Identity authentication method for Hadoop cluster
A hadoop cluster and identity authentication technology, applied in user identity/authority verification, digital transmission systems, electrical components, etc., can solve problems such as weak password attacks, achieve the effect of improving security, improving security, and reducing risk points
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The preferred embodiments of the present invention are given below in conjunction with the accompanying drawings to describe the technical solution of the present invention in detail.
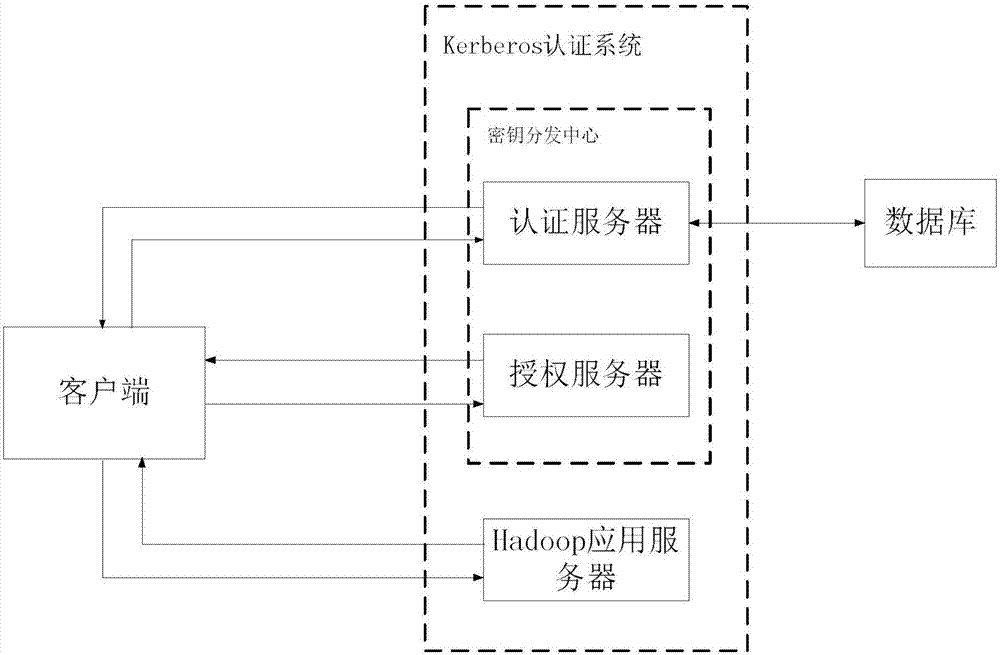
[0034] The present invention uses a third-party service called KDC (Key Distribution Center) to verify the mutual identities of entities in the cluster, and establish keys to ensure secure connections between entities. KDC consists of two parts, the authentication server AS and the authorization server TGS. Kerberos (Kerberos is a dog that guards the entrance to hell in ancient Greek mythology. It has three heads. The reason why MIT MIT named its authentication protocol Kerberos is because they plan to establish a complete system through three aspects: authentication, authorization, and auditing. Security mechanism) The authentication system includes three parties in total: the authentication server AS, which is used to verify the identity of the user and issue the ticket TGT when loggin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com