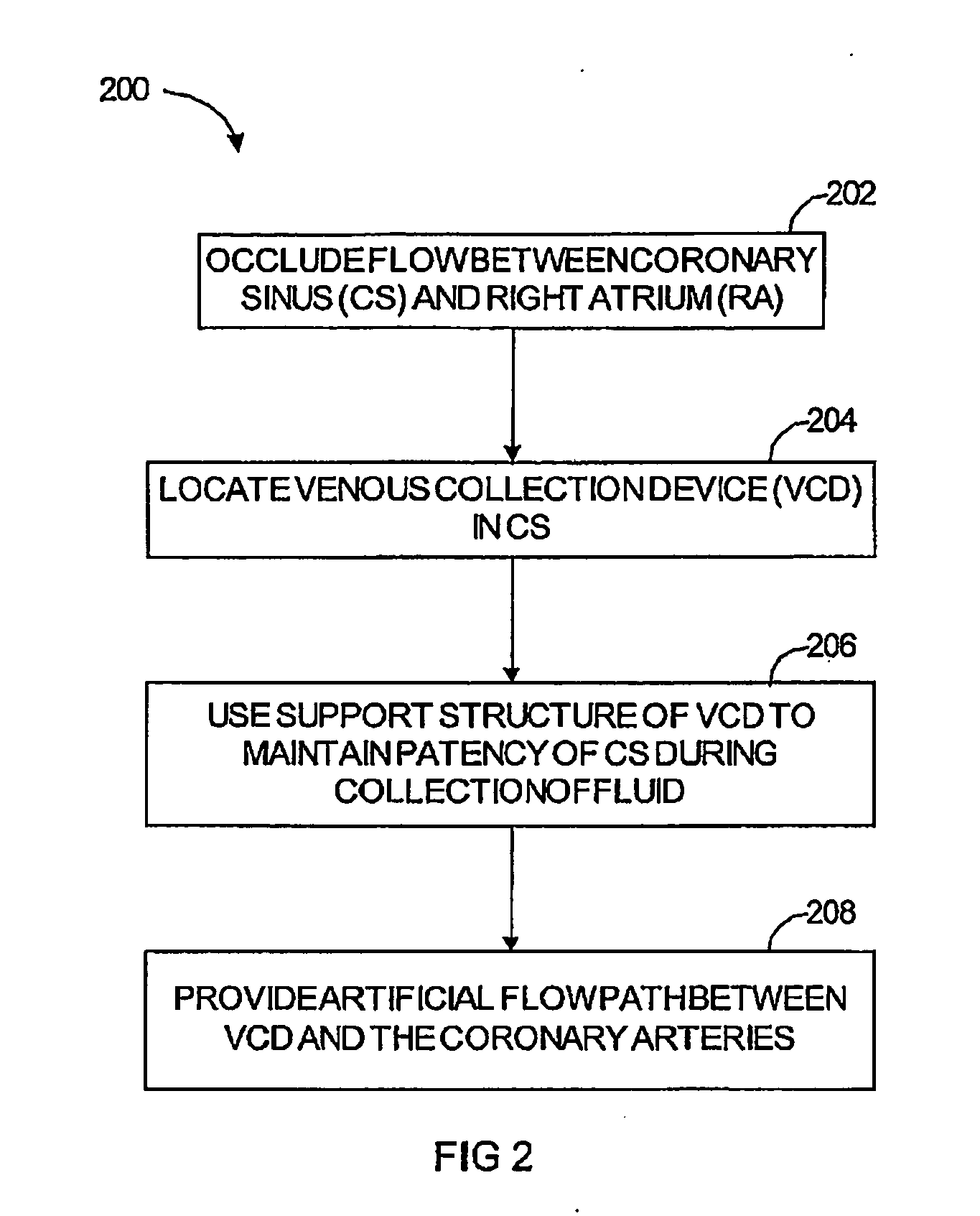
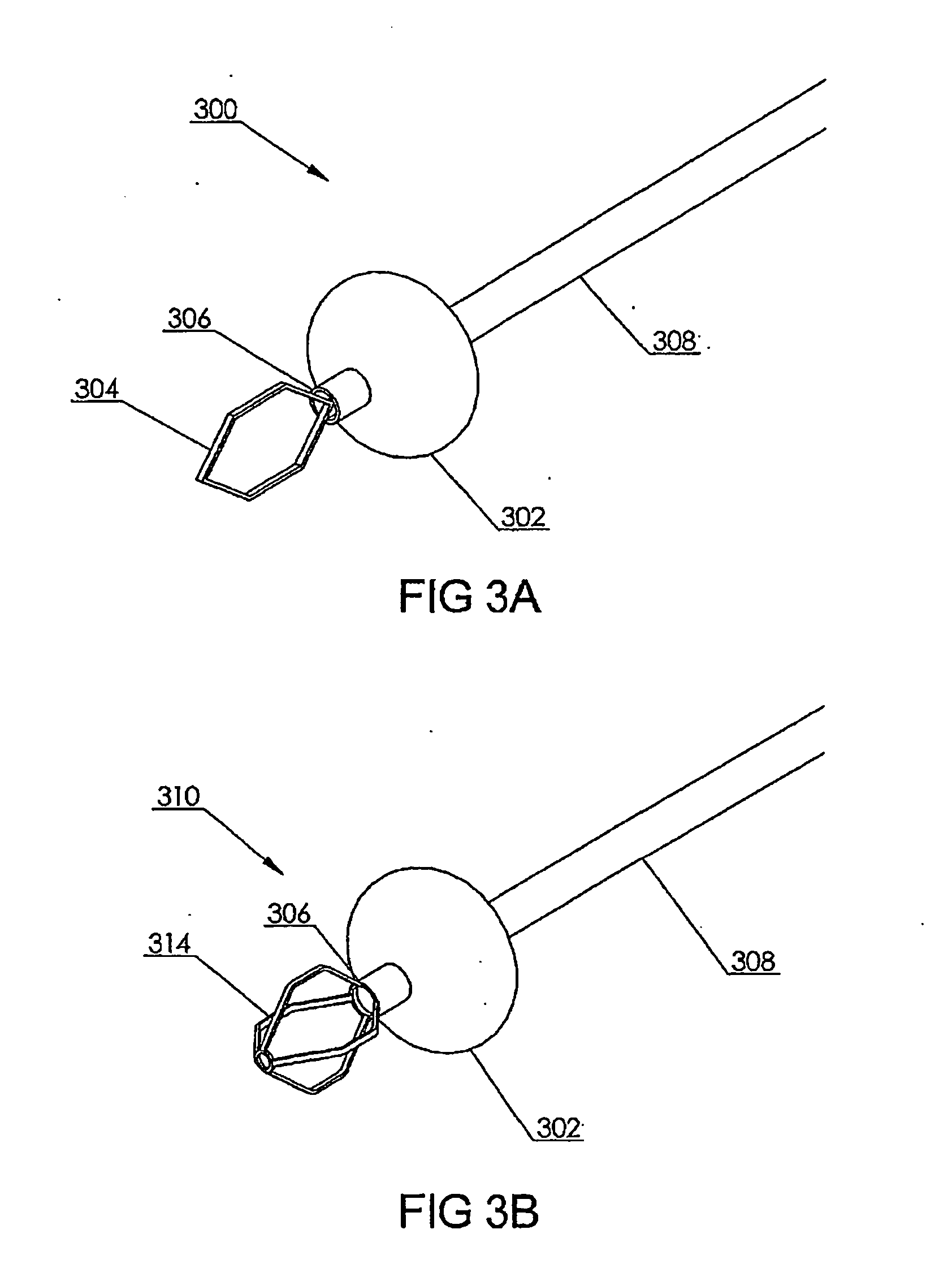
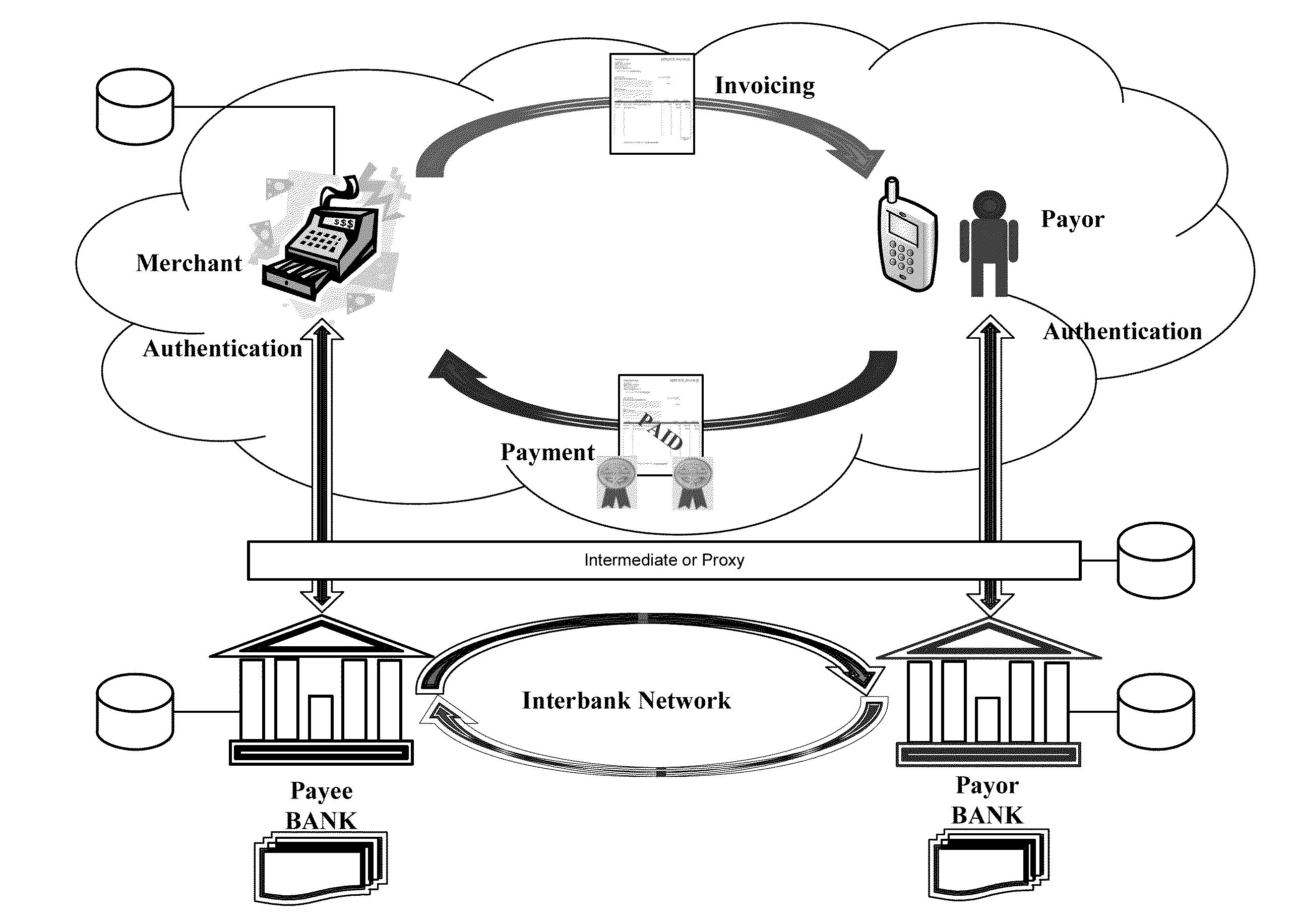
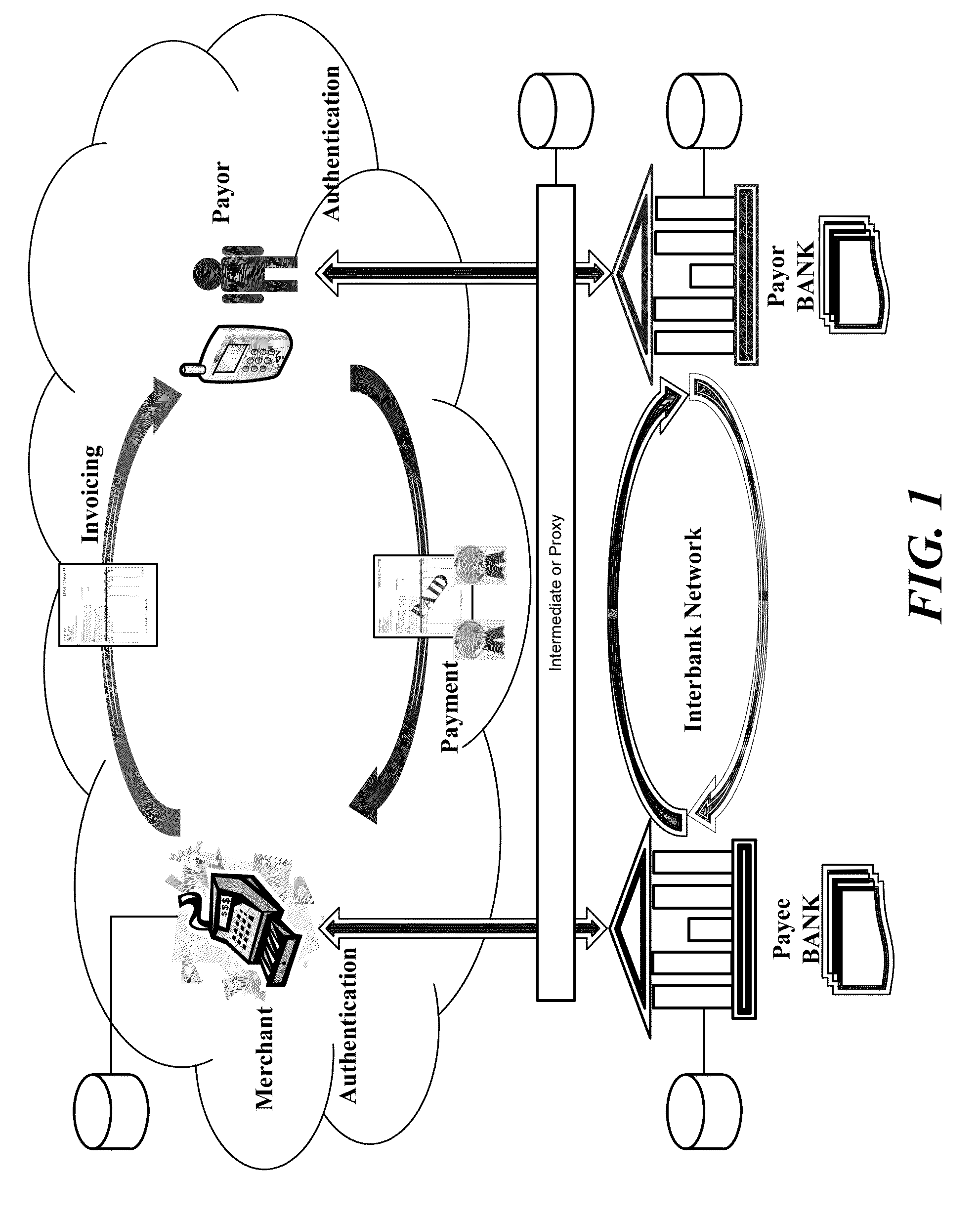
Patents
Literature
544results about How to "Opportunities decrease" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
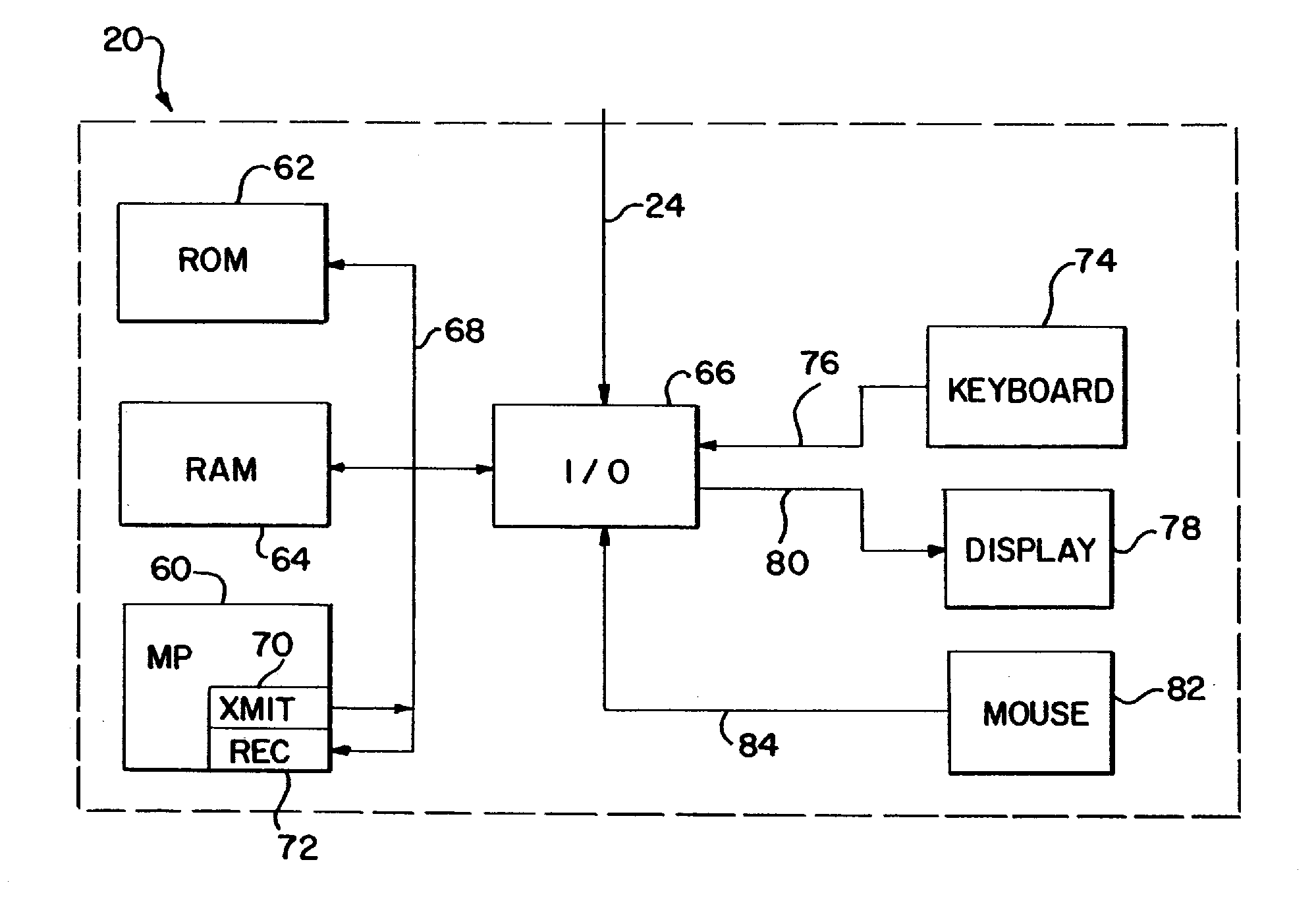
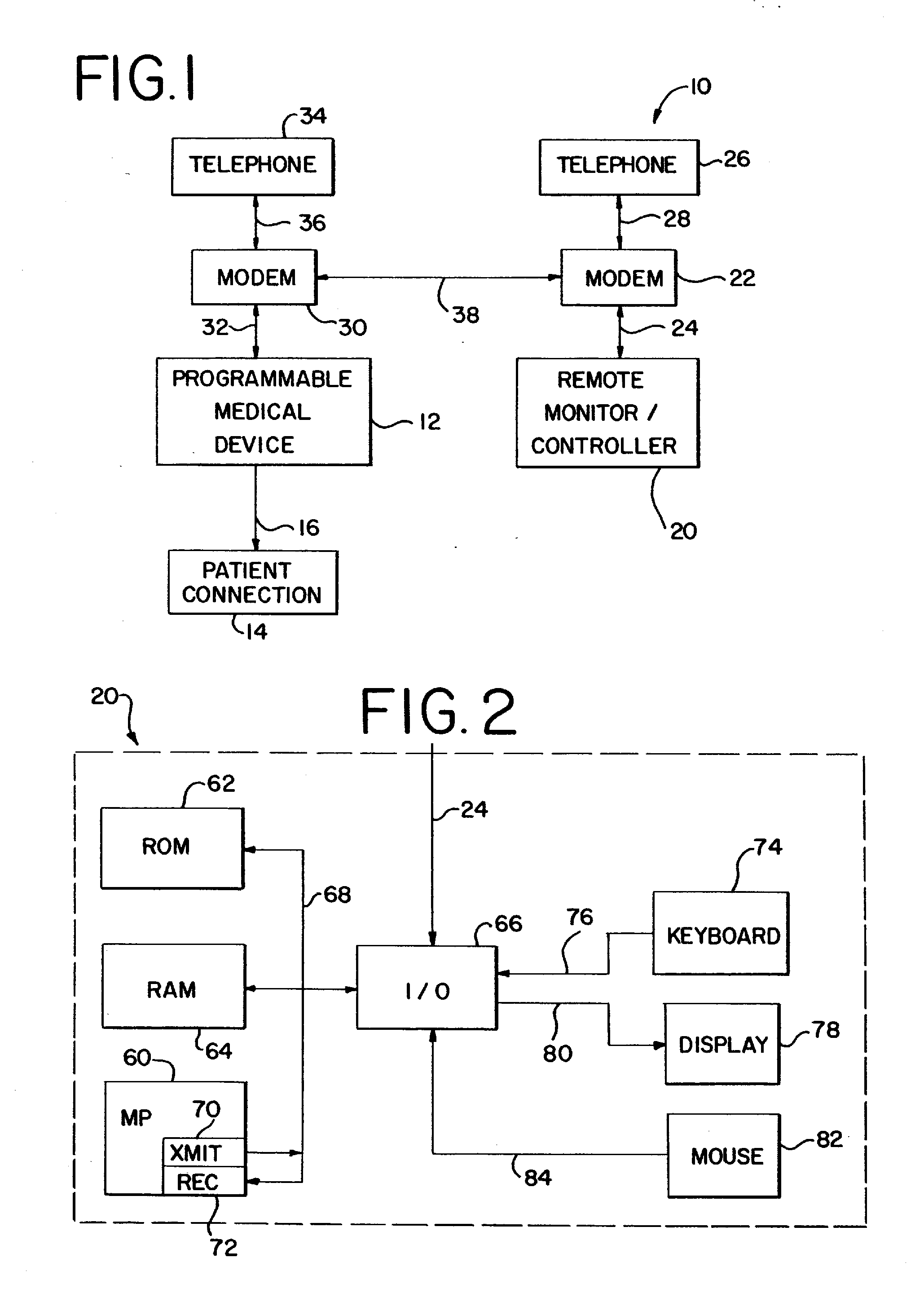
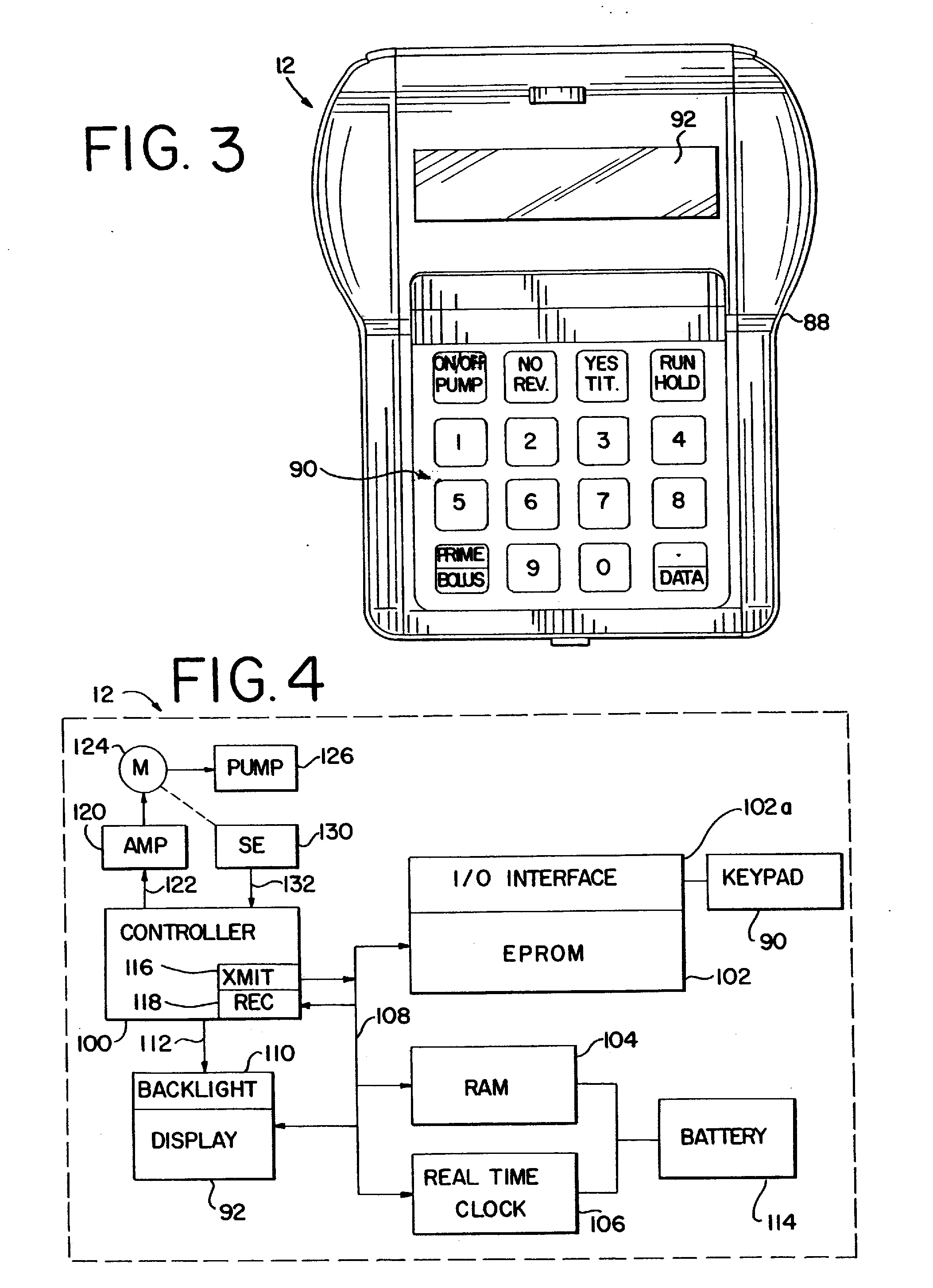
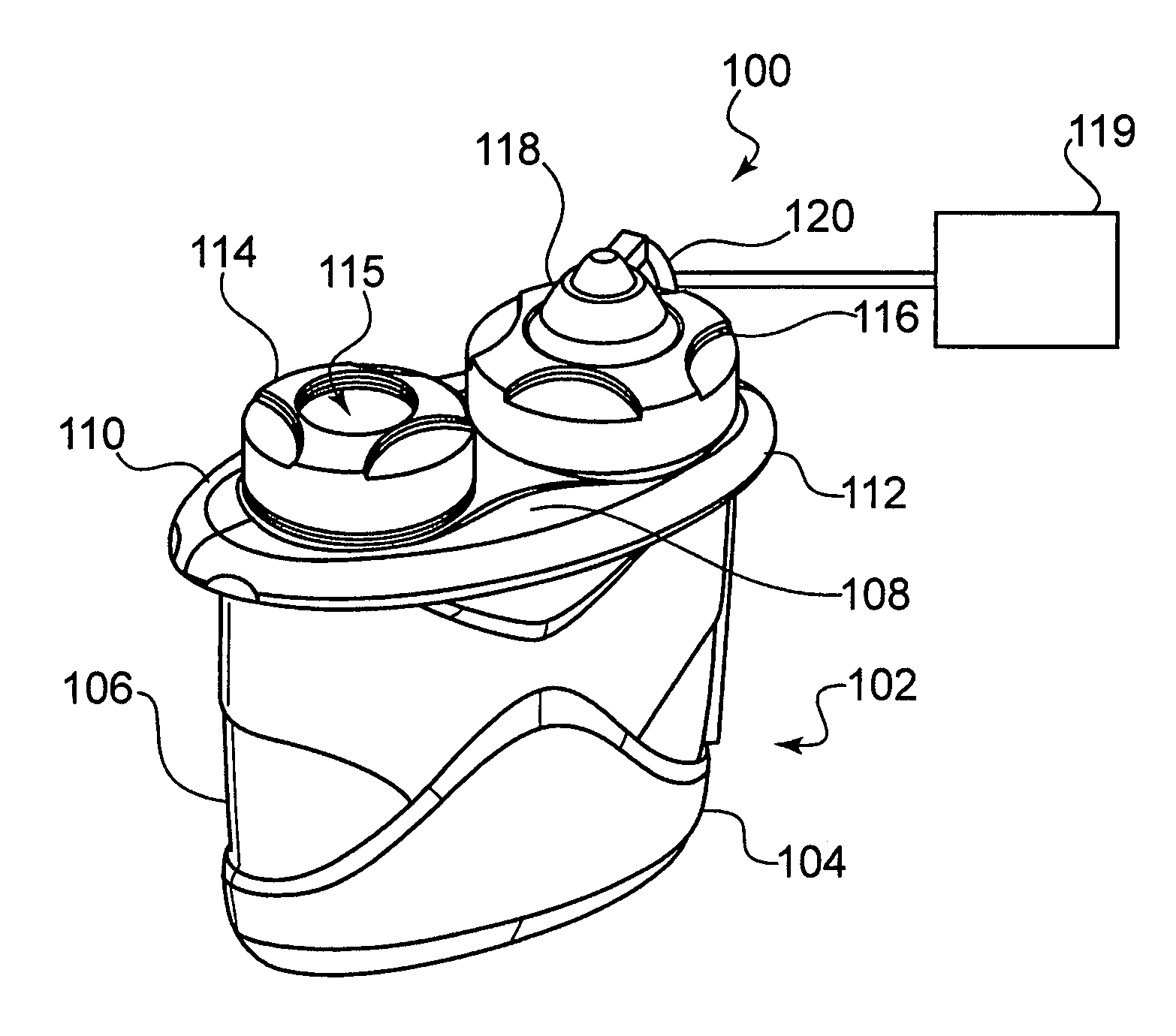
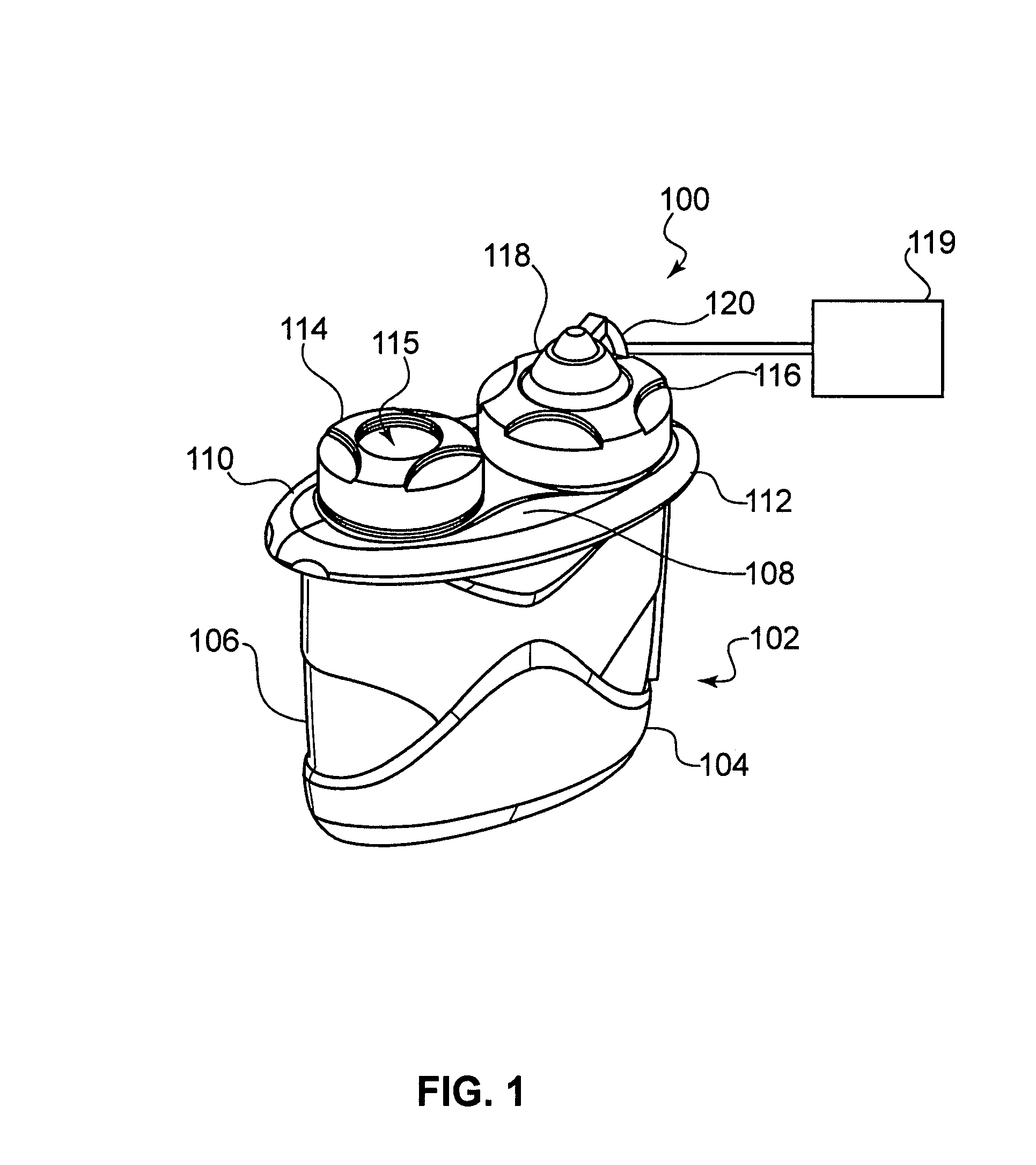
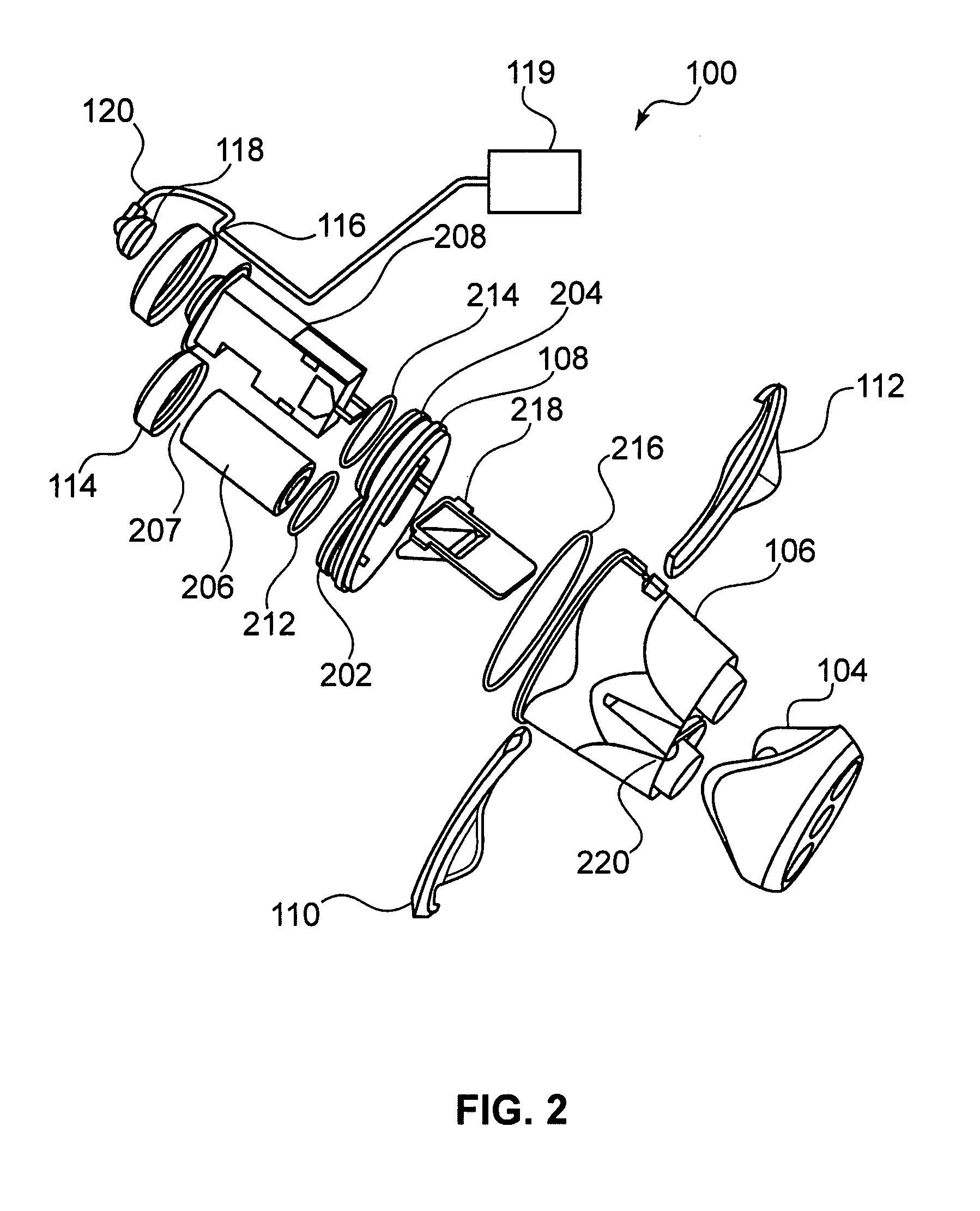
Medical apparatus using selective graphical interface
InactiveUS20040158193A1Easy to useLikelihoodRespiratorsInput/output for user-computer interactionProgrammable logic deviceMedical device
Abstract of the Disclosure A programmable medical device, such as an infusion pump, is programmed or configured to display, or make, as active, only those keys which can provide valid input during each particular programming or operational step. Similarly, a remote controller for controlling a programmable medical device is programmed or configured to display, or make, as active, only those keys which can provide valid input during each particular programming or operational step.
