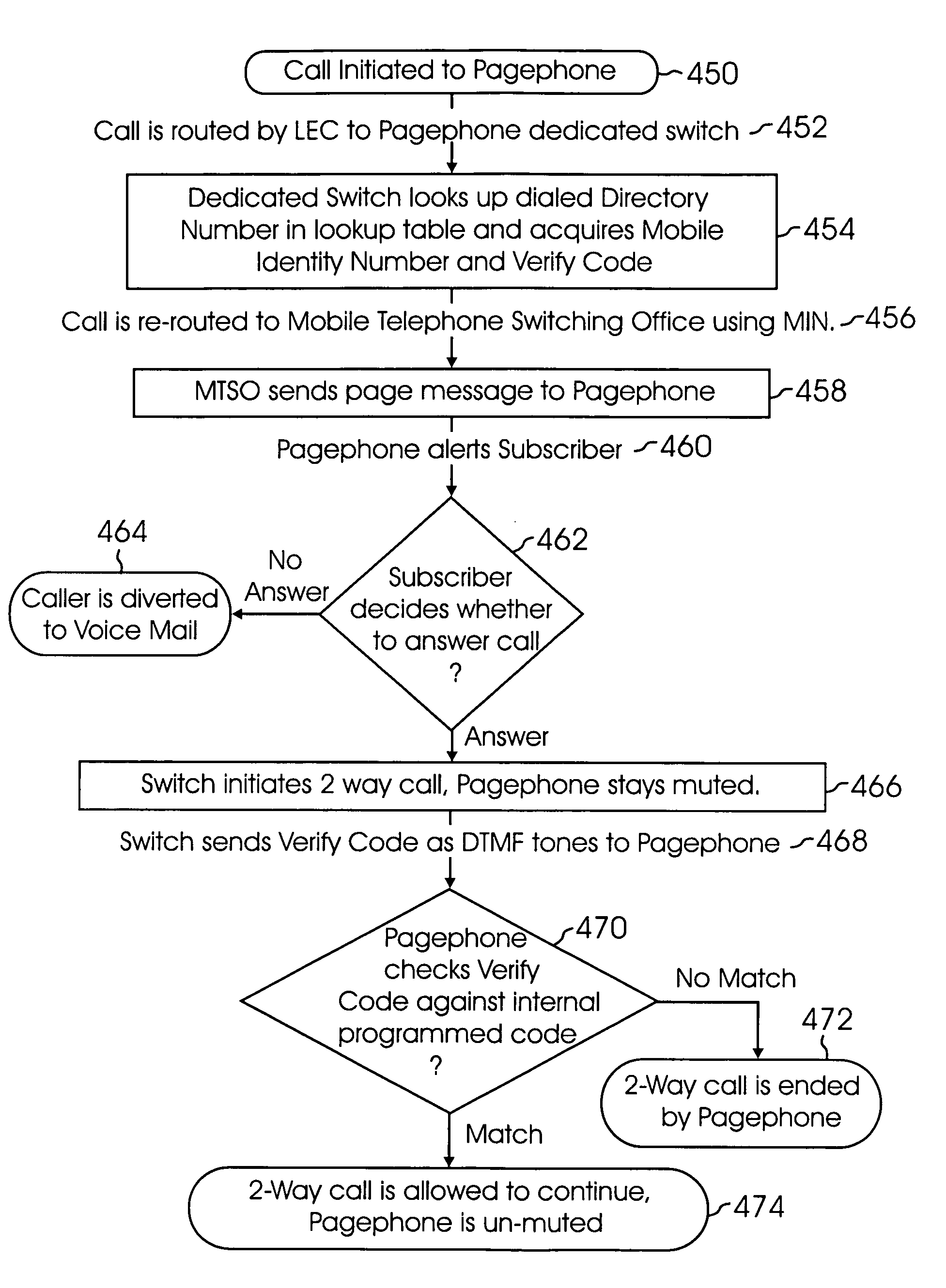
Call receiving system apparatus and method having a dedicated switch
InactiveUS6879244B1Reduce fraudInterconnection arrangementsFrequency-division multiplex detailsPagerUser equipment
A system and method for a call receiving pager apparatus, system and method utilizing a dedicated switch for providing proprietary access, billing functions and other enhanced features is described. The system utilizes a subscriber apparatus having pager or radiotelephone functions whereby a caller may call the apparatus and gain direct two-way communication with the subscriber. The caller is billed for the communication. A call receiving pager apparatus, system and method wherein a subscriber can initiate an outgoing connection to at least one predetermined telephone number in order to send a pre-recorded voice or data message is also provided. The subscriber is unable to initiate any real time two-way communication with the outgoing connection.
Owner:LBT IP LLC
Token for use in online electronic transactions
InactiveUS20050044393A1Improve reliabilityReduce fraudDigital data processing detailsUser identity/authority verificationInternet privacyAuthentication
An online transaction system configured to implement authentication methods that allow for strong multi-factor authentication in online environments. The authentication methods can be combined with strong security methods to further ensure that the authentication process is secure. Further, the strong multi-factor authentication can be implemented with zero adoption dependencies through the implementation of automated enrollment methods.
Owner:U S ENCODE CORP
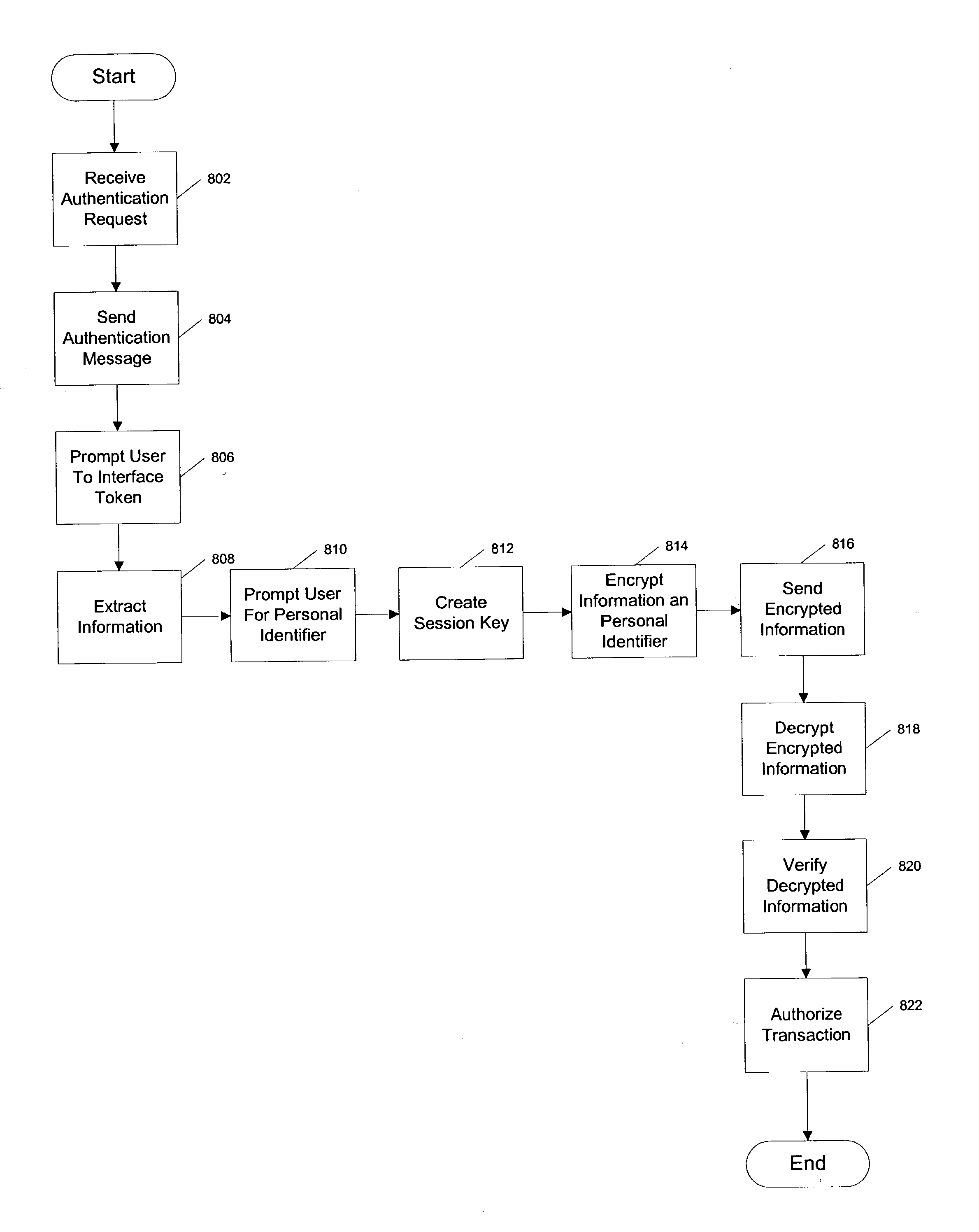
Systems and methods for secure authentication of electronic transactions
