Verifiable matrix multiplication security outsourcing calculation method and system
A security outsourcing, matrix multiplication technology, applied in the field of cloud computing, can solve the problem of not knowing the real data of the matrix, and achieve the effect of avoiding collusion attacks, improving robustness, and reducing computing pressure.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
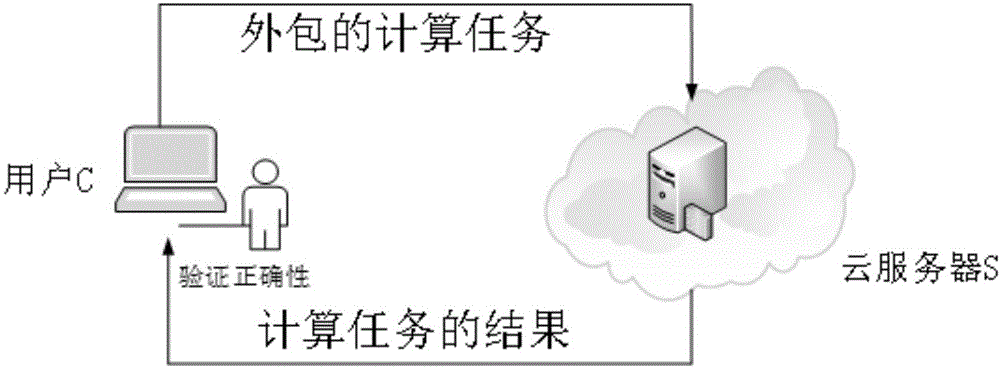
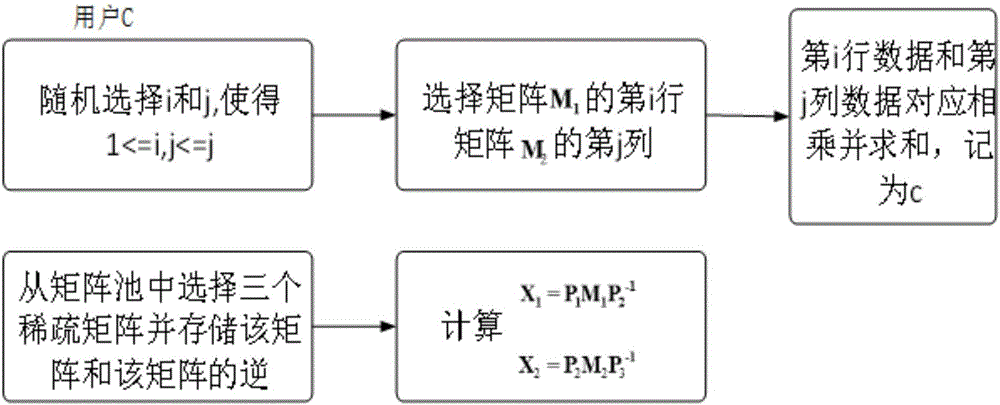
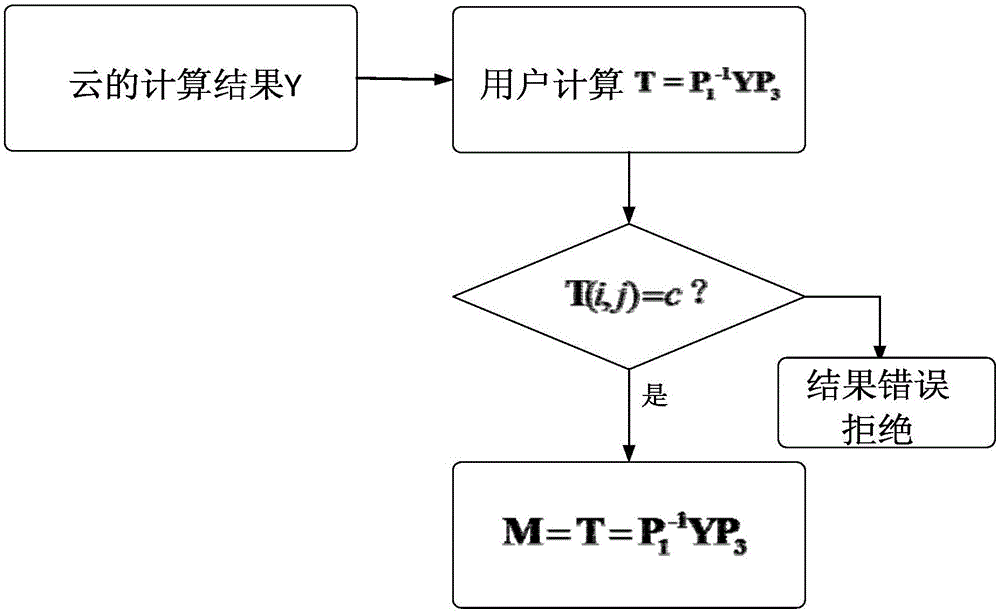
[0030] The participating members of the verifiable safe outsourcing calculation method of matrix multiplication provided by the present invention include user C and cloud server S, where user C is used to represent a user with limited computing ability. The cloud server S has sufficient computing power and can be provided to users in a pay-as-you-go manner. In the process of use, the user outsources the time-consuming calculation matrix multiplication operation to the cloud server. After the cloud server receives the matrix and operation, it uses its own powerful computing resources to perform the matrix multiplication operation. After the calculation is completed, the calculation result is returned to the user. . The user receives the calculation result returned by the cloud and verifies the correctness of the result.
[0031] The relevant theories used in the secure outsourcing computing method provided by the present invention are as follows:
[0032] matrix multiplicatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com