Network link detection method and system
A network link and detection method technology, which is applied in the field of Internet security, can solve the problems of high malicious link attack risk, etc., and achieve the effect of reducing attack risk and avoiding fraud
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
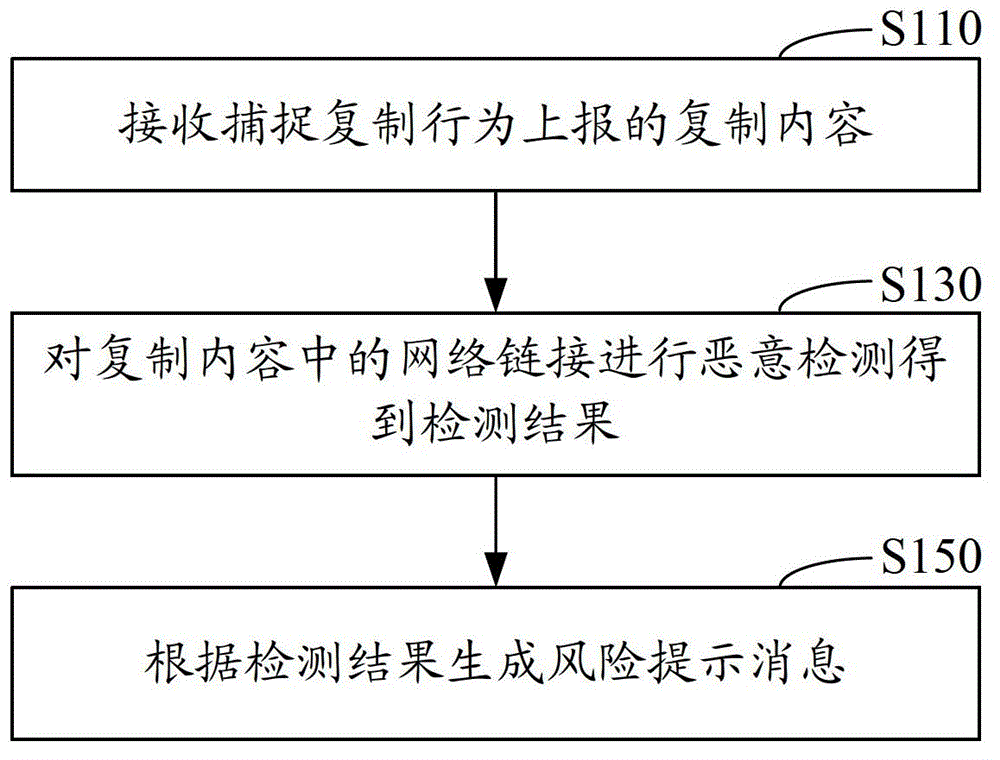
[0022] Such as figure 1 Shown, in one embodiment, a kind of network link detection method, comprises the steps:
[0023] Step S110, receiving the copied content reported by capturing the copying behavior.
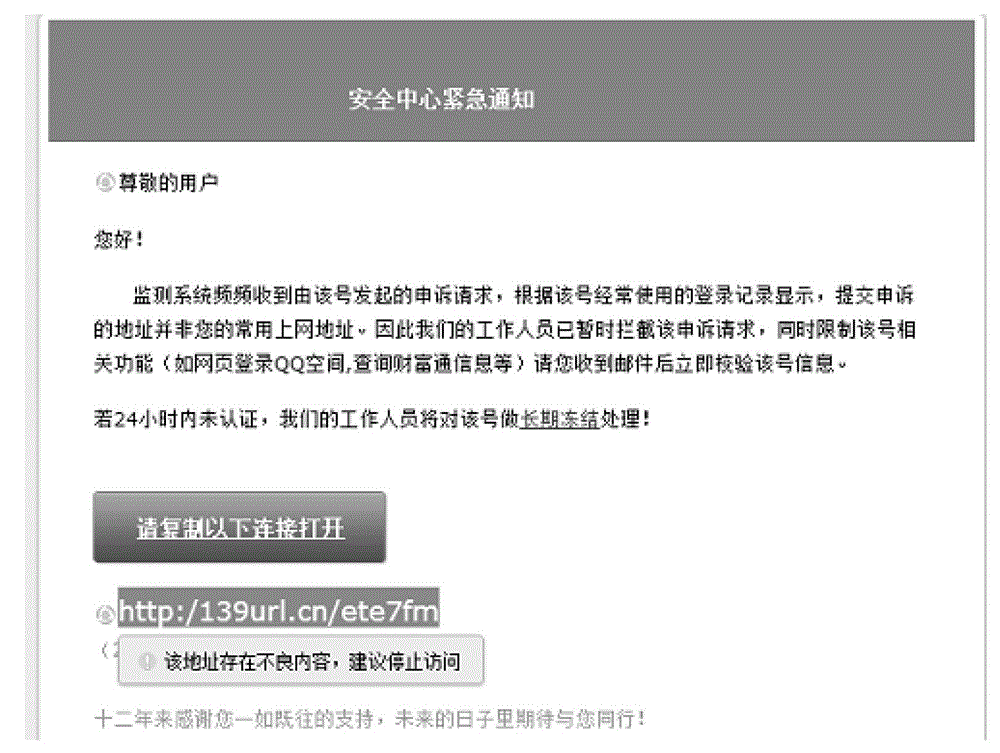
[0024] In this embodiment, the copied content is the object copied on the page when the user triggers the copying behavior, and may include text information, picture information, and network links.