InactiveUS20050044385A1Improve reliabilityReduce fraudDigital data authenticationElectronic credentialsInternet privacySecure authentication
Owner:U S ENCODE CORP
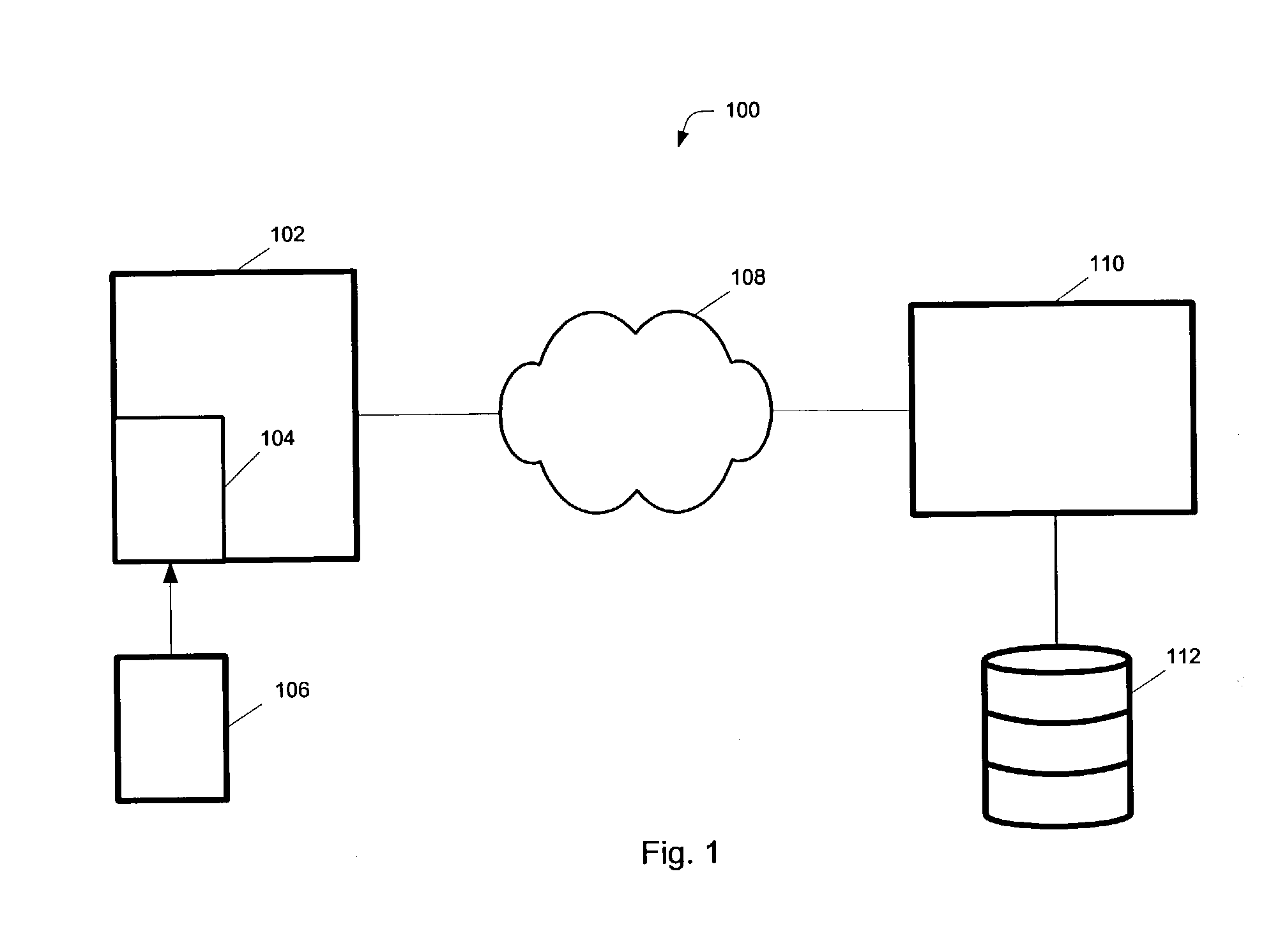
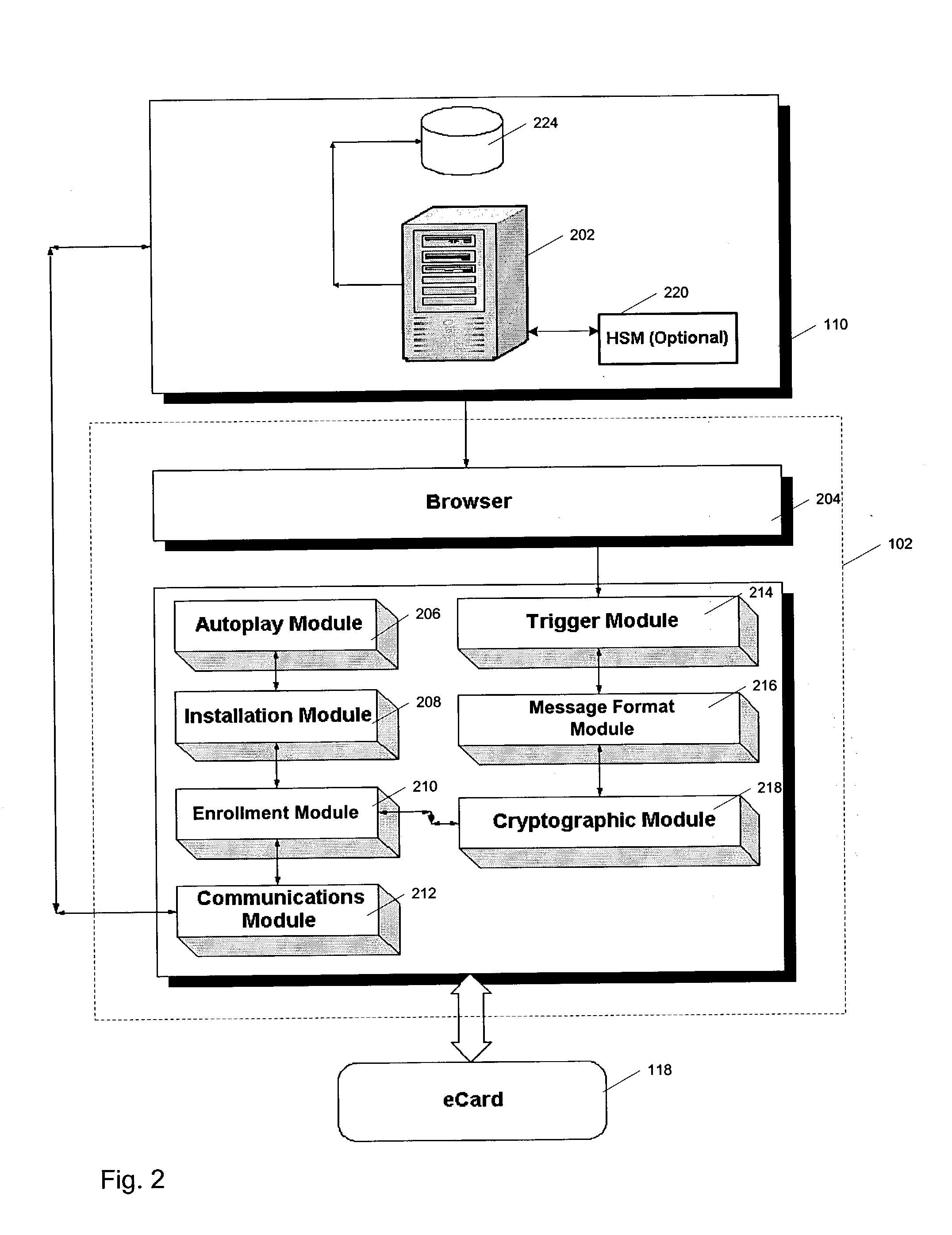
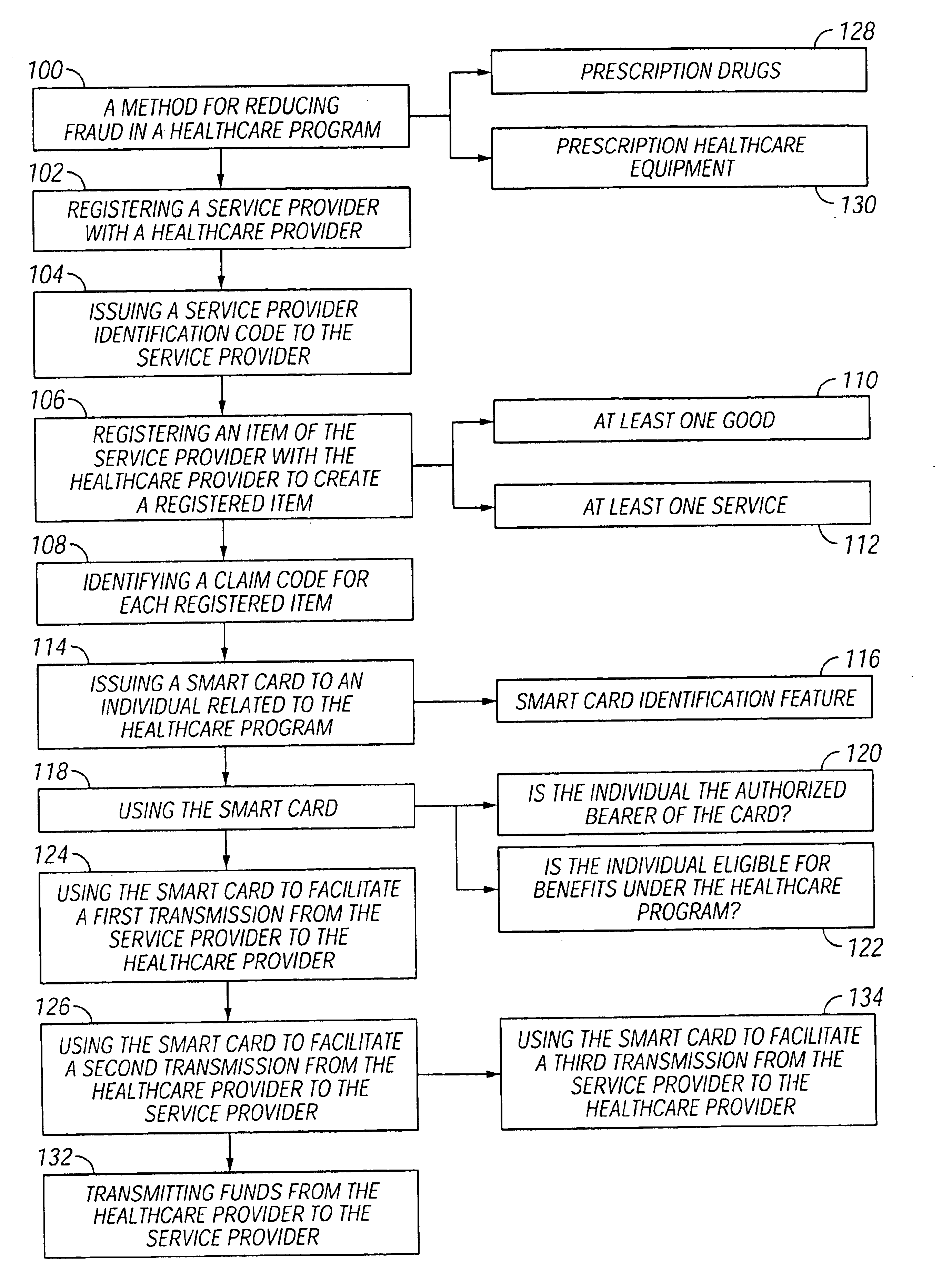
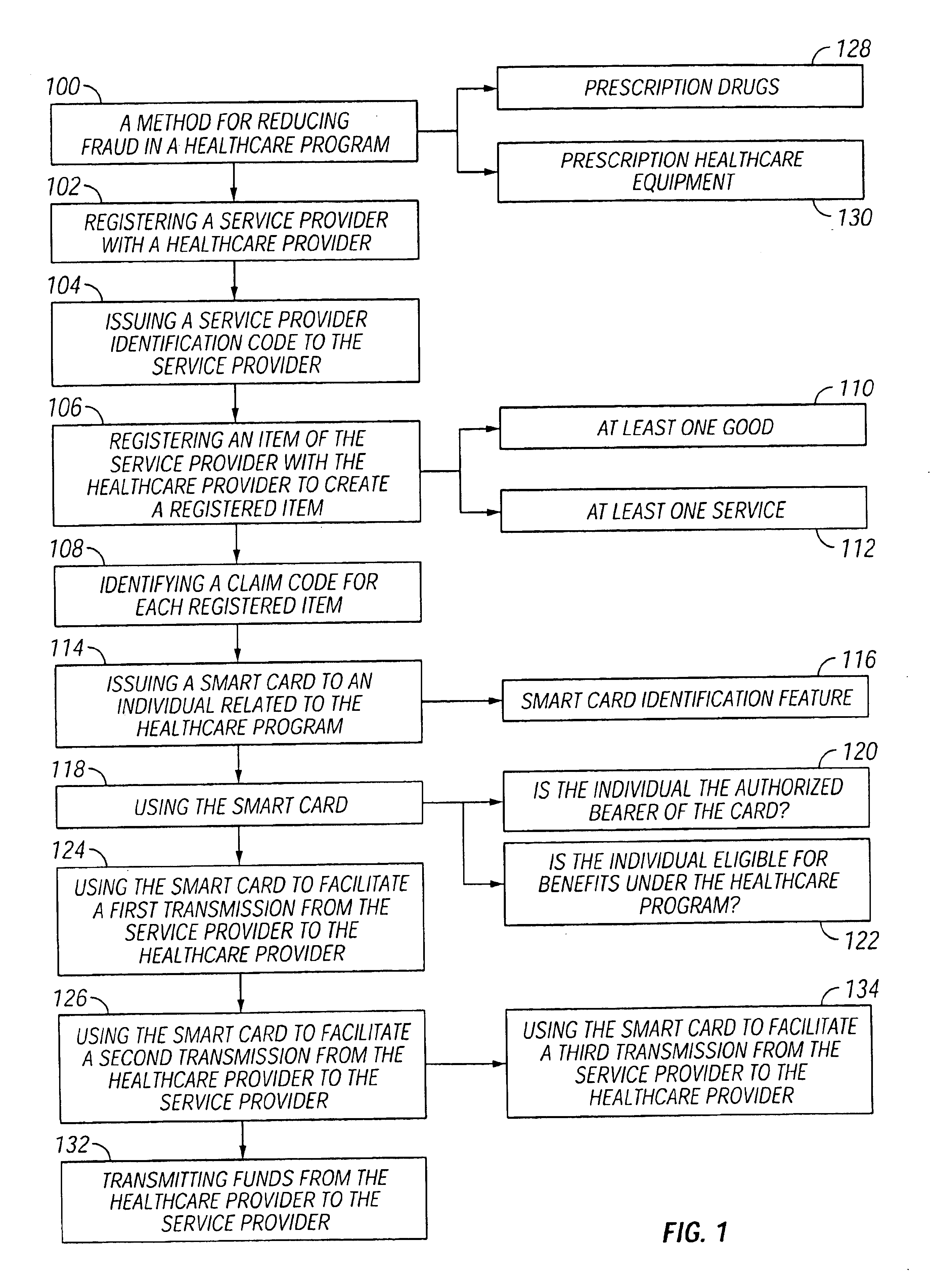
Methods for reducing fraud in healthcare programs using a smart card
ActiveUS6873960B1Reduce fraudCredit registering devices actuationFinanceService providerMedical treatment
Methods for reducing fraud in a prescription healthcare program are described herein. The methods generally include registering a service provider with a prescription healthcare provider and issuing a service provider identification code to the service provider and registering an item of the service provider with the prescription healthcare provider to create a registered item and identifying a claim code for each registered item. The item can include at least one service, at least one good and combinations thereof. The method further includes issuing a smart card to an person related to the prescription healthcare program, wherein the smart card has a smart card identification feature to identify the person and using the smart card to determine if the person is the authorized bearer of the smart card and is eligible for benefits from the prescription healthcare program. The method further includes using the smart card- to facilitate a first transmission from the service provider to the prescription healthcare provider. The method further includes using the smart card to facilitate the second transmission from the prescription healthcare provider to the service provider. In one embodiment, the method includes using the smart card to facilitate a second transmission from the service provider to the prescription healthcare provider.
