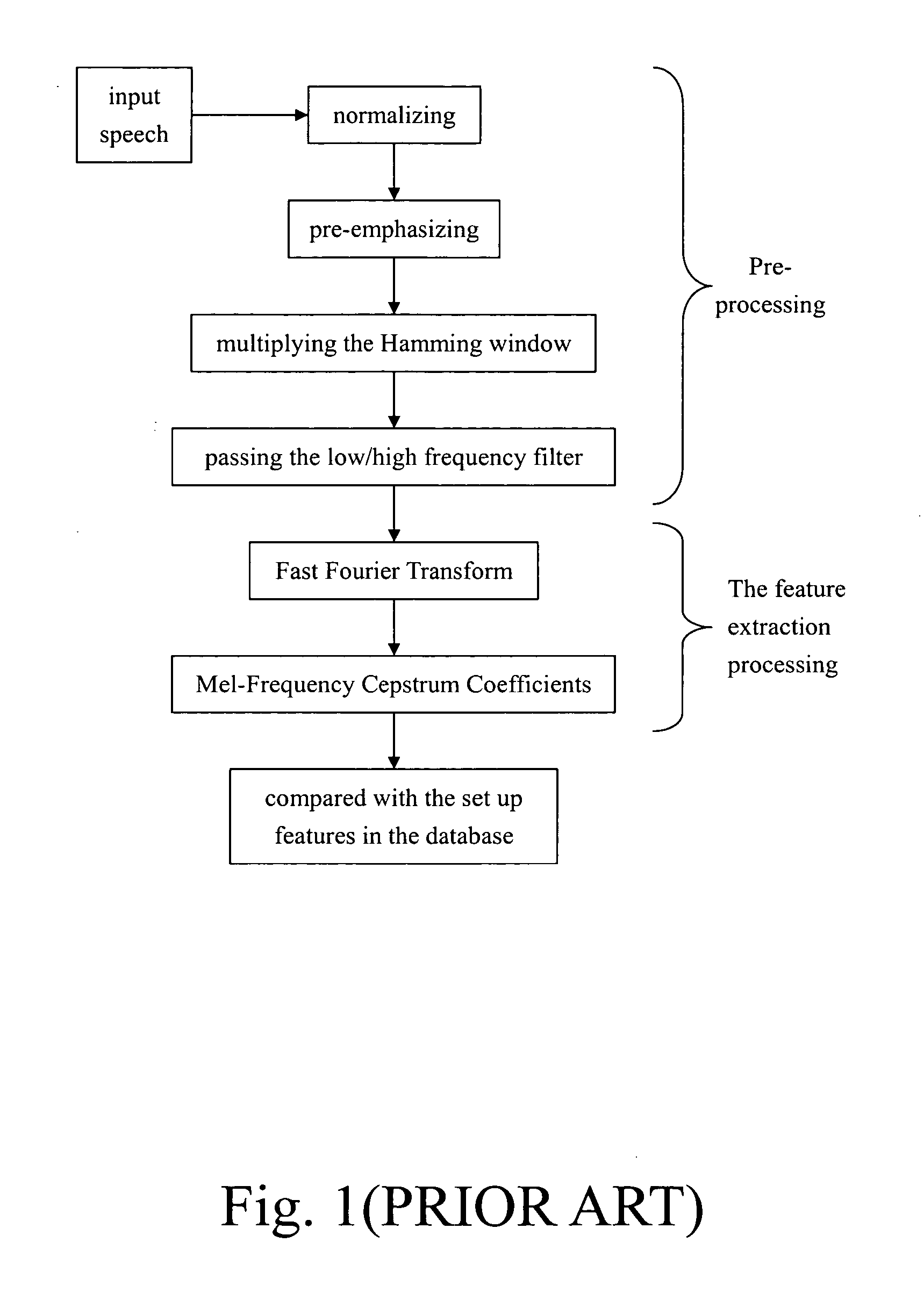
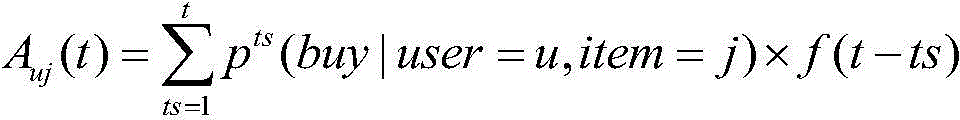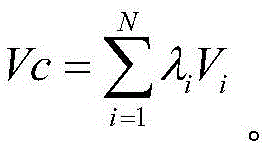Patents
Literature
402 results about "Time factor" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
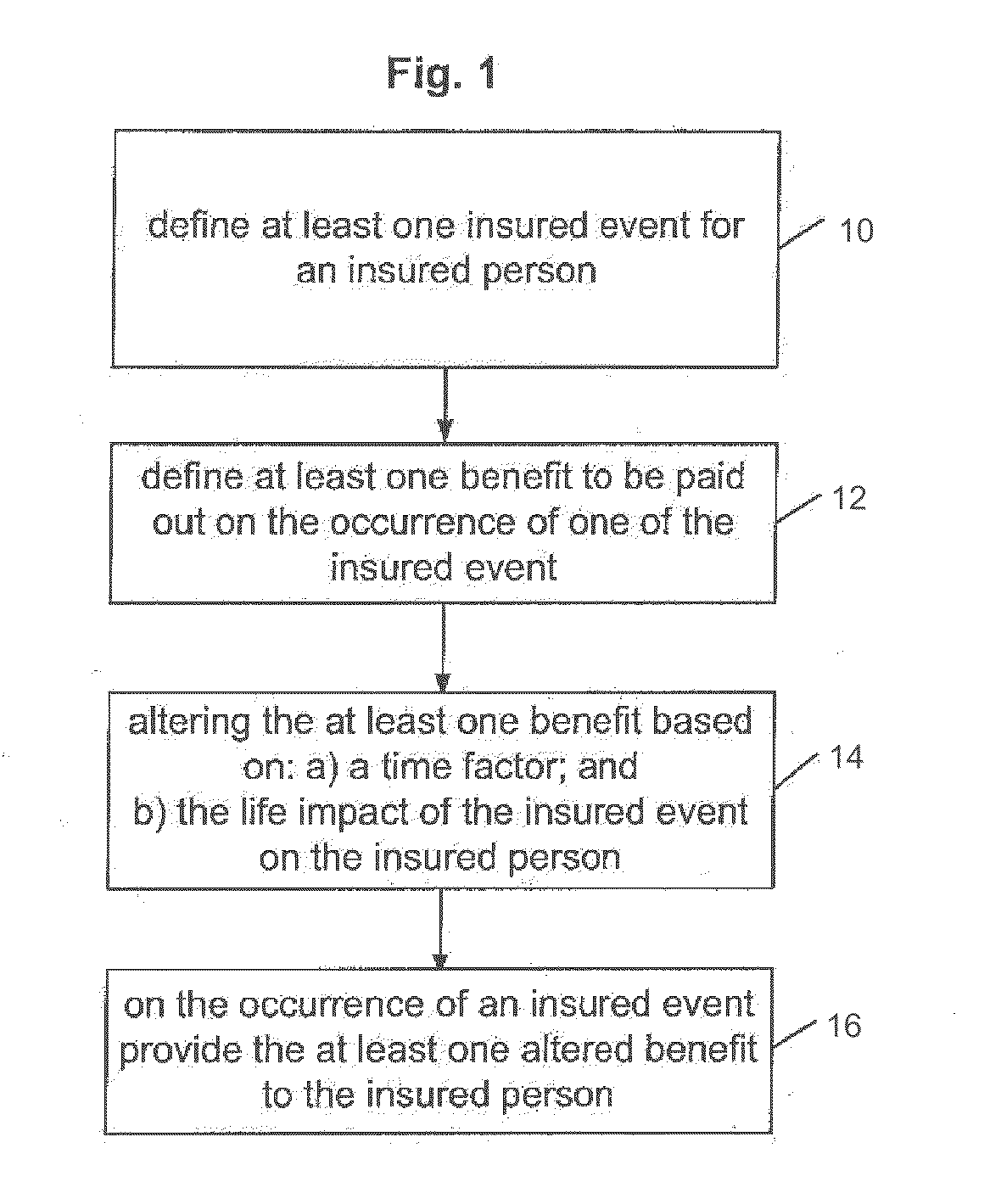
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
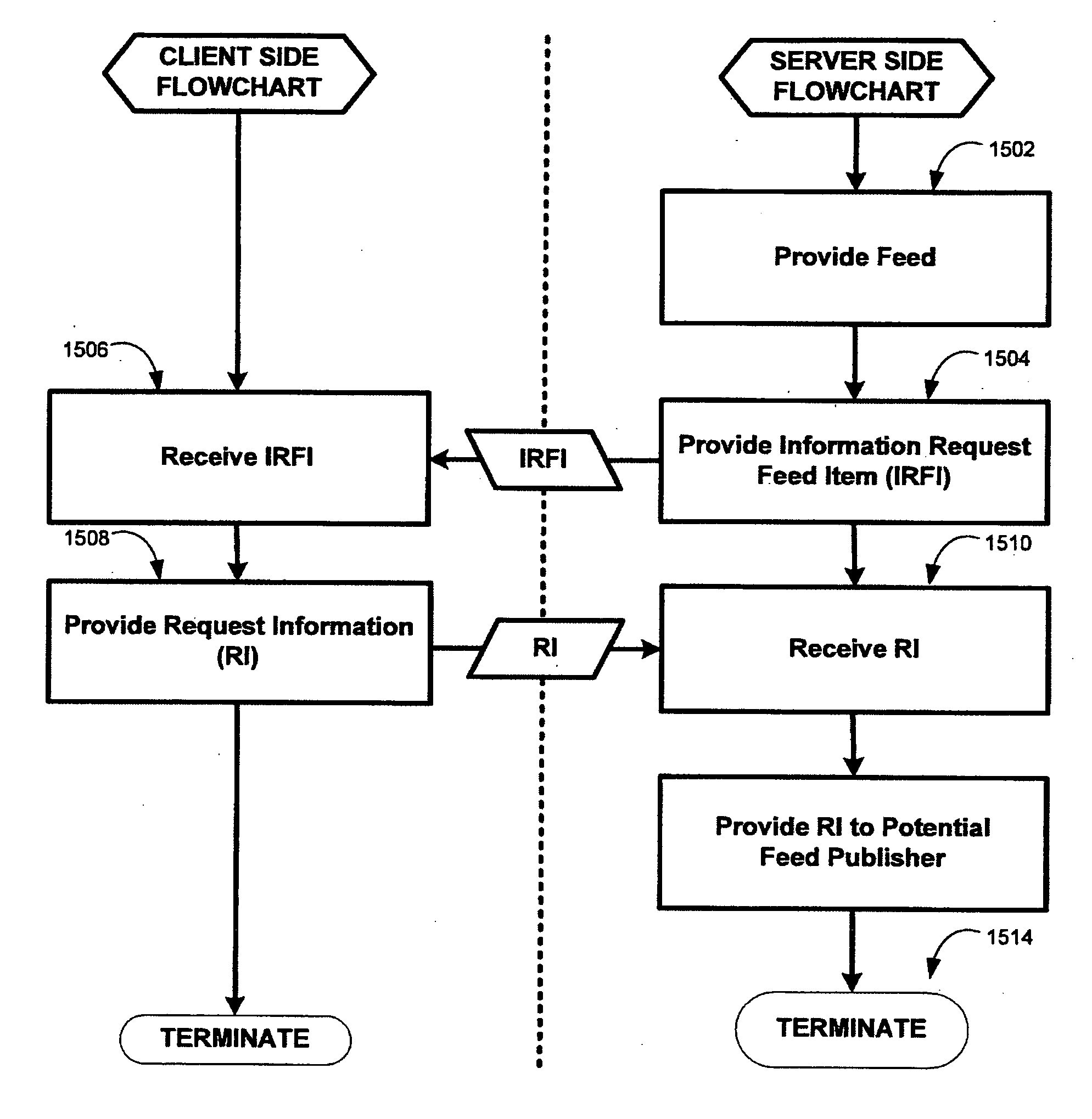
Method and system for the creating, managing, and delivery of feed formatted content
InactiveUS20060184617A1Simplifying and filtering informationMultiple digital computer combinationsTransmissionTime sensitiveTime factor
The invention provides a system and method of providing user interest to a potential feed publisher. The method includes providing at least one feed, providing at least one information request feed item in the feed, receiving request information associated with the feed; and providing the request information to a potential feed publisher. The invention further provides a method of providing time sensitive information on a multimedia device. The method includes receiving a multimedia file associated with feed formatted content at a multimedia device, receiving a time activator associated with the multimedia file and the feed formatted content at the multimedia device, storing the multimedia file in association with the time activator at the multimedia device, receiving an information request, determining a time factor, and selectively providing the multimedia file on the multimedia device based on the information request, the time factor, and the time activator.
Owner:DIZPERSION
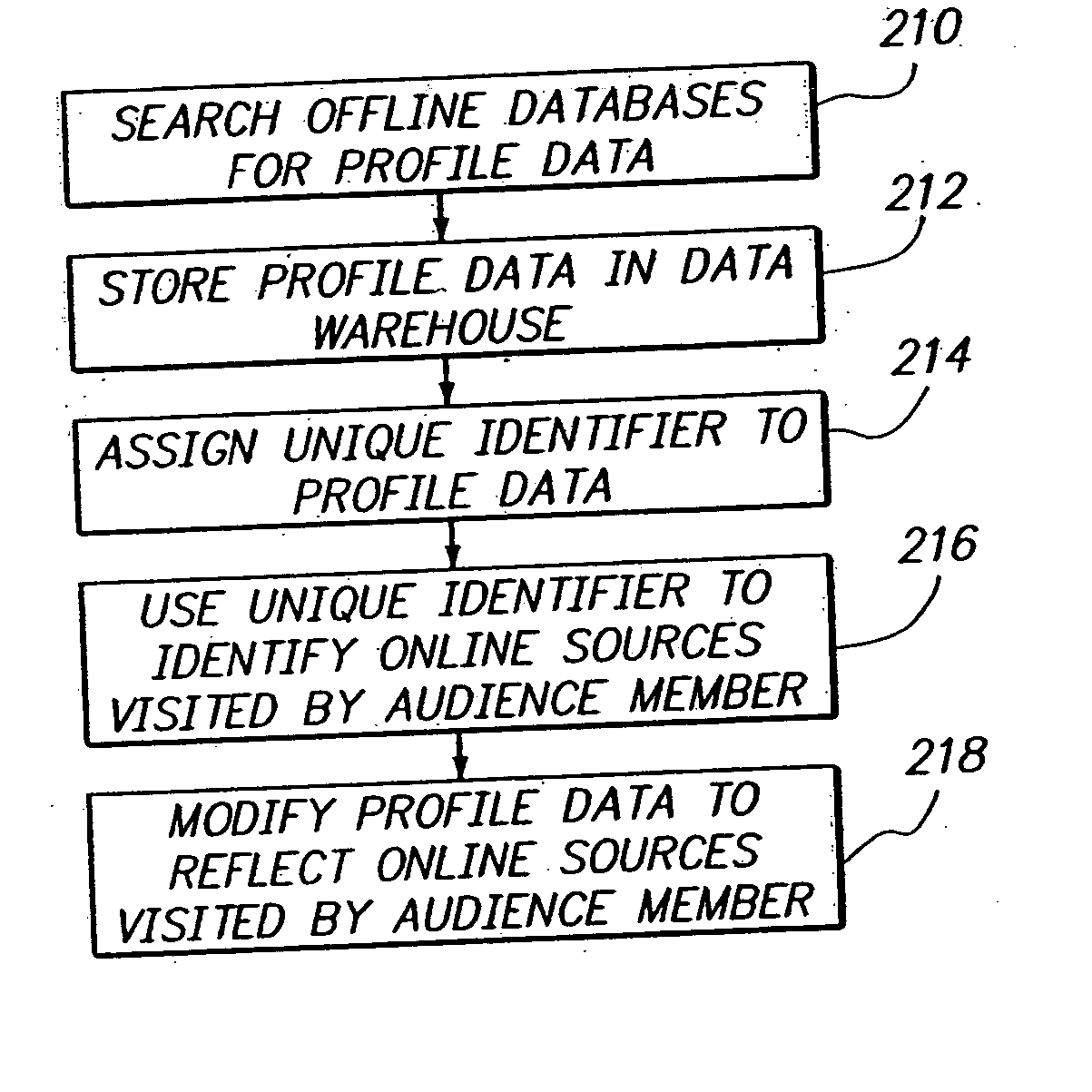
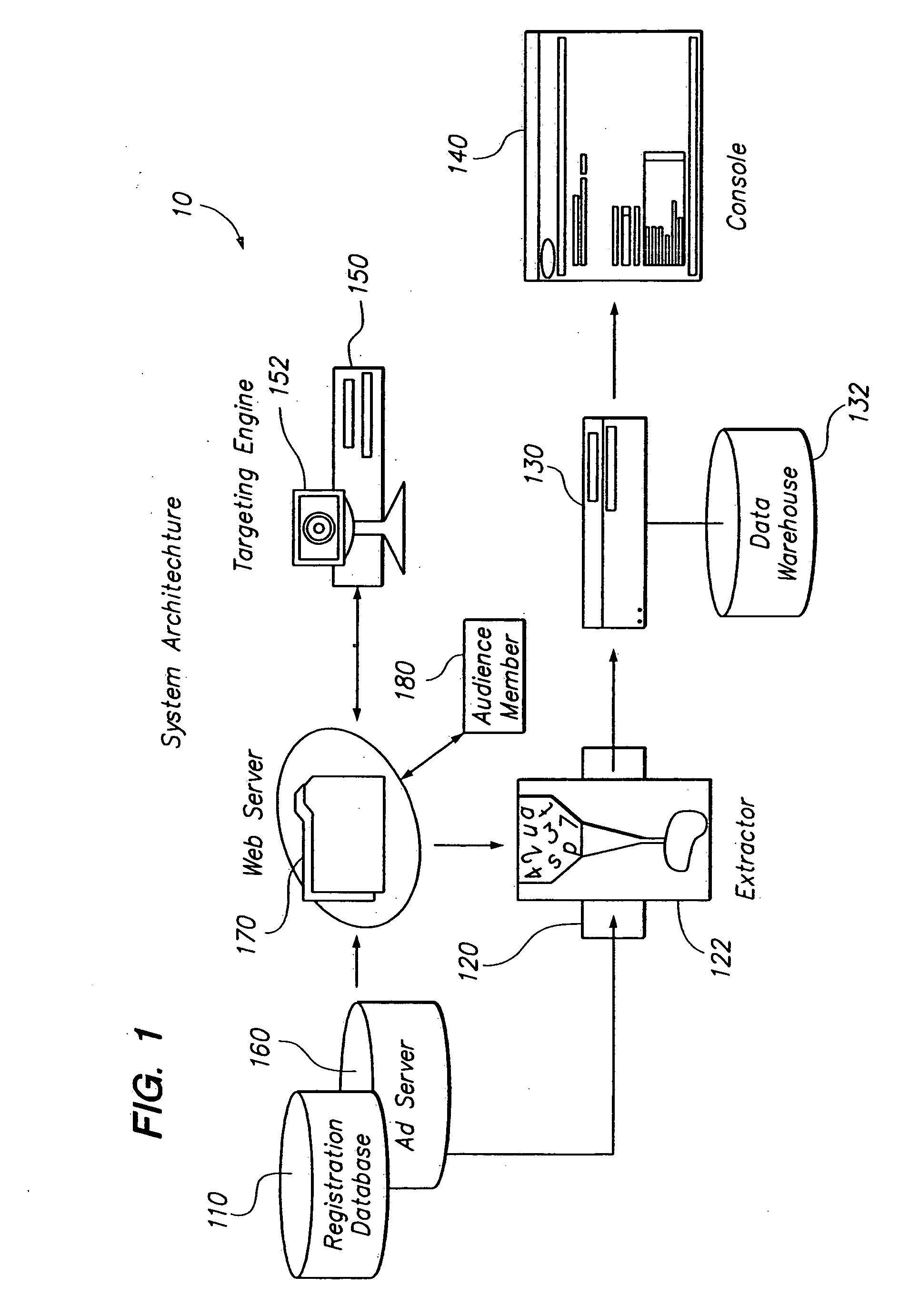
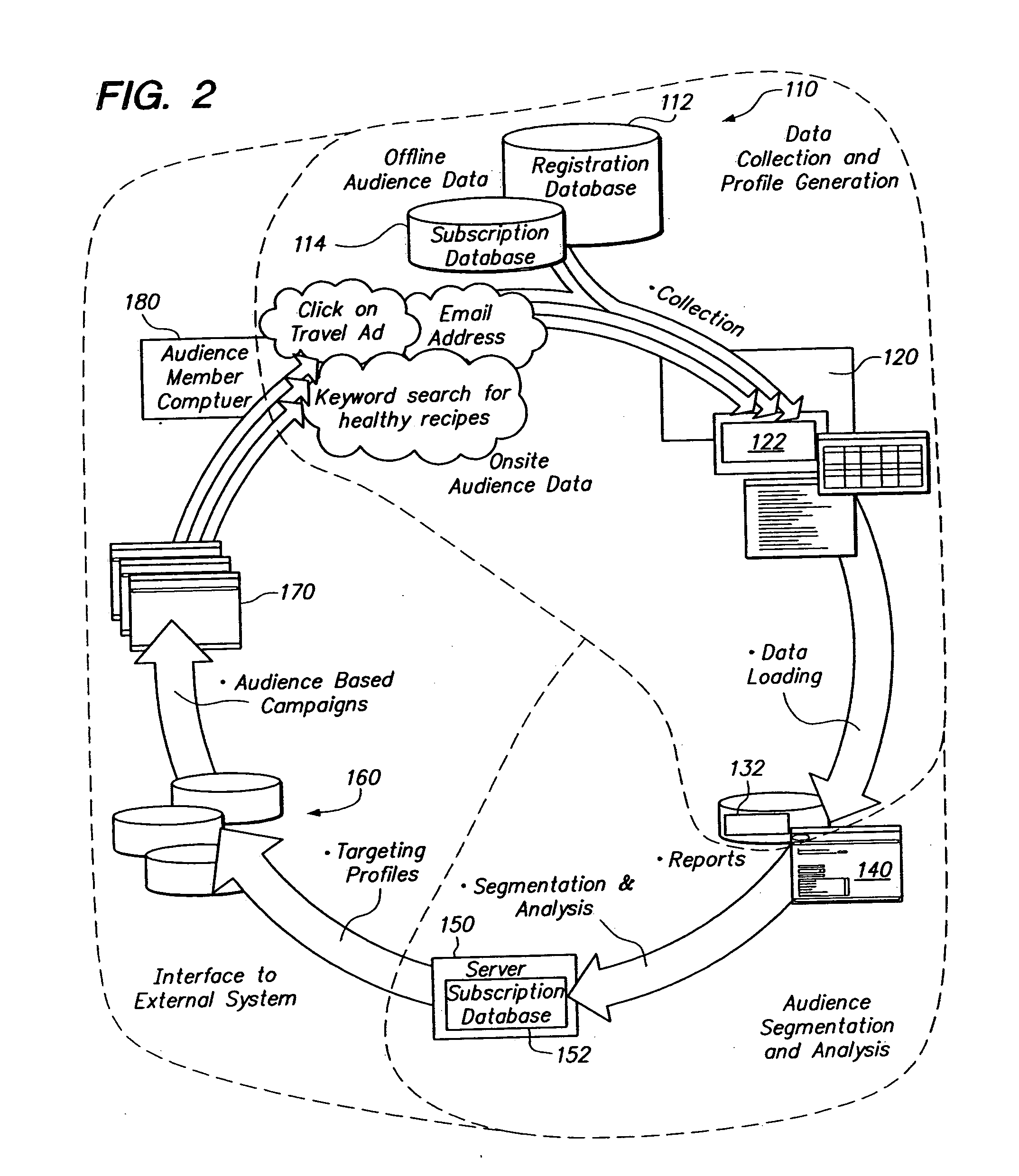
Audience server
ActiveUS20050246736A1Enhanced content deliveryReduce deliveryTelevision system detailsBroadcast systems characterised by addressed receiversData providerTime factor
Delivery of content such as advertisements to audience members. Profile data is collected regarding audience members to whom advertisements may be delivered, such that a given audience member has an established profile data. Upon receiving a request to serve an advertisement to an audience member, a recognition that the target of the request is the given audience member is made. Then it is determined that a particular advertisement should be served to the given audience member. The determination includes recognition of the given audience member and corresponding selection advertisements optimized for the recognized audience member. A configurable delivery decision making mode allows pre-optimized as well as delivery time factoring for determining advertisements. Performance criteria and revenue allocation based upon data provider participation are also provided.