Owner:BAXTER INT INC
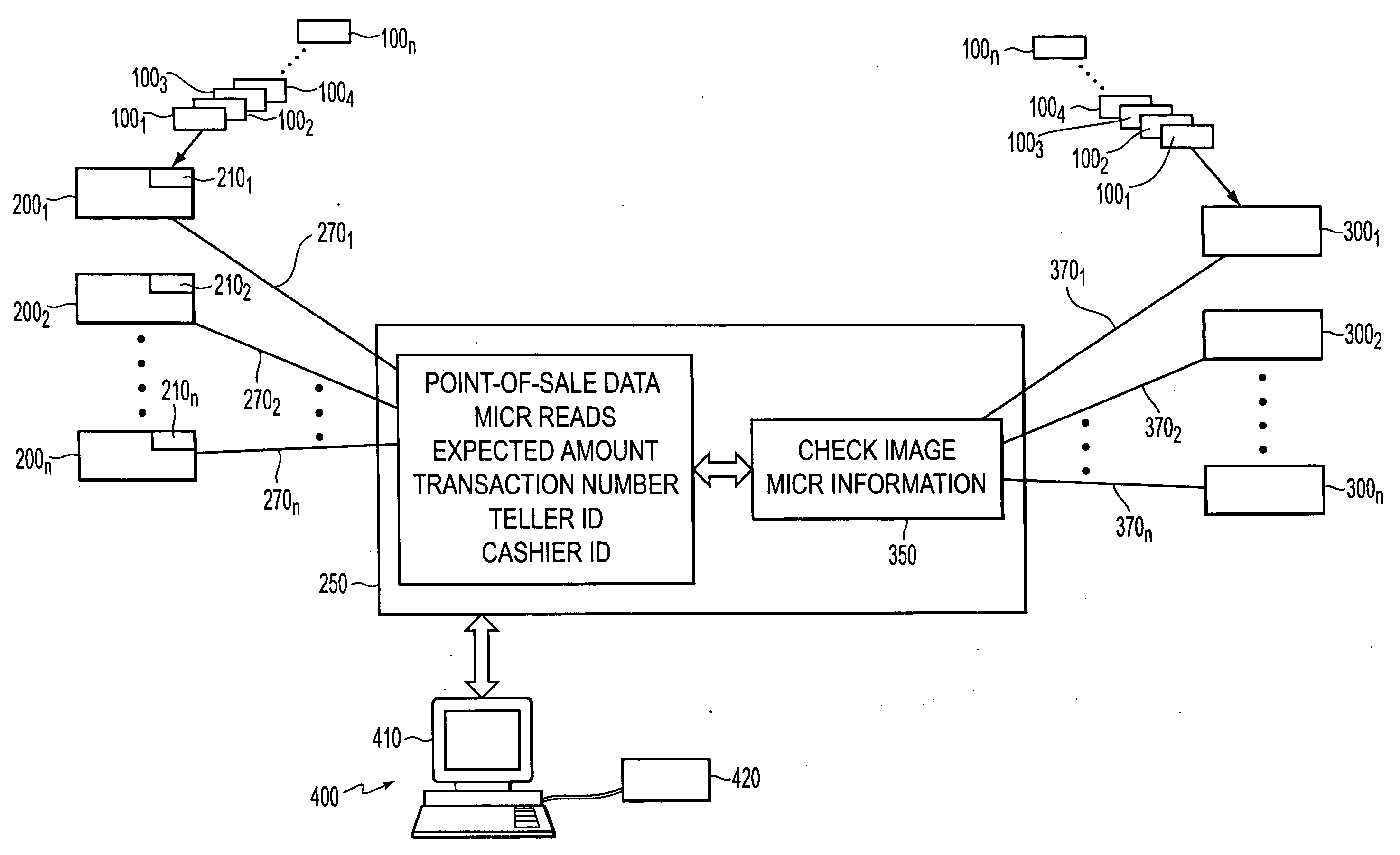
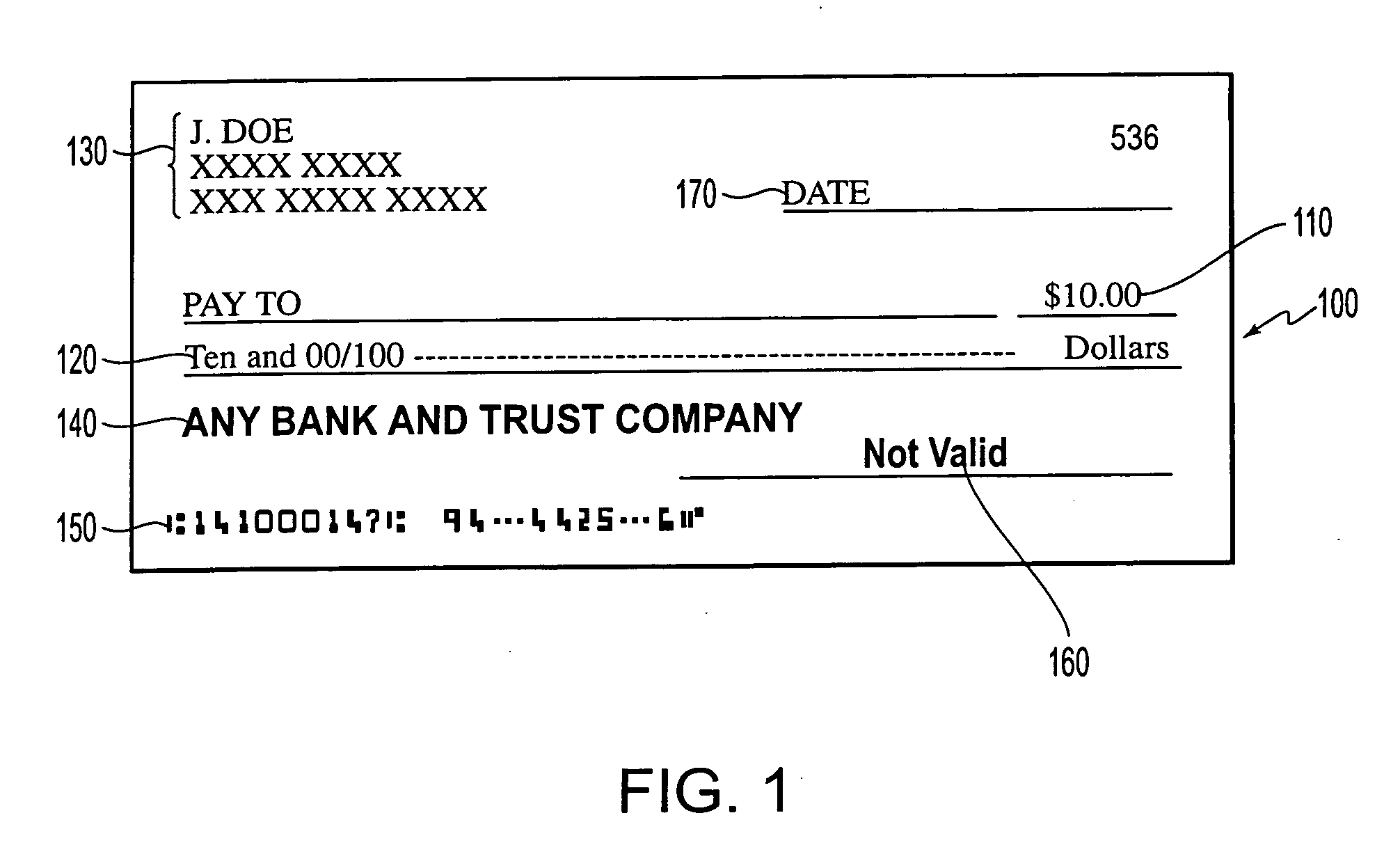
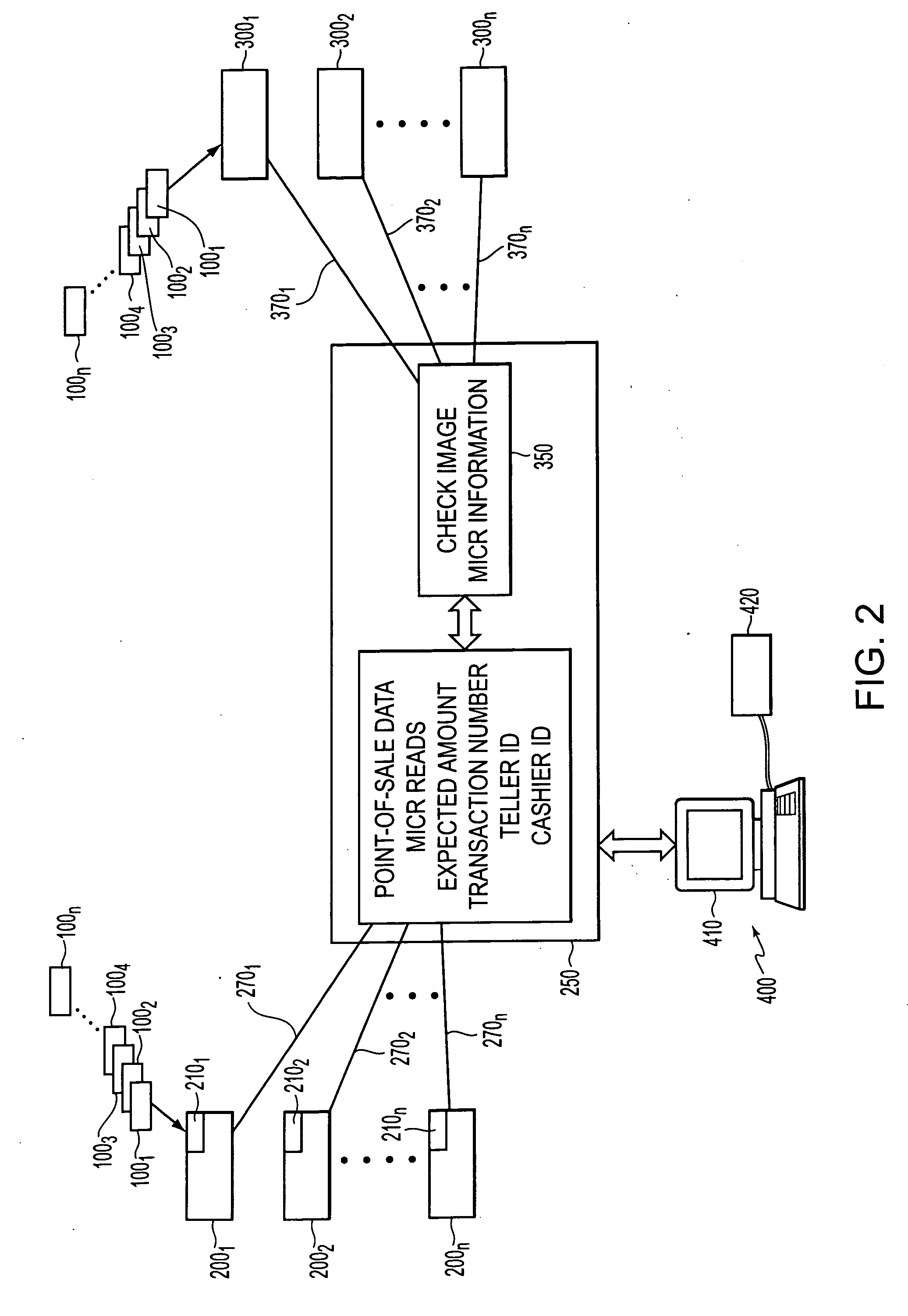
Method and apparatus for processing checks
ActiveUS20050108168A1Reduce physical activityImprove process integrityComplete banking machinesFinanceAlgorithmCheque
A check processing system and method comprising utilizes an image scanner that produces an electronic image of a check upon scanning of the check. The system and method receive the electronic image of the check from the image scanner, receive point-of-sale data generated at a point-of-sale, determine a monetary value of the check from the electronic image of the check, and reconcile the determined monetary value of the check with the point-of-sale data so that the check is correlated with a transaction that occurred at the point-of-sale.
Owner:TALARIS HLDG
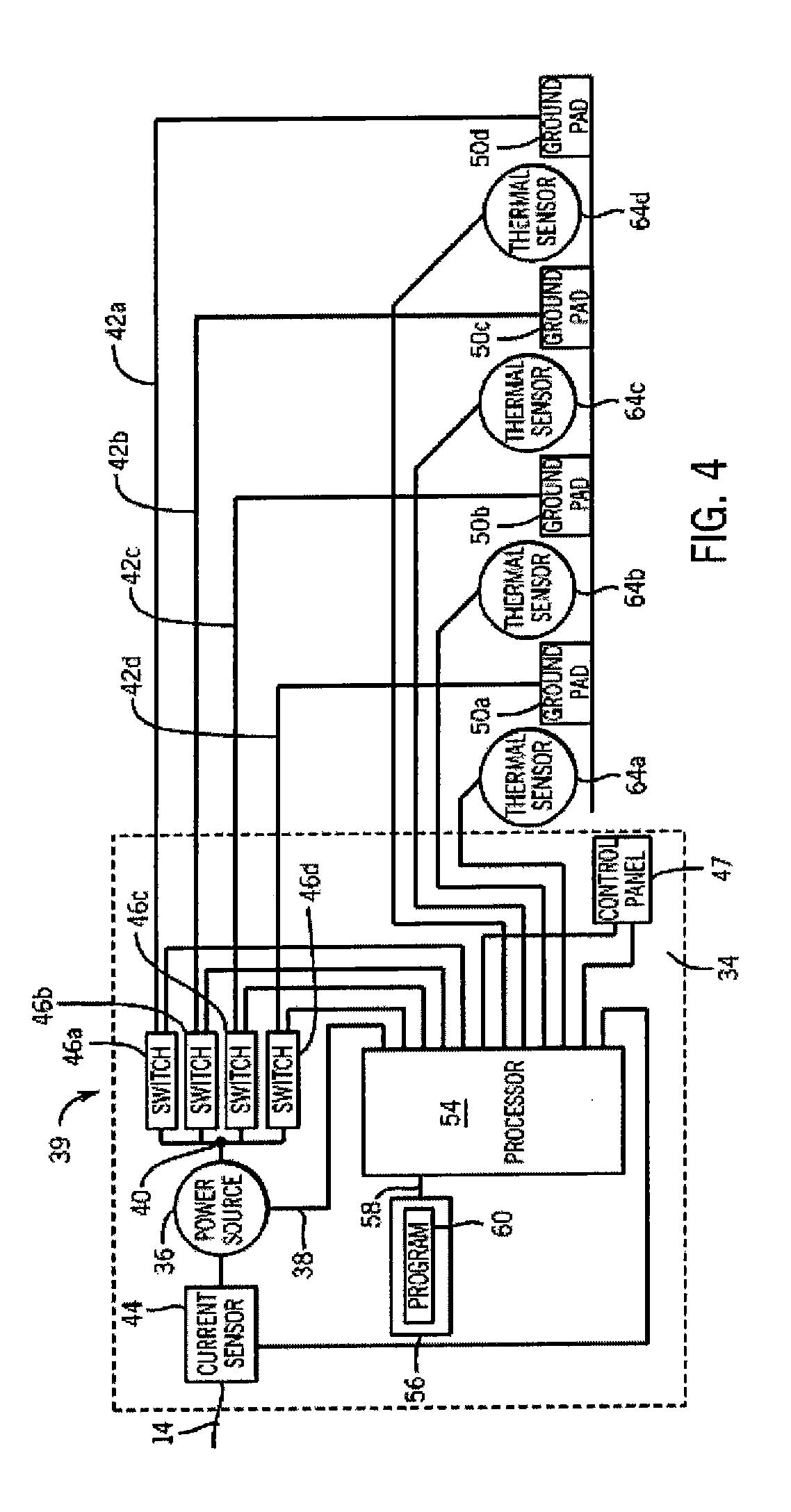
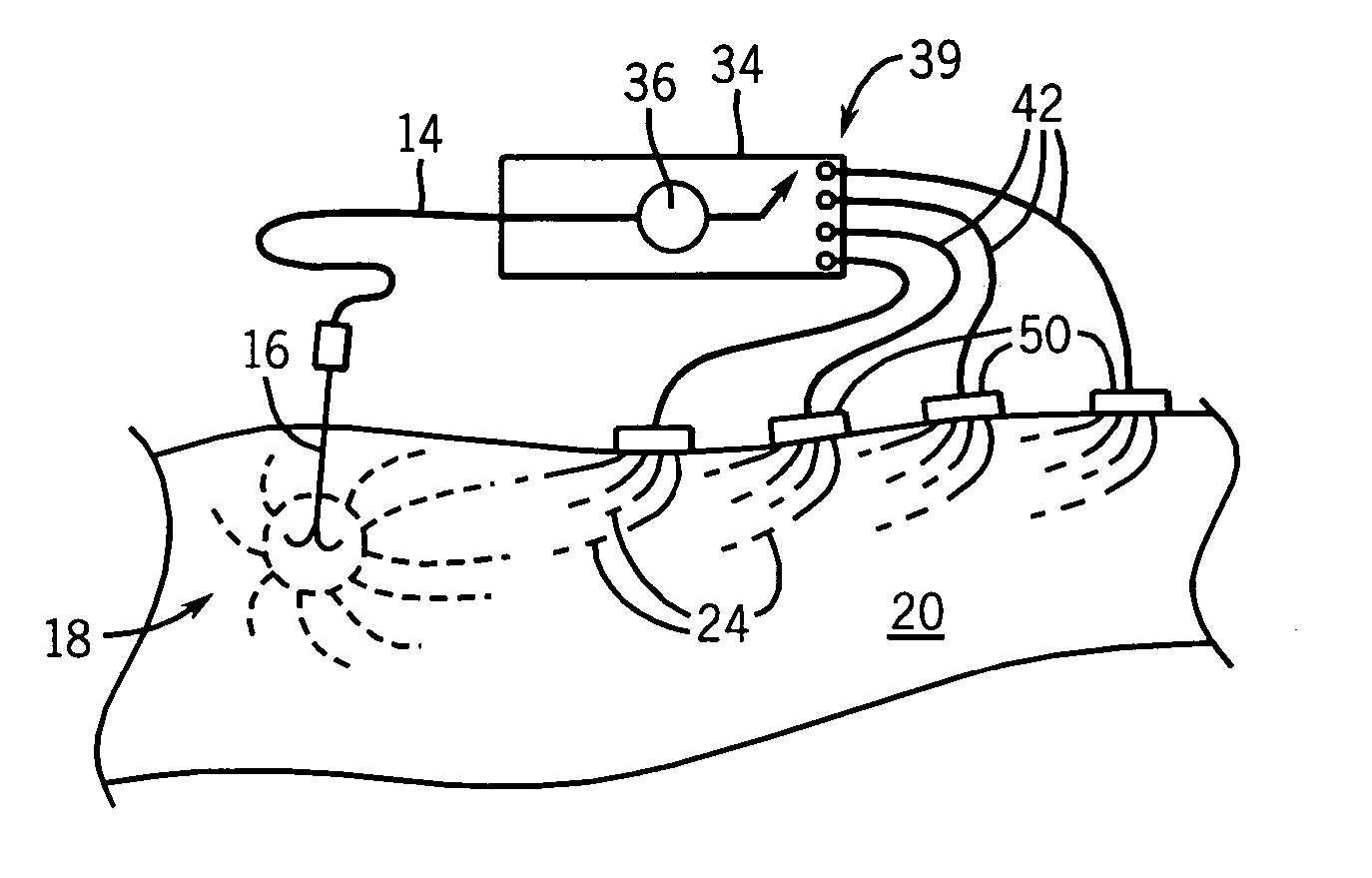
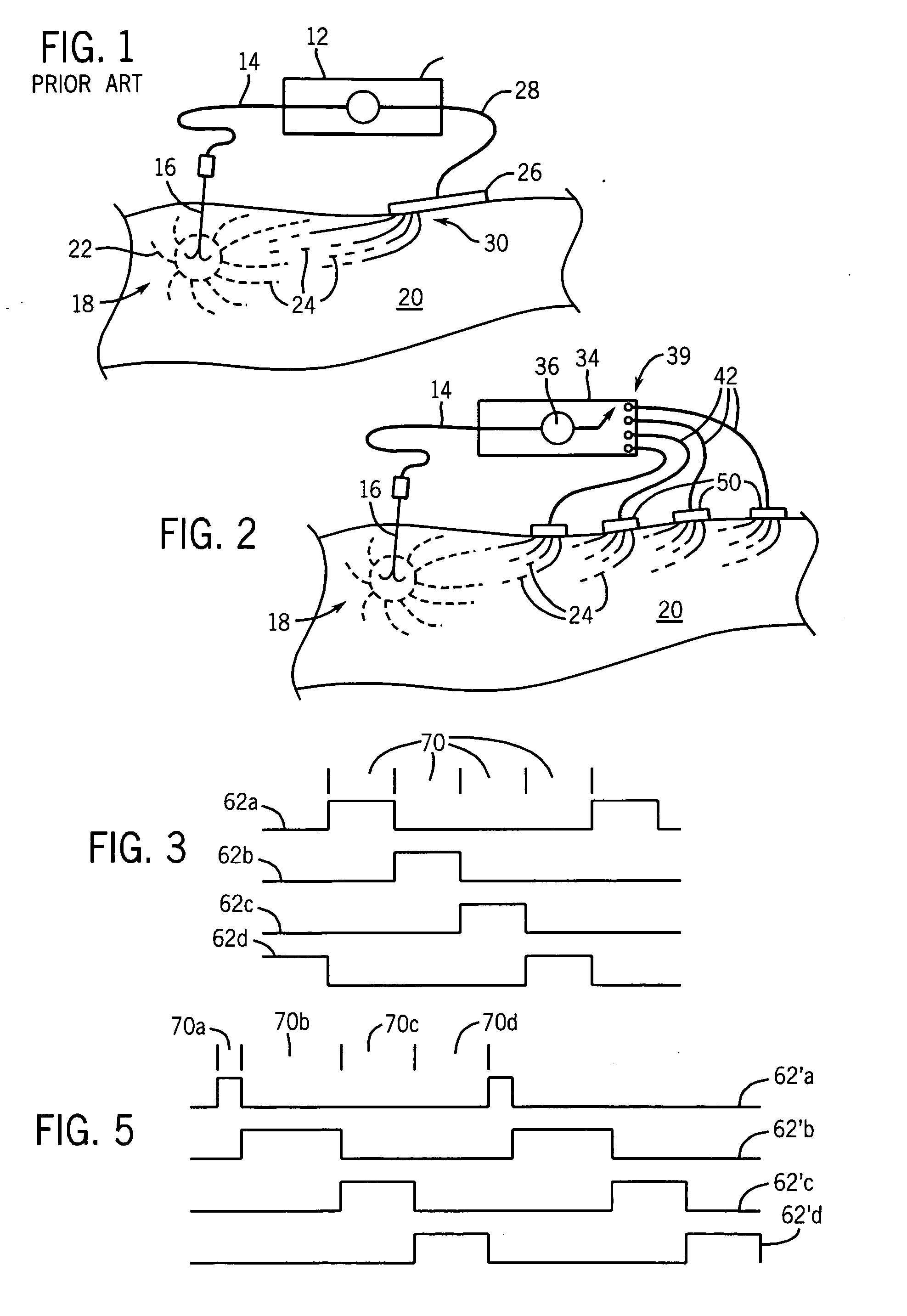
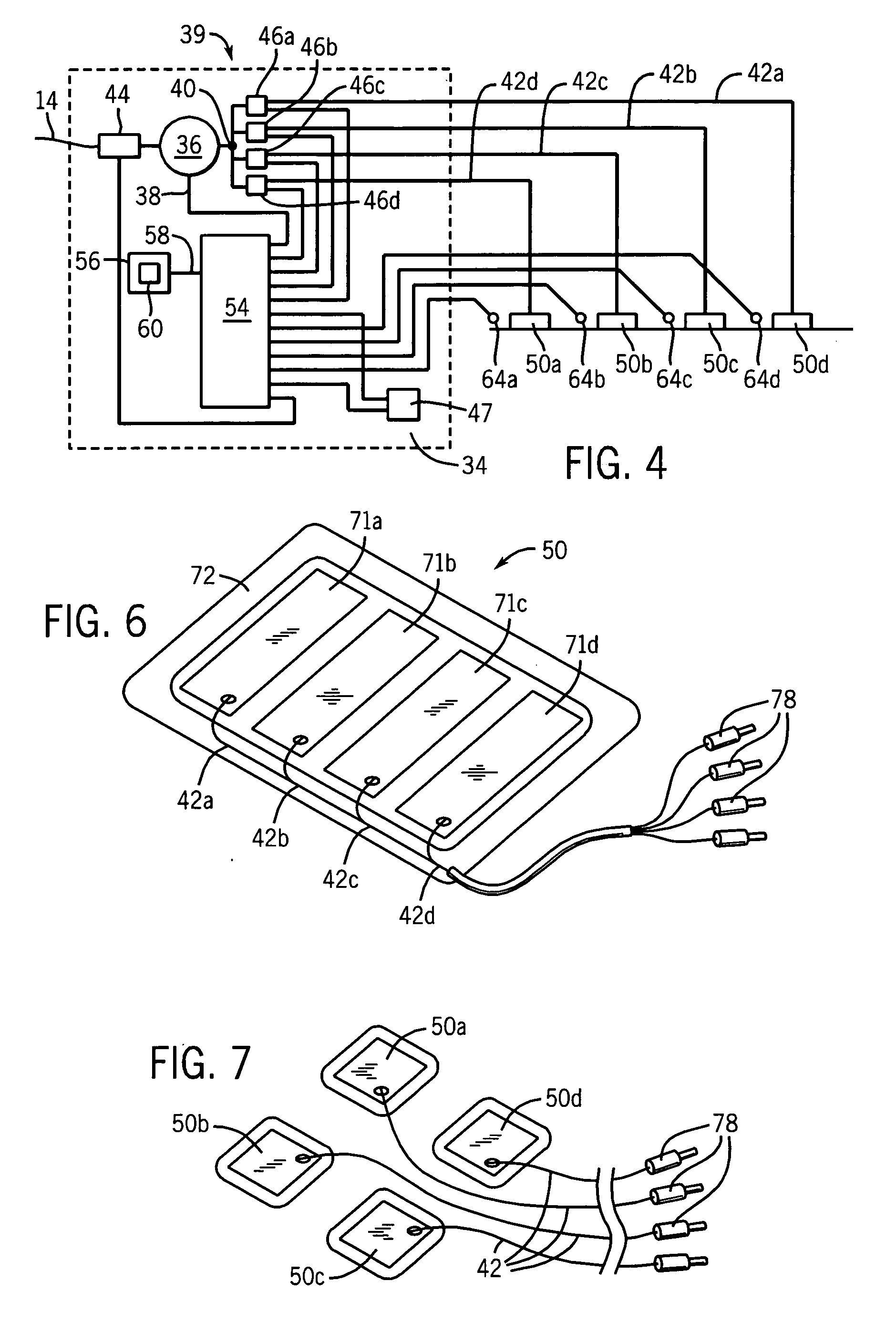
Radiofrequency ablation with independently controllable ground pad conductors
ActiveUS7736357B2Opportunities decreaseReducing maximum power outputSurgical needlesSurgical instruments for heatingRadiofrequency ablationElectrical conductor
A radiofrequency ablation system provides multiple ground pads and active control of current flow through the ground pads to provide improved power sharing at the tissue near the ground pads reducing risk of patient skin burns for higher power ablation generators.
