Patents
Literature
35results about How to "Prevent execution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
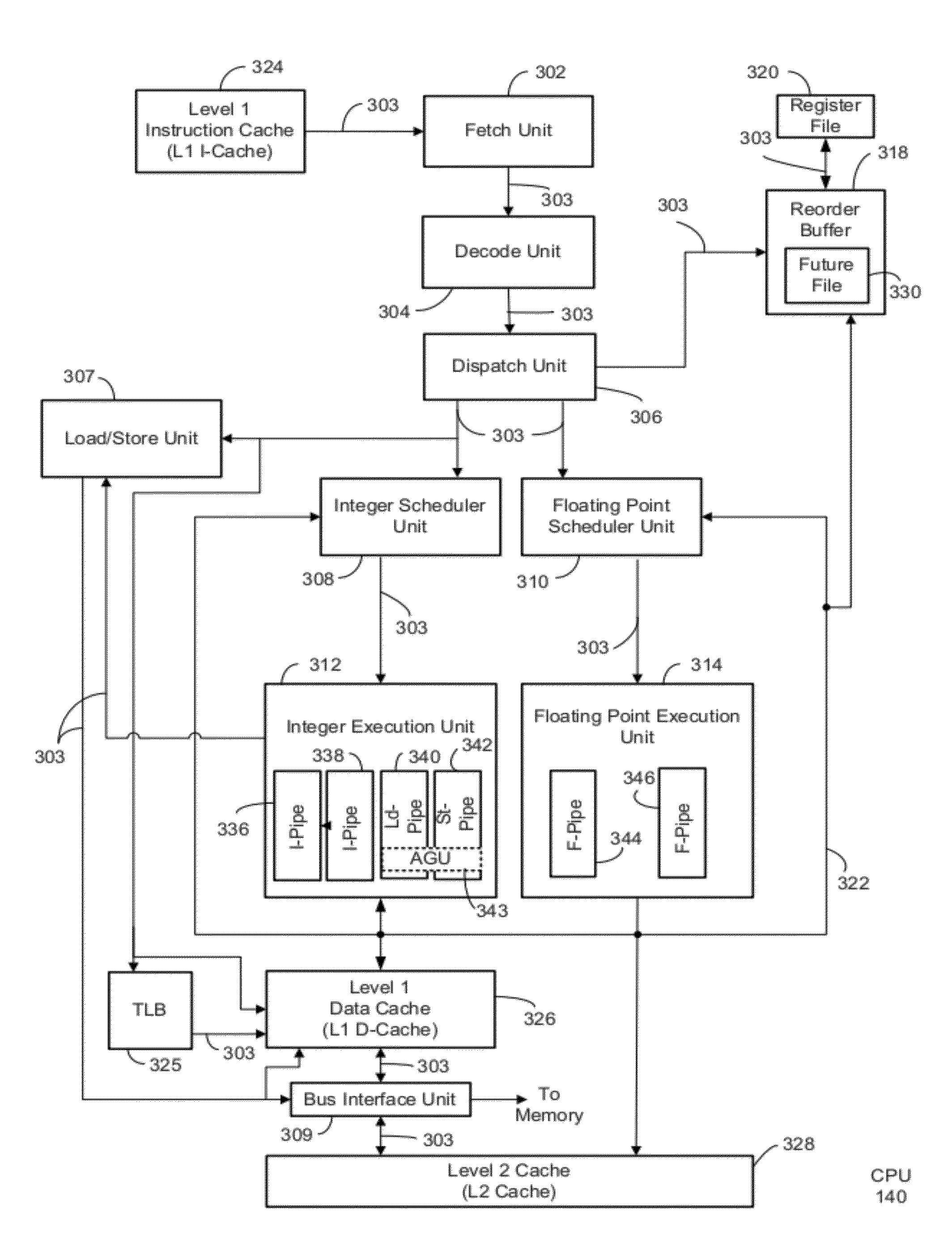
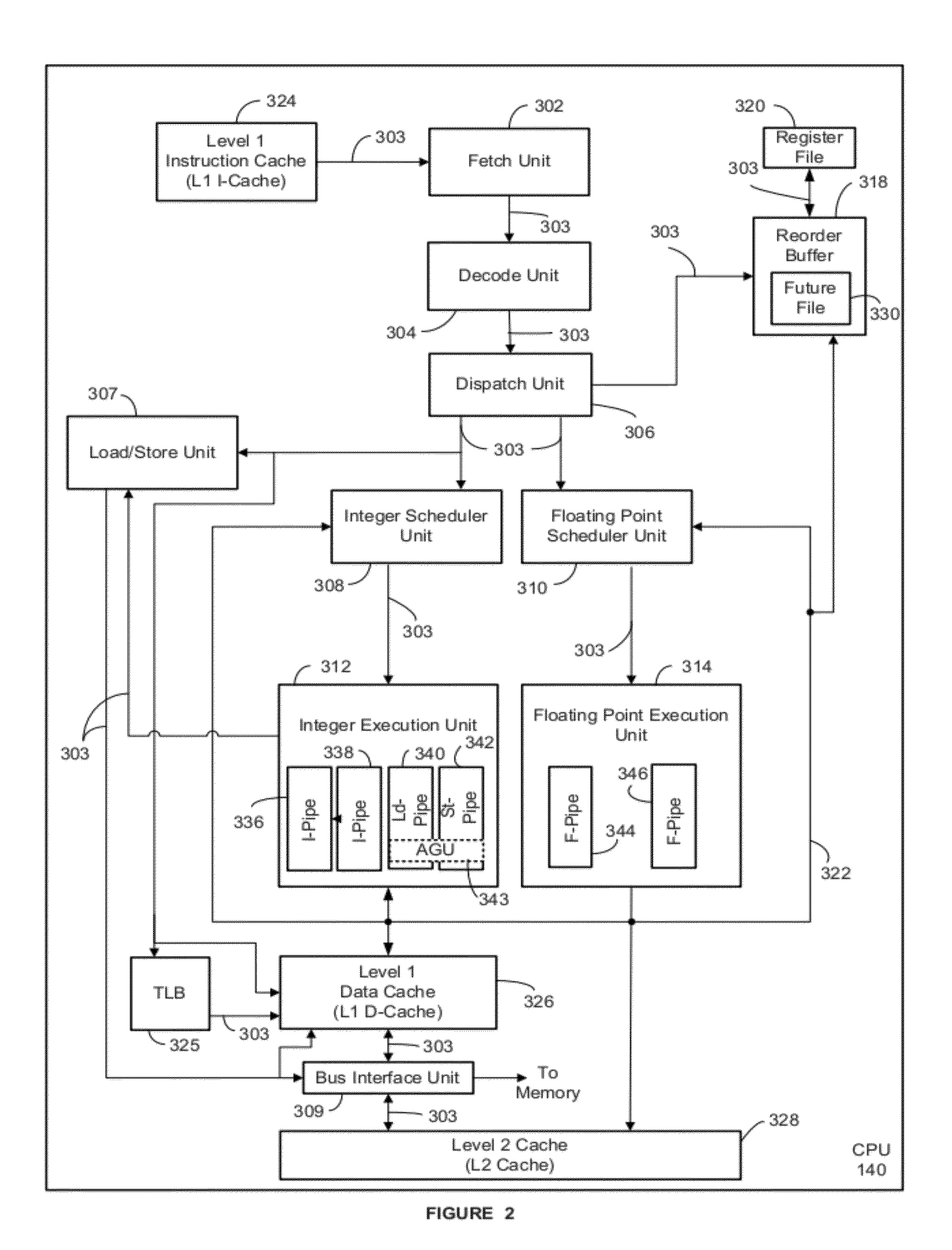
Processor with a function to prevent illegal execution of a program, an instruction executed by a processor and a method of preventing illegal execution of a program
InactiveUS6704872B1Prevent executionAvoid prolonged useUnauthorized memory use protectionHardware monitoringManagement unitComputerized system
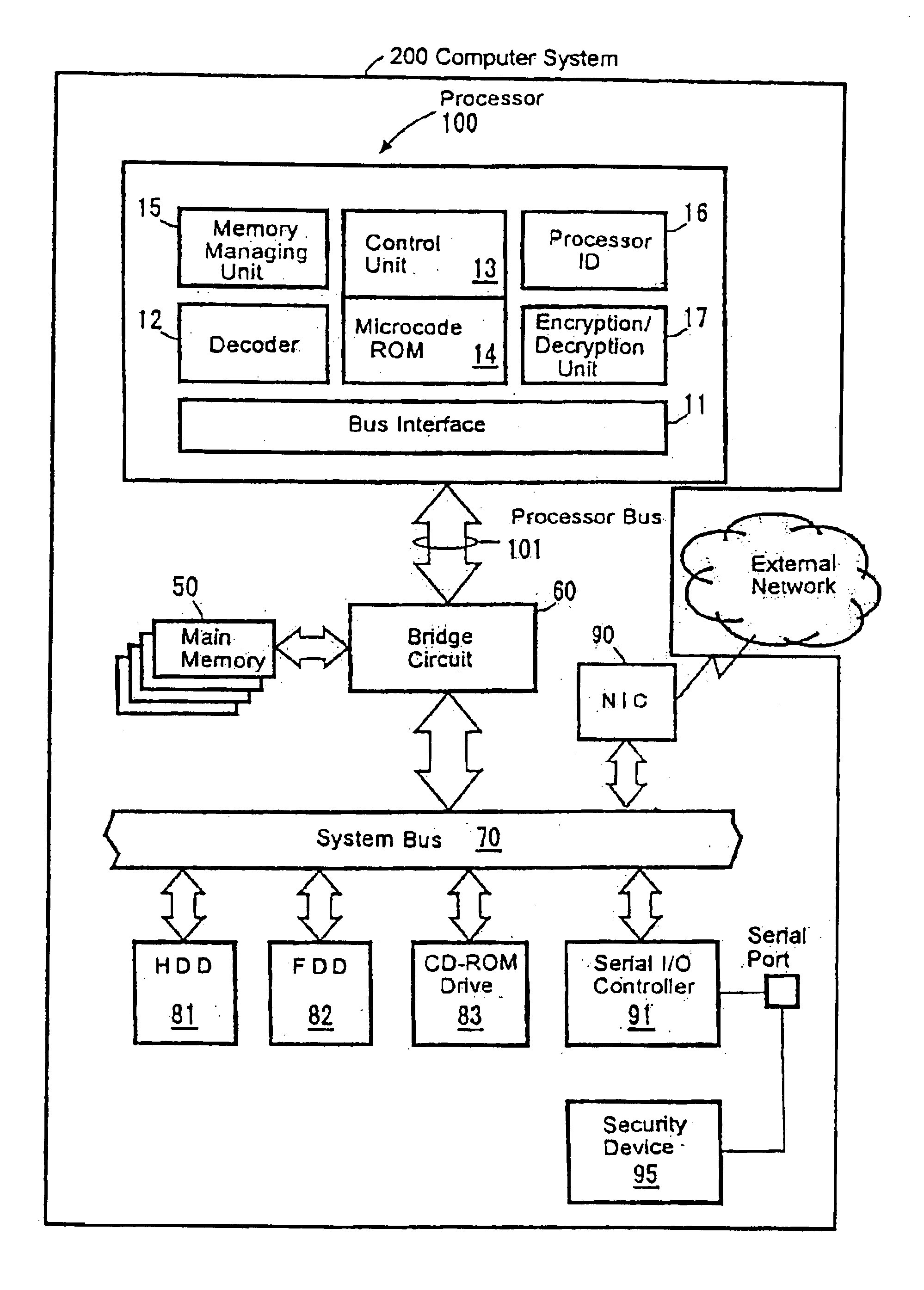
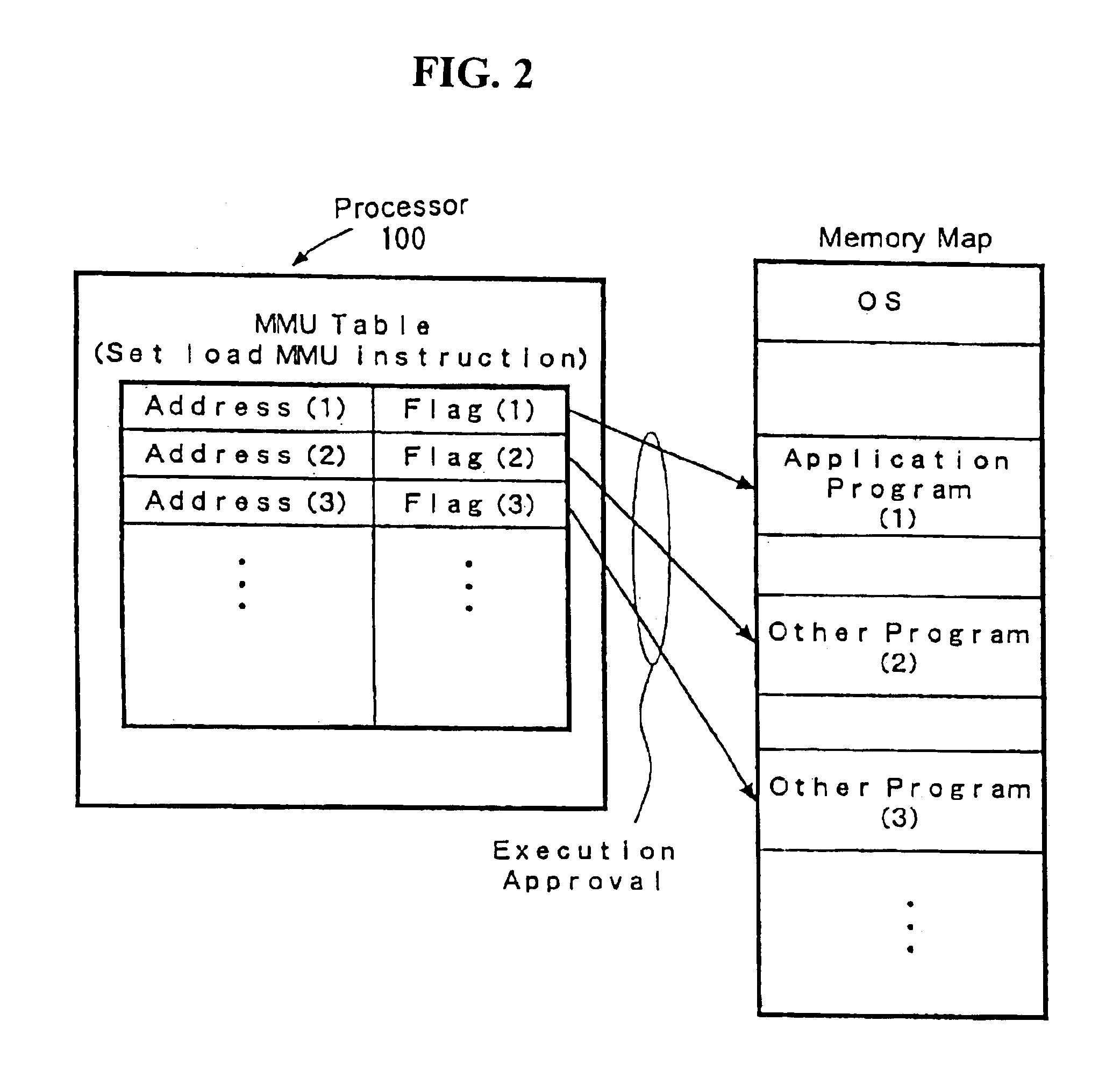
The present invention provides an improved technology of preventing illegal use and execution of a software program provided to a computer system. More particularly, the present invention is directed to a Processor of a type in which a memory managing unit is installed therein to manage storing operation of code / data in main memory and includes, as one of instruction set, an execution permitting instruction to permit execution of a program code (application) in the main memory. The procedure of execution permitting instruction is defined by a microprogram and includes an authentication procedure for authenticating the right to use the program beside a procedure for setting predetermined data in the memory managing unit in this invention. Execution of the software program is permitted only when the authentication processing is completed successfully. Because the authentication operation is performed within the processor, it is almost impossible to monitor or detect it from the exterior. Also, by using a processor ID unique to the processor chip as identification information for use in the authentication processing, the right to use a specific software program can be limited to a single processor.
