Patents
Literature
61 results about "Secured transaction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Generally, a secured transaction is a loan or a credit transaction in which the lender acquires a security interest in collateral owned by the borrower and is entitled to foreclose on or repossess the collateral in the event of the borrower's default. The terms of the relationship are governed by a contract, or security agreement. A common example would be a consumer who purchases a car on credit. If the consumer fails to make the payments on time, the lender will take the car and resell it, applying the proceeds of the sale toward the loan. Mortgages and deeds of trust are another example. In the United States, secured transactions in personal property (that is, anything other than real property) are governed by Article 9 of the Uniform Commercial Code (U.C.C.).
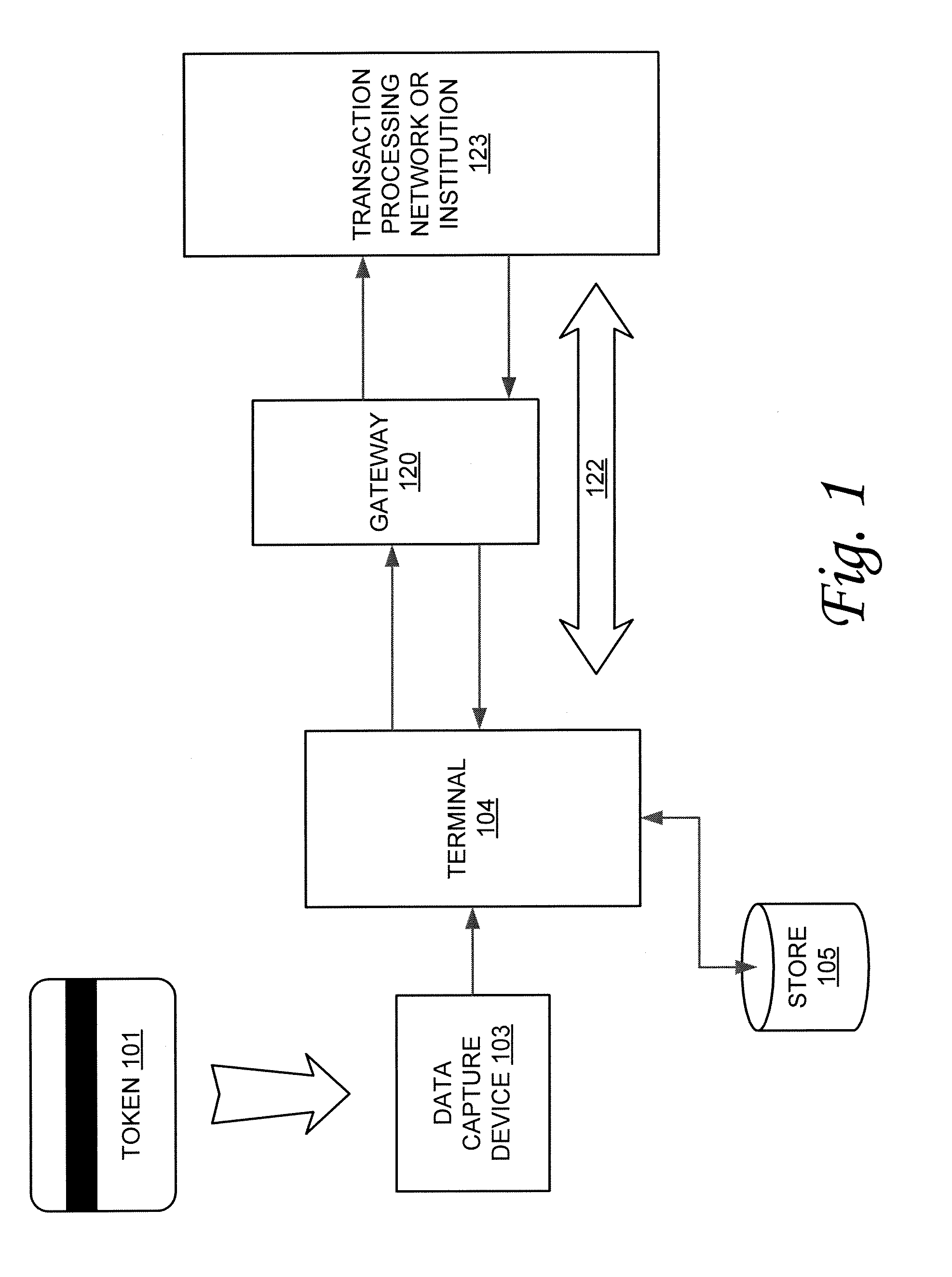
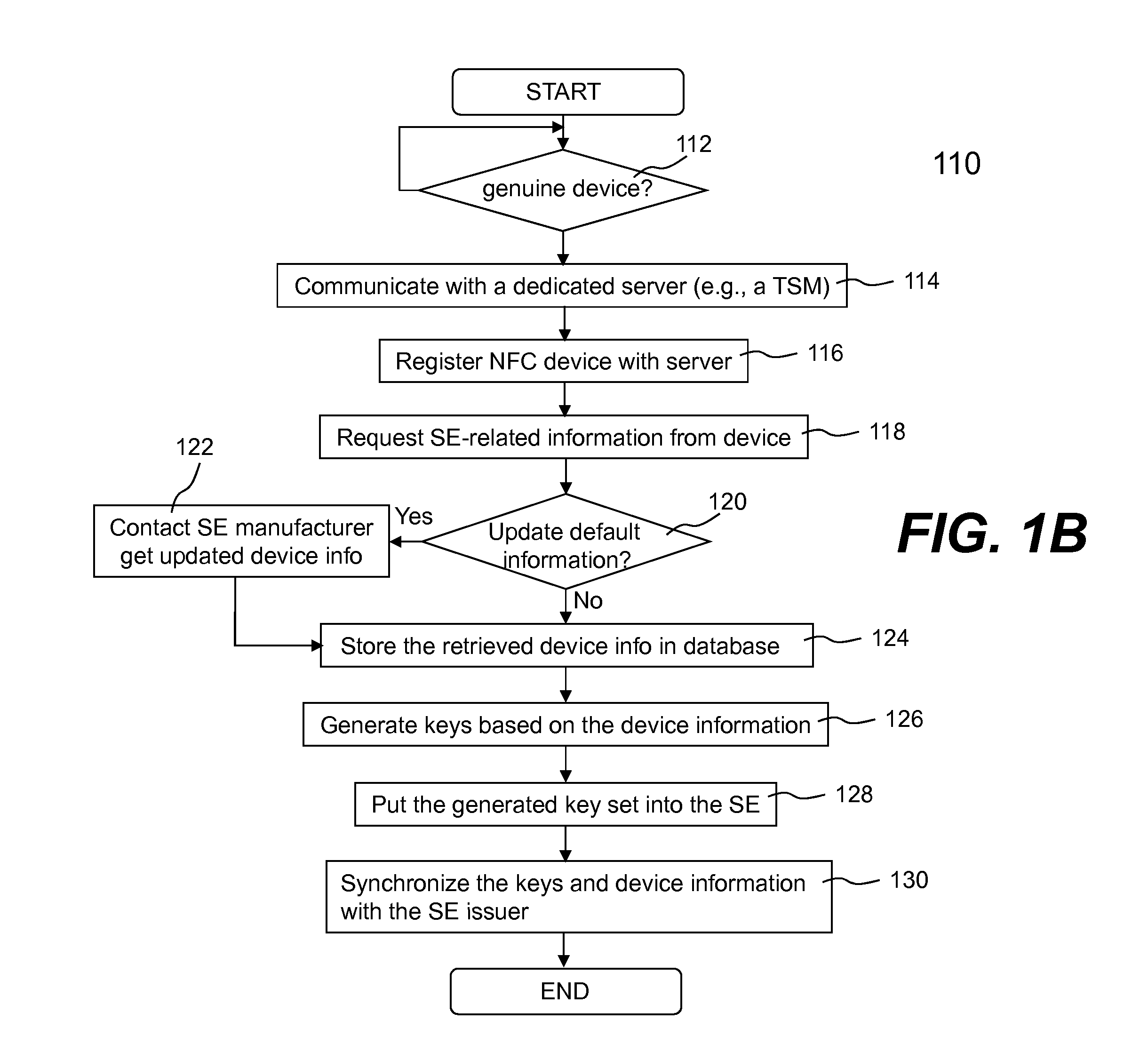
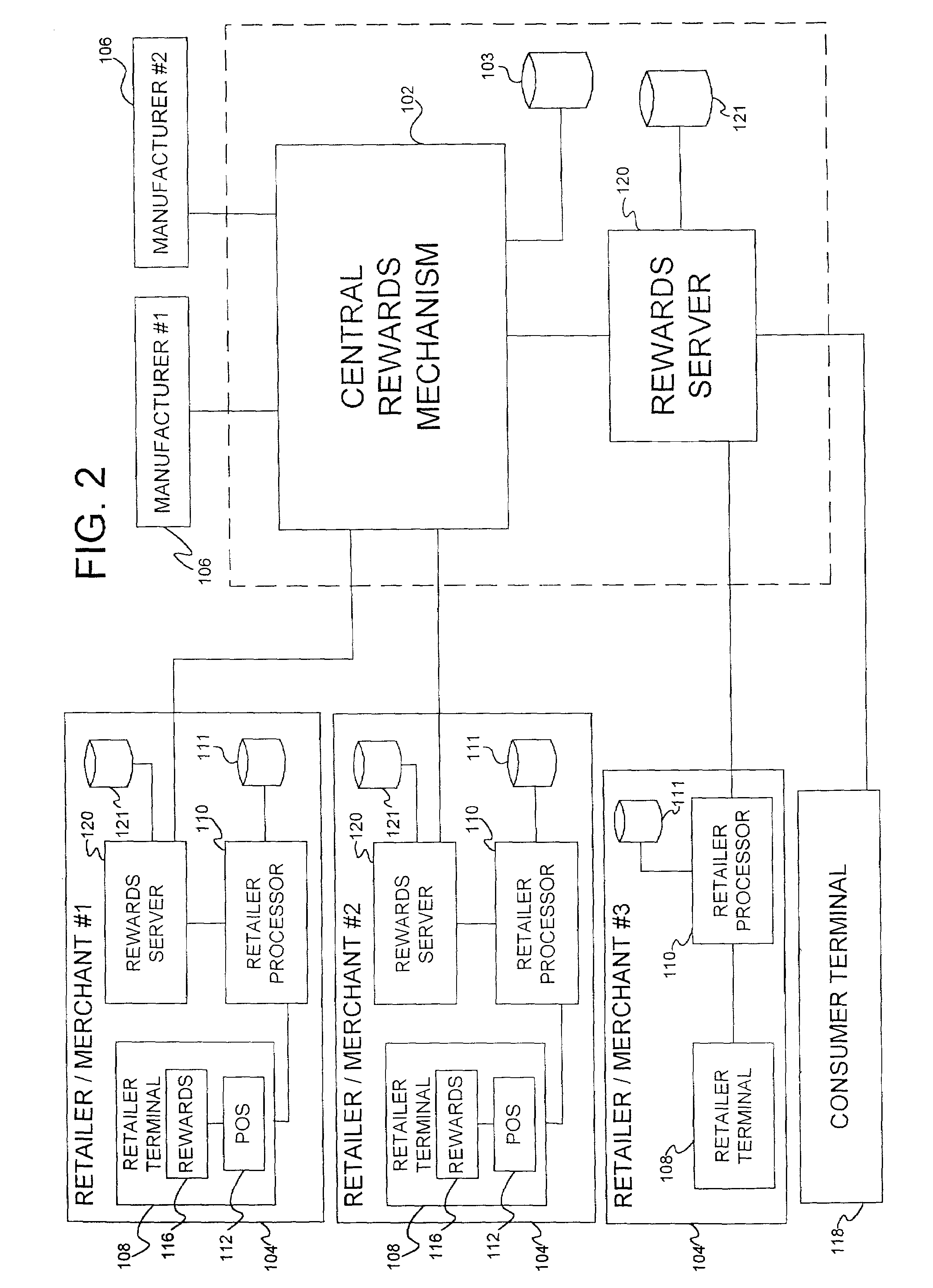
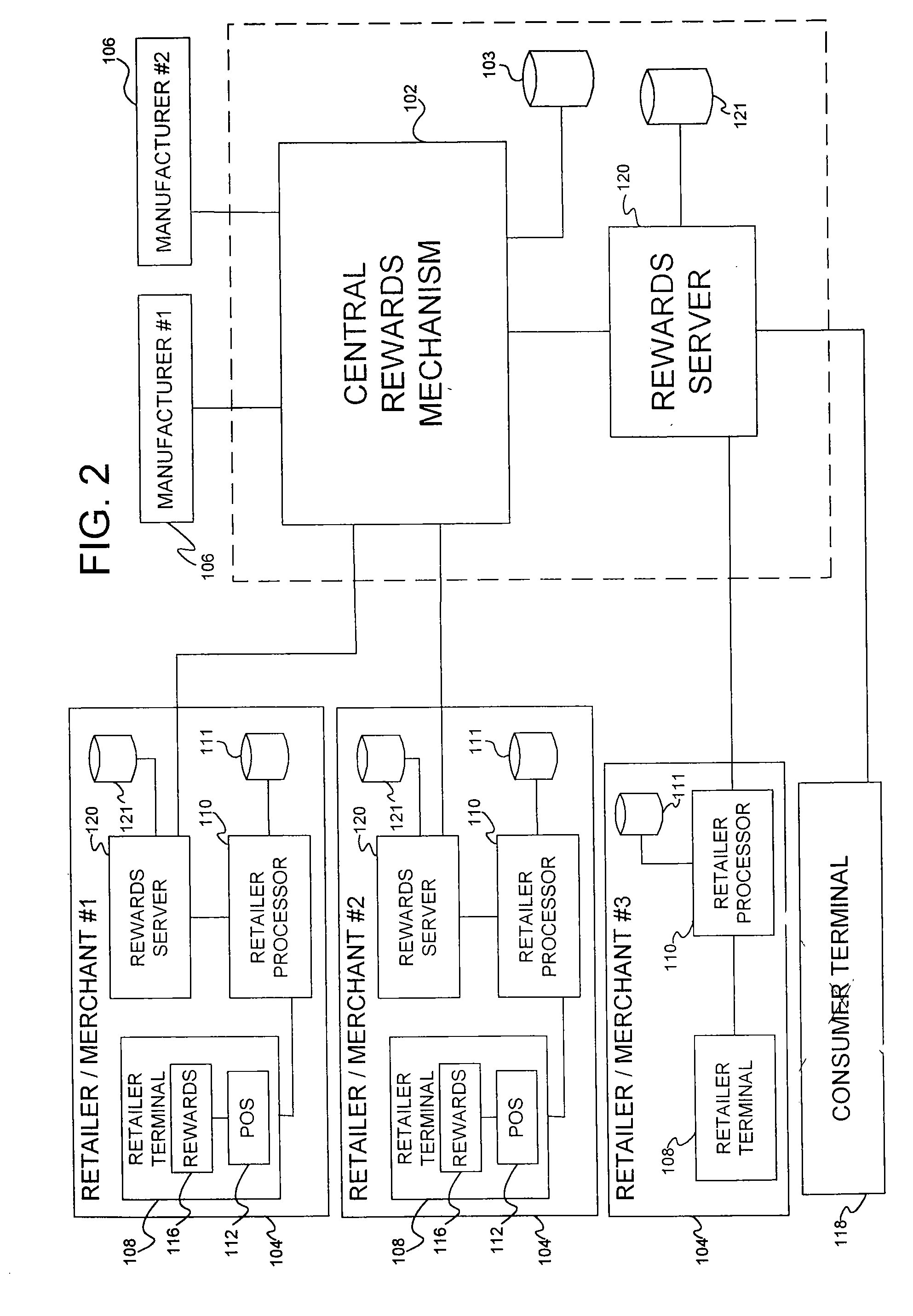
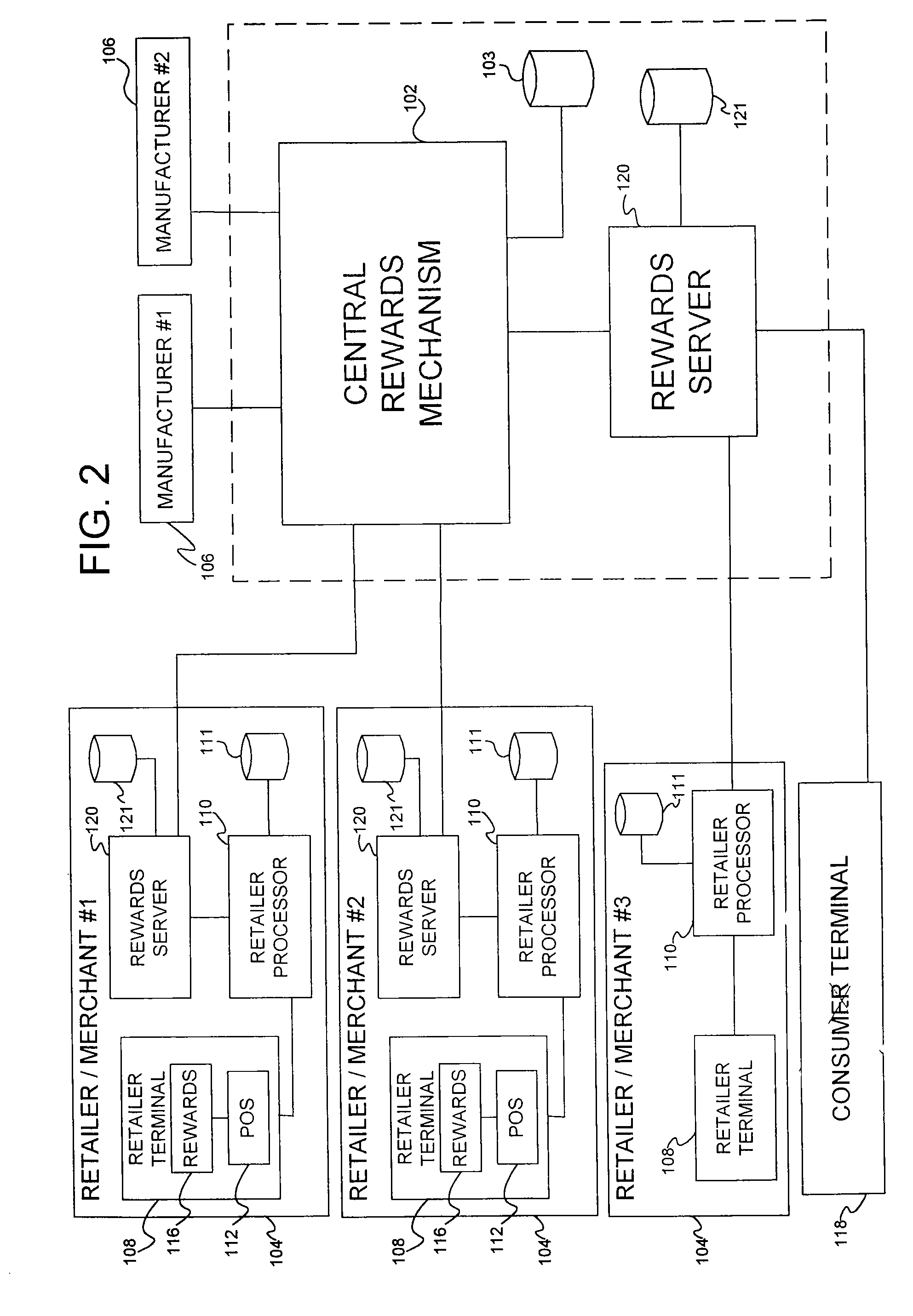
Secured transaction system and method
InactiveUS20130254117A1Reduce riskEasy to optimizePayment protocolsInternet privacyEncryption decryption
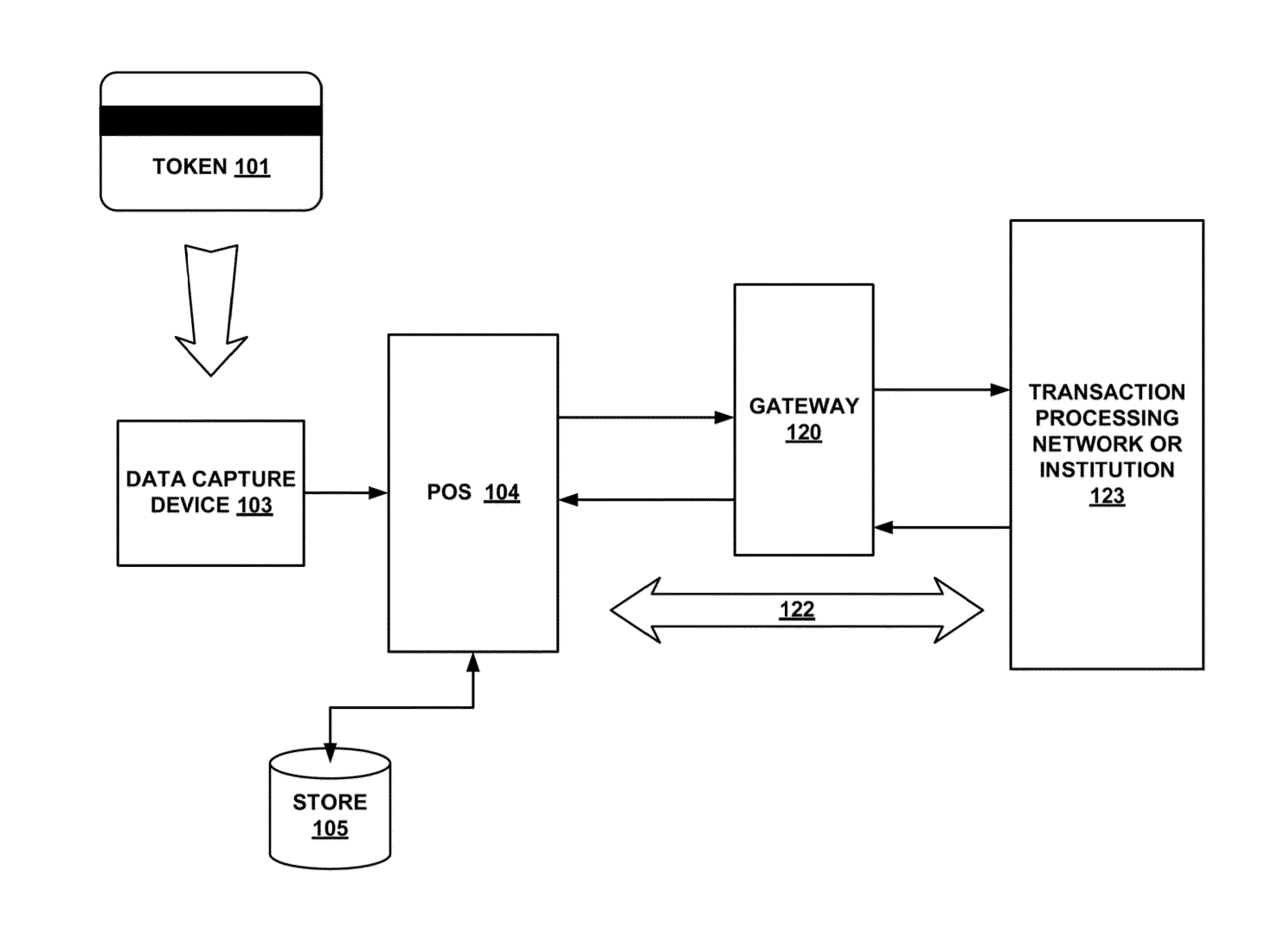
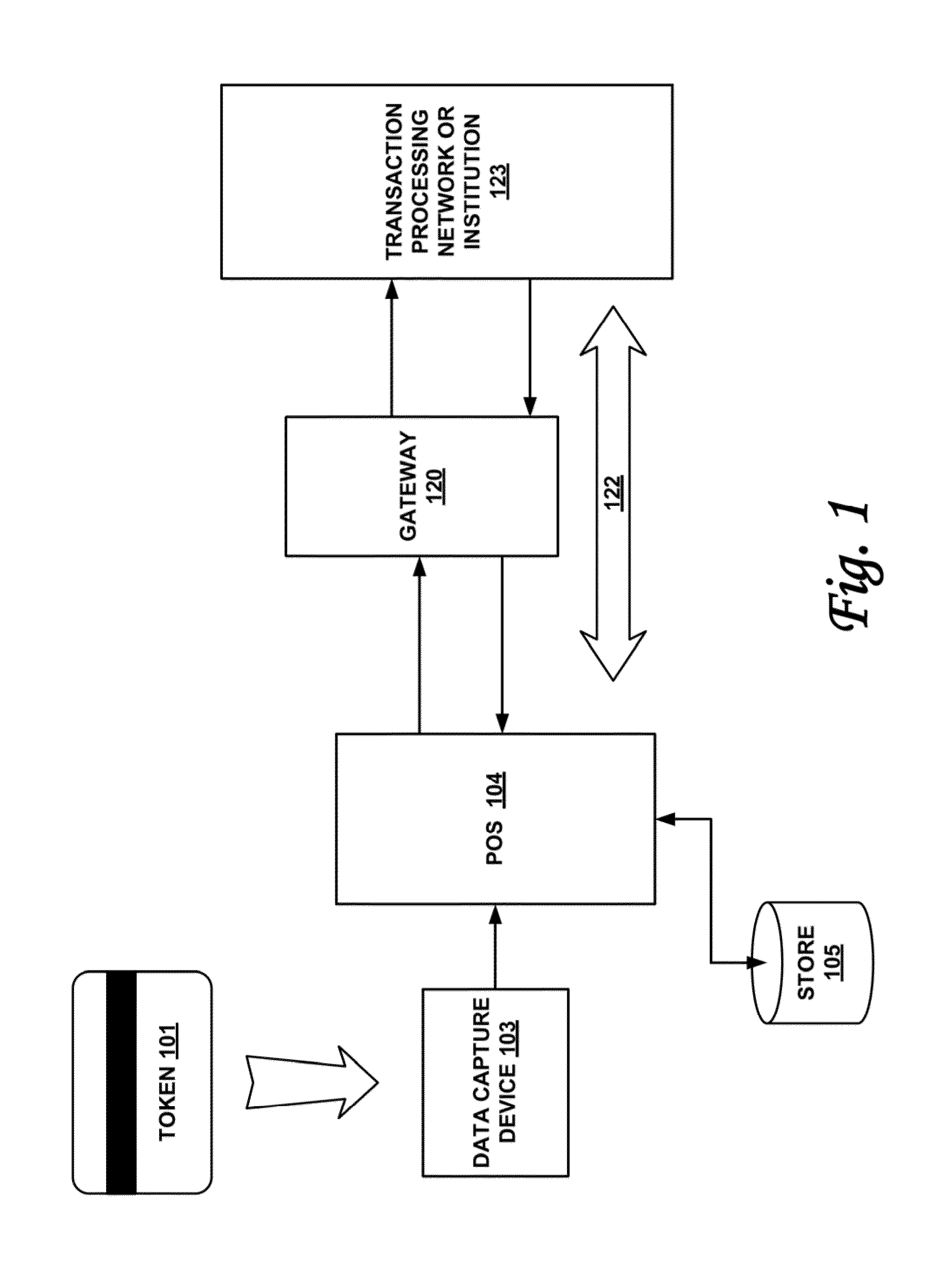
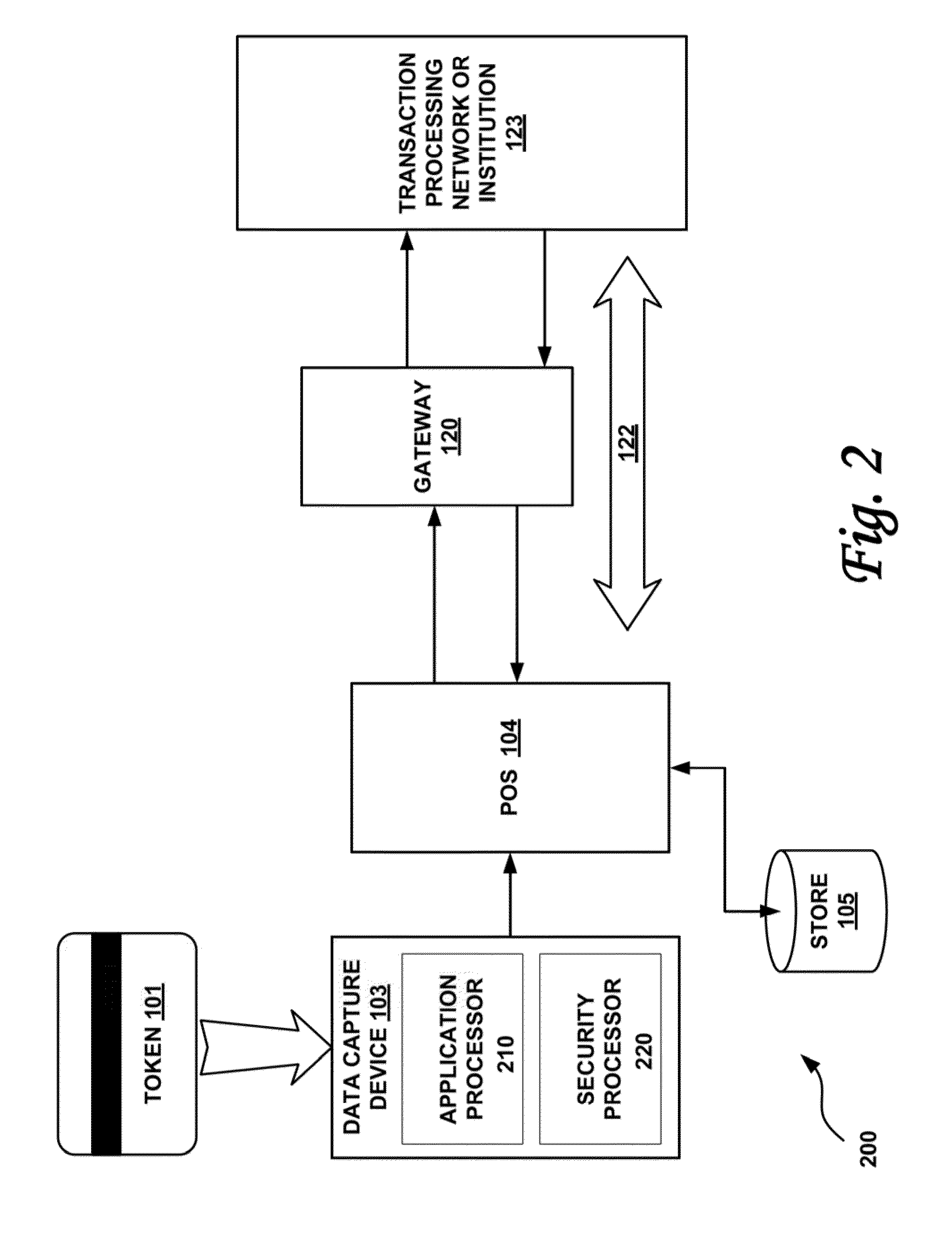
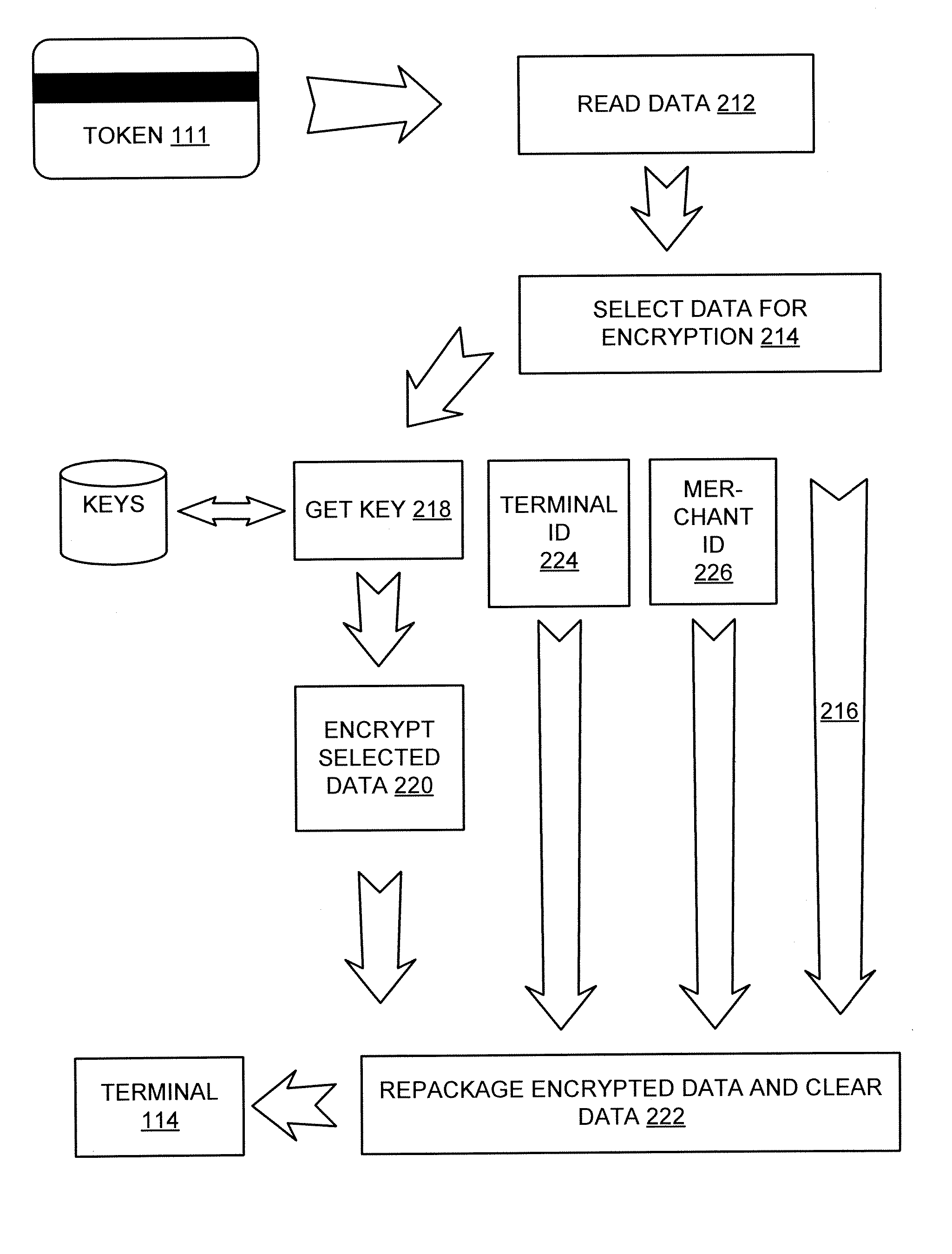
Systems and methods for performing financial transactions are provided. In one embodiment, the invention provides for method for bank card transactions, including: reading the token information at the point of swipe for traditional and non-traditional POS platforms; performing a low-security task on the token information using a first microprocessor, wherein the non-security task includes one or more tasks from the group of encryption determination, encryption-decryption request, key management, token information delivery, or transactional data delivery; and performing a security-related task on the token information using a second microprocessor based on a request from the first microprocessor, wherein the security-related task includes one or more tasks from the group of token information authentication, token information decryption, or token information encryption. Formatting the encrypted information such that it is compatible with the format of the current POS system.