Owner:WISCONSIN ALUMNI RES FOUND
Methods and devices for treating fractured and/or diseased bone
InactiveUS20030220648A1Opportunities decreaseOptimize allocationSurgical furnitureBone implantBiomedical engineeringLesion bone
Owner:ORTHOPHOENIX
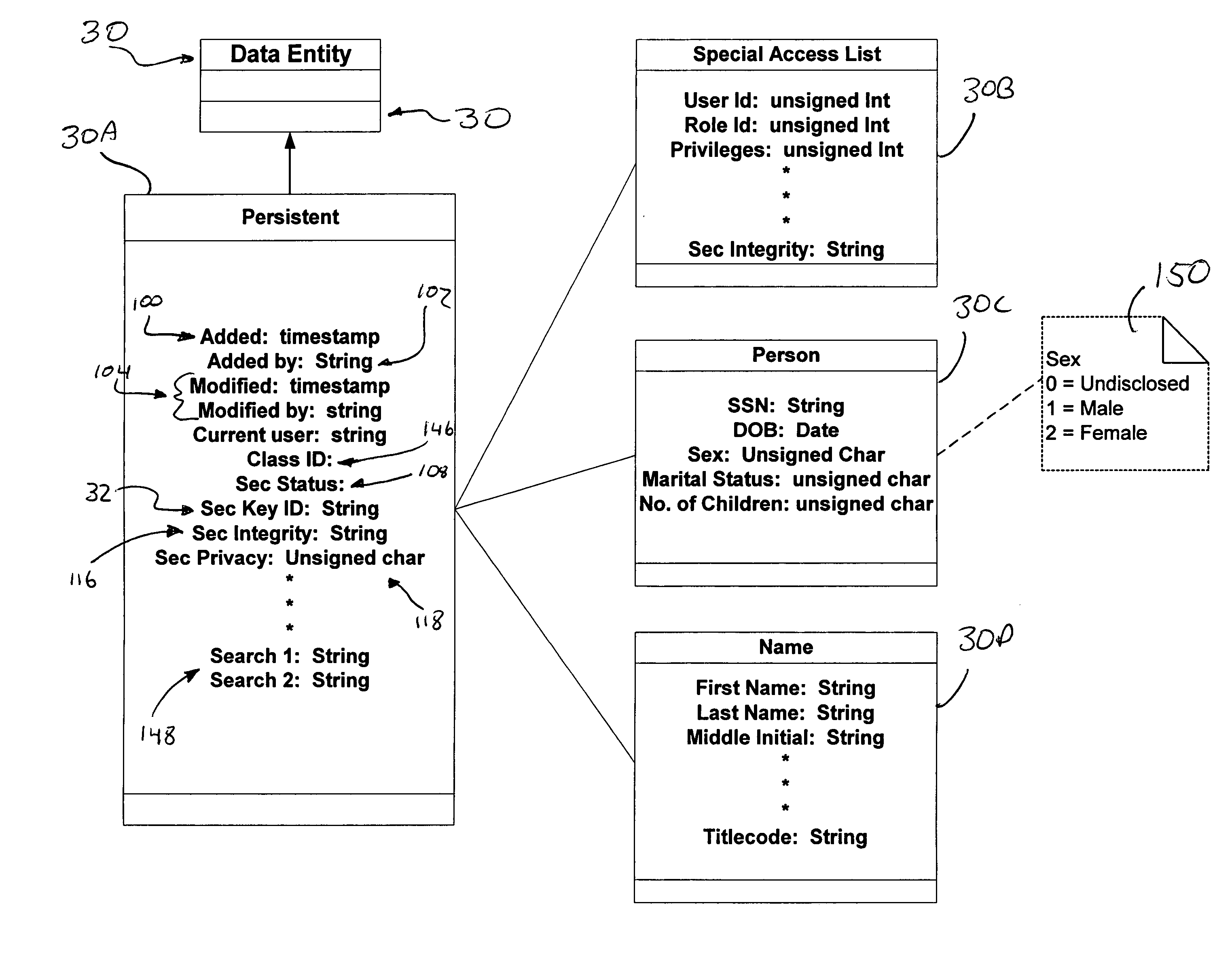
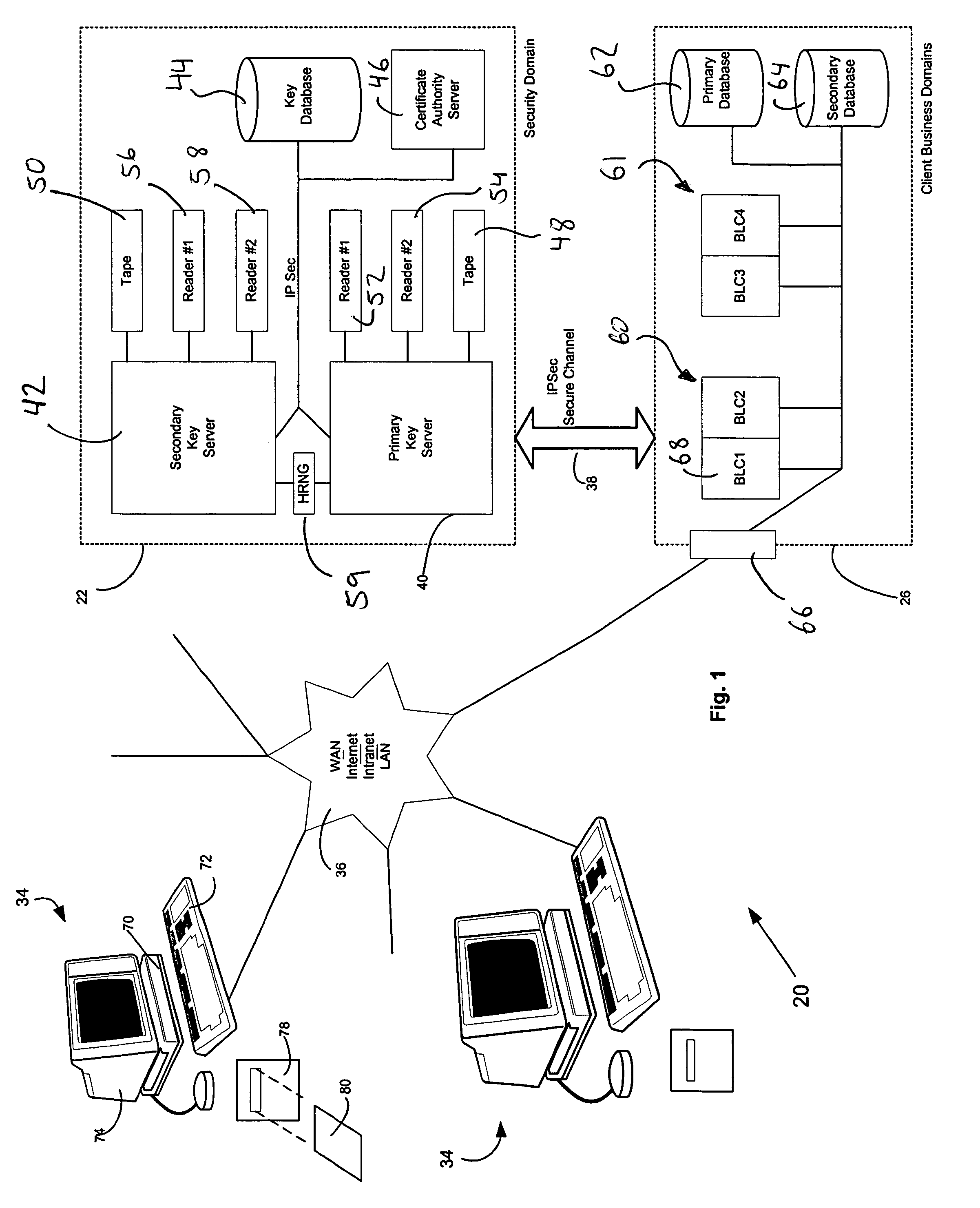
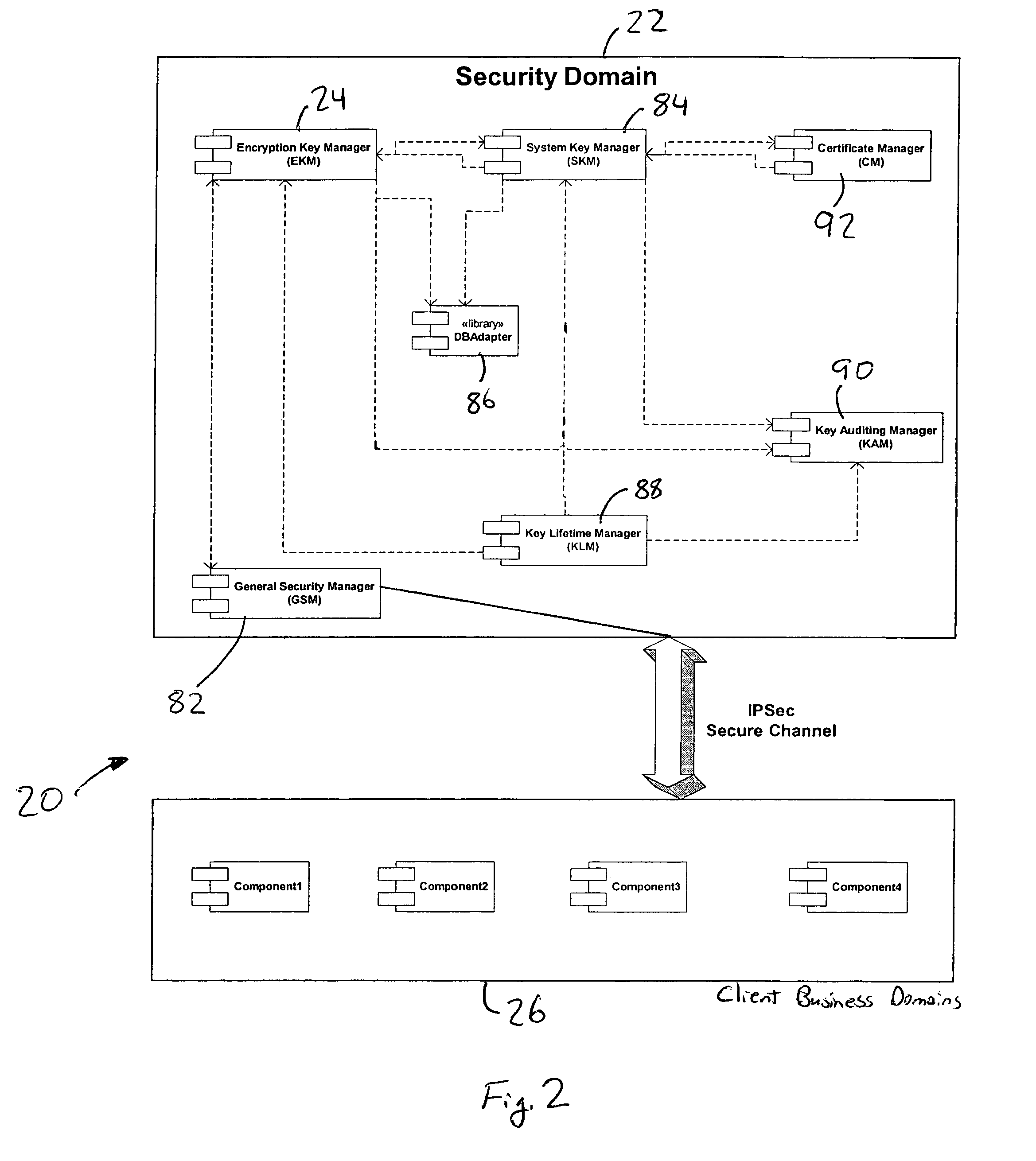
Hidden link dynamic key manager for use in computer systems with database structure for storage of encrypted data and method for storage and retrieval of encrypted data
InactiveUS7362868B2Improve securityOpportunities decreaseMultiple keys/algorithms usageComputer security arrangementsCommon nameSecurity domain
A computer system (20) having a security domain (22), at least one client business domain (26), and a plurality of client terminals (34) utilizes a hidden link dynamic key manager (24, 84) and a database structure that includes encrypted data entities (30C, 30D) and a security identification attribute (32) for storage of encrypted data. Methods for encrypting data and for storing, decrypting, and retrieving encrypted data operate on the computer system (20), which also includes an information database (62) and a key database (44). The key database (44) is isolated from the information database (62). The hidden link key manager is stored in the security domain (22) and includes a system key manager (84) operable to generate system keys with system key common names and an encryption key manager (24) operable to generate encryption keys having encryption key identifications. The key managers (24, 84) operate on a key server (40), which is mirrored by a secondary key server (42). A general security manager (82) also operates on the key server (40) to control access to the security domain (22). The security information attribute (32) is stored with a persistent data entity (30A) that is associated with the other encrypted data entities (30C, 30D) by a database schema. The encryption key identification (112) for the encryption key used to encrypt the data entities (30C, 30D) is encrypted by a system key and then stored as part of the security information attribute (32). The system key common name hash value (114) is also stored in the security information attribute (32). The information data entities (30) are stored on the information database (62), but the encryption key identification (153), encryption key (154), system key common name hash value (156, 157), and system key common name (158) are stored in the key database (44) inside the security domain (22). The system key itself is stored on a Smart Card reader (56) inside the security domain.
Owner:FARRUKH ABDALLAH DR +1
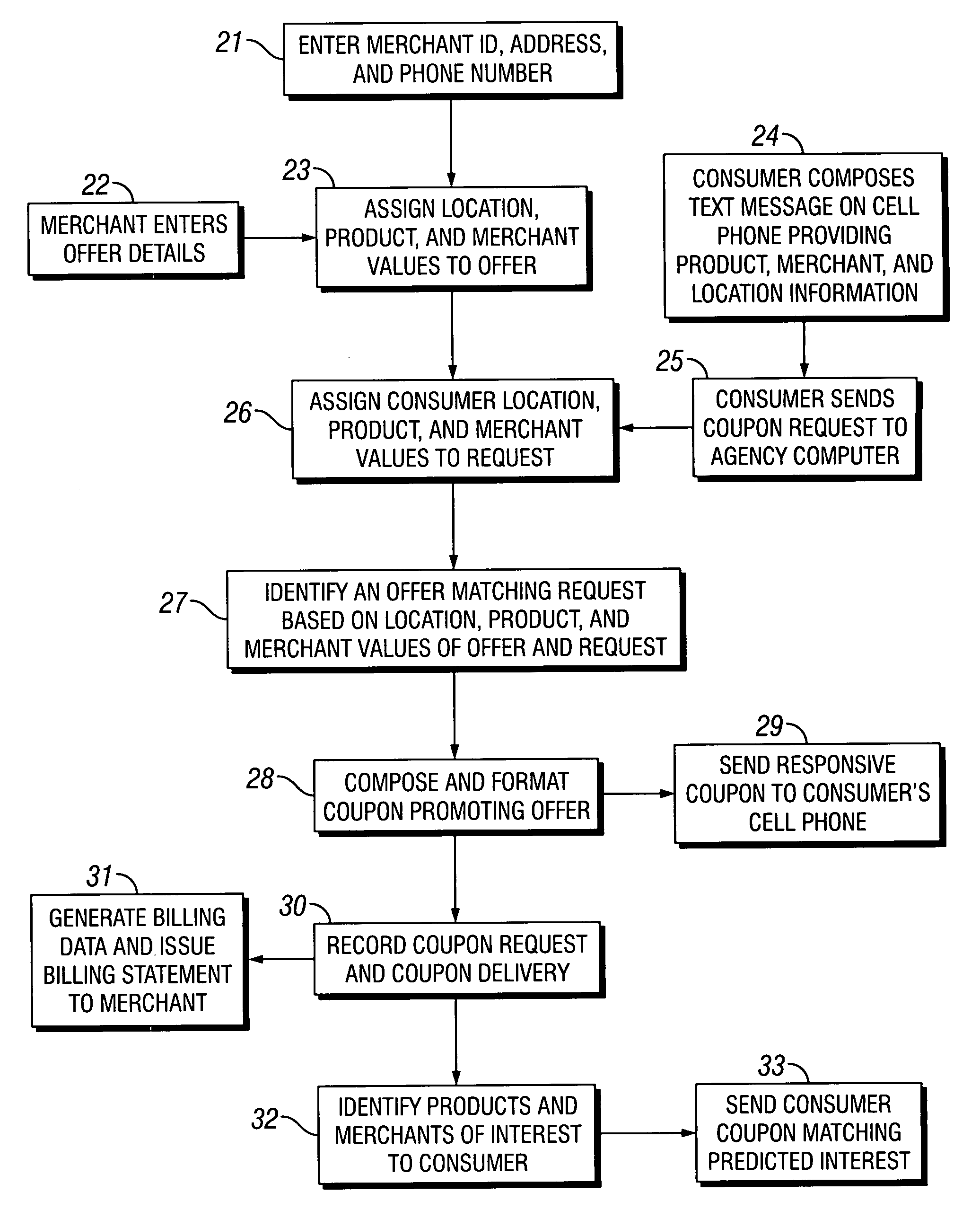
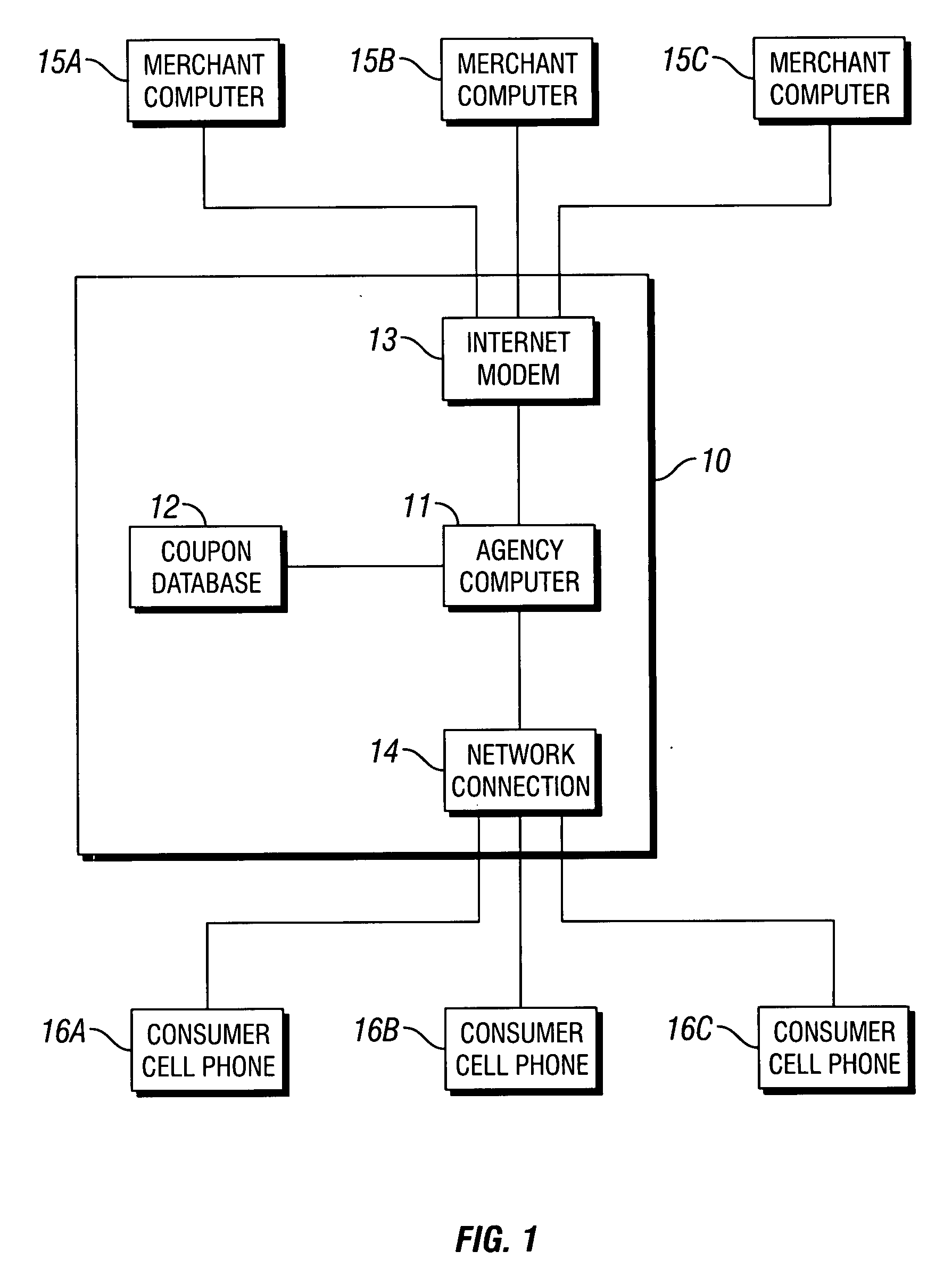
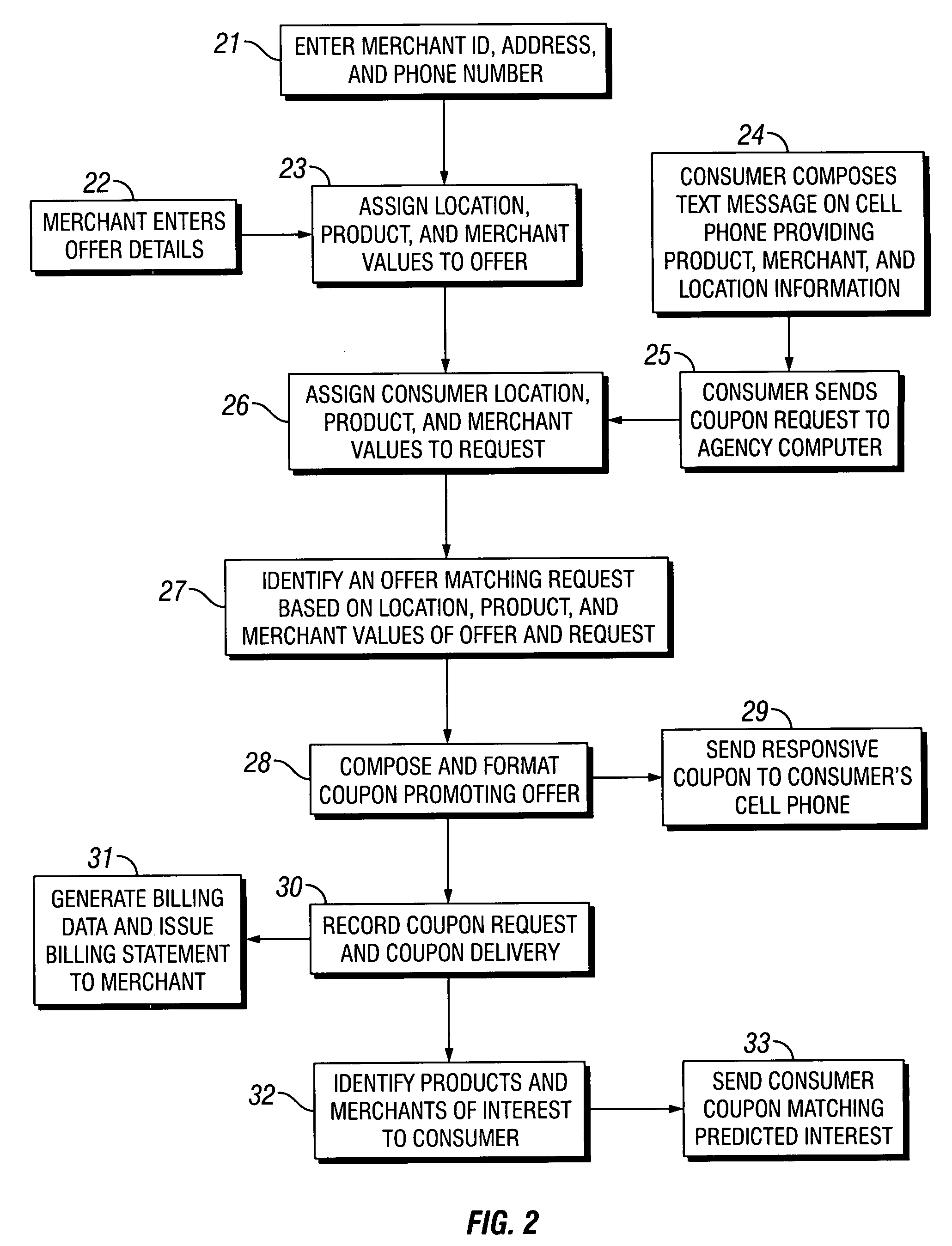
Coupons and systems for generating coupons on demand
InactiveUS20080027810A1High redemption ratePromote effectiveMarketingSystem identificationInformation agents
Coupons which are displayed as a text message on a mobile telecommunication device and include a code uniquely identifying the coupon are provided for. Systems for generating coupons on demand are also provided for. The system comprises an agency computer having access to a coupon database. The coupon database comprises information on offers and a location value assigned to each offer. The agency computer is connectable to a mobile communications network or other network for transmitting electronic mail. It receives requests for coupons from consumers that are transmitted via the network. Preferably, the requests originate from cells phones or other mobile telecommunication devices and are transmitted to the agency computer via a mobile communications network. The request is a text message that includes information identifying the consumer's location. The agency computer system identifies a coupon in the coupon database that is responsive to the coupon request based on the consumer's location and the offer location value. It then sends the identified coupon to the consumer via the network.