Owner:GOOGLE LLC
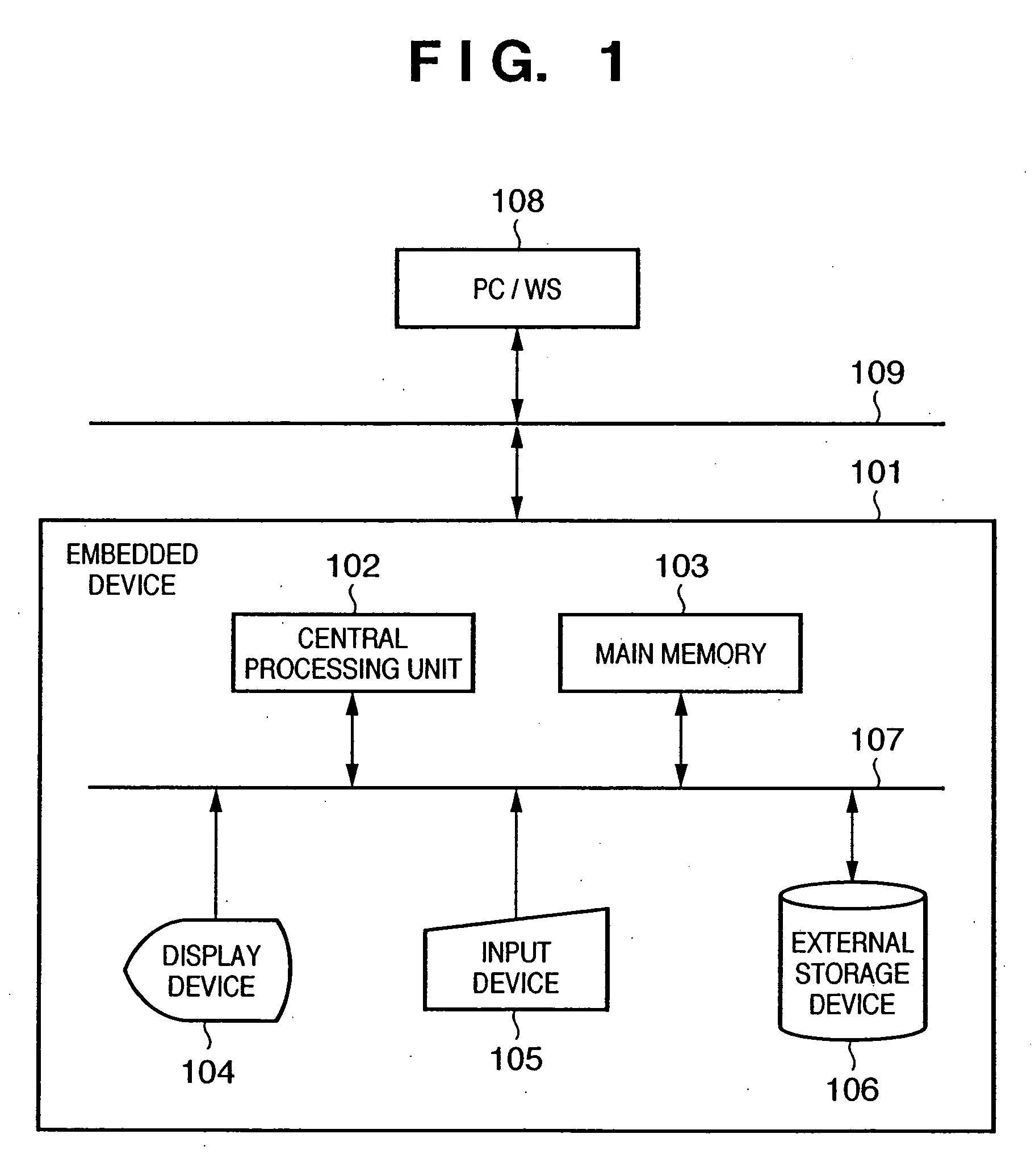
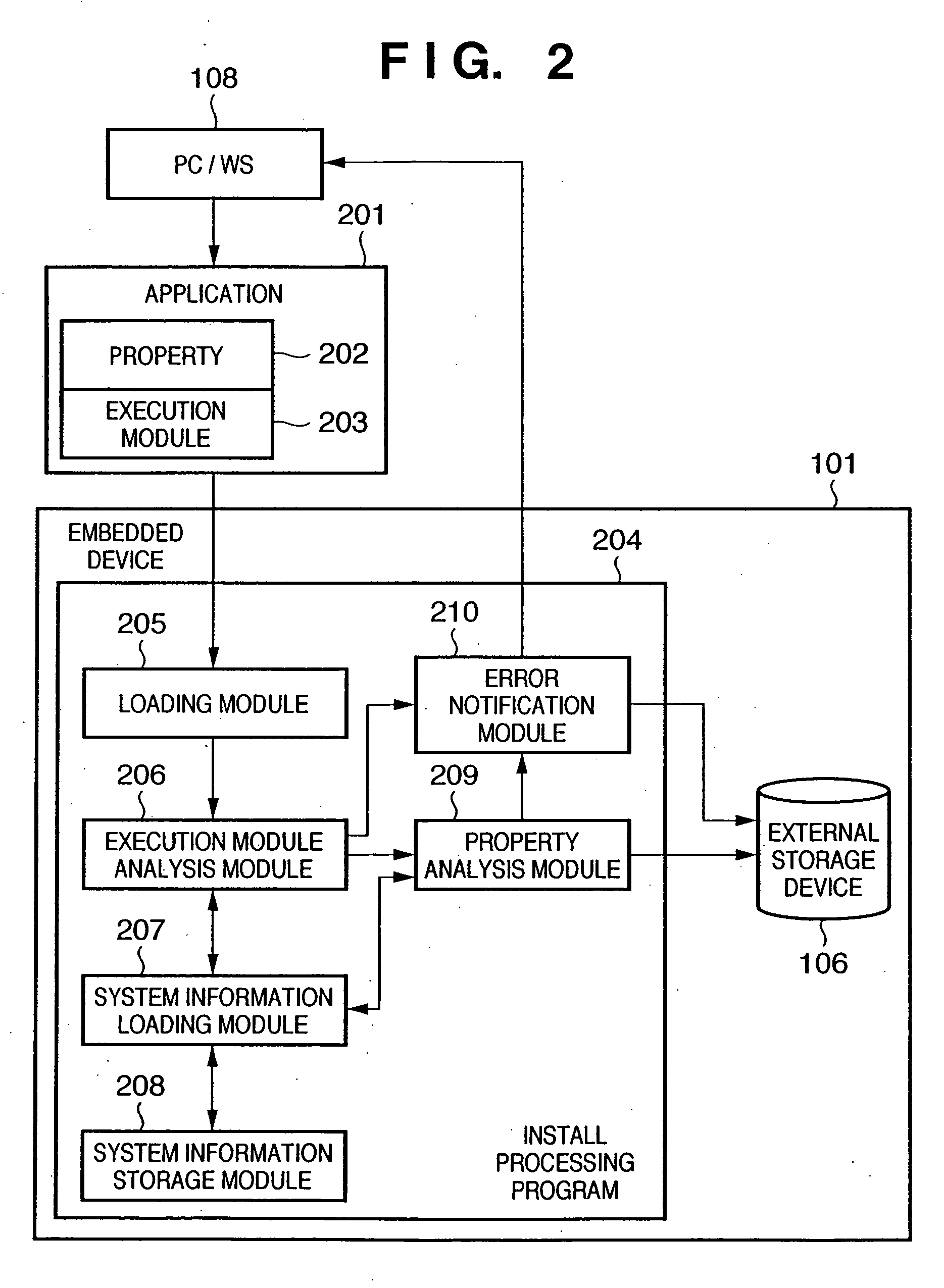
Install processing apparatus, processing method, storage medium, and program
InactiveUS20060230398A1Avoid installationPrevent executionData processing applicationsError detection/correctionComputer scienceSystem information
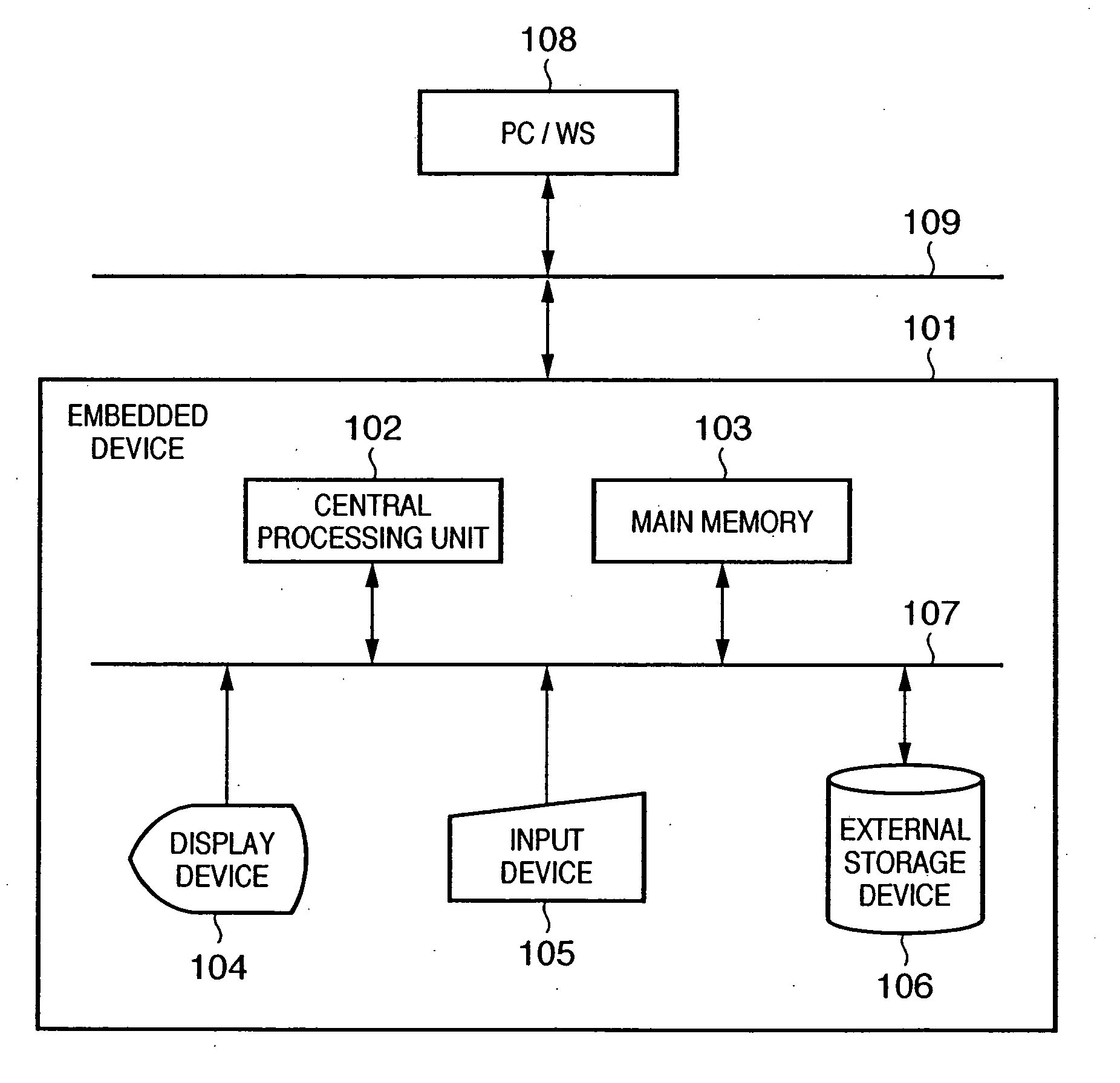
An object of this invention is to prevent installation of an unnecessary application into an embedded device. To achieve this object, a control program according to this invention includes a module (208) which stores system information of an embedded device (101), a module (205) which loads an application (201), an module (206) which determines on the basis of a loaded execution module (203) and the system information whether the application (201) normally operates, a module (209) which determines on the basis of a property (202) and the system information whether the application (201) normally operates, and a module (210) which outputs an error when the application is determined not to operate normally.
Owner:CANON KK
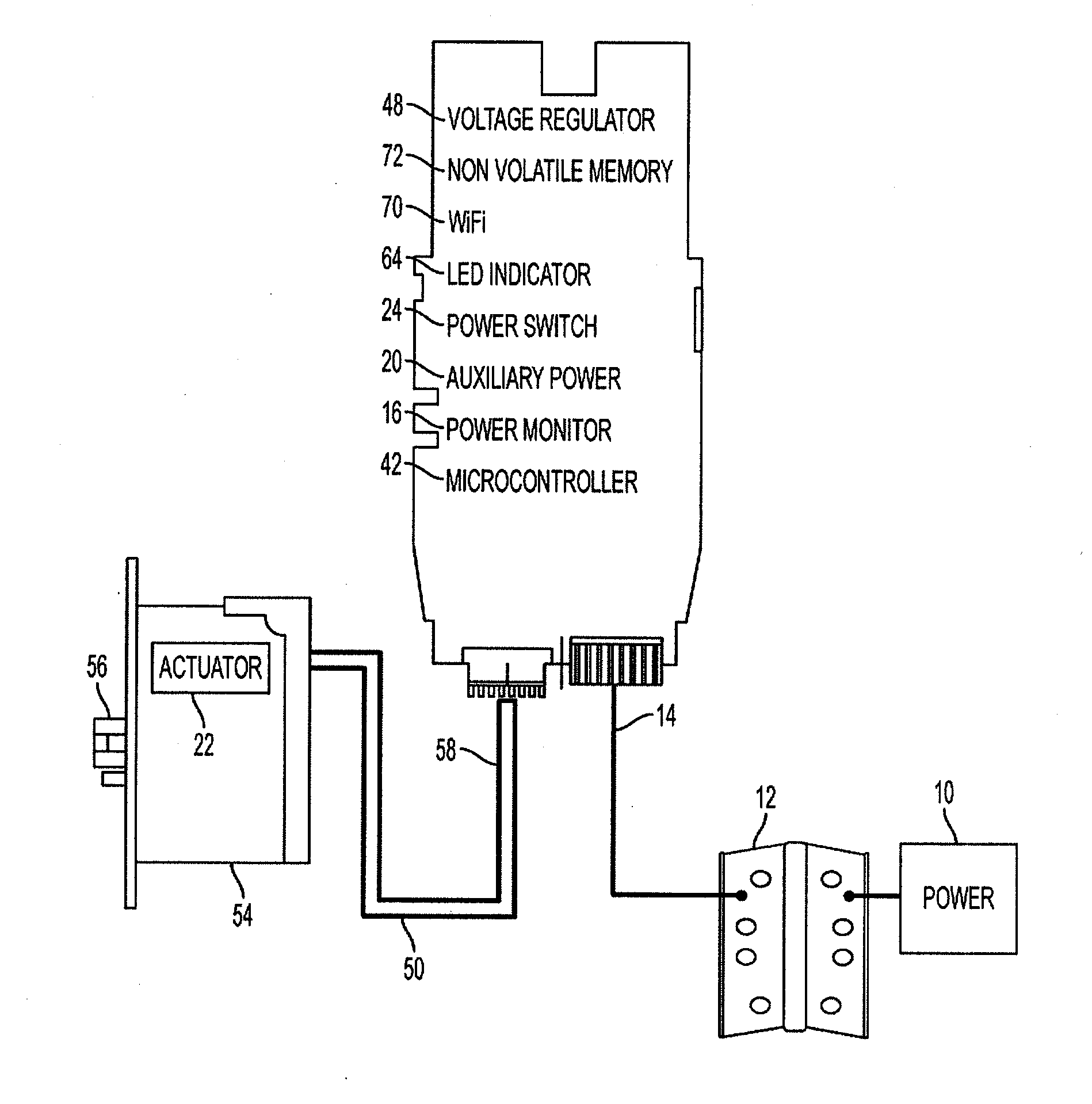
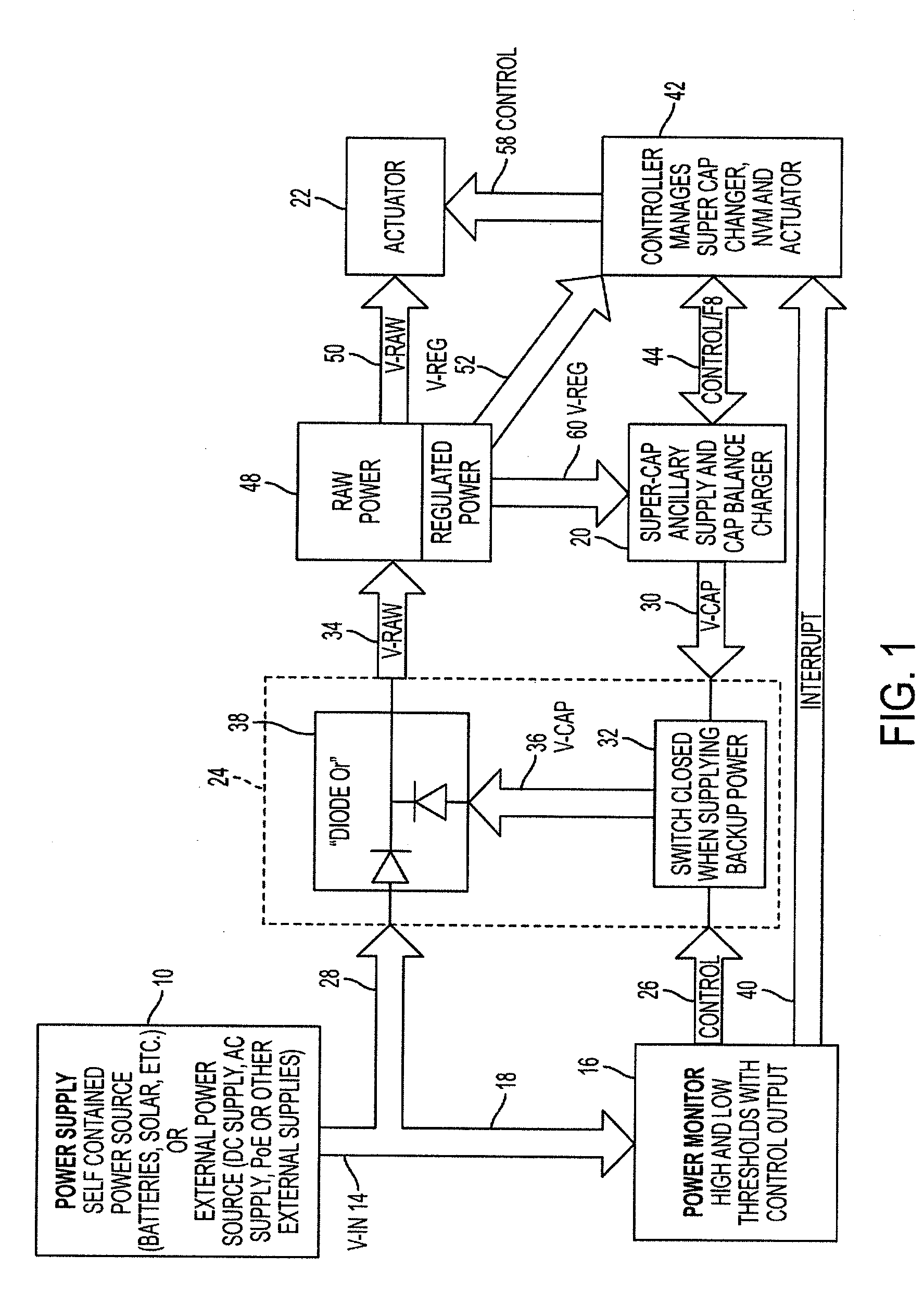
Electronic lock with power failure control circuit
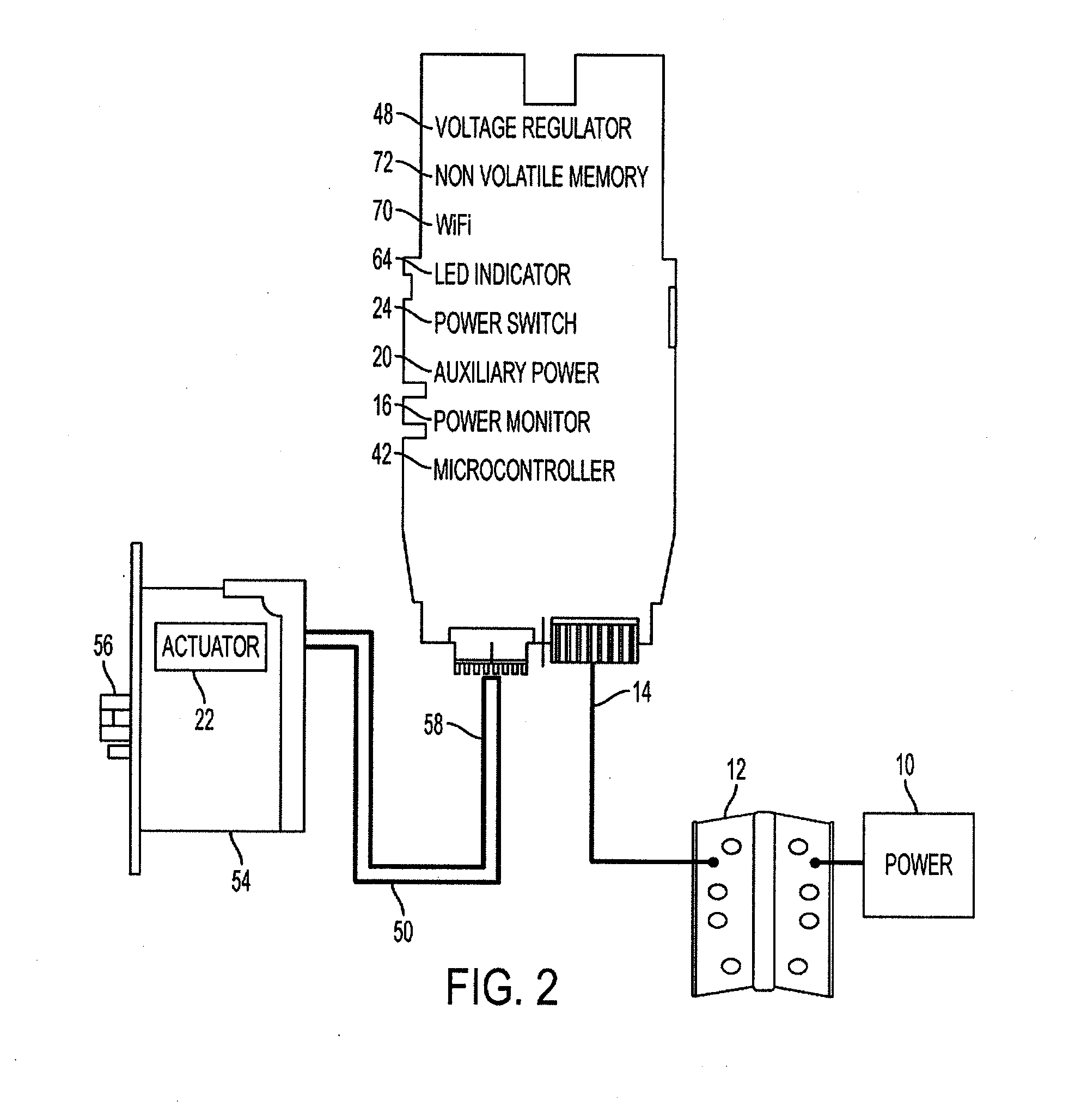
ActiveUS20120169453A1Prevent executionProgramme controlNon-mechanical controlsExecution controlEngineering
An electronic lock with power failure control circuit includes a lock mechanism having a latchbolt movable between extended and a retracted positions and an electrically powered lock actuator to lock and unlock the latchbolt. The power failure control circuit