Owner:ACCESS SECURITY PROTECTION
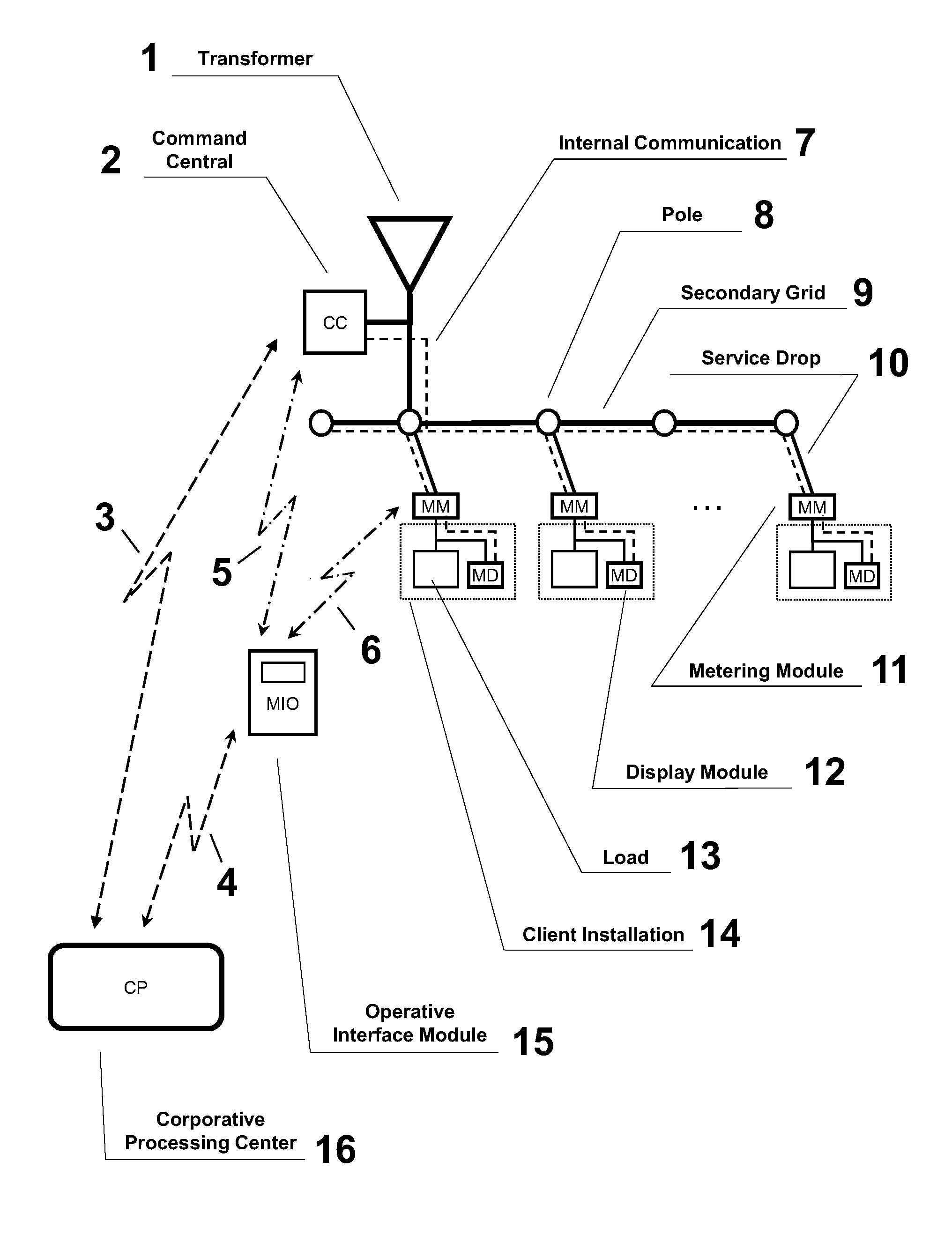
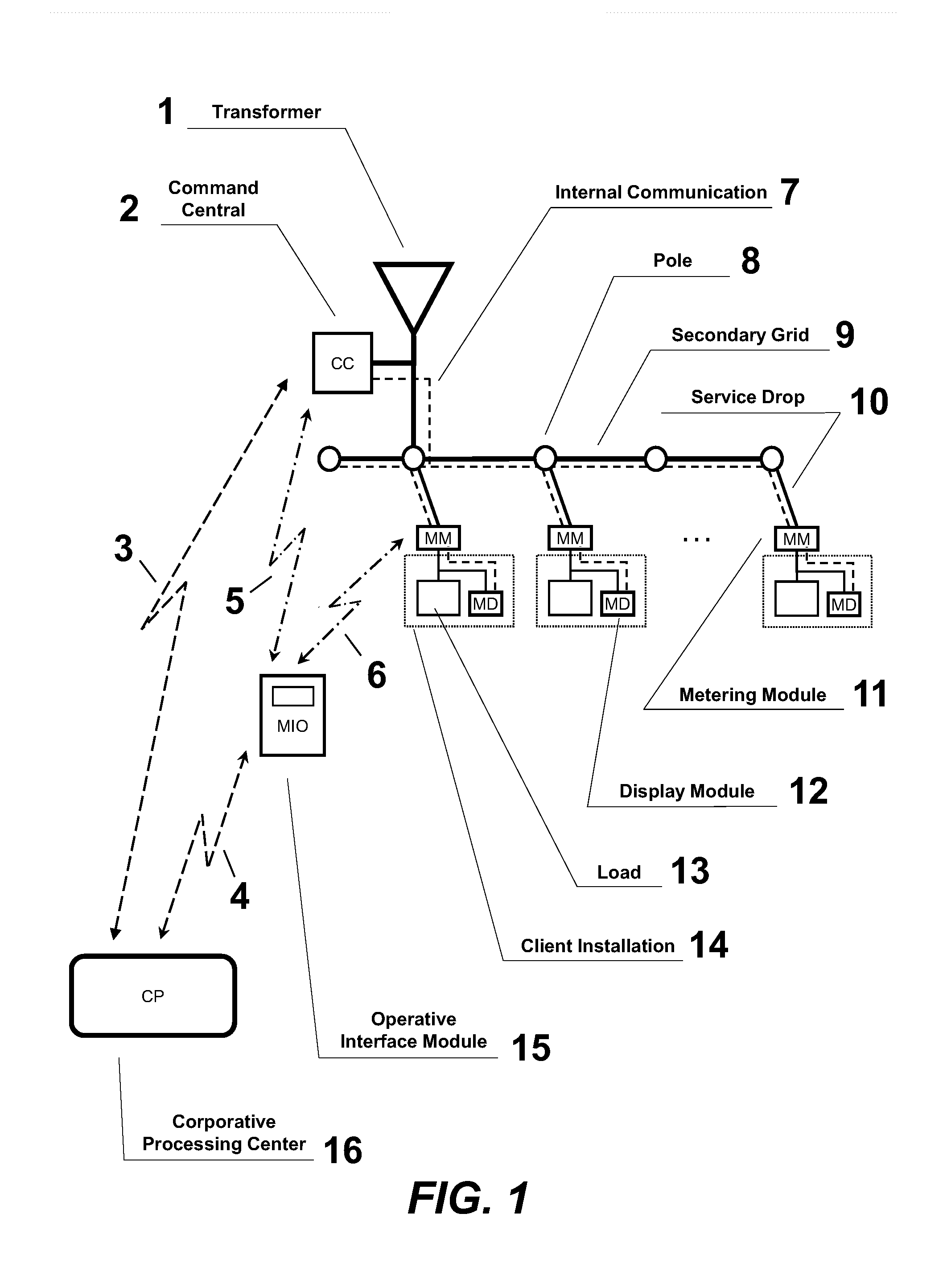
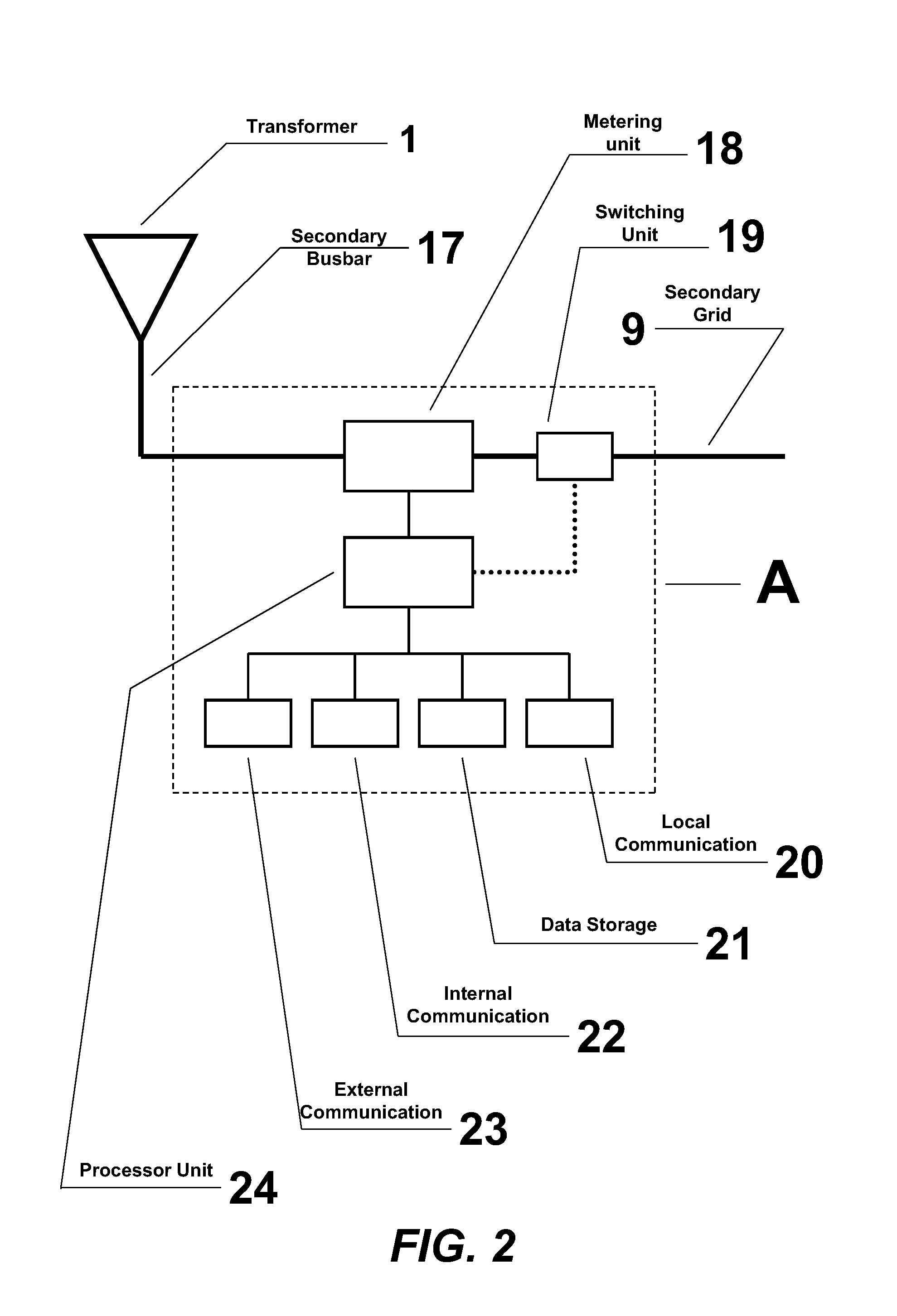
System for controlling, measuring and monitoring the secondary electric power distribution grid
InactiveUS20140300210A1Efficient deploymentReduce fraudBoards/switchyards circuit arrangementsSub-station arrangementsDistribution transformerElectric power distribution
The present invention relates to a system for controlling, measuring and monitoring the secondary electric power distribution grid with remote fraud and power theft detection, readings, power cuts-off, reconnection and client load control, besides continuous monitoring of the electric grid parameters, providing diagnostics on the status of the grid and public lighting from an assigned Command Central, located at the secondary bulbar of the distribution transformer, and Measuring Modules at clients installations.
Owner:ABI ACKEL MARCOS VALADAO
Method and system for convenient network job hunting and recruitment
InactiveCN101520867AIncrease success rateSimple and fast job huntingResourcesSpecial data processing applicationsWeb siteSoftware system
The invention discloses a method and a system for convenient network job hunting and recruitment. The method comprises the following steps that: a client job hunting and recruitment software system is installed in a user computer terminal, and job hunting or recruitment information is filled in and sent to a far end network station information data base server by a release interface of the system; the network station information data base server classifies and stores the job hunting information and recruitment information according to job parameter classification respectively, and by comparing a key word in the job hunting information with a key word in the recruitment information, the job hunting or recruitment information which meets the conditions is sent to the corresponding user computer terminal; and the user can check the information by the user computer and communicate with a suitable object. The method and the system have the advantages that: the user can directly release and search job hunting and recruitment information by the user computer, the job hunting or recruitment task can be finished only by the user computer terminal, and the user does not need to log on a recruitment network for registration, so that the mode is simple, fast and convenient in operation.
Owner:汤溪蔚
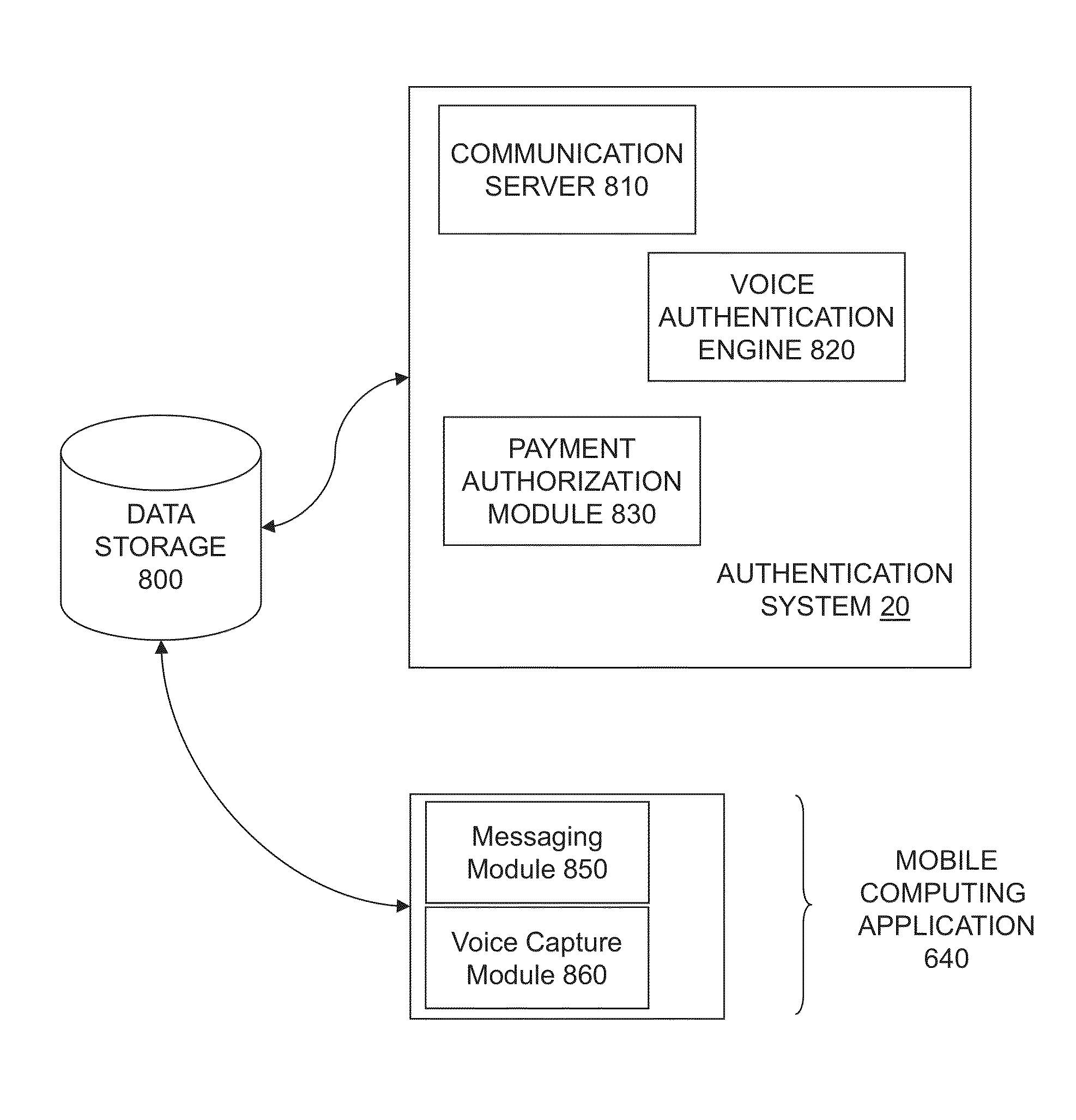
Systems and methods for authenticating benefit recipients
InactiveUS20130159194A1Facilitate secure transferReduce fraudFinanceDigital data authenticationThird partyBank account
Remote authentication that allows a previously enrolled individual to be remotely authenticated and provided with a benefit from a first party payor through a third-party agent. Remote authentication may include biometric authentication including voice biometric authentication. Use of an authorization token to prove current eligibility to receive a benefit transfer from a third-party agent that is not going to perform an independent biometric authentication. Processes for beneficiaries with a bank account and those without a bank account are disclosed.
