Patents
Literature
125 results about "Stack overflow" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
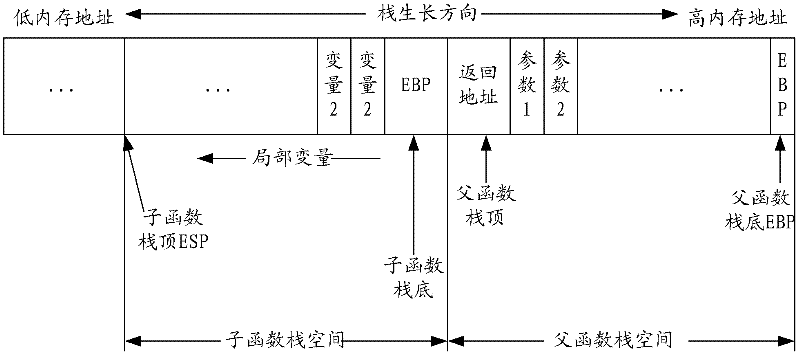
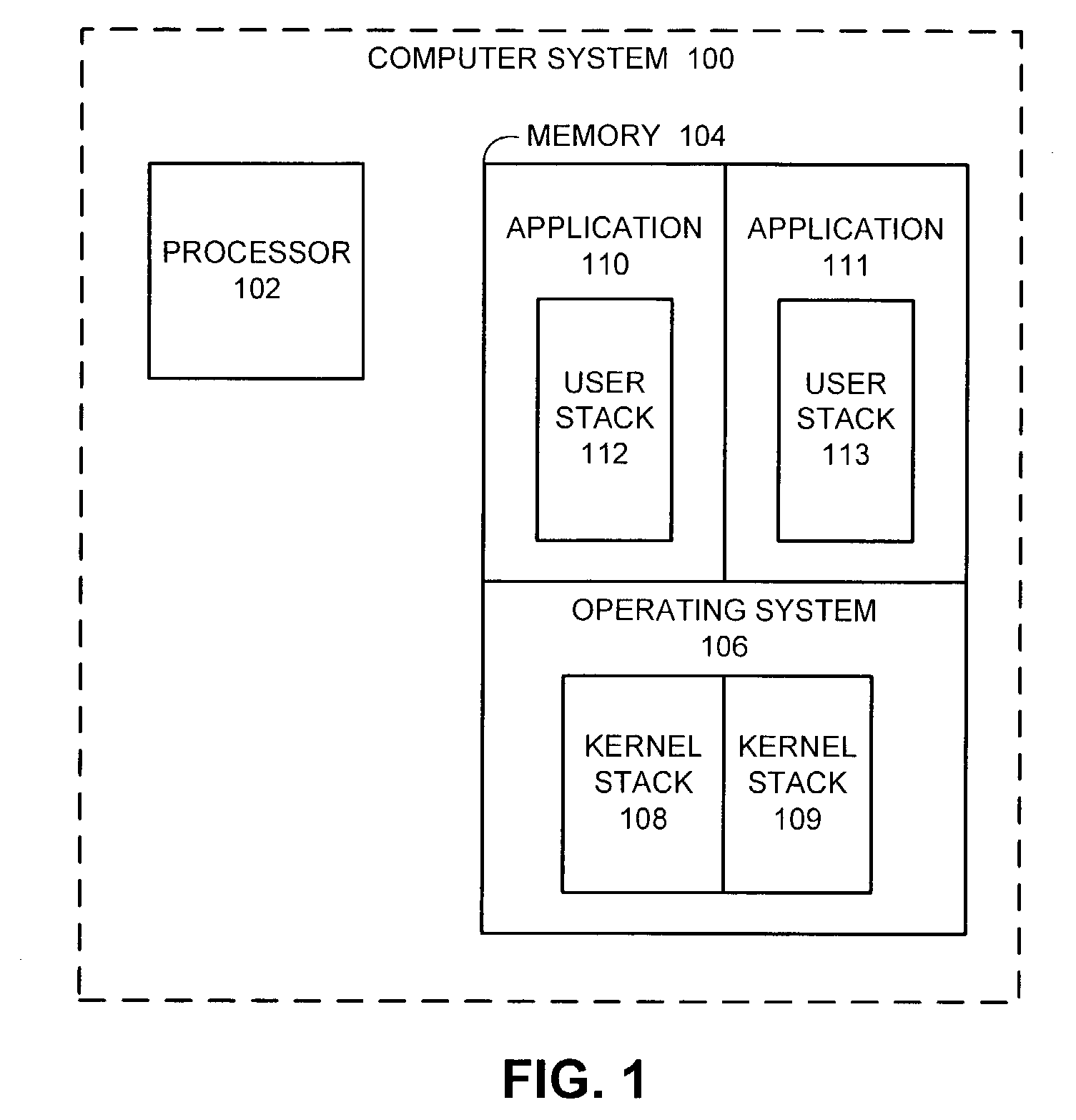
In software, a stack overflow occurs if the call stack pointer exceeds the stack bound. The call stack may consist of a limited amount of address space, often determined at the start of the program. The size of the call stack depends on many factors, including the programming language, machine architecture, multi-threading, and amount of available memory. When a program attempts to use more space than is available on the call stack (that is, when it attempts to access memory beyond the call stack's bounds, which is essentially a buffer overflow), the stack is said to overflow, typically resulting in a program crash.
Microprocessor protected against stack overflow
InactiveUS20130013965A1Improve securityFault responsePlatform integrity maintainanceCall stackStack overflow
A microprocessor includes a central processing unit, at least one call stack, a stack pointer, an address bus, and a data bus. The microprocessor further includes a hardware monitor configured to supply protection codes, insert the protection codes in the stack or let the central processing unit insert them, and then generate an error signal in response to an attempt to modify a protection code present in the stack.
Owner:STMICROELECTRONICS SRL
Method for use of stack
InactiveUS6948034B2Minimizing deteriorationProgram initiation/switchingSpecific program execution arrangementsParallel computingStack overflow
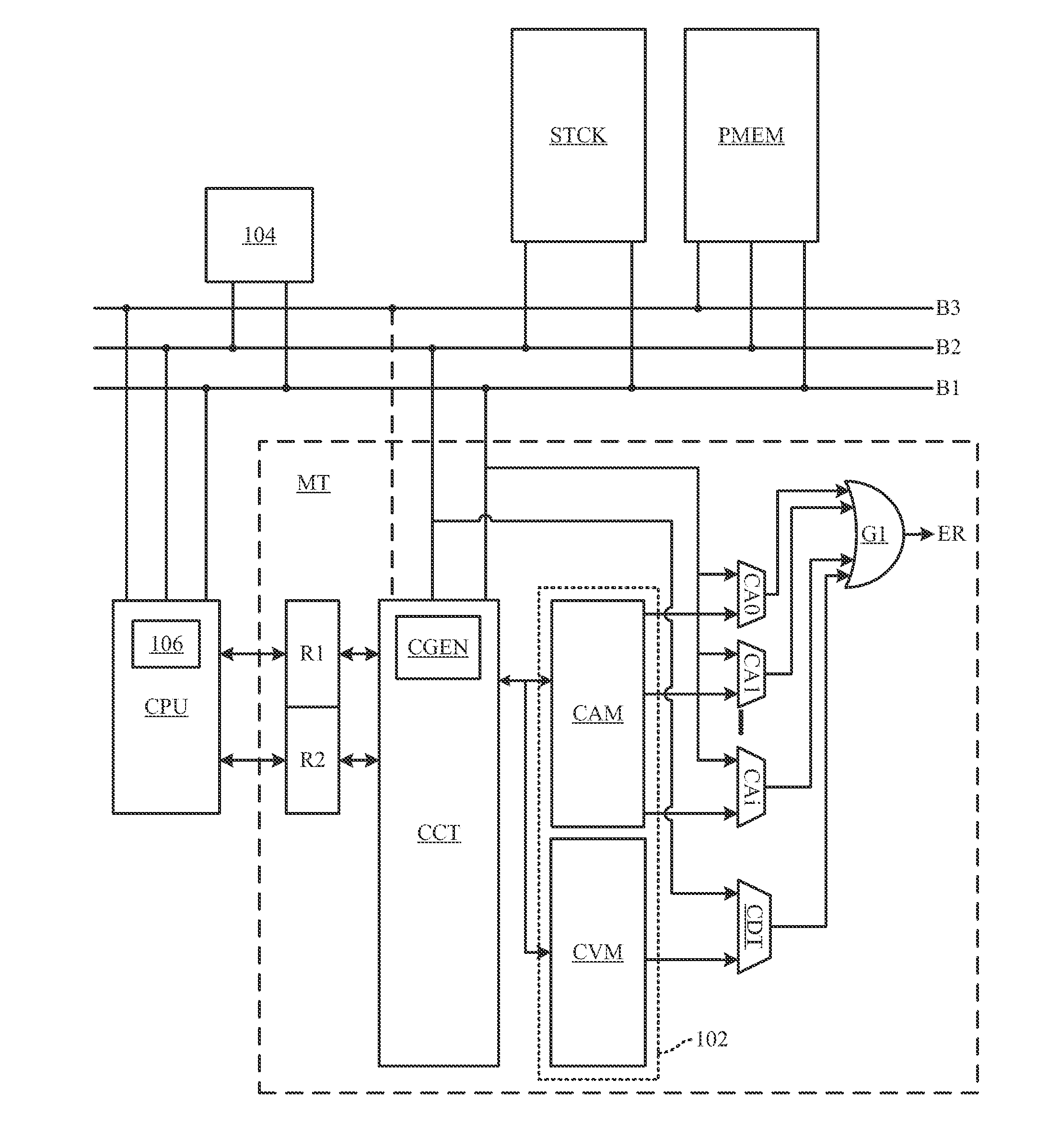
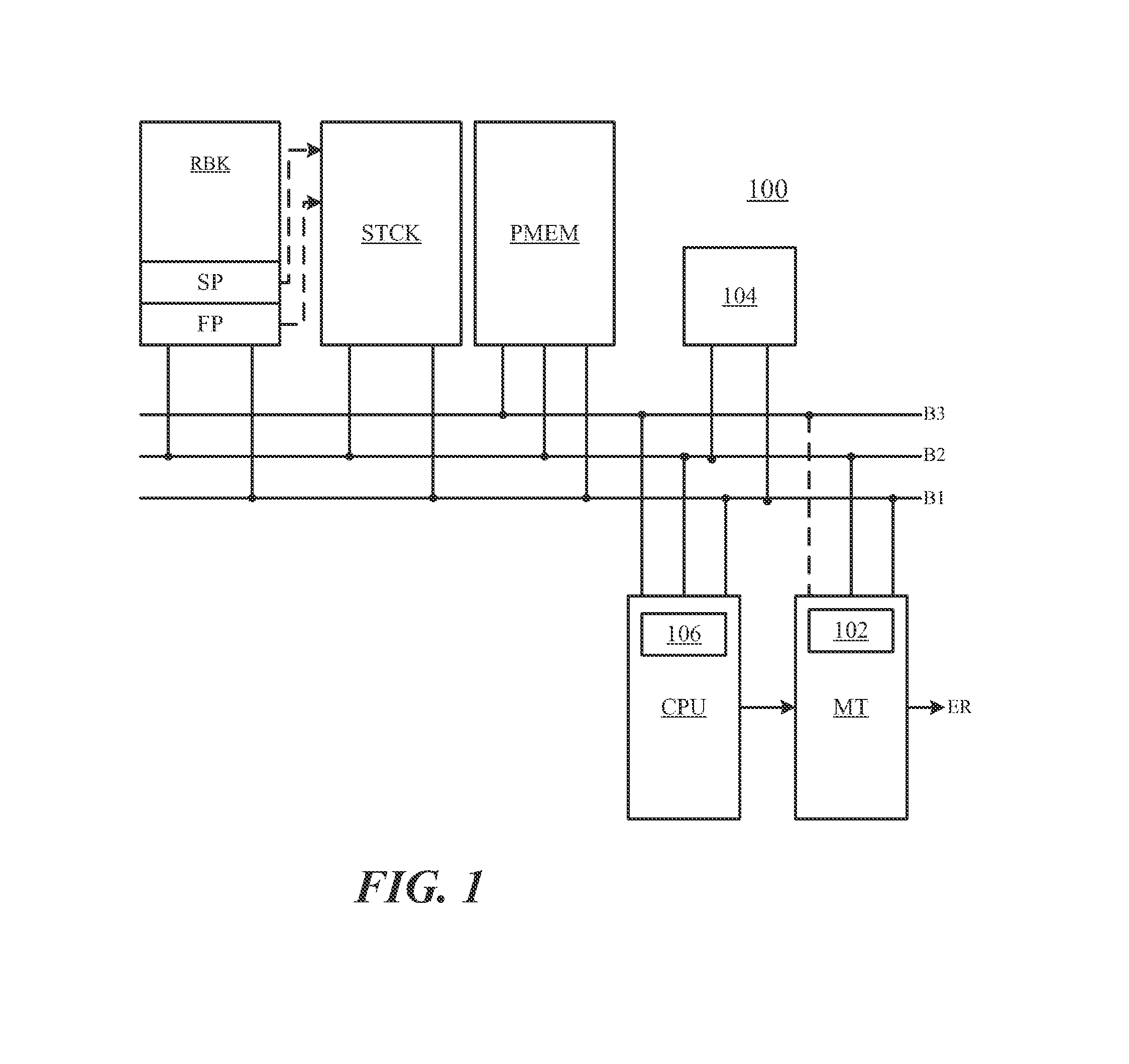
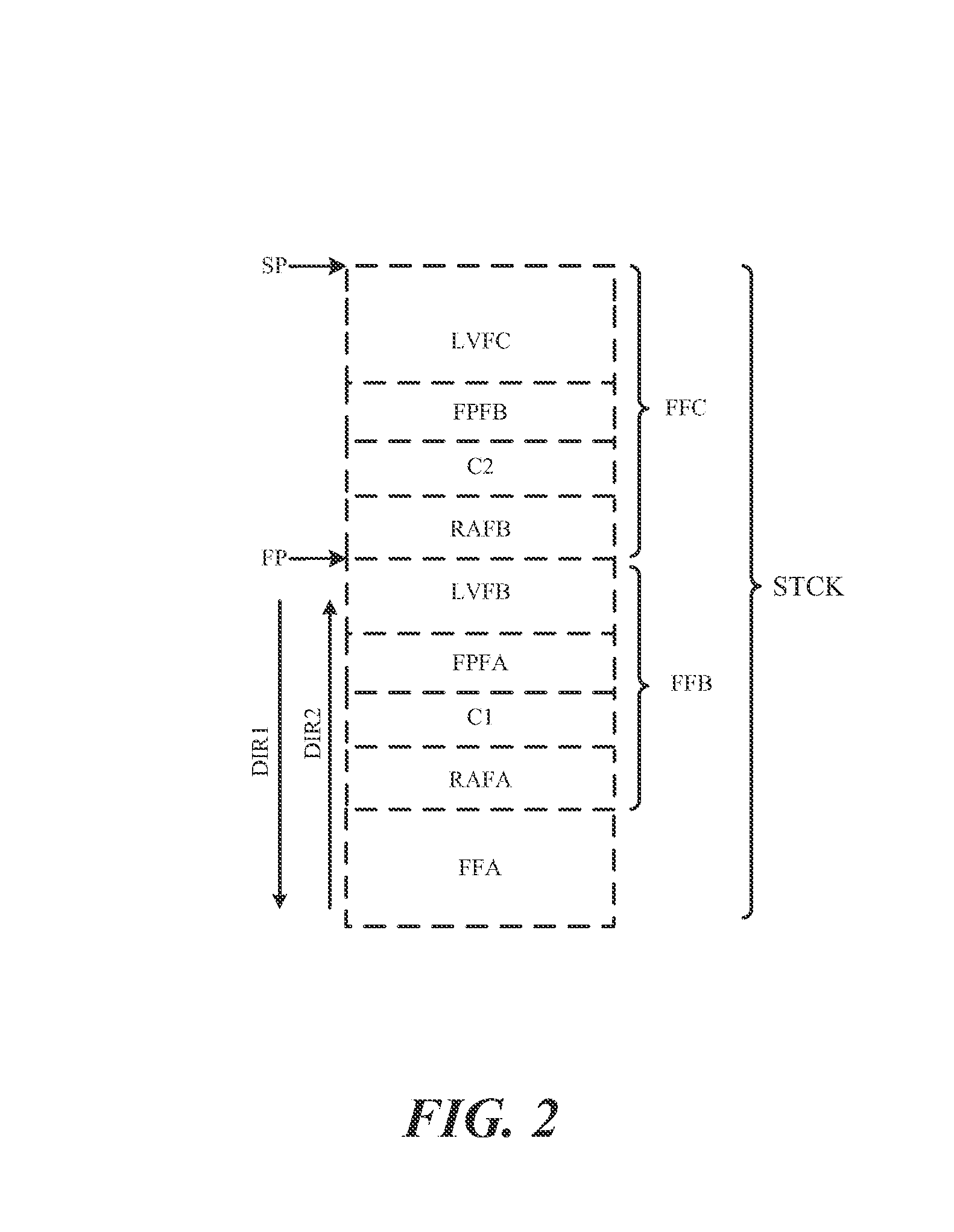
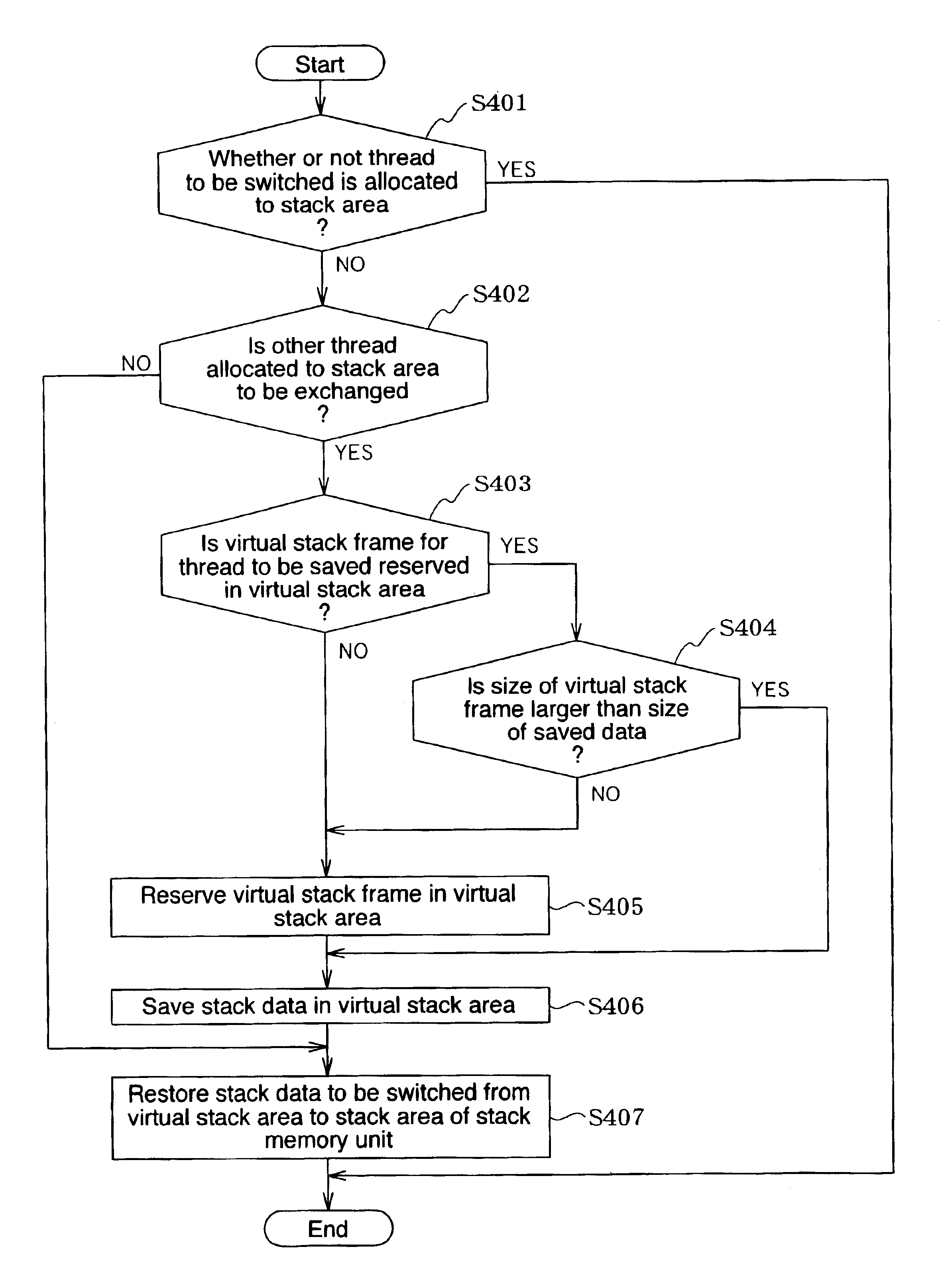
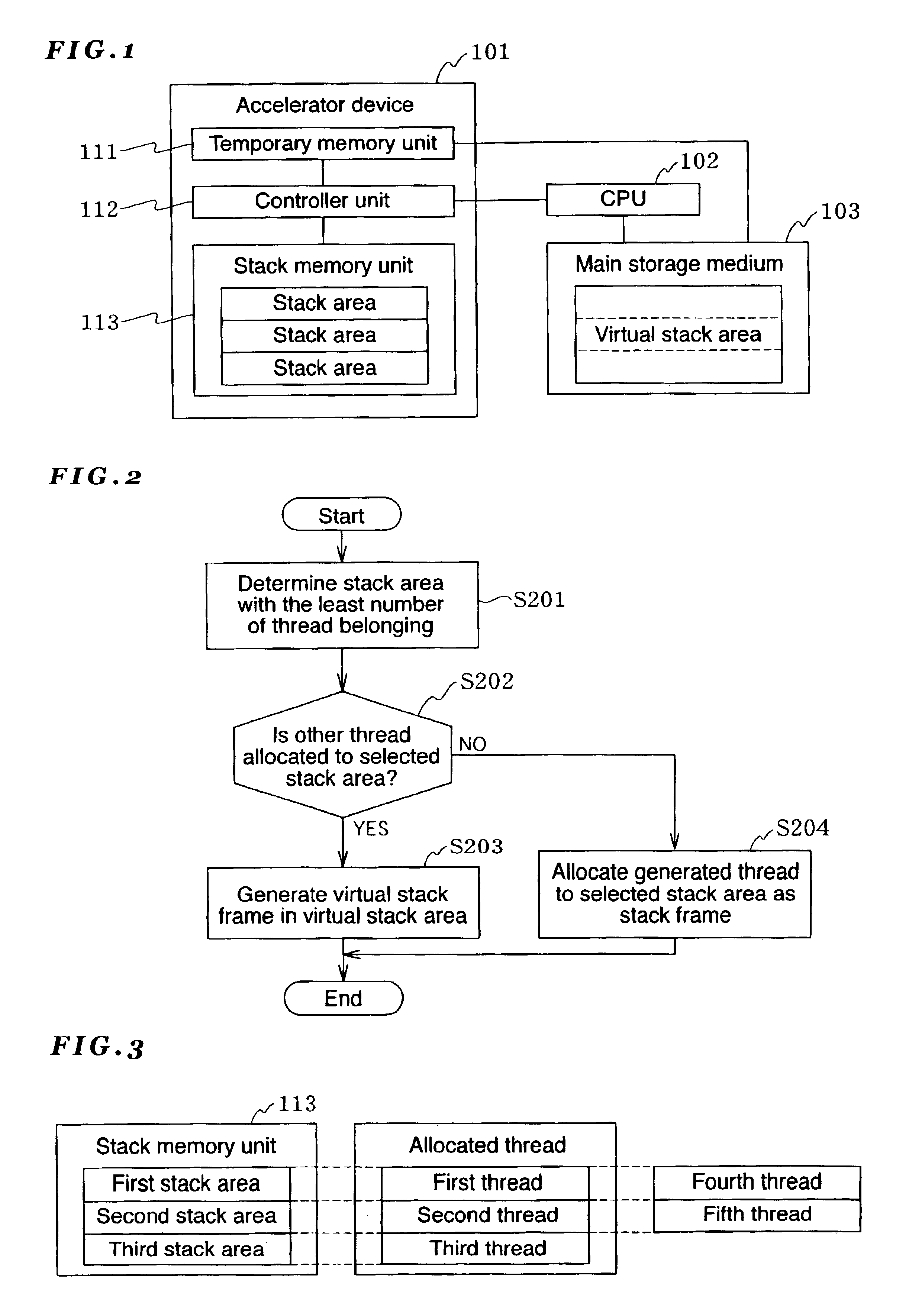
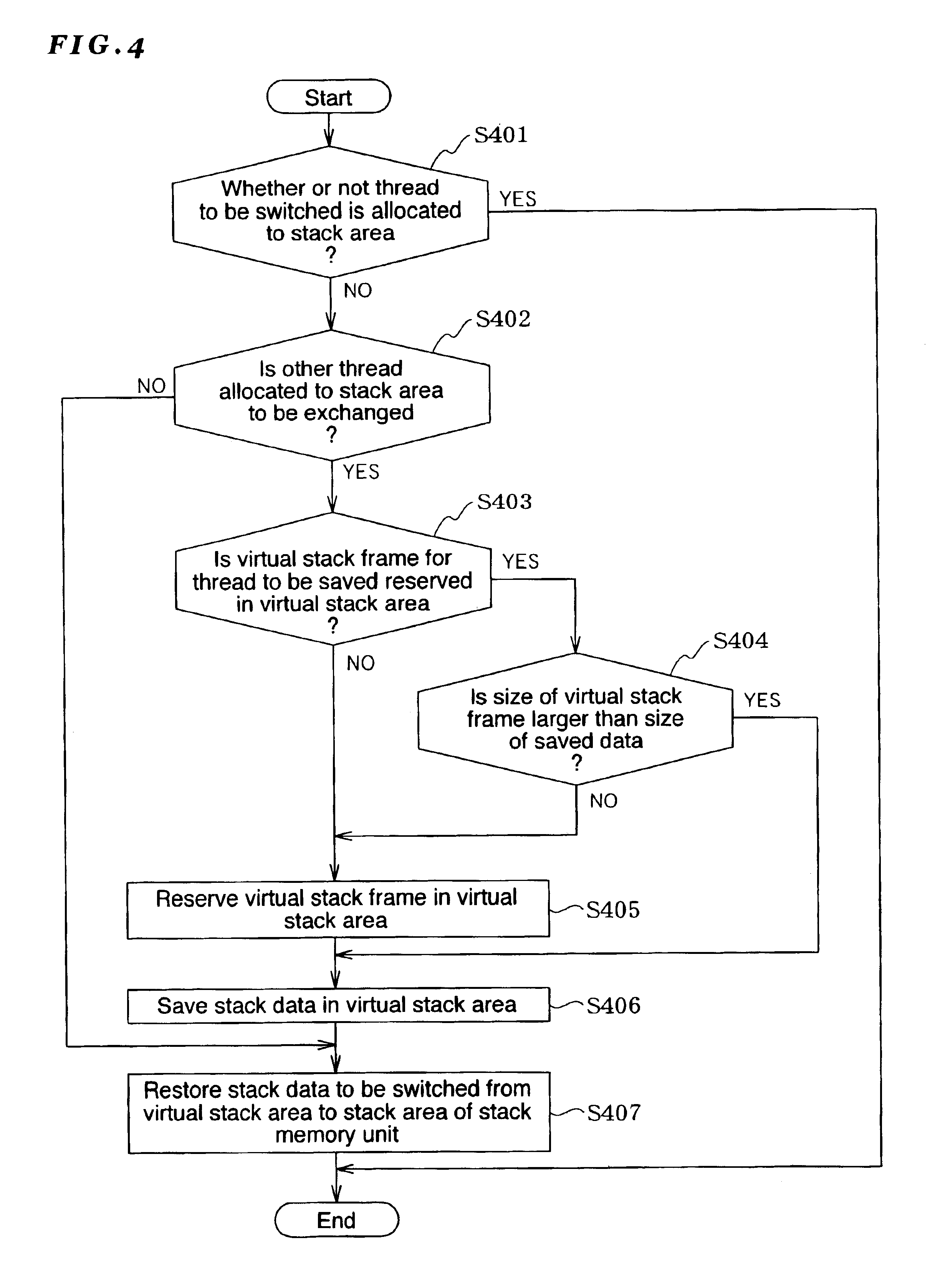
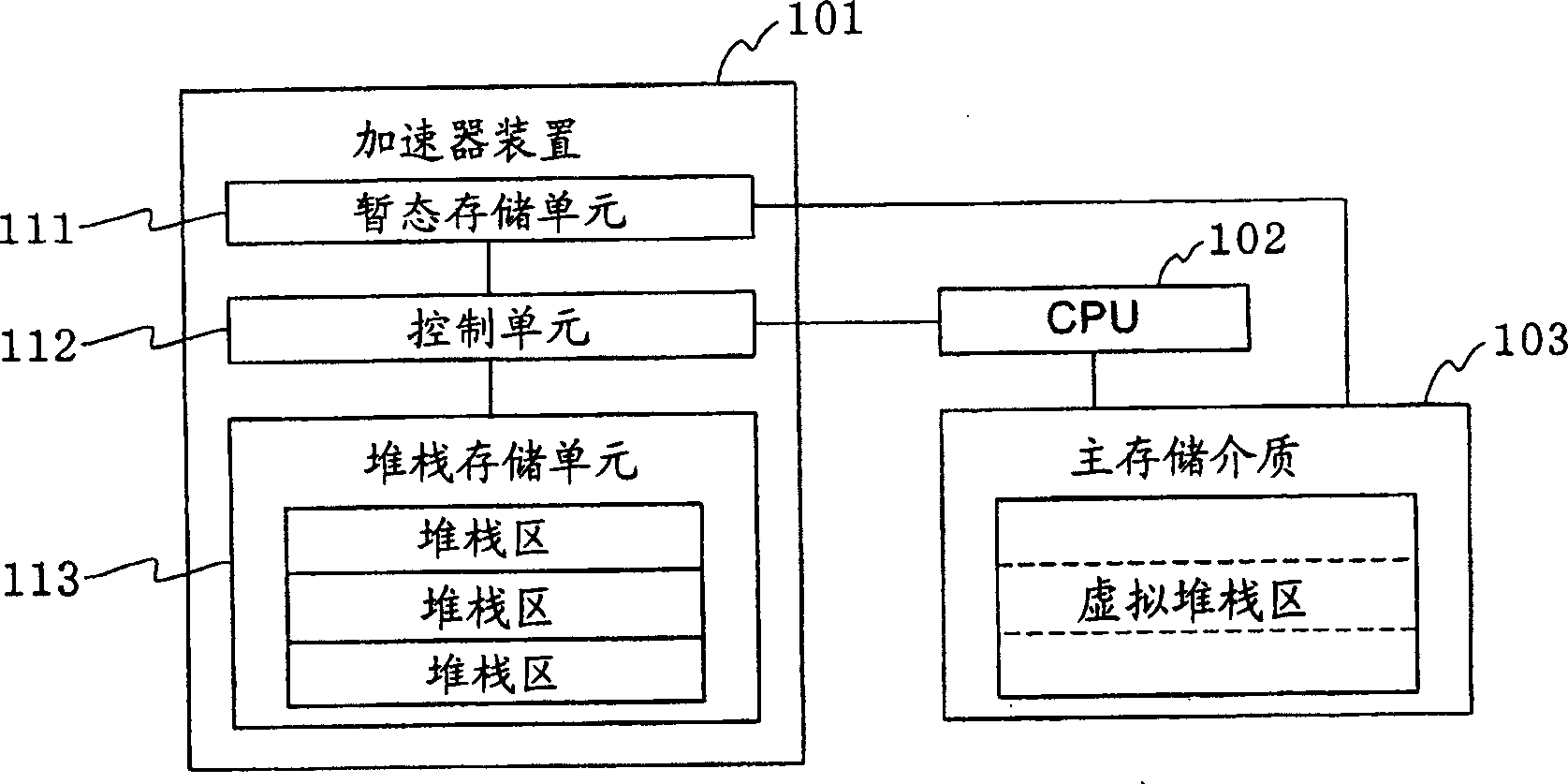
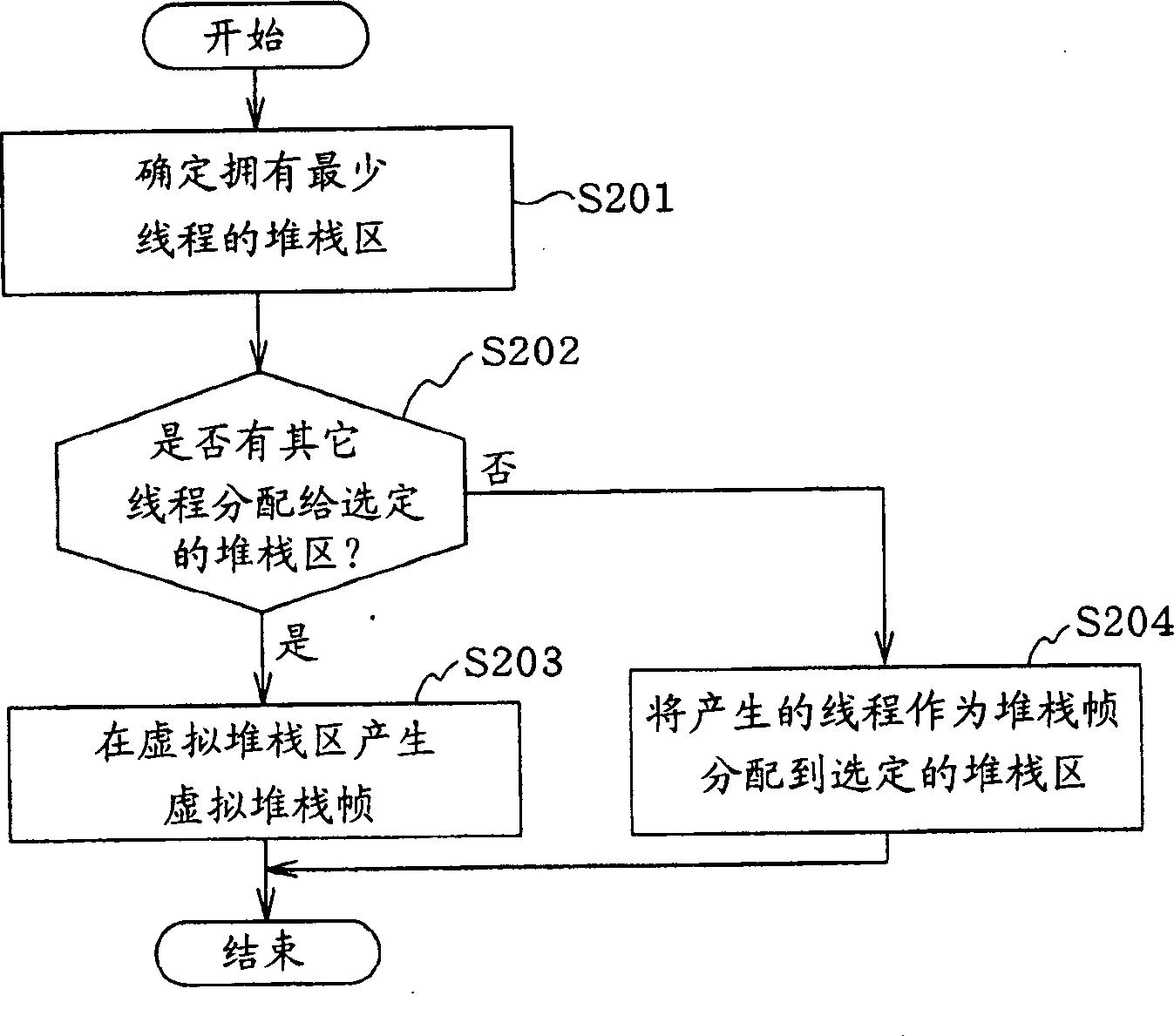
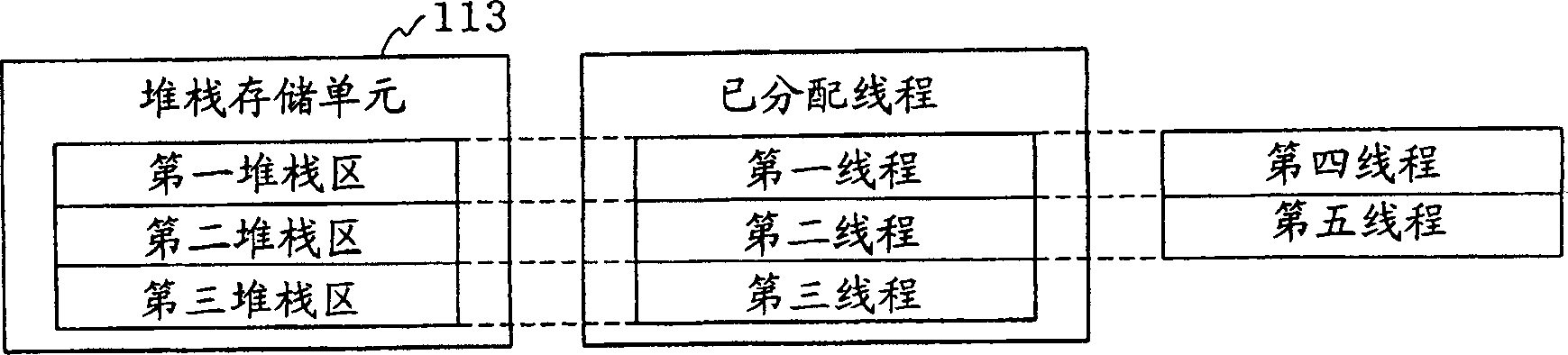
The present invention has an objective of minimizing deterioration of the processing speed of a Java accelerator device even when stack overflow occurs in a stack memory unit.A first thread presently allocated to a first stack area of a stack memory unit 113 to which a fourth thread belongs is saved in a virtual stack area of a main storage medium 103. Thereafter, the data of the fourth thread as stack data to be switched is copied to the first stack area of the stack memory unit 113 by the controller unit 112 (accelerator device 101).