includes a microcontroller and the lock is connected to a primary power source and an auxiliary power source, preferably supercapacitors and charger that can be turned on by the microcontroller and off when the charger signals a full charge. A power monitor circuit detects low voltage on the primary power supply and sets a power failure interrupt causing the microcontroller to execute power failure instructions that control the actuator so that the lock is placed into a desired locked or unlocked final state during the power failure. upon detection of the return of good power, the system resets the lock.
Owner:SARGENT MANUFACTURING CO INC
Software security
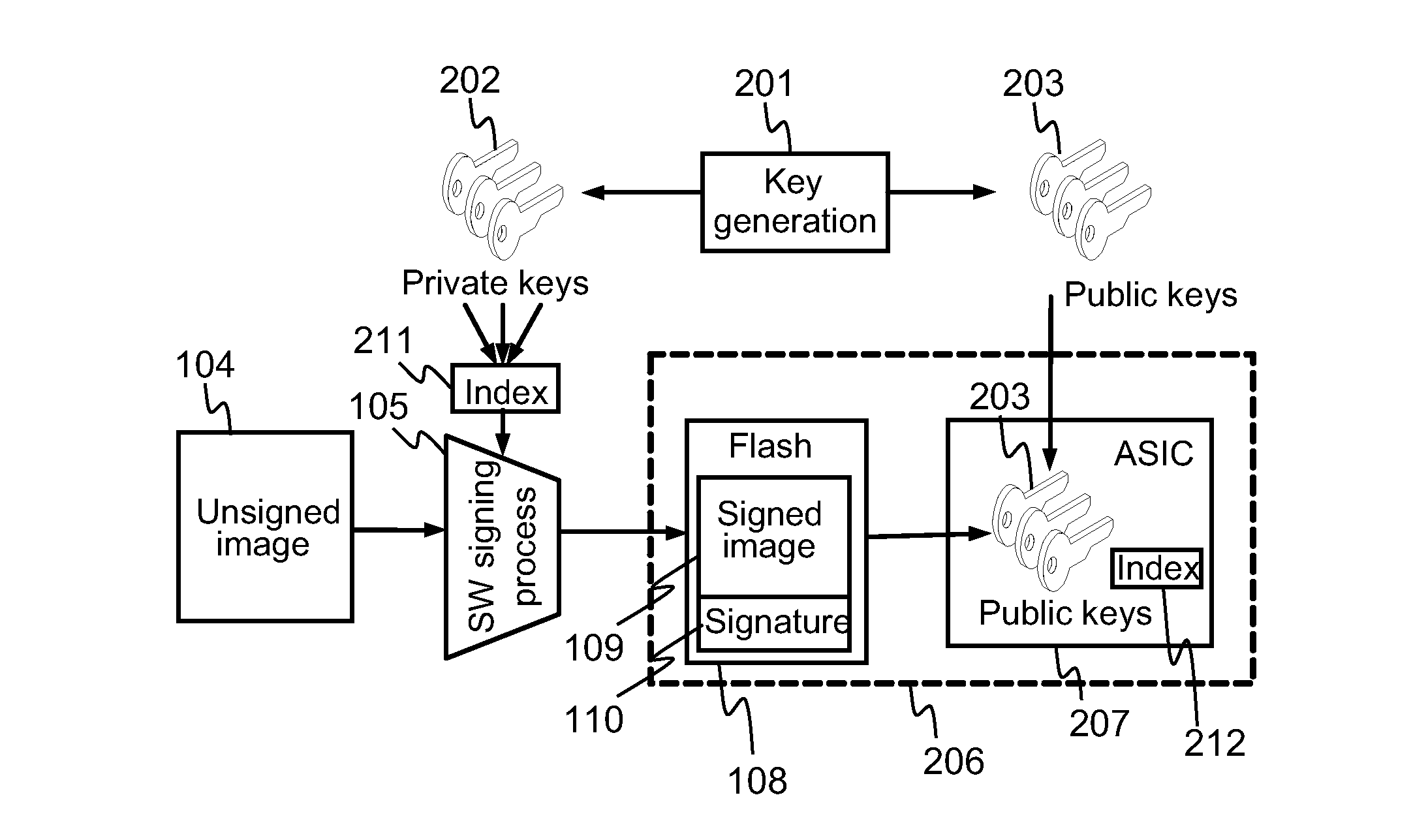
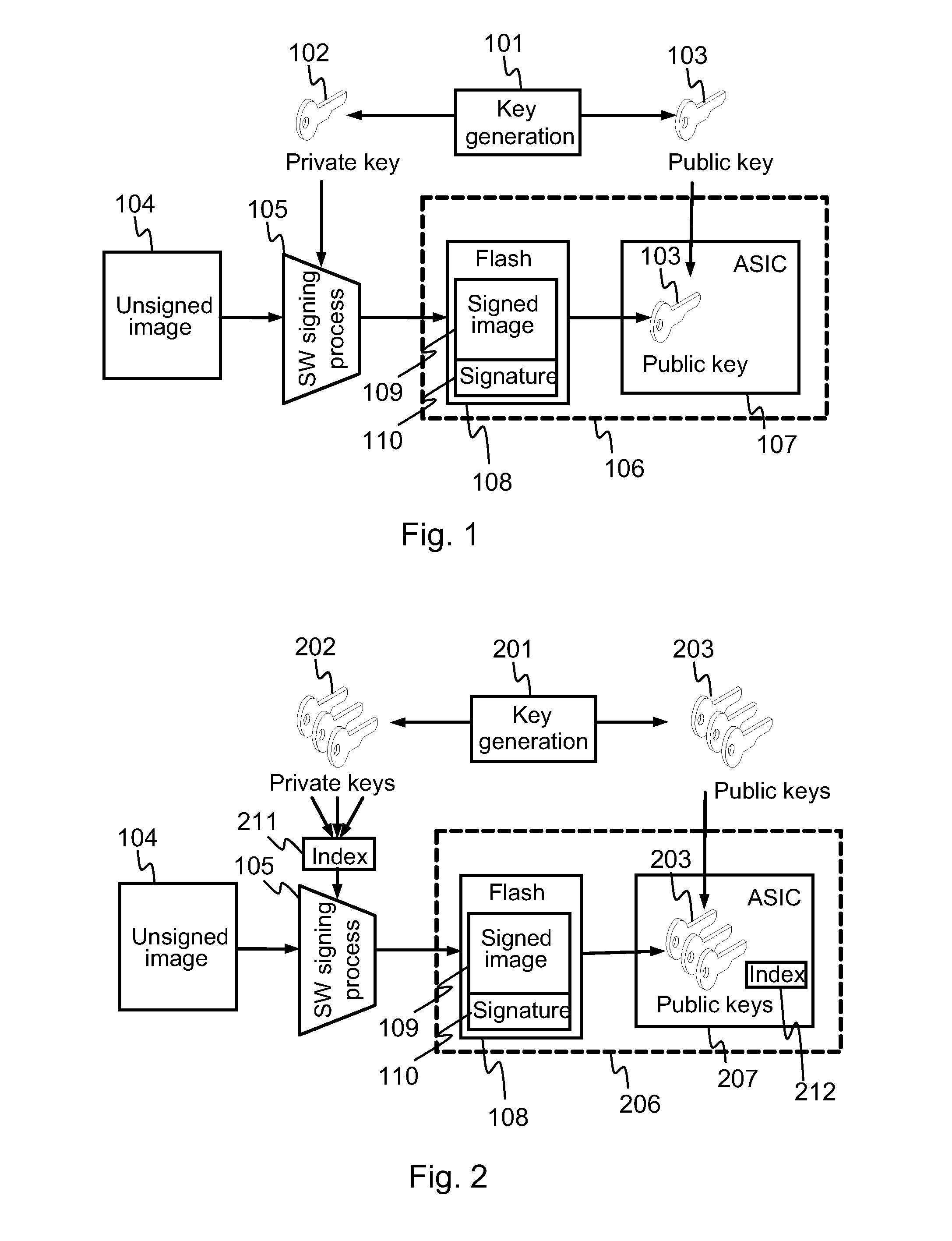
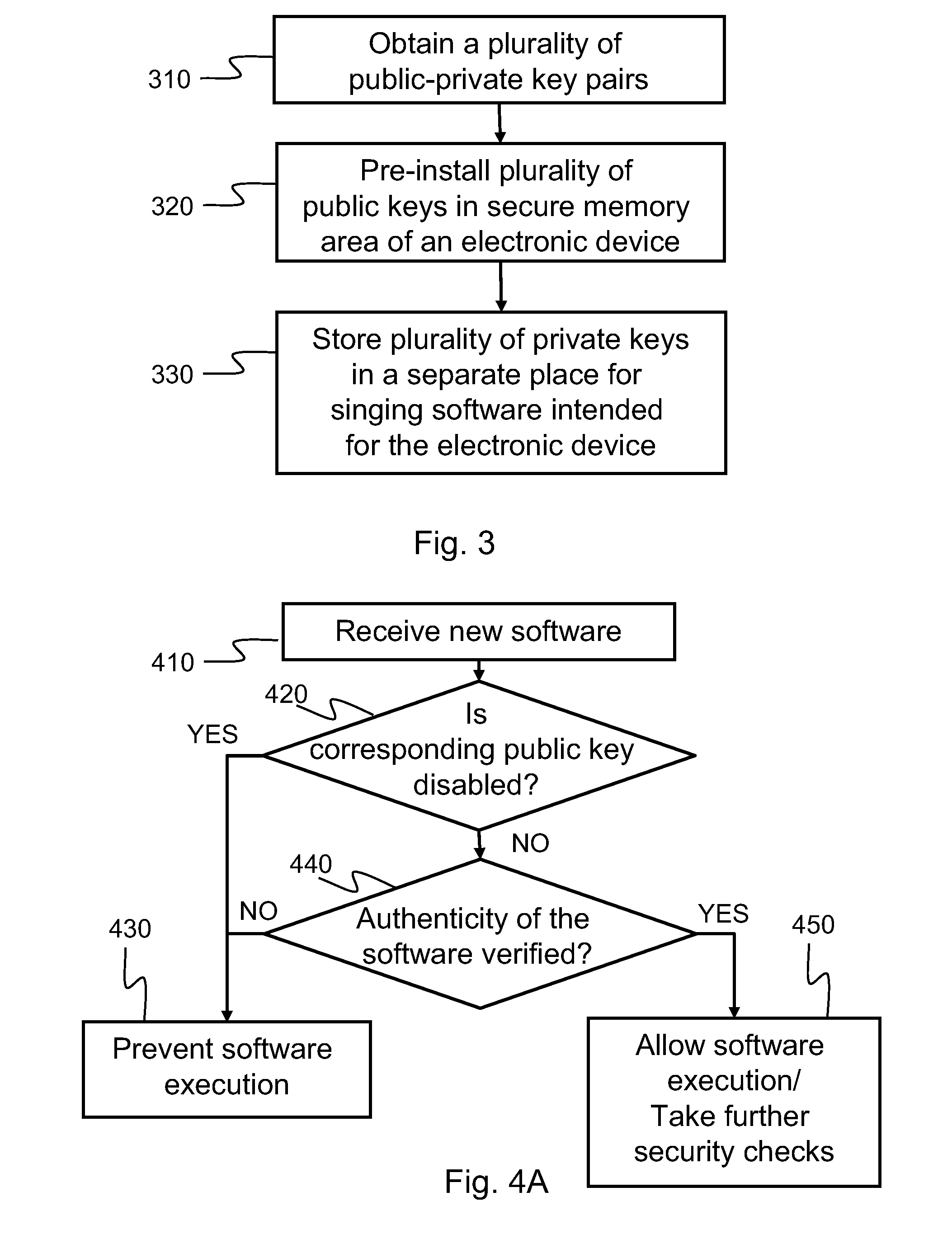
ActiveUS20120110333A1Prevent executionKey distribution for secure communicationMultiple keys/algorithms usageSoftware packageE infrastructure
An apparatus with at least one secure memory area comprising a plurality of pre-installed public keys for verifying software authenticity. The apparatus is caused to receive an indication that a software package signed with a private key according to public key infrastructure has been received; check from the secure memory area, whether a public key associated with the private key with which the software package has been signed, is disabled; and if the public key associated with the private key is disabled, prevent execution of the received software package, and otherwise, proceed to verify authenticity of the received software package using the public key associated with the private key.
