Cloud terminal identity authentication method and system
An identity authentication and cloud terminal technology, applied in the field of cloud computing security, can solve problems such as keyboard input account passwords are vulnerable to Trojan horse program attacks, large information security risks, etc., to reduce the risk of Trojan horse attacks, simple and convenient operation, and high security performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
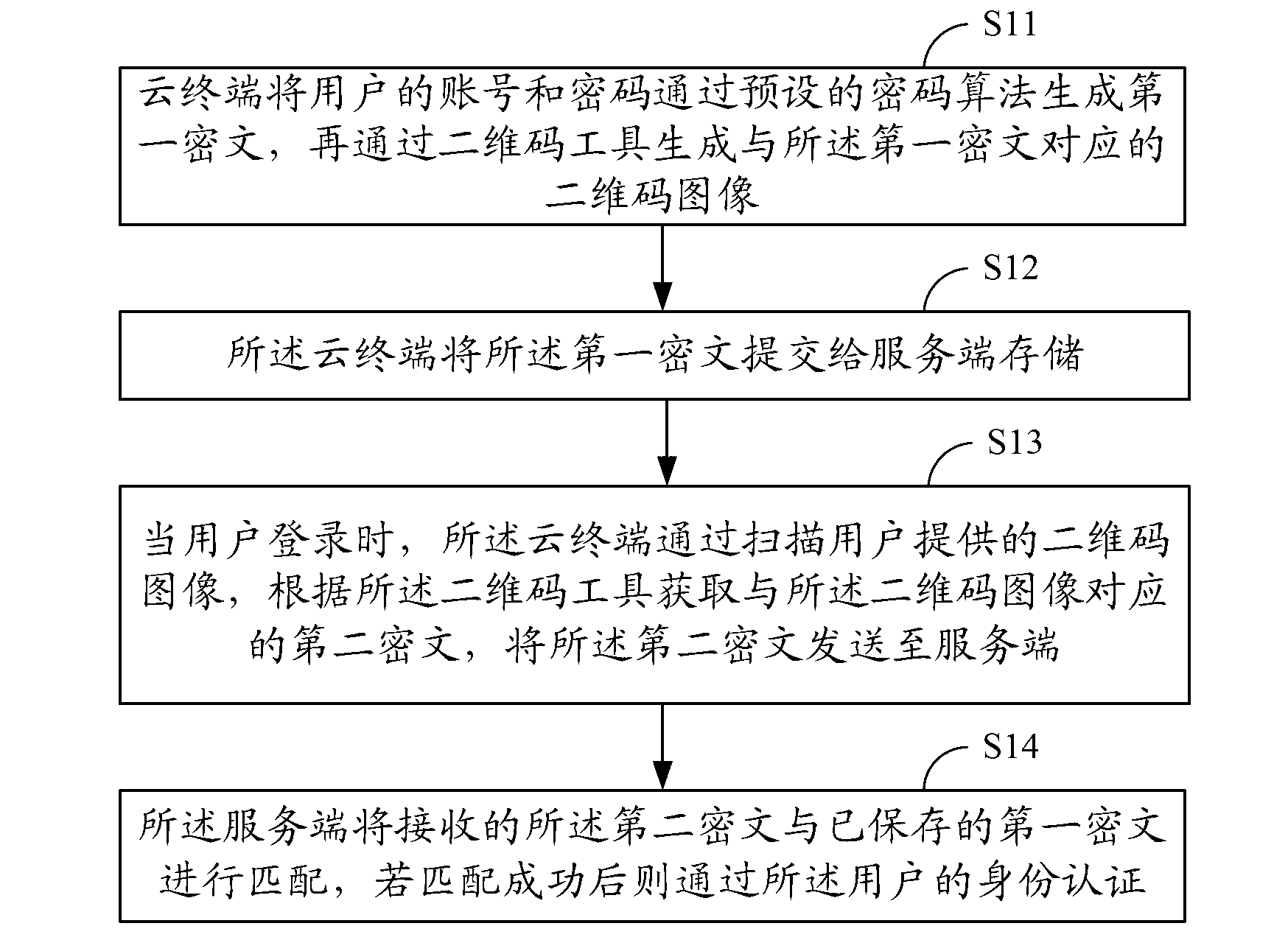
[0040] Such as figure 1 As shown, it is a schematic flow diagram of the cloud terminal identity authentication method in an embodiment of the present invention. In this embodiment, the two-way interaction process between the cloud terminal and the cloud server is used as an example to illustrate, including the following steps:
[0041] S11. The cloud terminal generates a first ciphertext with the user's account number and password through a preset cryptographic algorithm, and then generates a first two-dimensional code image corresponding to the first ciphertext through a two-dimensional code tool;
[0042] Two-dimensional code is to record data symbol information with a specific geometric figure distributed in black and white on a plane (two-dimensional direction) according to a certain rule. . The concept of "1" bit stream, which uses several geometric shapes corresponding to binary to represent text and numerical information, and automatically reads through image input equi...
