Method for protecting against ROP attacking and stack overflow based on simulated stacks and thread injecting
A stack overflow and thread technology, applied in the field of ROP attack stack overflow protection, can solve stack overflow and other problems, and achieve good accuracy, great independence, and great applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
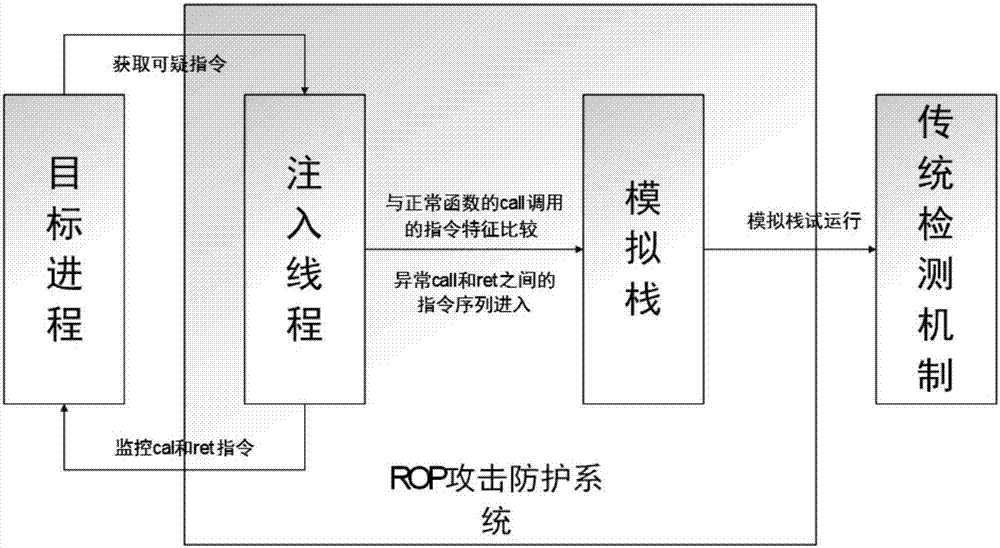
[0060] 1. The ROP attack protection system uses remote threads to inject into the target process
[0061] Use dll remote injection technology:
[0062] 1) OpenProcess obtains the handle to be injected into the process;
[0063] 2) VirtualAllocEx opens up a section of memory in the remote process, the length is strlen(dllname)+1;
[0064] 3) WriteProcessMemory writes the name of the Dll into the memory created in the second step;
[0065] 4) CreateRemoteThread uses LoadLibraryA as a thread function, and the parameter is the name of Dll to create a new thread;
[0066] 5) CloseHandle closes the thread handle.
[0067] 2. Monitor the instruction flow of the target process to obtain the instructions between call and ret
[0068] The injected thread can imitate Ollydbg to additionally monitor the target process, so as to obtain program execution instructions.
[0069] 3. Compare the characteristic instructions of normal function calls, and extract the suspected abnormal instru...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com