Patents
Literature
280 results about "Multi-factor authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Multi-factor authentication (MFA) is an authentication method in which a computer user is granted access only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism: knowledge (something the user and only the user knows), possession (something the user and only the user has), and inherence (something the user and only the user is).
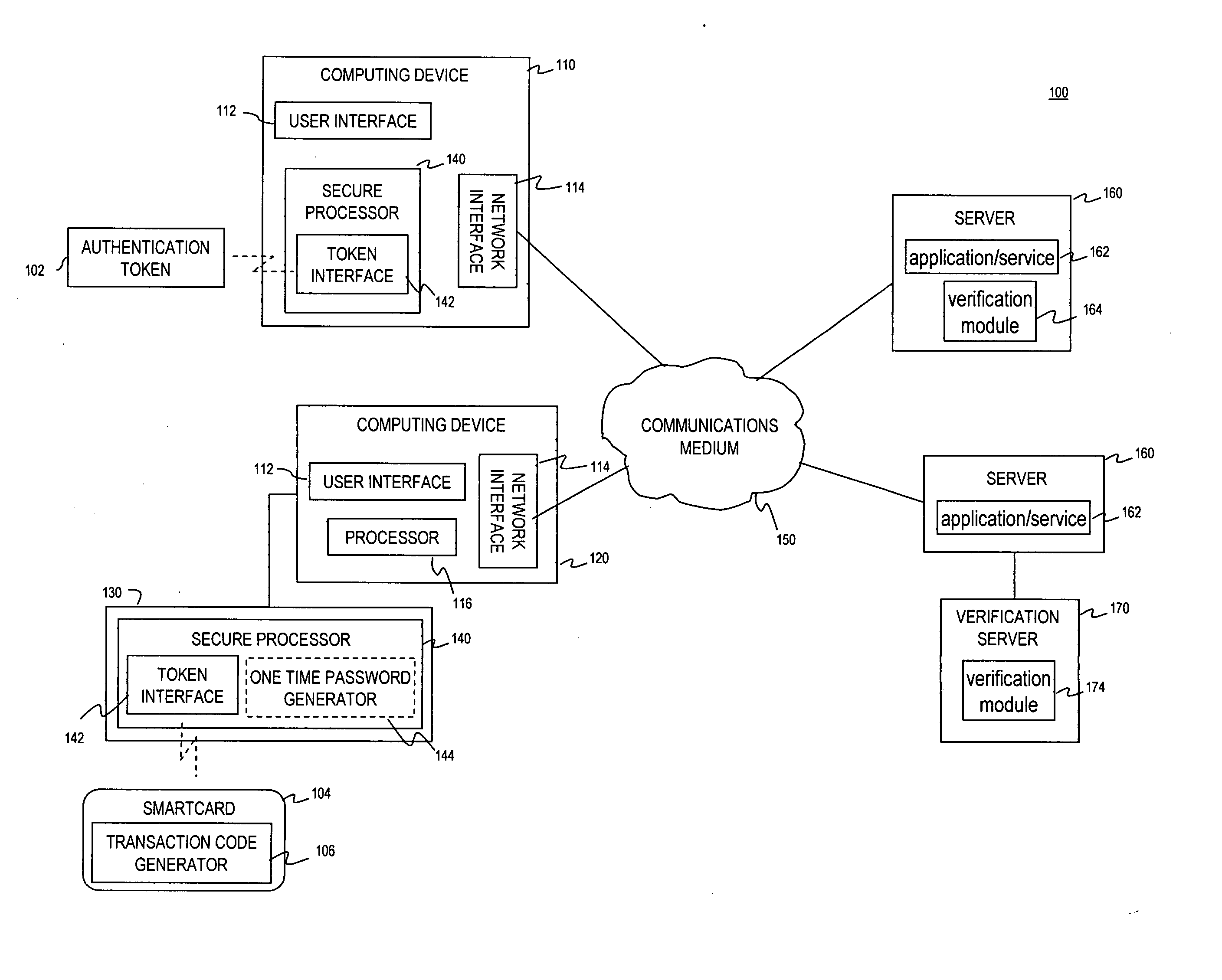
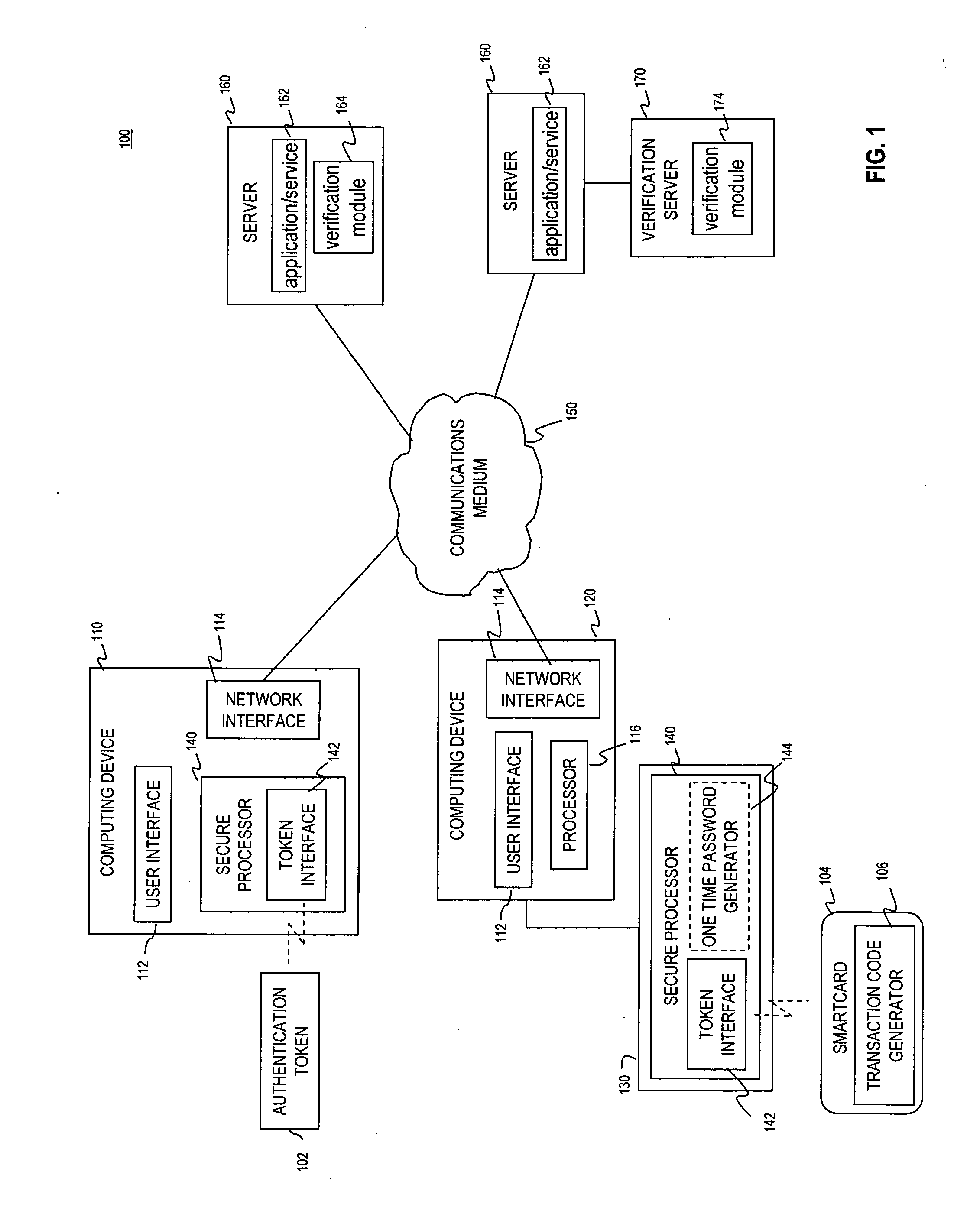
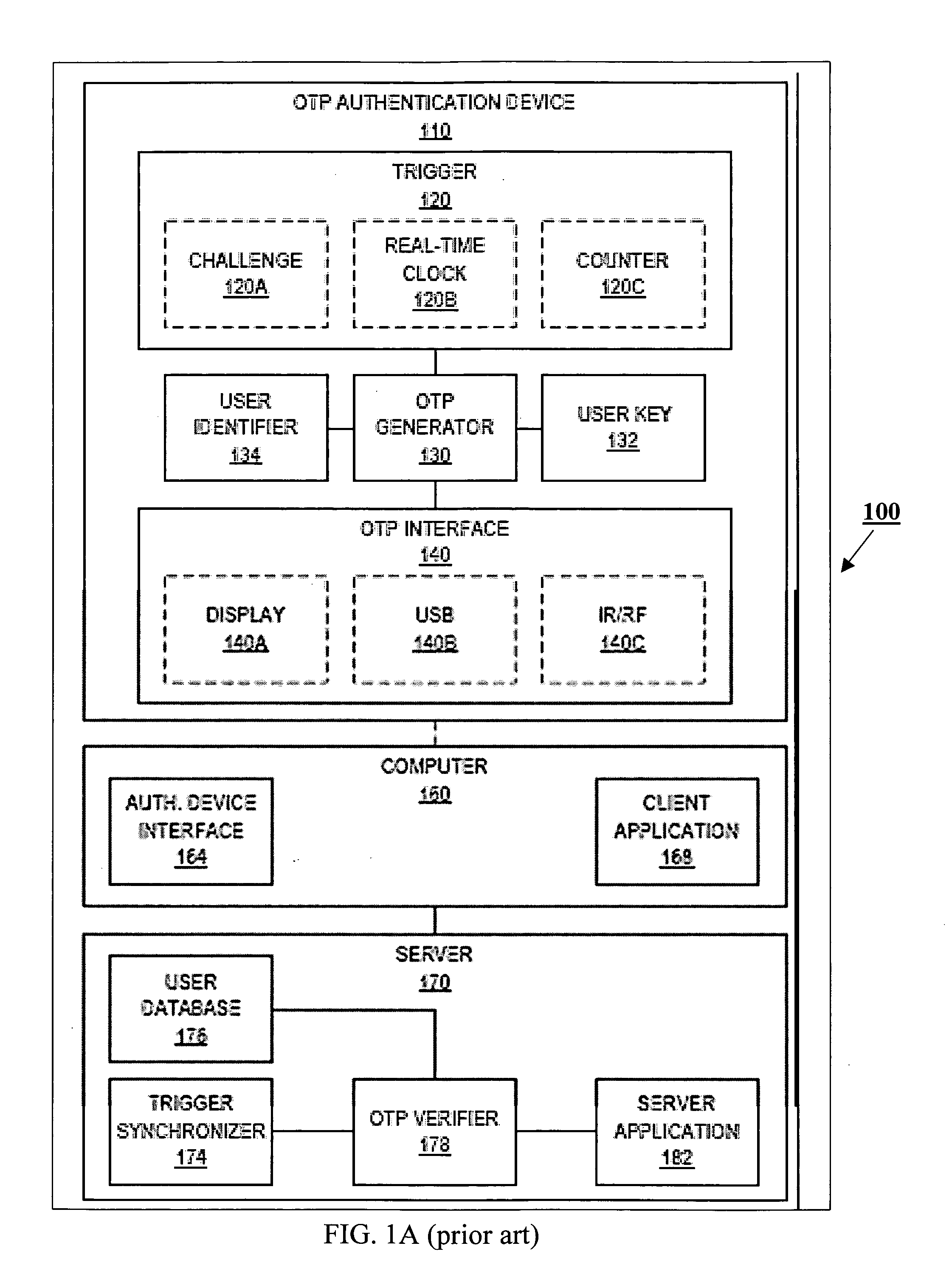
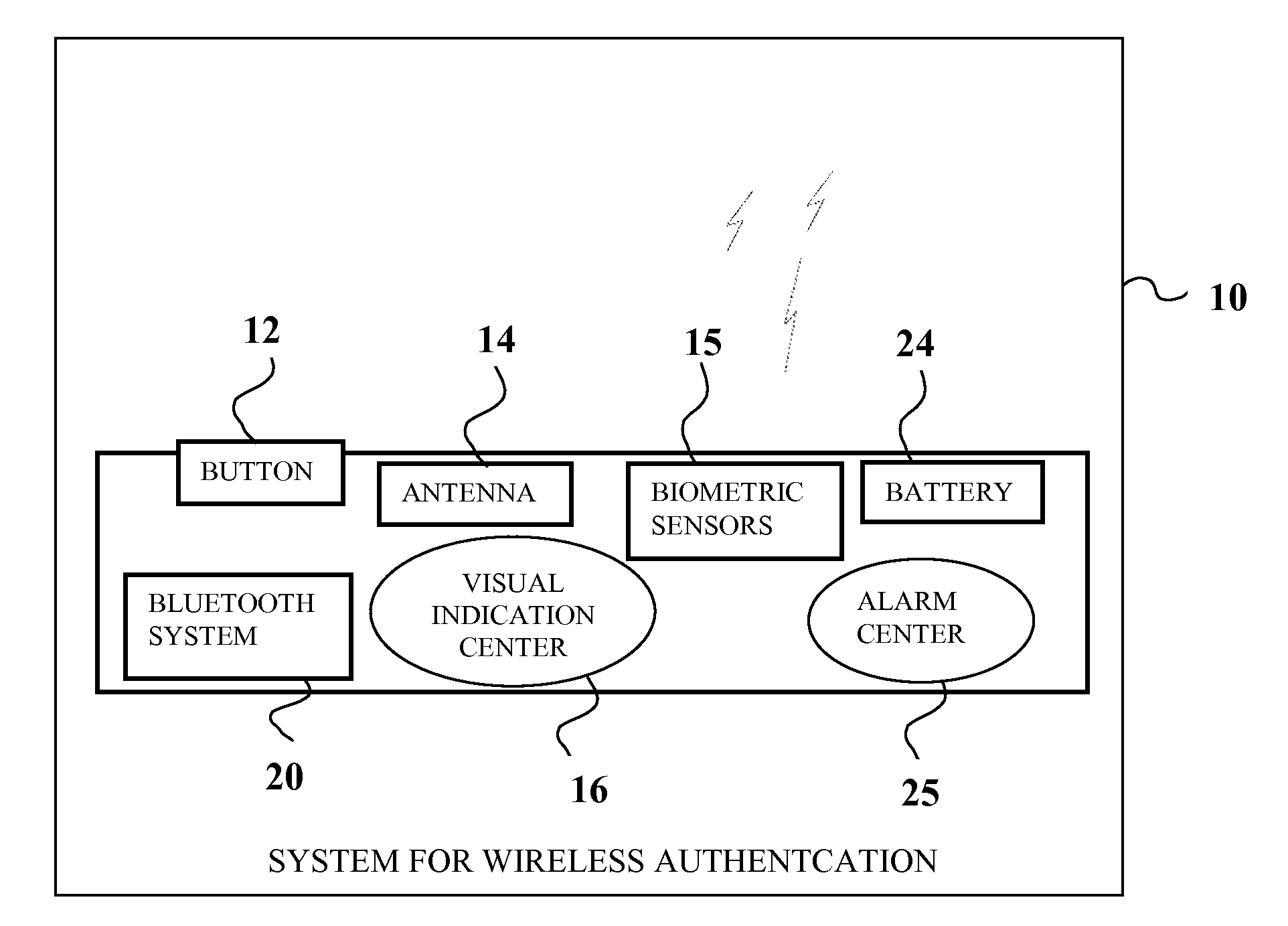
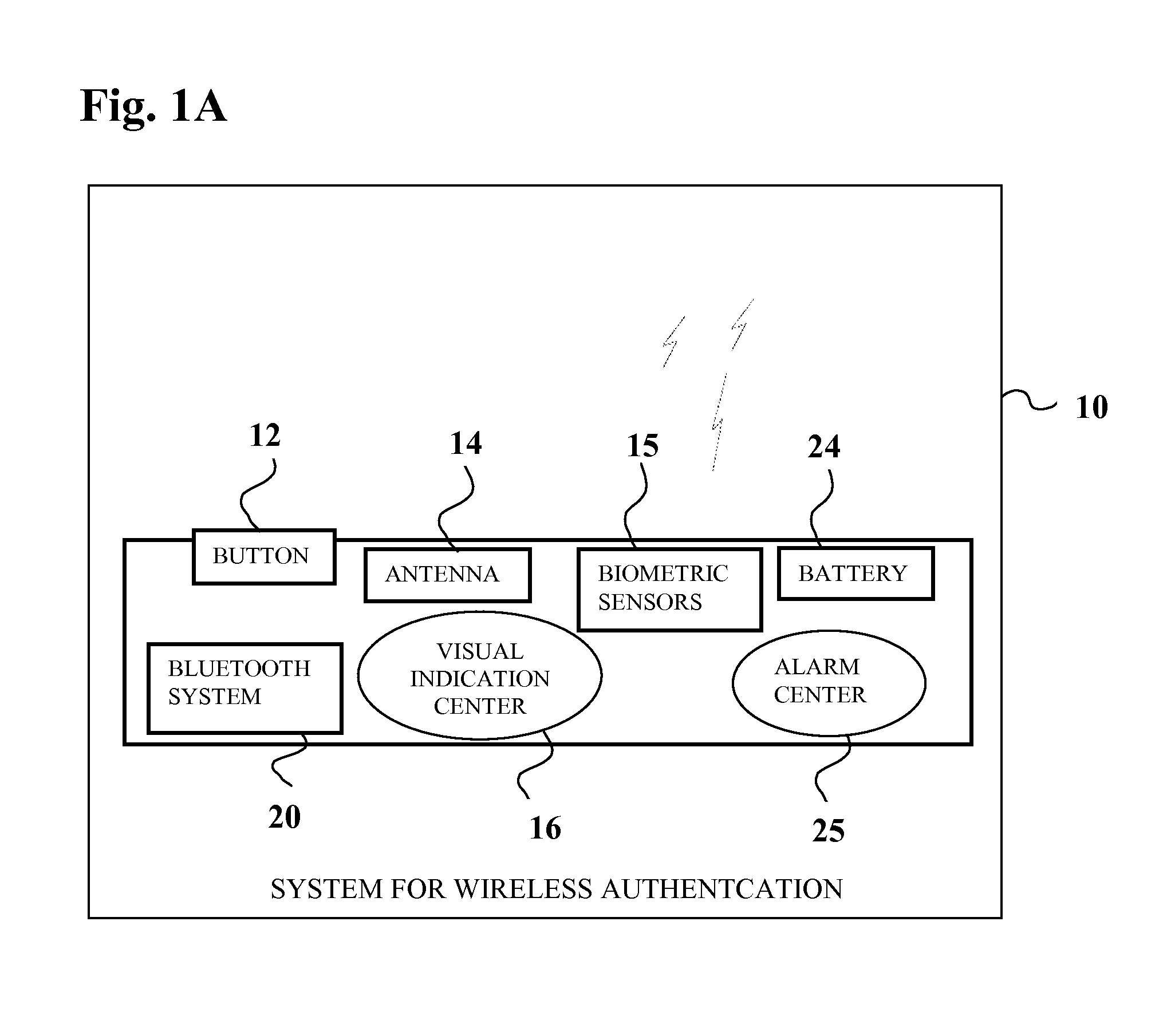
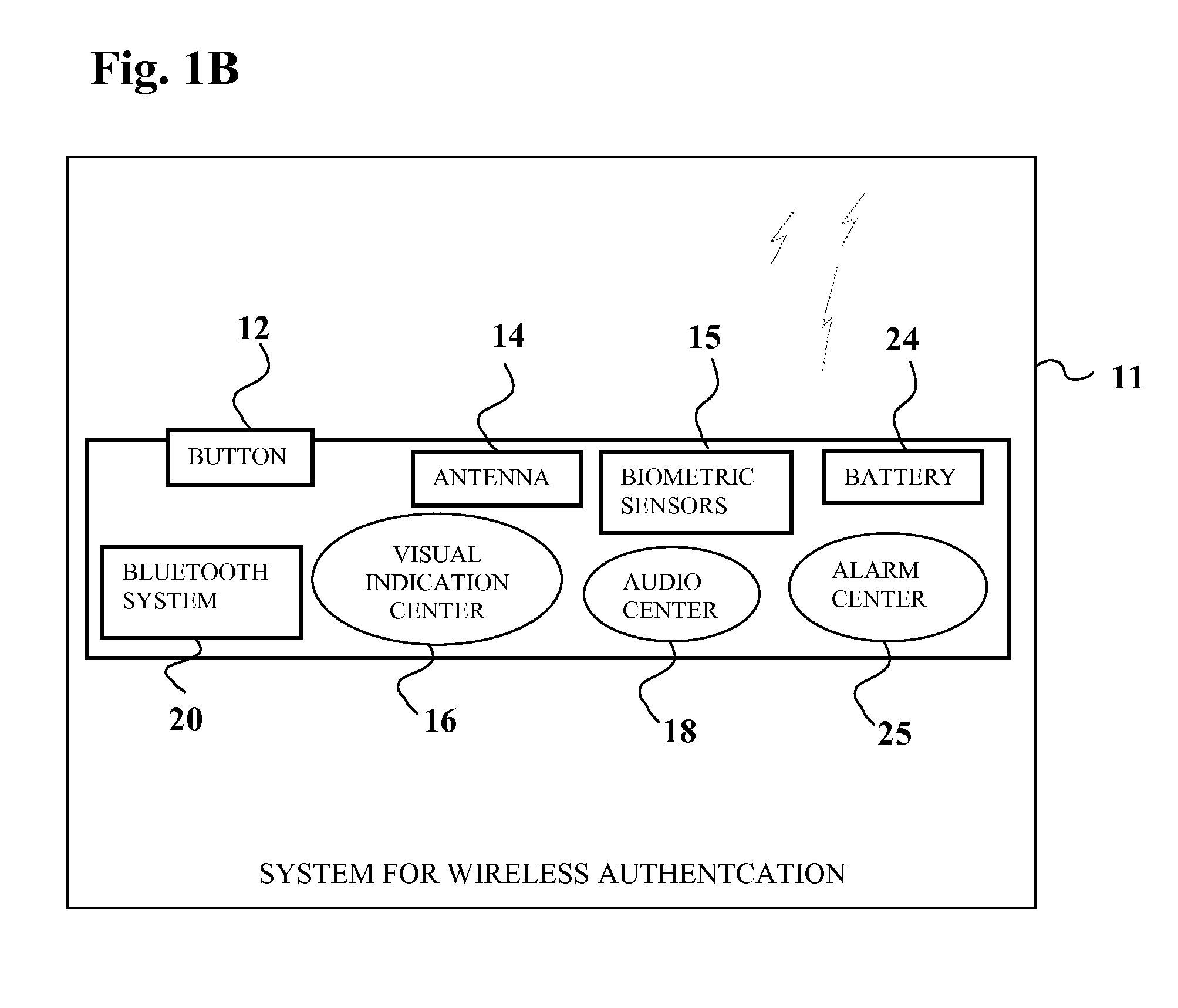
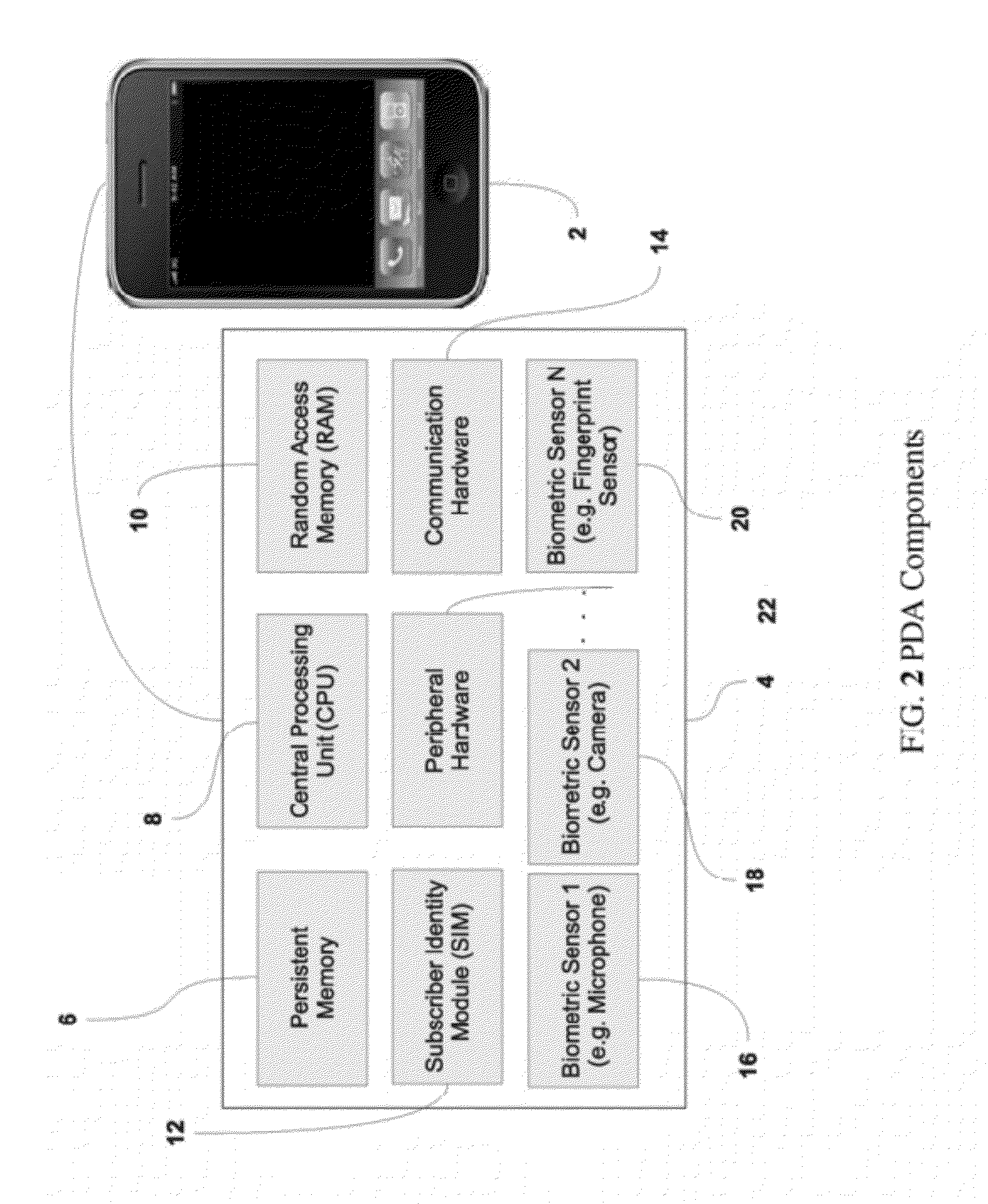
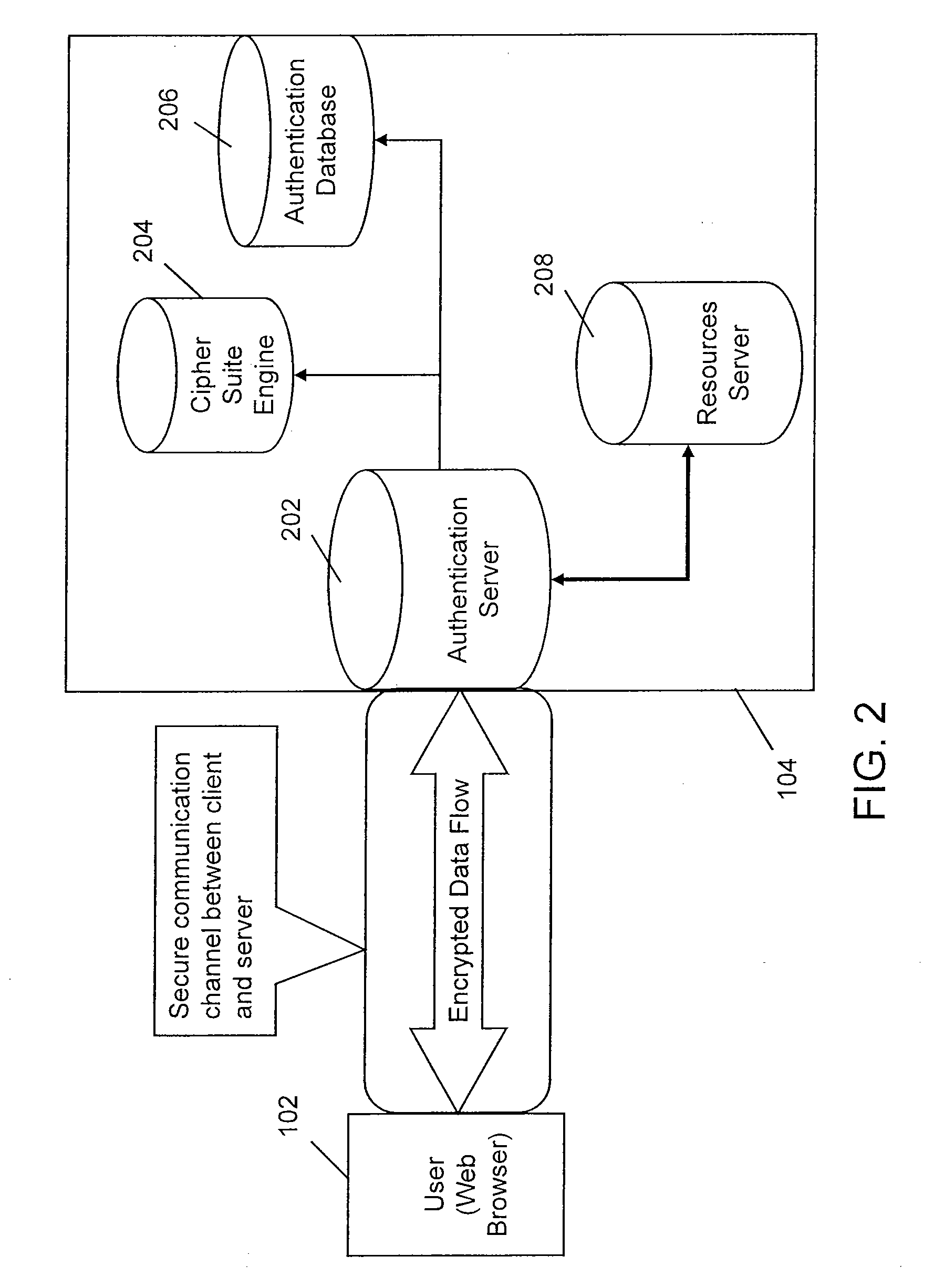
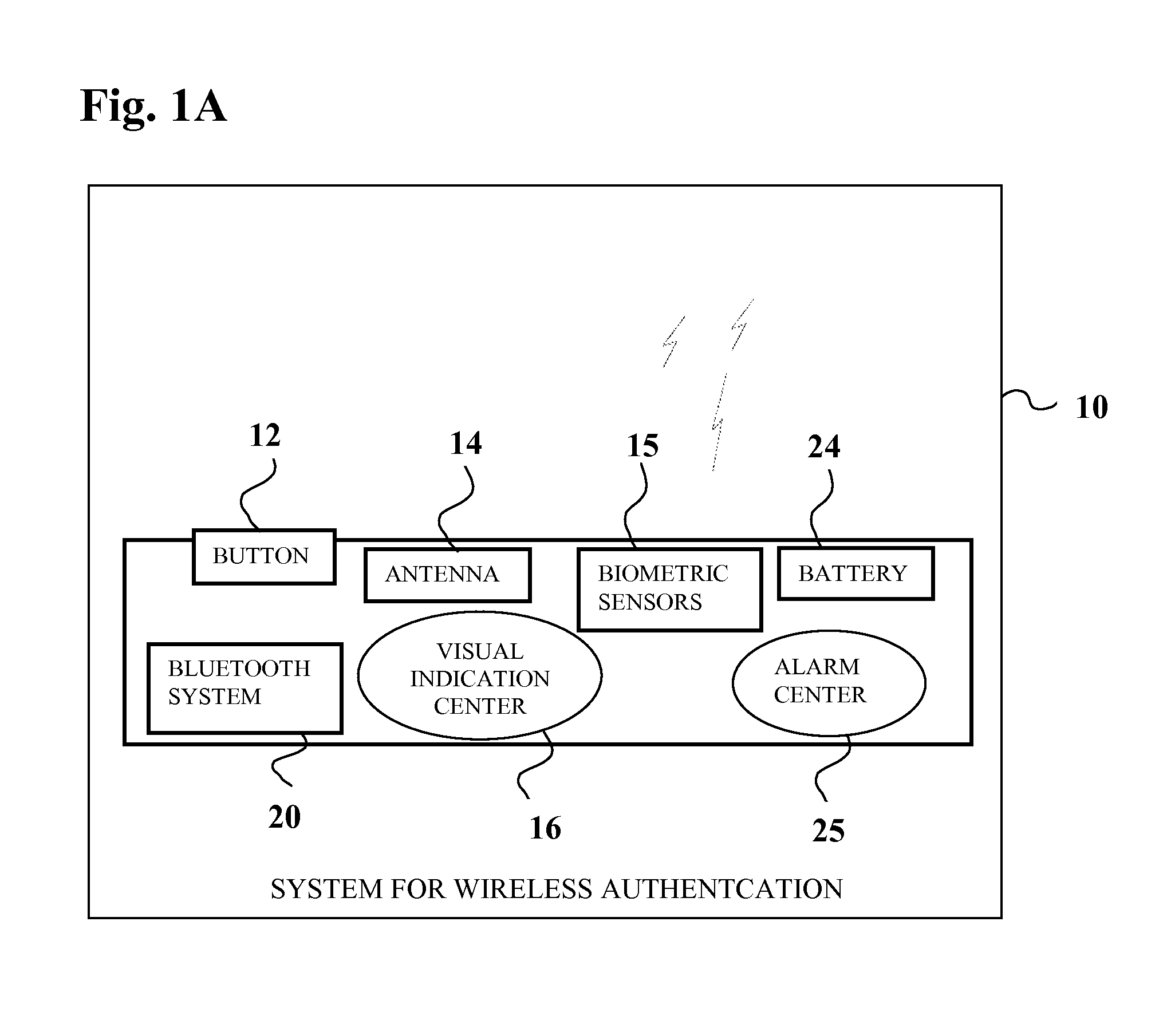
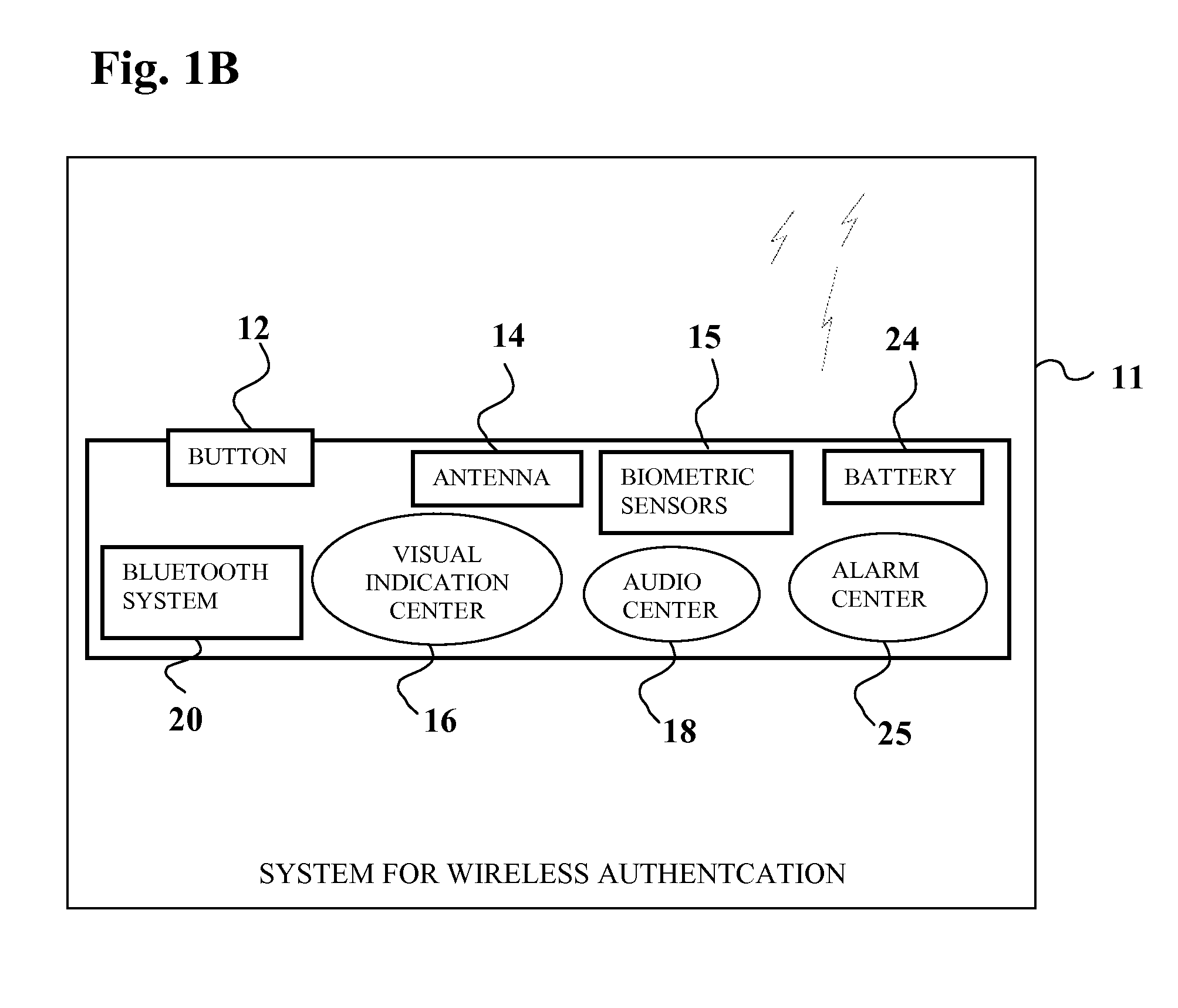
Multi-factor authentication system
InactiveUS20040187018A1Easy to understandUser identity/authority verificationUnauthorized memory use protectionPasswordUser identifier
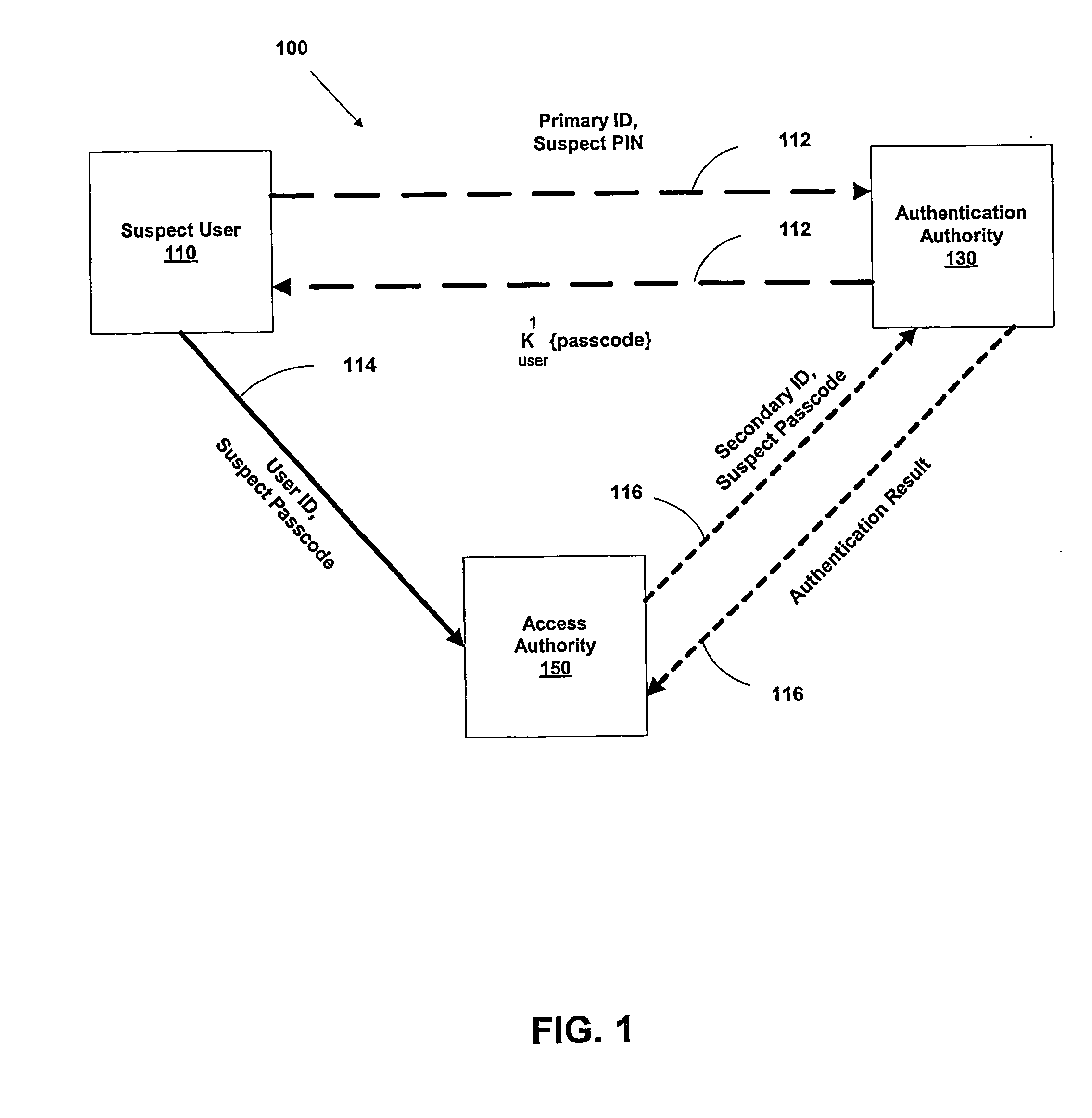
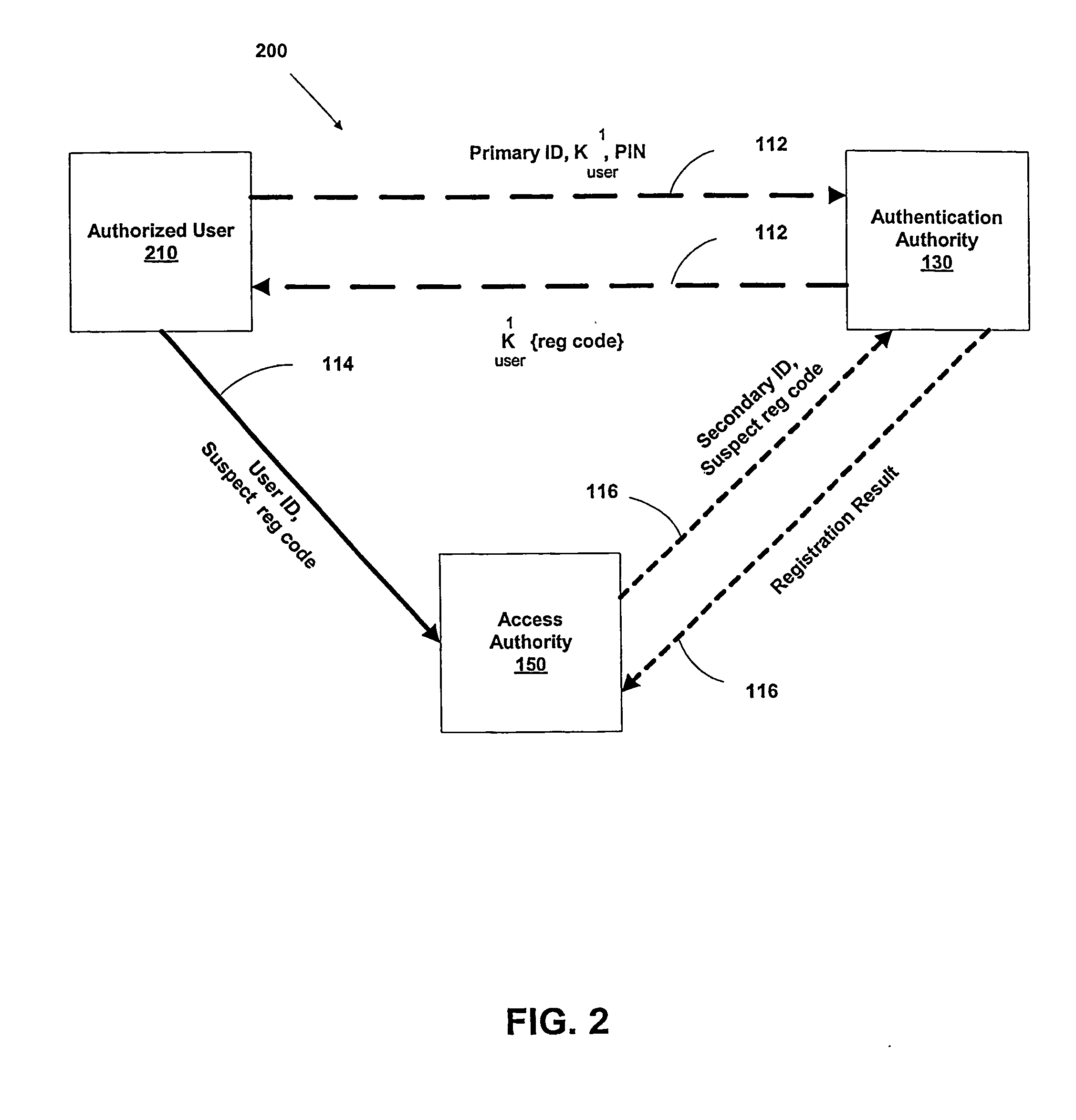
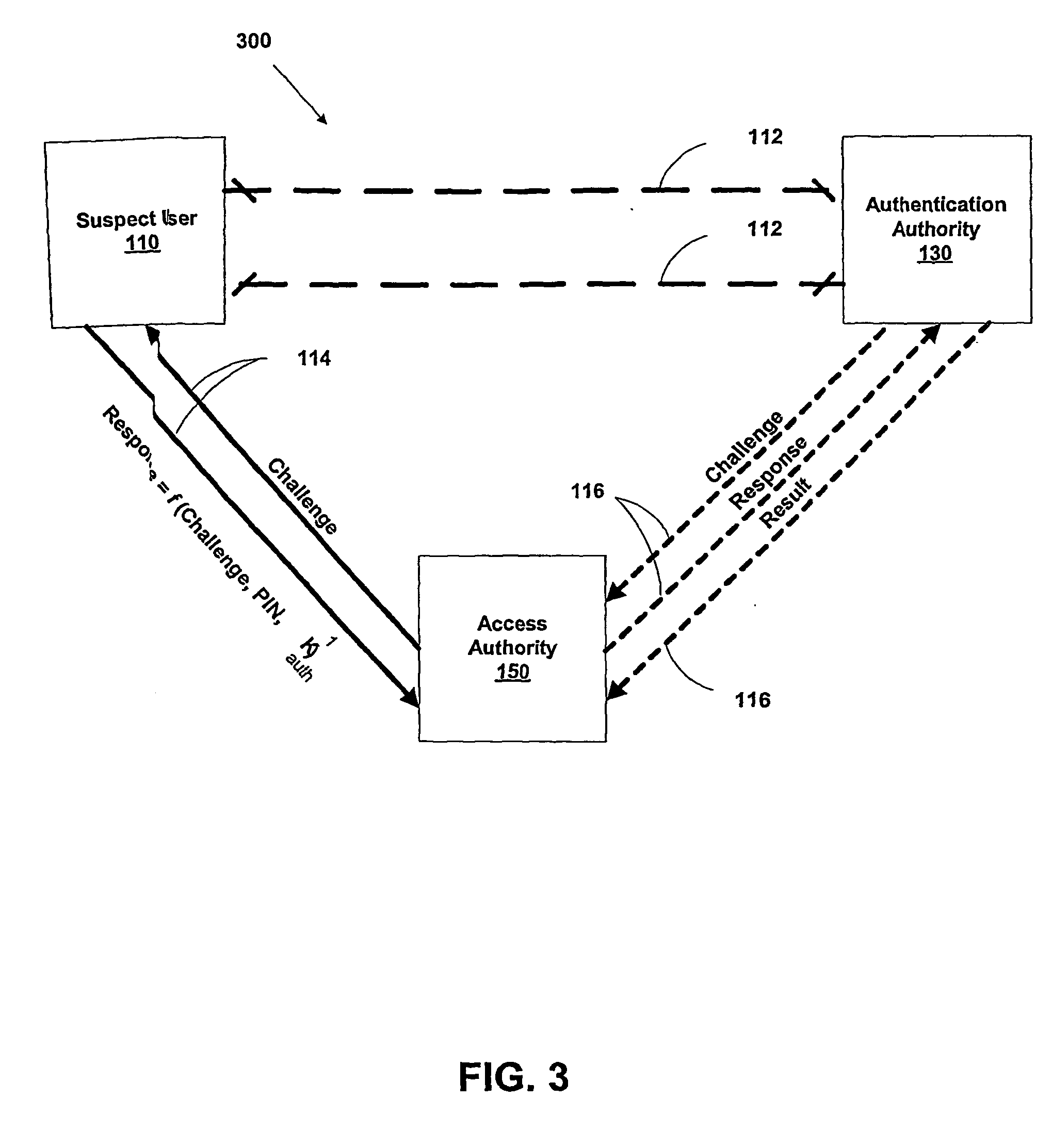
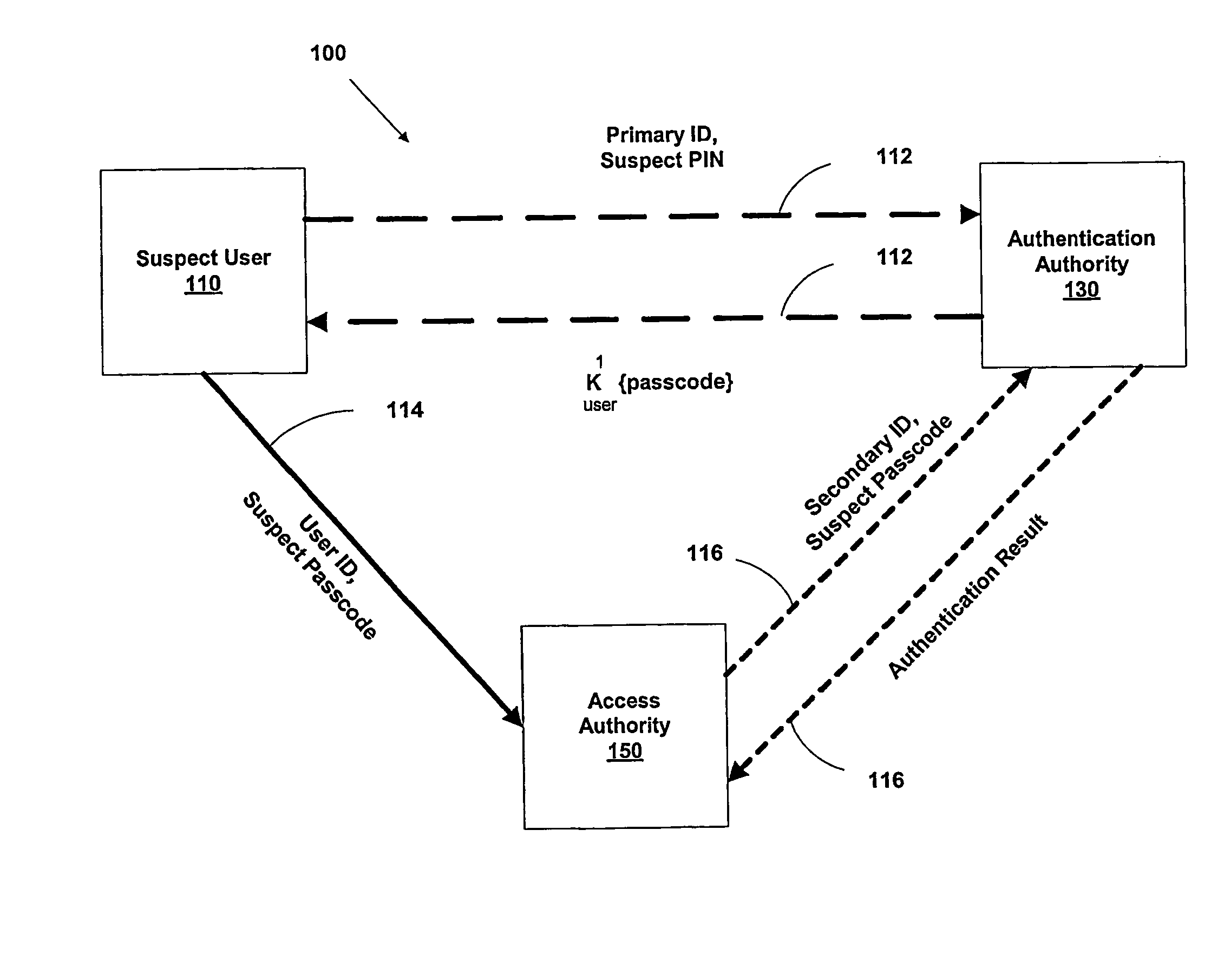
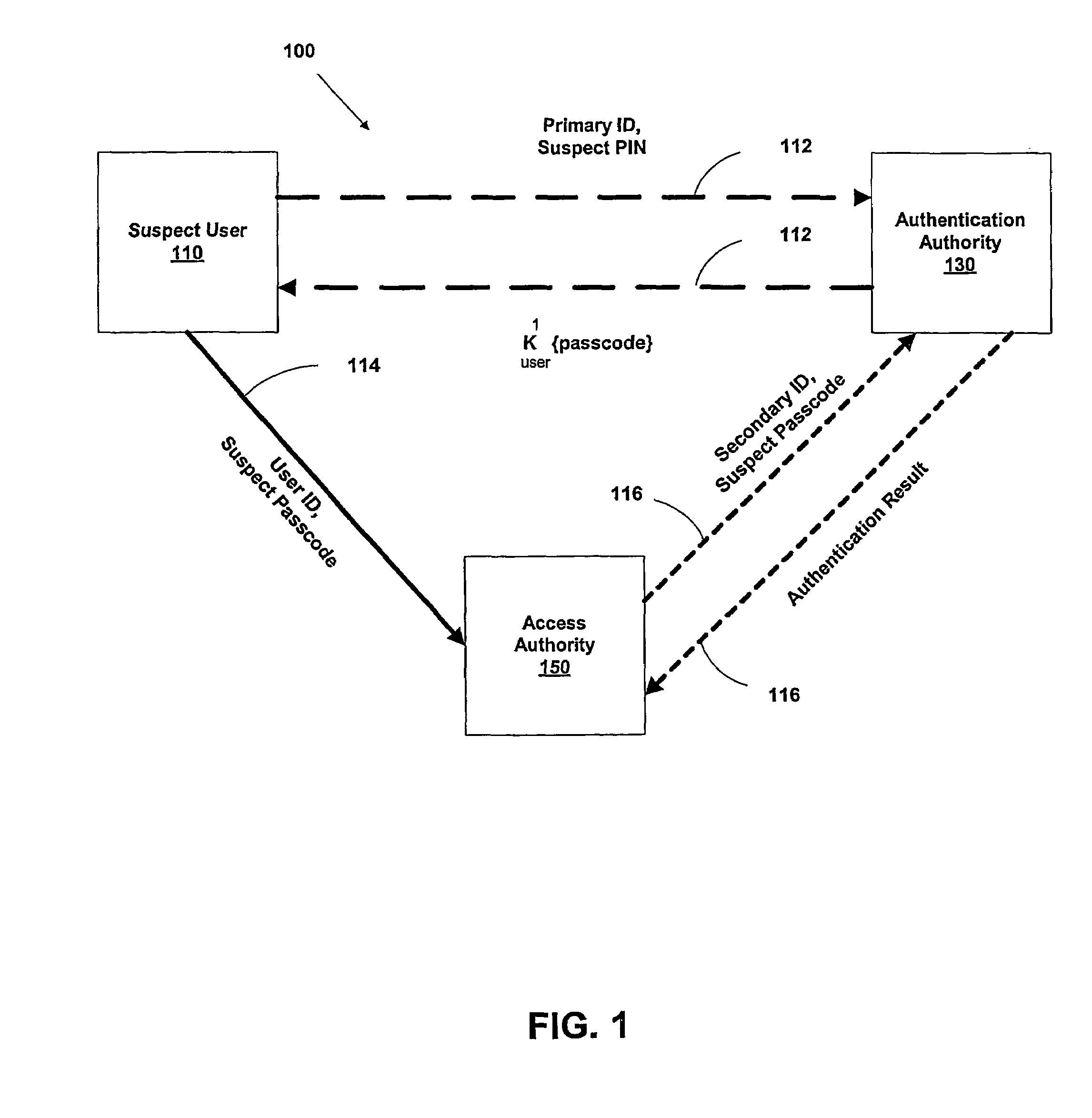
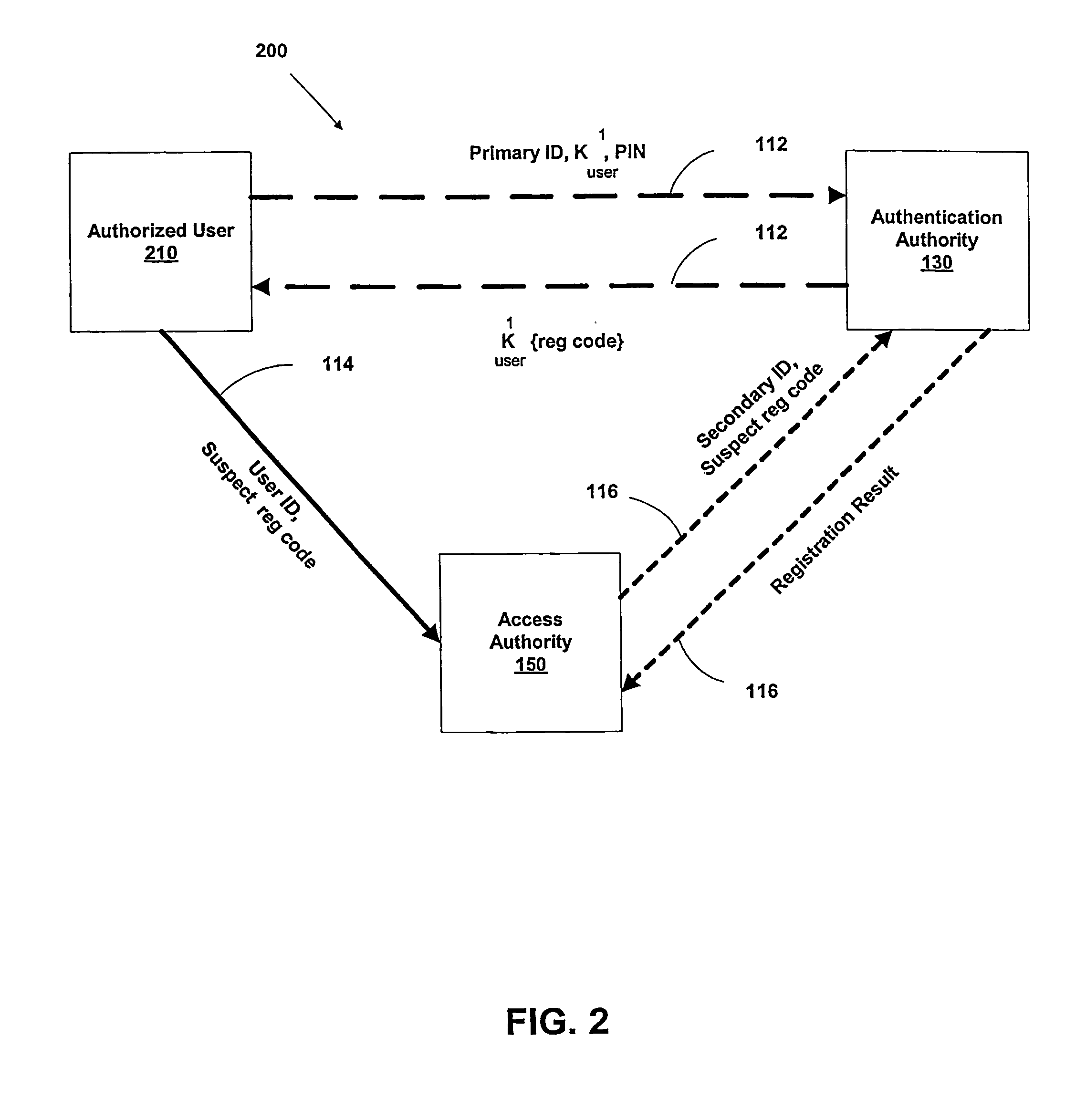
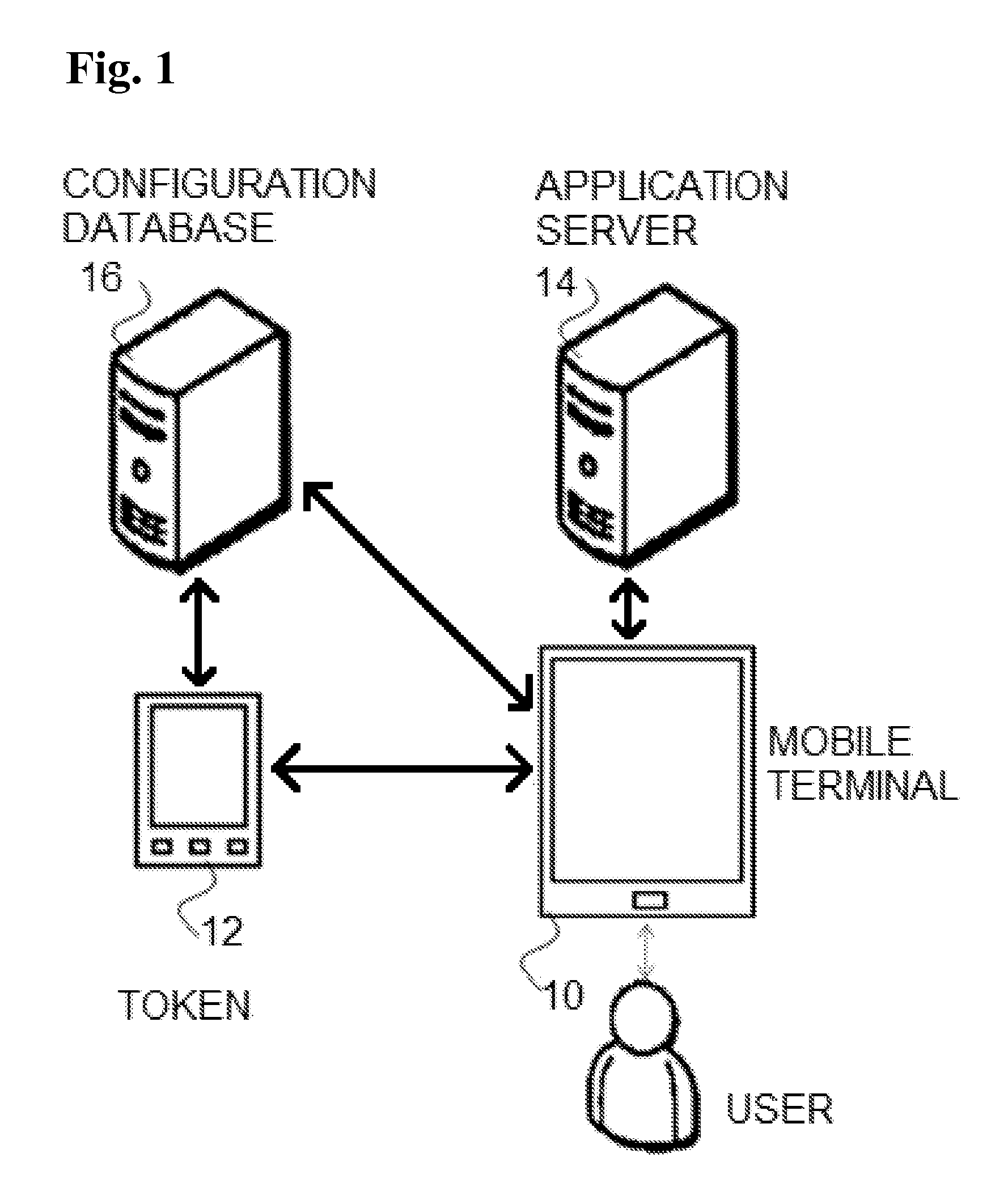
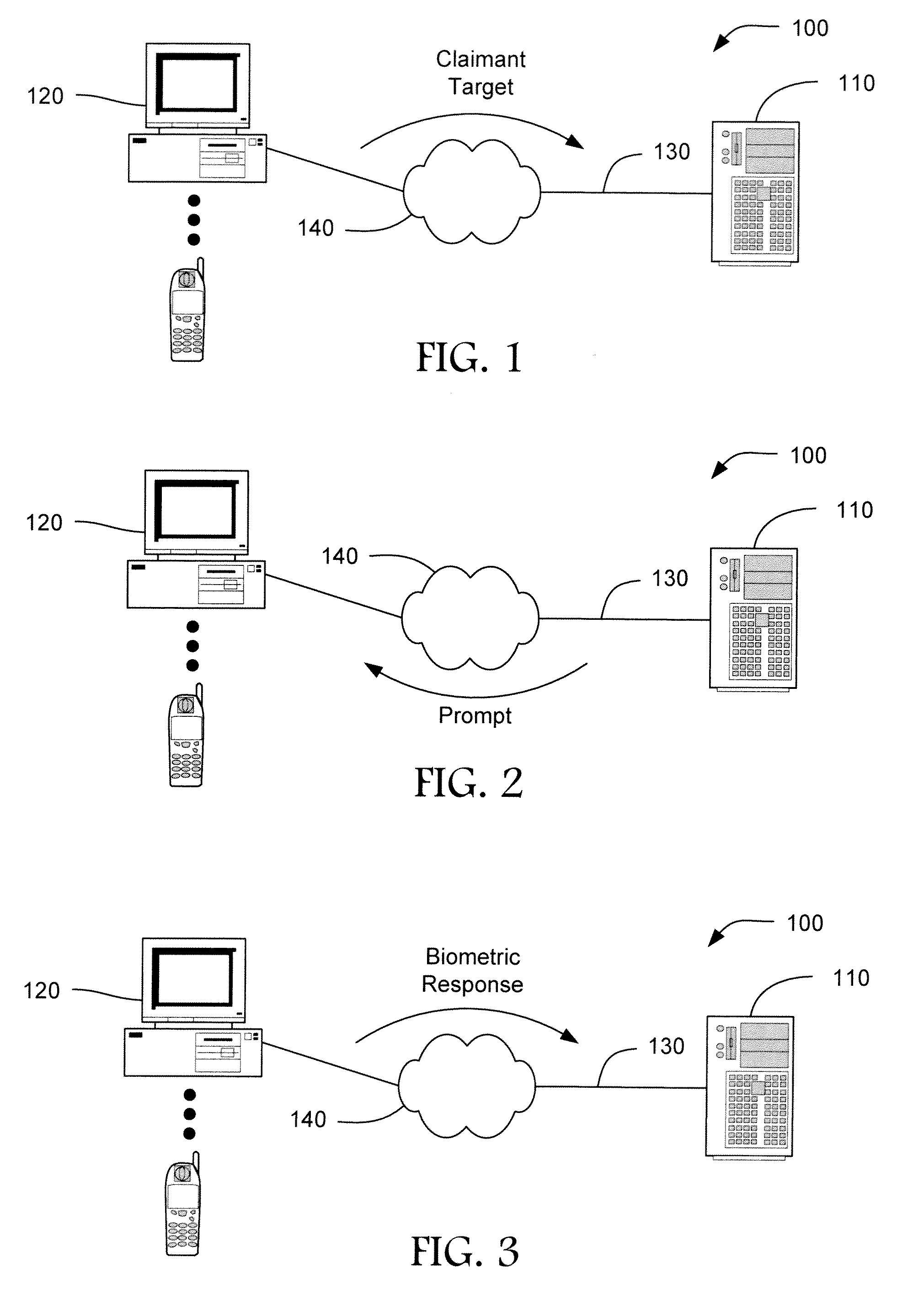
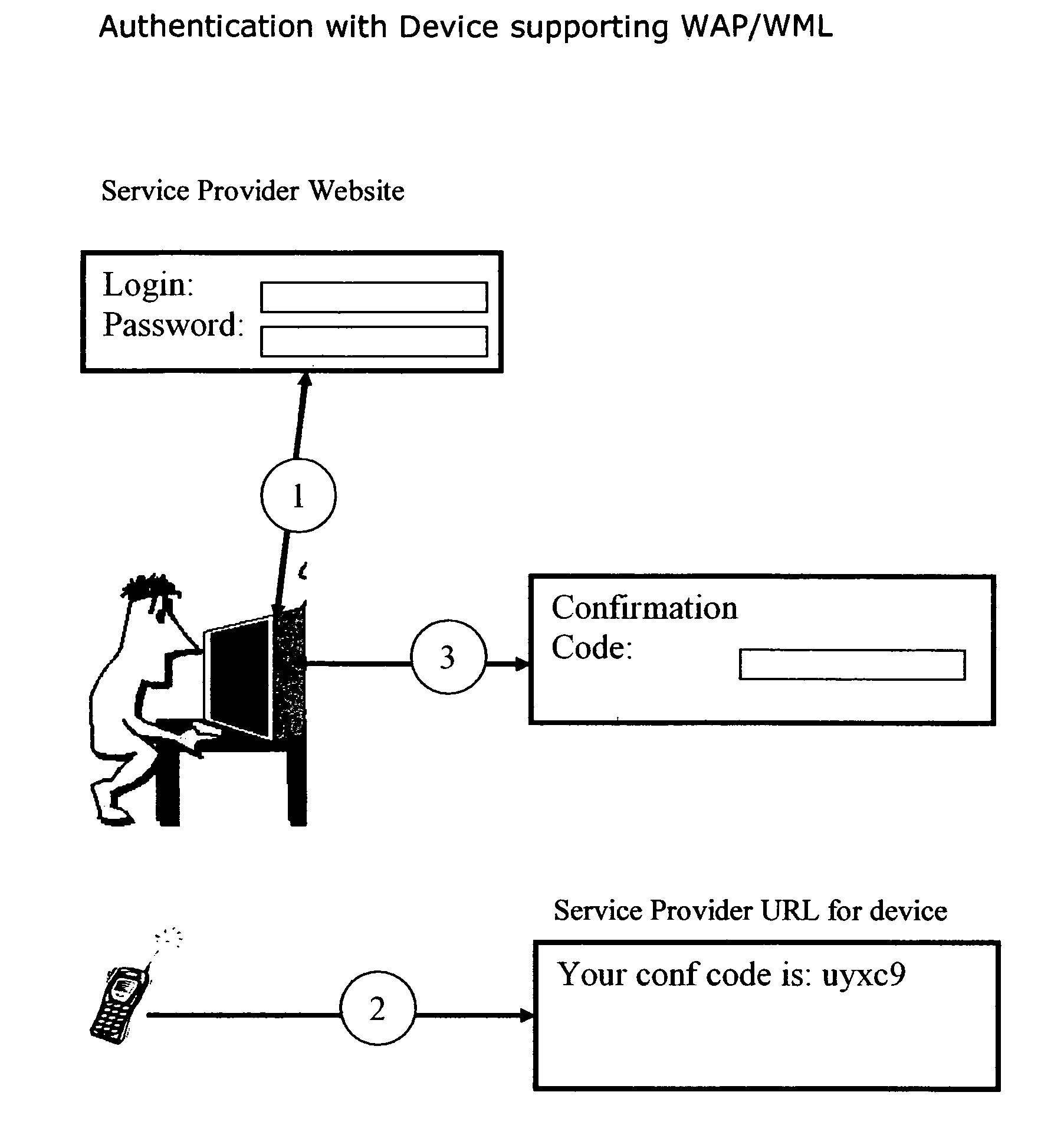
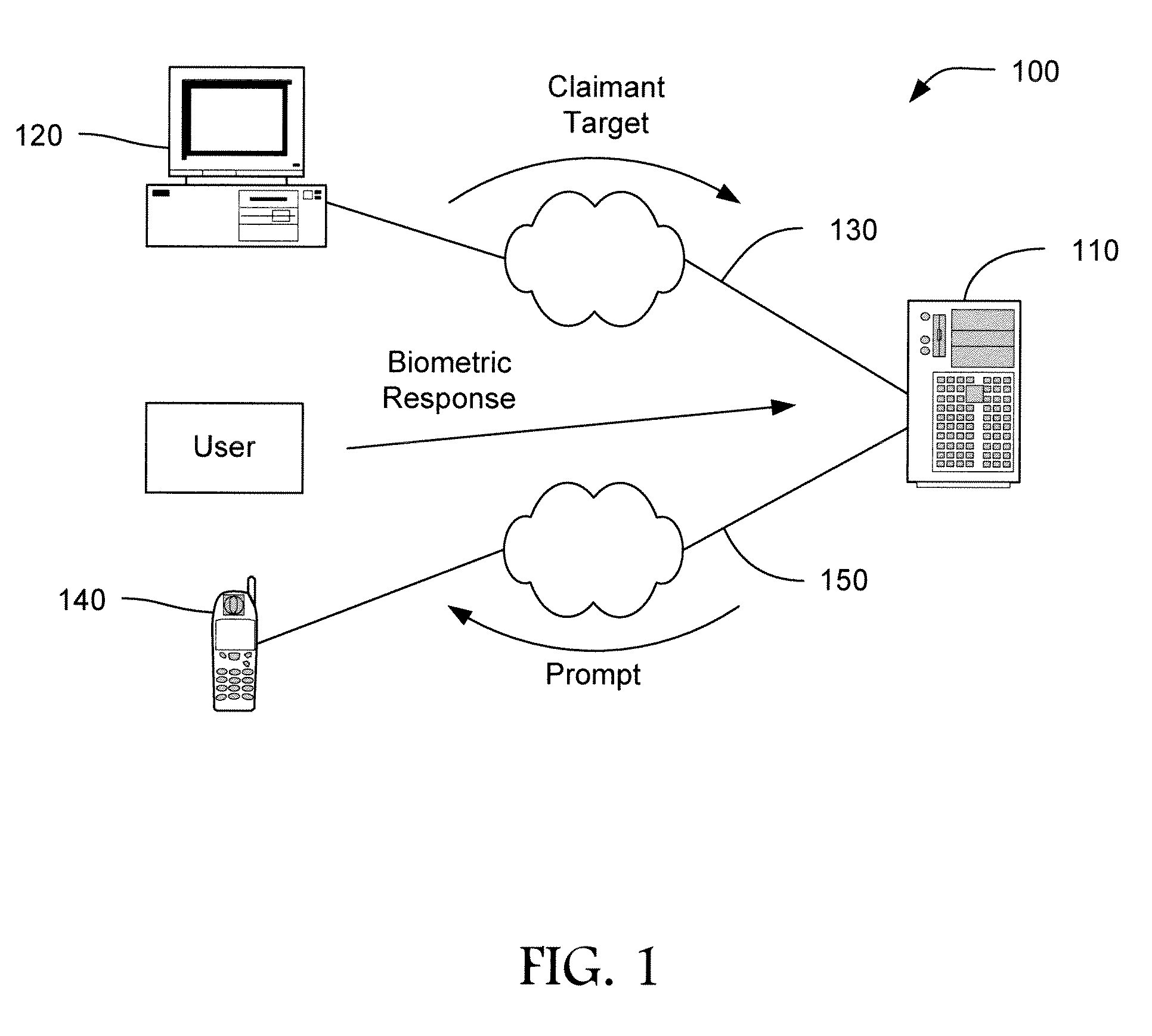
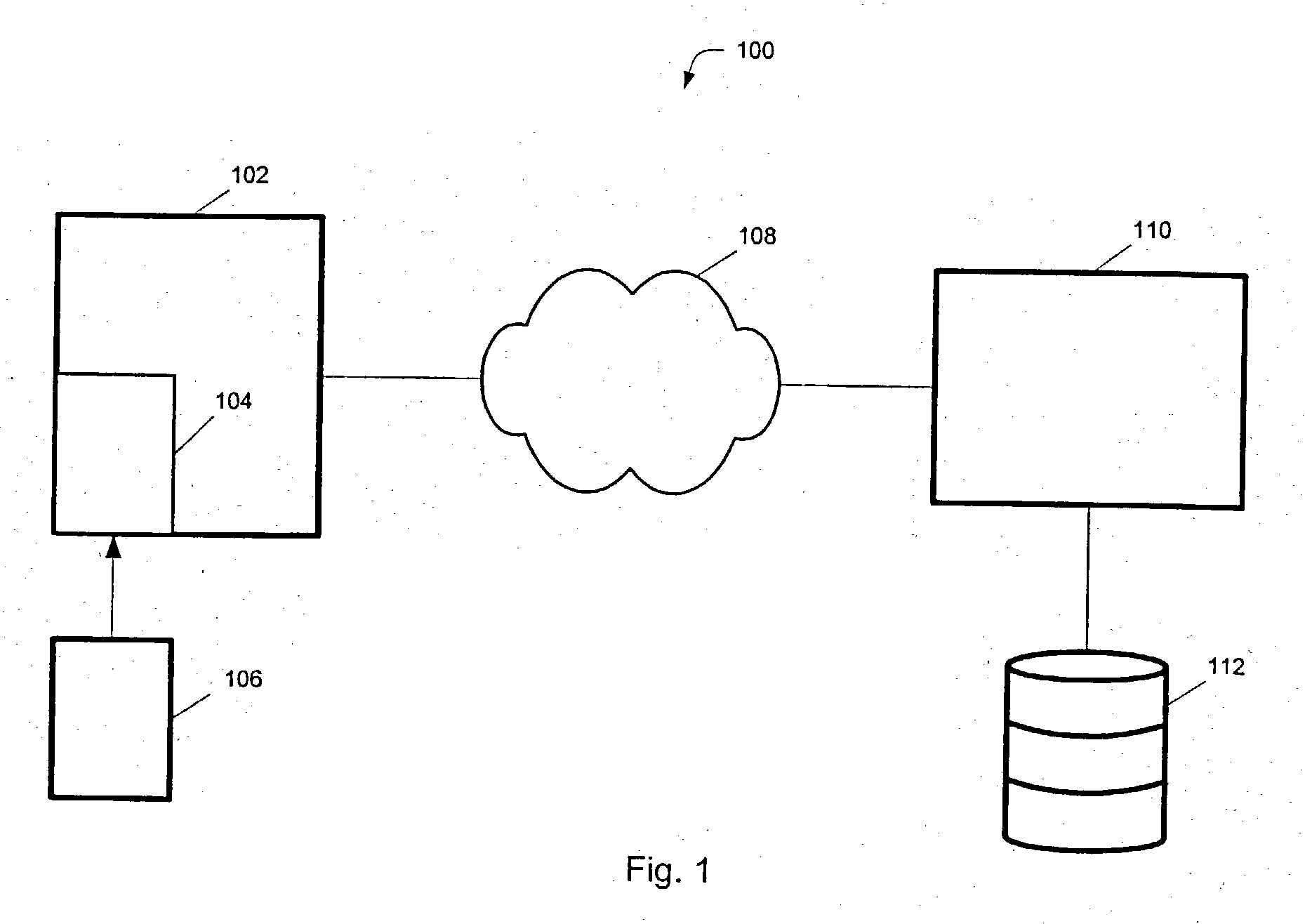
A suspect user (110) seeks access to a network resource from an access authority (150) utilizing a passcode received from an authentication authority (130). Initially, an ID of a device is bound with a PIN, the device ID is bound with a private key of the device, and the device ID is bound with a user ID that has been previously bound with a password of an authorized user. The device ID is bound with the user ID