Owner:VON MUELLER CLAY W +1
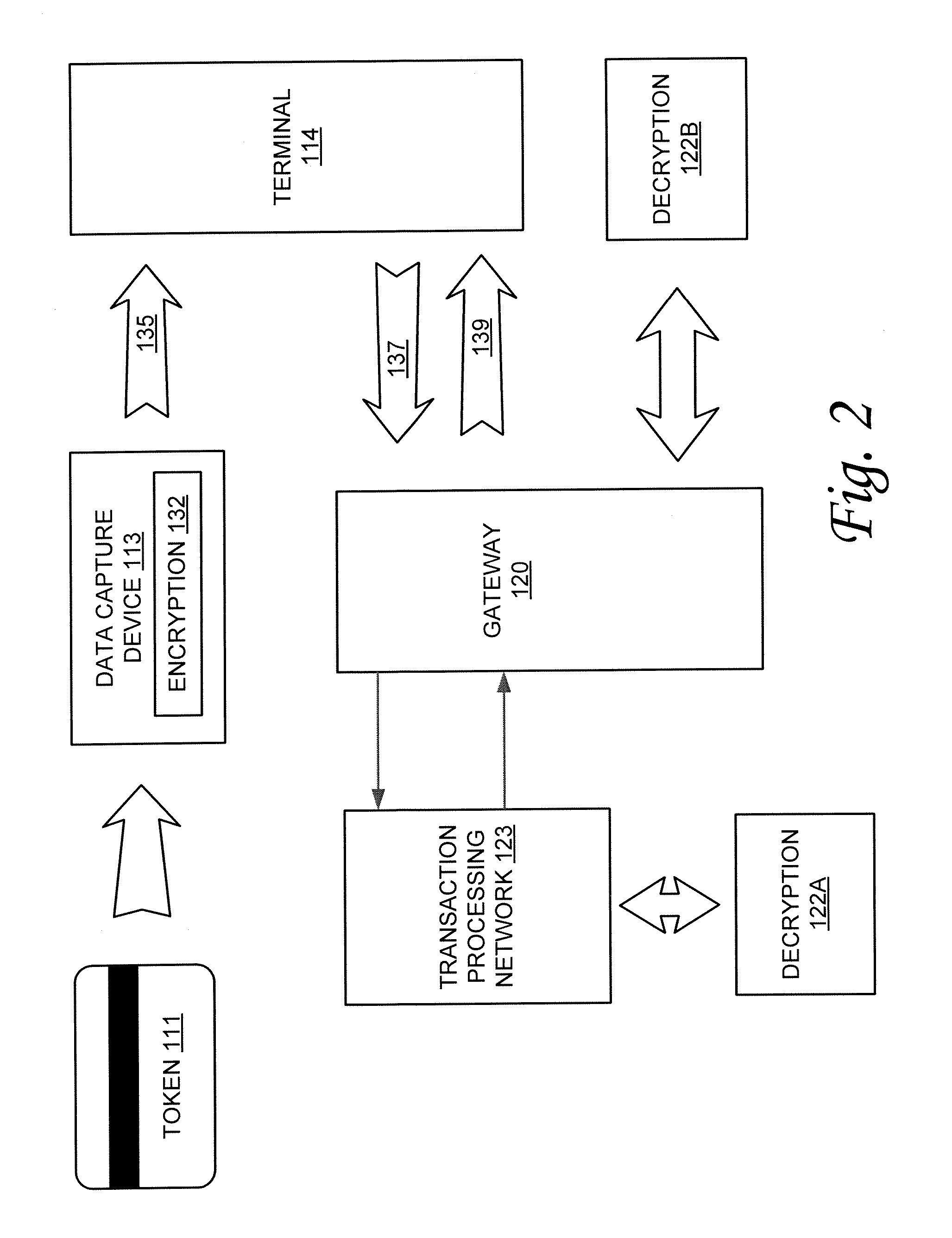
Method and system for secured transactions
InactiveUS20070276765A1Improve securityEasy to upgradeAcutation objectsFinancePlaintextBatch processing
Owner:SEMTEK INNOVATIVE SOLUTIONS
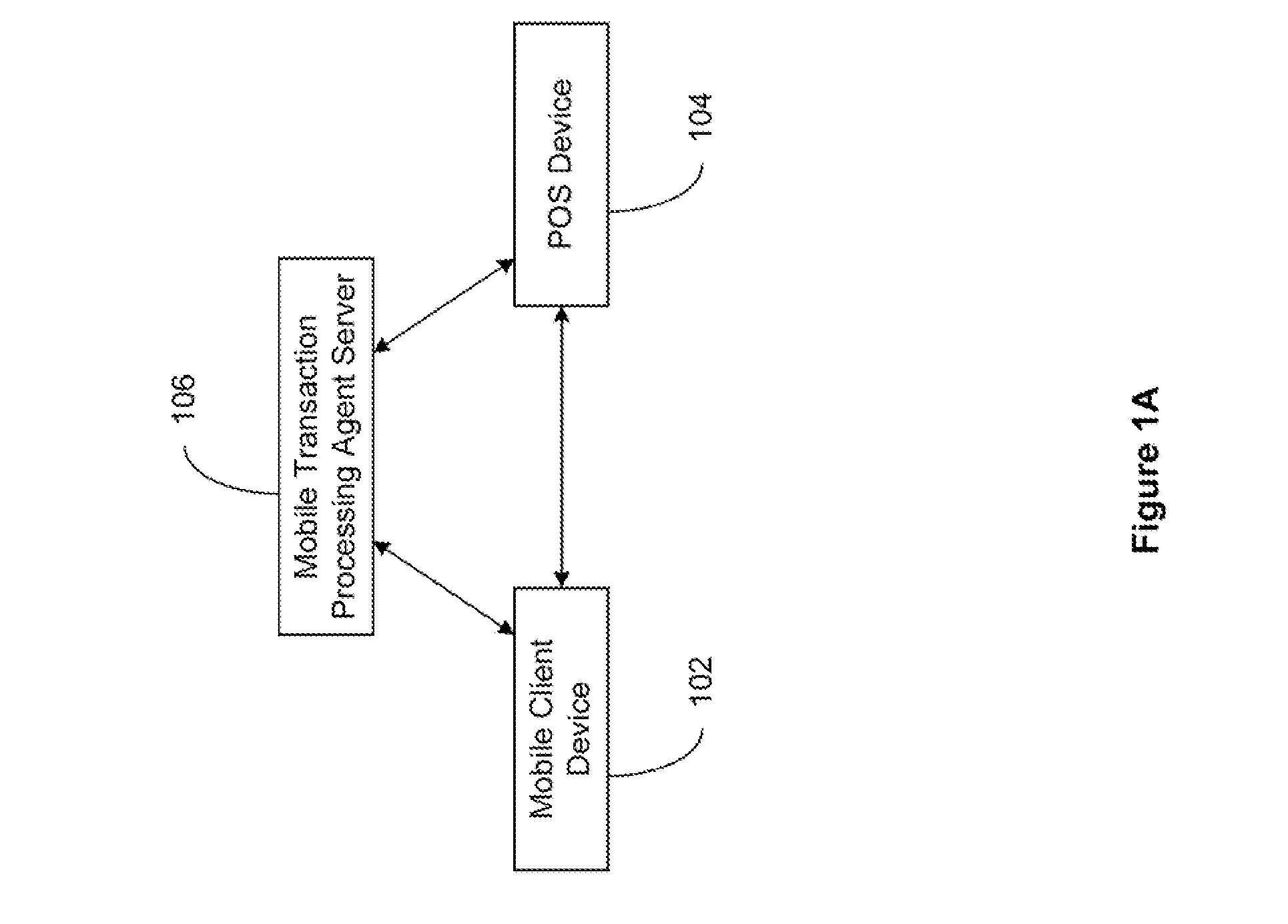
Secured Transaction System
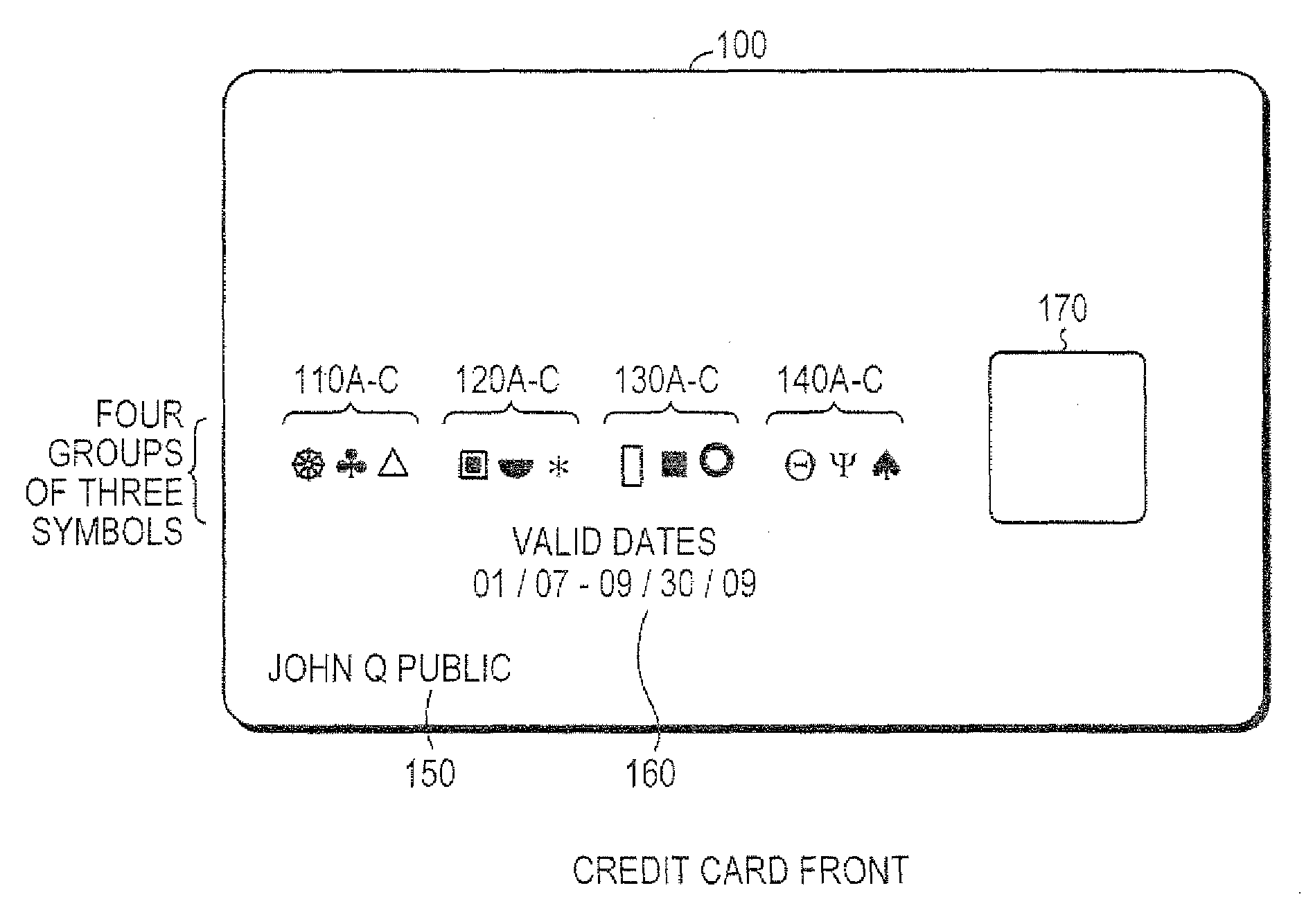
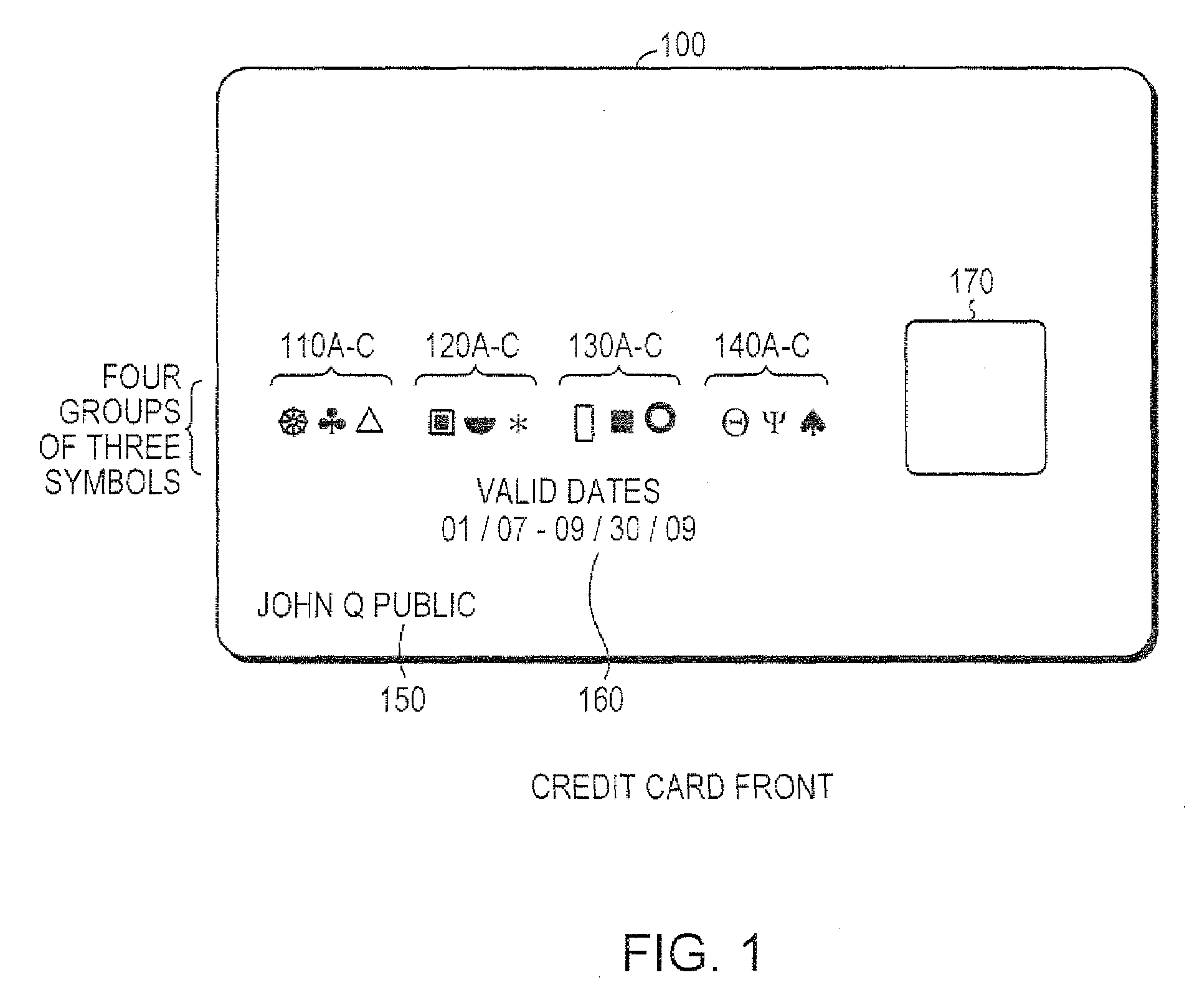
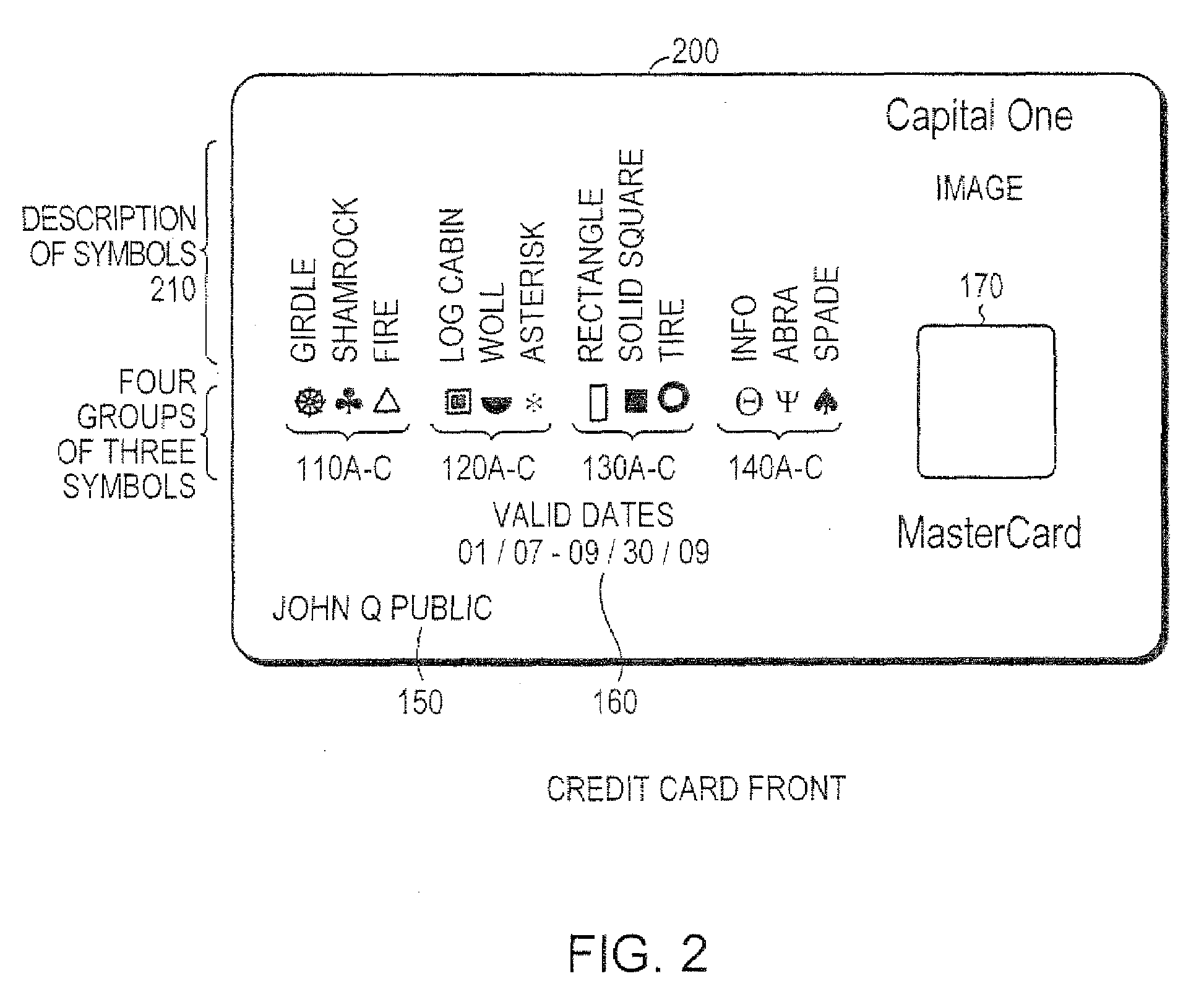
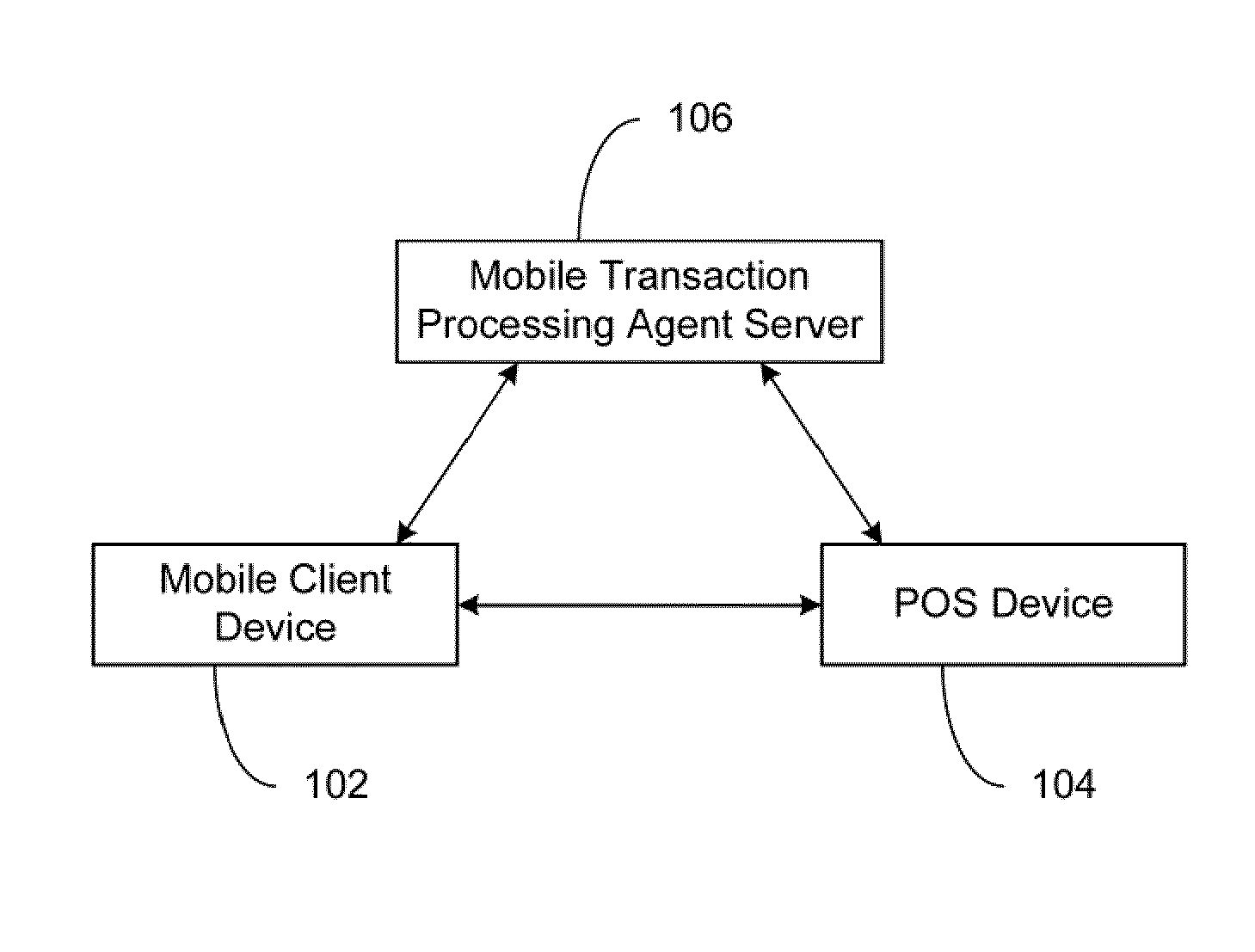
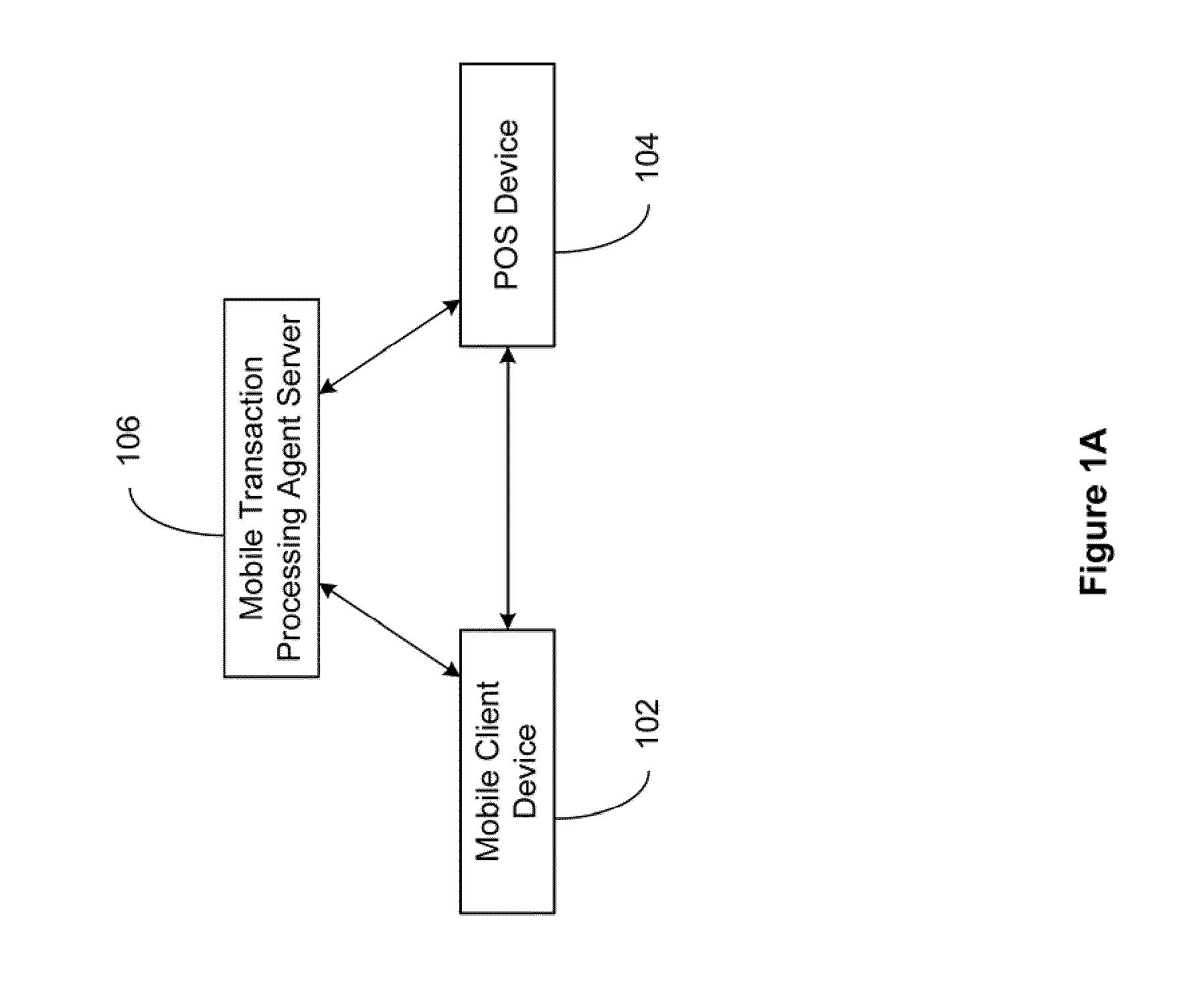
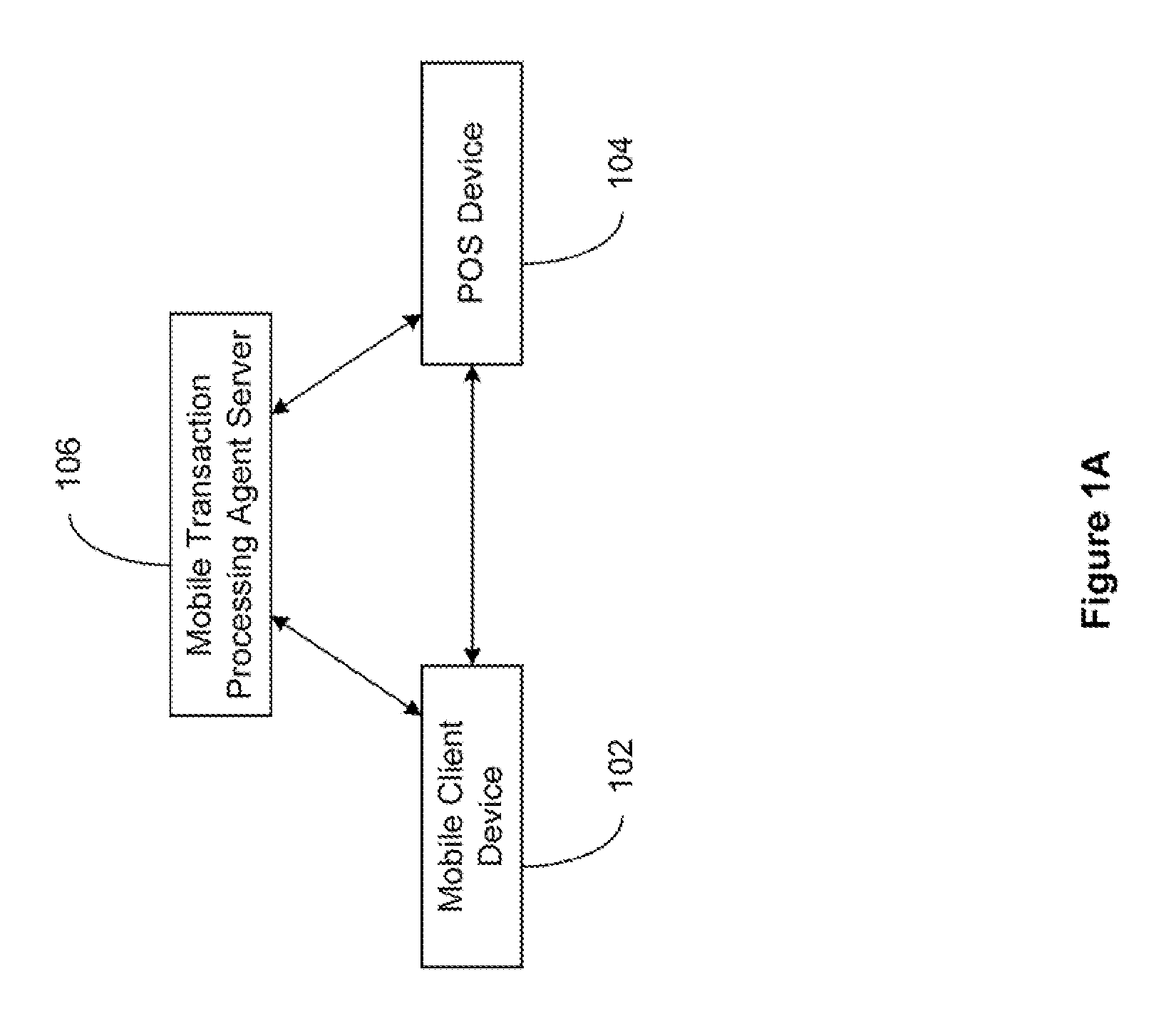
The present invention relates to a secured transaction system. In one embodiment, a mobile transaction processing agent system includes a communication module configured to receive a secured transaction description from a mobile client device or an encrypted transaction description from a point-of-sale (POS) device, wherein the secured transaction description is in the form of a bar code generated by the mobile client device, an authentication module configured to decode the secured transaction description and verify the secured transaction description is valid based on the mobile client device or the point-of-sale device, and a transaction processing module configured to process the transaction in accordance with the secured transaction description.
