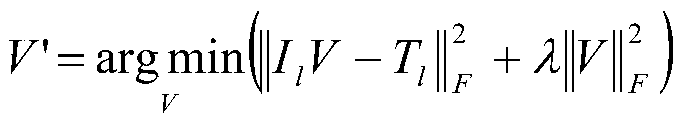Patents
Literature
253results about How to "Not easy to get" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Preparation method of injectable human hair keratin soft tissue filling material
The invention relates to the technical field of the medical reshaping cosmetology, which overcomes the defects of the existing soft tissue filling material by virtue of the advantages of high resistance of the human hair against physical and chemical factors, stable properties, acid and alkali resistance, capability of not being easily absorbed and degraded by tissues, convenient acquisition, repeated material use, easy processing and the like. The middle section of solid-state autologous human hair is used as a raw material and treated with cleaning, bleaching, milling processing, freeze-drying, packaging, and cobalt-60 radiation, so that the human hair is bleached to prepare power homogenate with different thicknesses and liquid human hair keratin granules, thereby providing a human hair keratin soft tissue filling material which is applicable to injection and has the advantages of autologous source, easy obtaining, safety, no toxicity, good tissue compatibility, easiness for a human body to accept and function of stimulating the collagen proliferation. The invention realizes the long-term repair of the skin and soft tissue, and satisfies the requirements of the soft tissue filling material in the field of the reshaping cosmetology.
Owner:泛亚润康(北京)生物科技有限公司
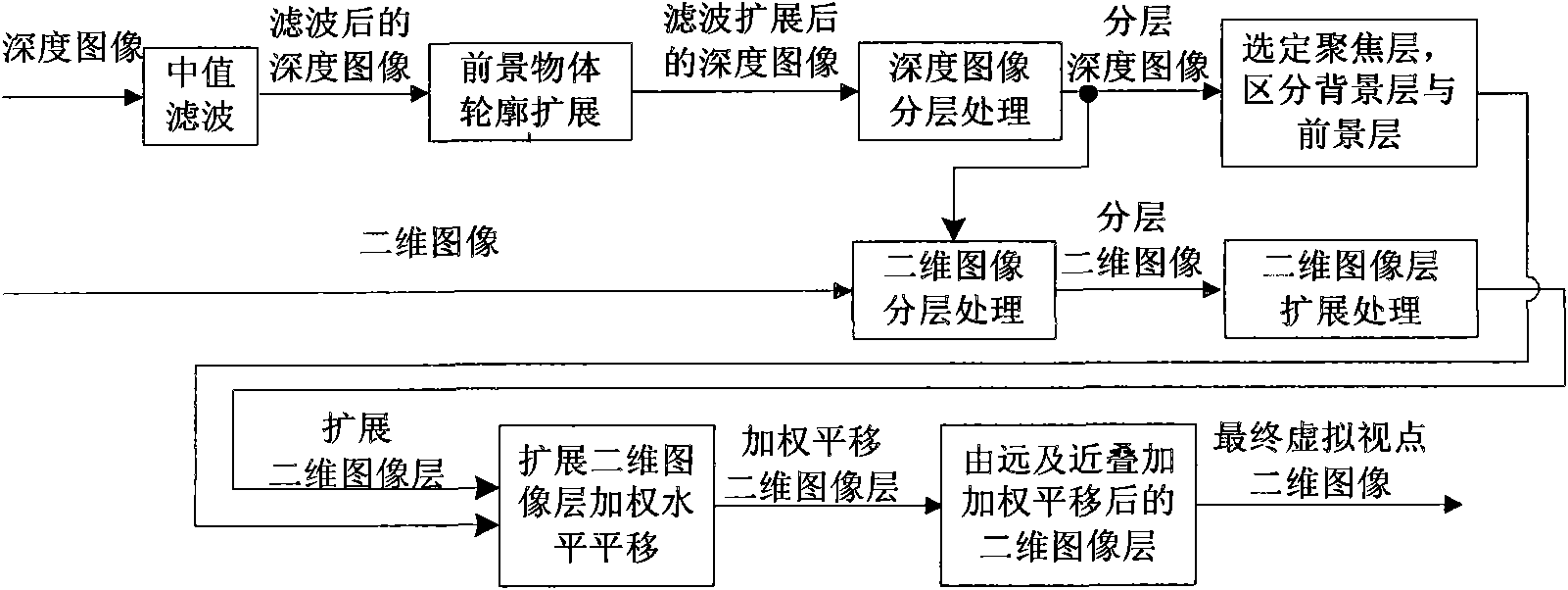
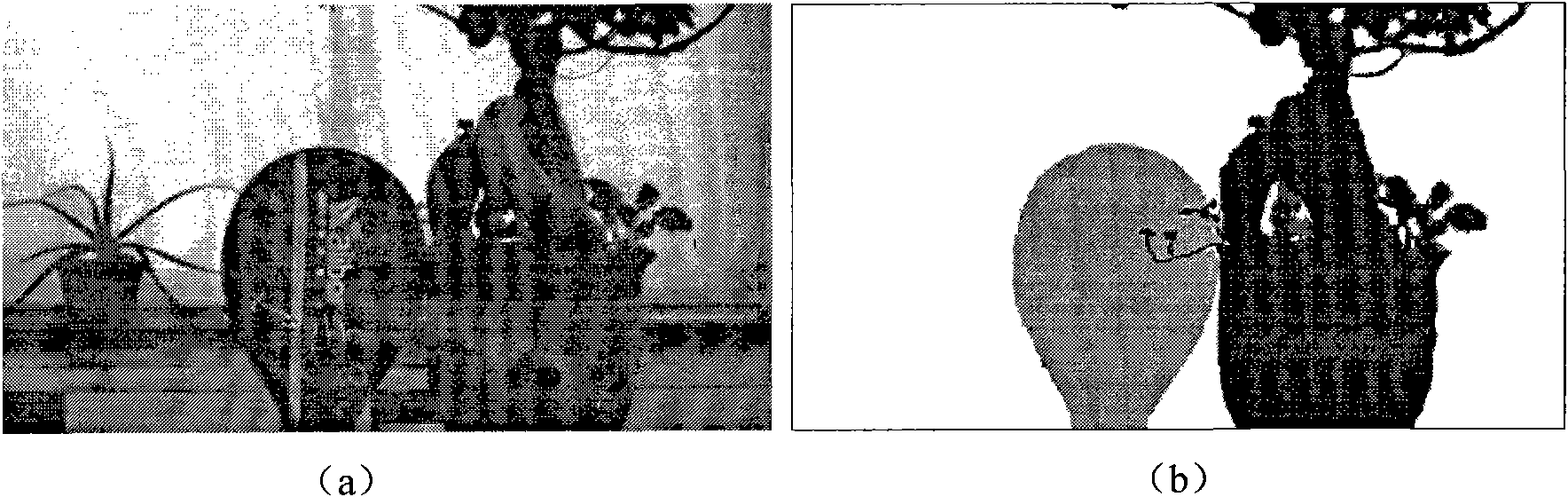
Method for generating virtual multi-viewpoint images based on depth image layering
ActiveCN101902657ANot easy to getImprove fault tolerance2D-image generationSteroscopic systemsParallaxTranslation algorithm
The invention discloses a method for generating virtual multi-viewpoint images based on depth image layering, which comprises the following steps: (1) preprocessing depth images to be processed; (2) layering the preprocessed depth images so as to obtain layered depth images; (3) selecting depth layers focused by camera arrays, and determining prospect layers and background layers; (4) layering two dimensional images to be processed so as to obtain layered two dimensional images; (5) calculating valves of parallax errors corresponding to the two dimensional image layers corresponding to various depth layers; (6) expanding the layered two dimensional images so as to obtain expanded layered two dimensional images; (7) obtaining the virtual two-dimensional images of various virtual viewpoint positions by using a weighted level translation algorithm. By using the method of the invention, virtual multi-viewpoint images required by a multi-viewpoint auto-stereoscopic display system can be generated rapidly and effectively without parameters of a virtual multi-viewpoint camera array model, and the method has good fault-tolerant capacity to the input depth images.
Owner:万维显示科技(深圳)有限公司
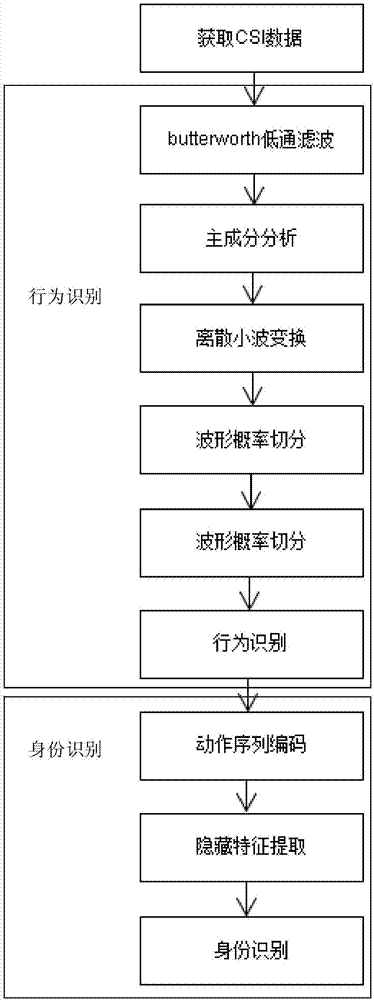
Active non-contact identity authentication method based on WiFi channel state information
ActiveCN106899968ALow costEasy accessSpeech analysisCharacter and pattern recognitionChannel state informationHuman body
The invention discloses an active non-contact identity authentication method based on the WiFi channel state information. The user body type, habits and other features contained in the human body behaviors are extracted through the WiFi channel state information. The first application of the WiFi channel state information on an identity recognition direction is utilized, the features are extracted by reasonably and effectively denoising the channel state information CSI in a WiFi signal extensively utilized at this stage; the waveform data related with the actions is segmented according to the extraction result; the user behavior recognition and the user identity related information (action direction, speed, user body type and others) extraction are further performed on the segmented data; and then the feature results are used for recognizing the user identity, and meanwhile, the reality of the whole mechanism is guaranteed.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
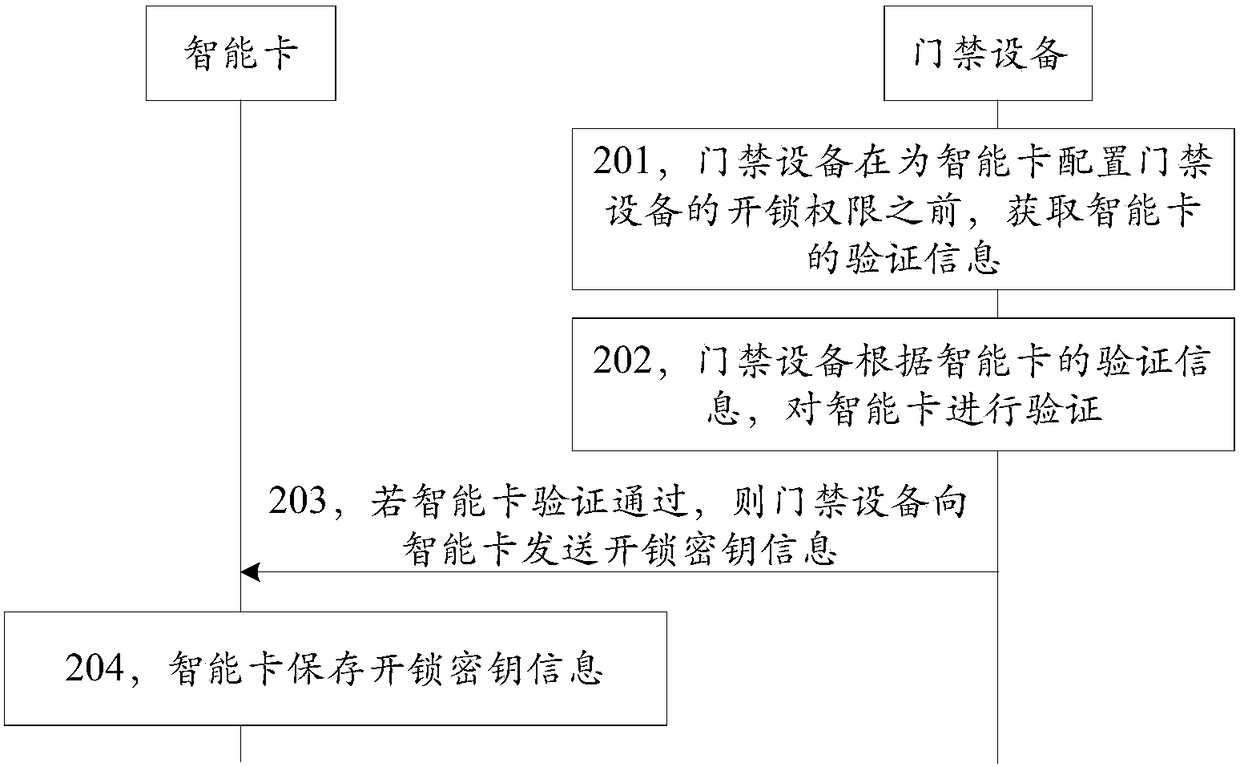
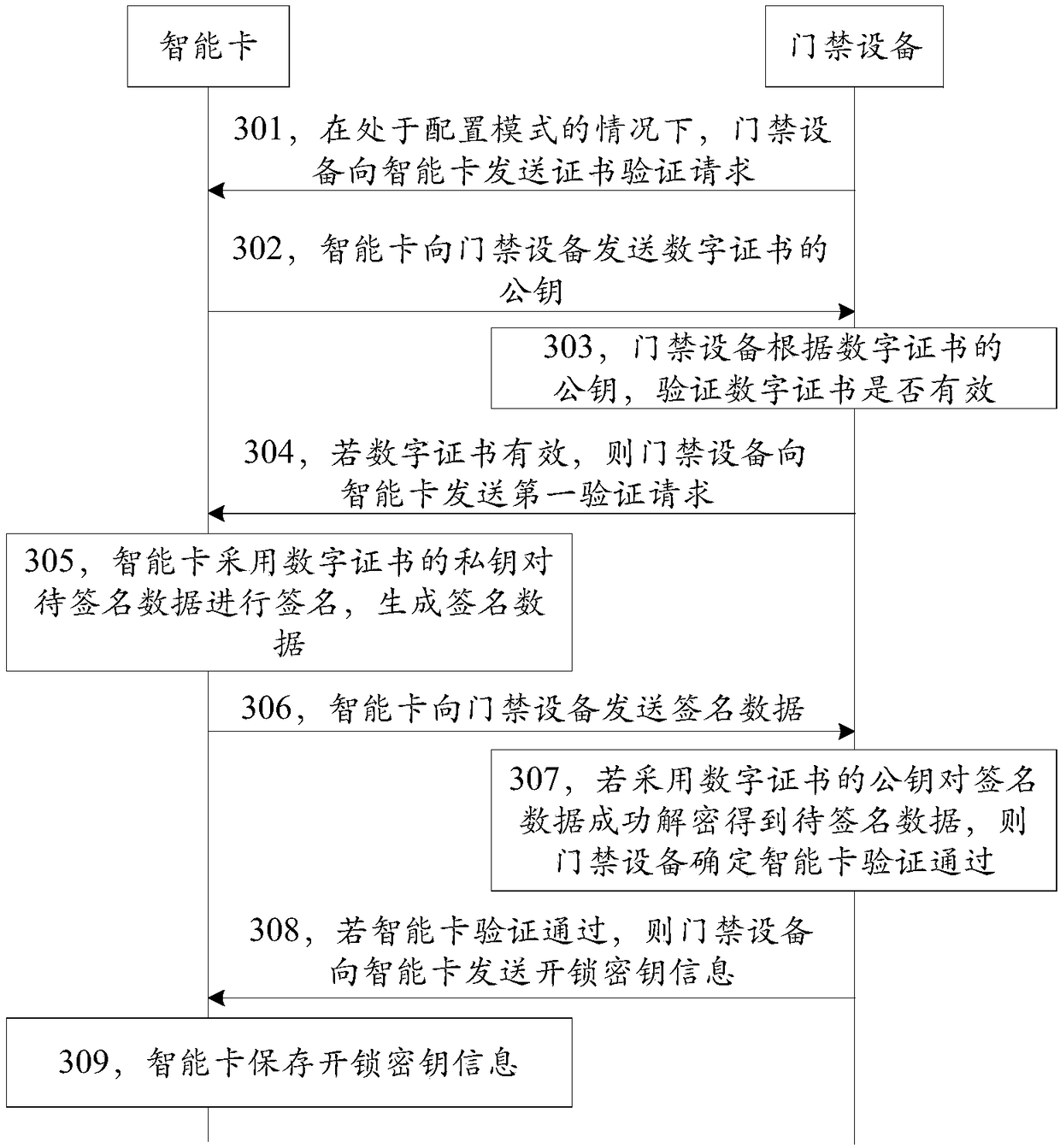
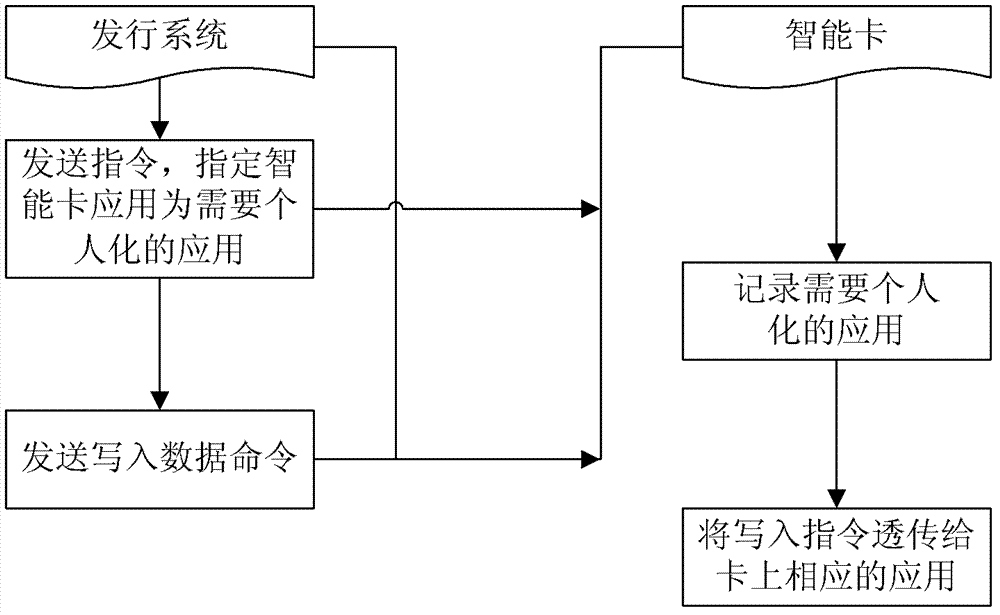
Smart card configuration method and device
ActiveCN108551455AEasy accessNot easy to getIndividual entry/exit registersTransmissionSmart cardControl equipment