by authenticating the user ID using the password. Thereafter, the suspect user communicates the device ID and the PIN from the device over an ancillary communications network (112); the authentication authority responds back over the ancillary communications network with a passcode encrypted with the public key of the device; and the suspect user decrypts and communicates over a communications network (114) the passcode with the user ID to the access authority.
Owner:KARETEK HLDG LLC
Multi-factor authentication system
InactiveUS7373515B2User identity/authority verificationUnauthorized memory use protectionPasswordUser identifier
Owner:KARETEK HLDG LLC
System and method of using two or more multi-factor authentication mechanisms to authenticate online parties
InactiveUS20070136573A1Minimal inconvenienceStrong authenticationDigital data authenticationSecuring communicationUser deviceBehavioral analytics
A system and method for authentication that comprises the use of at least one multiple multi-factor authentication with the optional addition of, mutual (site) authentication, transaction / behavior analysis, that utilizes user-facing geolocation communications and / or information about user device ownership periods, and / or a combination thereof to help prevent fraud.
Owner:STEINBERG JOSEPH
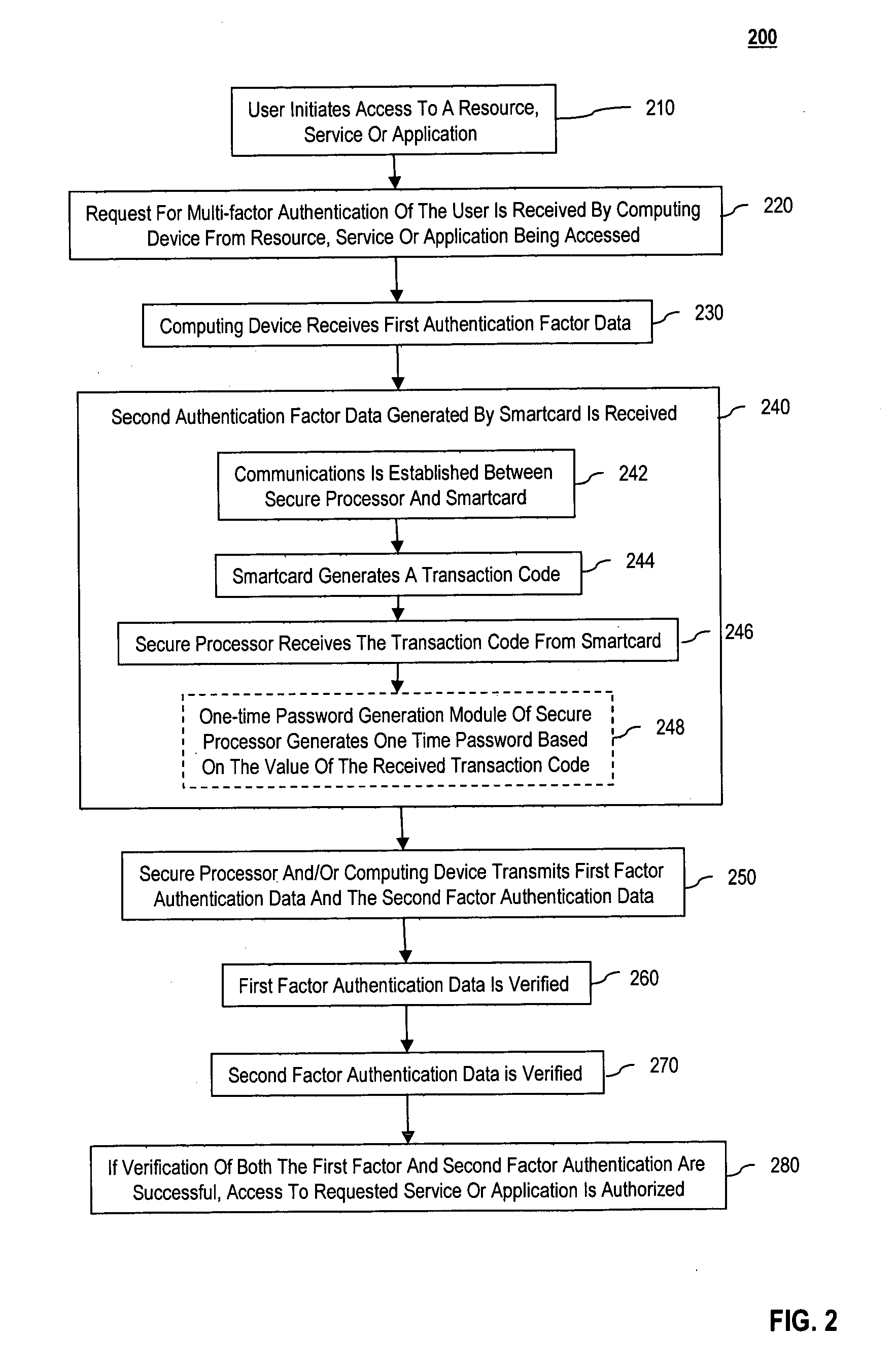
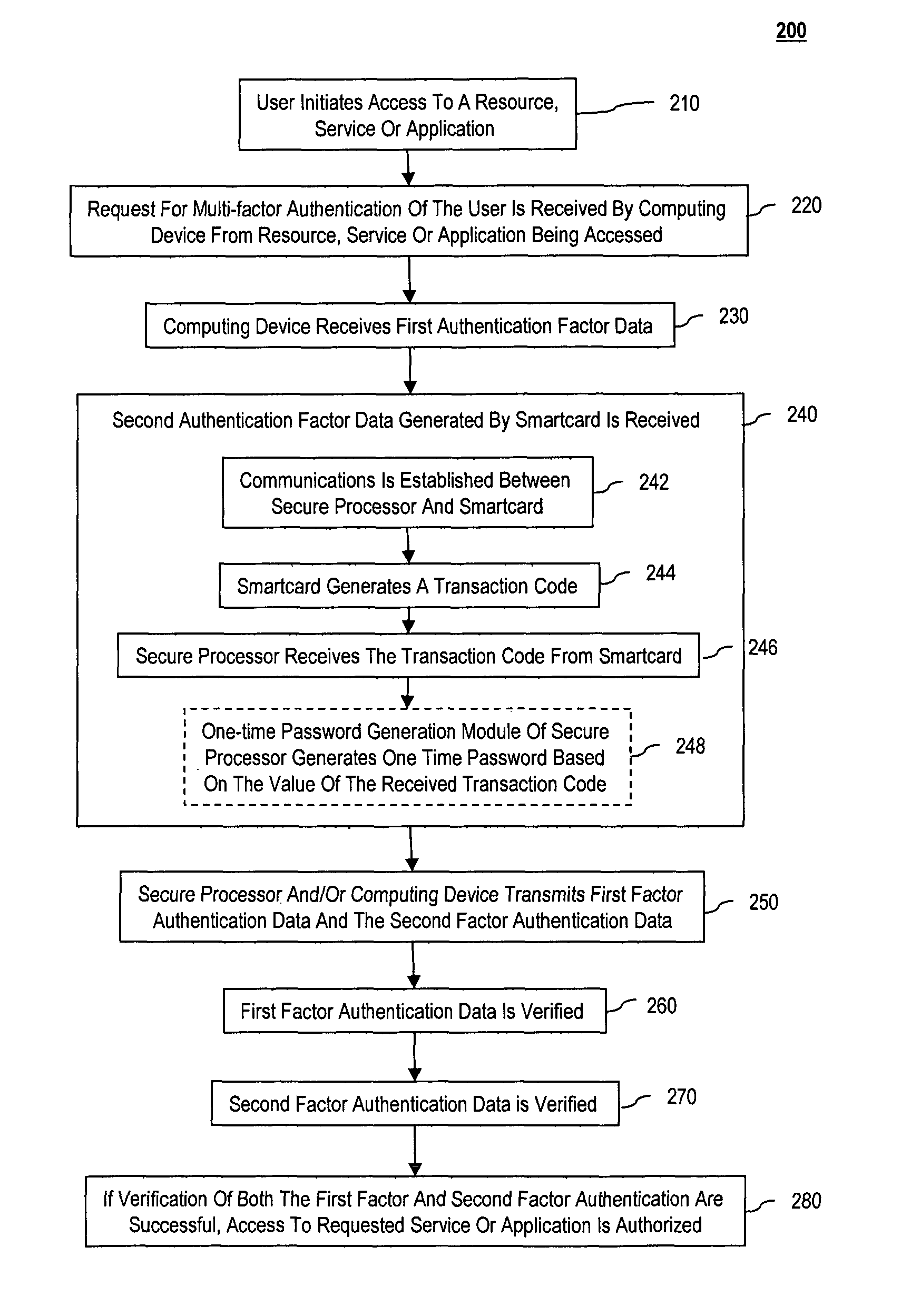
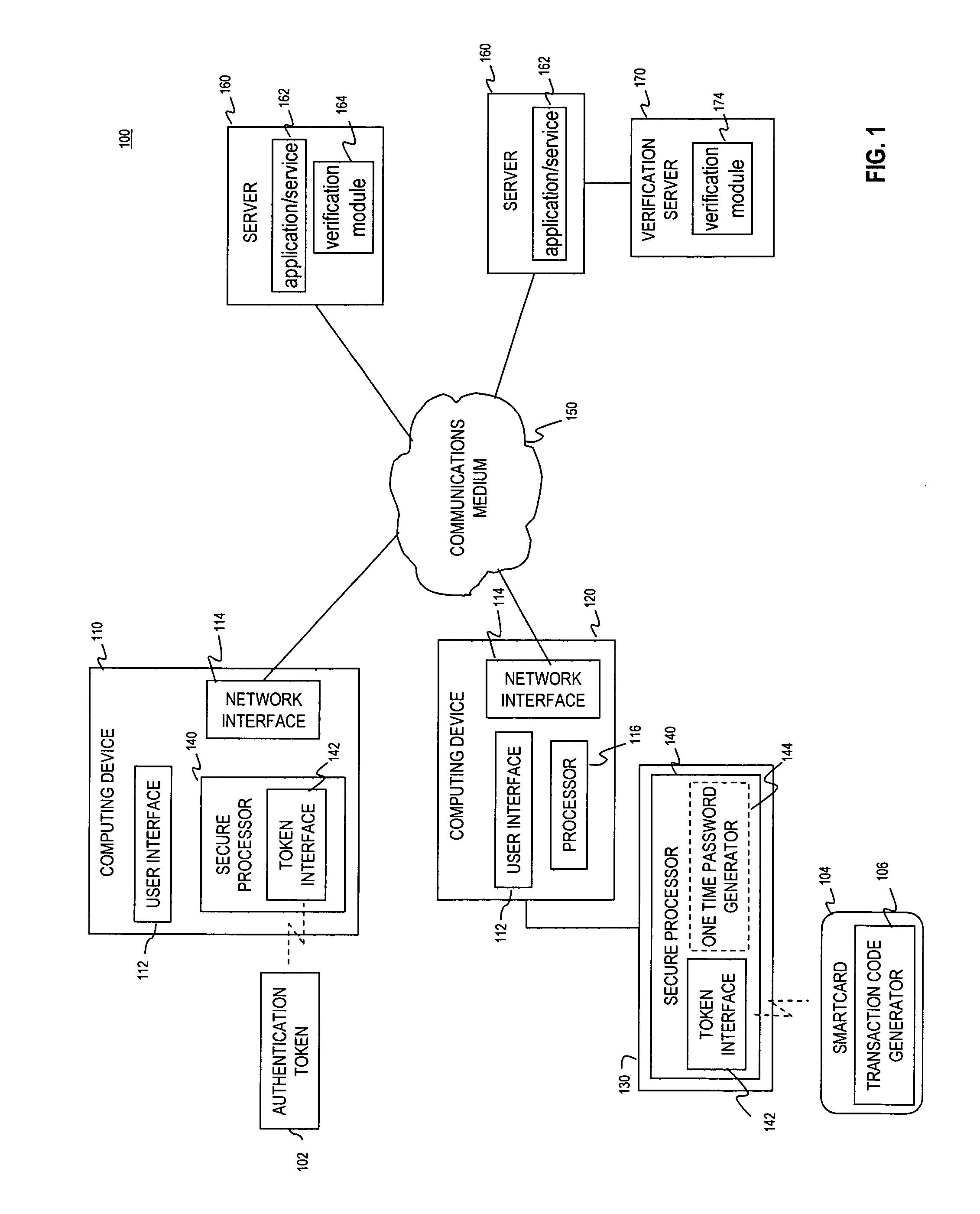
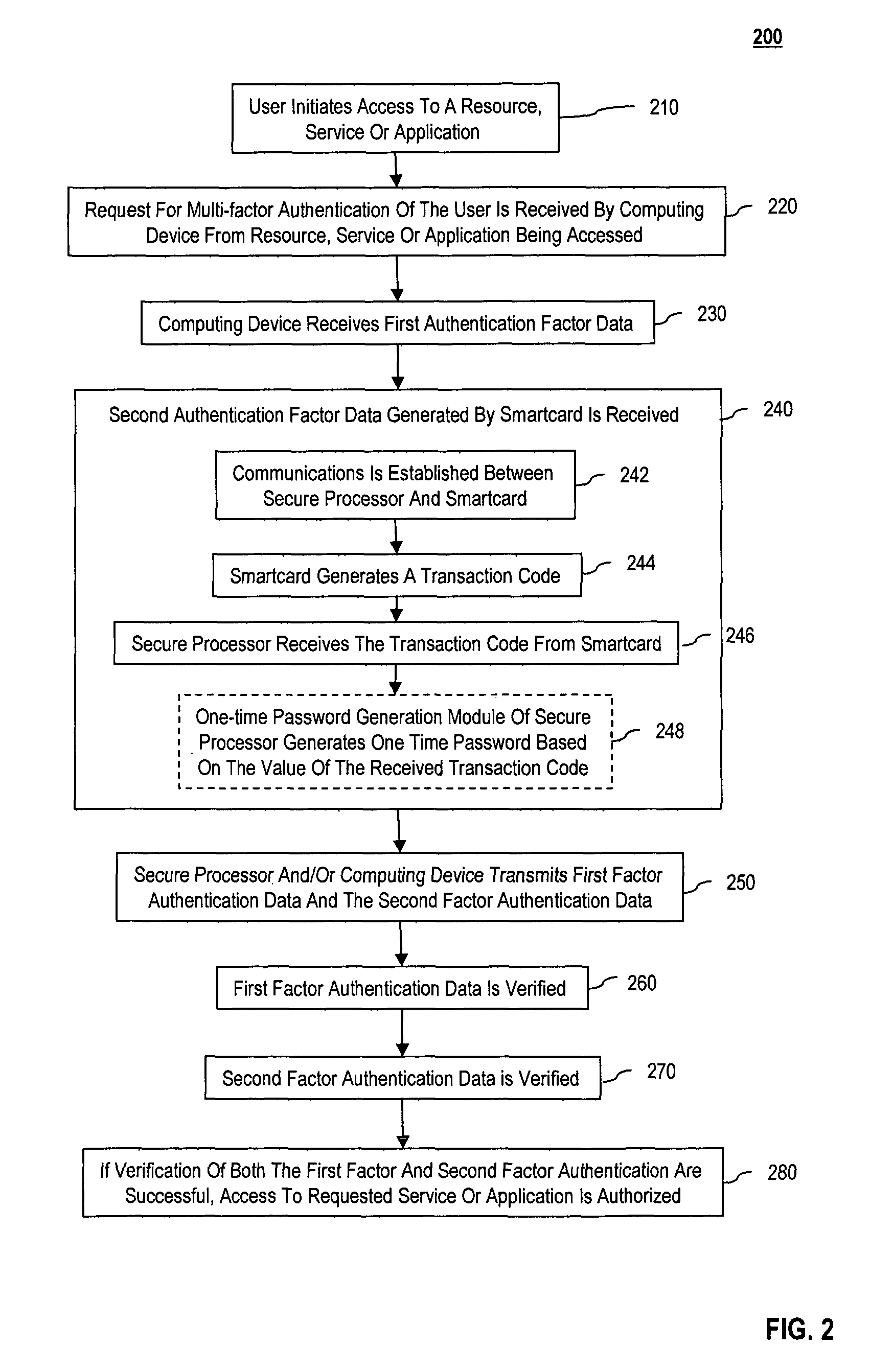
Multi-factor authentication using a smartcard
ActiveUS20070118745A1Digital data processing detailsUser identity/authority verificationSecure communicationThe Internet
