Method for checking stack frame destruction
A stack frame and stack technology, applied in the direction of software testing/debugging, can solve problems such as complexity and loopholes, achieve high security and prevent malicious attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
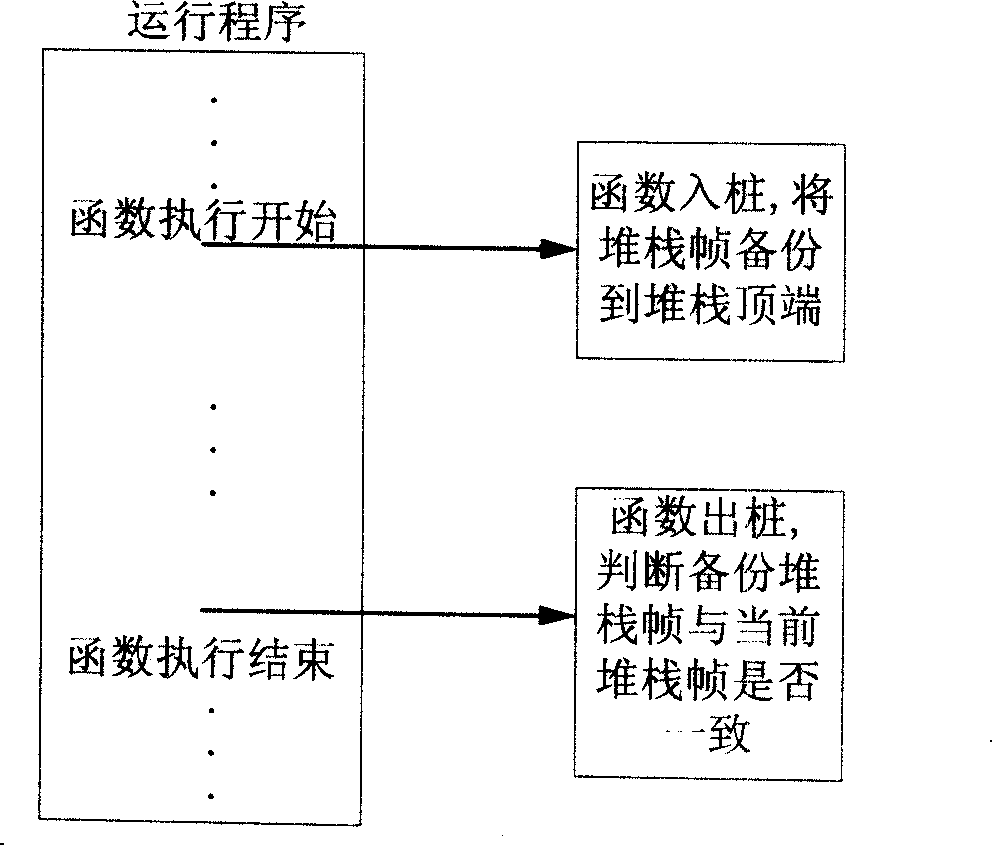
[0018] The present invention provides a pure software method that utilizes the automatic stub insertion of a compiler, backs up the return address to the top of the stack in the function entry, and judges whether the stack frame is destroyed according to the backed up return address in the function exit. A small amount of memory at the top of the space, at the cost of a small decrease in program running speed, in exchange for the timeliness and higher security of program bug location.