The disclosure relates to a smart card configuration method and device. The method includes the following steps: before access control equipment configures an unlocking permission of the access control equipment for a smart card, acquiring verification information of the smart card; verifying the smart card according to the verification information of the smart card; and when the verification of the smart card is successful, sending unlocking key information to the smart card. In a technical scheme provided by the embodiment of the disclosure, before configuring the unlocking permission of theaccess control equipment for the smart card, the smart card is first verified, and then the unlocking key information is provided, the operation of configuring the unlocking permission for a counterfeit smart card can be avoided, and the security can be improved; and moreover, compared with the manner of recording a card number of the smart card in the access control equipment, the manner of configuring the unlocking permission for the smart card by distributing the unlocking key information to the smart card is more secure and reliable.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
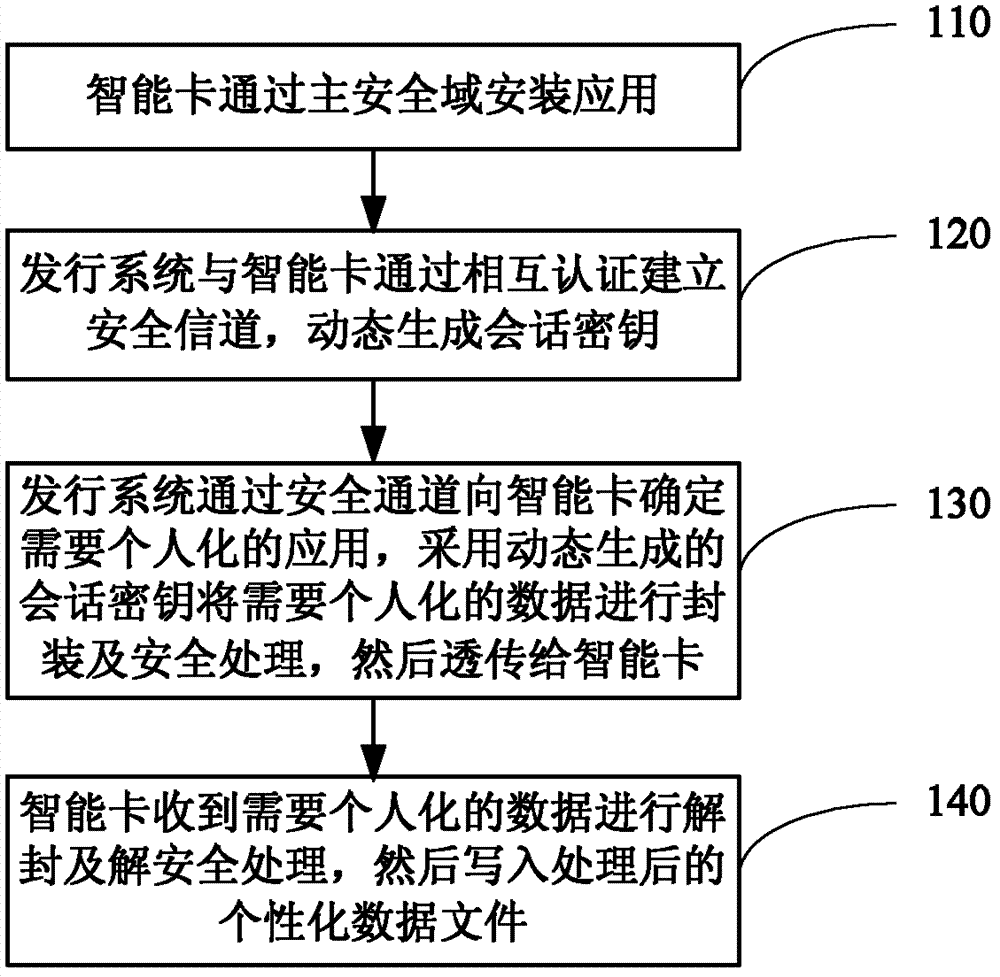
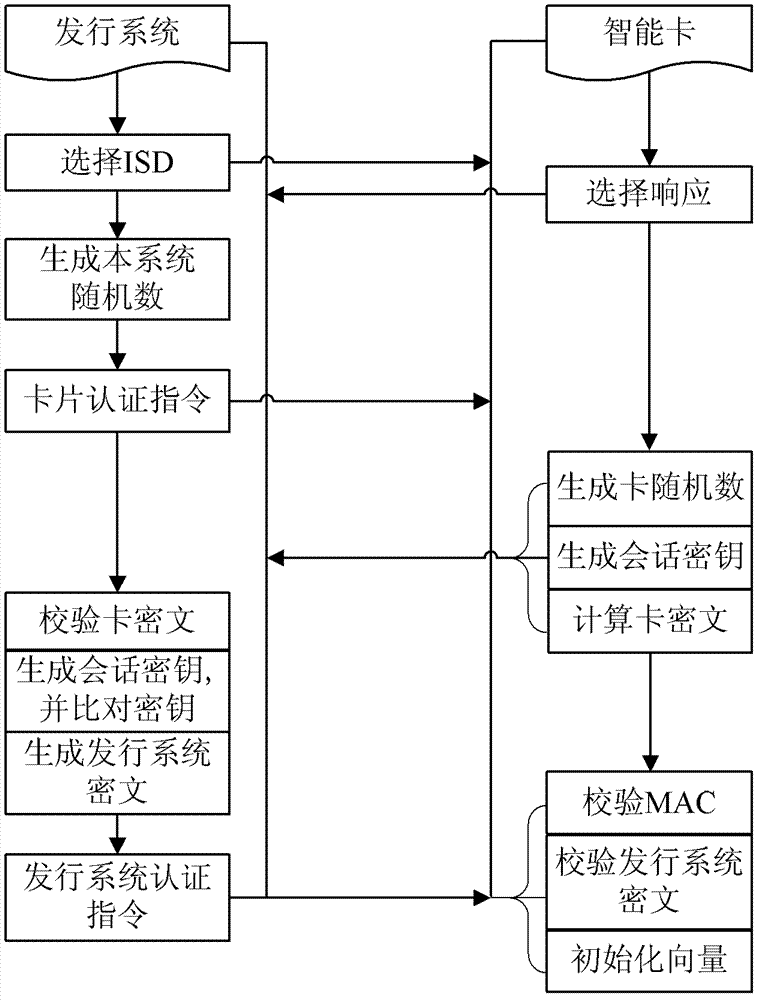
Method and system for realizing distribution of smart cards
ActiveCN102711101AImprove securityGuaranteed confidentialitySecurity arrangementDistribution systemSecurity domain
The invention provides a method and a system for realizing distribution of smart cards. The method comprises the following steps that: the smart cards are installed with applications by virtue of a main security domain; and a distribution system establishes a secure channel with the smart cards through mutual authentication, and a session key is dynamically generated. According to the invention, a mutual authentication process is carried out between the distribution system and the smart cards, and the session key is generated in a dispersed manner in the process by adopting a random number and is difficult to obtain, thus safety is good. By adopting a method that sensitive data is encrypted, security, completeness and safety of the sensitive data are guaranteed. By combining diversified data encryption and security technologies, a password is difficult to break, thus safety when the smart card applies individual data in a smart card distribution process can be guaranteed.
Owner:DATANG MICROELECTRONICS TECH CO LTD
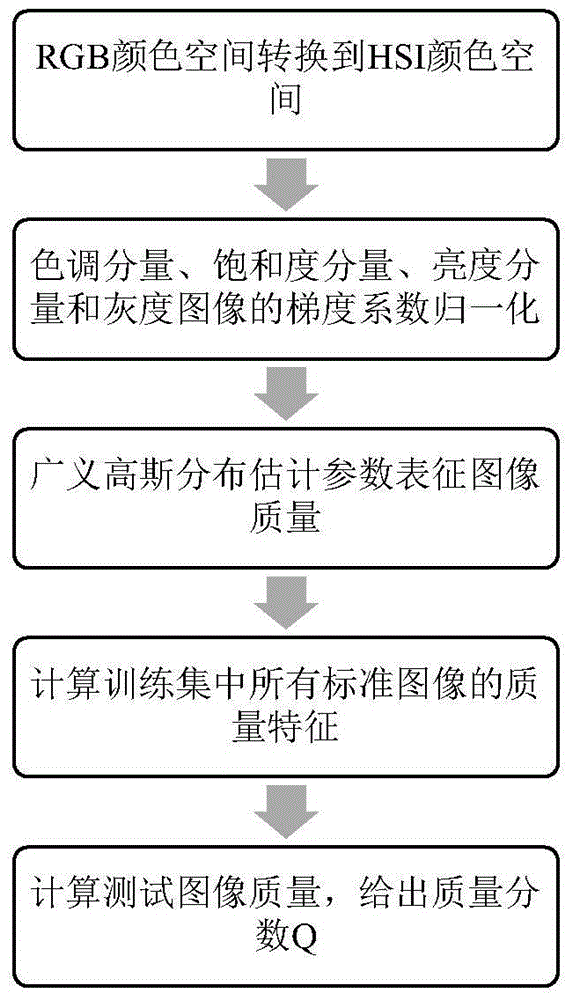
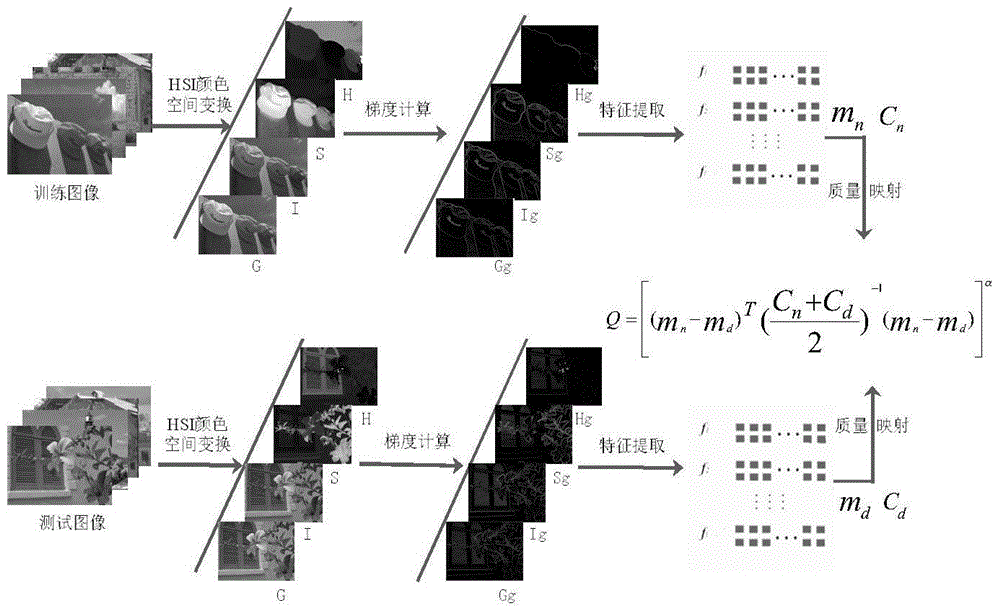
Shot image quality evaluation method based on visual perception
ActiveCN105741328AIn line with the actual distortion processImprove performanceImage analysisCharacter and pattern recognitionComparative testImaging quality
The invention discloses a shot image quality evaluation method based on visual perception, and mainly aims to solve the problem that the conventional image quality evaluation method is of poor performance for quality evaluation of shot images. The method comprises the following steps: shifting a standard image to an HIS color space; working out the gradient coefficient of the standard image, calculating the hue component, saturation component and brightness component of the standard image and the gradient coefficient of a gray image, and normalizing the gradient coefficients; representing the image quality with estimated parameters; carrying out model training, and calculating the quality characteristic of all standard images in a training set; and comparing the difference between a test image and the standard images in quality characteristic to get the quality score of the test image. The method is simple in calculation. Experimental results show that the test result obtained by the method is highly consistent with that of subjective quality evaluation, and the method has better evaluation performance than the existing image quality evaluation method and has strong practical value.
Owner:XIDIAN UNIV
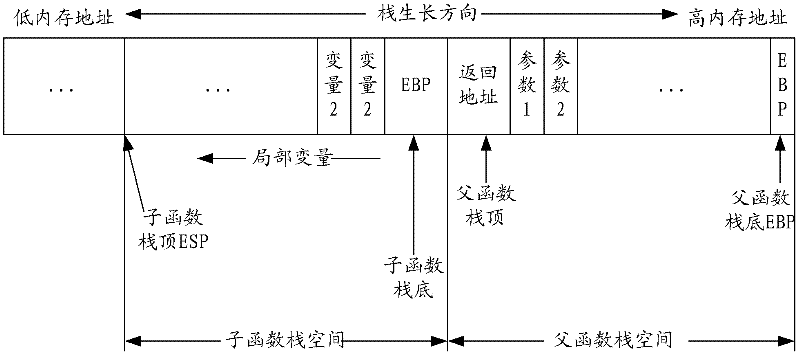
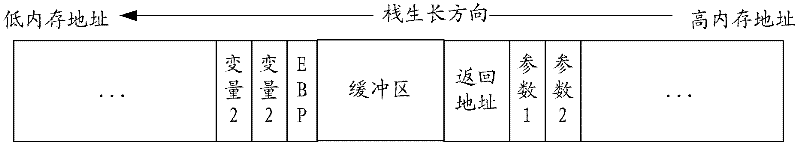
A stack overflow protection method and device
InactiveCN102298677AImprove protectionEasy to getPlatform integrity maintainanceRandom stringStack overflow
The invention provides a stack overflow protection method, by inserting a buffer into the stack, and filling the buffer with filling characters in the format of "fixed character string + random character string" or "random character string+fixed character string" String, and check the filling value in the buffer when the stack is released, which solves the problem of poor defense against stack overflow vulnerabilities, thereby reducing the risk of attackers using stack overflow vulnerabilities to damage the system. The invention also includes a stack overflow protection device.