Owner:YAHOO AD TECH LLC
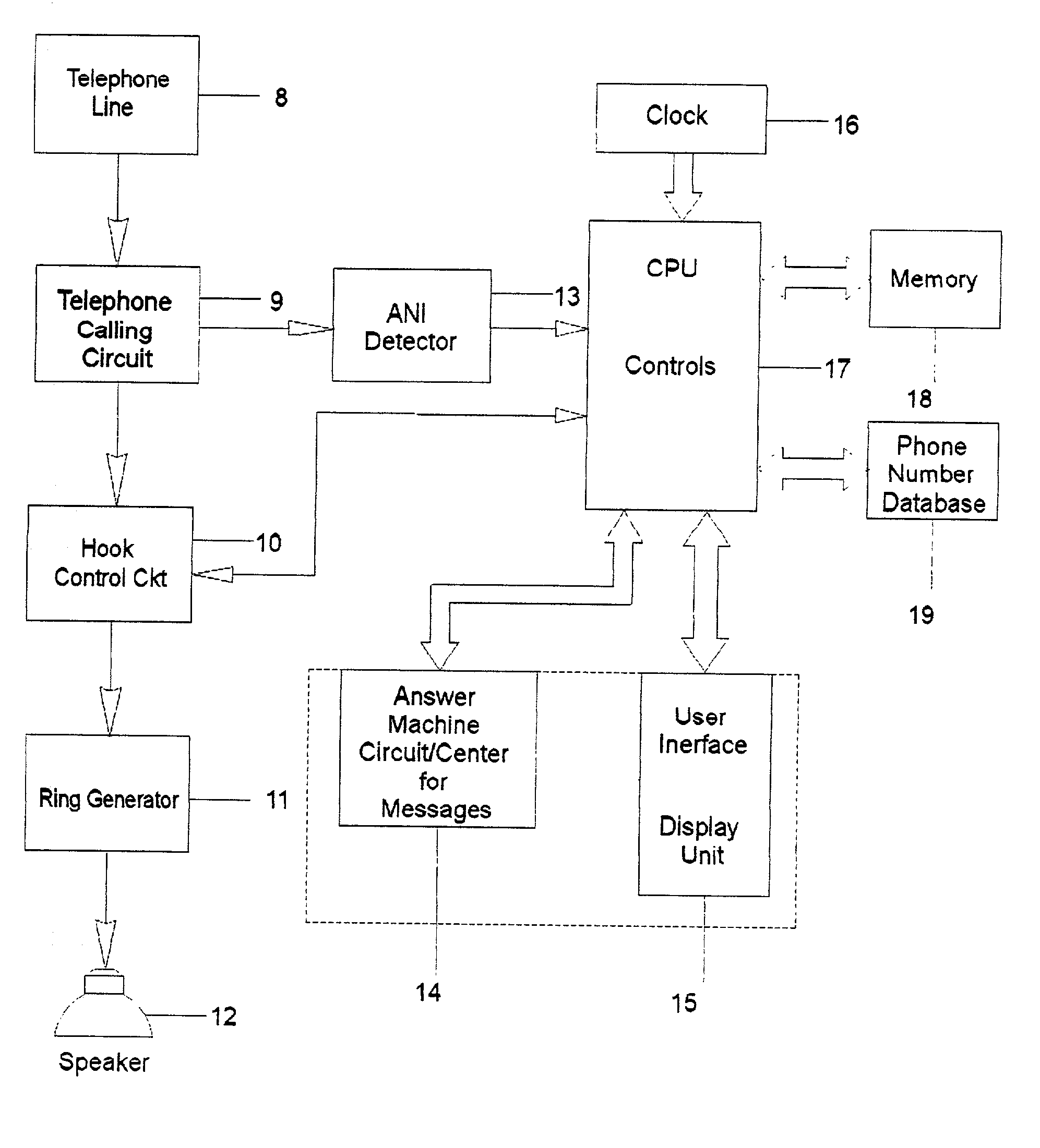
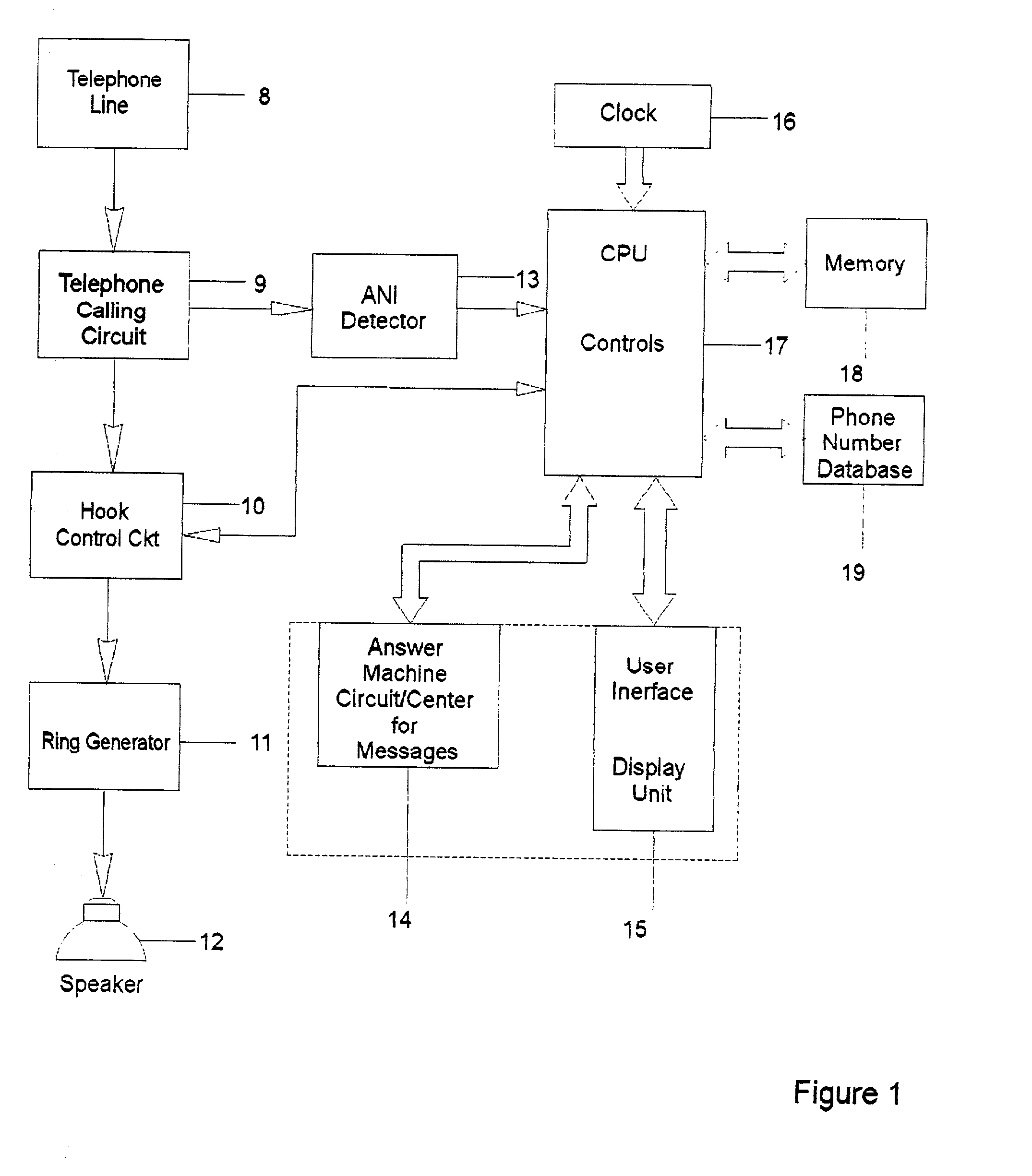
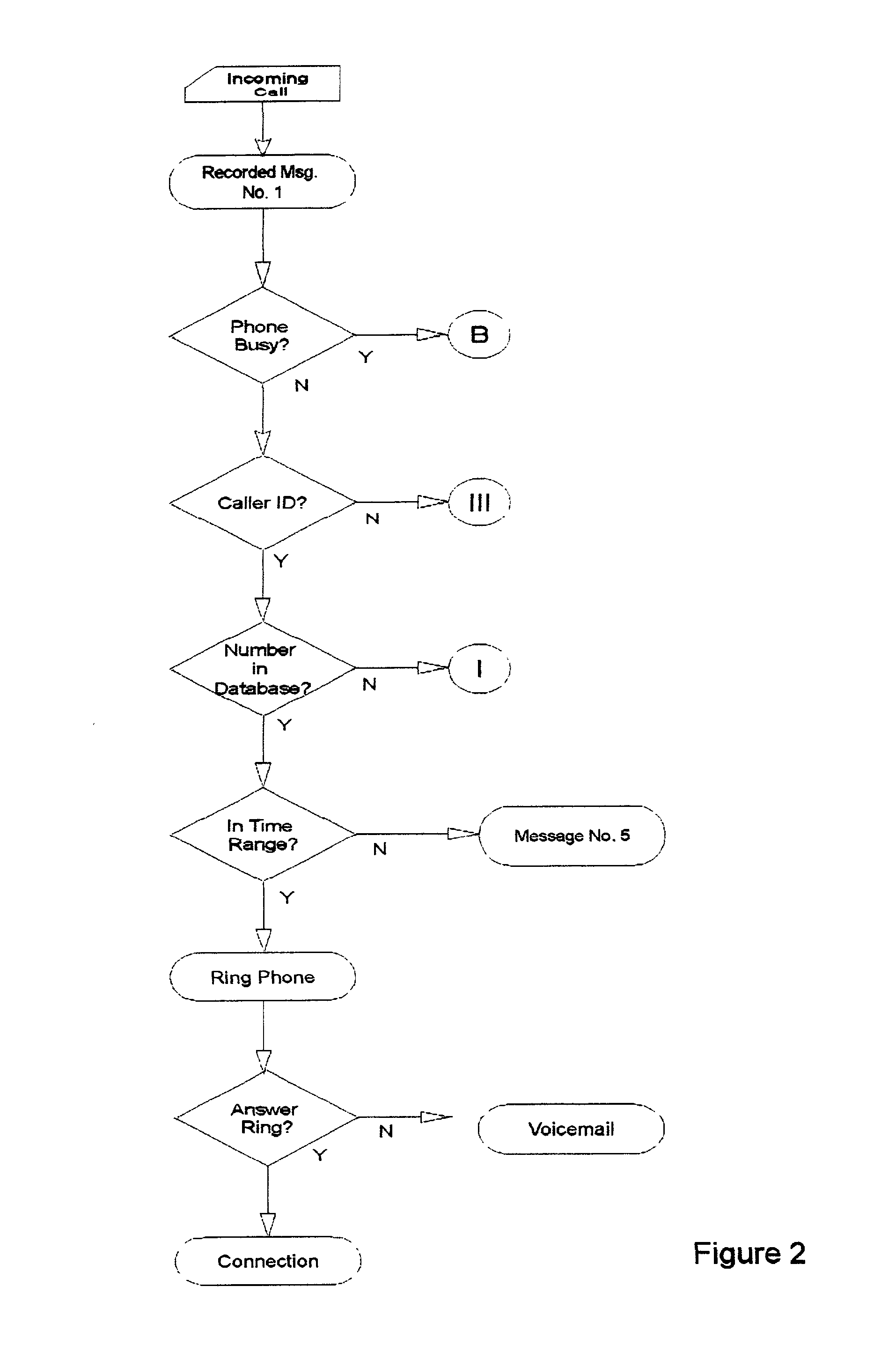
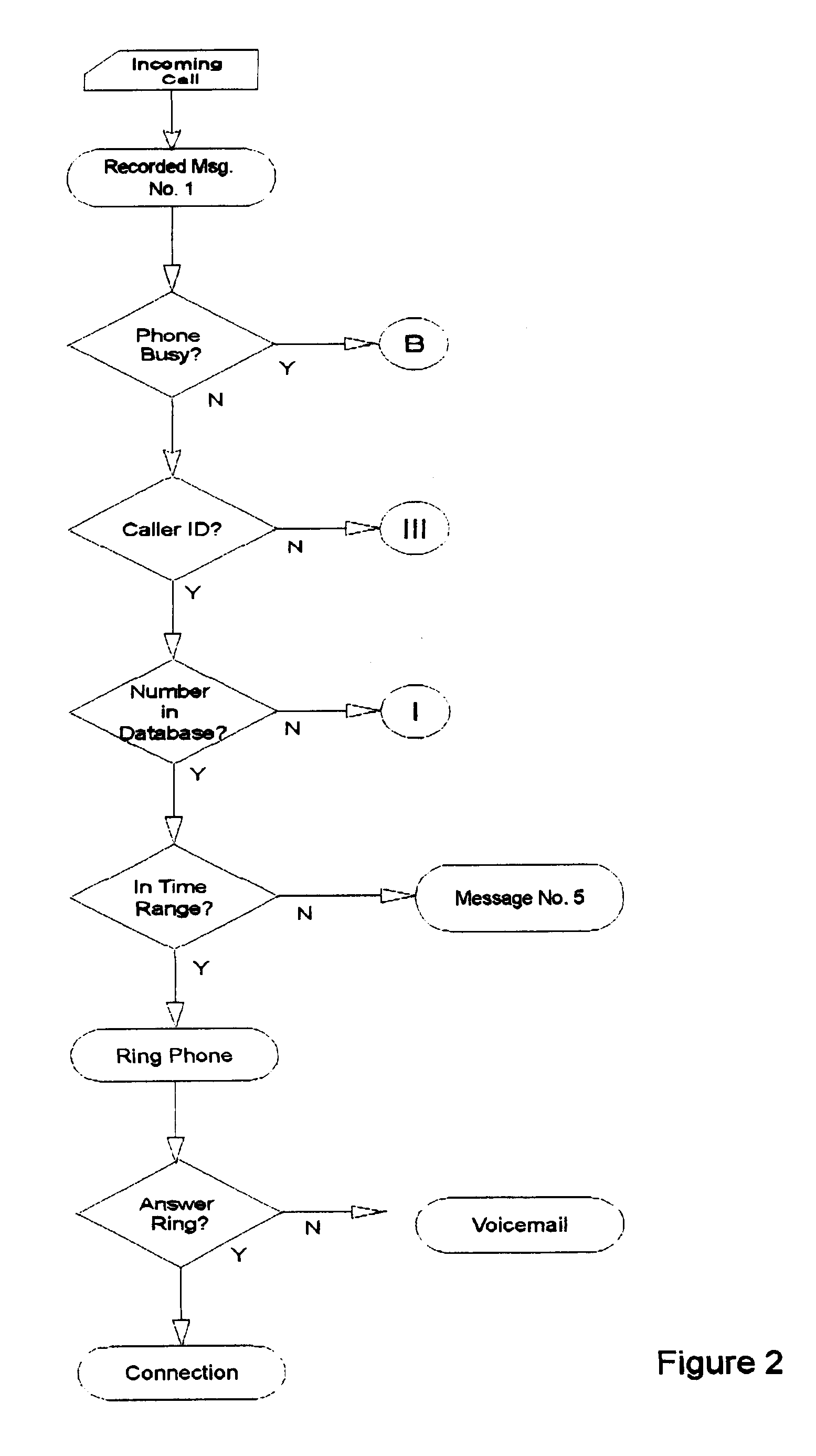
Automated personalized telephone management system
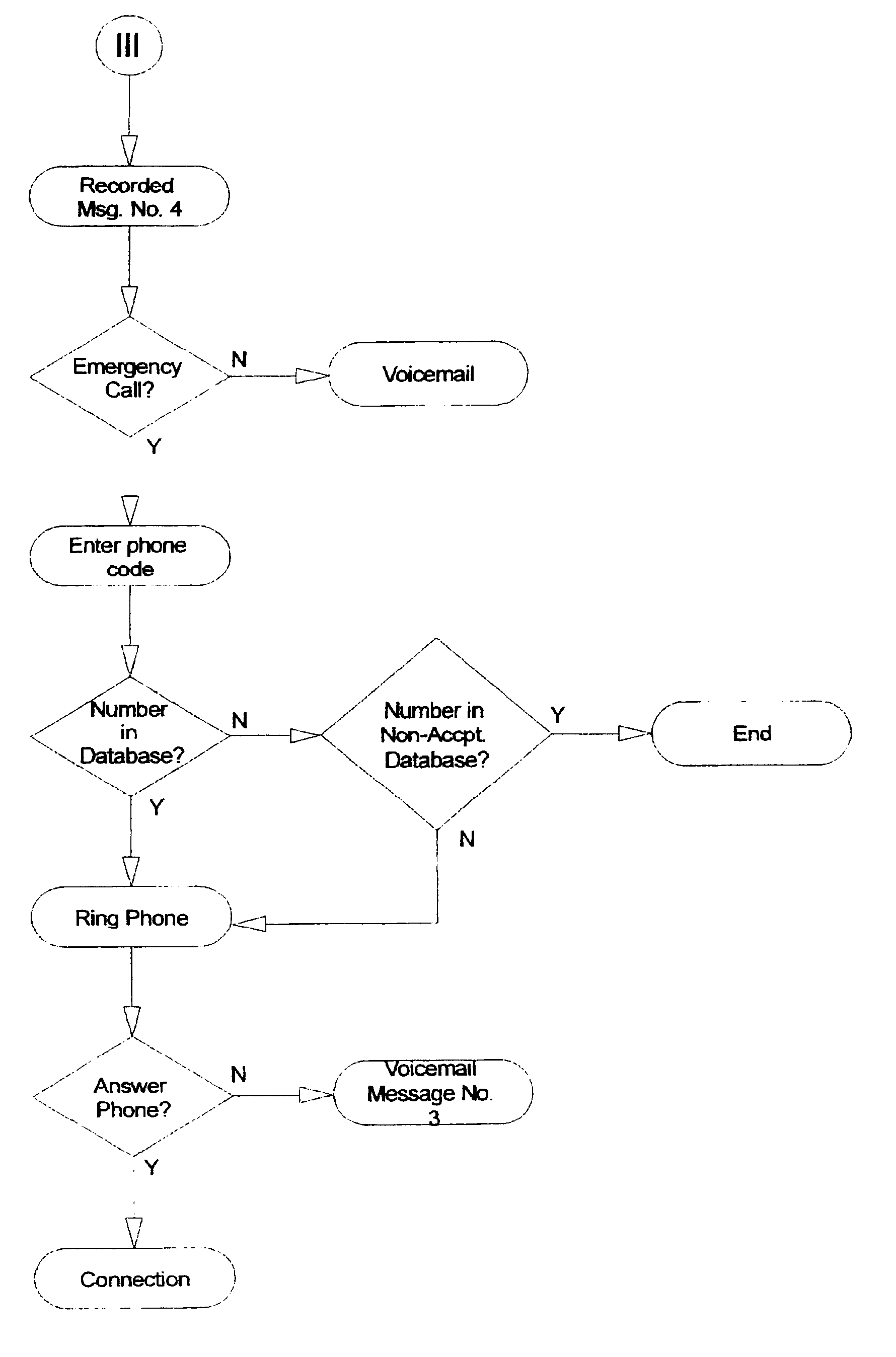
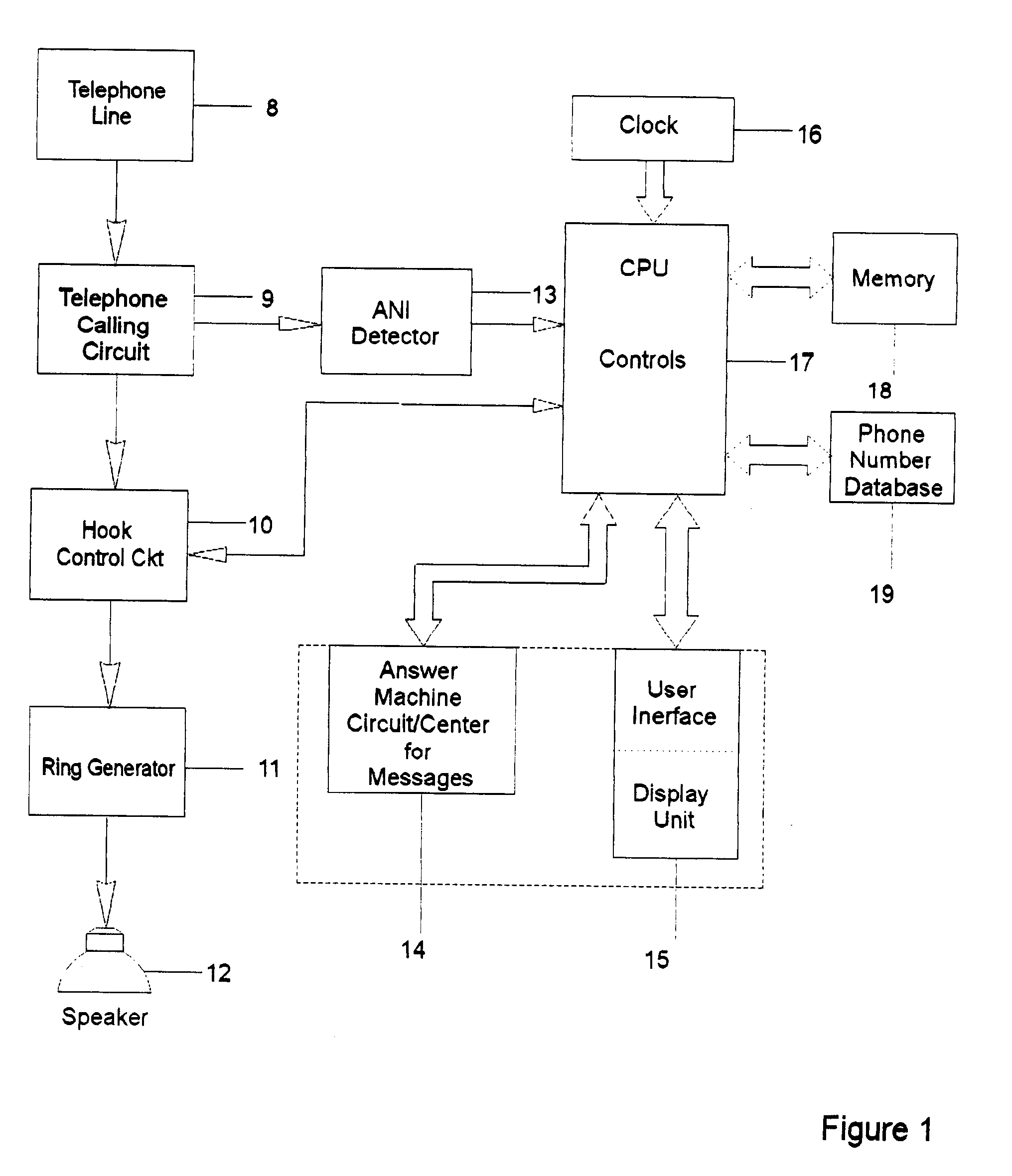
InactiveUS20020076026A1Privacy protectionAvoid spending any timeUnauthorised/fraudulent call preventionAutomatic call-answering/message-recording/conversation-recordingPersonalizationModem device
A holistic, automated, personalized telephone call management system is capable of responding to all incoming calls. The system employs customized software, computer chips, printed circuit board, ANI, where available, and a data input / output module, which are applied in an integrated manner to accomplish a broad array of functions important to modem household communication needs. System accepts operational time factors and telephone numbers as stored data to be matched automatically with the telephone numbers of incoming calls. The telephone rings under certain qualifying criteria, and an incoming call is passed in silent mode to a smart answering machine under other criteria. The smart answering machine is capable of handling emergency call situations, and the integration of call-waiting options. System also has a smart software function to deal with a state of delinquency on any lease / rent contract for the system.
Owner:BATTEN BOBBY G
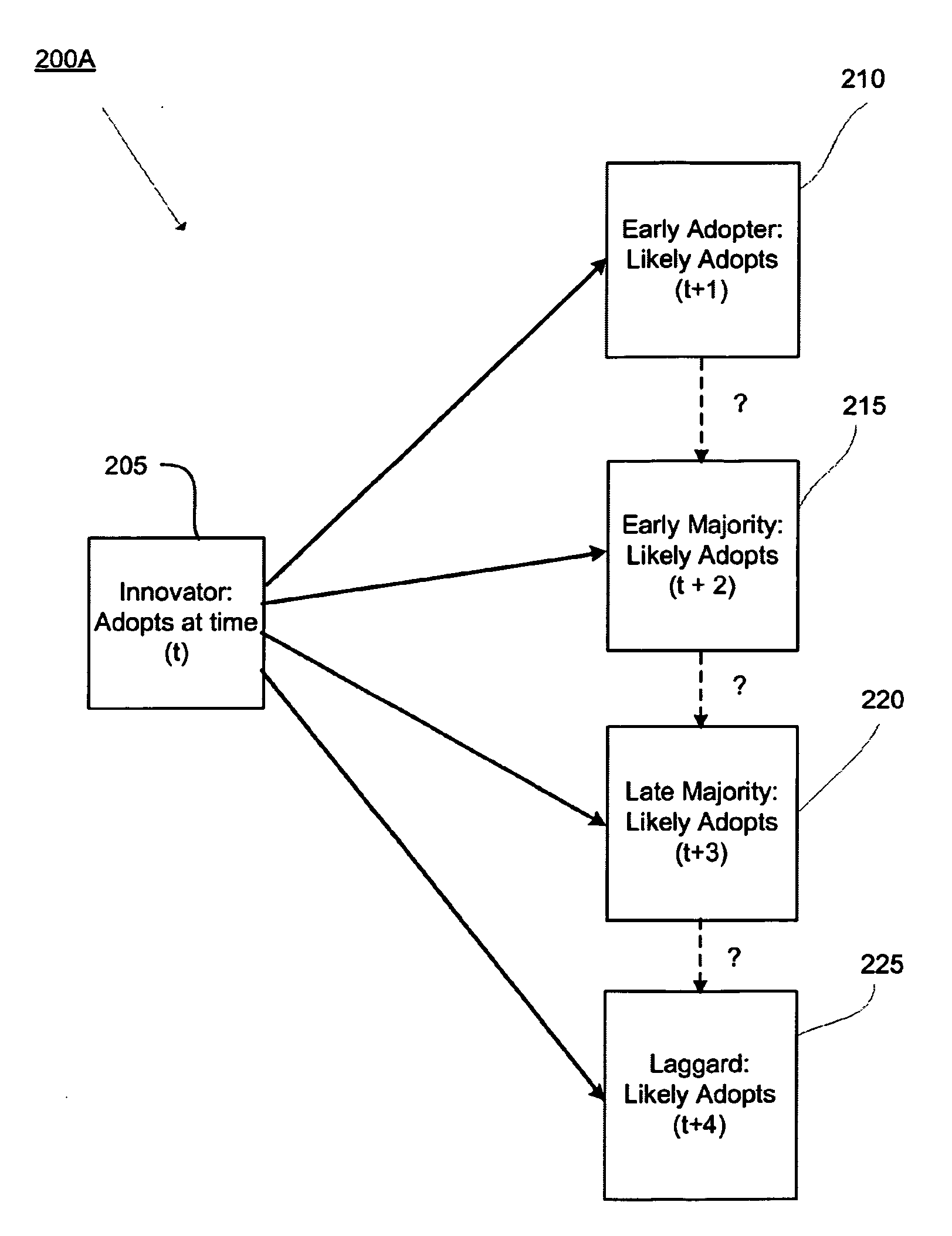
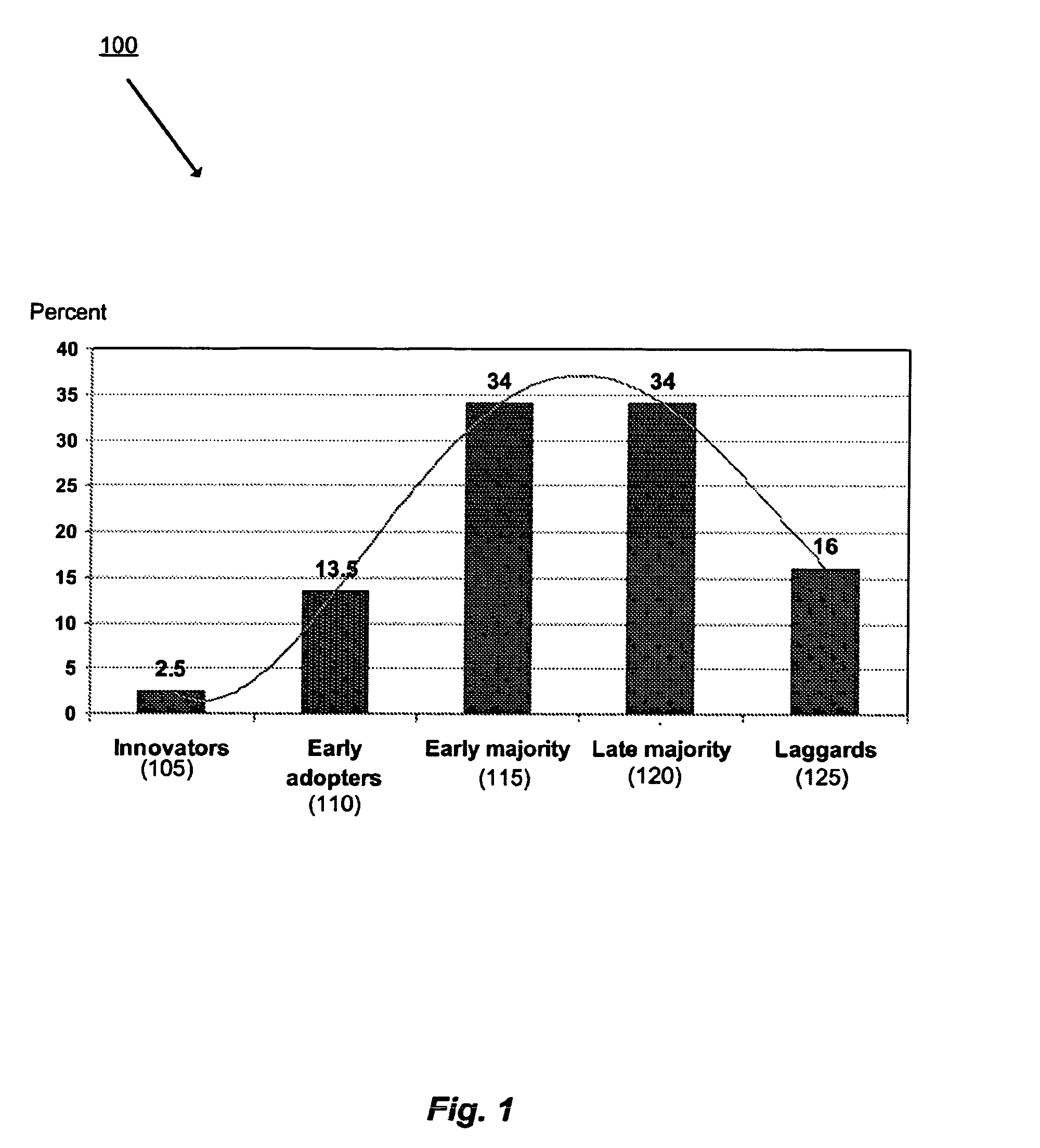
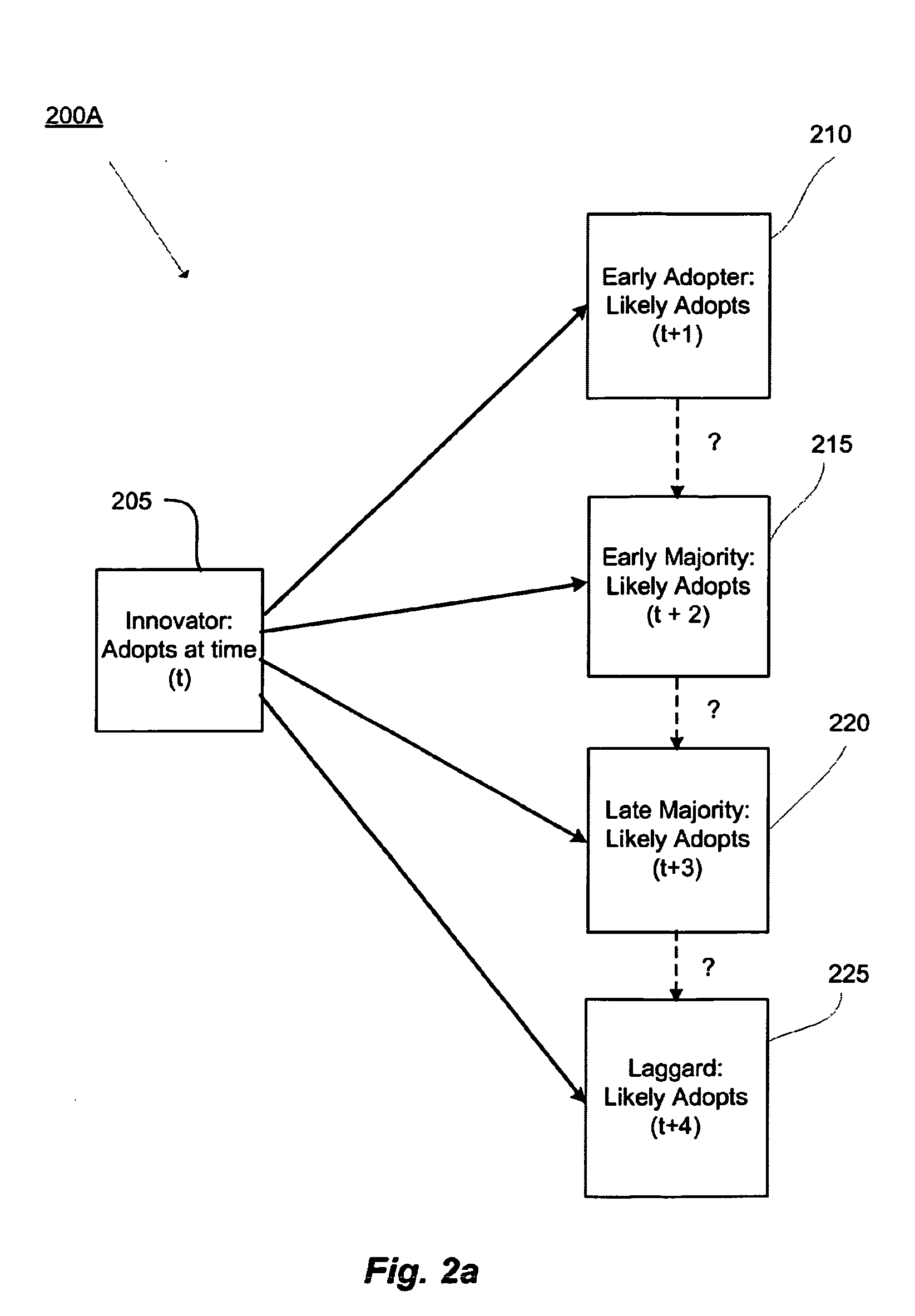
Methods and systems for utilizing a time factor and/or asymmetric user behavior patterns for data analysis
Methods and systems for data mining and analysis that may be used for capturing user / entity behavior, providing influence filtering and / or providing recommendations. One particular use may be for providing, among other things, personalized recommendations. The methods and systems may include generating an influence network. The influence network may include a user's adoption behavior of items. The influence network may further include temporal aspects of information flow or diffusion of information through the network. The influence network may also include adoption time(s) of one or more item(s) between users / entities. Further, the influence network may include asymmetric user / entity adoption behavior. Methods and systems of influence filtering are provided that include generating asymmetric relationship(s) between users and providing a filtering module utilizing the asymmetric relationship(s) between user / entity.