Owner:VOICE TRUST
Point-of-sale bill authentication
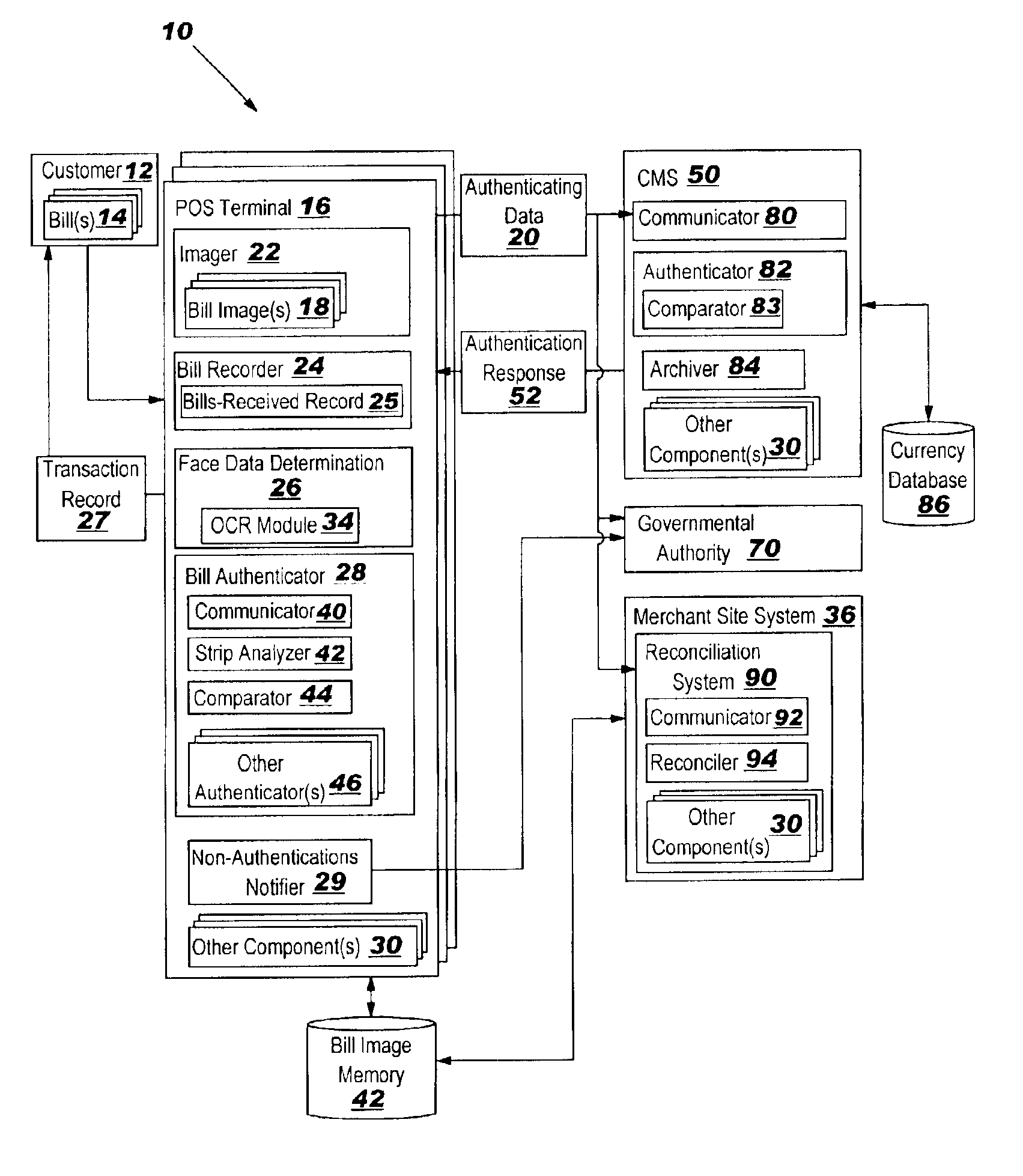
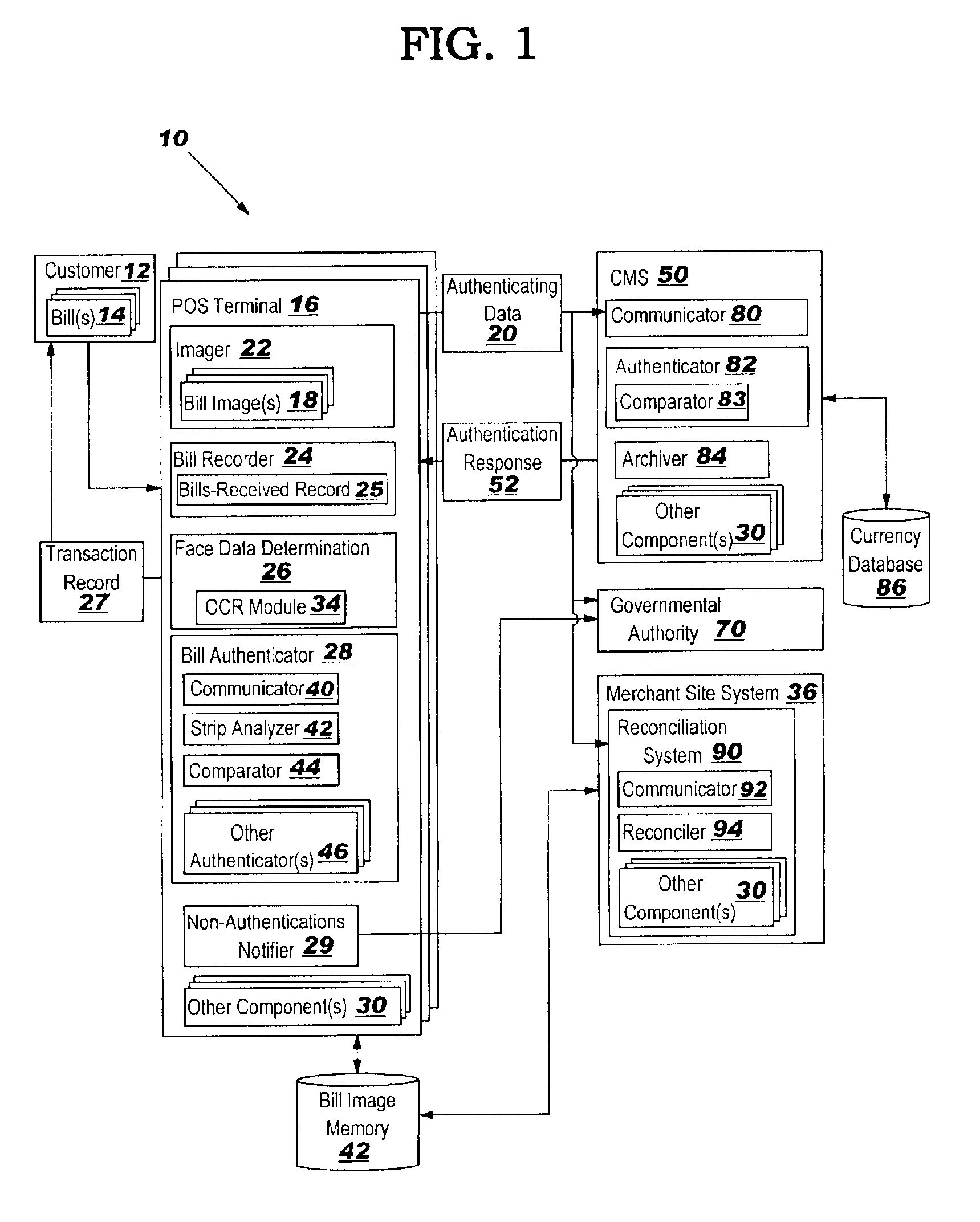
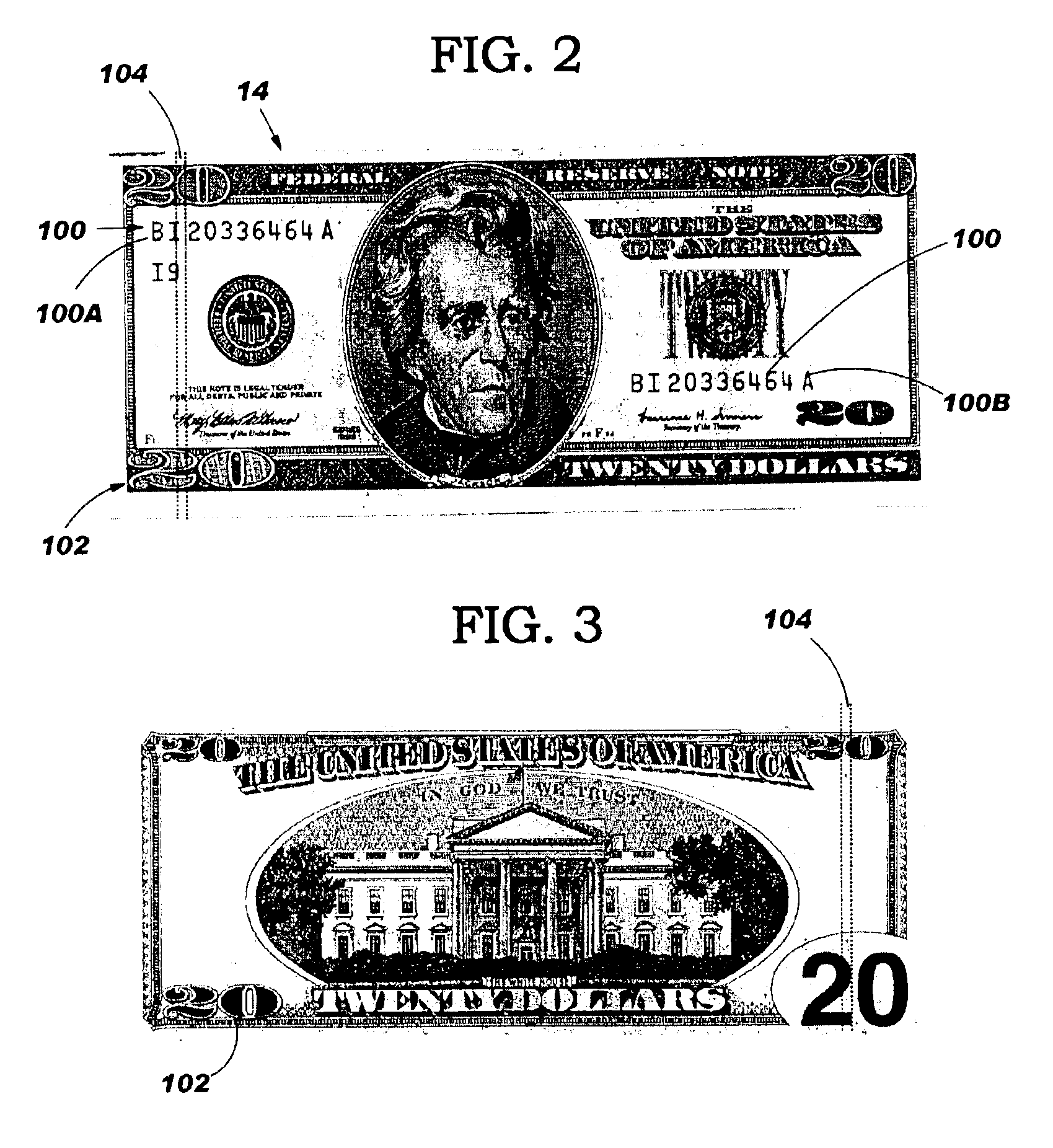
InactiveUS6883706B2Reduce fraudImprove securityElectric signal transmission systemsDigital data processing detailsMonitoring systemPoint of sale
The invention includes systems, methods and program products for providing real-time point-of-sale paper currency, i.e., bill, authentication and recordation. The invention provides a point-of-sale terminal capable of real-time authentication and recordation of paper currency, a currency monitoring system for tracking paper currency usage and conducting paper currency authentication relative to a currency issuing entity's database, and a reconciliation system for reconciling a point-of-sale terminal.