Owner:LENOVO INNOVATIONS LTD HONG KONG
Highly-available contract executing method and system
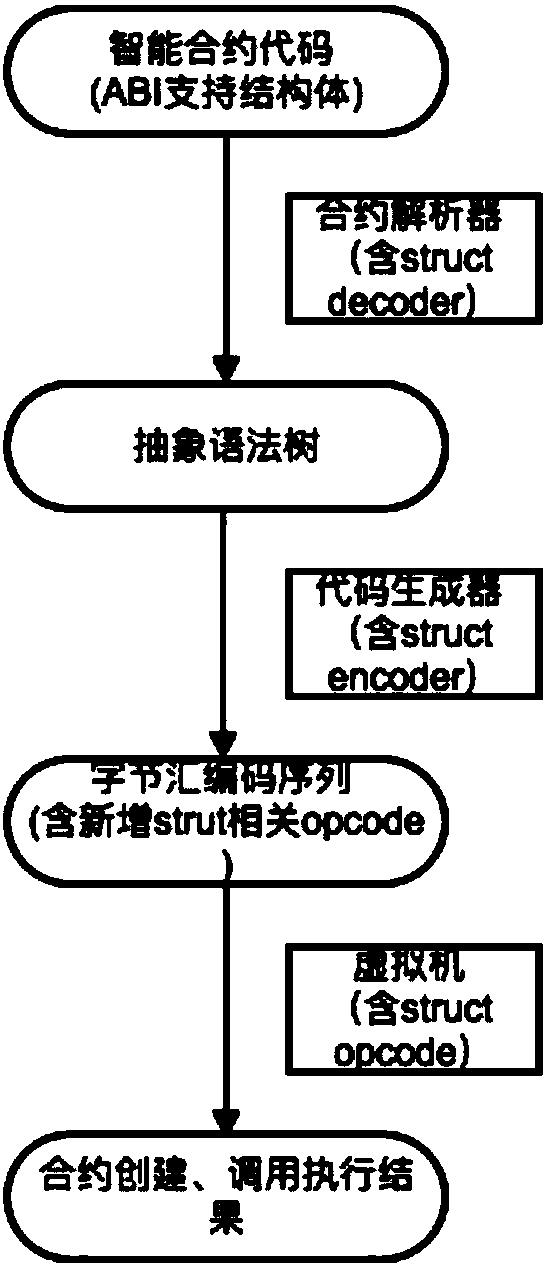
ActiveCN107844294AReduce writingCompile lowSoftware designCompiler constructionLocal variableTree (data structure)
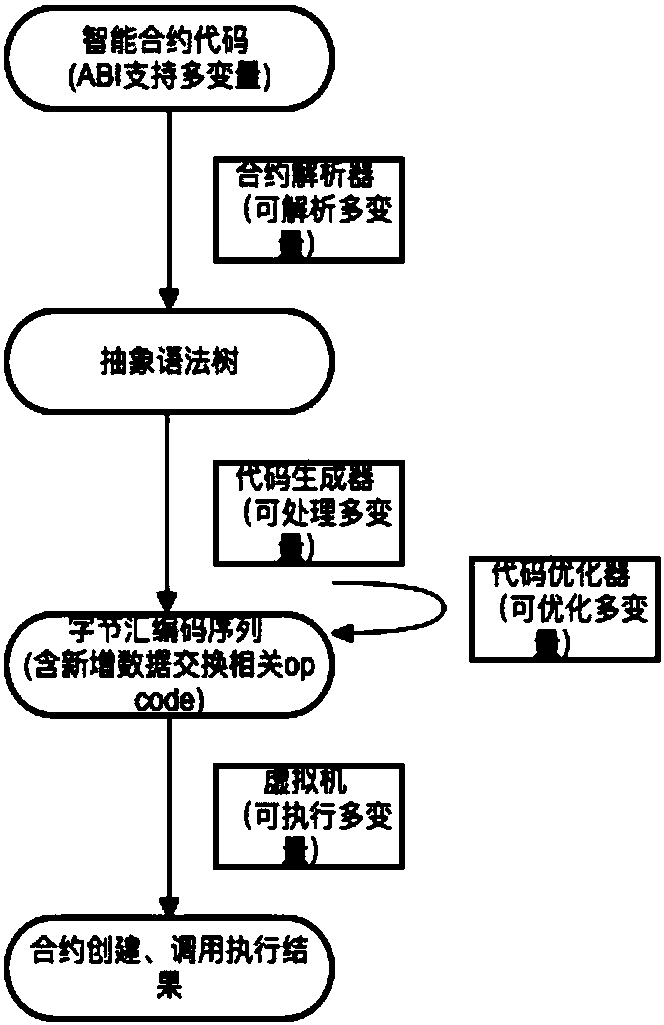
The invention discloses a highly-available contract executing method, which includes steps of (1), compiling an intelligent contract code according to contract information, wherein the intelligent contract code comprises more than maximum stack depth number of local variables, parameters or structure bodies; (2), performing grammar semantic parsing on the intelligent contract code, and generatinga corresponding abstract grammar tree; (3), converting the abstract grammar tree data structure to be a binary byte assembly code sequence and an related order; (4), explaining and executing the byteassembly code sequence by a contract virtual machine. Specific to the problems that the stack is easy to overflow and a stack element cannot be visited at random, the original intelligent contract design adopts an avoiding plan of small stack depth and exchangeable different storage spaces ordinarily; through the plan of realizing the order visit at random by the contract encoder and the virtual machine, the stack overflow is prevented and the random visit of the stack element can be realized. More complex available intelligent contract can be operated on the system; the cost for contract writing, compilation, and execution is lower.
Owner:HANGZHOU RIVTOWER TECH CO LTD
Method and machine for efficient simulation of digital hardware within a software development environment
InactiveUS20050066305A1Reducing CPU branch mis-predictionEasy to useCAD circuit designSpecial data processing applicationsSoftware development processParallel computing
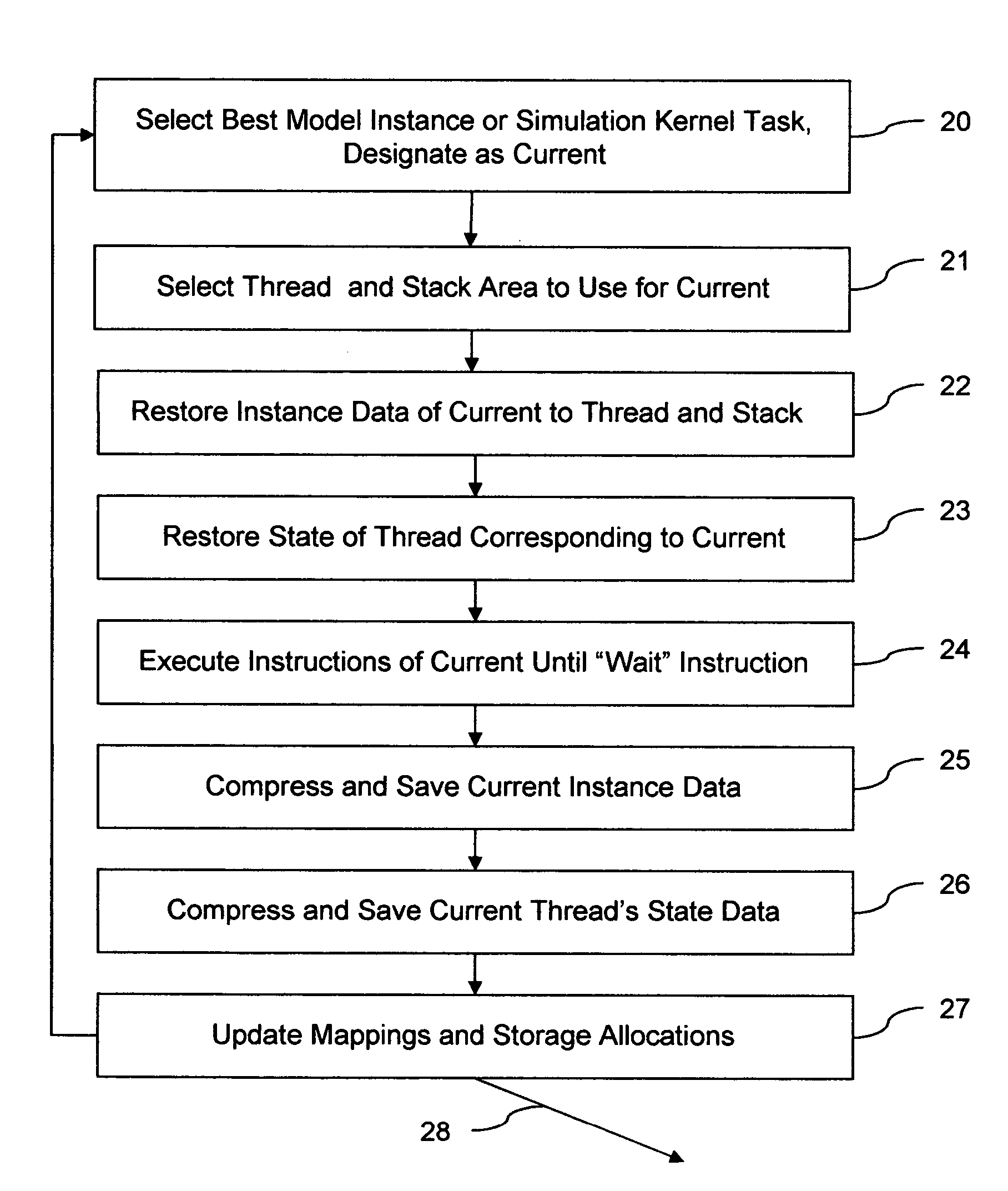
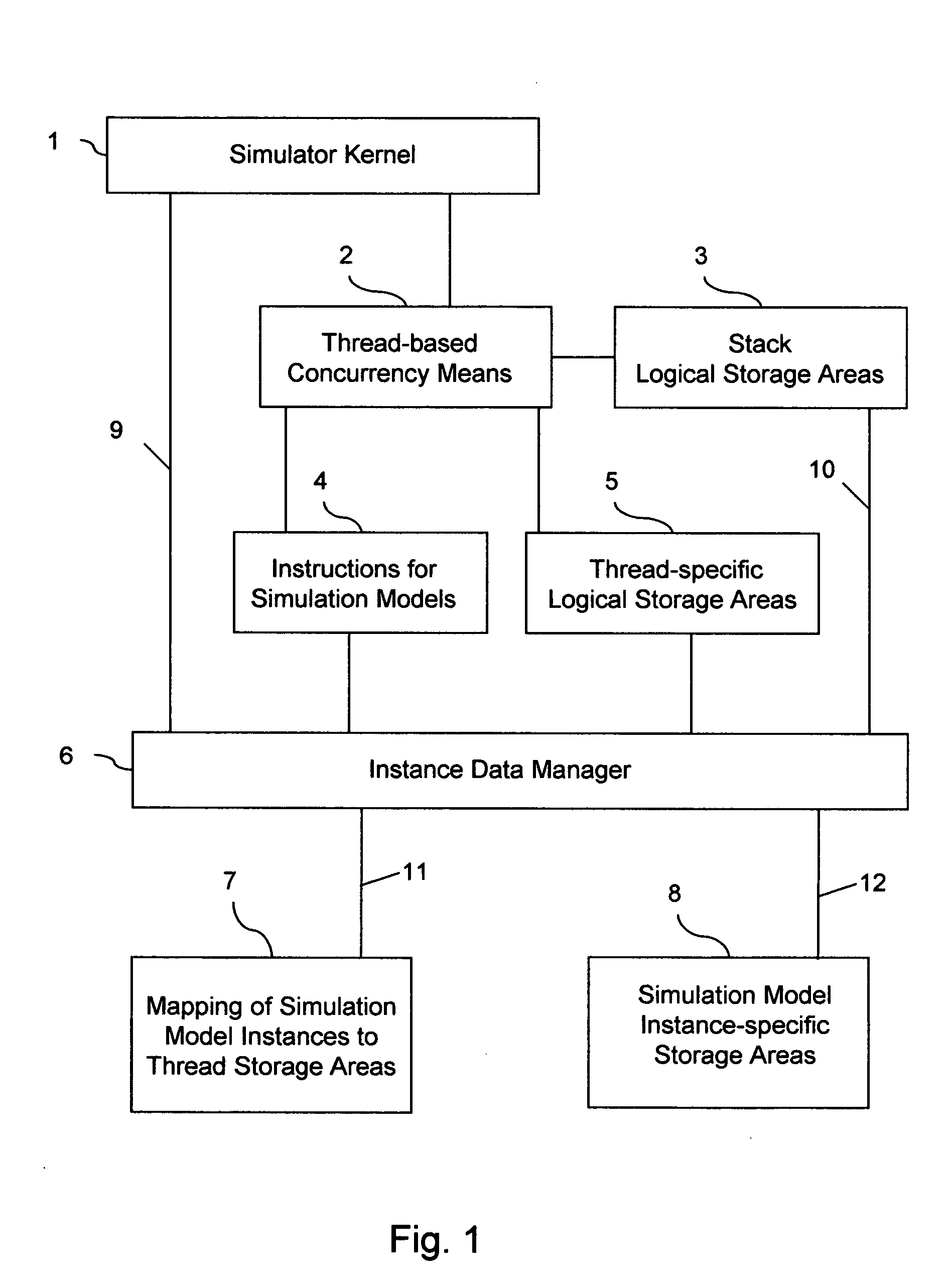
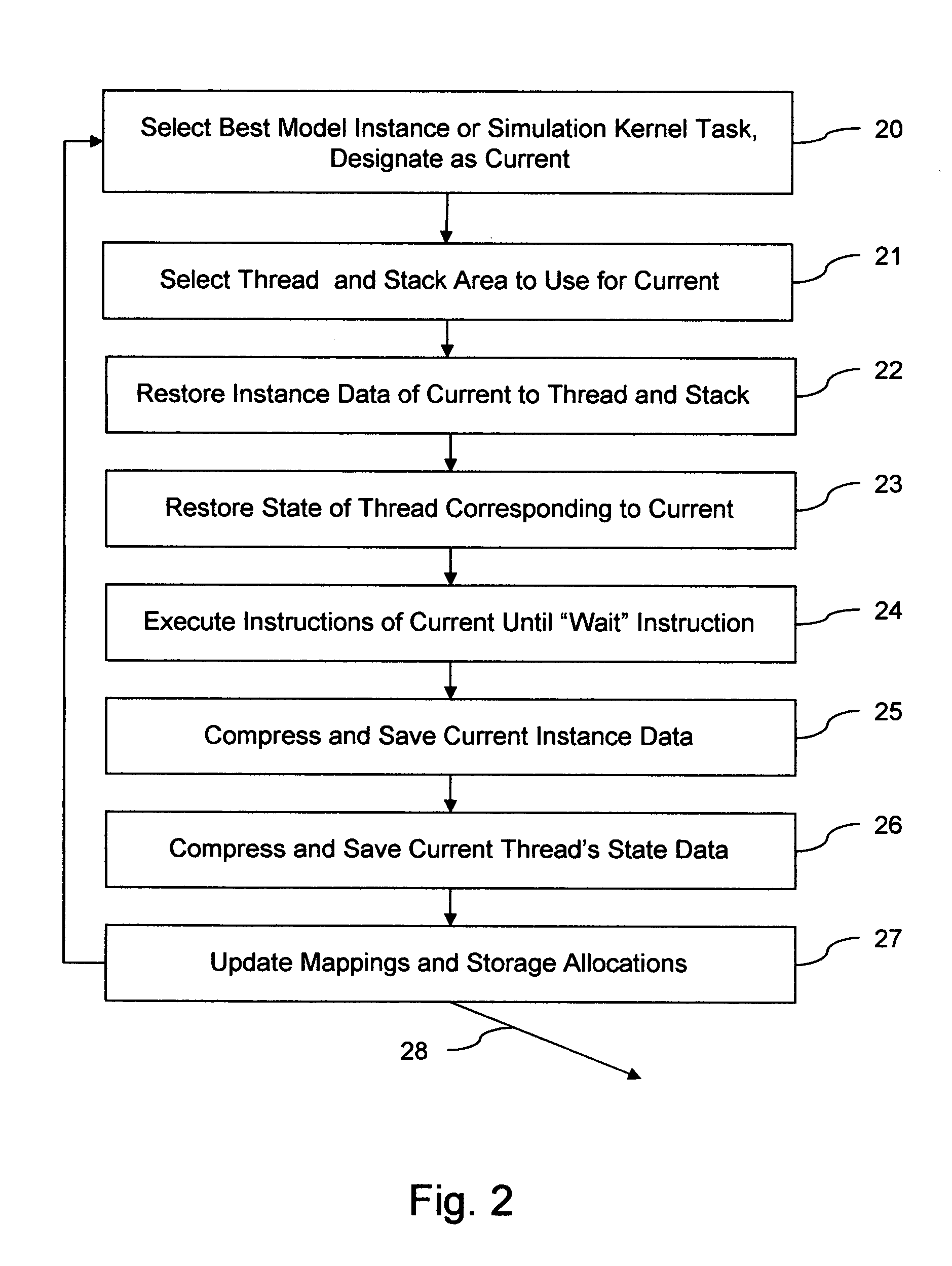
The invention provides run-time support for efficient simulation of digital hardware in a software development enviromnent, facilitating combined hardware / software co-simulation. The run-time support includes threads of execution that minimize stack storage requirements and reduce memory-related run-time processing requirements. The invention implements shared processor stack areas, including the sharing of a stack storage area among multiple threads, storing each thread's stack data in a designated area in compressed form while the thread is suspended. The thread's stack data is uncompressed and copied back onto a processor stack area when the thread is reactivated. A mapping of simulation model instances to stack storage is determined so as to minimize a cost function of memory and CPU run-time, to reduce the risk of stack overflow, and to reduce the impact of blocking system calls on simulation model execution. The invention also employs further memory compaction and a method for reducing CPU branch mis-prediction.
Owner:LISANKE ROBERT JOHN
Method and apparatus for preventing stack overflow in embedded system
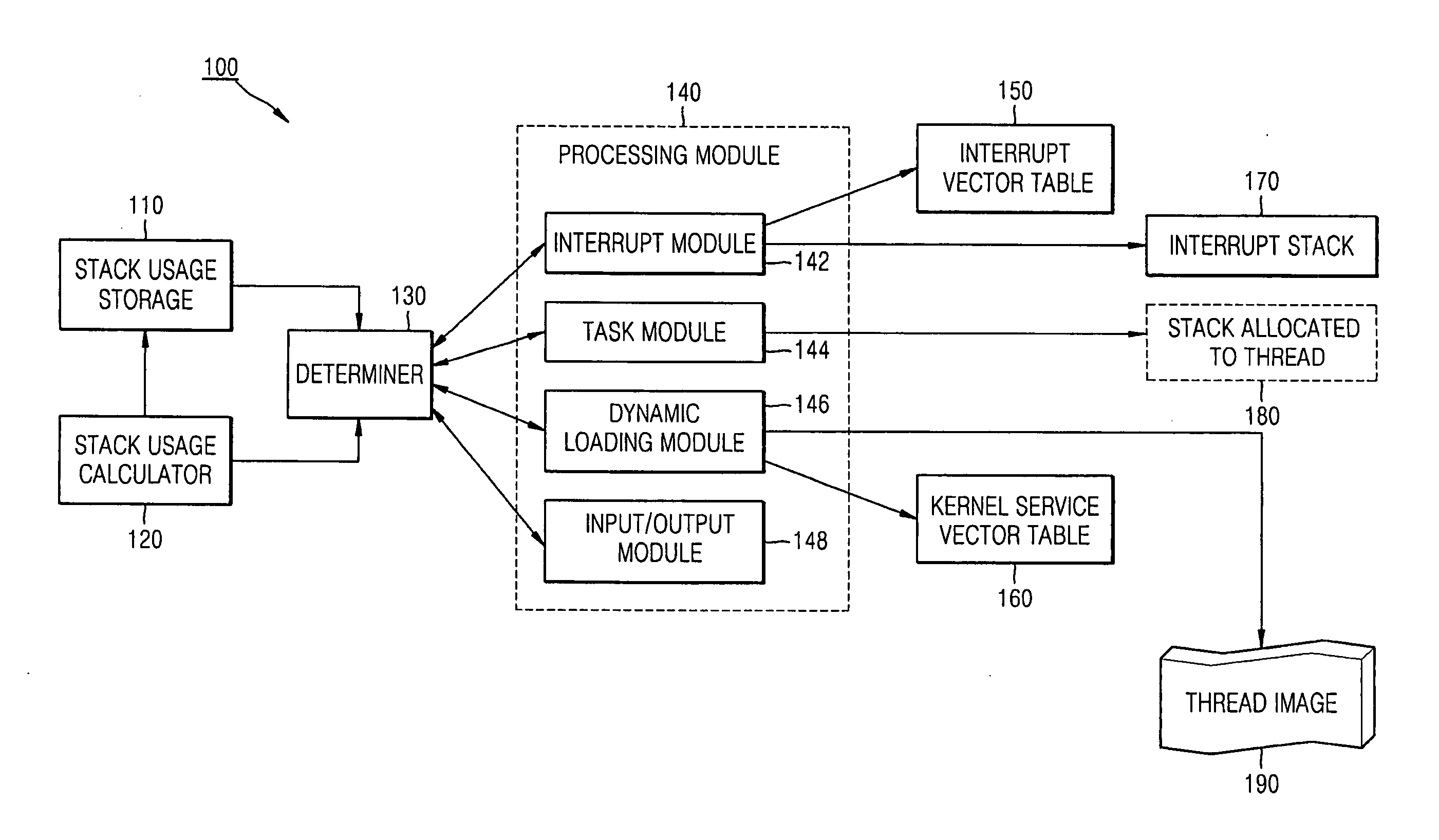
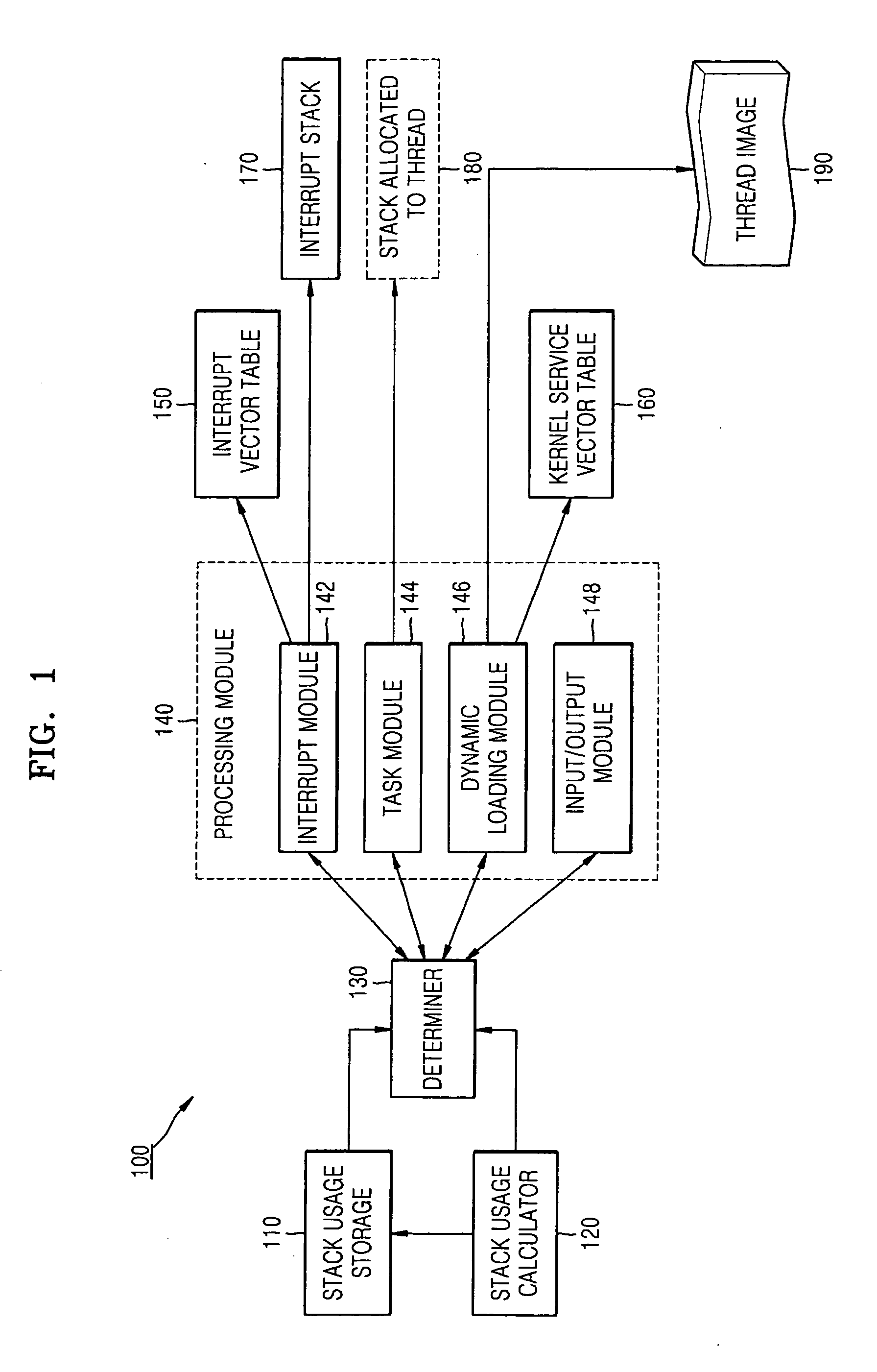
ActiveUS20080168460A1Preventing a stack overflowEnergy efficient ICTProgram control using stored programsRunning timeStack overflow
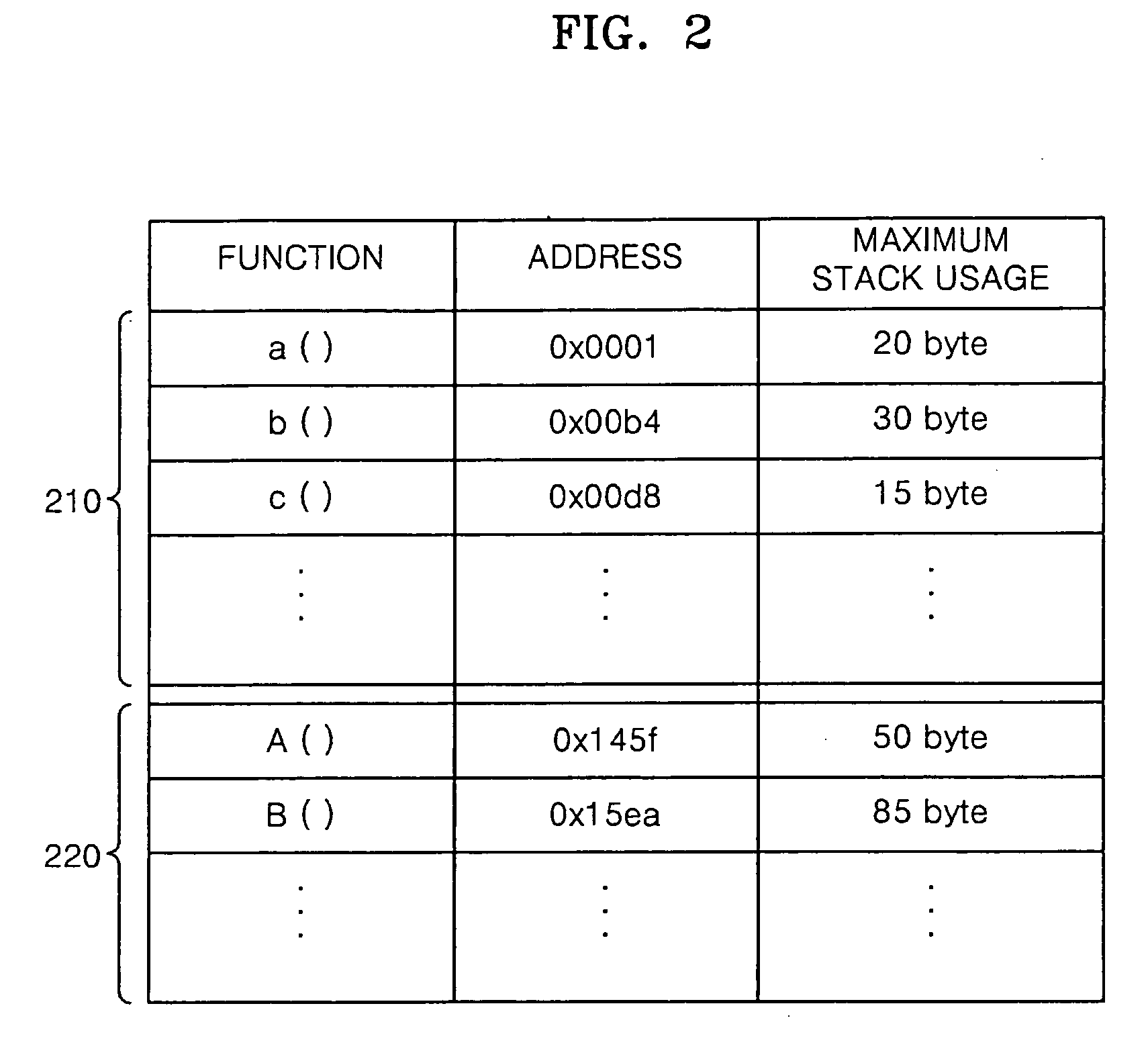
Provided is a method and apparatus for preventing a stack overflow in an embedded system. The method of preventing a stack overflow includes: reading a maximum stack usage of at least one function for executing a requested operation from maximum stack usages of functions provided from a kernel, which are stored in advance; and processing the requested operation on the basis of the read maximum stack usage of the at least one function and a size of a usable region in a stack for the requested operation. Accordingly, the stack overflow can be prevented without generating a run-time overhead.
