Cross-cloud security certification system and method based on identifier
A security authentication and identification technology, applied in the fields of government affairs, military affairs, commerce, finance, and cryptography, it can solve the problems of heavy load, serious key escrow, tedious certificate operation problems, etc., to reduce the certificate management process, avoid security risks, The effect of simplifying the certification work
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
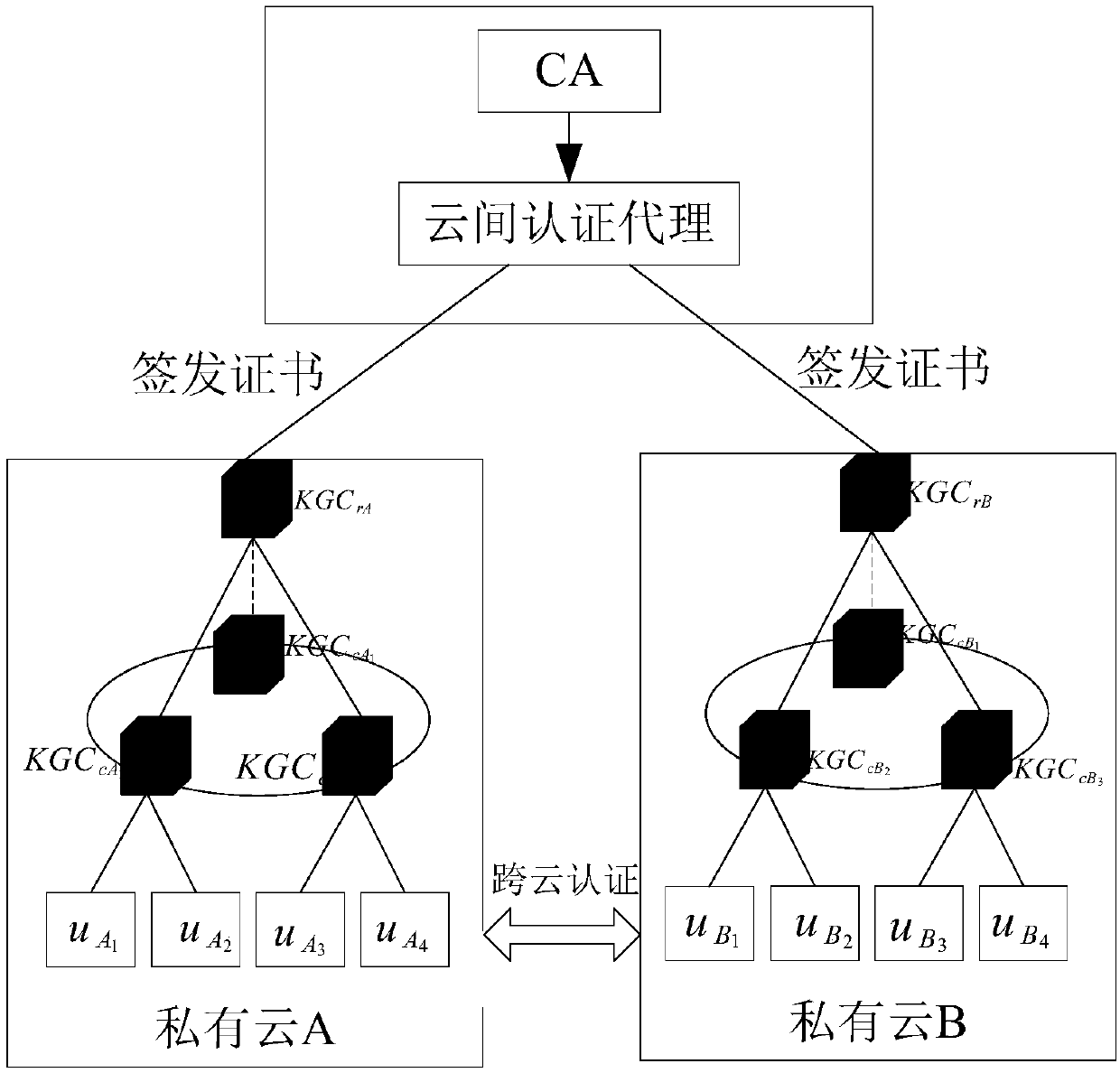
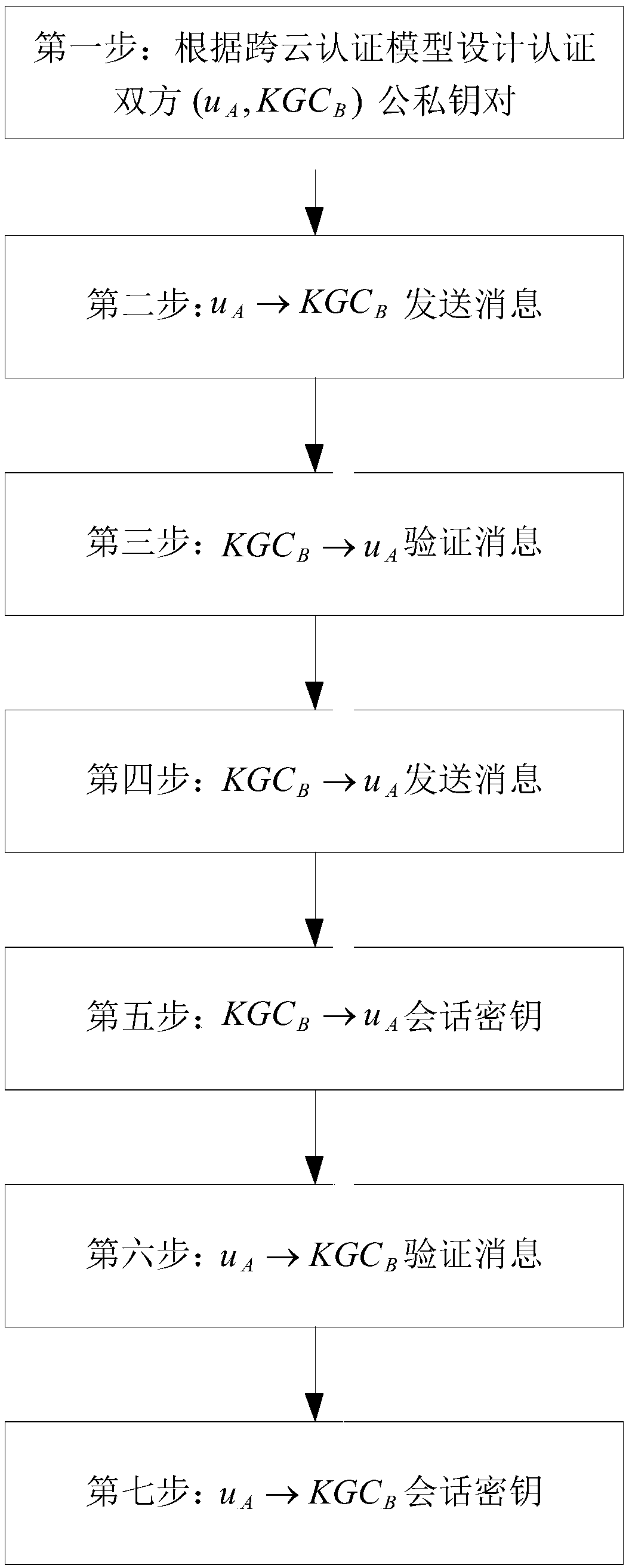
[0023]Currently, there are three main technologies to solve the identity authentication problem between users and cloud service providers. The certificate-based public key cryptosystem is suitable for large-scale networks, but the management of certificates consumes a lot of resources; the identity-based public key cryptosystem can Solve the problem of the uniqueness of cloud user identification, but it will cause key escrow; the non-certificate public key cryptosystem can effectively solve the problems in the first two authentications because it does not require a certificate and the user owns the secret value. Cannot authenticate efficiently. Aiming at the above problems, the present invention carried out innovation and research, and proposed a cross-cloud security hybrid authentication system based on identification. The identification is a group of bytes related to the user. Through the identification, the cloud system can know the user's authority and What the user is all...
Embodiment 2