Owner:TOSHIBA GLOBAL COMMERCE SOLUTIONS HLDG
Method for conducting financial transactions
InactiveUS20120011024A1Reduce the possibilityReduce fraudAcutation objectsFinancePaymentGeographic site
A method is providing of paying second parties where if f they do not have an established association with the payment service, have an established association with the payment service prior to payment. The first party has an association with the payment service. A tab is opened by the first party that can be selected by the qualified second party at any geographic location of a first party's mobile device. The qualified second party is only able to charge a first party's financial account when the first party's mobile device is within a defined geographic area. The tab is a relationship between the first party, the payment service and the qualified second party. The qualified second party can engage in a financial transaction with the first party when the first party is within the defined geographic area. In response to the second party, (i) attempting to charge the first party or (ii) charging the first party, a determination is made to see if a fraudulent attempt or fraudulent use of the first party's financial account is committed.
Owner:BLOCK INC
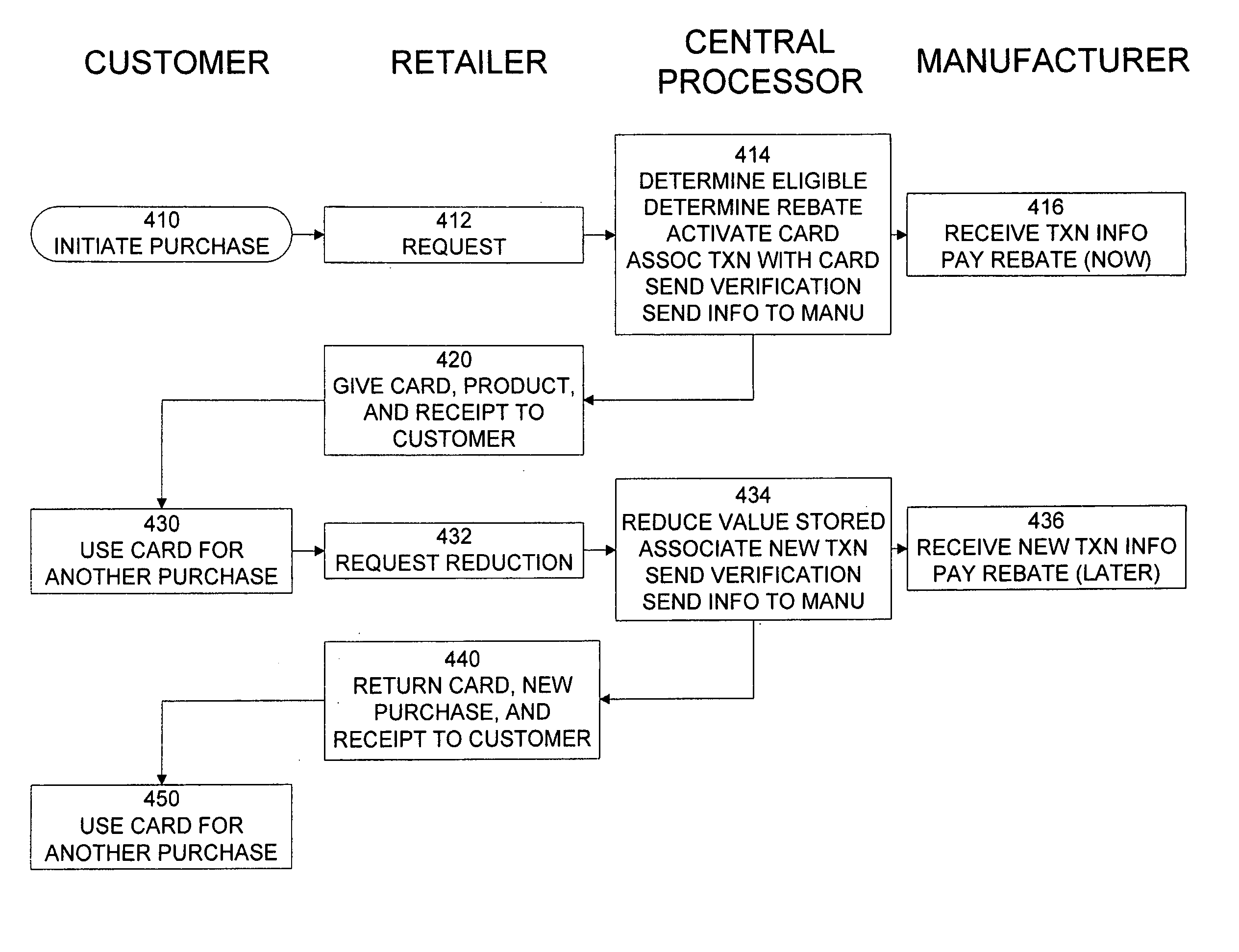
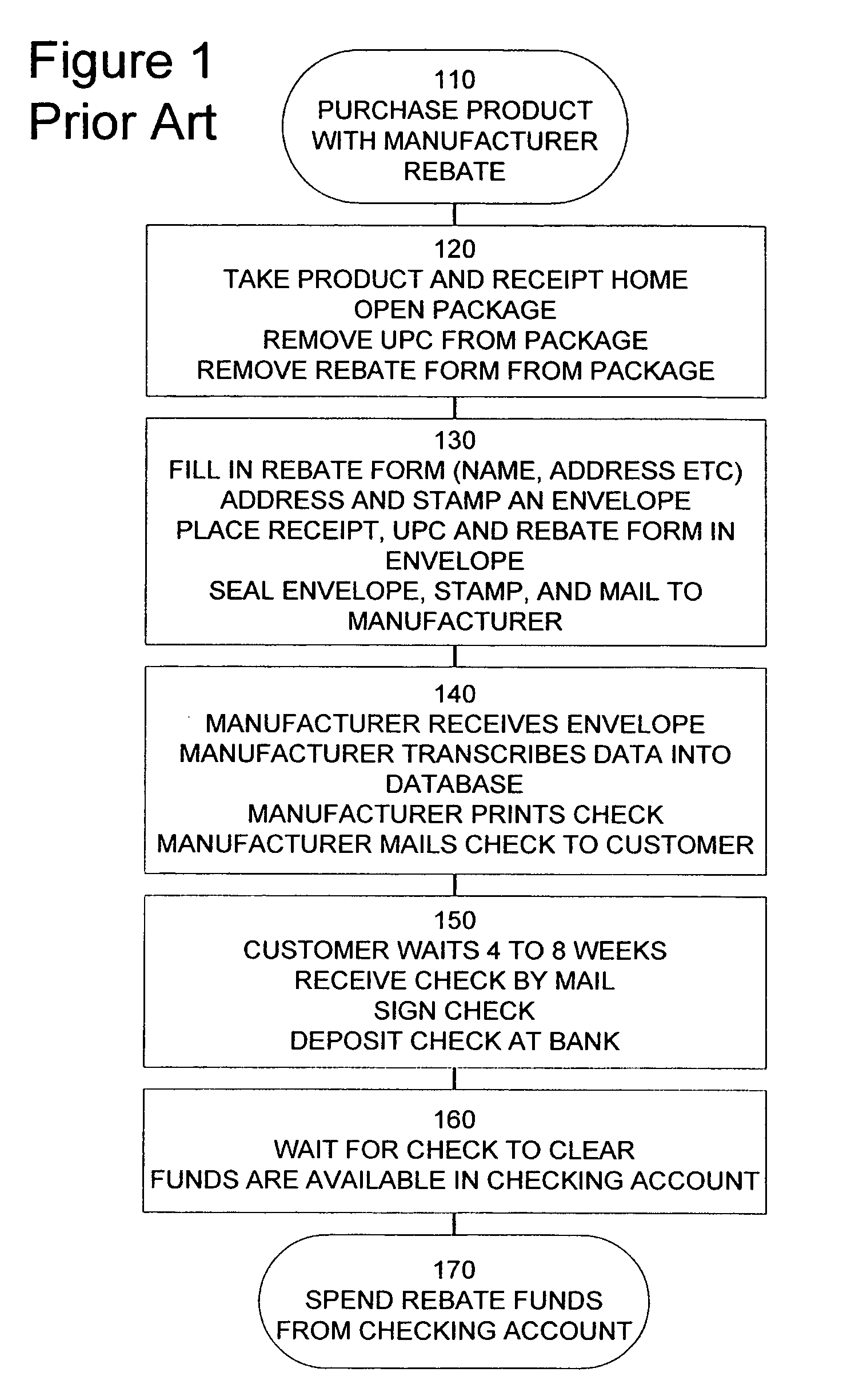
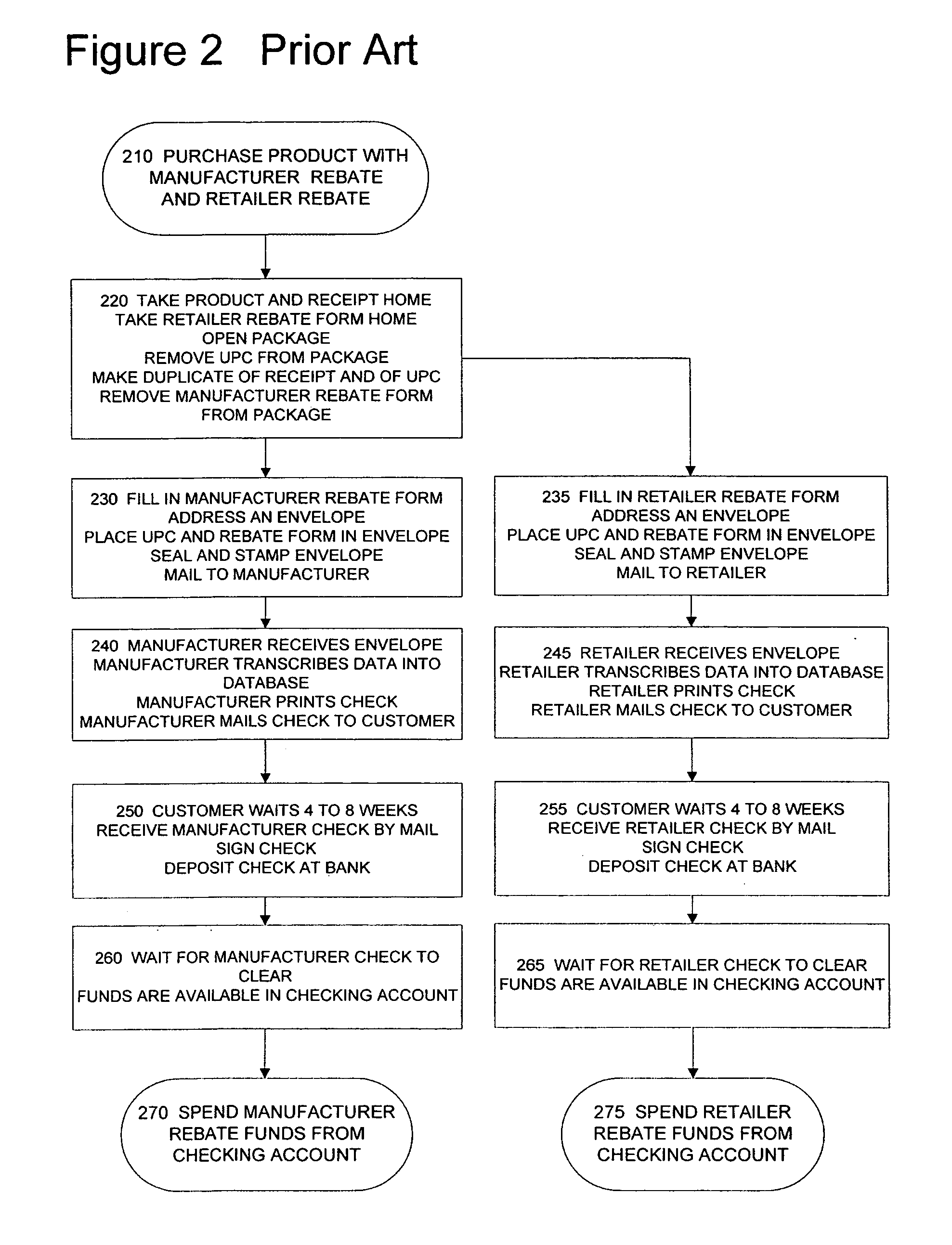
Rebate card system
ActiveUS20070143177A1Reduce fraudIncrease credibilityDiscounts/incentivesFinanceFinancial transactionComputer science
A method and system for using a rebate card are disclosed. The method may comprise initiating a purchase transaction for one or more products at a point of sale, determining whether the purchase transaction qualifies for a rebate, determining a rebate value based on the purchase transaction and the rebate, activating a rebate value in a rebate card account associated with a rebate card based on the determining action, and delivering the rebate card to a customer of the one or more products during the purchase transaction.
Owner:E2INTERACTIVE INC D B A E2INTERACTIVE
Method and system for securing a third party payment electronic transaction
InactiveUS8290876B1Improve securityReduce fraudPoint-of-sale network systemsComputer securityThird party
Owner:SDP DEV
Call receiving method and apparatus having two-way text messaging and automatic retrieval of call numbers making calls to apparatus
InactiveUS7005963B1Reduce fraudInterconnection arrangementsAccounting/billing servicesPagerMessage passing
A system and method for a call receiving pager apparatus, system and method utilizing a dedicated switch for providing proprietary access, billing functions and other enhanced features is described. The system utilizes a subscriber apparatus having pager or radiotelephone functions whereby a caller may call the apparatus and gain direct two-way communication with the subscriber. The caller is billed for the communication. A call receiving pager apparatus, system and method which enables two-way text messaging as well as the storage, retrieval, and recall of telephone numbers making calls to the pager apparatus where the recalls are made by way of sending a data package to the stored caller number is described. The subscriber is unable to initiate any real time two-way communication with the outgoing connection.