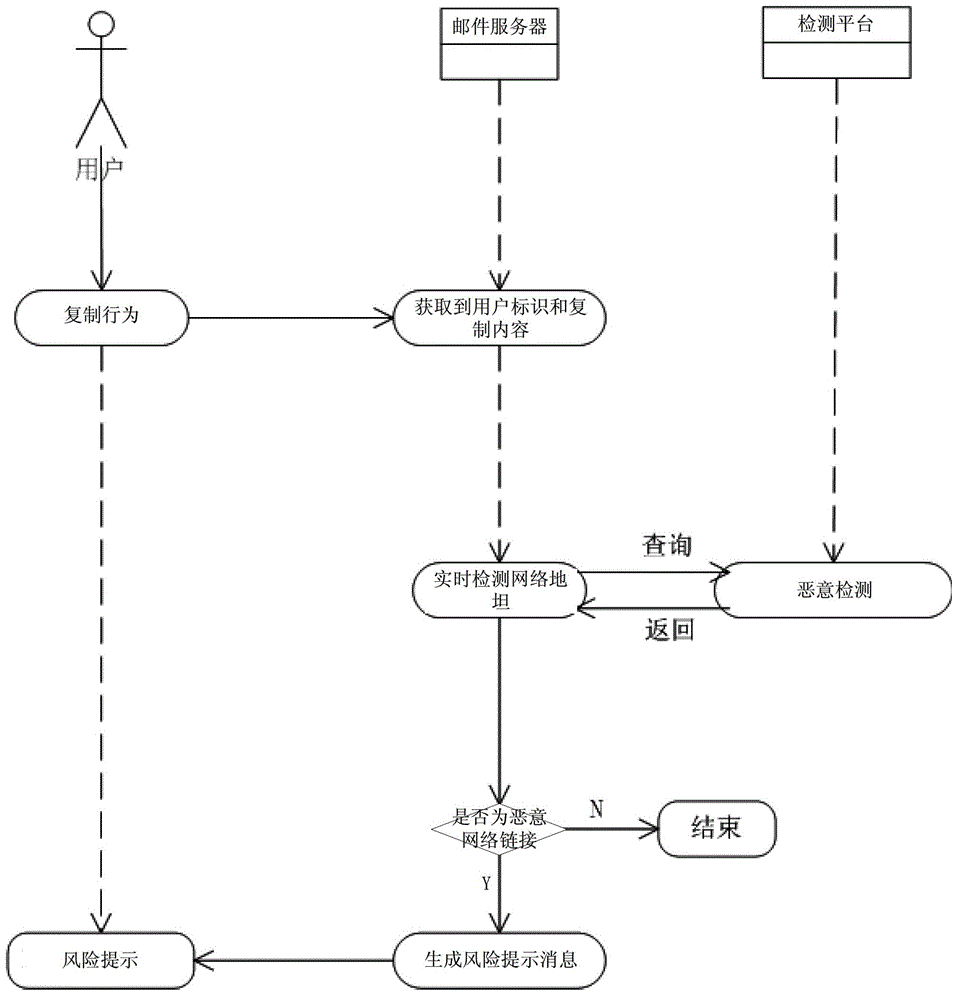
[0025] In one embodiment, before the above step S110, it also includes: capturing the copying behavior in the page, obtaining the copied content according to the copying behavior, and reporting the copied content.
[0026] In this embodiment, the copying behavior triggered in the currently displayed page is captured to obtain the copying content corresponding to the copying behavior, and report it to the background server.
[0027] Step S130, performing malicious detection on the network link in the copied content to obtain a detection result.
[0028] In this embodiment, af...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com