Owner:WHAMMOBILE
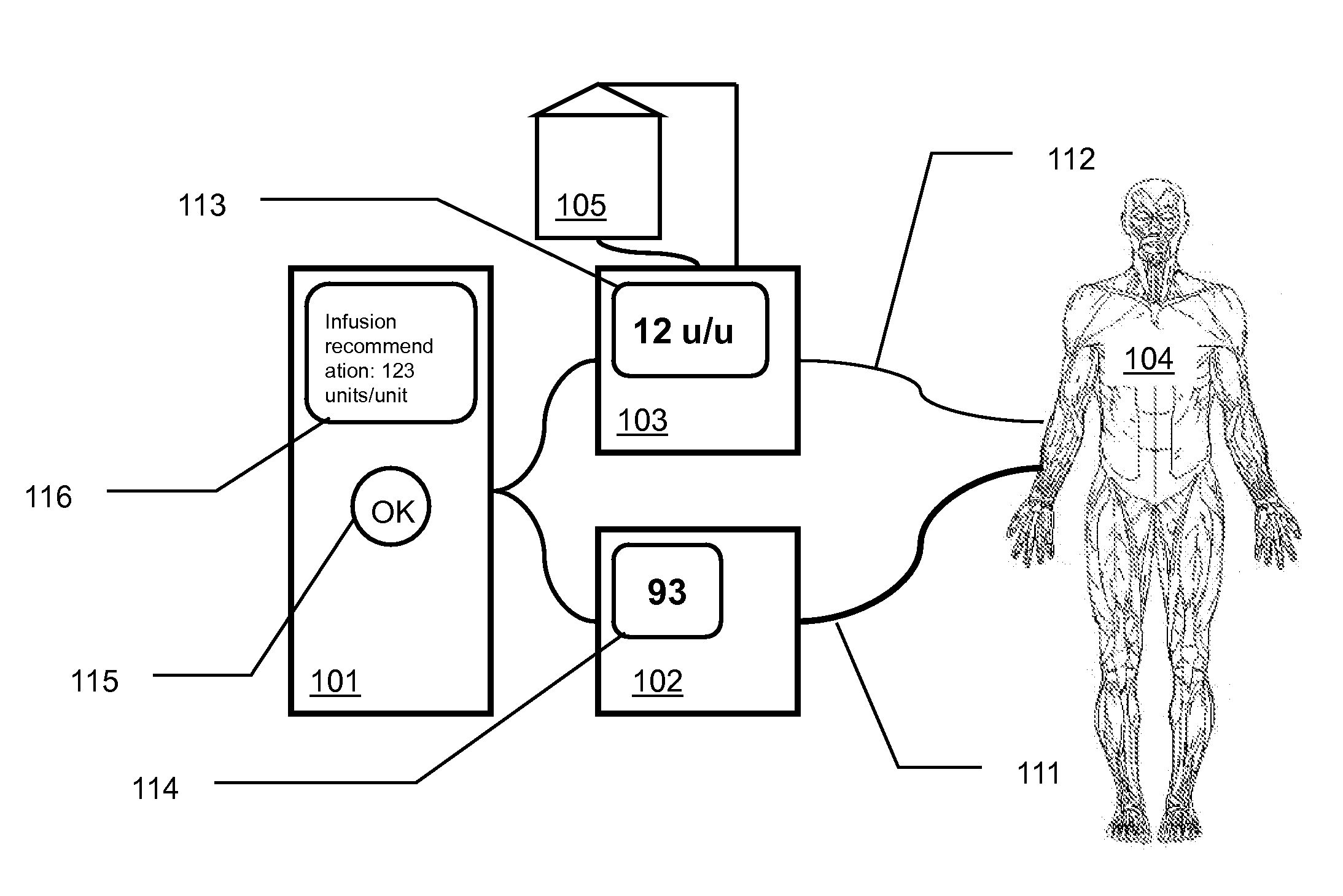
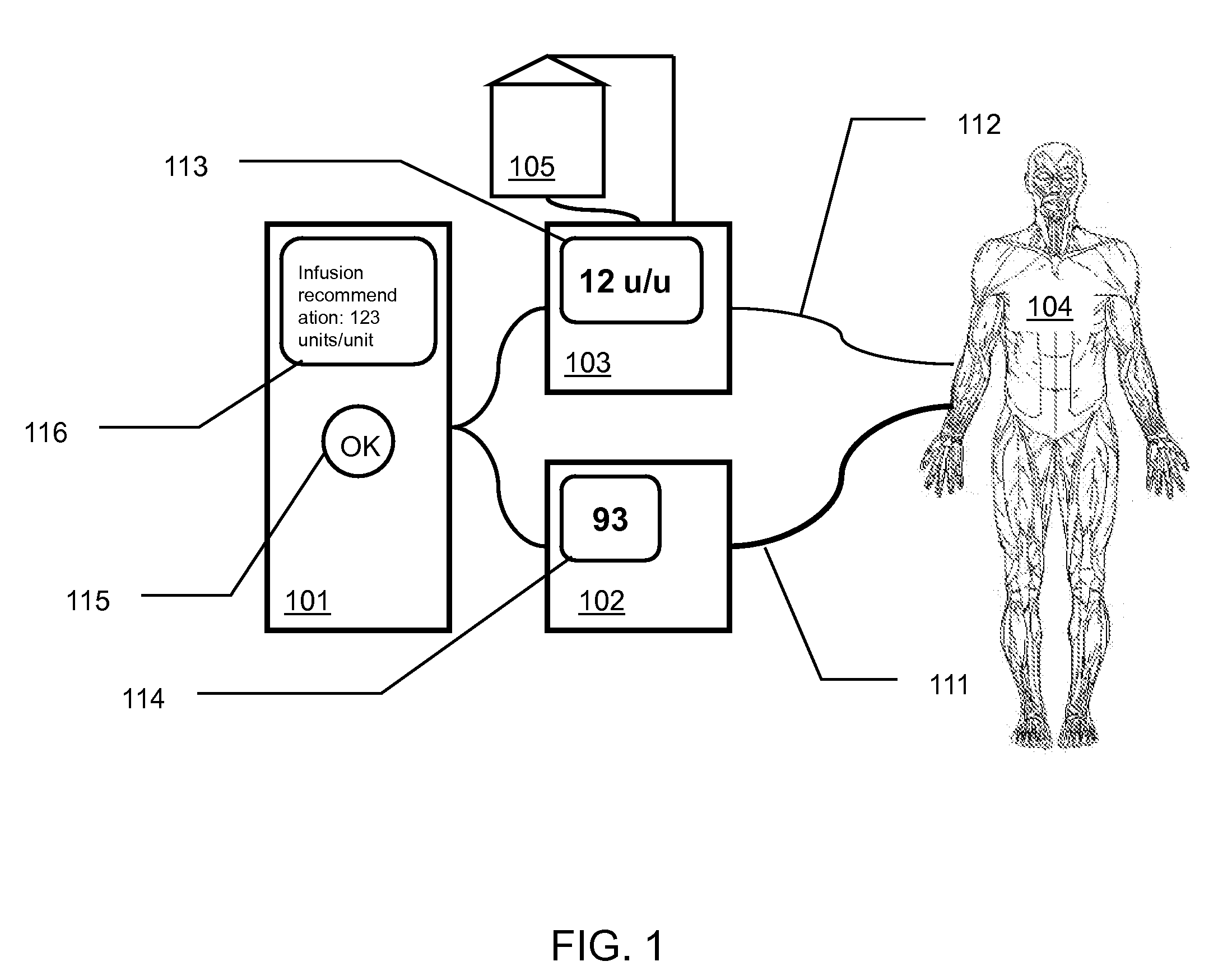
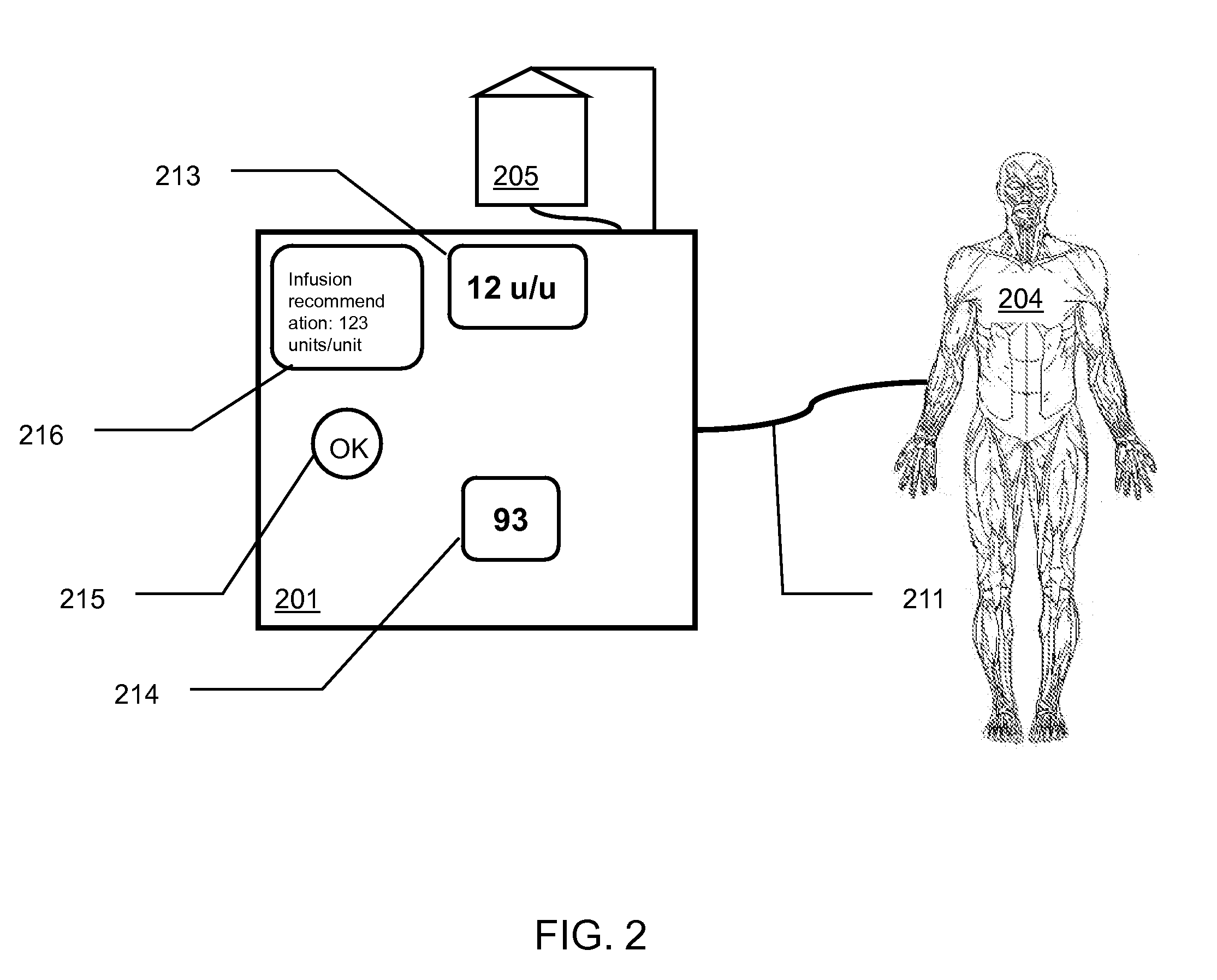
Clinician-controlled semi-automated medication management
InactiveUS20090054754A1Opportunities decreaseEfficient managementDrug and medicationsMedical devicesMedication infusionAnalyte
The present invention is directed to methods and apparatuses of medication management based upon active authorization of medication infusion by a clinician that can provide for effective management of an analyte in a patient's blood, reducing the opportunities for human error common with current manual systems while still placing final control of the medication management with the human clinician. For example, a semi-automated glucose management system can measure the glucose level in a patient's blood, recommend infusion parameters to a clinician who can authorize an infusion of glucose or insulin, and infuse the glucose or insulin into the patient.
Owner:LUMINOUS MEDICAL
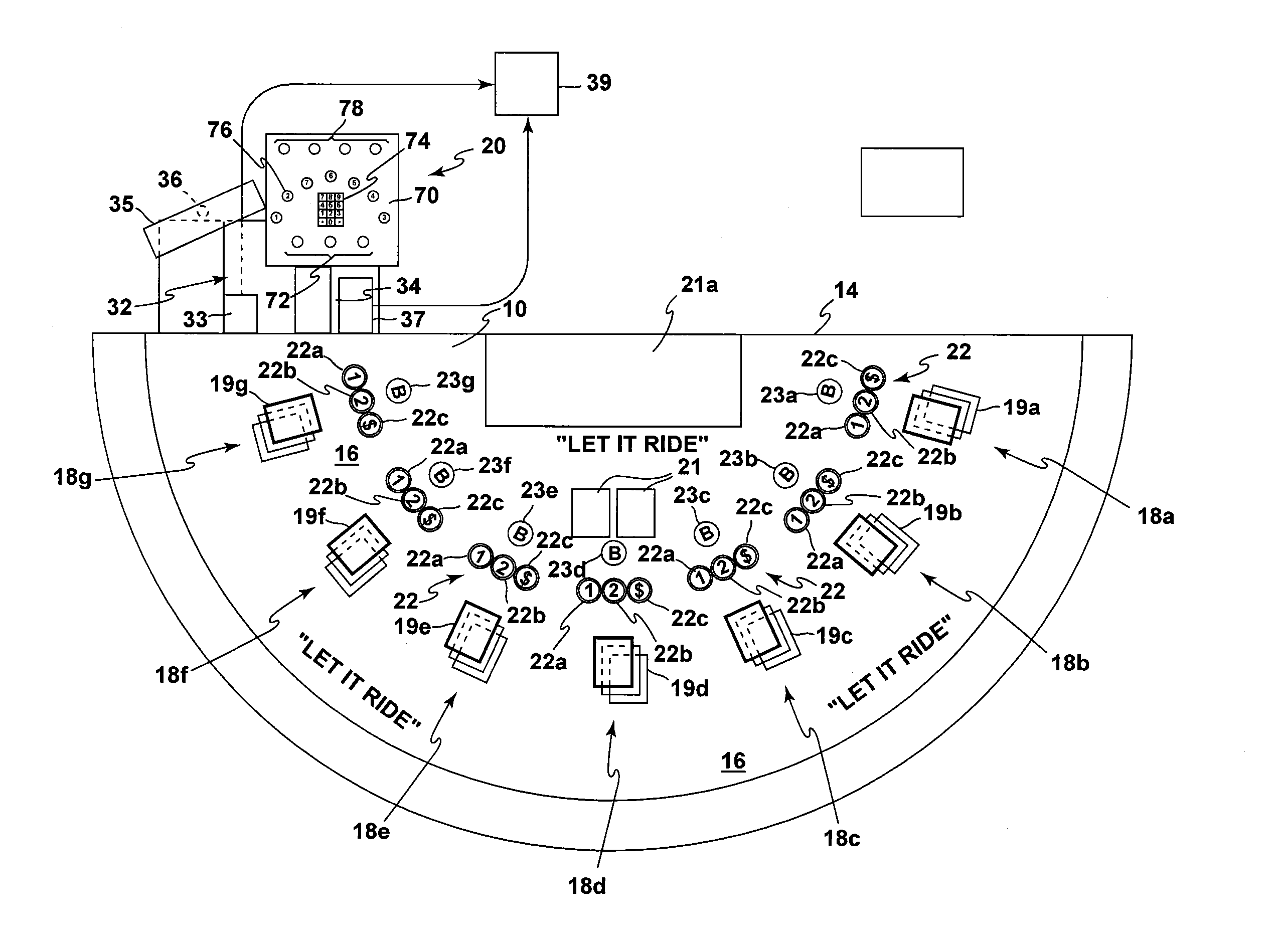
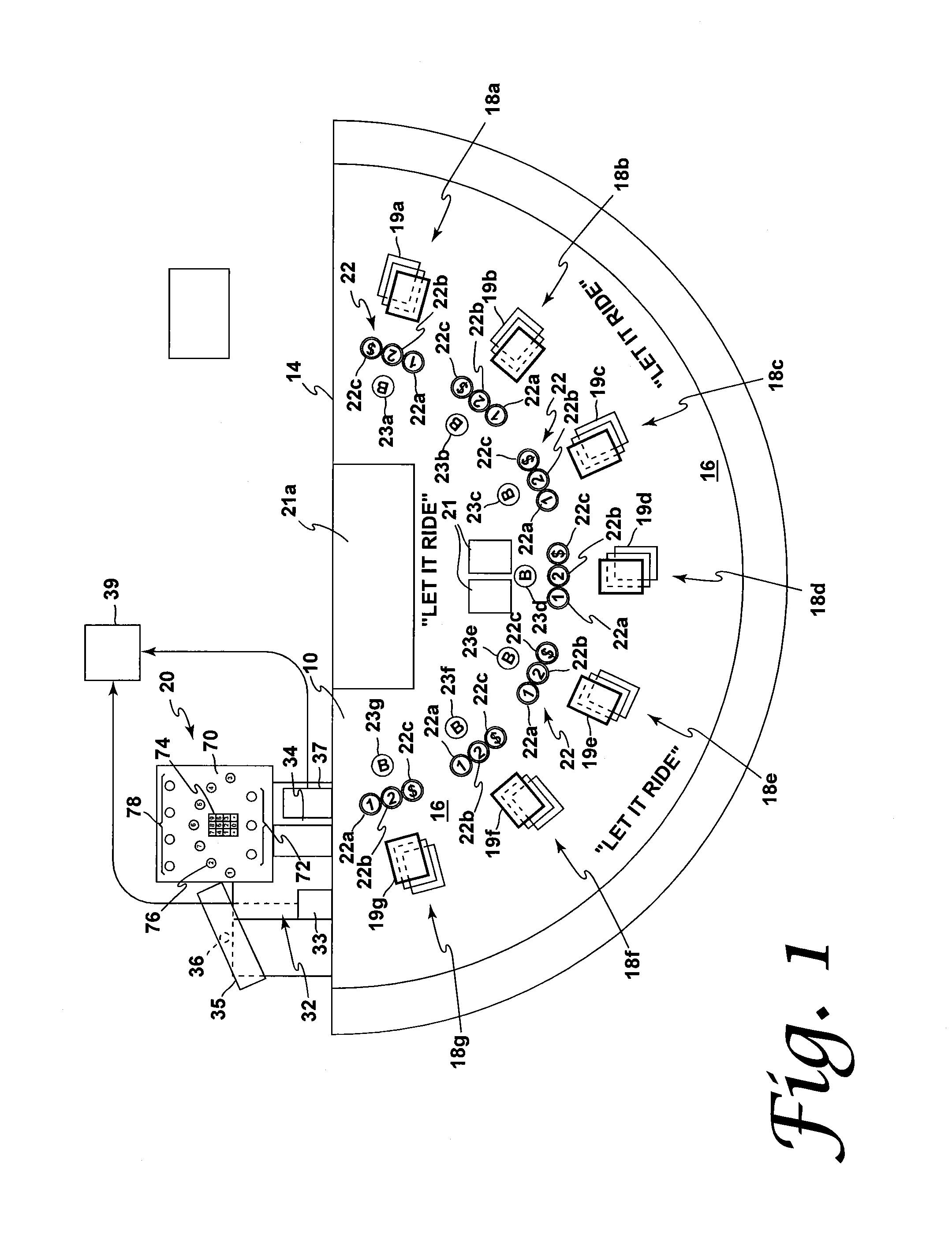
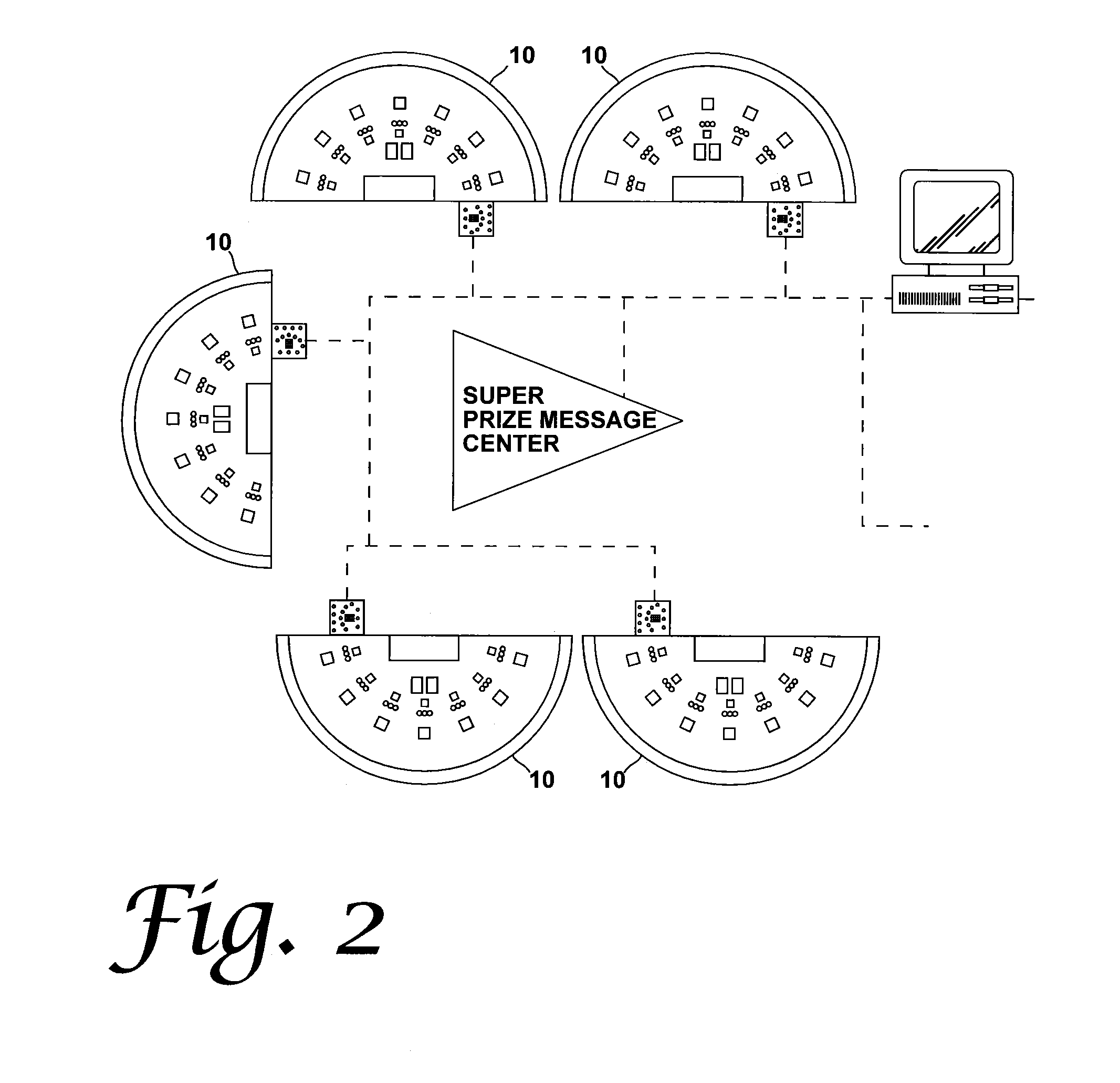
Method and apparatus for using upstream communication in a card shuffler
InactiveUS20130109455A1Opportunities decreaseMaximize safetyCard gamesRoulette gamesOperating systemSecurity system
A security system for a casino table card game has a casino table with i) indicia thereon for the placement of wagers, ii) a data entry system with an associated computer, and iii) sensors that can detect the placement of at least one specific category of wager; a shuffling device with a microprocessor integral to the shuffler for providing information regarding cards or hands; a central table gaming computer that receives information from the shuffler in real time, receives information from the sensors, and receives information from the data entry system, the associated computer, the microprocessor and the central table gaming computer communicating data among each other in real time.
Owner:BALLY GAMING INC
Method and apparatus for using upstream communication in a card shuffler
ActiveUS8337296B2Reduce riskStay attractiveLottery apparatusCard gamesComputer hardwarePlastic materials
A tray, serving as a transaction drawer, optimally fitted to X-ray inspection equipment for ease and efficiency of the operation. Yet, easy to handle by the operator and stackable for storage and having a test wedge to verify read outs by the X-ray machine, made out of translucent, plastic material, economically produced.
Owner:LNW GAMING INC
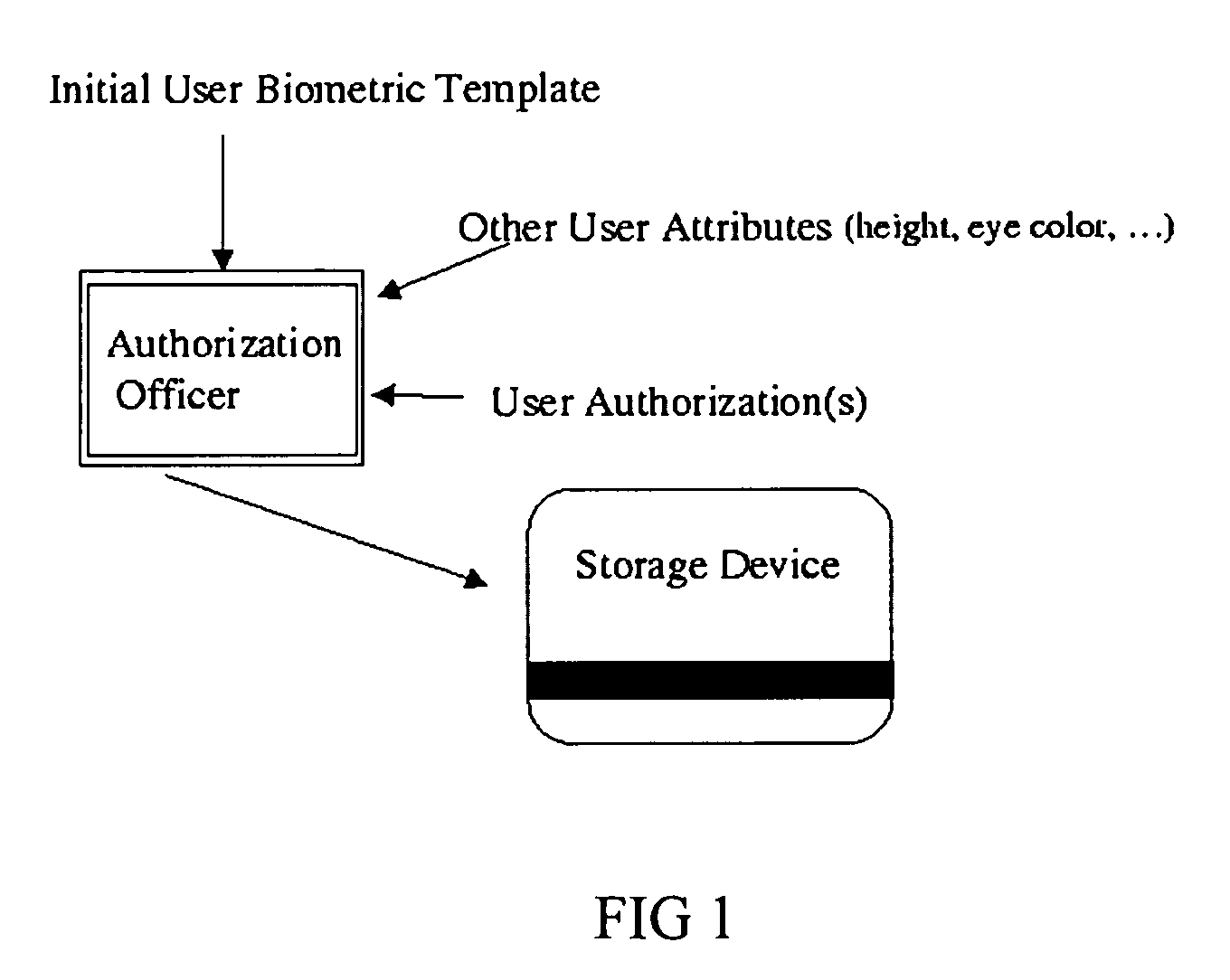
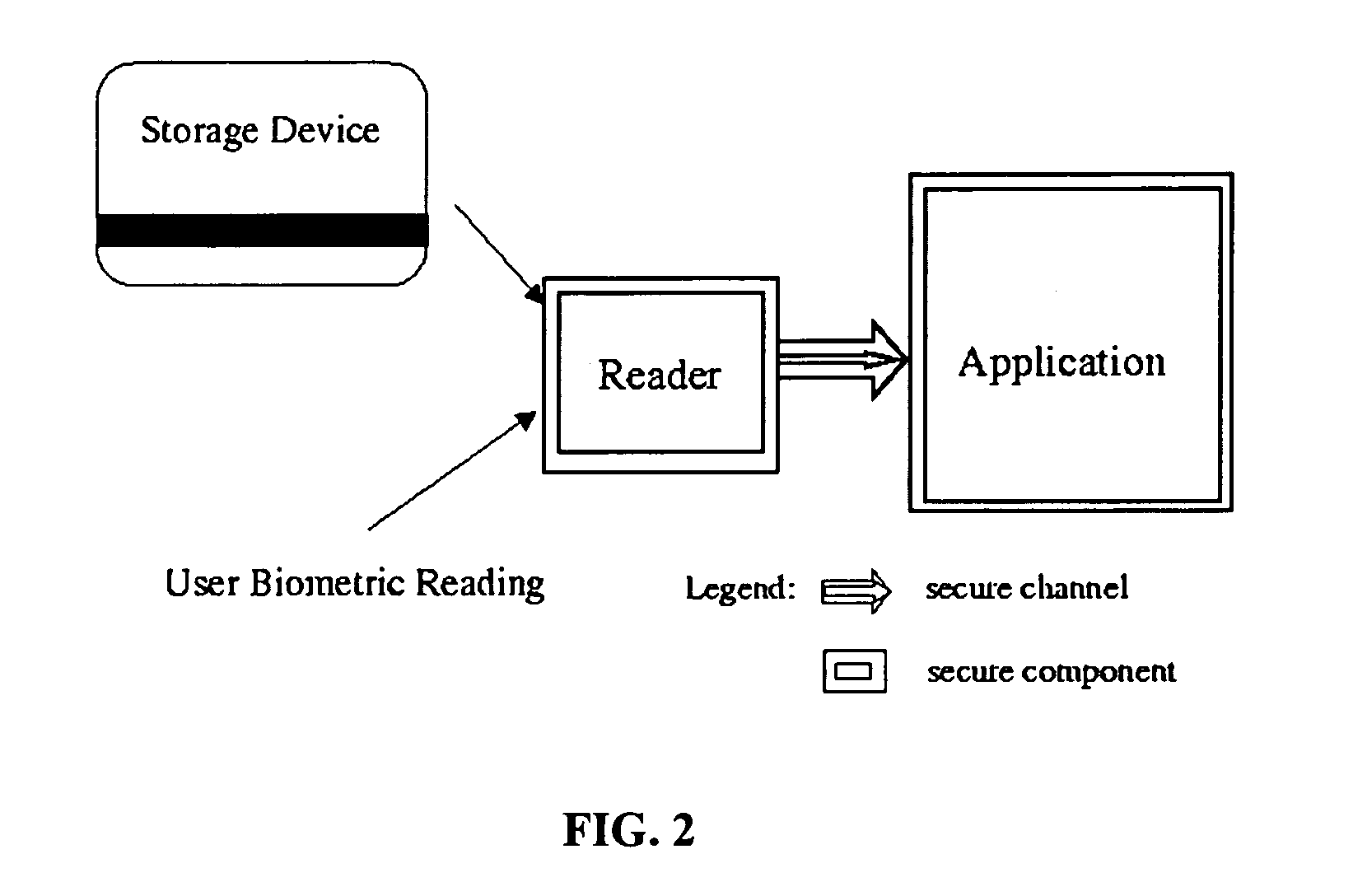
System and method for authenticated and privacy preserving biometric identification systems
InactiveUS7711152B1Opportunities decreaseElectric signal transmission systemsImage analysisOnline modelControl system
A system and method for the identification of users and objects using biometric techniques is disclosed. This invention describes a biometric based identification and authorization systems which do not require the incorporation of an on-line database of stored complete biometrics for the security infrastructure. In order to remove the connectivity requirements, an off-line biometric system is achieved by incorporating an identity verification template (IVT) on a storage device / token (e.g., magnetic strip or smart-card) during the user's registration which provides for a reliable storage medium; however, there are no security requirements required of the token even to protect the privacy of the stored biometric. The IVT does not contain complete information of the user's biometric but allows for the verification of the user when that user later provides a biometric reading. To deal with errors that may be introduced into later scans of the biometric (for example at the time of verification) error correcting techniques, well known in the art of communication and error control systems, are incorporated into the system. The system is also usable in the online model. Moreover, it may also be used to enable cryptographic operations by being used to partially compose or encrypt private keys for cryptographic operation.