Owner:LBT IP LLC
Systems and methods for authentication of electronic transactions
InactiveUS20050033702A1Reduce fraudIncrease reliabilityDigital data authenticationElectronic credentialsMulti-factor authenticationElectronic transaction
An online transaction system configured to implement authentication methods that allow for strong multi-factor authentication in online environments. The authentication methods can be combined with strong security methods to further ensure that the authentication process is secure. Further, the strong multi-factor authentication can be implemented with zero adoption dependencies through the implementation of automated enrollment methods.
Owner:U S ENCODE CORP
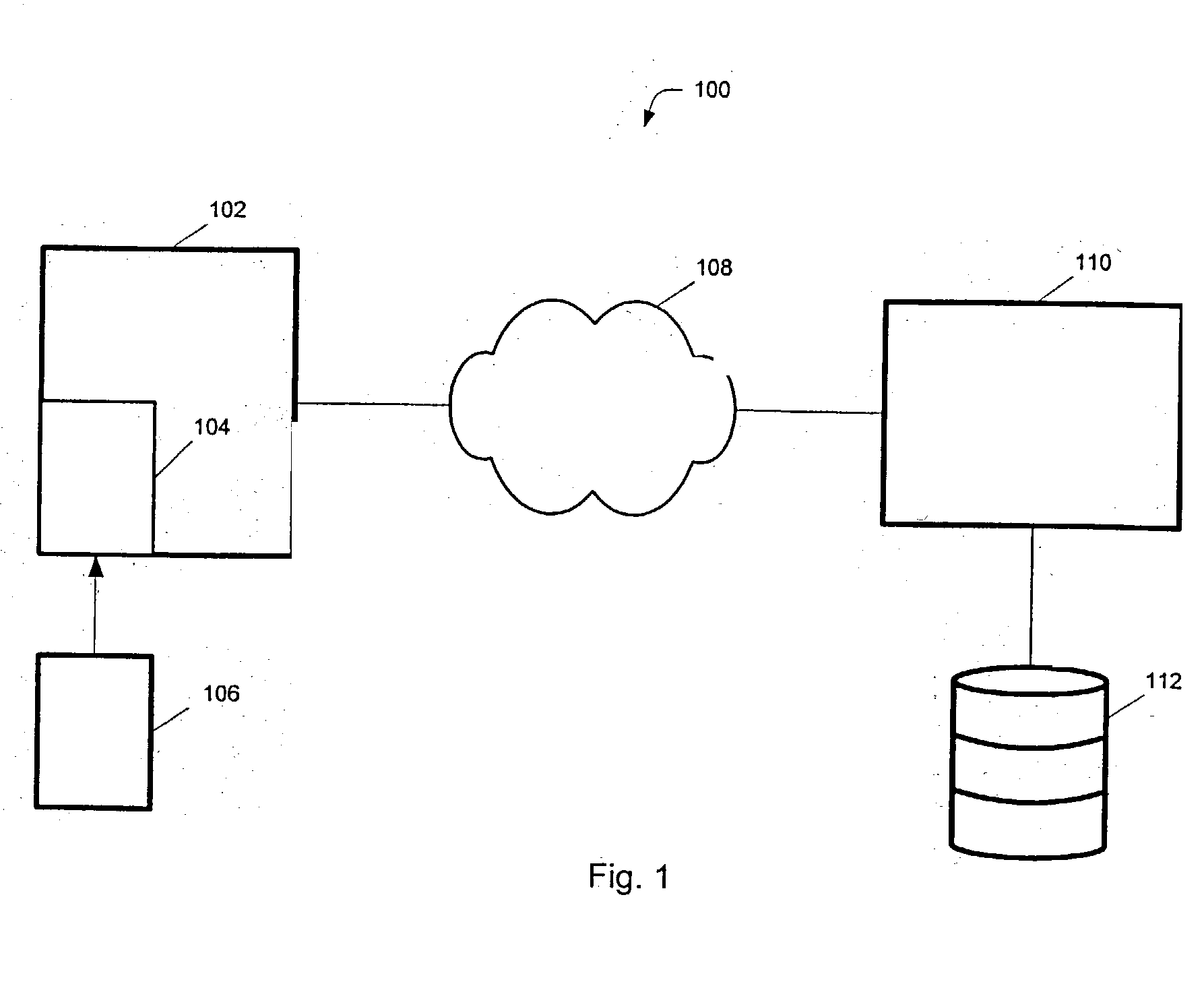
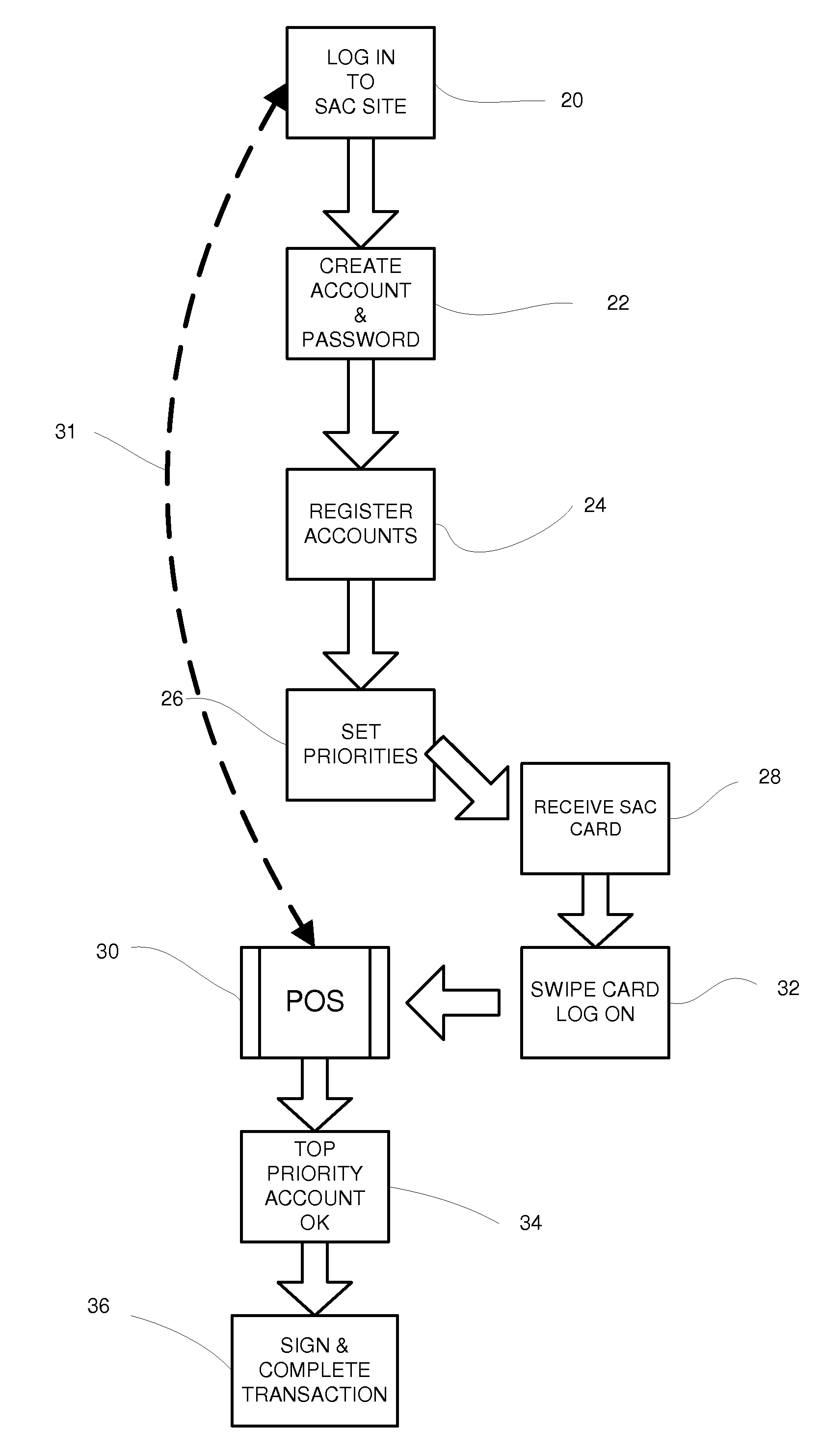
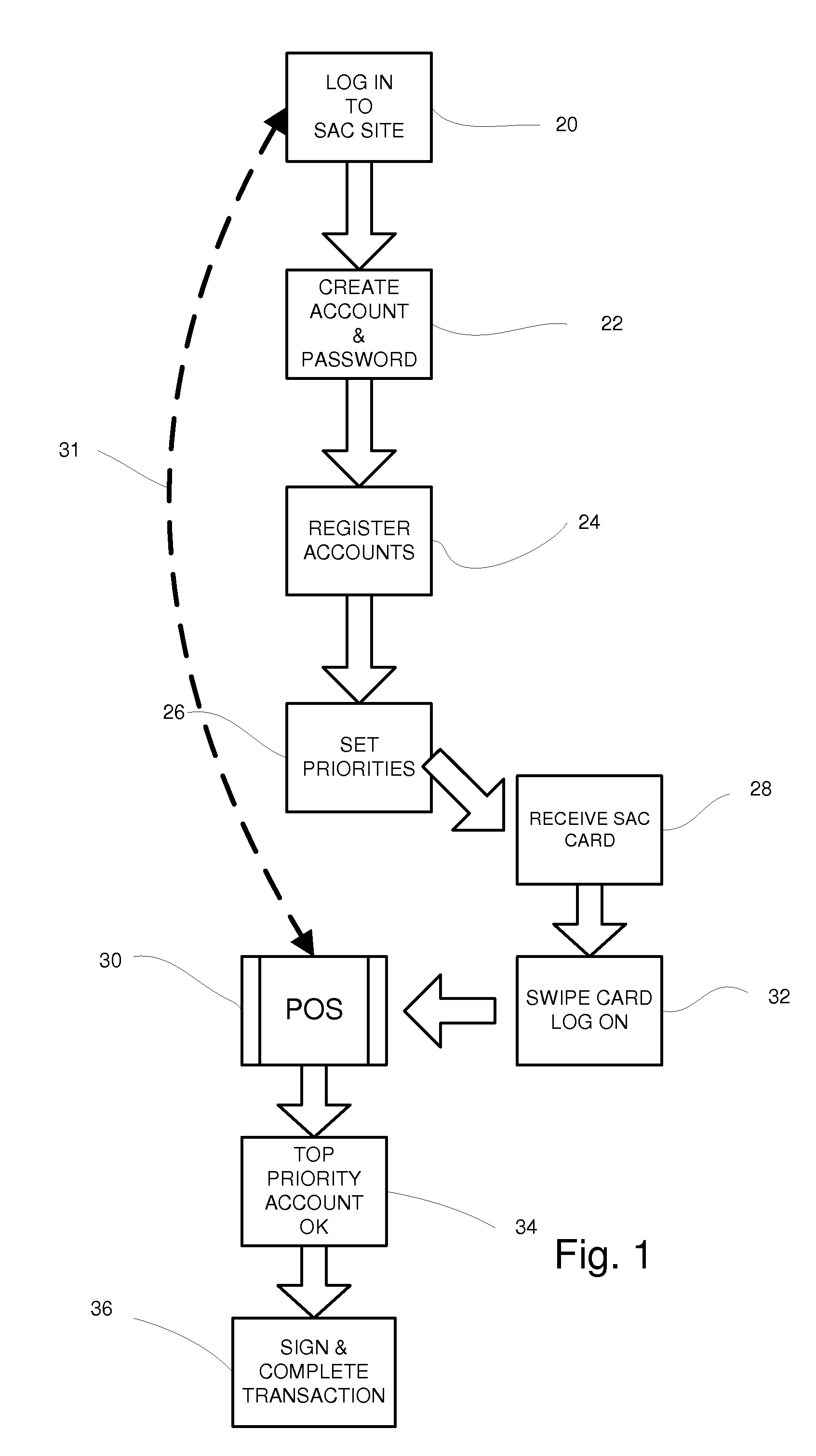
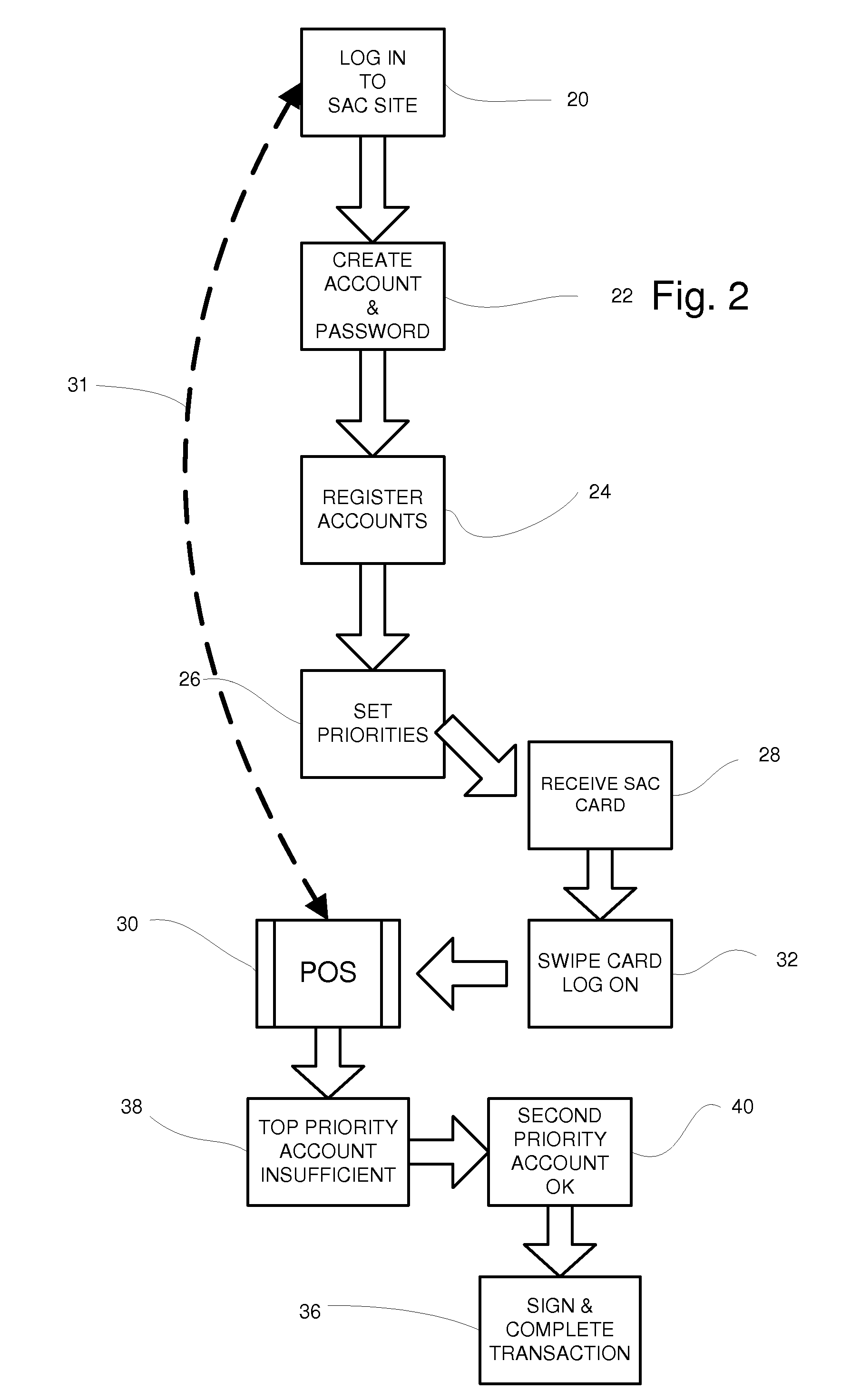
System for managing multiple credit accounts
In an improved method and system for managing consumer credit accounts a consumer registers a plurality of credit accounts through a secure web page establishing a priority of accounts in the process. The web page aggregates data from all of the registered accounts and a single credit card or device is issued to access the aggregated accounts. The single card is used at points of sale like an ordinary credit card except that it requires a password like a debit card. When a purchase is made the request is relayed to the credit account that has the top priority and sufficient available credit. A single card can access a plurality of separate credit accounts so there is no need to carry multiple cards. If the single card is stolen, it can be rapidly inactivated with a single call. It will not be necessary to cancel the underlying accounts.