Owner:DAI XIA
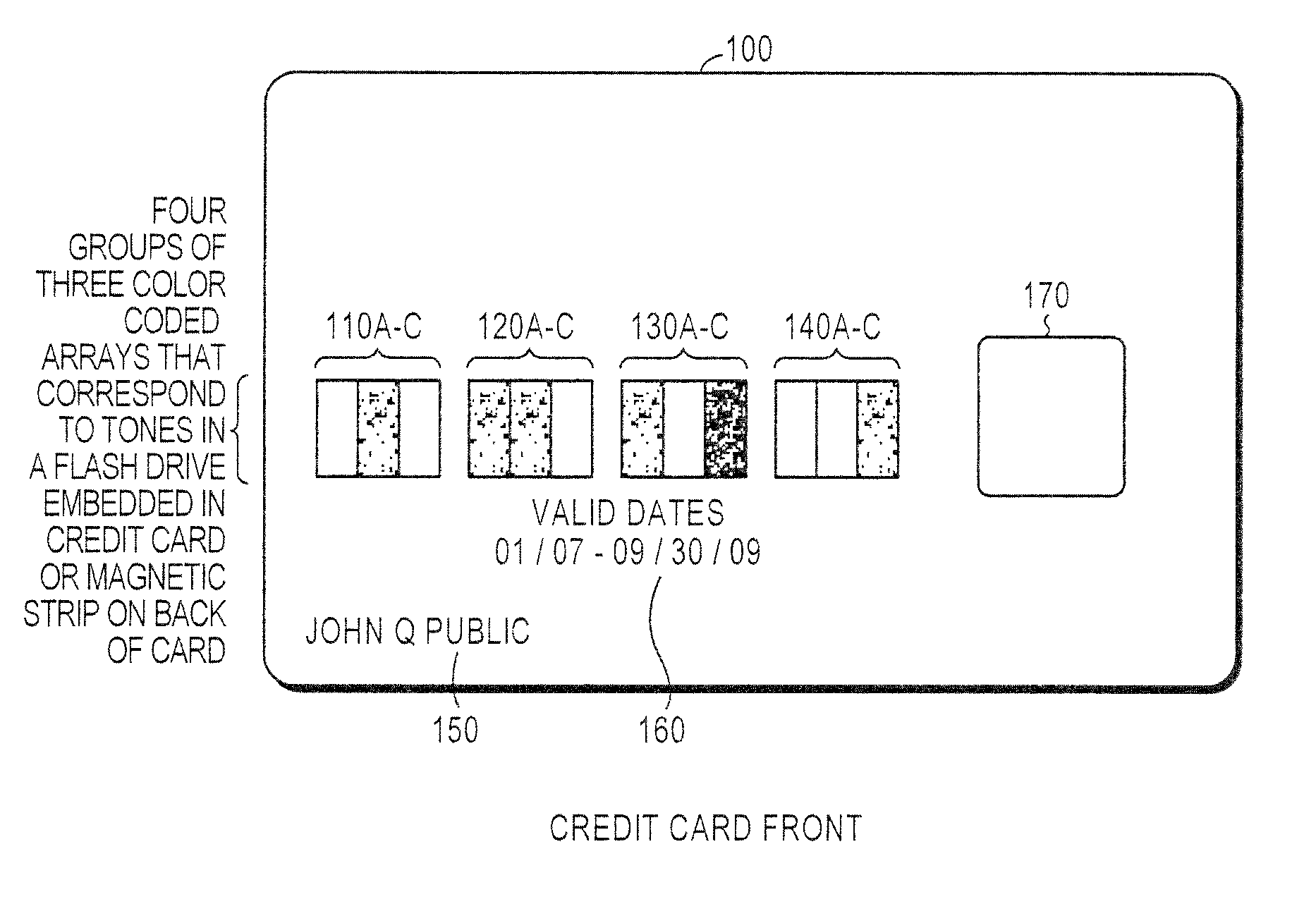
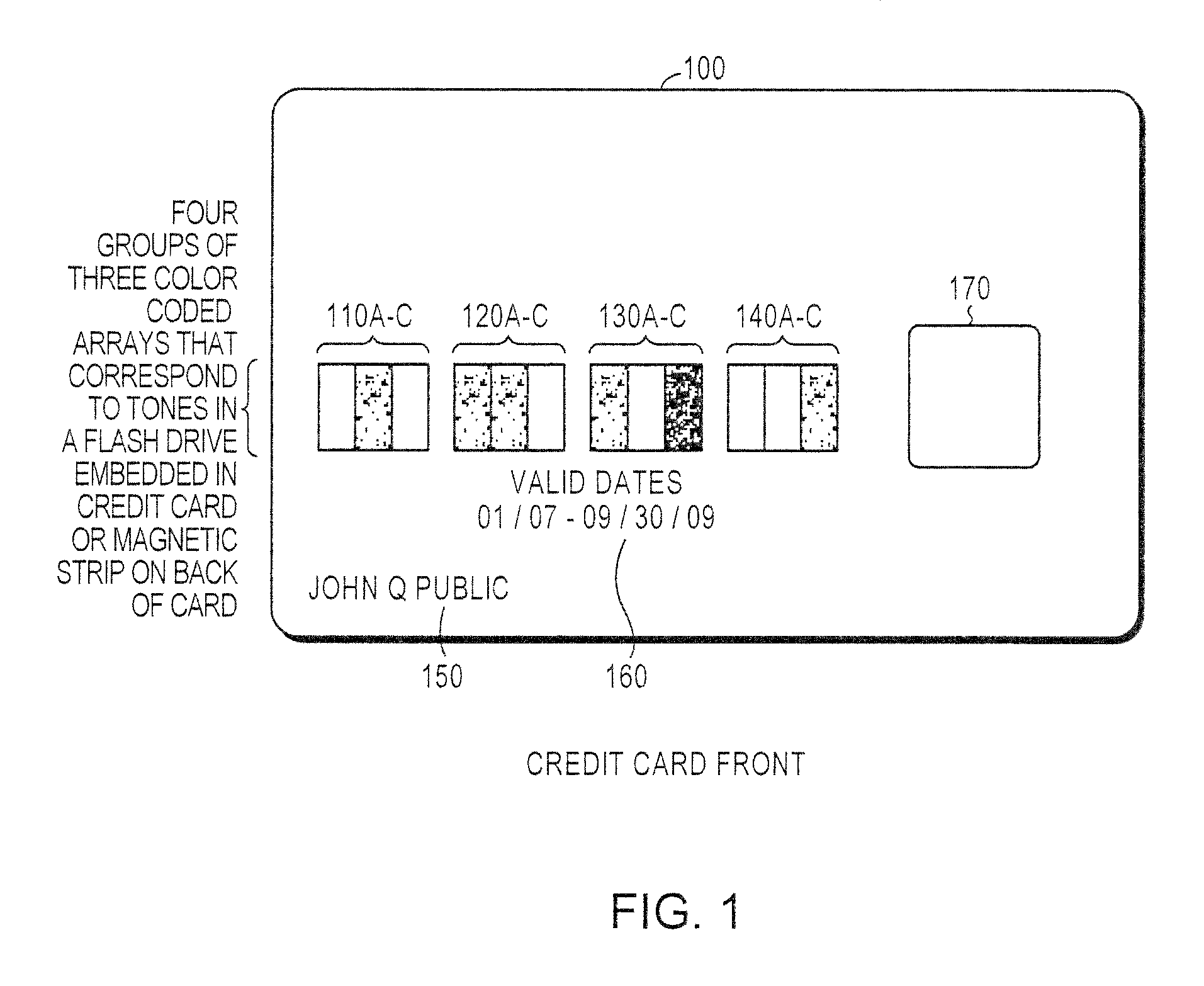
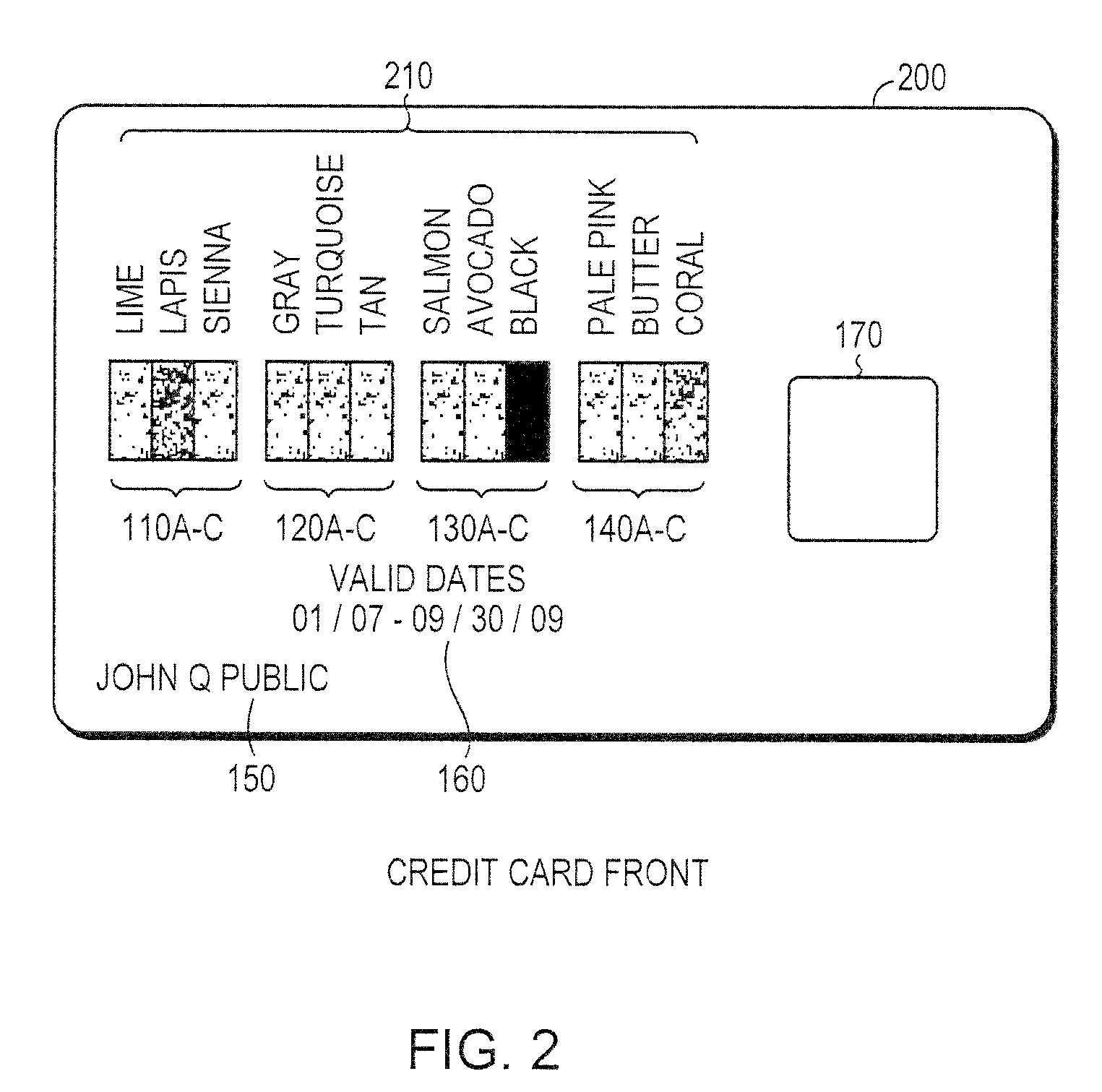
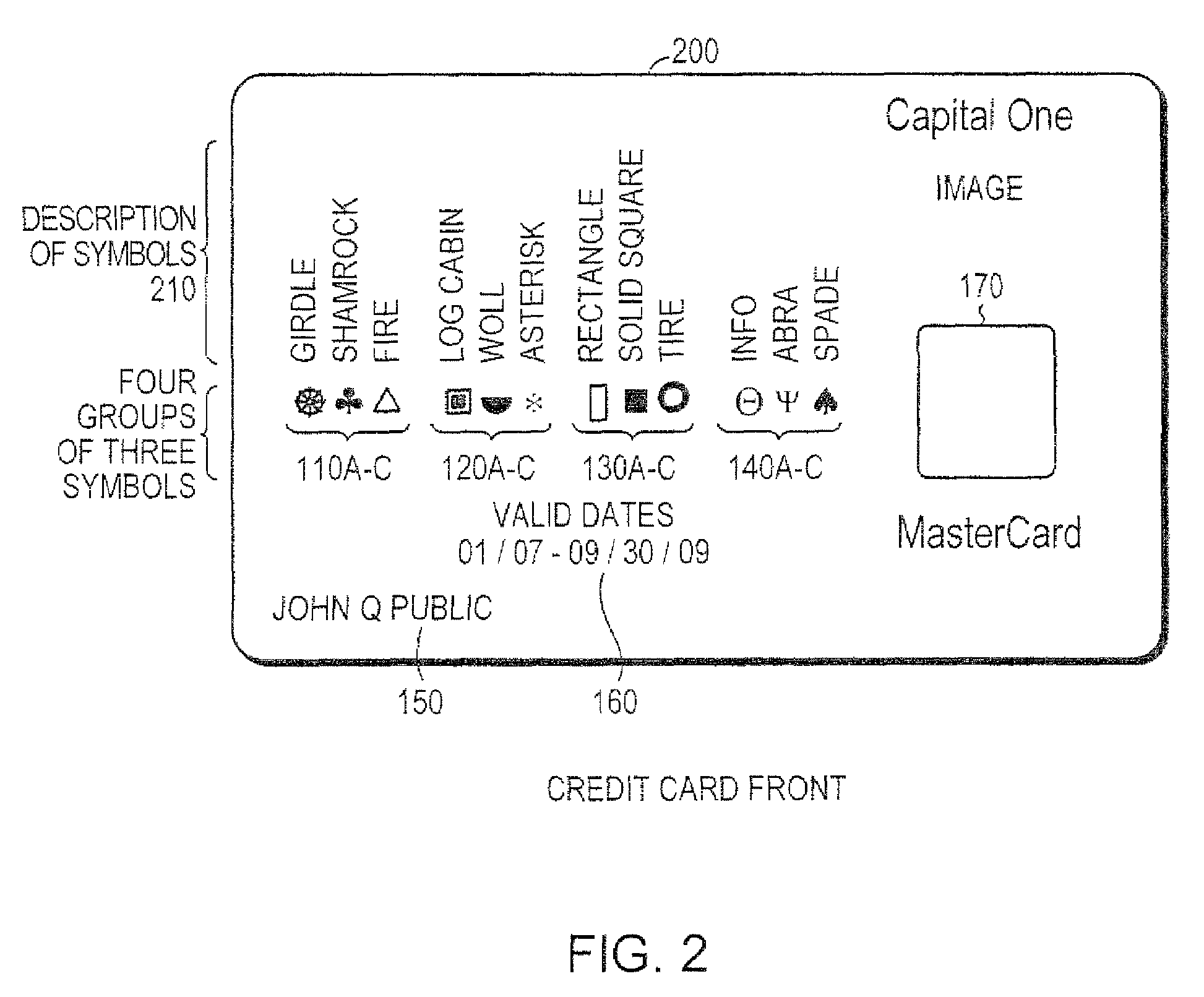
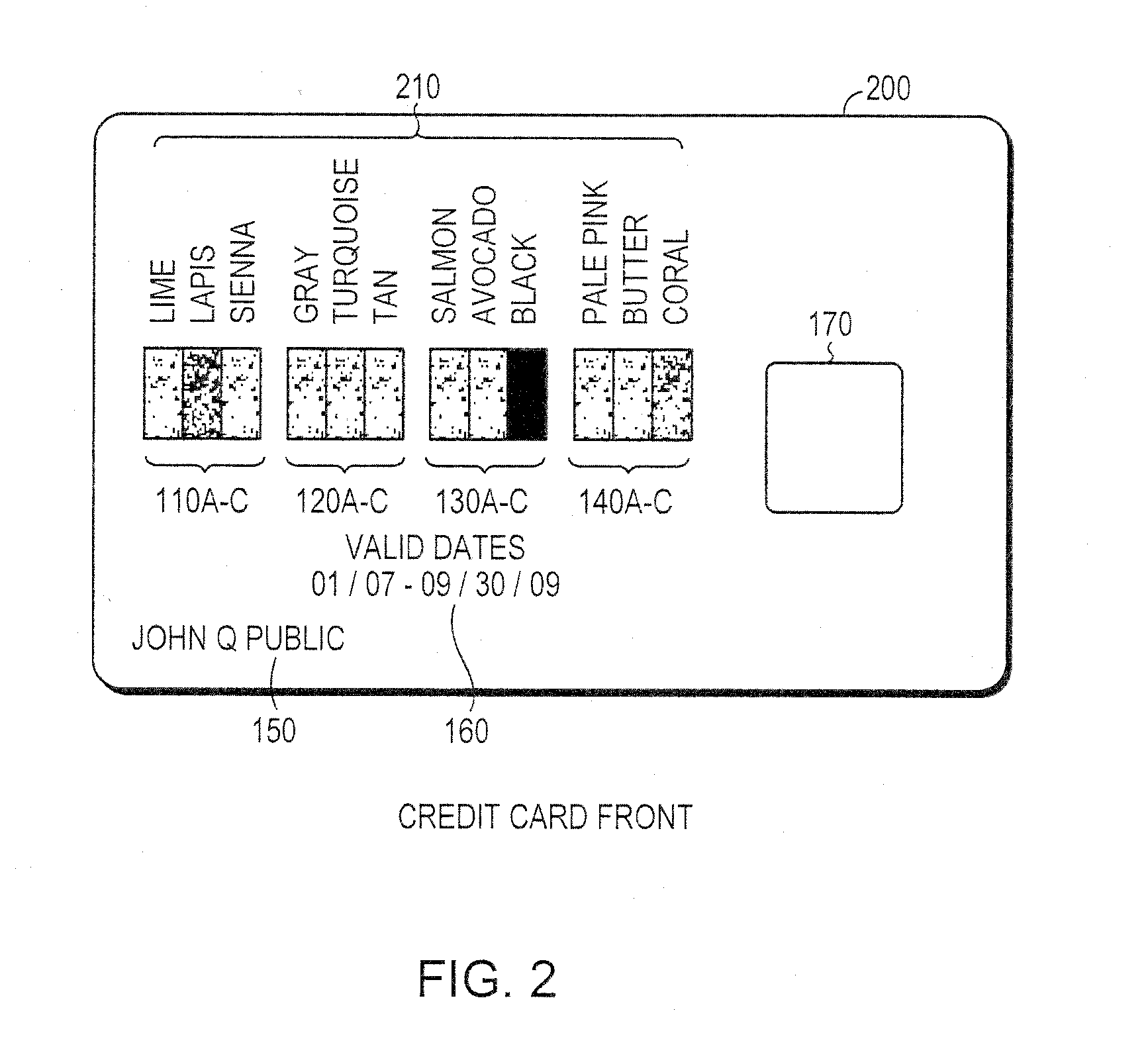
Secured transaction using color coded account identifiers
InactiveUS7896238B2Reduce fraudReduce piracyComplete banking machinesFinanceSecured transactionDatabase
A method and system provides coded access to a transactional or other type of system by acquiring account identification data corresponding to a combination of a plurality of colors. The account identification data is transmitted to, for example, a remote server to correlate the account identification data against an account database to evaluate corresponding account information. Based on the account information, access to the transactional or other type of system may be controlled.
Owner:XYLON LLC
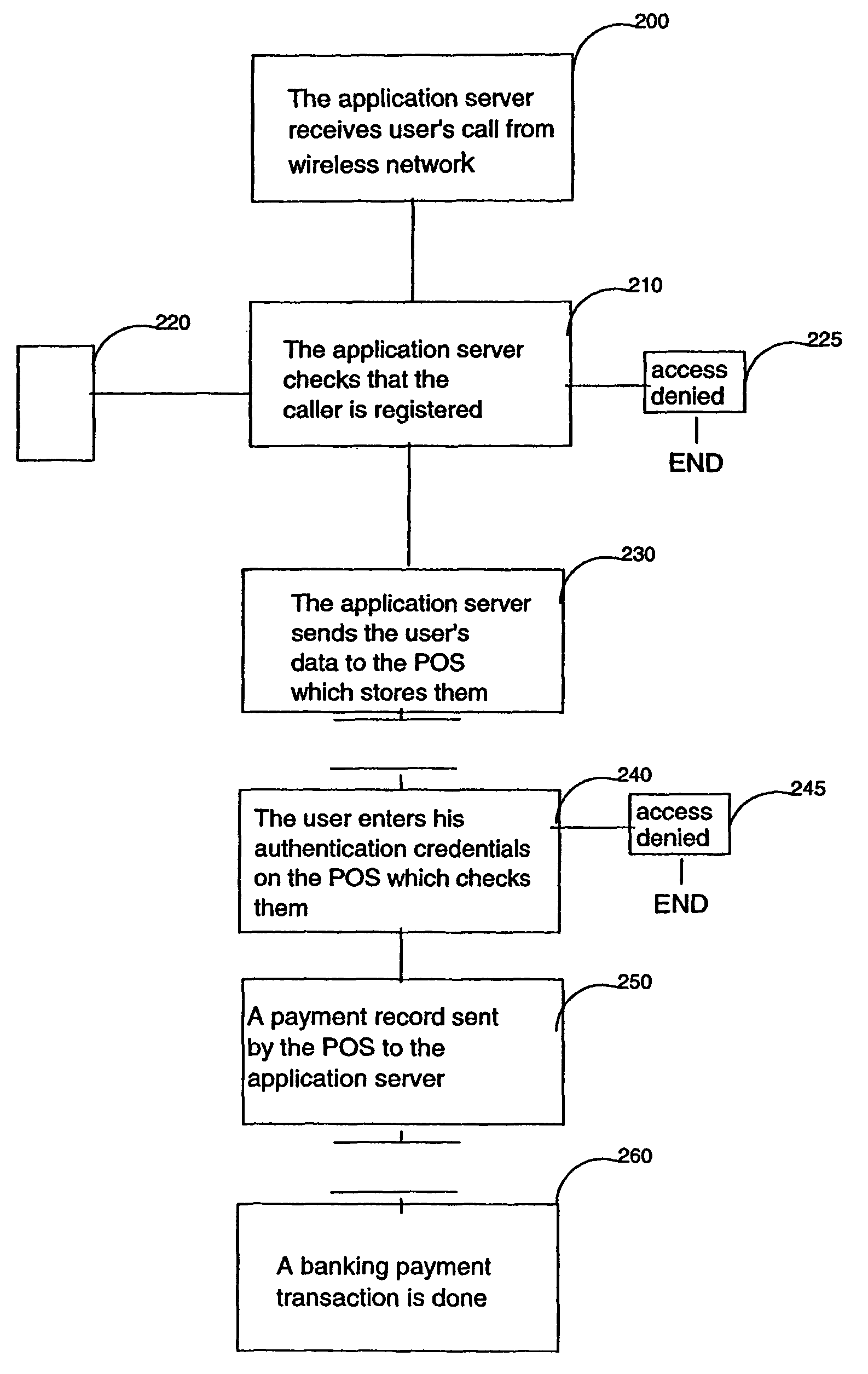
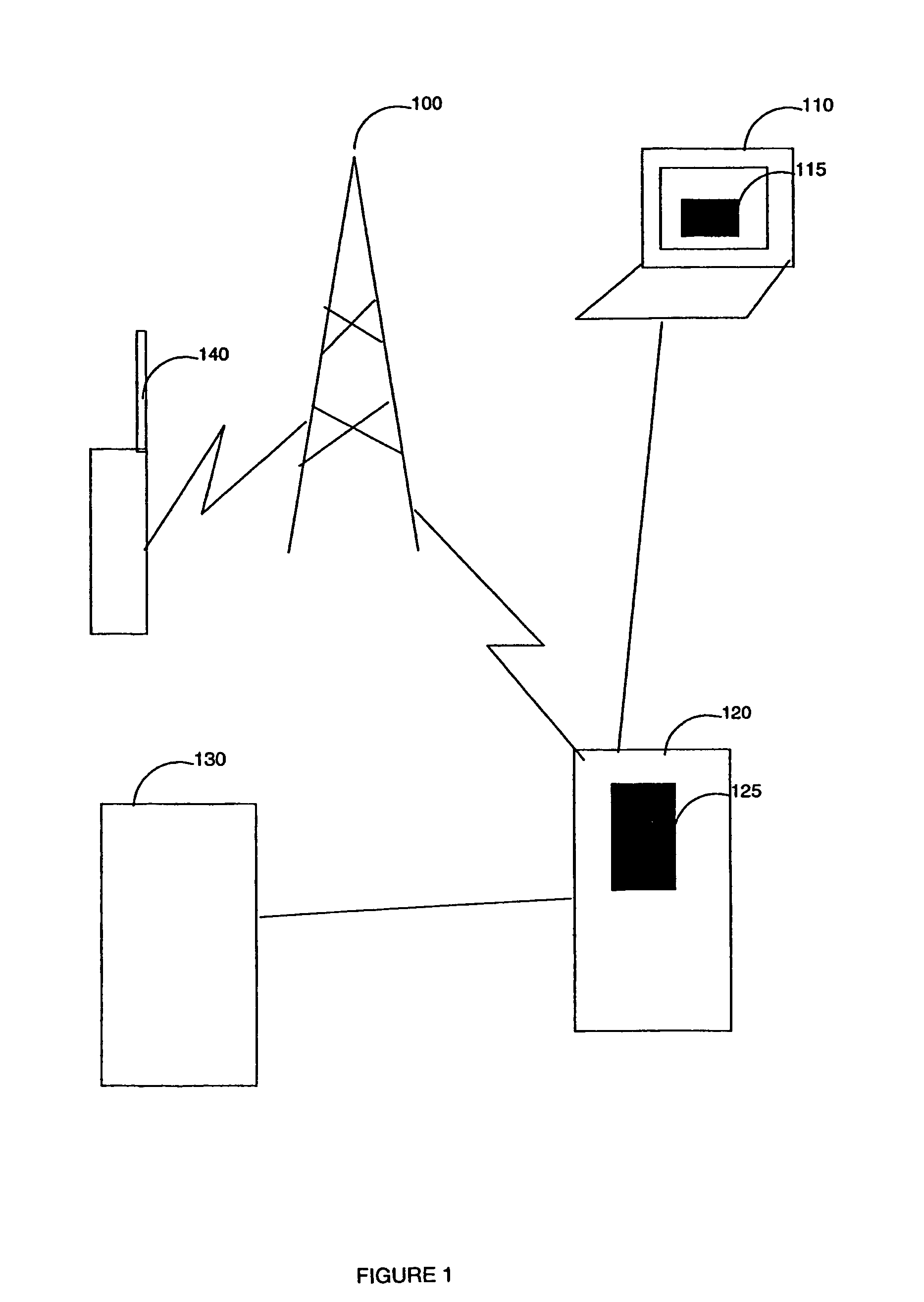
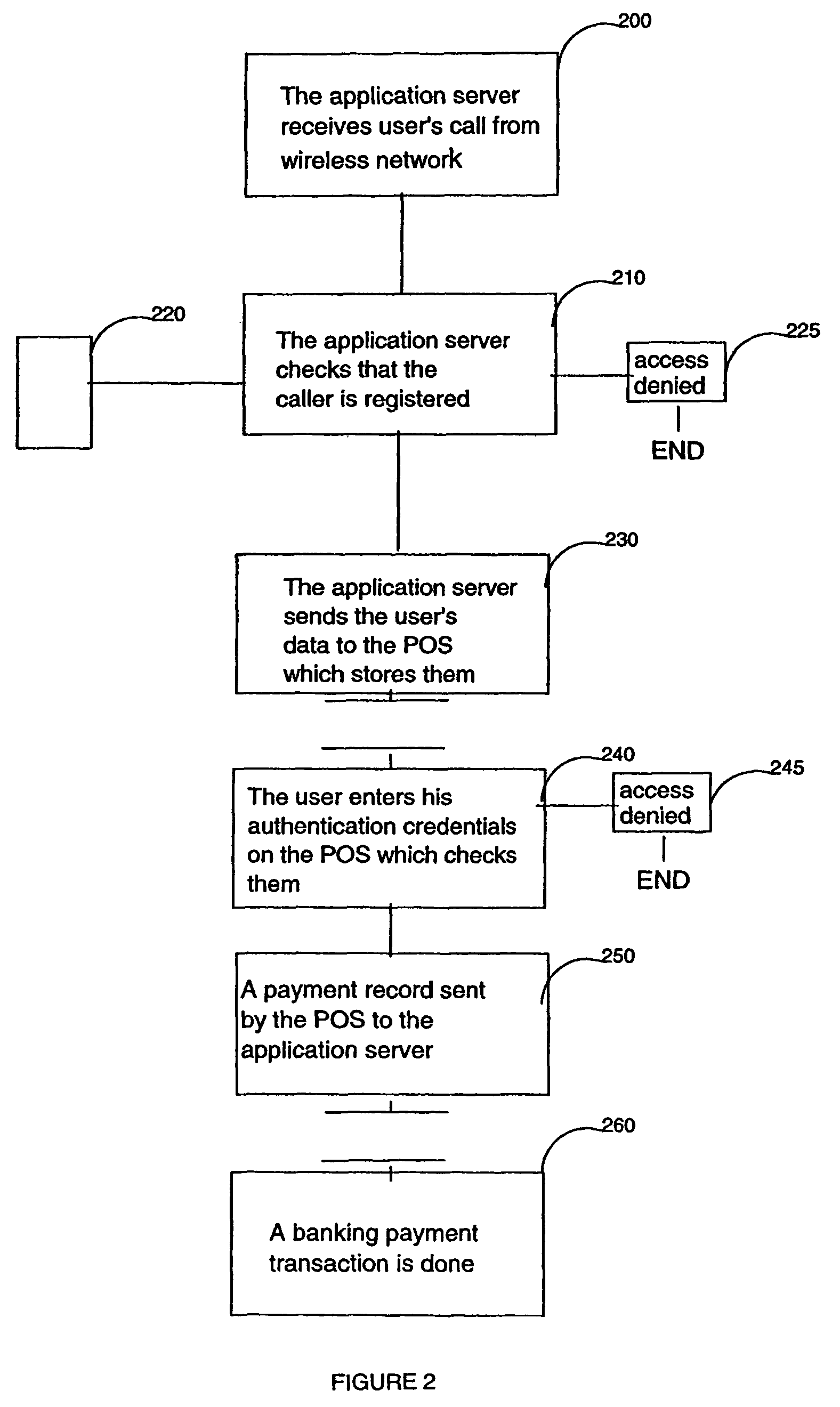
Method and system for secured transactions over a wireless network
InactiveUS8352360B2Easy to implementAccurate interactionHand manipulated computer devicesFinancePaymentClient-side
A method and system are disclosed for booking and paying a retailer having a POS, which can be a low cost thin client computer system, connected to a transaction server storing confidential user information including a retailer identification, a user code and a user wireless device phone number, said method comprising the steps of receiving at the transaction server, from the user wireless device which can be a common cellphone, an SMS containing a retailer identification, reading at the transaction server the phone number of the wireless device communicated by the carrier transporting the SMS, authentifying said phone number and retailer identification with the stored confidential user information and sending the user confidential information to the retailer POS, the user entering on the POS the user code and the POS reading and authentifying the user code with the user confidential information received from the transaction server, the retailer entering the payment information on the POS and sending it with user information to the transaction server.
Owner:TOSHIBA GLOBAL COMMERCE SOLUTIONS HLDG
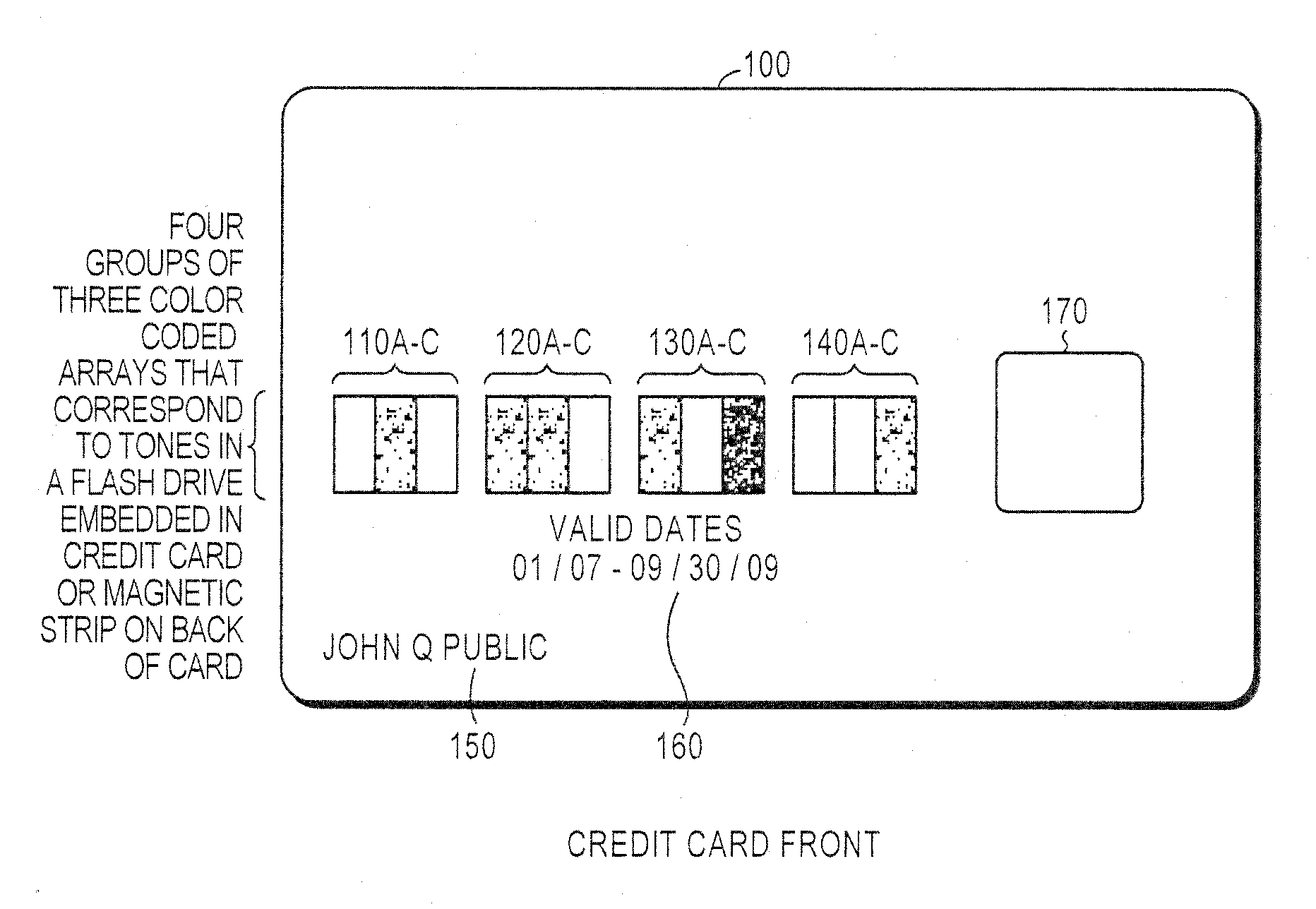
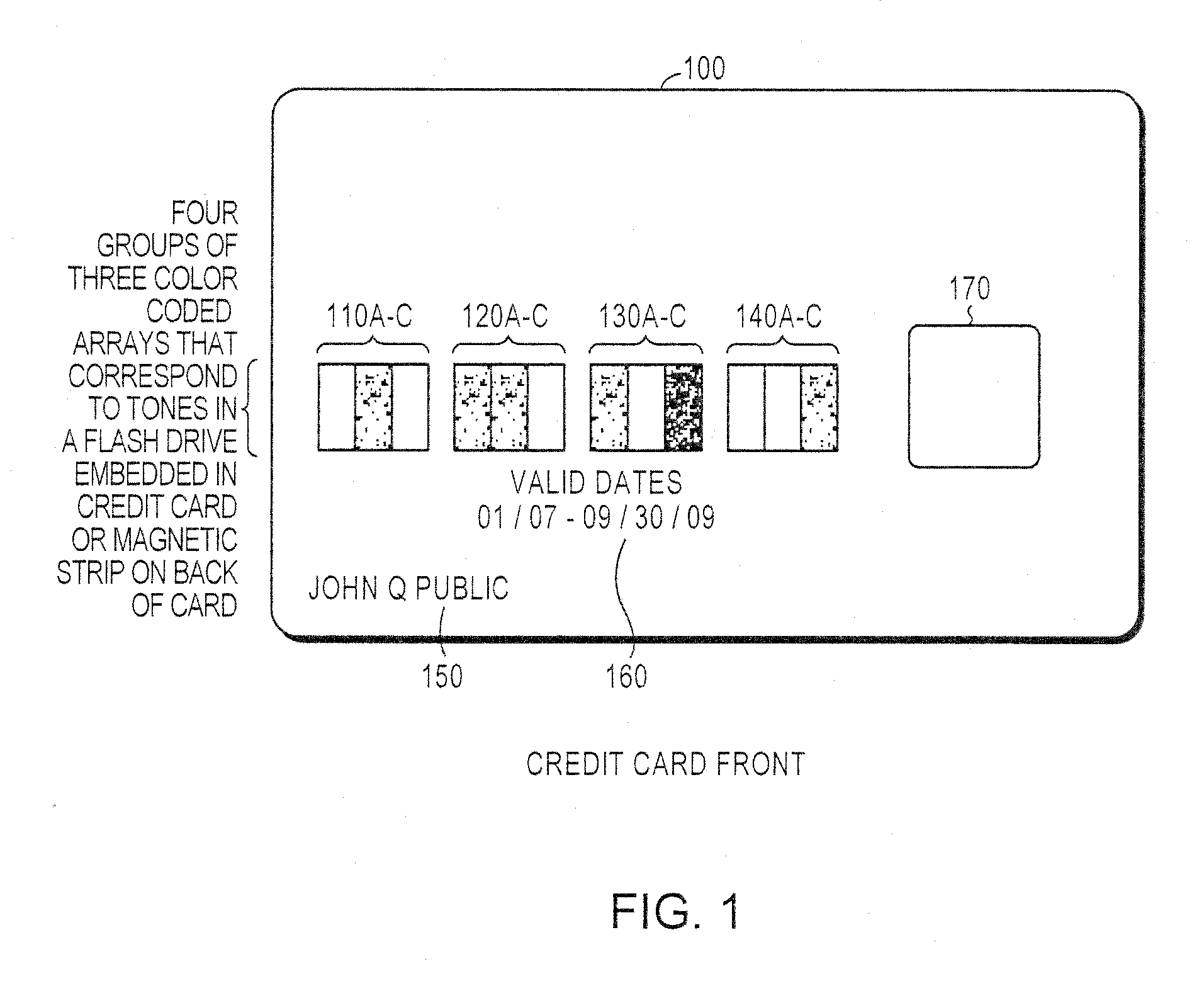
System and method for controlling secured transaction using directionally coded account identifiers
A control method and system provides coded access to a system by acquiring account identification data corresponding to a combination of a plurality of symbols. The account identification data is transmitted, for example to a remote server, to correlate the account identification data against an account database to evaluate corresponding account information. Based on the account information, access to the system may be controlled.
Owner:KIOBA PROCESSING LLC
System and method for controlling secured transaction using color coded account identifiers
InactiveUS20080245861A1Low costHigh degree of accuracyComplete banking machinesFinanceSecured transactionDatabase
A method and system provides coded access to a transactional or other type of system by acquiring account identification data corresponding to a combination of a plurality of colors. The account identification data is transmitted to, for example, a remote server to correlate the account identification data against an account database to evaluate corresponding account information. Based on the account information, access to the transactional or other type of system may be controlled.
Owner:XYLON LLC
System and method for controlling secured transaction using directionally coded account identifiers
InactiveUS20080245855A1Low costHigh degree of accuracyOther printing matterFinanceSecured transactionDatabase
A control method and system provides coded access to a system by acquiring account identification data corresponding to a combination of a plurality of symbols. The account identification data is transmitted, for example to a remote server, to correlate the account identification data against an account database to evaluate corresponding account information. Based on the account information, access to the system may be controlled.
Owner:KIOBA PROCESSING LLC
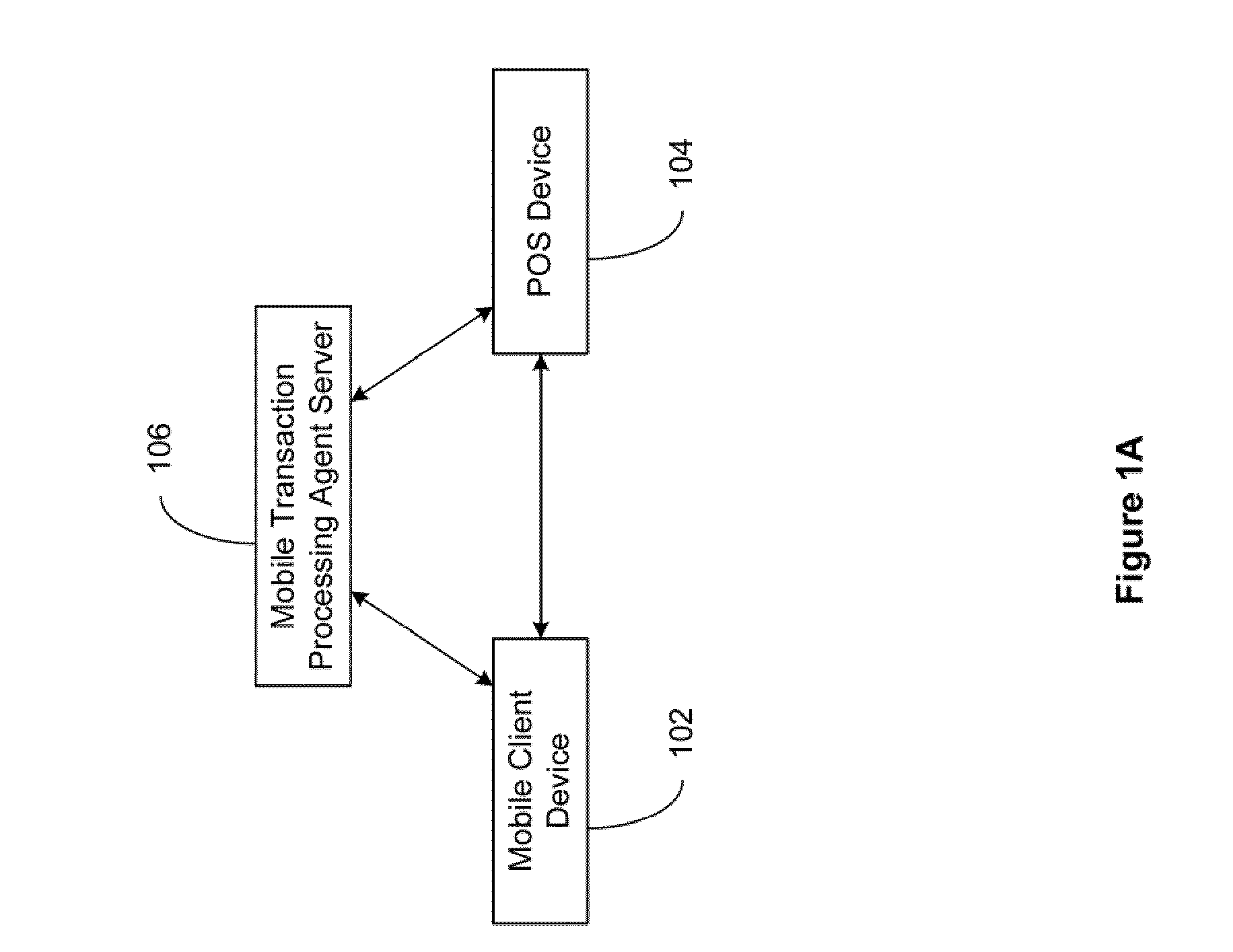
Secured Point-Of-Sale Transaction System
ActiveUS20110191252A1Improve securityFinancePoint-of-sale network systemsClient-sideSecured transaction
The present invention relates to a secured transaction system. In one embodiment, a point-of-sale (POS) system includes an input module configured to receive a transaction description from a mobile client device, an encryption engine configured to generate an encrypted transaction description using the transaction description from the mobile client device, and a communication module configured to transmit the encrypted transaction description for processing.