Owner:RAISECOM TECH
Instant messaging method and system
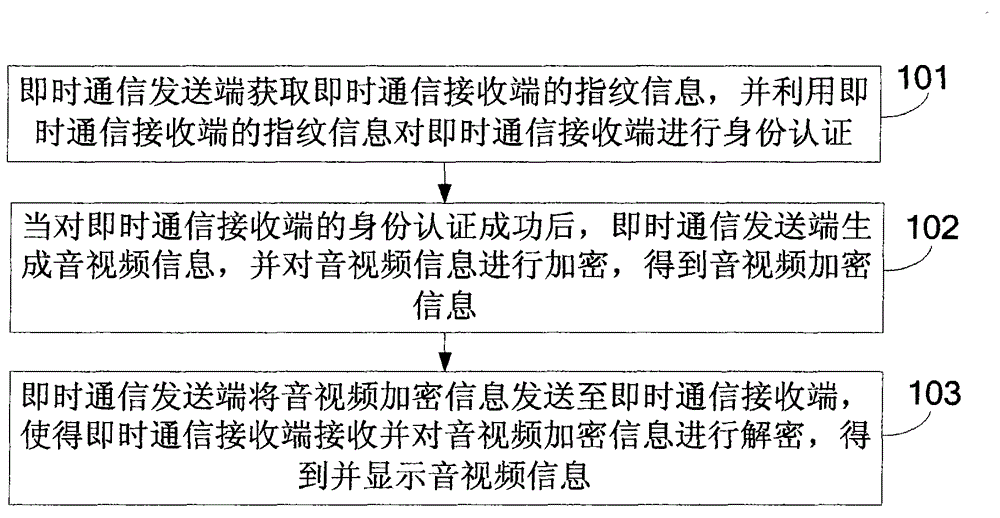
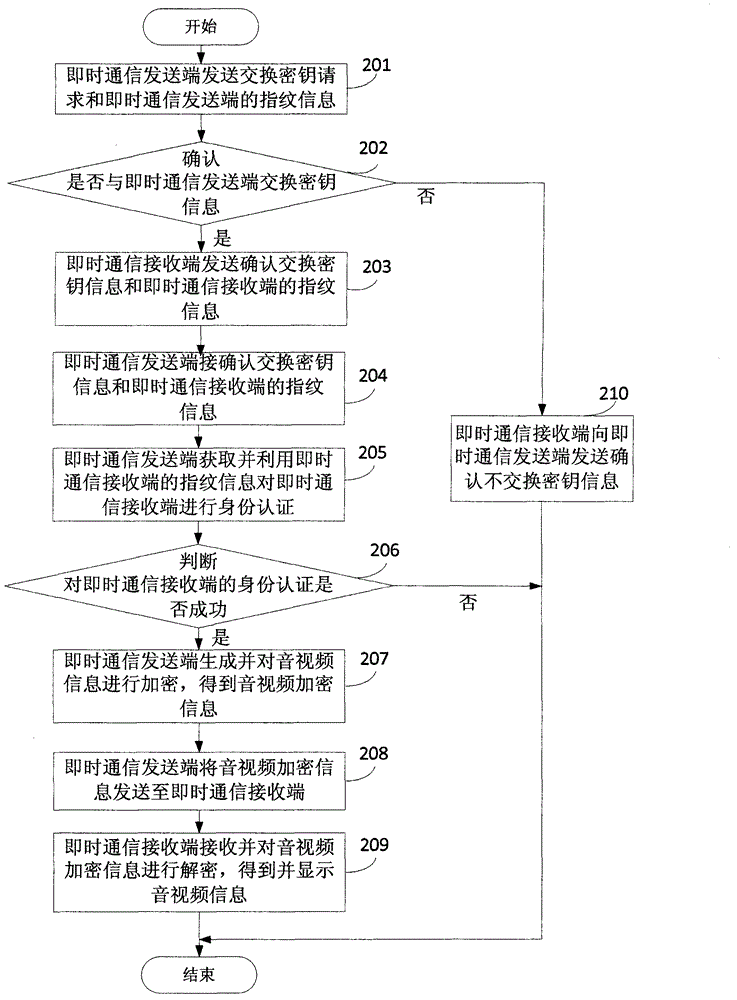
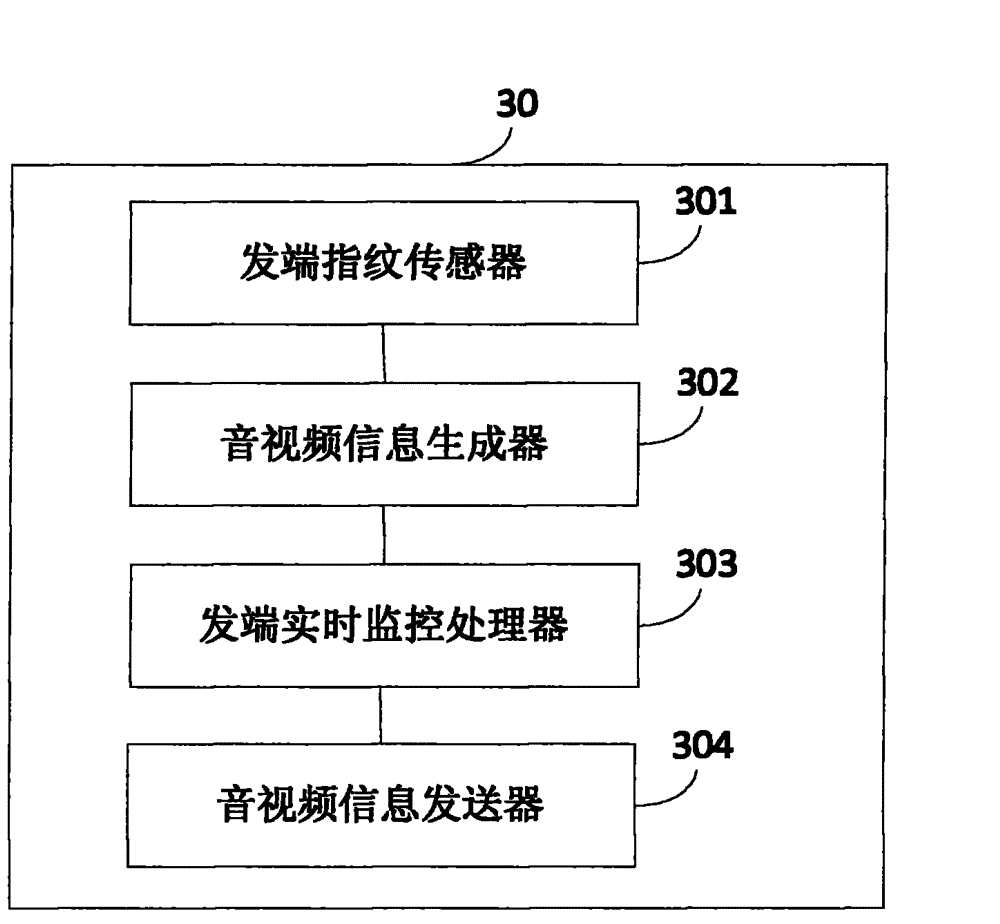
InactiveCN102916869ANot easy to getPrivacy protectionData switching networksInstant messagingAuthentication
The invention discloses an instant messaging method and an instant messaging system, belonging to the technical field of communications. The instant messaging method comprises the steps that an instant message sending end acquires a fingerprint information of an instant message receiving end and authenticates the identity of the instant message receiving end according to the fingerprint information of the instant message receiving end; after successful authentication to the identity of the instant message receiving end, the instant message sending end generates audio / video information and encrypts the audio / video information to obtain the encrypted audio / video information; the instant message sending end sends the encrypted audio / video information to the instant message receiving end; and the instant message receiving end receives the encrypted audio / video information, decrypts the encrypted audio / video information to obtain the audio / video information and displays the audio / video information. The instant messaging system comprises the instant message sending end. According to the instant messaging method and the instant messaging system, the privacy of instant messaging information such as audios and videos can be well protected, and the security is improved.
Owner:WWTT TECH CHINA
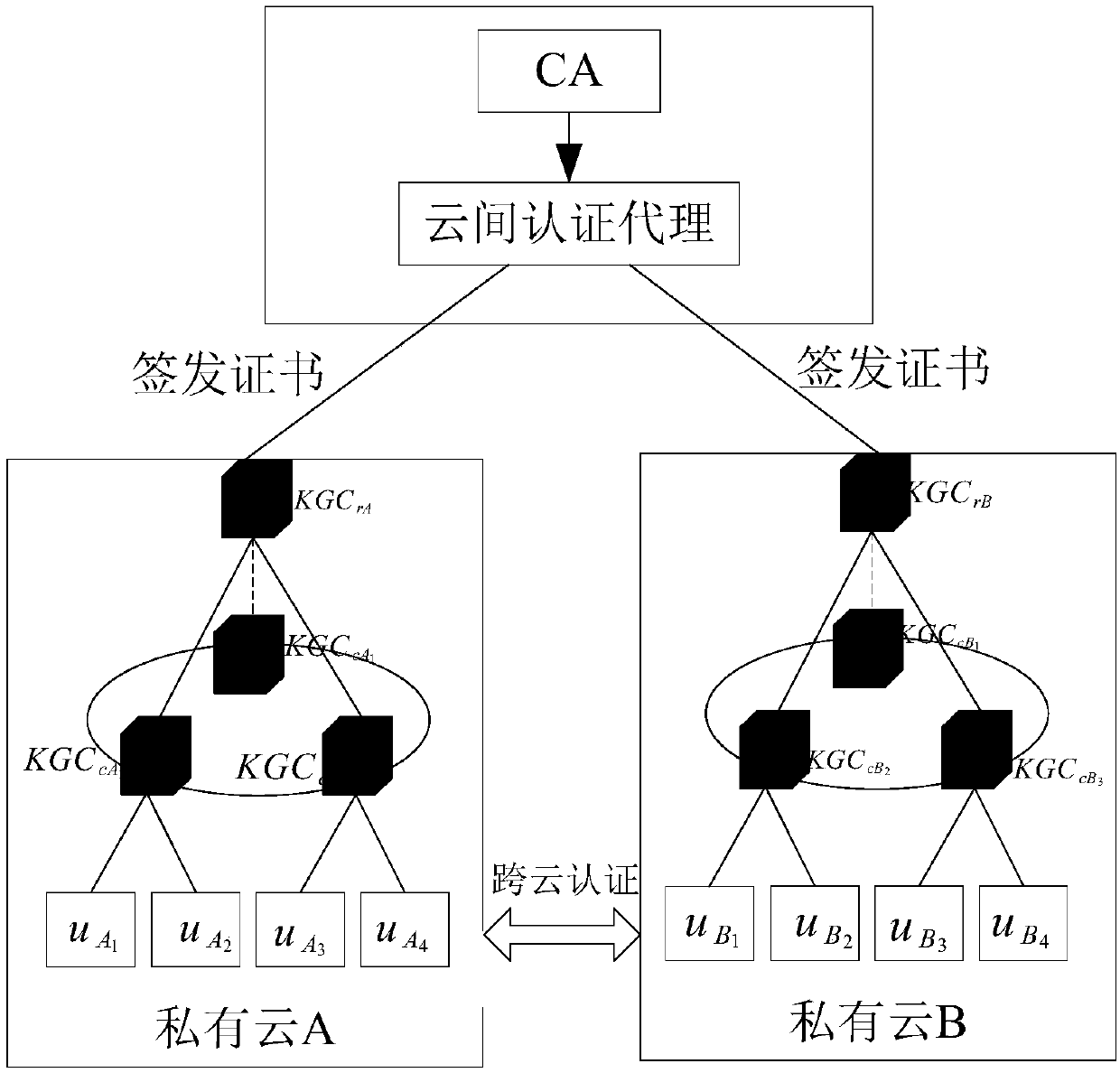
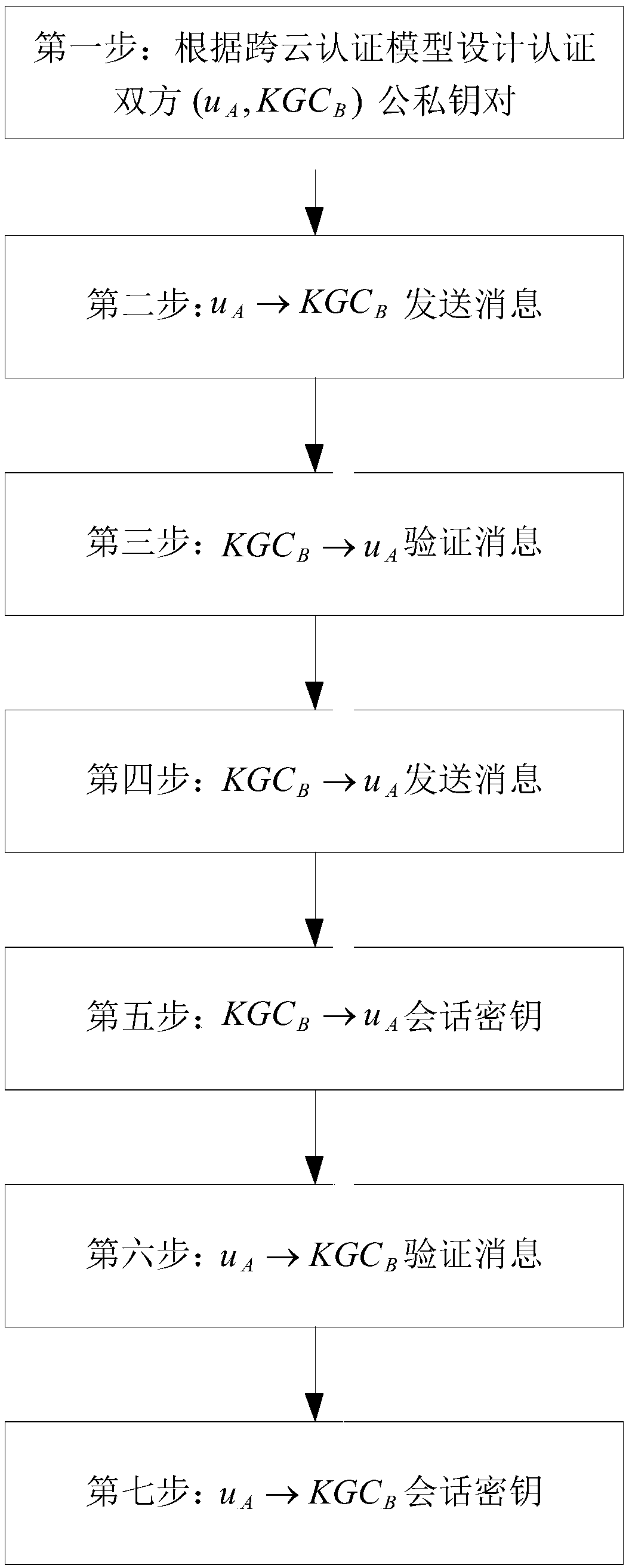
Cross-cloud security certification system and method based on identifier
ActiveCN108667616ANot easy to attackAvoid safety hazardsKey distribution for secure communicationPublic key for secure communicationRound complexityComputation complexity
The invention discloses a cross-cloud security certification system and a cross-cloud security certification method based on an identifier, in order to mainly solve the problem that cloud service providers within cloud domains securely manage privacy data of users. The cross-cloud security certification system introduces a layered identifier model and adopts a shared key ring structure, so that identity identifier of the user is unique; the user can get rid of a series of complicated certificate operations, thereby expanding a large-scale cloud network environment. The cross-cloud security certification method comprises the steps of: designing public and private key pairs for the users and the cloud service providers respectively by using the cross-cloud security certification system; sending and verifying messages; and performing key agreement to achieve identifier certification of both certification sides. The cross-cloud security certification system and the cross-cloud security certification method of the invention have the beneficial effects that: a cross-cloud certification model is built and a certificateless key agreement protocol is adopted, each link has safety protection, thus security and reliability of the whole system can be ensured; in addition, a computation complexity is low, thus certification and secure access requirements on the condition that the users in acloud environment respectively belong to different cloud domains can be met, and a practical application requirement that only one-time certification is needed for different cloud domains also can bemet.
Owner:XIDIAN UNIV
Artificial cultivating method for golden mushroom
The present invention relates to artificial cultivating technology for golden mushroom, and is especially artificial golden mushroom cultivating method. The method includes seed screening and preparation, compounding culture medium, bottling or bagging, high temperature sterilizing, cooling, inoculating seed and culturing. The method has culture medium comprising sawdust and rice bran in the weight ratio of 7 / 3 to 7.5 / 2.5, seed inoculation in no-bacteria ventilating operation stage, indoor air sterilization with 75 % alcohol solution, and the culture process at 14-16 deg.c and sterilizing condition for 21-23 days. The culture medicine of the present invention is easy to obtain and harmless to human body.