Owner:GIDIPO LLC
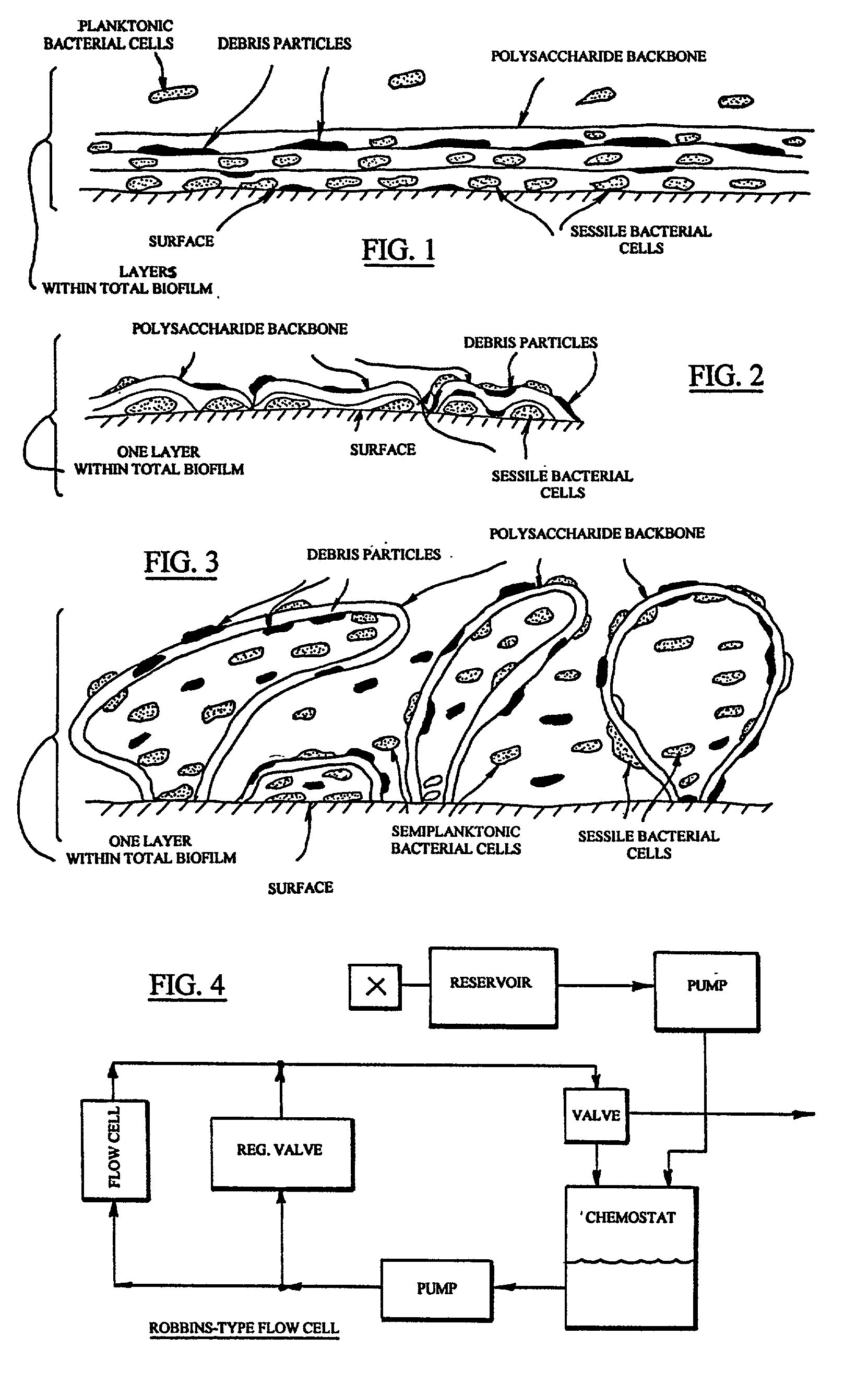
Compositions for treating biofilm
InactiveUS20020037260A1Improve the immunityReduced metabolic activityCosmetic preparationsBiocideBiofilmMicrobiology
Owner:BUDNY JOHN A +1
Wind turbine
InactiveUS6015258AImprove efficiencyImprove abilitiesPropellersWind motor controlElectric energyClassical mechanics
Wind turbine apparatus is described for converting wind energy into electrical energy. The apparatus includes a rotatable central shaft, a plurality of rotor blades attached to the central shaft, and a plurality of convex airfoils spaced around the periphery of the rotor blades. The ratio of the number of rotor blades to the number of airfoils is at least 1.25 to 1. The size of the apparatus may vary, and the apparatus is useful in a variety of applications and environments. It is very efficient in converting wind energy to electrical energy. It may be operated even in very high wind conditions.
Owner:TERRA MOYA AQUA
Apparatus and methods for production of biodiesel
InactiveUS20080220515A1Improve efficiencyImprove cost effectivenessBioreactor/fermenter combinationsBiological substance pretreatmentsBiodieselPhotobioreactor
A photobioreactor includes a cultivation zone configured to contain a liquid culture medium and facilitate growth of a microalgae biomass, a plurality of parallel edge-lit light transmitting devices mounted within the cultivation zone, and a collection zone oriented in relation to the cultivation zone such that at least a portion of the liquid culture medium and microalgae from the cultivation zone may be periodically harvested. Methods for illuminating algae, for dissolving materials into an algae medium, for extracting oil from algae, and for producing biodiesel from algal oil are also provided.
Owner:MIP
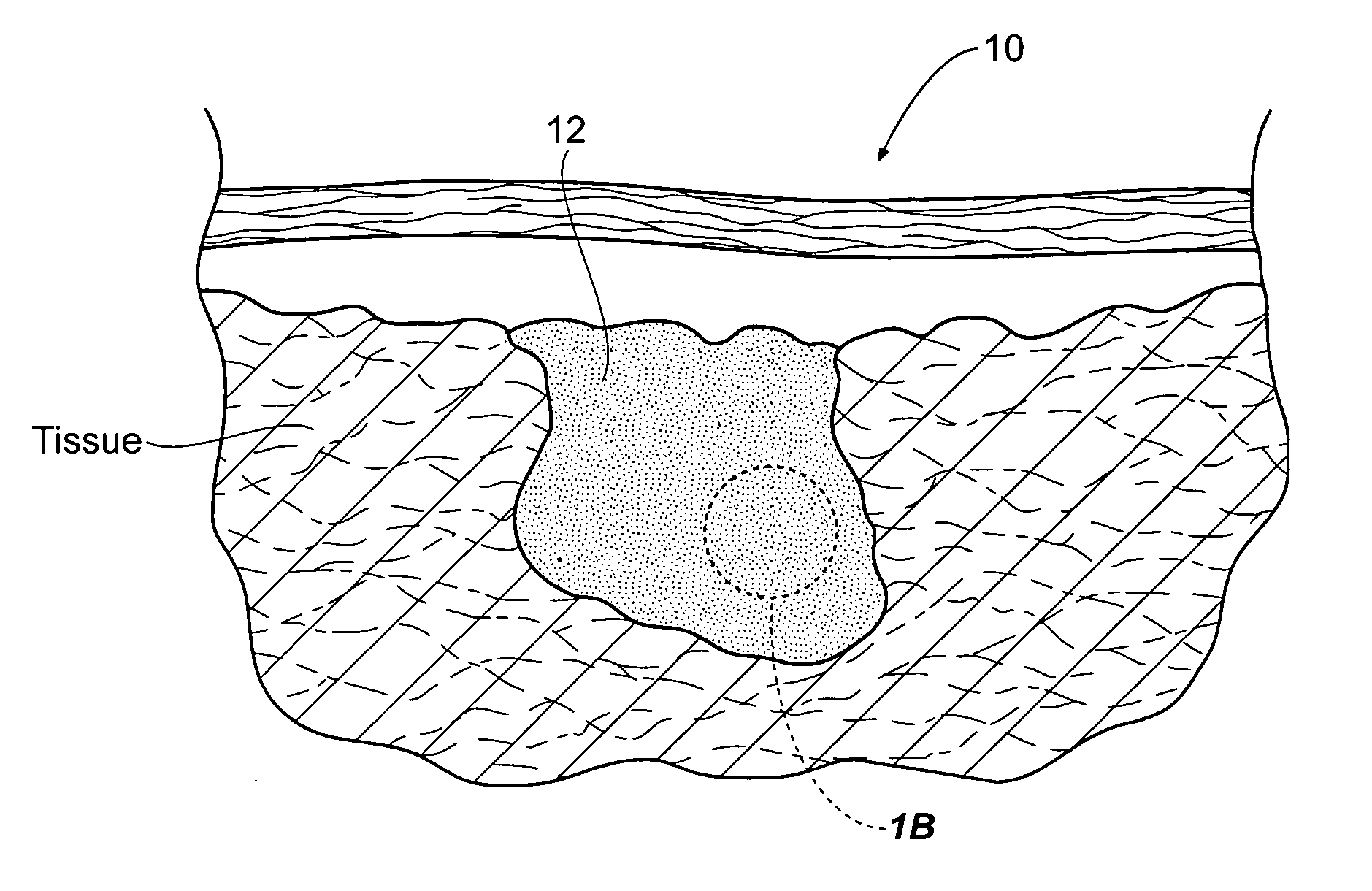
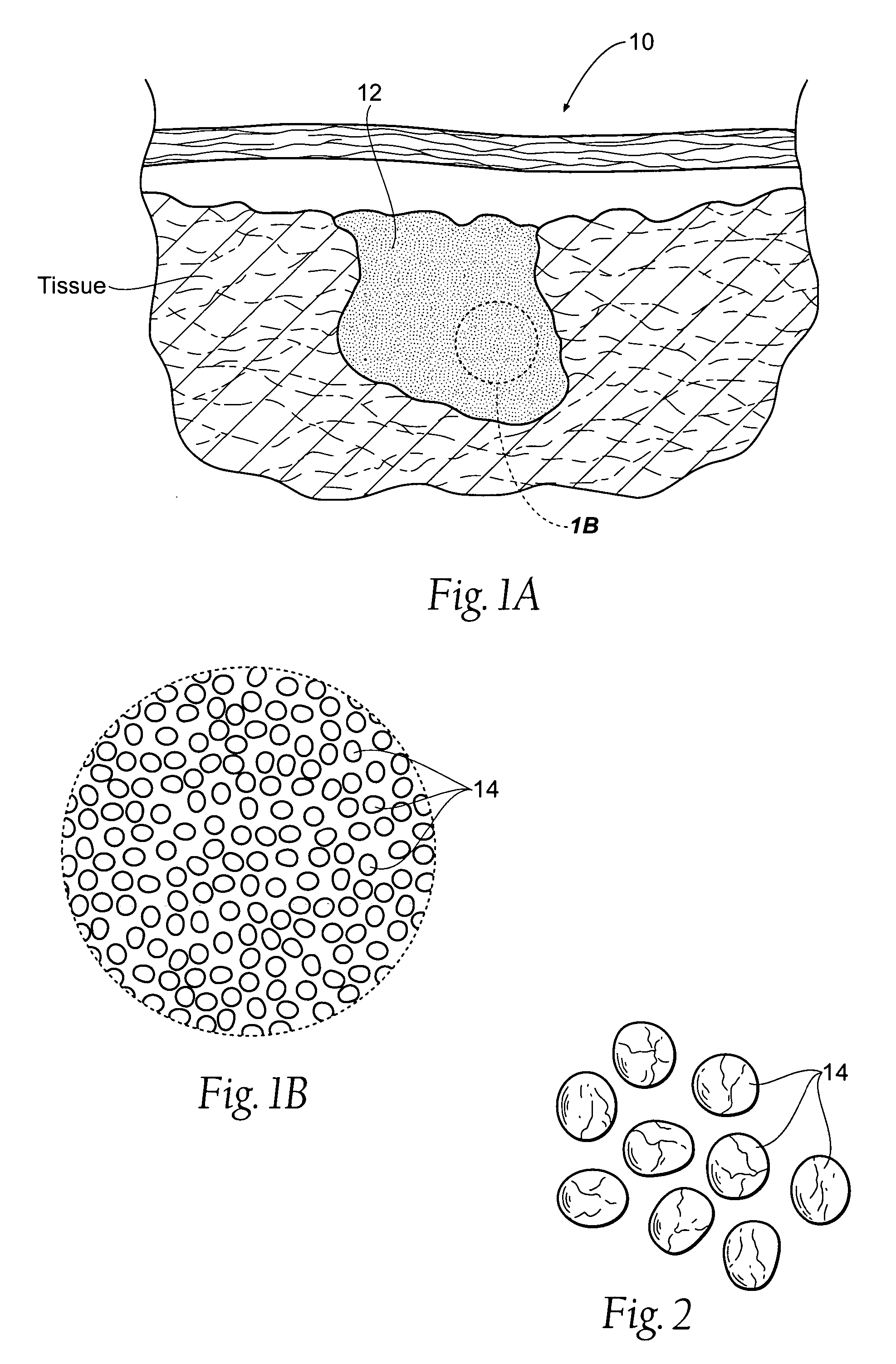
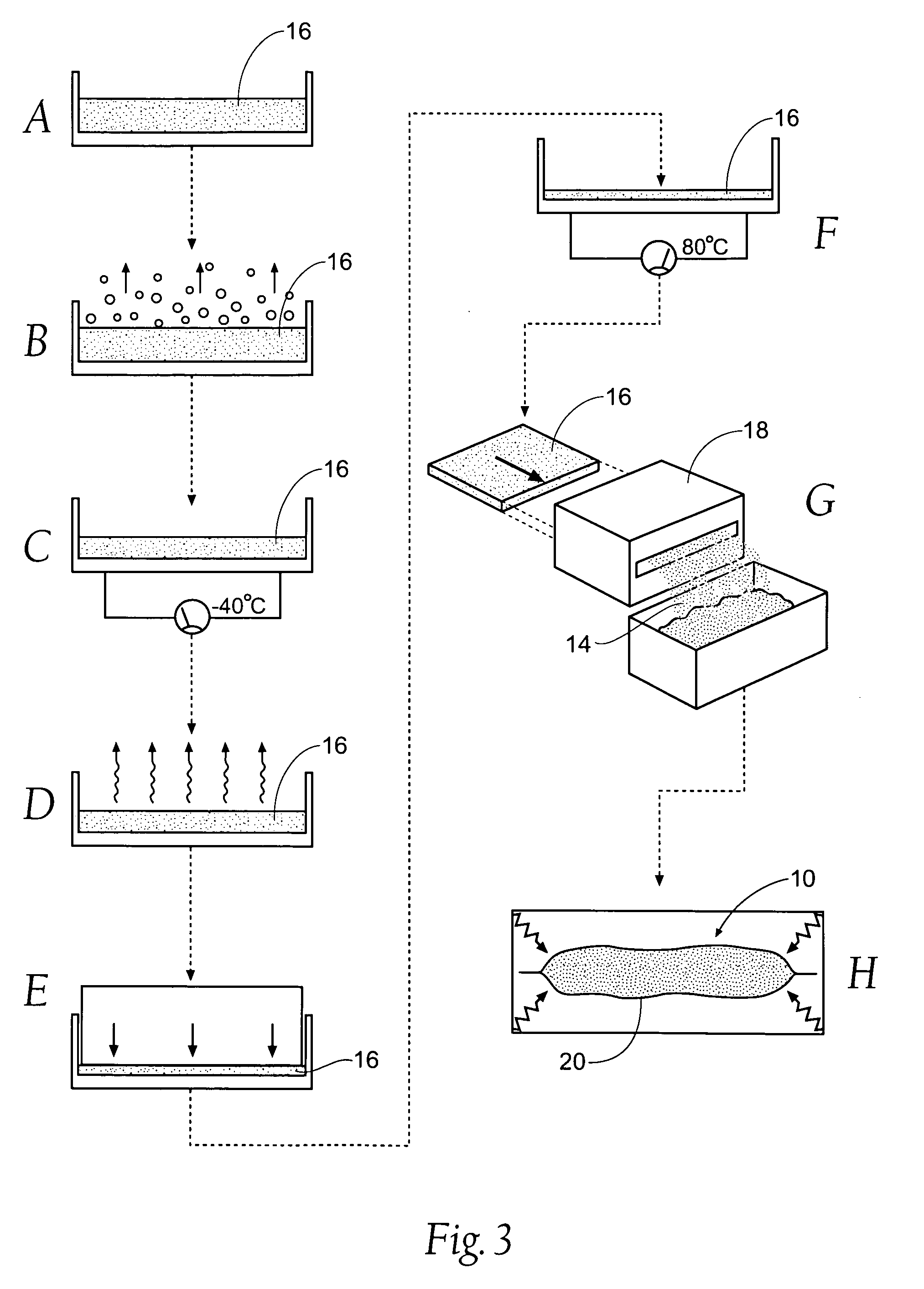
Hemostatic compositions, assemblies, systems, and methods employing particulate hemostatic agents formed from hydrophilic polymer foam such as chitosan
ActiveUS20070021703A1Safe and effective deliveryIncrease ratingsPharmaceutical delivery mechanismAbsorbent padsParticulatesPolymer
Improved hemostatic agents take the form of granules or particles that can be used to stanch, seal, or stabilize a site of hemorrhage, including a noncompressible hemorrhage.
Owner:TRICOL BIOMEDICAL INC
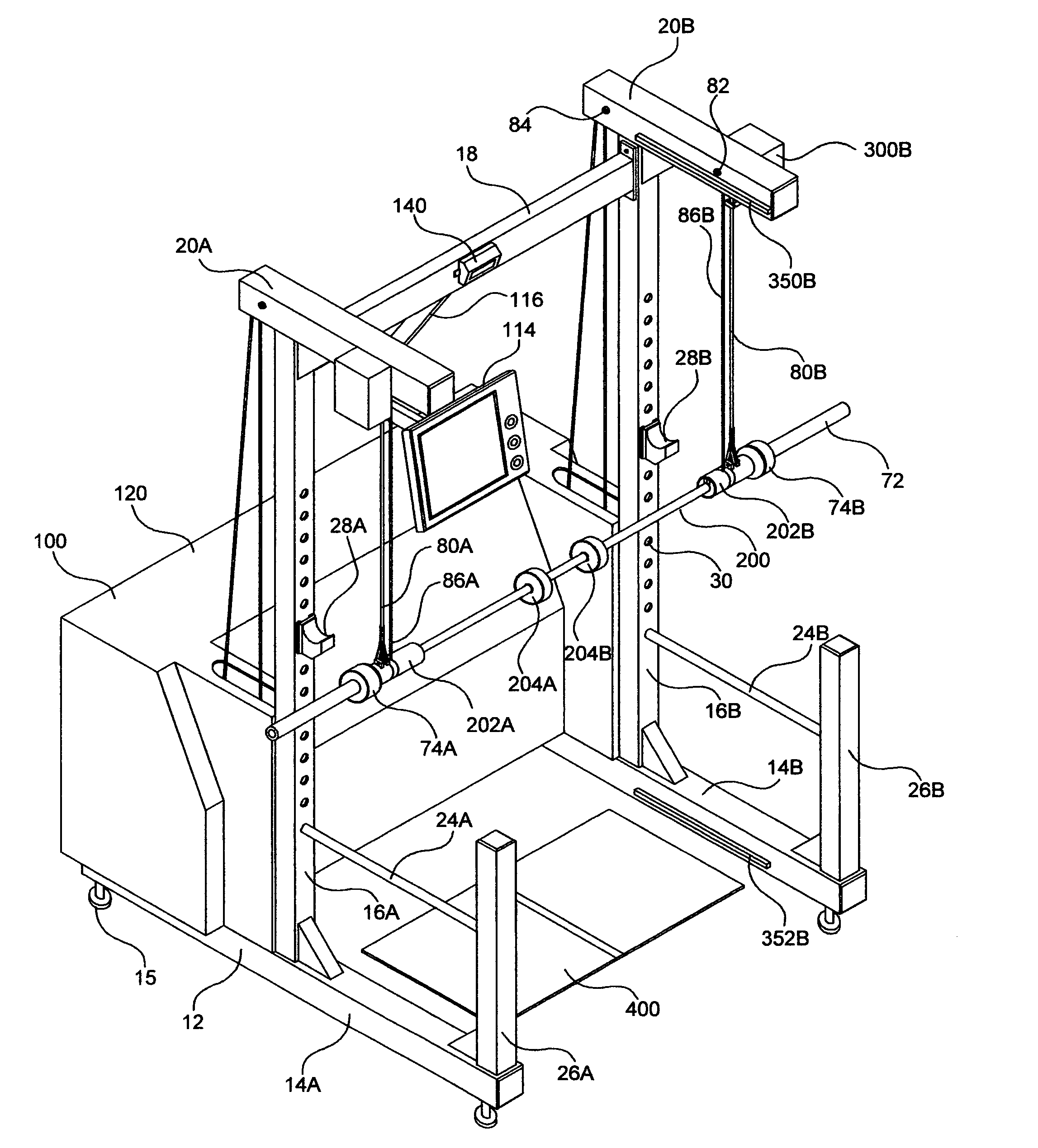
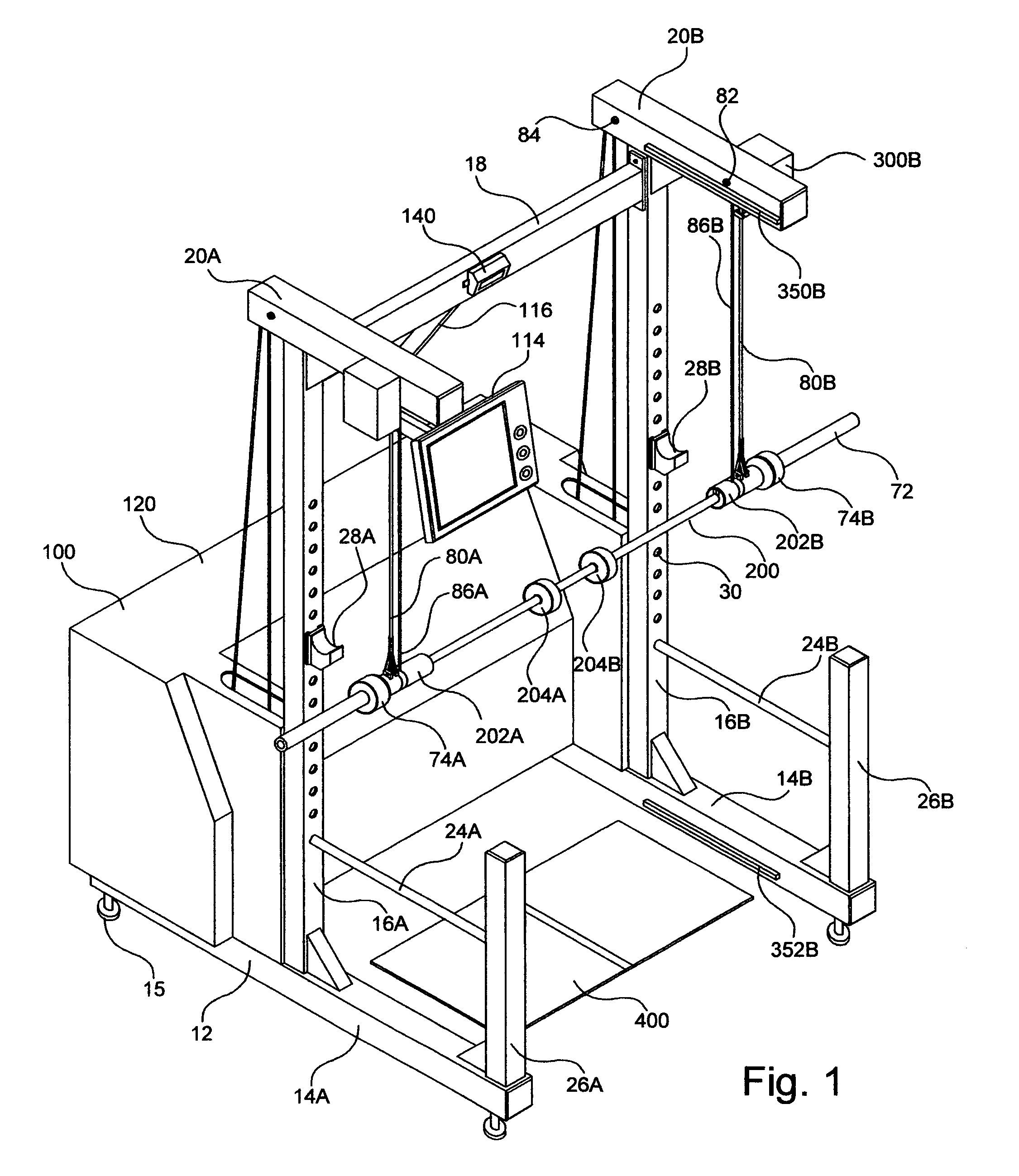
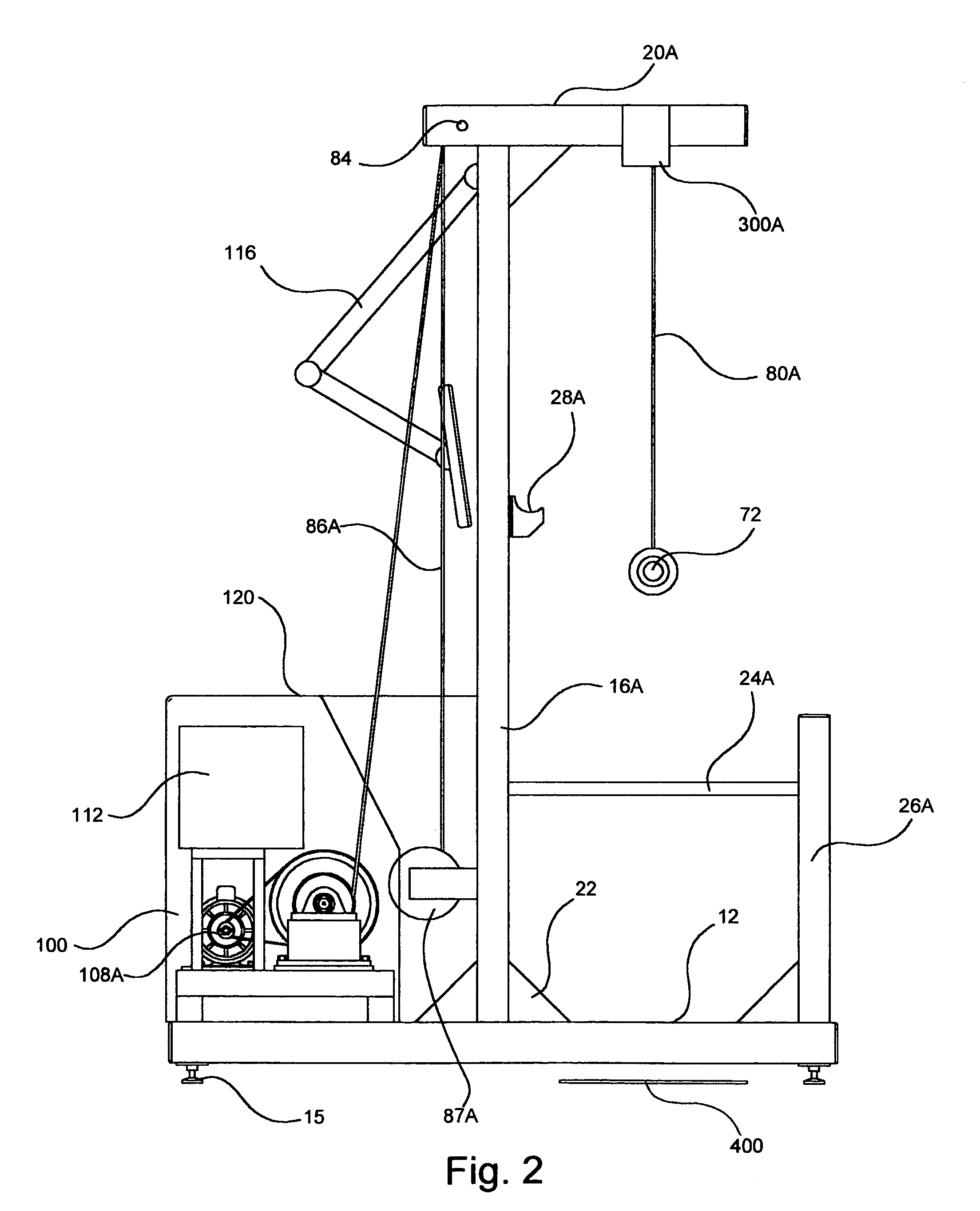
Free weight assistance and training device
ActiveUS7163488B2Reduce the amount requiredMinimize risk of injuryDumb-bellsEngineeringElectric cables
Owner:ANDERS DOUGLAS H +1
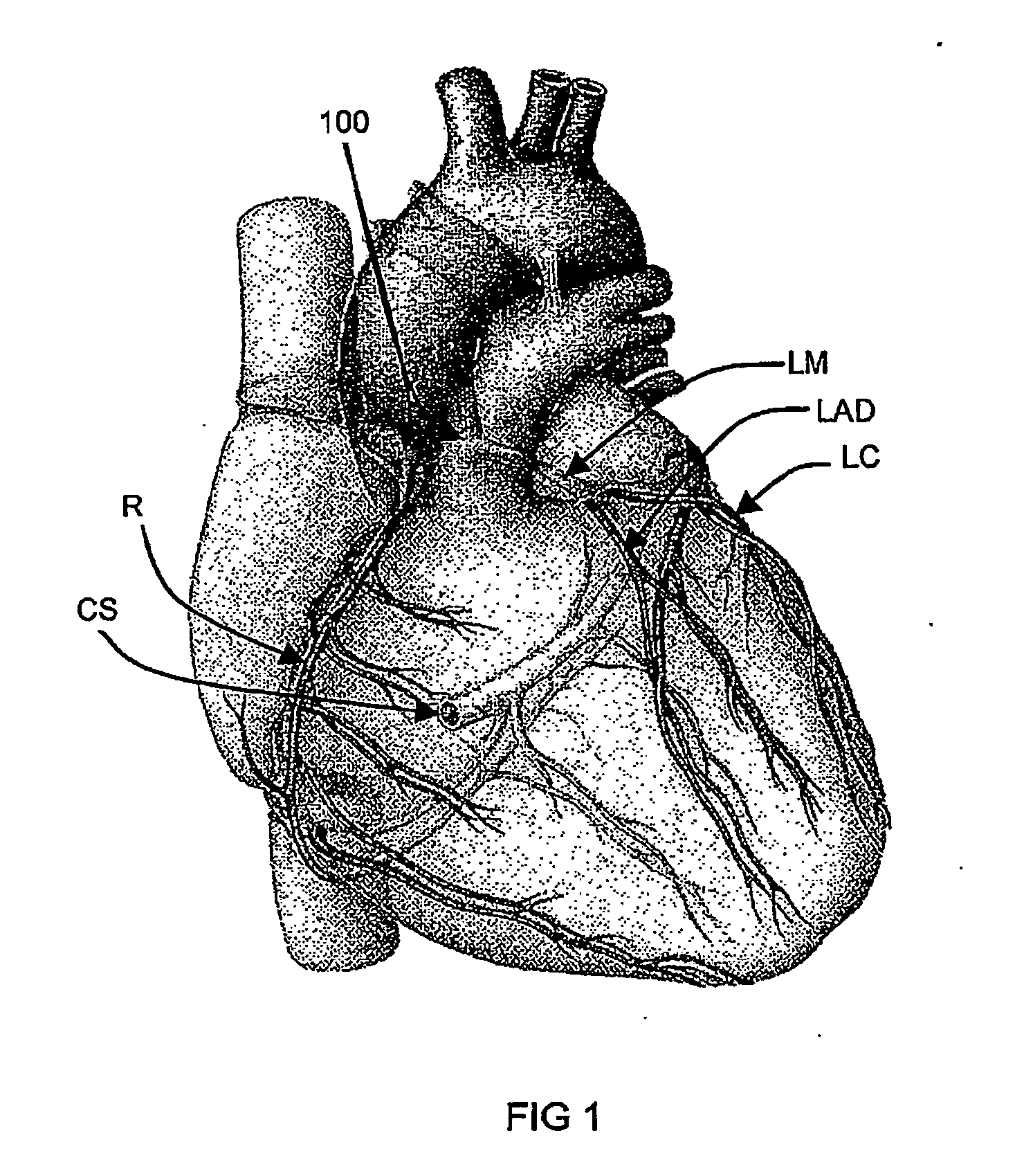
Polynucleotide delivery to cardiac tissue
InactiveUS20060148742A1Improve ejection fractionReduce probabilityVirusesBalloon catheterCoronary arteriesVein
A method for delivering a polynucleotide to cardiac tissue, including substantially isolating the coronary venous circulation from systemic circulation, and introducing a polynucleotide into the isolated coronary venous circulation to effect localized transfection of cardiac tissue. The polynucleotide advantageously produces a therapeutic effect, such as increasing or decreasing the expression level of a protein in the cardiac tissue.
