VANETs position privacy protection query method under fog computing architecture
A privacy protection and fog computing technology, applied in the field of network security, can solve problems such as no solution, inability to meet mobility, real-time, security, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
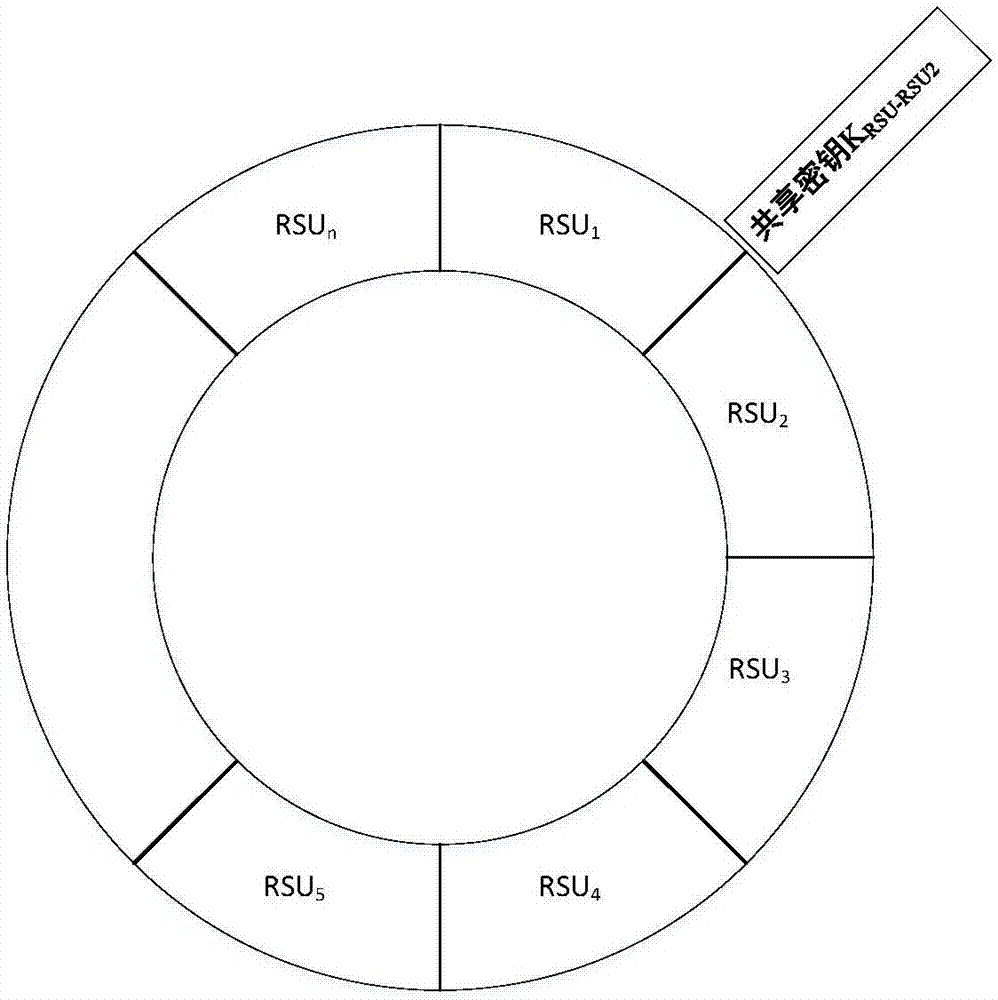
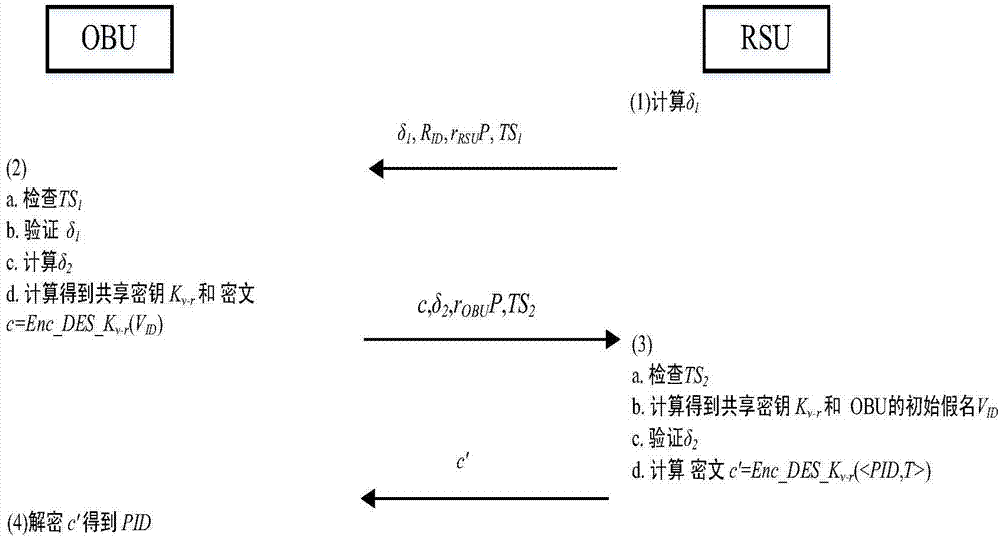
[0061] This embodiment applies the anonymous forwarding chain technology to the service query process of the vehicle nodes of the VANETs protocol, and uses the technology based on the anonymous forwarding chain, which effectively protects the location privacy of the vehicle nodes, effectively reduces the calculation overhead, and reduces the calculation of querying the vehicle side. Pressure, improve the overall query efficiency.