Owner:SALLY JOSEPH
Method and apparatus for tracking package deliveries
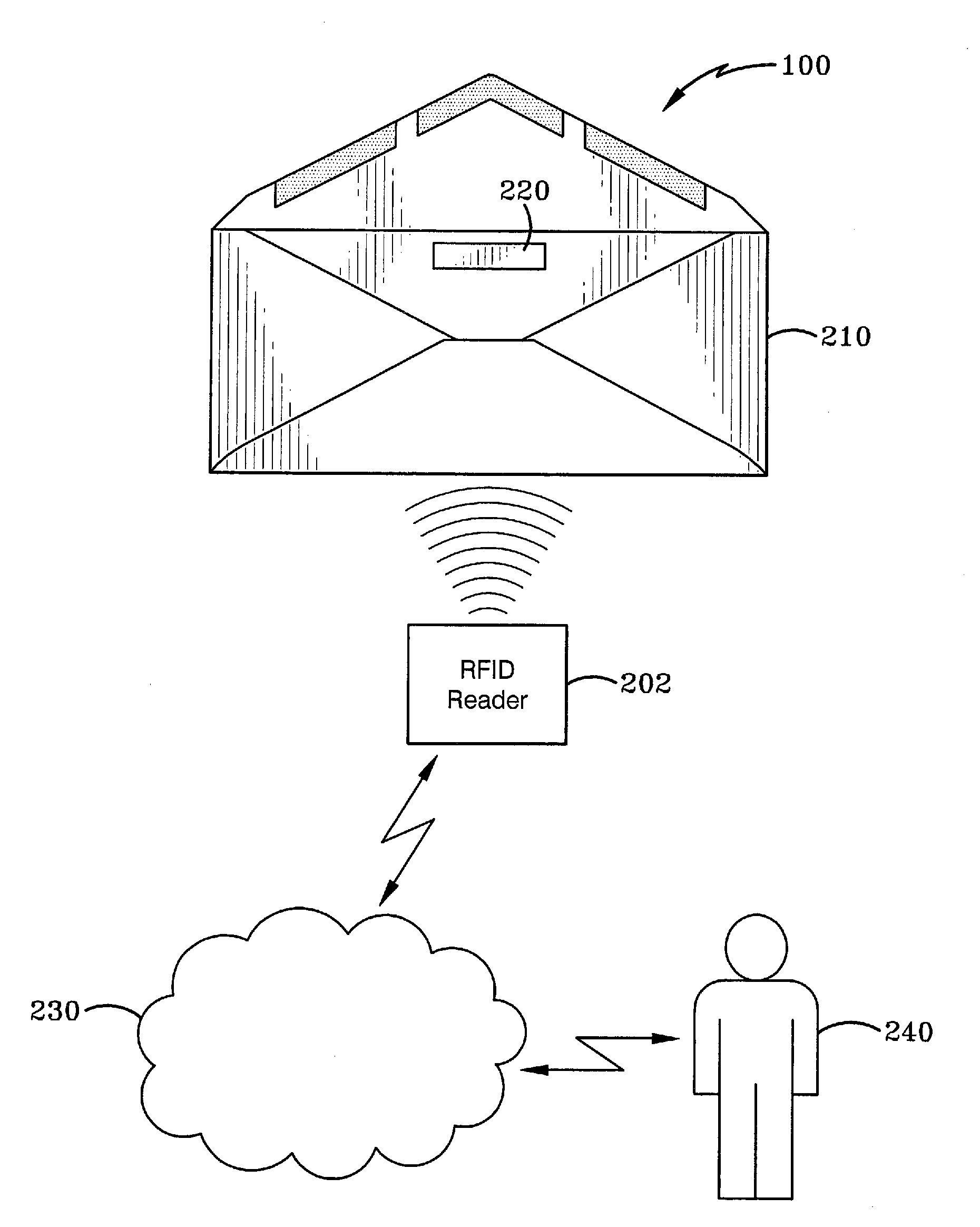
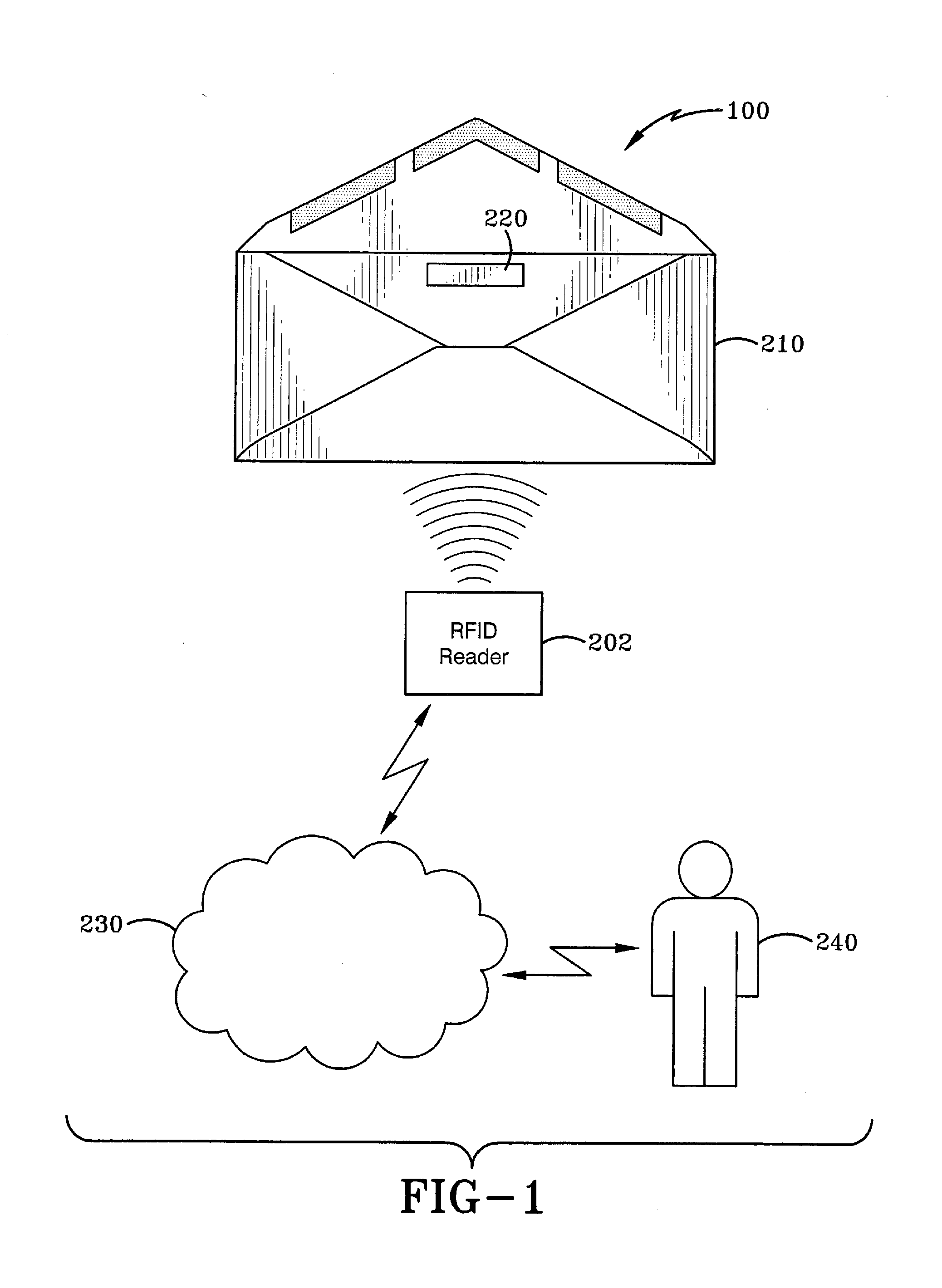
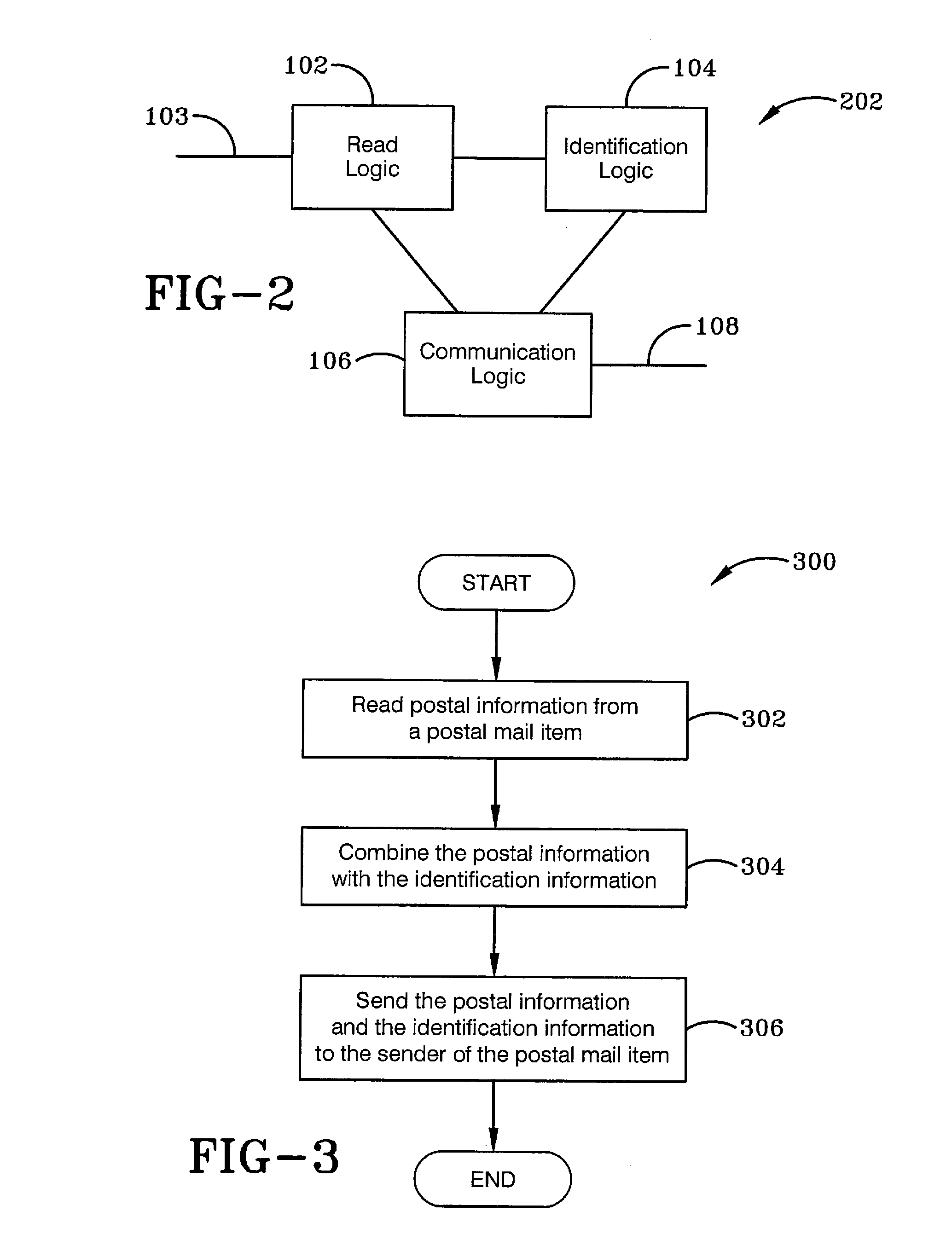
InactiveUS20130151434A1Speed up the processStreamlined operationLogisticsCommerceComputer hardwareConductive materials
A system and method for verifying receipt of a postal mail item mailed by a sender of the postal mail item is presented. Method detects whether a conductive material inside the parcel has been opened or not. The conductive material is a trace routed around the mail item in a way that makes it extremely difficult to open the mail item without breaking the conductive material. With an electronic device external to the parcel, the method energizes a communication device located in the parcel. Upon the communication device becoming energized, the method transmits from the communication device to the electronic device external to the parcel a signal that identifies if the conductive material in the parcel has been opened or not.