Owner:NEC LAB AMERICA
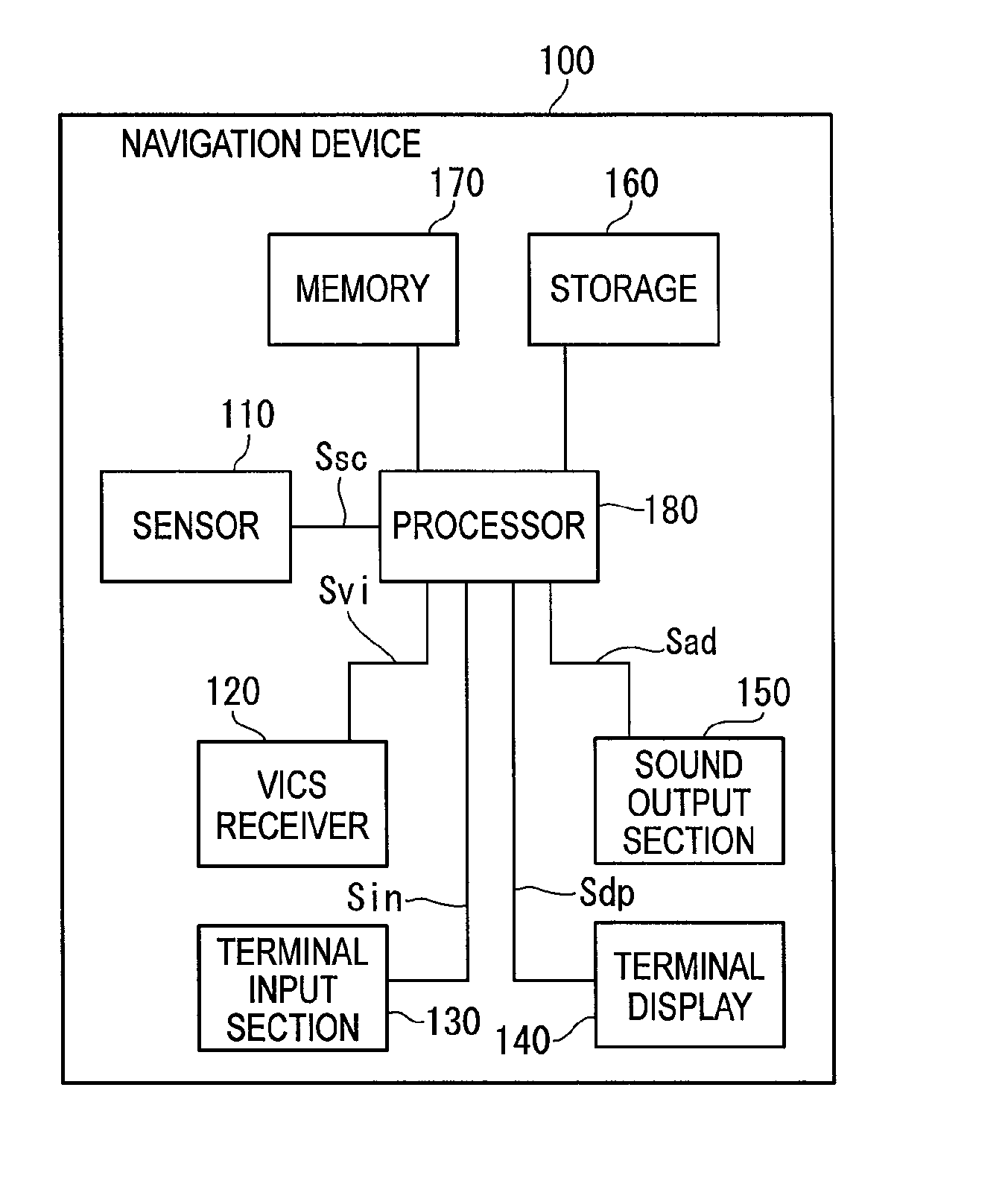
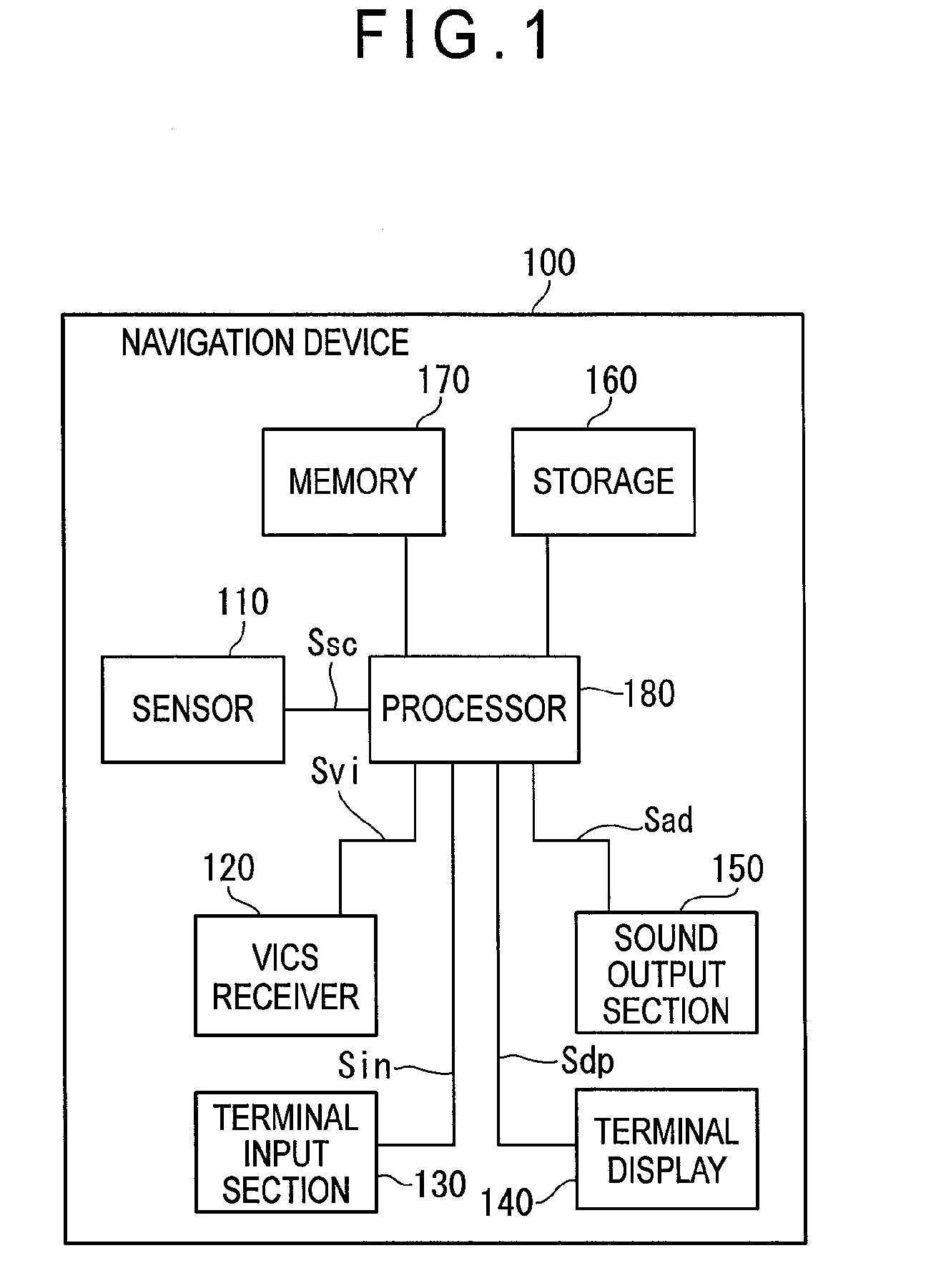
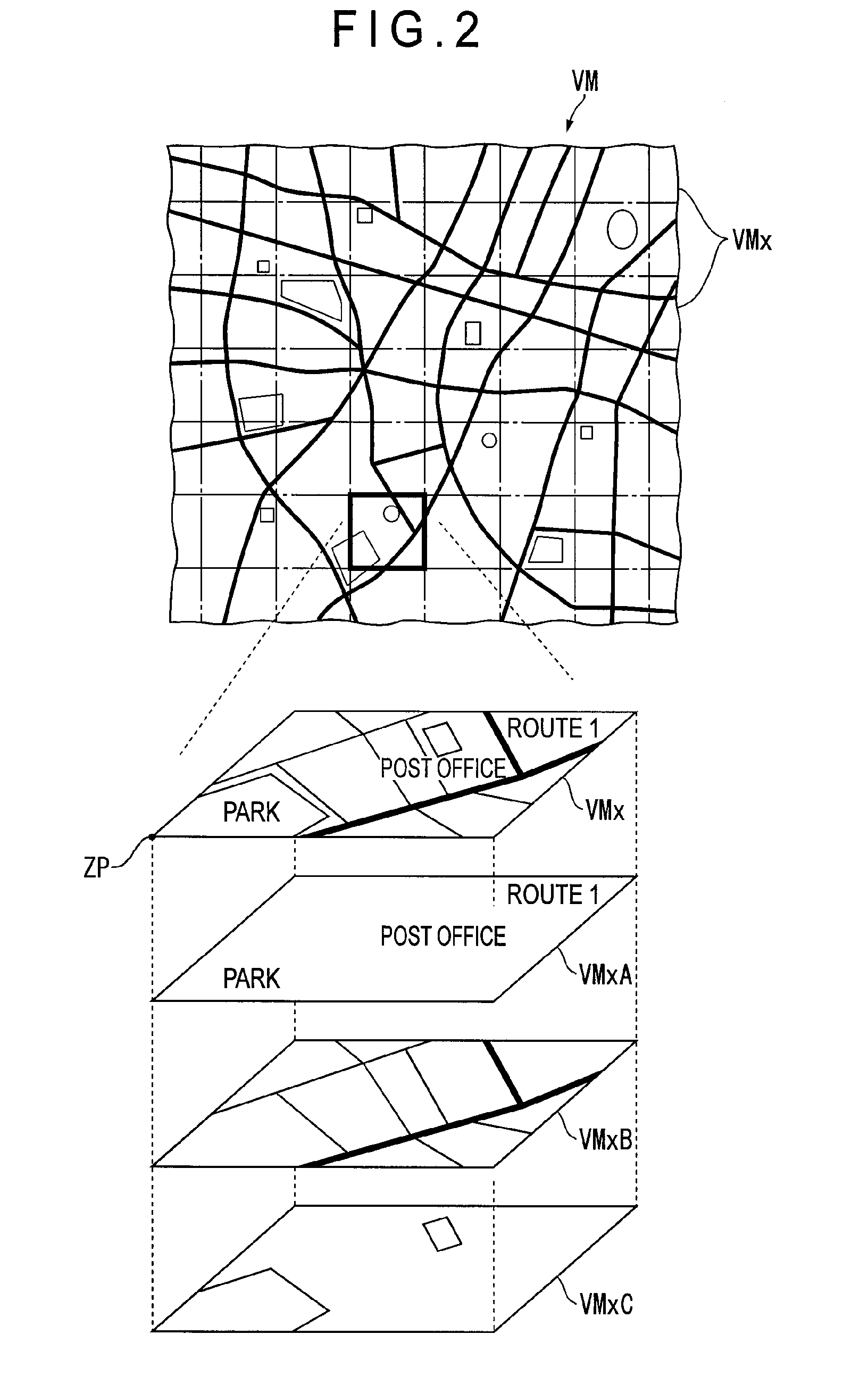
Guiding device, system thereof, method thereof, program thereof and recording medium storing the program
InactiveUS20050071081A1Improve smoothnessInstruments for road network navigationNavigational calculation instrumentsTraffic congestionTime factor
A route processor computes a plurality of travel routes using map information on the basis of current-position information and destination information. A travel route is set according to VICS data and traffic-congestion prediction information obtained by statistically processing the past traffic condition based on time factors, and a vehicle is navigated on the travel route. When it is determined that there is a change in travel smoothness such as a congested traffic or a heavy traffic on the travel route, the required time for the travel route and detouring travel routes is computed, and percentage is computed so that travel routes with shorter travel time have higher chances to be selected, thereby generating weighting information. On the basis of the weighting information, one of the travel routes is notified. The required time for the respective travel routes can be substantially equalized and thus preventing the concentration of heavy traffic-congestions only on certain roads. Therefore, the navigation for a smooth travel for vehicles in a stable traffic condition can be easily provided.
Owner:PIONEER CORP +1
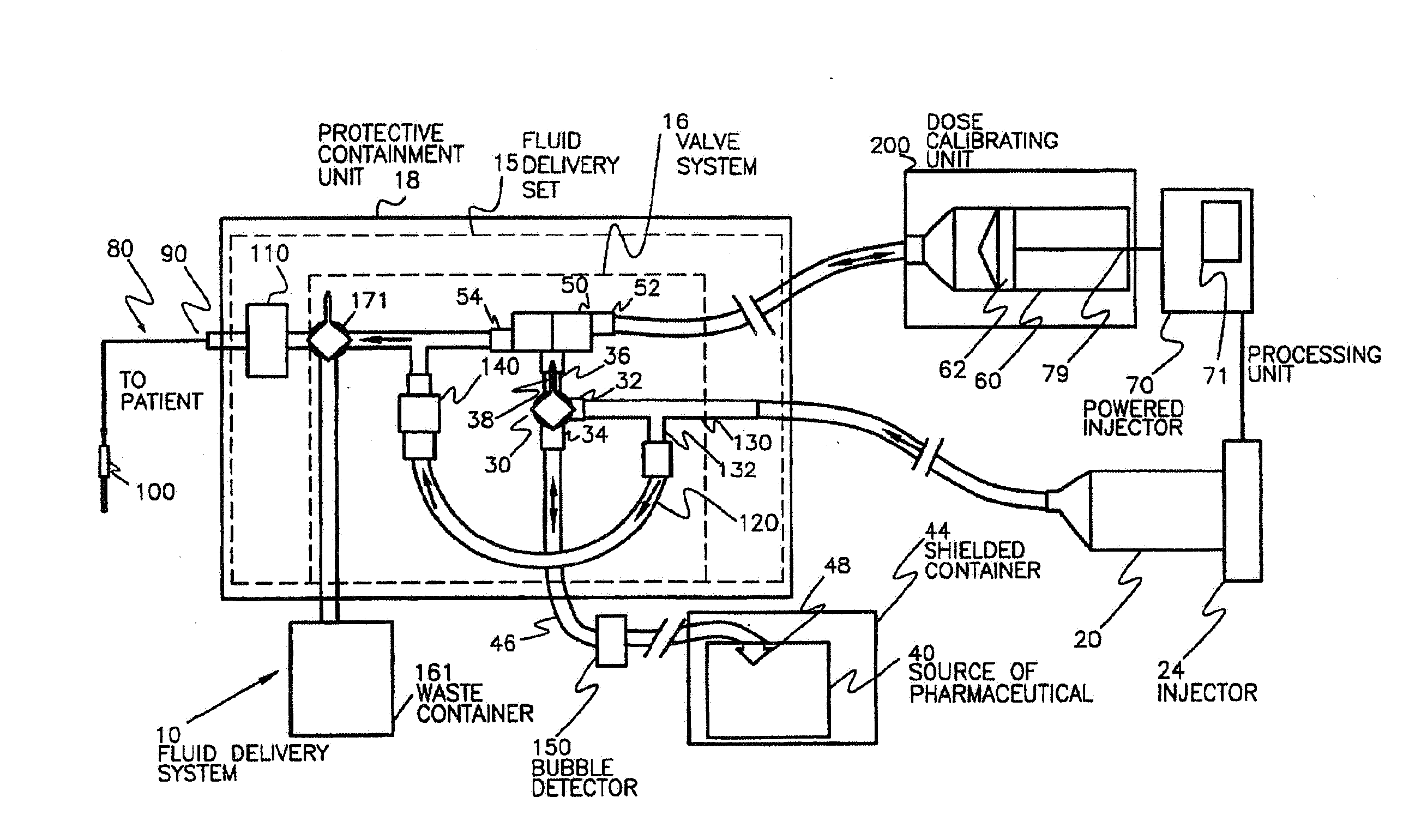
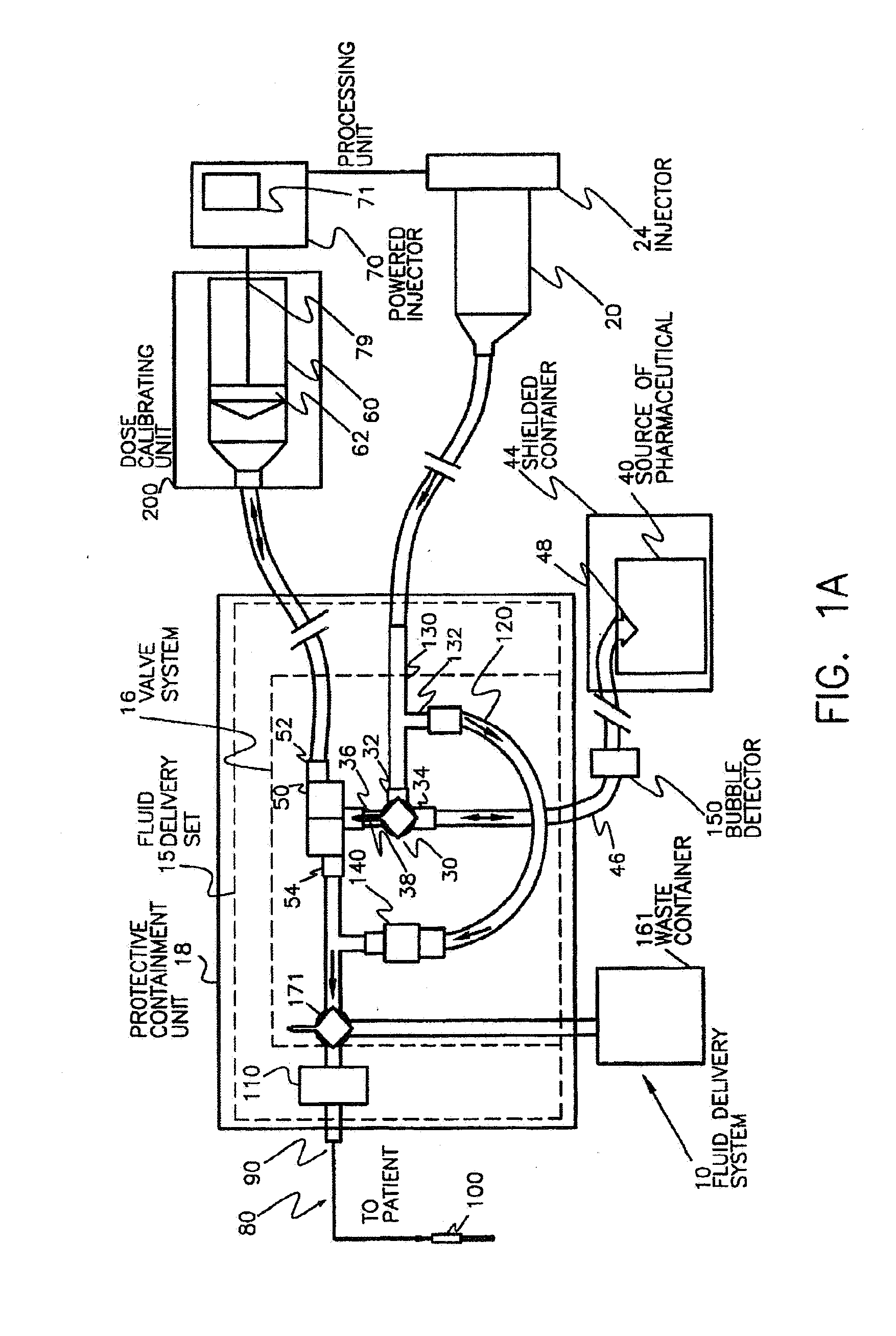
Pharmaceutical Dosing Method
InactiveUS20080166292A1Accurately determineMedical simulationIn-vivo radioactive preparationsTime factorTime standard
Systems, devices, and methods for more accurately determining a radiopharmaceutical dose administered to a patient by relying on a time factor. Particularly, broadly contemplated herein is the administration of a dose on the basis of an elapsed time from when a dose was last accurately measured in the past to when it is injected into the patient. As such, when a dose is first measured, that timepoint is preferably recorded whereupon the time of injection or administration into a patient is also recorded. Based on the original measured dose, the radionuclide (and thus its known decay rate) and the time elapsed, the dose is calculated and not directly measured on injection. The clocks on the filling station and the transport cart are synchronized to each other or to a known and accepted time standard. In this manner, there is temporal continuity and no inaccuracies of time or loss of time occurs between measurement and injection.
Owner:MEDRAD INC.
