Intelligent distribution terminal security protection method based on asymmetric digital signature authentication
An intelligent power distribution terminal and digital signature technology, applied in electrical components, circuit devices, user identity/authority verification, etc., can solve problems affecting users' safe and reliable power supply, intelligent power distribution terminal attacks, security threats, etc., to reduce attacks risks, good application prospects, and the effect of ensuring operational safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be further described below in conjunction with the accompanying drawings.
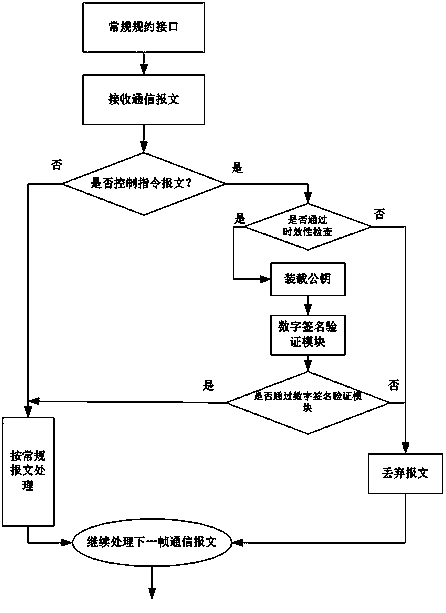
[0022] The security protection method for intelligent power distribution terminals based on asymmetric digital signature authentication of the present invention, according to the actual characteristics of intelligent power distribution terminals, realizes the authentication of asymmetric digital signatures on power distribution terminals. Minor changes to the communication protocol can realize the authentication of the digital signature technology without redefining a new communication protocol, reducing the risk of attacks from the public network, and ensuring the operation safety of the distribution automation system. The intelligent power distribution system of the present invention The terminal security protection method, wherein the CPU hardware of the intelligent power distribution terminal is implemented by a DSP processor based on embedded operating systems such...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com