Owner:XIA DAI
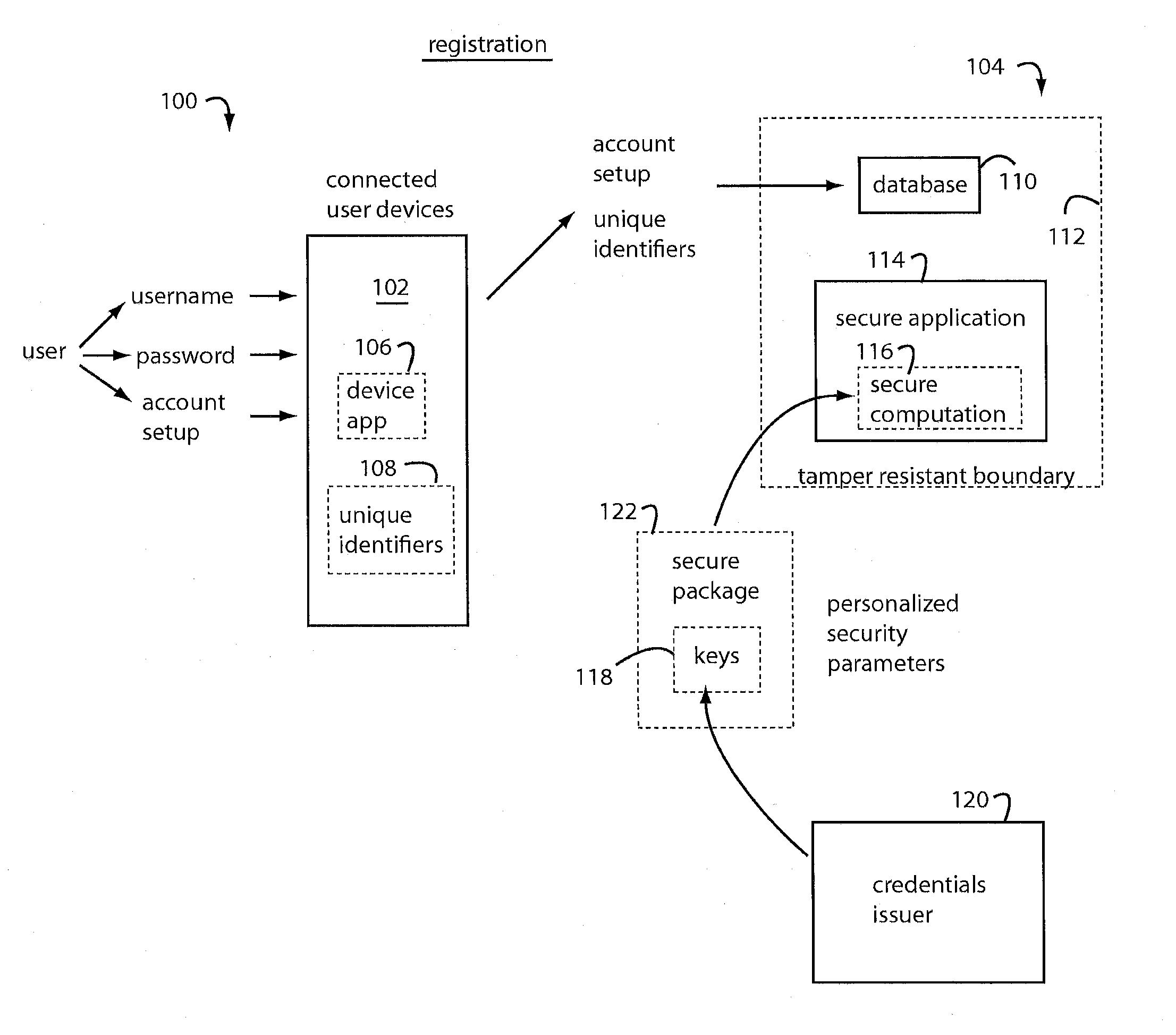
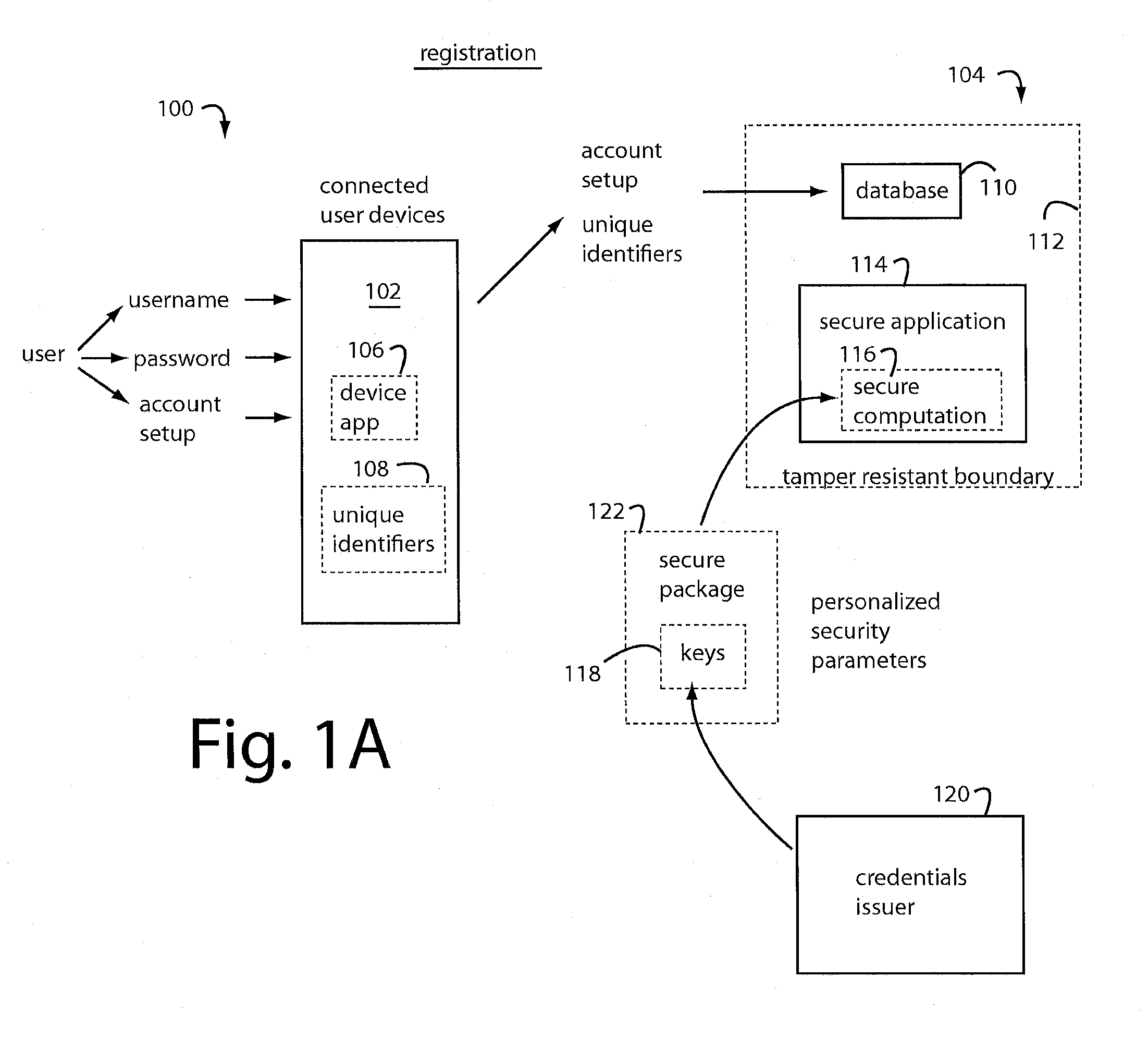
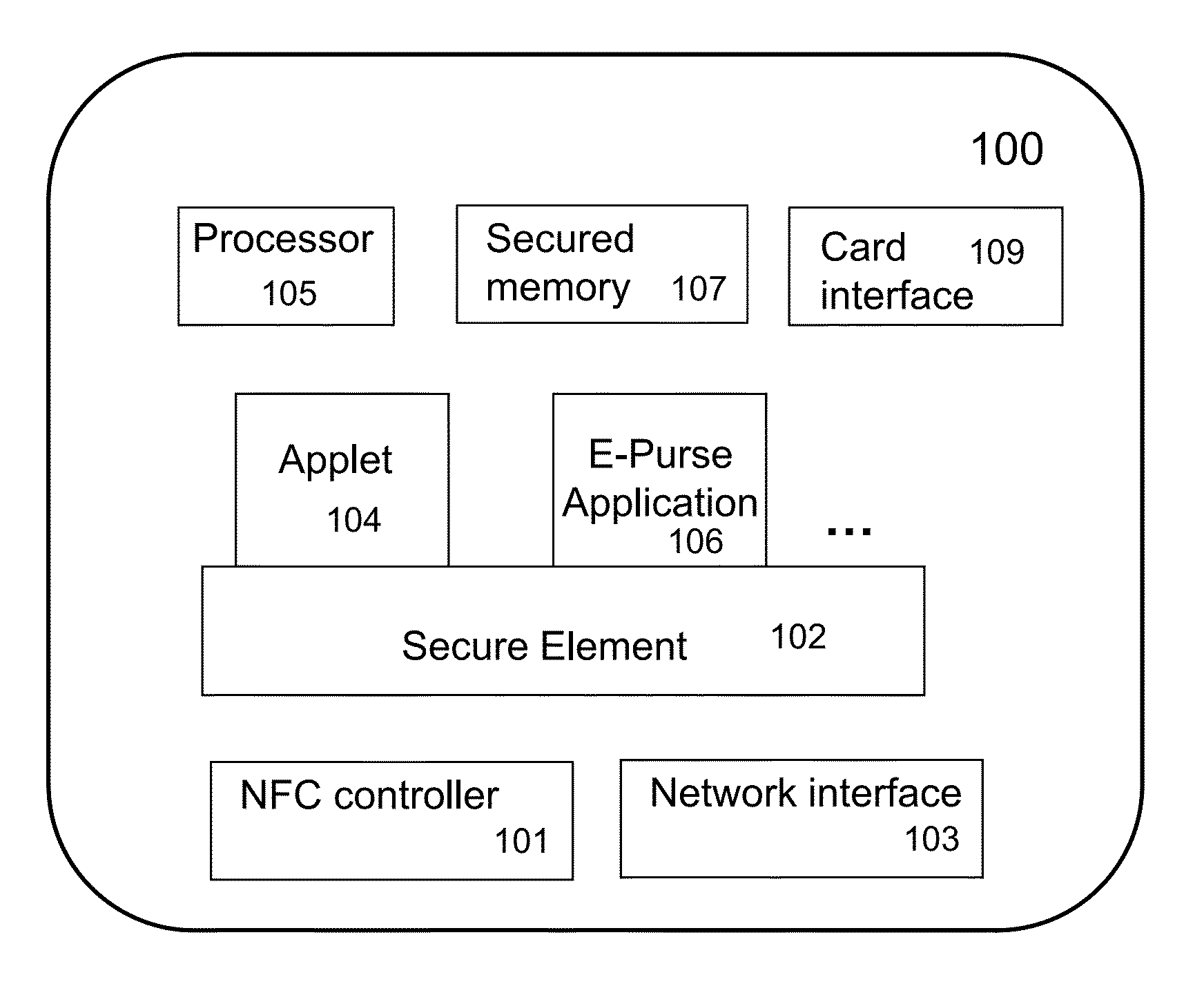
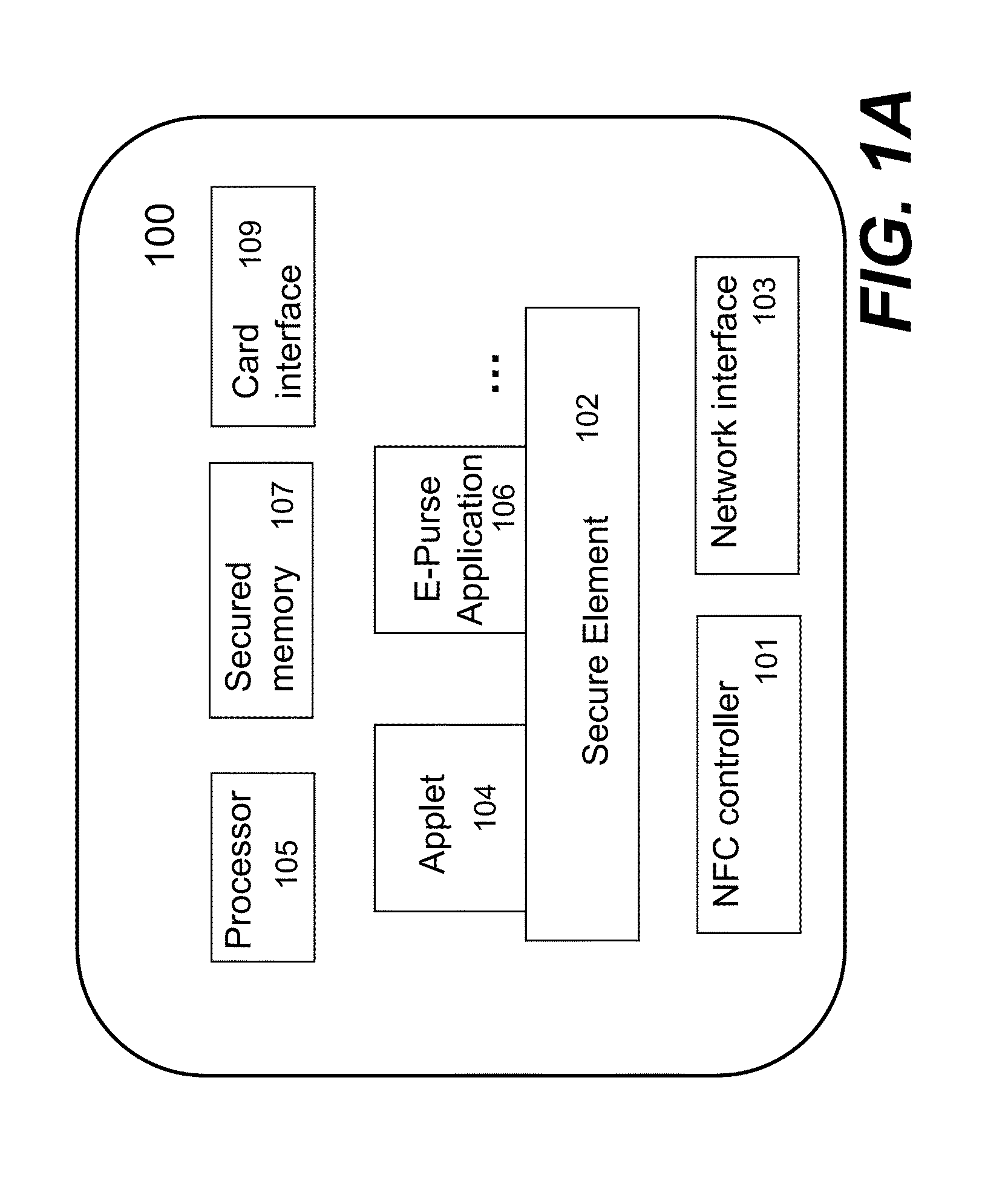
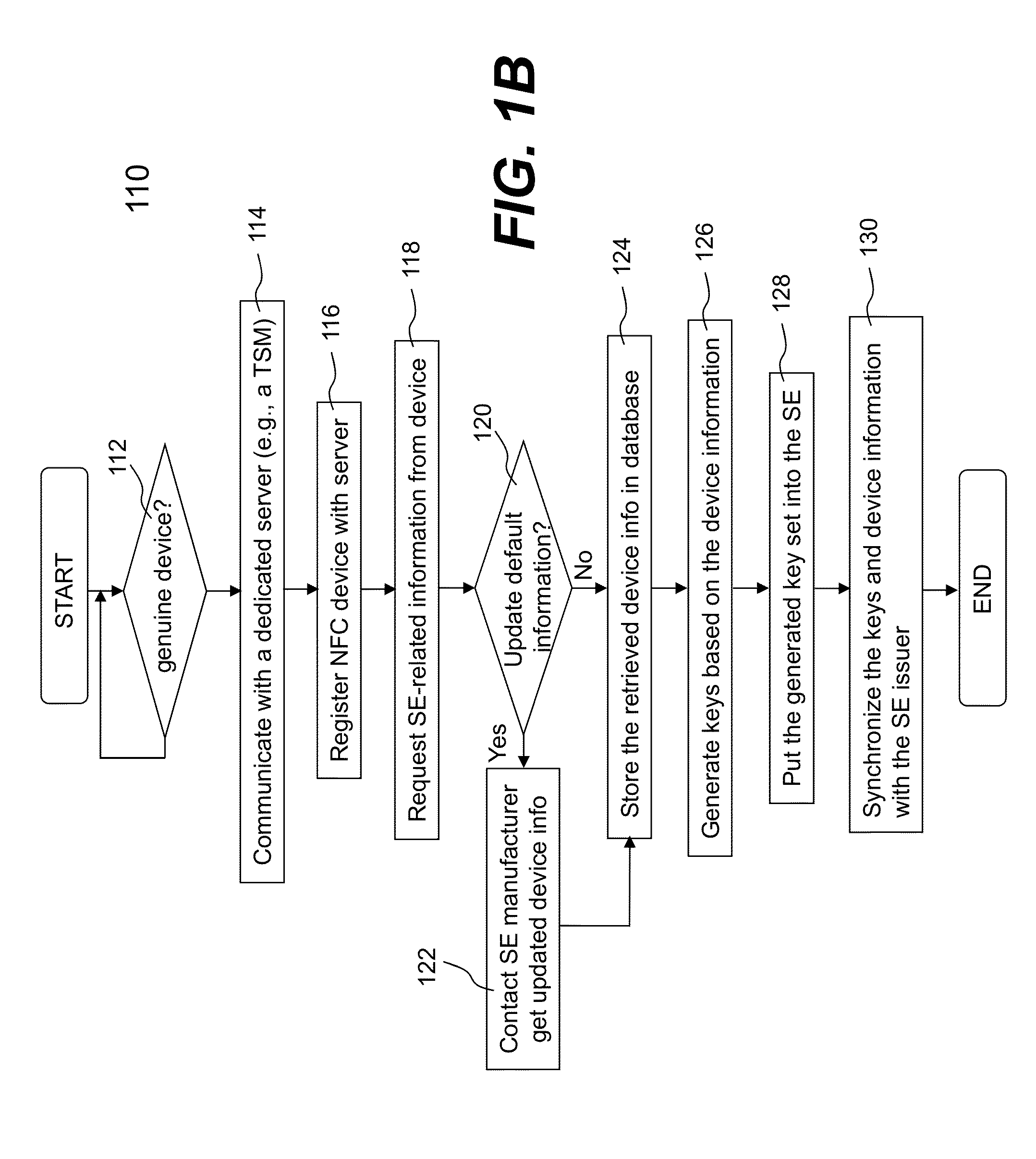
Mobile devices for commerce over unsecured networks
ActiveUS20120130839A1Digital data processing detailsMultiple digital computer combinationsPersonalizationComputer module
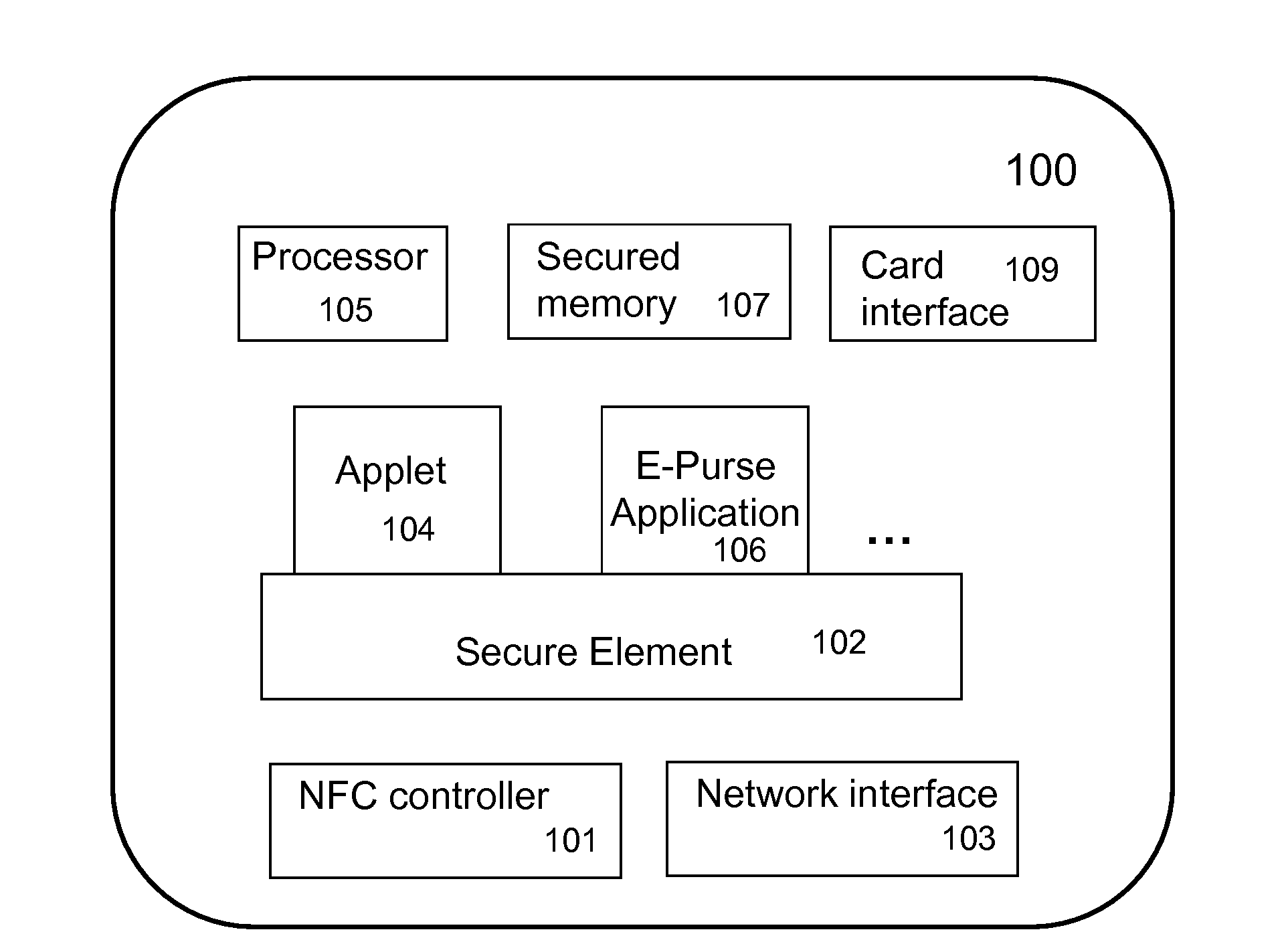
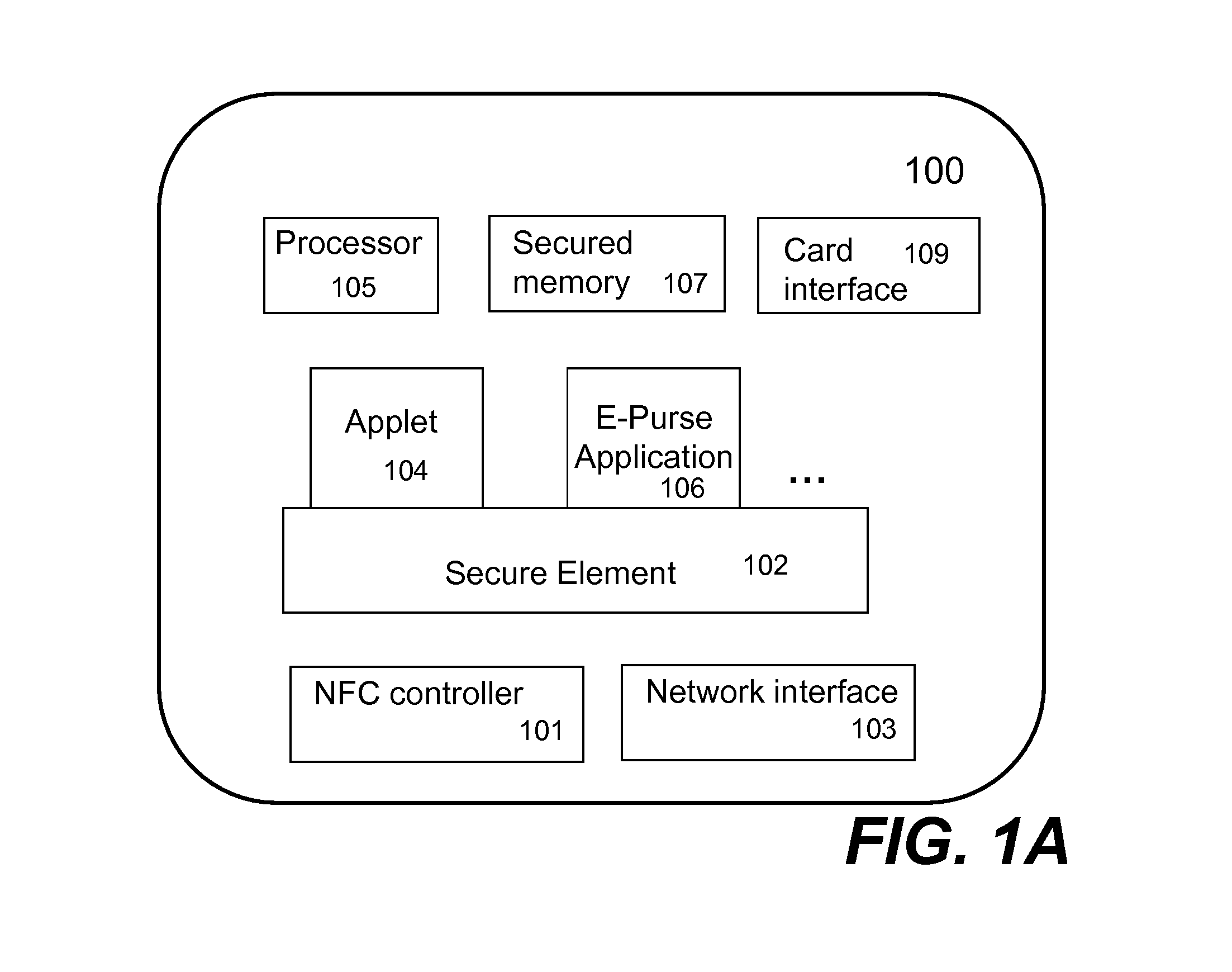
Techniques for managing modules or applications installed in a mobile device are described. To provide authentic and secured transactions with another device, each of the installed applications is provisioned with a server through data communication capability in a mobile device. A provisioned application is associated with the personalized secure element in the mobile device and works with a set of keys that are generated in accordance with a set of keys from the personalized secure element. Further management of controlling an installed application is also described.
Owner:RFCYBER CORP
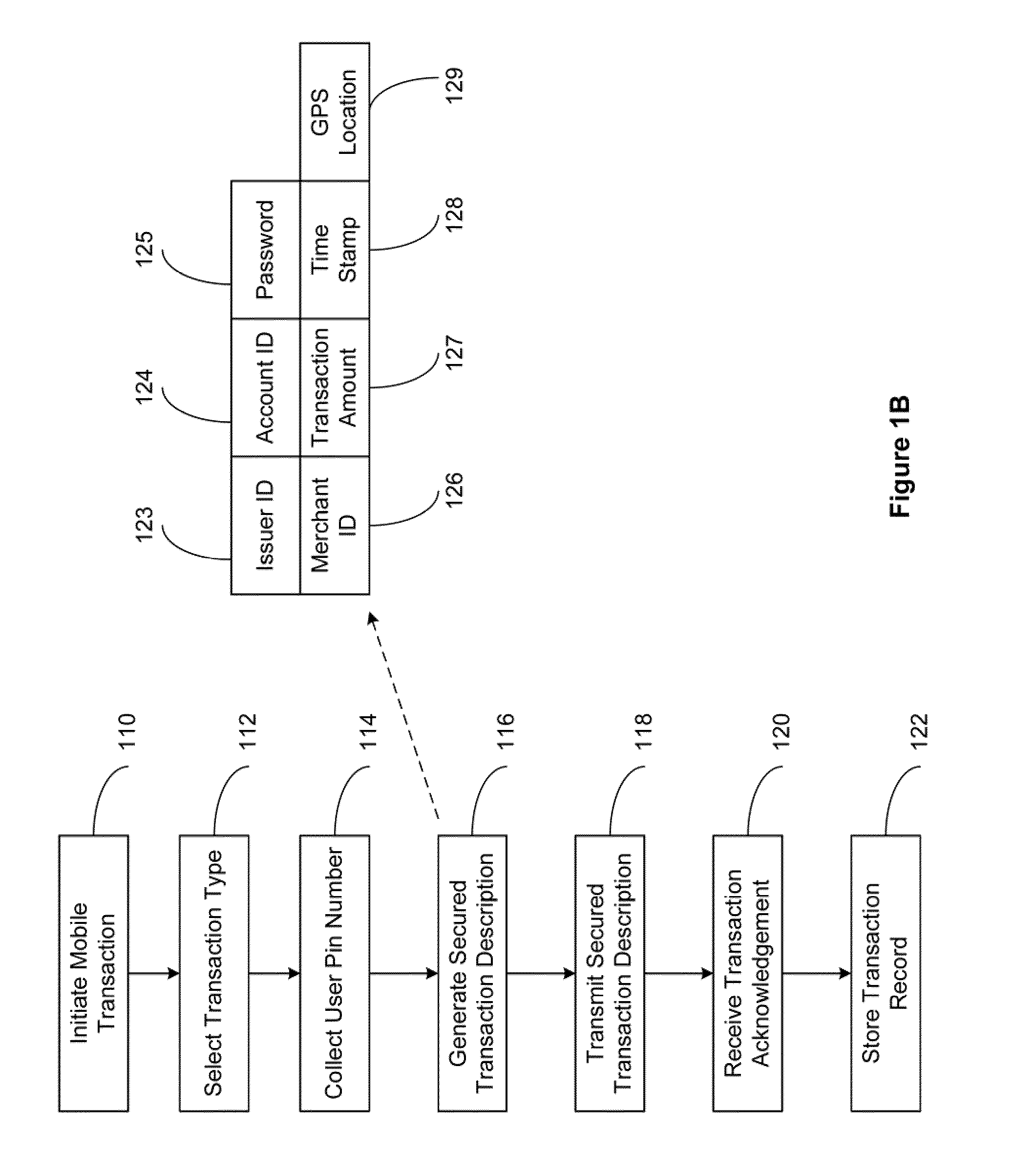
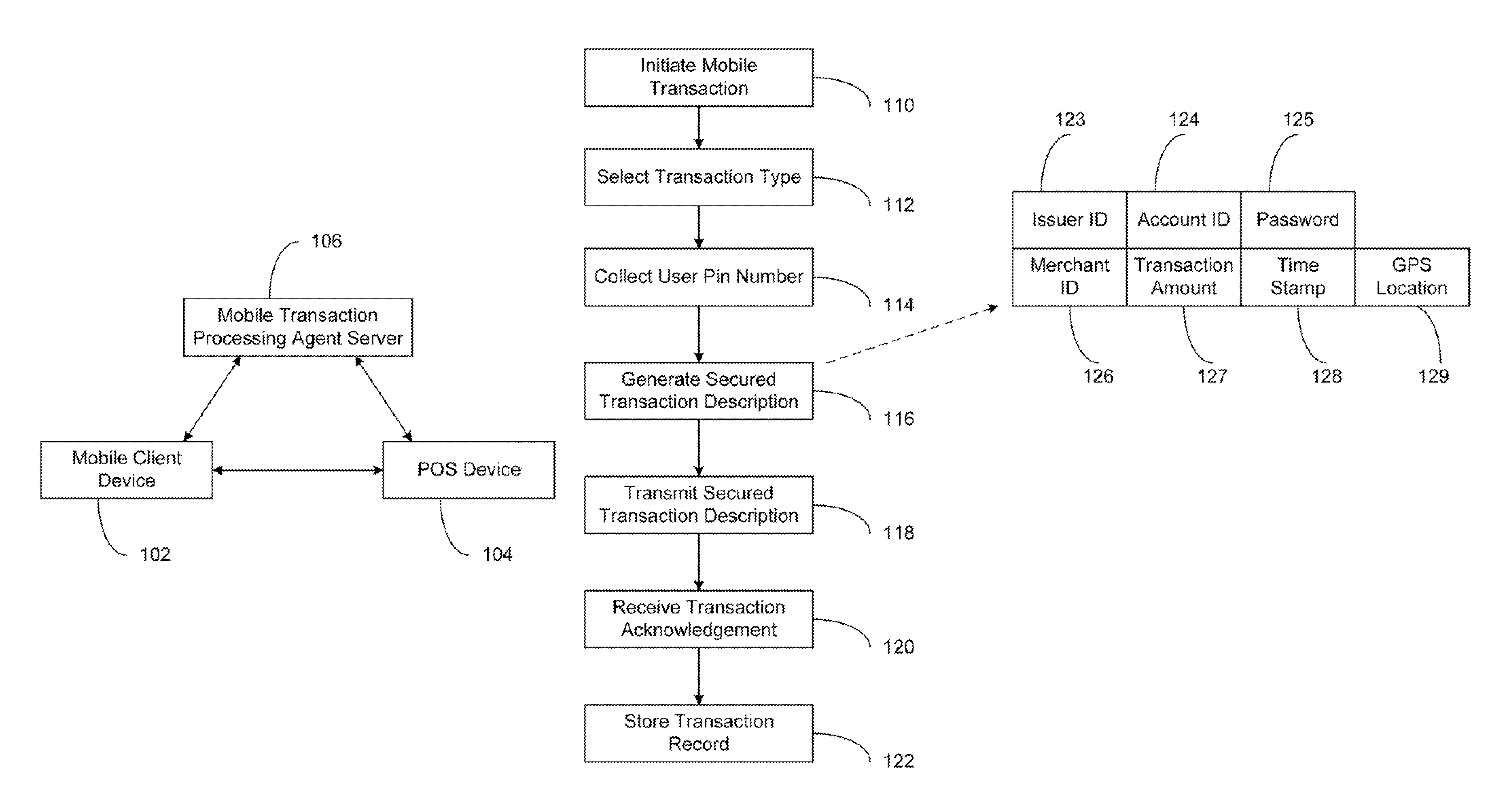
Secured Mobile Transaction Device
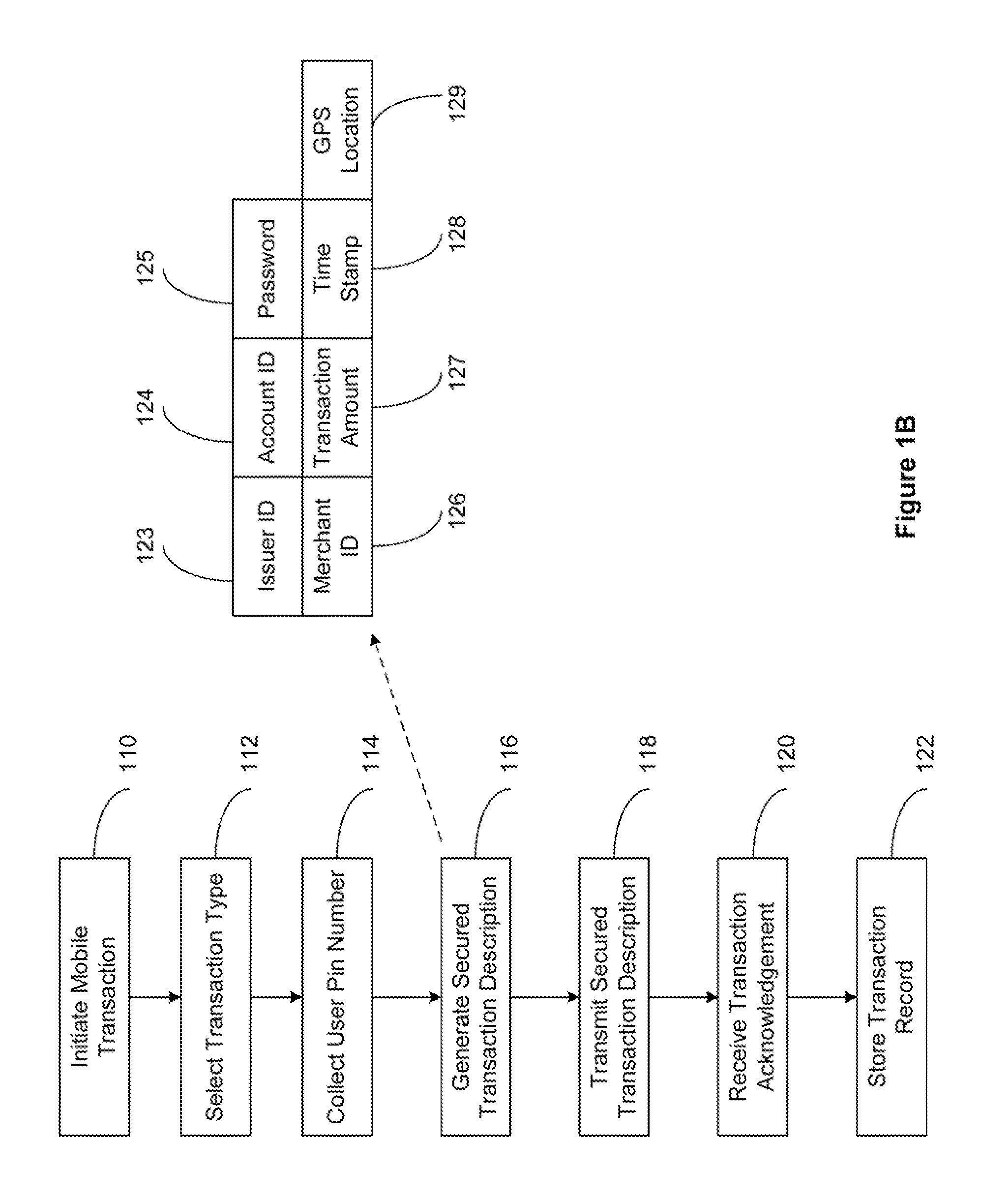
InactiveUS20110191161A1Improve securityFinanceBuying/selling/leasing transactionsPasswordMobile transaction
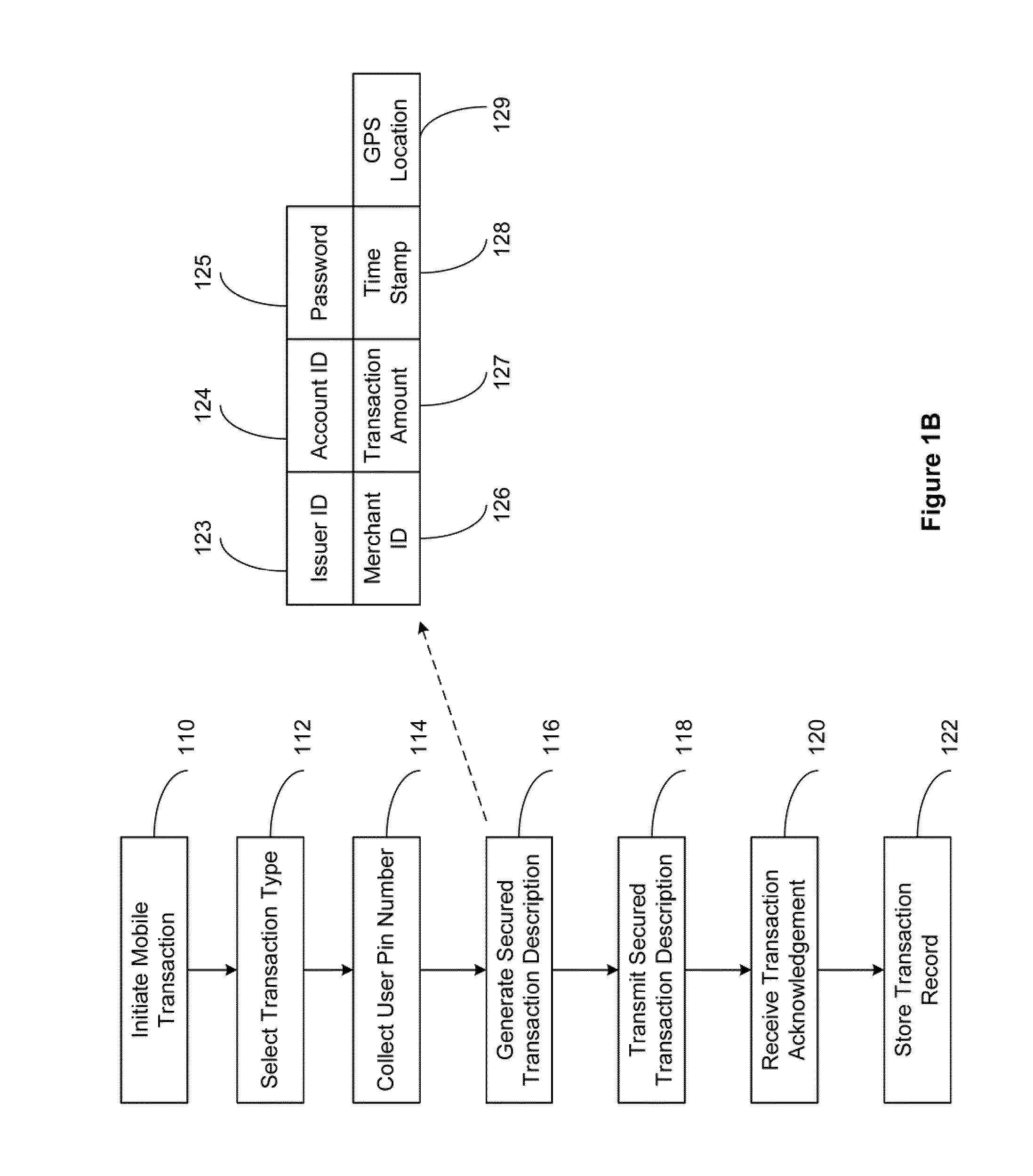
The present invention relates to a secured transaction system. In one embodiment, a mobile client device includes a user interface configured to enable a user to select a transaction type and collect a user pin number, a processor configured to generate a secured transaction description using the transaction type and the user pin number, wherein the secured transaction description includes issuer ID, account ID, merchant ID, password, transaction amount, and transaction time stamp, and the processor is further configured to transmit the secured transaction description to a mobile processing agent for processing, and receive a transaction record from the mobile transaction processing agent, and a memory configured to store the transaction record in the mobile client device.