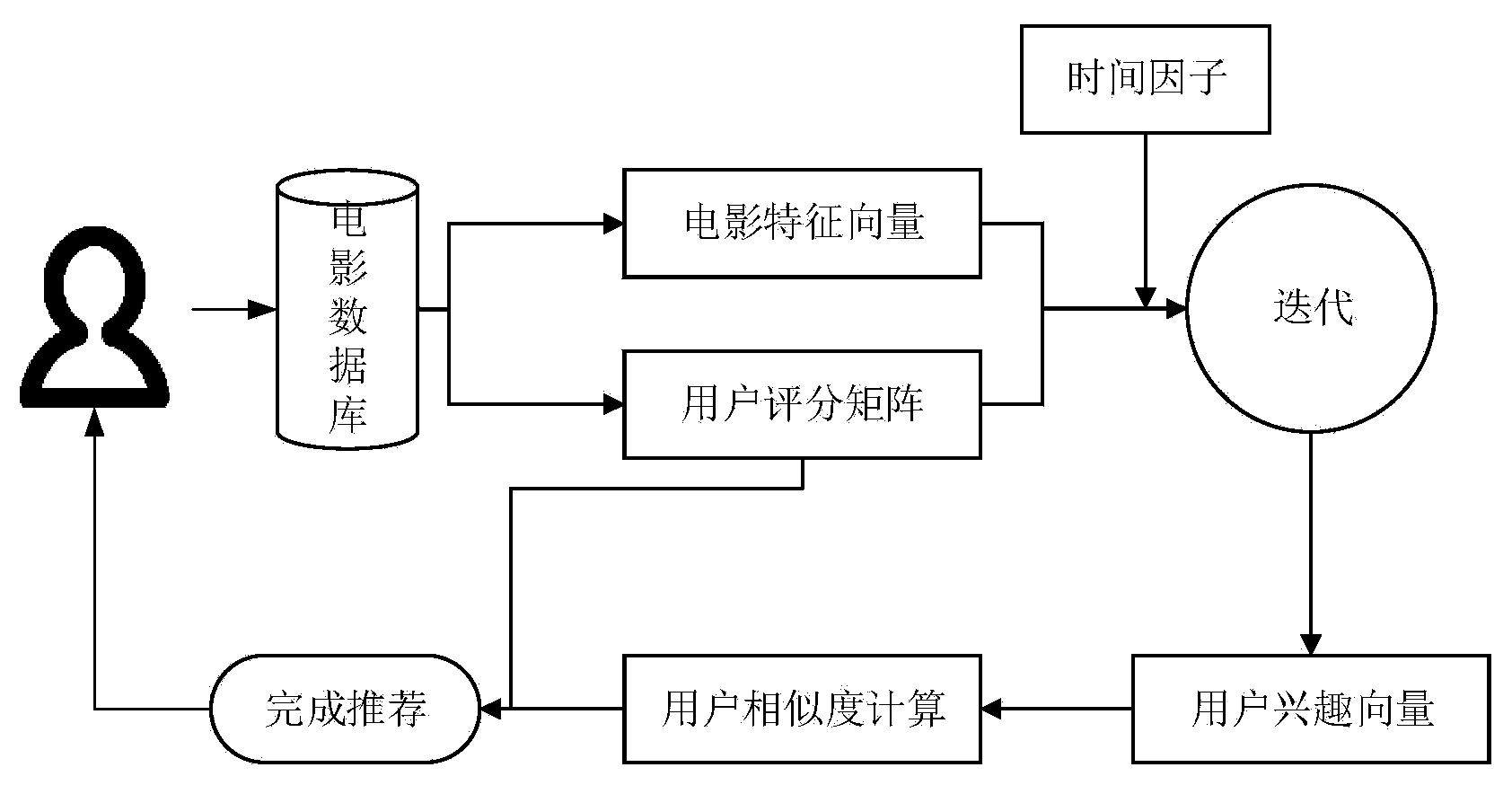
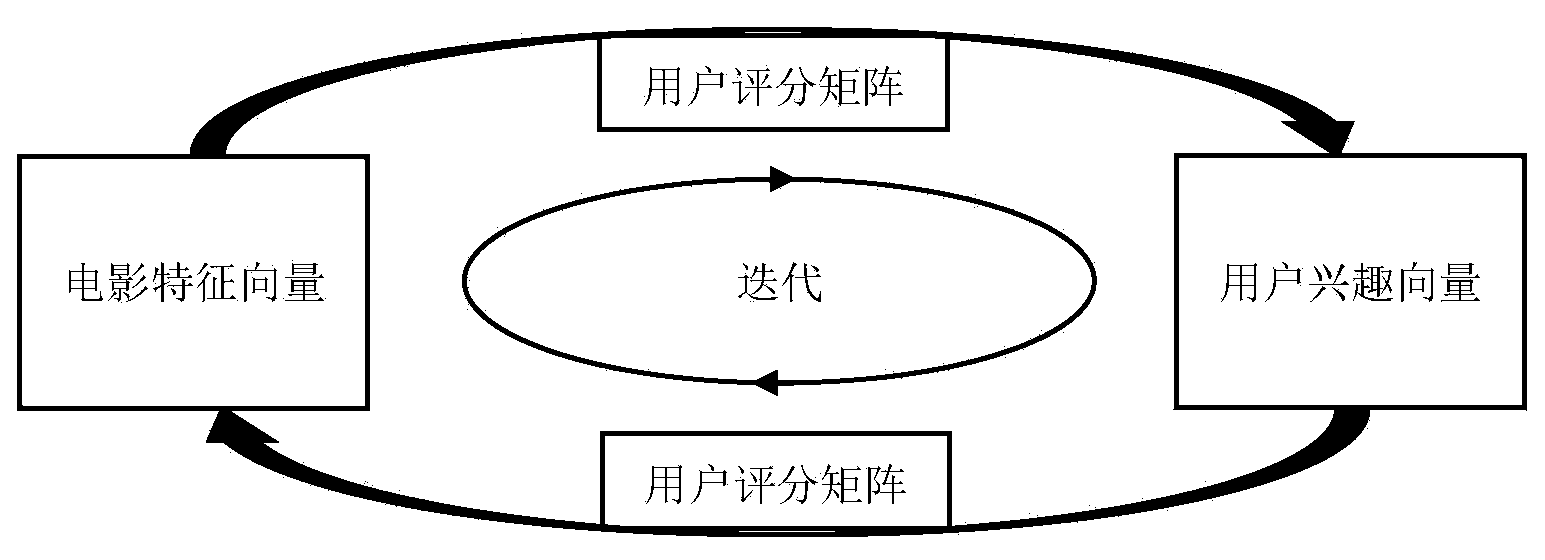
Film individuation recommendation method based on user real-time interest vectors
ActiveCN104063481AReal interest vectorReasonable modeling granularitySpecial data processing applicationsFeature vectorPersonalization
The invention discloses a film individuation recommendation method for combining film content and user real-time scoring information. The problem that a traditional recommended algorithm cannot reflect user interest change and data sparsity in time is mainly solved. In order to solve the data sparsity problem, the user interest vectors are introduced in the film individuation recommendation method. Starting from the film feature vectors, the obtained user interest feature vectors are processed in an iterative mode by the aid of a user scoring matrix, a user similar matrix is established according to the obtained user feature vectors, and finally recommendation can be achieved according to a traditional collaborative filtering scoring predicator formula. According to the user interest change condition, time factors are further integrated in the establishing process of the user interest vectors, the scoring behavior weight is bigger when scoring time more approaches the current time, and the user interest can be more represented.
Owner:SHANDONG UNIV
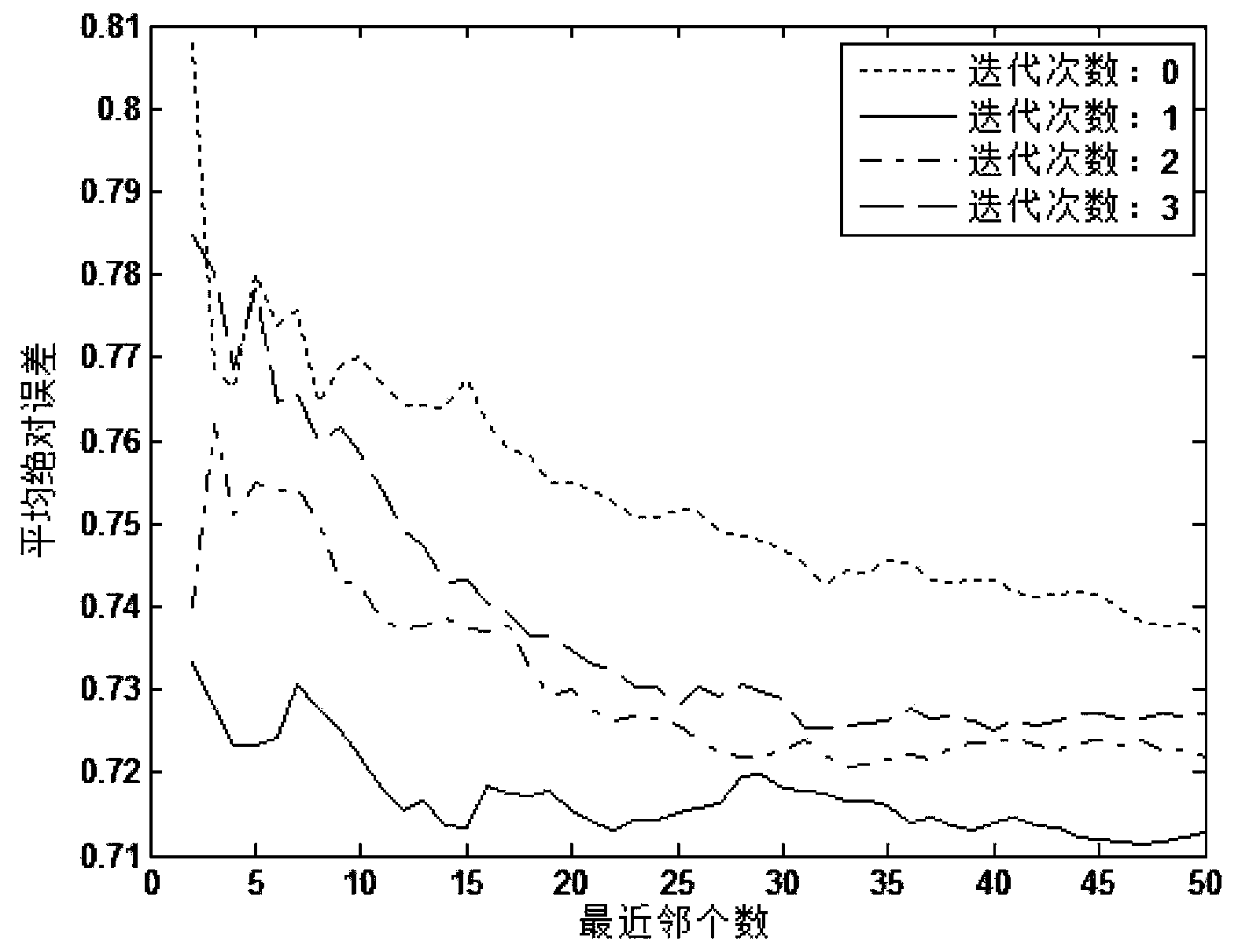
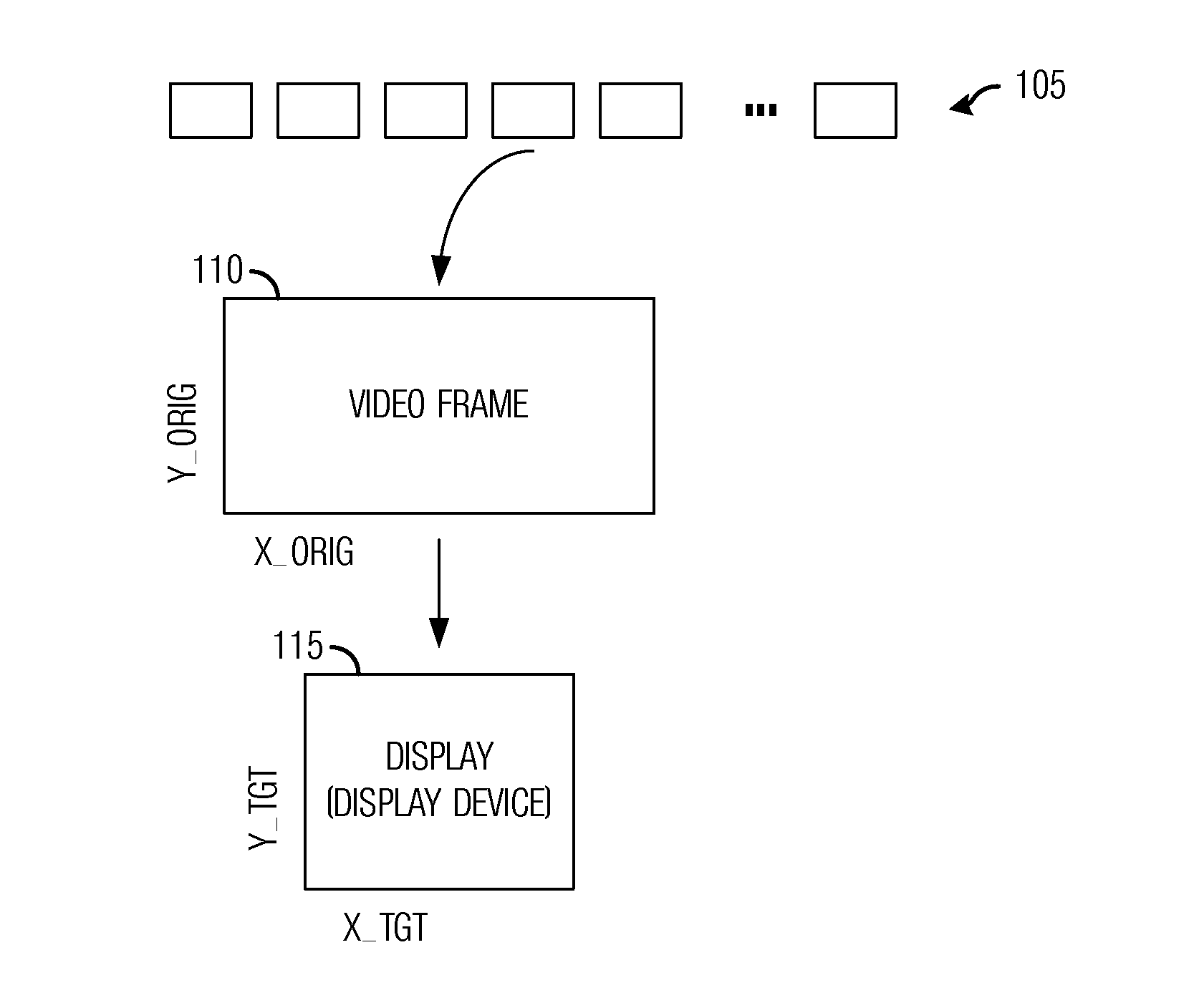
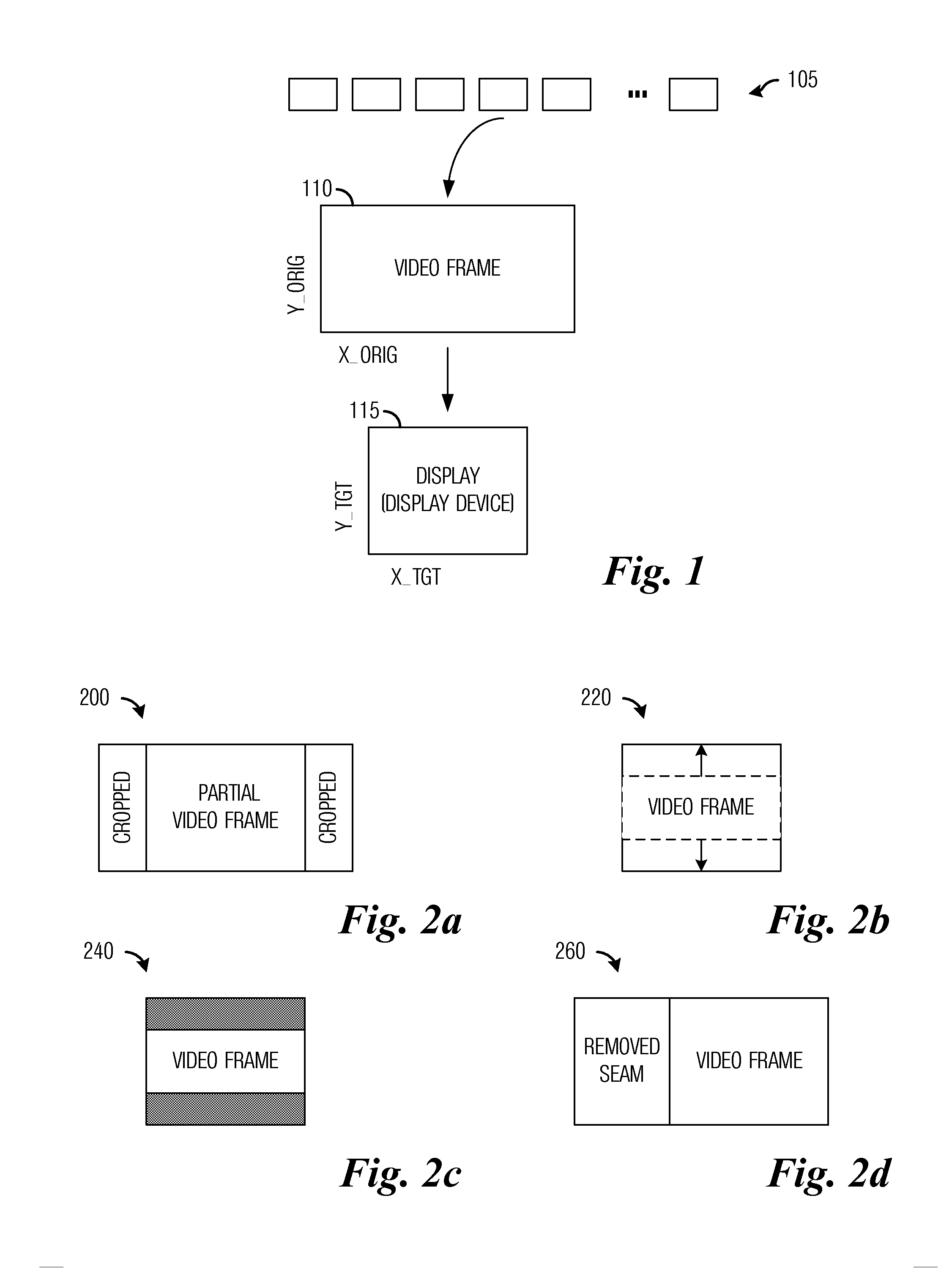
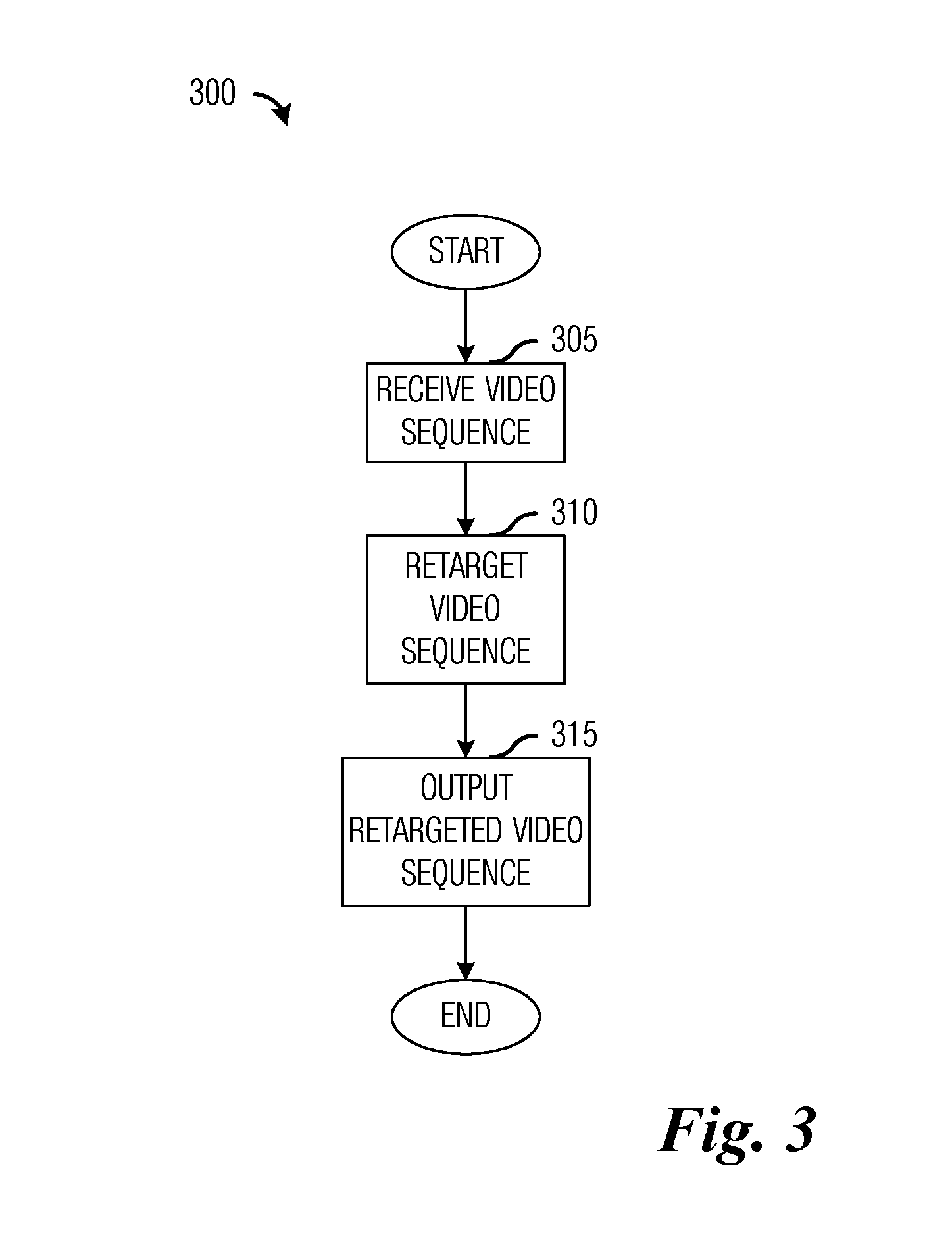
System and Method for Retargeting Video Sequences
InactiveUS20130050574A1Promote resultsImprove viewing experiencePicture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningCost metricVideo sequence
A system and method for retargeting video sequences are provided. A method for retargeting a video includes a plurality of frames includes determining saliency information for the plurality of frames, determining a cost metric for the video, and retargeting the video based on the cost metric to produce a retargeted video. The cost metric considers loss due to cropping, scaling, temporal factors, and spatial factors. The retargeting makes use of a crop window for each frame in the plurality of frames.
Owner:VID SCALE INC
Content recommending method and system
ActiveCN103544212AImprove use valueImprove recommendation effectSpecial data processing applicationsTime factorHuman life
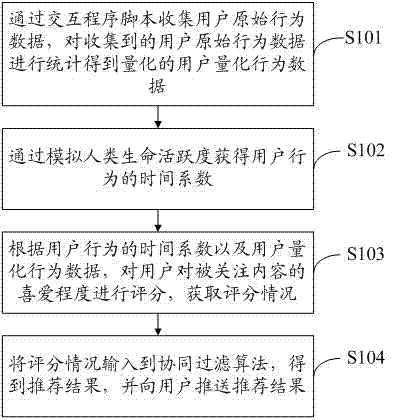
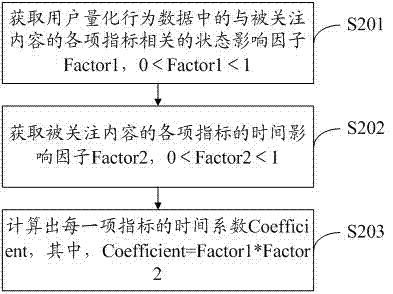
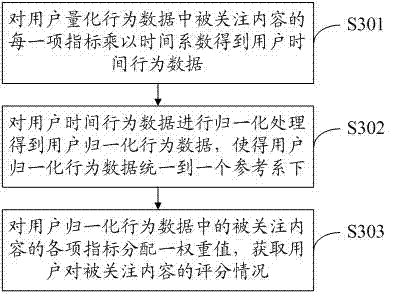
The invention discloses a content recommending method and system. The method comprises the steps of collecting user original behavior data through an interactive program script and conducting statistics on the collected user original behavior data to obtain quantized user quantitative behavior data; obtaining a time factor of user behaviors by simulating human life activity; scoring how much the user likes an attended content to obtain the scoring situation; inputting the scoring condition into the collaborative filtering recommendation to obtain a recommended result, and pushing the recommended result to the user.
Owner:TCL CORPORATION
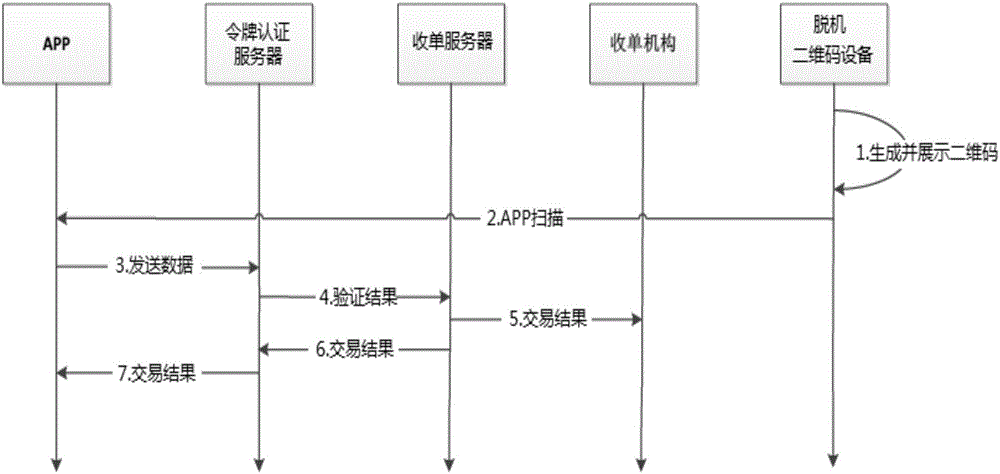
Electronic payment method and system
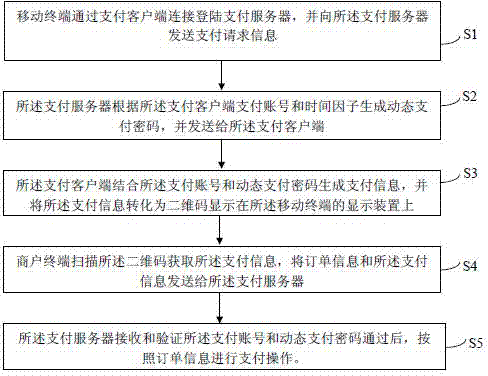
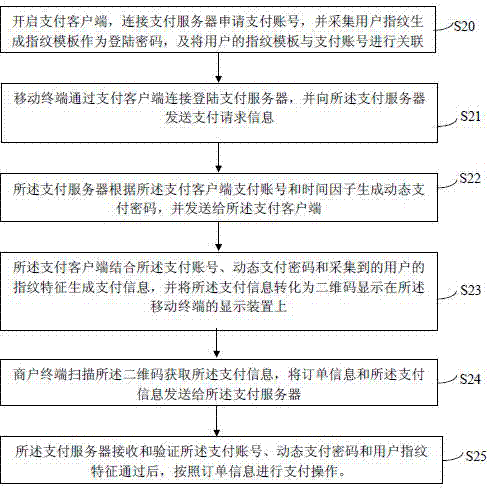
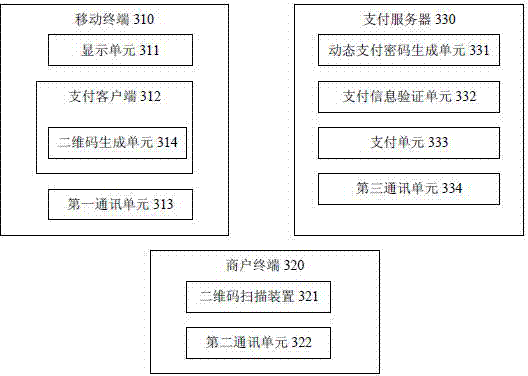
The invention discloses an electronic payment method. The electronic payment method comprises the steps that a mobile terminal sends a payment request message to a payment server; the payment server generates a dynamic payment code according to a payment account and a time factor; a payment client side generates a payment message by combining the payment account and the dynamic payment code, and converts the payment message into a two-dimensional code for display; a merchant terminal scans the two-dimensional code to obtain the payment message, and sends an order message and the payment message to the payment server; the payment server receives and verifies the payment account and the dynamic payment code, and after verification succeeds, payment operation is carried out according to the order message. According to the technical scheme, through information interaction of the generated dynamic payment code and the two-dimensional code, the safety and privacy of electronic payment are improved, and user experience is improved.
Owner:SHENZHEN ARATEK BIOMETRICS TECH CO LTD
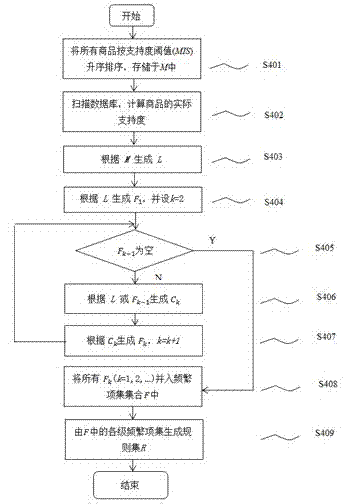
Association-rule recommending method based on self-adaptive multiple minimum supports
ActiveCN103700005APrecise personalized recommendationReduce sparsityMarketingPersonalizationValue set
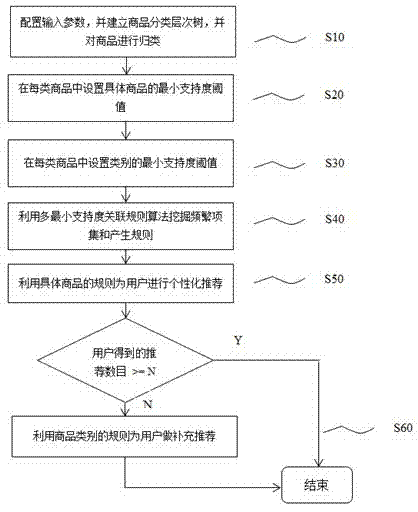
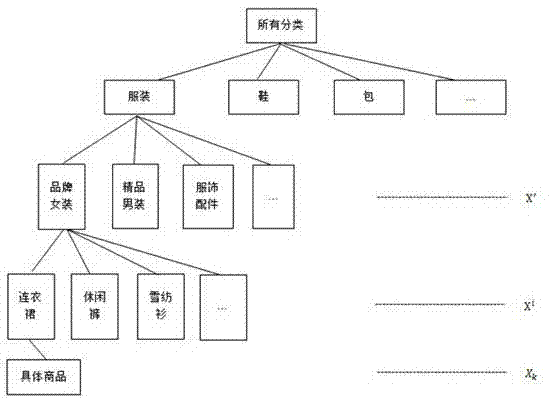
The invention discloses an association-rule recommending method based on self-adaptive multiple minimum supports. The method comprises the following steps of firstly, establishing a commodity-classifying hierarchical tree according to commodity classification, and classifying concrete commodities according to the classifying hierarchical tree; next respectively carrying out minimum-support threshold-value setting on each concrete commodity and the upper-layer class of a concrete-commodity layer, and then mining frequent item sets and generating rules by utilizing a multiple-minimum-support association-rule expanding algorithm on the basis of the support threshold-value setting, wherein the threshold-value setting relates to the influences of time factors, concrete-commodity price factors and concrete-commodity brand factors; finally generating recommendation for each user by adopting a TOP-N recommending method. When personalized recommendation is made for the user by the association-rule recommending method, the characteristics of different objects can be better embodied by considering the influences of many factors on the multiple-minimum-support threshold-value setting for the concrete commodities and the classes; meanwhile, a data-sparsity problem and a cold-starting problem in a recommending system are relieved, so that the personalized recommendation can be more accurately made for the user.