Owner:SAMSUNG ELECTRONICS CO LTD
Method for monitoring task stack overflow
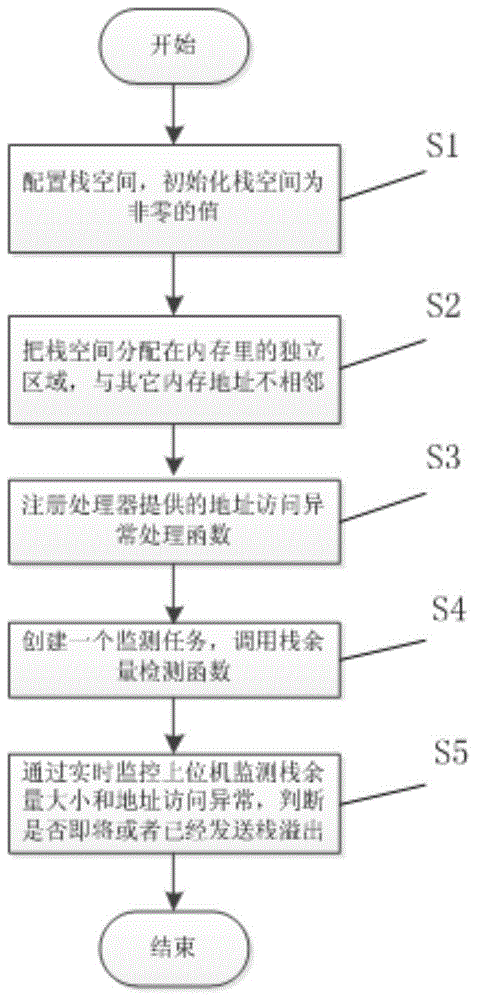
ActiveCN101154180AHelpful for analysisHelp with positioningHardware monitoringMultiprogramming arrangementsOperational systemStack overflow
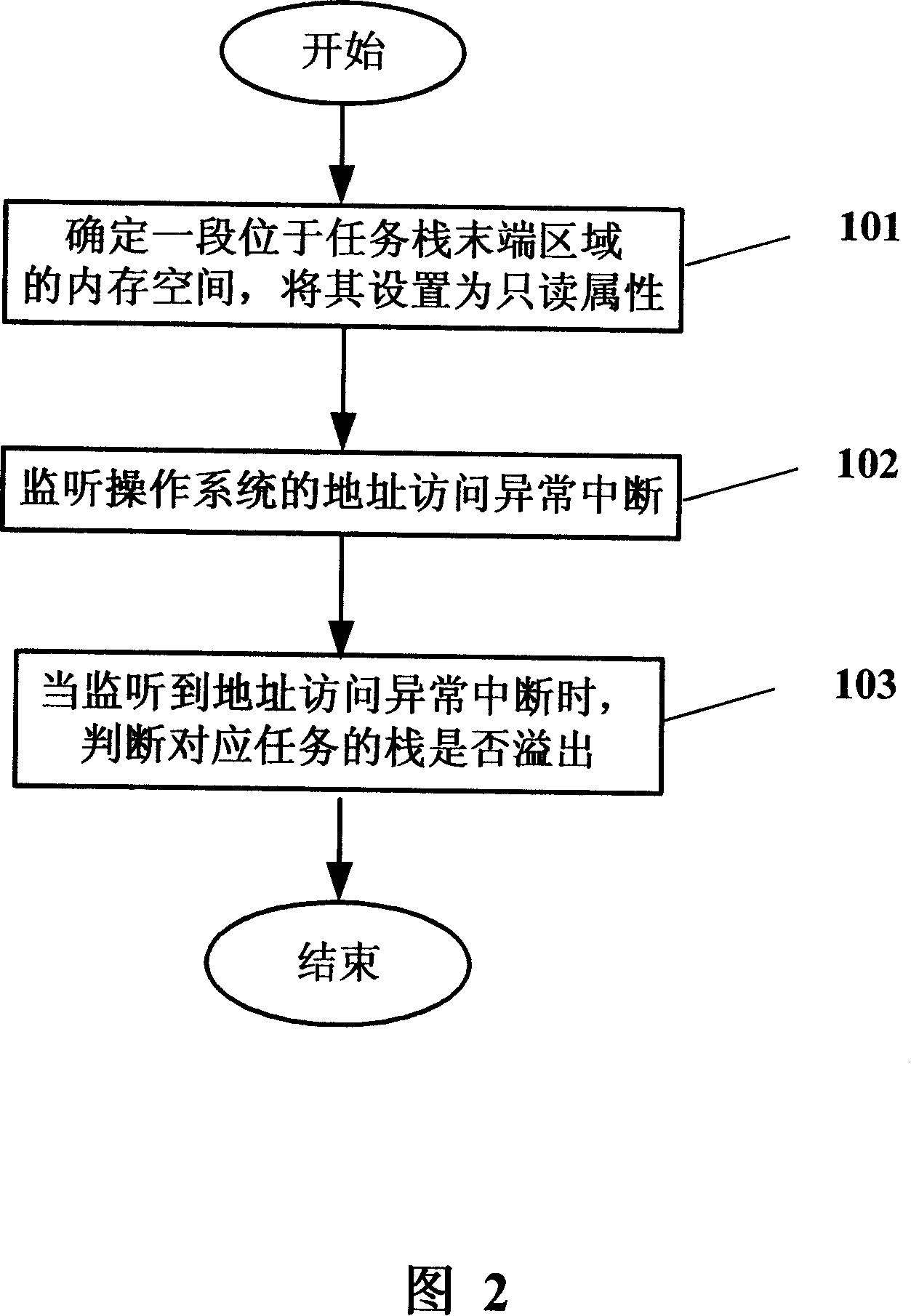
The invention discloses a method of monitoring the overflow of a task stack, comprising the steps as follows: a memory space positioned in the area of the tail end of the task stack is conformed and is set to have a read only attribute; the abnormal interrupt of address access of an operating system is monitored; when the abnormal interrupt of address access of the operating system is monitored, whether the task of the abnormal interrupt of address access stack overflows is judged. The method can monitor the overflow of the task stack real-time and avoid causing damage to other tasks because of the overflow of the task stack.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Tasks stack overflow real-time detection method and apparatus
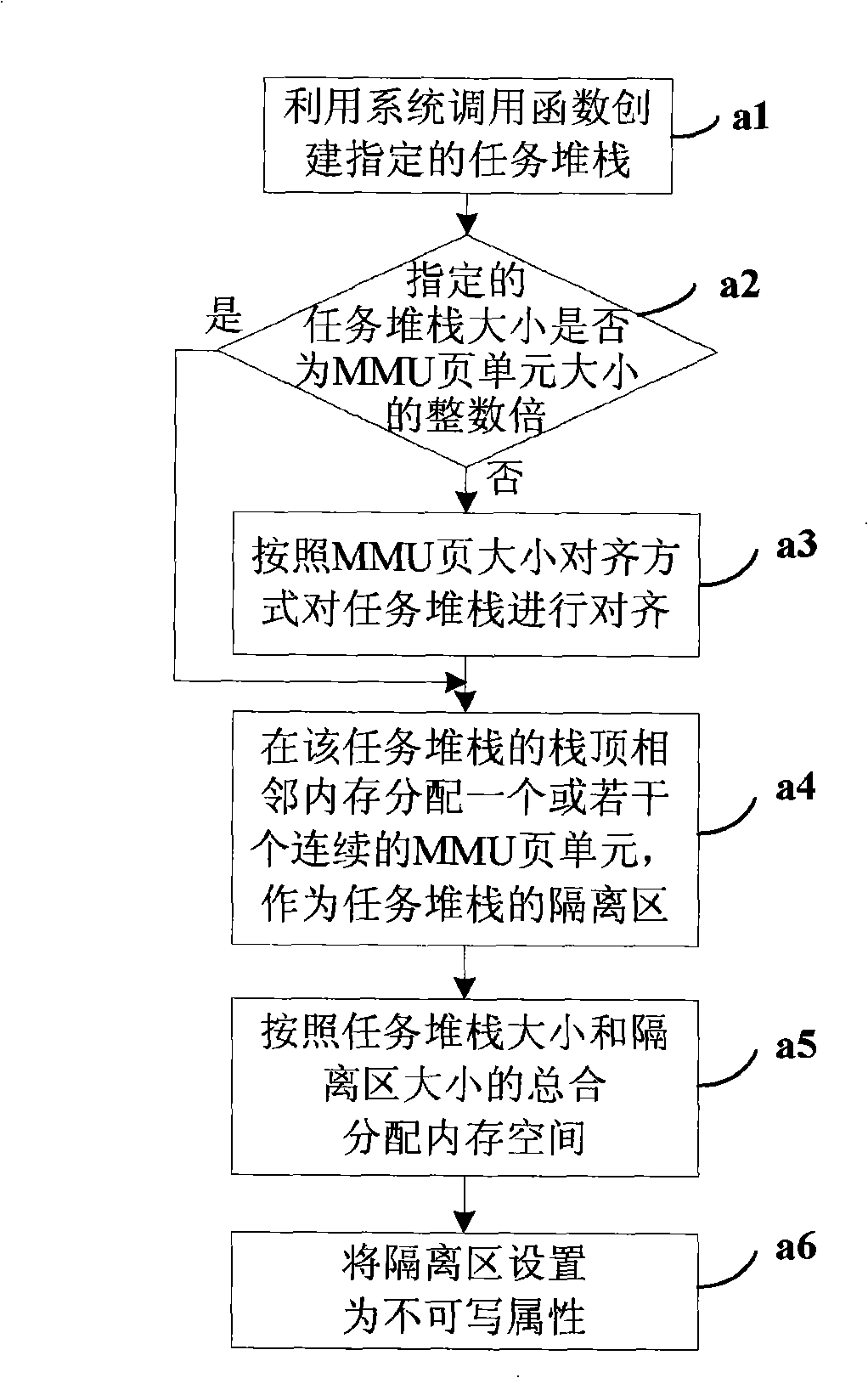
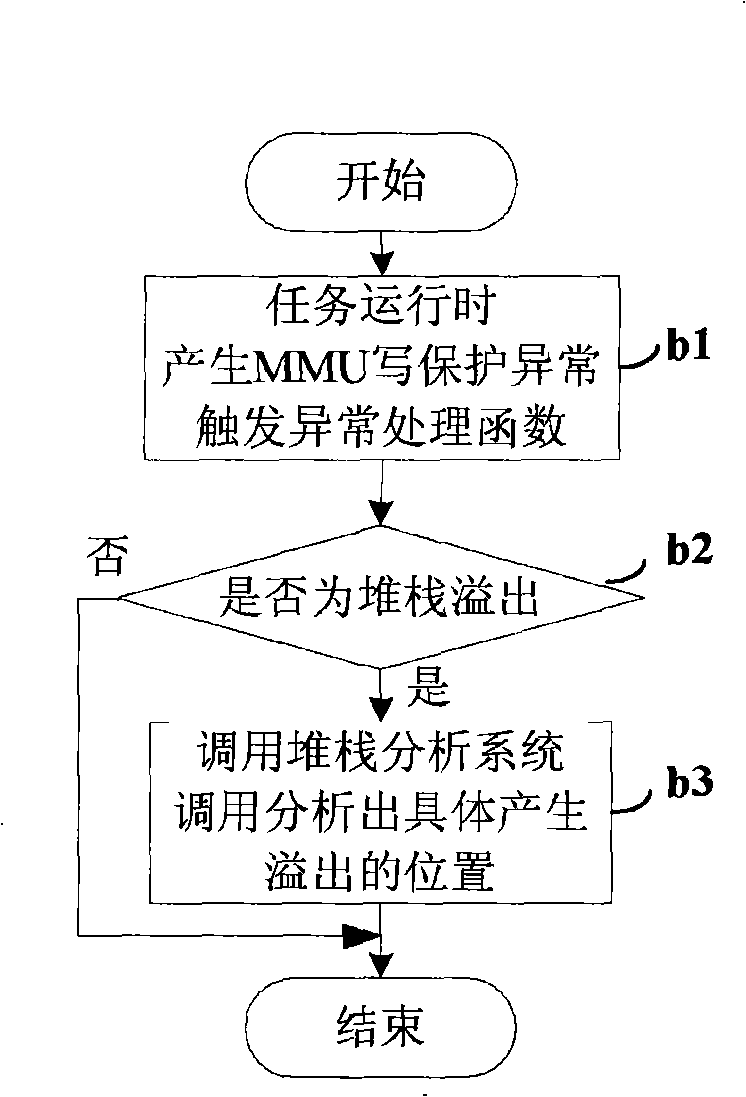
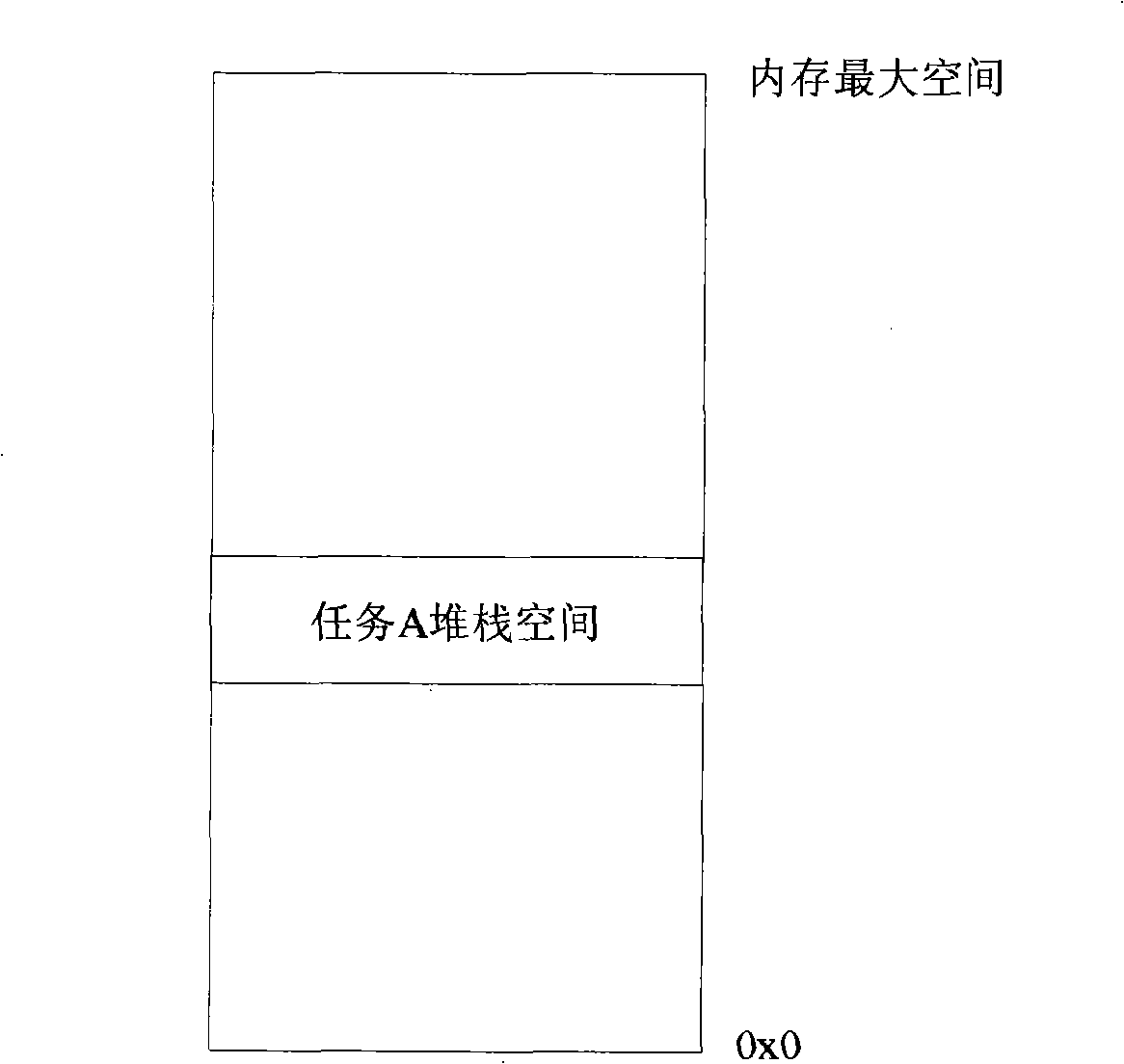
The invention discloses a method and a device for the real-time detection of task stack overflow, relating to the computer operating system field. The method comprises the following steps that: when task stack is allocated, memories in the part adjacent to the top of task stack are set to be an isolation region, and the attribute of the isolation region is set to be non-writable; in the process of pressing the task stack, if stack pressing operation carries out write operation to the isolation region, the task stack is judged to be overflowing. The invention also discloses a device for the real-time detection of task stack overflow. A technical proposal of the invention positions tasks generating stack overflow, and can position concrete positions causing stack overflow by analyzing the stack of the tasks.
Owner:ZTE CORP
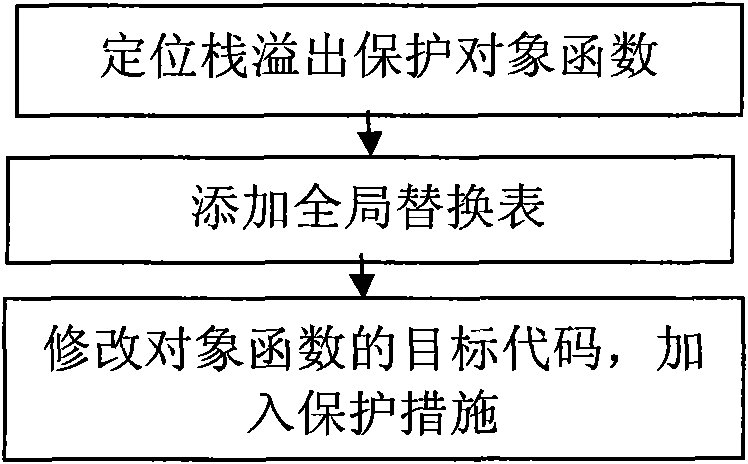
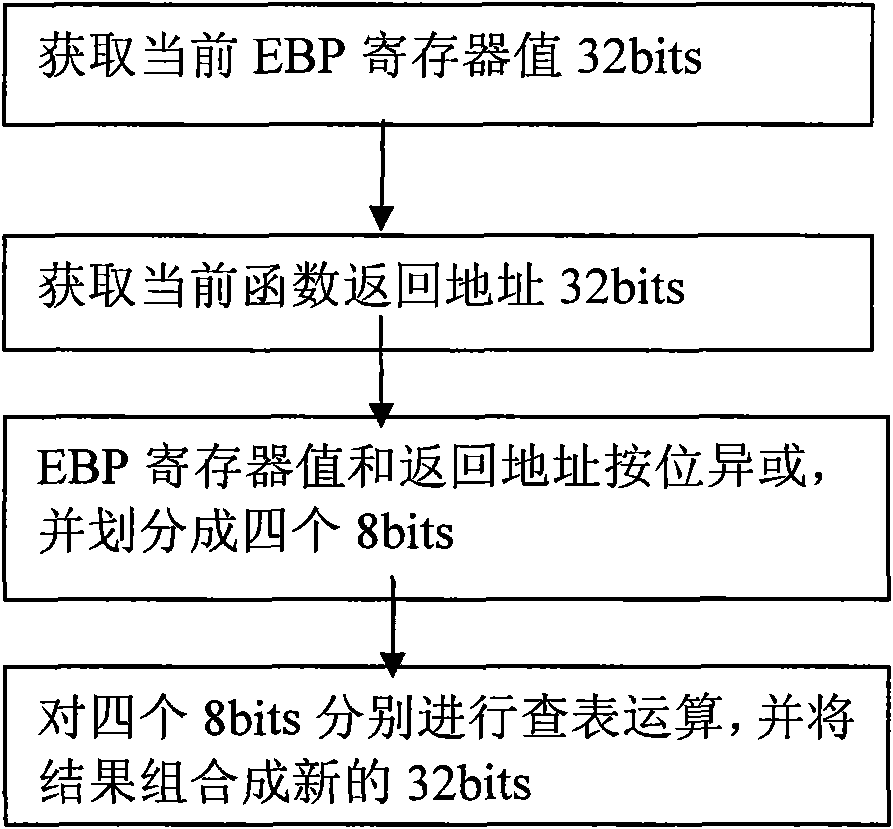
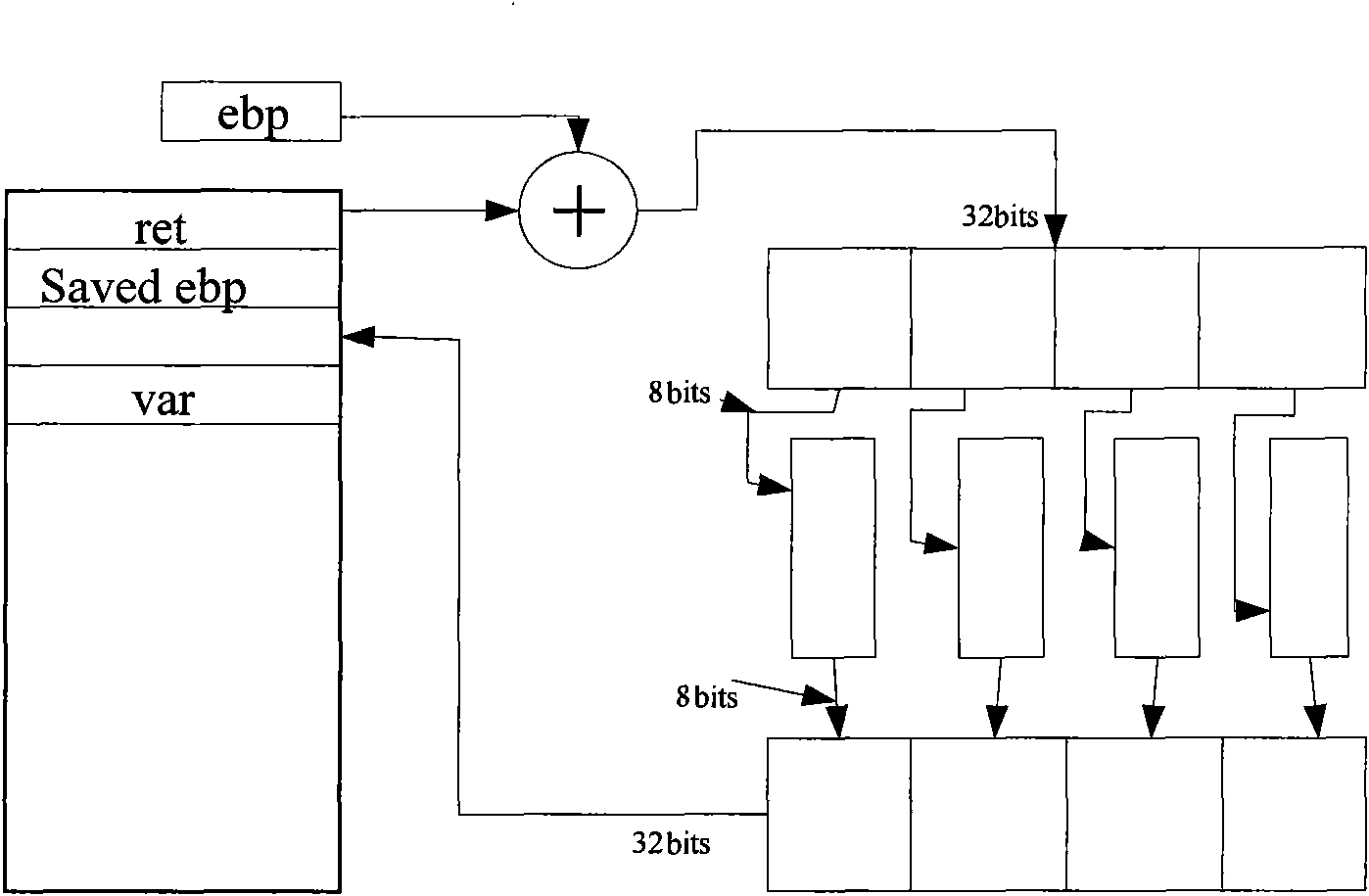
Stack overflow attack defense method
The invention discloses a stack overflow attack defense method, which belongs to the field of security guarantee of a computer system. The method comprises the following steps of: a) positioning a function with potential stack overflow defect in a program; b) before the function is executed, encrypting a return address to obtain first encrypted message by using a key register and storing the encrypted message; and c) before the function is returned, encrypting the return address to obtain second encrypted message by using the key register likewise, and if the first encrypted message and the second encrypted message are different, showing that the stack overflow attack exists. The method can be used for stack overflow attack defense, and is applicable in multiple fields of aerospace, finance, manufacture, communication, energy, medicinal treatment, education and the like.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
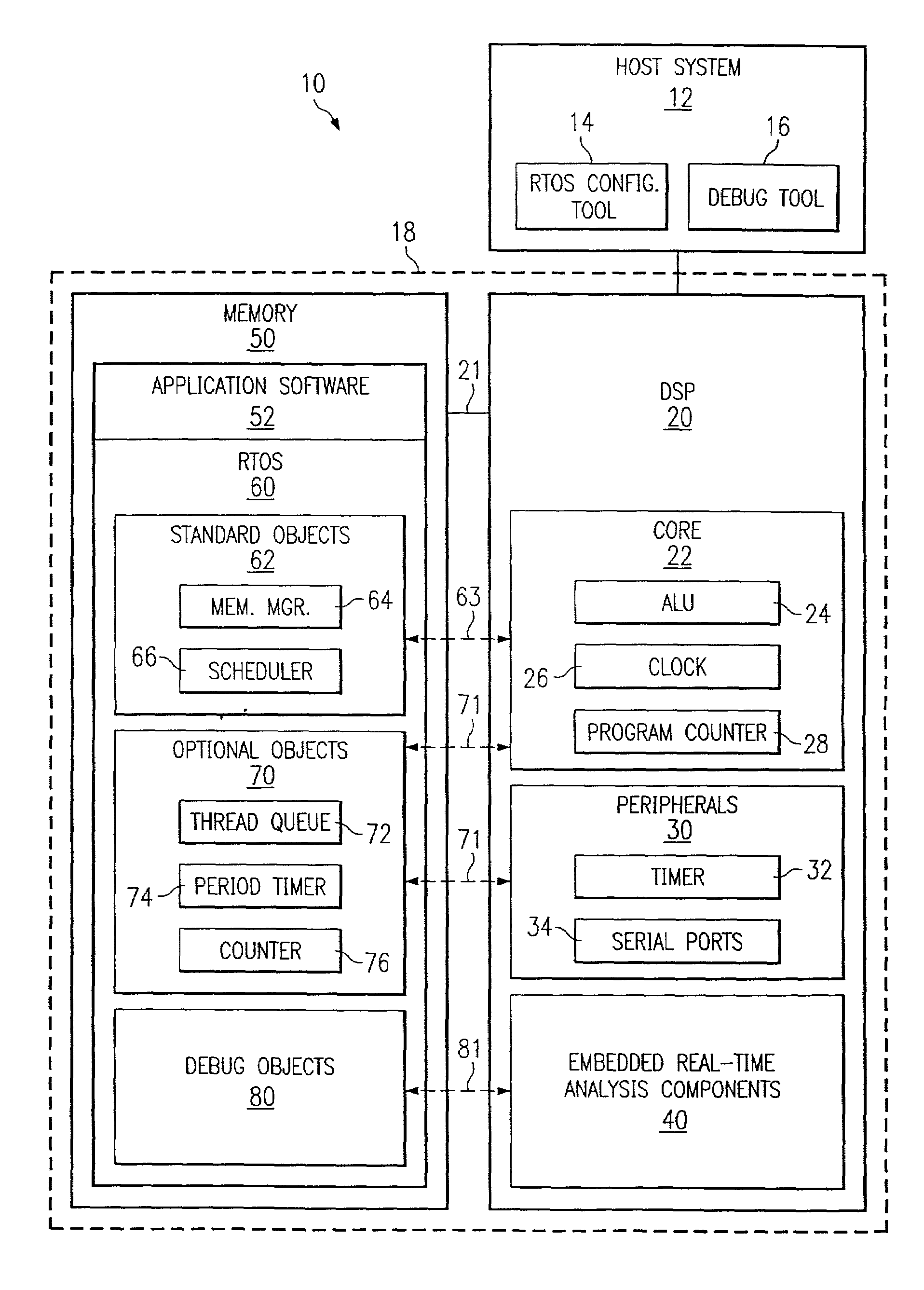
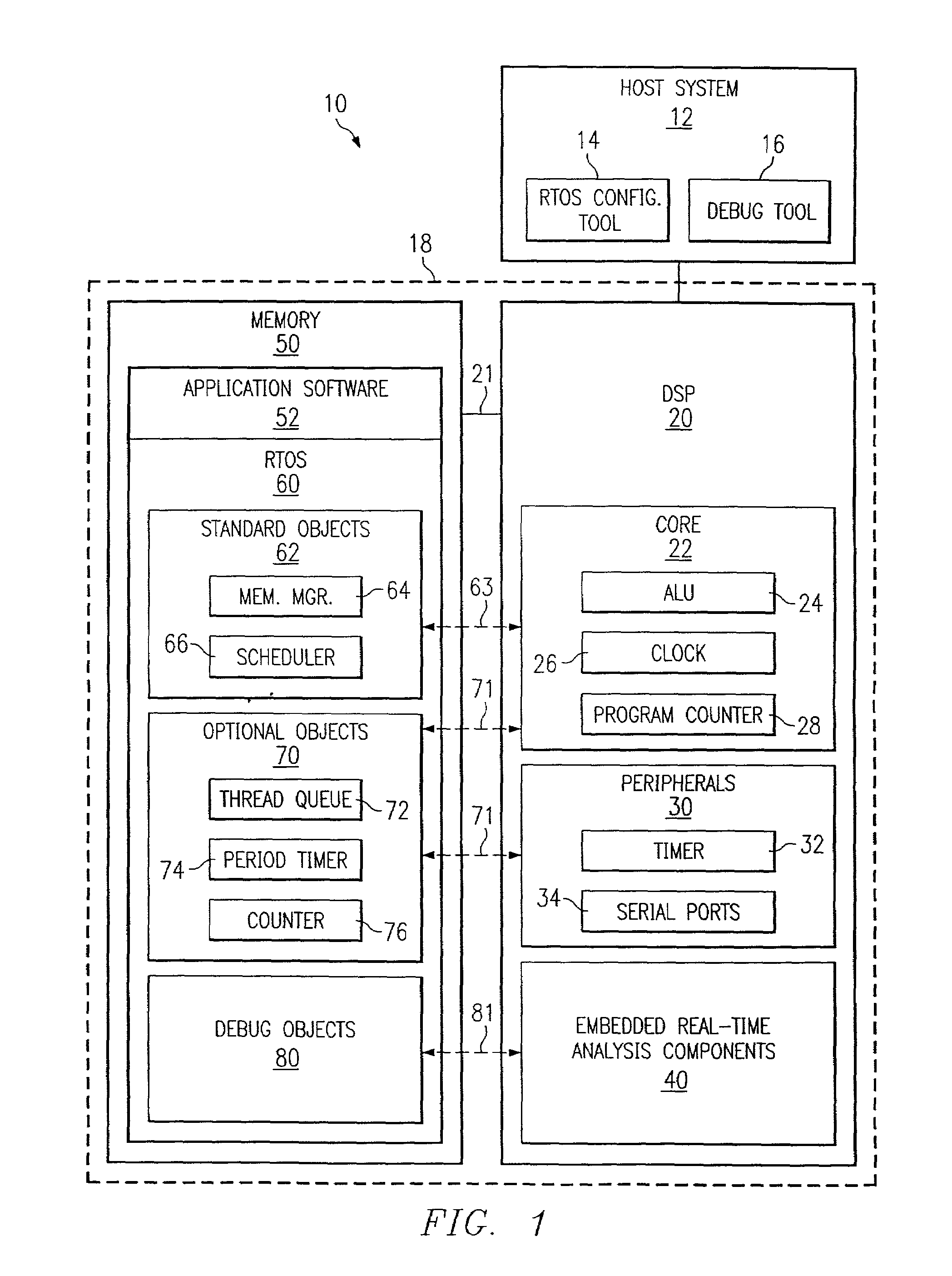
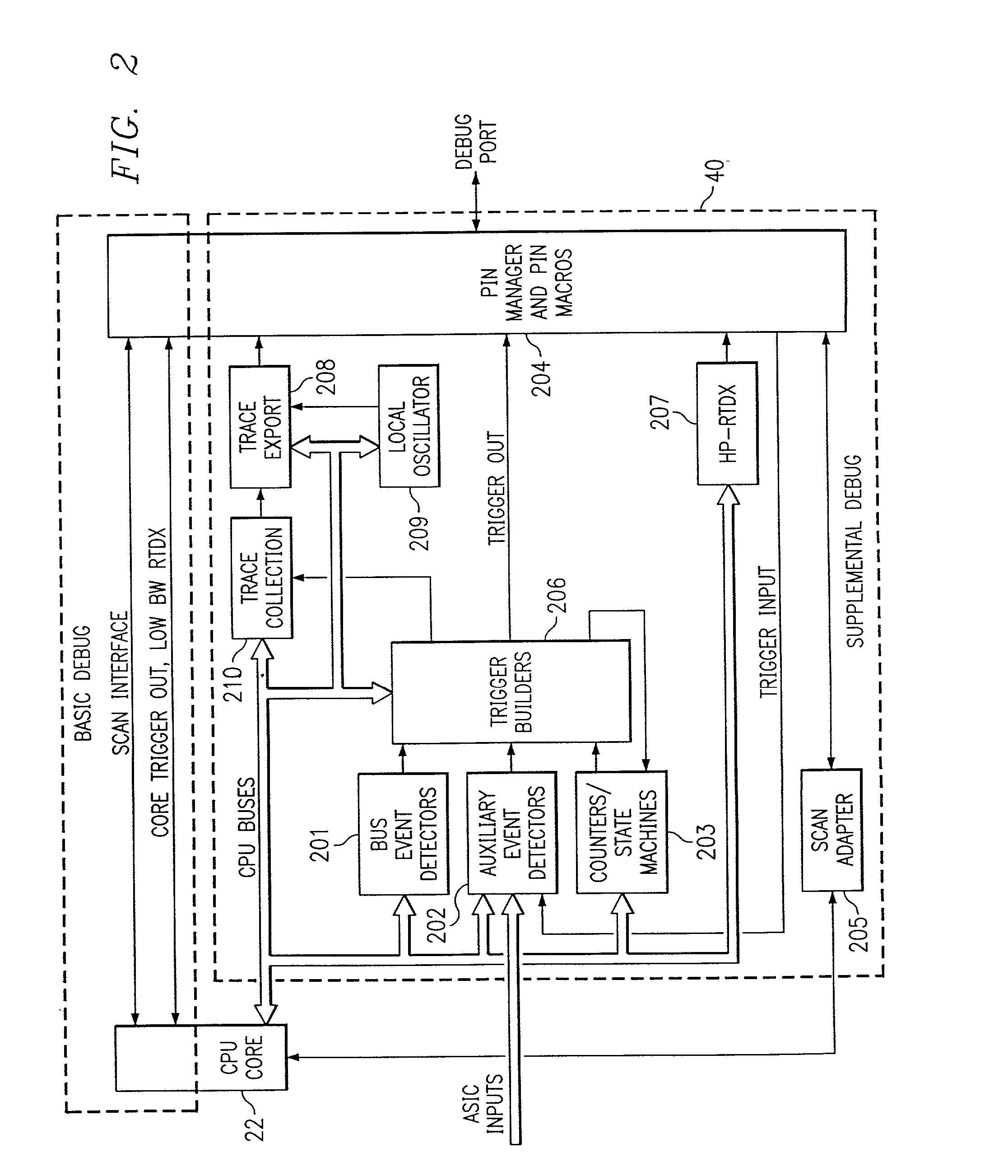
Method using embedded real-time analysis components with corresponding real-time operating system software objects
ActiveUS7191445B2High level of serviceMore processedMultiprogramming arrangementsSoftware testing/debuggingReal time analysisOperational system