Methods and systems are provided for non-cryptographic capabilities of a token such as a smartcard to be used as an additional authentication factor when multi-factor authentication is required. Smartcards are configured to generate a transaction code each time a transaction is attempted by the smartcard. The transaction code is dynamic, changing with each transaction, and therefore is used as a one-time password. When a user attempts to access a service or application requiring at least two authentication factors, a secure processor is used to read transaction code from the smartcard. The secure processor establishes a secure communication with the remote computer hosting the service or application. The transaction code can then be encrypted prior to transmission over the public Internet, providing an additional layer of security.
Owner:AVAGO TECH INT SALES PTE LTD
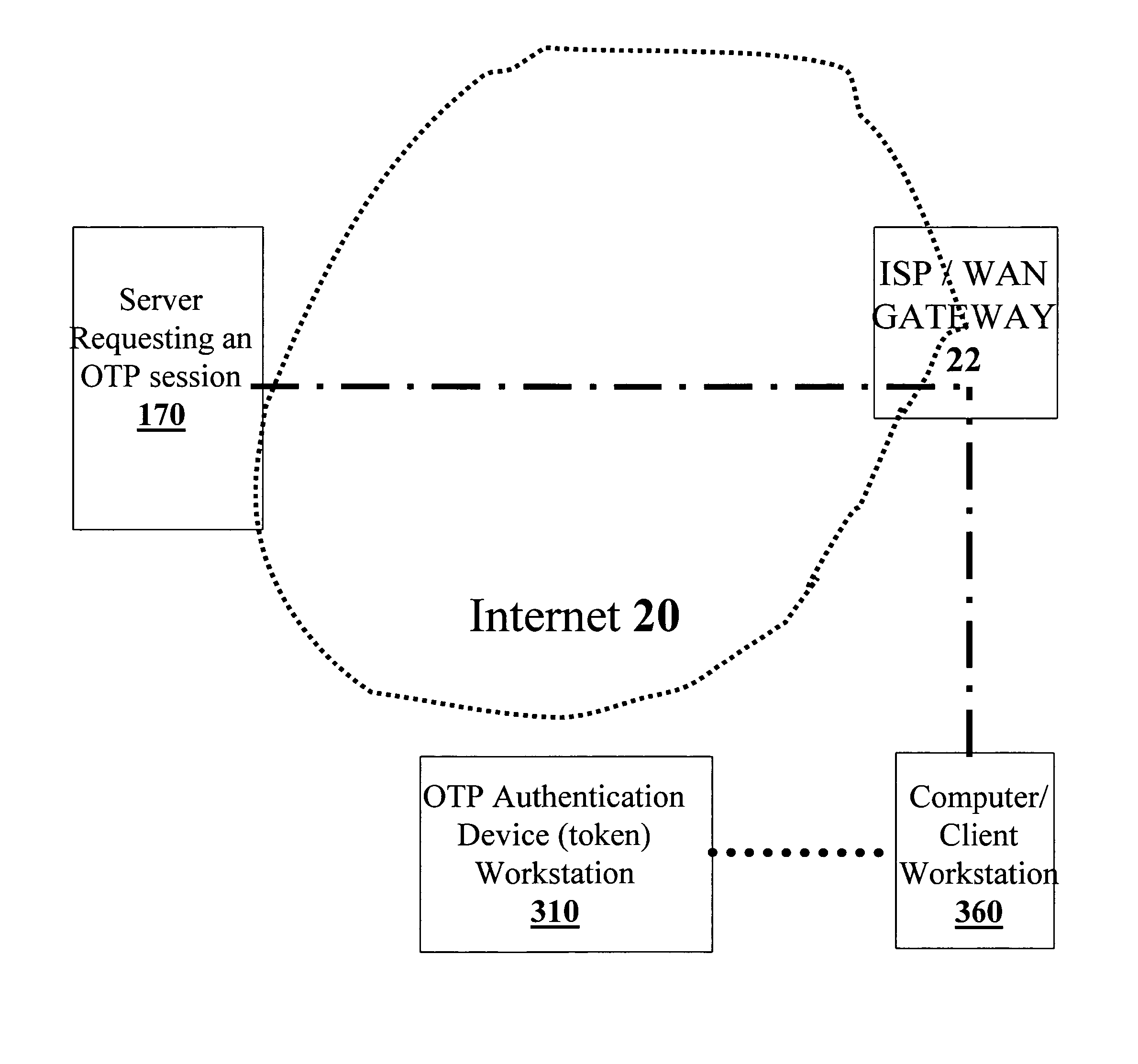
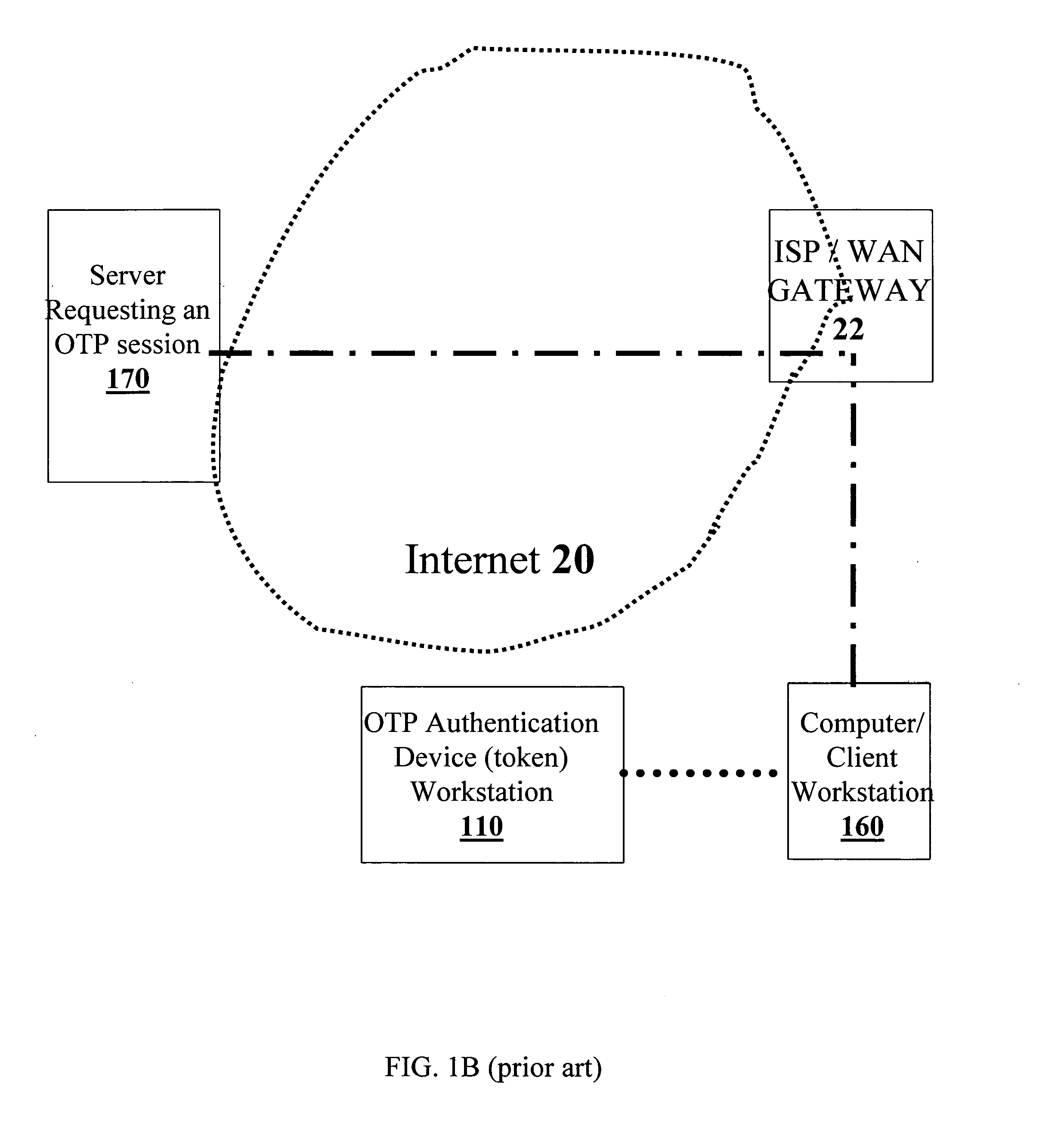
Extended one-time password method and apparatus
ActiveUS20070067828A1Vehicle testingKey distribution for secure communicationThe InternetUser authentication
An OTP token for facilitating the authorizing of a client workstation to conduct a session with a server over the Internet is disclosed. Information at least partially identifying the server is provided to the OTP token and / or the client workstation, and a determination is made, using this identifying information, if the server is a legitimate server. In accordance with this determination, it is decided whether or not to transmit data indicative of a session OTP from the OTP token to the client workstation. In some embodiments, if the identifying information is indicative of a legitimate server, the data indicative of the session OTP is transmitted from the OTP token to the client workstation, and otherwise, the data indicative of the session OTP is withheld from the client workstation. Data indicative of the session OTP may include, in various embodiments, either multi-factor authentication data derived from user authorization data, or session OTP data that is independent of user authentication data.
