A stack overflow protection method and device
A protection device and stack overflow technology, applied in the field of stack overflow protection methods and devices, can solve the problems of large consumption of Canaries, fixed character filling is easy to be detected by attackers, errors, etc., to achieve the effect of enhanced protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
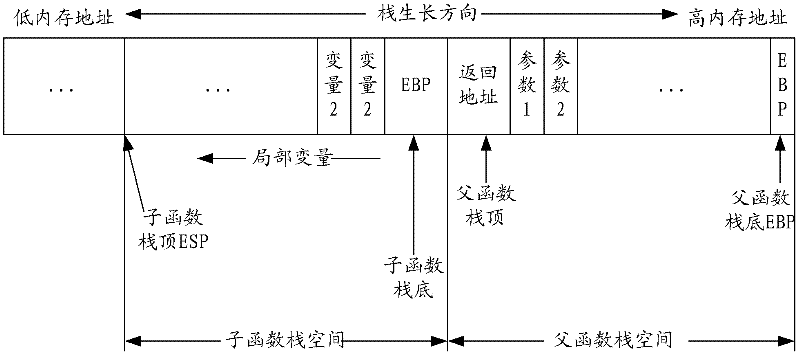
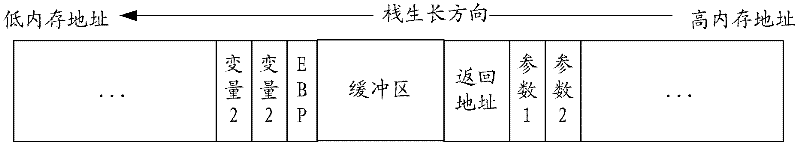
[0051] As an embodiment of a stack overflow protection method of the present invention, it includes the step of generating a random character string; the step of applying for a stack; the step of filling a string in a buffer; the step of checking the stack and the step of releasing the stack, specifically as Figure 4 shown.
[0052] Generate Random String: Generates a string of random length and content as part of filling the buffer. The upper limit of the string length can be determined according to the combination of device performance and actual application, and the value of each character is randomly generated from 0-255;
[0053] Applying for the stack: The application of the heap is operated by malloc. By en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com