Owner:DAI XIA
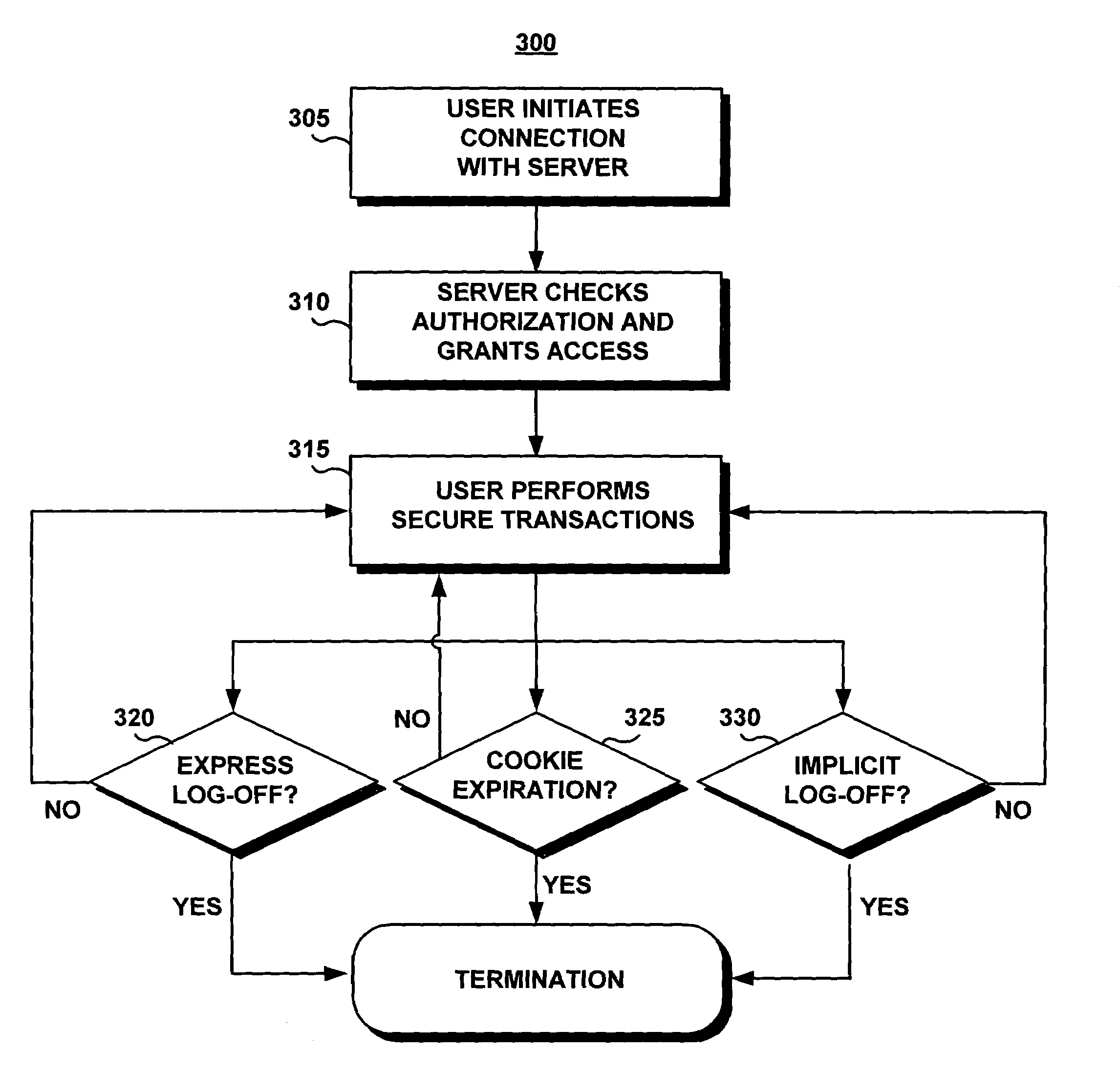
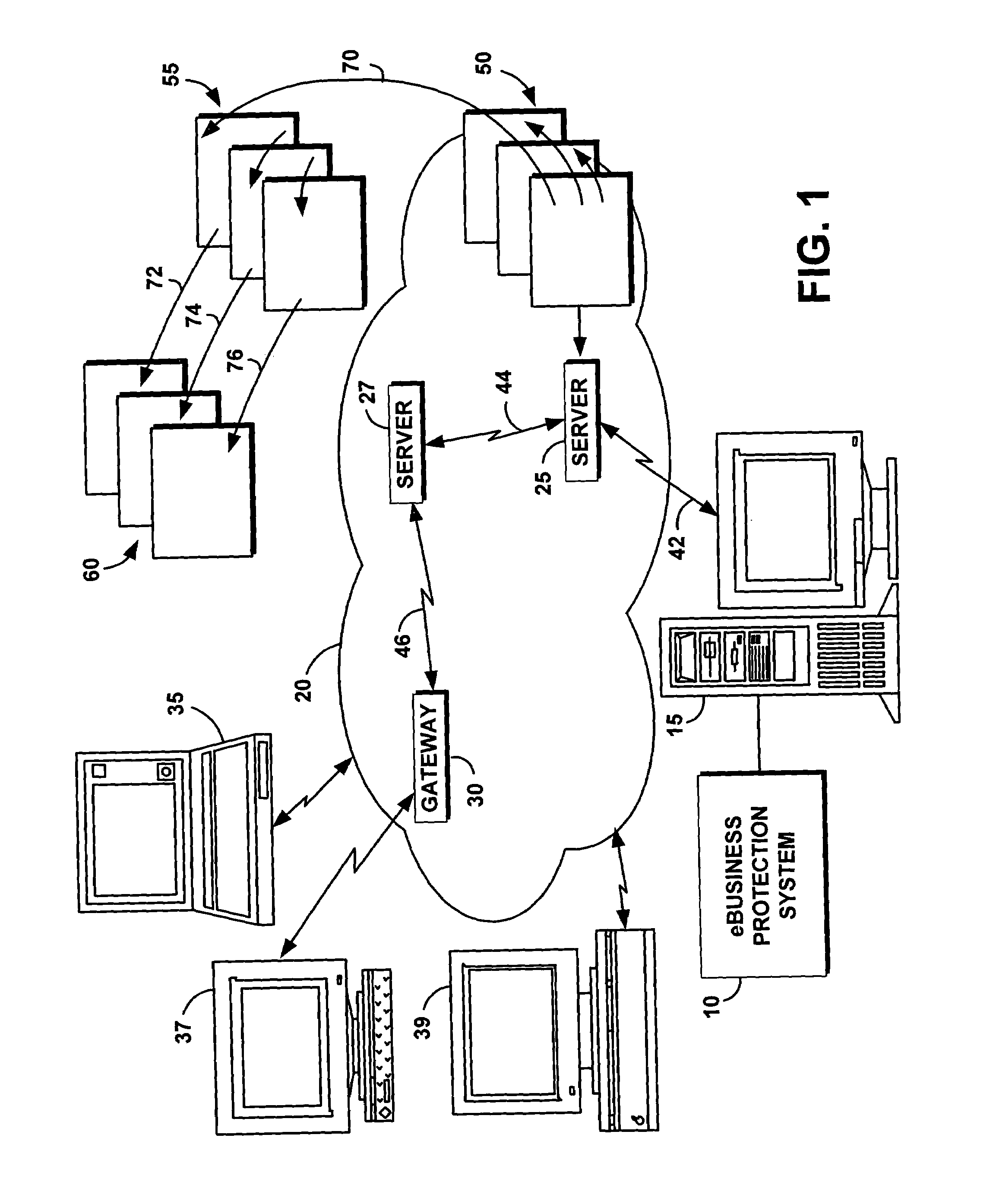
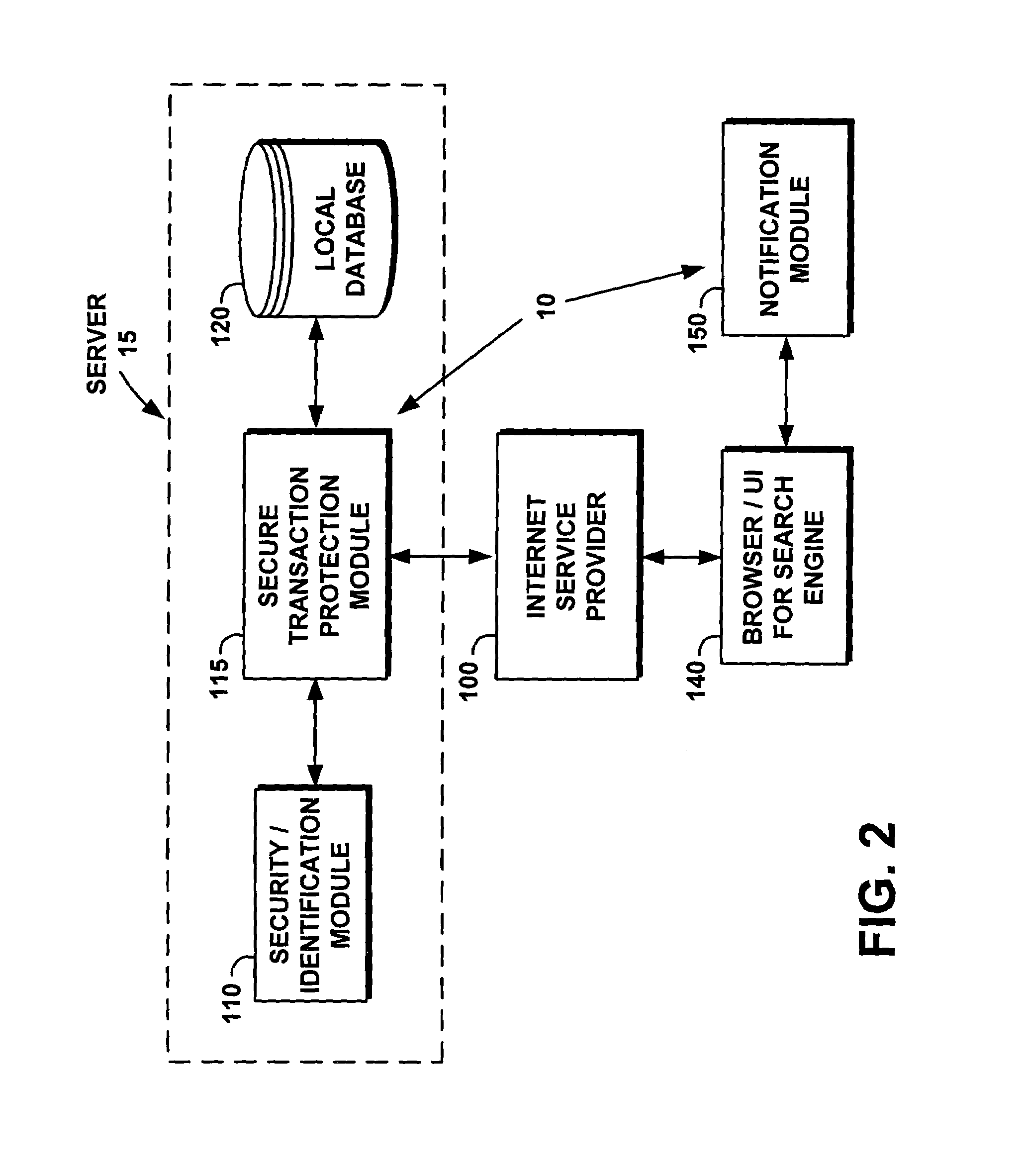
System and method for protecting user logoff from web business transactions
InactiveUS7024394B1Reduce riskReduce chanceComputer security arrangementsPayment architectureWeb siteWeb browser
A computer program product is provided as a system and associated method for use with a web browser and an Internet, to improve the access security to a secure web site and to protect the user from undesirable hacking. The system presents a novel, secure, implicit log-off procedure in addition to the conventional express log-off and cookie termination. The implicit log-off procedure reduces the risks resulting from transiting to an insecure site while remaining logged onto a secure site. The system is comprised of a secured transaction protection module implemented on a business server that includes a security / identification module and a local database; and a notification module which is implemented on the user's browser. The system tracks the user's access state to the server, and issues a termination command shortly as soon as the notification module detects migration to another site or to an insecure page on the same site.
Owner:IBM CORP
Smart apparatus for making secure transactions
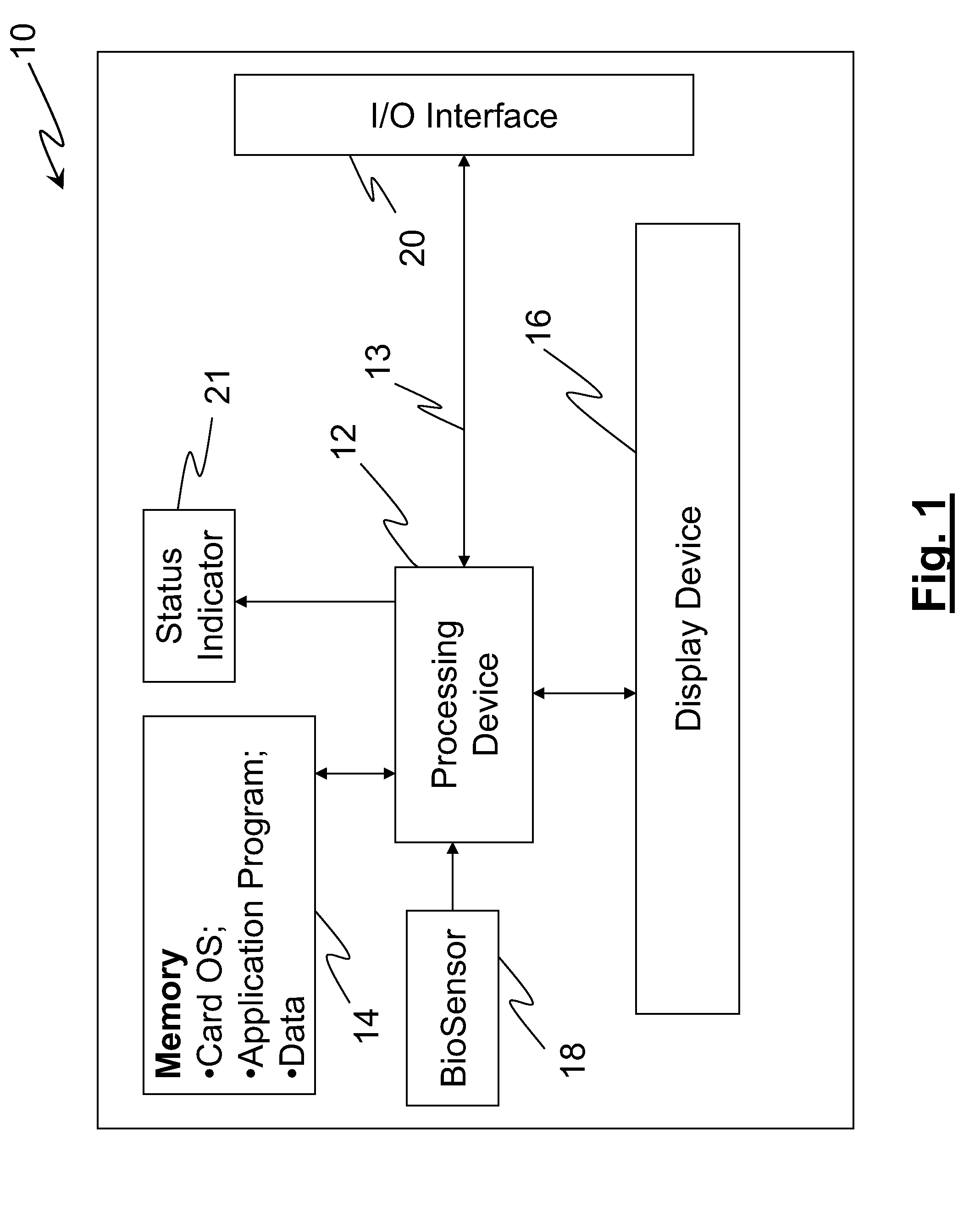
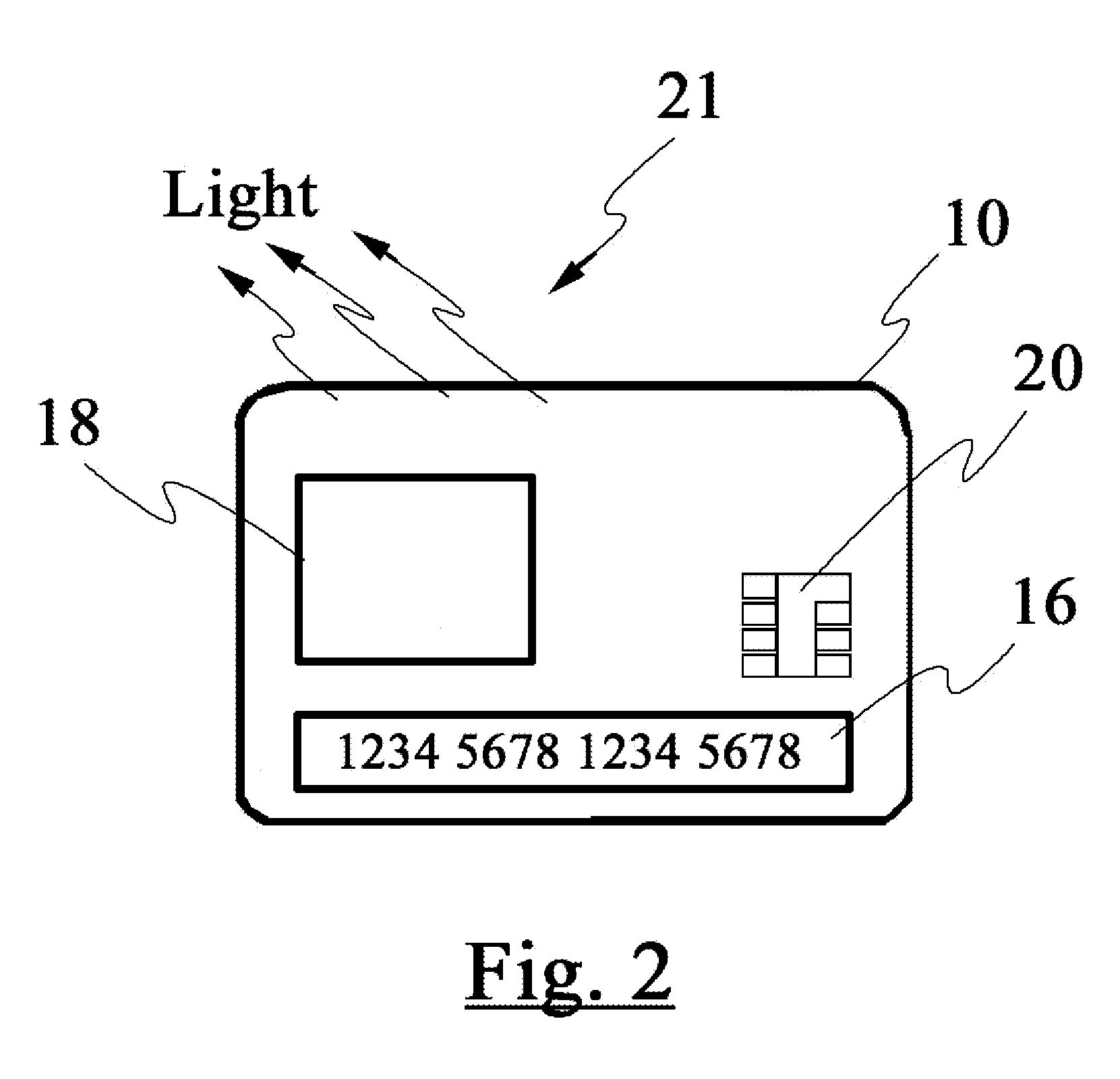
InactiveUS20080223937A1Internal/peripheral component protectionDigital data authenticationDisplay deviceFinancial transaction
The disclosed invention relates to an apparatus and method for making secured transactions. Such an apparatus may include a smart card device configured with a display for display a static or dynamic number for making a secured transaction. The display is configured to display a valid card number after the user's identify has been verified using a biometric verification process. The device may further comprise a programmable magnetic strip that is programmed with user data after the user's identify has been verified. The apparatus may further include a cloning process to allow a second device to perform secure transactions. One such second device is a smart module associated with a vehicle.
Owner:PATENT ZERO
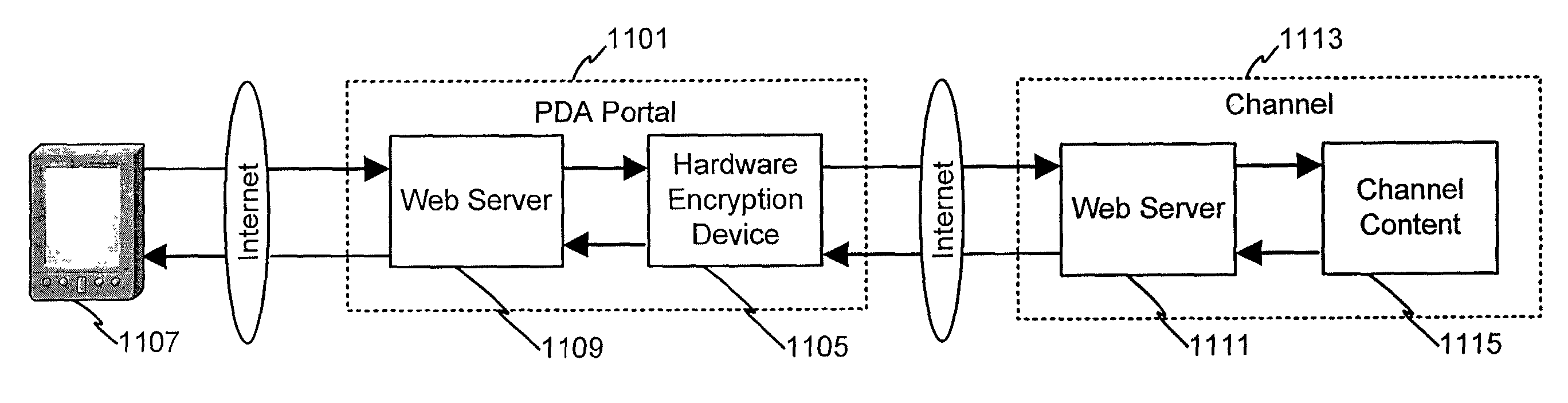
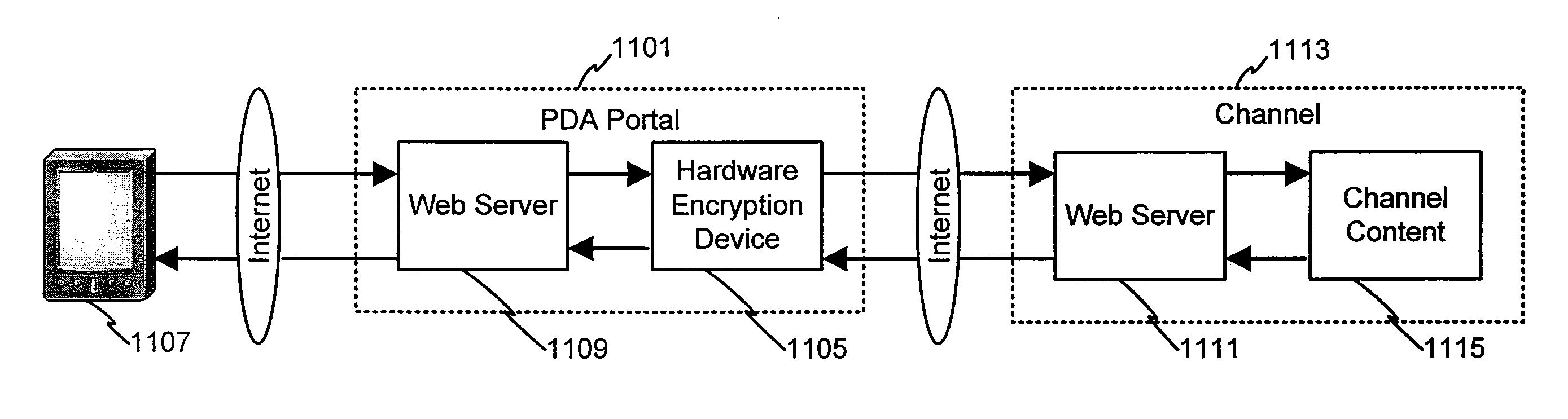
System and method for securing data through a PDA portal
InactiveUS7222101B2Easy to purchaseFacilitate loyalty processVolume/mass flow measurementAnalogue secracy/subscription systemsWeb siteSecured transaction
Owner:LIBERTY PEAK VENTURES LLC
Method for verifying a consumer's identity within a consumer/merchant transaction
InactiveUS20140214670A1Overcome disadvantagesFinanceProtocols using social networksUnique device identifierUser authentication
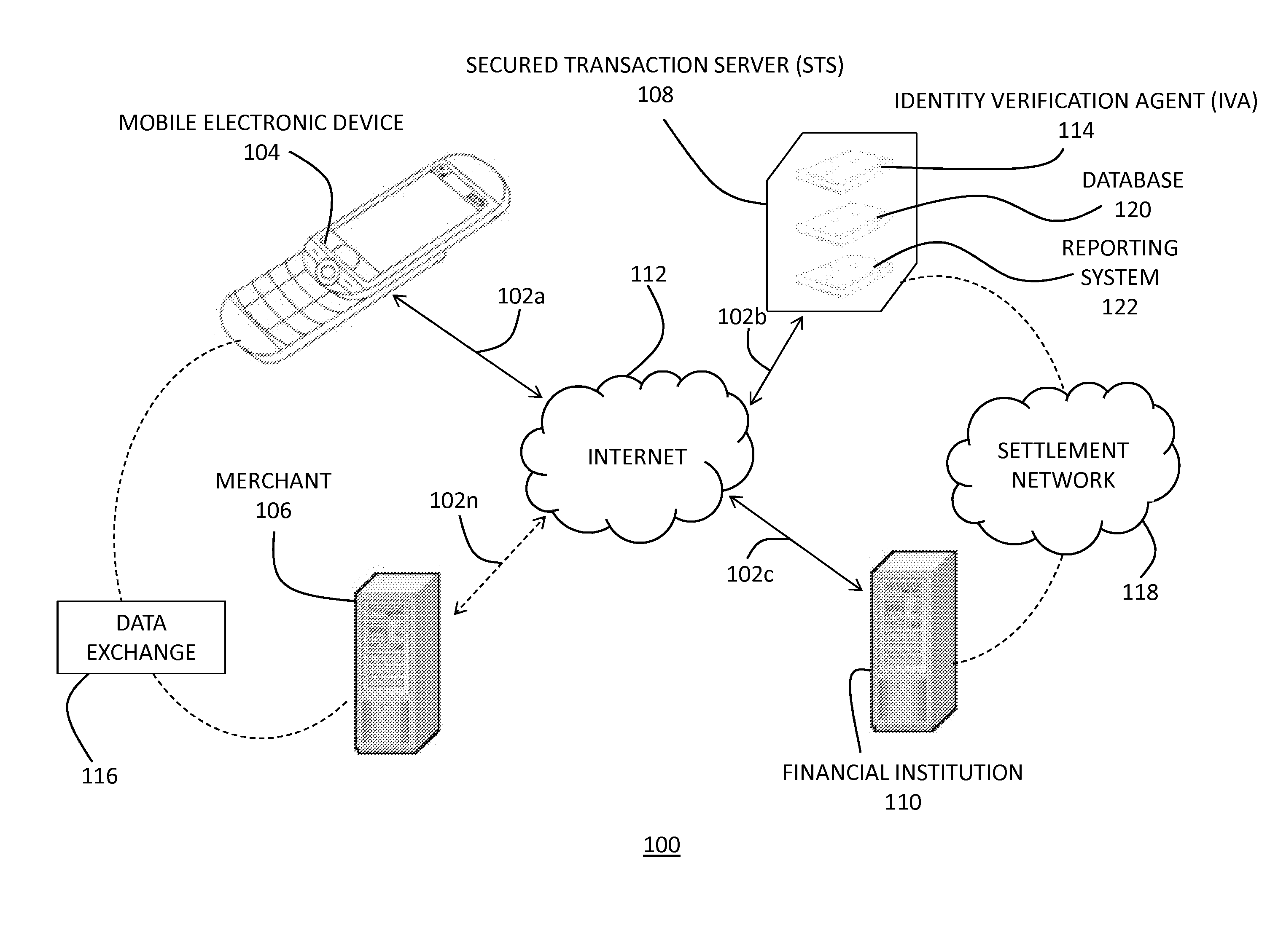
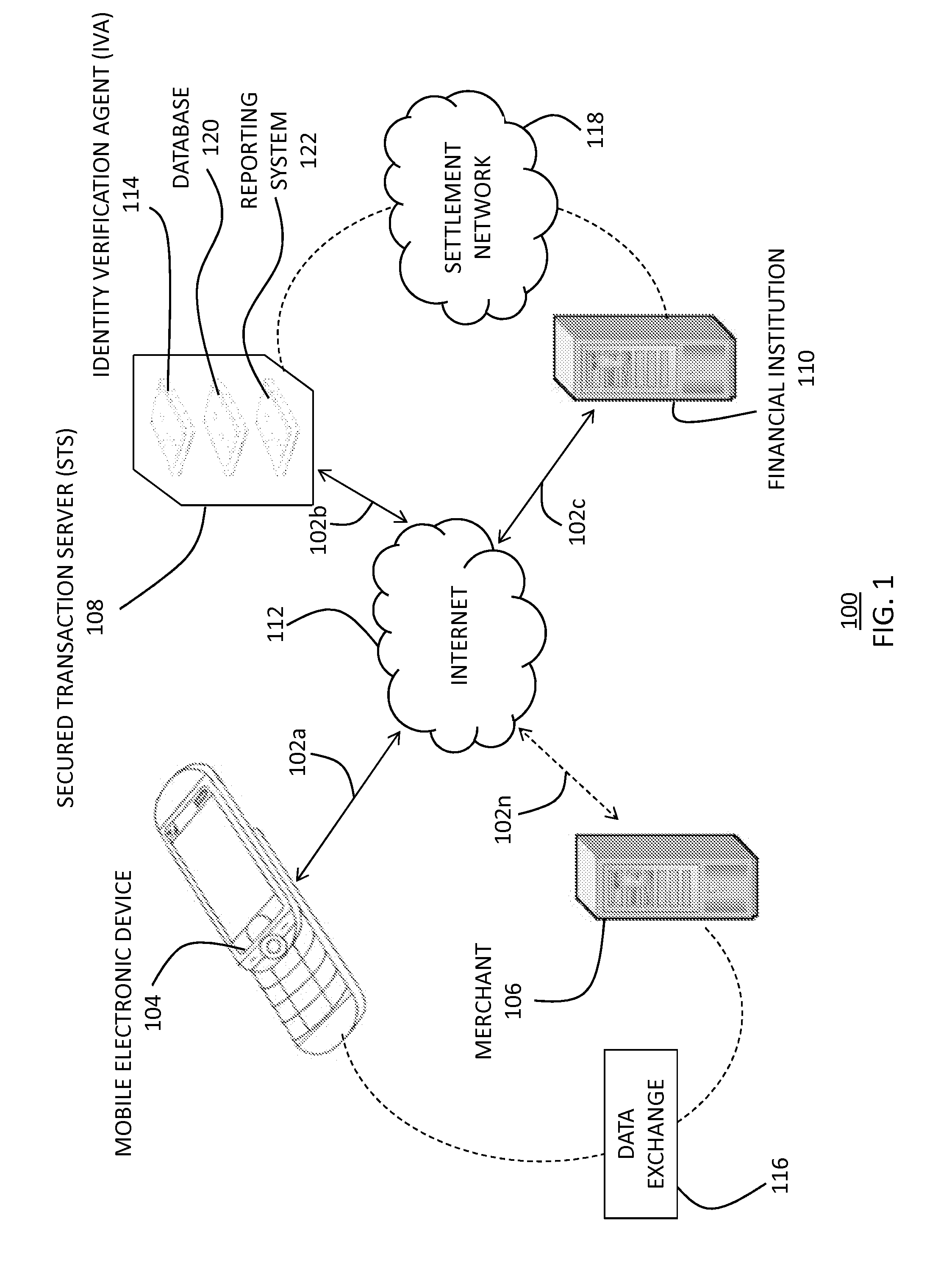
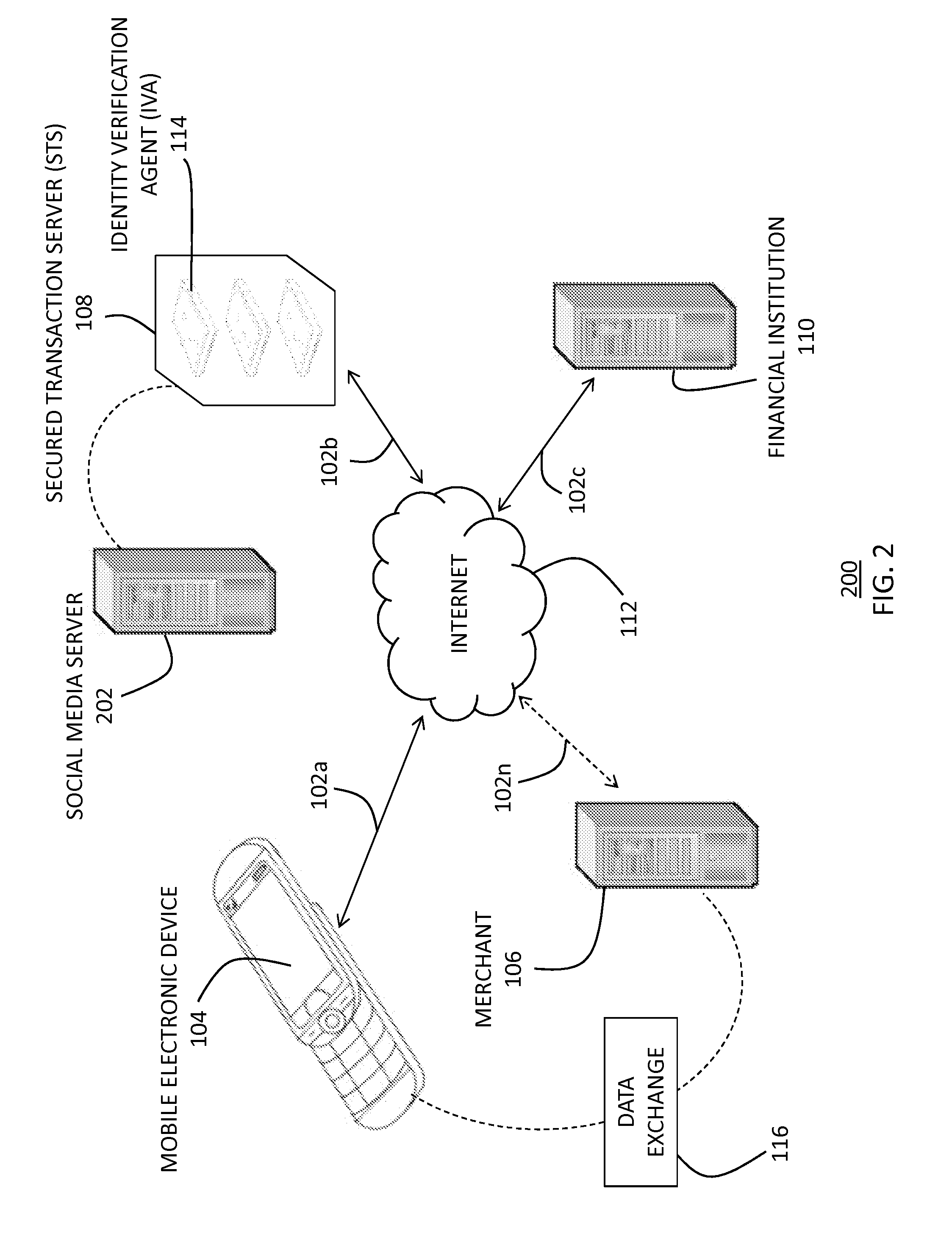
A method for verifying a consumer's identity in connection with a consumer / merchant transaction, including receiving a user-identifier from a user, receiving a unique device identifier from an electronic device associated with the user, associating the user-identifier and the unique device identifier of the user to a user account residing on a secured transaction server (“STS), the STS not operated by the merchant and including an identity verification agent. The method further includes receiving a consumer identity verification request at the STS, receiving a unique device identifier associated with an electronic device of the consumer at the STS, comparing, through the identity verification agent, the user's unique device identifier and the consumer's unique device identifier to determine at least one of a positive or negative user-identity verification, and then communicating to the merchant the at least one of the positive or negative user-identity verification.
