Method for monitoring task stack overflow
A task stack and stack overflow technology, applied in the field of memory management, can solve the problems of memory space destruction, destruction, and inability to realize monitoring functions, so as to reduce the impact and enhance competitiveness.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
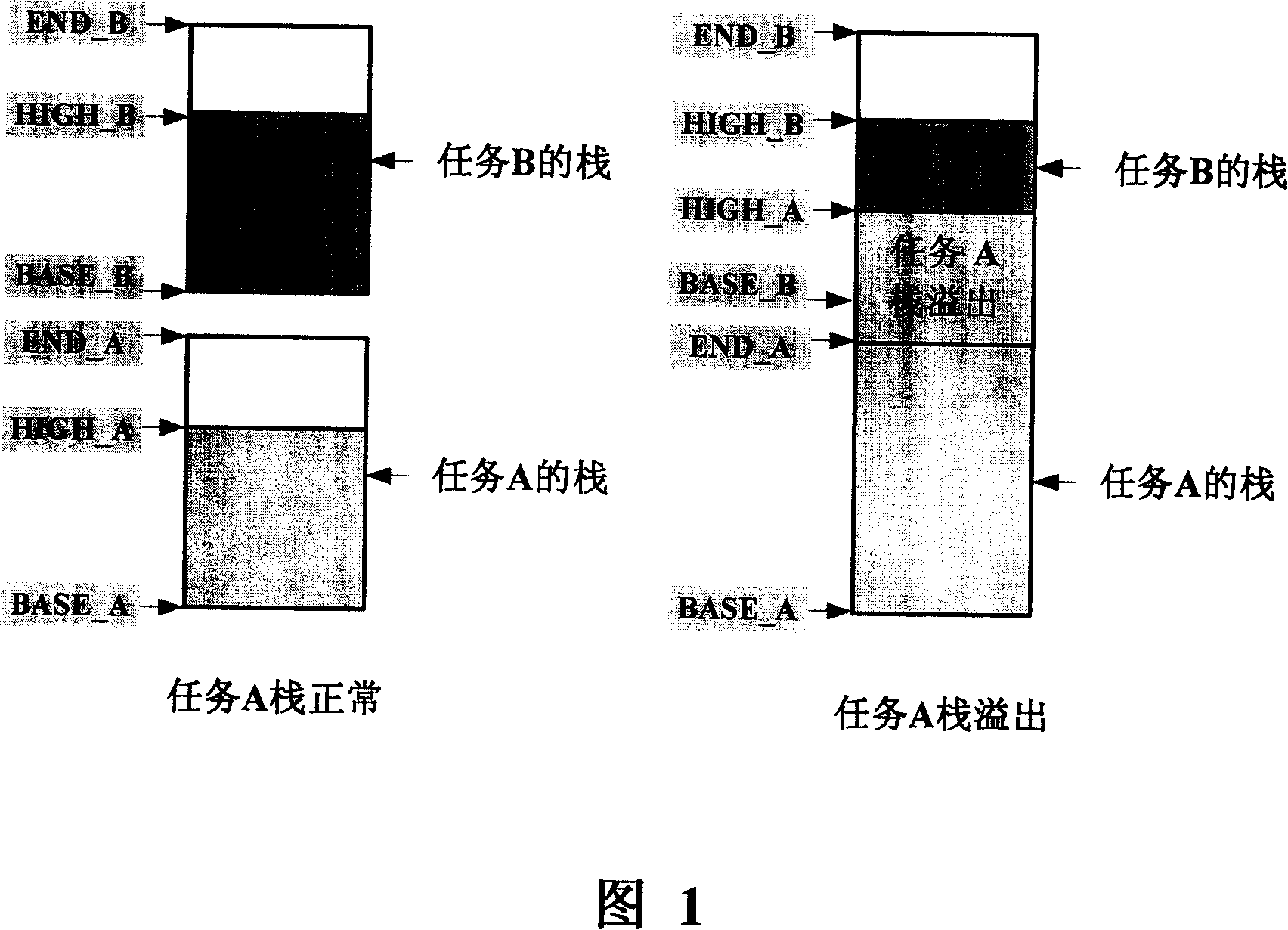
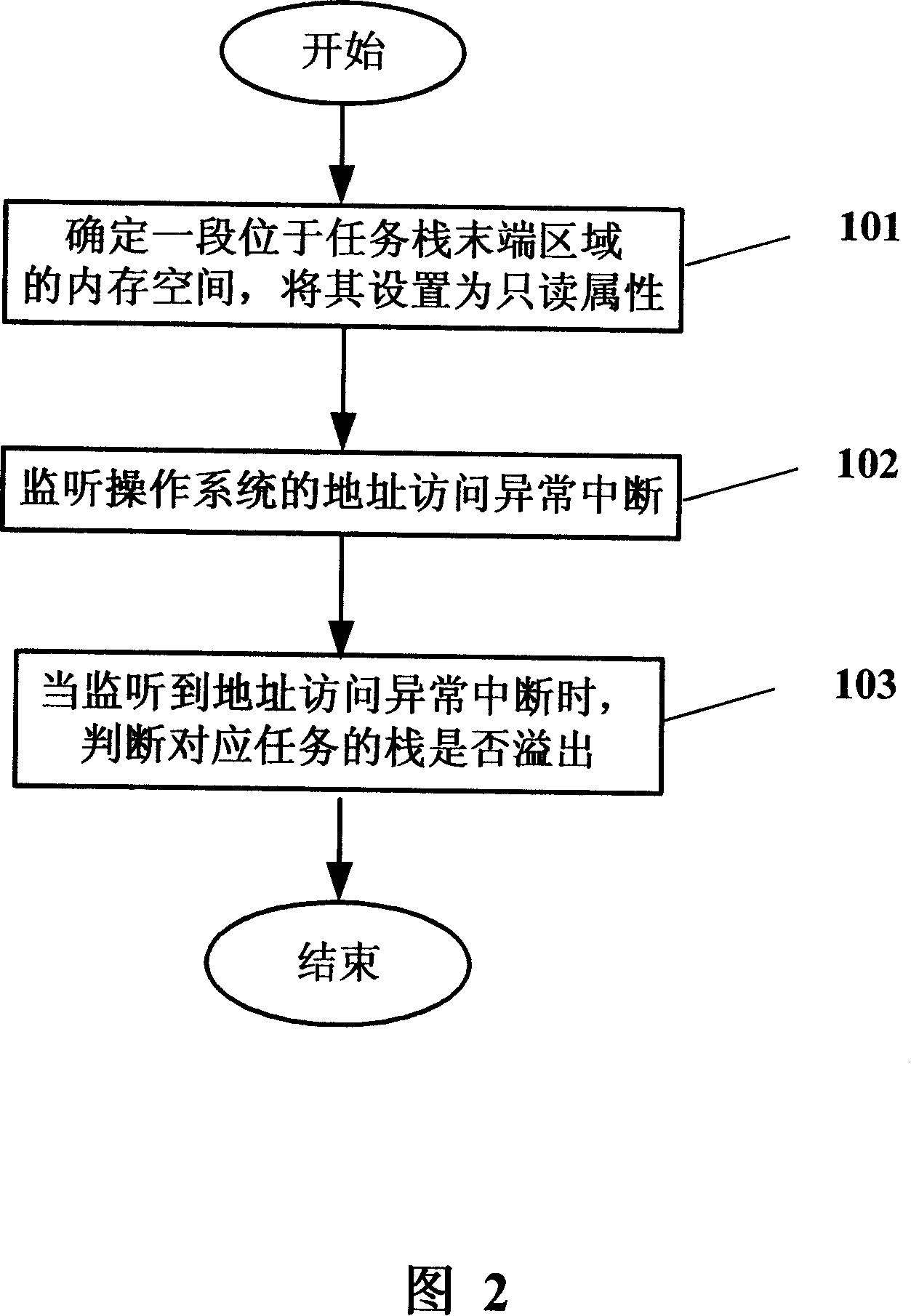
[0037] The basic idea of the present invention is to determine a section of memory area at the end area of the task stack and set it as a read-only attribute, as an isolation area between the task stack and other memory areas; and utilize the following characteristics of the operating system: when the operating system finds that there is When "attempting" to write to the memory area of the read-only attribute, an address access exception interrupt is generated, and the overflow of the task stack is monitored and processed accordingly.
[0038] As shown in Figure 2, a kind of monitoring method of task stack overflow of the present invention comprises the following steps:
[0039] Step 201, determine a memory space located at the end of the task stack, and set it as a read-only attribute.
[0040] The operating system allocates the memory space required by the task stack for the task from the system memory. In the prior art, the system memory of the real-time operating sy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com