An operating system (OS) is used in a system with a processor that includes embedded real-time analysis components. The OS includes software objects which provide functionality in response to signals from the embedded real-time analysis components. In an example embodiment, the OS is a real-time OS (RTOS), the embedded real-time analysis components include an embedded event trigger component, and the software objects include a debug object that responds to signals from the embedded event trigger component. For instance, those signals may relate to program flow, data flow, or a hardware operation such as a cache miss, and the debug object may be a breakpoint handler, a trace handler, or an event sequence handler. In the example embodiment, the software objects in the RTOS provide functionality such as stack overflow detection, real-time task priority modification, and / or system scheduling error assertion for a real-time application. Alternative embodiments involve related methods and systems.
Owner:TEXAS INSTR INC
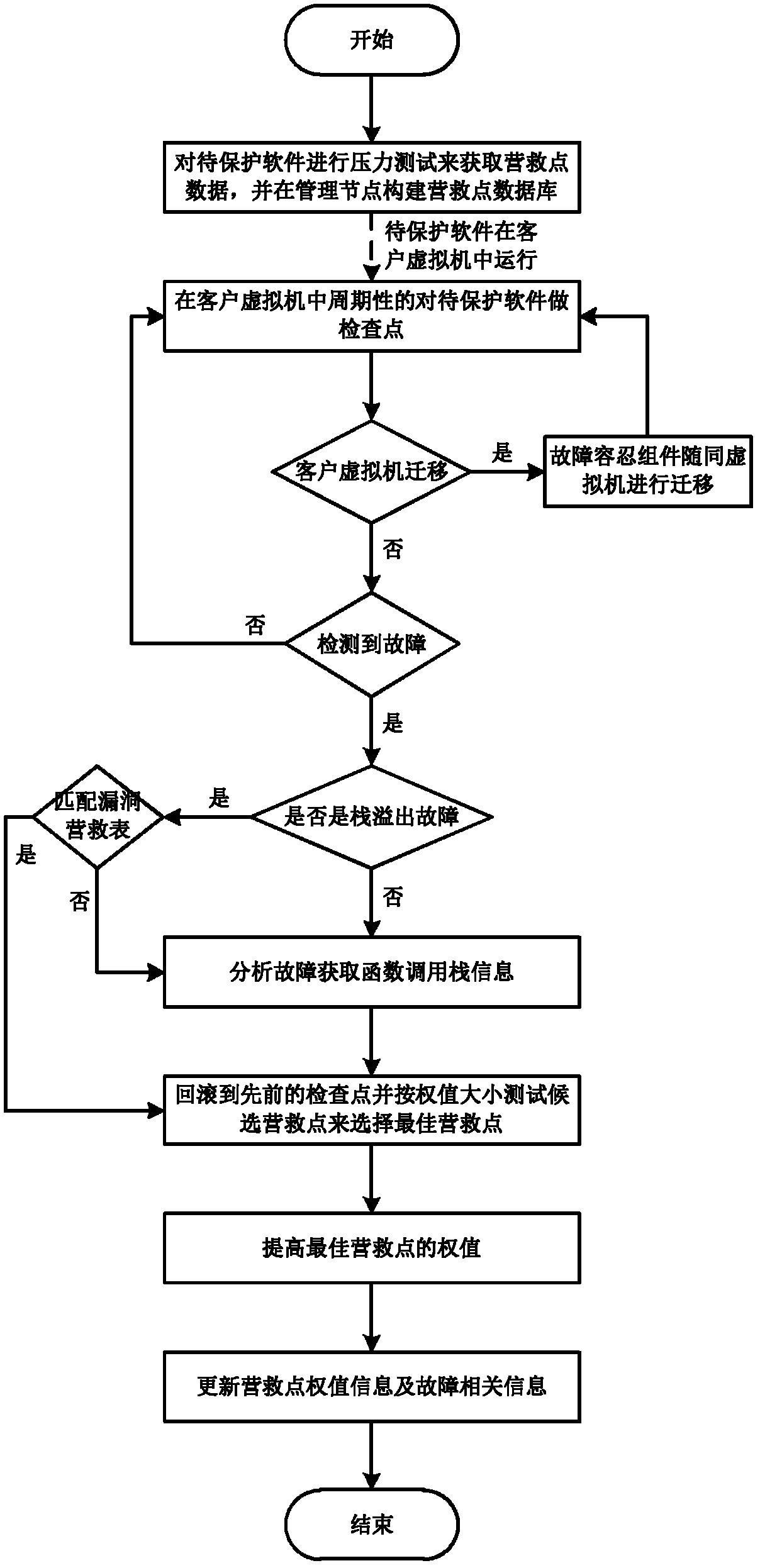
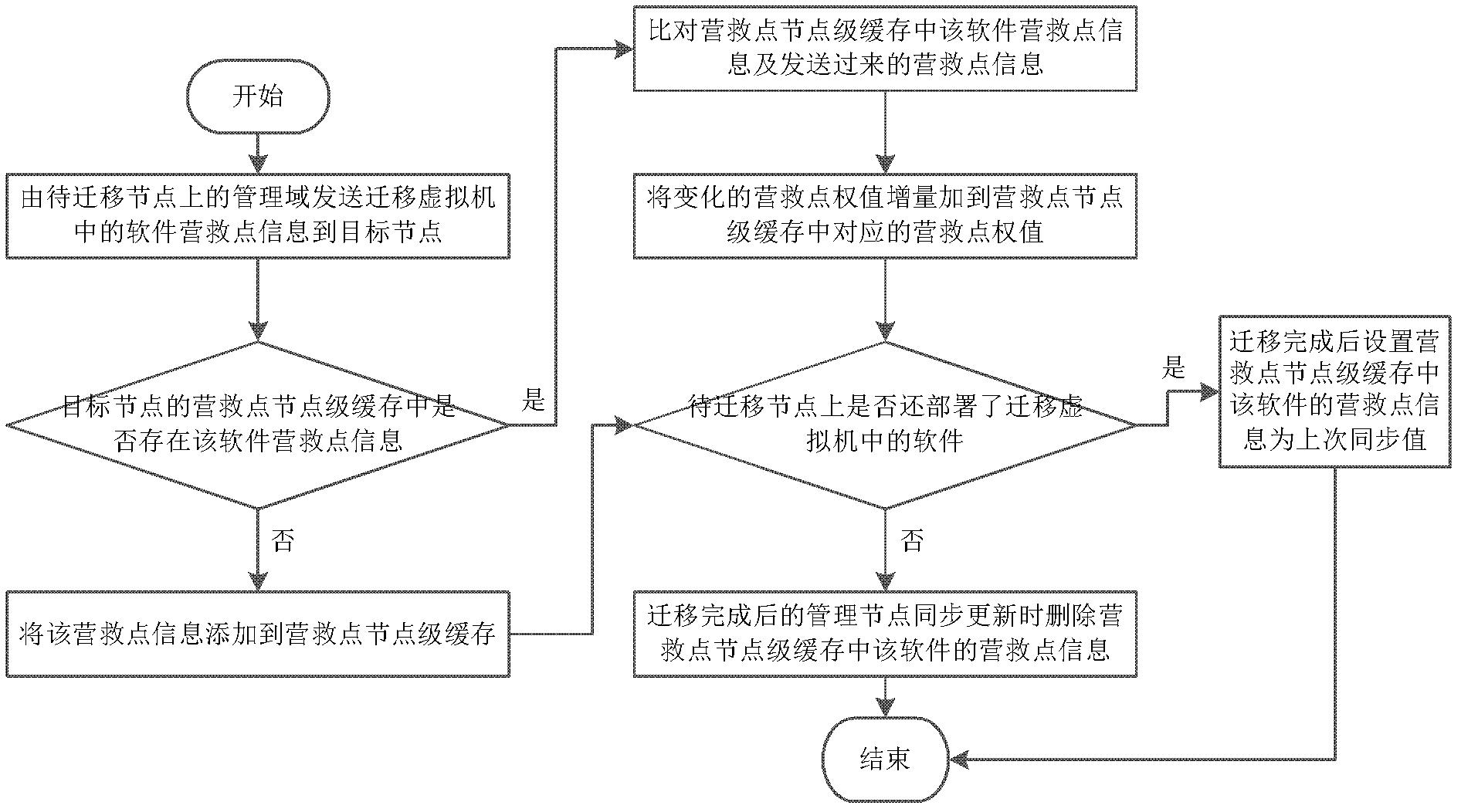
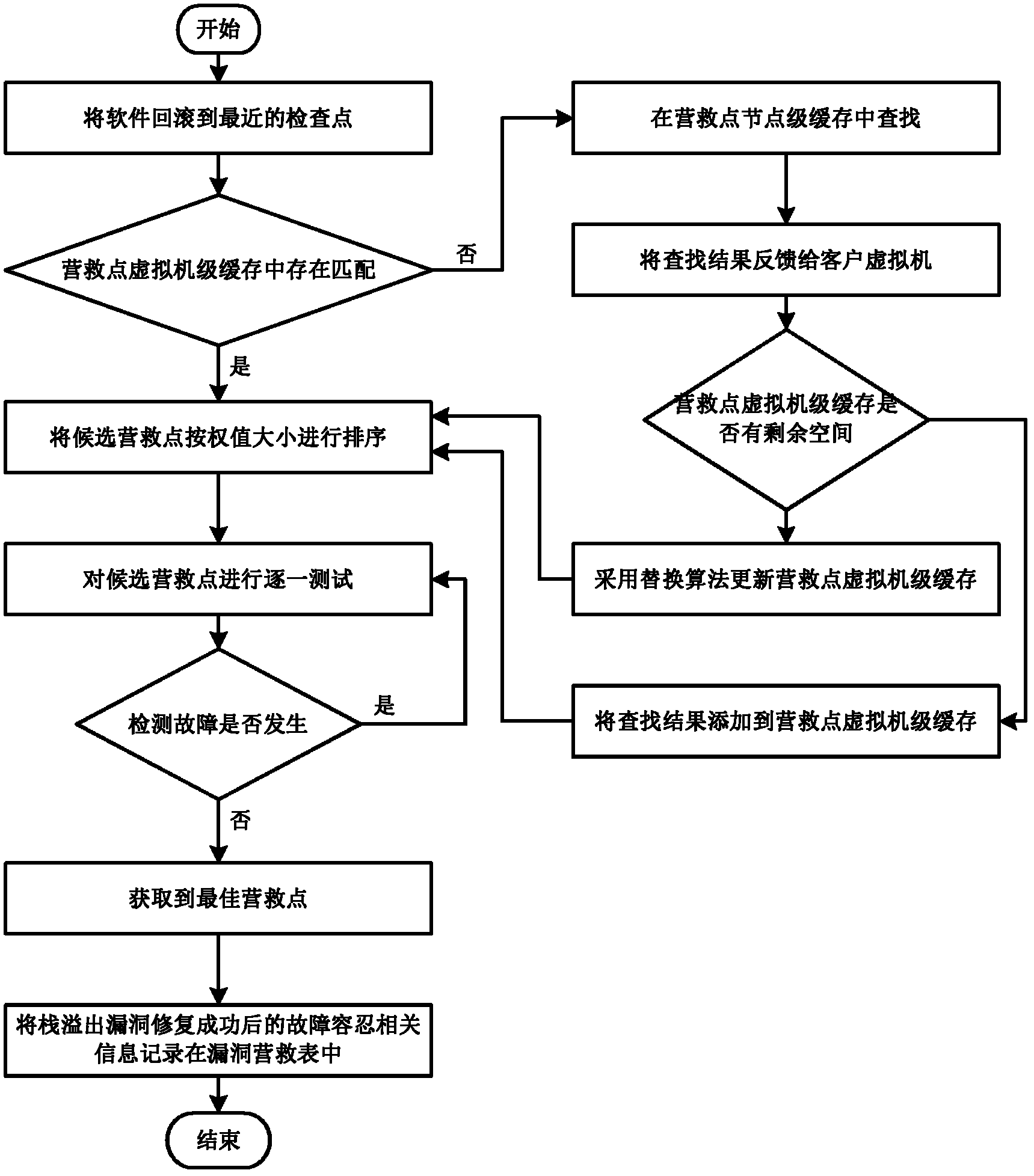
Software fault tolerance method facing cloud platform
The invention discloses a software fault tolerance method facing cloud platform. The method comprises the following steps: testing stress of software to be protected to obtain rescue point of the software; periodically constructing software check points in a virtual machine to determine whether a fault exists in the software; acquiring software fault related information if the fault exists; judging whether the fault is stack overflow fault according to the software fault related information; judging whether function call stack information matching the fault exists in a loophole rescue table if the fault is stack overflow fault; extracting the function stack information if the function call stack information matching the fault exists in a loophole rescue table; rolling the software back to a check point closest to the fault; acquiring candidate rescue points according to the function call stack information; and testing the candidate rescue points according to weight of the candidate rescue points to obtain the optimum rescue point with fault tolerance. The soft fault tolerance method provided by the invention can effectively improve the fault tolerant capability of software, and can lower data redundancy caused by the fault tolerance mechanism.
Owner:HUAZHONG UNIV OF SCI & TECH
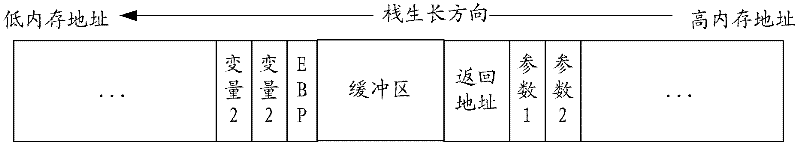
A stack overflow protection method and device
InactiveCN102298677AImprove protectionEasy to getPlatform integrity maintainanceRandom stringStack overflow
The invention provides a stack overflow protection method, by inserting a buffer into the stack, and filling the buffer with filling characters in the format of "fixed character string + random character string" or "random character string+fixed character string" String, and check the filling value in the buffer when the stack is released, which solves the problem of poor defense against stack overflow vulnerabilities, thereby reducing the risk of attackers using stack overflow vulnerabilities to damage the system. The invention also includes a stack overflow protection device.
Owner:RAISECOM TECH
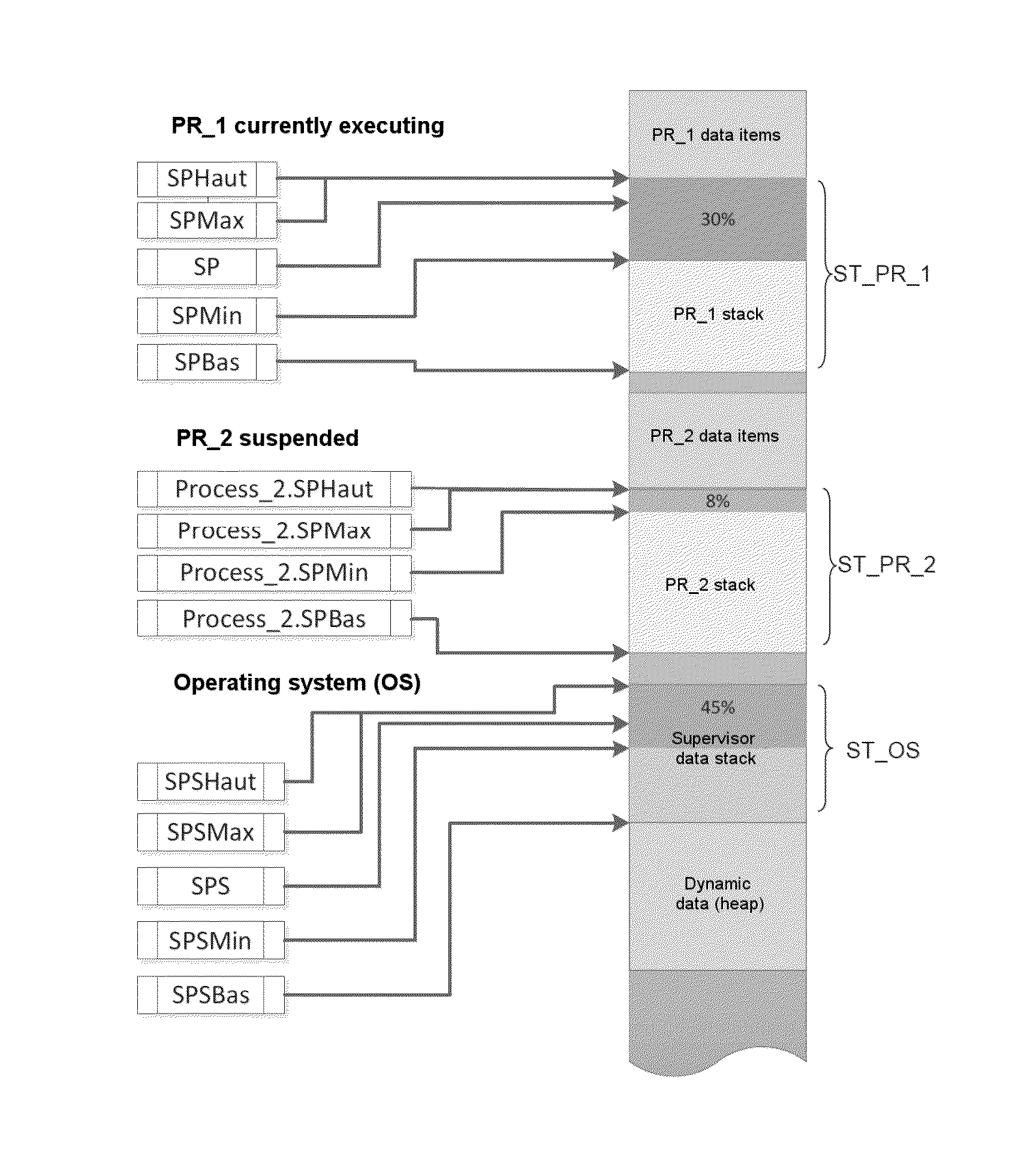
Method of detecting stack overflows and processor for implementing such a method
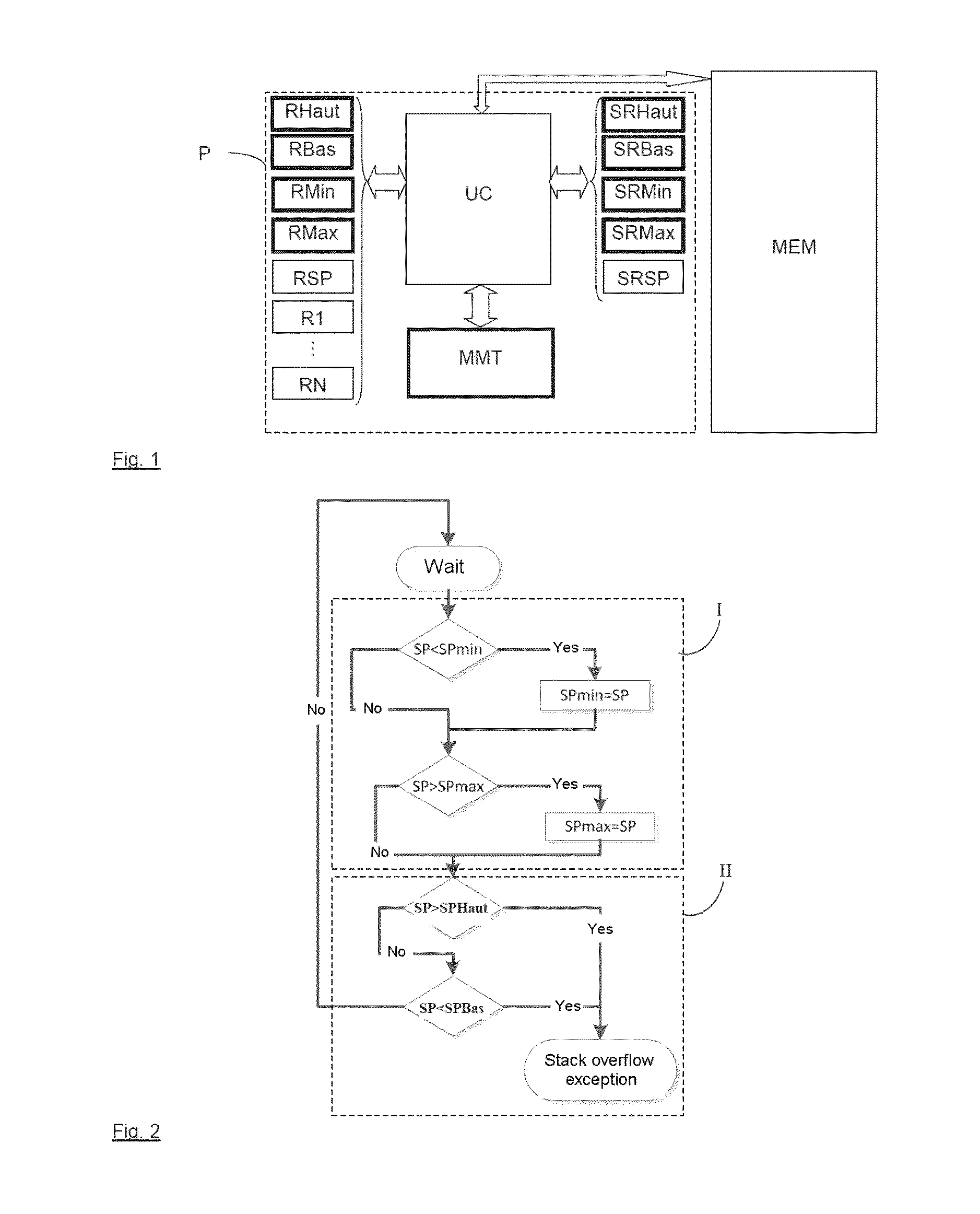
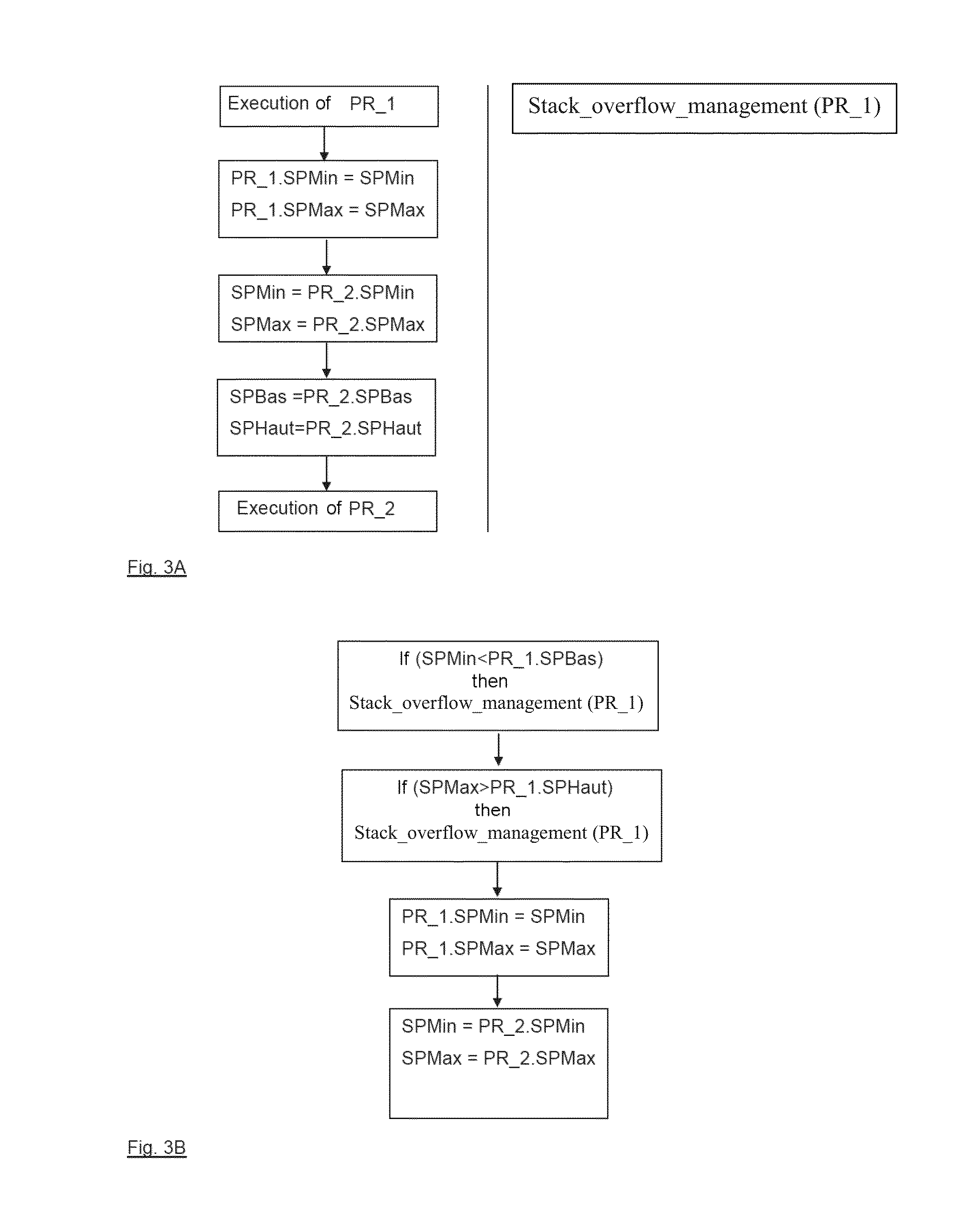
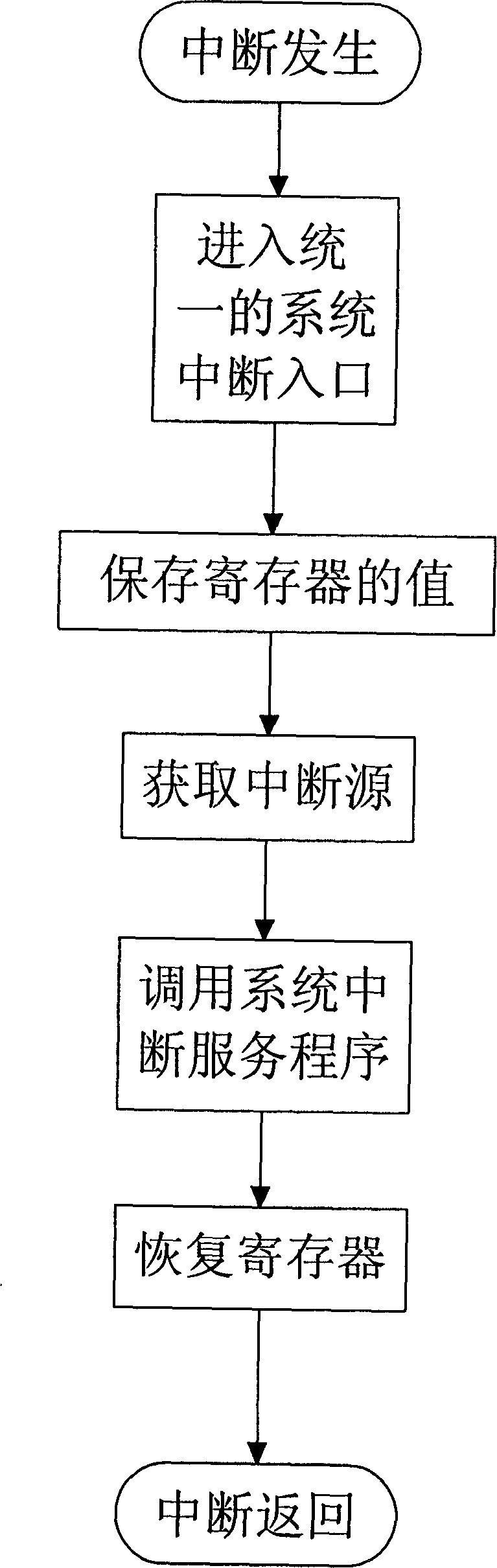
ActiveUS20150150024A1Easy to implementNot slowing execution of programProgram initiation/switchingDigital computer detailsComputer hardwareProcessor register
A method of detecting stack overflows includes the following steps: storing in at least one dedicated register at least one data item chosen from: a data item (SPHaut) indicating a maximum permitted value for a stack pointer, and a data item (SPBas) indicating a minimum permitted value for said stack pointer; effecting a comparison between a current value (SP) or past value (SPMin, SPMax) of said stack pointer and said data item or each of said data items; and generating a stack overflow exception if said comparison indicates that said current or past value of said stack pointer is greater than said maximum permitted value or less than said minimum permitted value. A processor for implementing such a method is also provided.