Owner:KITARU INNOVATIONS
Anti-fraud POS transaction system
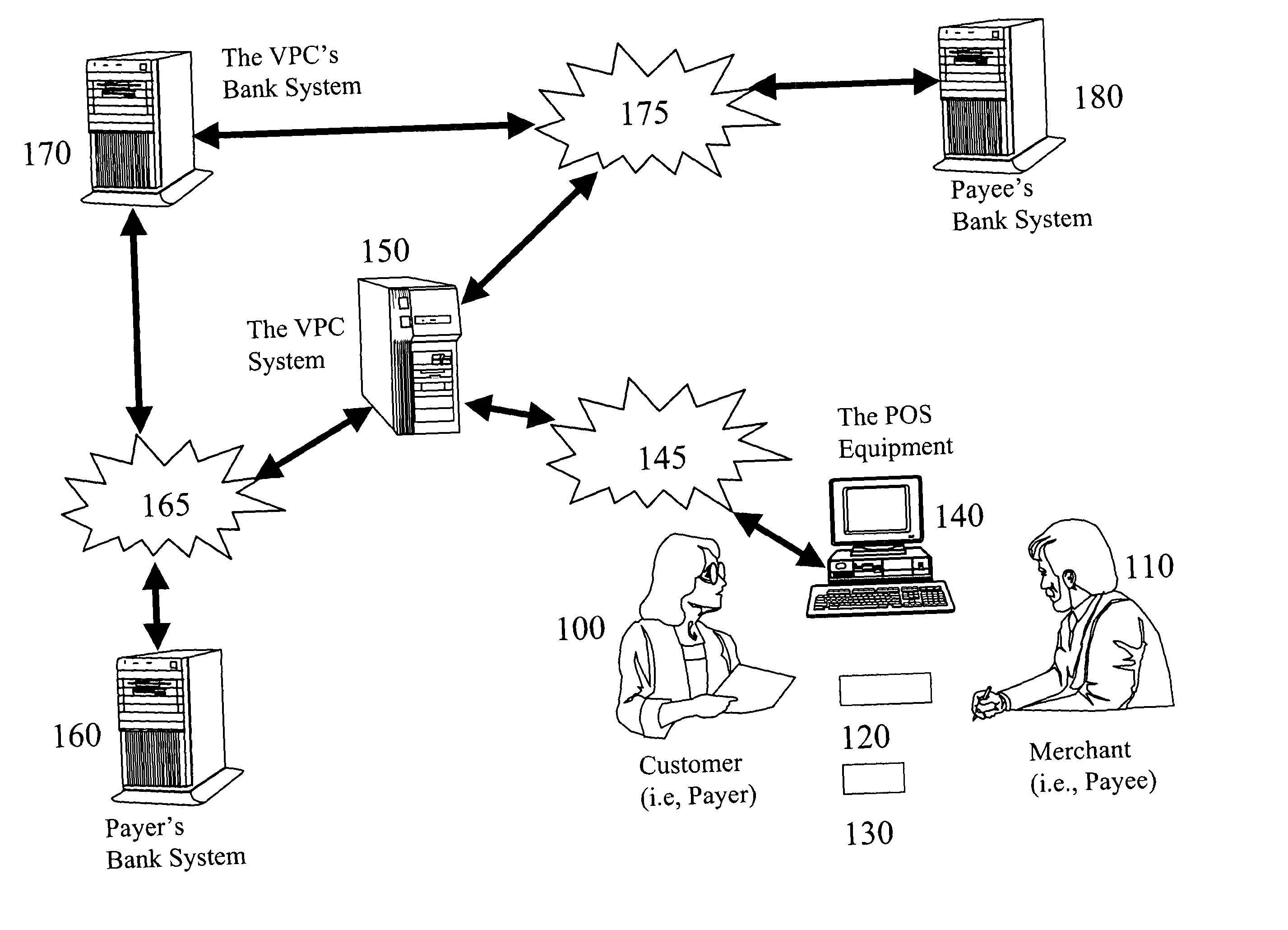
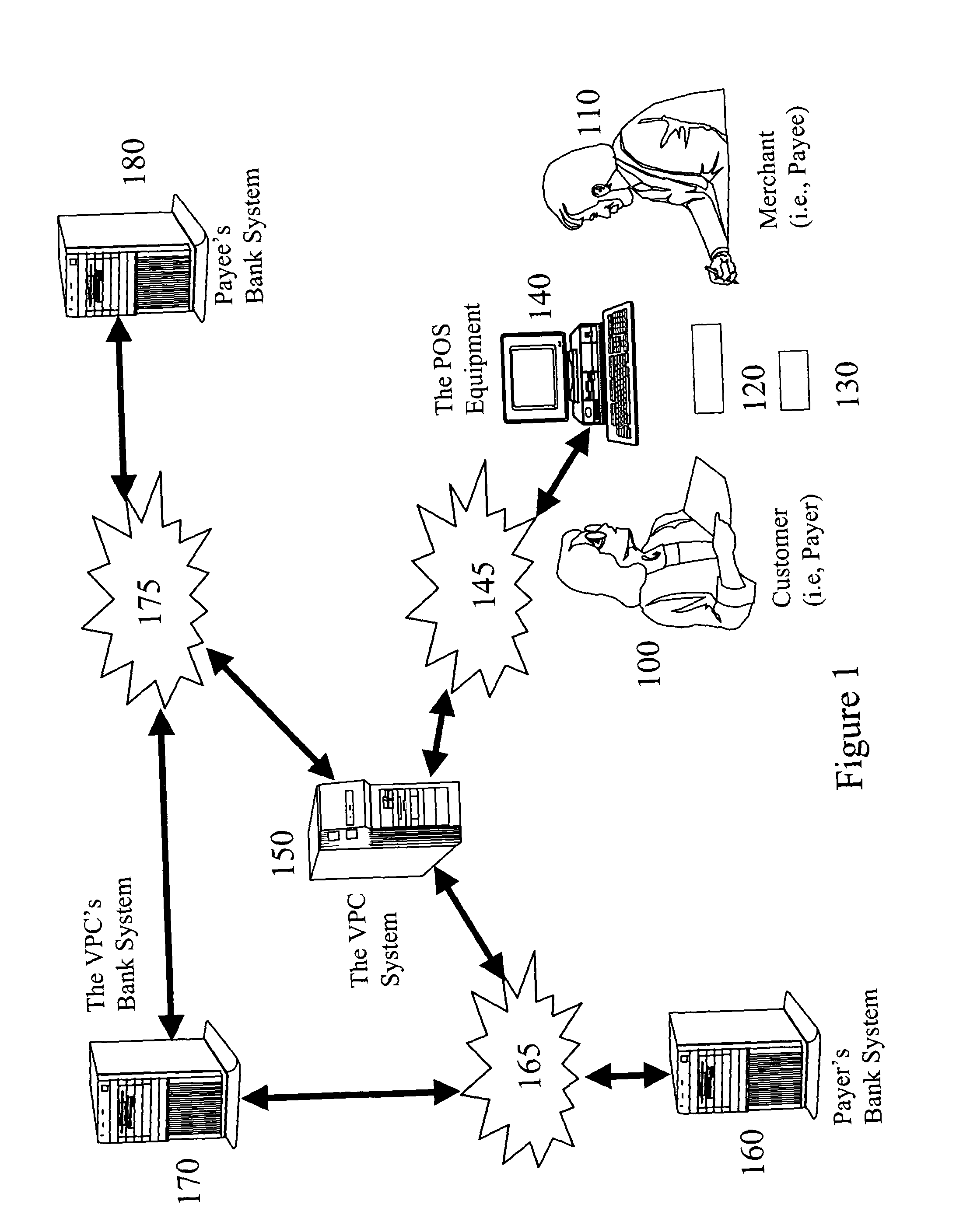
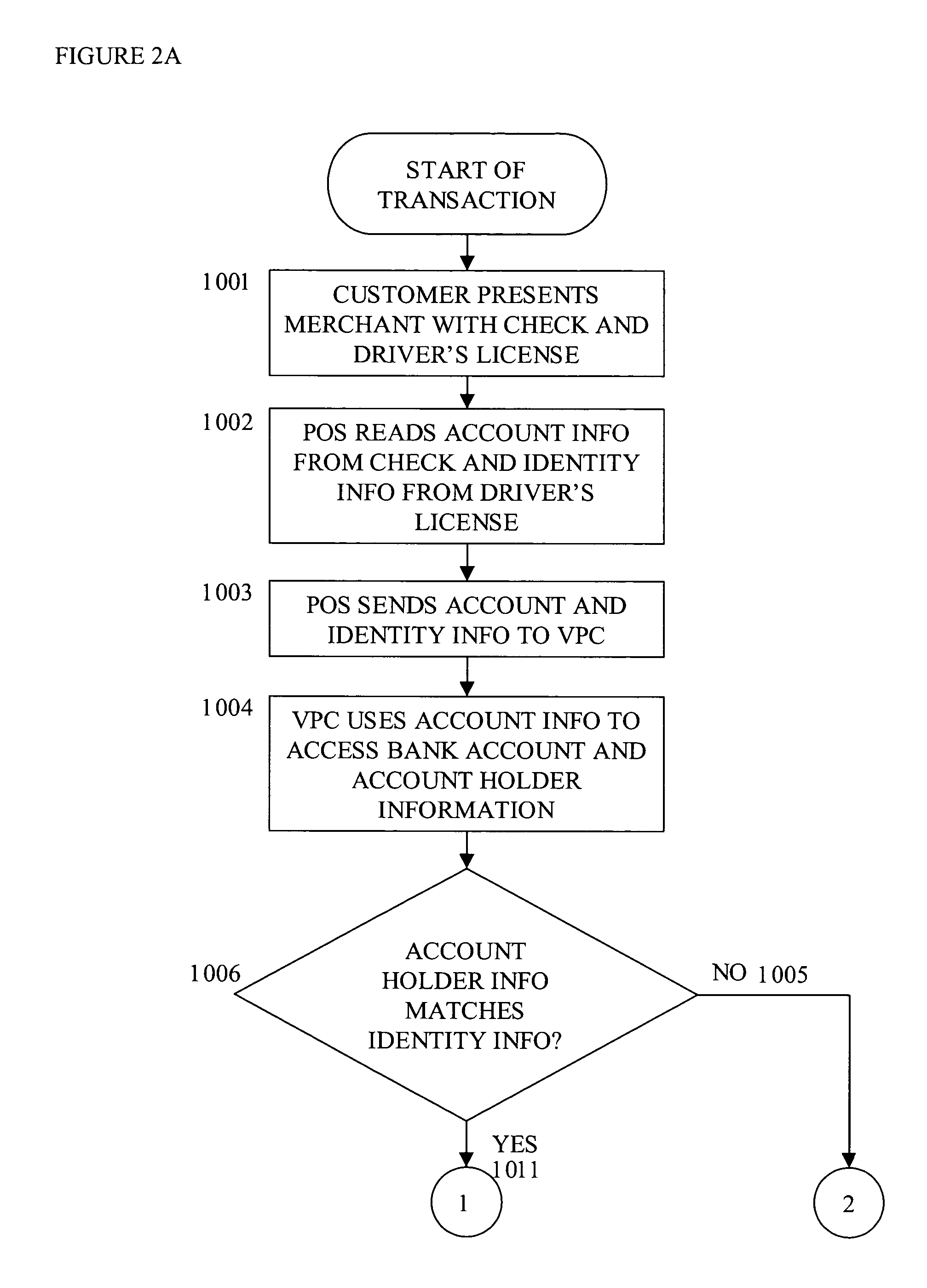
InactiveUS20040138955A1Reducing resultant financial lossReduce fraudPayment circuitsPoint-of-sale network systemsPayment transactionDebit card
Anti-fraud measures are provided for a point-of-sale transaction using various consumer-oriented financial instruments such as credit cards, debit cards, and checks. Through a network, the payer is authenticated by a machine-readable official identification document and the availability of funds is verified by the payer's financial institution before the transaction is completed and the funds are immediately secured during the transaction. The entire transaction is securely verified and maintained in such a way that no party has a chance to alter any part of the transaction.
Owner:SONG YUH SHEN +3
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com