Owner:MCKENNA JASON C
System and method for secured data transfer over a network from a mobile device
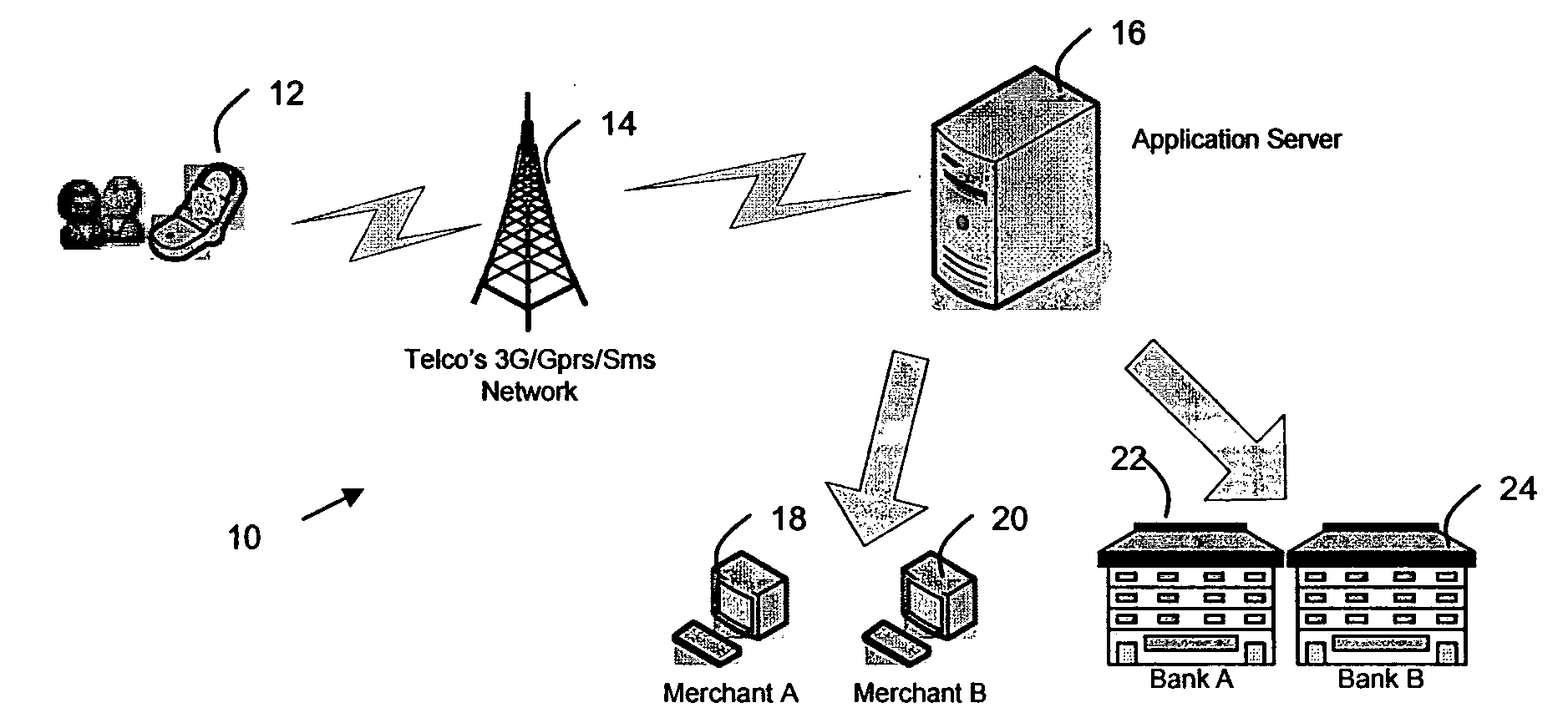
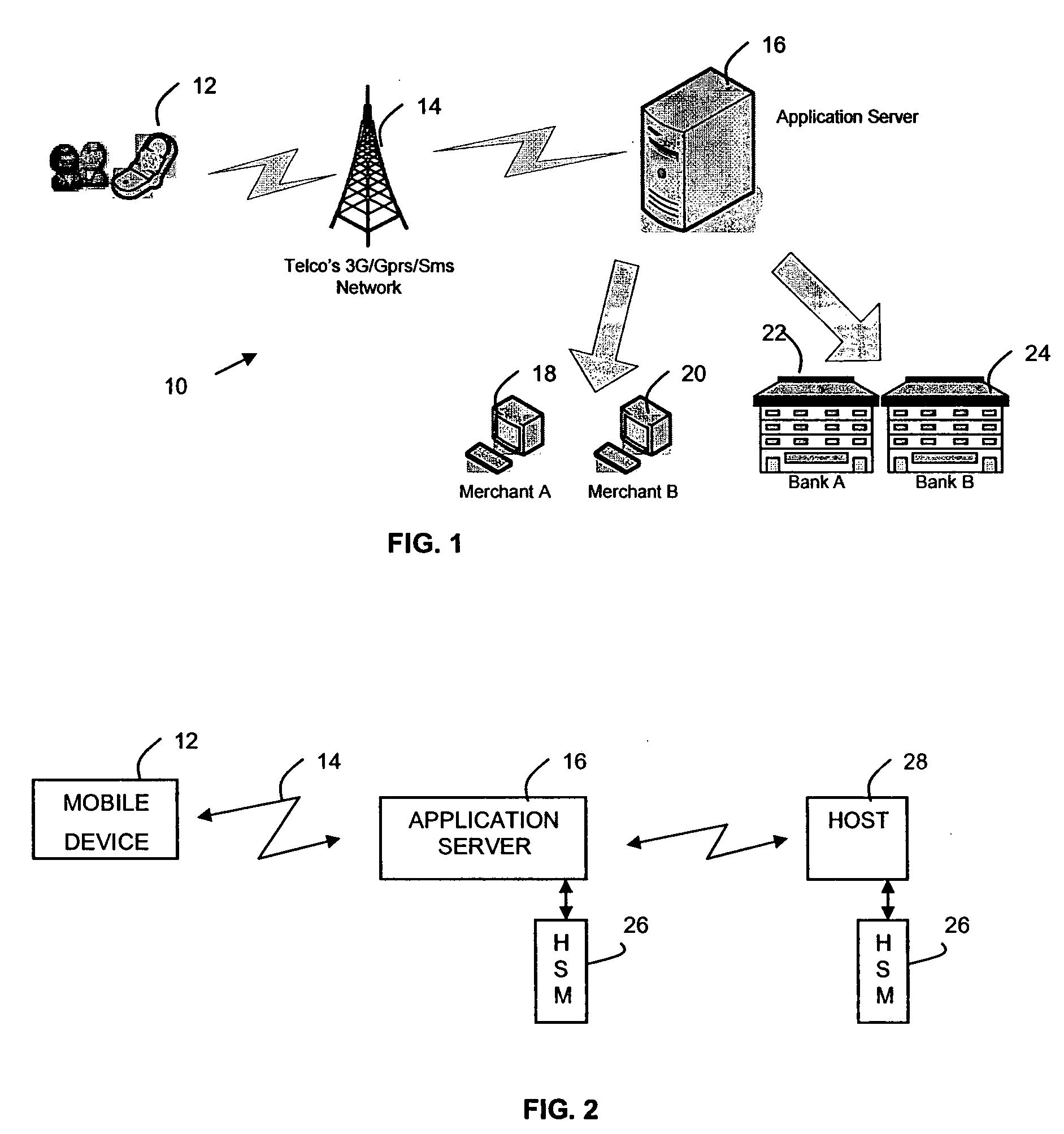
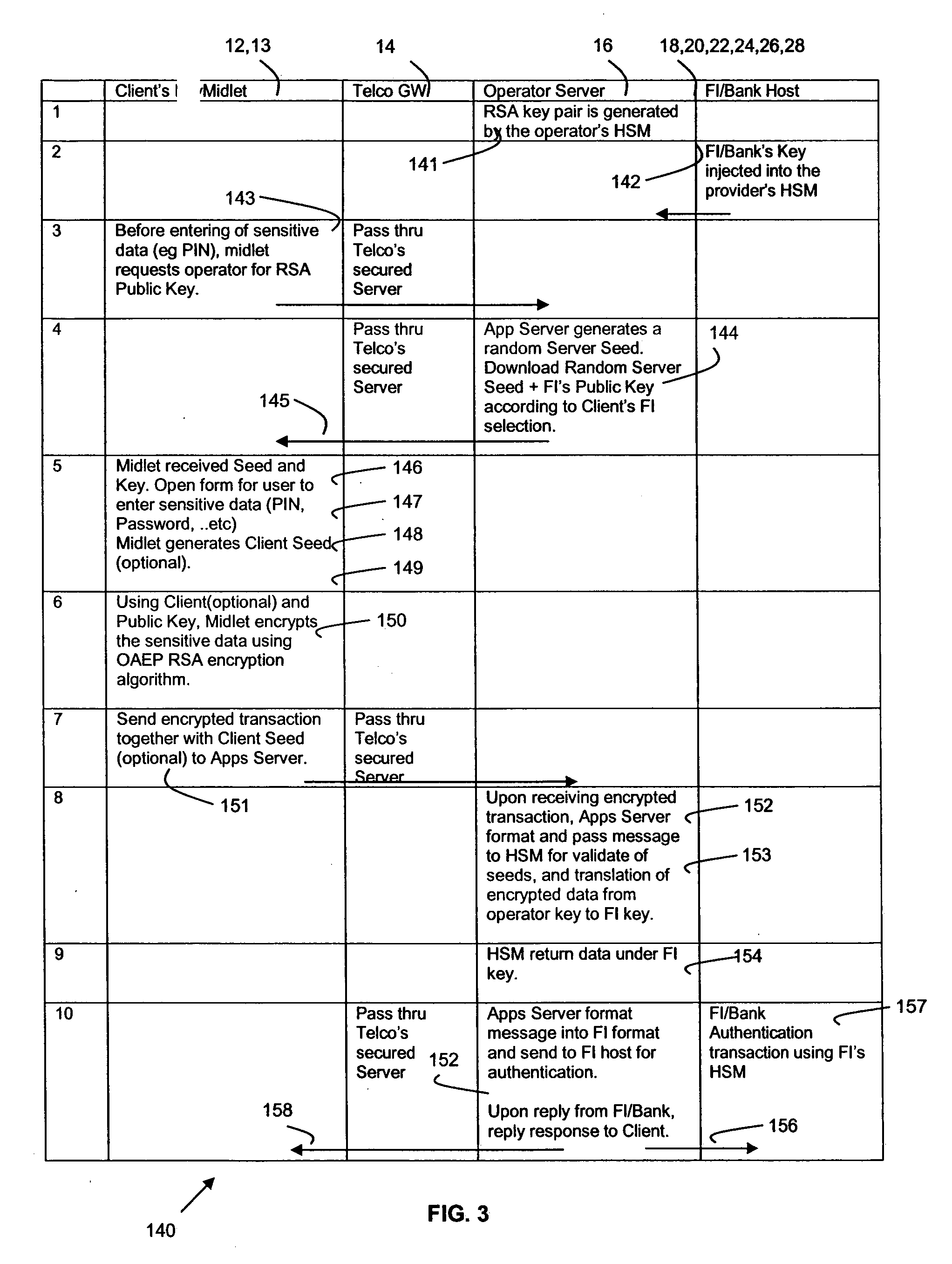
A secured data transfer system (10) and method is disclosed in accordance with an embodiment of the invention that enables sensitive data to be securely exchanged from a user / client's mobile device (12), phone, personal digital assistant (PDA), or the like to a back-end host (28), flowing through many hops and points in an public network, for example the Internet and / or in applications such as service provider's wireless networks, without being exposed to any security gaps in between servers. The system and method provides a secure solution that plugs the gaps and ensures a true end-to-end, bank-grade secured transaction exchange between the user / client's mobile device (12) and the back-end host (28) and using caching method for network traffic data reduction techniques.
Owner:EZYPAY PTE
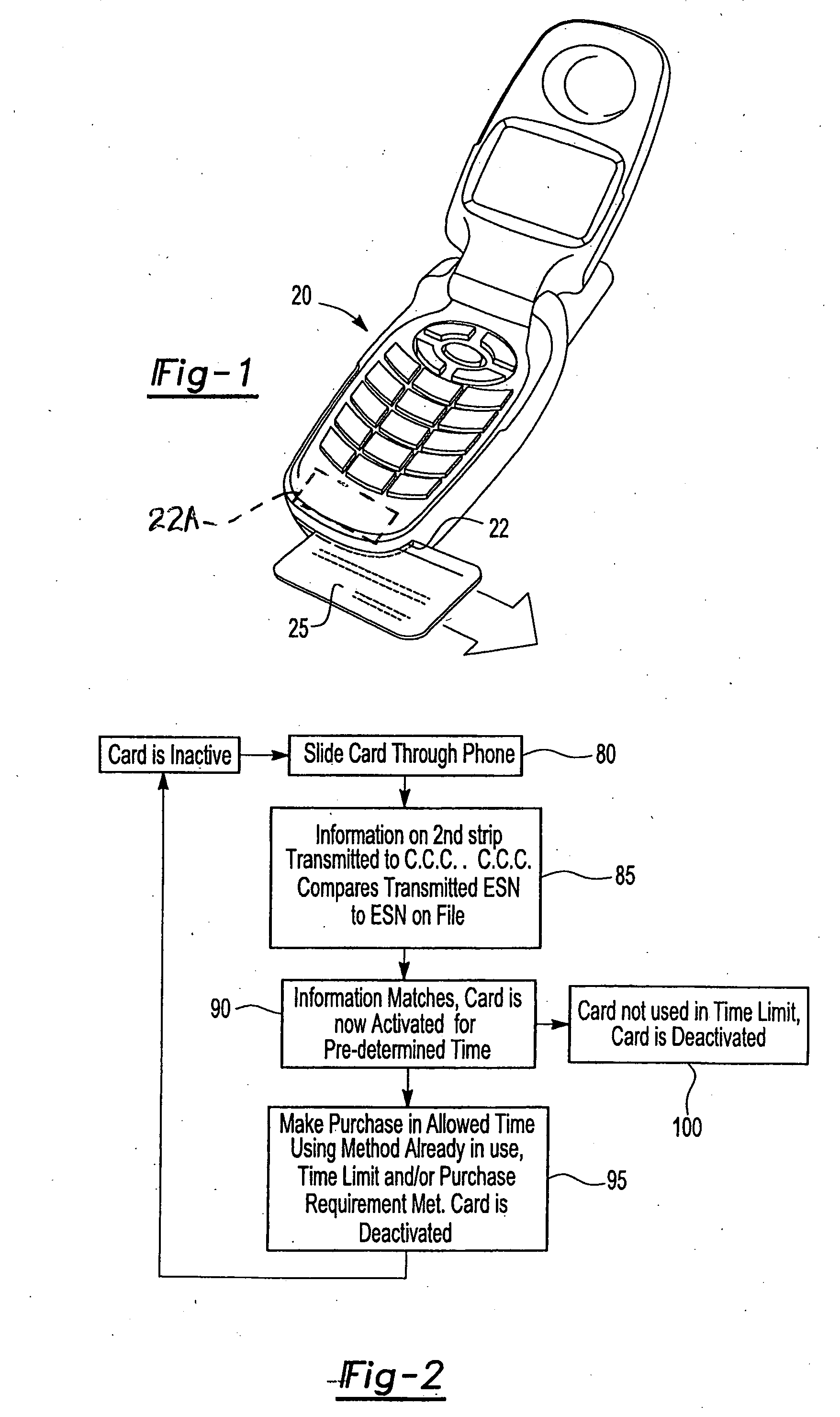
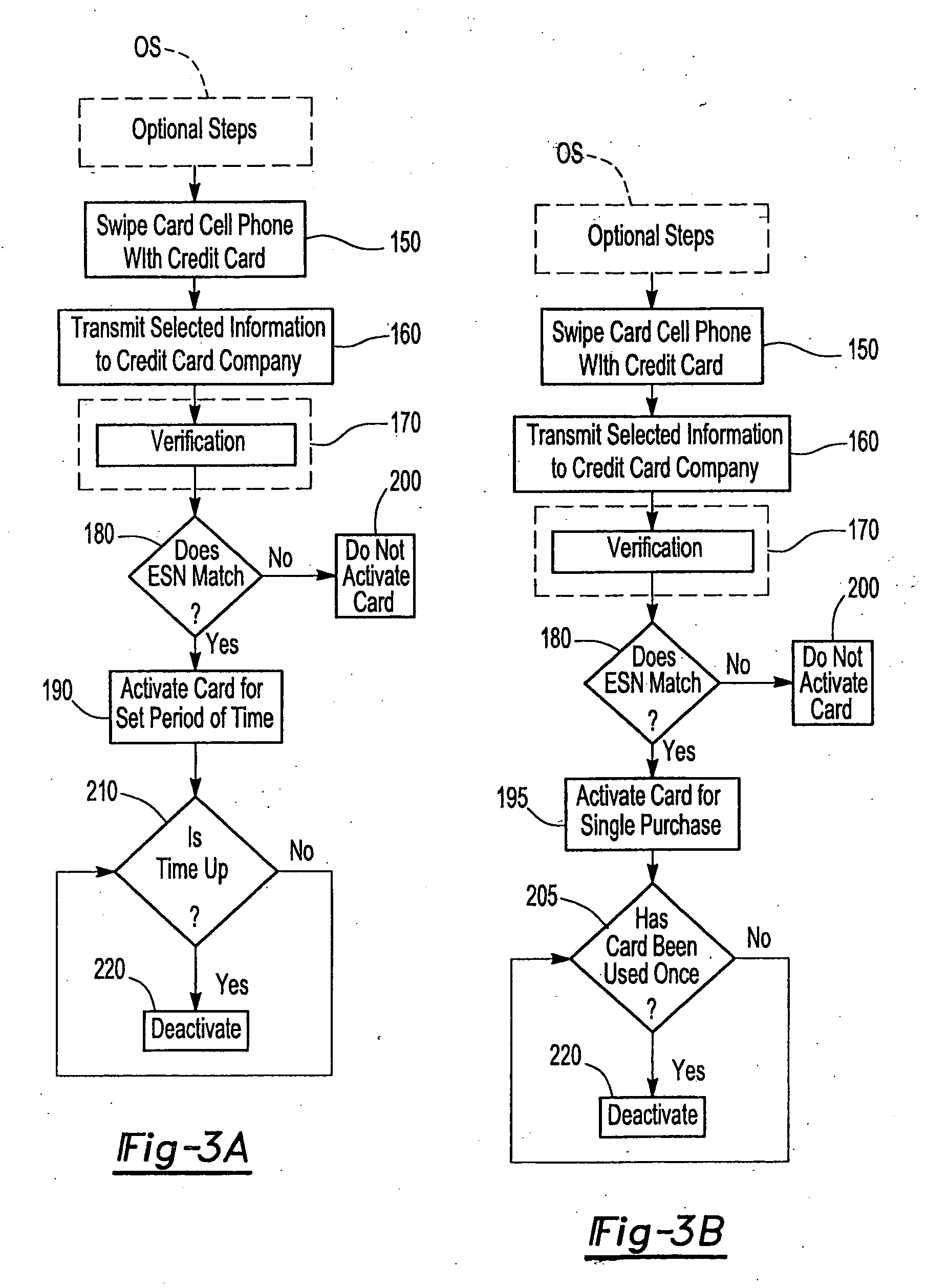
Method and apparatus for securely activating a credit card for a limited period of time
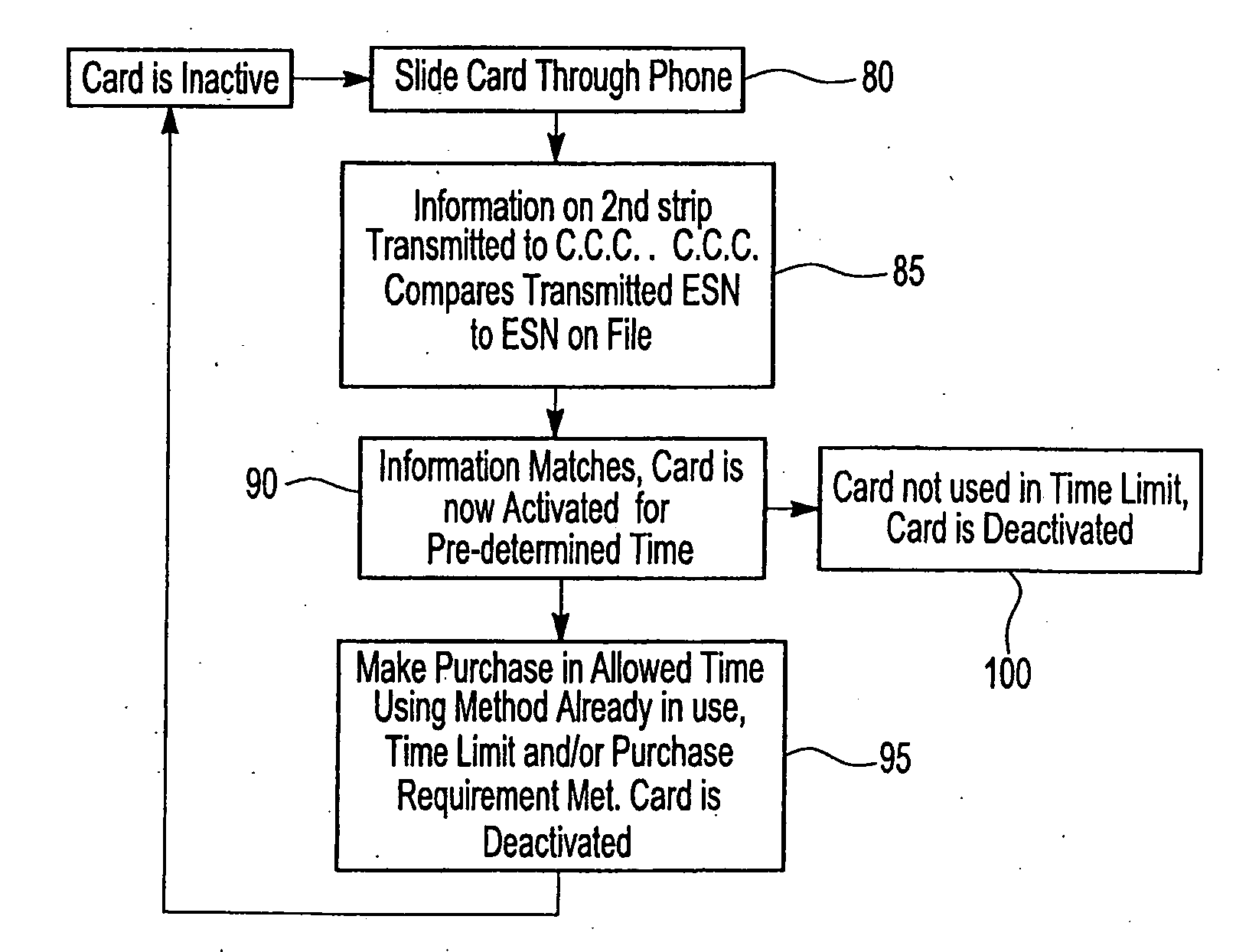
An apparatus and methods securely activate a credit or debit card for a single purchase, a predetermined amount of time, or a predetermined amount of purchases in a predetermined amount of time, while utilizing a portable phone, especially a cell phone, having a card reader. Only transactions using the electronic telephone number and electronic serial number of the cell phone being used, along with preselected information identifying the owner of a swiped card will be authorized to perform credit and debit card transactions, thus providing secured transactions. Current card magnetic strips and possibly magnetic or other type of strips that are smaller in size and closer to the edge of the credit or debit card are serviced.
Owner:WORONEC JOHN S
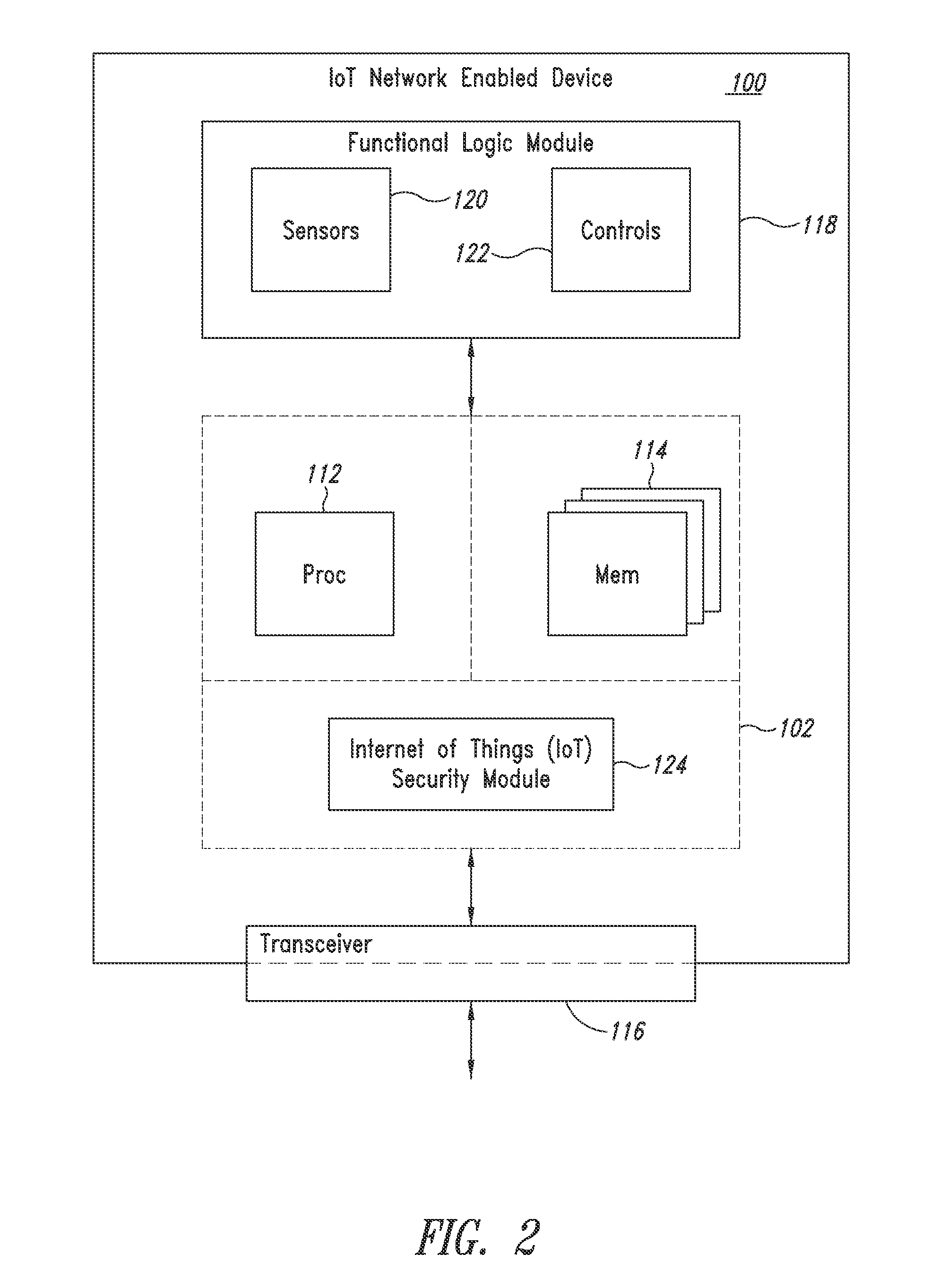
Secured transactions in internet of things embedded systems networks
ActiveUS20150229654A1Digital data processing detailsMultiple digital computer combinationsTransceiverComputer network
A secure network enabled device has a distinct security module and lacks a human user input interface. The security module is formed in an integrated circuit. The security module is initialized. Data is electronically communicated to and from the secure network enabled device via at least one transceiver. The security module is configured to test the integrity of a subset of the data communicated to the secure network enabled device, and the security module is configured to test the integrity of a transaction protocol, which governs the stream of data bits of the data communicated to the secure network enabled device.