Owner:FUMAO EDIBLE MUSHROOM SHANGHAI
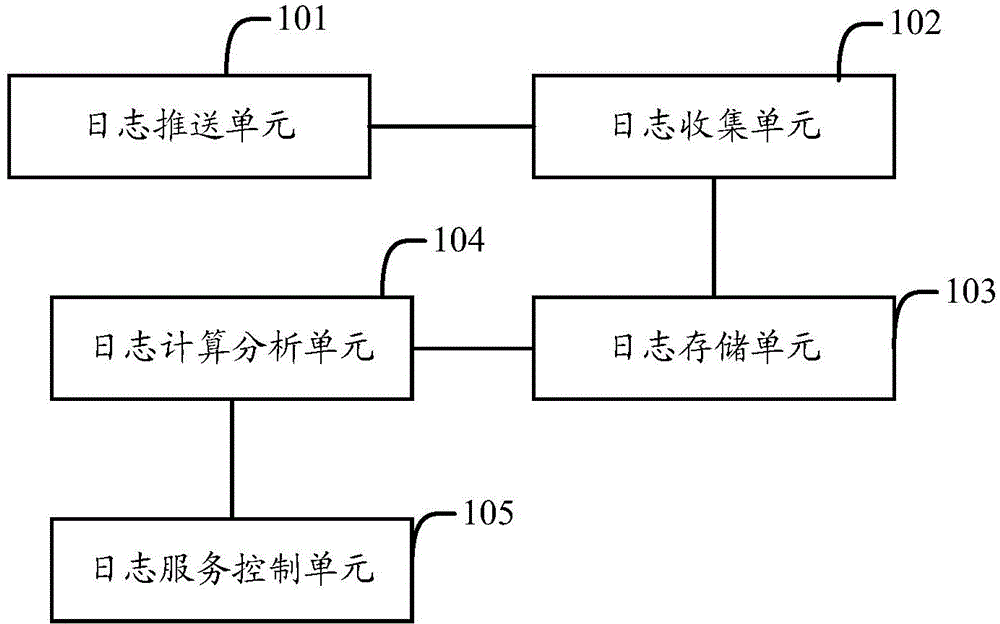
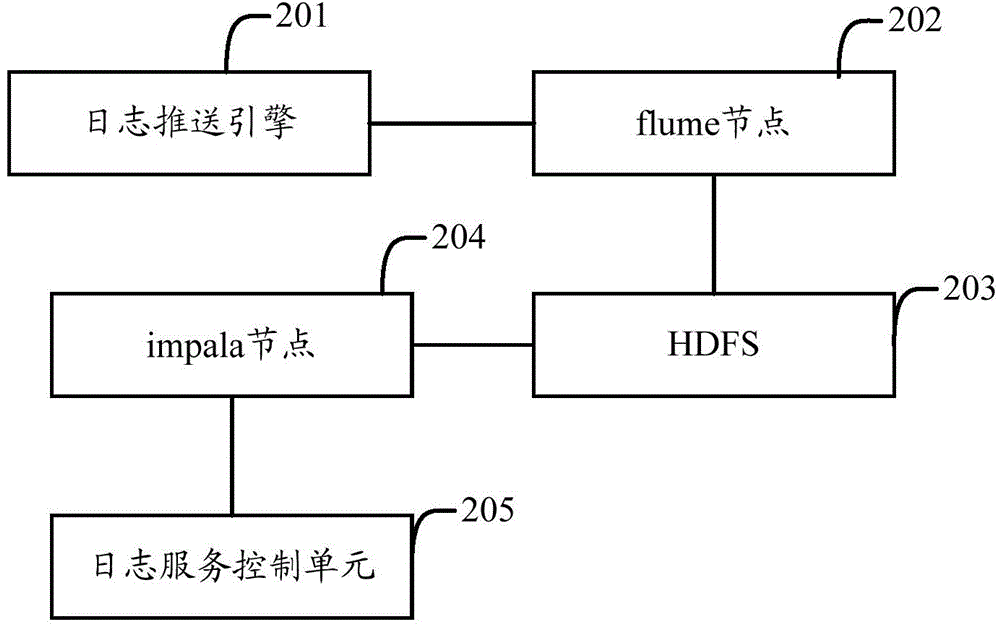
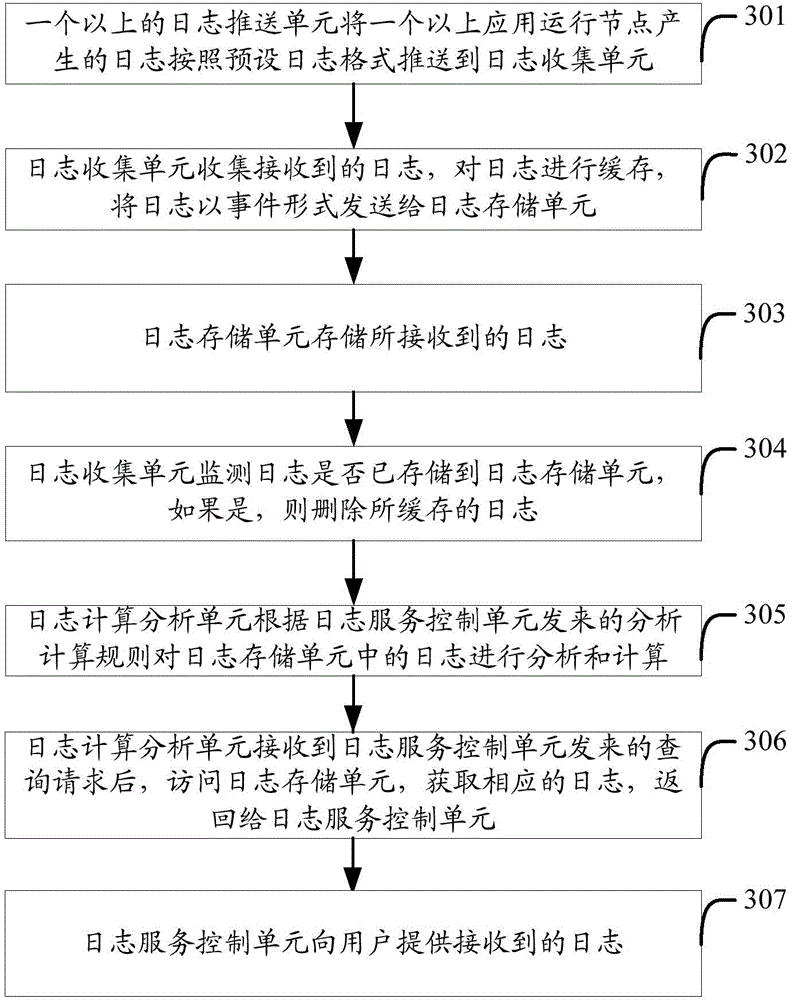
Log management system and implementation method
InactiveCN104579777ARealize unified collectionSolve the problem of decentralized managementData switching networksLog managementService control
The invention provides a log management system and an implementation method. The system comprises one or more log pushing units, a log collecting unit, a log calculation and analysis unit and a log service control unit, wherein the log pushing unit pushes logs generated by one or more application operation nodes to the log collecting unit; the log collecting unit is used for collecting received logs, caching the logs, sending the logs to a log storage unit in an event form and monitoring whether the logs have been stored in the log storage unit, and if the logs have been stored in the log storage unit, the cached logs are deleted; the log calculation and analysis unit is used for analyzing and calculating the logs stored in the log storage unit according to analysis and computation rules, having access to the log storage unit after receiving an inquiry request sent by the log service control unit, obtaining a corresponding log and returning the corresponding log to the log service control unit; the log service control unit sends the analysis and computation rules to the log calculation and analysis unit, sends the inquiry request and provides the received logs for users. Problems generated by decentralized management of logs can be solved according to the log management system and the implementation method.
Owner:INSPUR SOFTWARE CO LTD
Seal lock and encryption identification method, device and system based on same
InactiveCN101949237AEasy accessIncrease the difficultyBuilding locksUser identity/authority verificationComputer scienceEncryption
The embodiment of the invention provides a seal lock and encryption identification method, device and system based on the same. The seal lock is provided with a lock body, wherein the lock body is provided with a seal lock code in an exposed state and a verification code in a hidden state, wherein the verification code corresponds to the seal lock code and is obtained by physically damaging the seal lock. Because the verification code in the hidden state is arranged on the lock body of the seal lock, the verification code is not easy to be acquired and can be obtained by physically damaging the lock body, but the lock body of the seal lock is not recovered after physically damaged, and is easy to expose a trace of being maliciously unsealed by an illegal unsealing person, which is beneficial to the immediate finding and prevention of abnormal unsealing behavior, increases the difficulty of copying and counterfeiting the seal lock by the illegal unsealing person, improves the safety of goods, property or facilities during the seal or transportation, thus the seal lock can being widely applied to interregional and transnational trades.
Owner:刘玉来
Taxol nanosuspension and preparation method thereof
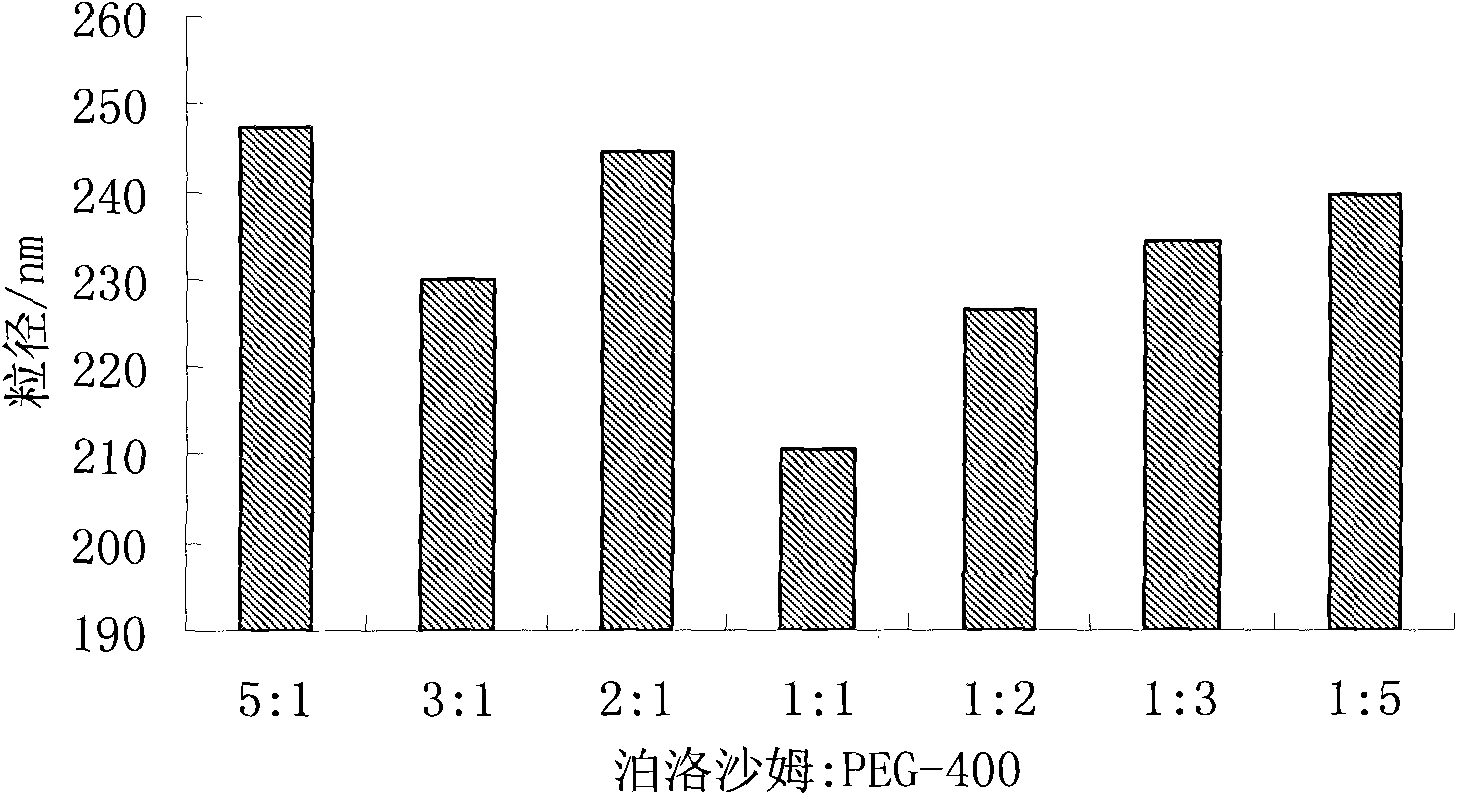
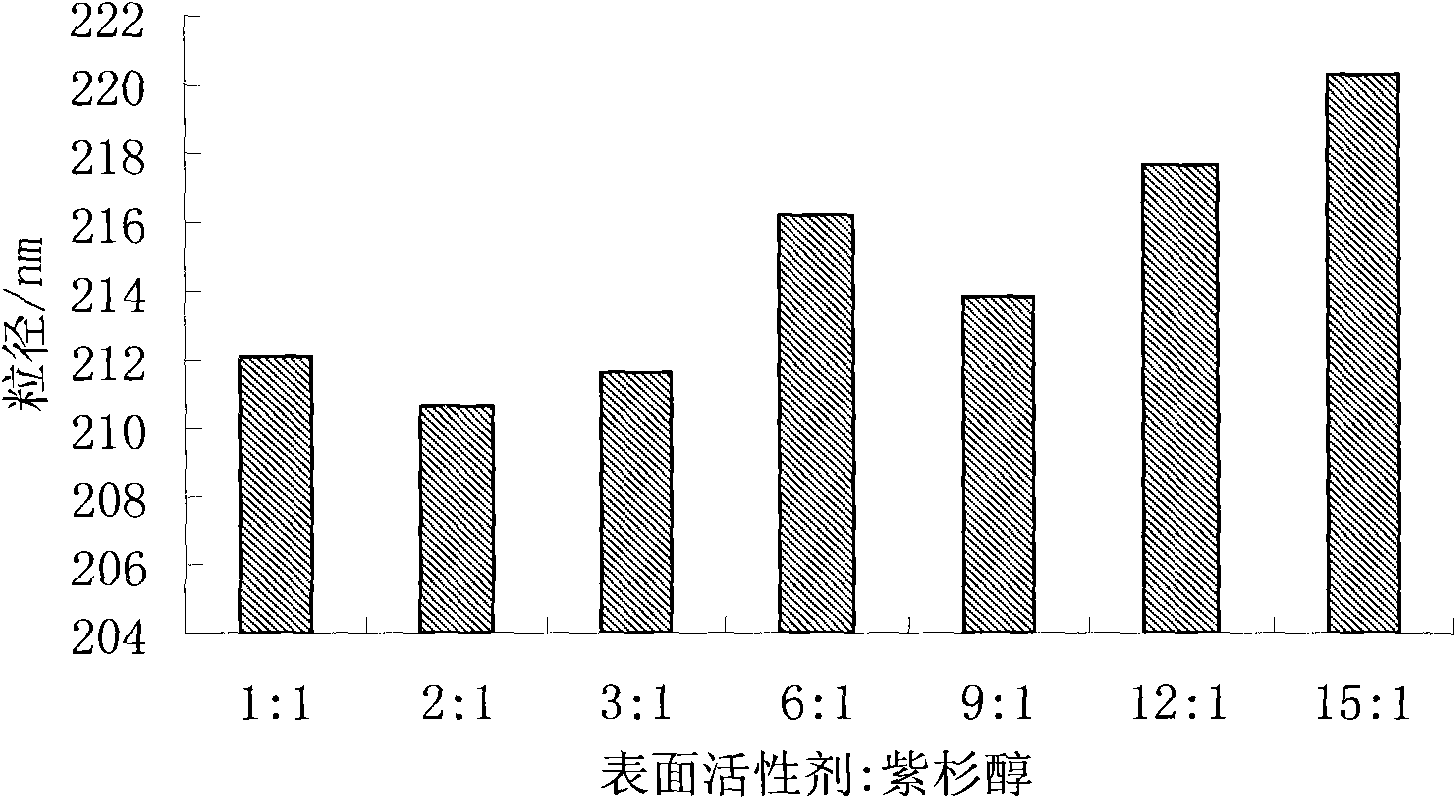
ActiveCN101843582AHomogeneous pressure dropReduce the number of cyclesOrganic active ingredientsSolution deliveryChemistryToxicity
The invention relates to the field of medicinal preparations, in particular to a taxol nanosuspension and a preparation method thereof. The taxol nanosuspension is characterized in that: a surfactant consists of poloxamer 188 and polyethylene glycol in a weight ratio of 1:1-1:3. According to the invention, the defects of low medicament loading rate, strong toxic or side effect, low stability, complex preparation process, high cost and the like in the conventional taxol preparation are overcome, and the technical breakthrough in the field is achieved; and the taxol nanosuspension has the advantages of increasing medicament content, reducing administration toxicity and production cost and improving the adaptability and compliance of a patient so as to realize clinical use.