Owner:THALES SA
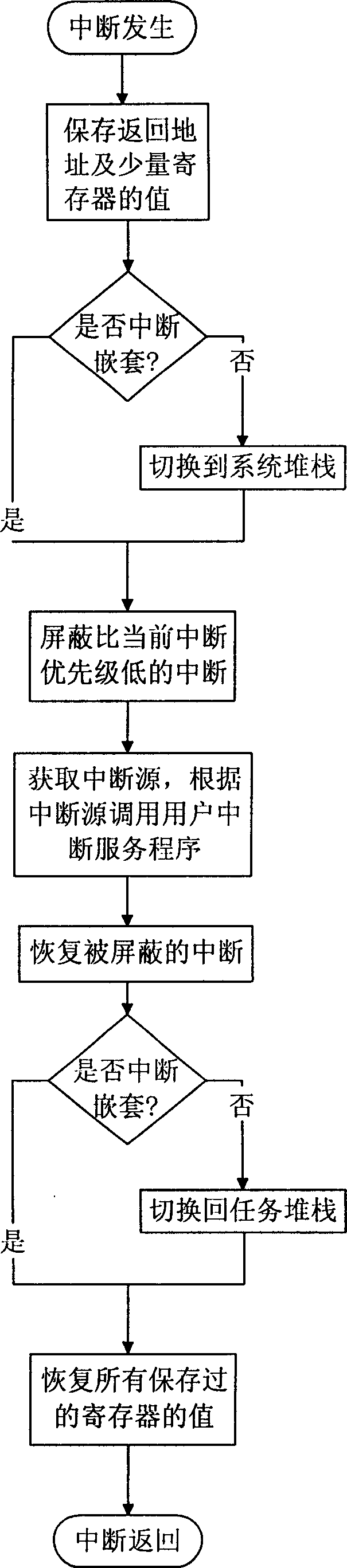
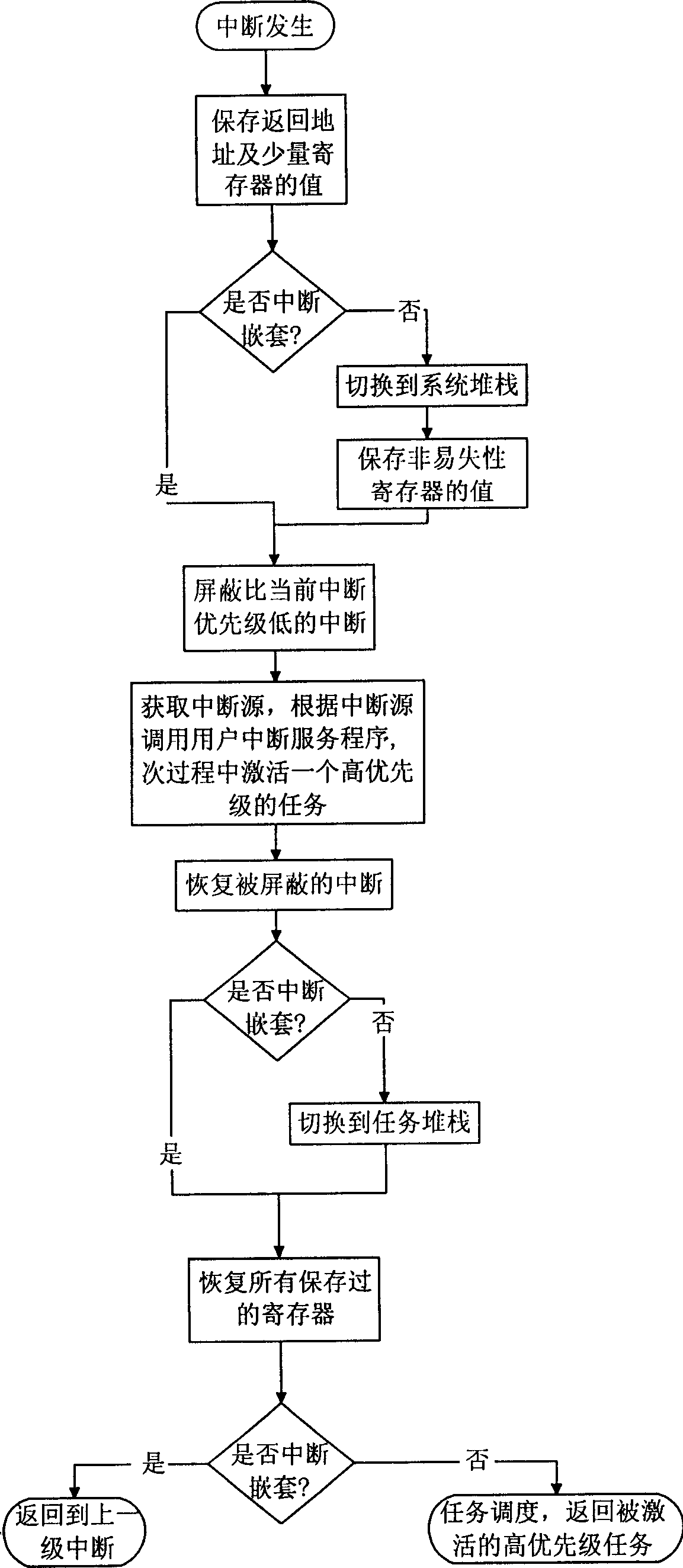
Interrupt managing method for embedded operation system based on PowerPC system structure
InactiveCN1783020APrevent executionImprove execution efficiencyProgram initiation/switchingOperational systemPowerPC
The interrupt management method for embedded operation system based on PowerPC system structure includes the following steps: dividing interrupts into two classes of system interrupt and user interrupt and dividing user interrupt service programs into class-I interrupt service program and class-II interrupt service program; first hardware responding the user interrupt; then, maintaining the context, stack switching and interrupt nesting for resuming the interrupted task after interrupt treatment; finding out and calling corresponding interrupt service program from the user interrupt vector list via the interrupt source; and maintaining the interrupt nesting and stack switching, restoring the context for the treater to resume the interrupted task. The present invention has the advantages of raised interrupt executing efficiency, raised interrupt utilizing efficiency, convenient interrupt control and use, raised user stack size controllability and predicting property.
Owner:ZHEJIANG UNIV
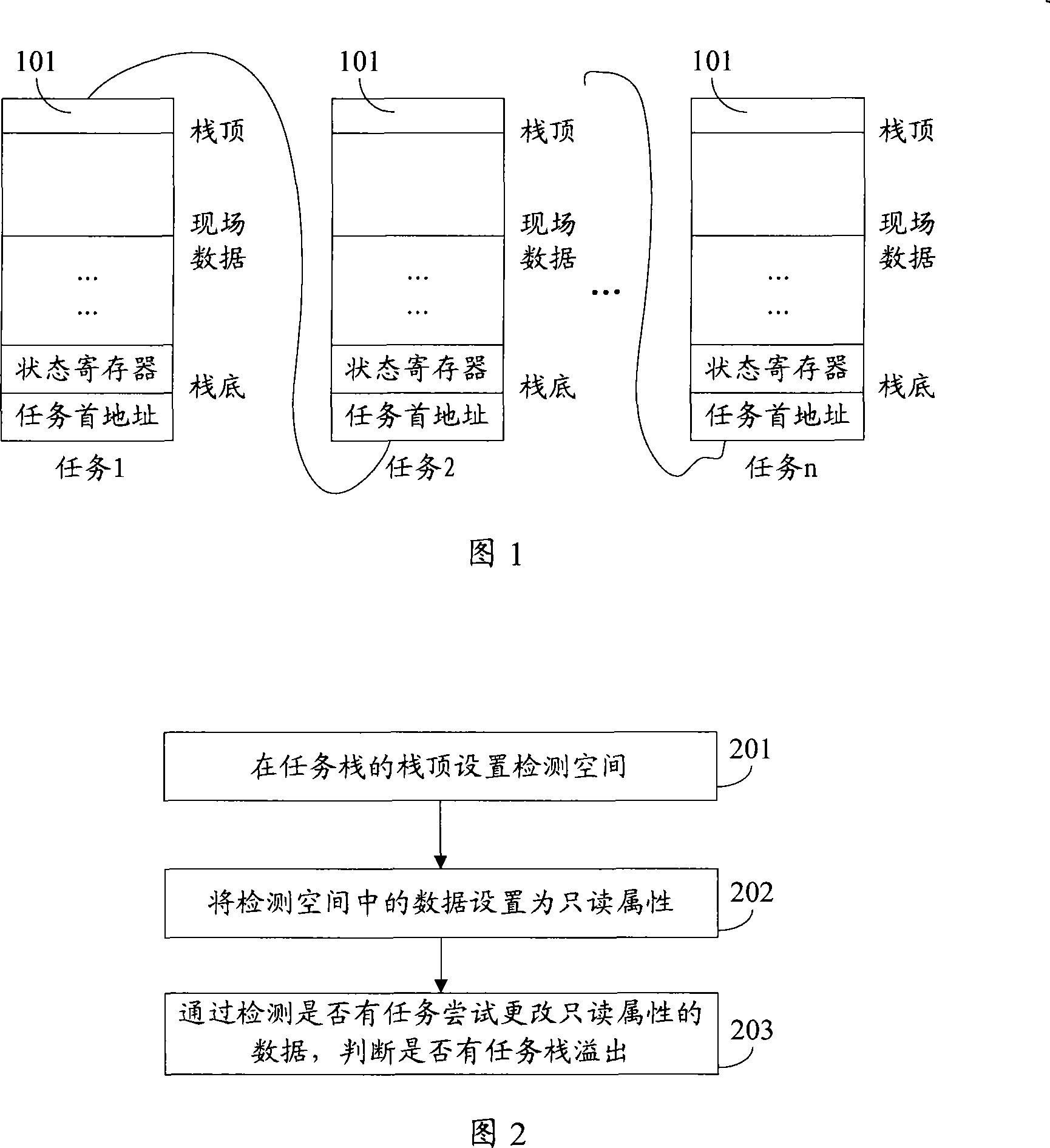
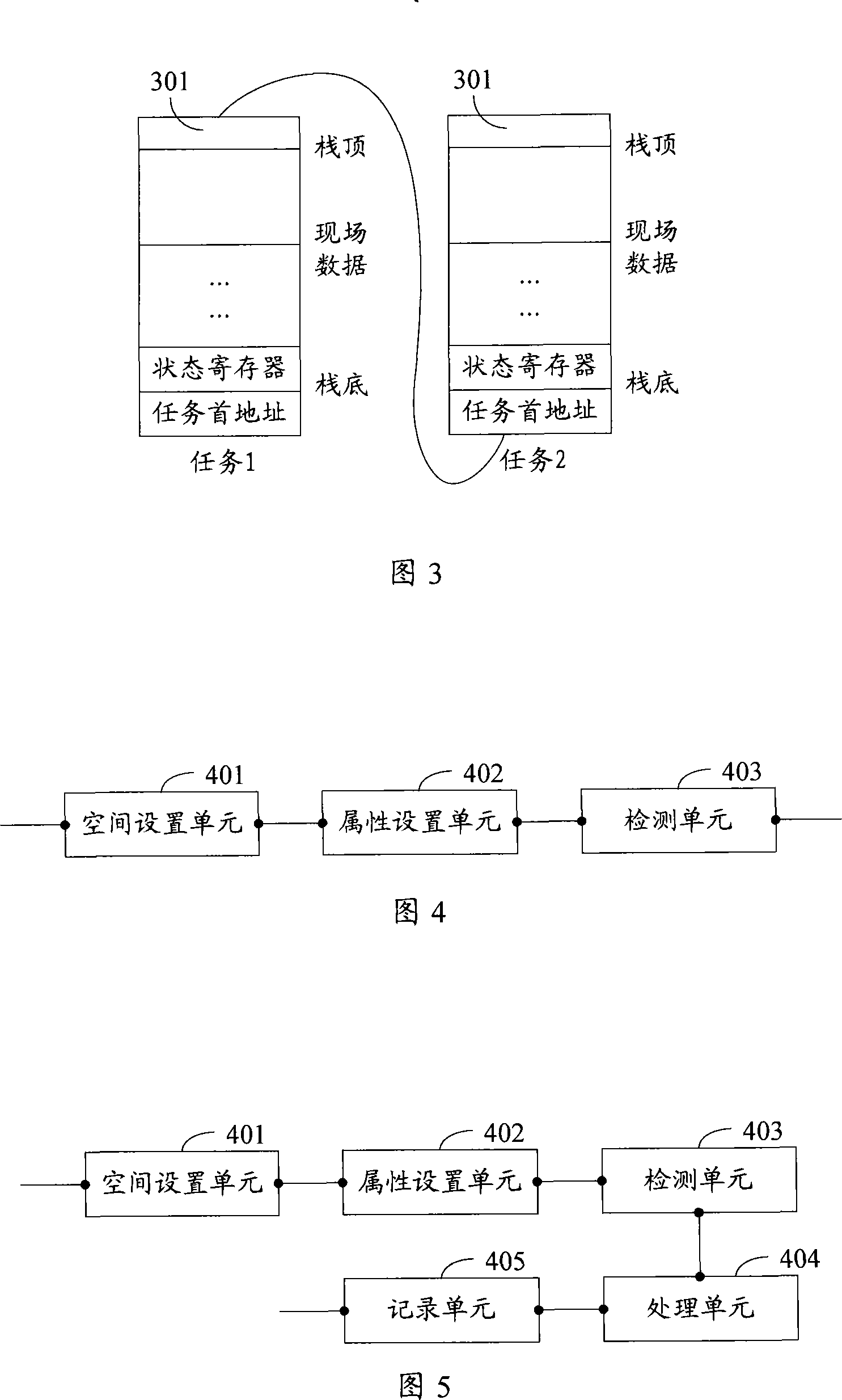
Tasks stack overflow detection method, device and computer system thereof
InactiveCN101183331ASave resourcesImprove stabilityMultiprogramming arrangementsSoftware testing/debuggingComputerized systemStack overflow
The invention discloses a stack overflow detection method, a device and a computer system for tasks stack overflow , belonging to a stack processing technology, which is characterized in that: the detection method for the stack overflow of the tasks comprises steps as follows: detection space is arranged at the top of the task stack; data in the detection space is provided with read-only attribute; by detecting whether task exists and tries to modify the data with read-only attribute, the task stack overflows are judged. Adopting the technical proposal, the invention has the advantages of no need for extra timing detection or timing interruption for detection stack overflow of the tasks, and saving limited system resources.
Owner:SHANGHAI HUAWEI TECH CO LTD
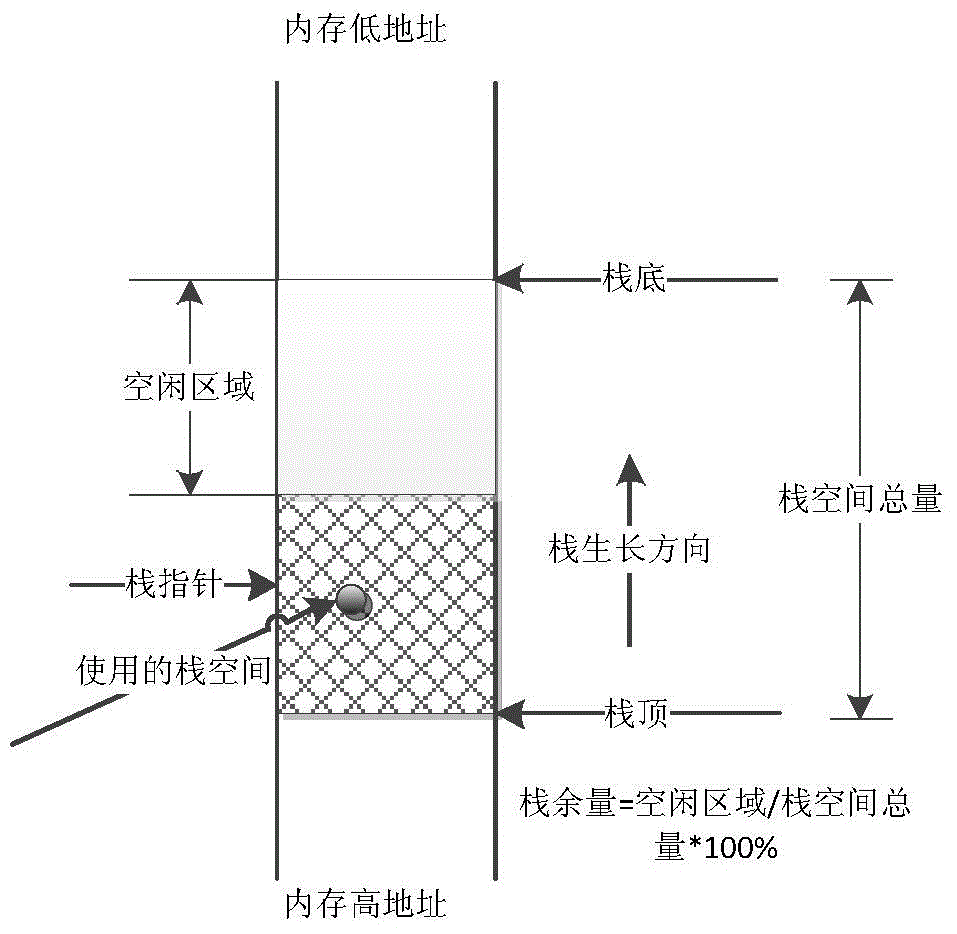
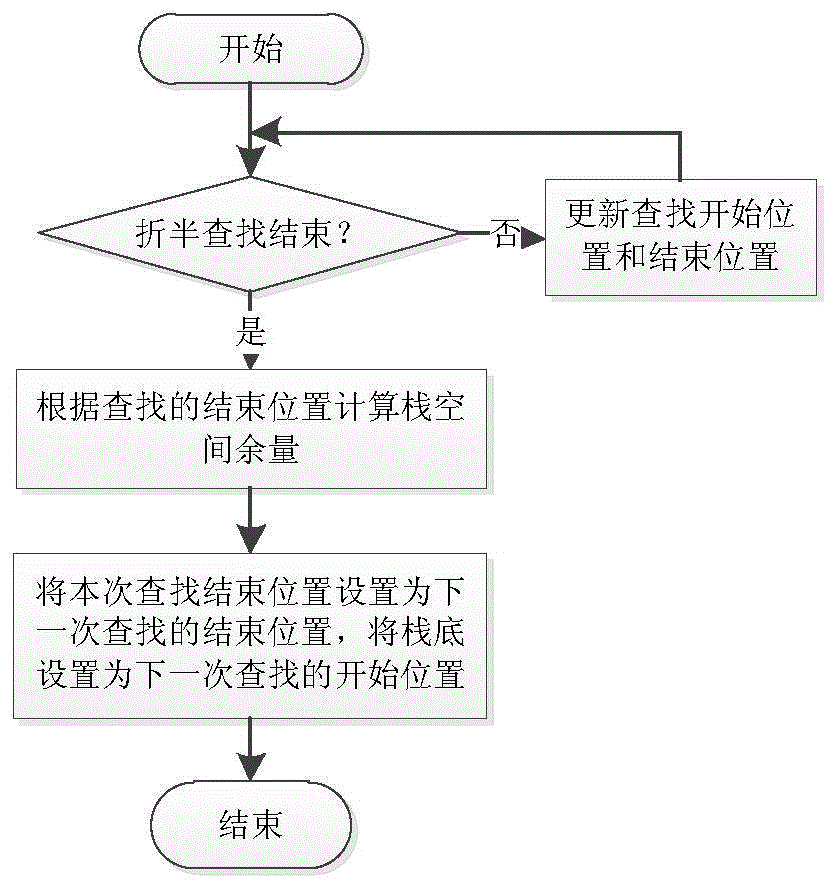
Method for detecting stack space allowance on real time
The invention provides a method for detecting stack space allowance on real time, and aims at solving the technical problems that most of the existing engine control software in domestic completely have one stack space which is shared by all tasks or interrupting processing operations, and the stack space and other data areas share the internal memory, thus stack overflowing caused by any function process can even damage the resource of the whole system and leads to the breakdown of the whole system. The method can detect the use condition of the stack space and whether the stack overflows, and the sue condition of the stack can be reported to the application software on real time; if the application software finds that the use of the stack exceeds the specified limit, corresponding measures can be carried out, and thus, the strength of the software can be improved.
Owner:中国航空工业集团公司航空动力控制系统研究所
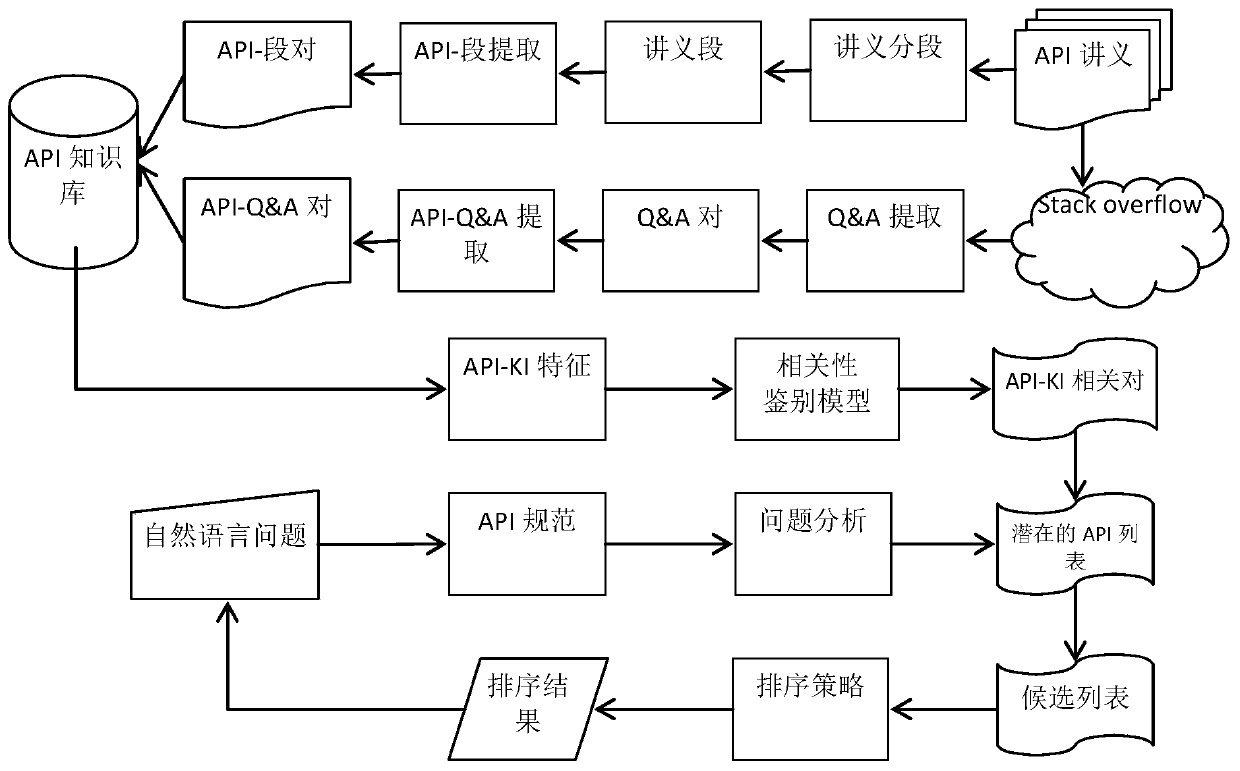
API information retrieval method for natural language form and based on lecture note and Stack Overflow
ActiveCN109933660AEfficient searchBridging the gapText database queryingSpecial data processing applicationsQuestions and answersQuestion answer
The invention belongs to the field of information retrieval, and discloses an API information retrieval method for natural language form and based on lecture notes and Stack Overflow. The method comprises: constructing an API-KI library of API and knowledge items and performing extraction, the API-KI library comprising API and lecture segment API-segment pairs, API and question and answer sheet API-Q&A pairs; analyzing the questions in the natural language form, and obtaining potential APIs corresponding to the questions; identifying related API-KI using a relative identification mode TDML; performing potential APIs with related API-KI pair to generate a candidate list, carrying out descending sorting on the candidate list according to a sorting strategy, and finally returning the sorted API-KI list as a question answer. According to the retrieval method provided by the invention, information of API lecture and SO is integrated, the retrieval precision is effectively improved, and moreuseful API related knowledge can be provided for developers.
