Seal lock and encryption identification method, device and system based on same
A verification method and verification code technology, applied in the field of devices and systems, seal locks and encryption verification methods based on seal locks, can resolve trade disputes, endanger enterprises, institutions/personal property, cargo safety, and cannot verify seals Lock authenticity and other issues, to achieve a wide range of application prospects, to avoid trade disputes and litigation, property or facility security effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0048] Embodiment 1 of the present invention provides a seal lock.
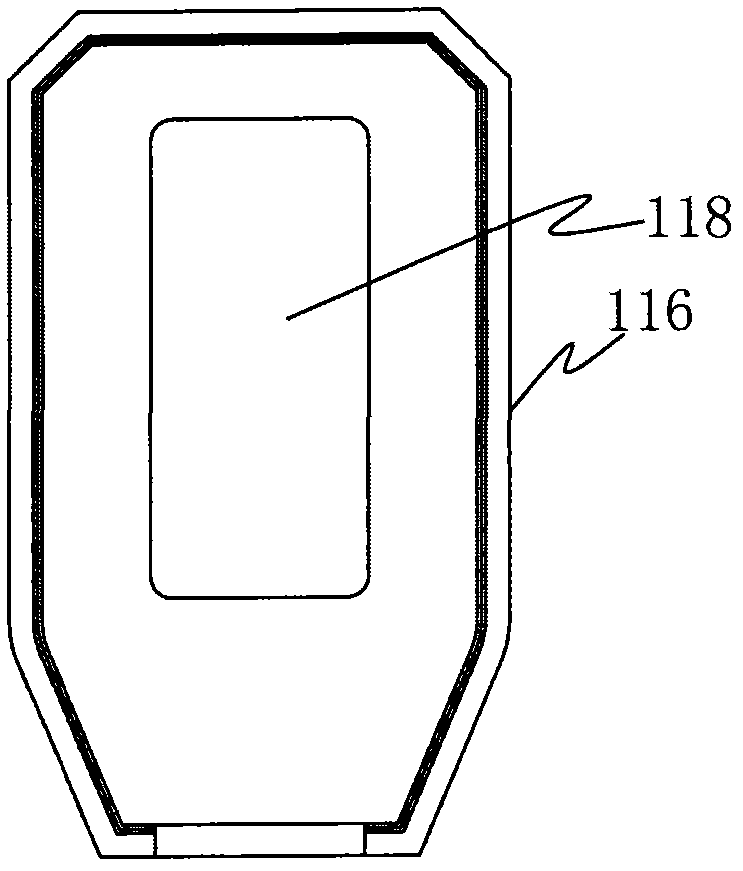
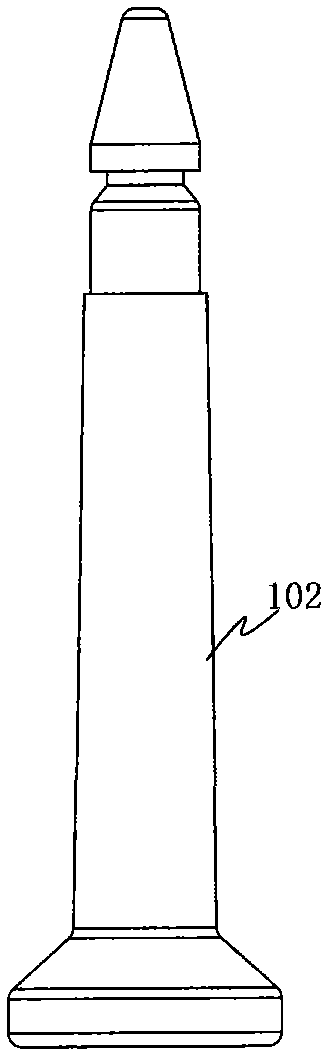
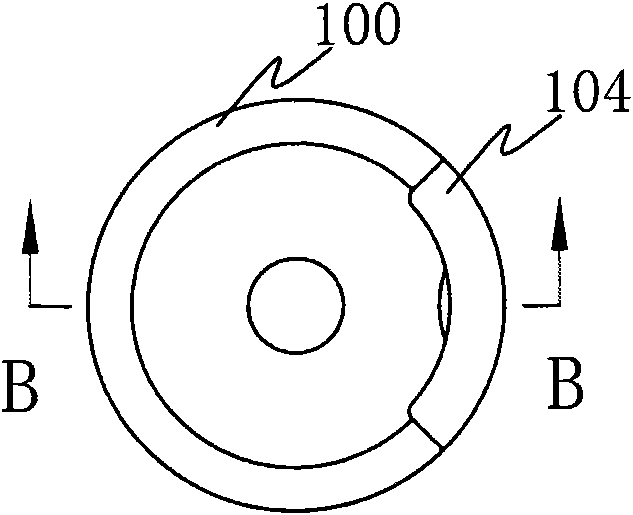
[0049] The seal lock of Embodiment 1 of the present invention has a lock body, and the lock body of the seal lock is provided with a seal lock code in an exposed state and a verification code in a hidden state corresponding to the seal lock code, and the above-mentioned code is in a hidden state The verification code needs to be obtained by physically destroying the seal lock. It should be noted that the seal lock provided by Embodiment 1 of the present invention is formed by improving the structure of high-security seals, steel wire seals, draw-tight seals, iron sheet seals, padlock seals or other types of seals in the prior art. The high-security seal is taken as an example for illustration below, and those skilled in the art can understand that the improvement methods described below for the structure or structure of the high-security seal can also be applied to other types of seals mentioned above.
[00...
Embodiment 2
[0062] Embodiment 2 of the present invention provides an encryption verification method based on a seal lock. It should be noted that the lock body of the above-mentioned seal lock is provided with a seal lock code in an exposed state and a verification code in a hidden state corresponding to the above-mentioned seal lock code. Obtained by physically destroying the Zhi Lock.
[0063] Figure 4 It is a flow chart of the encryption verification method in Embodiment 2 of the present invention. This method is suitable for authenticating servers such as Figure 4 As shown, the method includes the following steps:
[0064] Step S401, receiving the first code of the seal lock sent by the sealer terminal of the seal lock, where the first code of the seal lock corresponds to the first verification code;
[0065] Step S402, receiving a verification request including a second verification code sent by the unsealing terminal of the seal lock;
[0066] Step S403, when the second verif...
Embodiment 3
[0080] The purpose of Embodiment 3 of the present invention is to provide an encryption verification method and encryption verification system based on a seal lock, to protect the confidential places / outdoor facilities and property / goods transportation safety of the person who applies the seal lock, and to protect the unsealed person In addition, during the delivery and transportation of the goods, the consignor, the consignee and the person who has unsealed and verified the seal lock applied by the consignor and applied a new seal lock during the transportation of the goods The intermediary party shall promptly know the identity of the unsealed person, unsealed time, unsealed reason, as well as the code and application time of the re-applied new seal lock when the goods are not unsealed by the consignee during the delivery and transportation process, and form a cargo transportation The point-to-point or seamless connection of the process is delivered safely, clearly dividing t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com