Owner:NOKIA TECHNOLOGLES OY
Information processing apparatus, executability determining method, and computer program for the same
InactiveUS20050262496A1Prevent executionEffective guidanceDigital data processing detailsUnauthorized memory use protectionComputer programDatabase
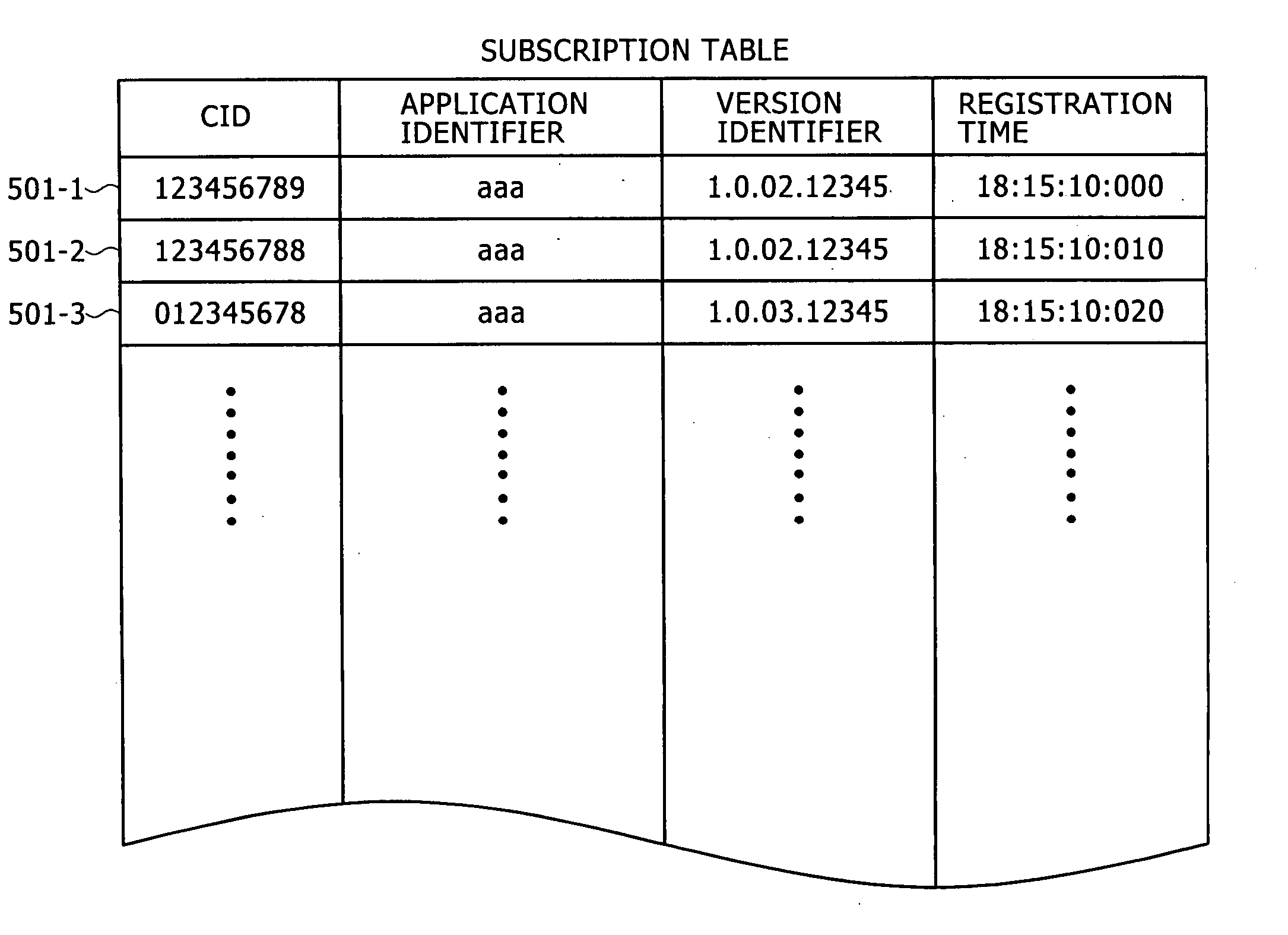
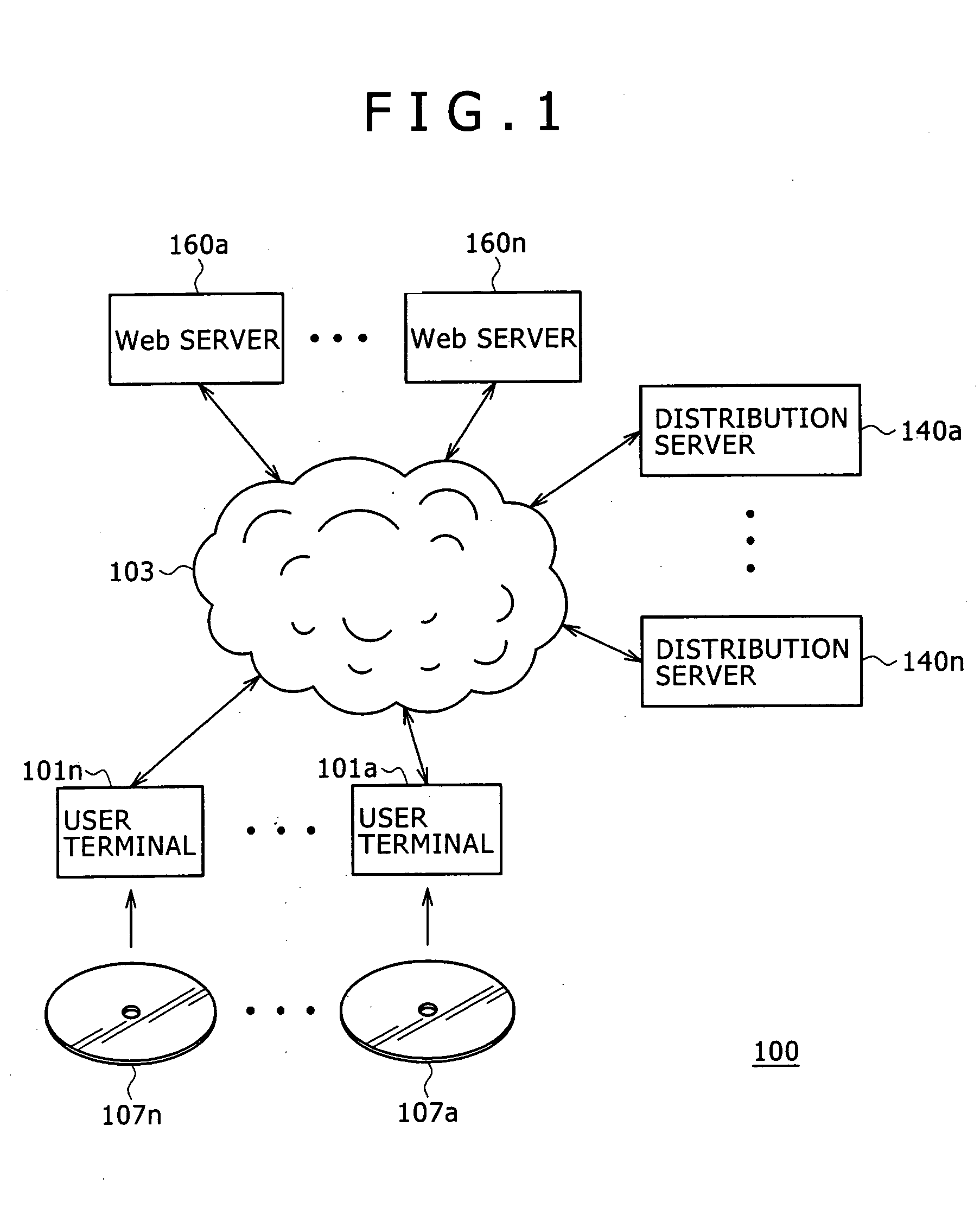
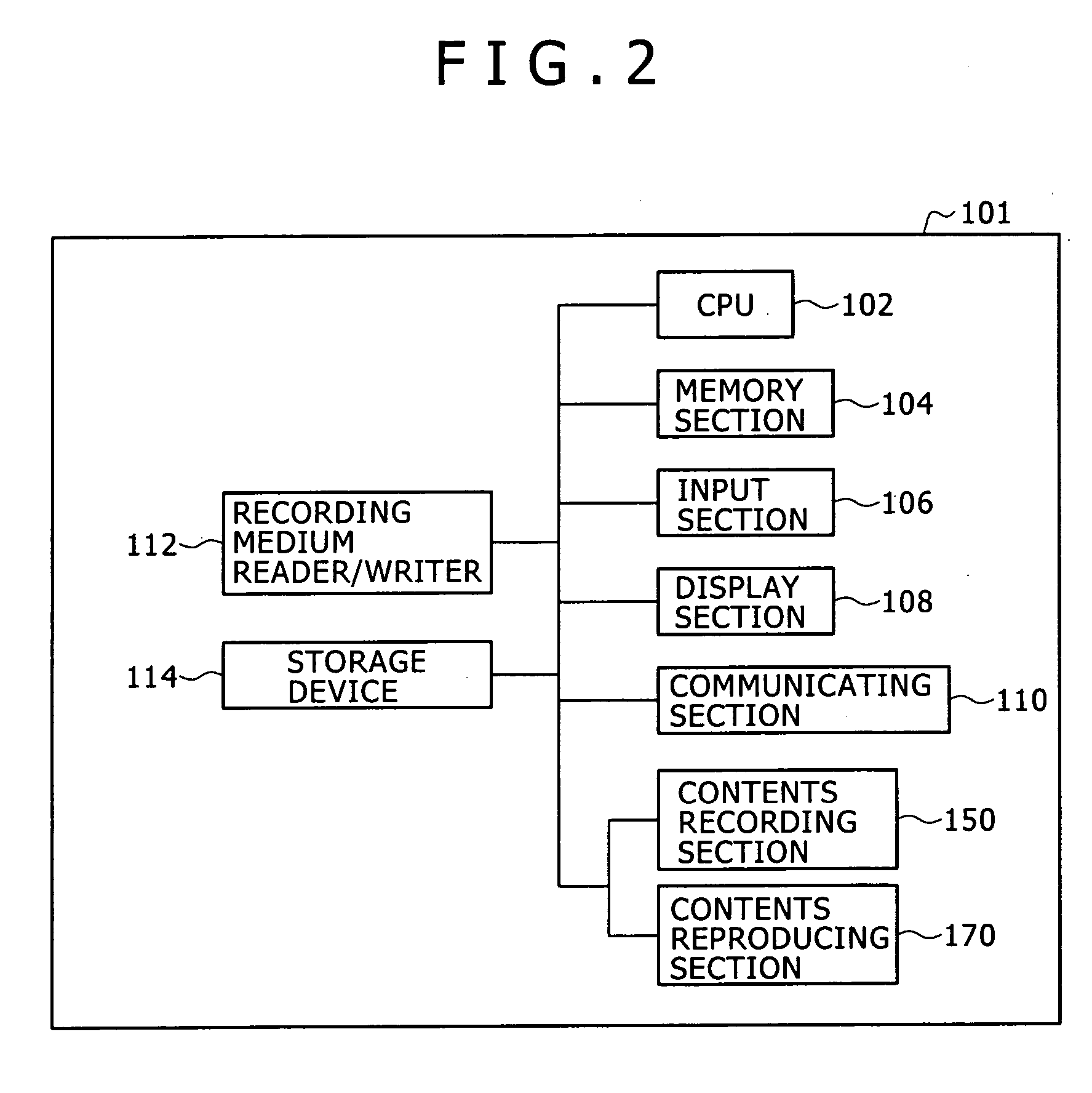
The present invention provides an information processing apparatus, an executability determining method and a computer program for the same. The information processing apparatus according to the present invention includes a list fetching section for fetching from outside disabled contents list information indicating disabled contents information disabling execution of an application program, when the contents data is subjected to a contents data reproducing / copying process for at least reproducing or copying the contents data, including a type and / or a version of the application program; and a verifying section for verifying a type and / or a version of an application program identified by referring to a starting file fetched together with the disabled contents list from the outside to at least one or more disabled contents information described in the disabled contents list information. When it is determined as a result of verification that a type and / or a version of the application program identified by referring to the starting file corresponds to a type and / or a version of any disabled application program described in the disabled contents list information, the starting file is not distributed to the application program.