Owner:南京百思福医药科技有限公司
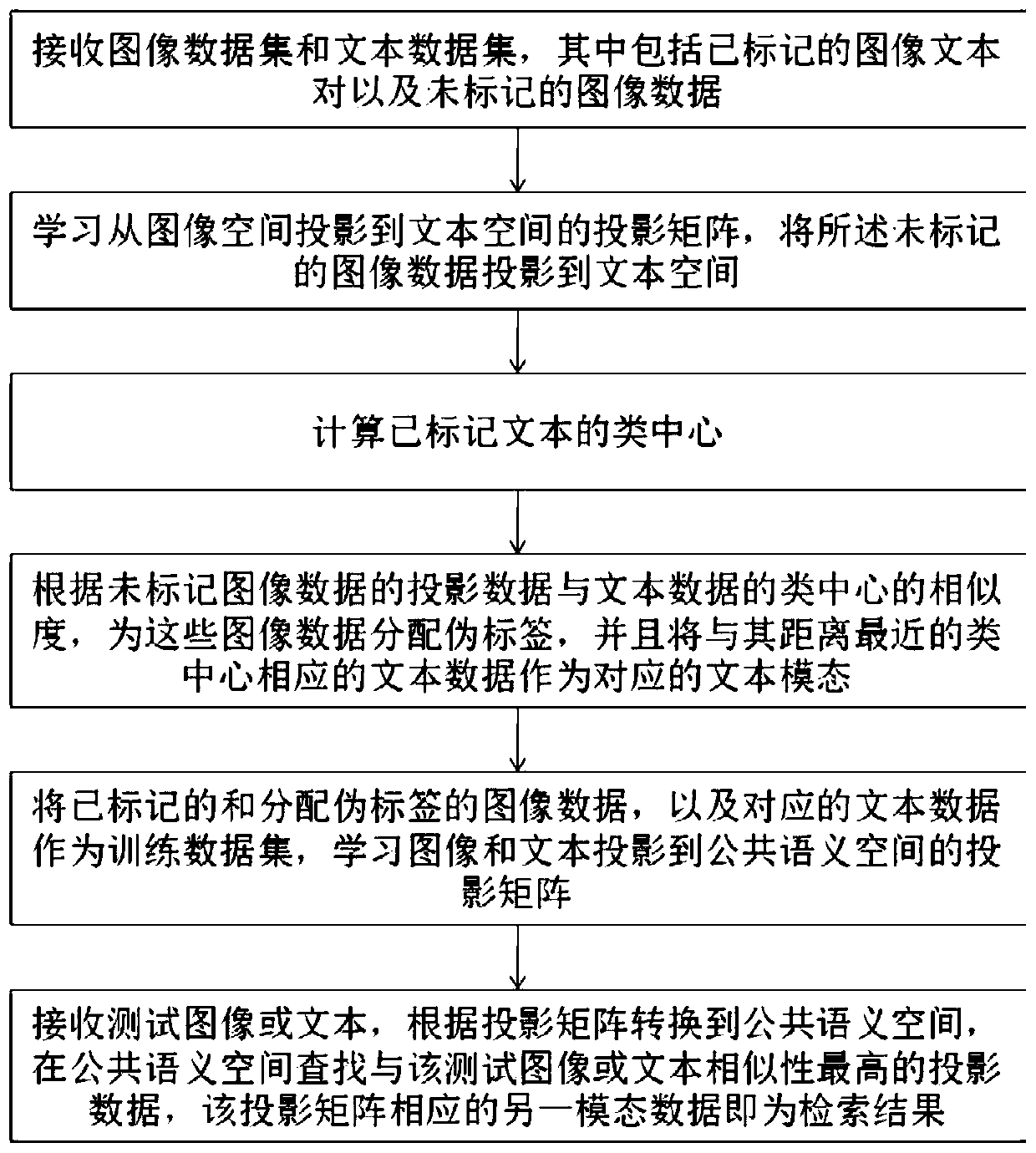
Cross-modal retrieval method and system based on pseudo label learning and semantic consistency
ActiveCN109784405AImprove retrieval performanceEasy accessCharacter and pattern recognitionNeural architecturesHat matrixData set
The invention discloses a cross-modal retrieval method and system based on pseudo label learning and semantic consistency, and the method comprises the steps: receiving an image data set and a text data set which comprise marked image text pairs and unmarked image data; Learning a projection matrix projected from the image space to the text space, and projecting the unmarked image data to the textspace; calculating the class center of the marked text; Distributing pseudo labels for the image data according to the similarity between the projection data of the unmarked image data and the classcenters of the text data, and taking the text data corresponding to the class center closest to the image data as a corresponding text mode; Taking the marked image data distributed with the pseudo tags and the corresponding text data as a training data set, and learning a projection matrix of images and texts projected to a public semantic space; Performing cross-modal retrieval. Unmarked data isintroduced into the training data set, and a more effective projection matrix can be obtained.
Owner:SHANDONG JIANZHU UNIV
High yield veiled lady seed preparing and cultivating process
InactiveCN101019491AEffective and strongWon't softenBio-organic fraction processingFungiHyphaHyphomycetes
The high yield veiled lady cultivar preparing and cultivating process includes compounding culture medium, bottling or bagging, sterilizing, inoculating, covering the mouth with cotton, culturing to obtain white hypha, eliminating the cotton cover after the hypha grows to 2-2.5 cm thickness and further culturing to obtain the veiled lady cultivar with high vitality, and further cultivating in fermented culture medium and through spraying herbicide, covering with fermented rice straw, etc. The present invention has greatly raised veiled lady yield.
Owner:张远富
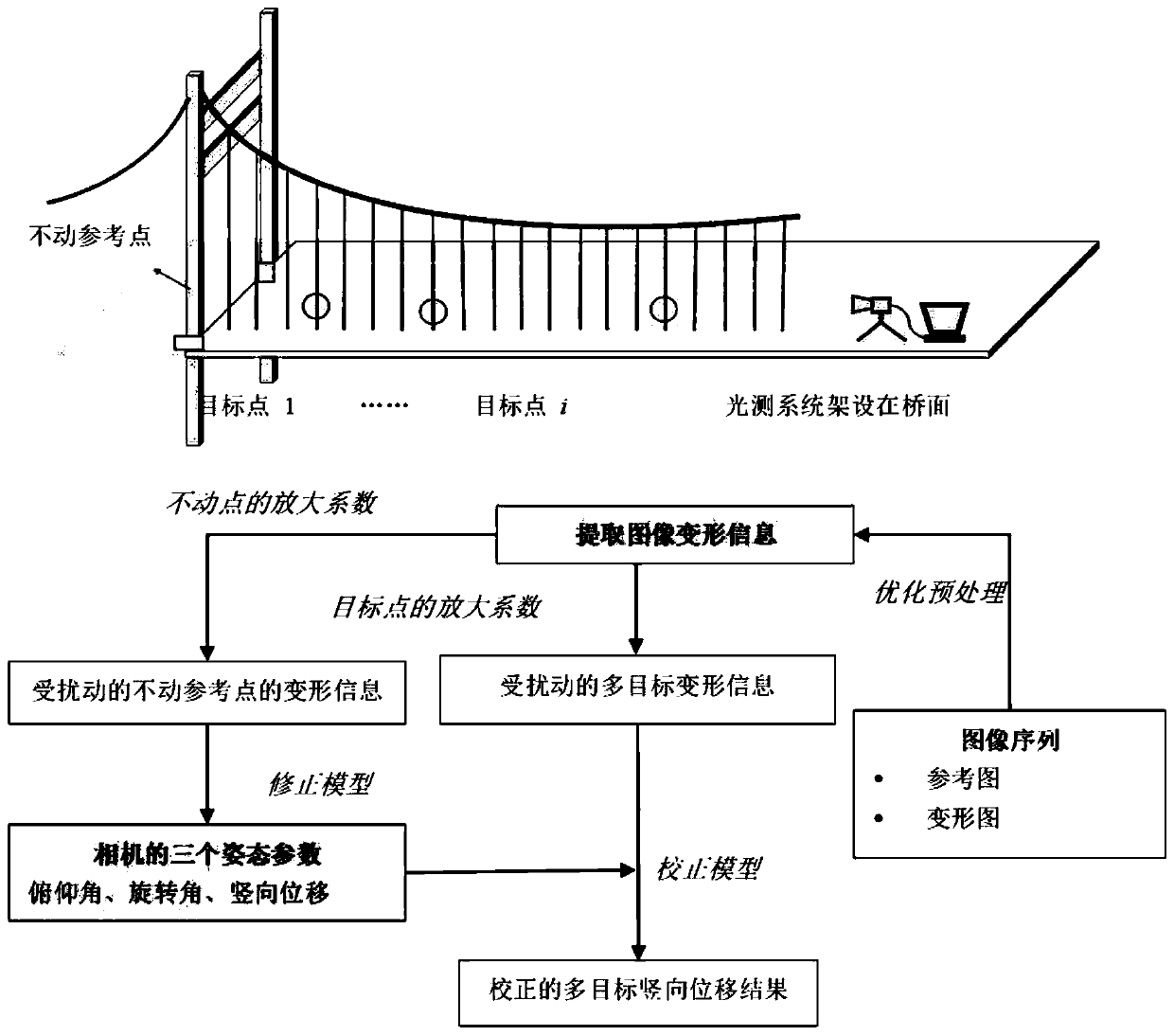
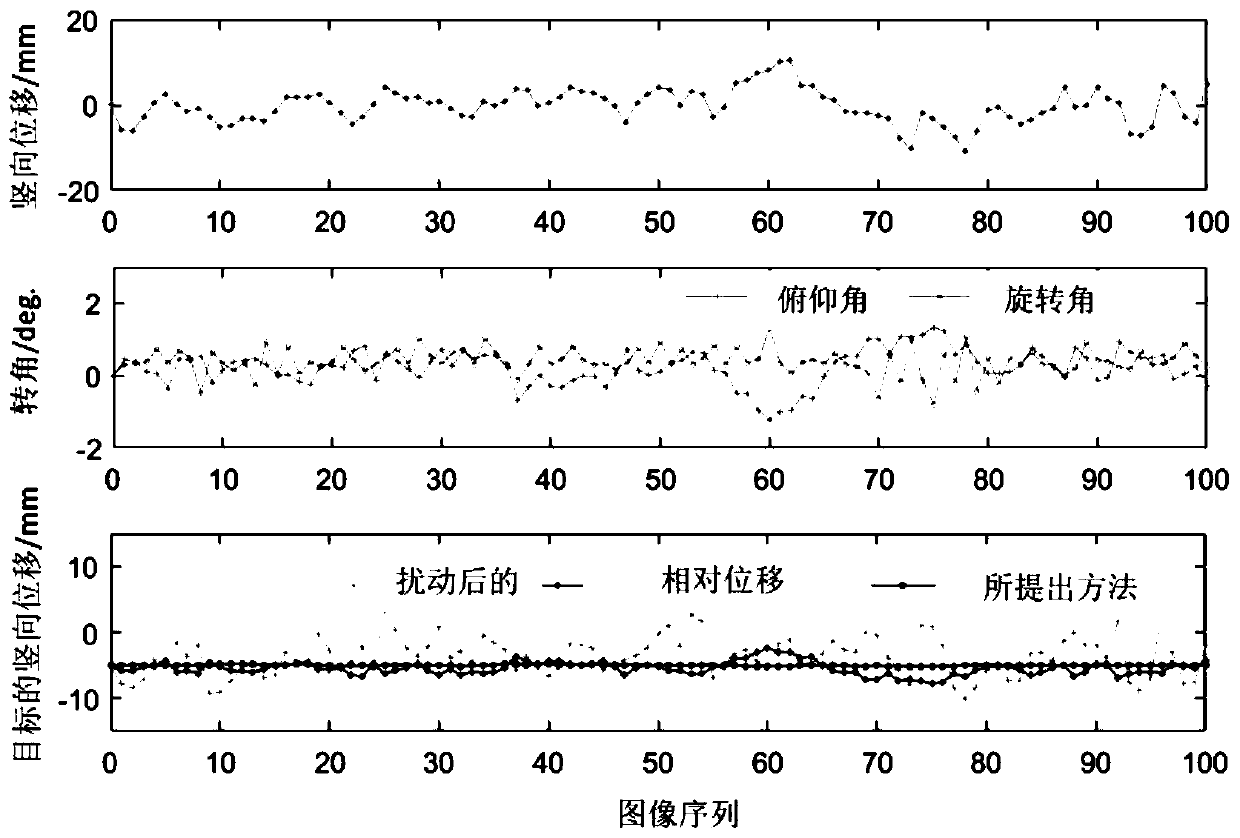
Large-span bridge multi-point deflection measurement method considering camera attitude change
ActiveCN111076880AImprove work efficiencyEasy to solveElasticity measurementComputer graphics (images)Deblurring
The invention discloses a large-span bridge multi-point deflection measurement method considering camera attitude change. According to the invention, aiming at a picture imaging problem, Wiener filtering deblurring on an image and detail improvement based on a multi-scale image are carried out, and a template size is increased when a digital image correlation method is used to calculate vertical displacement of the image so as to control matching precision. The method has certain engineering universality, and compared with a conventional method in which a camera is erected on the shore, more view fields are saved; the camera is erected on the bridge floor, the limitation of observing structures on the outer side of the bridge through an existing optical measurement method is broken through, and a target measurement point is easier to locate; and because the camera is erected on the bridge floor, known size parameters of multiple structures can be directly utilized, and scale calibration is more convenient and accurate.
Owner:SOUTHEAST UNIV
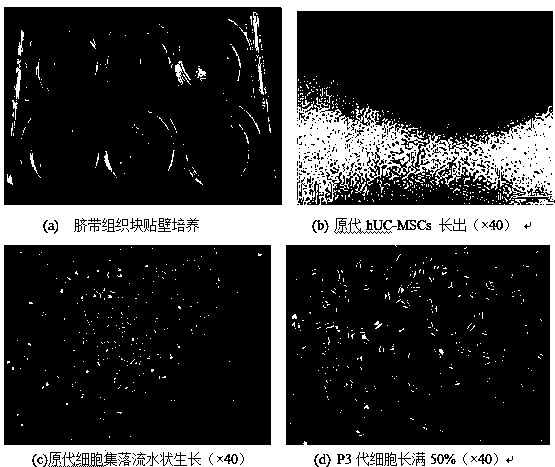
Method for in-vitro directional differentiation inducing of mesenchymal stem cell towards melanocyte
InactiveCN104232574AEasy to getLow immunogenicityArtificial cell constructsMammal material medical ingredientsMelanocyteStromal cell
The invention relates to a method for in-vitro directional differentiation inducing of a mesenchymal stem cell towards melanocyte, particularly relates to a method for in-vitro directional differentiation inducing of the mesenchymal stem cell with an umbilical cord source towards the melanocyte, and belongs to the technical field of biology. The mesenchymal stem cell with the umbilical cord source is cultivated by adopting an explants method, and then the mesenchymal stem cell with the umbilical cord source is identified, so as to determine the characteristics of the mesenchymal stem cell; a culture medium is induced to carry out in-vitro inducing differentiation to form the melanocyte by using improved melanine; and finally the cultivated melanocyte is identified. An ES cell source and a marrow or adipose tissue-derived stromal cell source are limited or not easy to obtain while the stem cell can be easily obtained from the umbilical cord, the immunogenicity is very low, and an individual difference is not easily generated, so that the method is suitable for large-scale clinical application, and the induced melanocyte can be applied to epichrosis leucasmus therapy.
Owner:AFFILIATED HOSPITAL OF JIANGSU UNIV
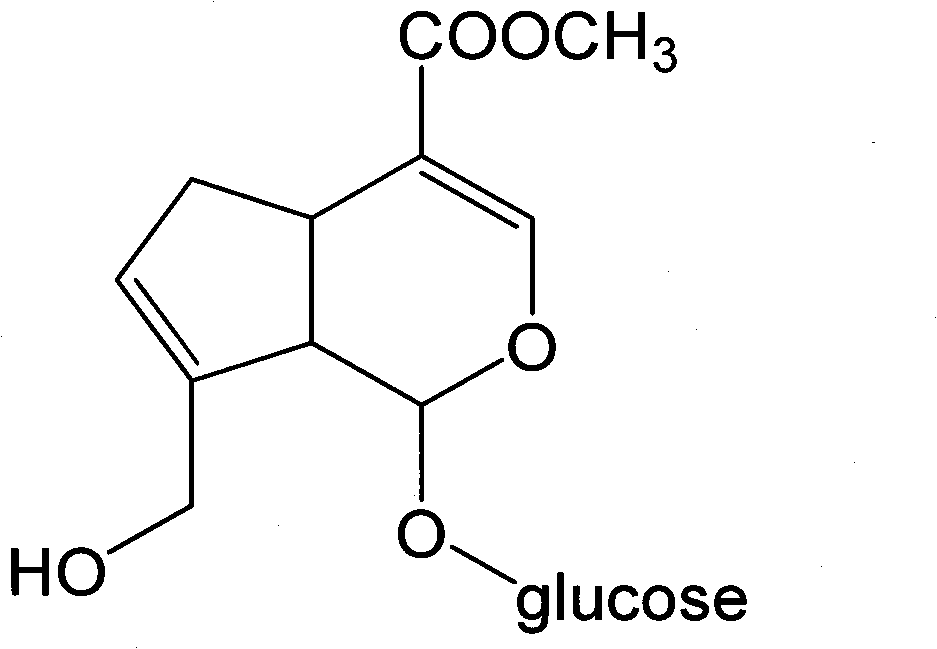
Method for preparing genipin
InactiveCN102146423AReduce supplyEasy to getChemical industryOn/in organic carrierSodium acetateDouble phase
The invention discloses a method for preparing genipin. In the invention, sodium alginate serving as a carrier and glutaraldehyde serving as a crosslinking agent to immobilize glycoside hydrolase, the immobilized glycoside hydrolase catalyzes the hydrolysis geniposide in a double-phase system consisting of acetic acid-sodium acetate buffer solution and ethyl acetate to convert the geniposide into the genipin, the ethyl acetate in the reaction solution is separated out, and white genipin crystalsare obtained by concentration and crystallization. In the invention, the glycoside hydrolase is immobilized before an enzymatic reaction, so the side reactions of the enzymatic reaction glycoside hydrolase and the genipin are reduced, the glycoside hydrolase can be recycled repeatedly, and the production cost is reduced; and the double-phase system used in the invention can extract the genipin to the ethyl acetate phase from a water phase in reaction, so the hydrolysis reaction of the genipin and the side reactions of the glycoside hydrolase and the genipin can be reduced, the yield of the genipin can be improved, the reaction is accelerated, and the separation and purification of the product is more easy.