[0019] Below in conjunction with the accompanying drawings, specific embodiments of the present invention will be described in detail on the IA-32 architecture, the GNU C compiler, and the VxWorks operating system. Including the following steps:
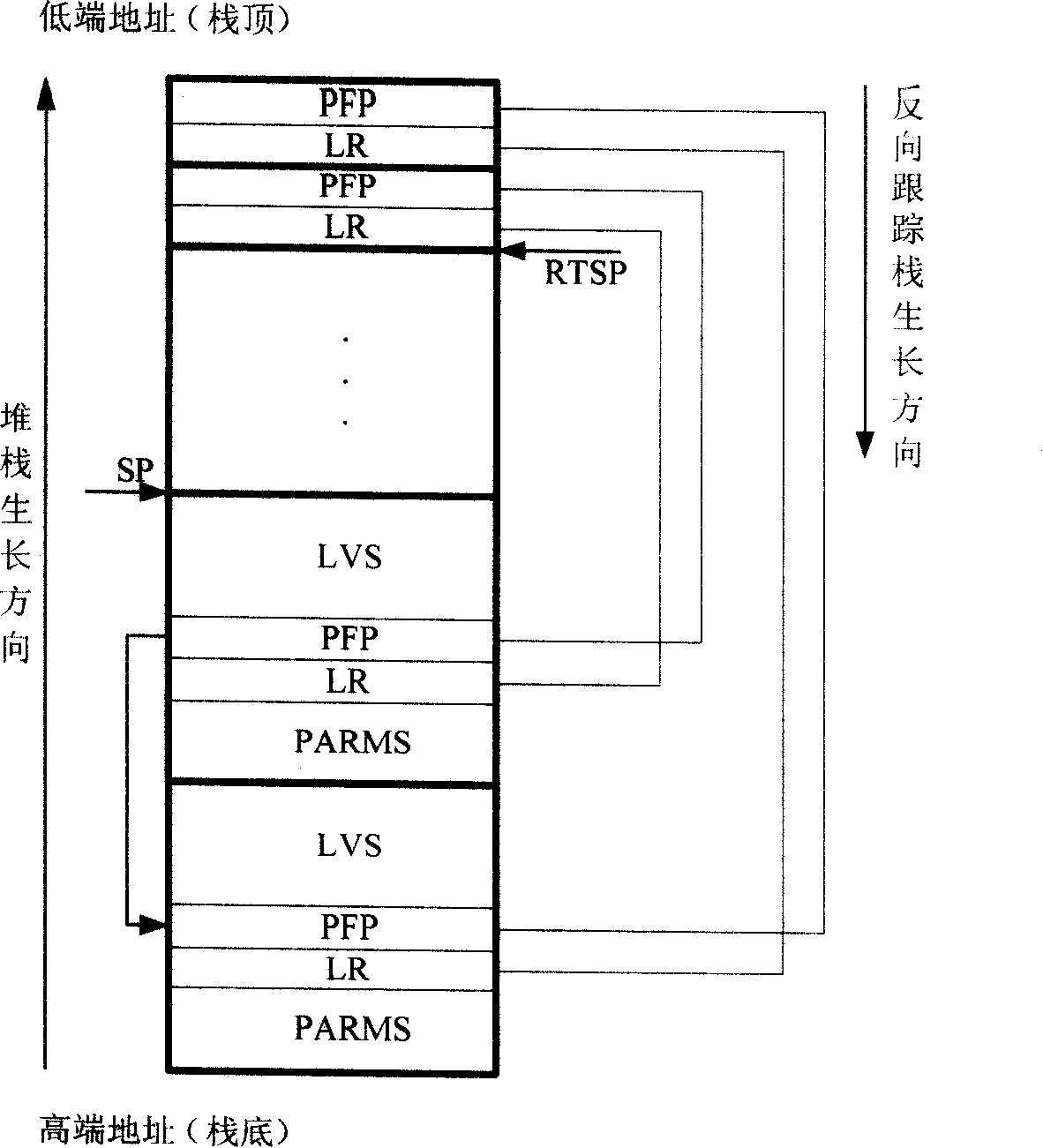
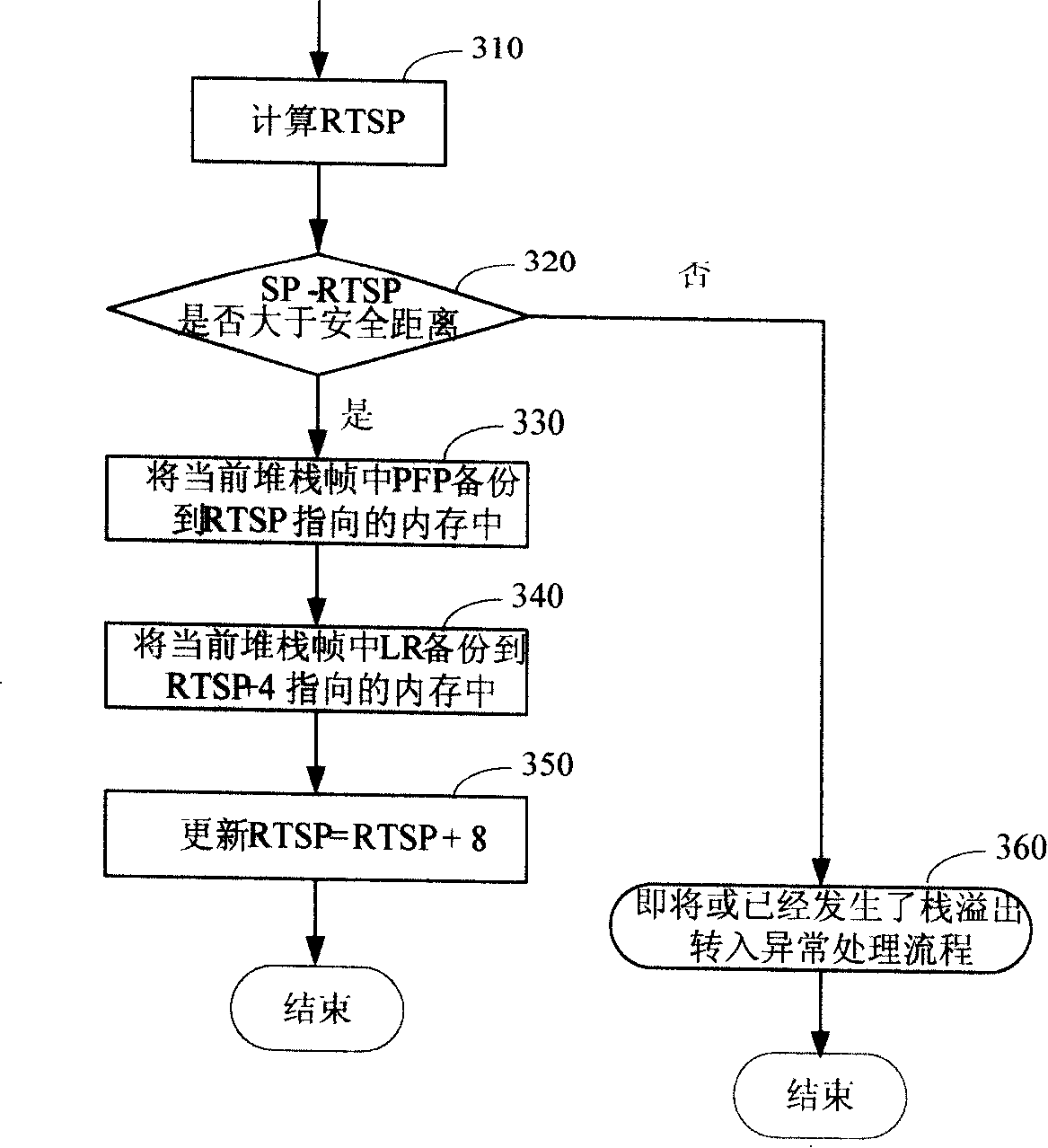
[0020] Step 110, increase a reverse tracking stack pointer (RTSP) field in the task control block of the operating system, and this RTSP points to the memory area storing the safety backup of the return address (LR) and the current stack frame pointer...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com