Method for preventing Ethernet from being attacked
a technology of ethernet and prevention methods, applied in the field of network security, can solve problems such as new destructive methods, network paralysis, and attacks on network reliability, and achieve the effects of reducing maintenance costs, improving network maintenance efficiency, and reducing the risk of attacks on ethern
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
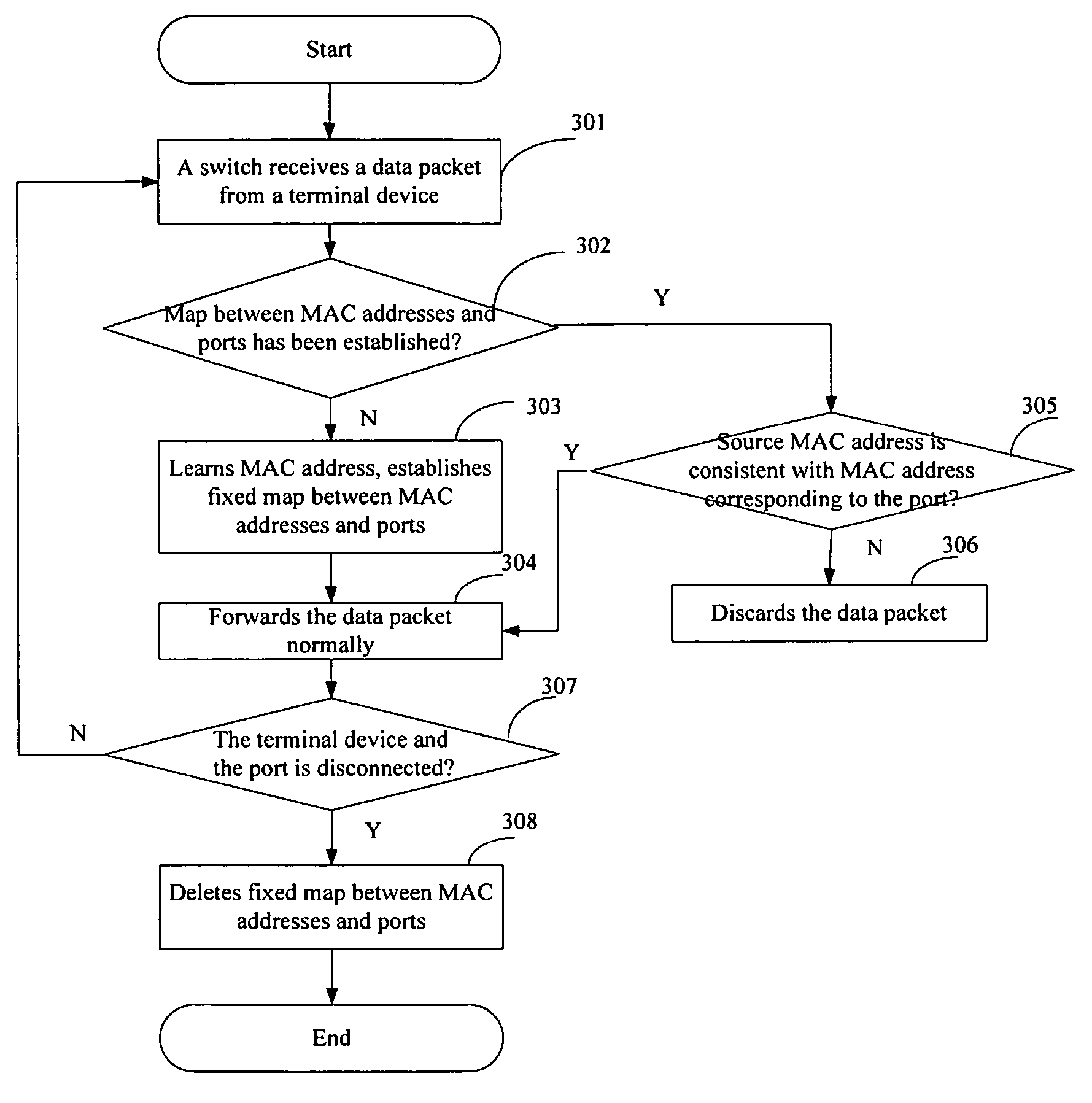
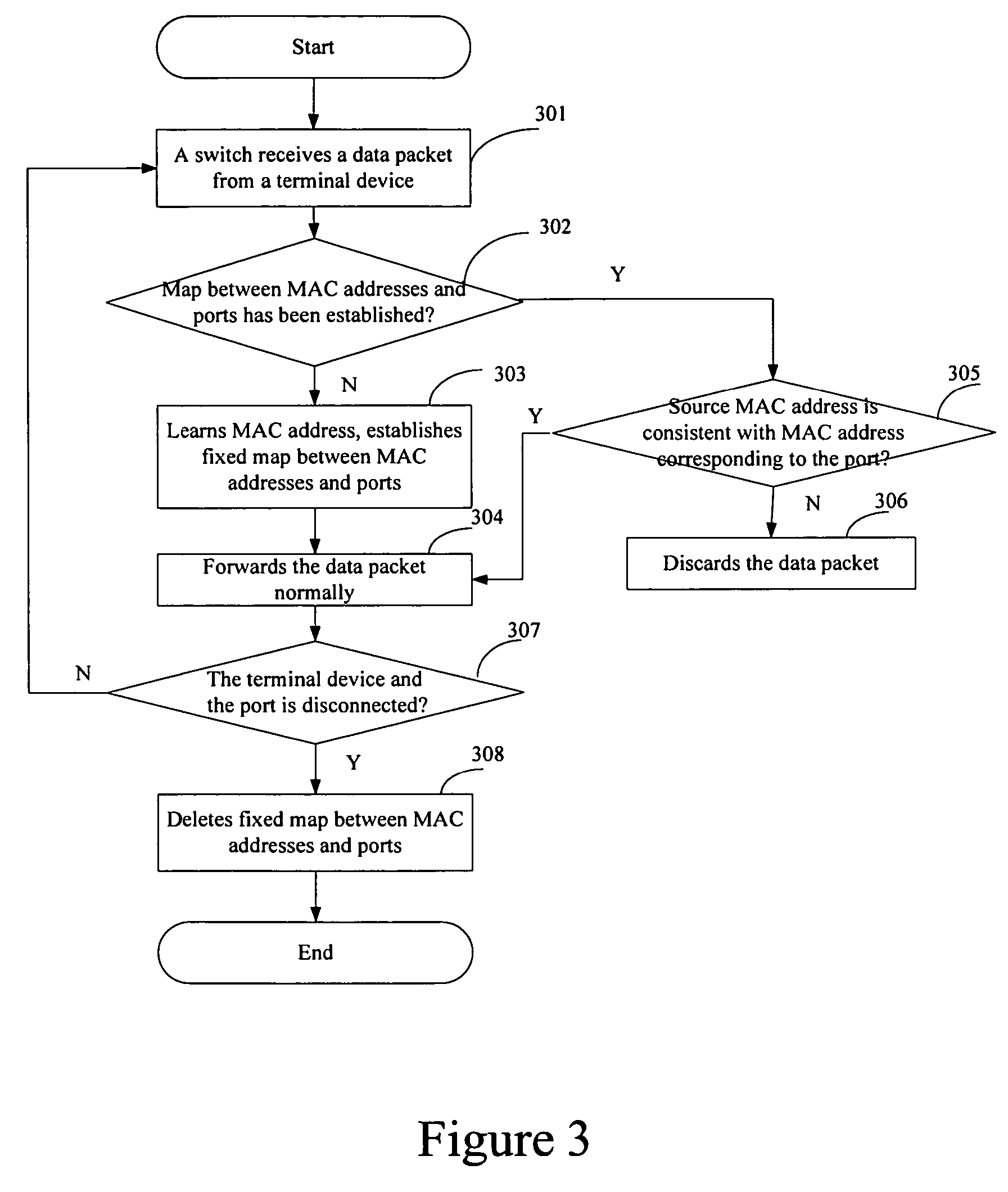
[0020]Now, an embodiment of the present invention will be described in detail hereinafter with reference to accompanying drawings.