[0026] The overall composition of the identity-based cross-cloud security authentication system is the same as that of Embodiment 1. In the present invention, the inter-cloud security agent connects to the authentication center and connects to each cloud domain. The inter-cloud security agent of the present invention has two responsibilities. One is Manage the digital certificates issued by the certification center, including the application, issuance, query, and issuance of the revocation list of digital certificates, etc. The second is to save the root KGC in each cloud domain r The generated system public parameters realize the transmission of information between various cloud domains in the system. In the present invention, due to the introduction of the hierarchical model, the inter-cloud security agent is endowed with a new meaning.
Embodiment 3
[0028] The overall structure of the identity-based cross-cloud security authentication system is the same as that of Embodiment 1-2. In the shared key ring structure of the sub-root of the hierarchical model of the present invention, there are n nodes, a positive integer of n≥0, and the threshold value is k. 0≤k≤n, once the sub-root KGC is maliciously attacked by the attacker, due to the effect of the threshold, the number of sub-keys must reach the threshold or above the threshold, that is to say, the attacker must attack at least k sub-keys It is possible to obtain the master key, and any sub-key below the threshold cannot restore the master key, because the equations below k cannot solve the equation system with unknown number k, and even if the attacker can forge k sub-keys The key must also fully ensure that all the k subkeys are correct to protect the security of the master key and system security. And even if KGC c One of them is attacked, and for the user's private ke...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com