Owner:OSPREY MEDICAL
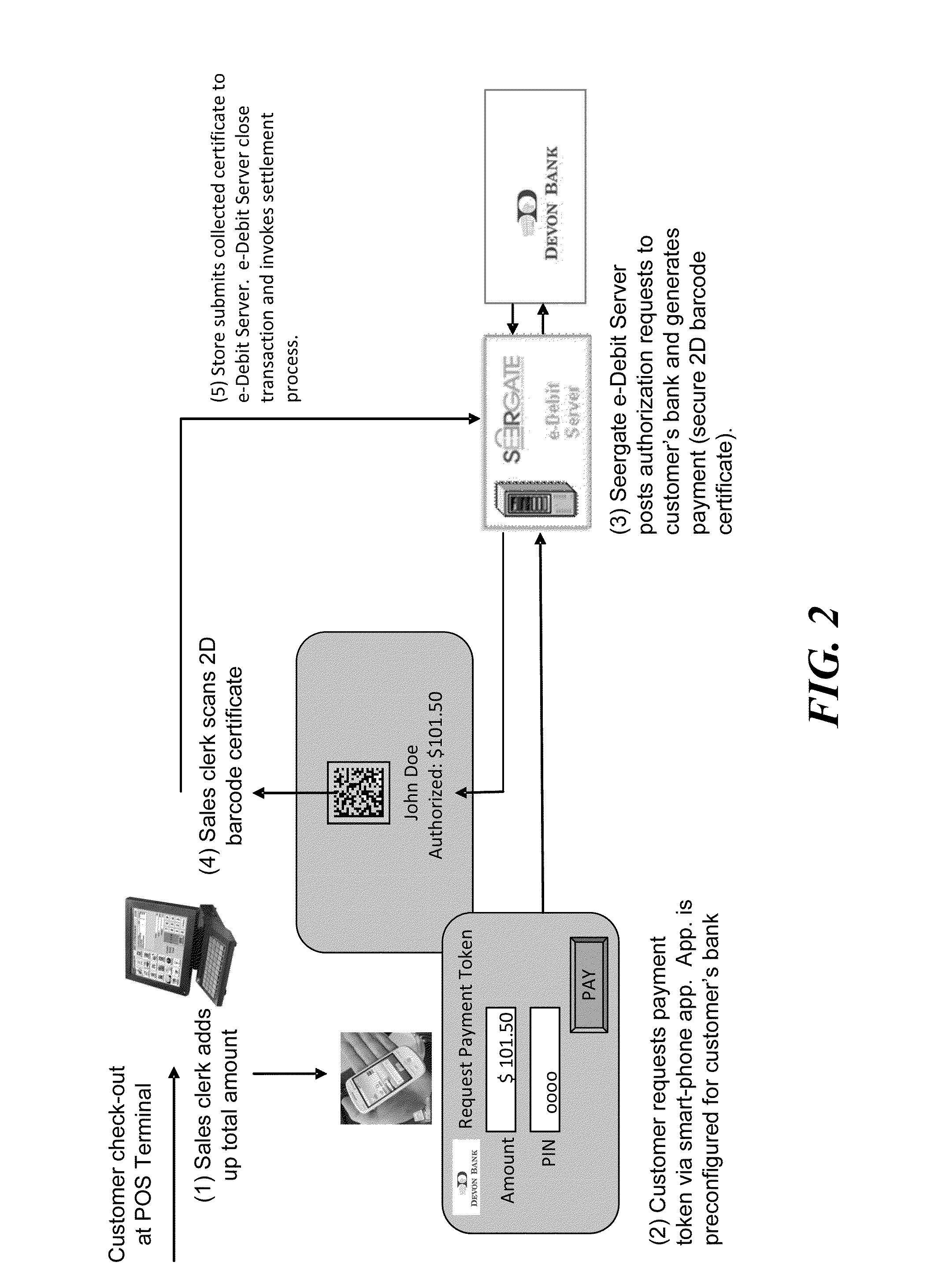
Point of Sale Payment System and Method
InactiveUS20110208600A1Improve securityIncrease flexibilityPoint-of-sale network systemsInvoicePayment system
A point of sale (POS) payment system does not require the payor to disclose confidential and sensitive financial information to the payee in order to settle the transaction. The payee presents the payor with an invoice or bill. The payor requests from their bank (or proxy for the bank) a payment token for a predefined sum and receives the payment token electronically, such as via smart phone or other portable device. The payment token is transferred to the payee as payment for the invoice. The payee stores the electronic payment token or the data associated therewith and submits the token to the payor bank (or proxy for the bank) to settle the transaction or invoke the settlement process.
Owner:SEERGATE
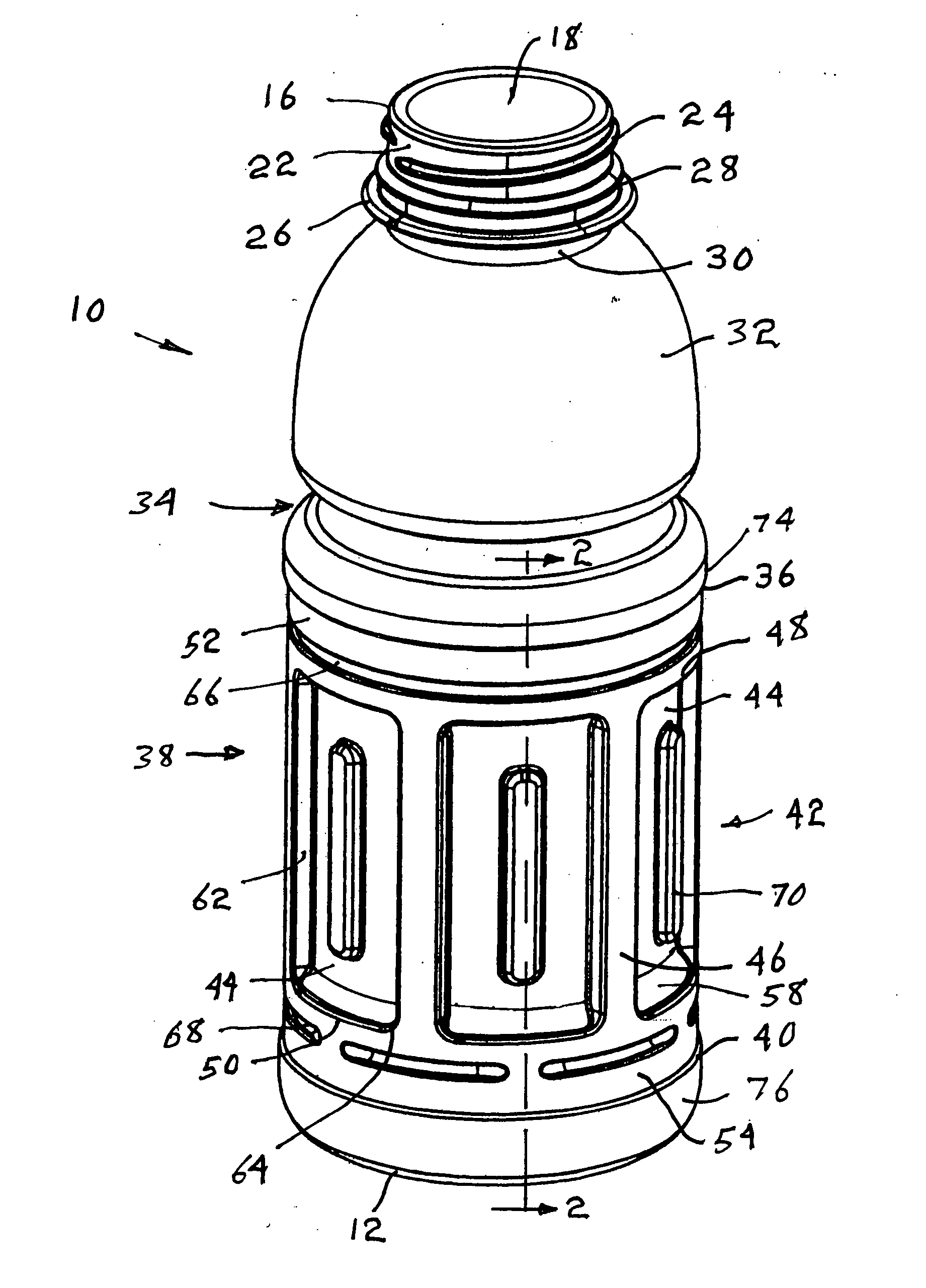
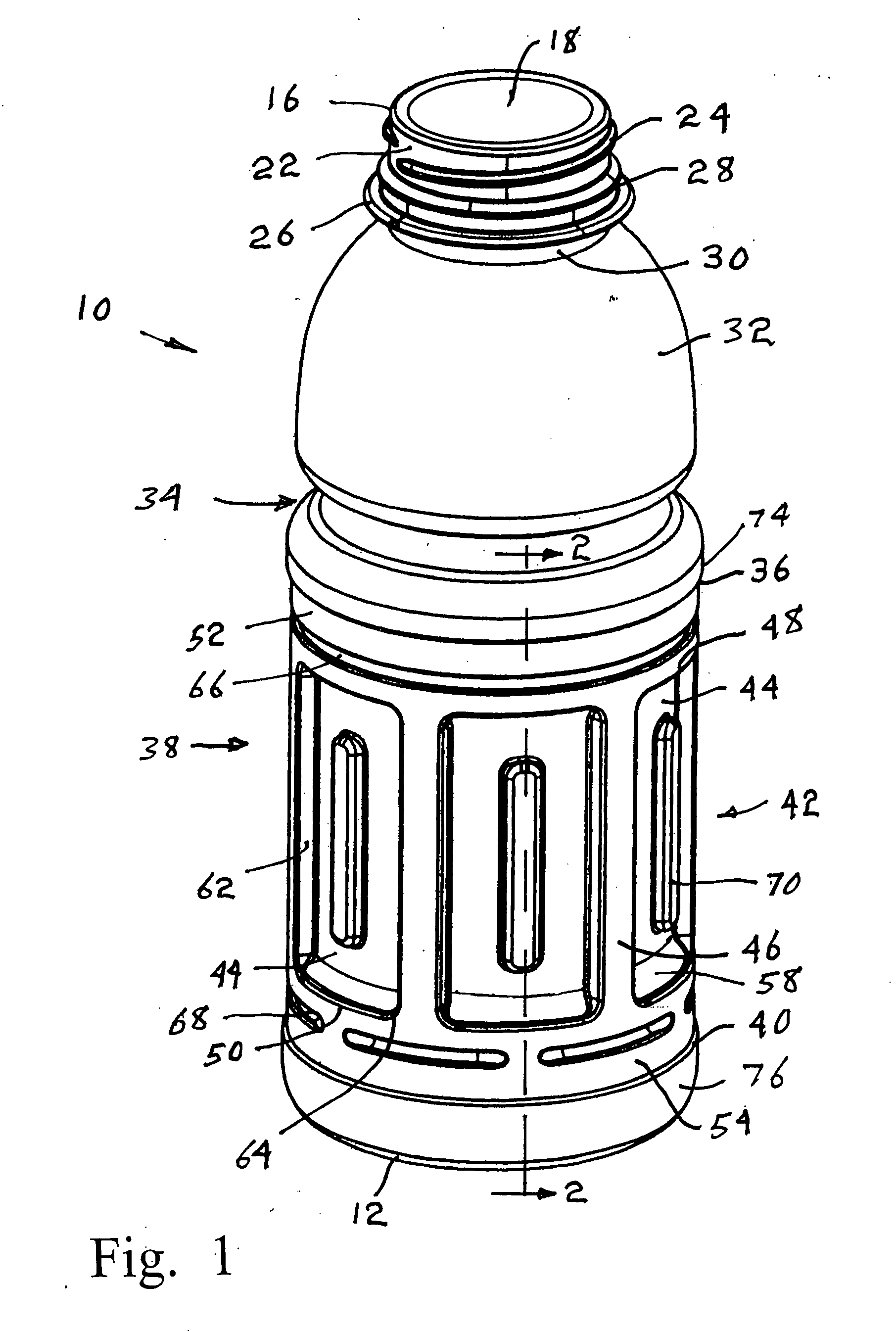
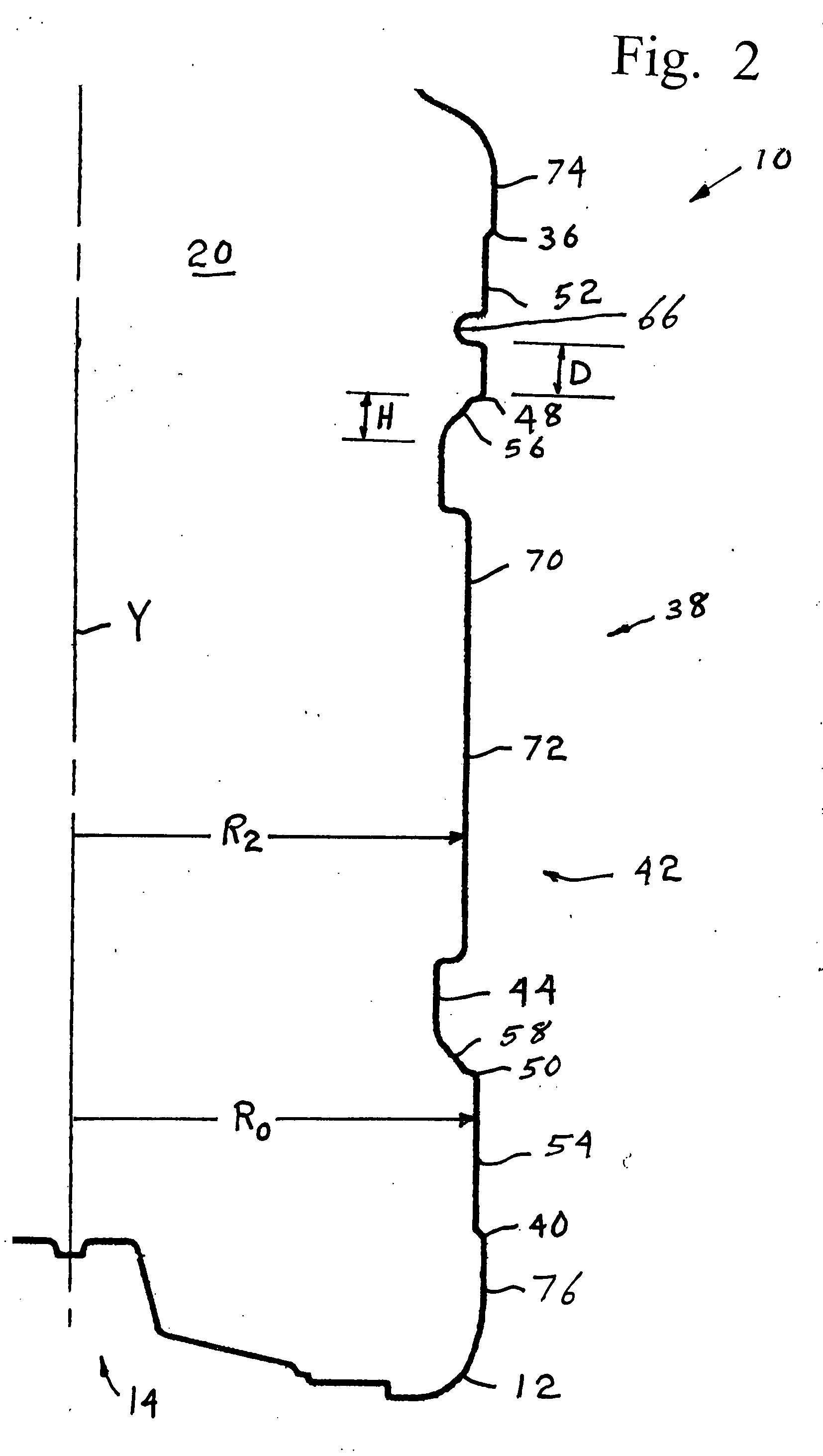
Hot fill container with restricted corner radius vacuum panels
InactiveUS20060186082A1Opportunities decreaseReduce impactLarge containersRigid containersLateral marginEngineering
A thin walled, plastic hot-fill container has a finish to receive a closure, a neck supporting the finish, a shoulder situated below the neck, a base, and a body between the shoulder and base. The body includes upper and lower margins defining a label mount area that includes a plurality of inwardly recessed vacuum panels separated by vertical posts. At least one indented reinforcing ring separates the upper and lower edges of the vacuum panels from the adjacent margins of the label mount area by a distance D. Each vacuum panel includes an inclined upper and lower margin of height H that is greater than distance D, and has corners defined by radius R, which is less than or equal to D. Lateral margins of each vacuum panel extend vertically between the corners and connect the adjacent posts to a central depressed region, each lateral margin being essentially perpendicular to the adjacent surface of the vacuum panel.
Owner:BALL CORP
Radiofrequency ablation with independently controllable ground pad conductors
ActiveUS20070049919A1Opportunities decreaseReducing maximum power outputSurgical needlesSurgical instruments for heatingRadiofrequency ablationElectrical conductor
A radiofrequency ablation system provides multiple ground pads and active control of current flow through the ground pads to provide improved power sharing at the tissue near the ground pads reducing risk of patient skin burns for higher power ablation generators.
Owner:WISCONSIN ALUMNI RES FOUND
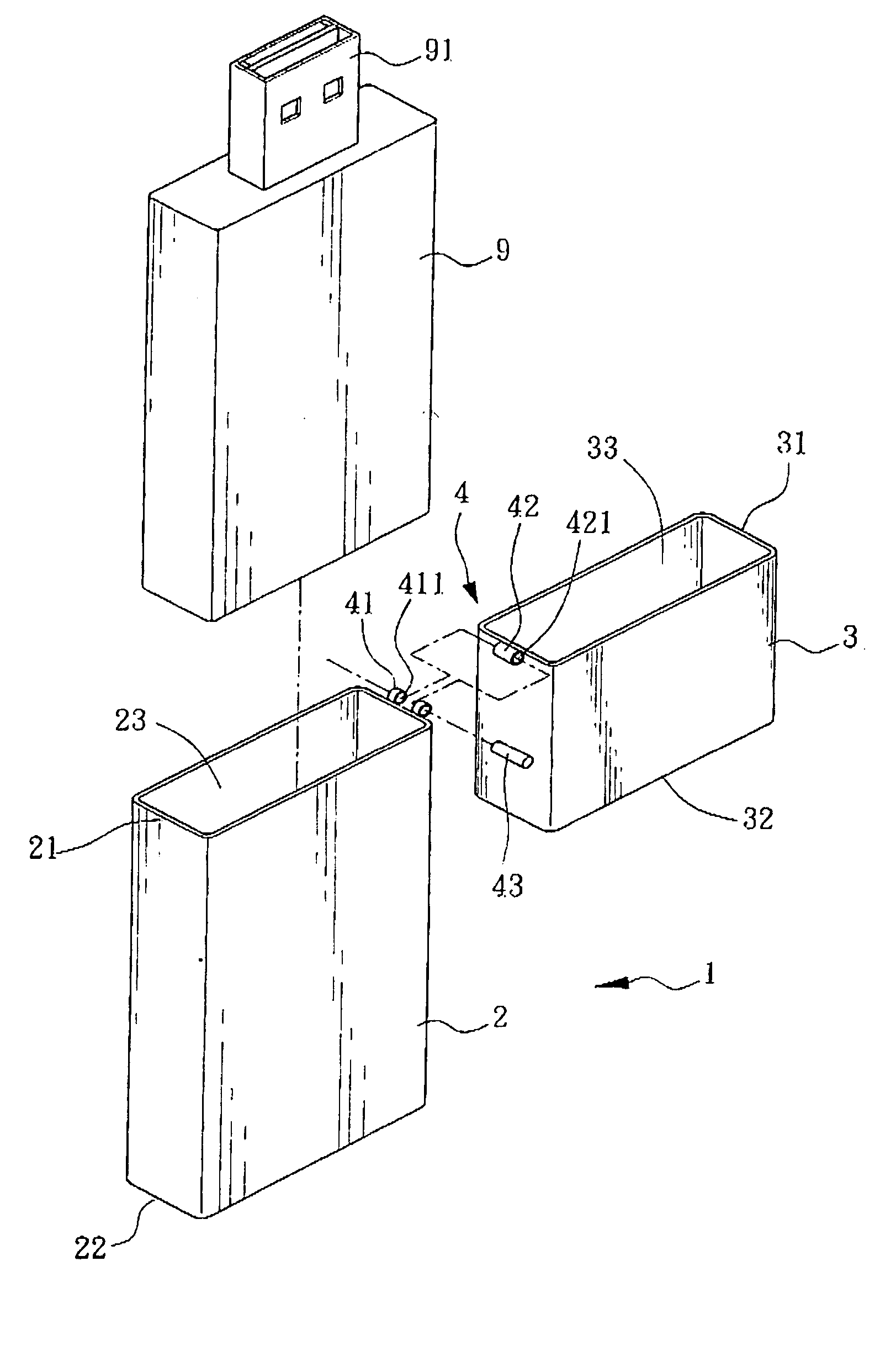
Portable media-accessing device
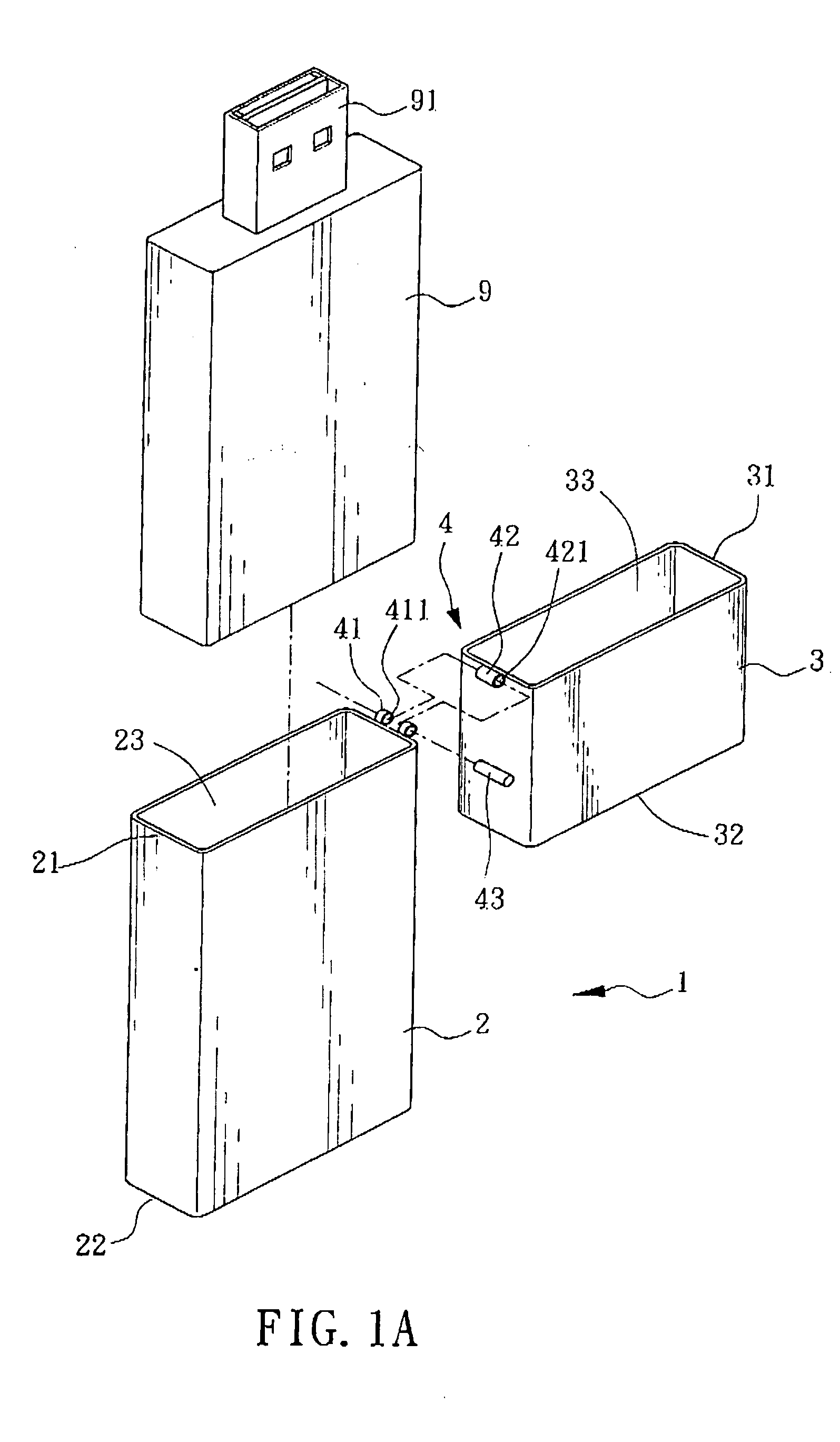
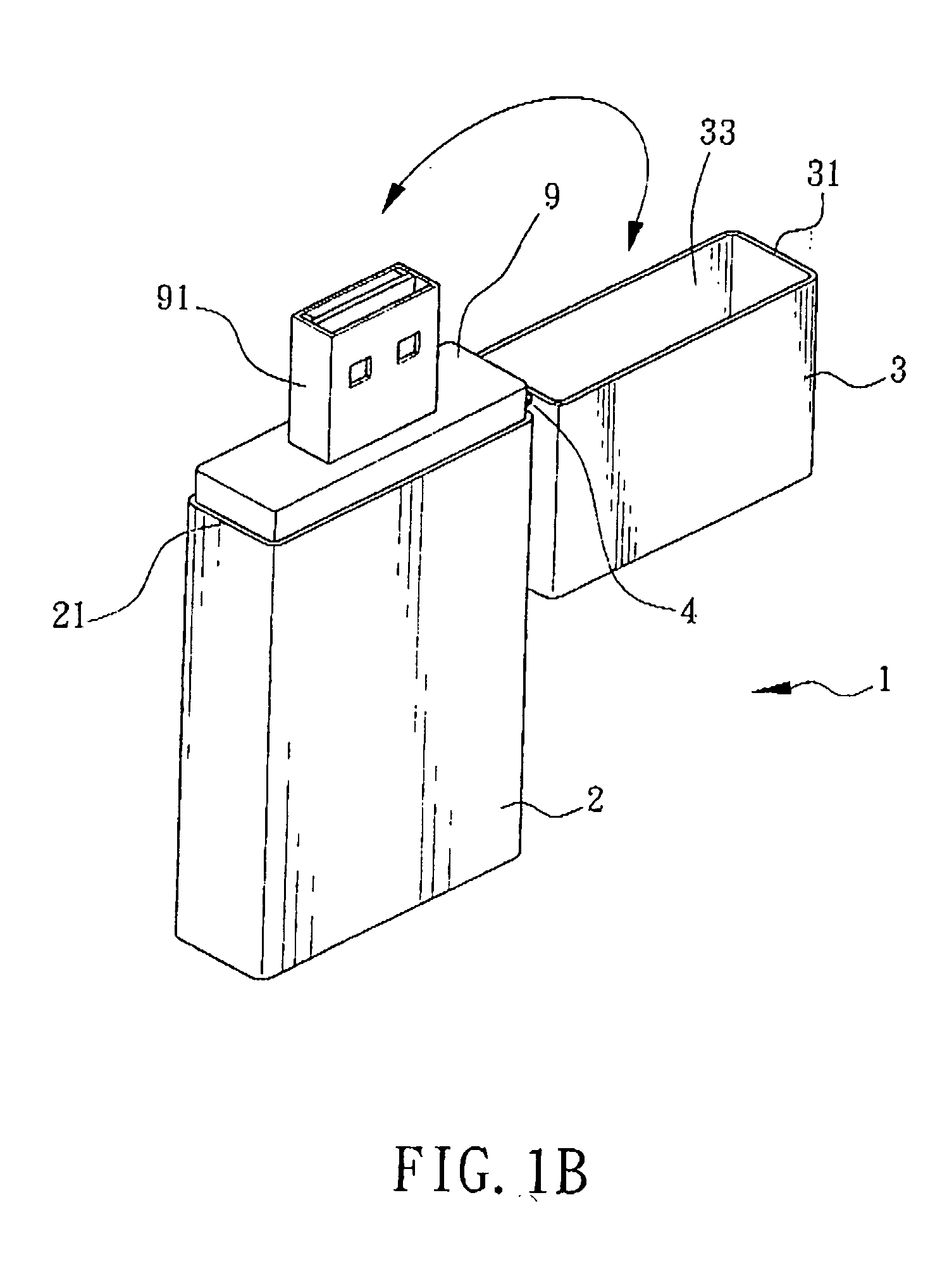
InactiveUS20050029137A1Opportunities decreaseFunction increaseCoupling device detailsOther accessoriesBiomedical engineeringMedia access
The invention is mainly to provide a portable media-accessing device, which includes a body, an upper lid, and at least one pivotal part. The body has a hollow casing having an opening side communicating to a first accommodation space; the first opening side may provide a memory module to be placed into the first accommodation space; the upper lid has a hollow casing having a second opening side communicating to a second accommodation space; the pivotal part may make the body connected to the upper lid such that, by taking the pivotal part as an axial center, a rotation motion with an appropriate angle between the upper lid and the body is possible.