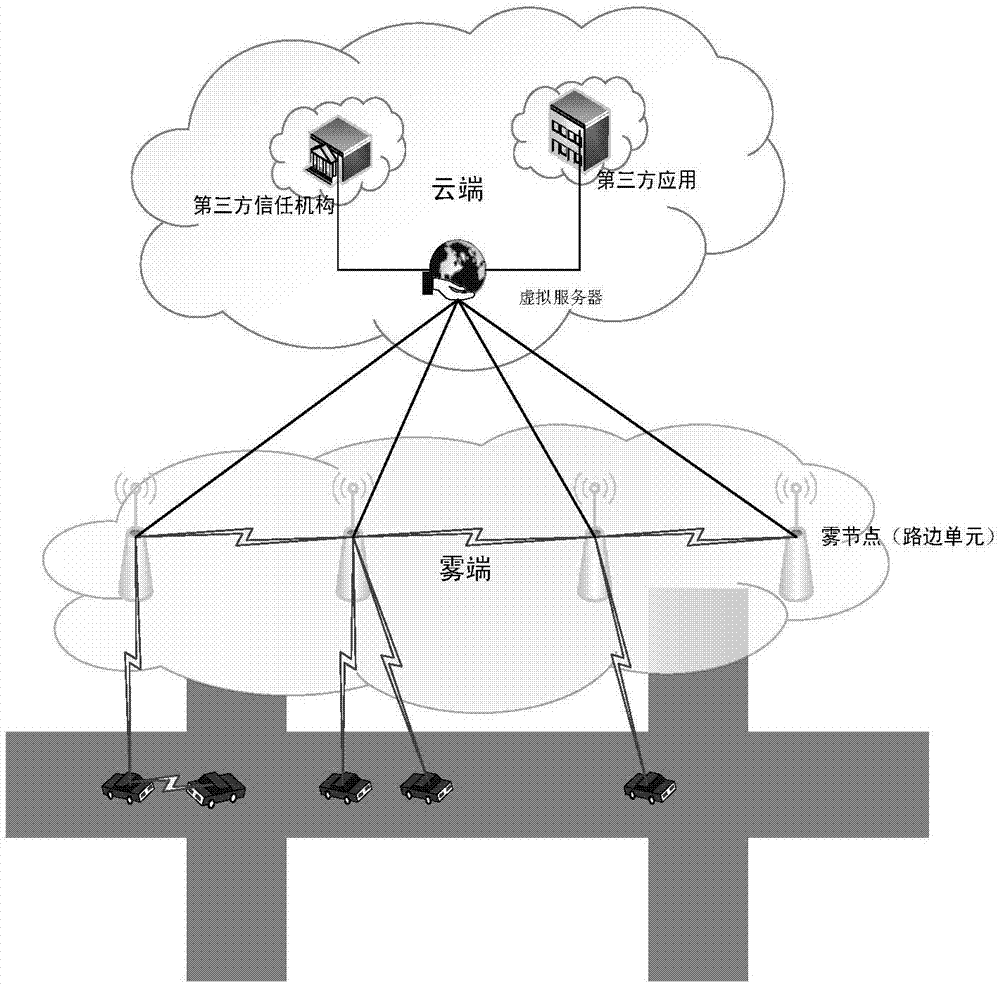
[0062] The VANETs query environment involved in this embodiment is as follows figure 1 As shown, the third-party trusted organization TA is connected to two roadside units RSU through a wired security channel, and the roadside unit RSU is connected to the vehicle-mounted unit OBU. It is assumed that the on-board unit OBU has completed the initial two-way authentication with the roadside unit RSU. fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com