Owner:WESTERN DIGITAL ISRAEL LTD
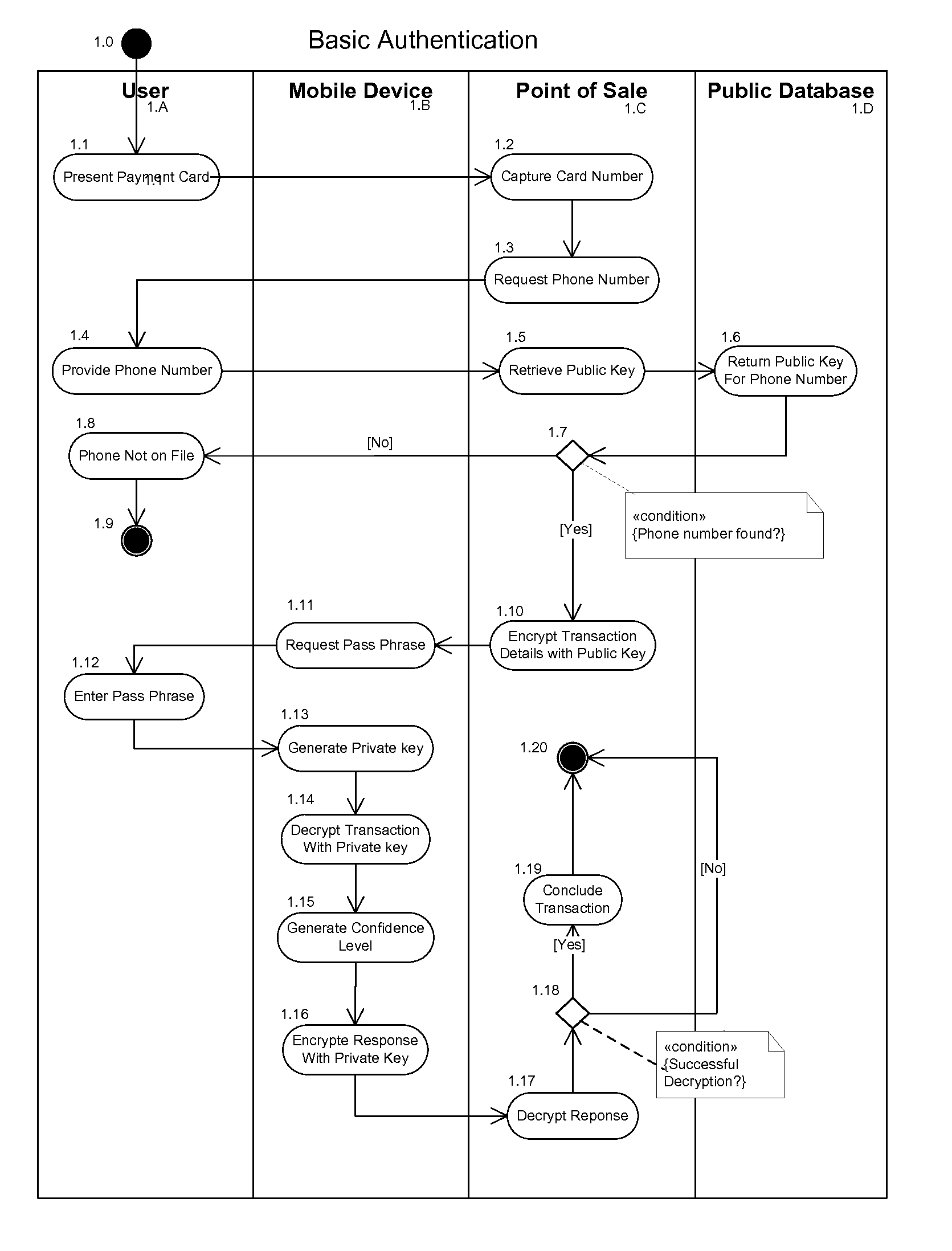
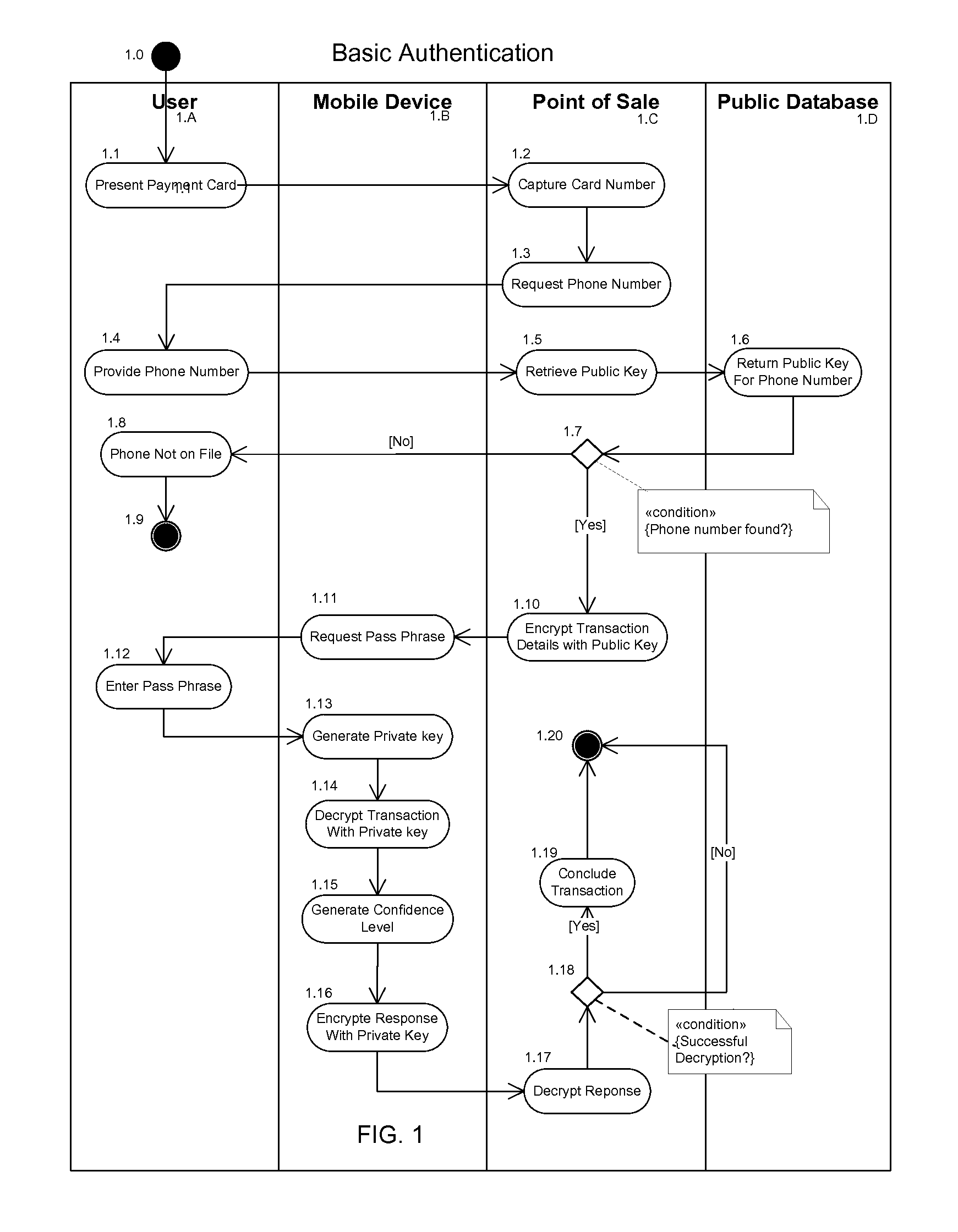
Multi-Factor Authentication Using a Mobile Phone
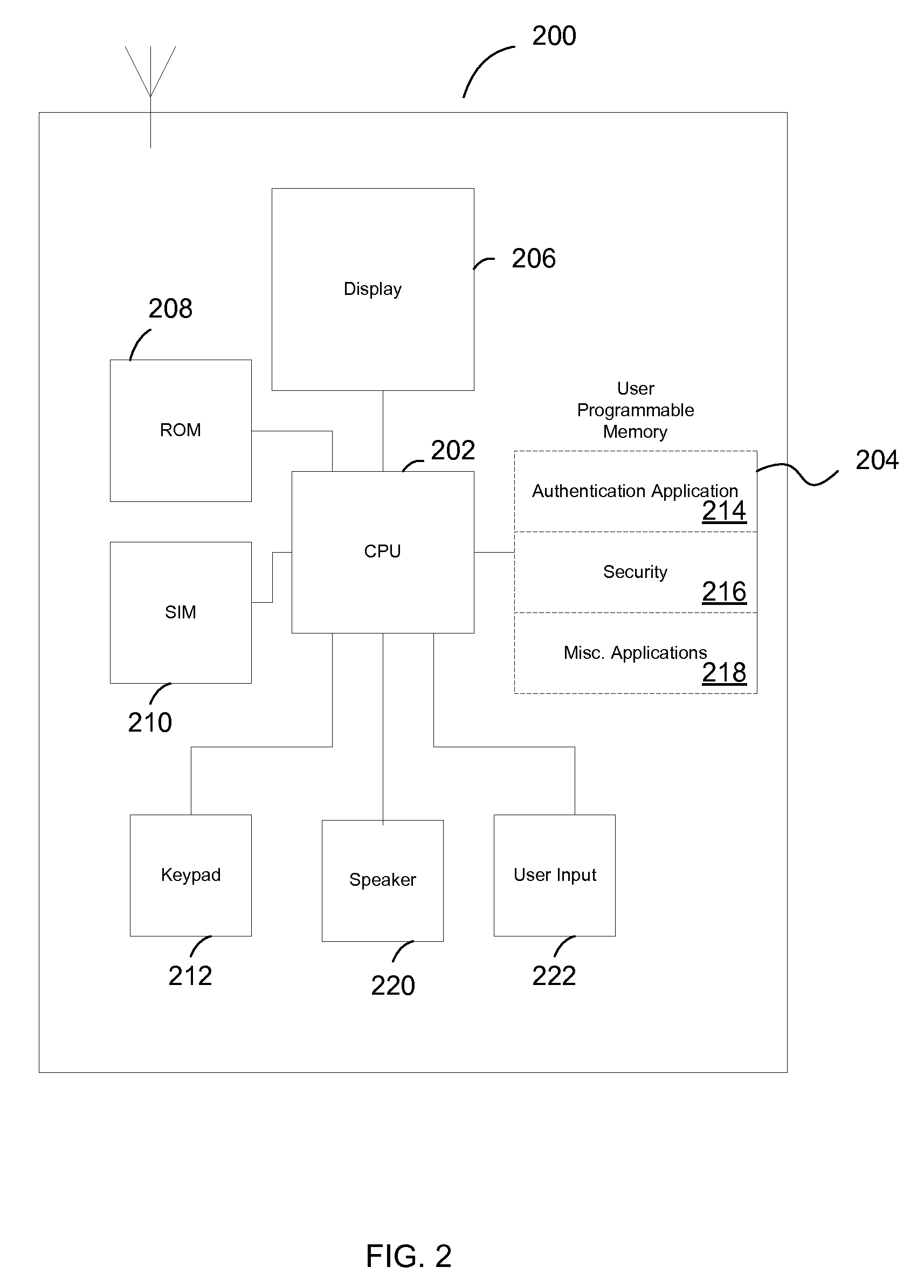
InactiveUS20110142234A1Acutation objectsUnauthorised/fraudulent call preventionPaymentBiometric data
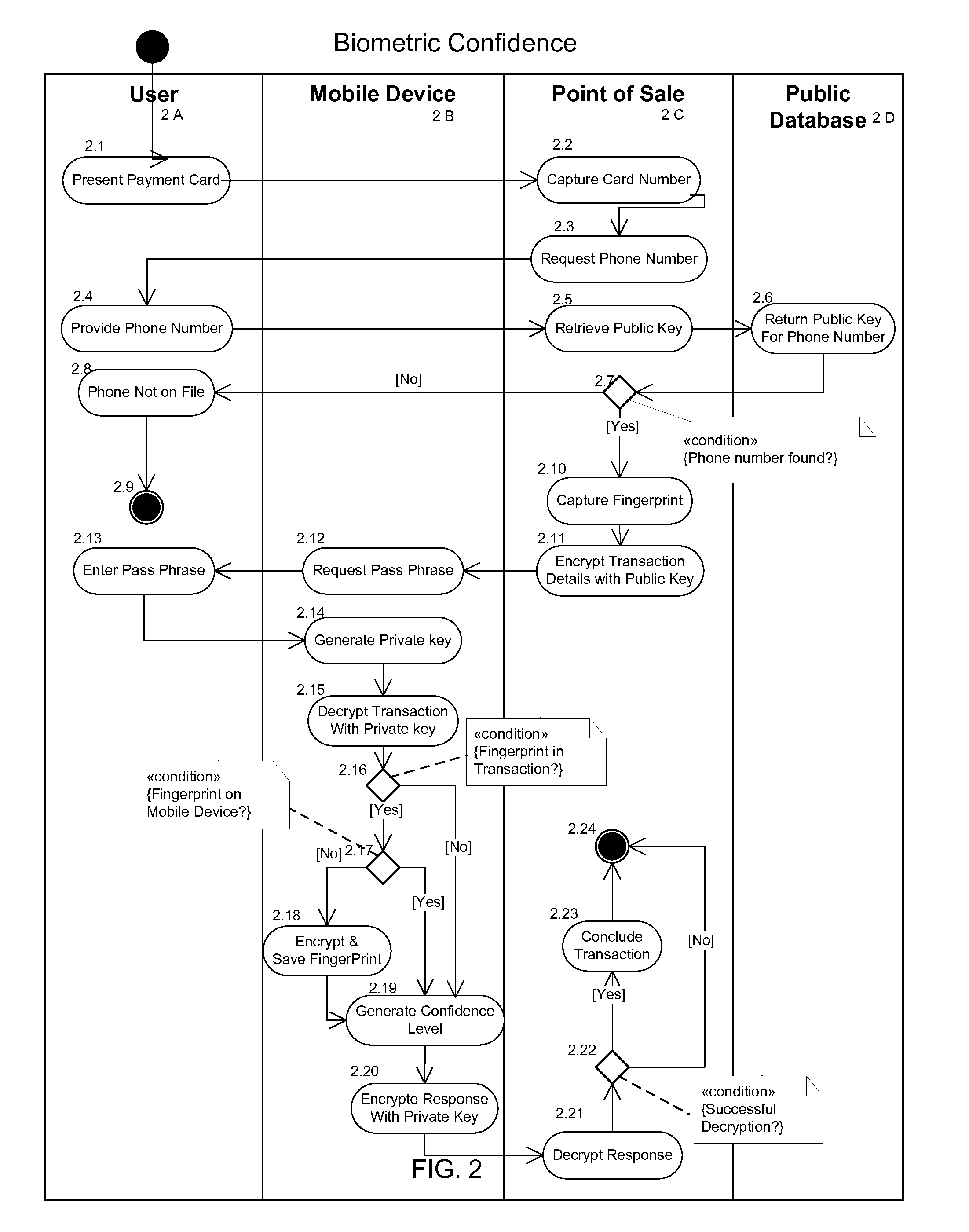
The invention described here provides a fully-distributed solution to the problem of confirming the identity of the presenter of a payment card or other credentials, using multiple factors to authenticate the presenter. The invention leverages the wide penetration of mobile phones in modern economies as the basis for the distributed multi-factor authentication. For additional confidence levels biometric data can be incrementally included as part of the multi-factor authentication. The loss of any one of the multiple authentication factors does not compromise the integrity of the system or the individual, and there is no single point of vulnerability for attack or theft. The invention is fully backwards compatible with current payment cards systems and can be extended to almost any situation where the identity of the presenter of credentials needs to be authenticated prior to allowing the individual access to the protected services, systems, or locations. This allows for incremental adoption across a wide range of current and future systems.
Owner:ROGERS MICHAEL LEONARD
Multi-factor authentication
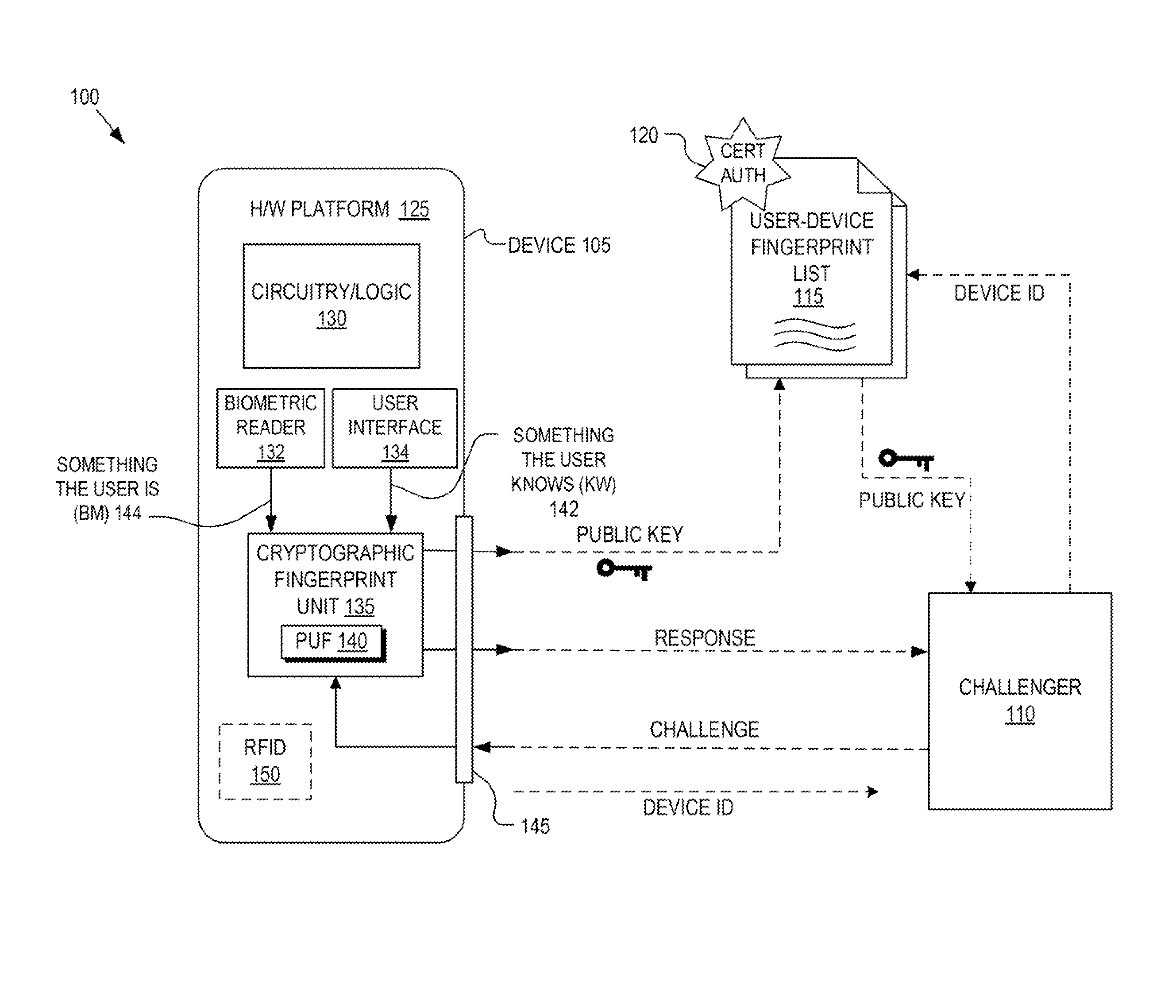
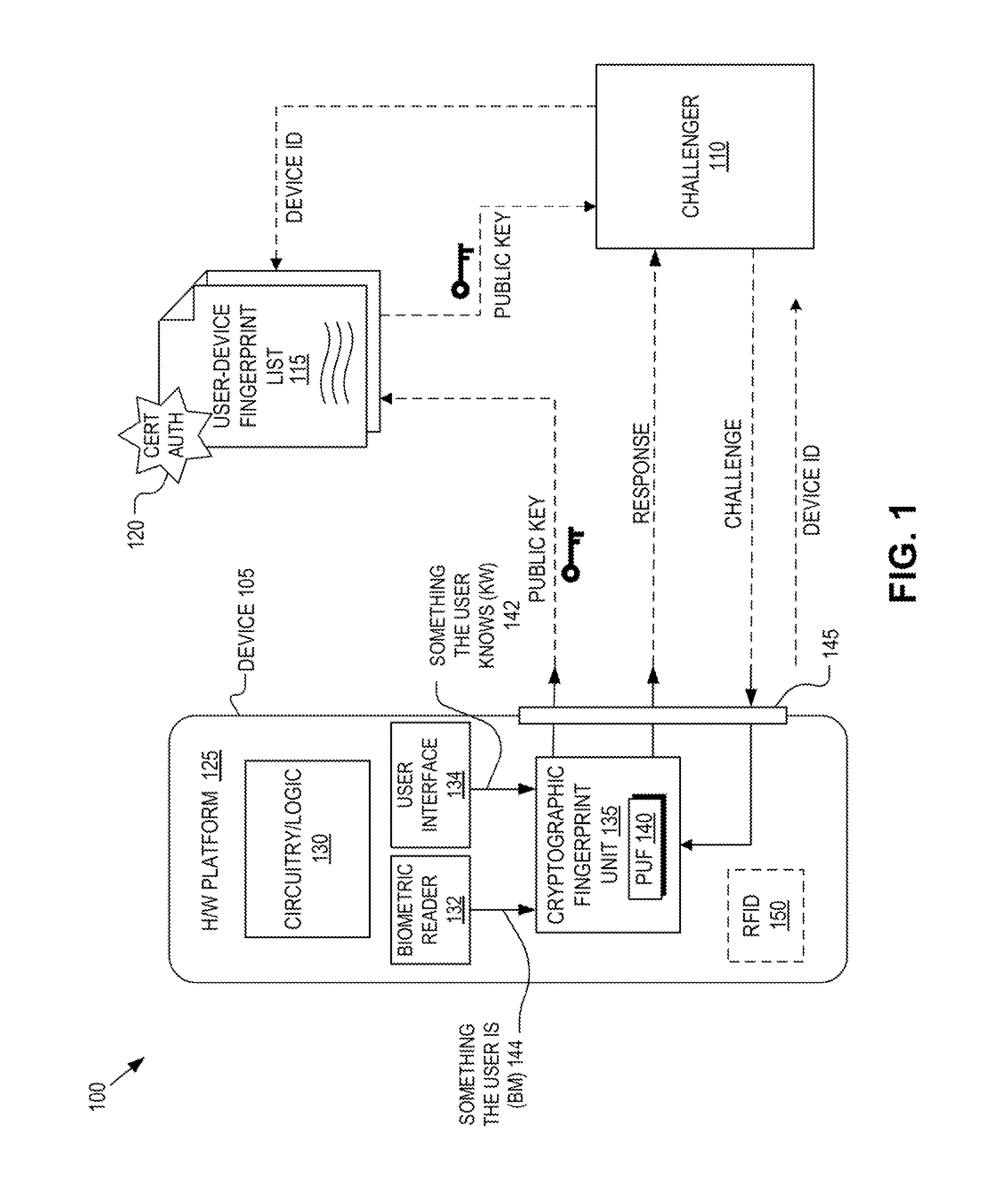
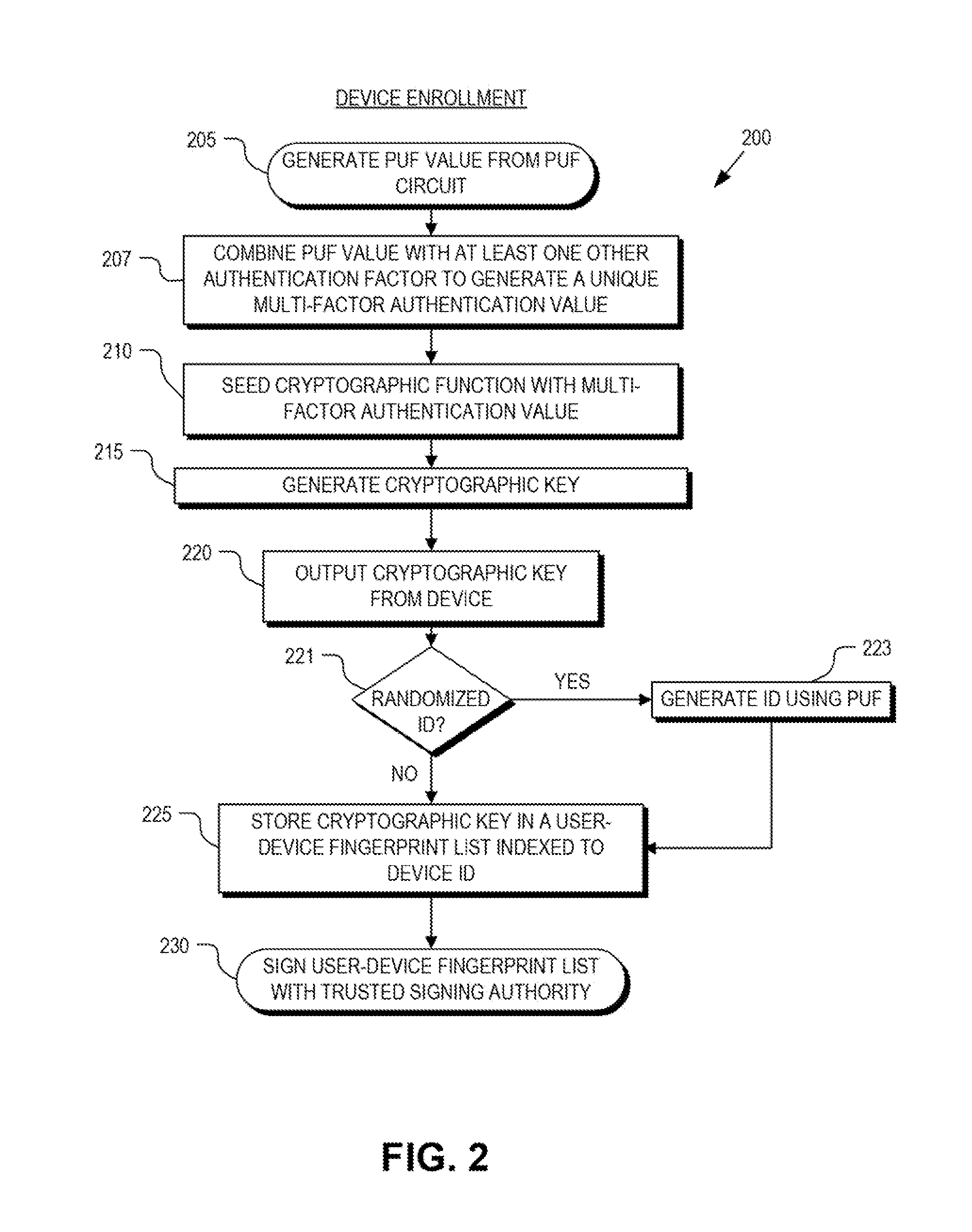
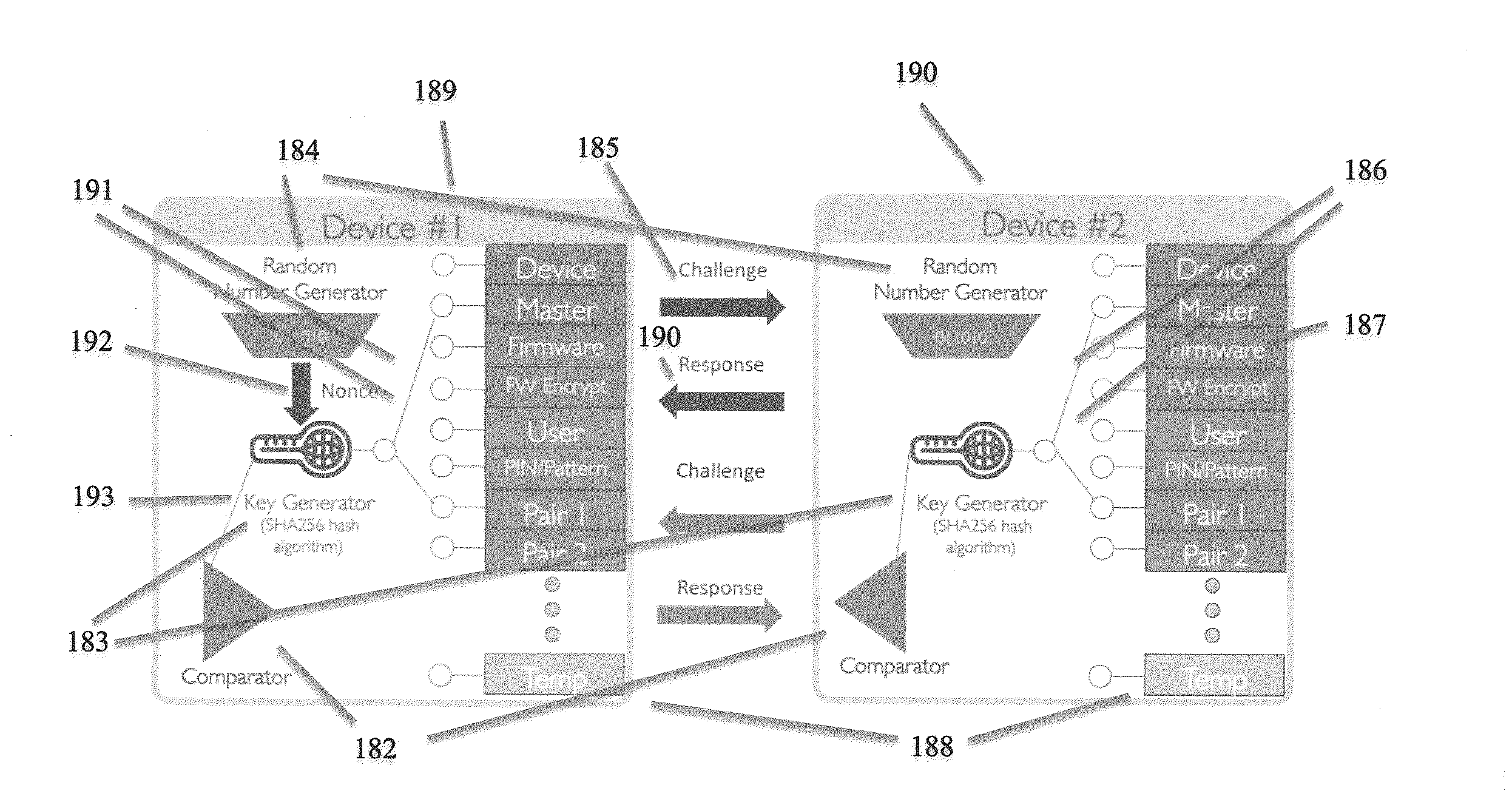
ActiveUS8868923B1Reliability increasing modificationsElectric signal transmission systemsPhysical unclonable functionUser authentication
Detection and deterrence of spoofing of user authentication may be achieved by including a cryptographic fingerprint unit within a hardware device for authenticating a user of the hardware device. The cryptographic fingerprint unit includes an internal physically unclonable function (“PUF”) circuit disposed in or on the hardware device, which generates a PUF value. Combining logic is coupled to receive the PUF value, combines the PUF value with one or more other authentication factors to generate a multi-factor authentication value. A key generator is coupled to generate a private key and a public key based on the multi-factor authentication value while a decryptor is coupled to receive an authentication challenge posed to the hardware device and encrypted with the public key and coupled to output a response to the authentication challenge decrypted with the private key.