Owner:SHANGHAI ZHENKE BUSINESS CONSULTING CO LTD
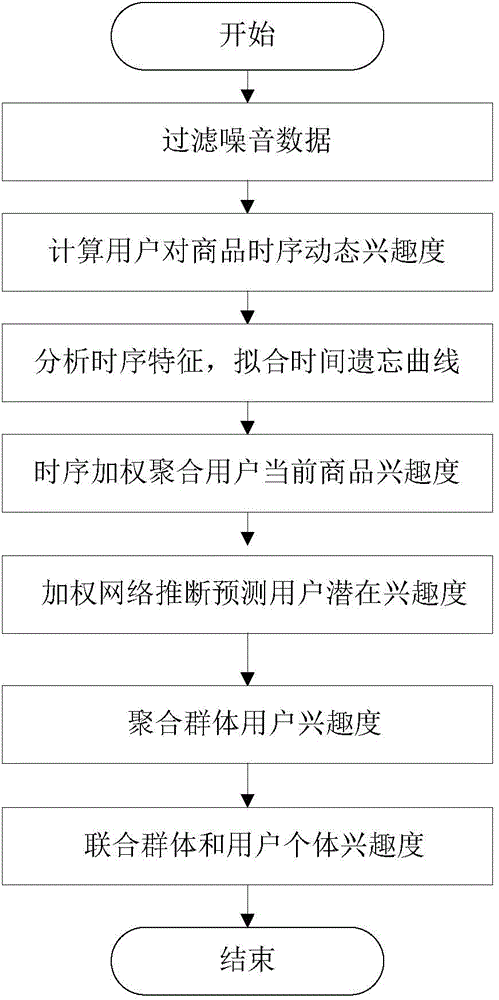
Personalized recommendation method based on group user behavior analysis
ActiveCN104866540AImprove accuracyHigh precisionSpecial data processing applicationsPersonalizationBehavioral analytics
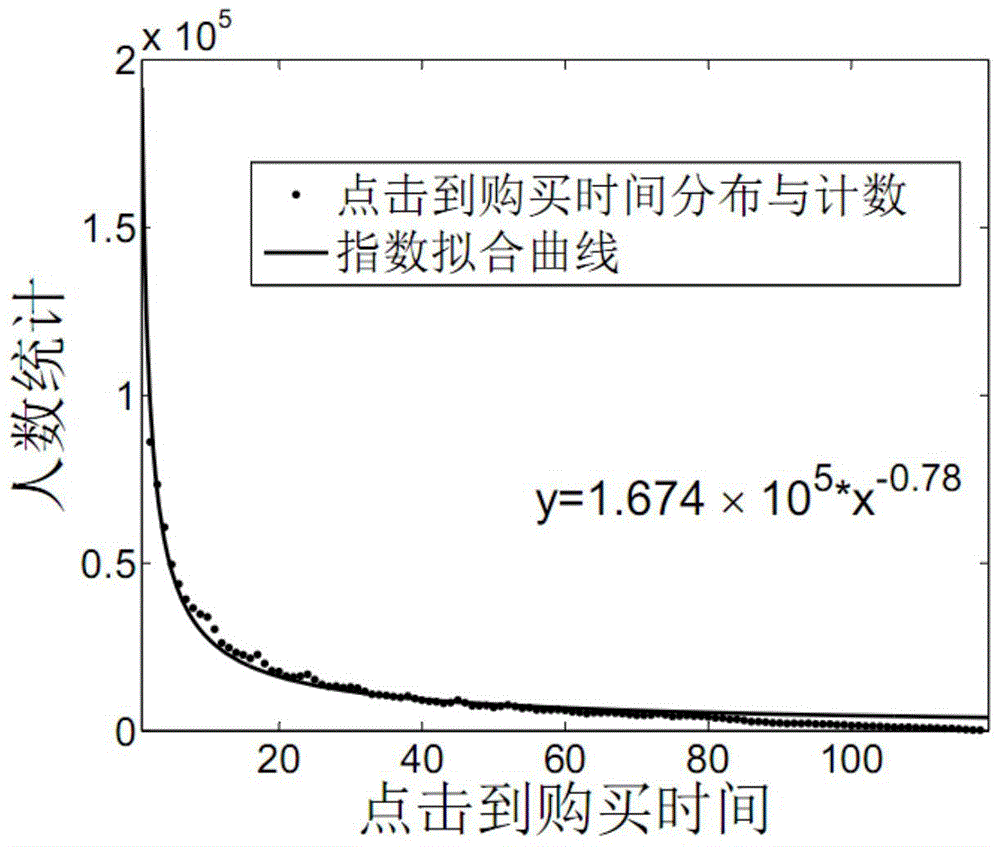
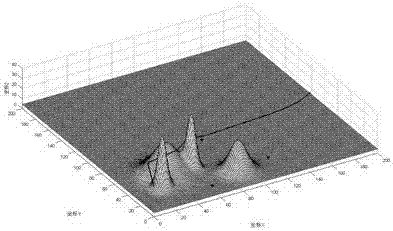
The invention discloses a personalized recommendation method based on group user behavior analysis, which belongs to the technical field of computer network application and provides a personalized recommendation method based on group user interest change, wherein a recommendation list with higher accuracy is obtained rapidly and effectively by collecting temporary dynamic interest degree of a large number of users to a commodity; in addition, the effect of time factor to a user's interest degree is analyzed quantitatively; by combining the time from contacting goods to buy goods by public users and the distribution diagram of the number of users who buy the goods at different time sections, so the accuracy of recommendation is improved; and after fully analyzing the datum of users' behaviors and summarizing the interest of users, the interest correlation between the goods and users is calculated.
Owner:HUAZHONG UNIV OF SCI & TECH
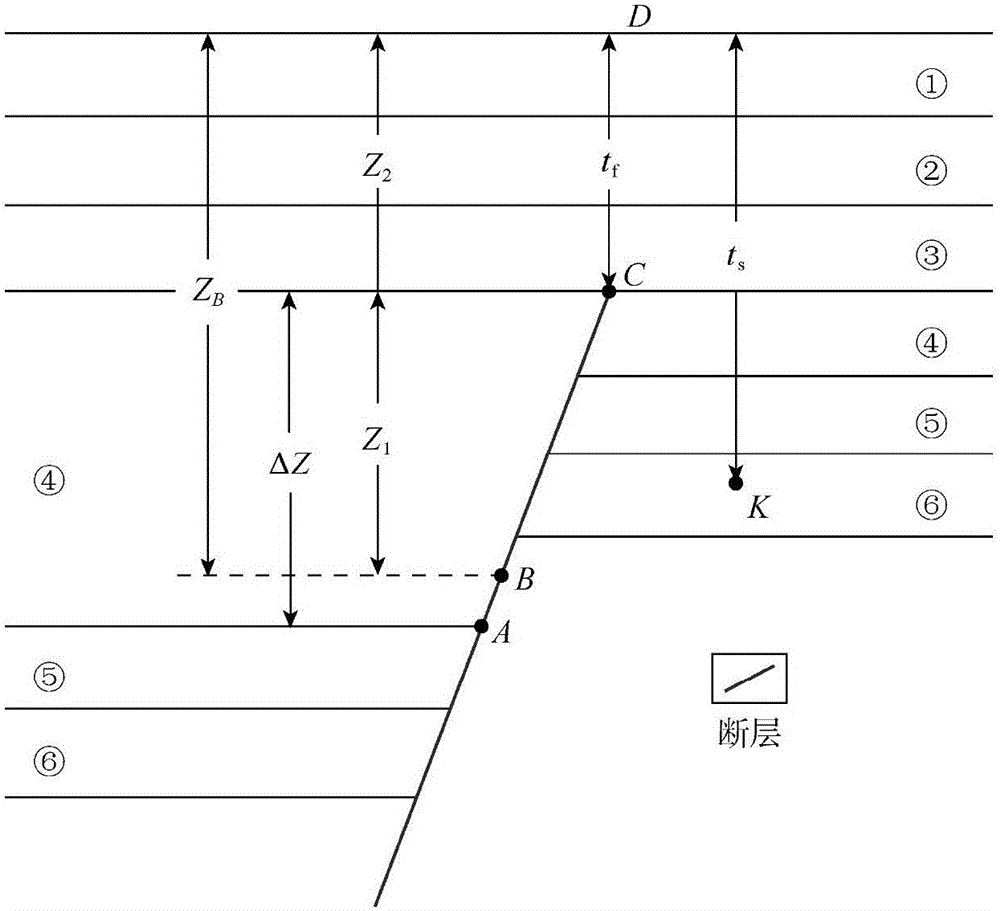
Quantitative evaluation method for lateral sealing of fault
InactiveCN105760668AThe evaluation results are in line with the actualInformaticsSpecial data processing applicationsMathematical modelEngineering
The invention discloses a quantitative evaluation method for lateral sealing of a fault.The method is mainly based on the research about the fault sealing mechanism and influence factors thereof, under the circumstance that pressure bearing time of the fault is considered, a fault-reservoir displacement pressure difference method for quantitative evaluation of fault sealing is improved, and a fault sealing quantitative evaluation geological and teaching model taking the time factors into consideration is established.The gradual-approximation algorithm with the given step length is adopted, it is determined that rocks of a surrounding rock stratum have the same shale content as a target spot stratum and the burial depth at the diagenetic degree, then according to the relation between the product of the shale content of the rocks built in a research area and the burial depth and the displacement pressure, the displacement pressure of target spot stratum rocks is calculated quantitatively and compared with the displacement pressure of a target disc reservoir stratum, and whether the fault is sealed or not as well as the magnitude of the sealing capability are evaluated quantitatively.It is verified through actual data that when compared with a fault rock shale content (SGR) method and the fault-reservoir displacement pressure difference fault sealing evaluation method which does not consider pressure bearing time, the method has feasibility.
Owner:NORTHEAST GASOLINEEUM UNIV
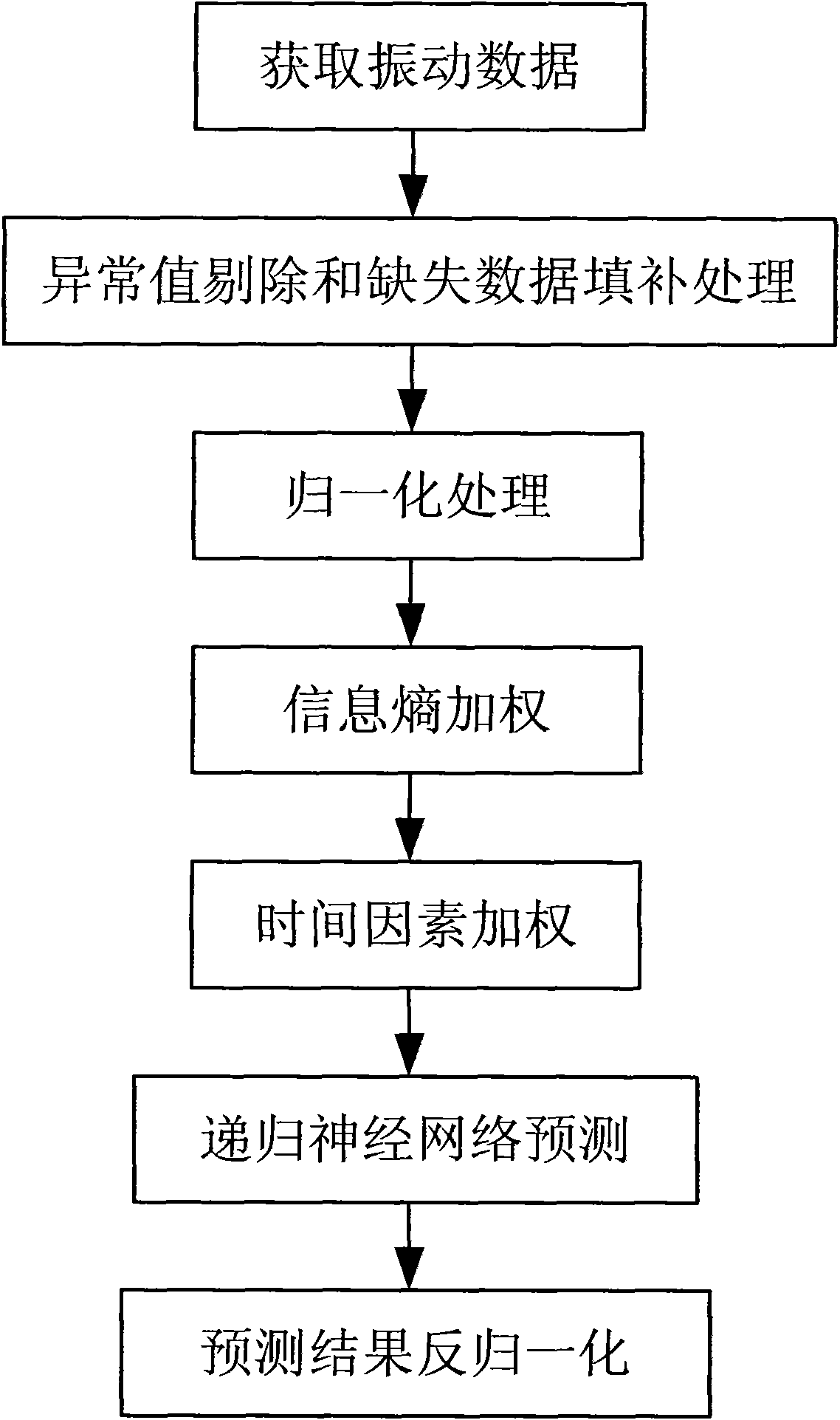
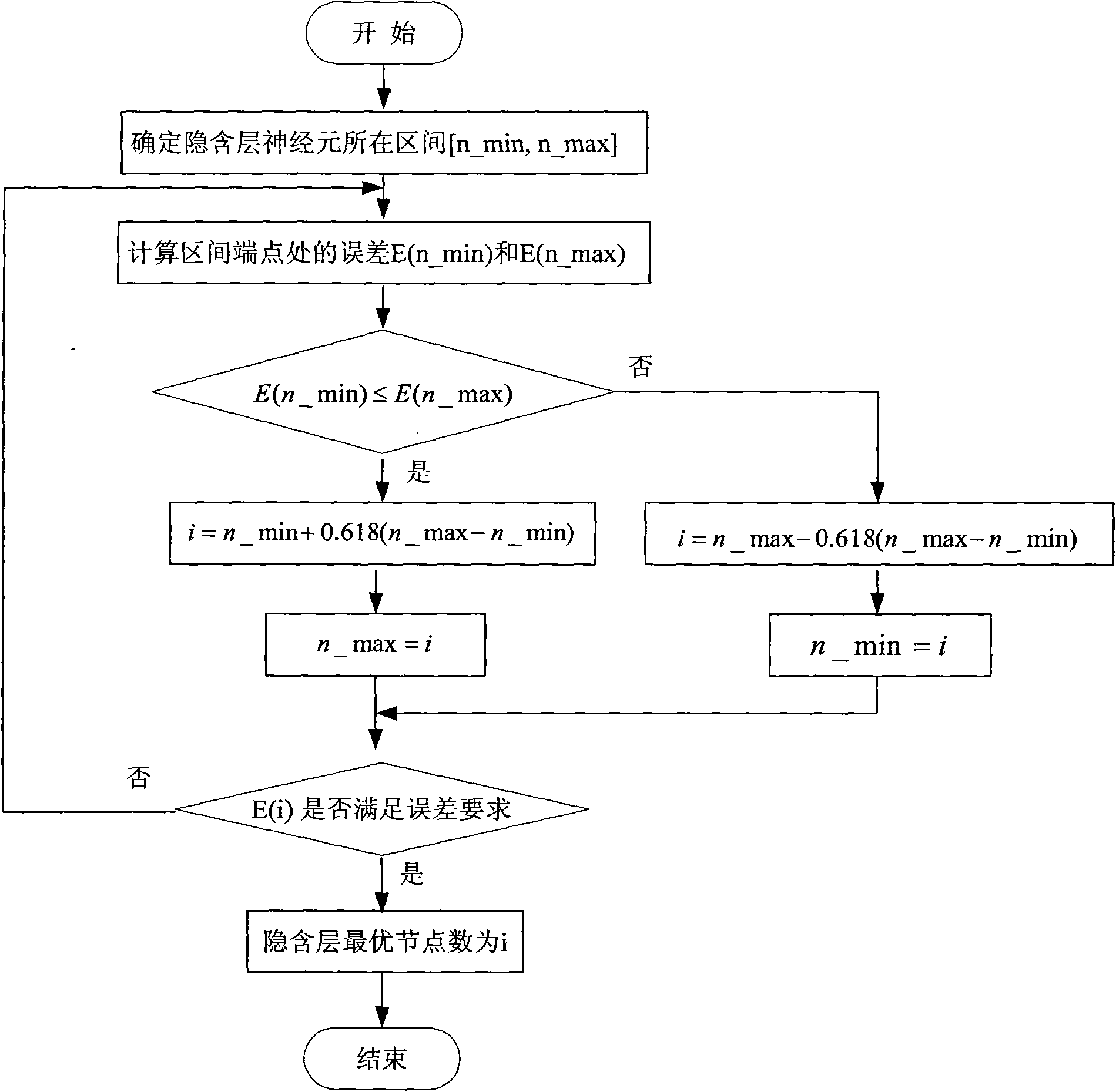
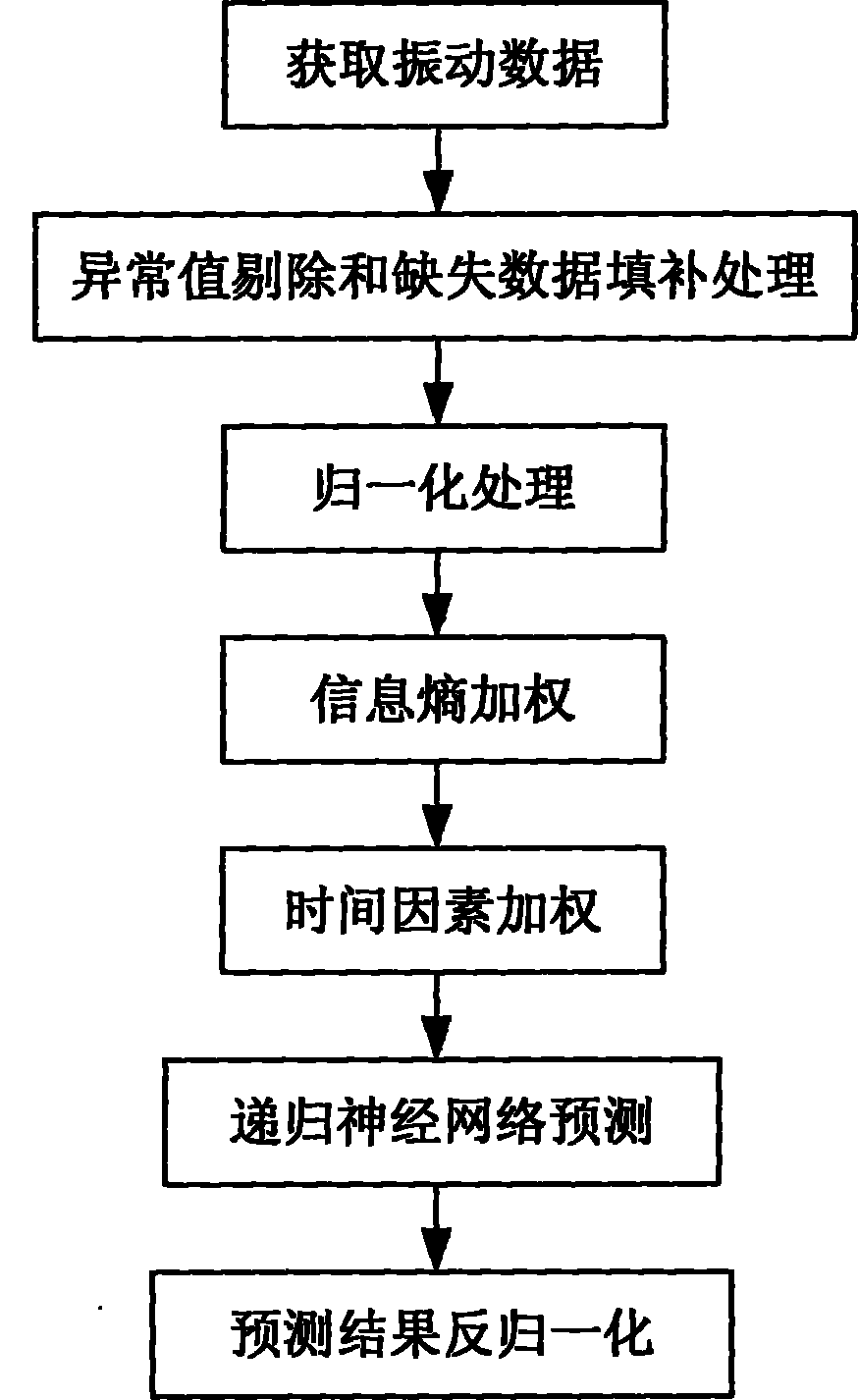
Electromechanical device neural network failure trend prediction method
InactiveCN101799367AEfficient use ofDynamic adaptiveSubsonic/sonic/ultrasonic wave measurementBiological neural network modelsHidden layerNerve network
The invention relates to an electromechanical device neural network failure trend prediction method, comprising the following steps: (1) obtain a section continuous vibration signal which is sensitive to the failure and is output by a measuring point sensor; (2) respectively carry out exceptional value elimination and missing data filling to the vibration data by a 3 sigma method and an interpolation method; (3) carry out a normalization process to a vibration data sequence; (4) calculate a vibration data sequence which is entropy-weighted according to the sequence which is carried out the normalization process; (5) carry out a time-weighted calculation to the vibration data sequence which is entropy-weighted by utilizing time weight due to the influence of time factor; (6) build a nonlinear dynamic recurrent neural network prediction model by utilizing the data sequence which is obtained by step (5) and determine a hidden layer optimal node number by utilizing a golden section method; (7) carry out normalization process to a trend prediction result and obtain a actual prediction result. A dynamic recurrent neural network model is adopted to carry out prediction in the invention, therefore, the failure prediction reliability is increased. The electromechanical device neural network failure trend prediction method can be widely applied to the failure prediction and analysis of all kinds of electromechanical devices.
Owner:BEIJING INFORMATION SCI & TECH UNIV
Automated personalized telephone management system
InactiveUS6697473B2Avoid spending any timePrivacy protectionUnauthorised/fraudulent call preventionAutomatic call-answering/message-recording/conversation-recordingPersonalizationModem device
A holistic, automated, personalized telephone call management system is capable of responding to all incoming calls. The system employs customized software, computer chips, printed circuit board, ANI, where available, and a data input / output module, which are applied in an integrated manner to accomplish a broad array of functions important to modem household communication needs. System accepts operational time factors and telephone numbers as stored data to be matched automatically with the telephone numbers of incoming calls. The telephone rings under certain qualifying criteria, and an incoming call is passed in silent mode to a smart answering machine under other criteria. The smart answering machine is capable of handling emergency call situations, and the integration of call-waiting options. System also has a smart software function to deal with a state of delinquency on any lease / rent contract for the system.
Owner:BATTEN BOBBY G
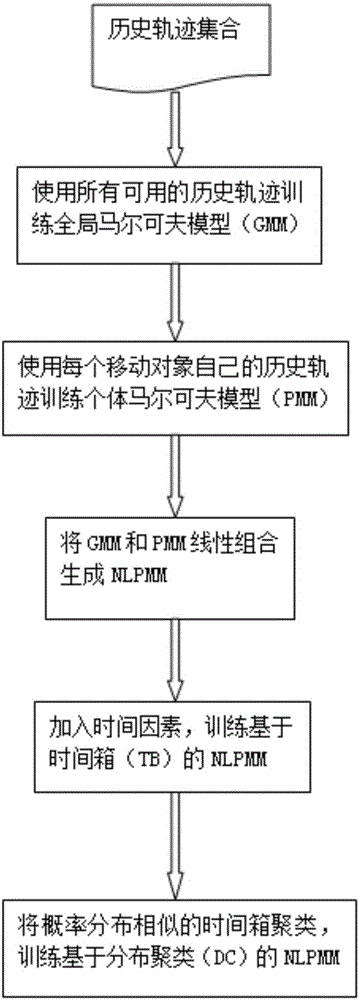
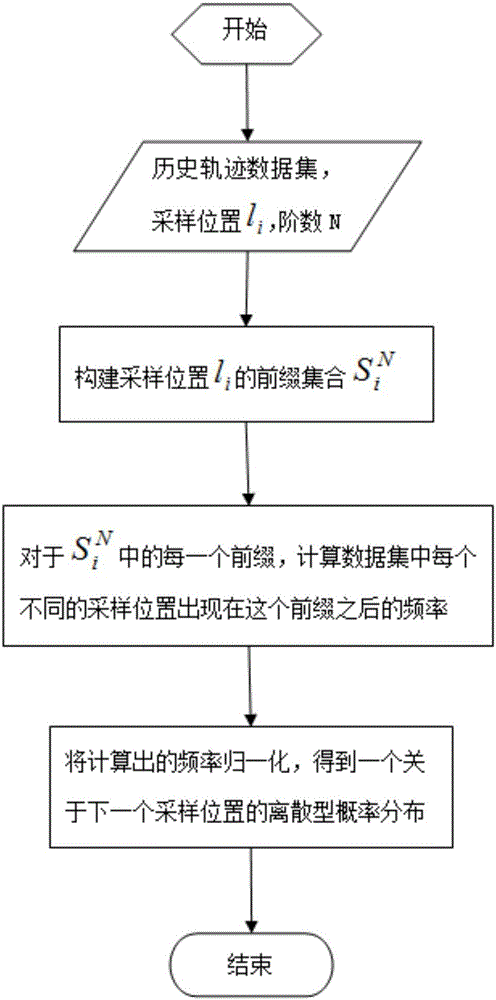
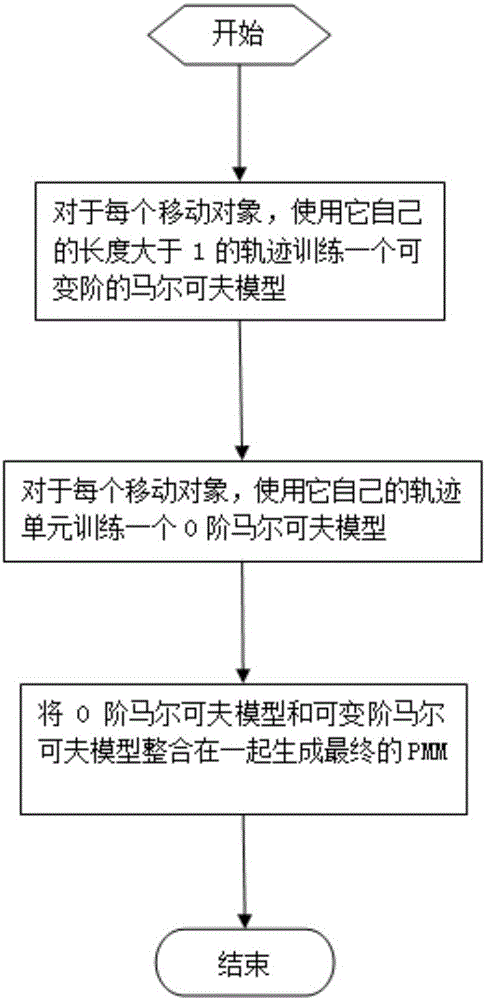
Markov-model-based position prediction method
InactiveCN105825297AForecasts are complete and accurateImprove forecast accuracyForecastingCharacter and pattern recognitionAlgorithmEuclidean vector
The invention discloses a markov-model-based position prediction method. The method comprises: a historical track is collected, data centralization probabilities of all sampling positions are determined, normalization processing is carried out, discrete probability distribution is determined, and a variable-order global markov model is established; according to a historical track of each moving object, an individual markov model of each moving object is constructed; and on the basis of linear regression, the global markov model and the individual markov models are combined to generate a probability vector linear combination, time period division is carried out, all tracks are mapped to the time periods according time stamps, probabilities of falling into all time periods by all objects are calculated, clustering is carried out, and then a next position is predicted by combining a clustering result and the markov models. According to the invention, the time factor is taken into consideration and different models are trained at different time periods. When a next position is predicted, a proper model is selected based on the time stamp, so that the prediction accuracy is improved substantially.