Owner:SONY CORP
Electric document anti-disclosure system and its implementing method
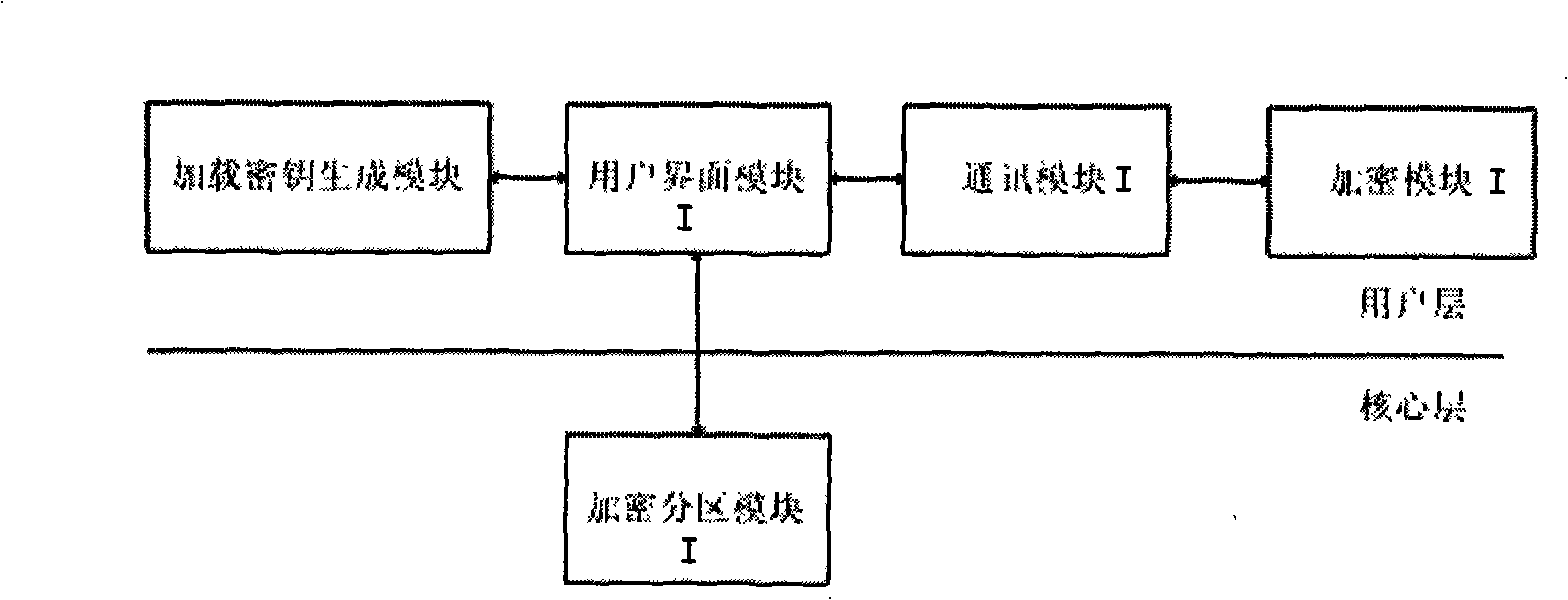
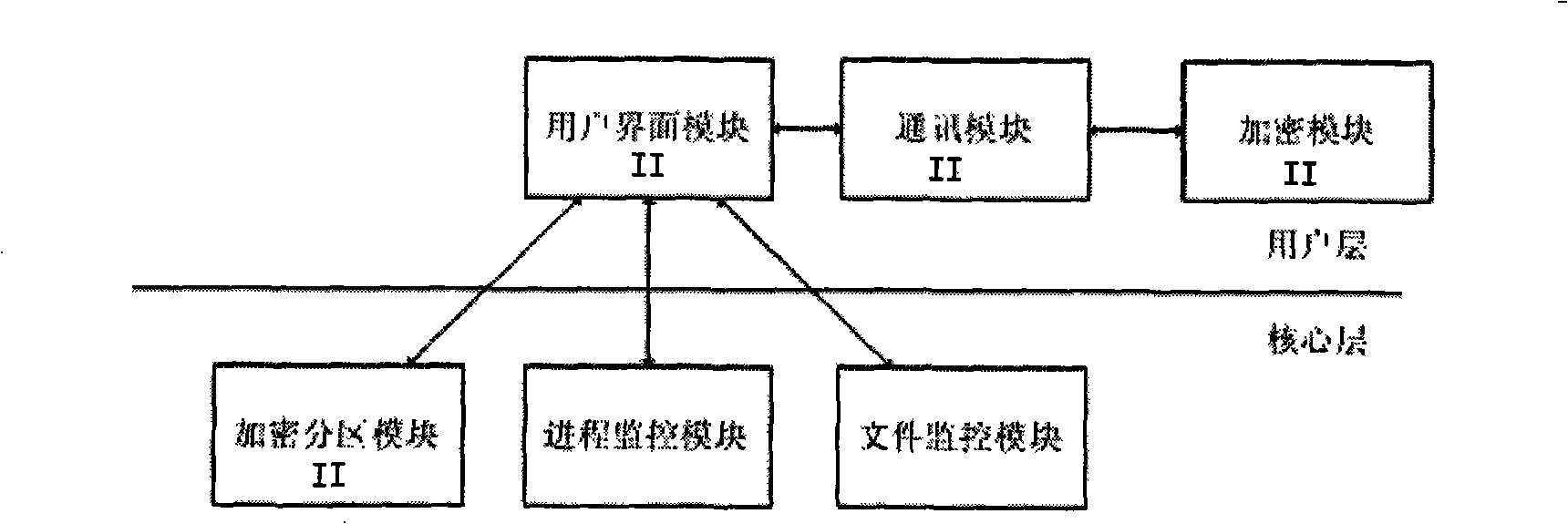
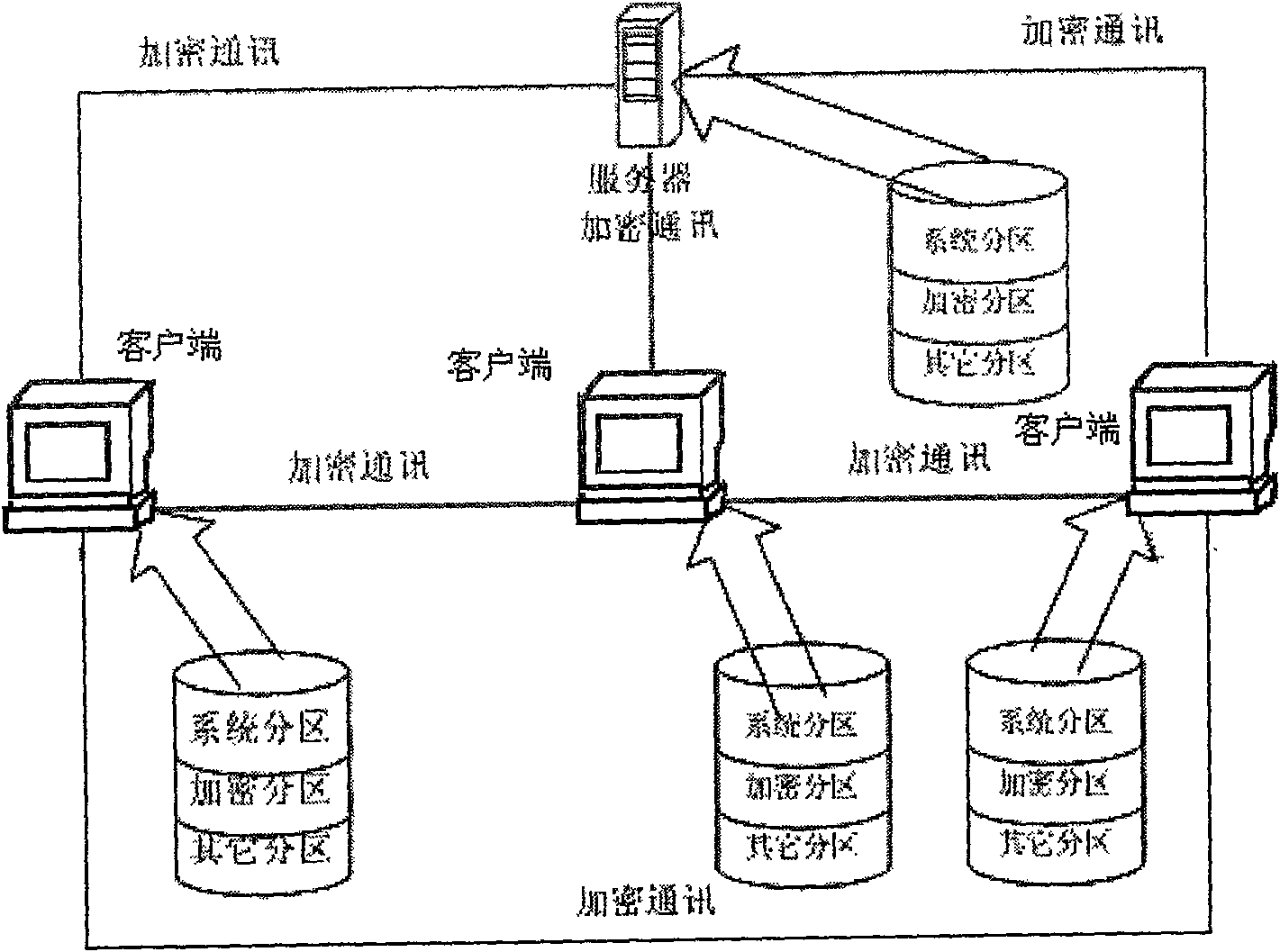
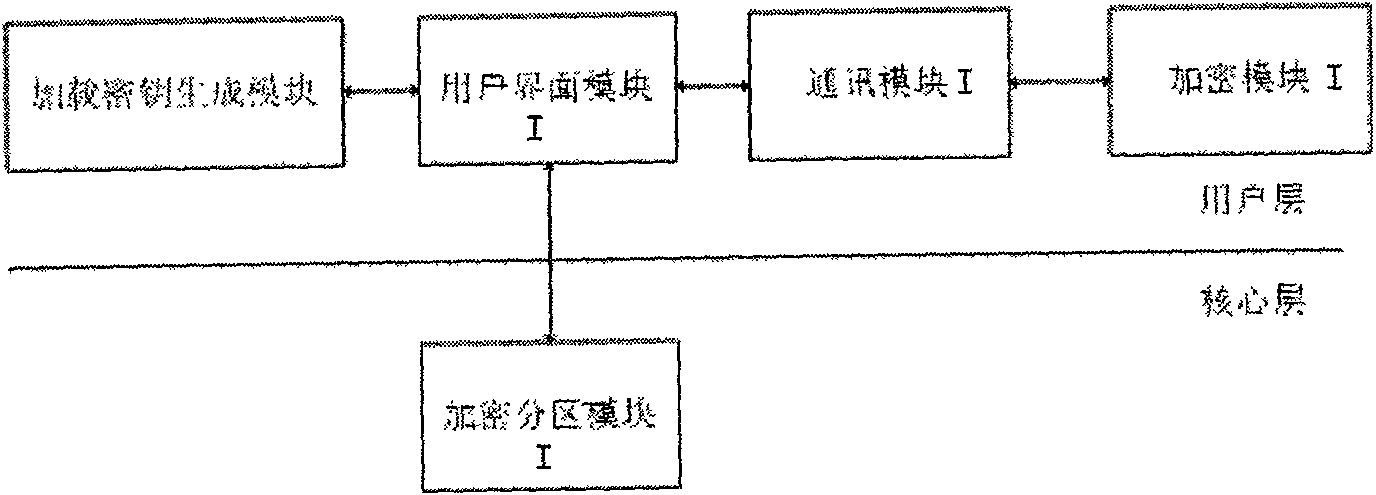
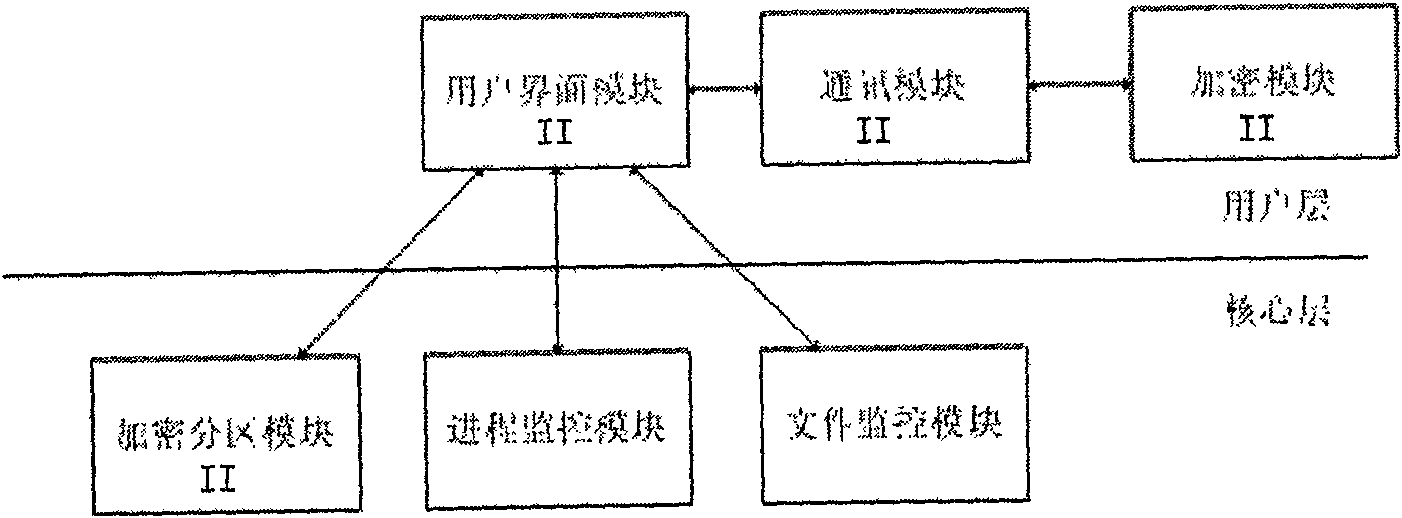
InactiveCN101271497APrevent executionUnlimited useDigital data protectionTransmissionElectronic documentComputer module
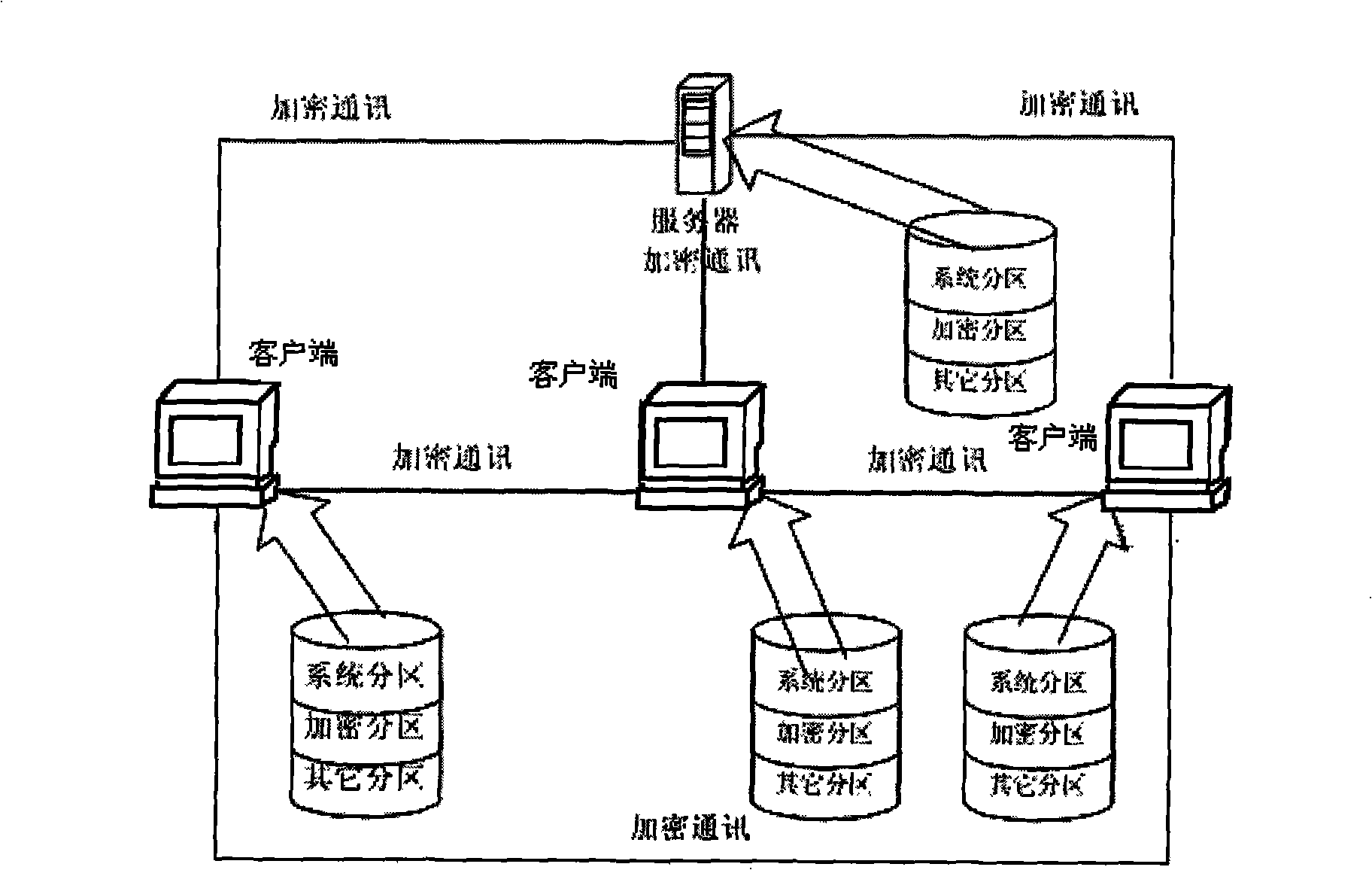
The invention discloses an electronic document divulgence prevention system and a realizing method. The system essentially comprises a server and a client. The server implements an information communication with the client through a computer network. A user interface module I in the server is respectively connected with an encryption division module I, a loading key generation module and a communication module I which is connected with an encryption module I. A user interface module II in the client is respectively connected with an encryption division module II, a process monitoring module, a file monitoring module and a communication module II which is connected with an encryption module II. The realizing method of the system includes the following steps: (1) the server is initialized; (2) the client is initialized; (3) an encryption division is used for the client. The electronic document divulgence prevention system and the realizing method of the invention not only facilitate free communication of electronic documents on the network, but also effectively avoid the divulgence of the electronic documents, thus having good application prospect.