Owner:NAT TECH & ENG SOLUTIONS OF SANDIA LLC
Multi-factor authentication using a smartcard
ActiveUS8245292B2Digital data processing detailsUser identity/authority verificationSecure communicationThe Internet
Methods and systems are provided for non-cryptographic capabilities of a token such as a smartcard to be used as an additional authentication factor when multi-factor authentication is required. Smartcards are configured to generate a transaction code each time a transaction is attempted by the smartcard. The transaction code is dynamic, changing with each transaction, and therefore is used as a one-time password. When a user attempts to access a service or application requiring at least two authentication factors, a secure processor is used to read transaction code from the smartcard. The secure processor establishes a secure communication with the remote computer hosting the service or application. The transaction code can then be encrypted prior to transmission over the public Internet, providing an additional layer of security.
Owner:AVAGO TECH INT SALES PTE LTD
Systems and methods for providing authentication and authorization utilizing a personal wireless communication device
InactiveUS20100257357A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyPassword
Owner:BOOJUM MOBILE
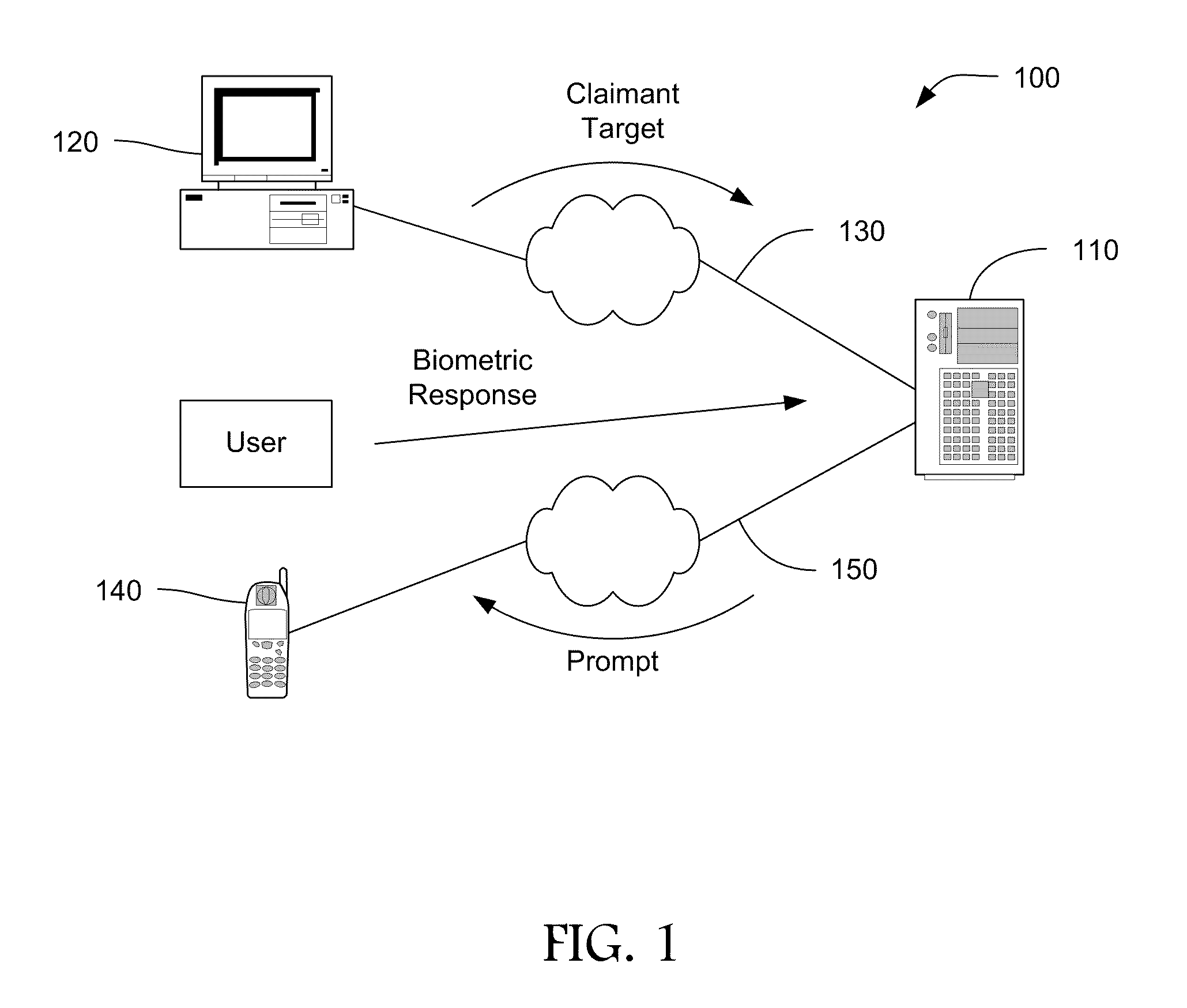
Multi-factor authentication and certification system for electronic transactions
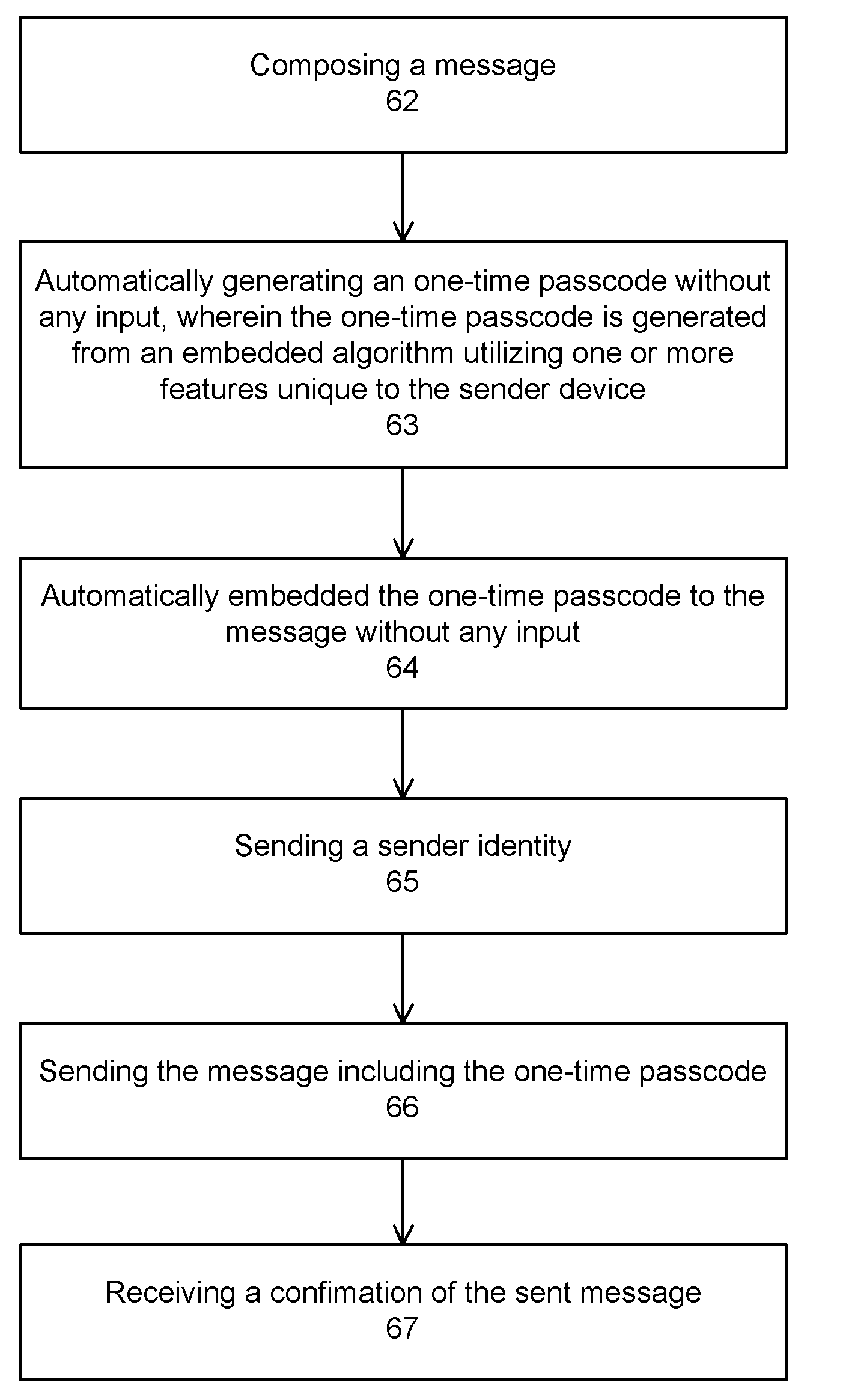
InactiveUS20090172402A1Environment safetyImprove securityFinanceUser identity/authority verificationE-commerceOne-time password
The present invention provides computer-enable certification and authentication in, for example, e-commerce with wireless and mobile devices. The present authentication method offers ease of operation by automatically embedding a one-time passcode to the message without the sender input. A one-time key can also be used to encrypt the message, further providing transmission security. In addition, sensitive information and one-time passcode generator are pre-arranged and stored at both sender and receiver devices, avoiding information comprising in wireless environment transmission.
Owner:TRAN NGUYEN THO
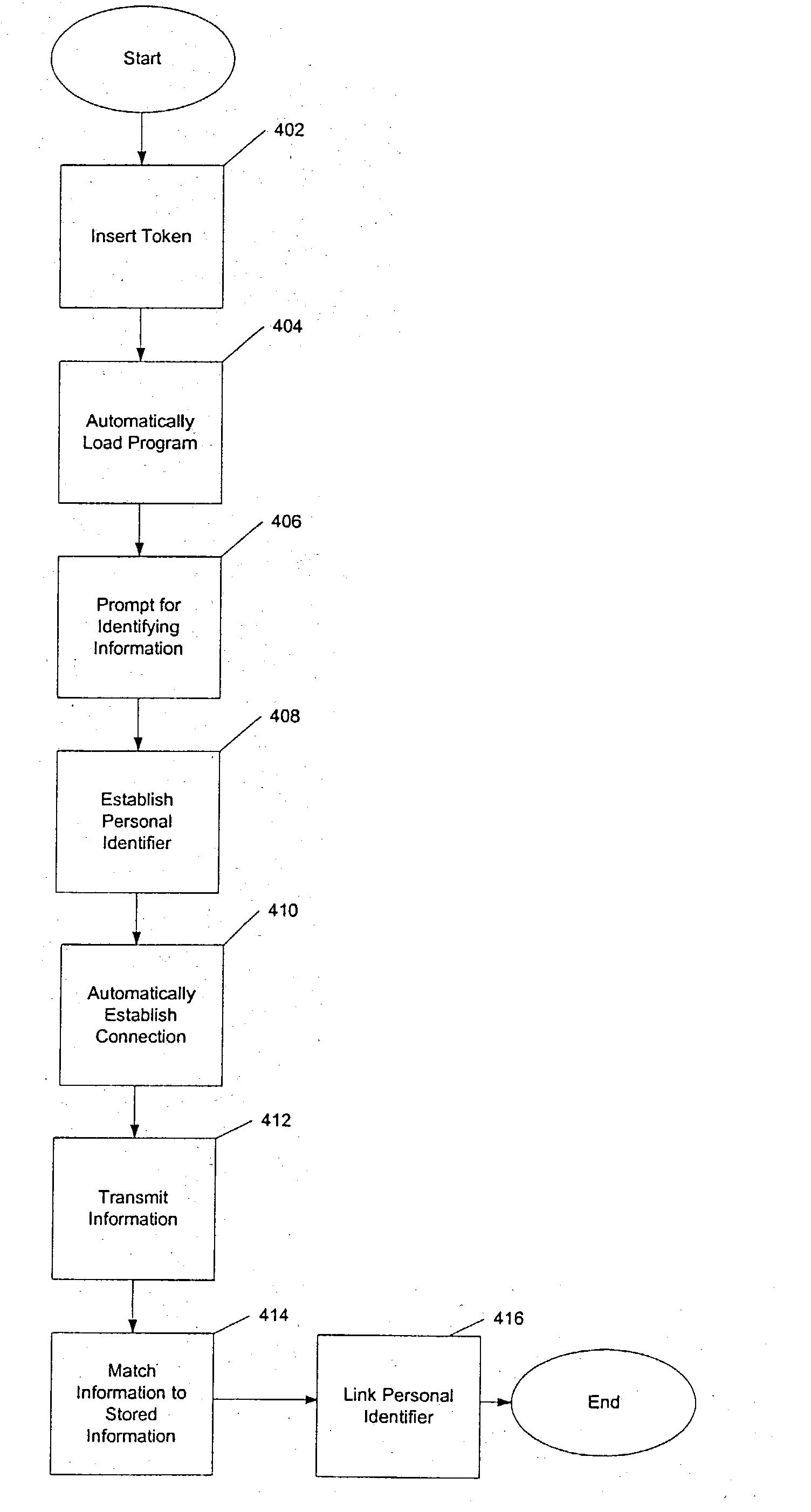
Systems and methods for enrolling a token in an online authentication program
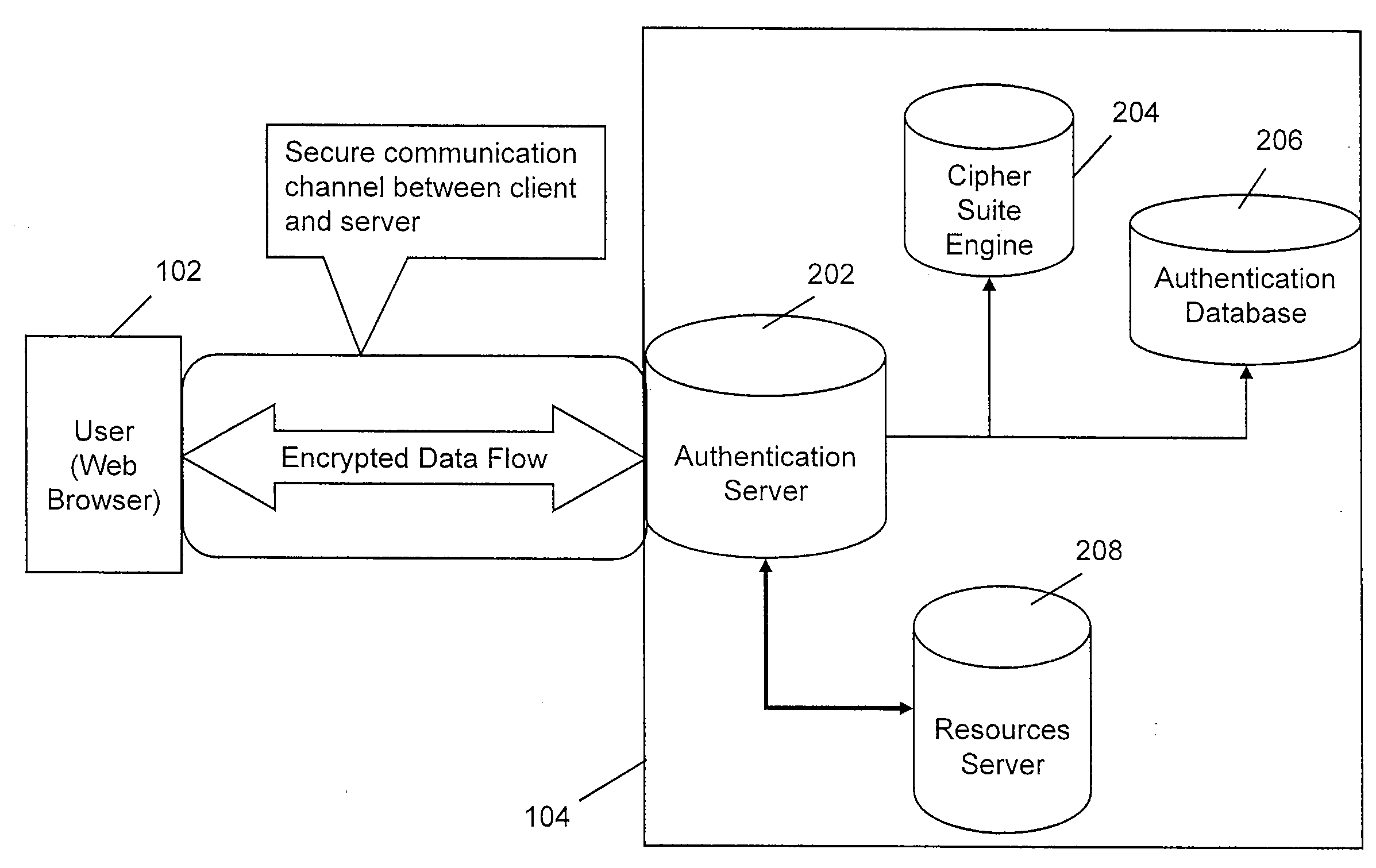
InactiveUS20050033703A1Improve reliabilityReduce fraudFinanceDigital data processing detailsInternet privacyAuthentication
An online transaction system configured to implement authentication methods that allow for strong multi-factor authentication in online environments. The authentication methods can be combined with strong security methods to further ensure that the authentication process is secure. Further, the strong multy-factor authentication can be implemented with zero adoption dependencies through the implementation of automated enrollment methods.
Owner:U S ENCODE CORP
Risk-link authentication for optimizing decisions of multi-factor authentications
A system for evaluating risk in an electronic banking transaction by estimating an aggregated risk value from a set of risk factors that are either dependent or independent of each other, comprising: user input means for enabling an end user to provide authentication information related to a desired electronic banking transaction; financial institution authentication means for authenticating that an end user is authorized to conduct the desired electronic transaction; risk computation means for imposing authentication requirements upon the end user in adaptation to a risk value of the desired banking electronic banking transaction; transaction session means for tracking an amount of time that the desired electronic banking transaction is taking; and financial institution transaction means for storing data related to the desired electronic banking transaction.
Owner:ALNAJEM ABDULLAH ABDULAZIZ I
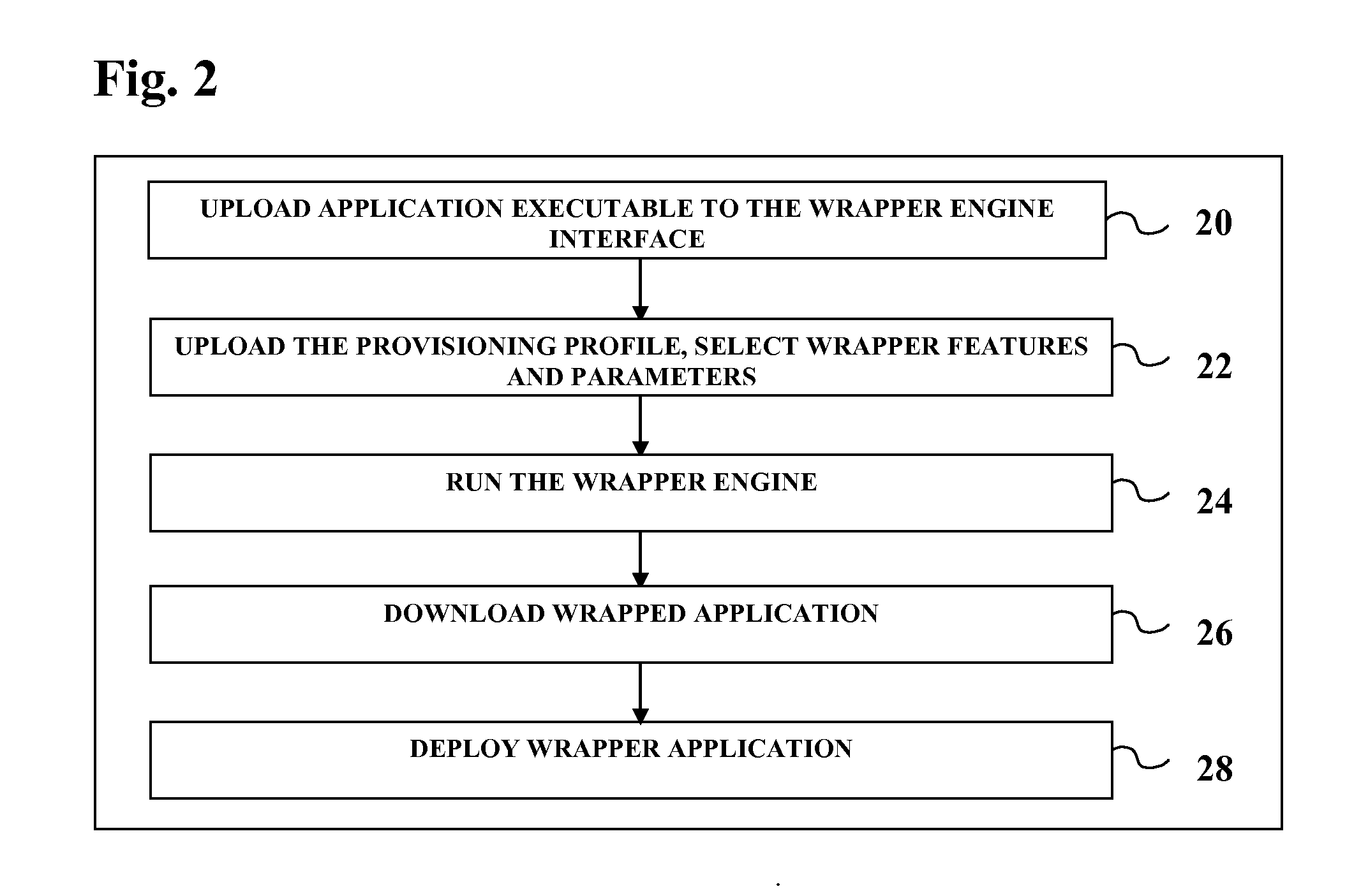
Method for automatically updating application access security
InactiveUS8595810B1Digital data processing detailsUser identity/authority verificationApplication softwareComputer science
A method for automatically updating access security on existing applications with multi-factor authentication, intelligent auto-login, single sign-on, proximity logout, pro-active loss prevention and real-time incident notification using a wrapping function.
Owner:OPTIMA DIRECT LLC
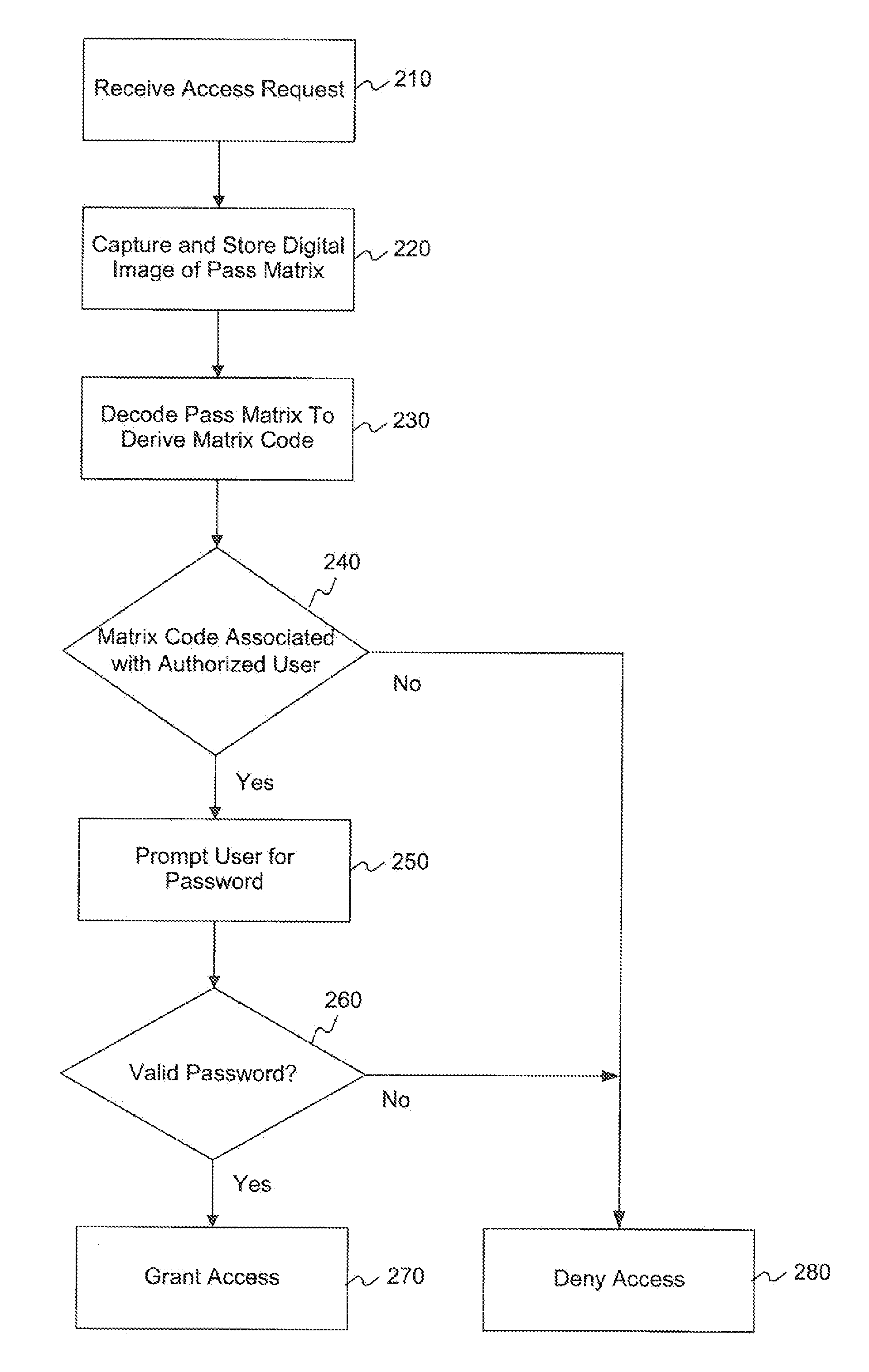
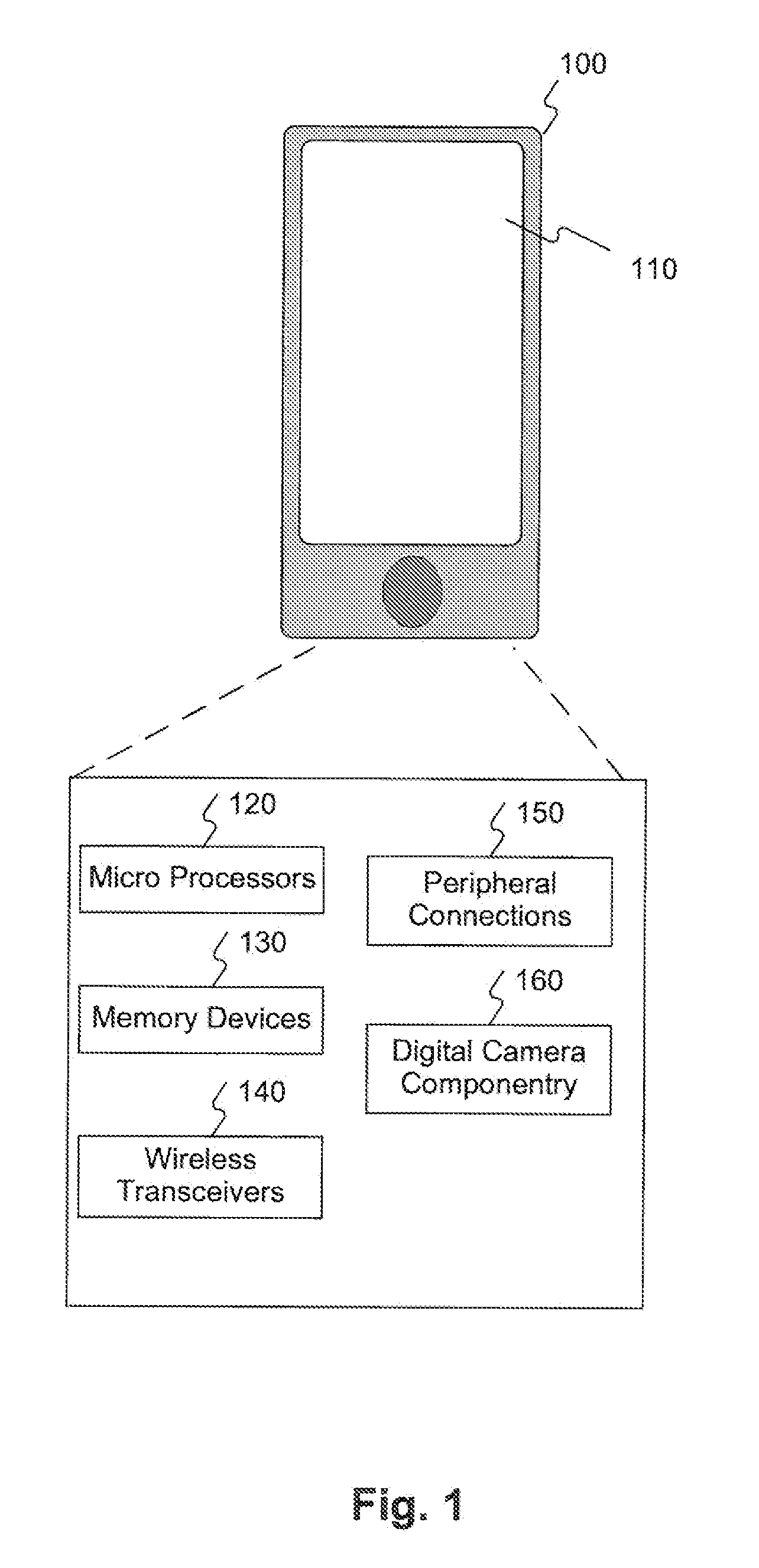
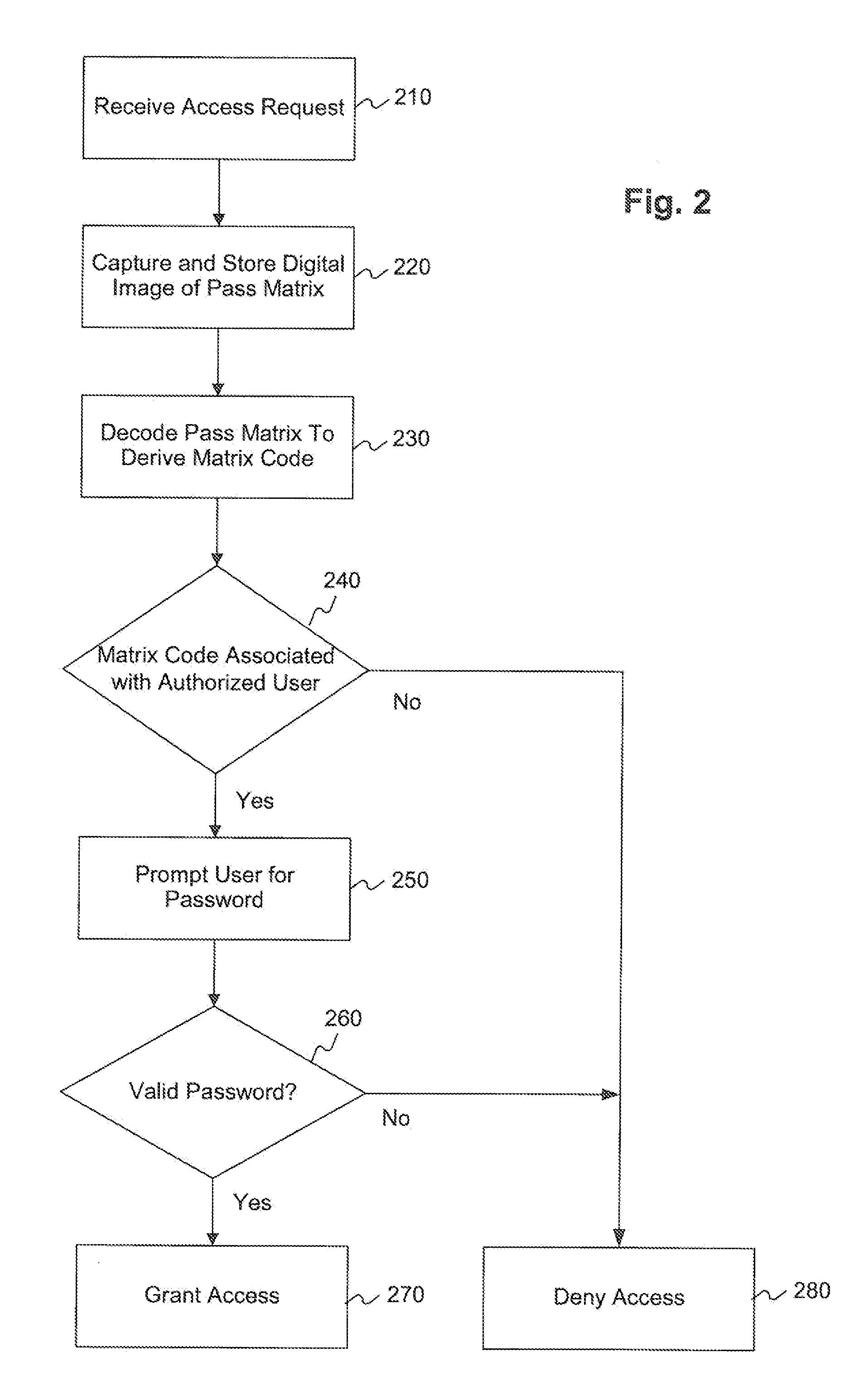
Multi-factor authentication using digital images of barcodes
ActiveUS20130031623A1Easy to operateReduce memory loadDigital data processing detailsUnauthorized memory use protectionComputer graphics (images)Password
Methods, systems, and computer-readable media for implementing a multi-factor authentication scheme utilizing barcode images in computing devices, such as standard mobile devices and smartphones having no native hardware support for reading barcodes other than standard digital camera componentry for capturing digital images of real-world phenomena. A mobile device may be configured by software to require a user, as a first authentication factor, to present a barcode, such as a Quick Response (QR) Code for image scanning using digital camera componentry built into the mobile device. The device analyzes the digital image of the barcode to decode the barcode into its encoded character data. If the device recognizes the character data as valid, then, as a second authentication factor, the device prompts the user to enter a valid password associated with the barcode. If the user-entered barcode is also valid, then the device may grant the user access.