Owner:SHANDONG UNIV +1
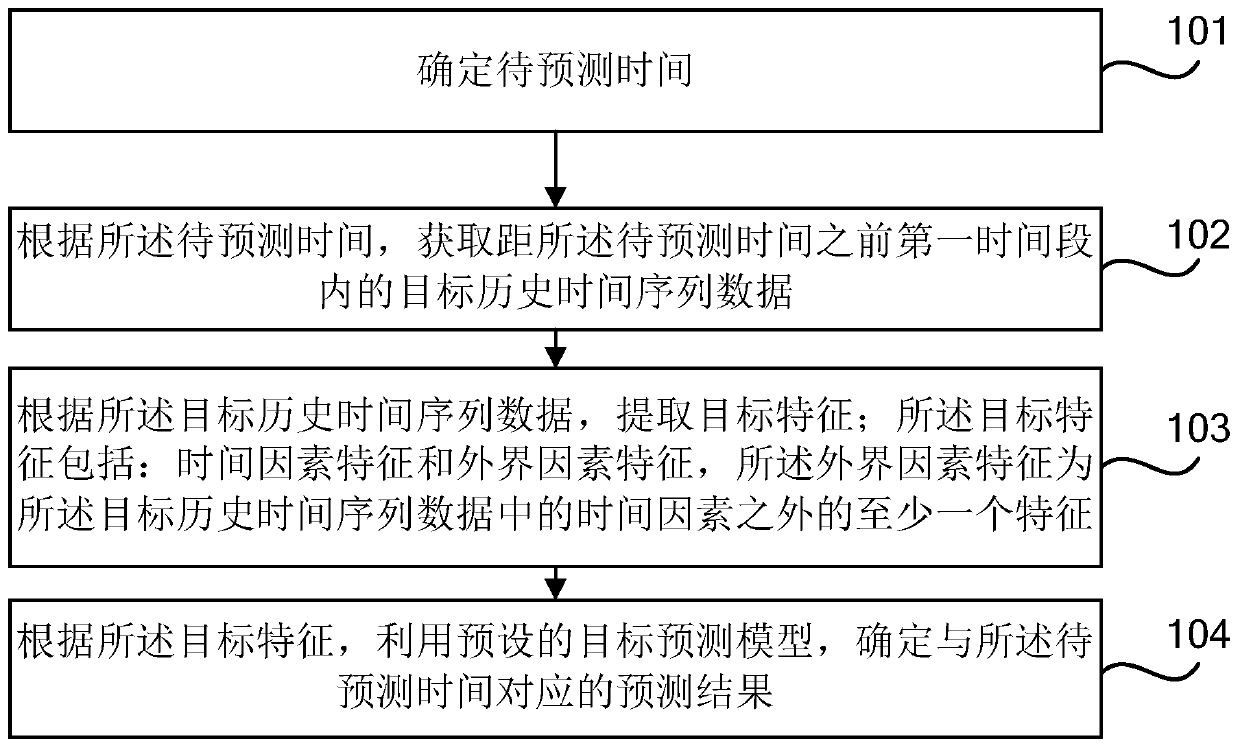
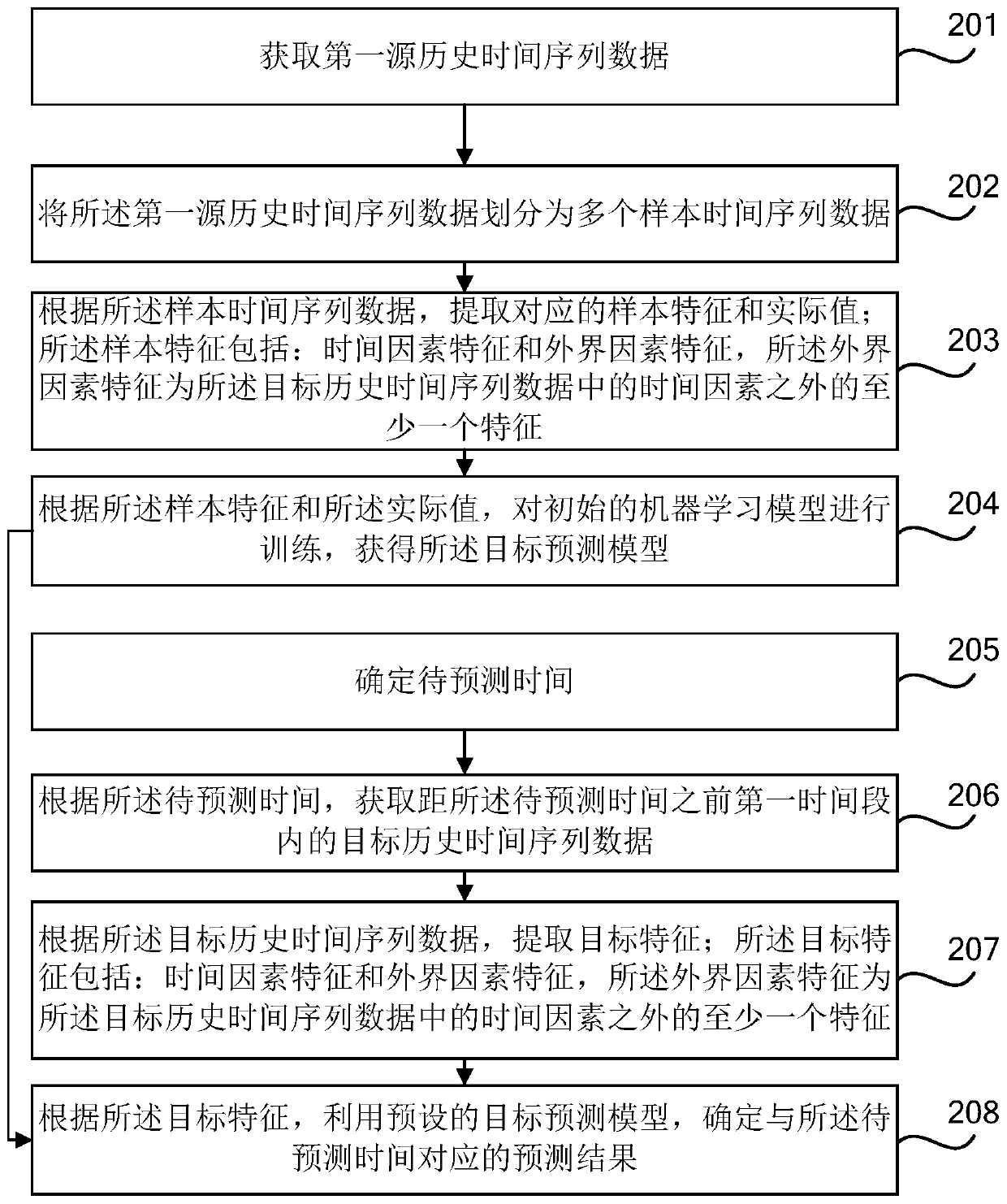
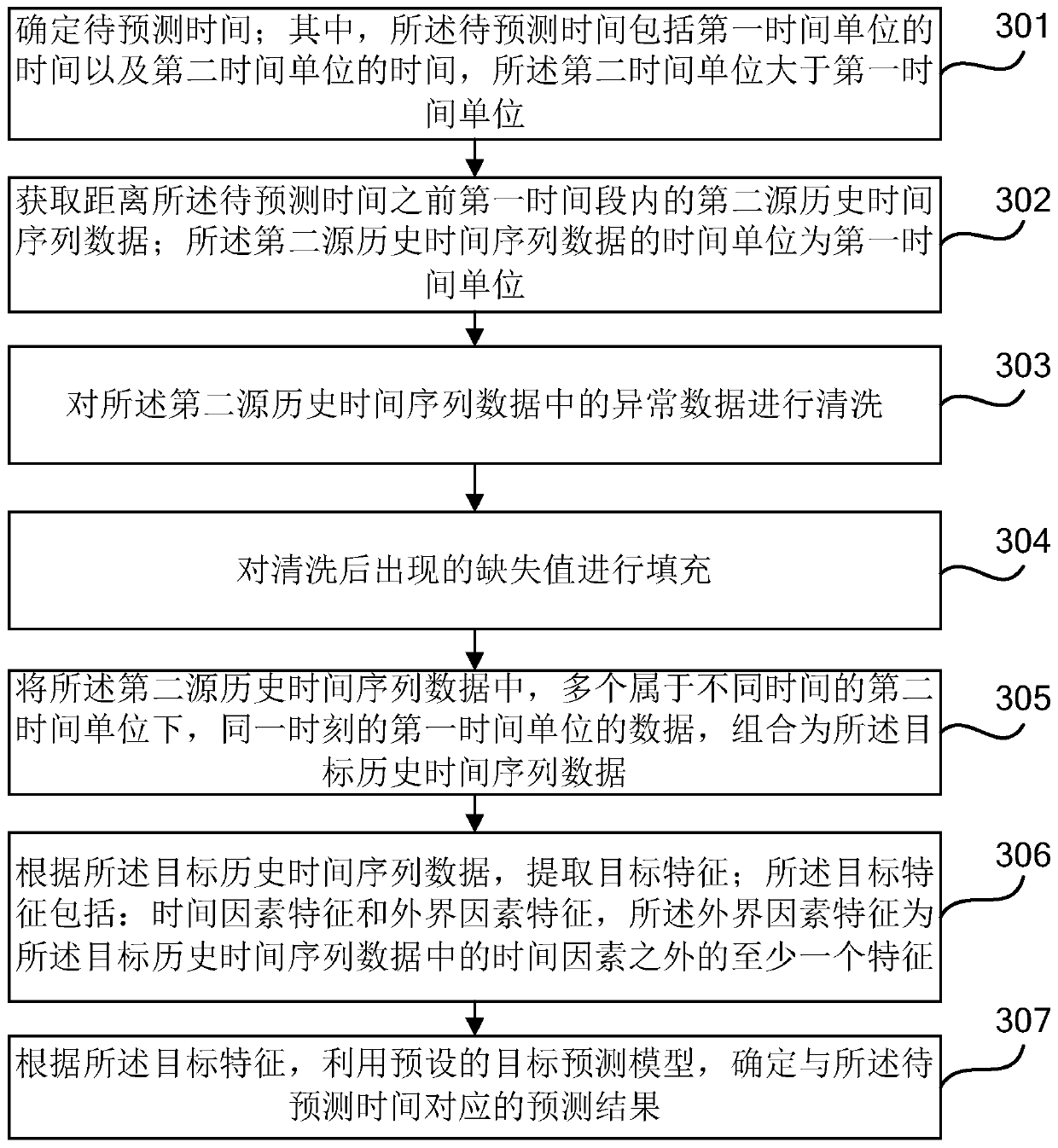
Prediction method and device, electronic equipment and computer readable storage medium
The invention provides a prediction method and device, and relates to the technical field of computers. The method comprises the steps of determining to-be-predicted time; according to the to-be-predicted time, obtaining target historical time sequence data in a first time period before the to-be-predicted time; extracting target characteristics according to the target historical time sequence data; Wherein the target feature comprises a time factor feature and an external factor feature, and the external factor feature is at least one feature except a time factor in the target historical timesequence data; and according to the target feature, determining a prediction result corresponding to the to-be-predicted time by using a preset target prediction model. According to the embodiment ofthe invention, by combining the time sequence and the machine learning model, prediction can be carried out by combining the characteristics of the external factors except the time factors in the target historical time sequence data, so that the prediction accuracy is improved, and the prediction accuracy of the unstable time sequence can also be improved.
Owner:BEIJING CHENGSHI WANGLIN INFORMATION TECH CO LTD
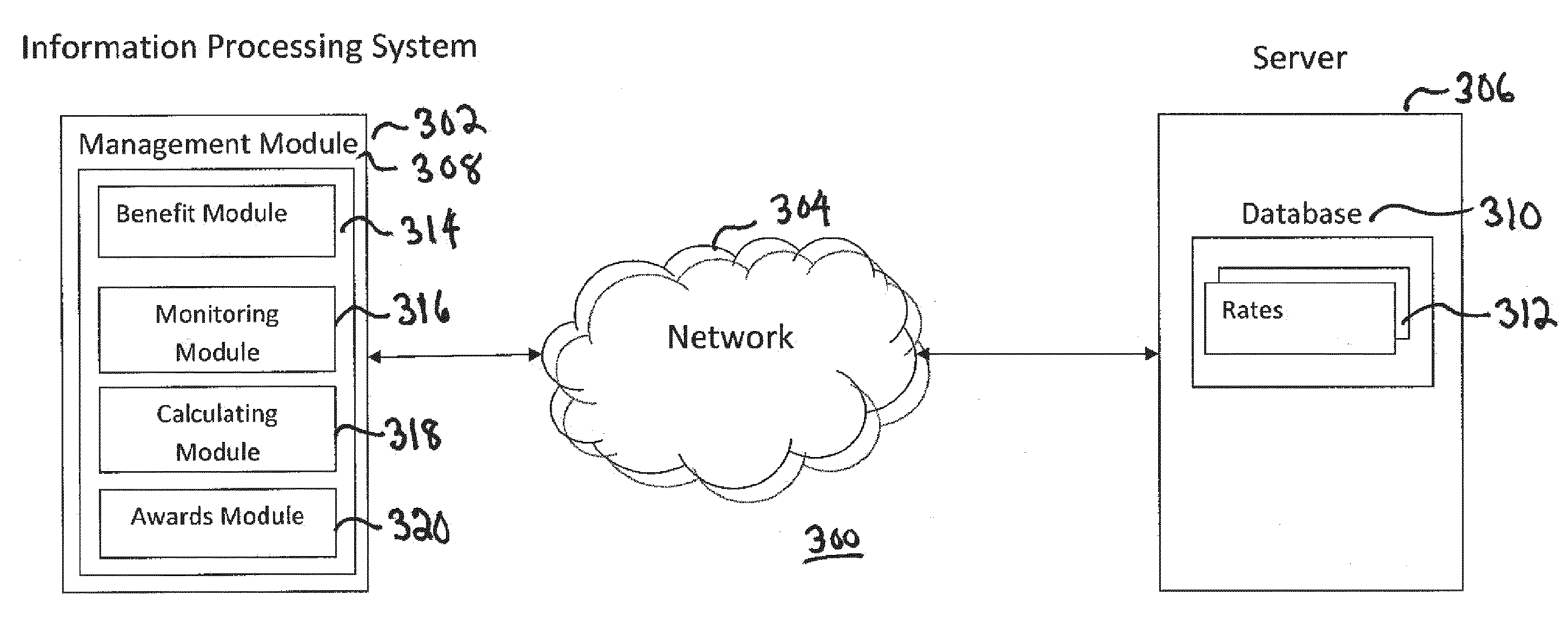
System and method of managing an insurance scheme
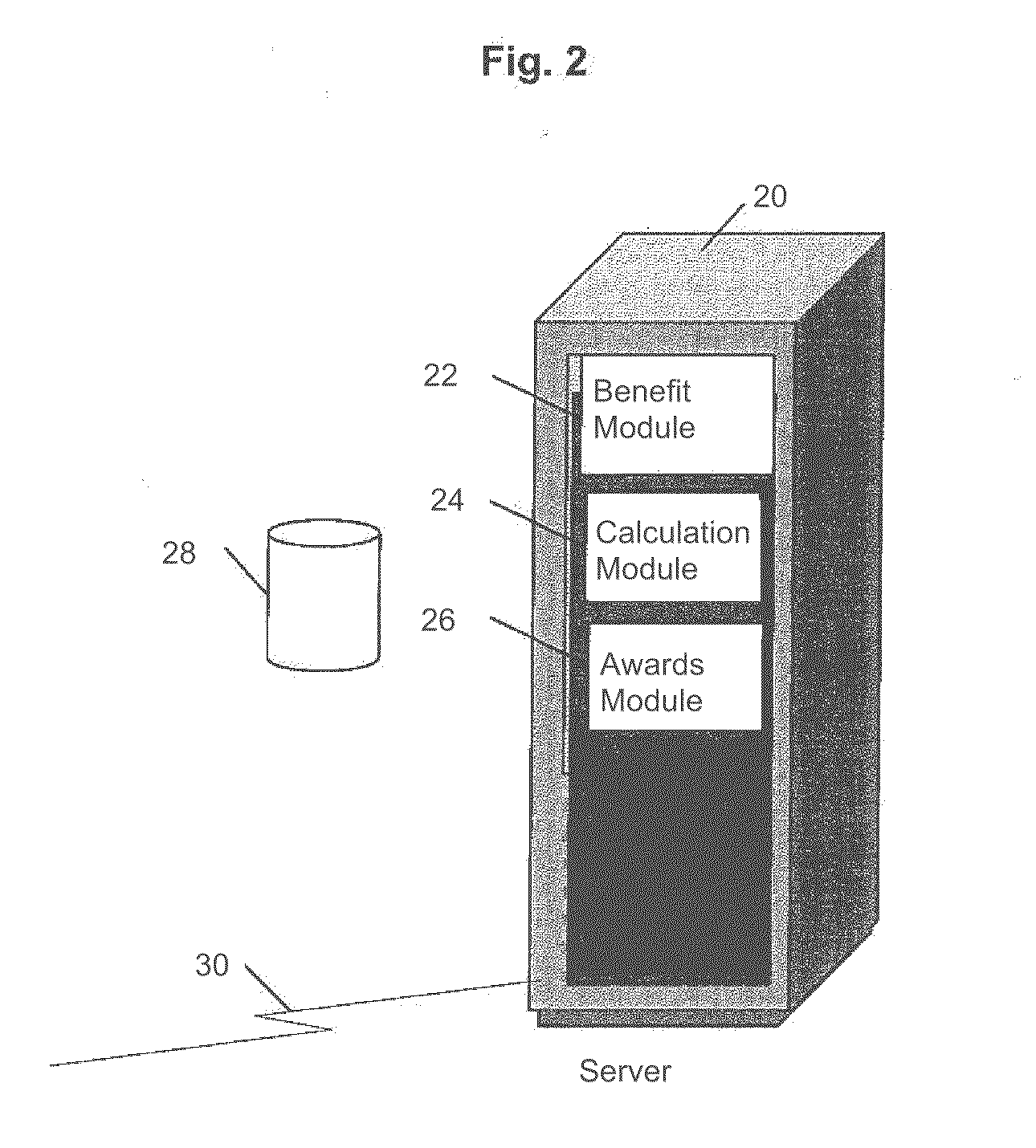
A system for managing an insurance scheme includes a benefit module to define at least one insured event for an insured person and to define at least one benefit to be paid out on the occurrence of one of the insured events. A calculation module alters the at least one benefit based on a) a time factor; and b) the life impact of the insured event on the insured person. An awards module, on the occurrence of the at least one insured event, provides the at least one altered benefit to the insured person.
Owner:DISCOVERY HOLDING COMPANY
Method of planning three dimensional route of unmanned plane by means of improved artificial fish swarm algorithm
InactiveCN107392388AReduce complexityImprove search capabilitiesForecastingArtificial lifeOptimum routeLandform
The invention discloses a method of planning three dimensional route of an unmanned plane by means of an improved artificial fish swarm algorithm. The method of planning three dimensional route of an unmanned plane by means of an improved artificial fish swarm algorithm is used for carrying out static state planning of route and real-time dynamic re-planning of route when an unmanned plane executes a single task. The method of planning three dimensional route of an unmanned plane by means of an improved artificial fish swarm algorithm includes the steps: constructing a digital map through a landform model and a simplified threat model, considering the influence of space division granularity on the complexity of an optimizing control algorithm, and realizing division of space according to a fence self-adaptive algorithm; realizing static state route planning by means of an improved artificial fish swarm algorithm; and considering the time factor, constructing a threat prediction model based on a dynamic Bayesian network, predicting the unexpected threat, combined with flight constraint of the unmanned plane, obtaining the re-planning starting point, and realizing global route dynamic re-planning by means of the improved artificial fish swarm algorithm. The method of planning three dimensional route of an unmanned plane by means of an improved artificial fish swarm algorithm has the advantages of reducing the complexity of a route optimizing control algorithm, improving the optimum route searching capability, and satisfying the practical route planning demand.
Owner:NANCHANG HANGKONG UNIVERSITY
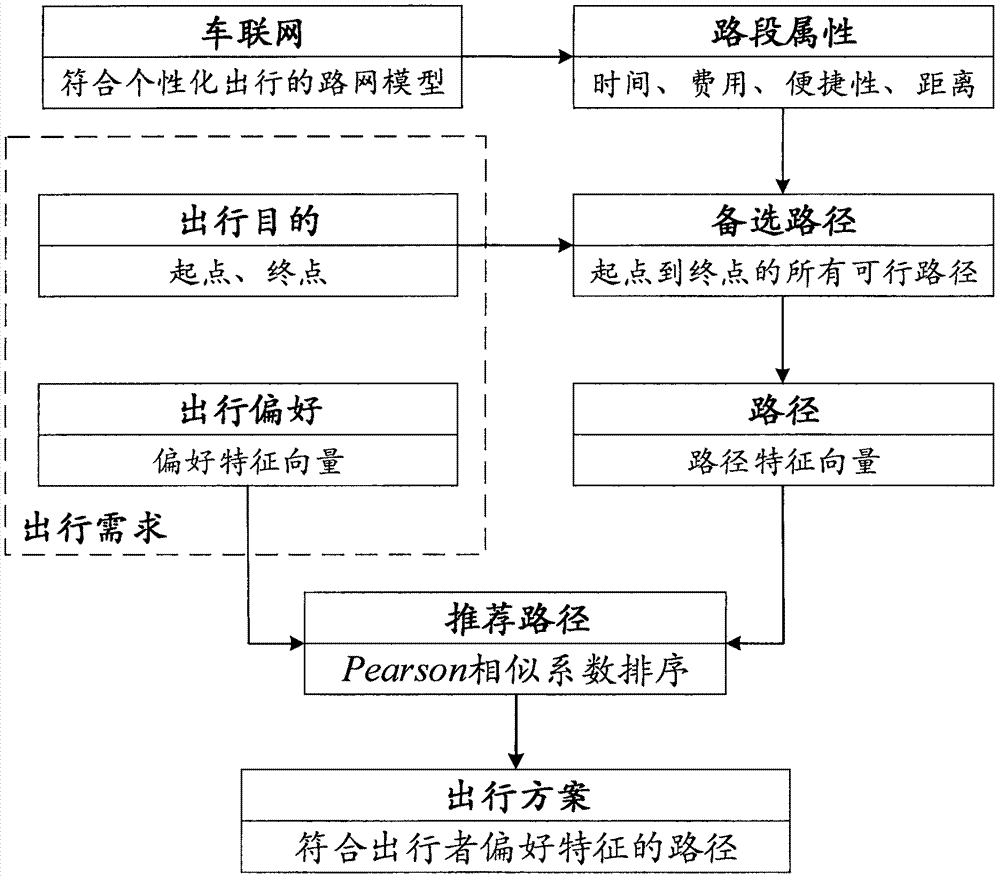
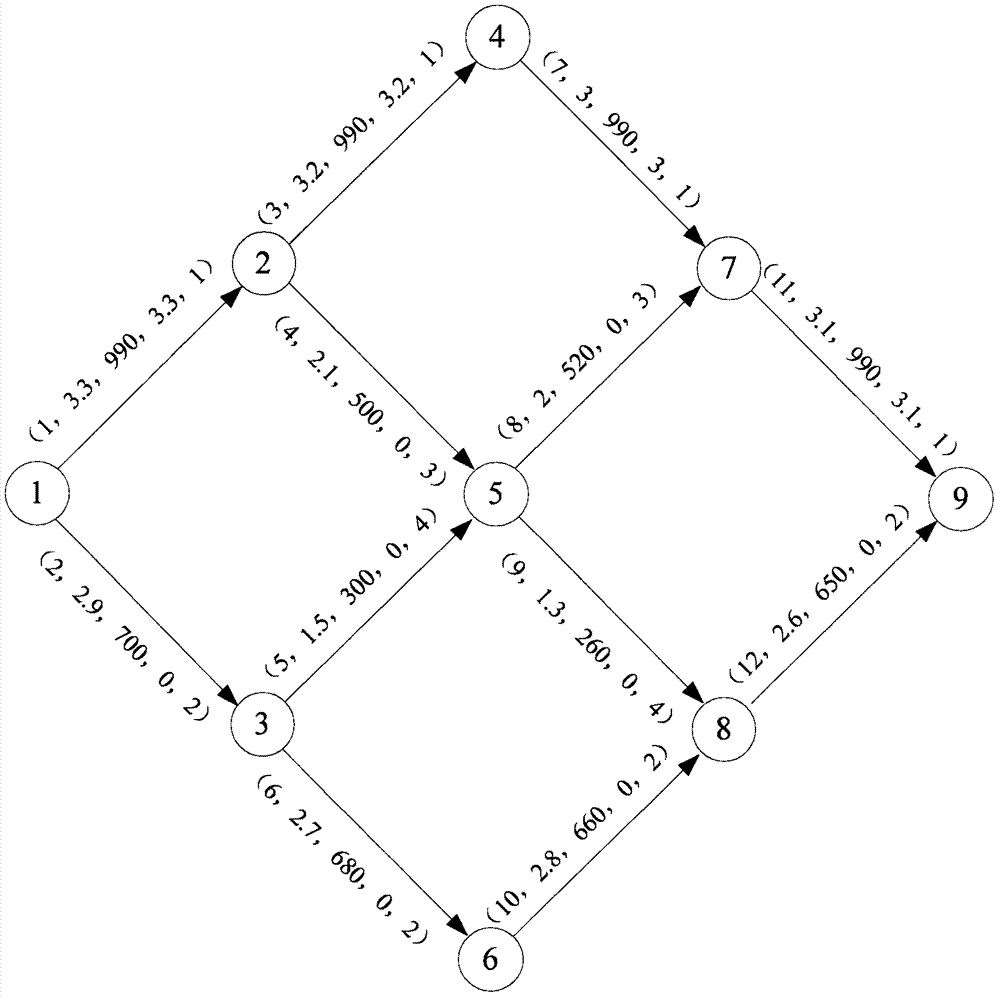
Customized path recommending method in Internet of Vehicles environment
InactiveCN106940829ARealize private customizationReal-time response to unexpected traffic conditionsRoad vehicles traffic controlForecastingCorrelation coefficientFeature vector
The invention discloses a customized path recommending method in an Internet of Vehicles environment. According to the method, in customized path recommending processes, a set of four trip factors including time factors, fee factors, convenience factors and distance factors are taken into account; in a traffic network, a stack idea-based backtracking algorithm for solving a set of all feasible paths from a starting point to an end point is adopted, and a Pearson correlation coefficient-based path recommending algorithm which is implemented according to traveler personality preference characteristic vectors and feasible path characteristic vectors is adopted. According to the method, a plurality kinds of accurate real-time traffic information provided by the Internet of Vehicles is fully used, customized trip demand of a traveler is taken into account, path recommending service in line with individual preference demand can be provided for the traveler, an individual trip path can be customized, accident traffic conditions can be responded to in real time, and customized path recommending service can be provided when traffic accidents occur.