Owner:GUANGDONG UNIV OF PETROCHEMICAL TECH
Method and apparatus for detecting an overflow condition in a kernel stack during operating system development
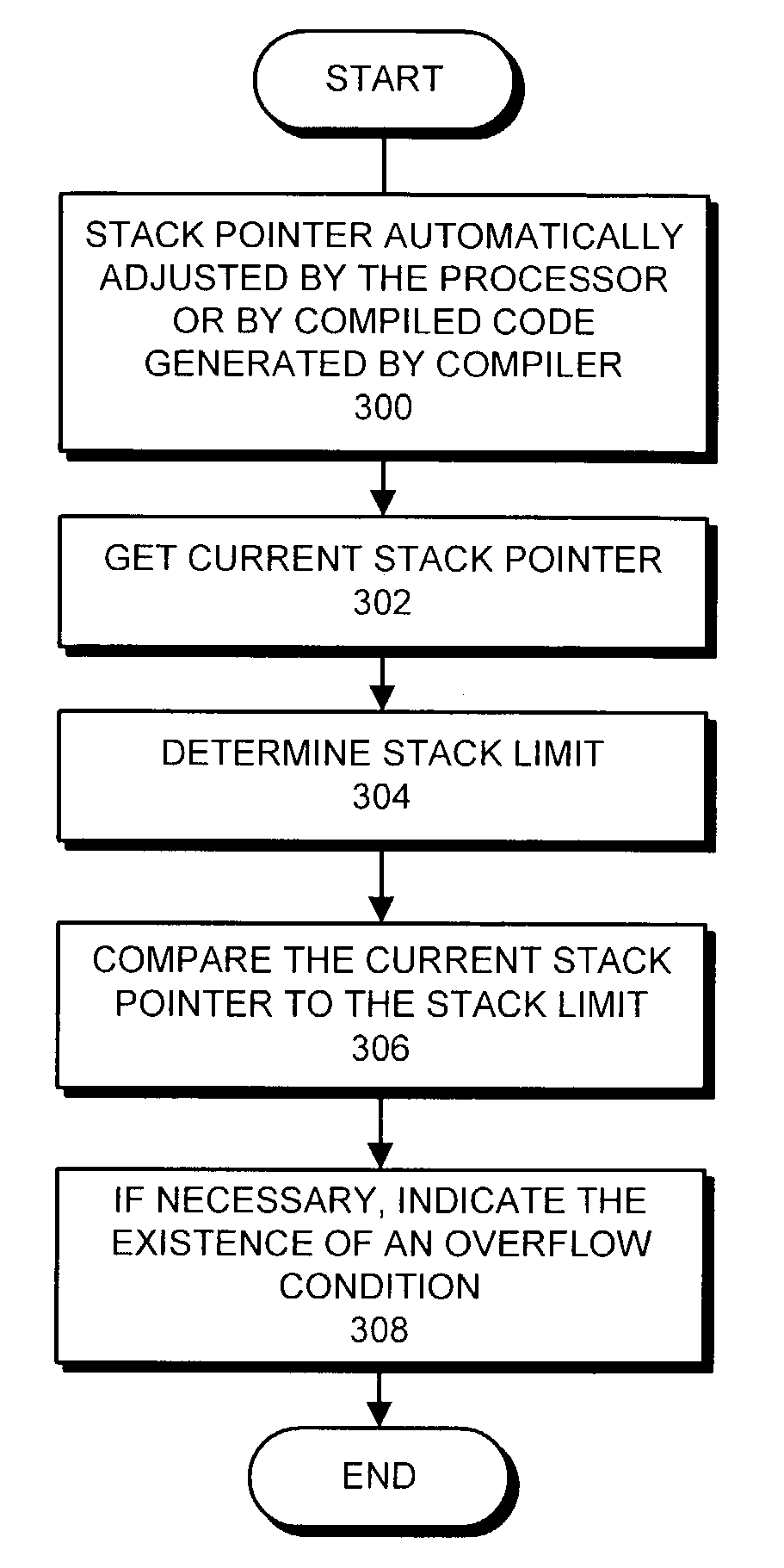
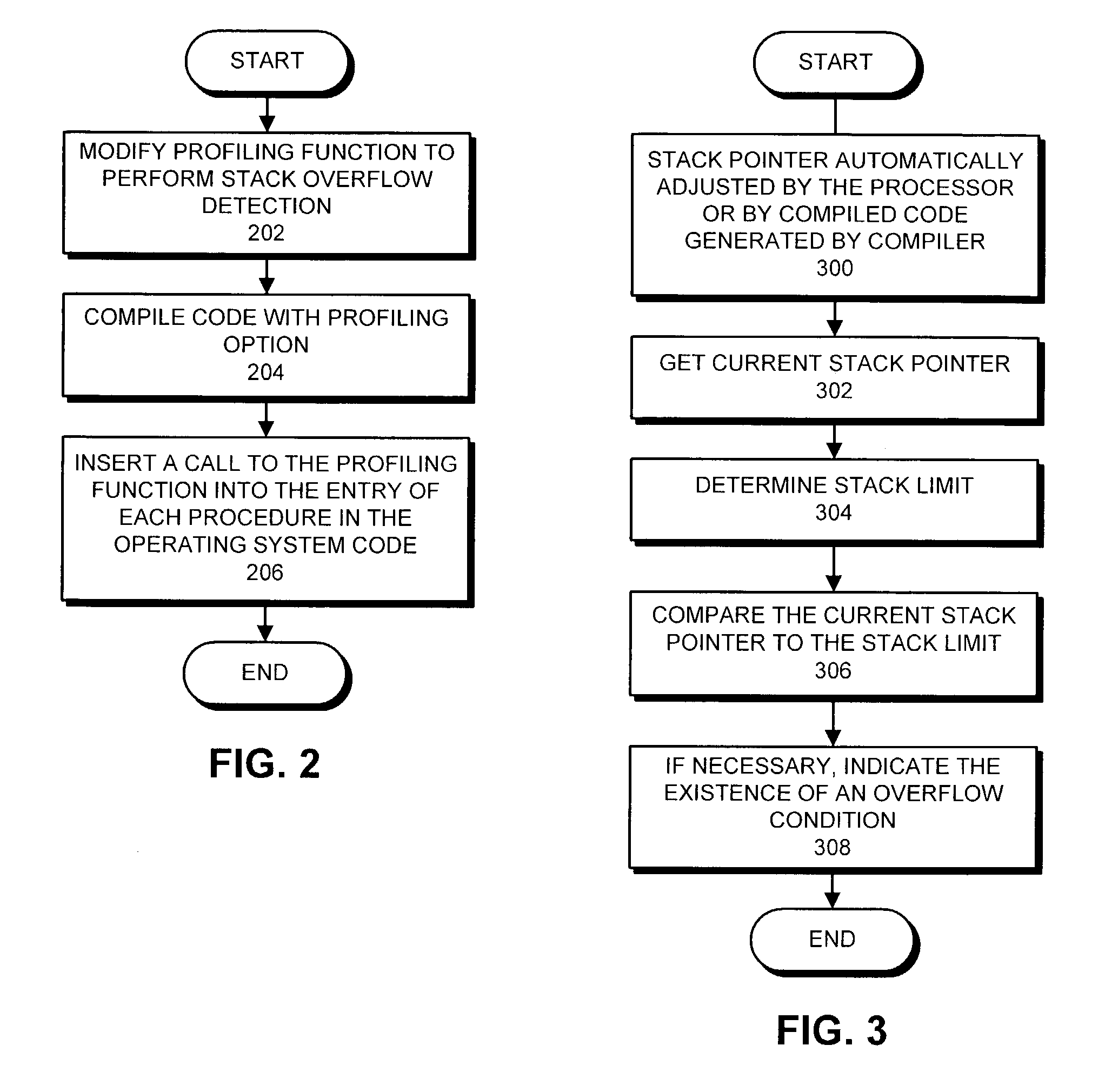
ActiveUS7181733B2Easy to determineError detection/correctionSpecific program execution arrangementsOperational systemSystem development
One embodiment of the present invention provides a system with a mechanism that facilitates determining whether a kernel stack will overflow during development of an operating system. During execution of the operating system, the operating system executes a procedure. Upon entering the procedure, after the current stack pointer has been automatically adjusted to provide stack space for the procedure, the system retrieves the current stack pointer for the process, and determines the stack limit for the process. The system then compares the current stack pointer to the stack limit to determine if the process will cause, or is likely to cause a stack overflow. If a stack overflow will occur, or is likely to occur, the system indicates the existence of a stack overflow condition.
Owner:ORACLE INT CORP
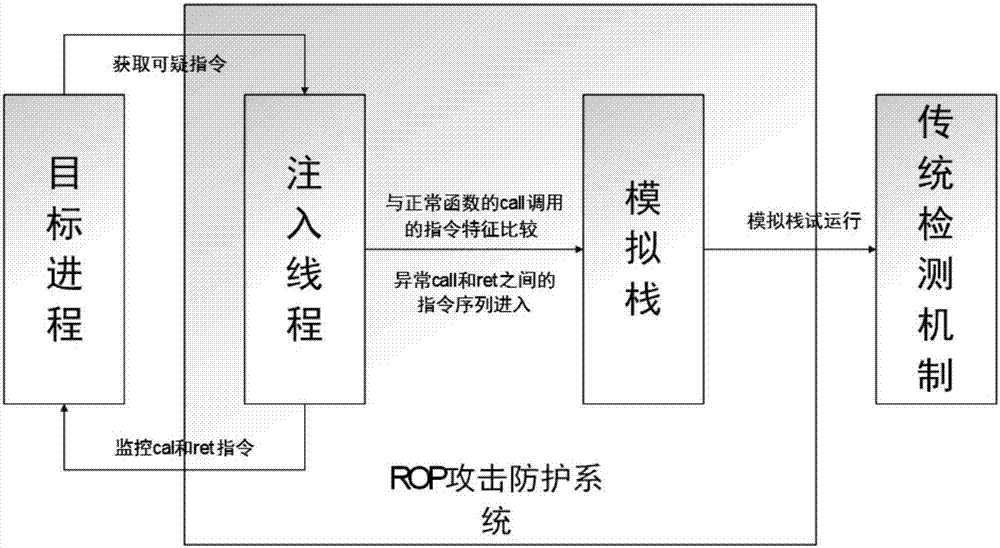
Method for protecting against ROP attacking and stack overflow based on simulated stacks and thread injecting
ActiveCN107229862ATo achieve the purpose of detecting ROP attacksNo need to change the overflow protection mechanismPlatform integrity maintainanceStack buffer overflowProtection mechanism
The invention discloses a method for protecting against ROP attacking and stack overflow based on simulated stacks and thread injecting, and relates to the technical field of protection of ROP attacking. According to the technical scheme, the technical problems are solved in the prior art that ROP vicious codes without commands can bypass stack-overflow protection since a program loading position is fixed and the stack overflow occurs when remote threads utilized in using the simulated stacks to monitor a target progress are injected. The method comprises the steps of using the threads to inject the threads into the target progress (the progress which needs to be protected), opening up a simulated stack space, monitoring a command procedure which simulates the target progress, conducting execution on the simulated stacks by obtaining effective code strings among call commands and ret commands attached by ROP, and then achieving the purpose of detecting ROP attacking by using a traditional overflow protection mechanism.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
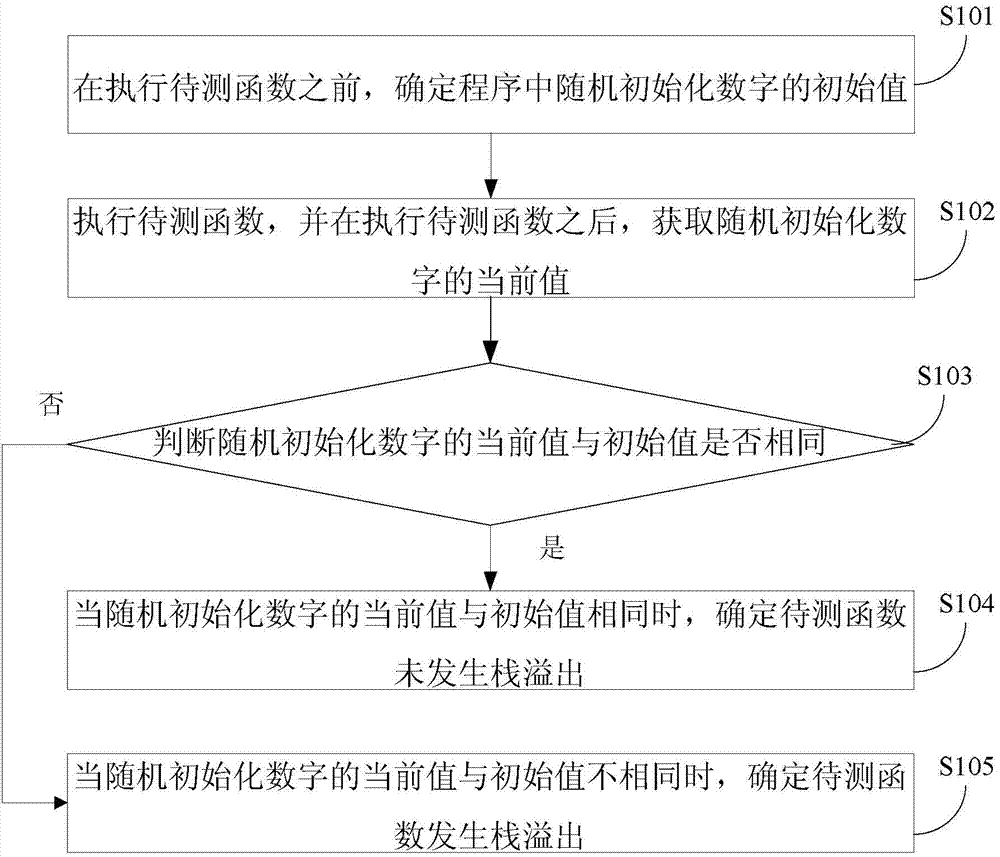
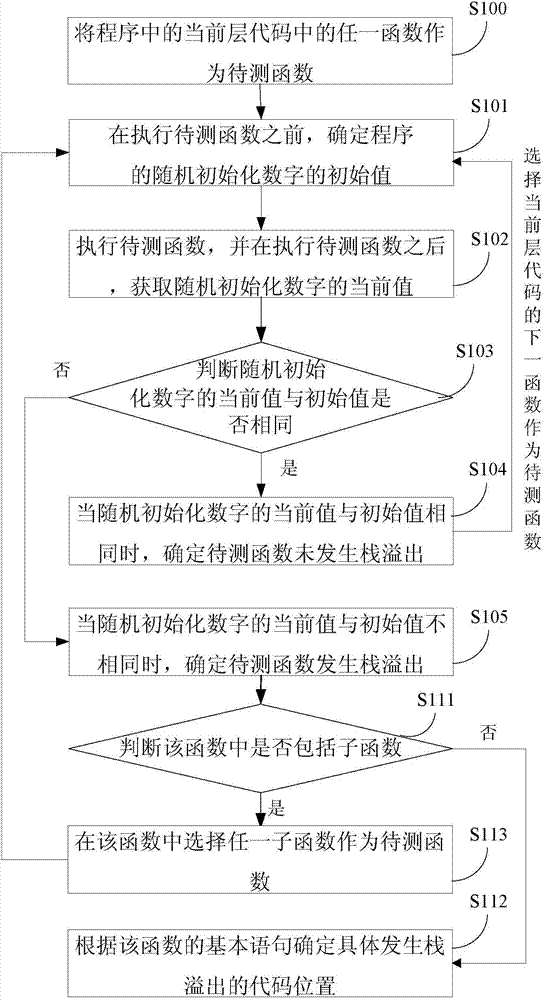
Method and device for detecting stack overflow position
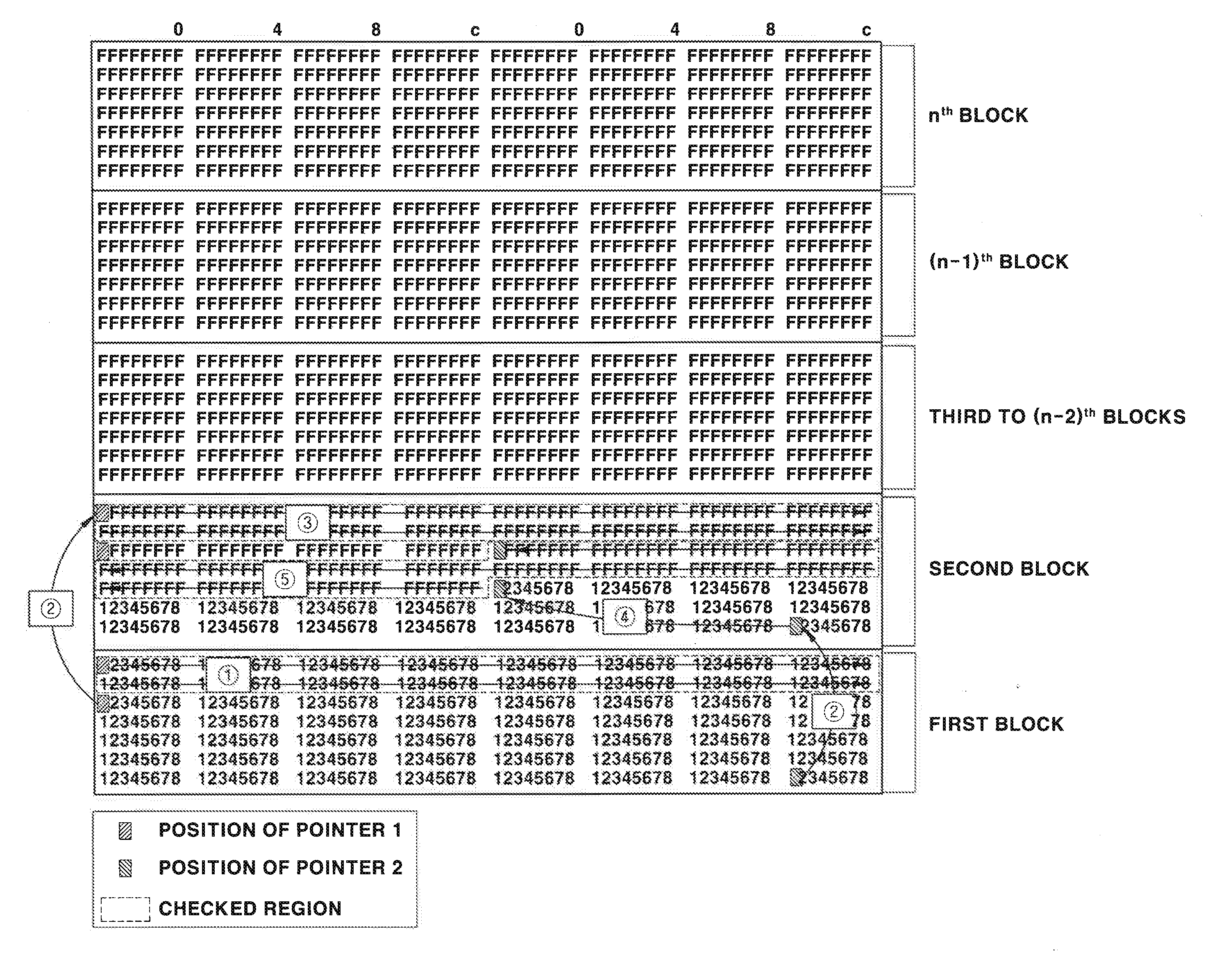
ActiveCN104714885AConvenient process debuggingDetection is simple and fastSoftware testing/debuggingPlatform integrity maintainanceArray data structureStack overflow
The invention relates to a method and device for detecting the stack overflow position. The method and device are used for rapidly and conveniently detecting the stack overflow position. The method comprises the steps that before a function to be detected is executed, the initial value of a randomly initialized figure in a program is determined, wherein the randomly initialized figure is located at the bite alignment address which is closest to and in front of the last element of an array buffering area of the program; the function to be detected is executed, and after the function to be detected is executed, the current value of the randomly initialized figure is obtained; whether the current value and the initial value are equal or not is judged; if the current value is equal to the initial value, it is determined that stack overflow does not happen to the function to be detected; if the current value is not equal to the initial value, it is determined that stack overflow happens to the function to be detected. By the adoption of the method, the stack overflow position can be rapidly and conveniently detected out.
Owner:XIAOMI INC
Embedded software stack overflow detection method and device
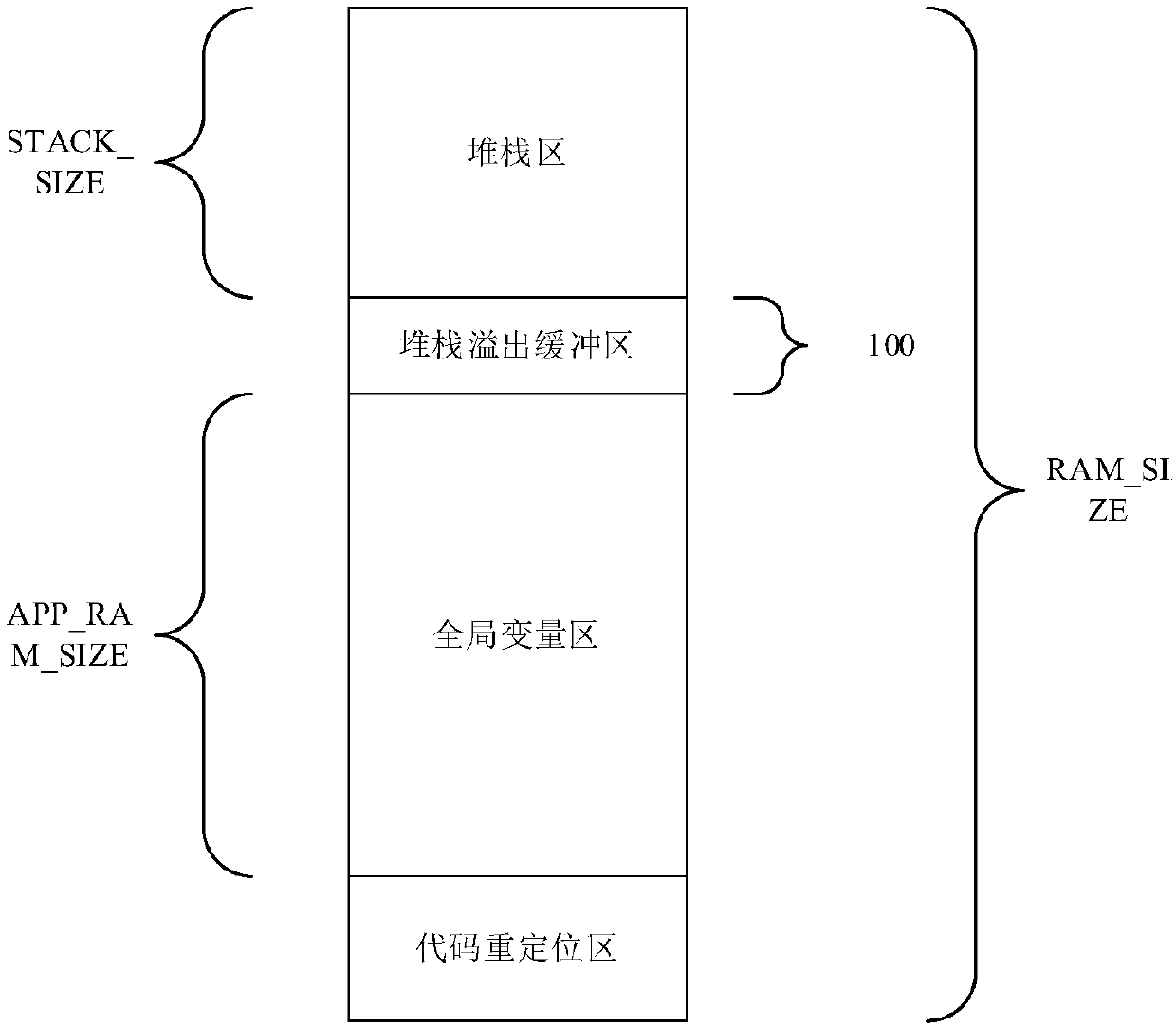
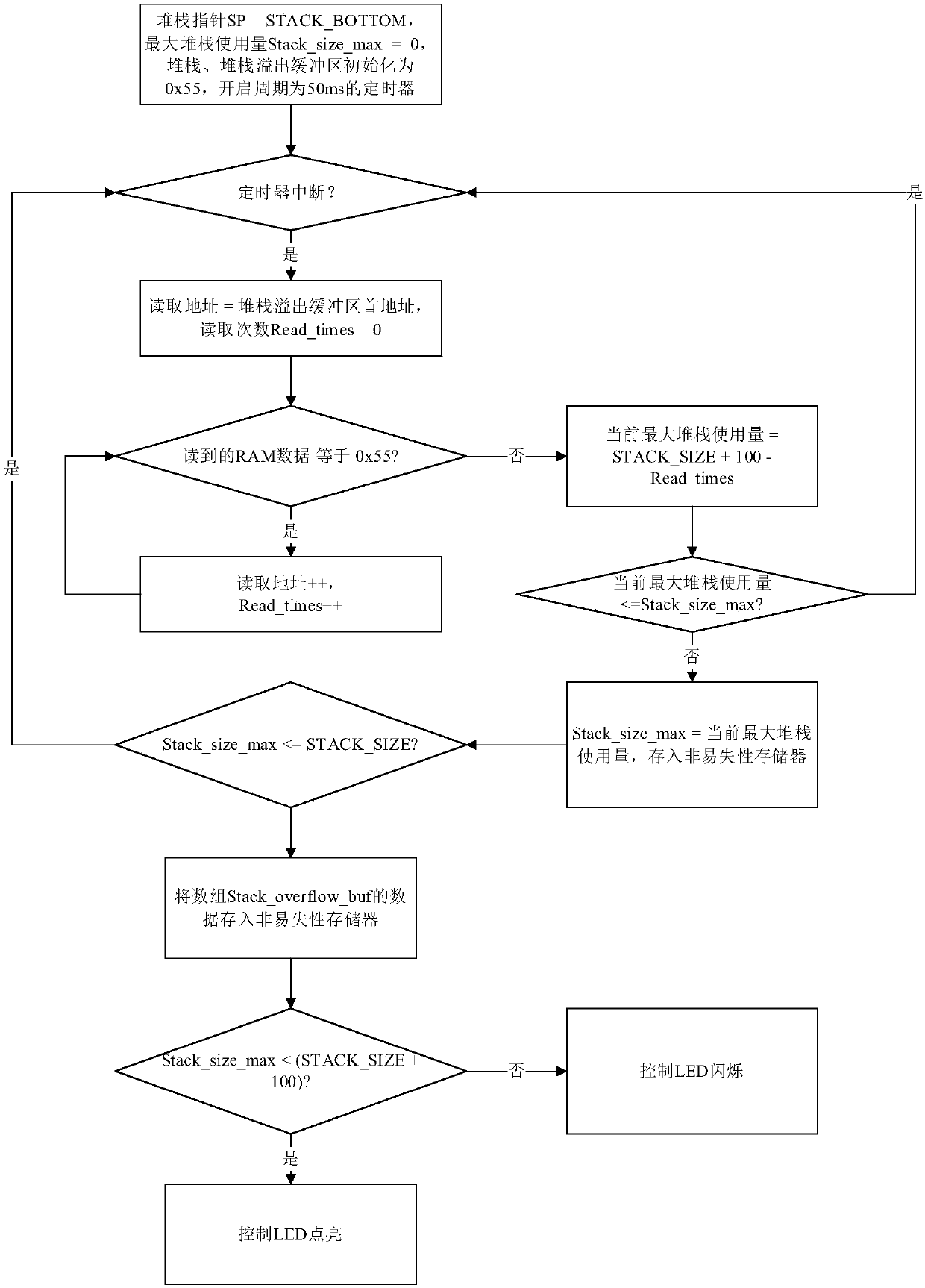
ActiveCN107729240ADoes not affect normal operationGlobal variables do not affectSoftware testing/debuggingArray data structureEmbedded software
The invention discloses an embedded software stack overflow detection method and a device. The method includes steps of classifying a random memory space of a processor to be a stack zone, a stack overflow buffer zone and a global variable zone through a chained file; defining a stack overflow buffer array at the stack overflow buffer zone; electrifying the processor and starting a timer; readingdata of the stack overflow buffer zone and the stack zone in an interrupted service procedure of the timer, and calculating the maximum stack usage amount; judging if the maximum stack usage amount ismore than the dimension of the stack zone; if it is, judging it is stack overflow; storing the information of overflowed upper and lower texts in the stack overflow buffer array; judging if the maximum stack usage amount is less than or equal to the preset threshold value; if it is, judging the stack overflow position according to the stack overflow buffer array. Through arranging the stack overflow buffer zone, the shallow stack overflow cannot cause the abnormal running of the system, and developers can be assisted to perform the procedure revision.
Owner:SHANDONG ACAD OF SCI INST OF AUTOMATION
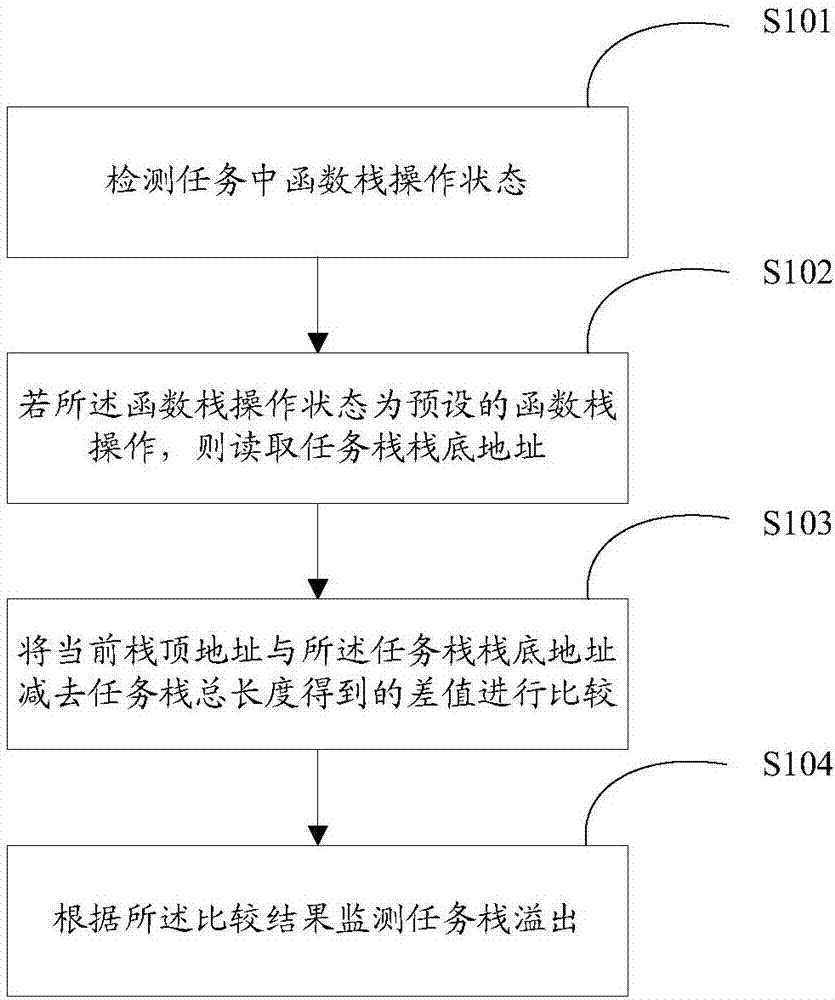
Task stack overflow monitoring method and system
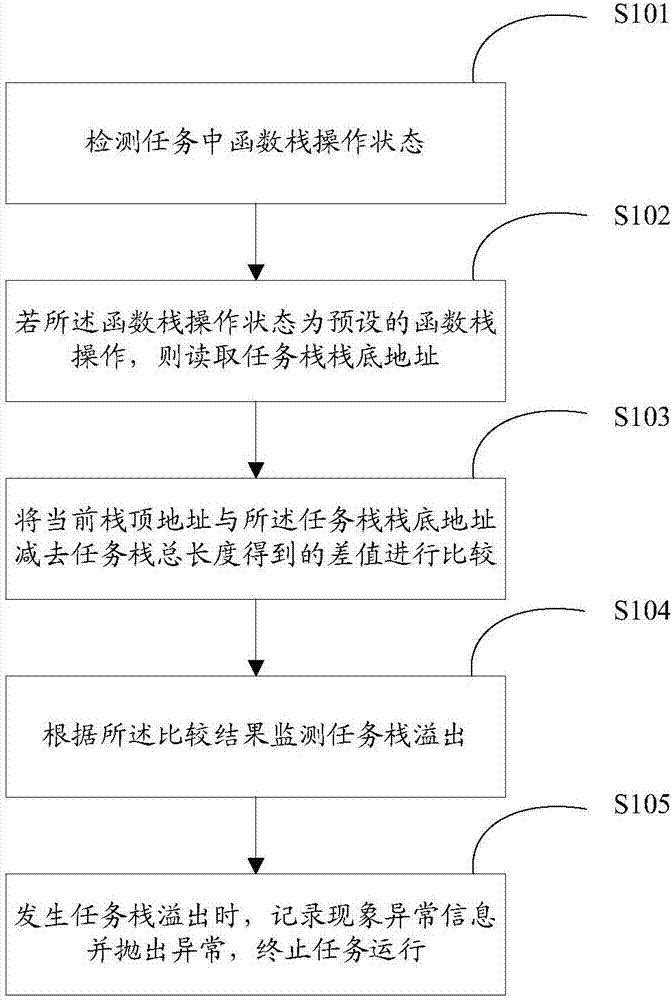
PendingCN107491373AReal-time monitoring of overflow phenomenaReal-time monitoring of overflow phenomenonHardware monitoringSoftware testing/debuggingStack overflowRead-only memory
The invention provides a task stack overflow monitoring method, which comprises the following steps that: detecting the operation state of a function stack in a task; if the operation state of the function stack is a preset function stack operation, reading the stack bottom address of the task stack; comparing a difference value obtained in a way that the total length of the task stack is subtracted from a current stack top address and the stack bottom address of the task stack; and according to a comparison result, monitoring task stack overflow. Compared with the prior art, the scheme disclosed by the invention does not occupy additional memory space used for setting a read-only memory area, and a task stack overflow phenomenon is monitored in real time and does not fail to be reported.