Owner:XEROX CORP
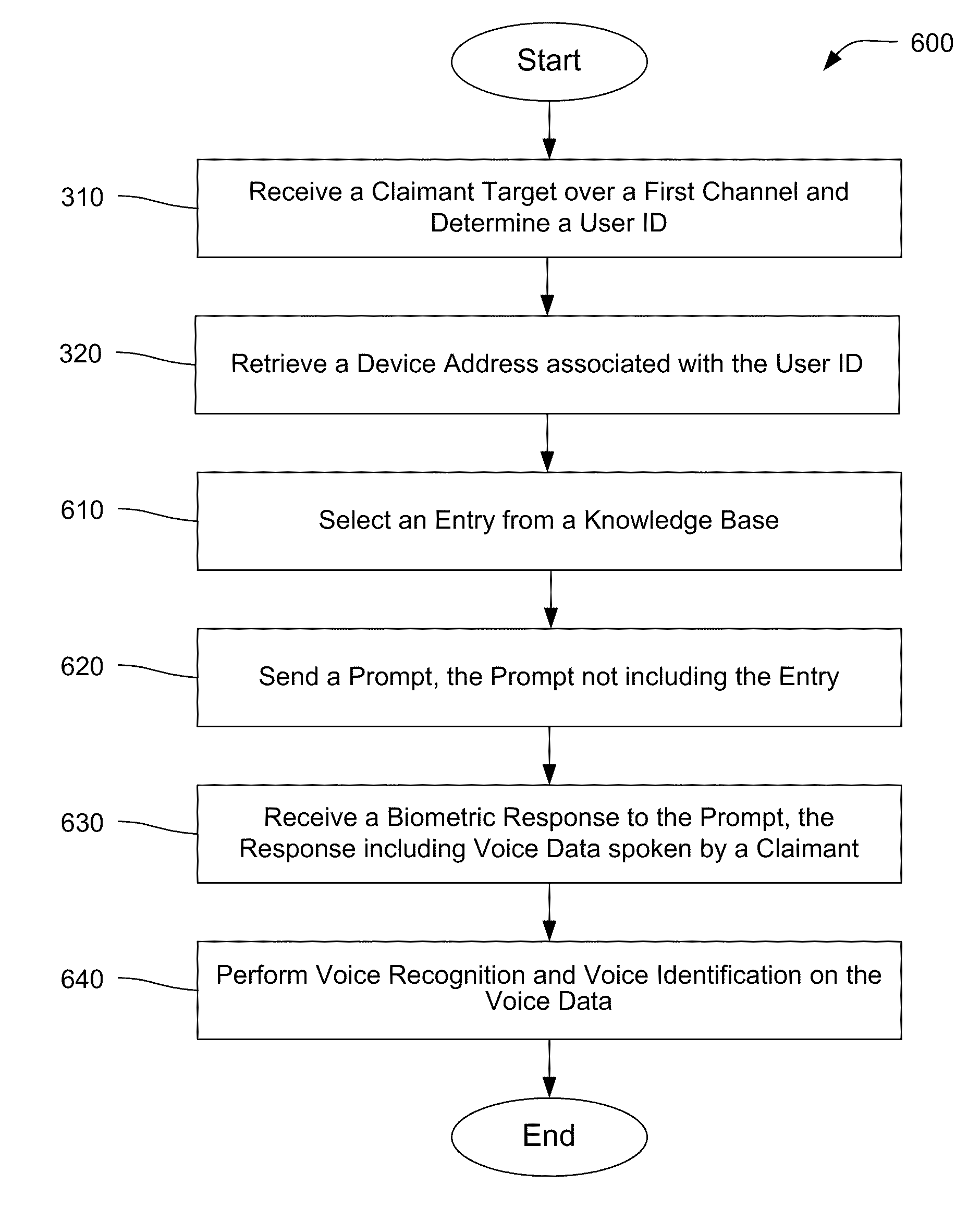
Single-Channel Multi-Factor Authentication
ActiveUS20090309698A1Electric signal transmission systemsMultiple keys/algorithms usageInternet privacyAuthentication
Systems and methods for authenticating electronic transactions are provided. The authentication methods employ a combination of security features. These security features can be based, for example, on unique knowledge of the person being authenticated, unique personal features and attributes of the person, the ability of the person to respond, and to do so in a fashion that a machine cannot, and so forth. Methods for enrolling the person prior to authentication are also provided, as well as systems for enrollment and authentication.
Owner:SAMSUNG ELECTRONICS CO LTD
Systems for three factor authentication
A method and apparatus for three-factor authentication using a short wireless device. The short wireless device stores a digital key and sends the digital key wirelessly to a third party application or device. The short wireless device can authenticate the user voice or movements in 2 dimensional or 3 dimensional space.
Owner:OPTIMA DIRECT LLC
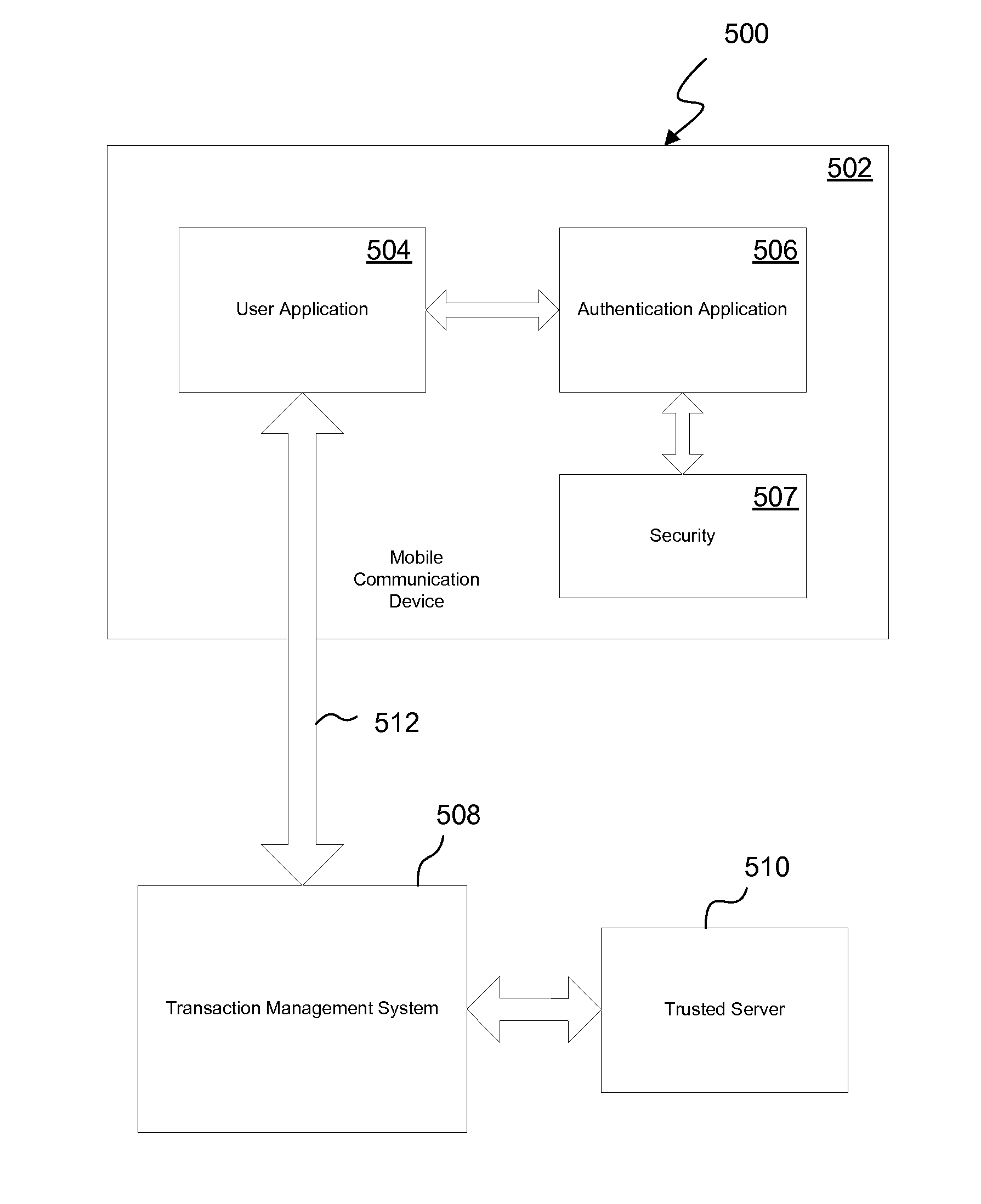
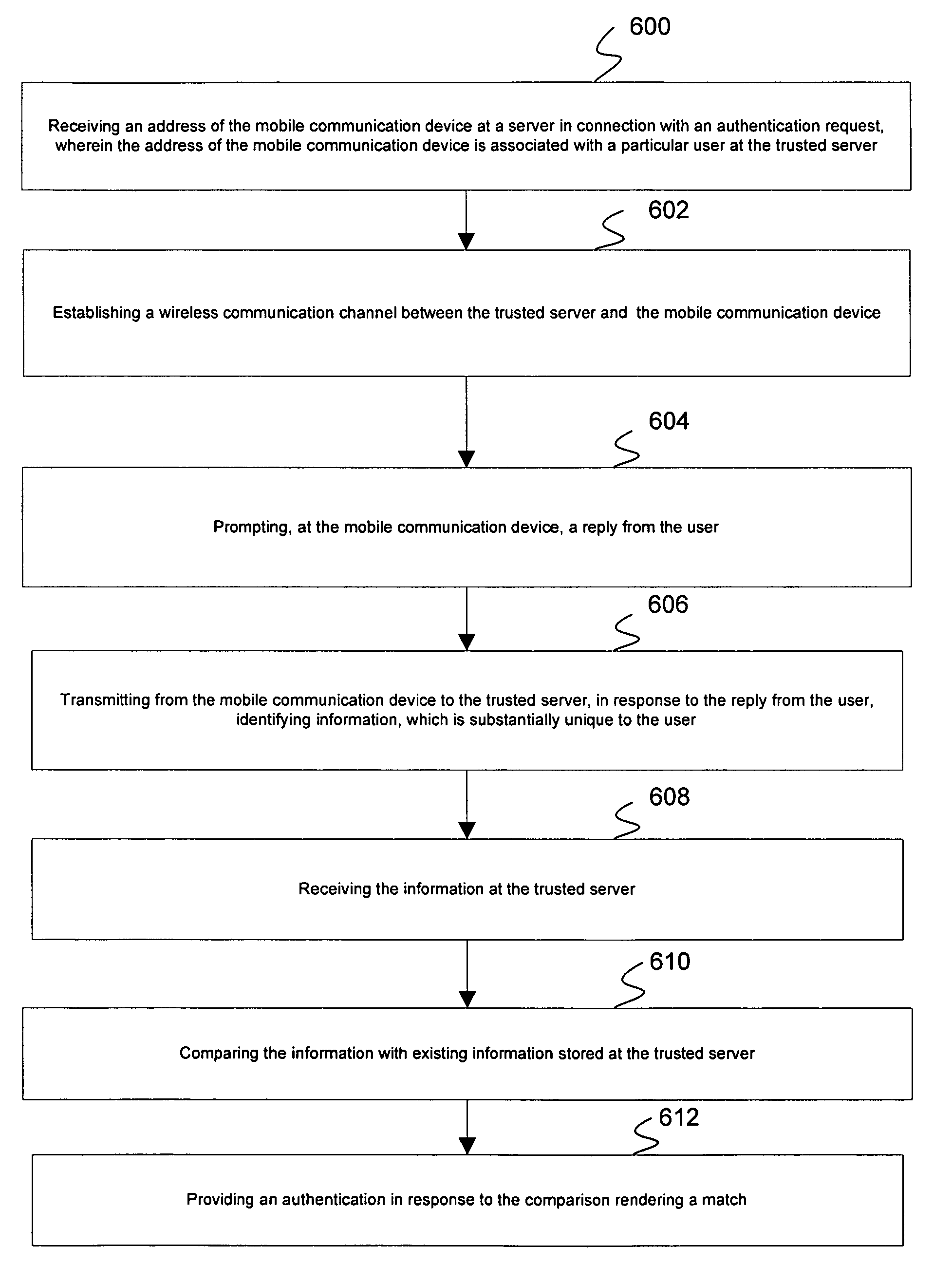
System and method for providing authentication and authorization utilizing a personal wireless communication device
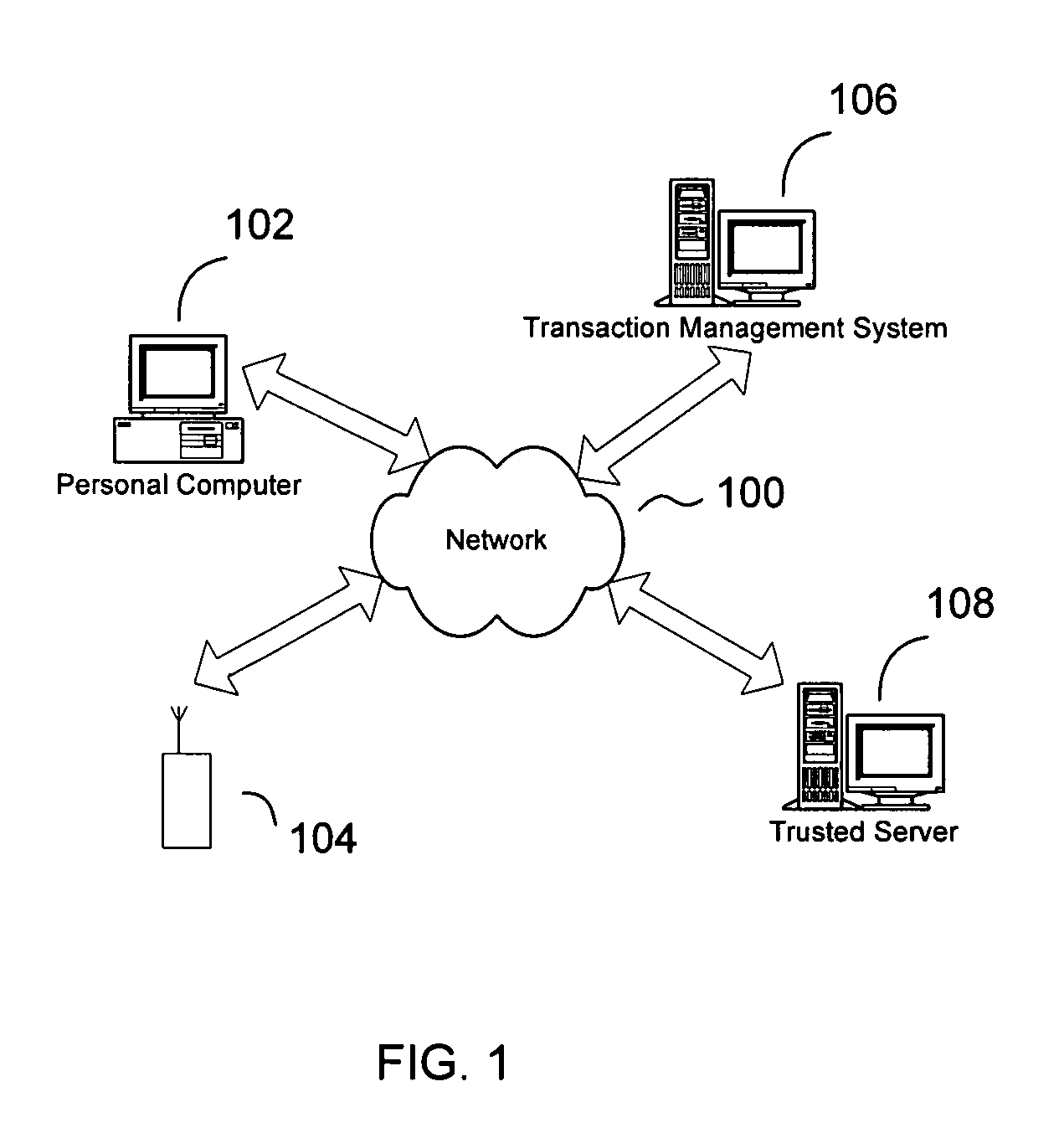
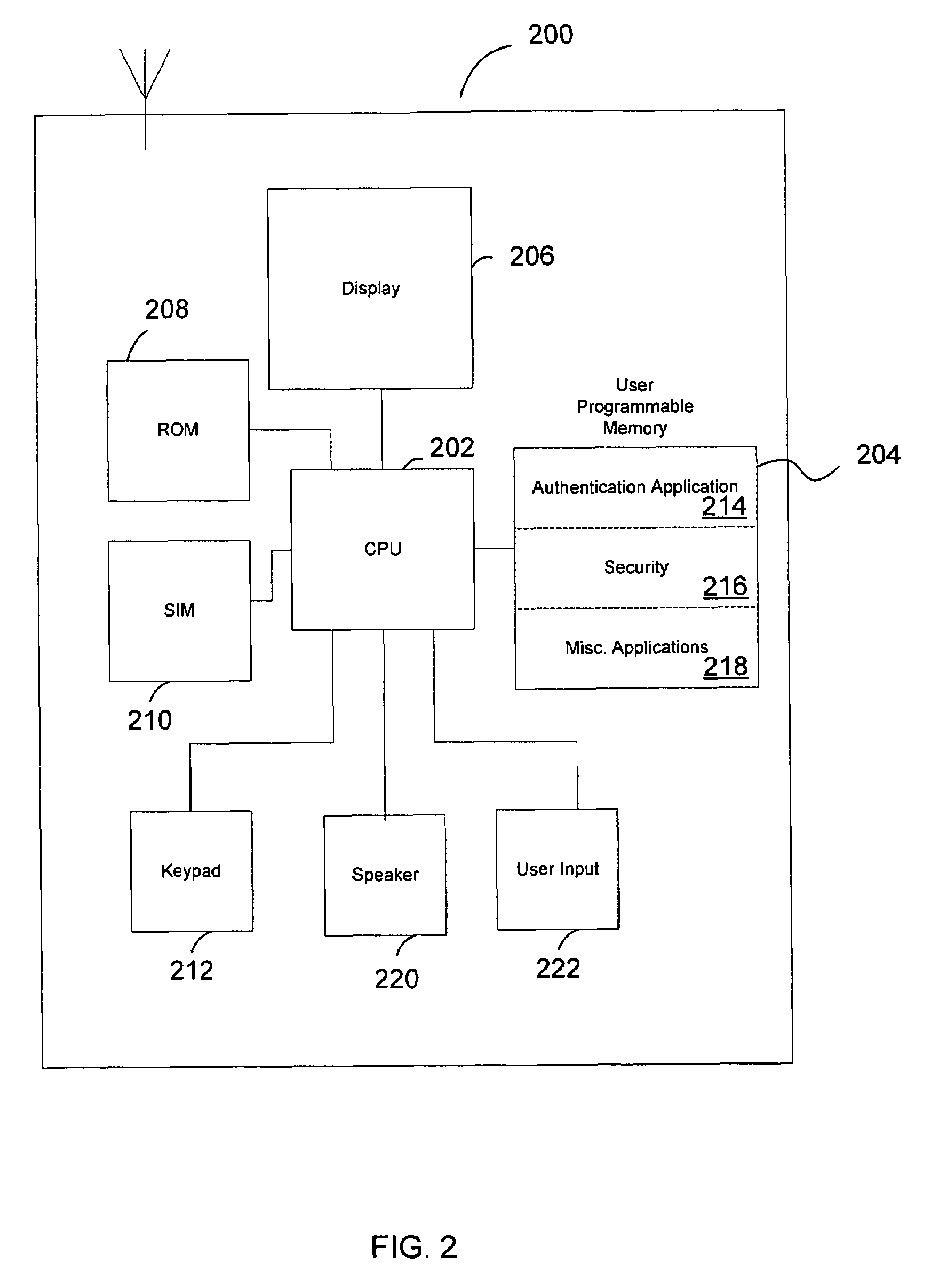
ActiveUS7697920B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyInternet privacy
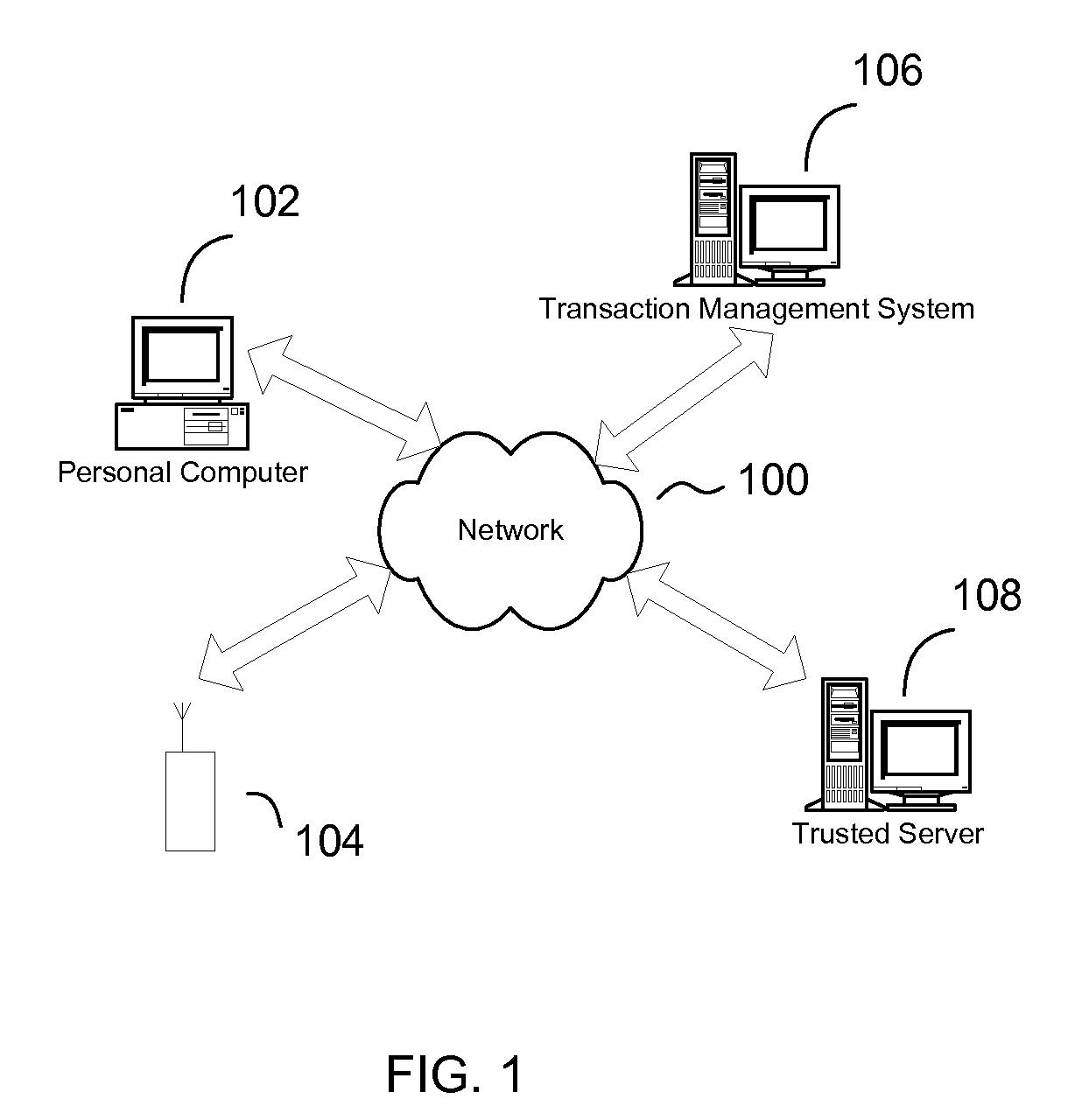
An authorization and authentication system utilizing a mobile communication device. The authentication and authorization system enables a trusted server, in conjunction with a user controlled mobile communication device (which has been registered with the trusted site), to authorize a transaction carried out at a transaction management system. An identity of the user is authenticated by a verification that the user is in possession of the mobile communication device. In this way, the transaction management system is able to effectuate an authorized transaction with confidence that the authorization was from the user and not a third party. In variations, the authentication is a multi-factor authentication, i.e., the user must both possess the mobile communication device and information, e.g., a password.
Owner:BOOJUM MOBILE
Mobile Device Transaction Using Multi-Factor Authentication
ActiveUS20120110341A1Reduce chanceImprove securityComputer security arrangementsPayment architectureThe InternetHand Held Computer
The following is a system in which a person may use a Cellular (Mobile) Telephone, a PDA or any other handheld computer to make a purchase. This is an example only. The process may entail any type of transaction which requires authentication, such as any financial transaction, any access control (to account information, etc.), and any physical access scenario such as doubling for a passport or an access key to a restricted area (office, vault, etc.). It may also be used to conduct remote transactions such as those conducted on the Internet (E-Commerce, account access, etc.). In the process, a multi-factor authentication is used.
Owner:BEIGI HOMAYOON
Multi-Channel Multi-Factor Authentication
ActiveUS20110302645A1Digital data processing detailsUser identity/authority verificationMulti-factor authenticationResponse capacity
Systems and methods for authenticating electronic transactions are provided. The authentication methods employ a combination of security features and communication channels. These security features can be based, for example, on unique knowledge of the person being authenticated, a unique thing that the person has, unique personal features and attributes of the person, the ability of the person to respond, and to do so in a fashion that a machine cannot, and so forth. Methods for enrolling the person prior to authentication are also provided, as well as systems for enrollment and authentication.
Owner:SAMSUNG ELECTRONICS CO LTD
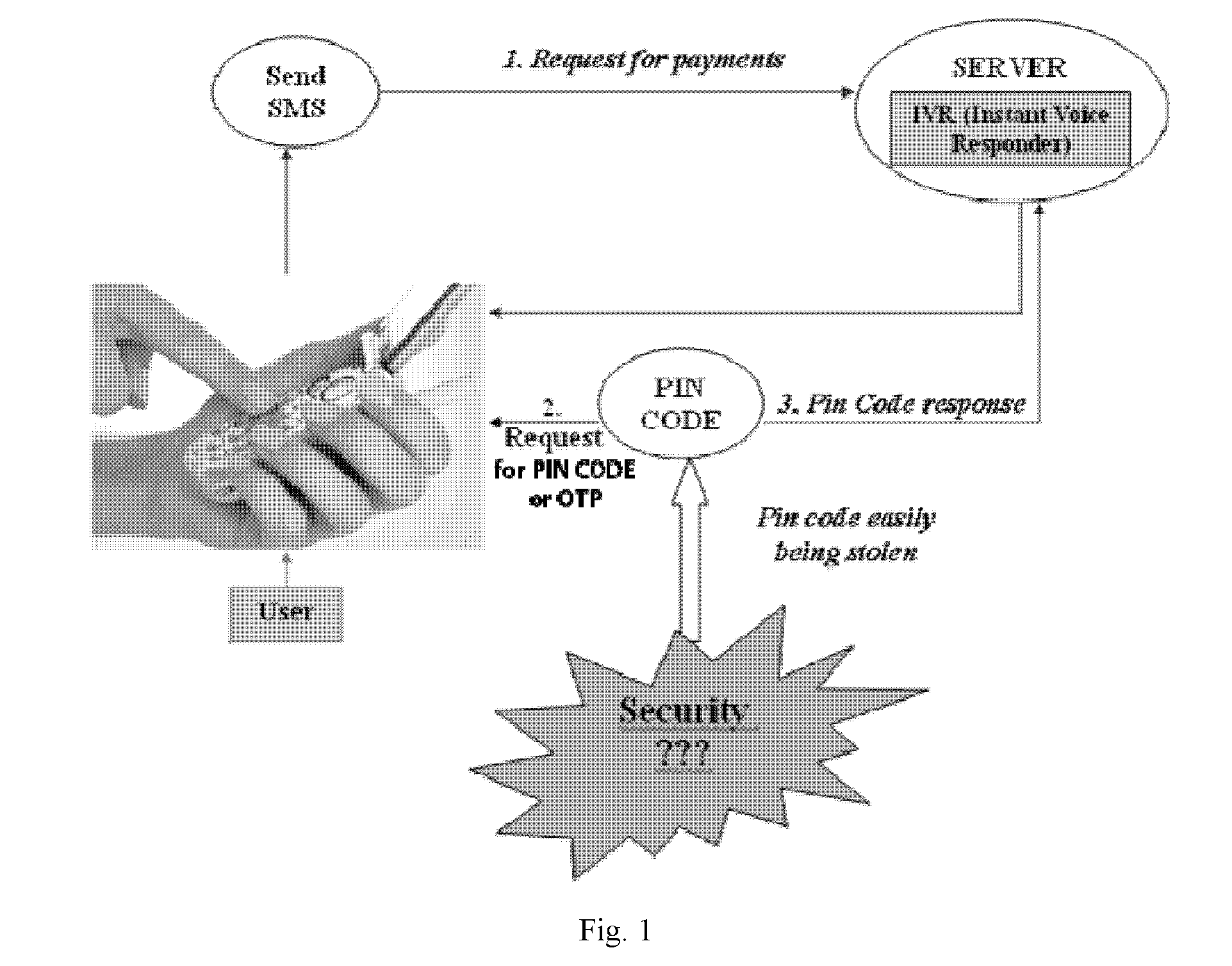
Simple two-factor authentication
InactiveUS20070107050A1Eliminate Internet fraudEasy accessRandom number generatorsUser identity/authority verificationPasswordThe Internet
Internet Security is increasingly of concern as more and more cases of identity theft of online data is reported. Simple login and password authentication for access to sensitive websites like financial, health or other personal data is no longer sufficient. Several mechanisms for additional security, called two-factor authentication have been proposed. Most of them involve the use of a physical device like a card which is read by a card reader or suggest the use of biometric authentication. Although, these are very secure, the cost of implementation of these “physical” authentications is high. This invention outlines the use of a simple two factor authentication using mobile phones, PDAs or Credit and Debit cards that most users already have, without the need for any special hardware.