Owner:李硕 +2
Threat isolation using a plurality of containers
ActiveUS20190098019A1Prevent executionPlatform integrity maintainanceTransmissionDistributed computing
Owner:L3 TECH INC
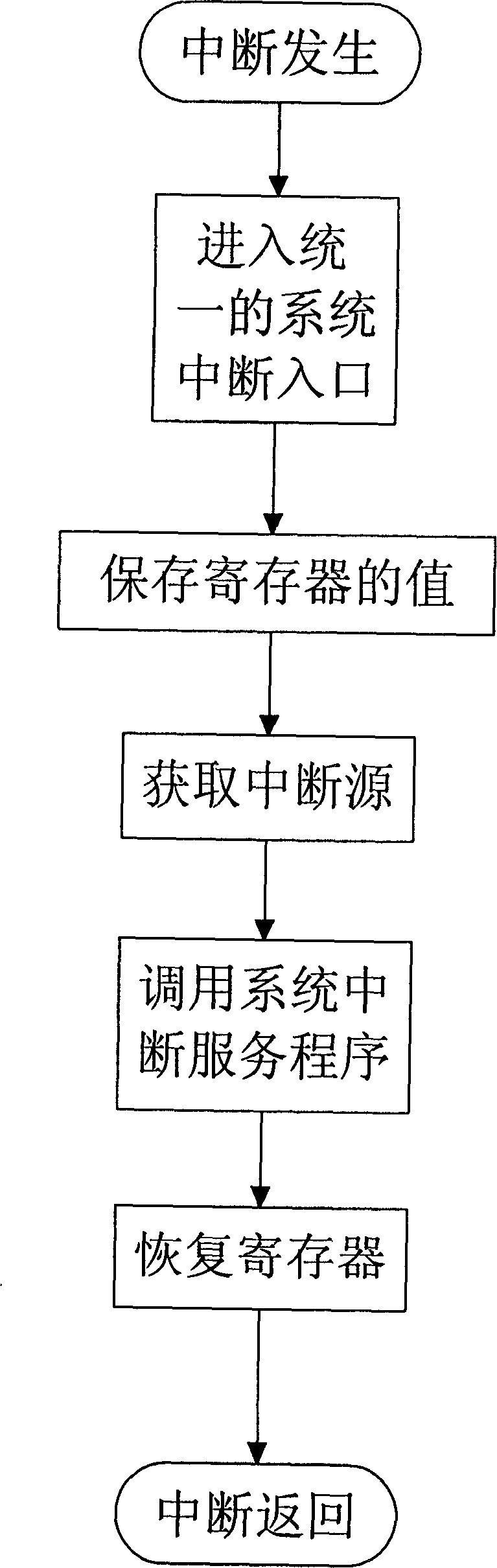
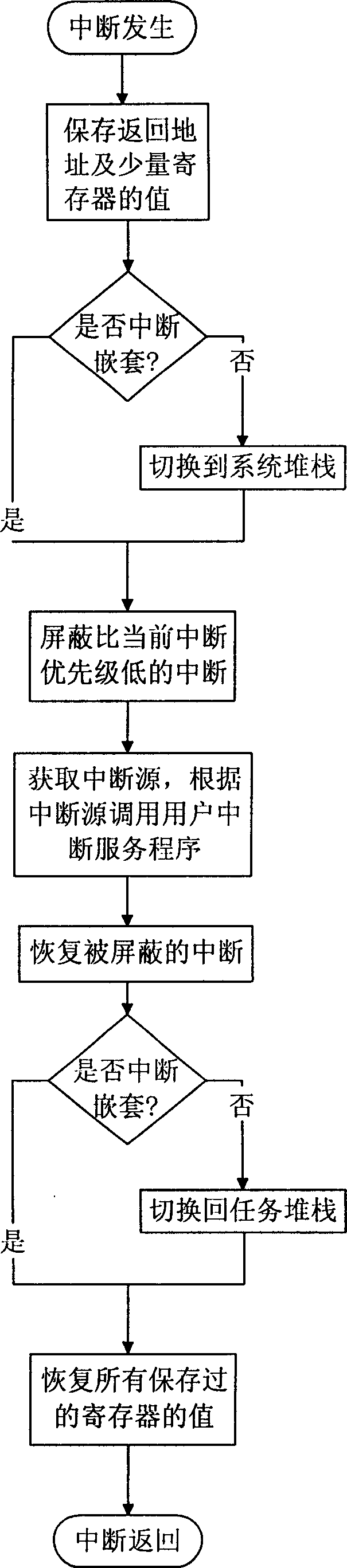
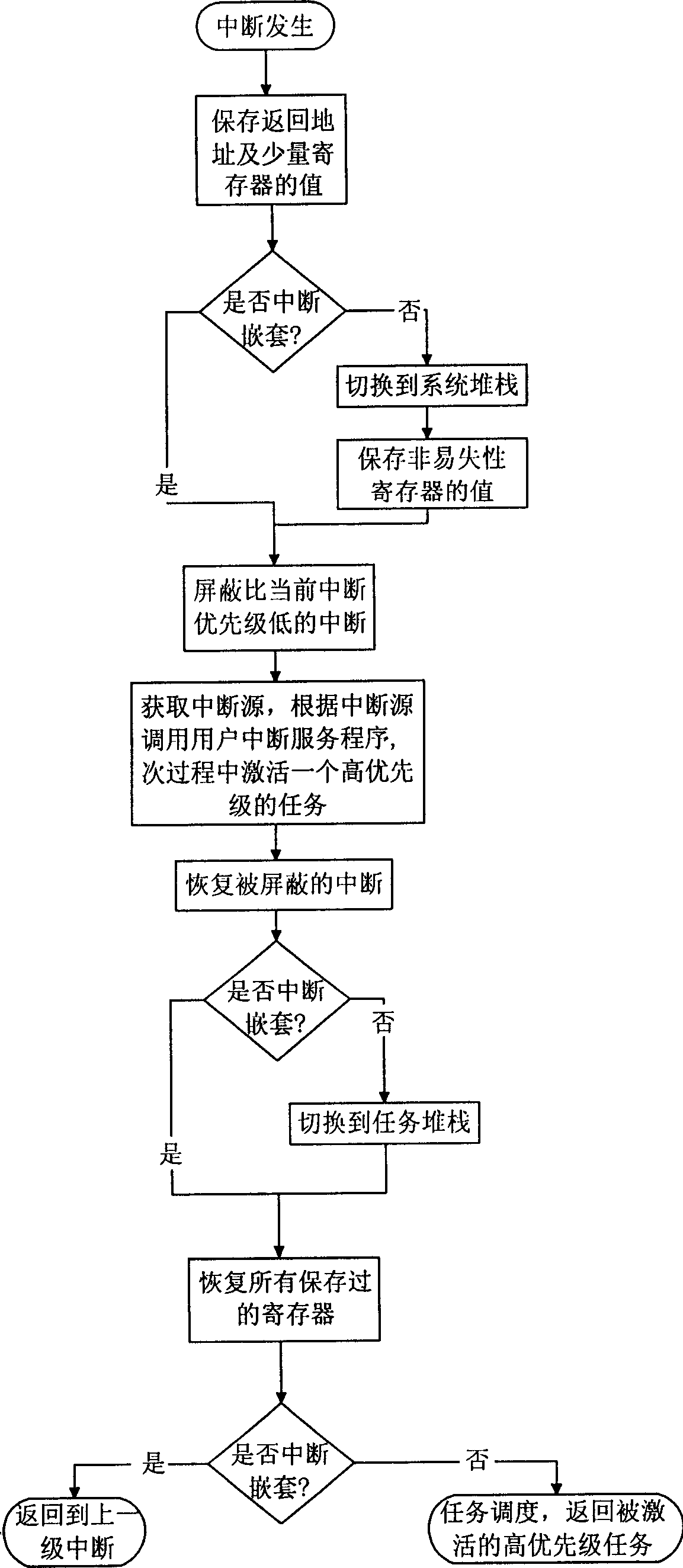
Interrupt managing method for embedded operation system based on PowerPC system structure
InactiveCN1783020APrevent executionImprove execution efficiencyProgram initiation/switchingOperational systemPowerPC
The interrupt management method for embedded operation system based on PowerPC system structure includes the following steps: dividing interrupts into two classes of system interrupt and user interrupt and dividing user interrupt service programs into class-I interrupt service program and class-II interrupt service program; first hardware responding the user interrupt; then, maintaining the context, stack switching and interrupt nesting for resuming the interrupted task after interrupt treatment; finding out and calling corresponding interrupt service program from the user interrupt vector list via the interrupt source; and maintaining the interrupt nesting and stack switching, restoring the context for the treater to resume the interrupted task. The present invention has the advantages of raised interrupt executing efficiency, raised interrupt utilizing efficiency, convenient interrupt control and use, raised user stack size controllability and predicting property.
Owner:ZHEJIANG UNIV
Method and system for preventing cross-site scripting attacks
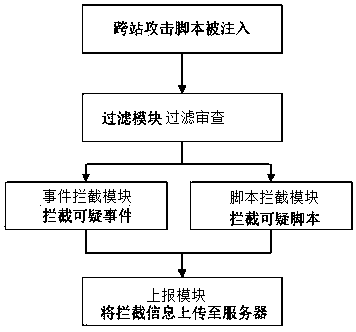
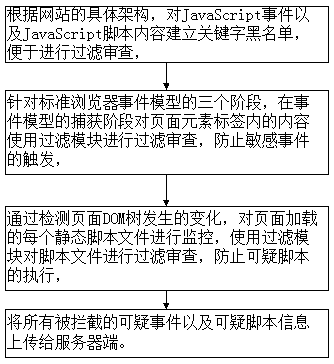
The invention discloses a method and system for preventing cross-site scripting attacks, relating to the field of website security. The method includes the following steps: establishing a keyword blacklist for JavaScript events and JavaScript script contents according to a specific architecture of a website to facilitate filtering review, using a filtering module to perform filtering review on contents of a page element tag in a capture stage of an event model for three stages of a standard browser event model, preventing the trigger of sensitive events, detecting the changes in a page DOM tree, monitoring each static script file loaded on the page, performing filtering review on the script files by using the filtering module, preventing the execution of suspicious scripts, and uploading all intercepted suspicious events and suspicious script information to a server. According to the scheme of the invention, the execution of the sensitive events and attack scripts can be effectively prevented in the case that a Web page has vulnerabilities or the attack scripts are injected into the Web page, the security of the system can be improved, and the cross-site scripting attacks can be effectively prevented.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
Device and method for monitoring connection of blood treatment unit to liquid system of extracorporeal blood treatment device
ActiveCN102946920APrevent executionReliable monitoringDialysis systemsMedical devicesBlood treatmentsMedicine
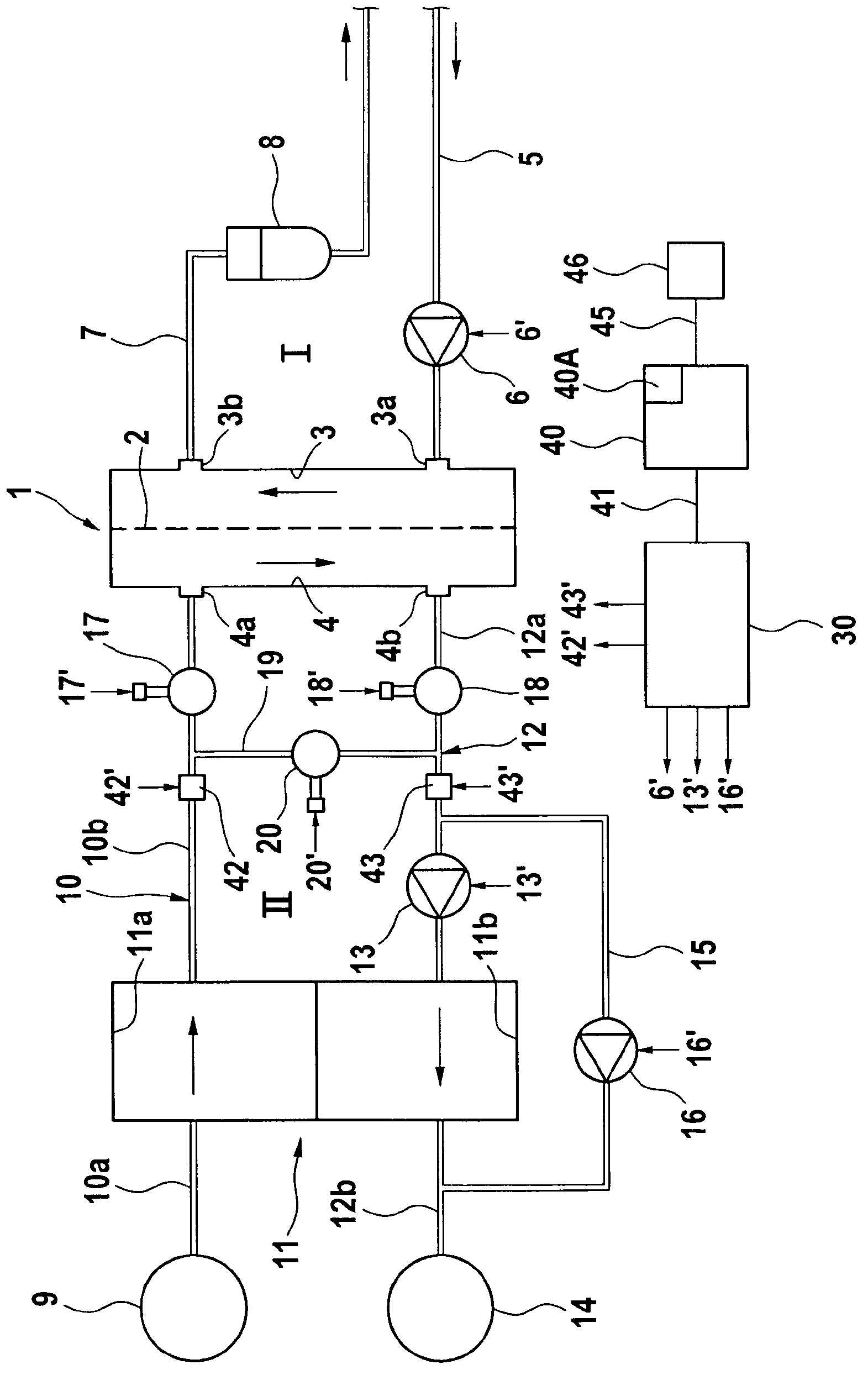
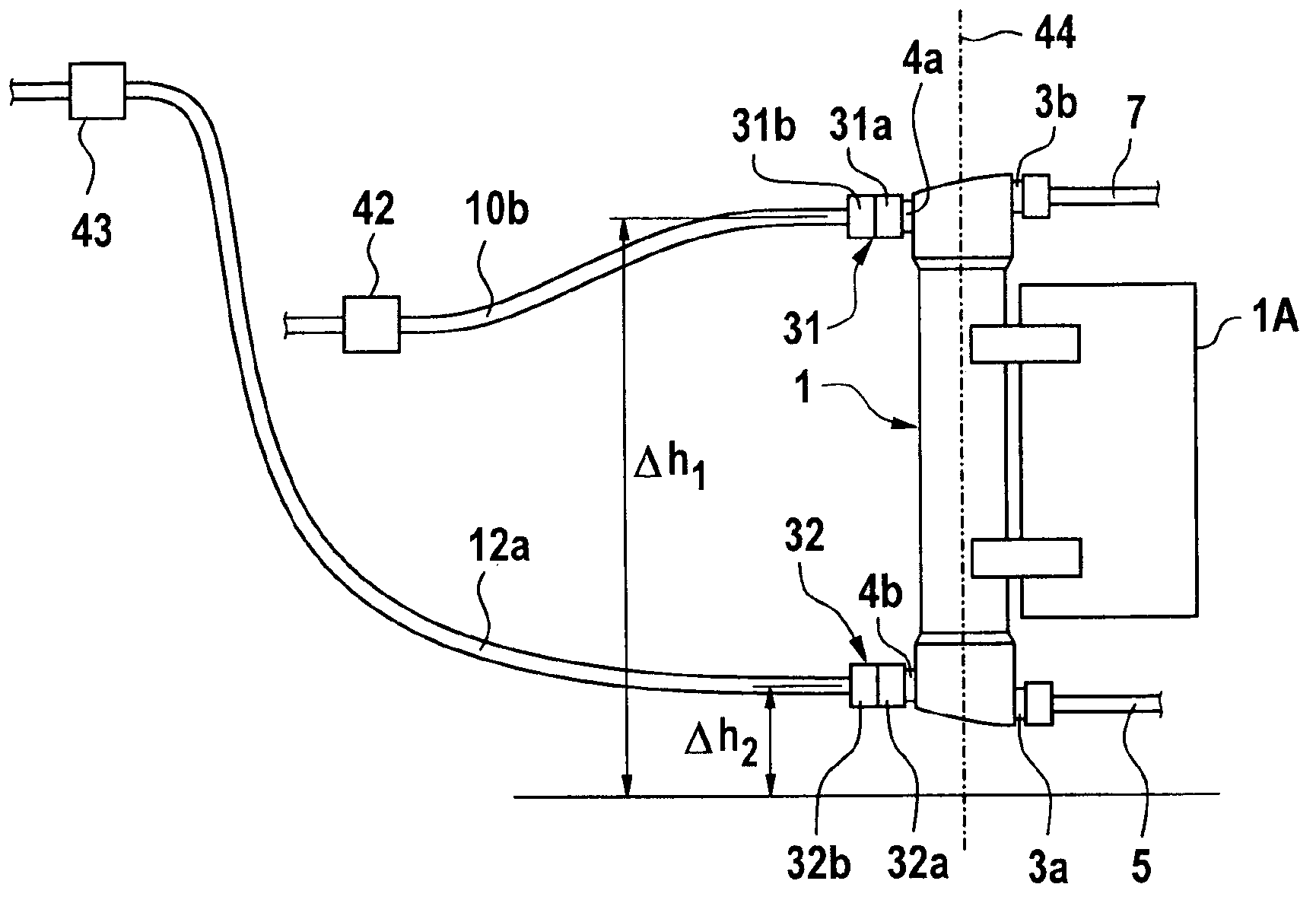
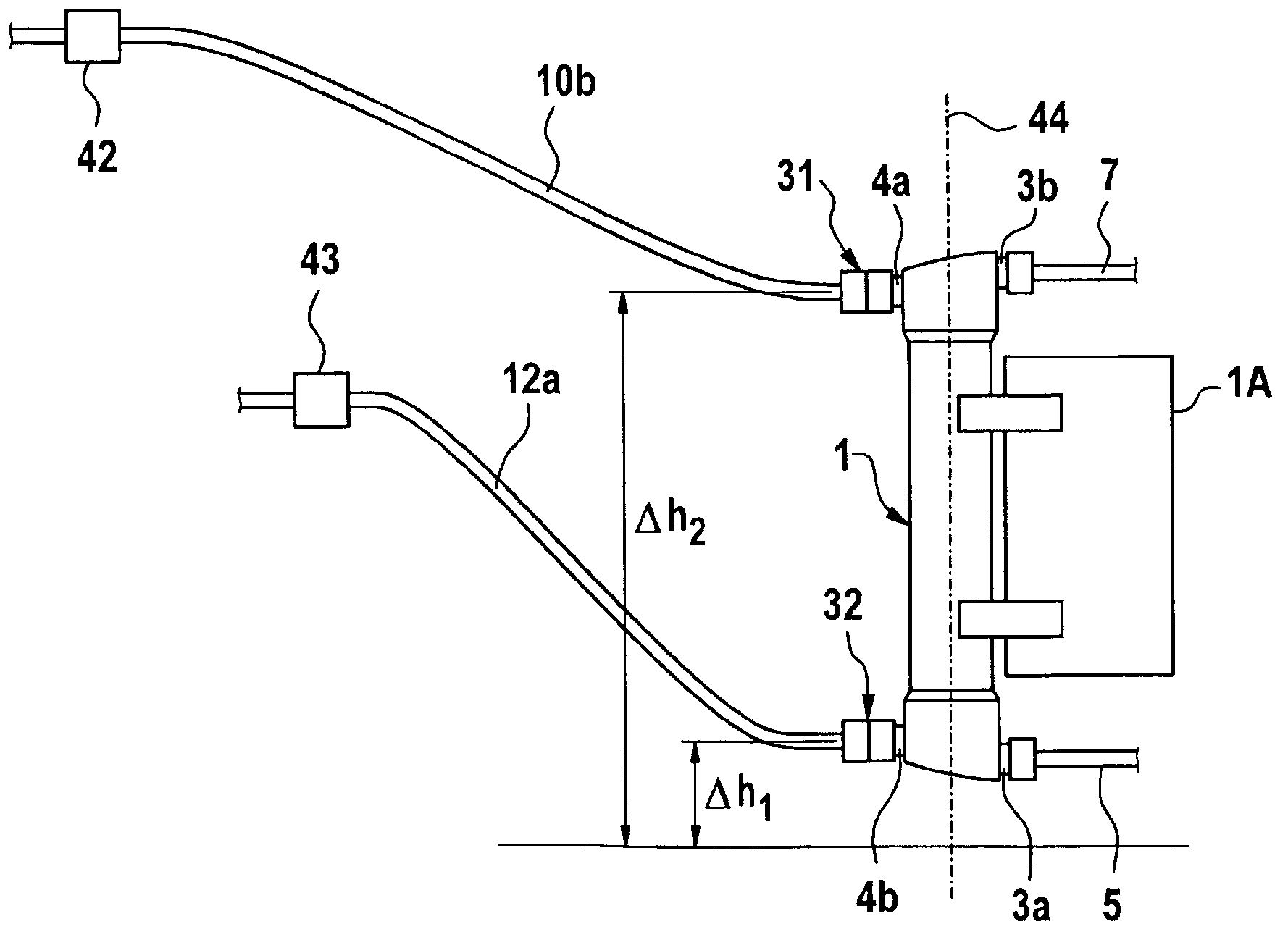
The invention relates to a device and a method for monitoring the connection of a blood treatment unit (1) to the liquid system II of an extracorporeal blood treatment device, wherein the blood treatment unit (1) has an inlet (4a) and an outlet (4b) for connection to the liquid system, and the liquid system has a conduit system with a first conduit section (10b), which is connected to the inlet (4a), and a second conduit section (12a), which is connected to the outlet (4b) of the blood treatment unit (1). The invention further relates to an extracorporeal blood treatment device with a device for monitoring the connection of the blood treatment unit to the liquid system. The device according to the invention and the method according to the invention for monitoring the connection of a blood treatment unit to the liquid system of an extracorporeal blood treatment device are based on measuring the pressure in the liquid system II of the blood treatment device. On the basis of the pressure measurement alone, it is possible to establish whether the connection of the blood treatment unit to the liquid system is in order or not in order.