Embodiment 2
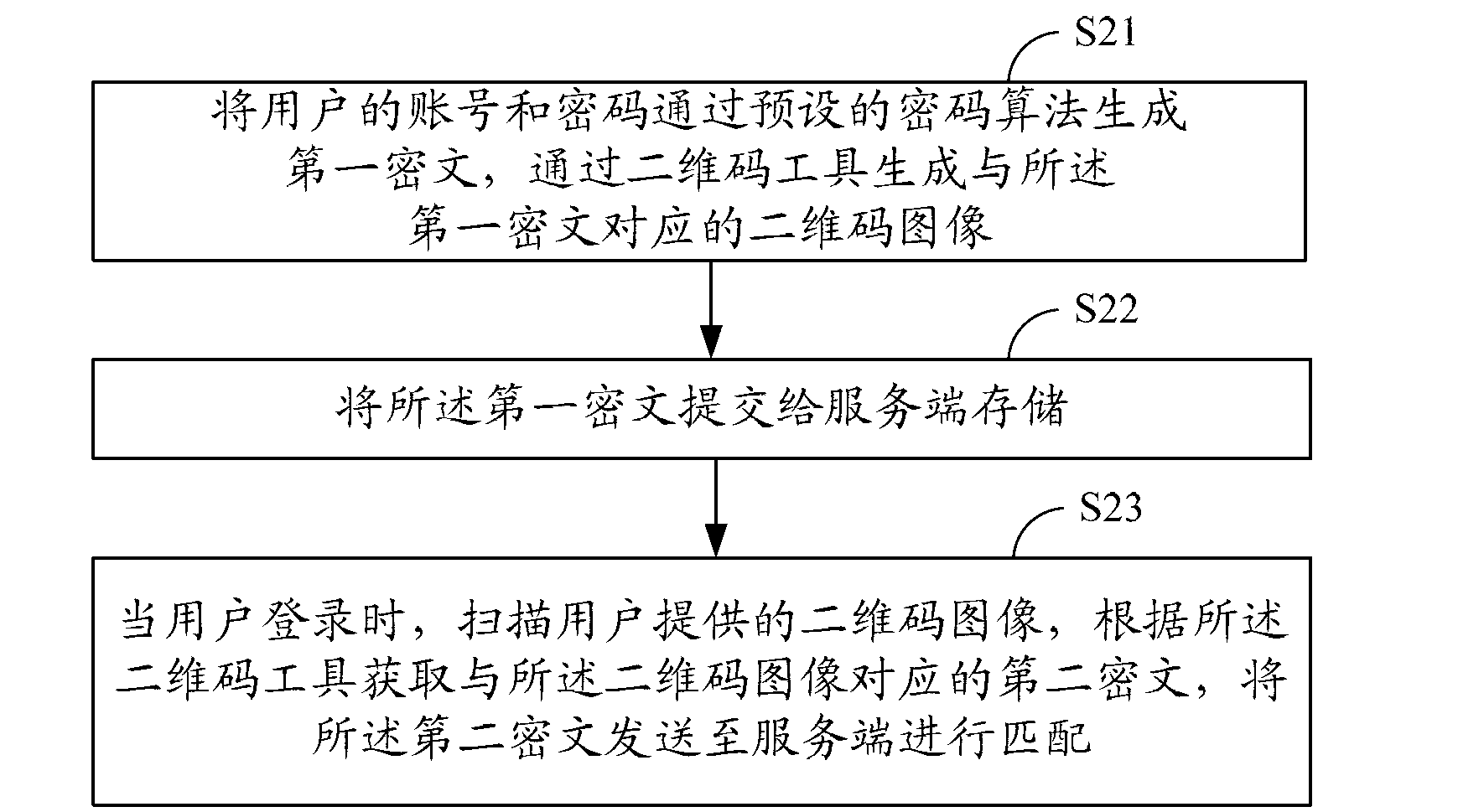
[0059] figure 2 A schematic flowchart of another embodiment of the cloud terminal identity authentication method of the present invention is shown. In this embodiment, the processing process of the cloud terminal is taken as an example for description.
[0060] S21. Generate a first ciphertext with the user's account number and password through a preset cryptographic algorithm, and generate a two-dimensional code image corresponding to the first ciphertext through a two-dimensional code tool;
[0061] S22. Submit the first ciphertext to the server for storage;
[0062] S23. When the user logs in, scan the two-dimensional code image provided by the user, obtain the second ciphertext corresponding to the two-dimensional code image according to the two-dimensional code tool, and send the second ciphertext to the server for processing match.