Owner:BENQ CORP
Password-less security and protection of online digital assets
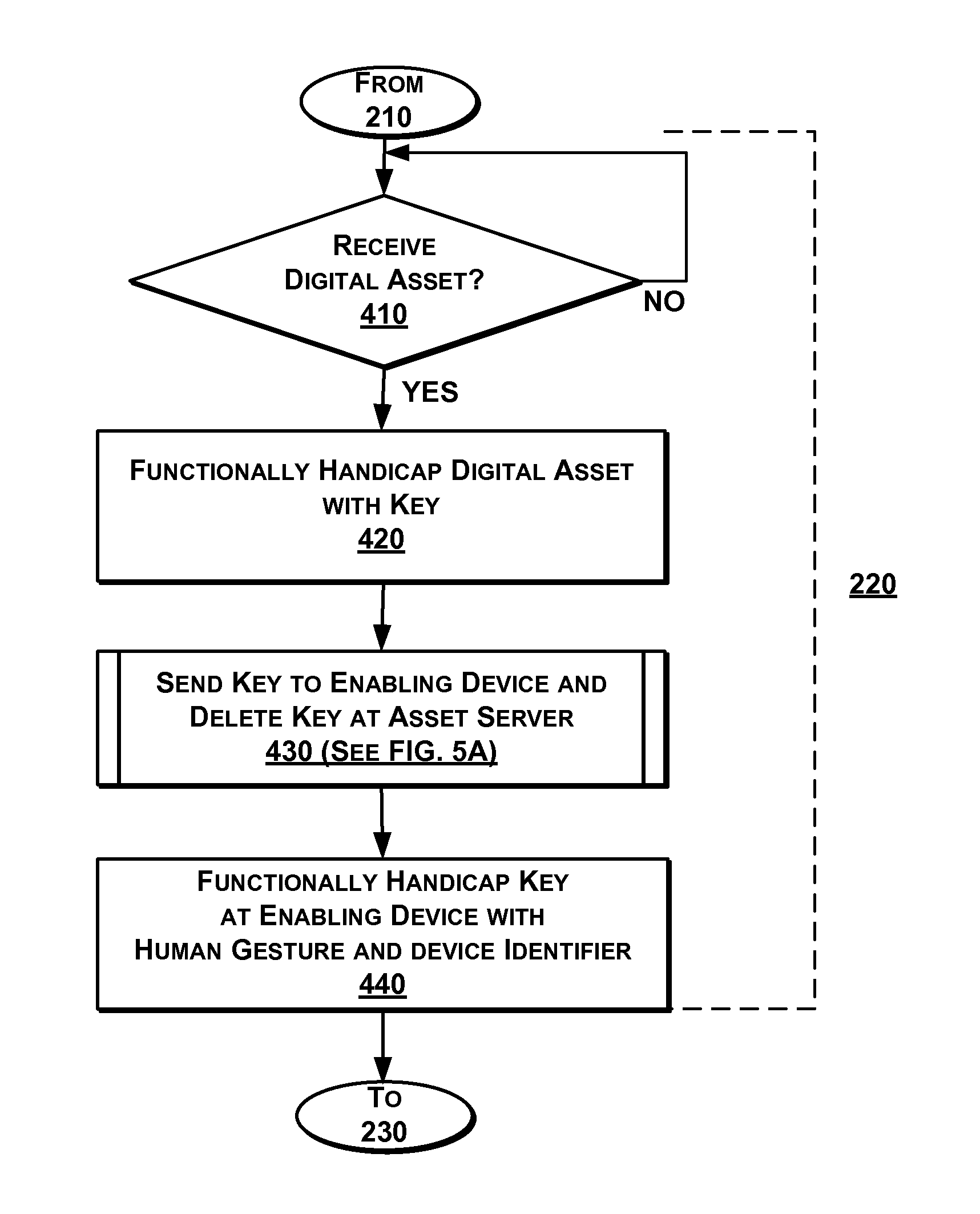
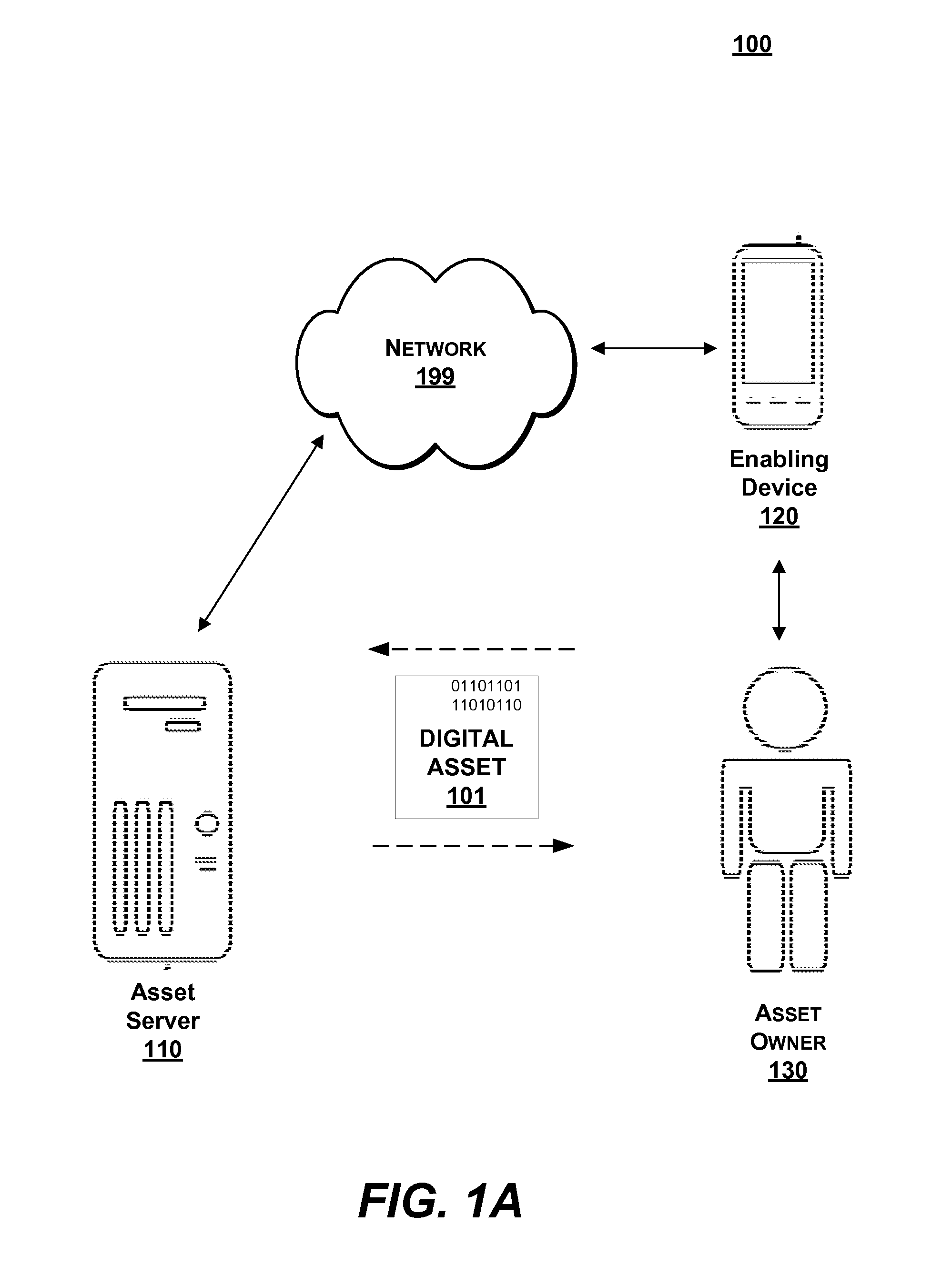
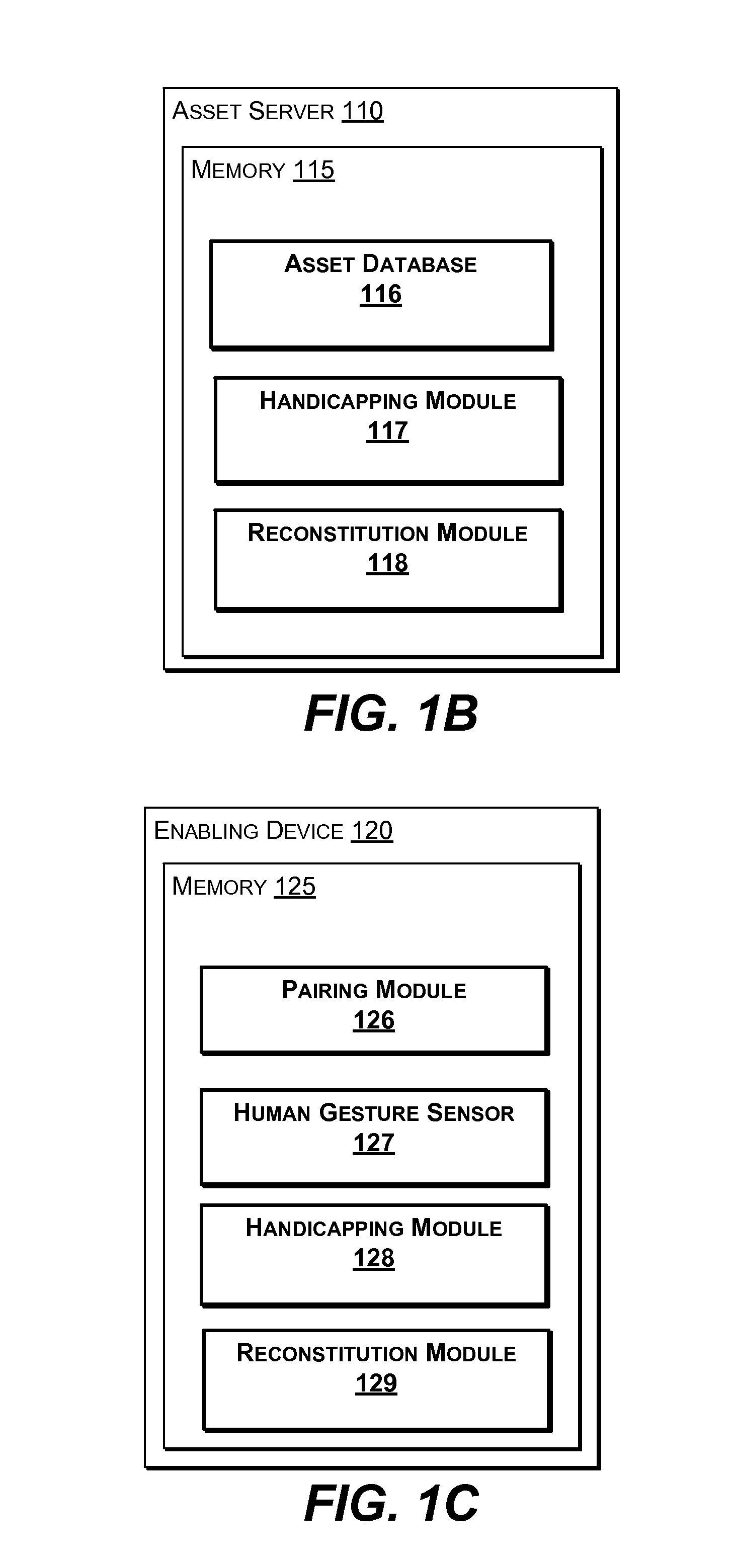
ActiveUS20130159732A1Reduce opportunityOpportunities decreaseDigital data processing detailsUnauthorized memory use protectionDigital assetDigital data
Digital assets stored on an asset server by an asset owner are protected without a password. Instead, the digital assets are functionally handicapped by removing at least a portion of digital data (or a key) associated with the digital asset and discarding the key after being sent to an enabling device. The portion of digital data (or a key) is then handicapped by the enabling device by a cryptographic key which is formed from a human gesture and subsequently discarded. When access to the digital asset is requested, an asset owner is notified by the enabling device for approval. A human gesture from the asset owner first provides a key to reconstitute the digital data portion which is transmitted to the asset server to reconstitute the digital asset upon which the access is granted and logged.
Owner:LEOUTSARAKOS NICOLAS
Implantable lead with isolated contact coupling
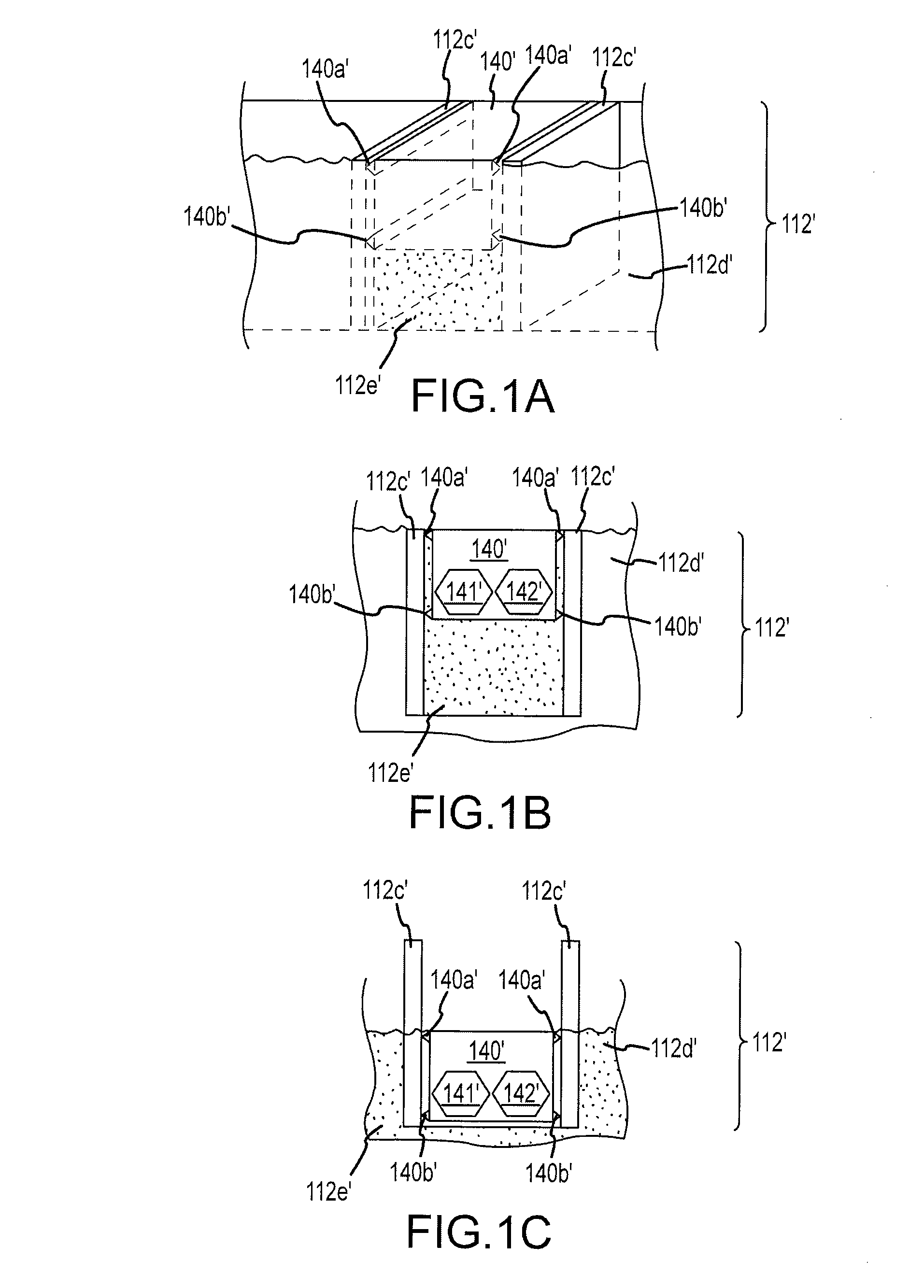
InactiveUS7184840B2Opportunities decreaseSoldered/welded conductive connectionsInternal electrodesEngineeringBiomedical engineering
An implantable lead for a medical device with an isolated contact connection for connecting a conductor to a contact reduces the opportunity for conductor material to migrate to a contact or into a patient. The implantable lead comprises a lead body having a proximal end and a distal end, at least one conductor, at least one contact carried on the proximal end, at least one contact carried on the distal end, at least one coupling. The lead has an exterior surface. The conductor is contained in the lead body and extends from the lead proximal end to the distal end. The conductor is electrically insulated. The contact carried on the proximal end is electrically connected to the conductor. The coupling has a conductor coupling and a contact coupling. The conductor coupling is placed over the conductor and attached to the conductor. The contact coupling exits the lead body and has a weld to connect the contact coupling to the contact. There is an isolation space created between the conductor and the contact to prevent the weld from containing conductor material.
Owner:MEDTRONIC INC
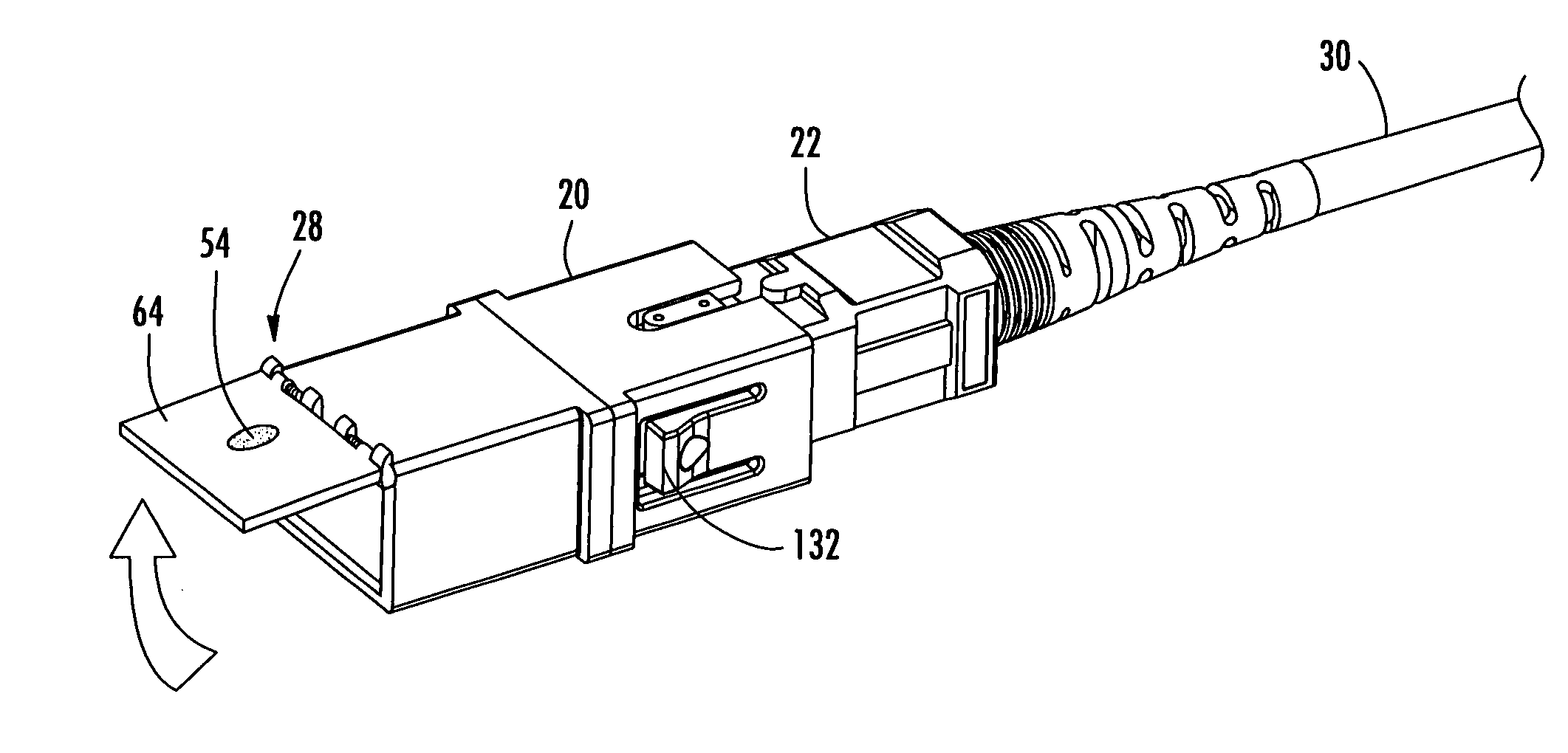
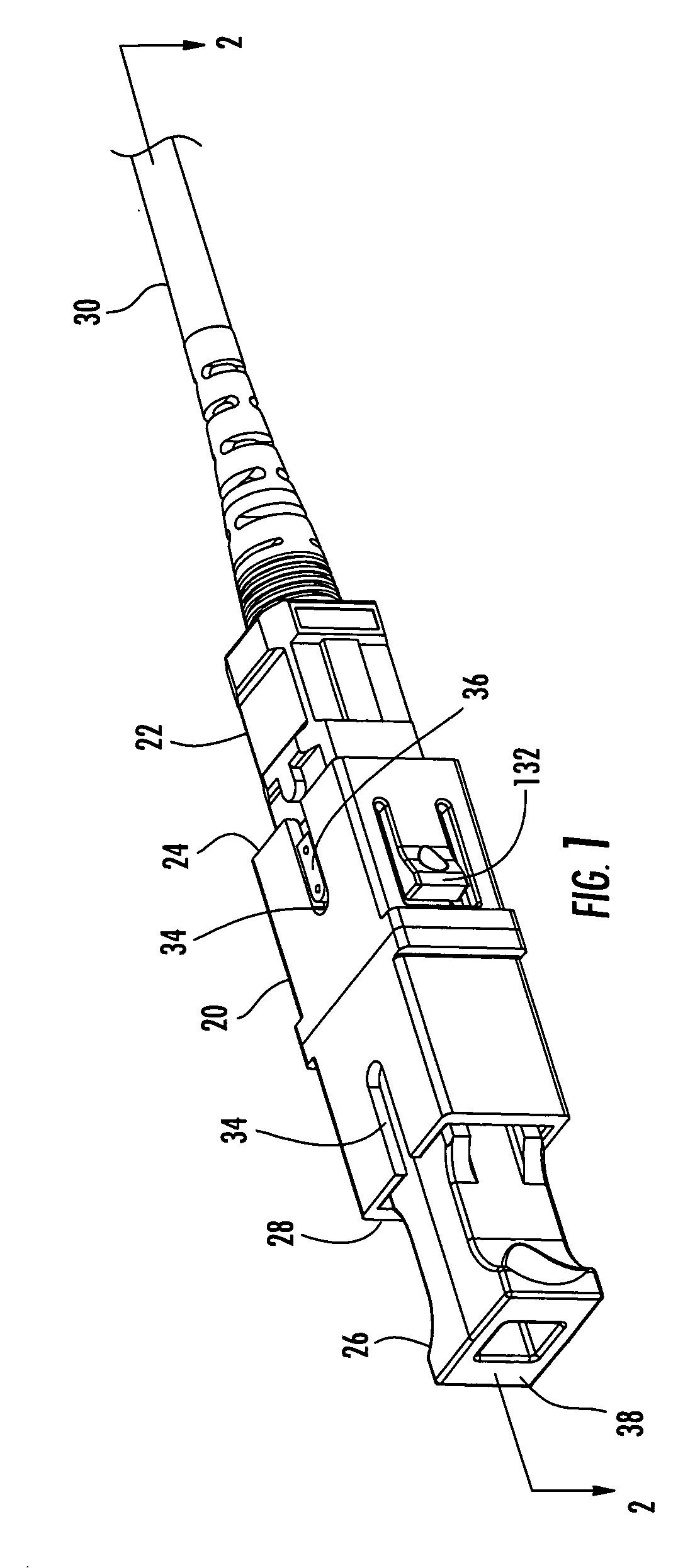
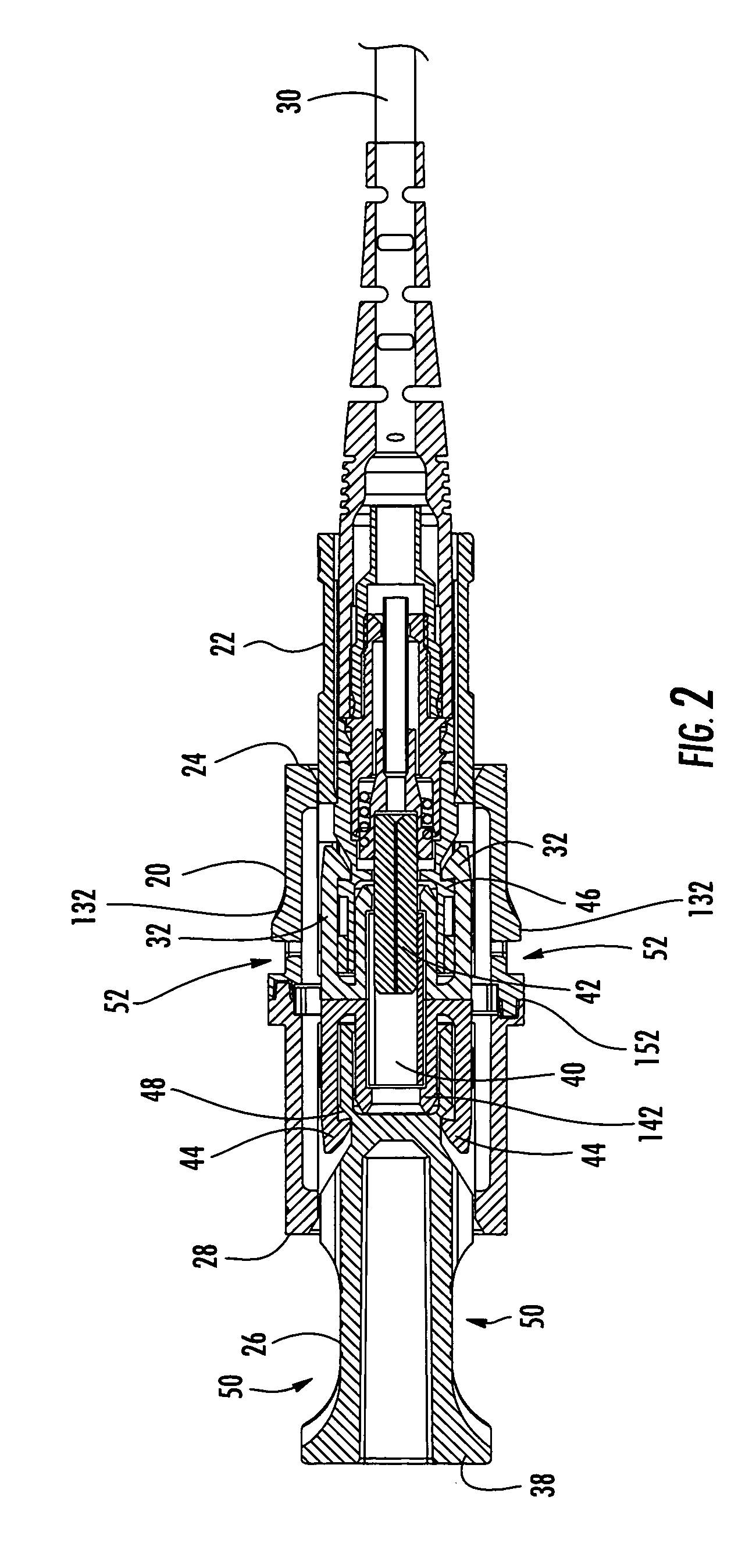
Translucent dust cap for fiber optic adapter
ActiveUS20070217749A1Prevent eye damageGood sealCoupling light guidesOptical fiber connectorEngineering
A translucent dust cap for a fiber optic adapter allows the viewing of visible light emanating from a fiber optic connector coupled to the adapter, without removing the dust cap. A translucent dust cap for a fiber optic adapter that serves to diffuse a visible light source of sufficient power, such as that from a VFL, and lights up to aid in connector identification. A translucent dust cap for a fiber optic adapter that serves to attenuate infrared optical transmission power to prevent eye damage.