Owner:HANGZHOU DPTECH TECH
Task stack overflow detection algorithm for SPARC (scalable processor architecture) platform
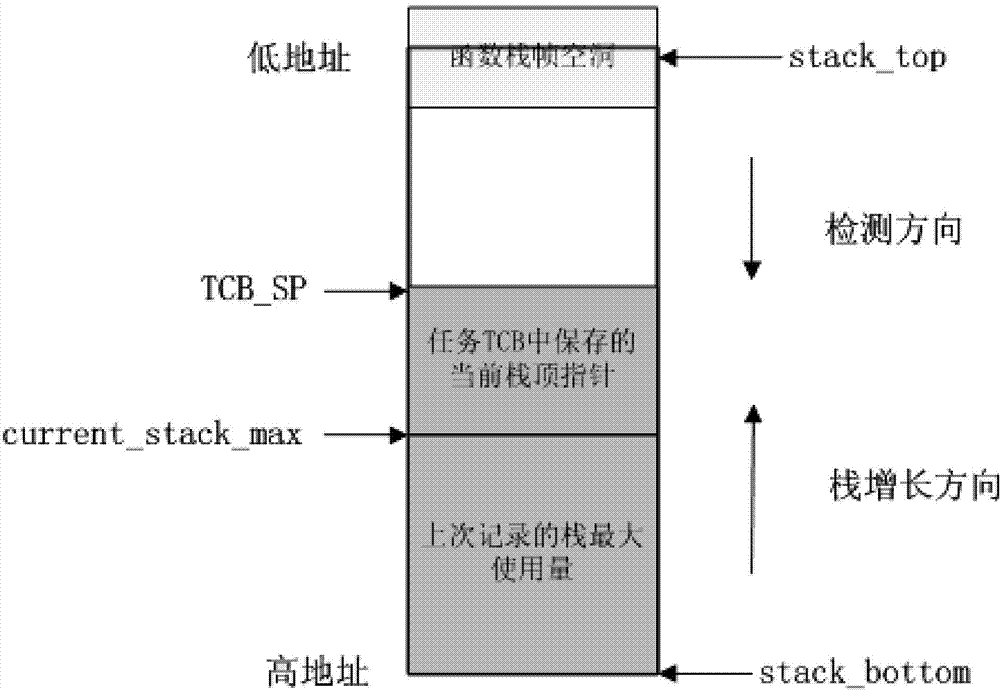
ActiveCN103870244AReasonable allocation of sizeImprove efficiencyPlatform integrity maintainanceMachine execution arrangementsDependabilityStack overflow
The invention discloses a task stack overflow detection algorithm for an SPARC (scalable processor architecture) platform. The detection algorithm is characterized by comprising the following steps of maintaining an independent variable current_stack_max for each task, and recording the maximum usage of a current stack, wherein an initial value of the maximum usage is 0; initializing a task stack to be 0 during task creation; reserving allowance of which the size is the same as that of an empty function stack frame at the top of the task stack, and determining overflow if the usage of the stack exceeds the allowance. The algorithm is accurate and high in efficiency, an application developer can be effectively helped to reasonably allocate the task stack size, and the reliability and the security of a system are improved.
Owner:北京神舟航天软件技术股份有限公司
Method and device for protecting stack
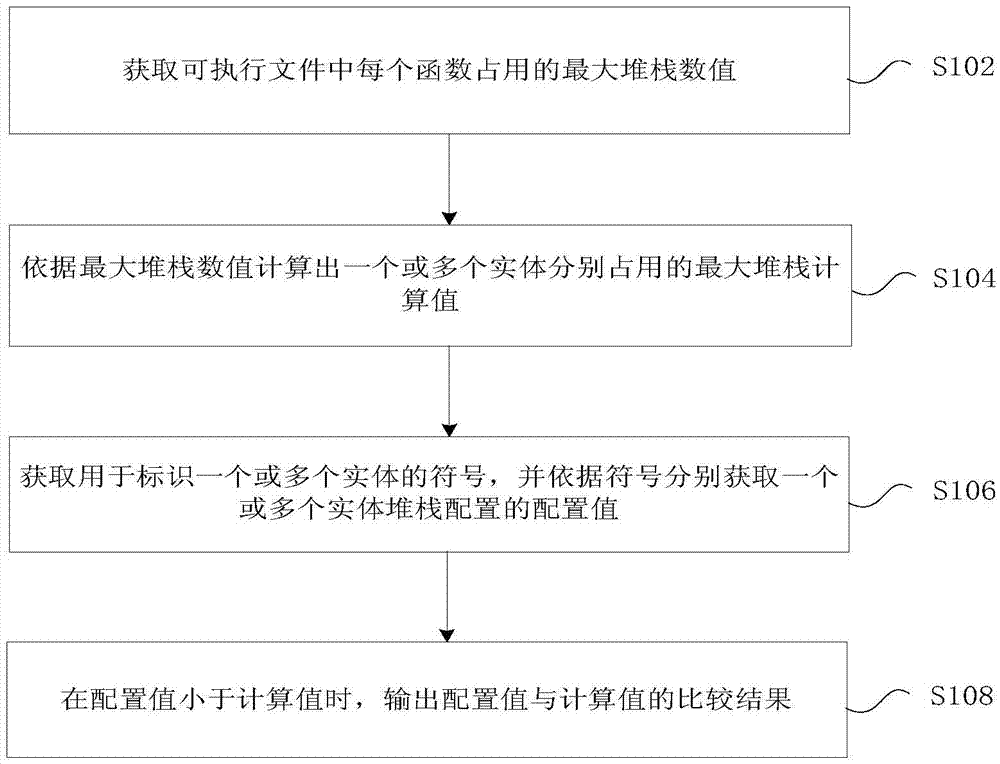
ActiveCN107015904ARealize detectionAddressing Occupancy IssuesSoftware testing/debuggingComputer hardwareLag
The invention provides a method and a device for protecting stack. The method comprises: obtaining a maximum stack numerical value of each function occupation in an executable file, wherein the executable file is configured with a plurality of threads and one or more entities used to operate the stack are hung under each thread; according to the maximum stack numerical value, calculating a maximum stack calculated value of respective occupation of one or more entities; obtaining a symbol used to identify one or more entities, and according to the symbol, respectively obtaining a configuration value of configuration of one or more entities; when the configuration value is smaller than the calculated value, outputting a comparative result of the configuration value and the calculated value. Through the method, problems in the prior art of detection lag caused by using dynamic stack detection, and stack memory occupation using static stack detection analysis are solved, so that detection on stack overflow is conveniently and rapidly realized.
Owner:ZTE CORP
Stack-using method
InactiveCN1423196ARun fastEnhance memory access speedProgram initiation/switchingSpecific program execution arrangementsParallel computingStack overflow
The present invention has an objective of minimizing deterioration of the processing speed of a Java accelerator device even when stack overflow occurs in a stack memory unit. A first thread presently allocated to a first stack area of a stack memory unit 113 to which a fourth thread belongs is saved in a virtual stack area of a main storage medium 103. Thereafter, the data of the fourth thread as stack data to be switched is copied to the first stack area of the stack memory unit 113 by the controller unit 112 (accelerator device 101).
Owner:LENOVO INNOVATIONS LTD HONG KONG
Using an overflow list to process mark overflow
ActiveUS20090259702A1Avoid memoryObject oriented databasesProgram controlProgramming languageWaste collection
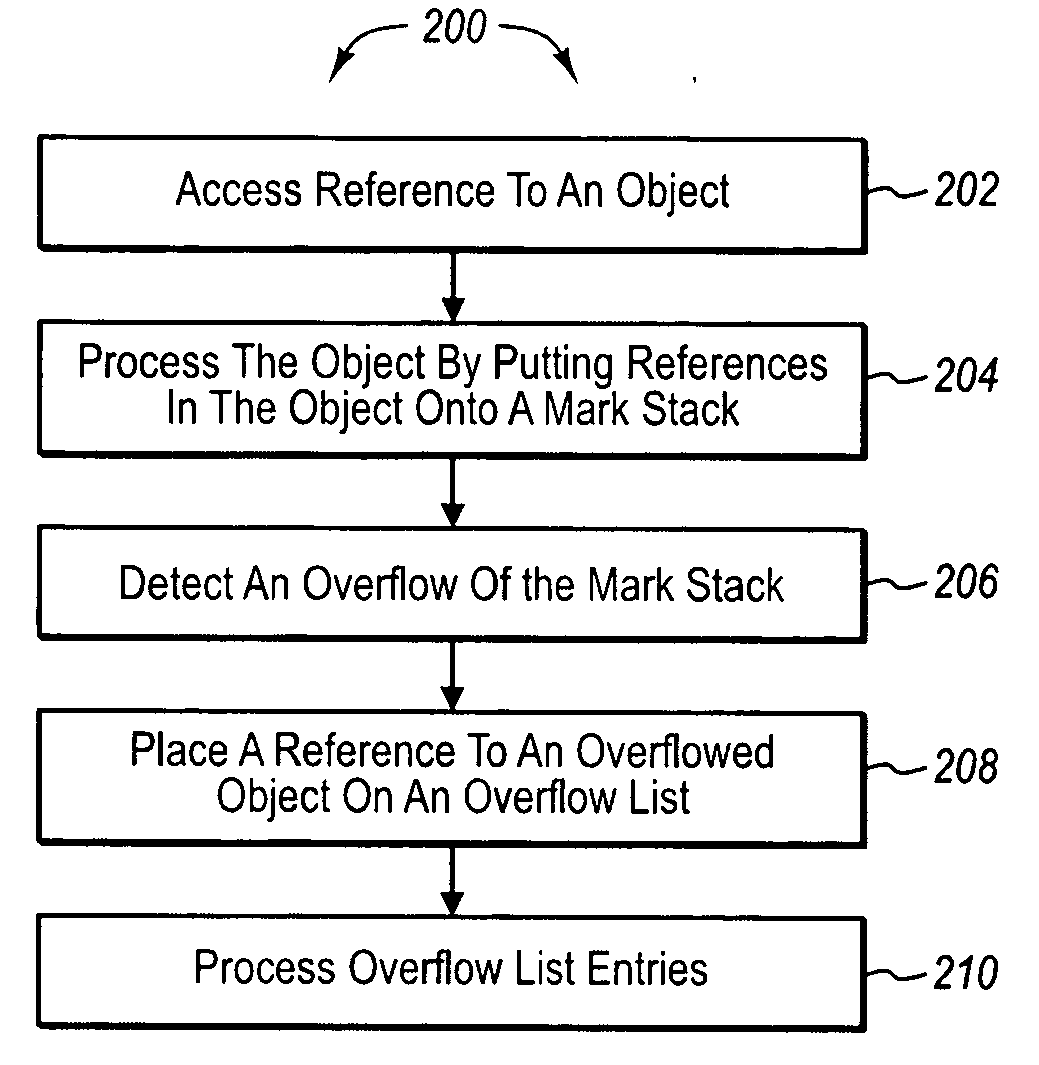
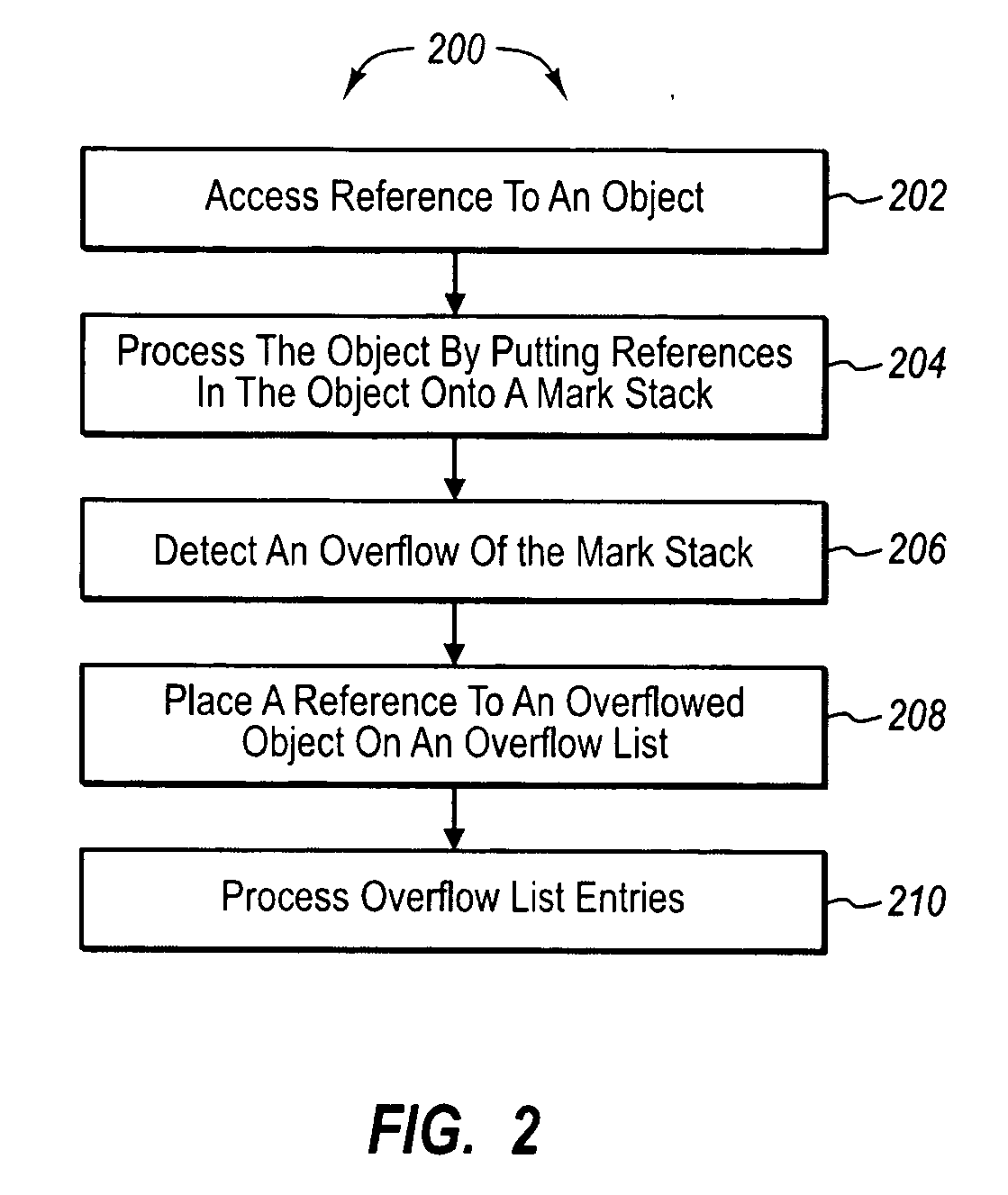
Mark stack overflow list. A method may be practiced in a computing environment including application code that implements garbage collection functionality. The garbage collection functionality includes pushing object references onto a mark stack, such that objects referenced on the mark stack can be marked so as to prevent memory for the objects from being recycled for use with other objects instances. The method includes acts for handling overflows of a mark stack. The method includes accessing a reference to an object. The object is processed by attempting to enumerate references to other objects from the object onto a mark stack. An overflow condition of the mark stack is detected for a referenced other object. A reference to the referenced other object is placed on an overflow list. References from the overflow list are processed.
Owner:MICROSOFT TECH LICENSING LLC
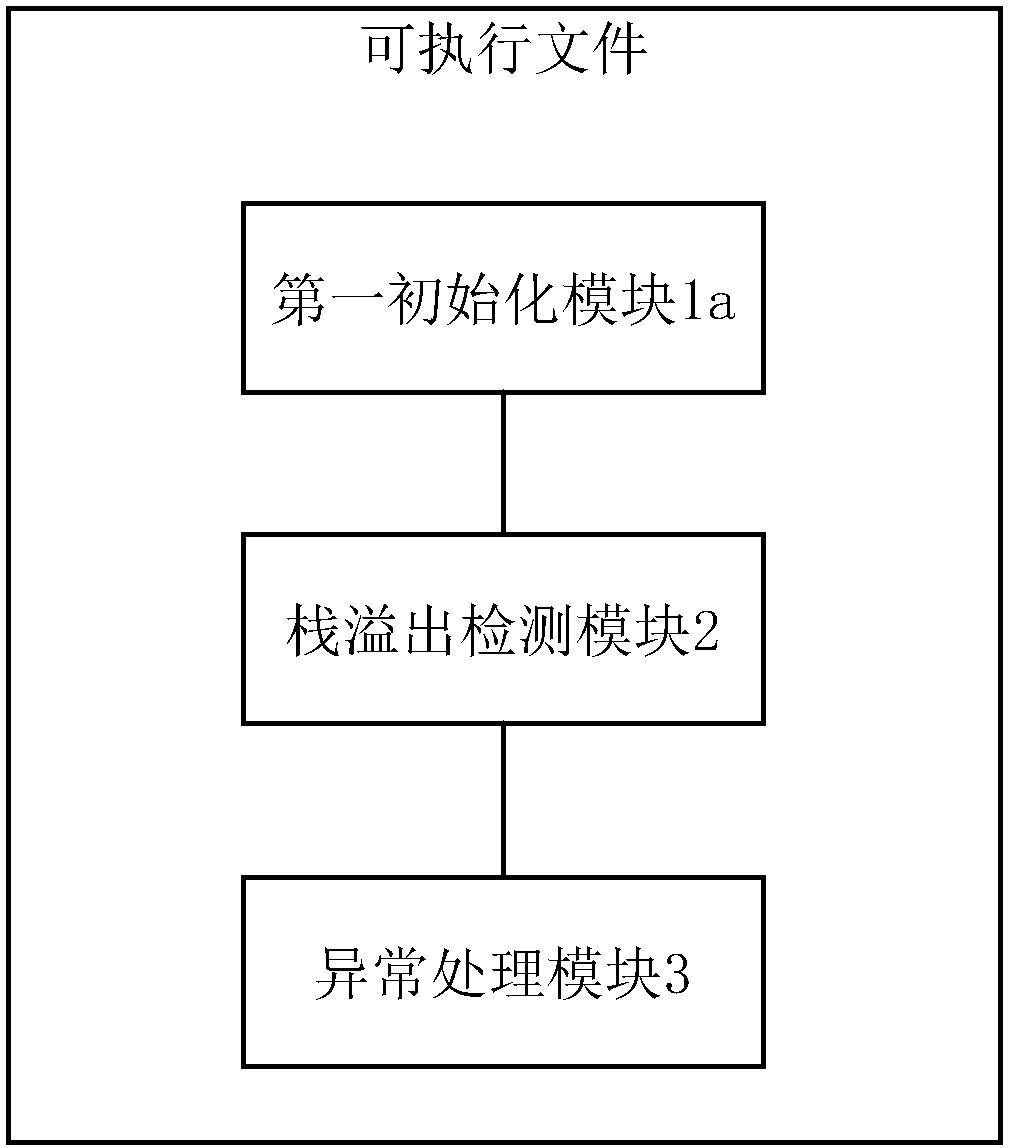
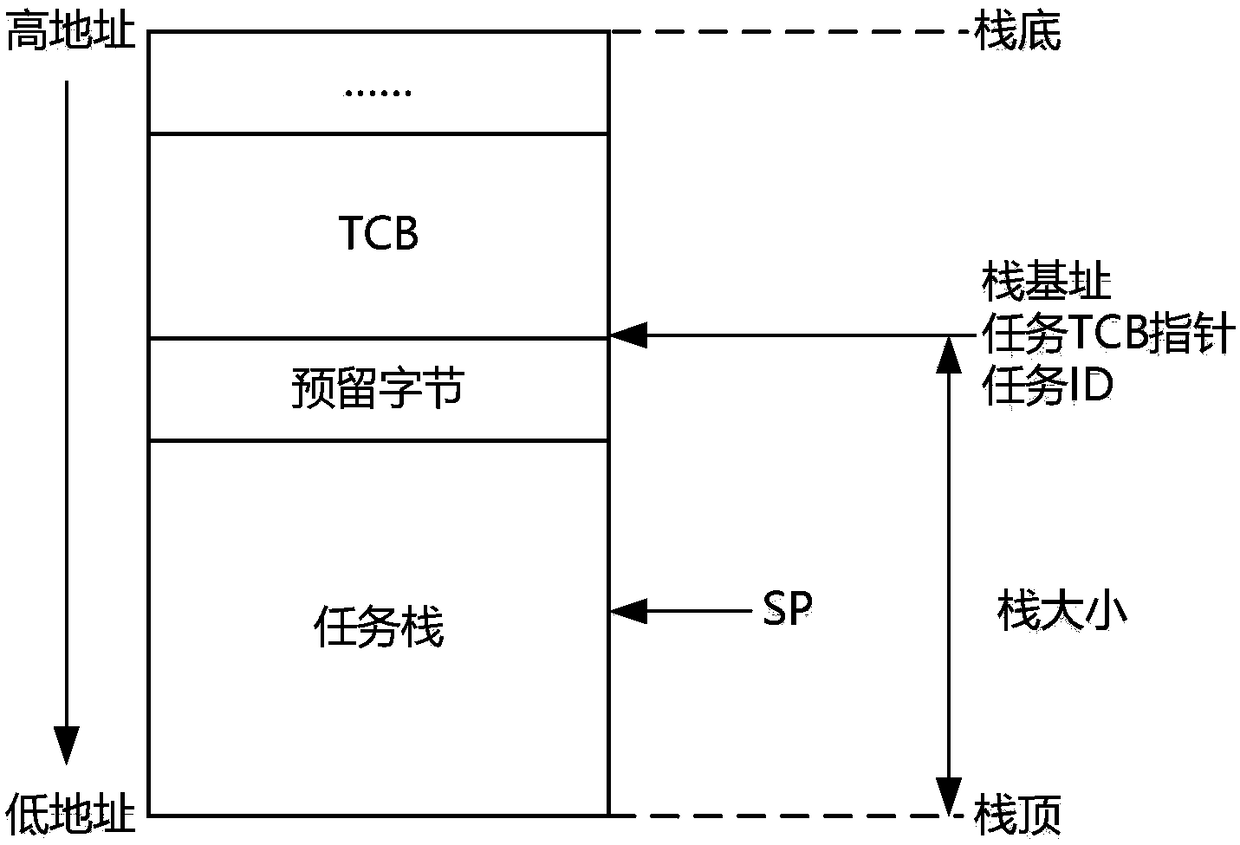
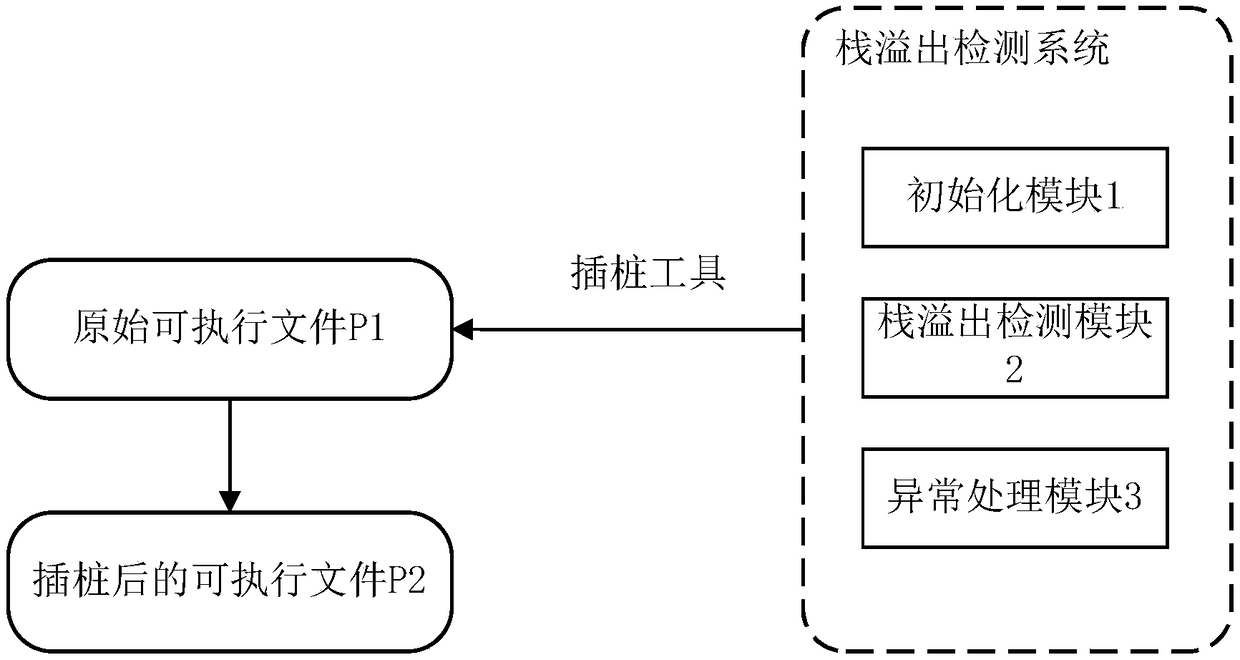
Stack overflow detection system and method
ActiveCN108268770AOverflow accurateAvoid missingPlatform integrity maintainanceComputer moduleParallel computing
The invention discloses a stack overflow detection system and method and relates to the technical field of computers. The detection system comprises a first initialization module, a stack overflow detection module and an exception handling module, wherein the first initialization module is arranged at an output port of each task creation function of an executable file and used for acquiring basicinformation of a stack during task creation; the stack overflow detection module is arranged at an input port of each task execution function of the executable file and used for judging whether stackoverflow occurs according to an SP value corresponding to a current execution instruction of the task execution function and the basic information of the stack of the function; the exception handlingmodule is used for recording a judgment result of the stack overflow detection module and recalling illegally covered memory space addresses when stack overflow occurs. Stack overflow can be detectedaccurately in the first time, missing can be avoided, the probably illegally modified memory area beyond stack space can be reminded during stack overflow, and the stack space cost is saved.