[0063] According to the scheme in this embodiment, the user's account number and password are first converted to generate the correspond...
Embodiment 3
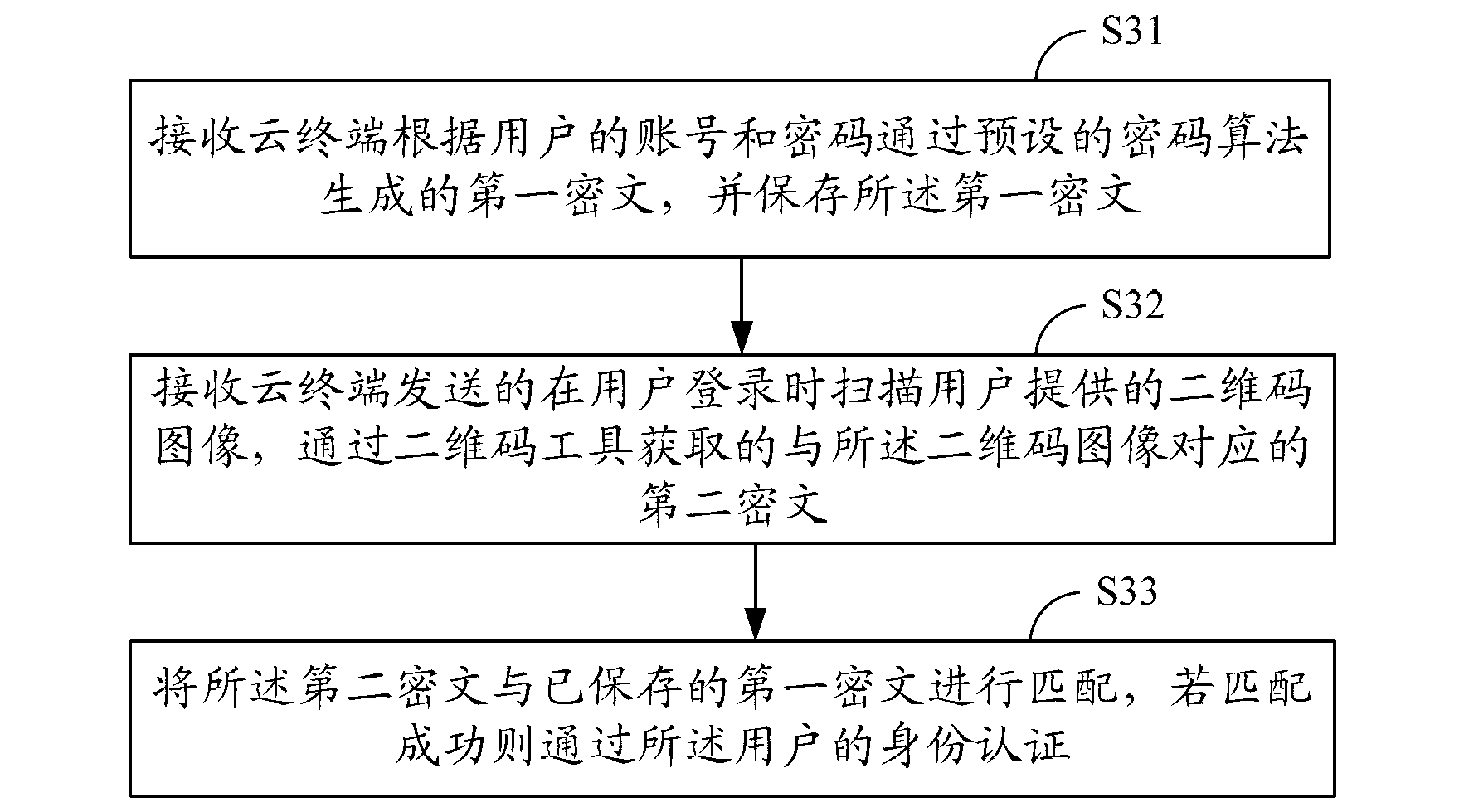
[0065] image 3 A schematic flowchart of another embodiment of the cloud terminal identity authentication method of the present invention is shown. In this embodiment, the processing process of the server is taken as an example for description.
[0066] S31. Receive the first ciphertext generated by the cloud terminal through a preset cryptographic algorithm according to the user account and password, and save the first ciphertext;
[0067] S33. Receive the second ciphertext corresponding to the two-dimensional code image obtained by scanning the two-dimensional code image provided by the user when the user logs in and scanning the two-dimensional code image sent by the cloud terminal;
[0068] S33. Match the second ciphertext with the saved first ciphertext, and pass the user's identity authentication if the matching is successful;
[0069] According to the solution in this embodiment, the server receives the first ciphertext sent by the cloud terminal, and the first ciphert...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com