Owner:CORNING OPTICAL COMM LLC
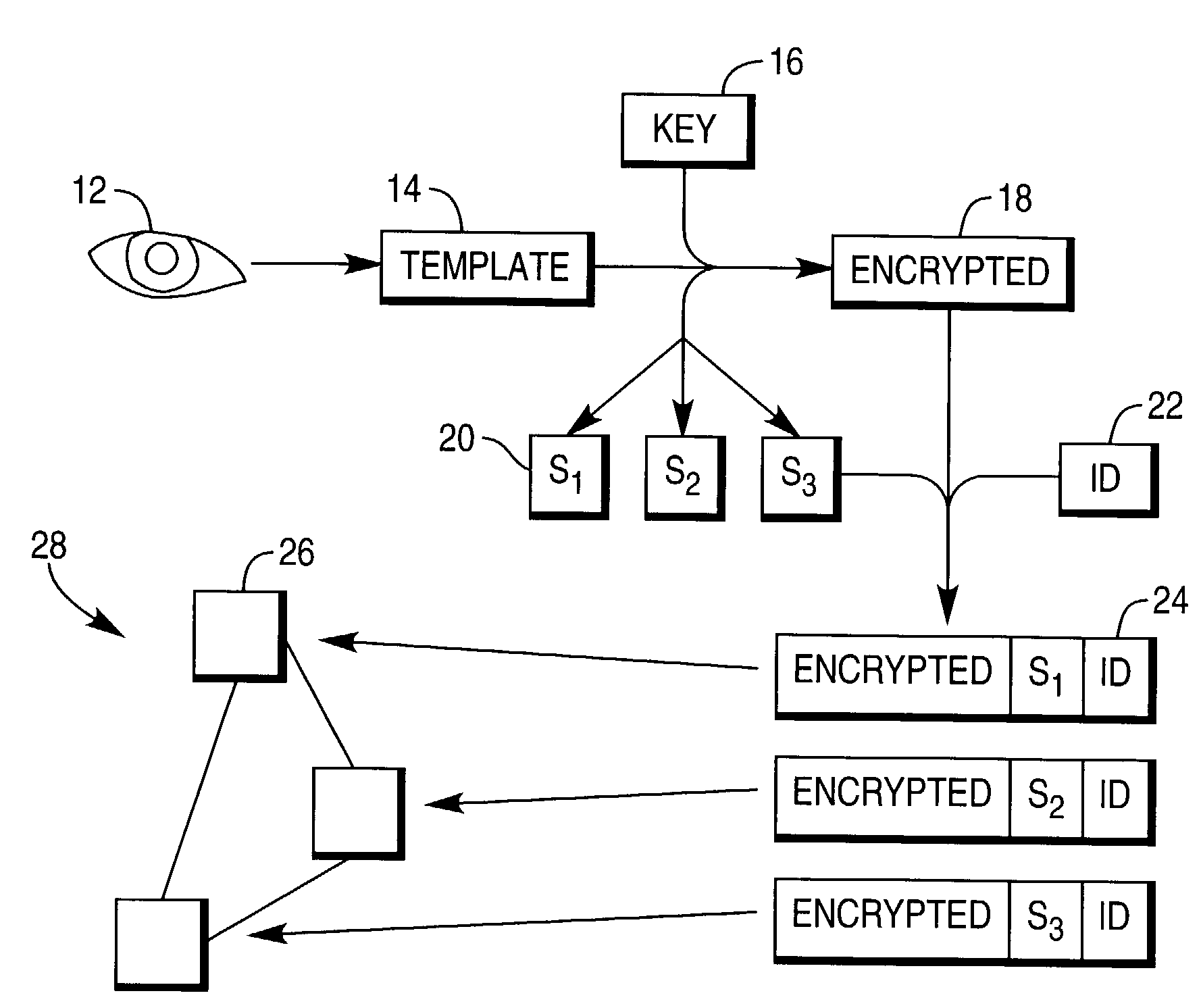
Biometrics template
ActiveUS7302583B2Reduce riskReassured of securityKey distribution for secure communicationDigital data processing detailsPresent methodUser identifier
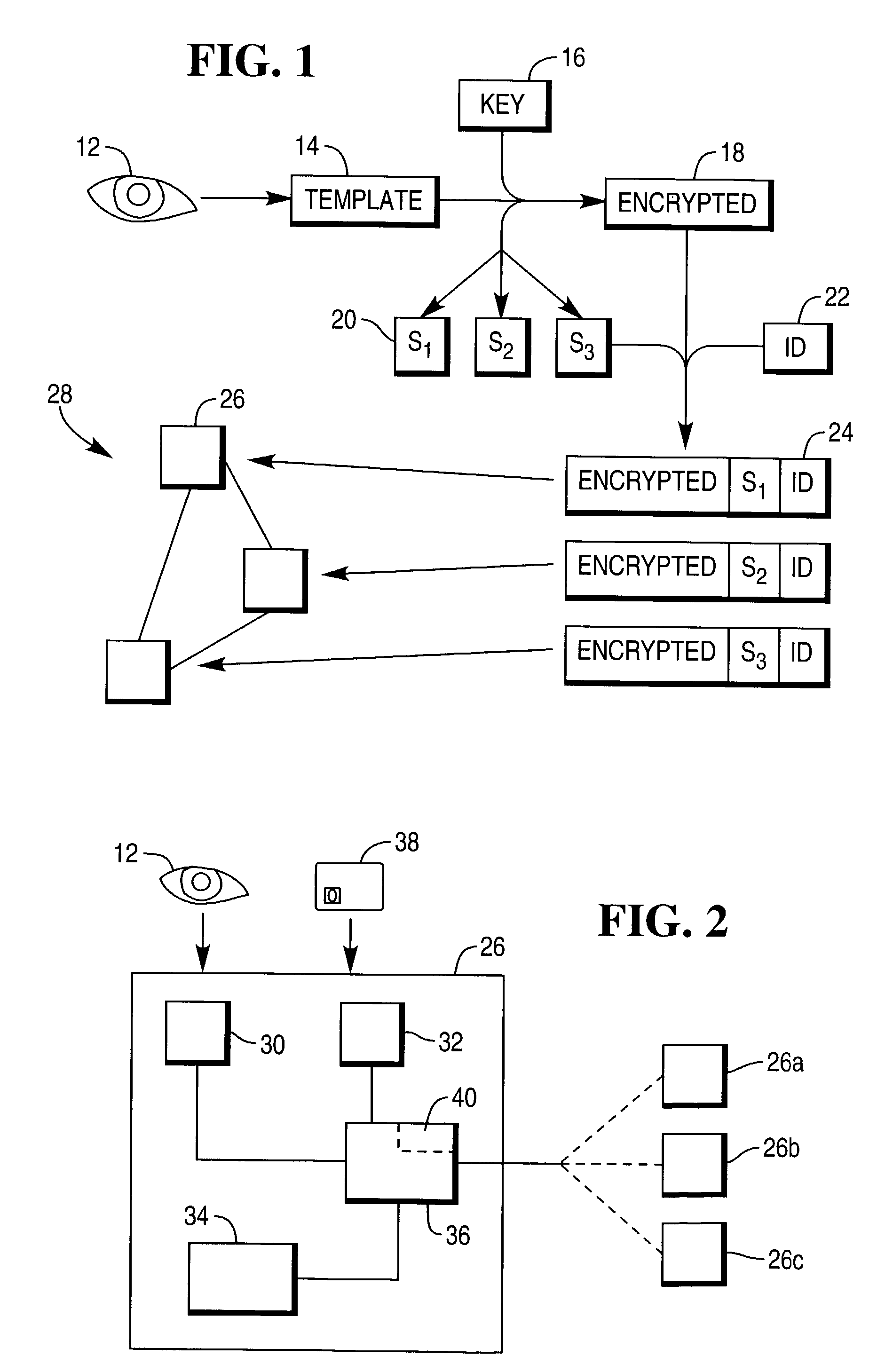
Methods of storing and decrypting biometrics templates on a terminal network are described. A biometrics template 14 is encrypted 18 using a key 16, and the key 16 is then divided into a number of key shares 20. The encrypted template 18, a key share 20, and a user identifier 22 are then combined to give an identification string 24. A number of strings 24 are then stored on separate terminals 26 of a terminal network 28. To decrypt the template 14, a user offers their identifier 22 to a terminal 26. The required number of identification strings 24 having that identifier 22 are retrieved from their respective terminals 26 on the network 28, and the key shares 20 combined to generate a key 16 which is then used to decrypt the template 14. The decrypted template 14 may then be used to verify the identity of the user. Using the present method, neither the unencrypted template nor the complete decryption key are transferred across the network, so improving security.
Owner:NCR CORP +1
Harvesting hydrocarbons and water from methane hydrate deposits and shale seams
InactiveUS20100006281A1Low extraction temperatureLess waterConstructionsMultiple-effect/fractional condensationNoble gasKerosene
A method of extraction of fuels, organic pollutants, and elements from Methane hydrate deposits, shale seams and the soil is described which freezes the zone and heats the center carrying the fuel, chemicals and water in these deposits and seams from where they are found, be it deep in the sea or on land, and carries them into the condensing unit in inert Nitrogen gas. Required drilling on the surface or sea bottom includes a main shaft and with auxiliary narrow drillings widely spaced from the shaft. The extraction zone, which is first cooled to brittle cold using the evaporation of Liquid Nitrogen and fractured with vibrations, is heated to the highest temperature of the hydrocarbon fraction desired to be extracted. The evaporating hydrocarbons are extracted in a Nitrogen gas carrier, a recognized fire suppressant (NFPA Code 2000). To speed the extraction rate, tonal input from two or more sounding units vibrates the seam structure freeing the evaporated hydrocarbons allowing more rapid escape into the shaft. To prevent air loss in aquifers, ice barriers seal the zone periphery. These hydrocarbons are separated into the hydrocarbons fractions, into fuel fractions as heating oil, kerosene, gasoline, ethers, and fuel gas including methane, Argon / Oxygen and rare gas segments, or, if pollutants, into the separate chemicals by boiling point. The thermal gradient of the extraction pipe is implemented by sourcing the Nitrogen from Liquid Nitrogen and bundling those pipes with the extraction pipe condensing its contents by hydrocarbon fractions into vessels and gas drums depending on boiling points of fractions. Water is separated from the gasoline segment and purified first by separation and then by freezing. The extraction of deep deposits layer the extraction zones as well as work neighboring extraction zones covering many acres. Fuel gases can be liquefied or burned in an on-site electric generating plant.
Owner:AIR WARS DEFENSE
Systems and methods for interactive digital data collection
InactiveUS20160283676A1Accurate collectionAccurately aggregatedFinanceComputer-assisted medical data acquisitionDigital dataTouchscreen
The present invention relates to a system and method for a digital data collection software in which a handheld electronic device collects and integrates one or more forms of data for outcome reporting. The various modules within the software can provide a patient-friendly and / or physician-friendly user interface for collecting various forms of data. The data collection templates, standardized reports and surveys can comprise consecutive predefined or custom questions or checklists, where the answers may be entered by using touch screen features, nested in menus or submenus, 3D virtual anatomical models, audio and / or visual cues. A permanent record can be generated from the collected data, where the permanent record can be synchronized for later manipulation such as optimization of the data collection template, production of reports or data analysis. All permanent records can desirably have redundant storage and compliant encryption methods.
Owner:K2M
Anchoring structure with concave landing zone
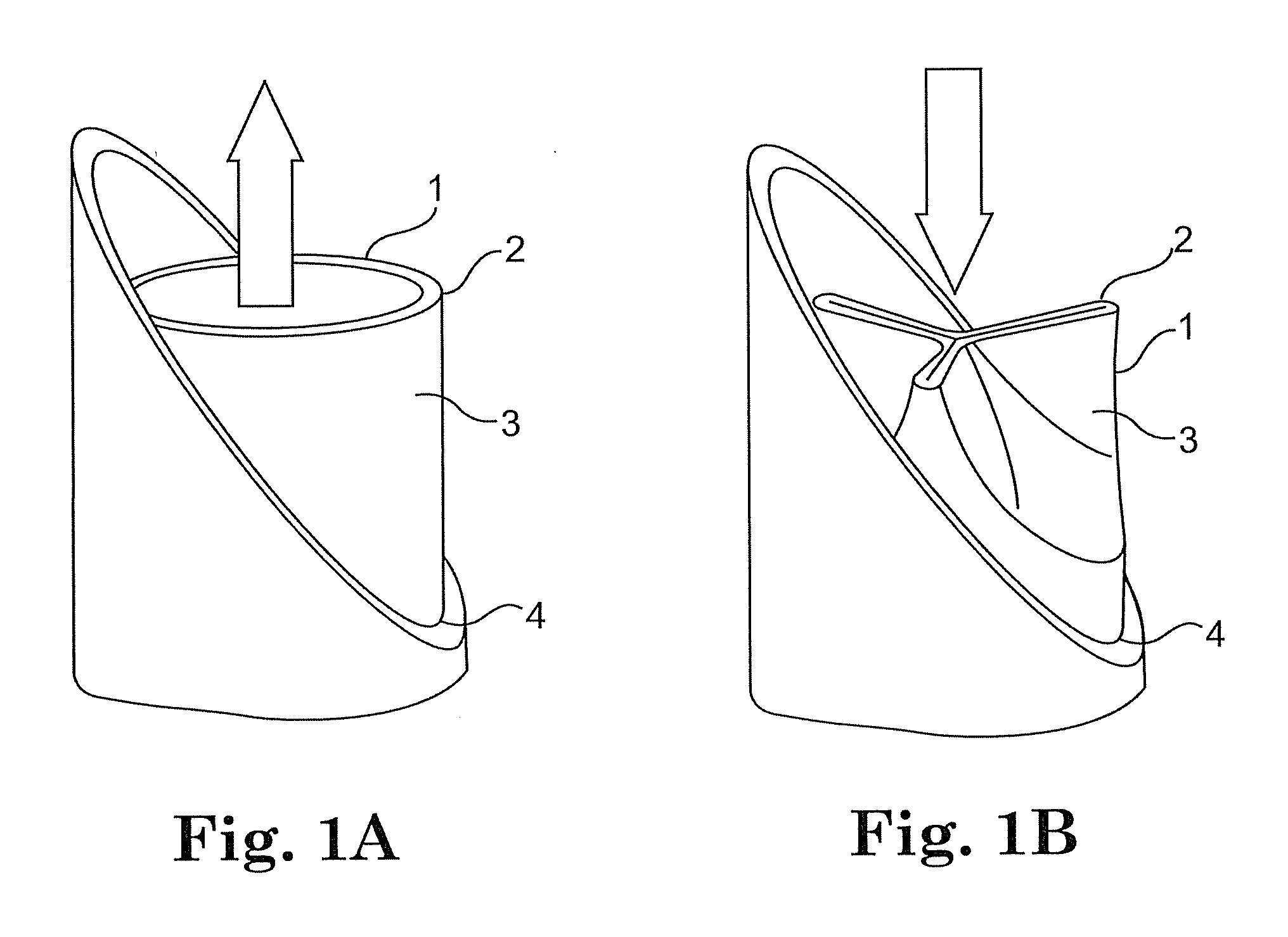
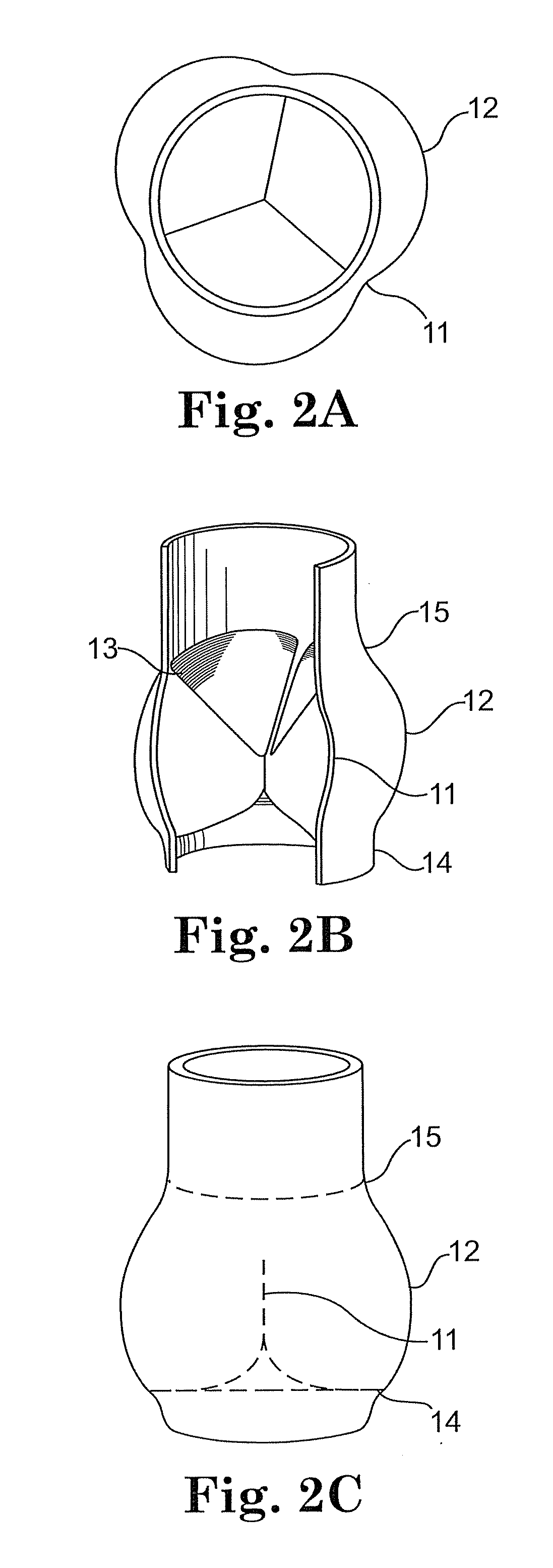
ActiveUS20100100176A1Reducing paravalvular leakageIncrease opportunitiesHeart valvesParavalvular leakageLanding zone
A method and device for reducing paravalvular leakage upon implantation of a replacement heart valve is provided. The valve assembly includes a tissue or bioprosthetic heart valve attached to an anchoring structure. The anchoring structure includes an inlet rim that is substantially C-shaped in cross section to form a concave landing zone. The anchoring structure self-seats when implanted in the sinus of a patient with the proximal and distal ends of the C-shaped inlet rim pushed against the aorta to effectively prevent paravalvular leakage.
Owner:MEDTRONIC PS MEDICAL
Cooling system for an electronic display
InactiveUS7161803B1Temperature fluctuationImprove life expectancyModifications for display panelsIndirect heat exchangersGas phaseCollector device
A cooling system for an electronic display may include a heat collector plate with internal gas and liquid phase lines. The cooling plate may be thermally isolated together with electronic components of the display within an enclosure of the display, while external lines carry liquid and gas phase refrigerant outside the enclosure to and from the heat collector plate. The external lines may be similar in size to each other and may be connected to the heat collector outside the heat collector plate by a manifold. The heat collector plate contacts a base plate of the electronic display in a thermally conductive relation to transfer heat from electronic components within the display to the gas phase refrigerant. Fans may be included for additional convective heat transfer. A single compressor may be fluidly connected to multiple heat collector plates in respective electronic displays.
Owner:FRONTLINE SYST
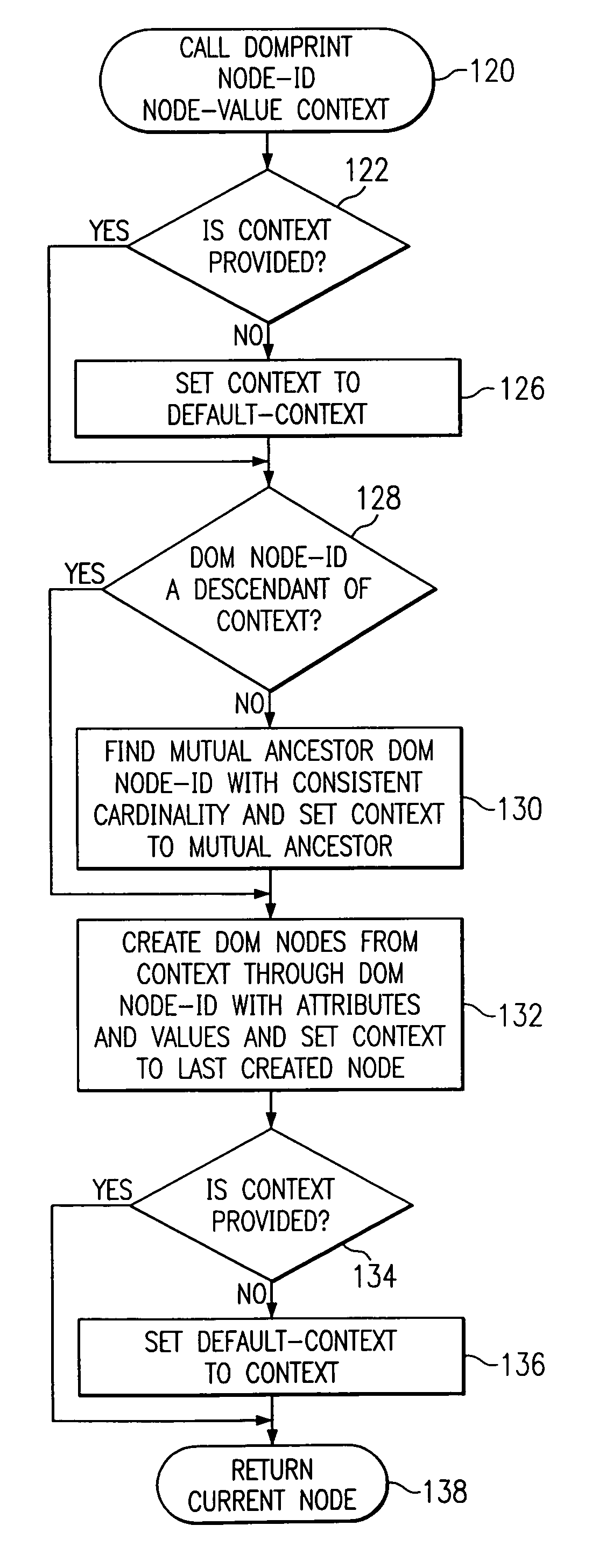
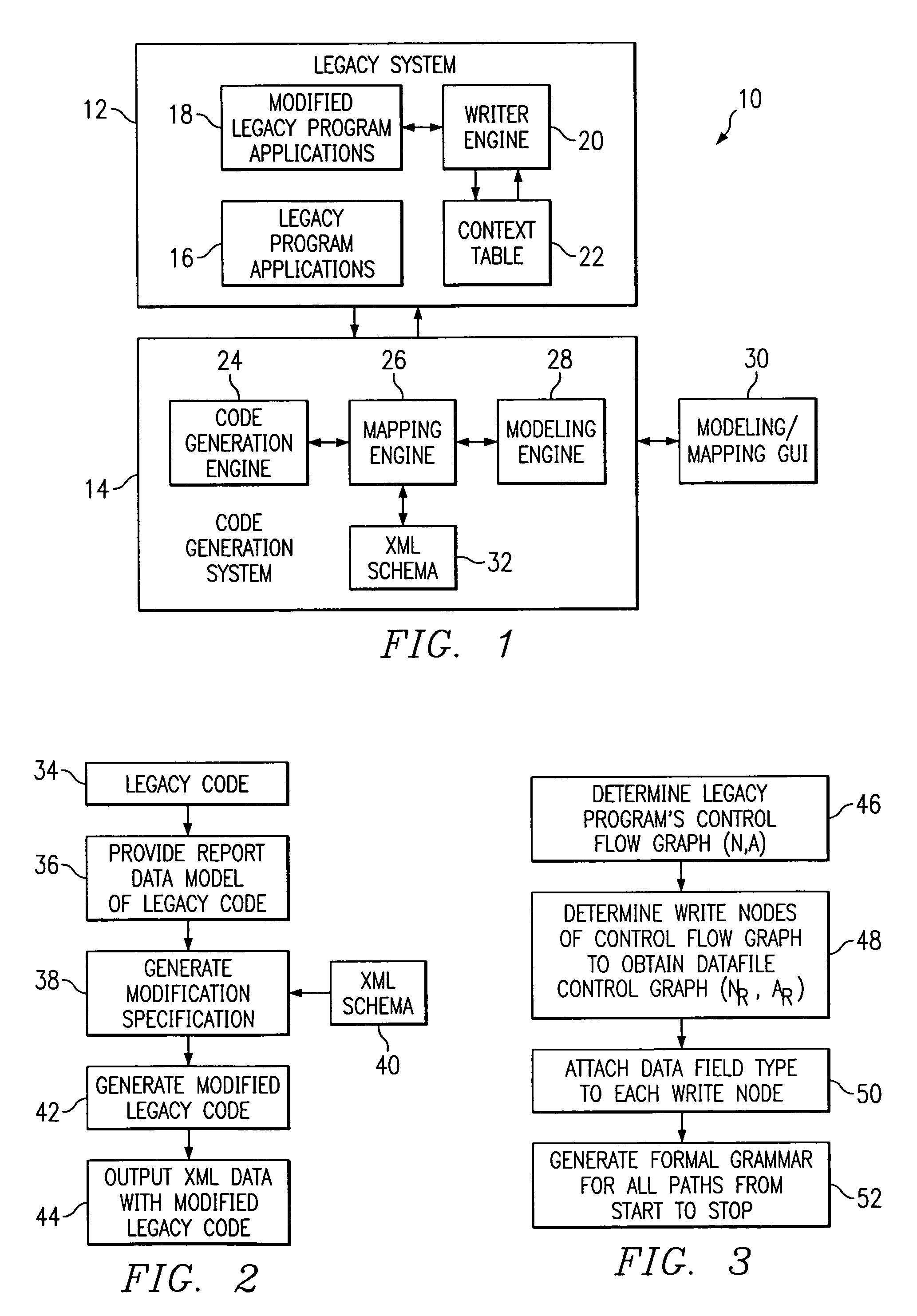
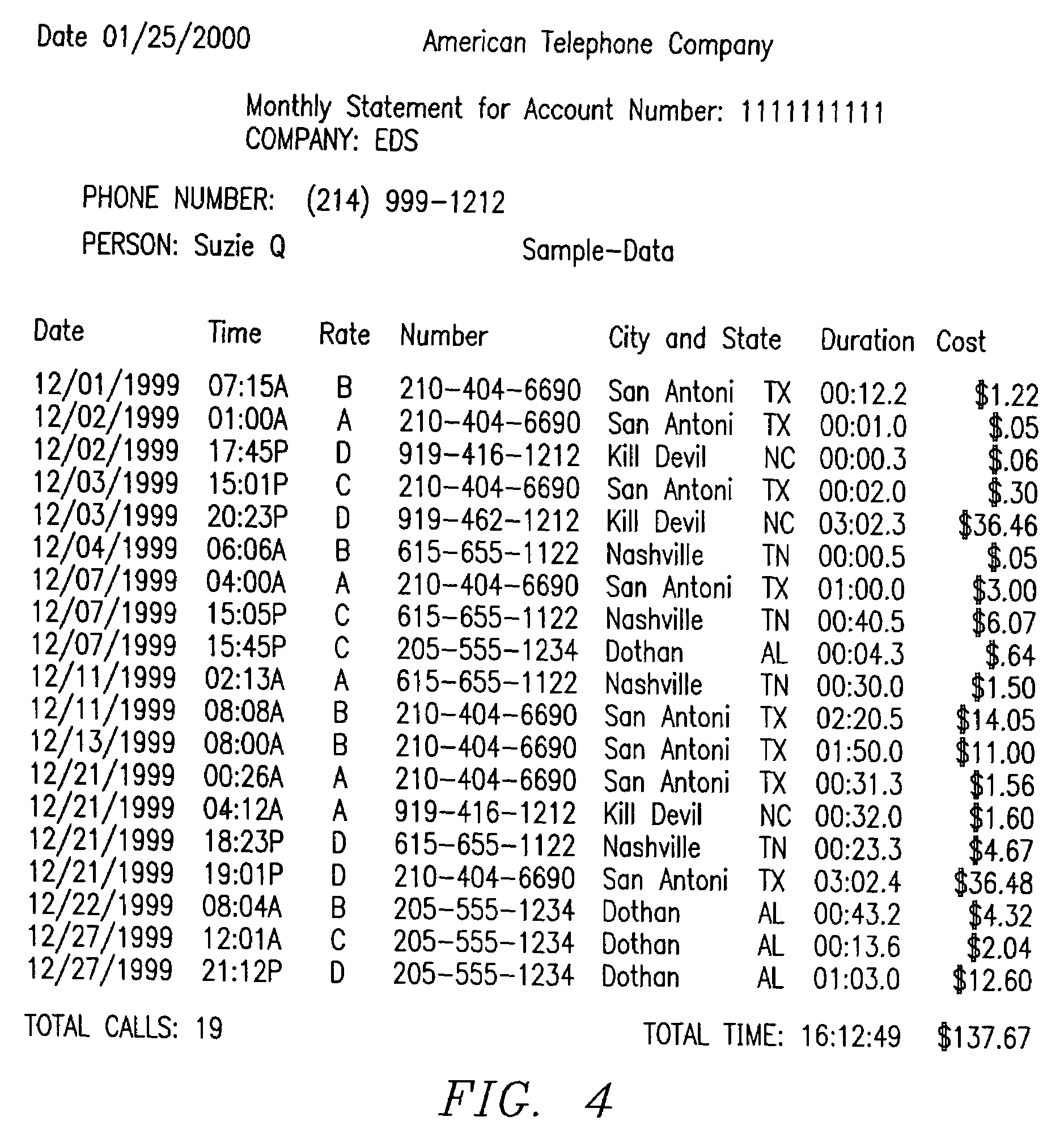
Method and system for reporting XML data based on precomputed context and a document object model
InactiveUS7114147B2Eliminate riskEasy to manageNatural language data processingProgram code adaptionXML schemaMultiple context
A method and system for modifying program applications of a legacy computer system to directly output data as XML using a DOM instance, models the legacy computer system, maps the model to an XML schema and automatically modifies one or more applications to directly output XML formatted data from an internally constructed DOM instance in cooperation with a writer engine. The writer engine allows for an arbitrary number of contexts to be simultaneously active and builds a complete DOM instance by using the multiple contexts to buffer output data. The writer engine directly loads XML schema information to construct and output DOM instances in accordance with the schema and subject to further transformation by XSLT stylesheets.
Owner:ENT SERVICES DEV CORP LP
Apparatus for purifying water
InactiveUS7238278B2Reduce concomitant disadvantageEconomical purification processLiquid solutions solvent extractionLoose filtering material filtersHypohaliteMetal salts
The invention relates to a method for purifying water by forming in an electrolytic cell molecular halogen, hypohalic acid, hypohalite ions or combinations thereof, from halide ions dissolved in the water; and dissolving one or more soluble metal salts in the water to provide corresponding metal ions. The invention also relates to a system for purifying water, having an electrolytic cell comprising a plurality of electrodes sufficient to electrolytically convert halide ion in the water into molecular halogen, hypohalic acid, or hypohalite ions, or combinations thereof; and a metal generator, which provides concentrations of one or more metals to the water.
Owner:ZODIAC POOL SYST LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com