Owner:LANZHOU JIAOTONG UNIV
Method for optimizing loads of speech/user recognition system
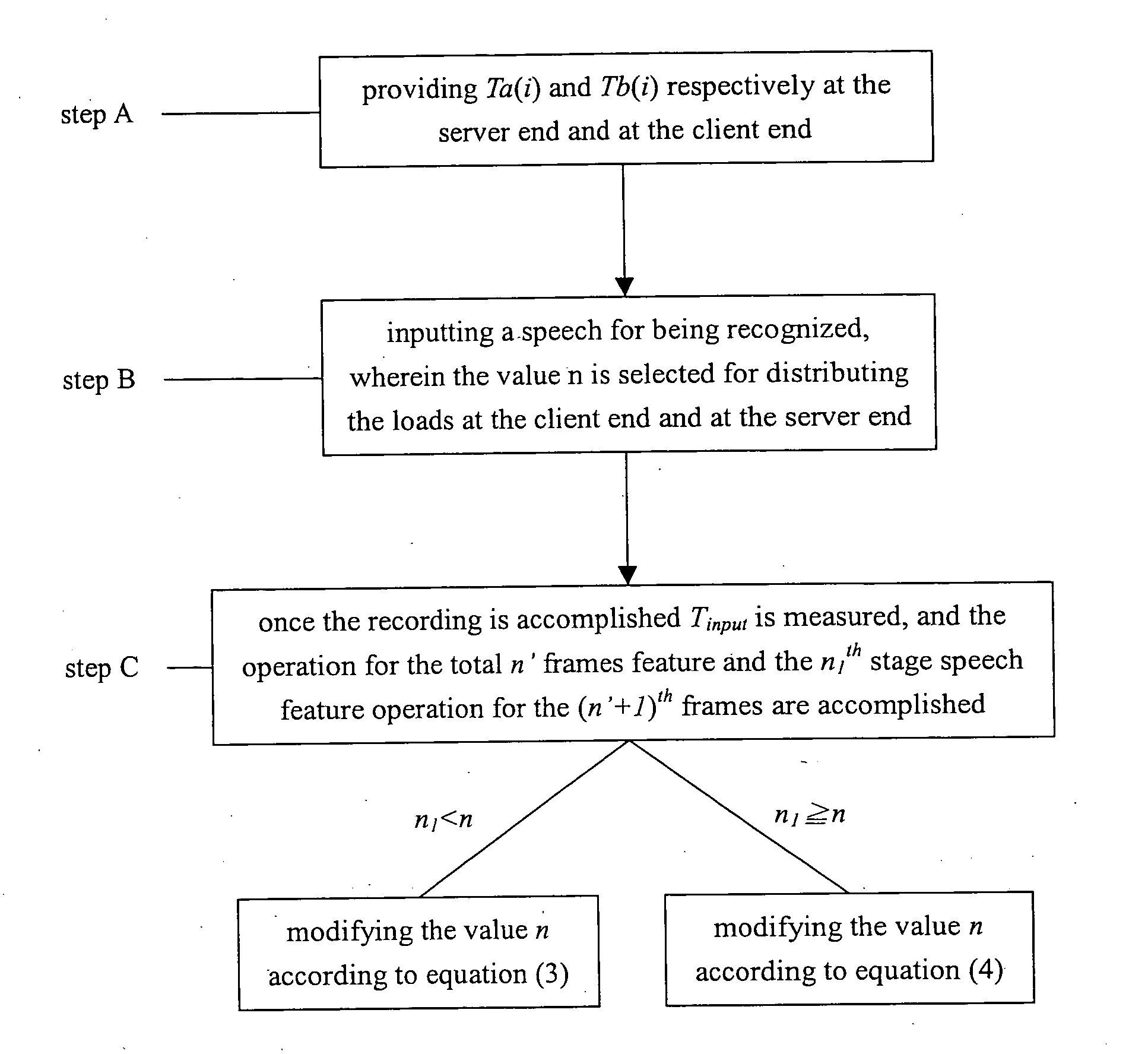
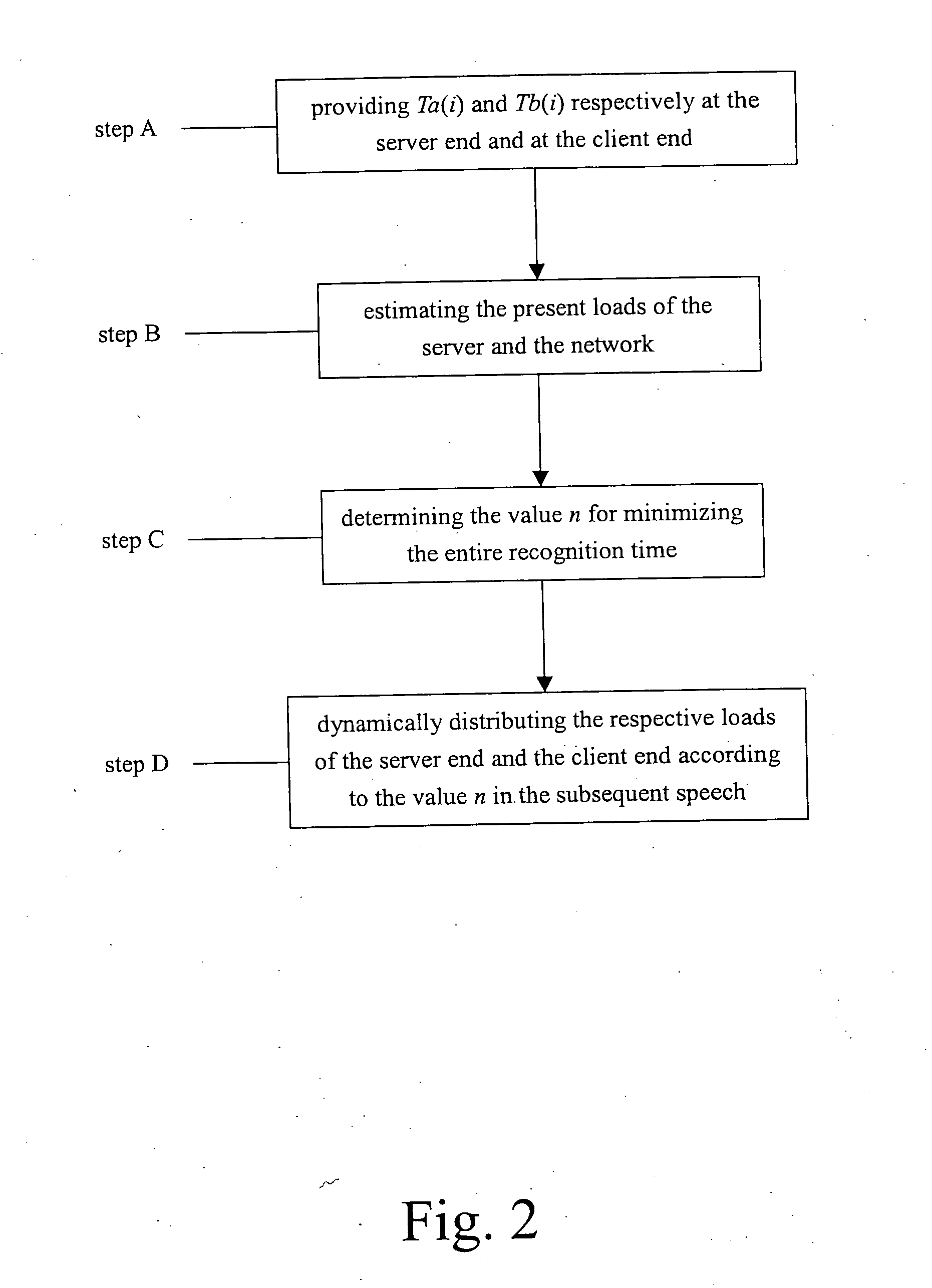
A method for optimizing a load of a speech / user recognition system is provided. The speech / user recognition system comprises a server end, a client end and a network, and the method is achieved by performing N stages of computations for speech features of a speech, where N is a positive integer, and an i is selected from 1 to N for representing the ith stage speech features, comprising steps of: (a) providing a real time factor Ta(i) for computing a respective stage i of the speech features at the client end, where Ta(i) is an average computation time of computing the ith stage speech features at the client end with respect to one second input speech; (b) providing a real time factor Tb(i) for computing a respective stage i of the speech features at the server end, where Tb(i) is an average computation time of computing the ith stage speech features at the server end with respect to one second input speech; (c) providing a load c of the server end and a load d of the network; (d) deciding an n in the range from 1 to N for minimizing a recognition time Toutput of the speech; (e) inputting the speech with time Tinput for being recognized; (f) performing an computation from the first stage speech features to the nth stage speech features of the speech at the client end, while performing an computation from the (n+1)th stage speech features to the Nth stage speech features of the speech at the server end; and (g) repeating steps (e) to (f).
Owner:DELTA ELECTRONICS INC
Dynamic cipher generation method for electronic equipment for fingerprint and voice recognition
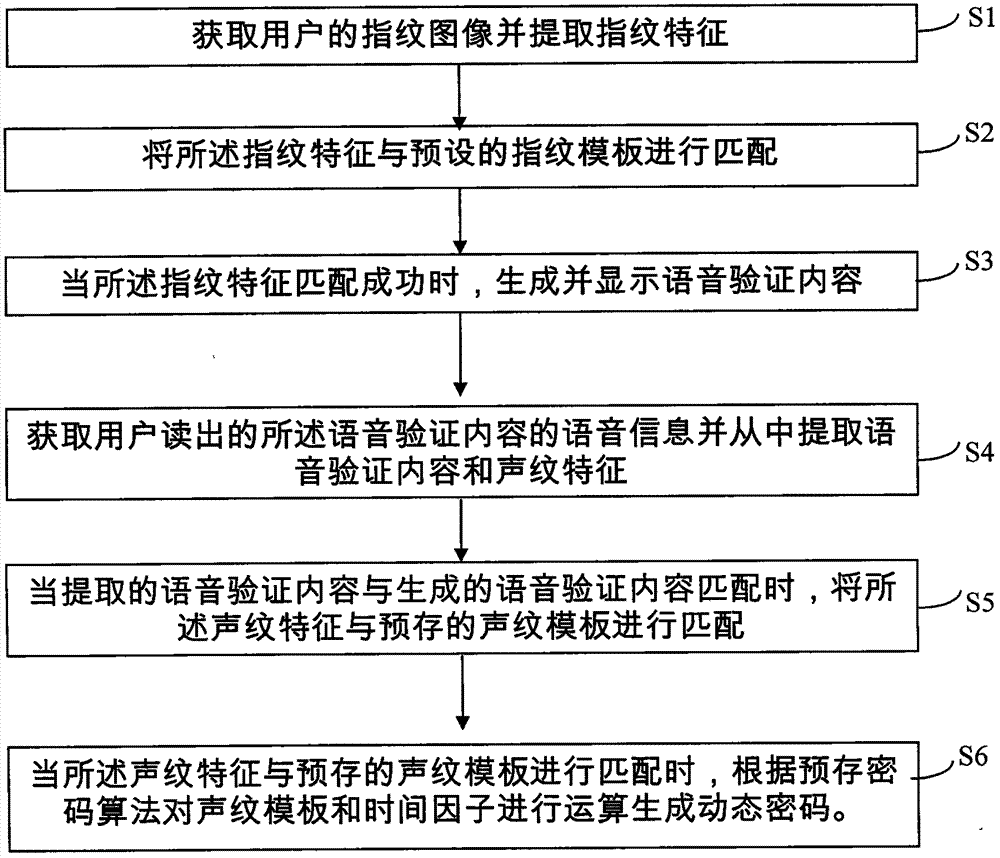
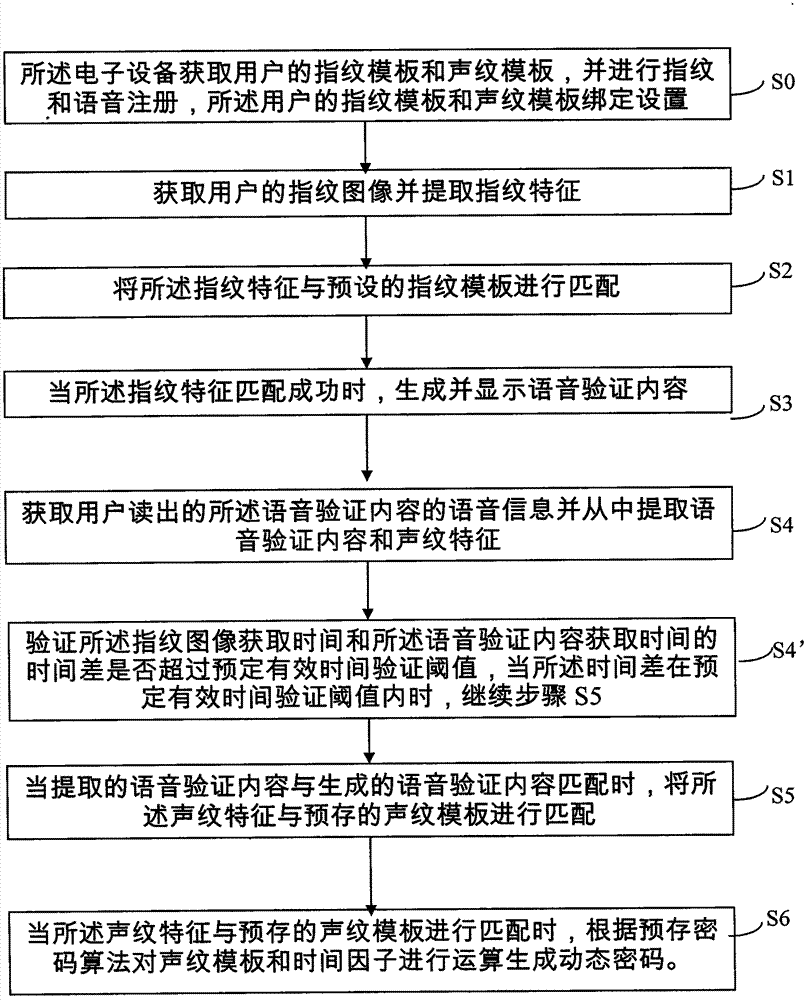
InactiveCN104331652AAddresses vulnerabilities that are vulnerable to crackingImprove securityDigital data authenticationUser authenticationDependability
The invention discloses a dynamic cipher generation method for electronic equipment for fingerprint and voice recognition. The dynamic cipher generation method comprises the following steps: acquiring a fingerprint image of a user and extracting fingerprint features; performing matching the fingerprint features and a fingerprint template; when the fingerprint features are matched successfully, generating and displaying voice verification content; acquiring the voice message of the voice verification content read by the user and extracting the voice verification content and voiceprint features from the voice message; when the extracted voice verification content is matched with the generated voice verification content, performing matching on the voiceprint features and a voiceprint template; when matching is performed on voiceprint features and the voiceprint template, performing operation on the voiceprint template and a time factor according to a pre-stored cipher algorithm to generate a dynamic cipher. According to the dynamic cipher generation method disclosed by the invention, user authentication is performed by closely combining the fingerprint and voice recognition technology, so that the safety and the reliability of the electronic equipment and dynamic cipher generation are improved.
Owner:WUXI BIOKEE BIOMETRICS TECH
Method for identifying and predicting bus passenger flow influence factor based on geographically and temporally weighted regression
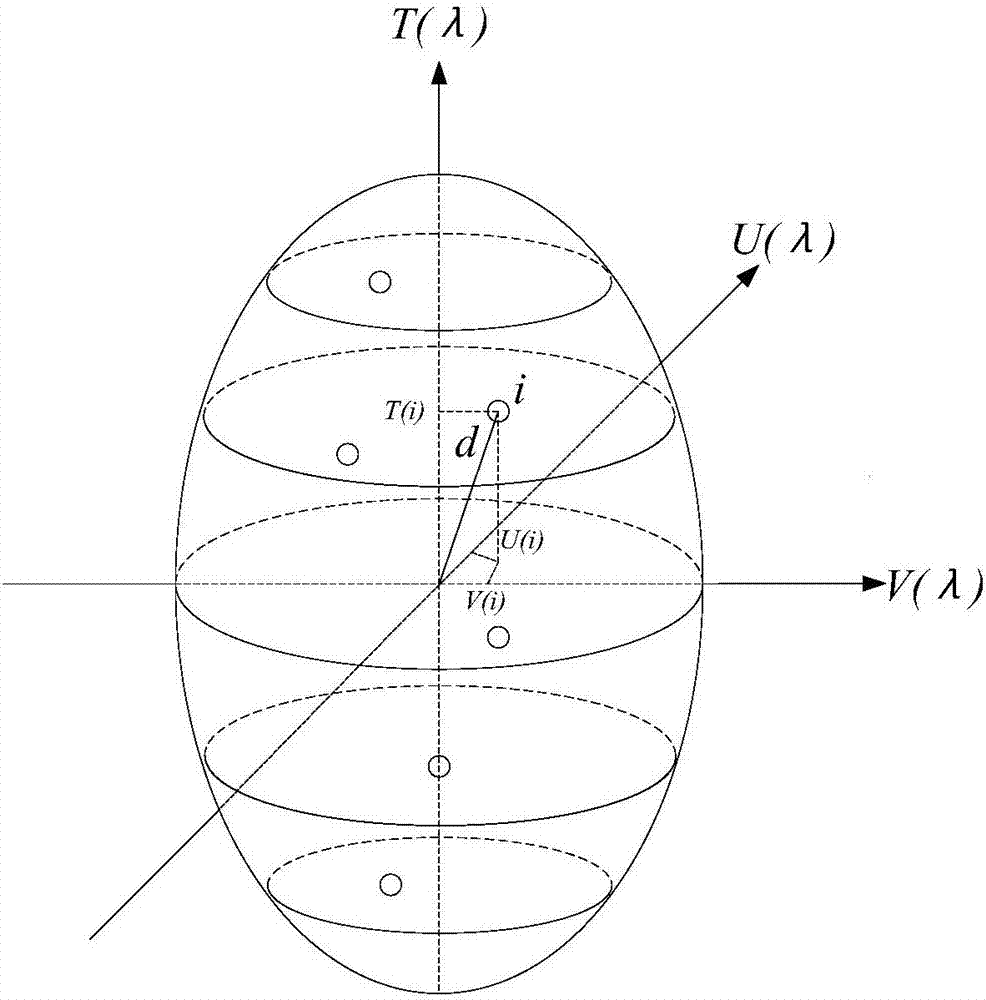
The invention discloses a method for identifying and predicting a bus passenger flow influence factor based on geographically and temporally weighted regression (GTWR). The method comprises steps of: extracting a traffic zone hour bus passenger flow and calculating built environment density; 2, constructing a space-time three-dimensional coordinate system according to the time of a passenger flow observation point and latitude and longitude to calculate space-time distance, and reckoning a spatial regression weight matrix according to a Gaussian function and the distance; 3, calculating a relation between a passenger flow volume and land utilization under different space-time conditions based on the GTWR; and 4, obtaining a change of a relevant parameter to a coefficient according to the calculation to perform visualization processing in time and space, and analyzing an inherent law. The method takes account of the influence of a time factor on the bus passenger flow and the built environment relation, can deeply excavate an internal relation between the passenger flow and the land utilization, accurately predicts the bus passenger flow, and provides the scientific theoretical guidance for the bus line planning and operation management.
Owner:BEIHANG UNIV
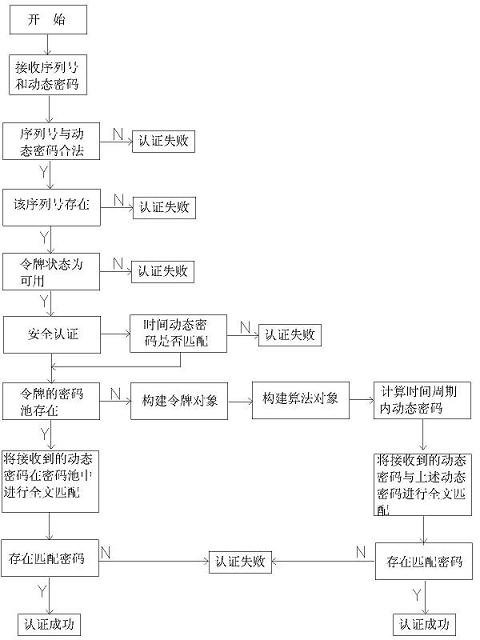
Driving dynamic code generating and authenticating system and method based on time factors
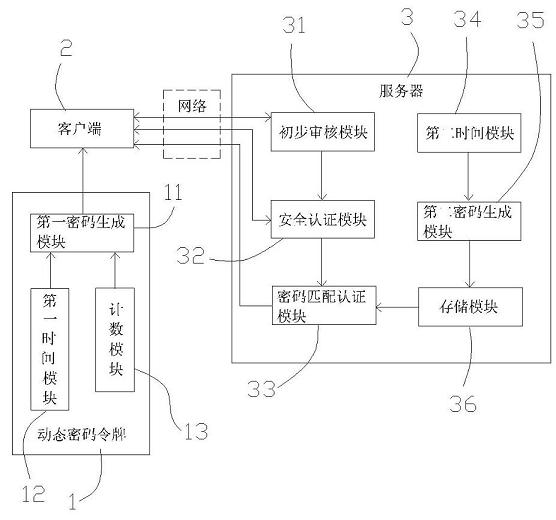
InactiveCN102185838AOvercome timeless issuesOvercoming inability to take the initiativeUser identity/authority verificationProgramming languageSecret code
The invention relates to a driving dynamic code generating and authenticating system and a driving dynamic code generating and authenticating method based on time factors, aiming at solving the problem that a dynamic code generator in the prior art can generate one dynamic code within a fixed time cycle and can carry out authentication correctly once. The system comprises a dynamic code token, a client terminal and a server, wherein the dynamic code token comprises a first code generating module, a first time module and a counting module, and generates one or more dynamic codes; and the server is connected with the client terminal and comprises a second time module, a second code generating module, a memory module and a code matching and authenticating module, and matches and authenticates the dynamic codes requesting the authentication. In the invention, a plurality of dynamic codes can be generated within a fixed time cycle, thereby solving the problems that a traditional time-type token can only generate one code within the fixed time cycle and a user can not obtain the codes actively and without restriction, so that the requirements of the user can be met.
Owner:HANGZHOU YUQIANG TECH
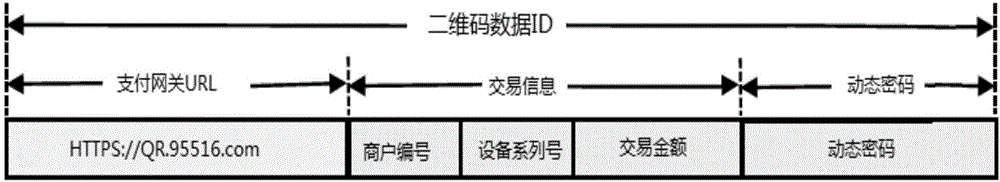
Off-line dynamic QR code generation method, and payment method and device
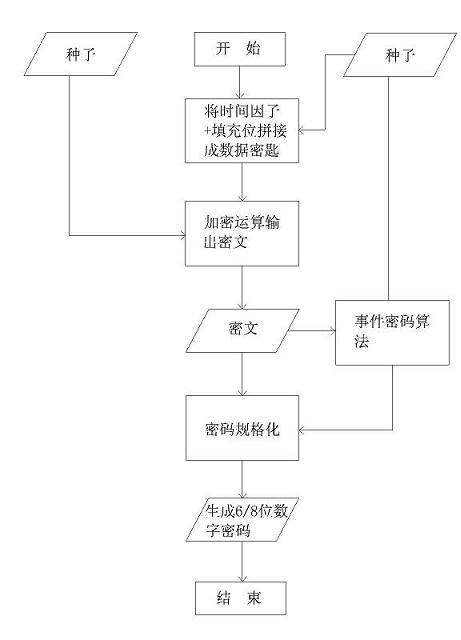
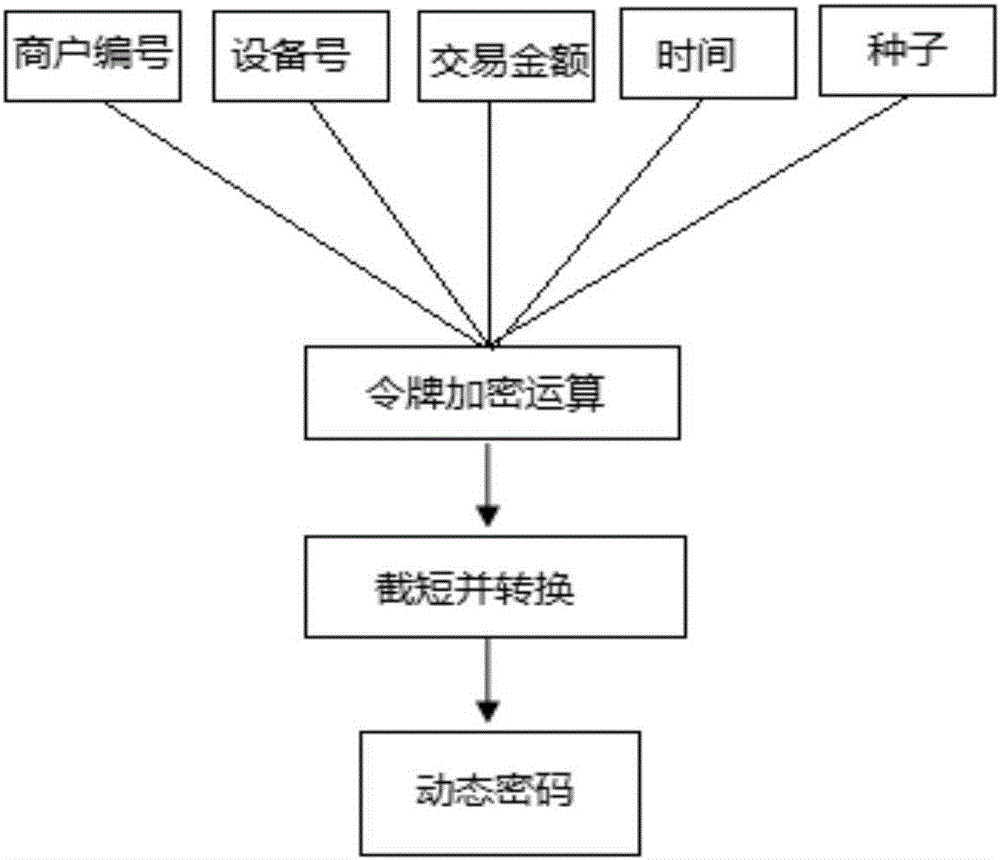
InactiveCN107180351ASolve the problem that one code at a time cannot be realizedReduce interaction timeKey distribution for secure communicationUser identity/authority verificationInteraction timeProgramming language
The invention discloses an off-line dynamic QR code generation method, and a payment method and device. For the scheme of the off-line dynamic QR code generation method, a dynamic password token technology based on time is used to perform encrypted operation to calculate the dynamic keyword of this time, according to a token seed key and a time factor, by means of combination with the transaction information containing the transaction amount, and a dynamic QR code pattern is generated according to the dynamic keyword of this time. The scheme applies to the dynamic password token technology to the dynamic QR code generation technology, thus being able to preferably solving the problem that a static QR code cannot realize one code for one time. Besides, in the scheme, the dynamic token and a certificate server are synchronous in time and are consistent in the algorithm, thus not depending on on-line and using the off-line mode to guarantee that the generated QR code data can be identified and authenticated by the background. And at the same time, the advantages of off-line are reduction of the on-line flow, reduction of network interaction time, reduction of transaction flow and steps, and improvement of transaction efficiency.