Owner:SHANGHAI UNIV OF T C M
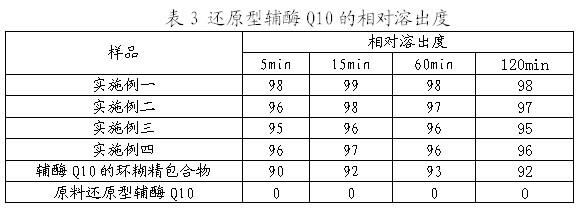
Hydrosoluble reduced enzyme Q10 composition and preparation method thereof
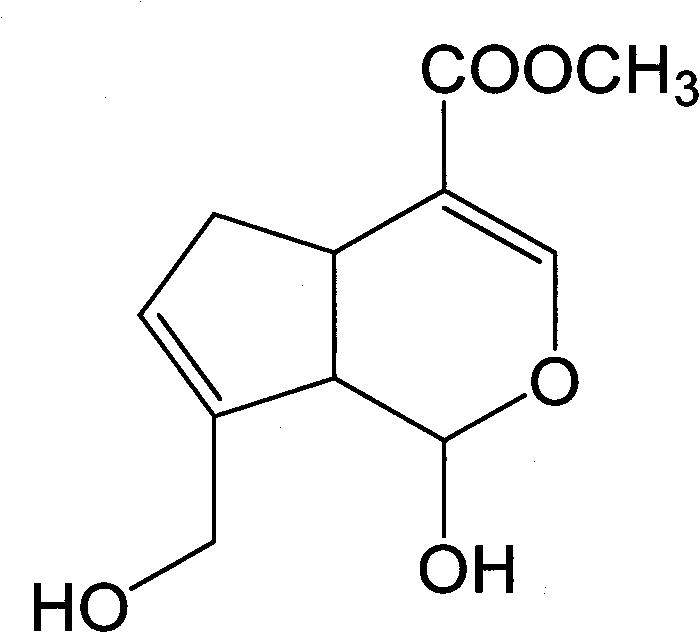
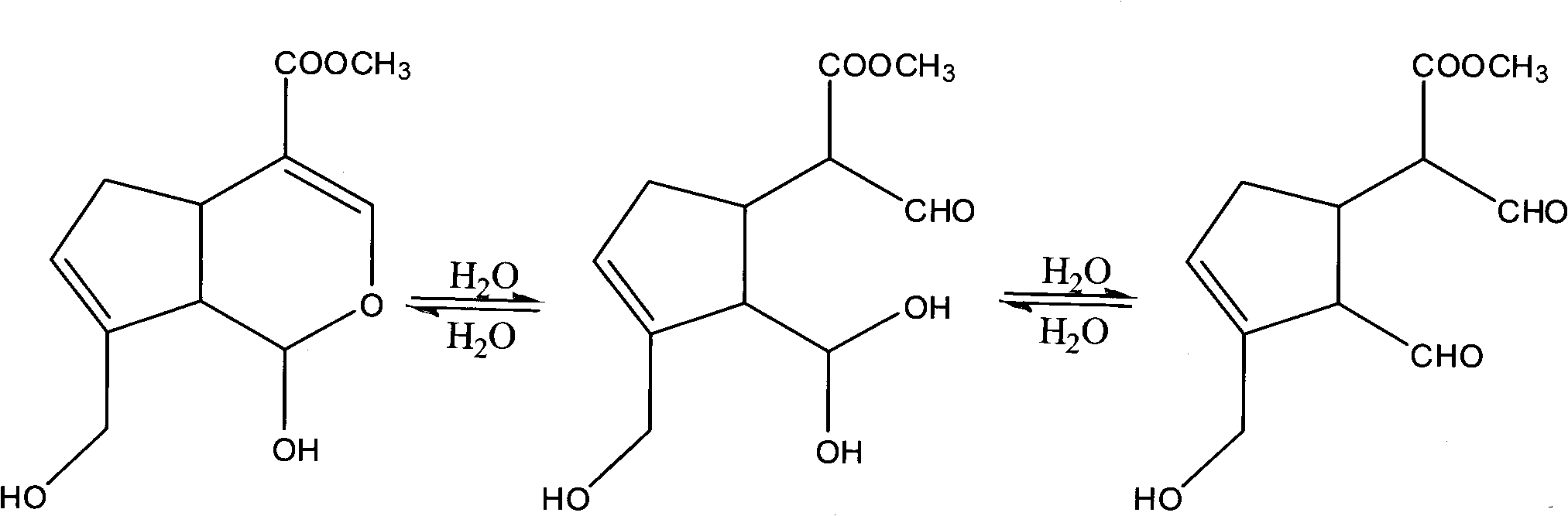
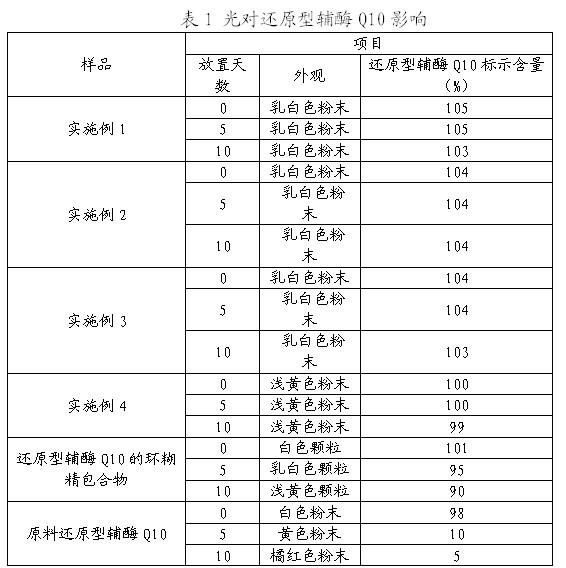
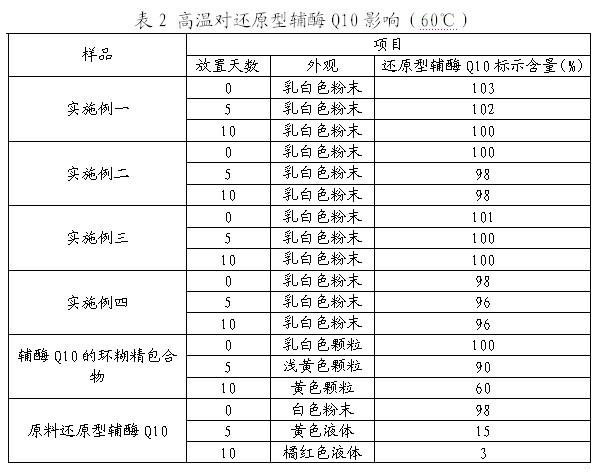
ActiveCN101966171AEasy to getSolve insolublePeptide/protein ingredientsHydroxy compound active ingredientsFructoseCarrageenan
The invention relates to a hydrosoluble reduced enzyme Q10 composition and a preparation method thereof, and provides a hydrosoluble reduced enzyme Q10 composition, which comprises raw materials and following mass components thereof: a reduced enzyme Q105-15, a hydrosoluble carrier 10-120, and an emulsifier 0.5-40; wherein the hydrosoluble carrier is one or more of maltose, CMC, gum rubber, soluble starch, lactose, fructose, sorbierite, mannitol, acacia and carrageenan; and the emulsifier is nonionic surfactant. The invention further provides the preparation method of the hydrosoluble reduced enzyme Q10 composition. In the method, the indissoluble reduced enzyme Q10 is mixed with the hydrosoluble carrier and the emulsifier to prepare the hydrosoluble reduced enzyme Q10 composition, advantages of an inclusion technology and a solid dispersion technology are synthesized, defects in the technologies are solved, a problem of slightly solubility of the reduced enzyme Q10 is solved, a series of tests shows that the reduced enzyme Q10 has water-solubility, high solubility, high dissolution rate, high stability and high active substance content.
Owner:杭州华东医药集团康润制药有限公司
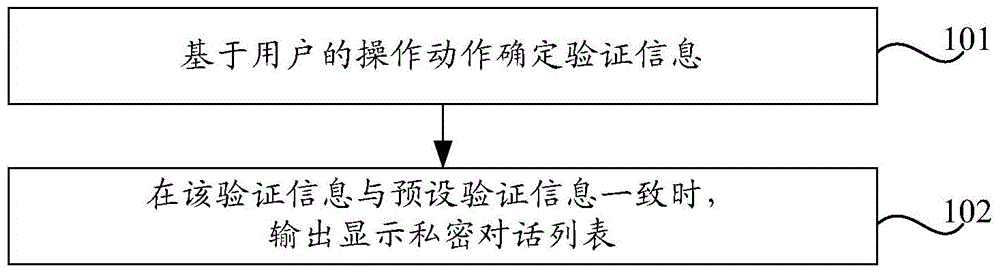
Dialog list display method and device and terminal
InactiveCN104899501AImprove securityGuaranteed privacyDigital data authenticationInput/output processes for data processingComputer engineering
The invention discloses a dialog list display method and device and a terminal. The dialog list display method comprises the steps of determining verification information based on operation actions of a user, and displaying a secret dialog list when the verification information is consistent to preset verification information. By adopting the dialog list display method and device, the verification information can be preset through the terminal, and the secret dialog list can be displayed as long as the verification information is determined based on the actions of the user and is consistent to preset verification information. Therefore, the privacy of the secret dialog list can be ensured, the information of secret dialogs is not easily obtained by other users, the safety of the information is improved, and operation is simple and easy to achieve.
Owner:XIAOMI INC
Method for catalyzing and synthesizing 1, 2-pentanediol by using titanium silicalite
The invention provides a method for catalyzing and synthesizing 1, 2-pentanediol by using titanium silicalite, comprising the following processes of: (1) reacting 1-pentene with oxyful catalyzed and activated by the titanium silicalite in a solvent to obtain 1, 2-epoxy pentane in high selectivity and high yield; and (2) after vaporizing and eliminating the solvent, carrying out the ring cleavage reaction on the 1, 2-epoxy pentane and water in the presence of the action of an acidic or basic catalyst to obtain the 1, 2-pentanediol. The purity of the rectified product is greater than 99 percent.
Owner:YUNNAN UNIV
Panax notoginseng saponins freeze-dried powder injection and preparation method thereof
ActiveCN102512466AGood resolubilityReduce moisture contentPowder deliveryPharmaceutical product form changePANAX NOTOGINSENG ROOTFreeze-drying
The invention relates to panax notoginseng saponins freeze-dried powder injection and a preparation method thereof. The freeze-dried powder injection is prepared by panax notoginseng saponins and water for injection. The panax notoginseng saponins freeze-dried powder injection is free of auxiliary materials or stent agents, good in re-dissolubility, low in water content and good in appearance forming.
Owner:GUANGXI WUZHOU PHARMA GRP
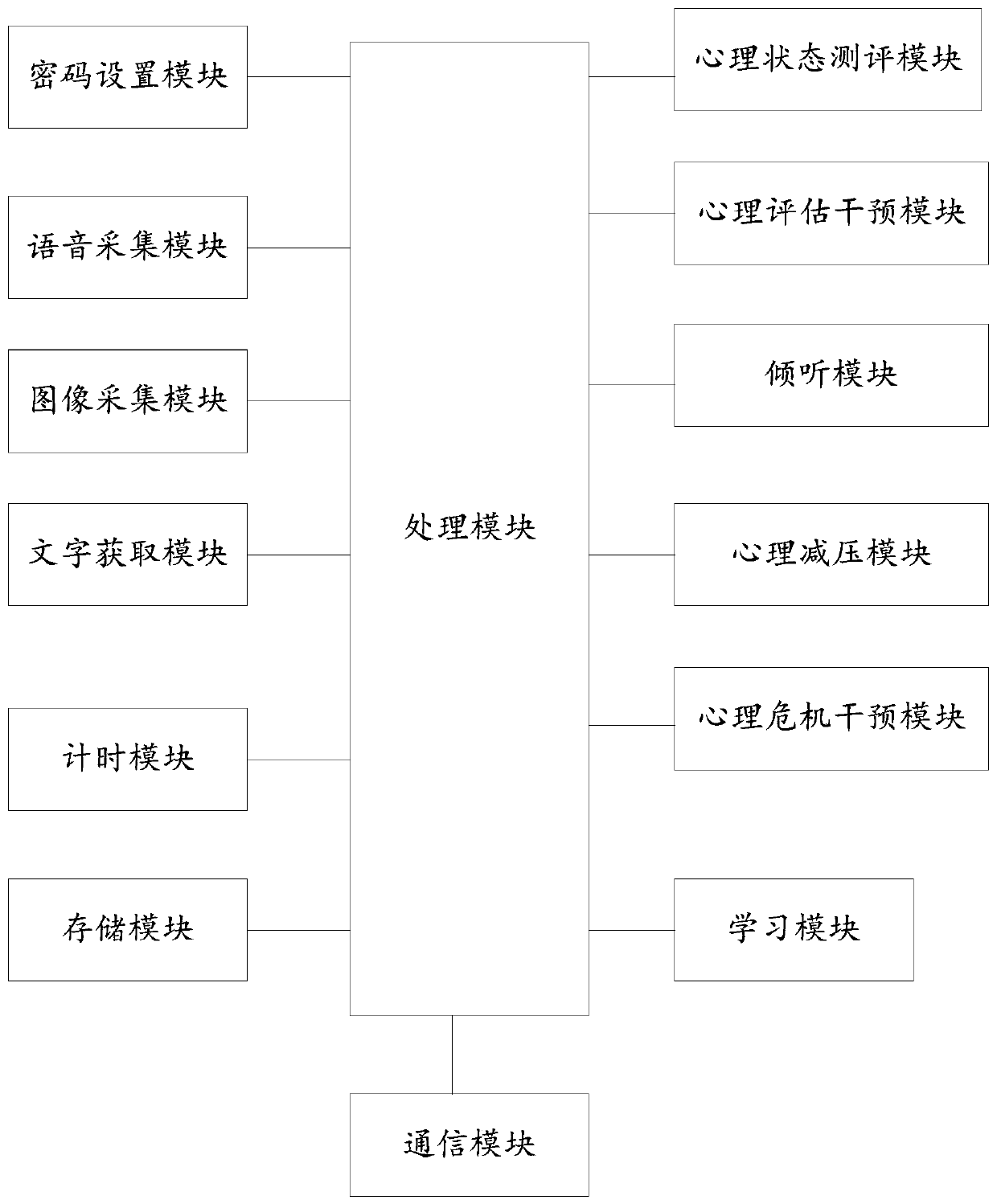
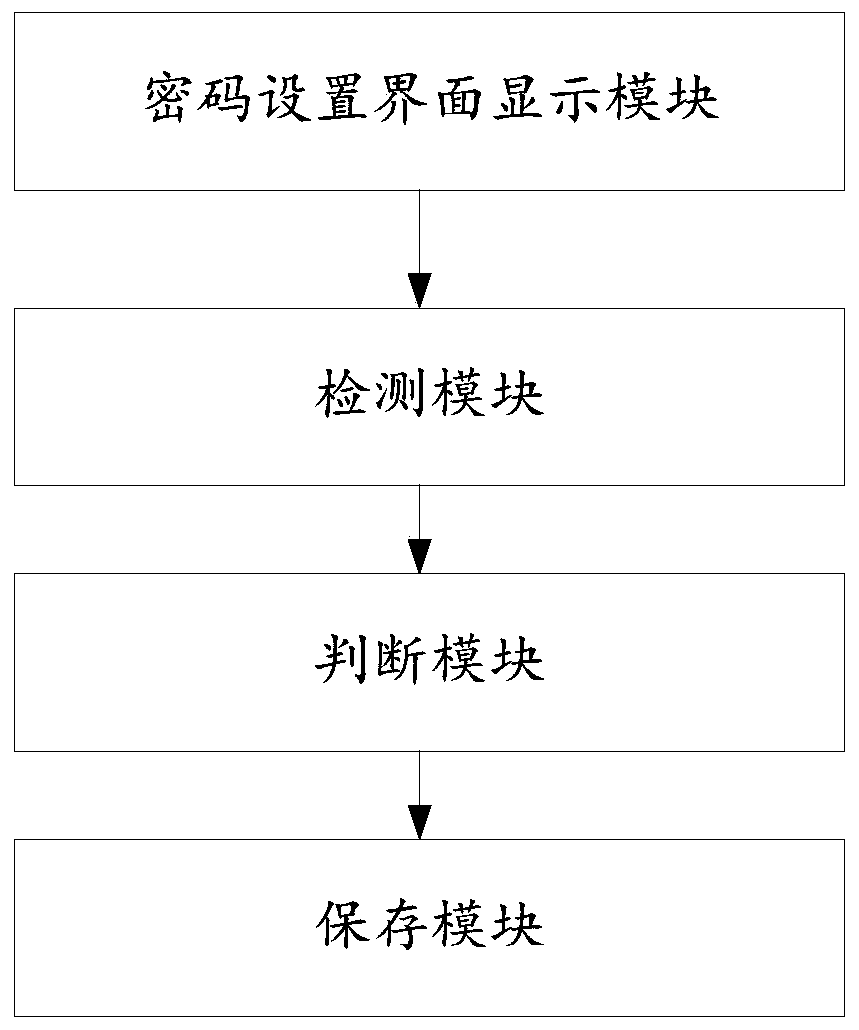
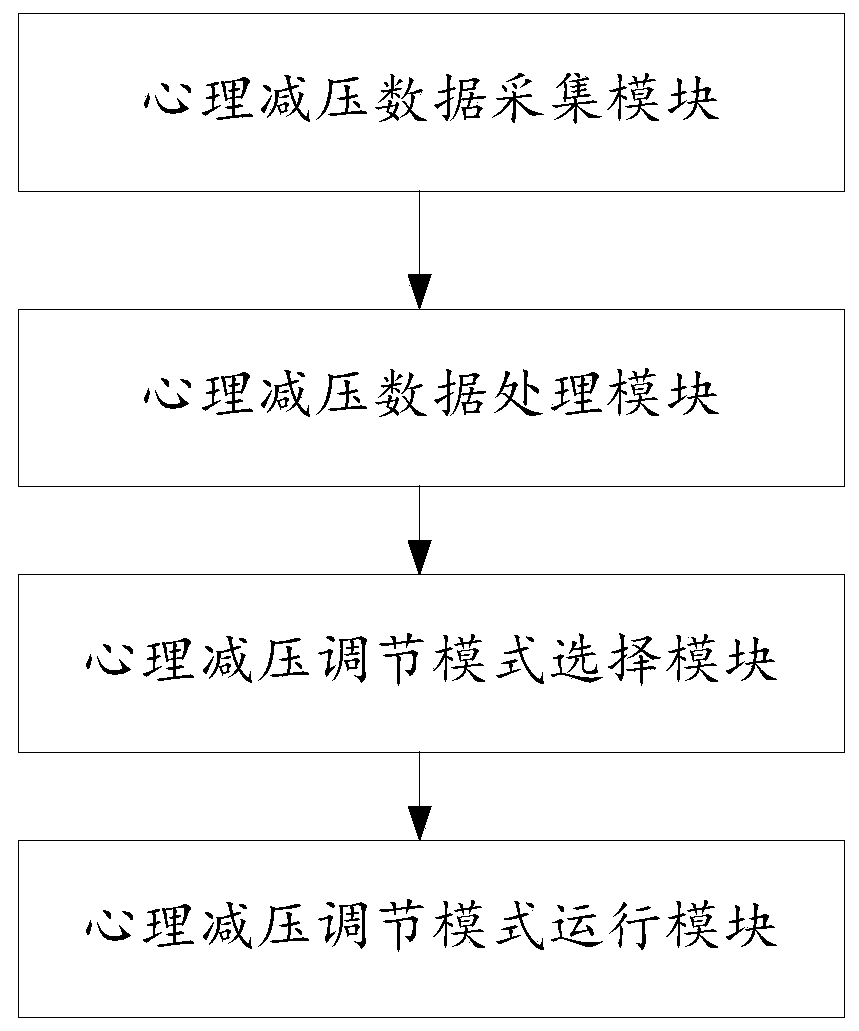
Interactive emotional counseling and psychological counseling robot
PendingCN110767290AEasy to carryEasy to relieve stressDigital data protectionMental therapiesEvaluation resultPhysical medicine and rehabilitation
The invention discloses an interactive emotional counseling and psychological counseling robot. The information is processed through a processing module, the user's complaint content is identified, and psychological and emotional states of a user are determined; a psychological state evaluation module evaluates a psychological state type of the user preliminarily and again according to the psychological and emotional states of the user; a psychological evaluation intervention module performs corresponding psychological intervention of the user according to the evaluation result of the psychological state evaluation module; a listening module acquires the listening content of the user, selects corresponding words for encouraging and comforting and feeds back the words to the user; a psychological decompression module decompresses the psychological pressure of the user according to different degrees of psychological pressure; and a psychological crisis intervention module determines whether the user faces a special crisis situation or not according to the evaluation result of the psychological state evaluation module, and performs psychological adjustment of the user facing the special crisis situation.