Owner:JEXP
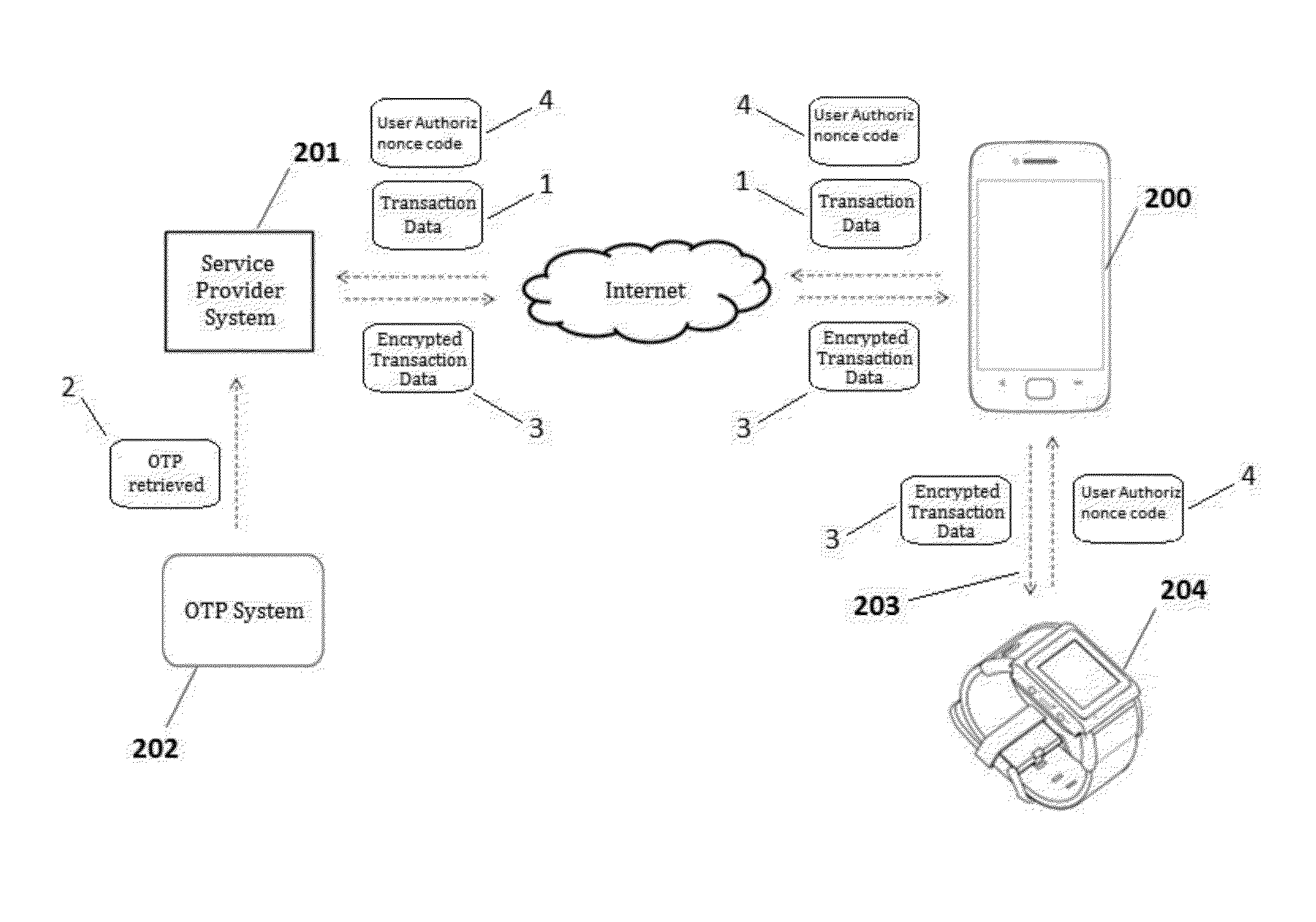
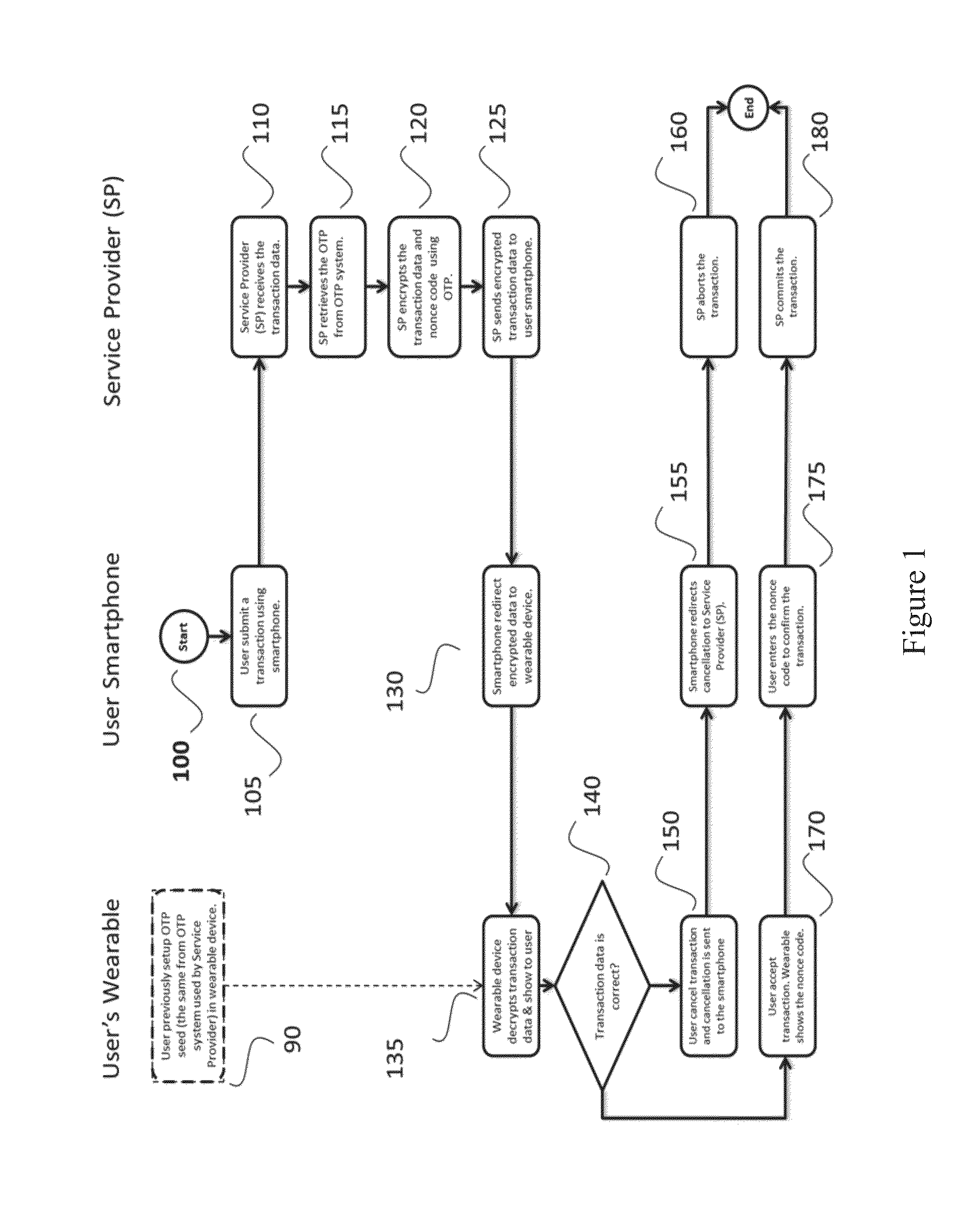
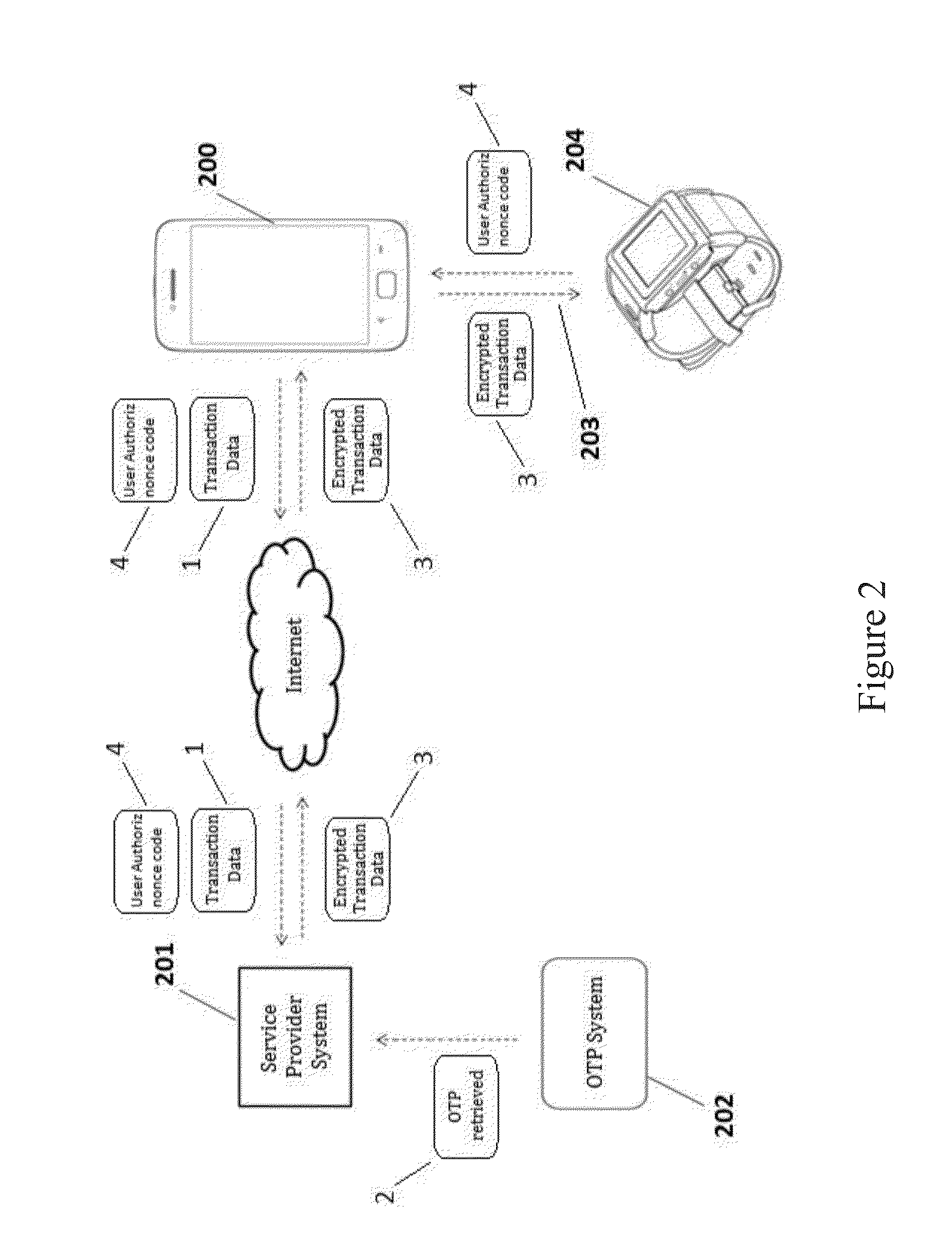
Method for multi-factor transaction authentication using wearable devices
The present invention relates to a method (100) for multi-factor authentication, which uses wearable devices as a secondary device (204) in conjunction with a primary / main device (200) (e.g., the smartphone of user who conducts the electronic transaction) to allow the user to verify the data integrity of electronic transaction before authorizing it (out of possible compromised device e.g. smartphone).
Owner:SAMSUNG ELECTRONICSA AMAZONIA LTDA
Method for Replacing Traditional Payment and Identity Management Systems and Components to Provide Additional Security and a System Implementing Said Method
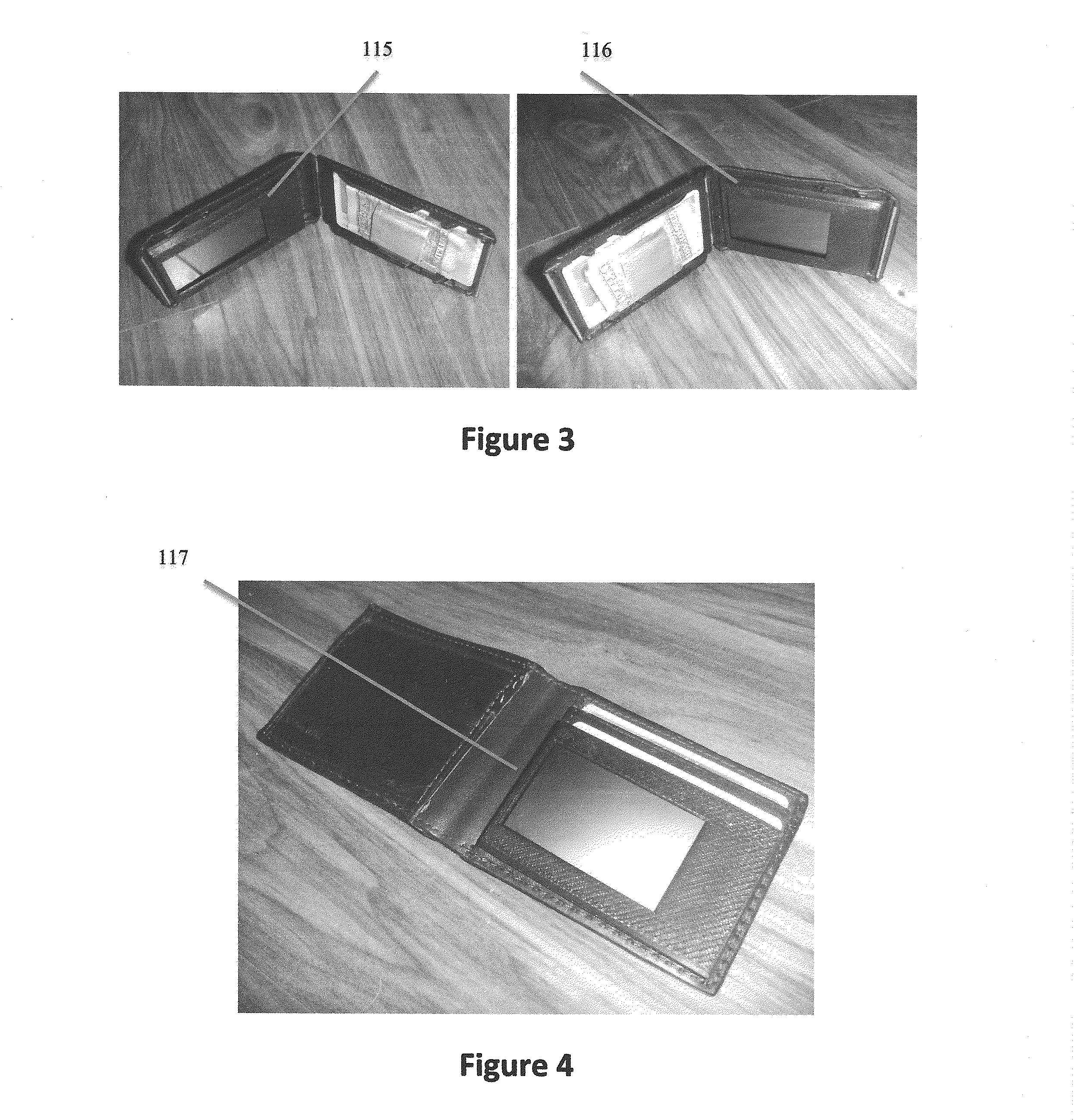
InactiveUS20140108241A1Improve securityReduce in quantityFinanceComputer security arrangementsComputer hardwarePayment
An electronic wallet system that protects payment accounts, identification and other personal information found within a typical wallet with a secure electronic vault (first) device that can be part of a physical wallet, insert to a wallet, or in other embodiments, wearable / portable devices. A unique biometrically enabled multi-factor authentication process ensures only owners of the information can copy the information to the device or retrieve it thereafter. Authenticated users may then select payment, identification, medical or virtually any private information via touch display or voice command on the vault or on another (second) device that operates in conjunction with the vault. The second device comprises, for example, a programmable card with dynamic magnetic stripe, cell phone, or other wearable technology, that initiates and processes a payment and / or transfer of private information.
Owner:GARMIN INT
Multi-channel multi-factor authentication
InactiveUS8006291B2Digital data processing detailsUser identity/authority verificationInternet privacyResponse capacity
Systems and methods for authenticating electronic transactions are provided. The authentication methods employ a combination of security features and communication channels. These security features can be based, for example, on unique knowledge of the person being authenticated, a unique thing that the person has, unique personal features and attributes of the person, the ability of the person to respond, and to do so in a fashion that a machine cannot, and so forth. Methods for enrolling the person prior to authentication are also provided, as well as systems for enrollment and authentication.
Owner:SAMSUNG ELECTRONICS CO LTD
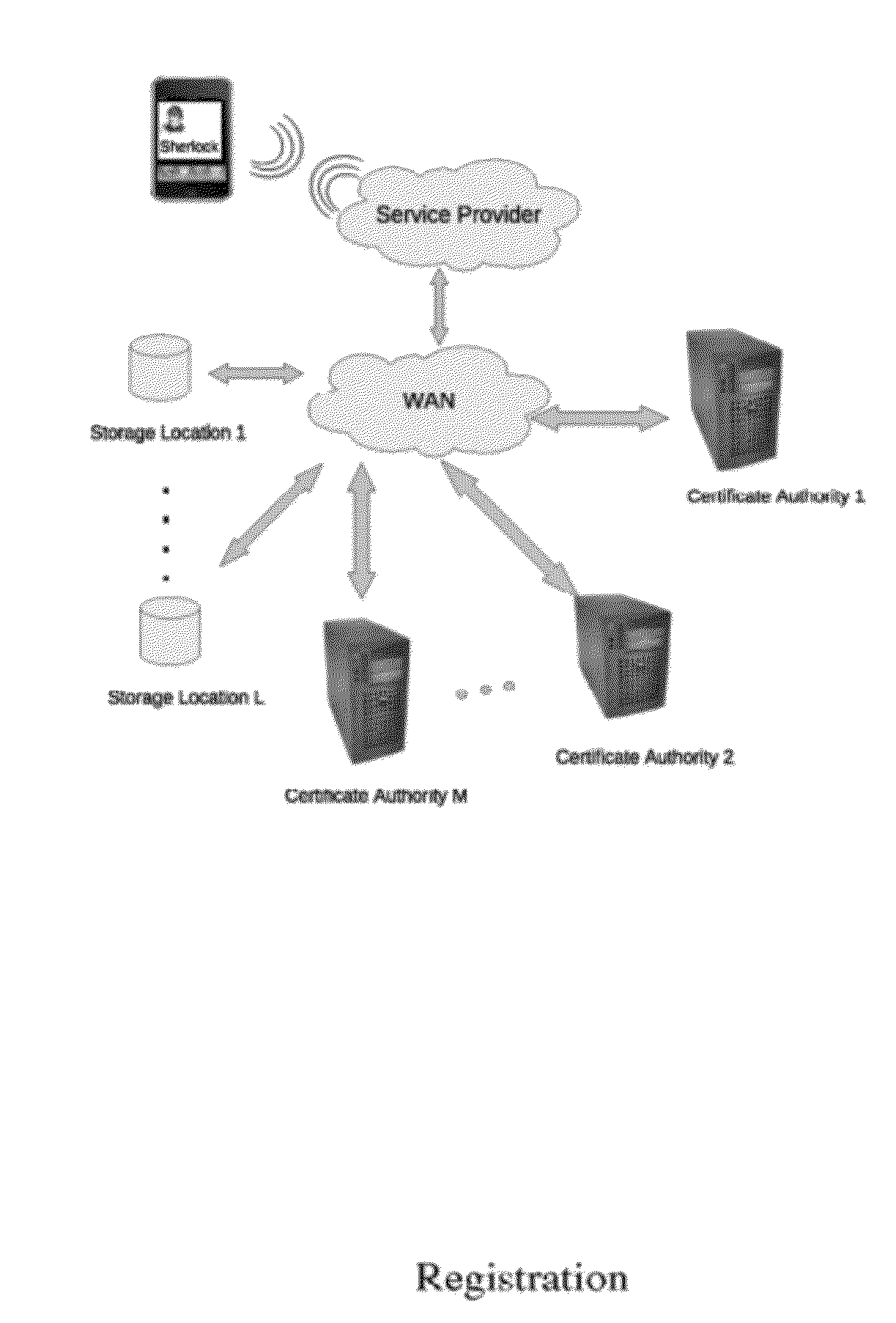
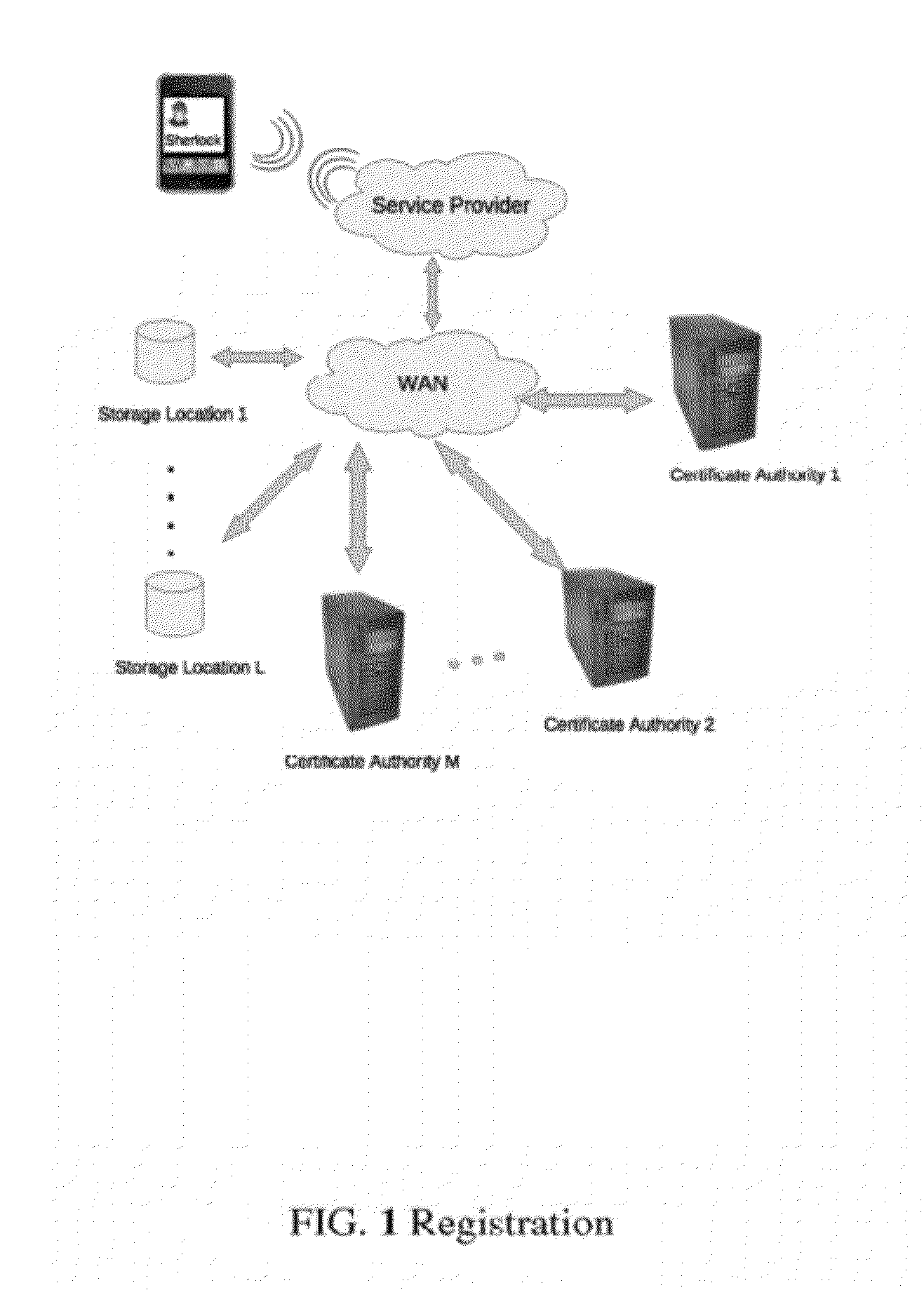
Shared Registration Multi-Factor Authentication Tokens
ActiveUS20120174198A1Avoid changeDigital data processing detailsMultiple digital computer combinationsChain of trustRegistration system
A system and method for more efficiently establishing a chain of trust from a registrant to a registry. A registrant credential is associated with a Shared Registration command and is sent by a registrar to a registry. Upon successful validation, a token is generated and bound to a registrant identifier. The token is included along with the registrant identifier in subsequent discrete Shared Registration commands submitted to the registry on behalf of the registrant. The registrant thus needs to submit its credential only once for changes that require several discrete commands. Also, it is more efficient for the Shared Registration System to validate a token for a set of commands than to validate different registrant credential for each discrete command.
Owner:VERISIGN
Identity Theft and Fraud Protection System and Method
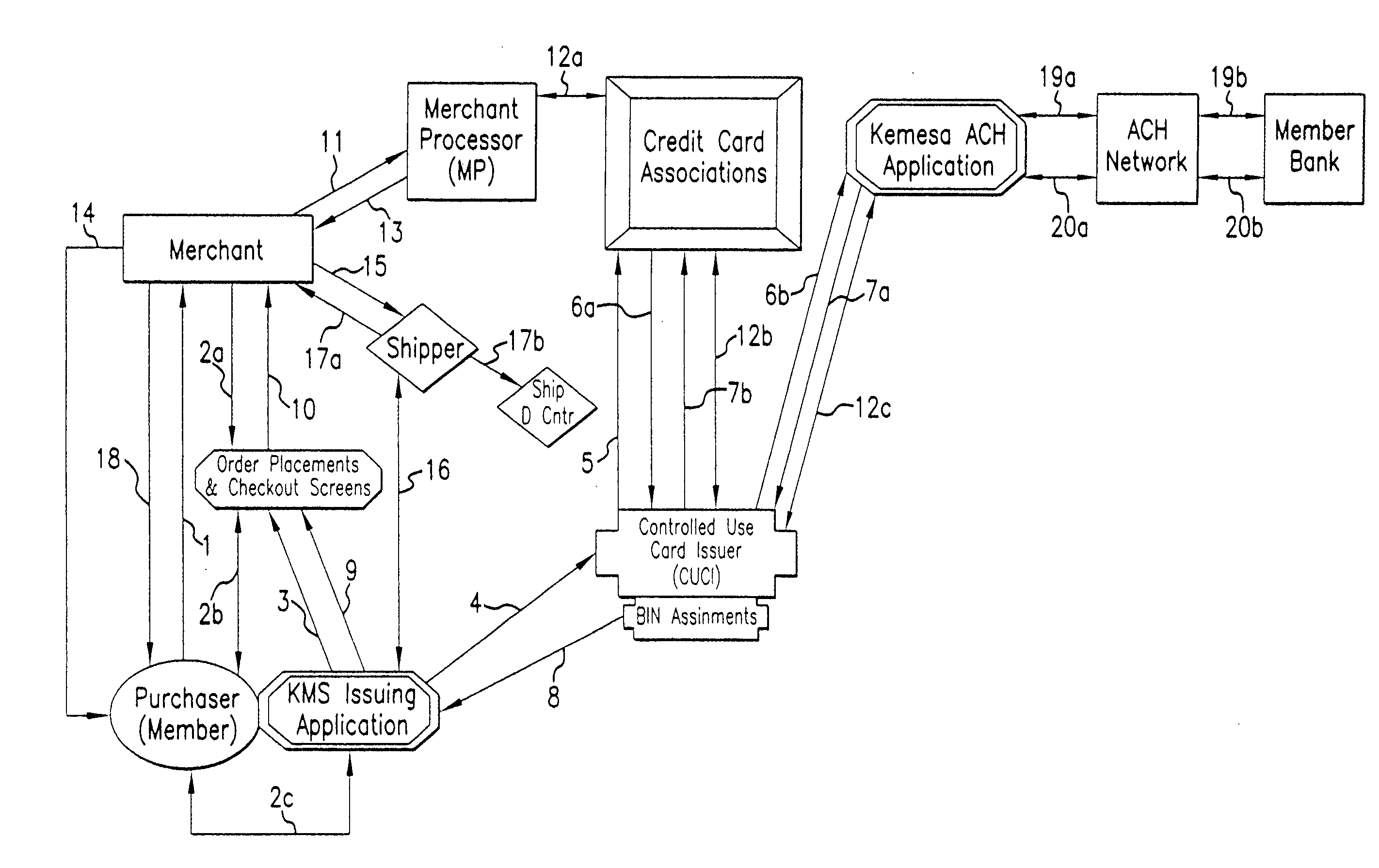
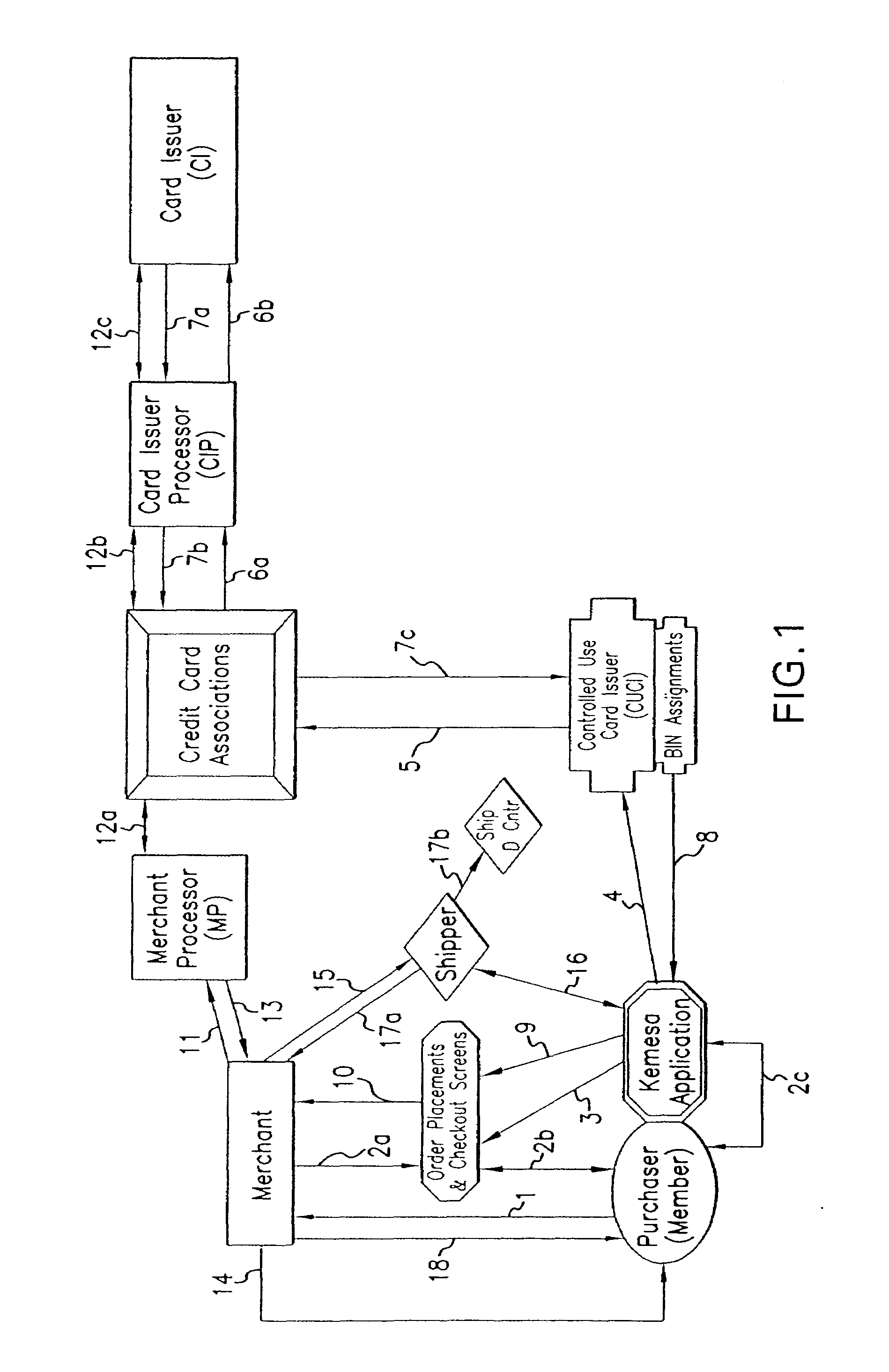
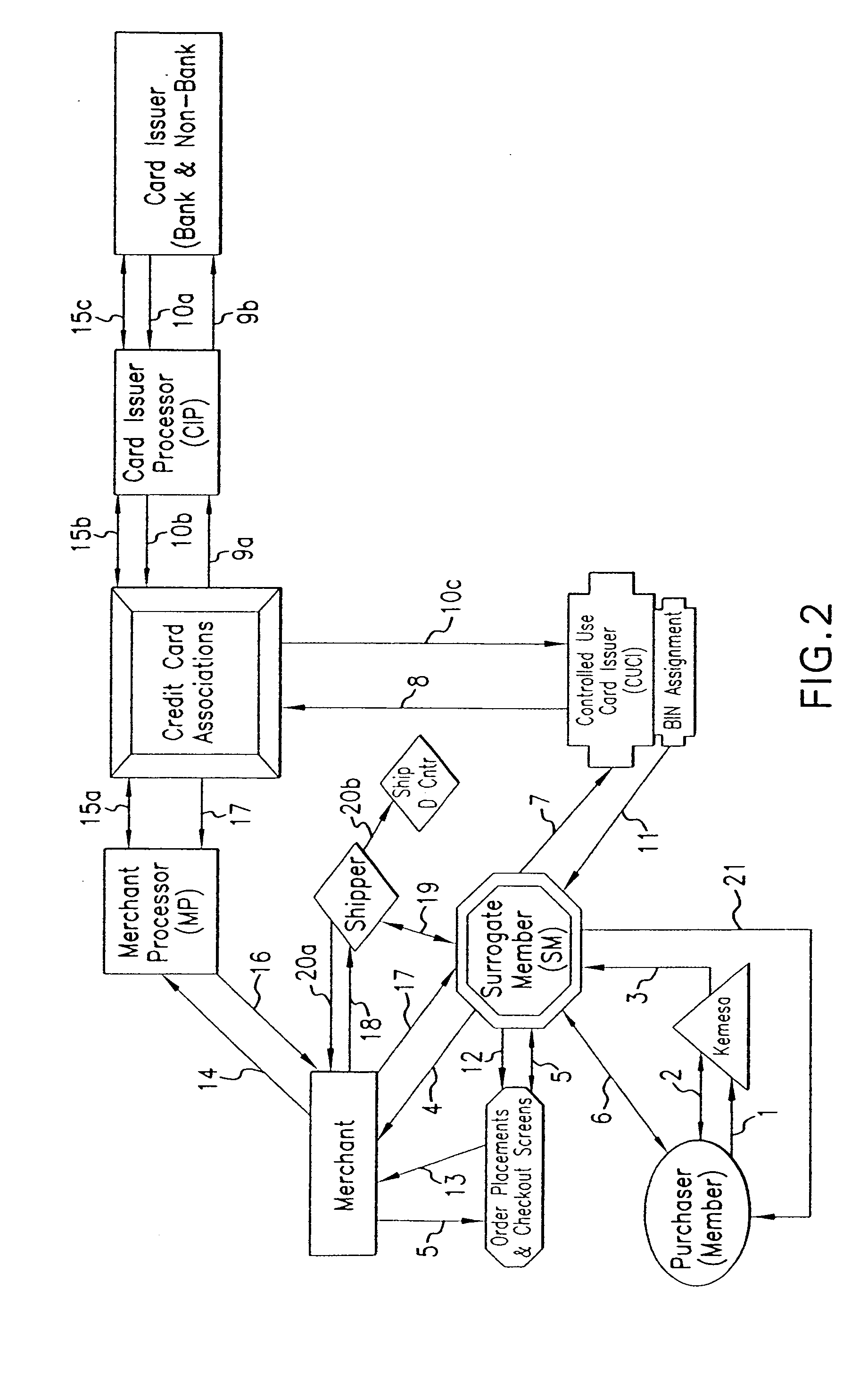
A system and method for preventing personal identity theft when making online and offline purchases requires a Purchaser to first subscribe and become a Member user by registering, providing relevant personal identity information, and establishing two-way multi-factor authentication information for security purposes. The subscribing Member provides relevant information to any one or more financial sources (e.g. credit card accounts, bank accounts) that will be used to fund subsequent purchase transactions. Once registered, the Member is assigned a user name and a password. The subscribing Member's personal identity information is then encrypted and stored at one or more highly secure locations. The ID protection system obtains a controlled use card (CUC) through a CUC issuer on behalf of the Member for use in making each purchase transaction. The CUC is anonymous with respect to user (Member) identity and may be a purchase-specific single-use card or a multi-purpose card with no traceable connection to any other financial account. The CUC is funded by the Member's one or more financial sources, as selected by the Member. When the Member makes a secure purchase, the Merchant is presented with anonymous information (i.e. not revealing the Member's real name, email address, billing information, etc.), except in instances where the Member's real identity information is required (e.g. airline tickets). The Merchant obtains credit approval and sends the shipping information to a shipper which independently obtains the correct shipping name and address from the ID protection system prior to shipping the purchased product(s) to the ultimate destination selected by the purchasing Member.