Owner:FRESENIUS MEDICAL CARE DEUTSCHLAND GMBH
False code prevention method and prevention program and the program recording medium
InactiveCN1886728APrevent executionRespond effectivelyProgram control using stored programsError detection/correctionBuffer overflowPerformed Procedure
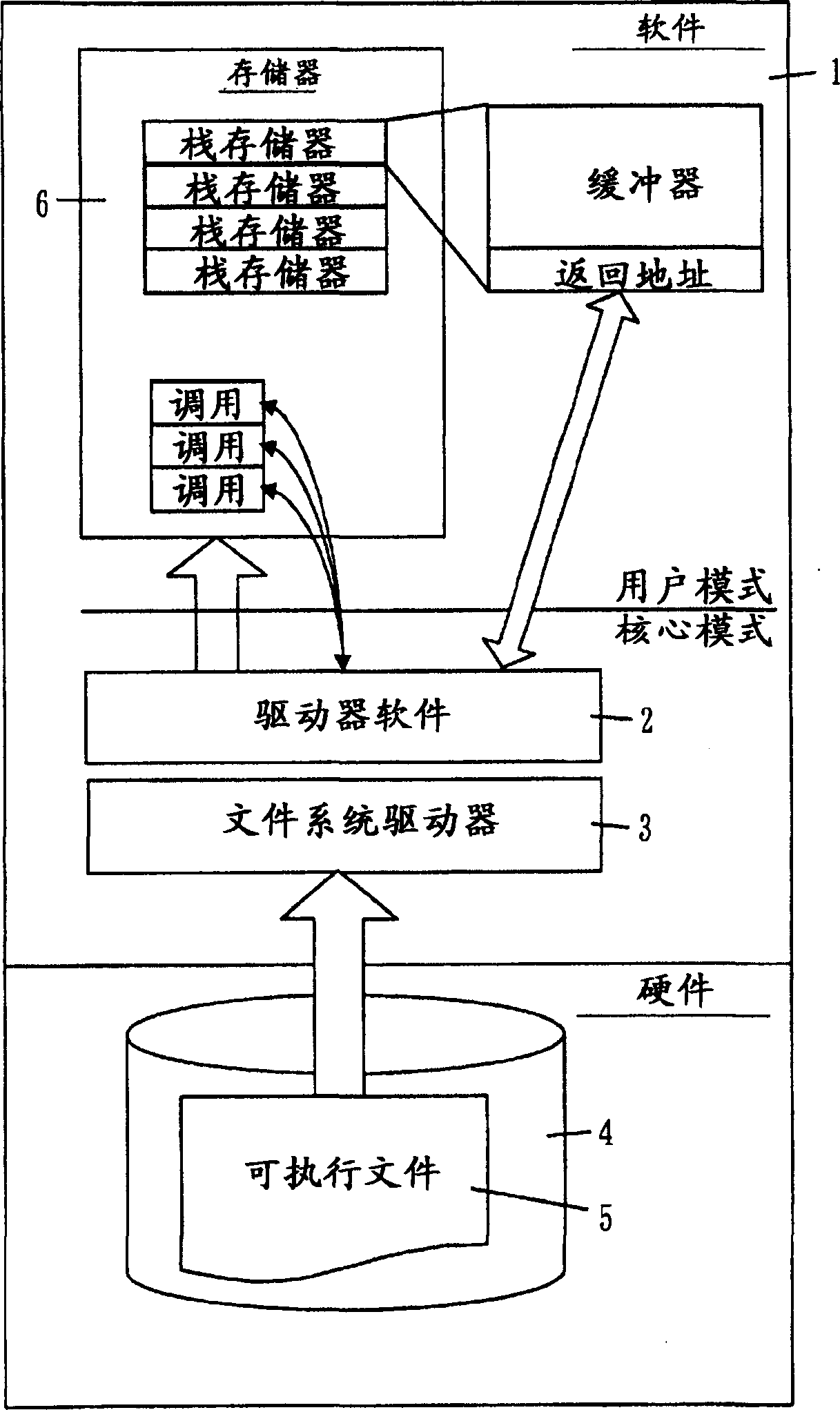
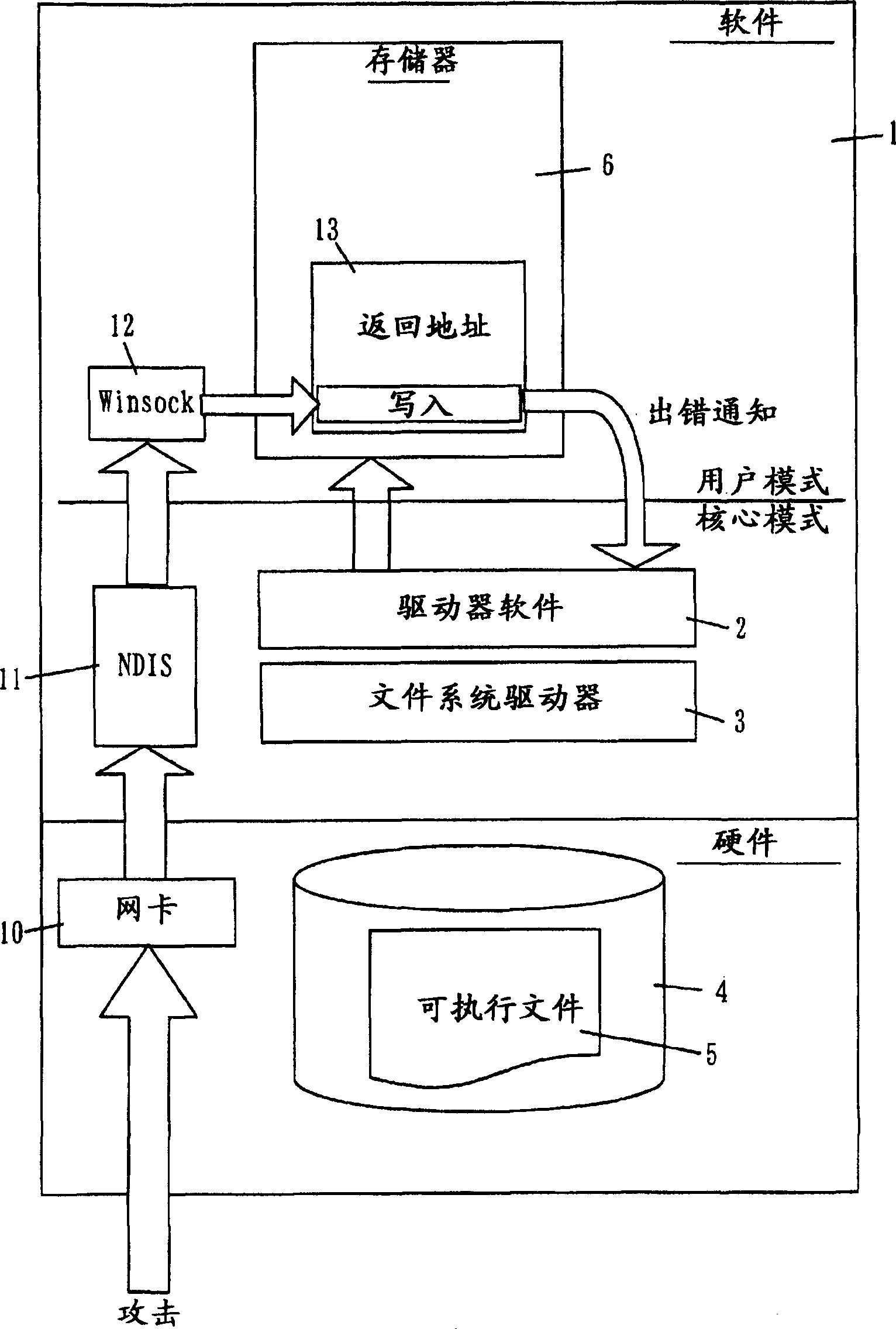
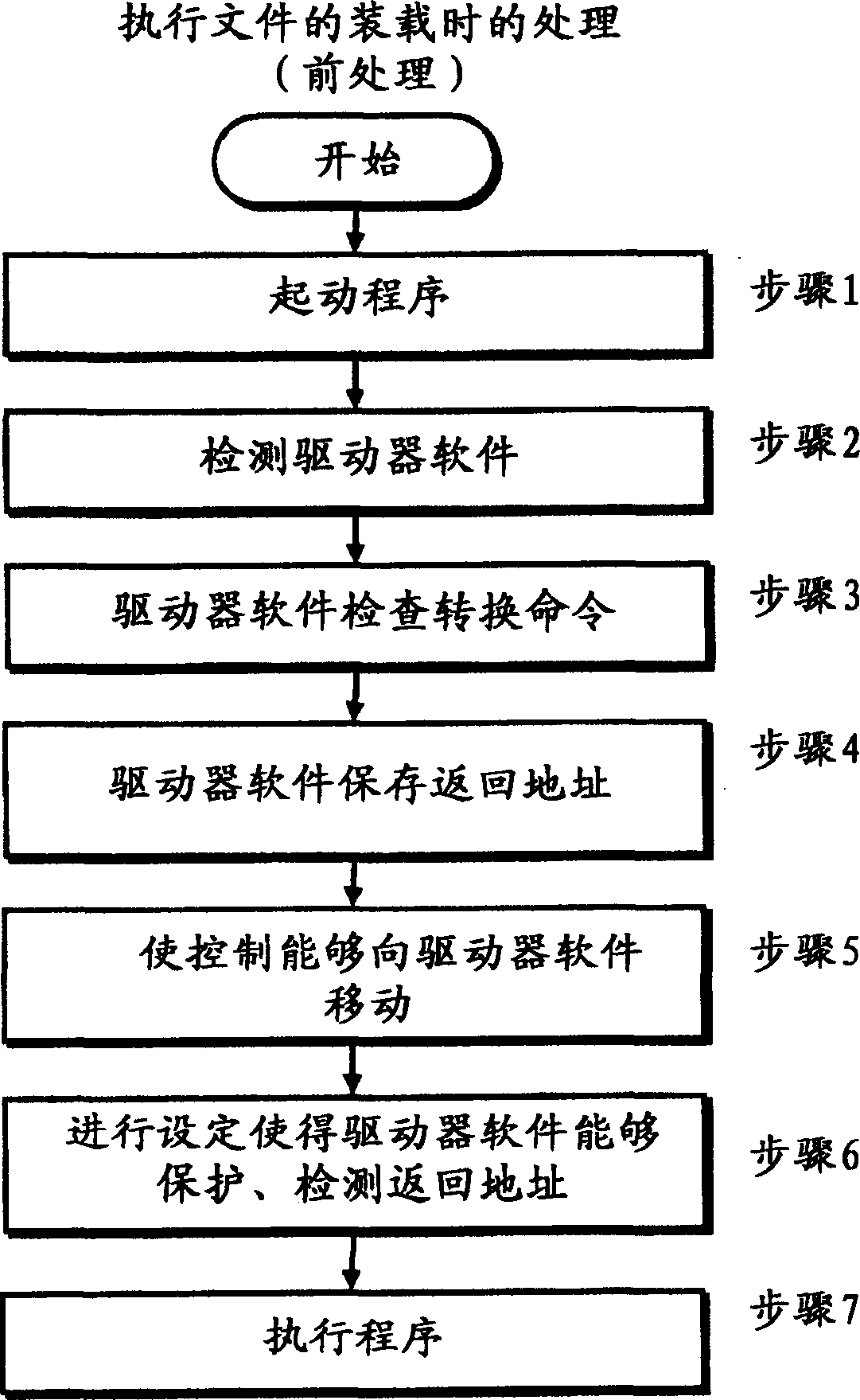
A method for preventing a return address from being falsified due to a buffer overflow during the program execution, and for detecting the buffer-overflow beforehand. When the return address is re-written during program execution, the debug function of the central processing unit is used to output an error. The falsification of the return address is detected through the error output. Then the falsified return address is re-written to a value stored in advance to enable the program to return to normal operation. When the falsification of the return address is detected, the executing program is terminated.
