Method based on combined public key authentication microprocessor card cloud management system
A technology combining public keys and microprocessors, applied in transmission systems, public keys for secure communications, user identity/authority verification, etc., can solve the problems of wasting resources, reducing efficiency, inconvenient promotion and use, and saving resources Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In order to make the measures, creative features, goals and effects achieved by the technology of the present invention easy to understand, the present invention will be further described below in conjunction with specific illustrations.
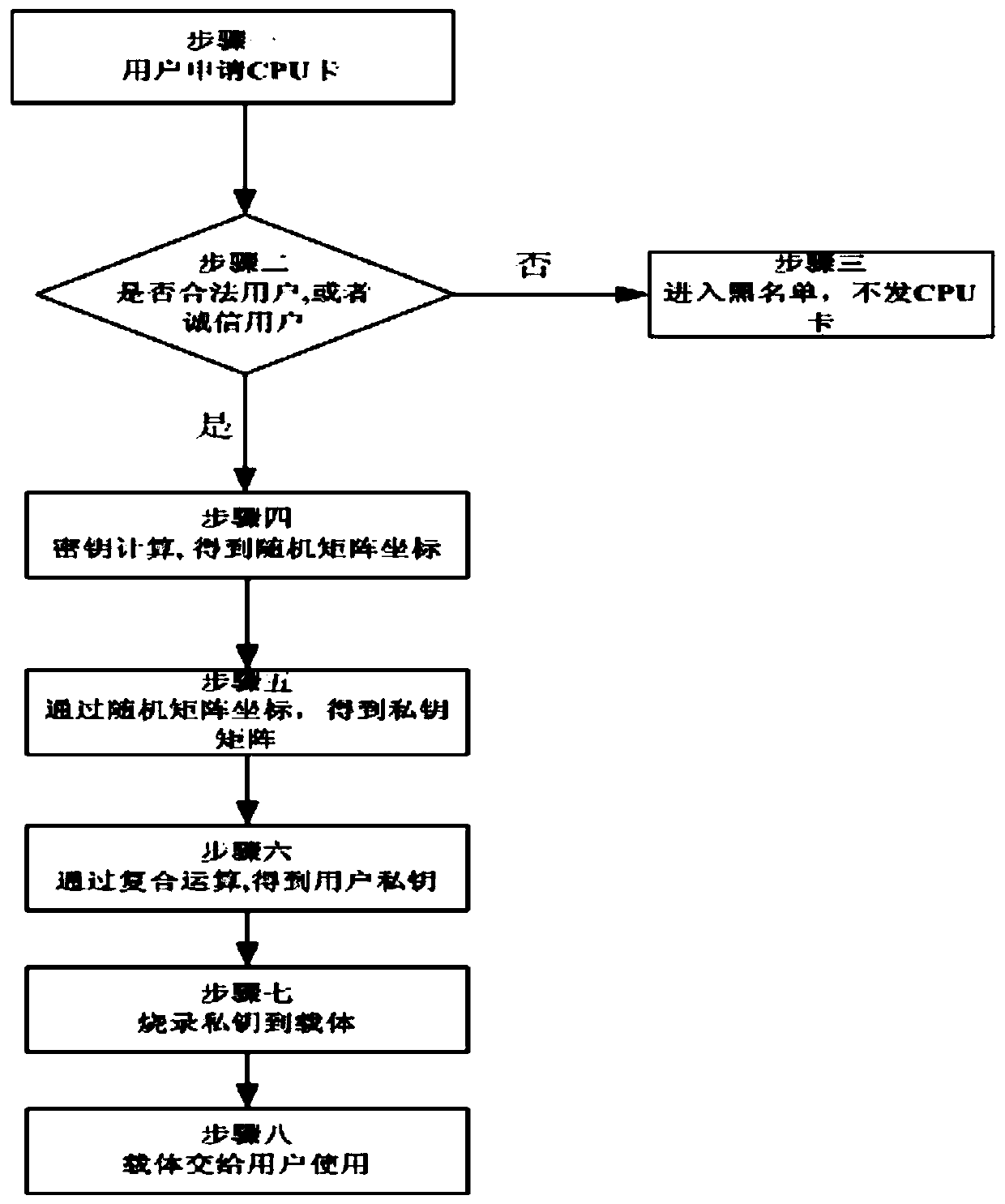
[0048] figure 1 It is a flow chart of the method of the present invention based on combined public key authentication microprocessor card cloud management system, as figure 1 As shown, the present invention provides a method based on combined public key authentication microprocessor card cloud management system, comprising the following steps:
[0049] Step 1, the user applies for a microprocessor CPU card, collects the user's identification information, and completes the identification;
[0050] Step 2: Use the user identification information collected in step 1 to further determine whether the user is a legitimate user or an honest user. If it is an illegal user or a dishonest user, enter the blacklist; if it is a legitimate user o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com