Owner:AURA SUB LLC +1
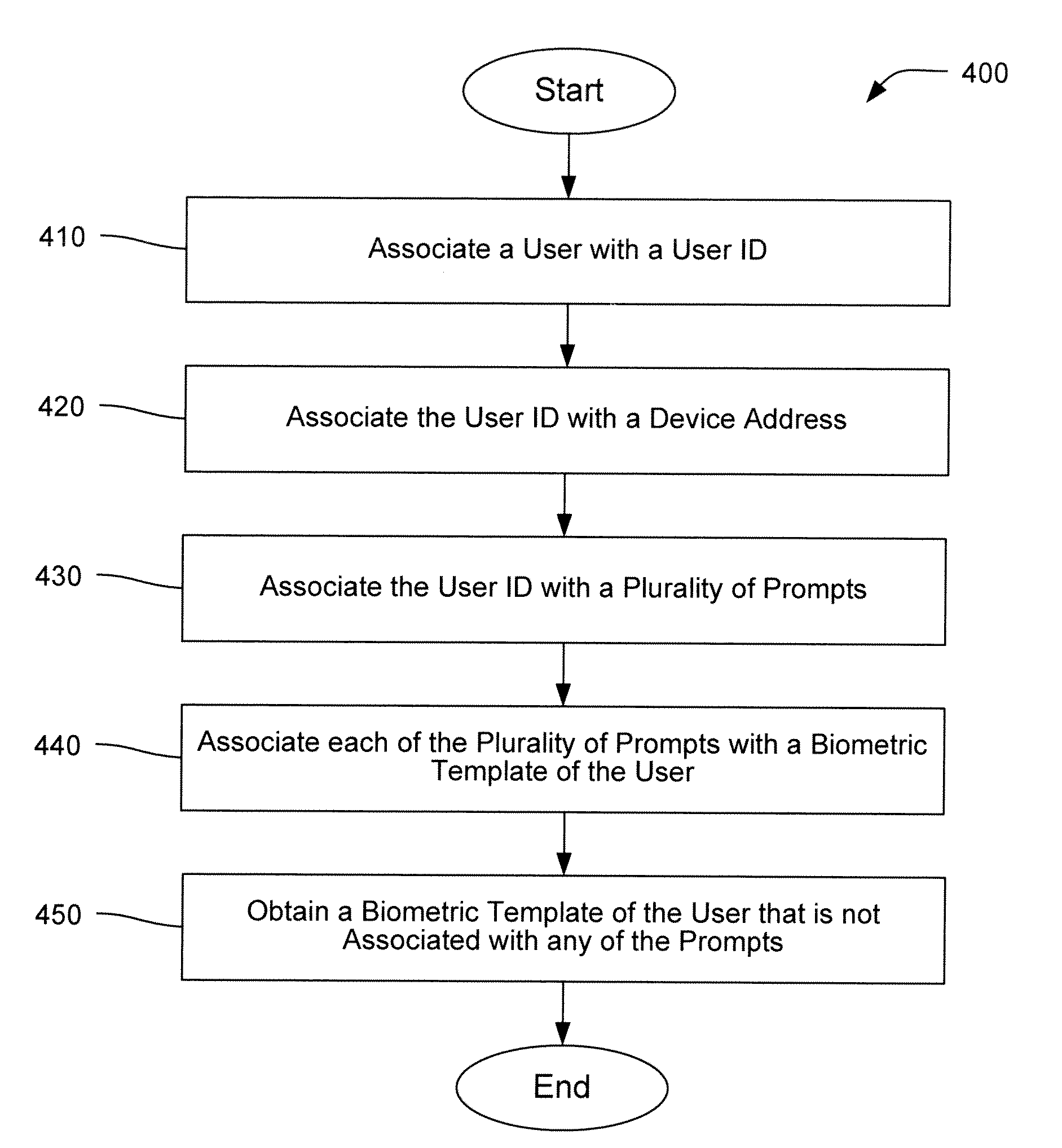
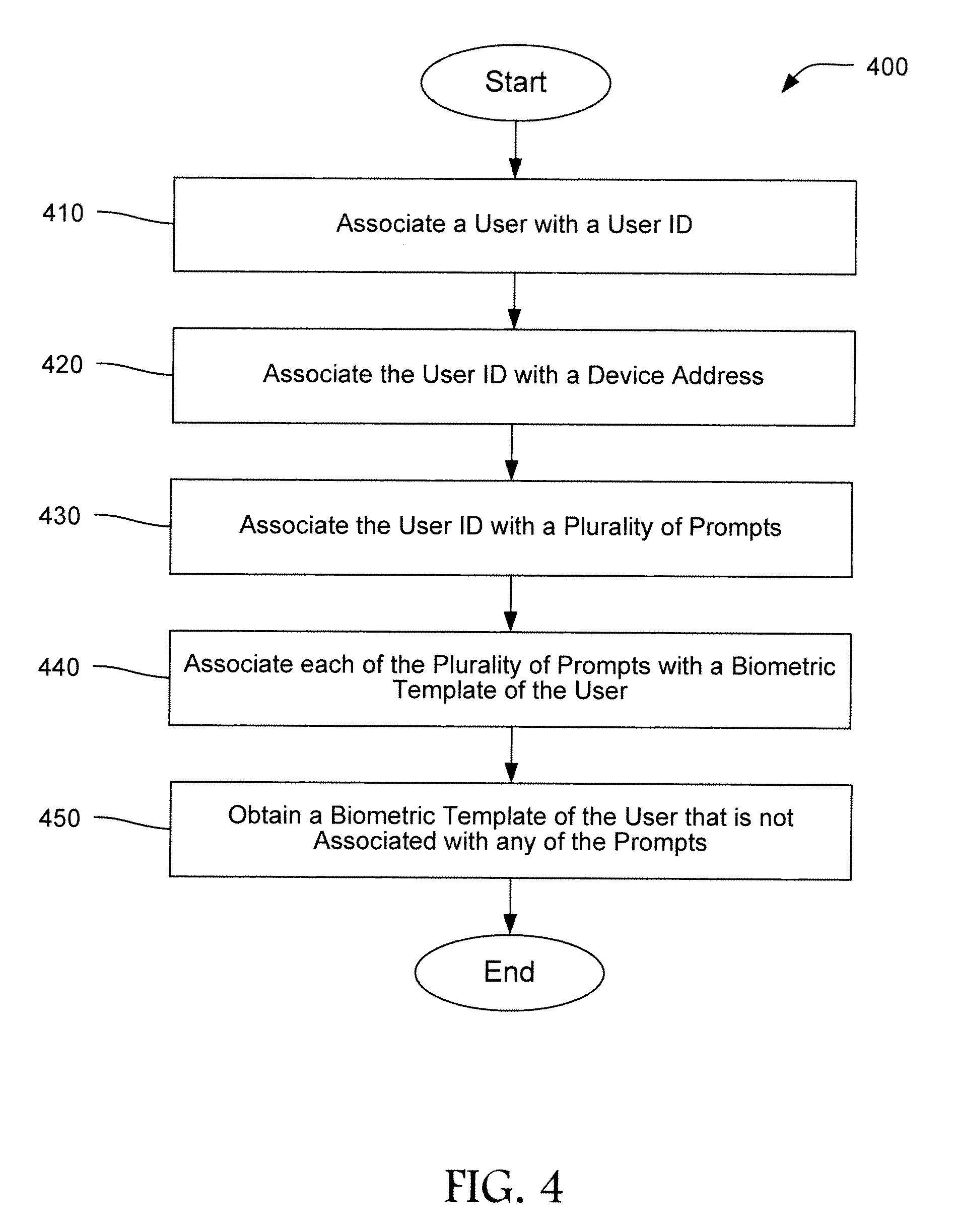
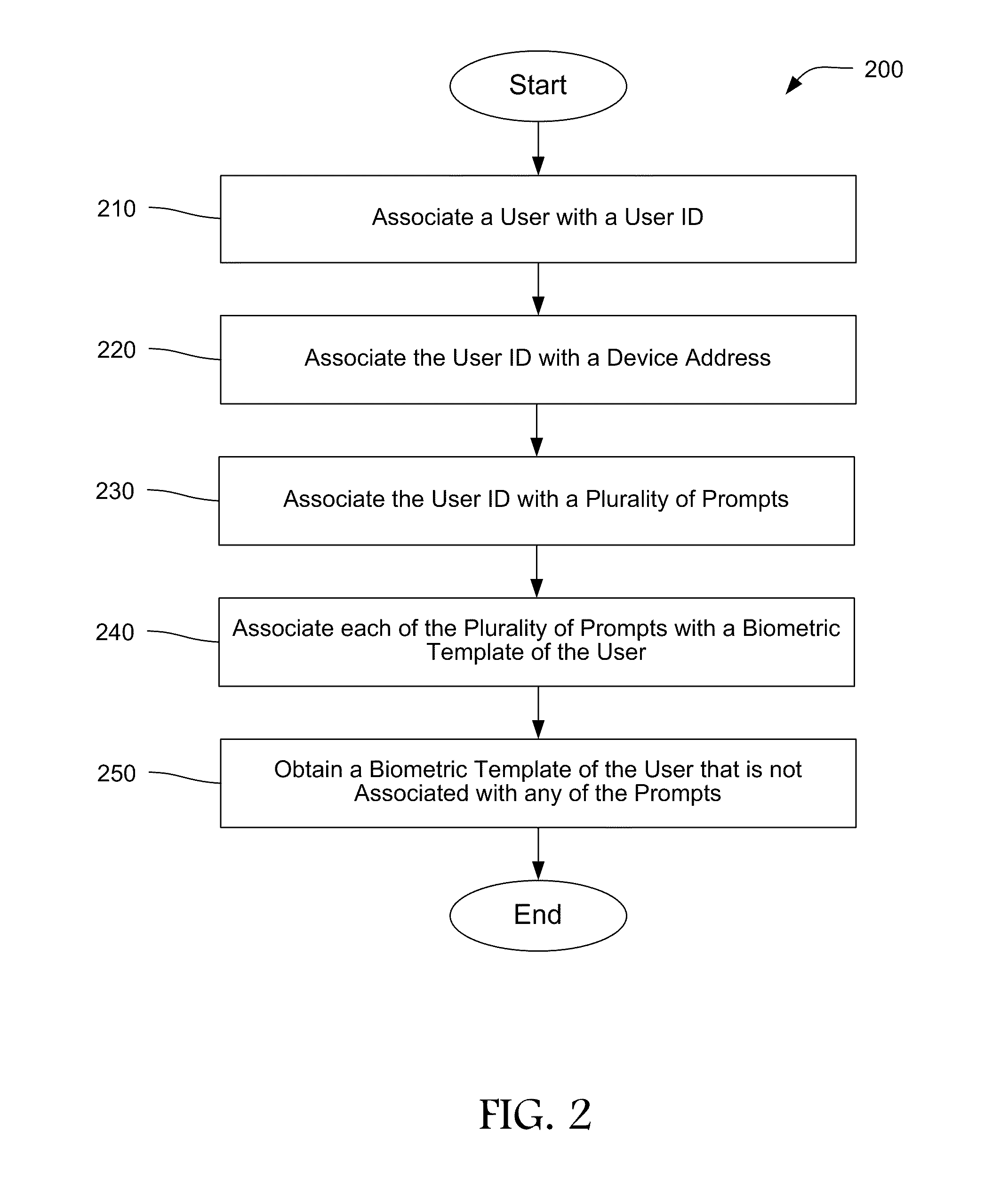
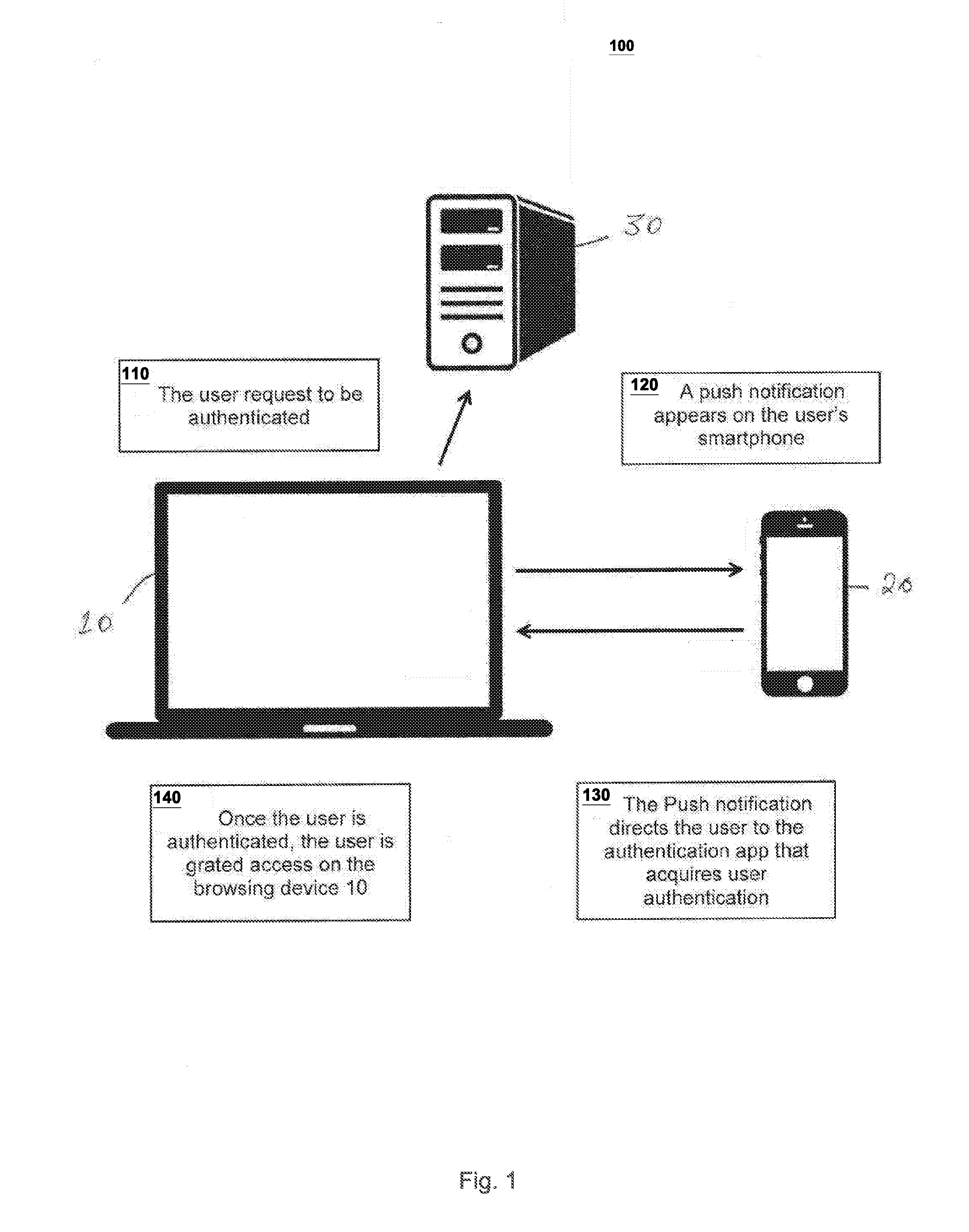
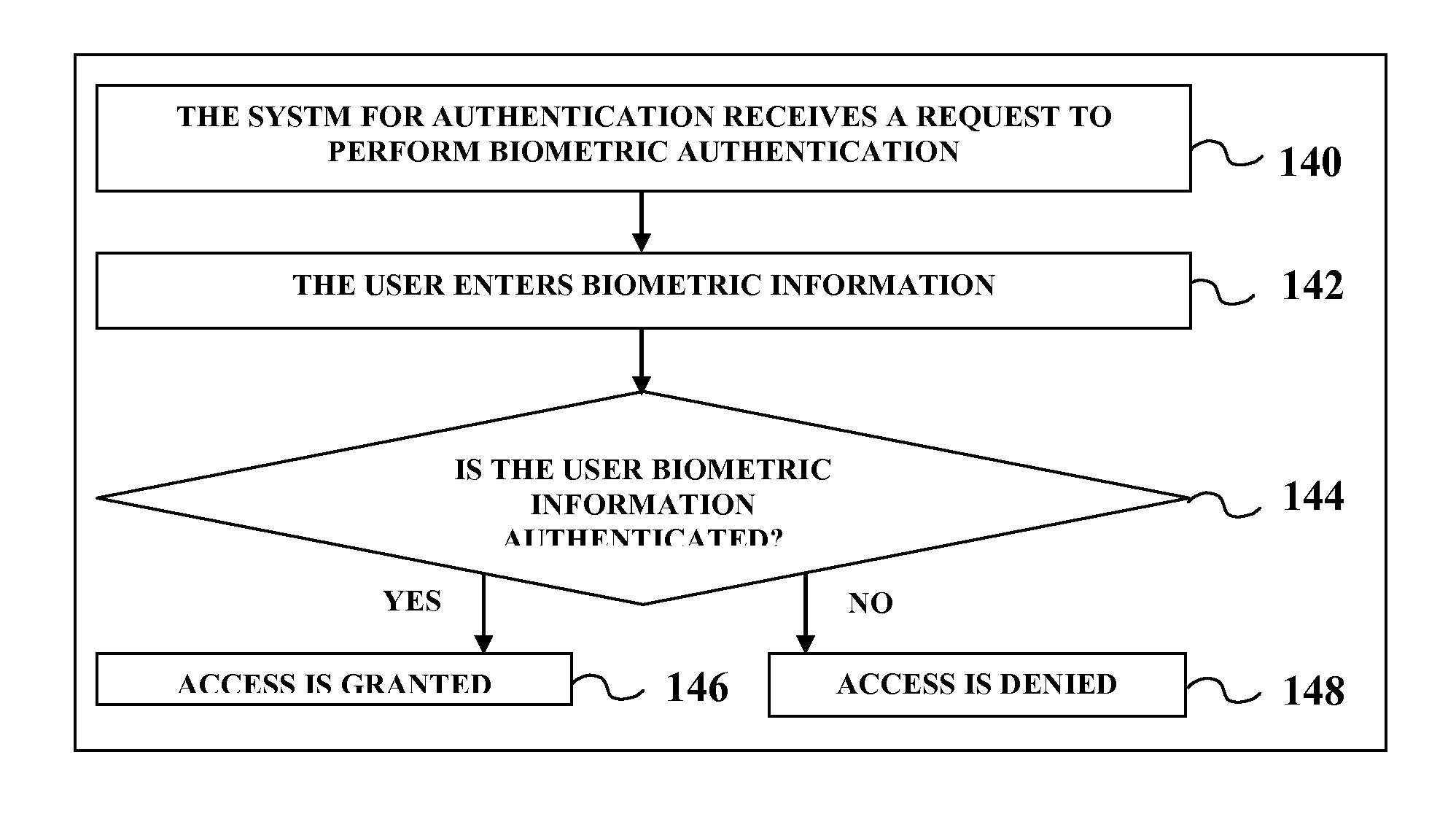
Multi-factor user authentication
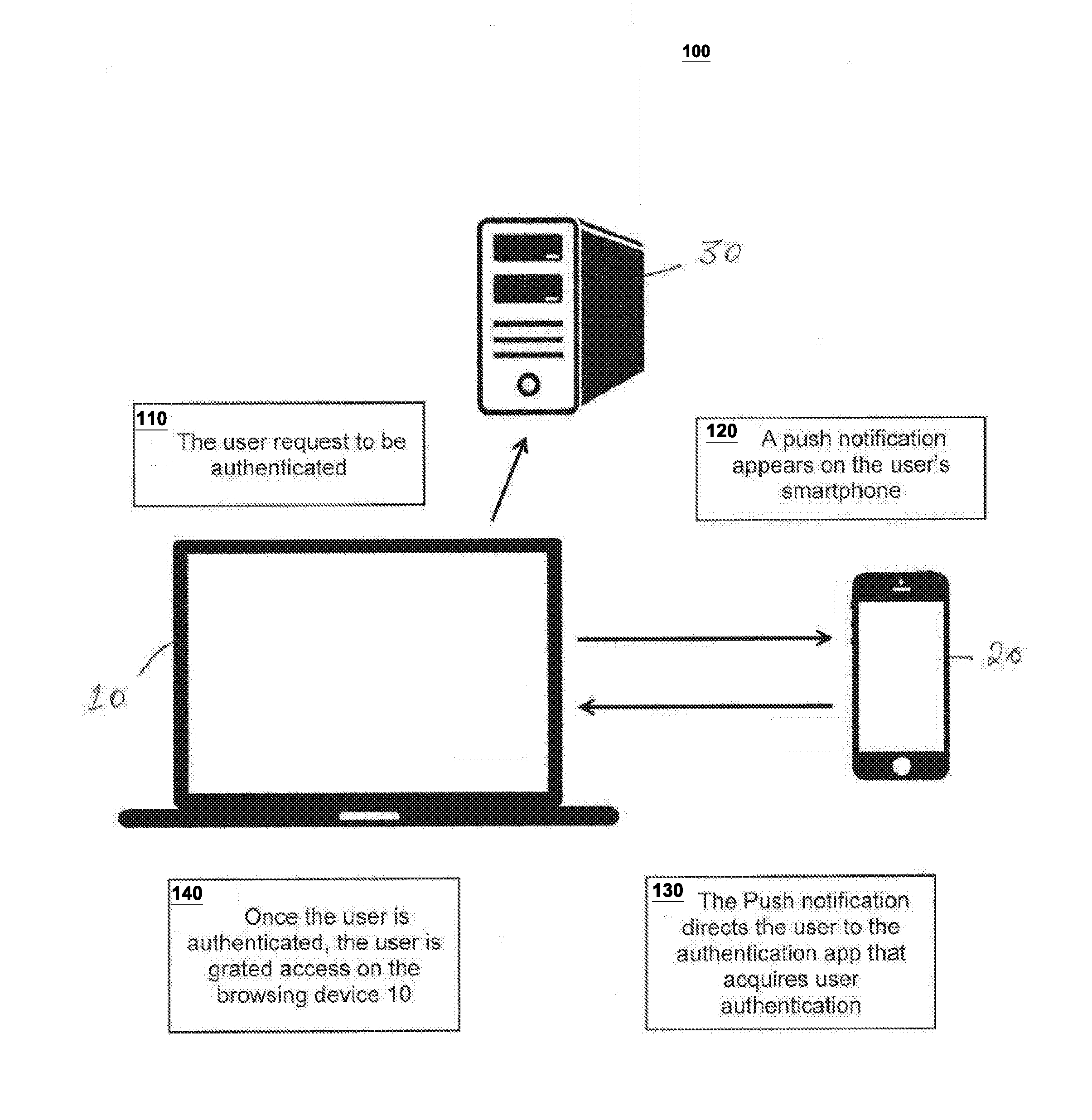
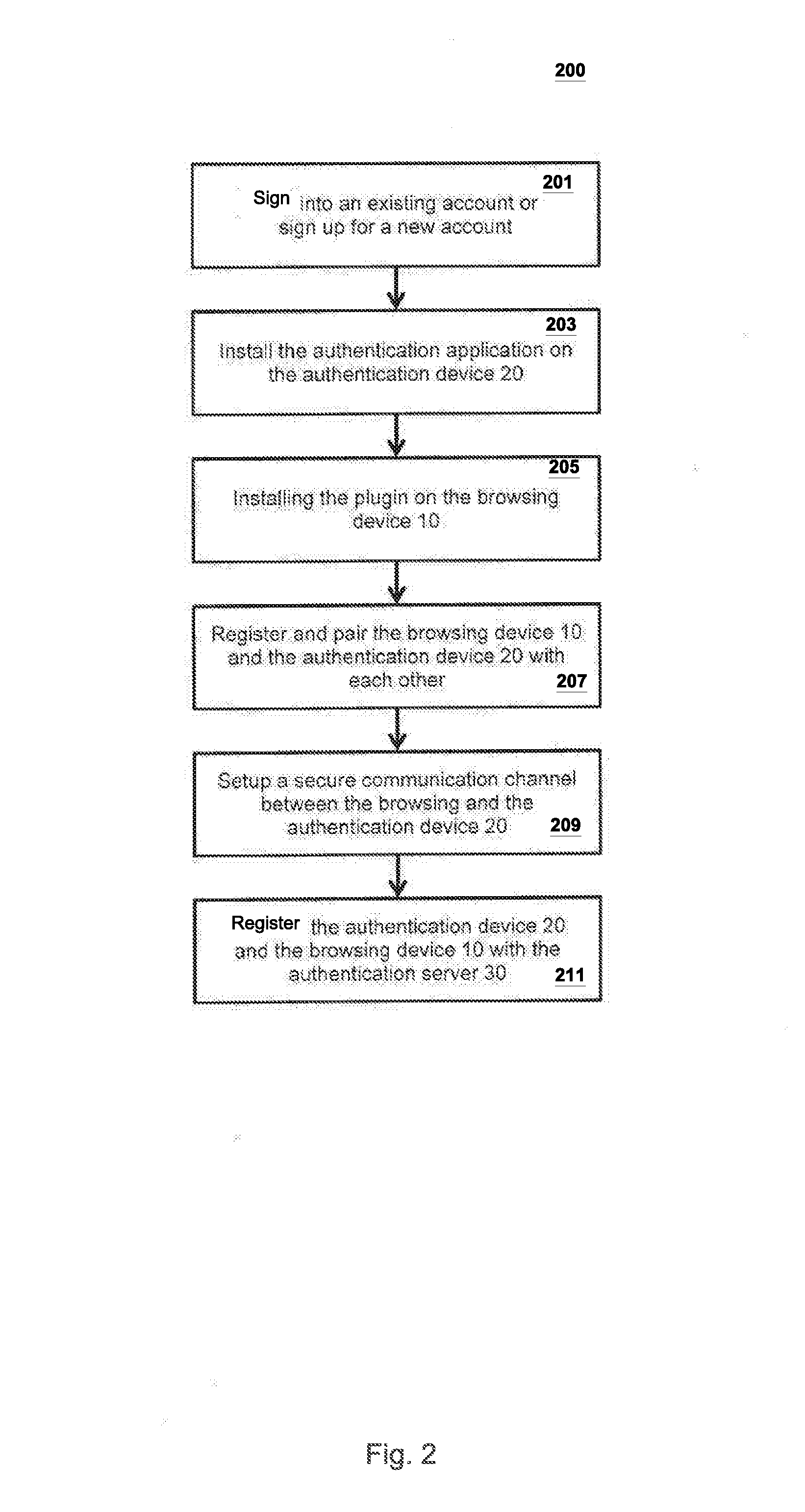
Embodiments of the present invention relates to a multi-factor authentication system and method using an authentication device, a browsing device and an authentication server. Authentication requires a user to keep an authentication device within a certain proximity of a browsing device, and to authenticate locally to the authentication device using biometric information. The biometric information of the user is stored locally in the authentication device to prevent the need to transmit sensitive biometric information to an authentication server. The authentication server is capable of detecting unusual activity based on information received from the authentication device and the browsing device.
Owner:WIACTS INC
Multiple factor user authentication system
InactiveUS20090063850A1Avoid attackUser identity/authority verificationDigital data authenticationUser authenticationUser identifier
The present invention describes a method and a system for multi-level authentication of a user and a server. The user registration process in the invention enables user to personalize the web page of the server. Further, the user authentication takes place in a multi-step process including entering credentials such as user ID, subset of user's password, subset of shared secret and a One Time Password (OTP). The system of the present invention provides various means of entering the said credentials which prevents phishing attacks.
Owner:JORAM SHARWAN KUMAR +3
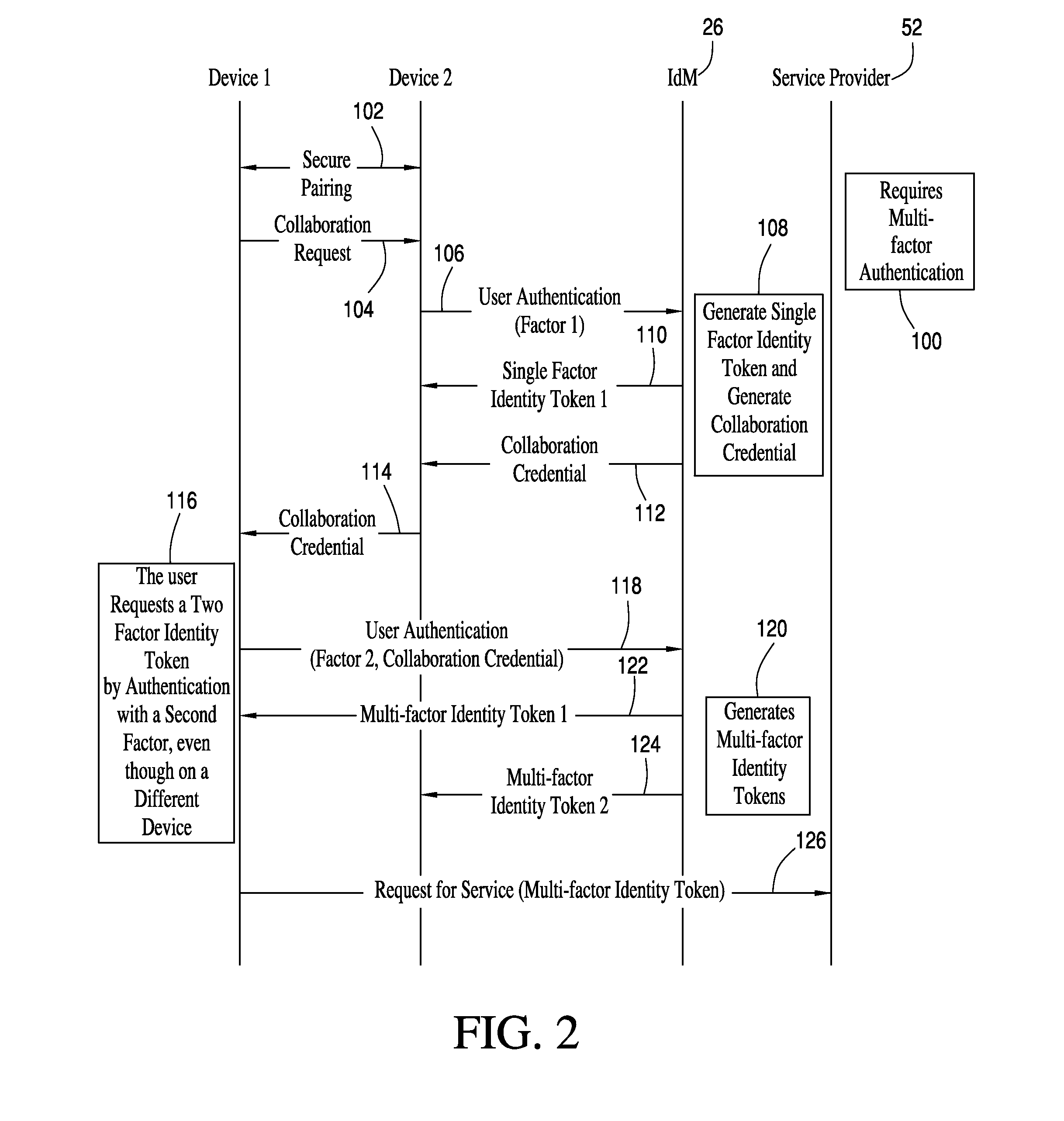
Apparatus for and method of multi-factor authentication among collaborating communication devices
ActiveUS20140189841A1Digital data processing detailsMultiple digital computer combinationsMulti-factor authenticationCollaboration
Multi-factor authentication is enabled across a plurality of communication devices. A user performs authentication by using a first authentication factor on a first of the communication devices, and by using a second authentication factor on a second of the communication devices. A collaboration credential is shared among the devices to enable the devices to collaborate with each other. Both of the authentication factors are bound together. A multi-factor identification token is issued to each device, to support multi-factor authentication for the user across the devices.
Owner:MOTOROLA SOLUTIONS INC
Systems for three factor authentication
A method and apparatus for three-factor authentication using a short wireless device. The short wireless device stores a digital key and sends the digital key wirelessly to a third party application or device. The short wireless device can authenticate the user voice or movements in 2 dimensional or 3 dimensional space.
Owner:OPTIMA DIRECT LLC
Token for use in online electronic transactions
InactiveUS20050044393A1Improve reliabilityReduce fraudDigital data processing detailsUser identity/authority verificationInternet privacyAuthentication
An online transaction system configured to implement authentication methods that allow for strong multi-factor authentication in online environments. The authentication methods can be combined with strong security methods to further ensure that the authentication process is secure. Further, the strong multi-factor authentication can be implemented with zero adoption dependencies through the implementation of automated enrollment methods.
Owner:U S ENCODE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com