Owner:DYNAMICODE
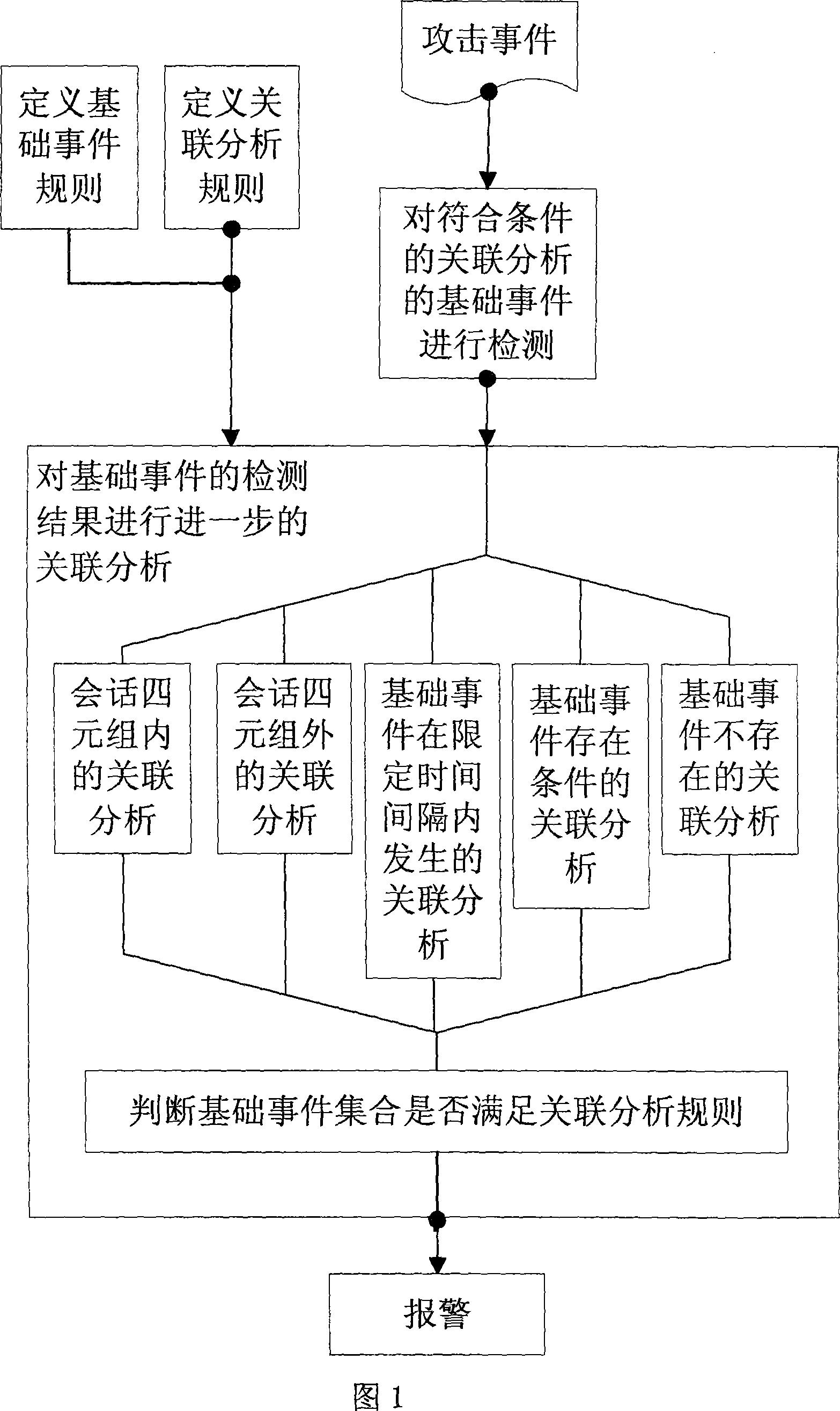
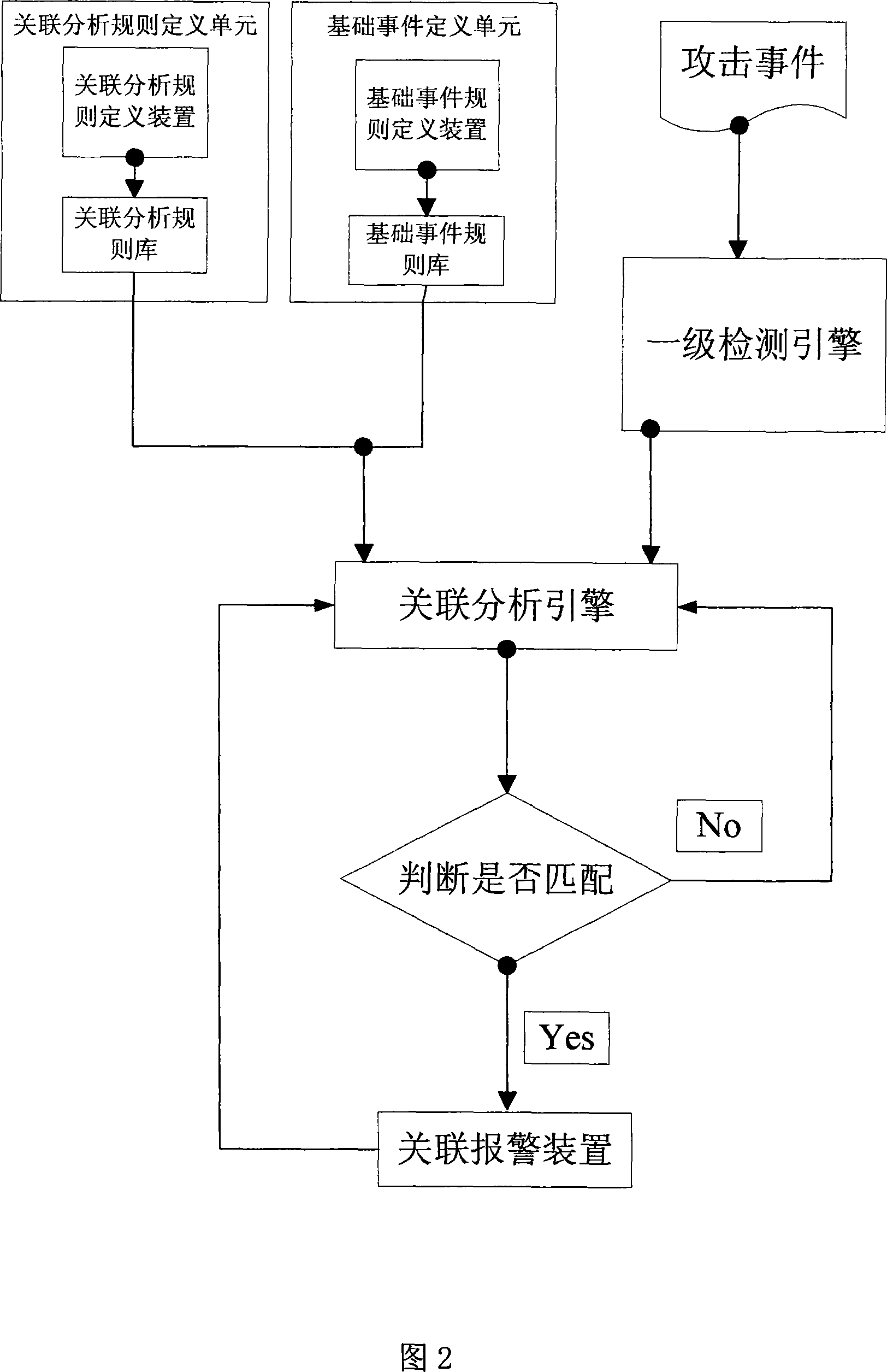
Associative attack analysis and detection method and device based on the time sequence and event sequence
InactiveCN101034974AAccurate detectionComprehensive descriptionData switching networksSecuring communicationCorrelation analysisAttack analysis
This invention is based on the time and events sequence to analysis attacking detection methods and devices involved in exchange for the function of the network. It is a methods and devices to prevent removing data from the data transmission channel without permission .The method provides a complex text-based attack description language to make the user can amend the built-related characteristics, and add new features of related events. The present invention include: basic rules of the incident, the rules of the association, first level detection engine, correlation analysis engine. The whole process of attacking are described more comprehensive and reasonable taking into account the time factor and the order of events Such description and testing which distinct the basic incidents more carefully are more in line with the requirements of detecting attacks. The invention also describes the relation between alarm incident and not alarm incident.
Owner:BEIJING VENUS INFORMATION TECH
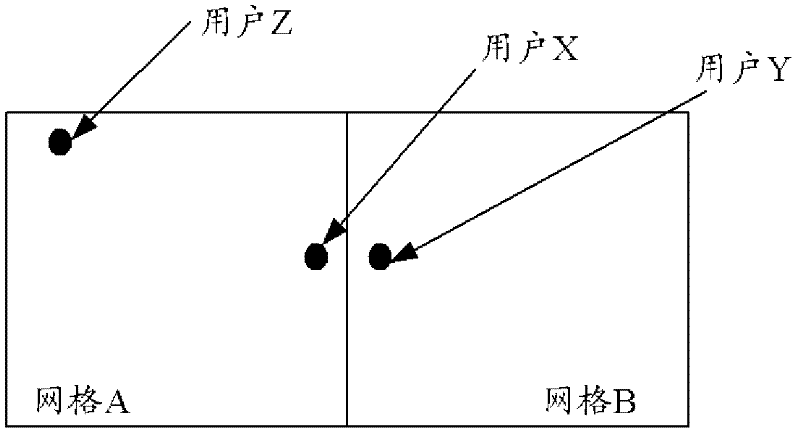
Method for searching nearby users in social network, and server
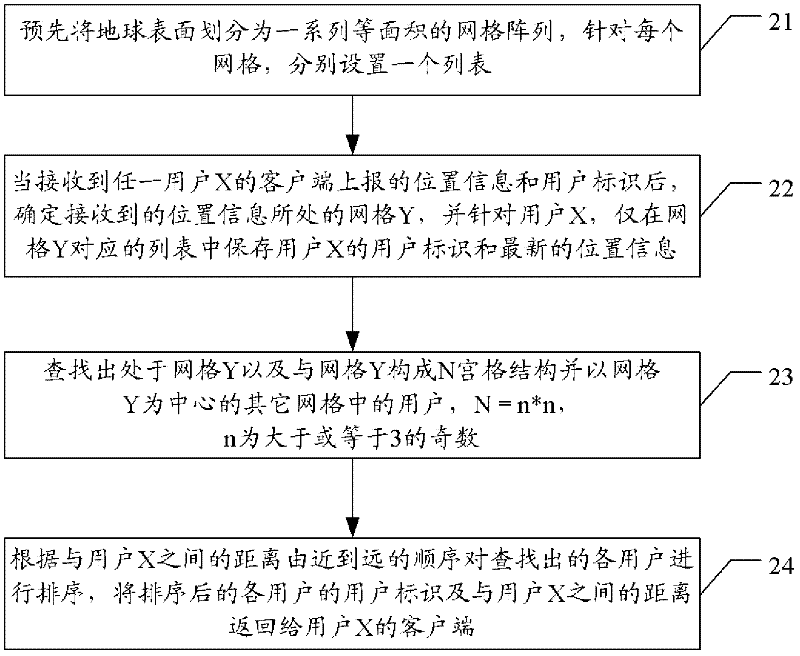
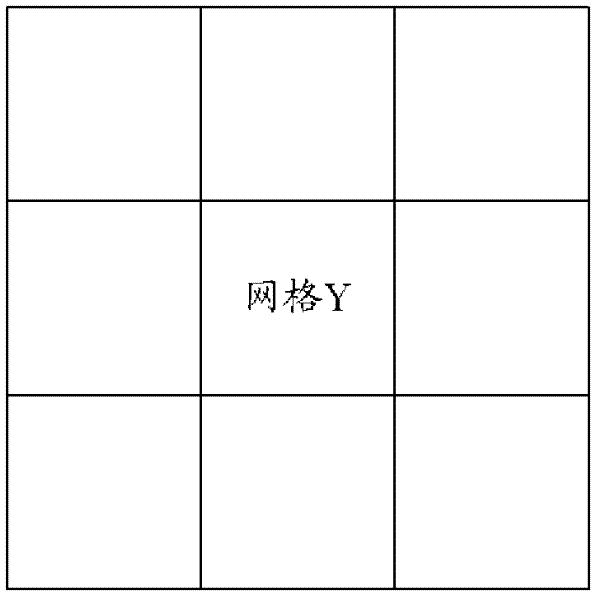
ActiveCN102571910AImprove accuracyOffice automationGeographical information databasesUser identifierEarth surface
The invention discloses a method for searching nearby users in a social network, and a server. The method comprises the following steps of: dividing the earth surface into a series of grid arrays with equal area in advance, and respectively setting a list for each grid; when receiving position information and a user identifier which are reported by a client side of any user X, determining a gird Y where the received position information is located, and storing the user identifier and latest position information of the user X in the list corresponding to the grid Y; searching users in other grids which are positioned in the grid Y, forms an N-grid structure together with the grid Y and takes the grid Y as a center; and searching and sequencing all the users according to a sequence of distances between the users and the user X from nearby to far, and returning user identifiers of all the sequenced users and the distances between the sequenced users and the user X to the client side of the user X, wherein in the sequencing process, a reporting time factor can be further considered. Due to application of the method and device disclosed by the invention, the result searching accuracy can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
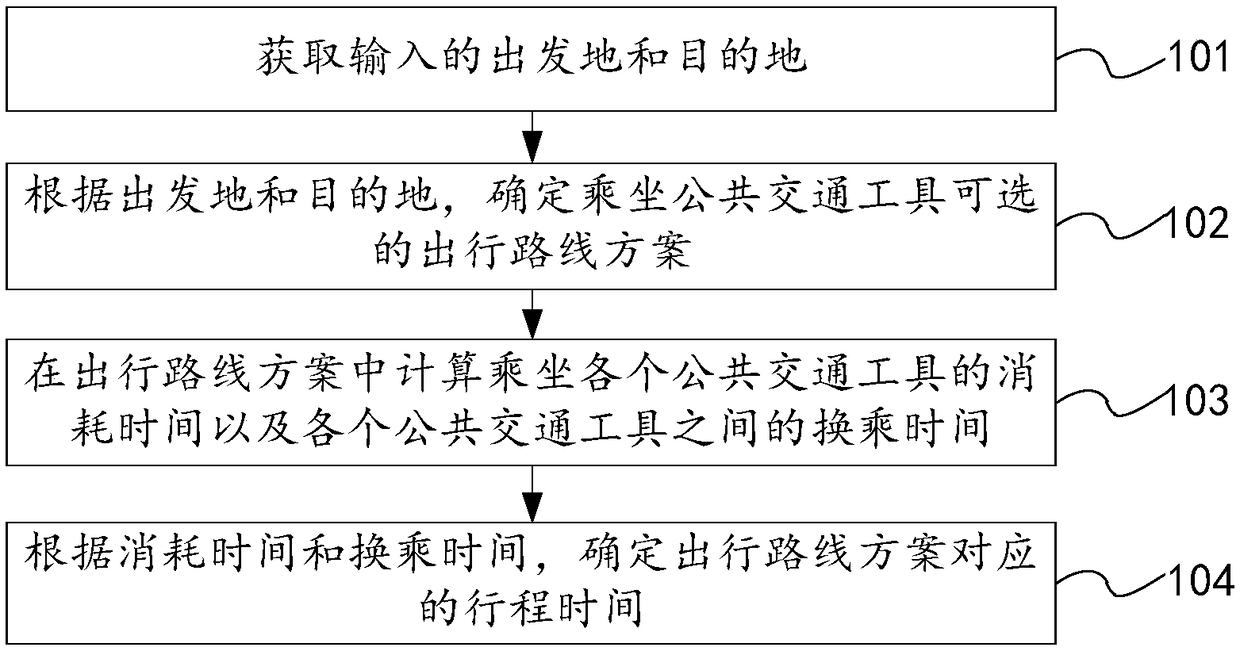
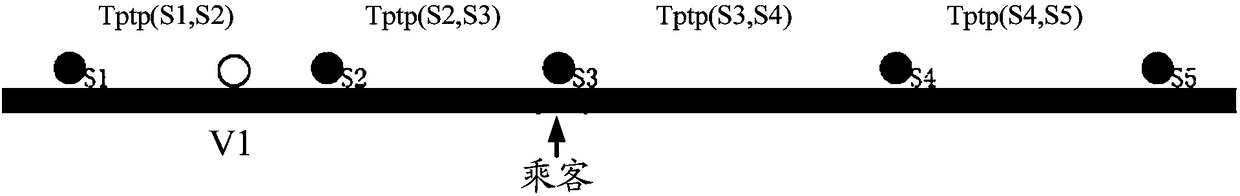
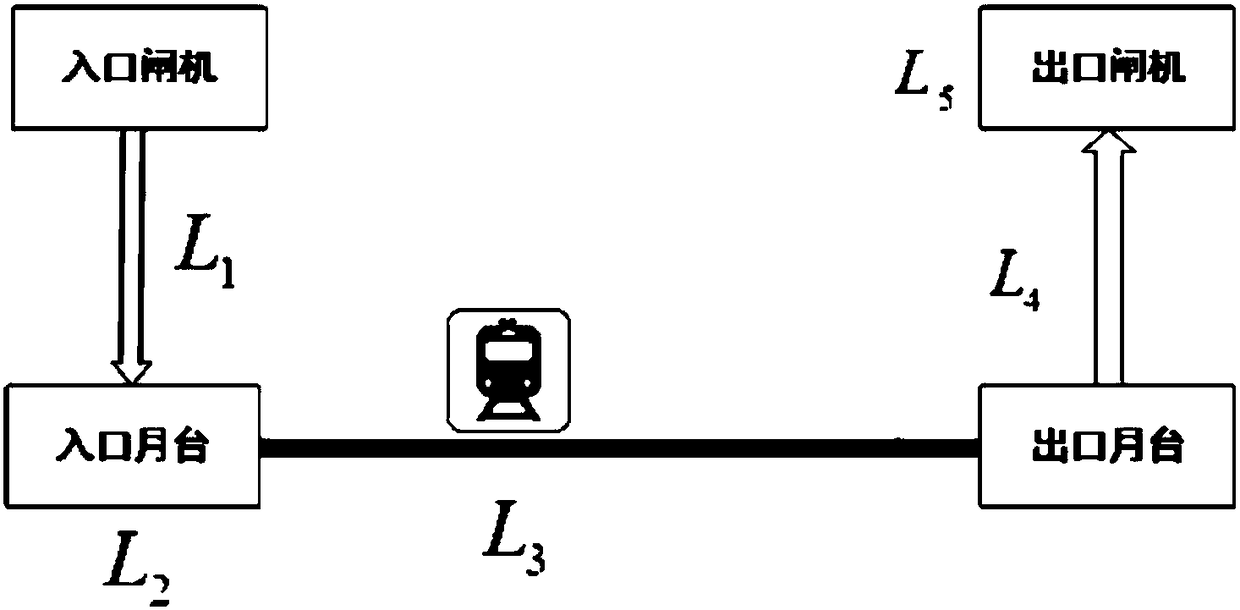
Method and device for calculating travel time of urban public transportation system
ActiveCN108151756AConvenient ArrangementComprehensive time factorInstruments for road network navigationForecastingWalking timeEngineering
The invention discloses a method and a device for calculating the travel time of an urban public transportation system. The method comprises the steps of acquiring an input departure place and an input destination; according to the departure place and the destination, determining optional travel route plans for taking public transport means; in the travel route plan, calculating the time consumedfor taking each public transport means, and the transfer time between each two public transport means, wherein the consumed time comprises walking time, waiting time, riding time, and / or card swipingenter time, and / or card swiping exit time, and / or exit card swiping queueing time; and the transfer time comprises transfer walking time and transfer waiting time; according to the consumed time and the transfer time, determining the travel time corresponding to each travel route plan. Multiple time factors during a taking process are combined, and the travel time of the whole travel route plane is accurately calculated, so that a user can better arrange a travel plan according to the travel time.
Owner:SHENZHEN INTEGRATION TRAFFIC OPERATION COMMAND CENT +1
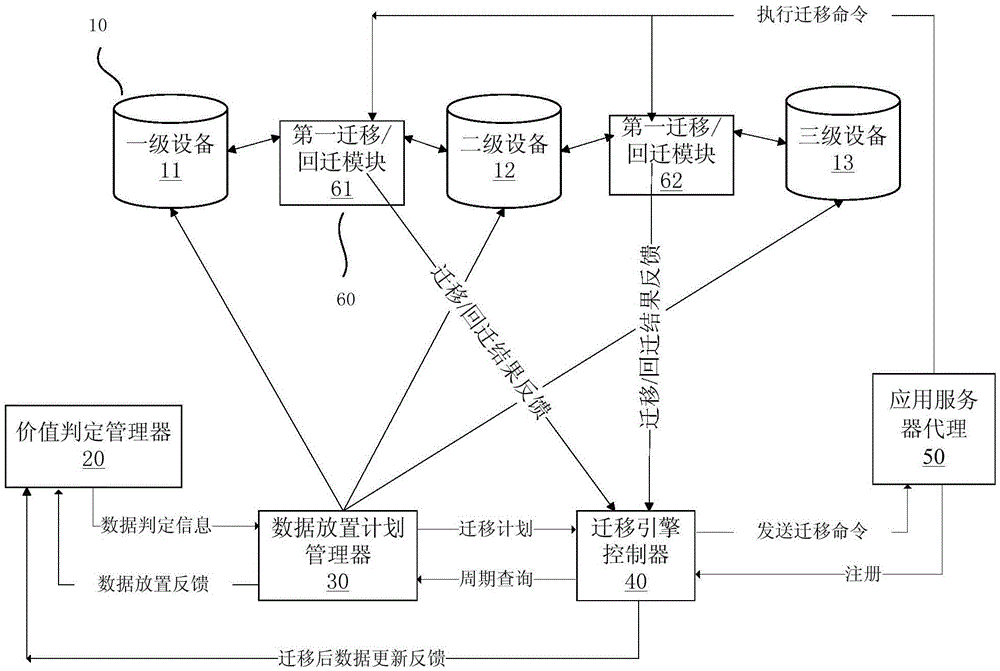
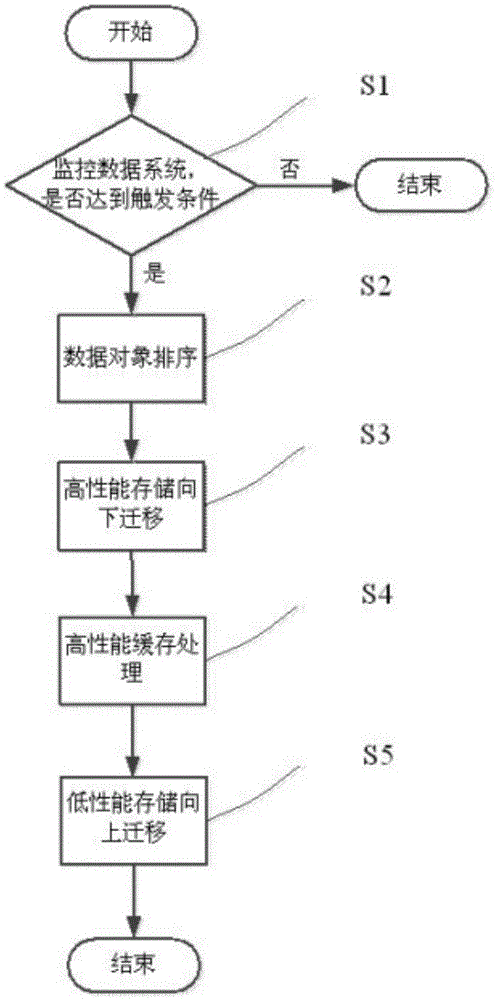
Hierarchical storage and migration method of industrial real-time data
ActiveCN105653591AImprove accuracyInhibit repeated migrationSpecial data processing applicationsDatabase indexingReal-time dataObject migration
The invention provides a hierarchical storage and migration method and system of industrial real-time data. The method comprises the following steps: monitoring a hierarchical storage system in fixed time, and triggering data migration calculation after the storage volume use ratio of advanced storage equipment achieves a first preset threshold value; during migration, firstly, carrying out value assessment on each data object in the storage equipment to obtain the value of each data object and sort the data object according to the value; and according to sorting, setting a migration strategy, picking up the data object to be migrated, and forming and migrating a migration queue. The method and the system set the migration strategy according to different storage equipment priorities and the value sorting of the current data objects, wherein value calculation considers a time factor, number of access users, other data object situations associated with the data object, the access contrast ratio of different storage equipment and the own size of the data object, and the time factor, the number of access users, other data object situations associated with the data object, the access contrast ratio of different storage equipment and the own size of the data object affect data object migration efficiency. The method improves data value judgment accuracy.
Owner:浙江舟山至控智能装备技术有限公司
Dynamic social network-oriented influence maximization analysis method
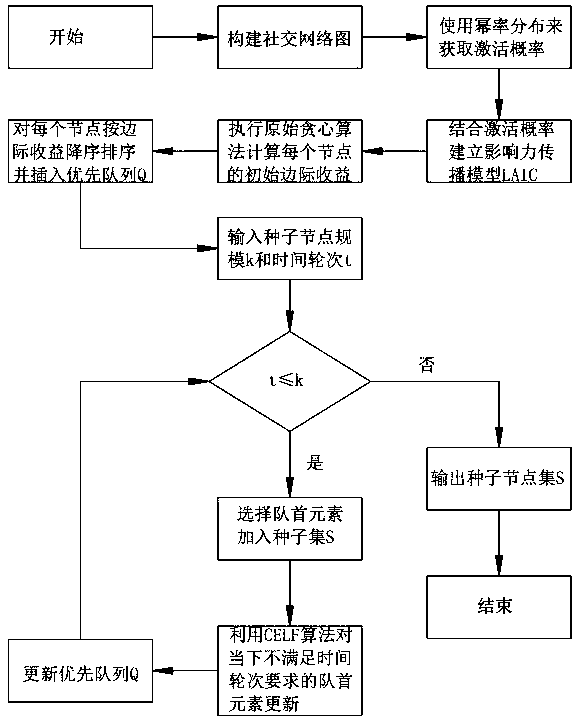
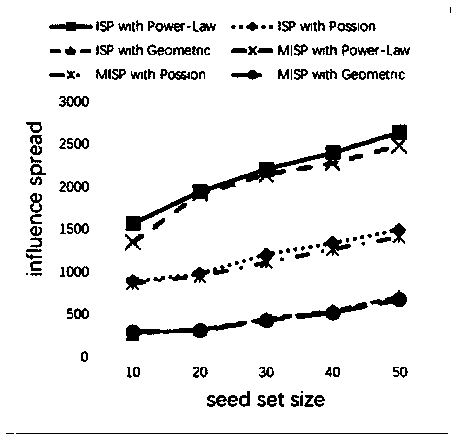
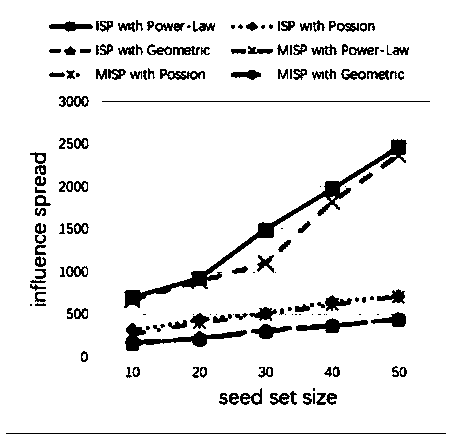
PendingCN108510115ARemarkable resultsReasonable running timeForecastingResourcesNODALInfluence propagation
The invention discloses a dynamic social network-oriented influence maximization analysis method. The method specifically comprises the steps of (1) obtaining an activation probability, and adding a time factor into the activation probability by using power law distribution of an influence delay distribution function; (2) building an influence propagation model LAIC; (3) executing a greedy algorithm, and calculating an initial marginal income of each node by utilizing the greedy algorithm; and (4) optimizing an original greedy algorithm by using a CELF algorithm, and improving the efficiency of searching for seed nodes through sub-mode characteristics of the influence function and an influence priority queue. By analyzing the effect of the time factor in influence propagation, the power law distribution of the distribution function, consistent with real social network node degree distribution is used, and finally an excellent result and reasonable running time are achieved in selectingTOP-K nodes with highest influence, so that the problem of dynamic social network influence maximization is effectively solved.
Owner:SHANDONG UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com