Owner:STMICROELECTRONICS INT NV
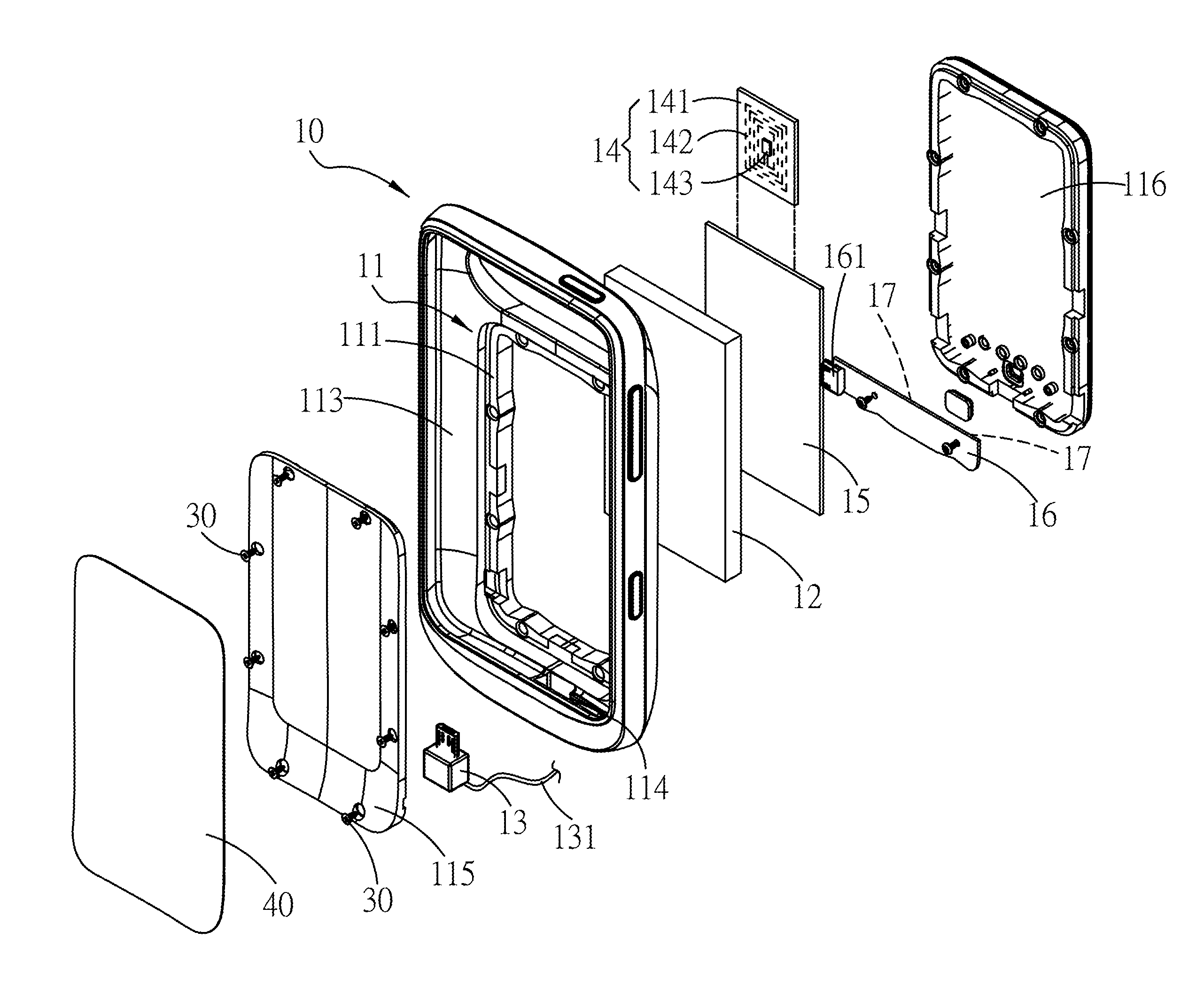
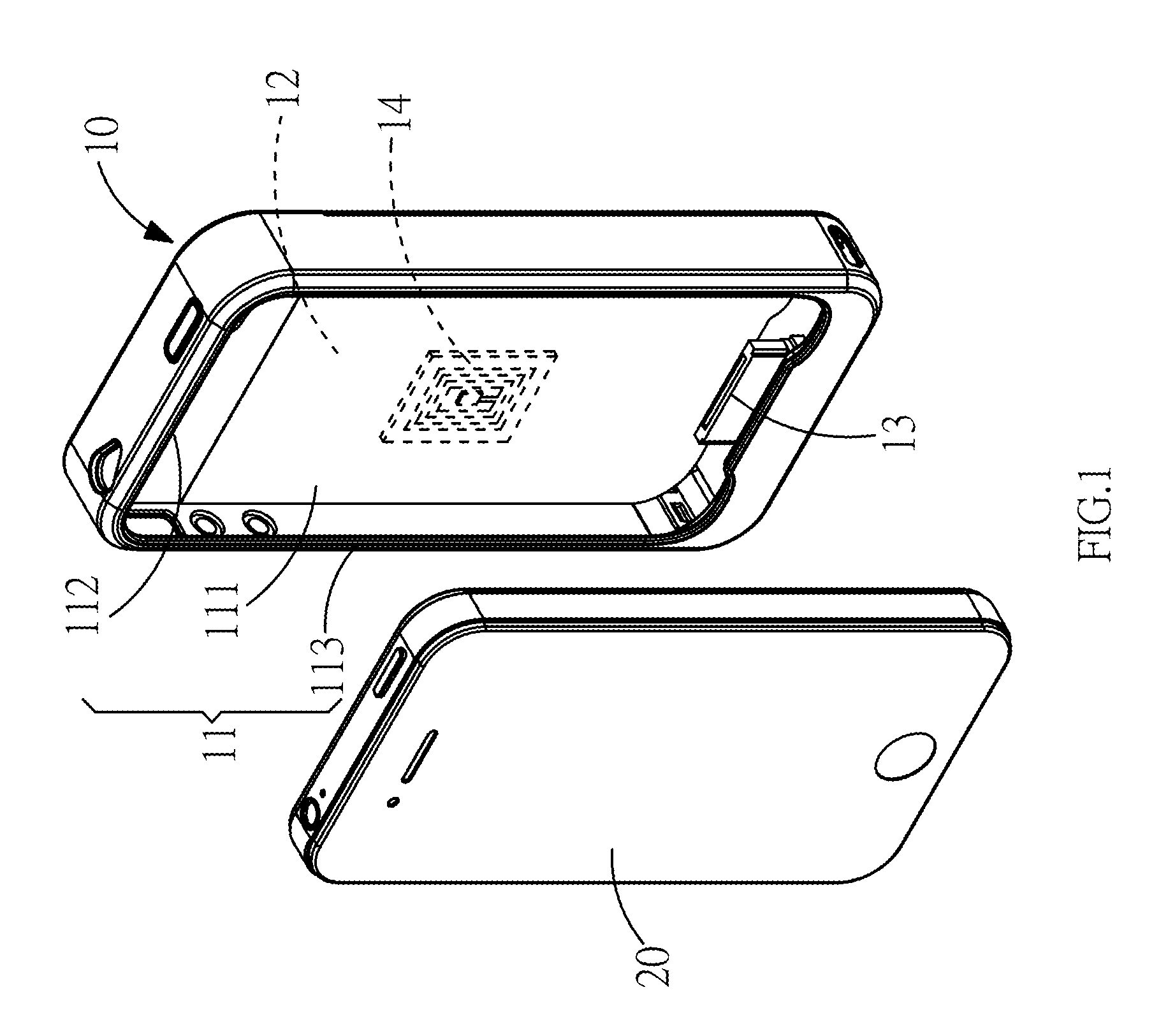
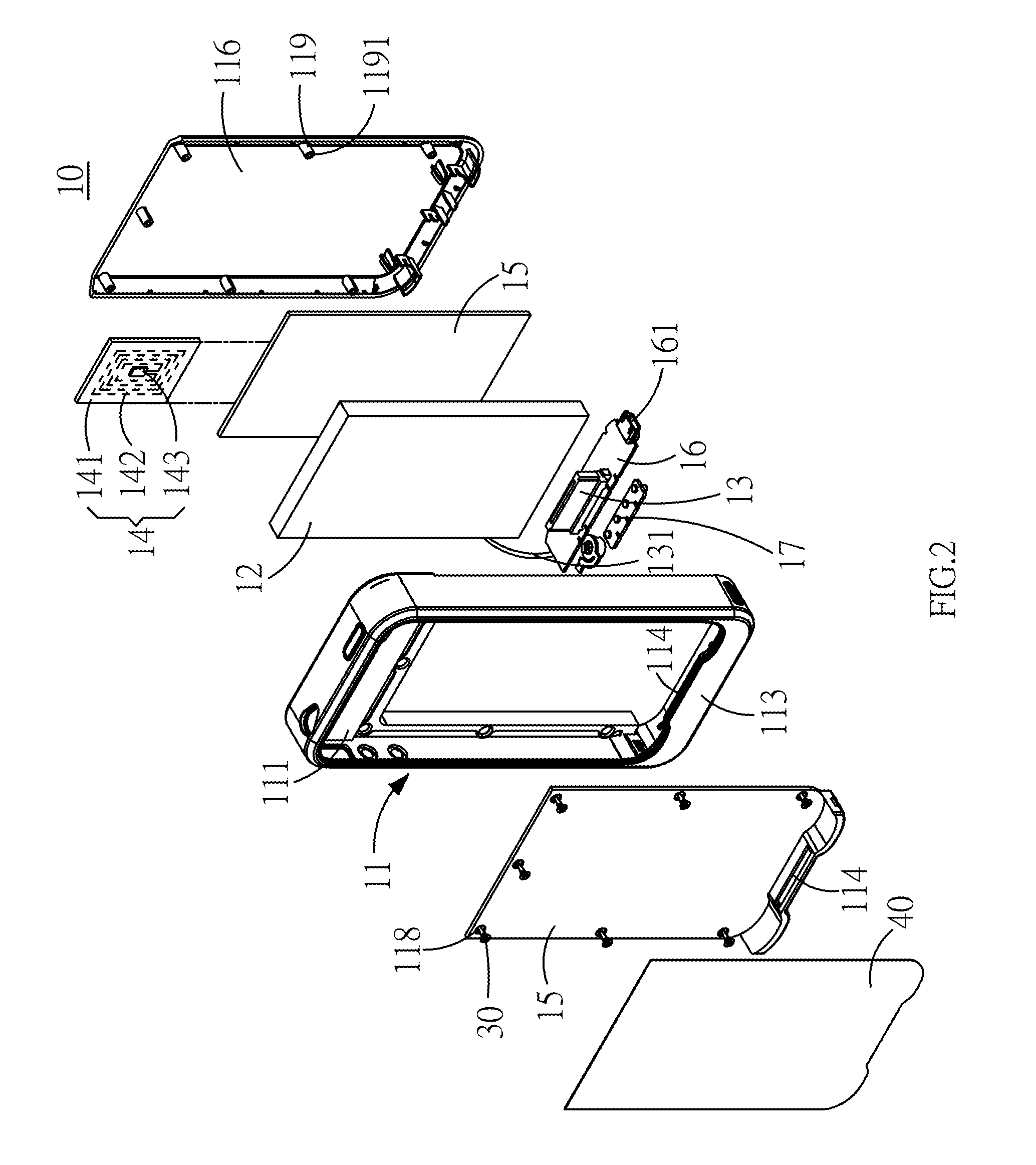
Protective cover of mobile electronic product
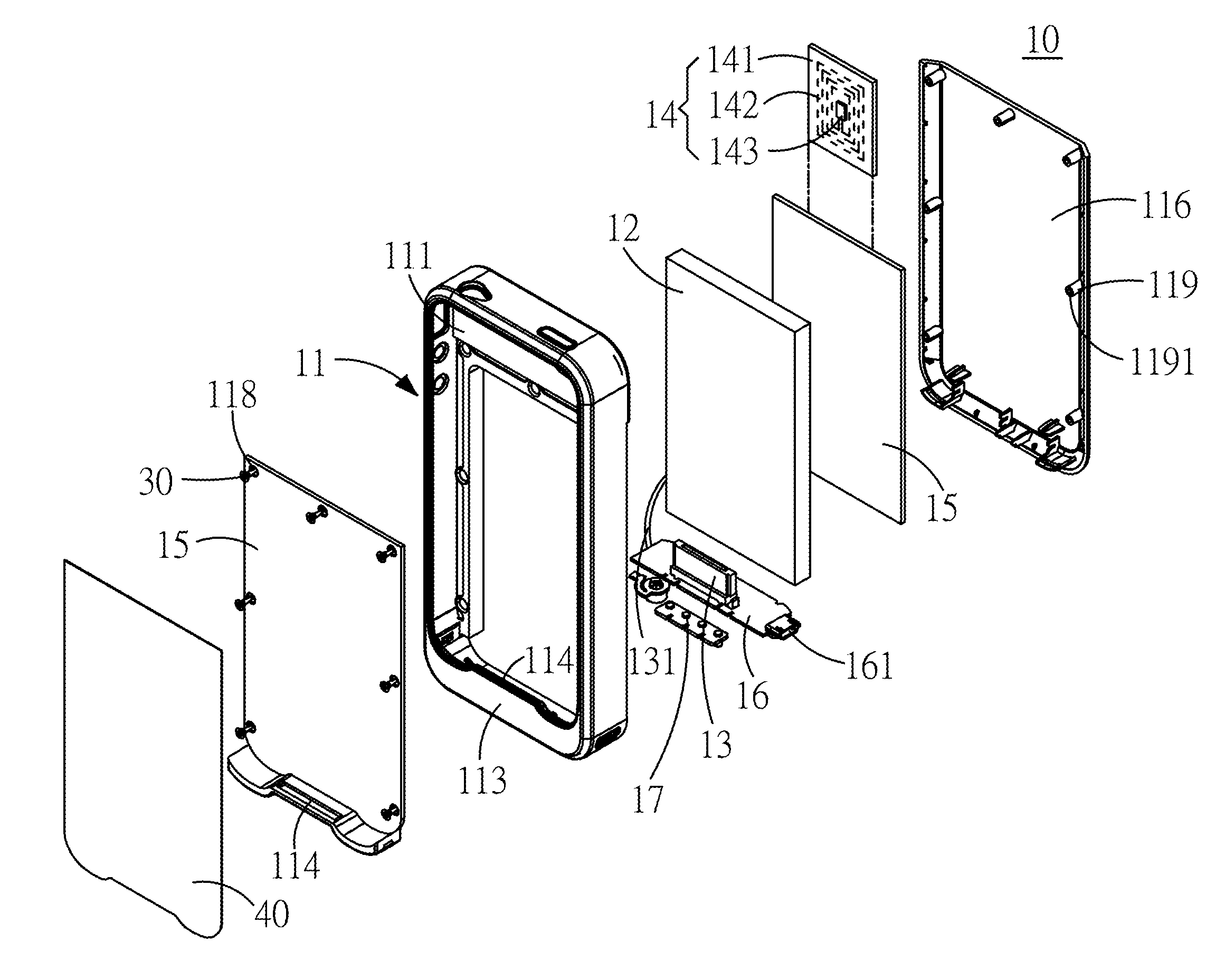
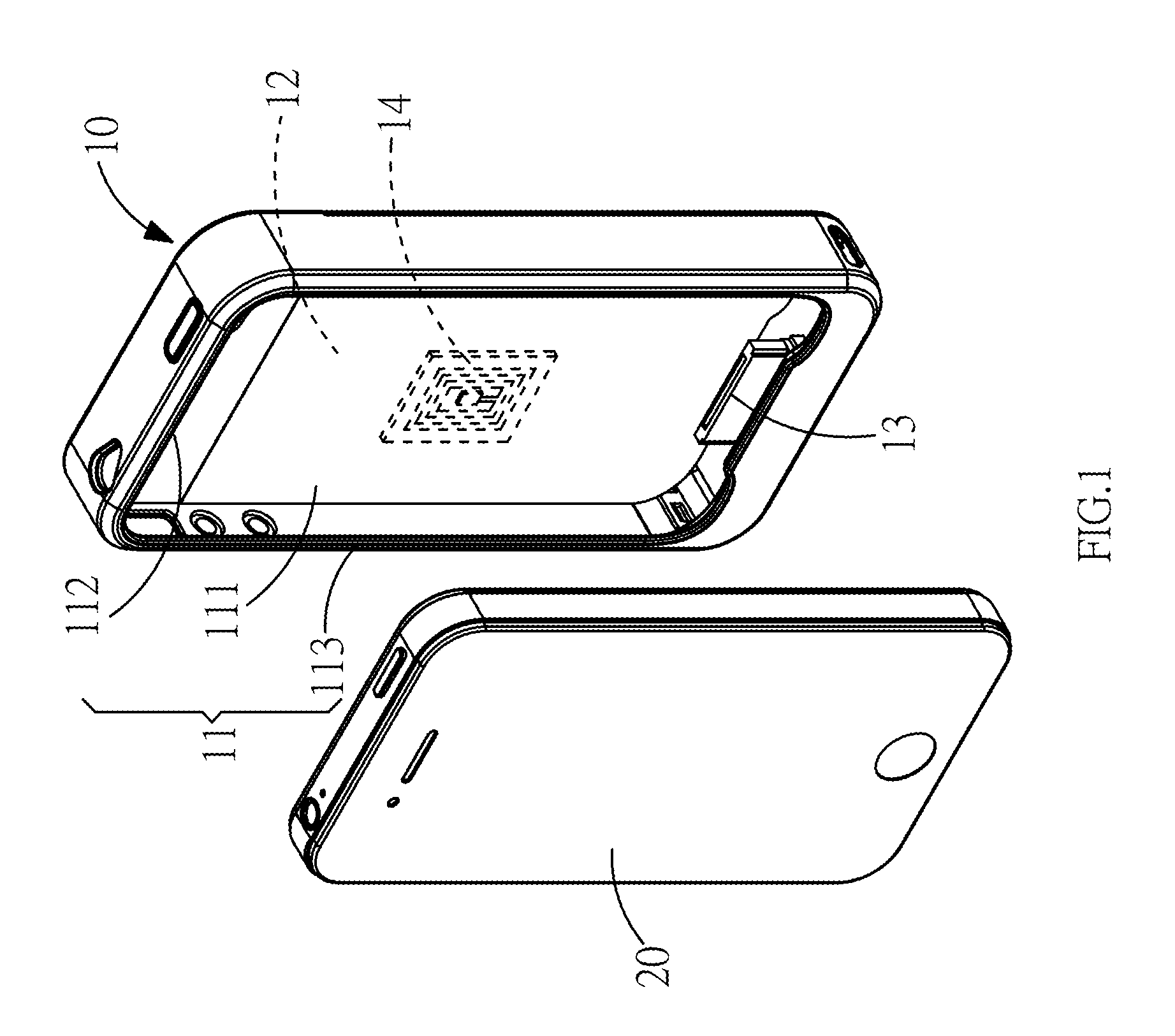
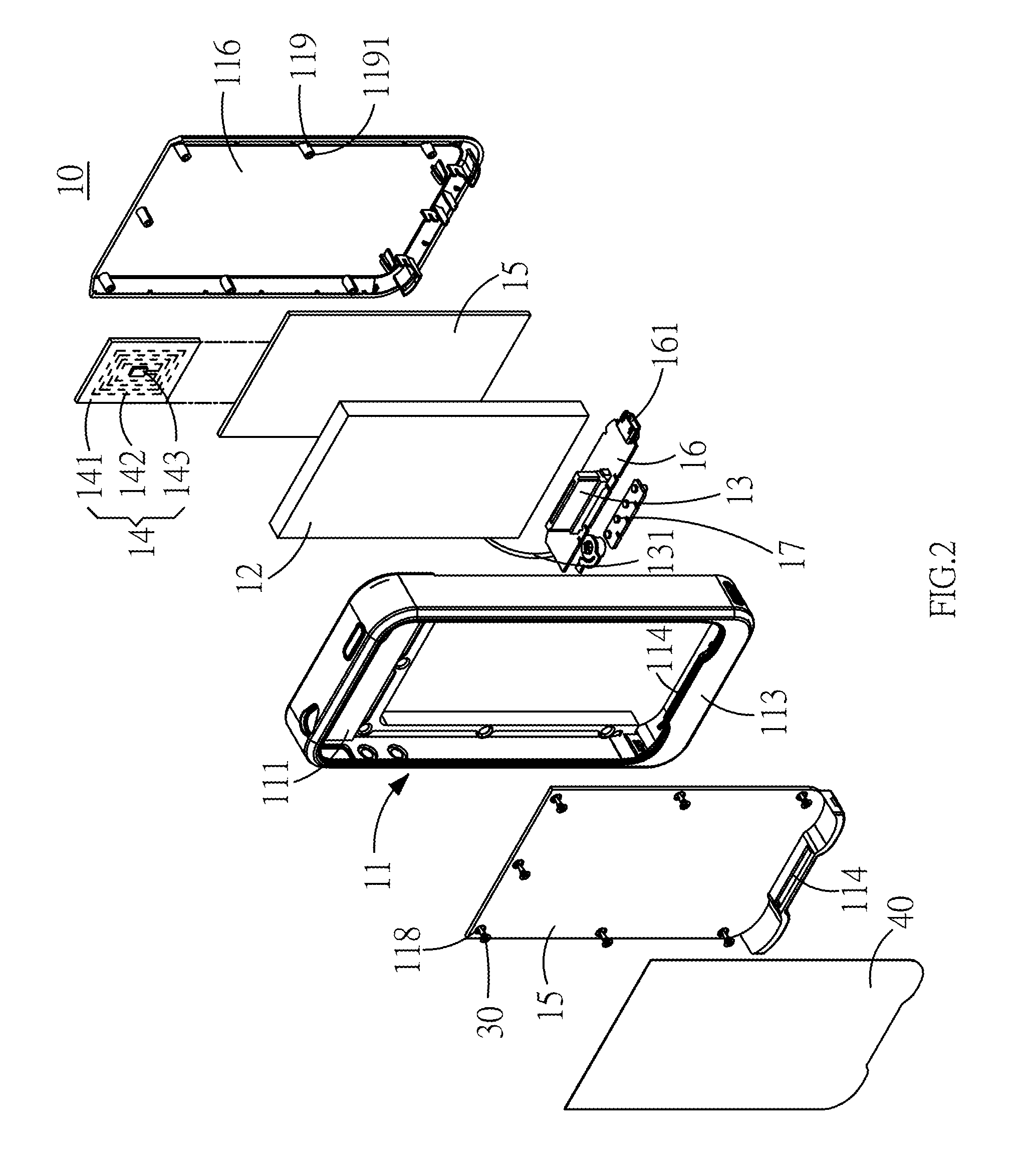
InactiveUS20130206844A1Overcome difficultiesPower managementDigital data processing detailsElectrical batteryElectric power system
A protective cover of a mobile electronic product capable of adding a backup battery to the exterior of the mobile electronic product, and the mobile electronic product is connected to the backup battery. In the protective cover of the mobile electronic product, a RFID module is installed for applying the mobile electronic product in a non-contact access identification device or a secured transaction device. The backup battery can supply electric power to the mobile electronic product to overcome the difficulty of accessing backup power.
Owner:TENNRICH INT
Protective cover of mobile electronic product
InactiveUS8646698B2Overcome difficultiesPower managementDigital data processing detailsElectrical batteryStandby power
A protective cover of a mobile electronic product capable of adding a backup battery to the exterior of the mobile electronic product, and the mobile electronic product is connected to the backup battery. In the protective cover of the mobile electronic product, a RFID module is installed for applying the mobile electronic product in a non-contact access identification device or a secured transaction device. The backup battery can supply electric power to the mobile electronic product to overcome the difficulty of accessing backup power.
Owner:TENNRICH INT
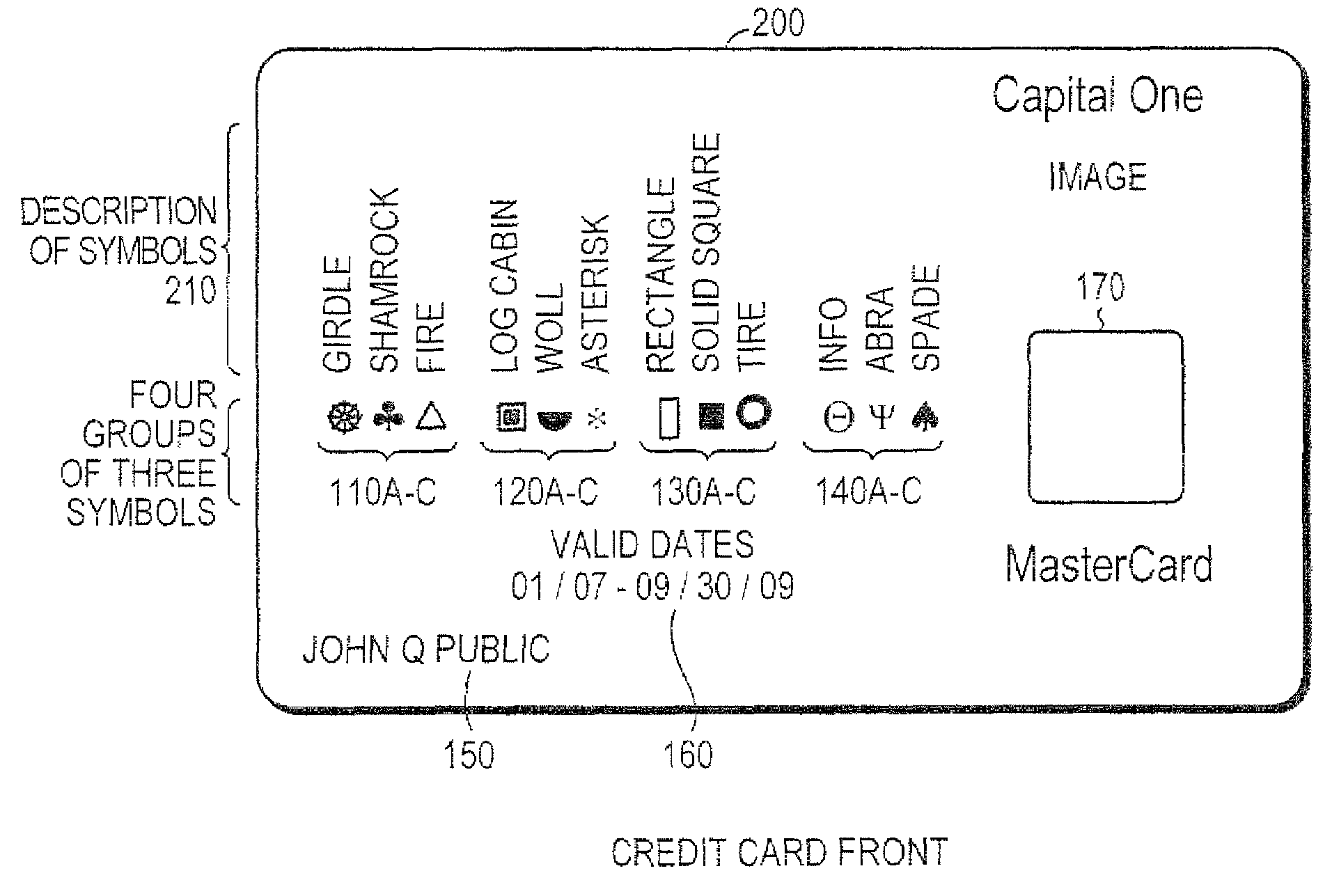
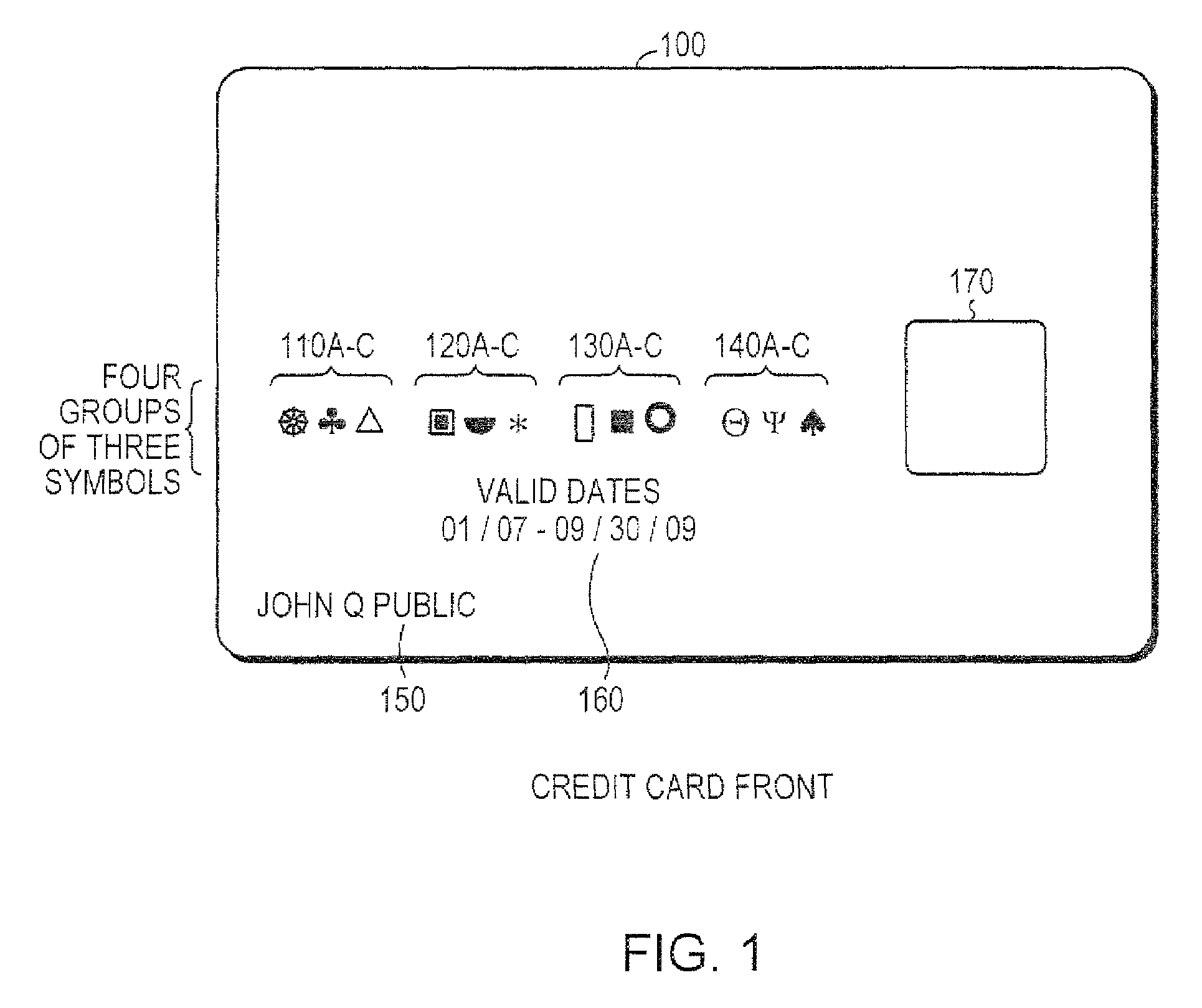
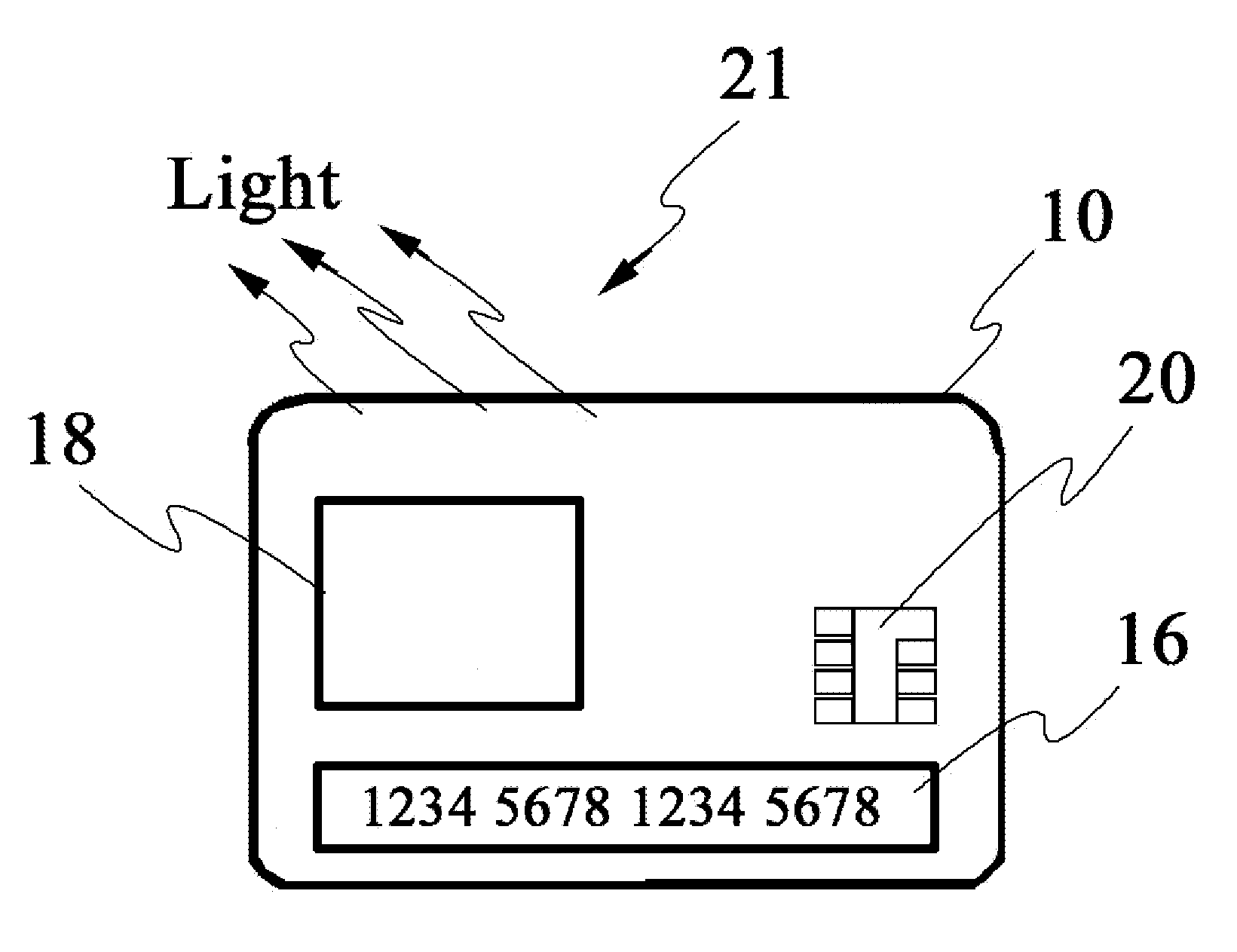
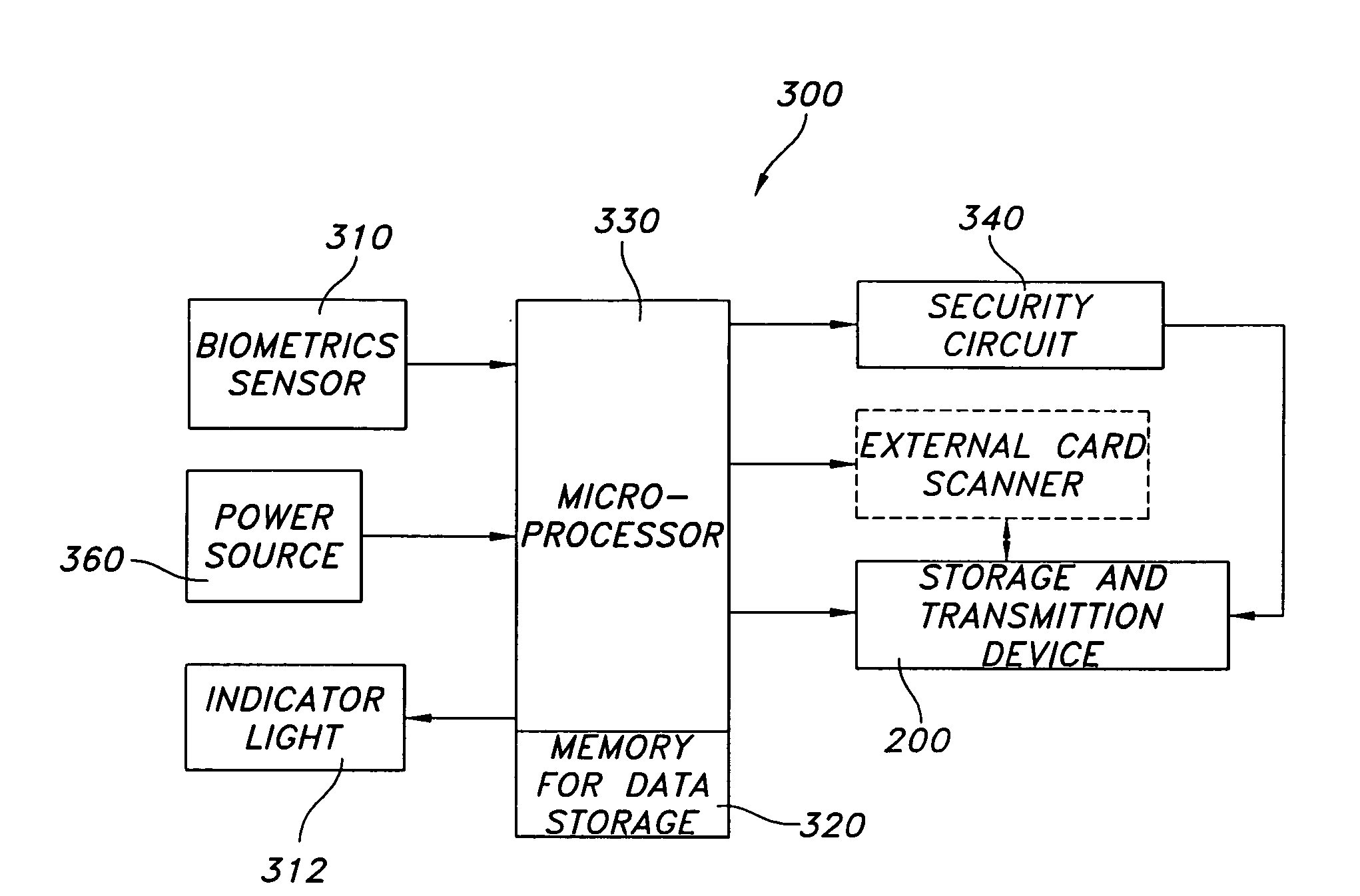
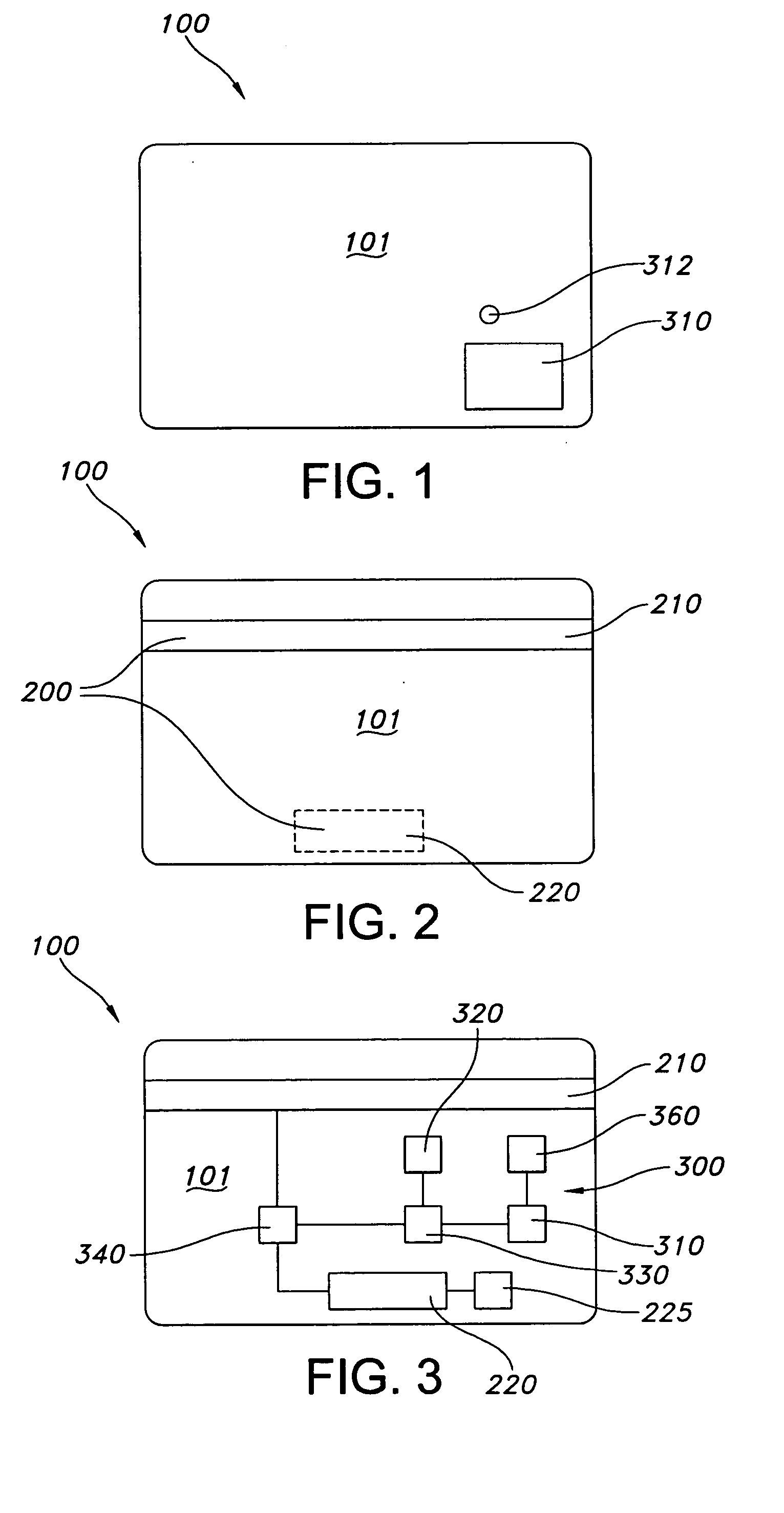
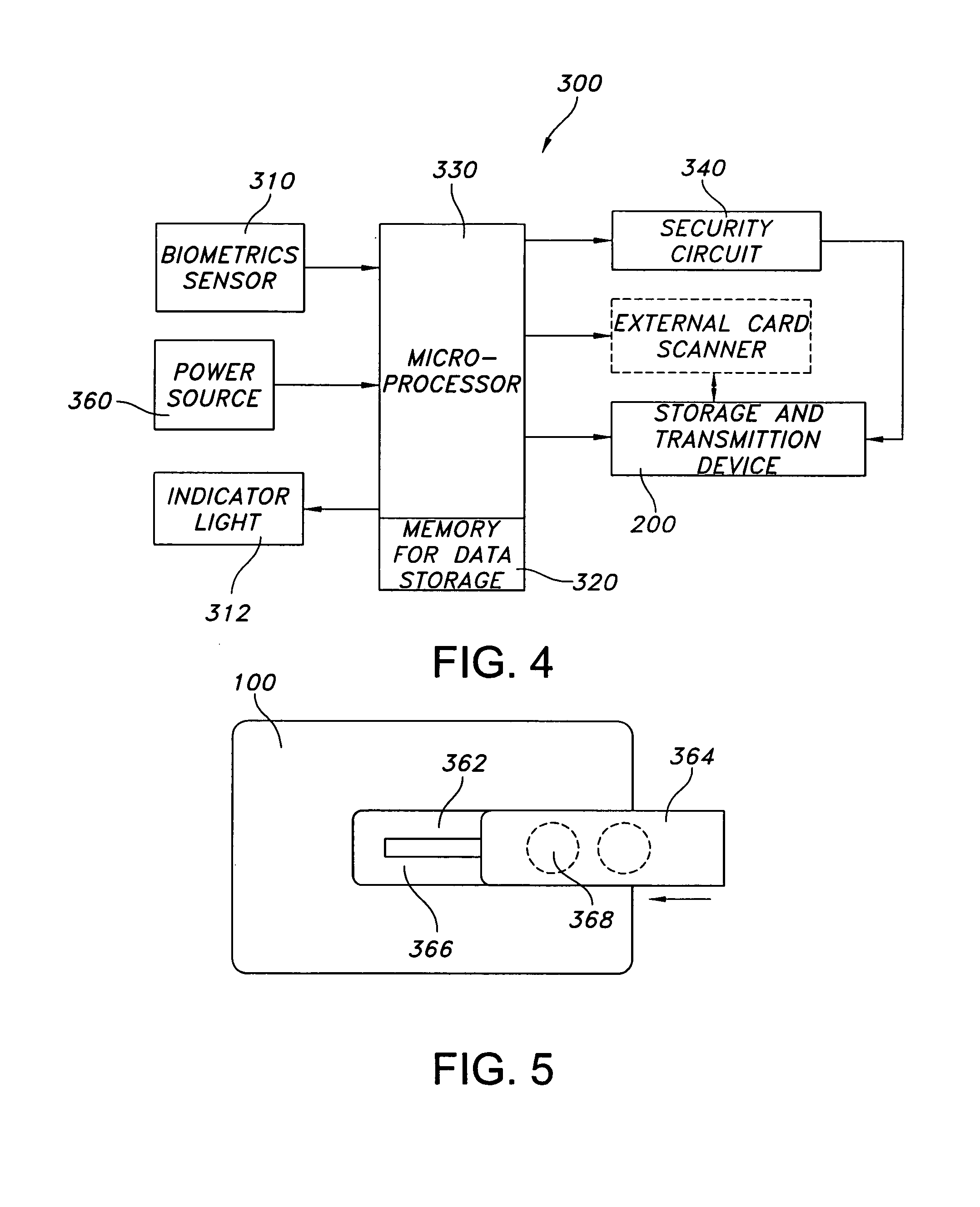
Biometrics-secured transaction card
InactiveUS20080120509A1Avoid spreadingAcutation objectsUser identity/authority verificationBiometric dataSecured transaction
Owner:THE PROCTER & GAMBLE COMPANY
System and method for secured transactions using mobile devices
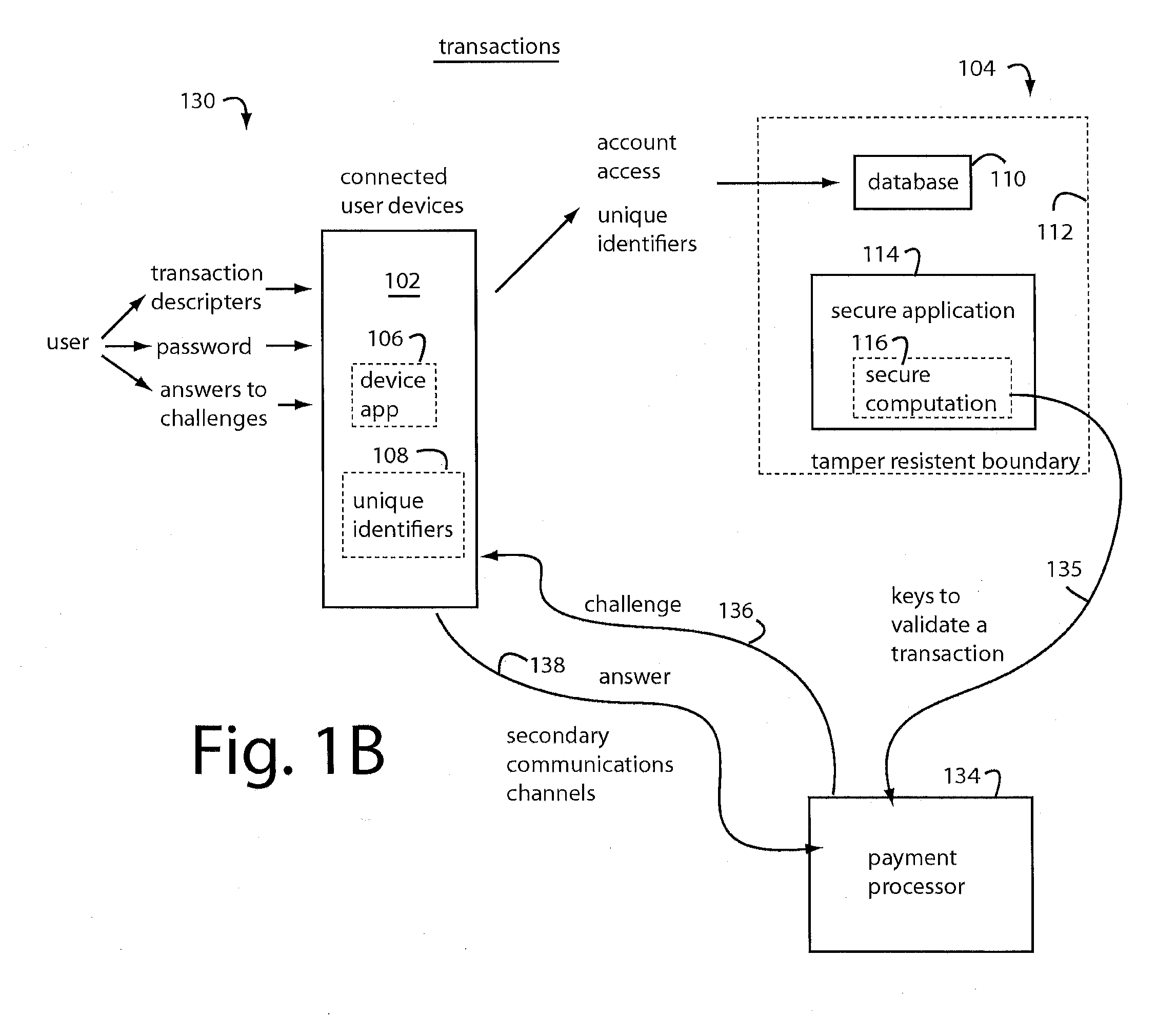
A secure payment system provisions a payment transaction proxy with virtual EMV-type chipcards on secure backend servers. Users authorize the proxy in each transaction to make payments in the Cloud for them. The proxy carries out the job without exposing the cryptographic keys to risk. User, message, and / or device authentication in multifactor configurations are erected in realtime to validate each user's intent to permit the proxy to sign for a particular transaction on the user's behalf. Users are led through a series of steps by the proxy to validate their authenticity and intent, sometimes incrementally involving additional user devices and communications channels that were pre-registered. Authentication risk can be scored by the proxy, and high risk transactions that are identified are tasked by further incrementally linking in more user devices, communications channels, and user challenges to increase the number of security factors required to authenticate.