Owner:SHANDONG PROVINCIAL HOSPITAL
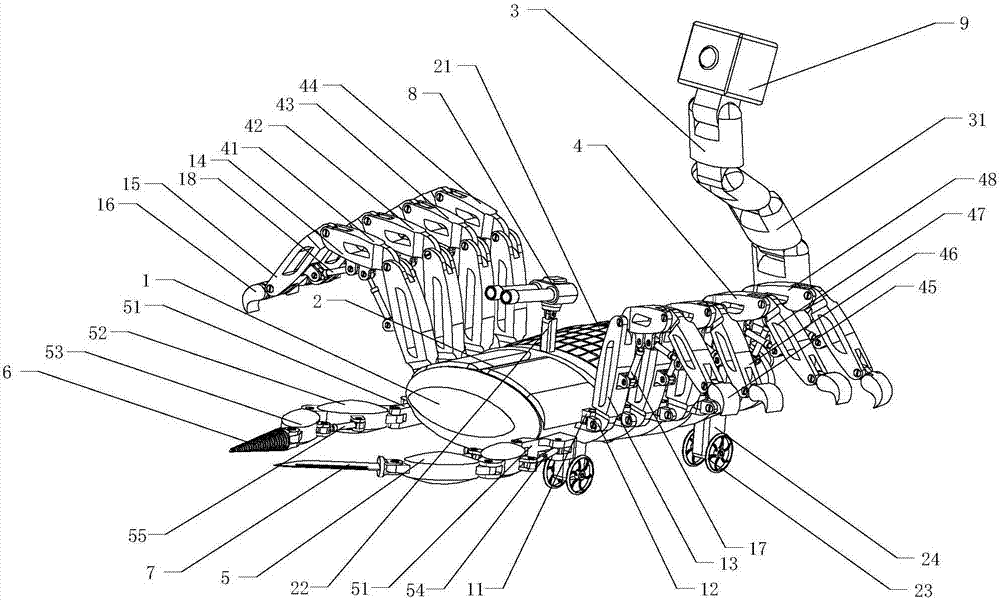
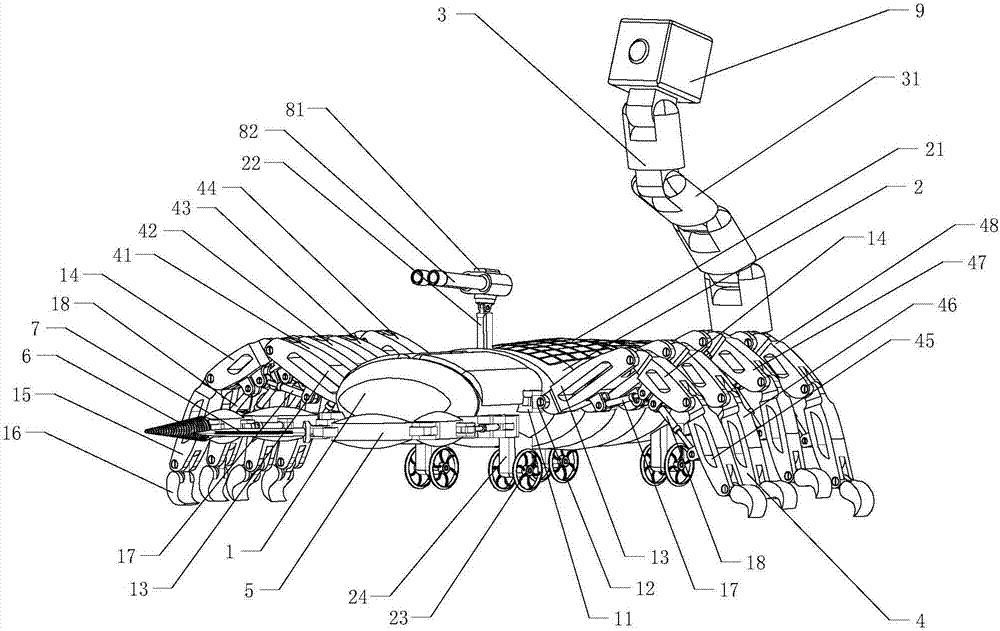
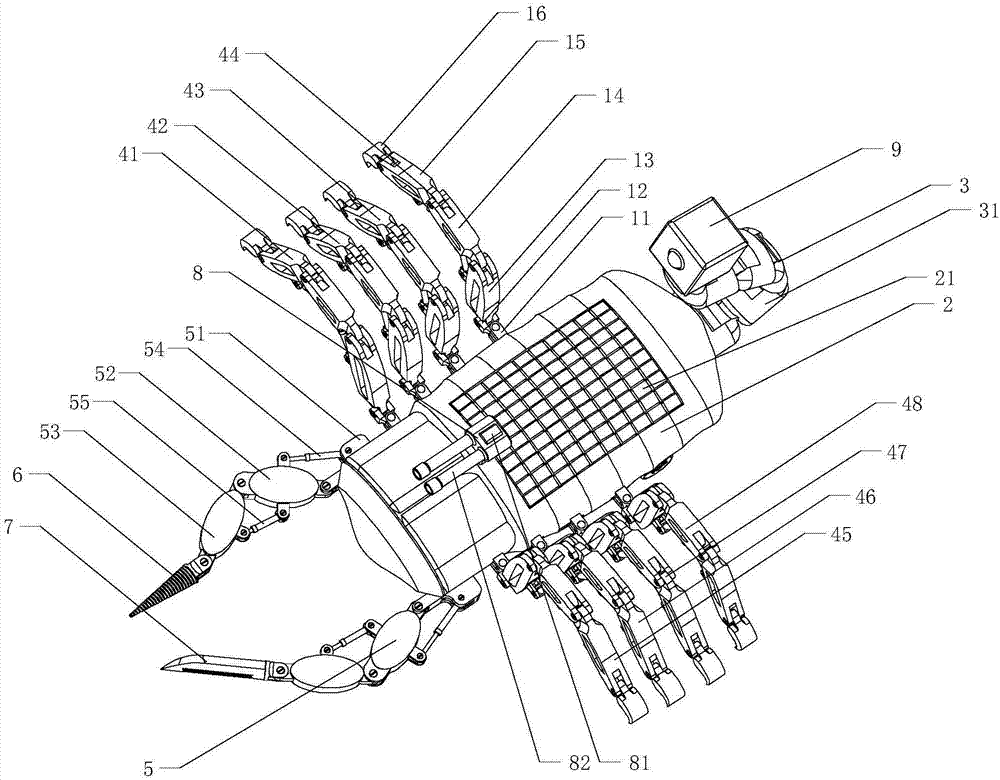
Bionic scorpion detecting robot
PendingCN107053207AEasy accessImprove obstacle performanceManipulatorVehiclesPhysical medicine and rehabilitationPhysical therapy
The invention discloses a bionic scorpion detecting robot. The bionic scorpion detecting robot comprise a head, a trunk, a tail, walking legs and front claws, wherein the trunk is of a shell body structure, the head is connected with the front end of the trunk, and the tail is connected with the rear end of the trunk. Solar panels are arranged at the middle-rear portion of the upper surface of the trunk and connected with storage batteries, and the storage batteries are connected with a main controller in the trunk. The number of the walking legs is eight, four walking legs are arranged at the left side of the trunk from front to back sequentially, and the other four walking legs are arranged at the right side of the trunk from front to back sequentially. The number of the front claws is two, the two front claws are connected to the left side and the right side of the front end of the trunk through front hinging seats correspondingly, an electric drill is arranged on one front claw, and a saber is arranged on the other front claw. The bionic scorpion detecting robot is designed through the bionic technology, has excellent obstacle surmounting performance, can adapt to complex geographical environments, is high in concealment and can attack the enemy actively or conduct self-defense, and smooth proceeding of the detecting action is guaranteed.
Owner:SHANDONG UNIV OF SCI & TECH
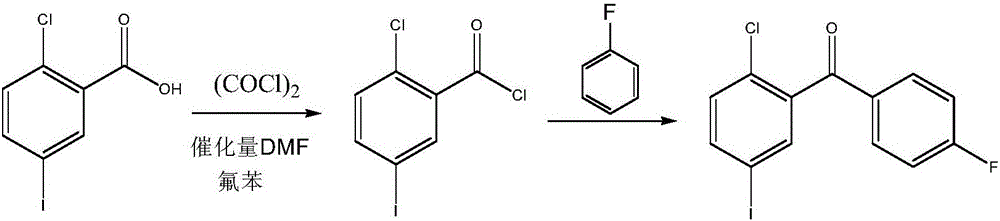
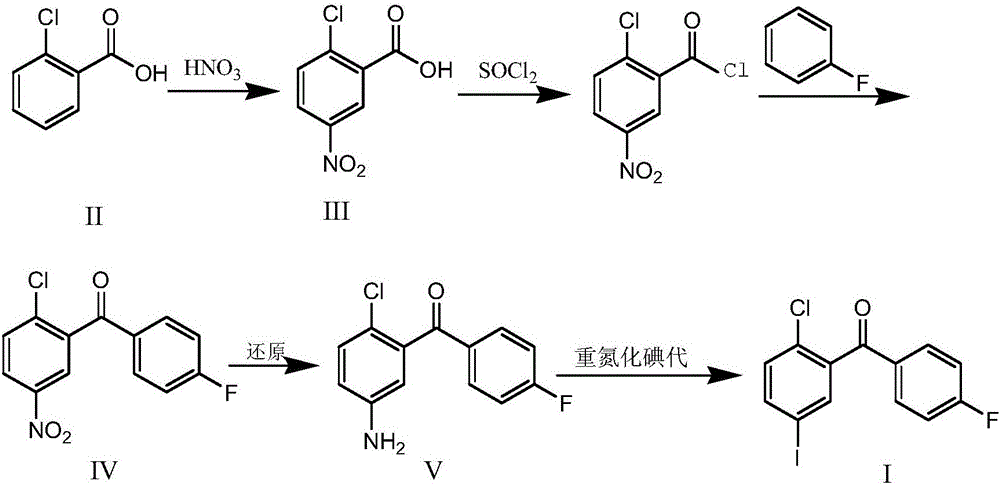
Synthesis method for (2-chloro-5-iodophenyl)(4-fluorophenyl)ketone
ActiveCN106699570AEasy to getIncrease profitOrganic compound preparationCarbonyl compound preparationSandmeyer reactionNitration
The invention discloses a synthesis method for (2-chloro-5-iodophenyl)(4-fluorophenyl)ketone. According to the method, with cheap o-chlorobenzoic acid as a starting material, (2-chloro-5-iodophenyl)(4-fluorophenyl)ketone is obtained by nitration, Friedel-Crafts acylation and reduction and finally by Sandmeyer reaction for iodination. The materials used by the method are cheap and easy to obtain, and the method adopting Sandmeyer reaction for iodination can increase the iodine utilization rate, and has the characteristics of simplicity in operation, high yield, high purity and suitability for industrialized production. (The chemical formula is shown in the specification).
Owner:SHANDONG BOYUAN PHARM CO LTD
Novel auxiliary material for barbecue fuel and preparation method thereof
The invention discloses a novel auxiliary material for barbecue fuel and a preparation method thereof. The auxiliary material comprises the following components in part by weight: 35 to 40 parts of cypress branch and leave powder, 10 to 15 parts of nut hull powder, 3 to 5 parts of orange meal, 10 to 15 parts of saw powder and 40 to 45 parts of crop straw powder. The method comprises the following steps of: crushing cypress branches and leaves, nut hulls, the saw powder, straw and orange peel, mixing the crushed materials, and sterilizing to prepare the auxiliary material for the barbecue fuel. The auxiliary material can control the temperature reasonably, so that the temperature of charcoal fire is constant due to the coverage of the auxiliary material powder; and products are fire-cured by generated high-temperature smoke, so that the products have unique flavors. By the auxiliary material, the defect that the original barbecue with the Gaeml flavor only can be prepared from fresh materials in national habitations due to the limit of raw materials is overcome; and various fire-cured barbecues are delicious in taste, the barbecue raw materials are difficult to burn, and the prepared seasoning bag is convenient to carry, transport and store and difficult to rot.
Owner:KAILI UNIV
Polypeptide sequence combined with bovine viral diarrhea E2 protein and application of polypeptide sequence
ActiveCN104597256AHigh affinityImprove bindingBiological material analysisPeptidesBiotinBacteriophage
The invention mainly relates to a polypeptide sequence combined with bovine viral diarrhea E2 protein and application of the polypeptide sequence. The polypeptide sequence is KRLREL and is a linear combined polypeptide, the polypeptide sequence can be prolonged and modified by taking the polypeptide sequence as a core, and modification materials can be but not limited to nano materials, fluorescent materials, enzymes, biotin and specific protein. By adopting a phage peptide library screening technique, the expressed and purified bovine viral diarrhea E2 protein can be screened for multiple rounds, and polypeptide clone strains which can be specifically combined with the bovine viral diarrhea E2 protein can be ultimately obtained; the polypeptide clone strains can be selected for sequencing, the core sequence of the polypeptide is KRLREL, the manually synthesized polypeptide used for ELISA combination experiment shows that the synthesized polypeptide can be well combined with the bovine viral diarrhea E2 protein; the process is simple, and the operation is relatively convenient compared with the operation that expression protein is manually expressed and is further immunized to obtain a protein antibody; by marking the polypeptide, a kit or a test paper bar (card) for quantitative and qualitative detection on the bovine viral diarrhea E2 protein can be rapidly produced.
Owner:HENAN ACAD OF AGRI SCI
Foamed basalt insulation material and preparation method thereof
InactiveCN107602147AImprove performanceLow thermal conductivityCeramicwareThermal insulationMetallic materials
The invention relates to a foamed basalt insulation material and a preparation method thereof, which belong to the field of the insulation material. The foamed basalt insulation material is prepared by the following main components in parts by weight: 50-90 parts of basalt ore, 0.3-10 parts of a foaming agent, 5-25 parts of a fluxing agent, 3-10 parts of a foam stabilizer, 0.1-0.5 parts of a dispersant, and 0.1-0.7 parts of an auxiliary material, The foamed basalt insulation material is prepared by the steps of crushing, ball milling, spray drying, and foaming. The foamed basalt insulation material is the inorganic non-metallic material having excellent performance, has the advantages of no toxicity and no radiation, low heat conduction coefficient, good thermal insulation performance, andstable chemical property, wherein the pH value is 7-8, the foamed basalt insulation material is neutral or weakly alkaline, and has no corrosion on the metal materials such as carbon steel, stainlesssteel and aluminium; refractiveness is good, the melting point is higher than 1200 DEG C, and a fireproof grade can reach a A-grade standard; and the compressive strength and shearing intensity are high.