Owner:武汉长江计算科技有限公司
System and method for monitoring memory stack size
ActiveUS20140359246A1Easy to useEfficiently and effectively monitoredInput/output to record carriersHardware monitoringRisk levelOperational system
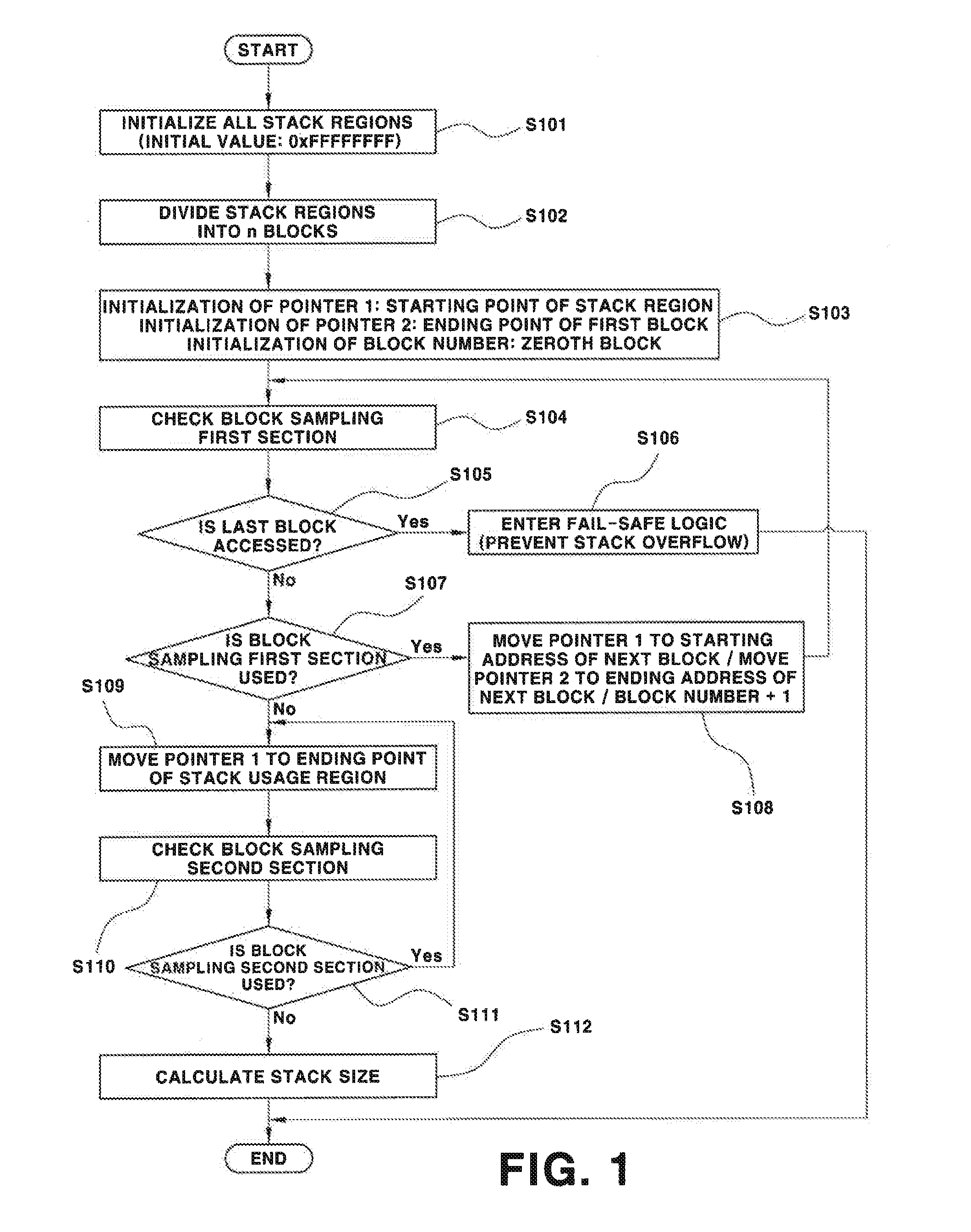
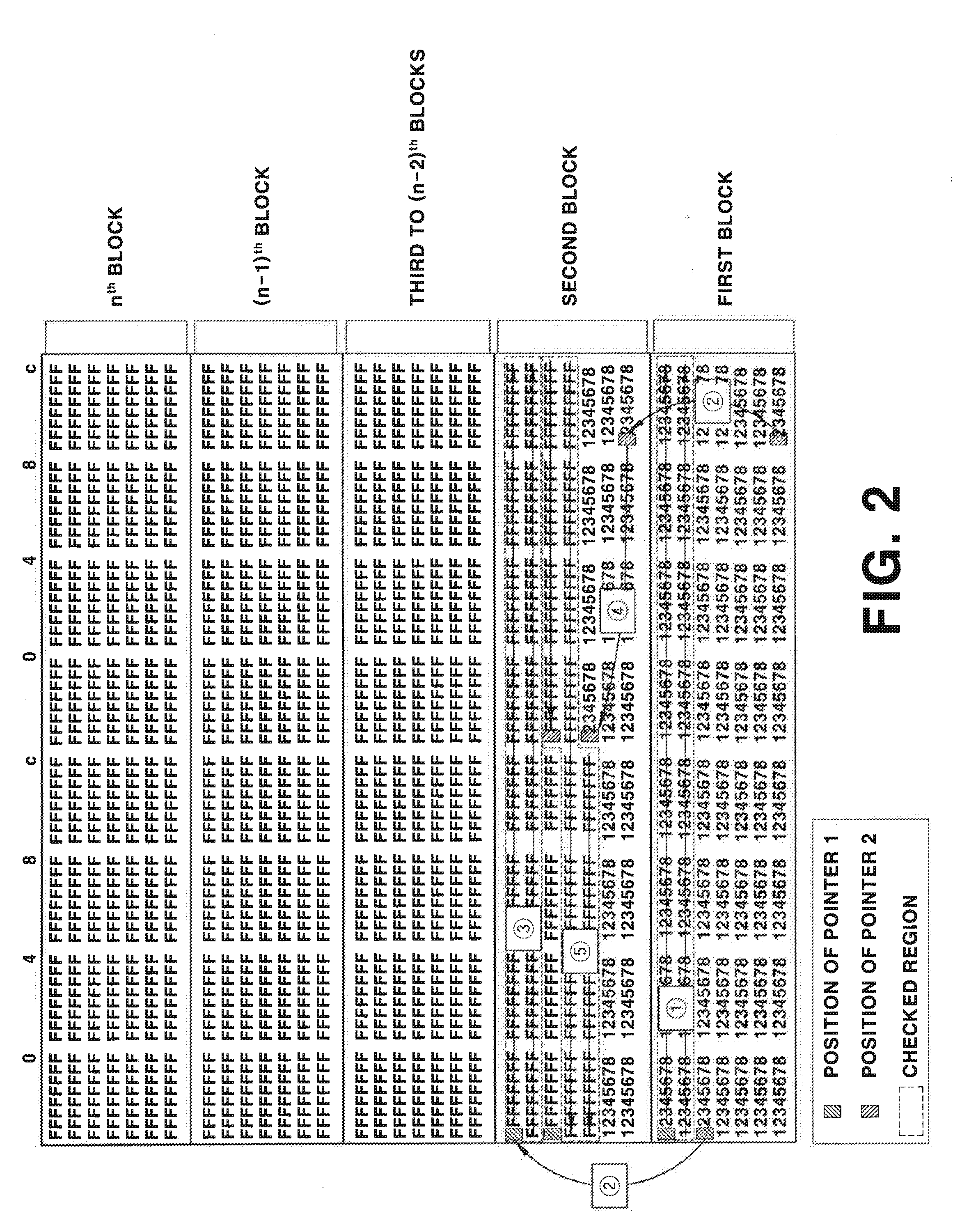
A system and method for monitoring a memory stack size is provided, and more particularly, a method for monitoring a memory stack size, whereby the size of a memory stack applied to an operating system of a controller for a vehicle is monitored so that an overflow phenomenon of the memory stack can be prevented. That is, an accurate usage amount of a memory stack of the entire control system for a hybrid vehicle is efficiently and effectively monitored so that, when the control system reaches a risk level of stack overflow, fail-safe logic is executed and an overflow phenomenon of the memory stack as a result can be prevented.
Owner:HYUNDAI MOTOR CO LTD +1
Instruction modification virtual platform execution method for kernel stack overflow defense
PendingCN109635562AImprove shielding effectEasy to identifyPlatform integrity maintainanceSoftware simulation/interpretation/emulationParallel computingComputer terminal
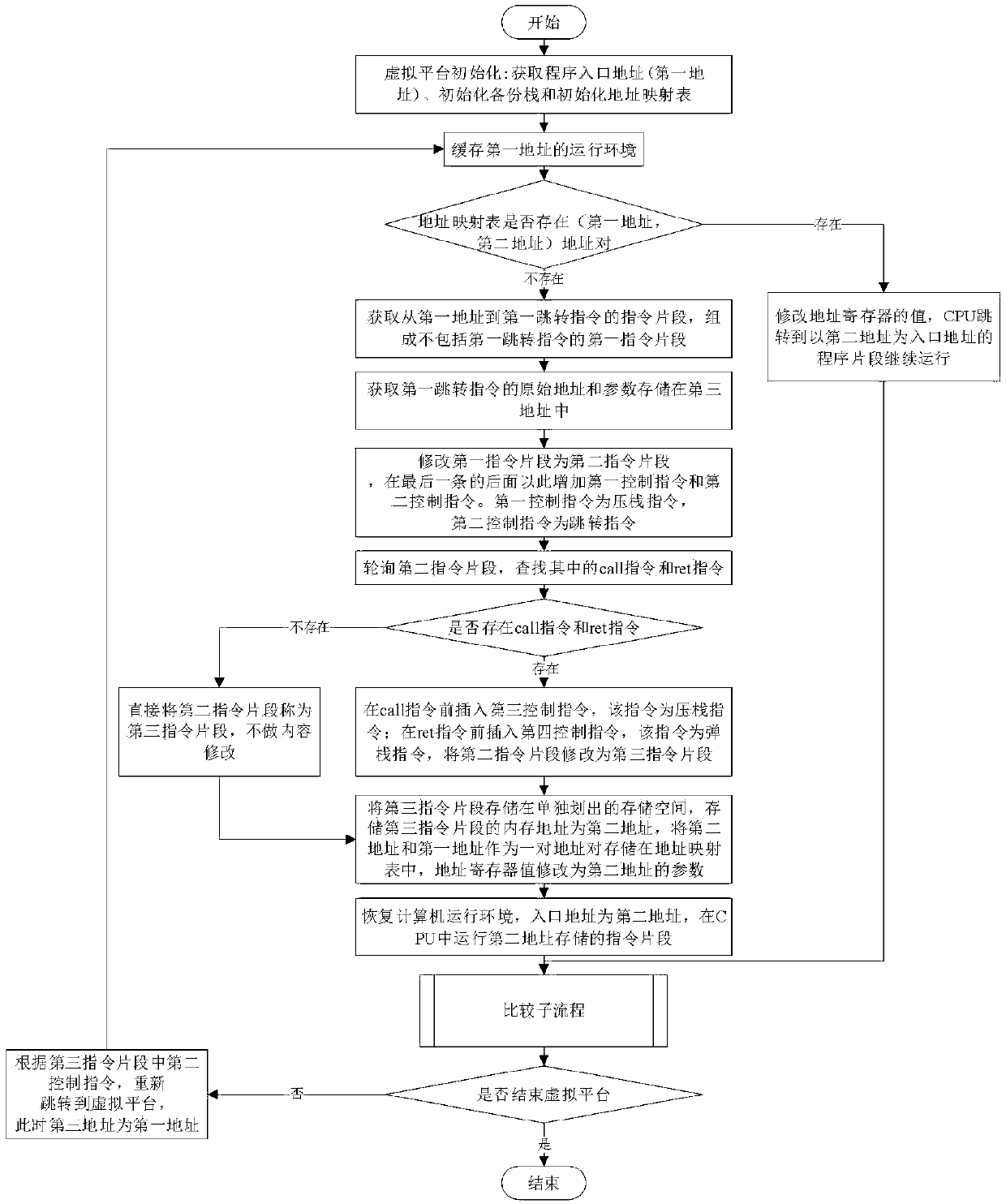
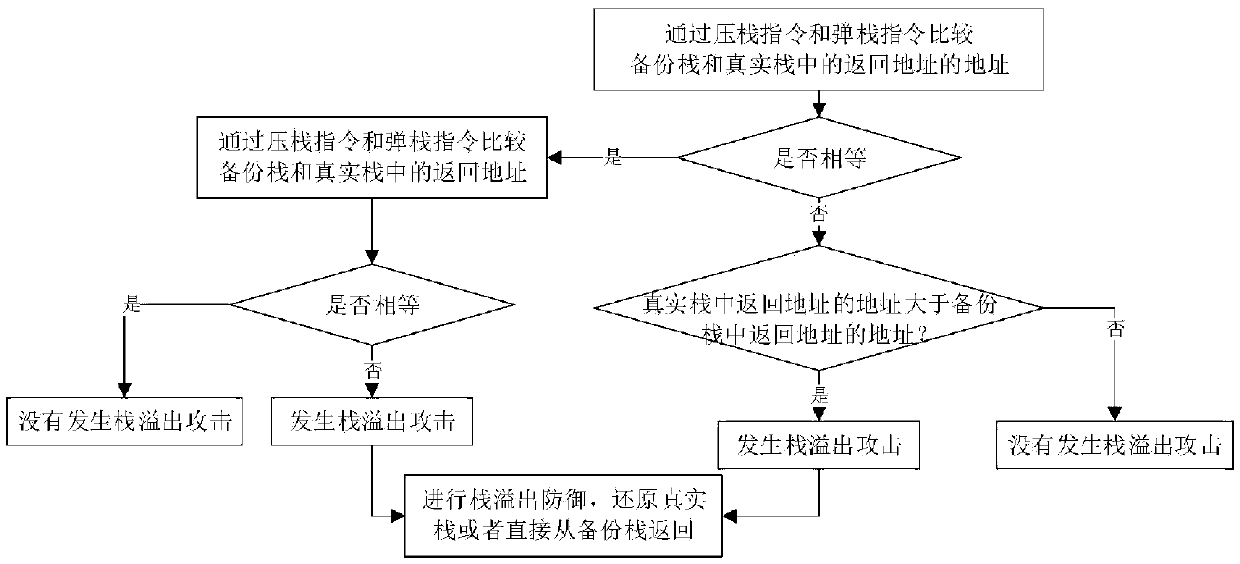
The invention provides an instruction modification virtual platform execution method for kernel stack overflow defense, and belongs to the field of computer security. The method comprises the following steps: establishing a backup stack, an address mapping table and a thread ID index table; with the jump instruction as a segmentation point, obtaining an instruction fragment from the first address,and inserting a first control instruction and a second control instruction; if the instruction fragment has a cal instruction and a let instruction, a third control instruction and a fourth control instruction need to be inserted; independently storing the third instruction fragment, and storing the first address and the second address into an address mapping table; and judging whether a stack overflow attack occurs or not, and if the stack overflow attack occurs, performing stack overflow defense by the virtual platform. According to the invention, the computer runtime instruction can be analyzed in real time, and the call instruction and the let instruction can be monitored. The invention aims to solve the problems of system crash and data loss which may be caused by a stack overflow attack occurring in a computer terminal, and even the risk that the computer terminal is controlled.
Owner:HARBIN ENG UNIV
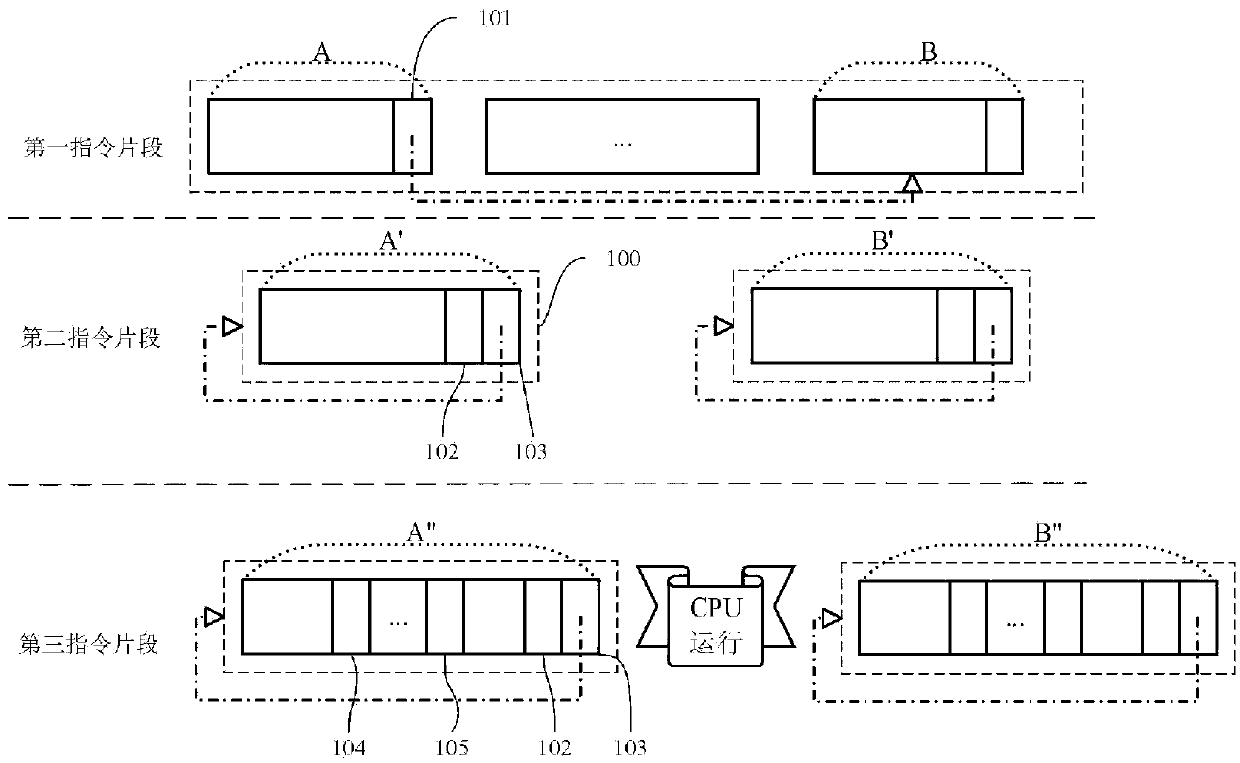
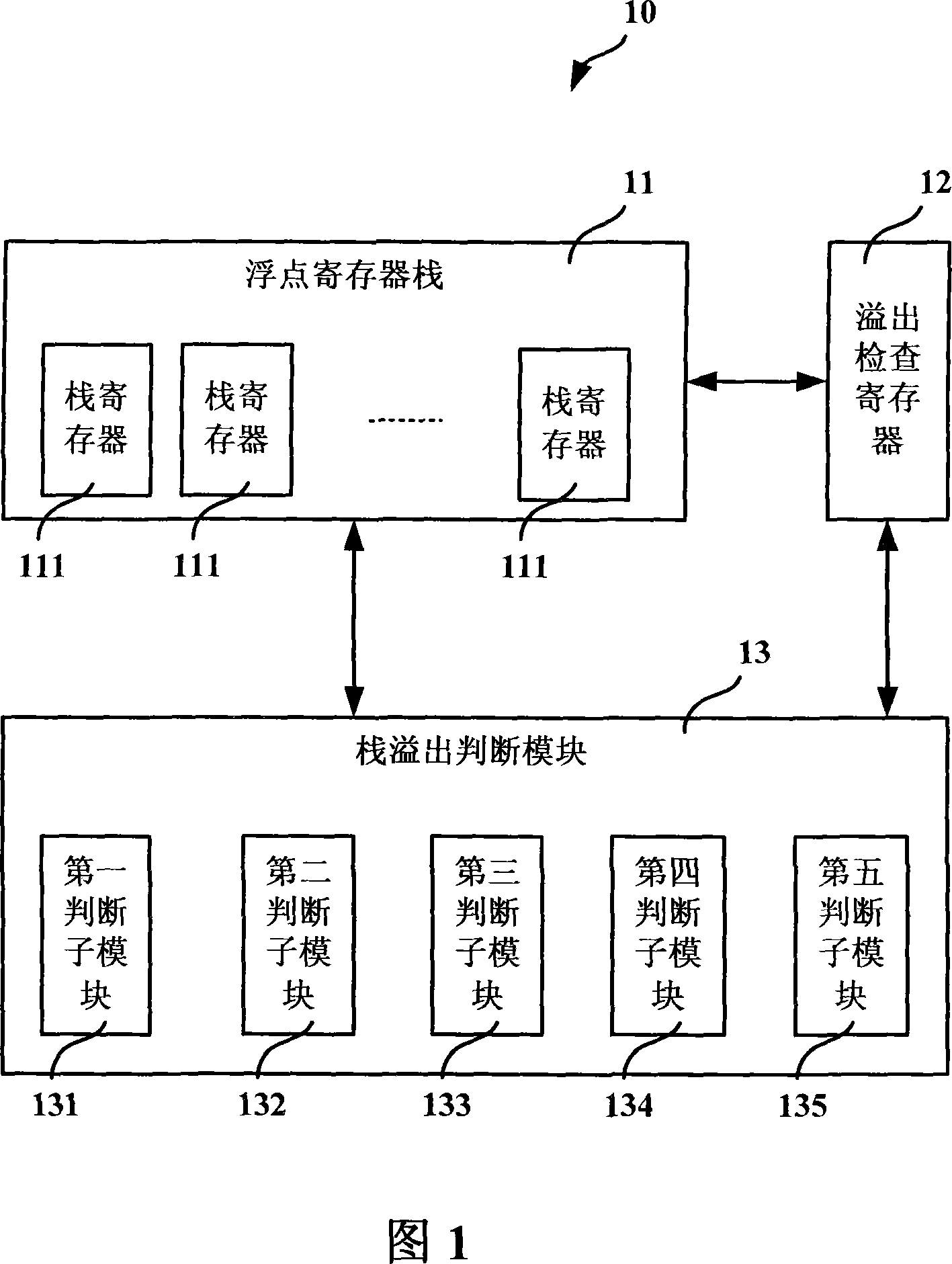
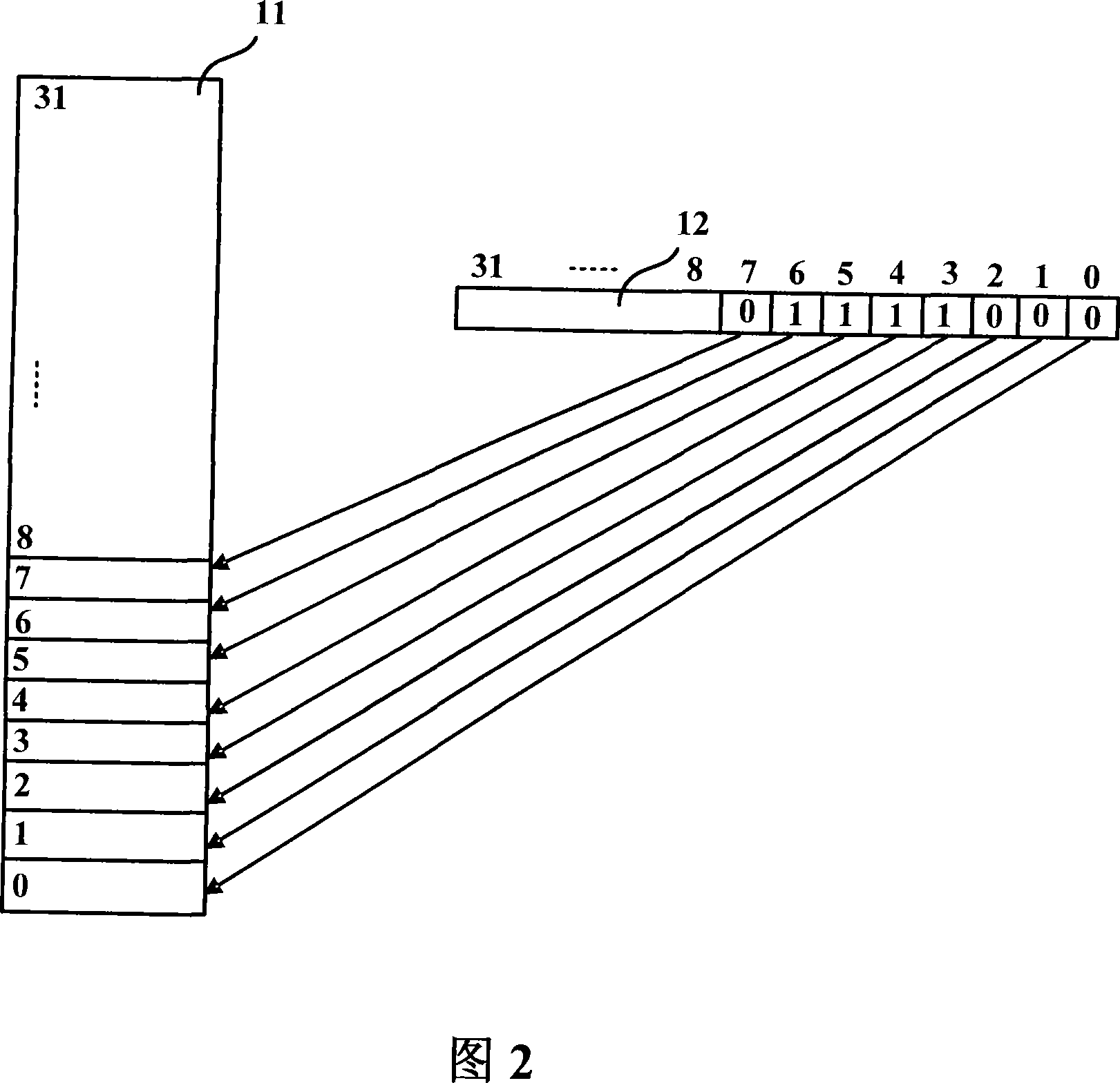
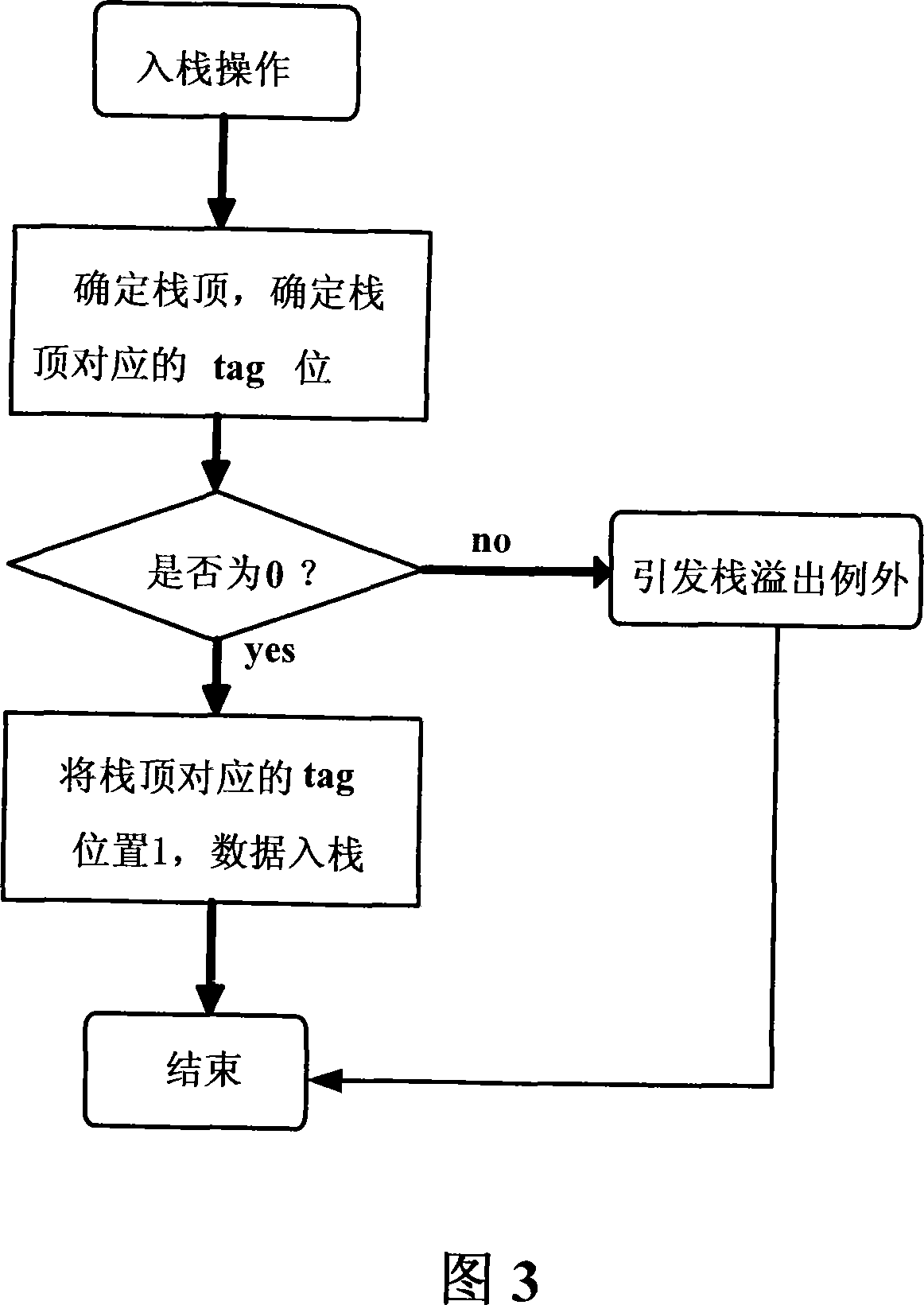
Apparatus and method for checking floating point stack overflow on non-CISC processor
ActiveCN101158891AImprove compatibilityFacilitate binary translation workDigital data processing detailsFloating pointWorkload
The invention discloses a device and a method conducting floating-point stack overflow check on a non-complex instruction set computer processor. The device comprises a floating-point register stack, which comprises a plurality of stack registers, which can conduct floating-point calculation; an overflow check register used for stack overflow exceptional check when conducting floating-point access, which comprises a plurality of bits corresponding to the stack registers, and all the bits separately indicate the states of corresponding stack registers; a stack overflow judge module, which is used for checking the stack registers in the specified floating-point register stack, conducting operation to the overflow check register in accordance with the values of the stack registers, and carry out the floating-point stack overflow check. The invention can greatly reduce the workload and improve efficiency of a virtual machine.
Owner:LOONGSON TECH CORP
Stack overflow protection method in operation for embedded system
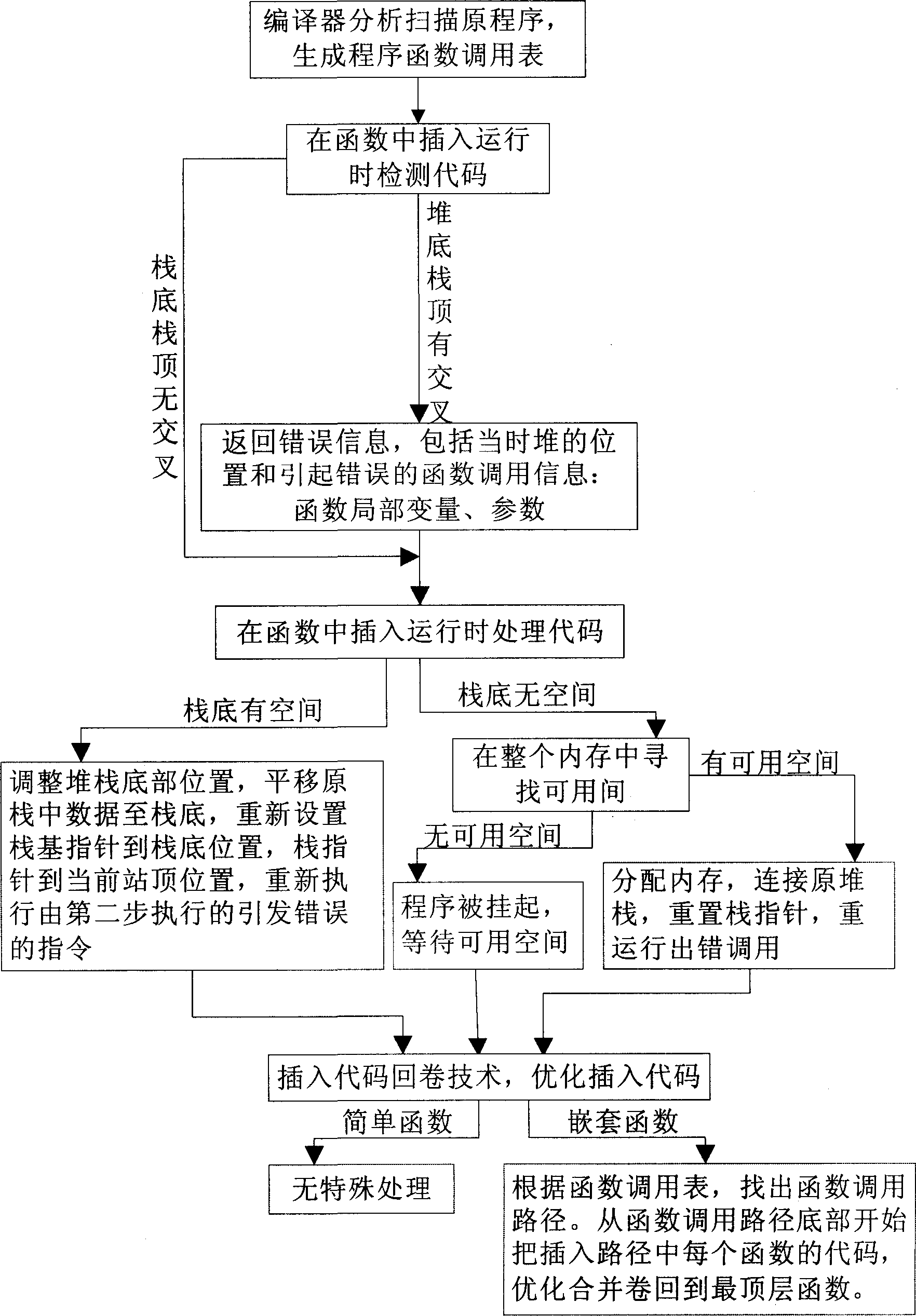
InactiveCN1851648AEasy to insertLess quantityProgram controlMemory systemsHandling CodeApplication software
Said method includes 1, compiler analysing scanning original program, generating program function call list for optimizing unreel function; 2, compiler detecting code and stack use state in function inserting operation, and feeding back information for processing code in inserting operation; 3, compiler processing code in functional inserting stack operation; 4, adopting functional unreel technology optimizing inserted code in function. The present invention does not insert code in nested function, greatly reduces code quantity, capable of dynamically detecting warehouse space in application program operation and doing relevant processing, excluding overflow possibility to ensure system safe operation.
Owner:ZHEJIANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com