Owner:CRYPTOMATHIC LTD
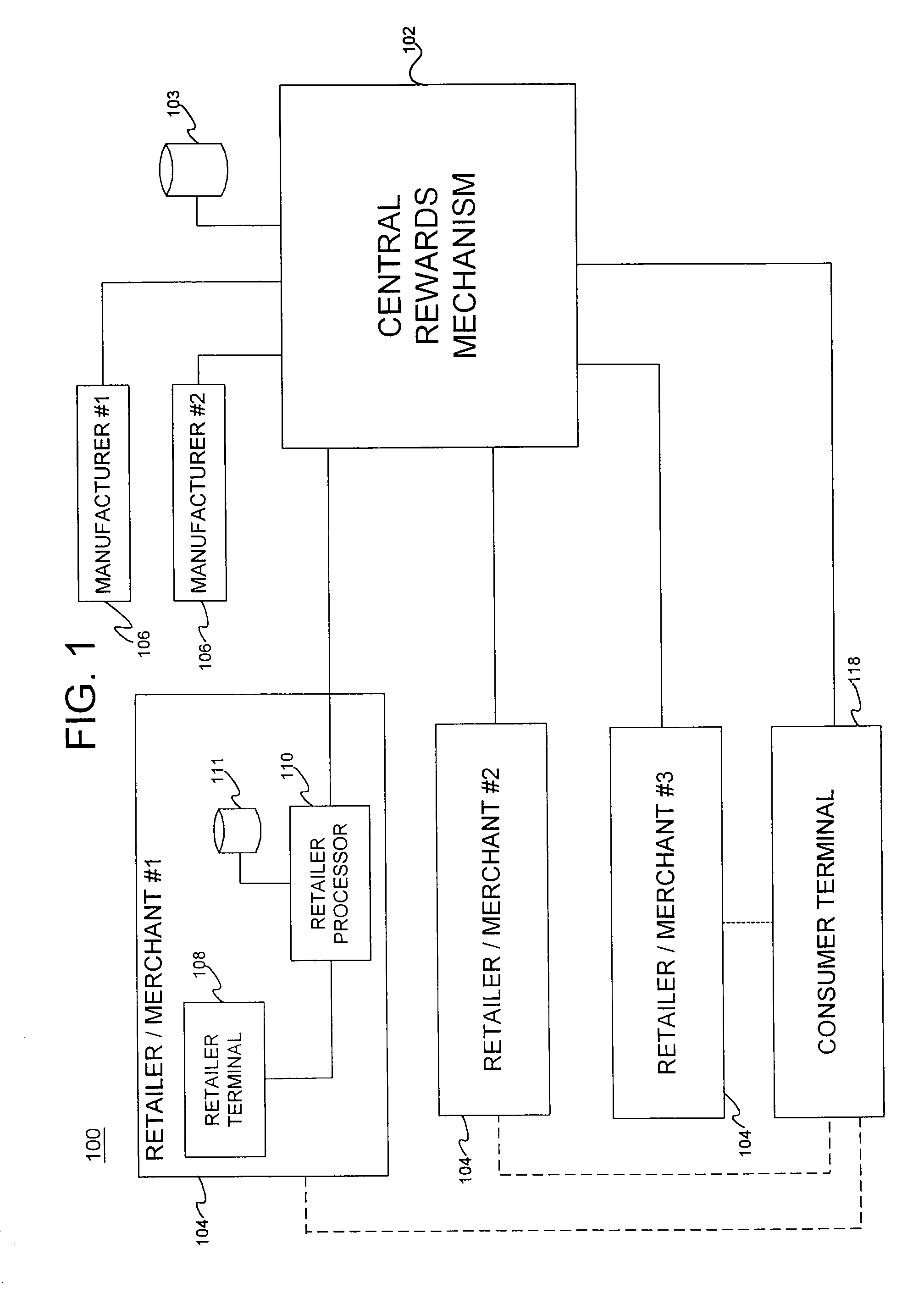
Bank quick credit granting system and method
InactiveCN103150672AReduce the hassle of multiple submissionsPromote rapid developmentFinancePaymentService development
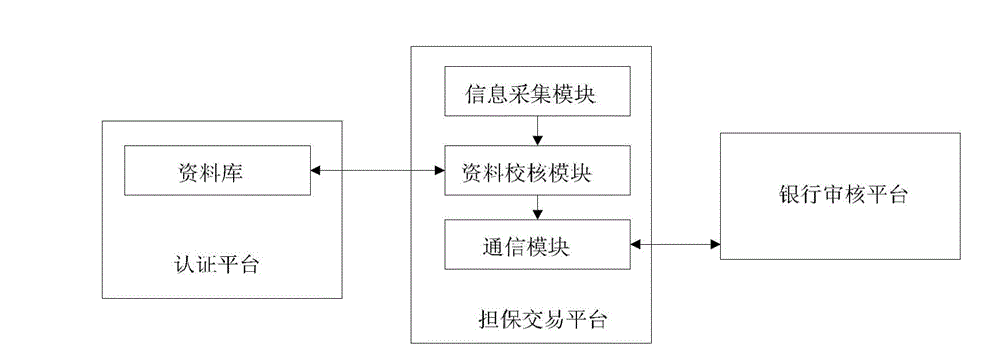
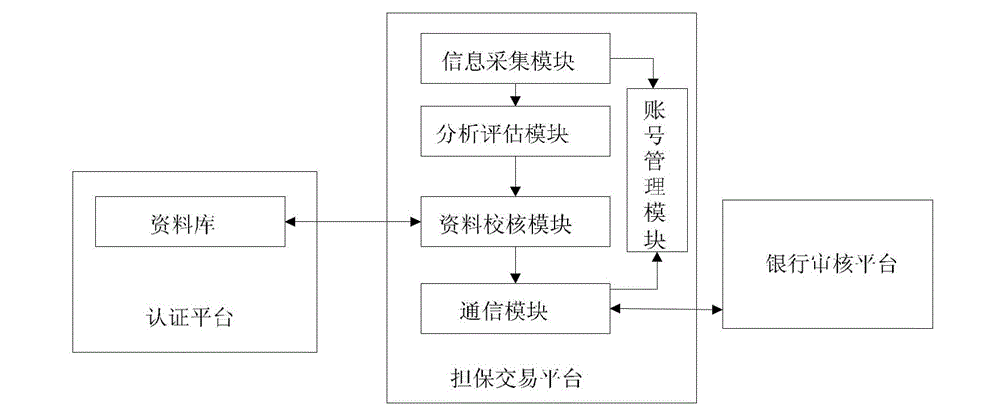
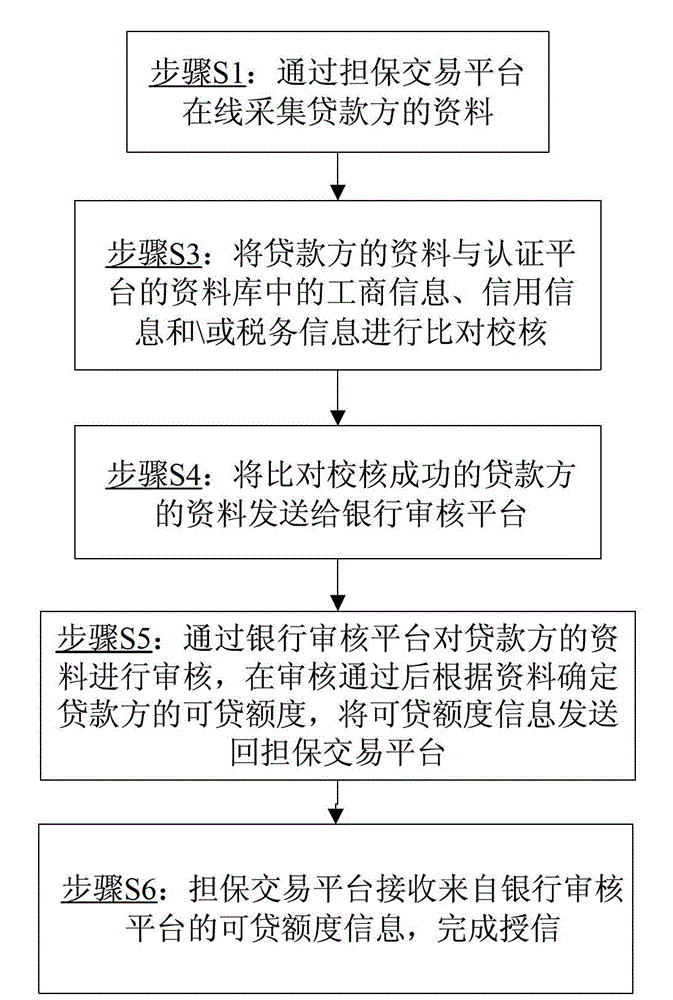
The invention discloses a bank quick credit granting system and a bank quick credit granting method. The system comprises a secured transaction platform, a bank auditing platform and a certification platform, wherein the secured transaction platform comprises an information acquisition module, a data checking module, a communication module; the information acquisition module is used for acquiring data of a credit side on line; the data checking module is used for comparing and checking the data of the credit side and industrial and commercial information, credit information and / or taxation information in a database of the certification platform; and the communication module is used for transmitting the successfully compared and checked data to the bank auditing platform and receiving loanable limit from the bank auditing platform. The bank auditing platform is used for auditing the data of the credit side, determining the loanable limit of the credit side according to the data after the auditing is passed and transmitting to the communication module. The certification platform comprises the database in which the industrial and commercial information, the credit information and / or the taxation information are stored. According to the system and the method, quick petty loan credit granting can be realized, large-area and low-cost payment service development is facilitated, and the risk can be reduced.
Owner:长沙钢为网络科技有限公司
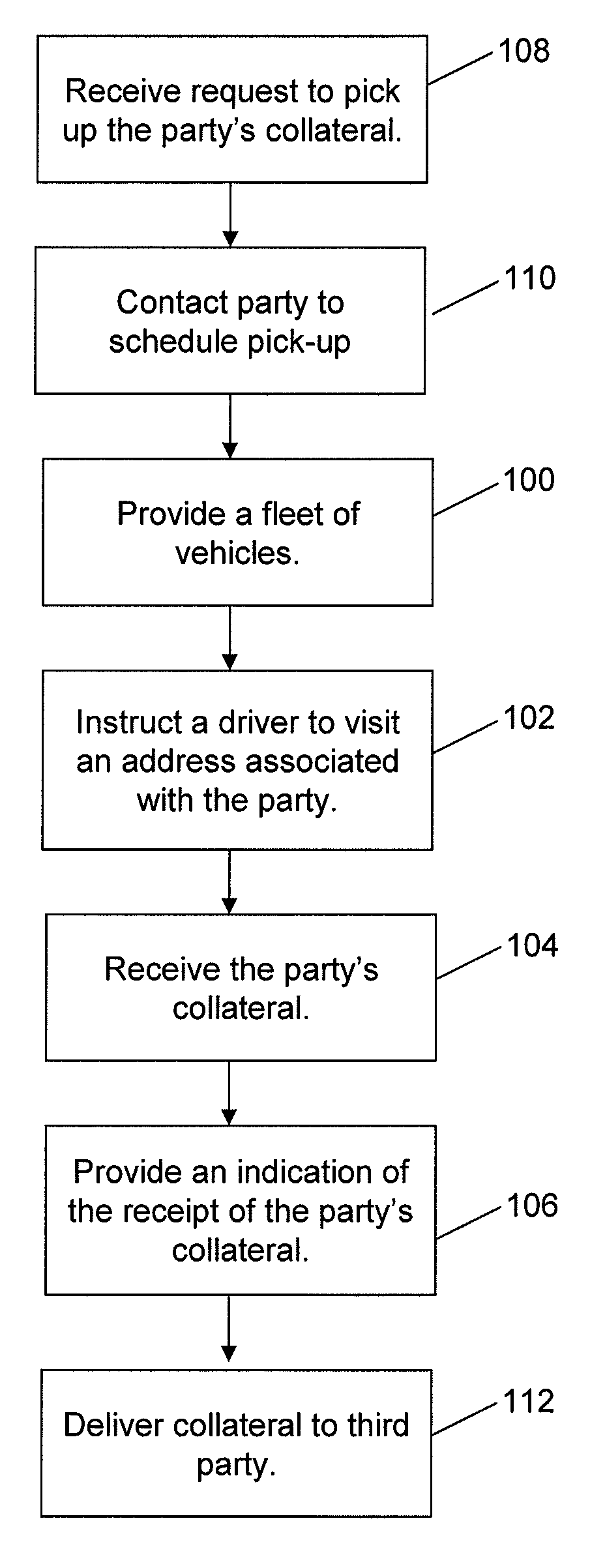
Collateral pick-up and delivery for secured transactions
ActiveUS20100293089A1Easy to optimizeConvenient transactionFinanceBuying/selling/leasing transactionsThird partyCommon carrier
Systems and methods for facilitating secured loan transactions are provided. Drivers of a fleet of parcel delivery vehicles associated with a particular common carrier are used to pick up collateral from a borrower to secure a loan. A driver visits the borrower's address as part of executing parcel delivery transactions to pick up the collateral. The driver may verify the borrower's identity and the validity of the collateral when receiving the collateral. An indication of the receipt of the borrower's collateral is provided to a system accessible by a lending facilitator, such as via the driver's DIAD. The indication can be used by the peer-to-peer lending facilitator to determine a level of risk associated with entering into a loan transaction with the borrower and / or an interest rate for the loan. In some cases, the collateral is delivered to a third party escrow service.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
Secured transaction system
Owner:DAI XIA
System and Method for Securing Data Through a PDA Portal
InactiveUS20090089581A1Easy to purchaseFacilitate loyalty processFinanceUser identity/authority verificationWeb siteSecured transaction
Consumers may utilize computing devices to assist in the purchase and / or loyalty process, and in particular, the consumer may utilize a PDA to facilitate the purchase and / or loyalty process. During the purchase and / or loyalty process, the consumer may need to insure that any content downloaded or used in association with the PDA is secure in how it is collected, assembled, and delivered to the PDA device. This system and method secures the data from its source to when it is actually viewed or used by the authorized user. The PDA may have direct access to an Internet web site portal that offers secure personal content from a content provider, such as, for example, an on-line banking or financial institution. Using the web site portal, the content provider may offer personal or confidential data, such as financial information, to PDA users in a secure (e.g., encrypted) environment. The exemplary system and method may establish a PDA portal link to the web site for collecting specified information for a user and transmitting the information to the remote device. To receive the information, the PDA contacts the portal and establishes a connection, authenticates itself to the network and allows the user to complete secured transactions or transmissions over the network.
Owner:LIBERTY PEAK VENTURES LLC
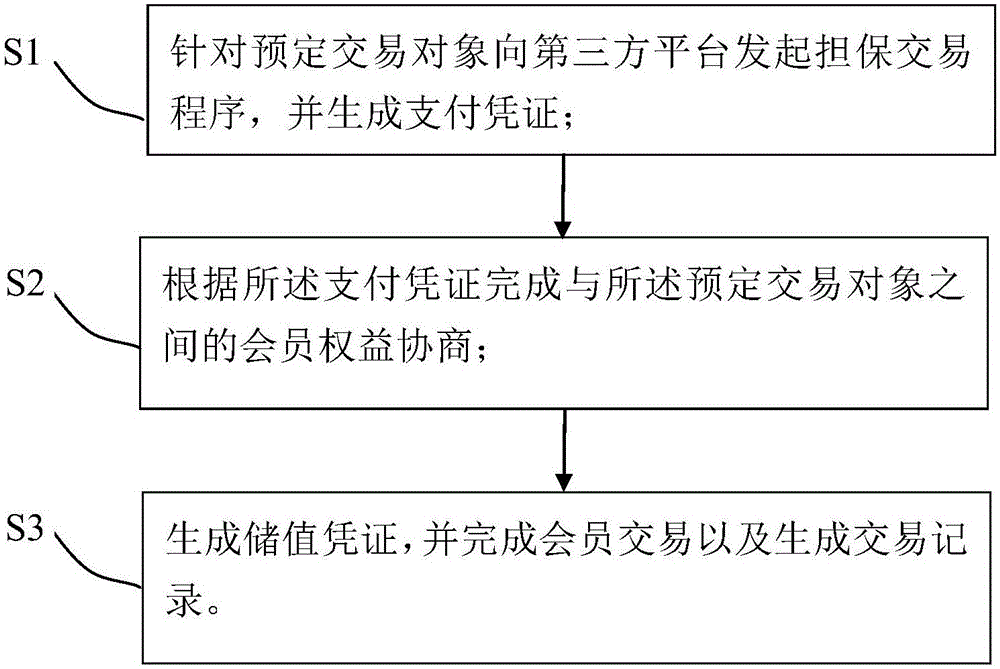
Decentralized stored-value voucher management method and system
InactiveCN106408279ASafety of tradementSecure Registration Verification ProcessDiscounts/incentivesElectronic credentialsThird partyPayment
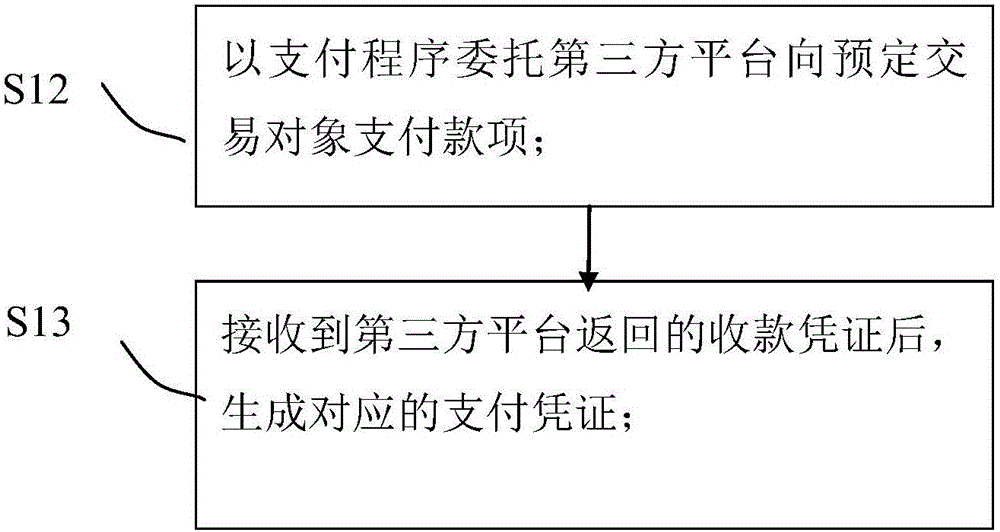
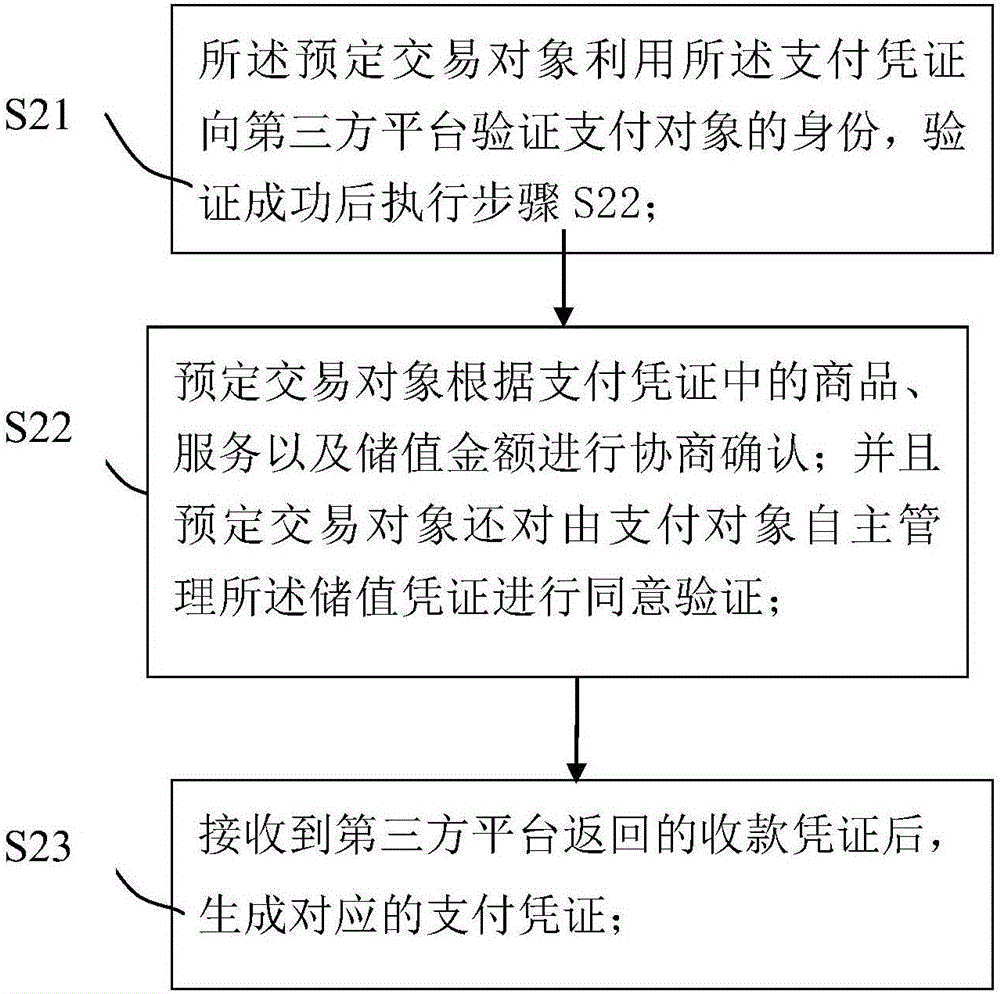
The invention provides a decentralized stored-value voucher management method and a decentralized stored-value voucher management system. The decentralized stored-value voucher management method is applied to user end equipment, and comprises the steps of: S1, initiating a secured transaction procedure to a third party platform for a predetermined transaction object, and generating a payment voucher; S2: completing a membership rights and interests negotiation between a merchant and the predetermined transaction object according to the payment voucher; S3, and generating a stored-value voucher, and completing membership transaction and generating a transaction record. The decentralized stored-value voucher management method and the decentralized stored-value voucher management system realize the decentralized management of the stored-value voucher, and realize the transfer purpose that a user can deal with the rights and interests corresponding to the stored-value voucher independently.
Owner:詹博凯
Method to operate a contactless mobile device as a low cost secured point-of-sale
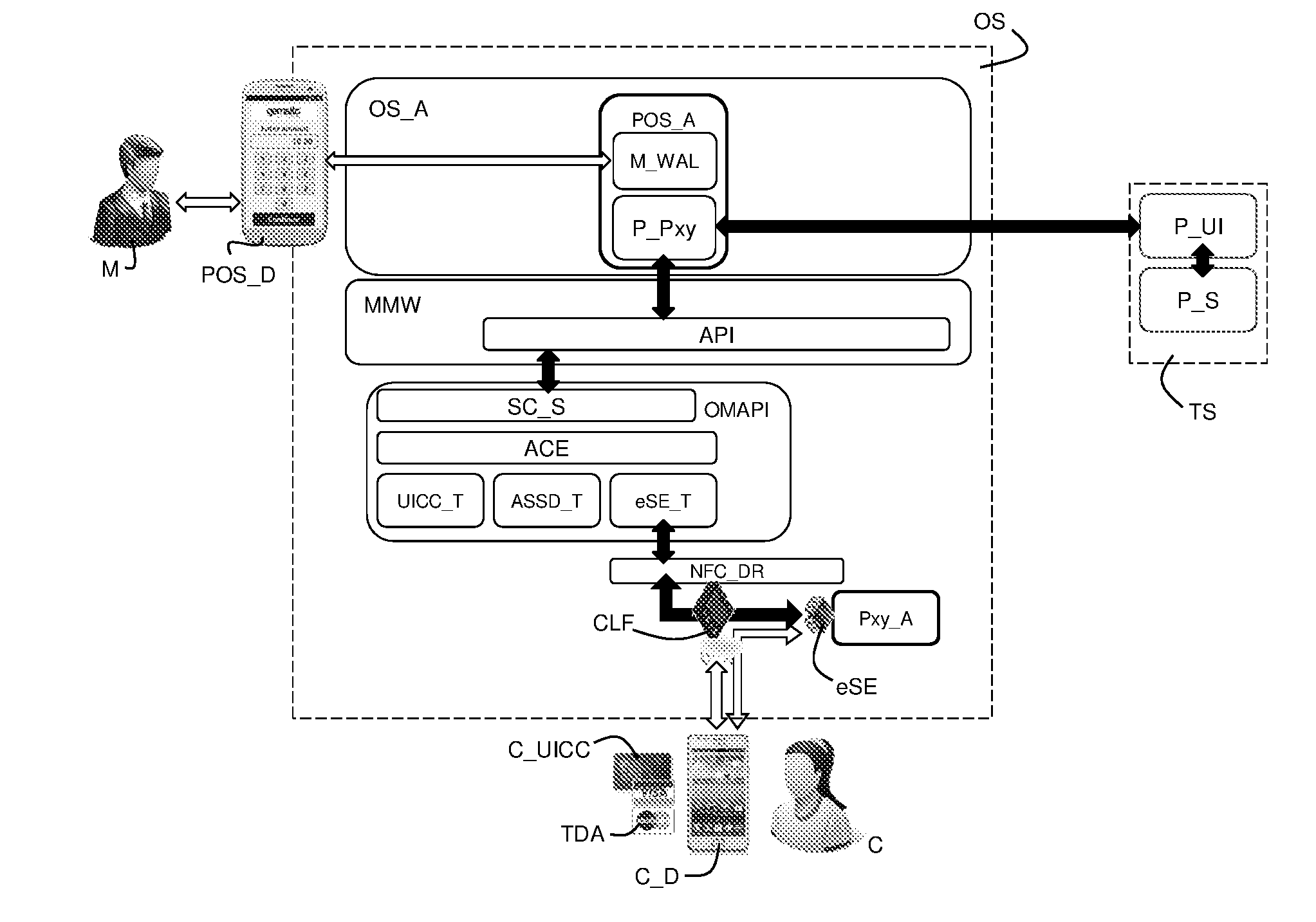
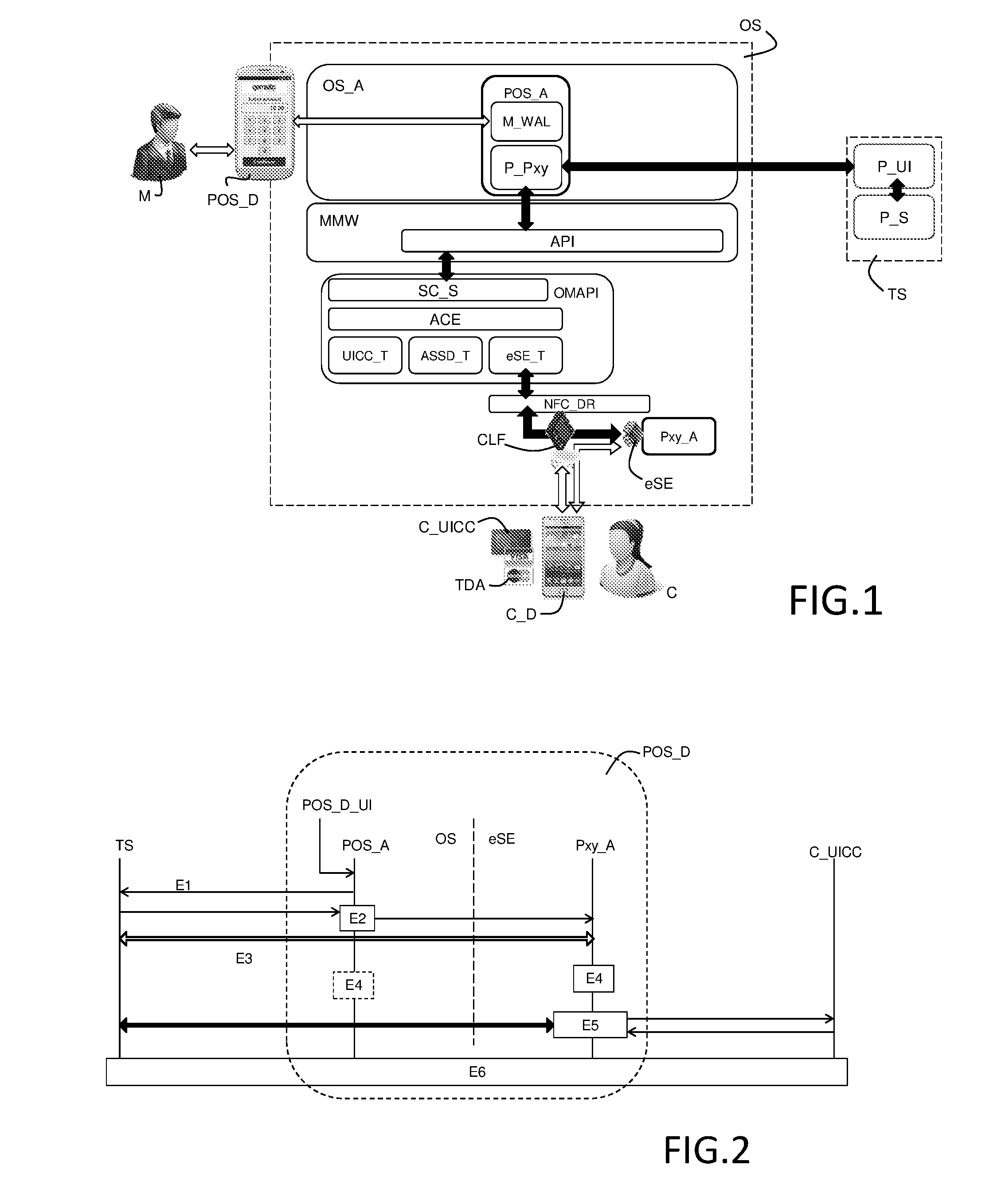
The present invention relates to a method to operate a contactless mobile device as a low cost secured point-of-sale, hereinafter POS device, said POS device having a non-secured operating system, a POS application installed in said non-secured operating system, an embedded secure element, a transaction proxy applet installed in said embedded secure element and a Contactless Front-End to contactless communicate with a customer mobile device having a secured transaction dedicated application.
Owner:GEMPLU
System and method for securing data through a PDA portal
Consumers may utilize computing devices to assist in the purchase and / or loyalty process, and in particular, the consumer may utilize a PDA to facilitate the purchase and / or loyalty process. During the purchase and / or loyalty process, the consumer may need to insure that any content downloaded or used in association with the PDA is secure in how it is collected, assembled, and delivered to the PDA device. This system and method secures the data from its source to when it is actually viewed or used by the authorized user. The PDA may have direct access to an Internet web site portal that offers secure personal content from a content provider, such as, for example, an on-line banking or financial institution. Using the web site portal, the content provider may offer personal or confidential data, such as financial information, to PDA users in a secure (e.g., encrypted) environment. The exemplary system and method may establish a PDA portal link to the web site for collecting specified information for a user and transmitting the information to the remote device. To receive the information, the PDA contacts the portal and establishes a connection, authenticates itself to the network and allows the user to complete secured transactions or transmissions over the network.
Owner:LIBERTY PEAK VENTURES LLC
Mobile devices for commerce over unsecured networks
Techniques for managing modules or applications installed in a mobile device are described. To provide authentic and secured transactions with another device, each of the installed applications is provisioned with a server through data communication capability in a mobile device. A provisioned application is associated with the personalized secure element in the mobile device and works with a set of keys that are generated in accordance with a set of keys from the personalized secure element. Further management of controlling an installed application is also described.
Owner:RFCYBER CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com