Owner:哈尔滨时代创新科技发展有限公司
Application program data protection method and device
InactiveCN105844150AEnsure safetyEnsure data securityDigital data protectionPlatform integrity maintainanceApplication softwareMechanism based
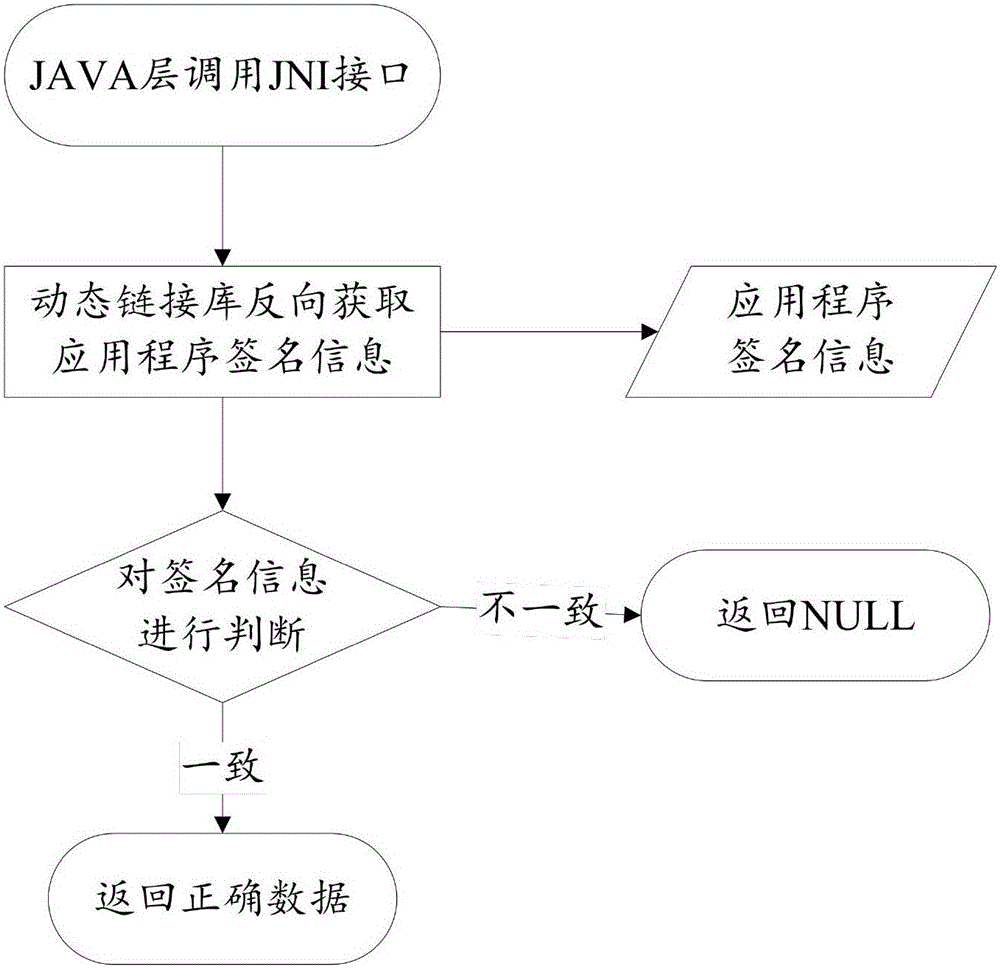
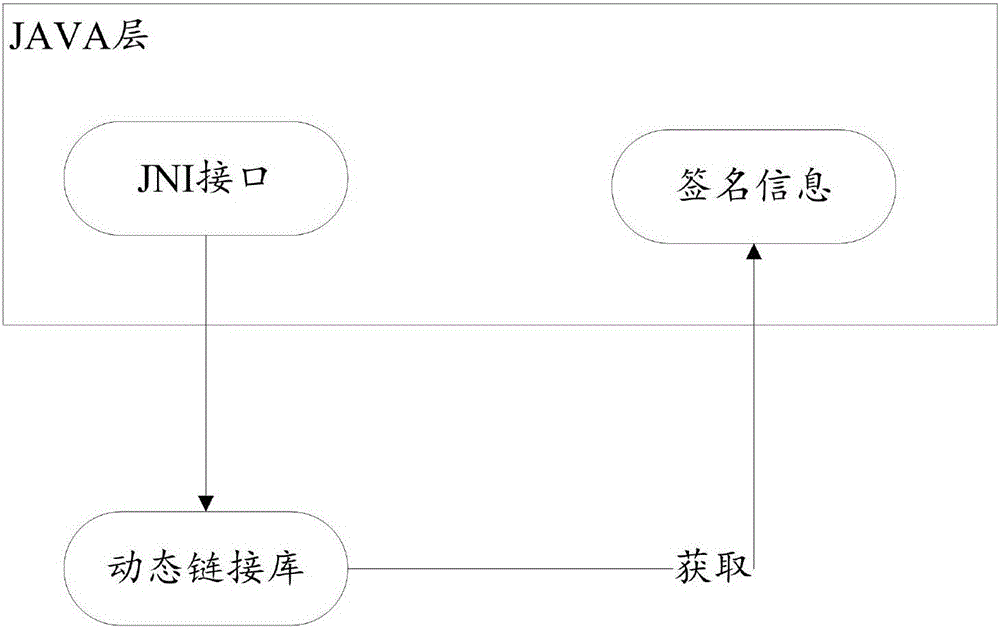
Embodiments of the invention provide an application program data protection method and device. The method comprises the steps: receiving a request command aiming at data of an application program; by aiming at the request command, invoking a JAVA local interface; acquiring dynamic signature value of the application program by utilizing the JAVA local interface; judging whether the request command is a trustable command according to the dynamic signature value. Therefore, according to the application program data protection method and device, addition of asymmetric encryption mechanism based on a unique signature of the application program is implemented, and the security of the data of the application program is ensured.
Owner:JUHAOKAN TECH CO LTD
Electronic contract data encryption storage method and signing client
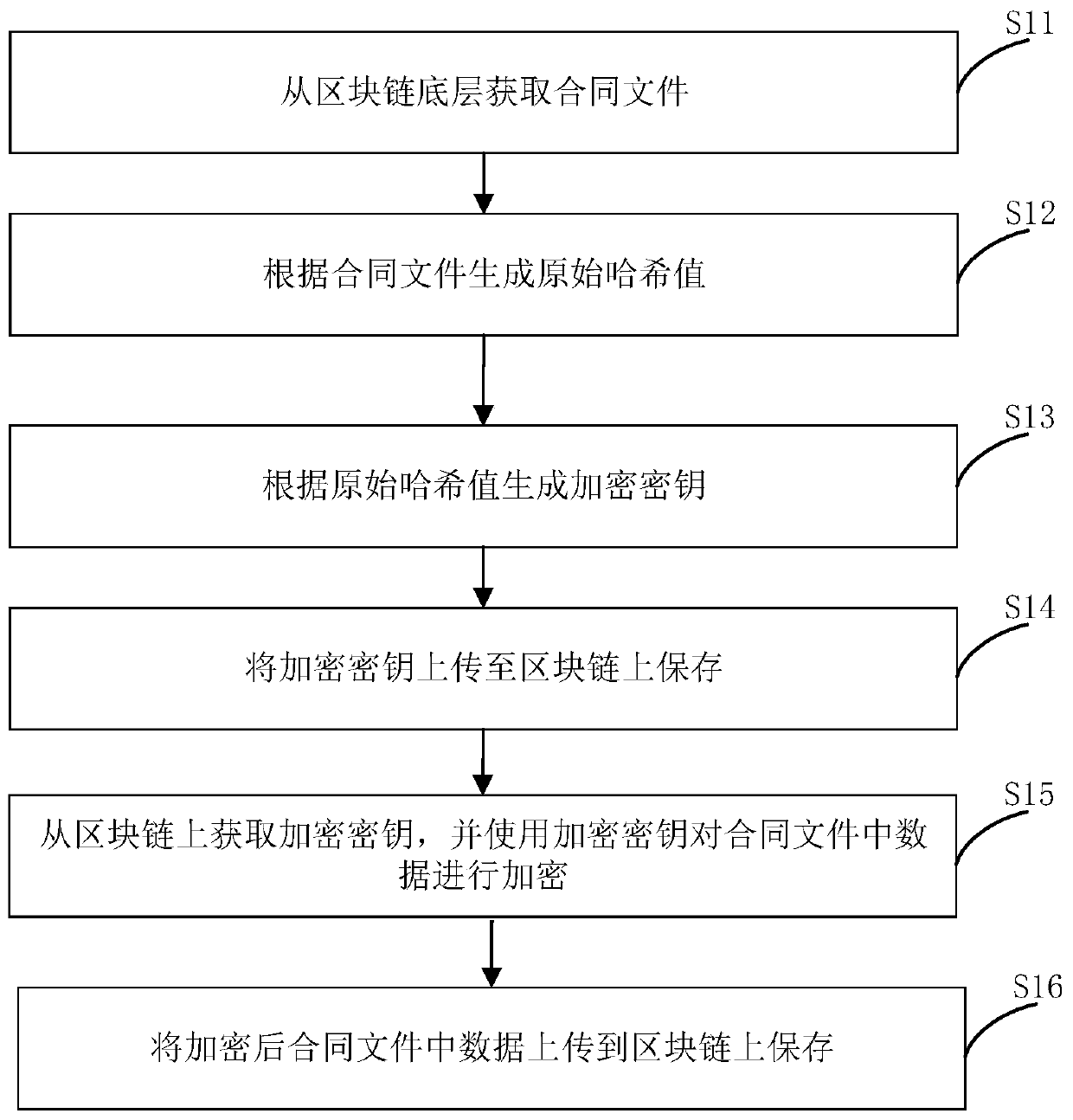
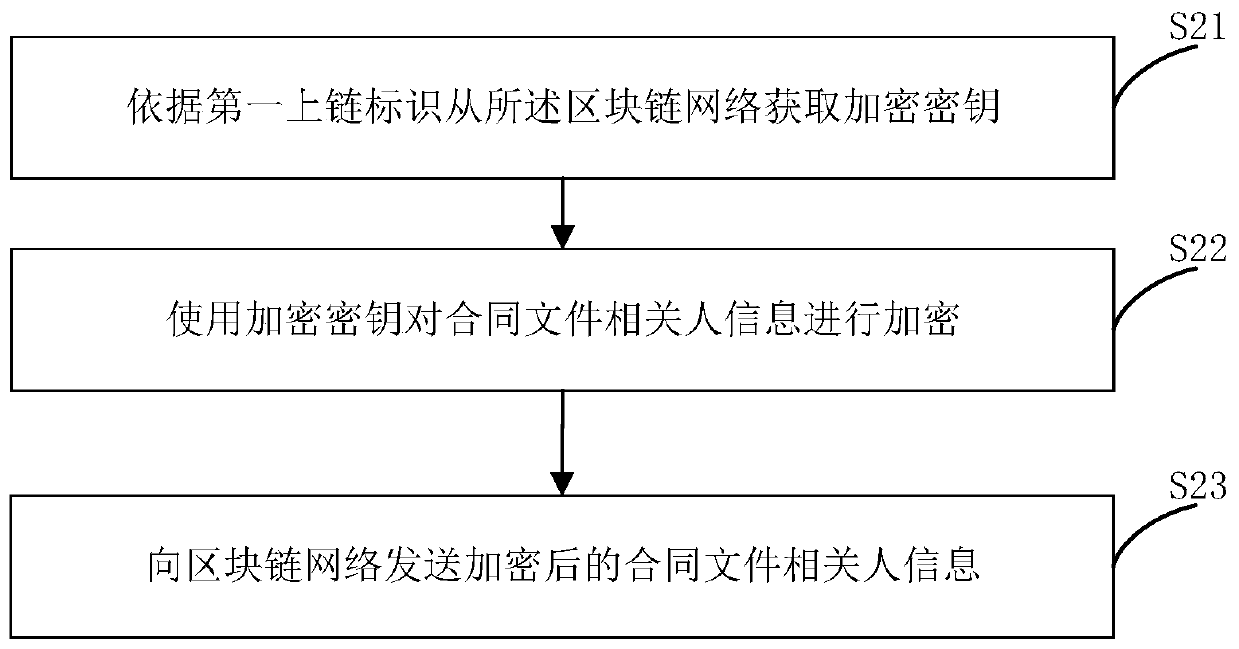
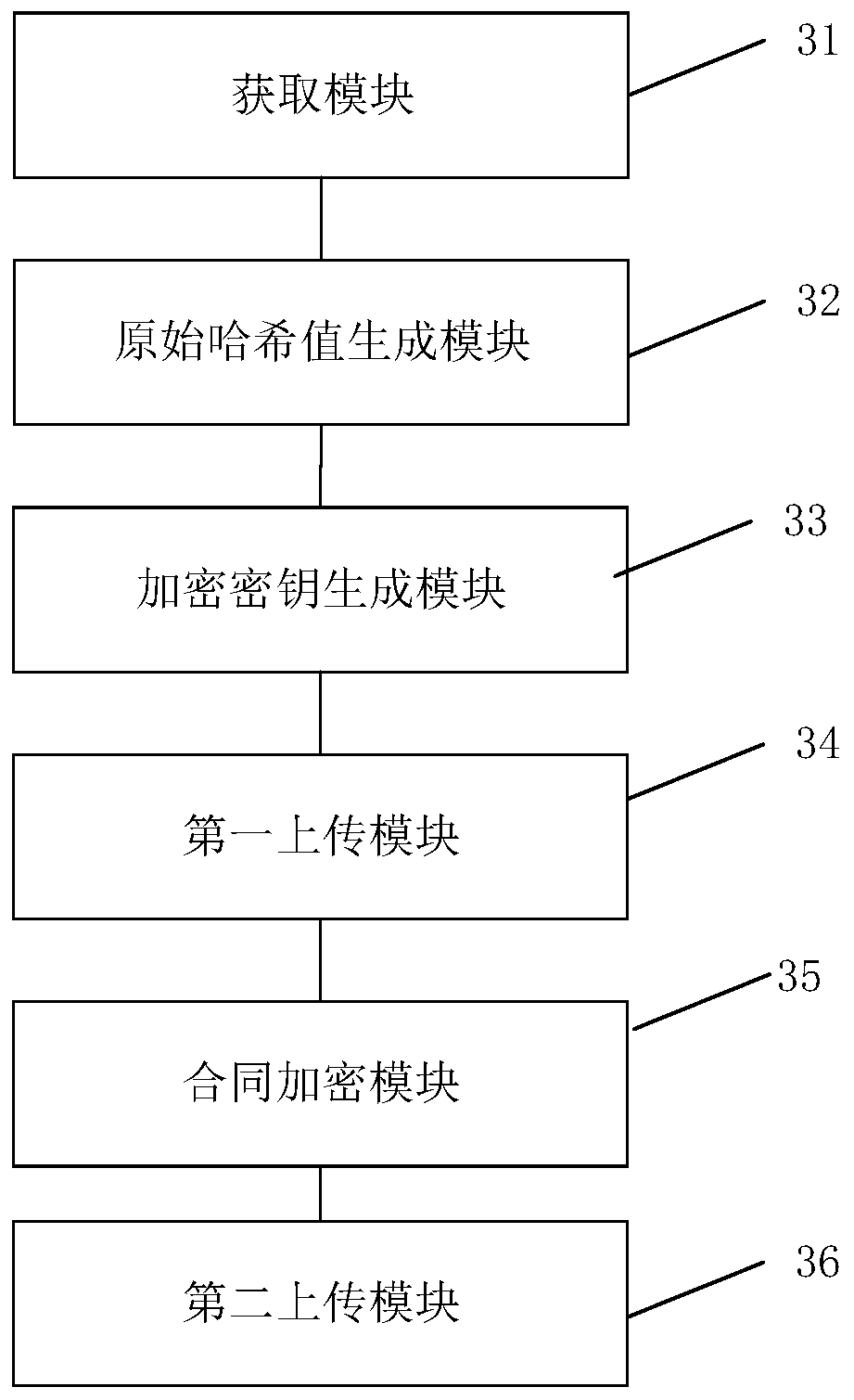
The invention relates to an electronic contract data encryption storage method and an electronic contract signing client. The electronic contract data encryption storage method comprises the steps ofobtaining a contract file from a block chain bottom layer; generating an original hash value according to the contract file; generating an encryption key according to the original hash value; uploading the encryption key to a block chain for storage; acquiring the encryption key from the block chain, and encrypting the data in the contract file by using the encryption key; and uploading the data in the encrypted contract file to a block chain for storage. The encryption key is not easily tampered, potential safety hazards of an electronic contract are eliminated, the original hash value is encrypted, and the security of the encryption key is further enhanced, so that the security of contract data information is more favorably protected.
Owner:北京智签科技有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com