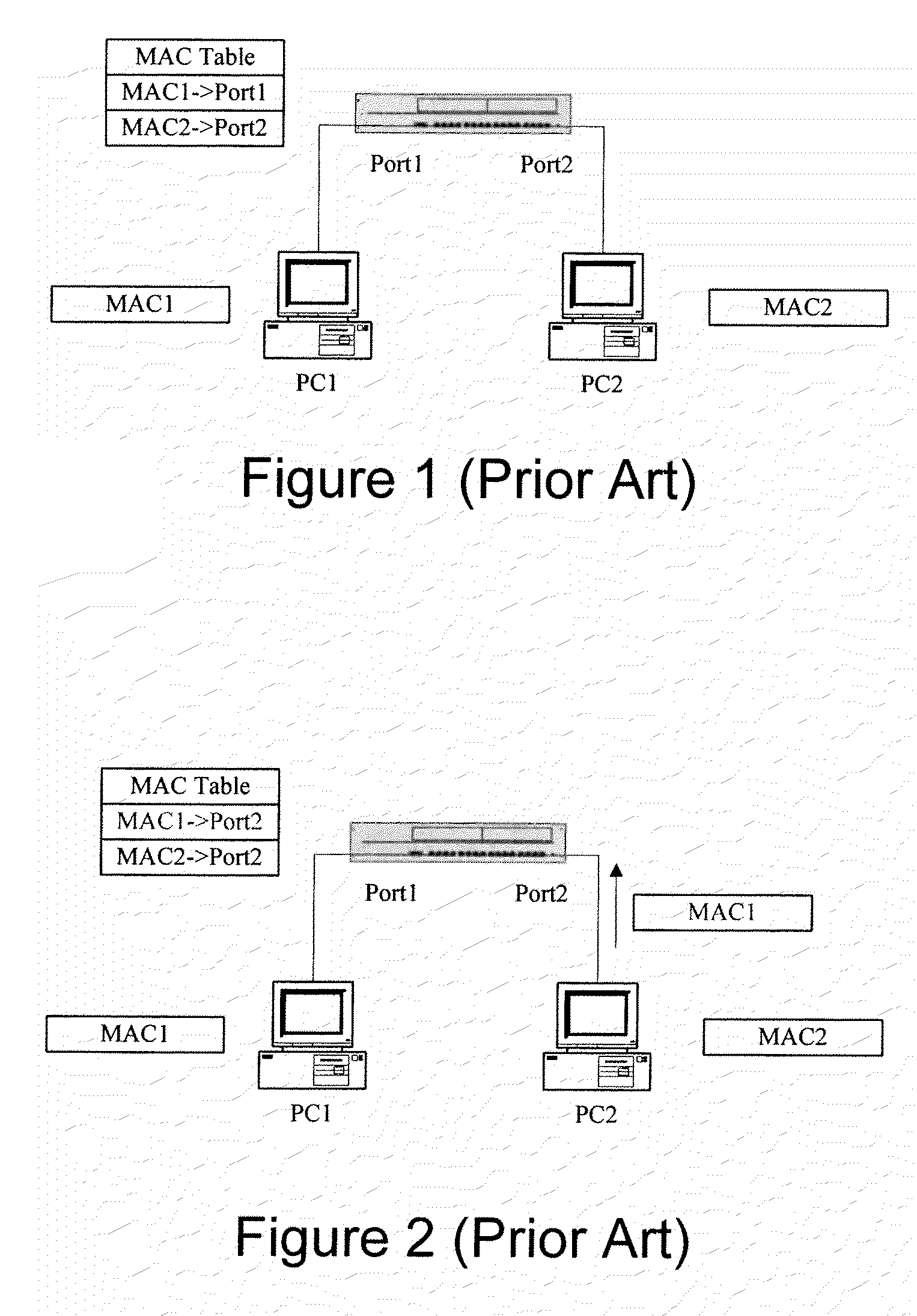
[0021]In Ethernet, all data packets to be forwarded come from user devices in a user layer of a network. The user devices include Ethernet terminal devices such as PCs, servers, IP telephone sets and so on, and switch which is in access layer connect these user devices together. Each of the Ethernet terminal devices has respective MAC addresses which usually do not change, i.e., the MAC address of each port at the switch usually does not change, unless the MAC addresses corresponding to the switch ports may change only under the circumstances of the entire terminal device being replaced, the PC network NIC being changed or the terminal device being moved with a long distance, under which physical connection between the terminal device and the switch needs to be disconnected. The present embodiment applies a learning mechanism to the switch, and determines...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com