Owner:SCI PARK CORP
Computing device configured for operating with instructions in unique code
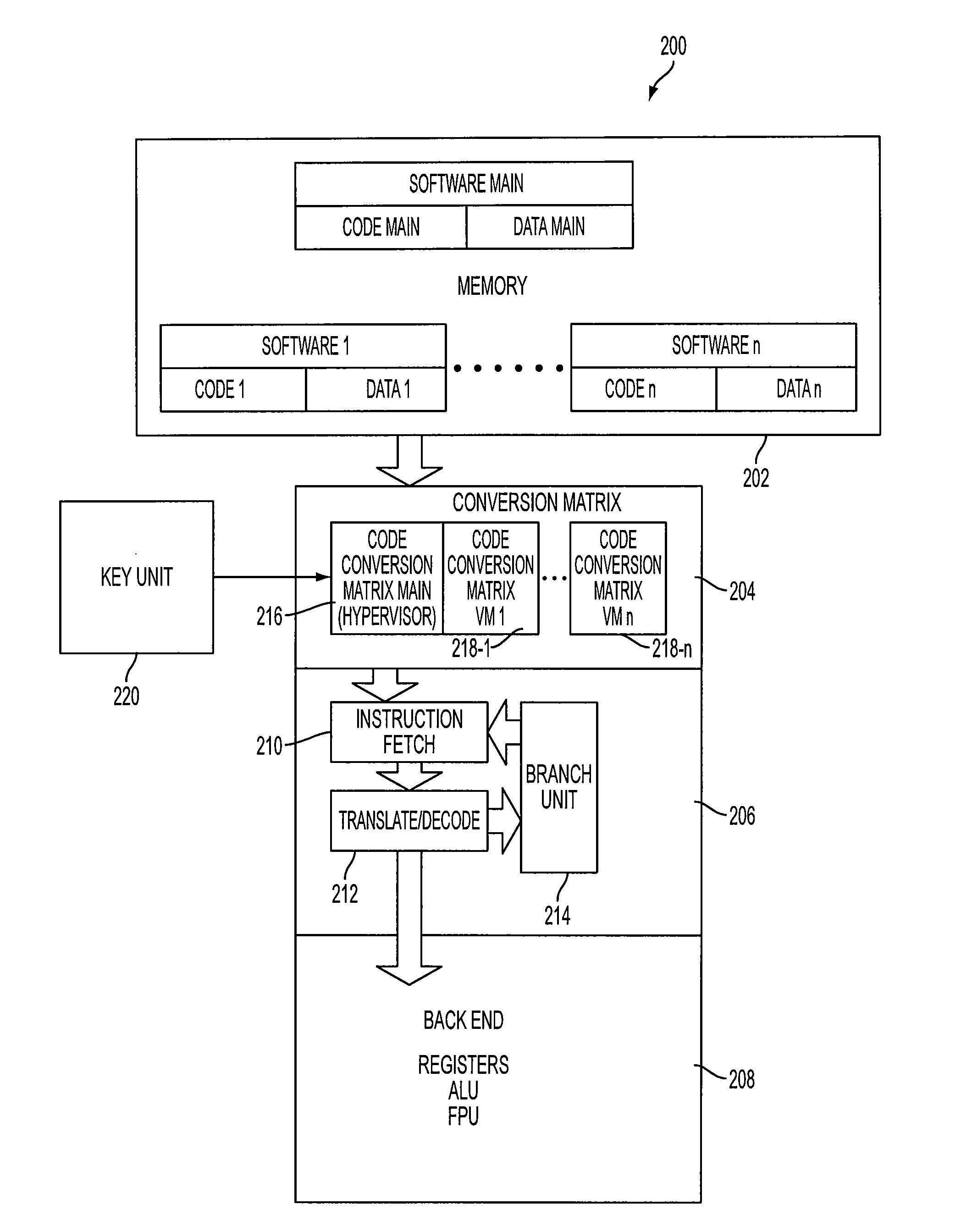
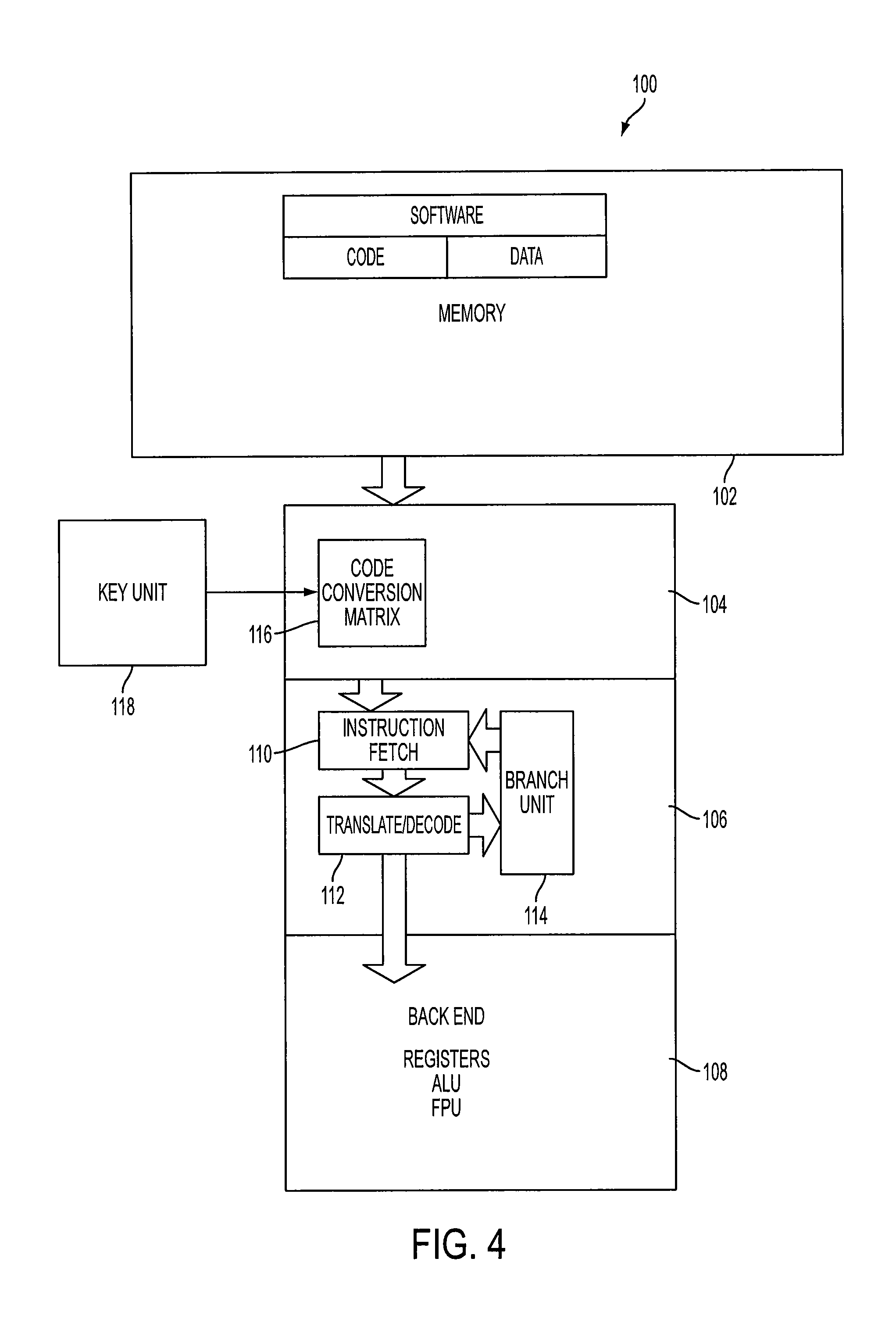
InactiveUS20110314303A1Prevent executionDigital computer detailsUnauthorized memory use protectionSoftwareCode conversion
A computing device having a memory for holding software instructions produced in a code, which is unique for a particular computing device. A code conversion unit converts the unique code into a generic code representing the instructions. The generic code different from the unique code is common for computing devices having a processor of a similar type. A processing circuit of the computing device is linked to the output of the code conversion unit for processing instructions in the generic code.
Owner:GBS LAB
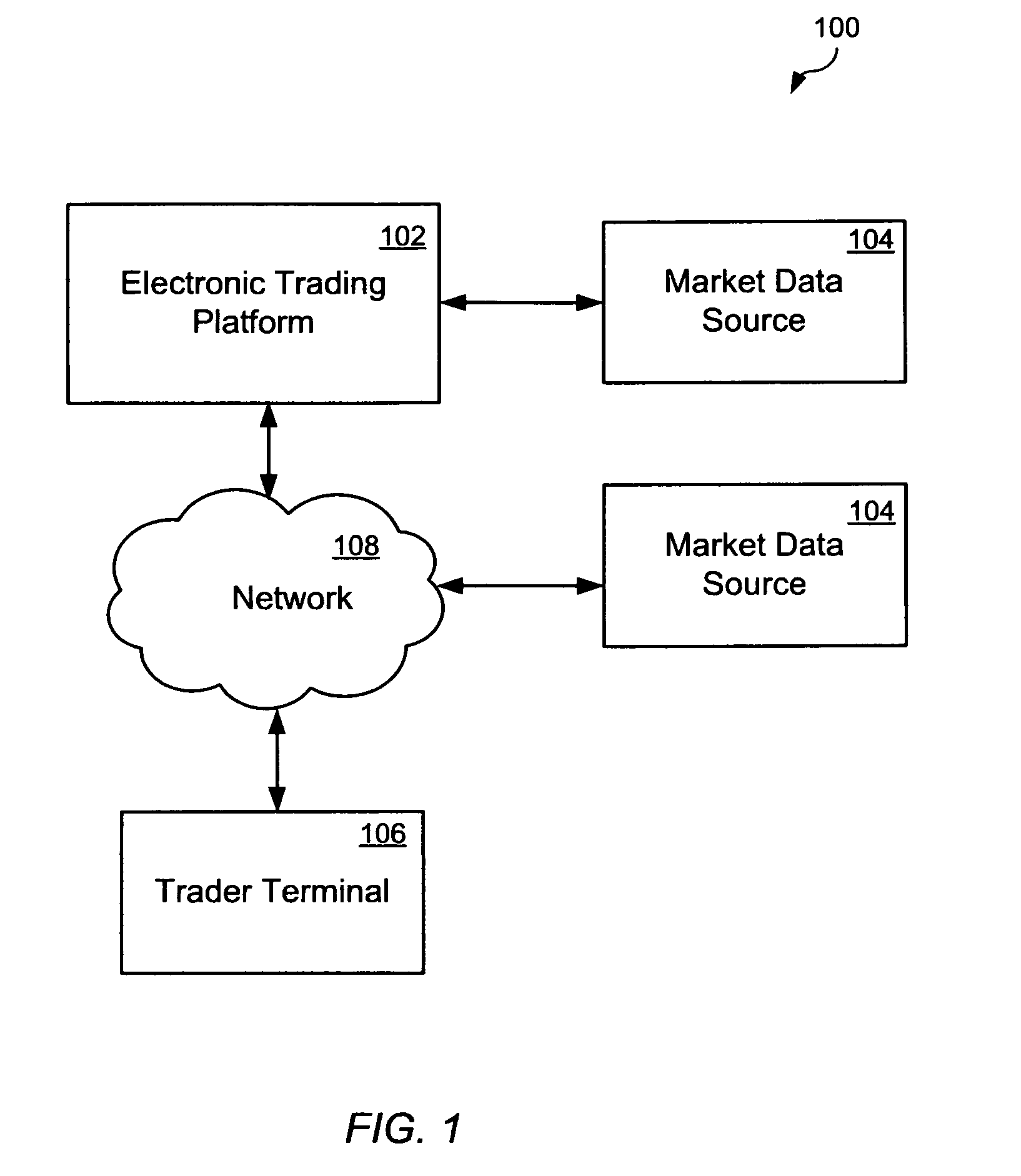
Intelligent execution for brokerage trade orders
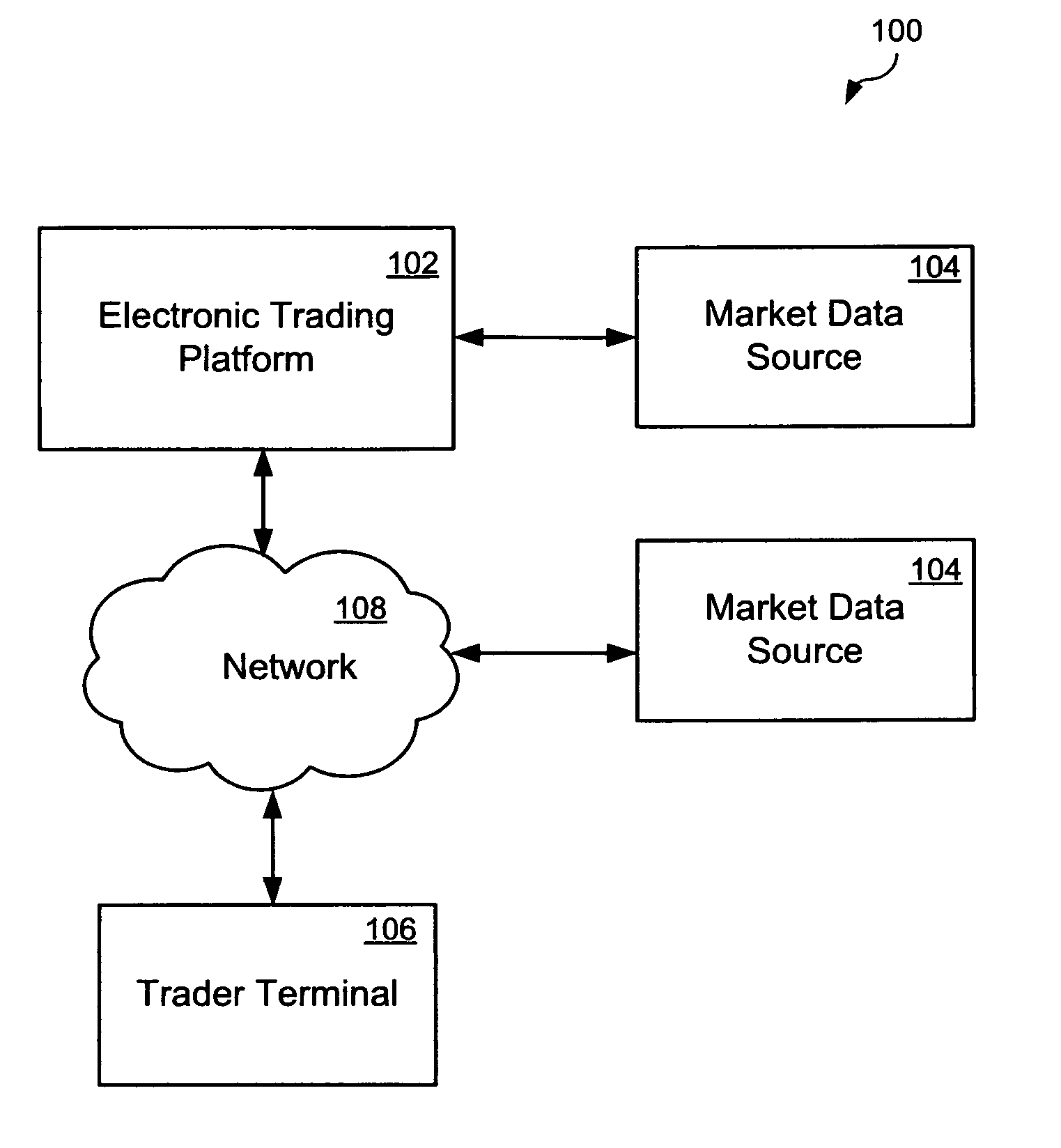
A method and apparatus for driving a trade via an electronic trading platform are provided. Traders may define trade order parameters including at least one monitored parameter and at least one rule for assigned thereto. The trade orders will only be executed when current market data satisfies the at least one monitored parameter and at least one rule. Said monitored parameters are selected from a current market price, a current bid and / or ask value, volume, a Volume Weighted Average Price (VWAP), or a combination thereof. The rules are based on a number and / or volume of executed market orders, placed by other traders, during a certain time period, a time period passed since it was determined that the at least one monitored parameter satisfies the market data, or a combination thereof.
Owner:NEXTROPIA
Automated code lockdown to reduce attack surface for software
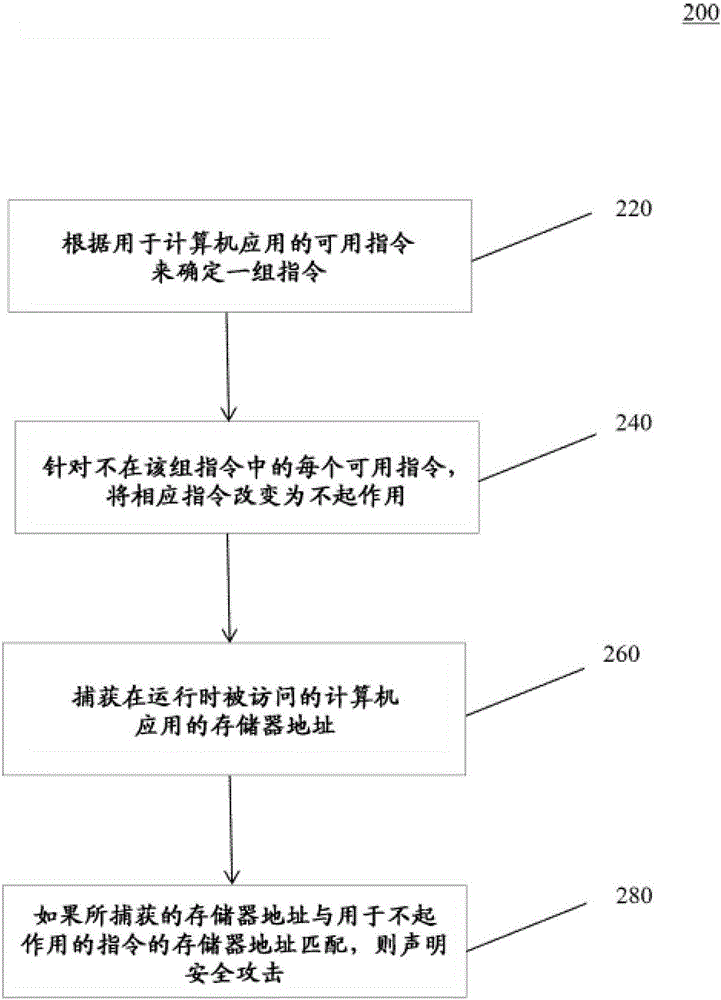
ActiveCN106687971ADoes not affect experienceReduce attack surfacePlatform integrity maintainanceMemory addressFunctional testing
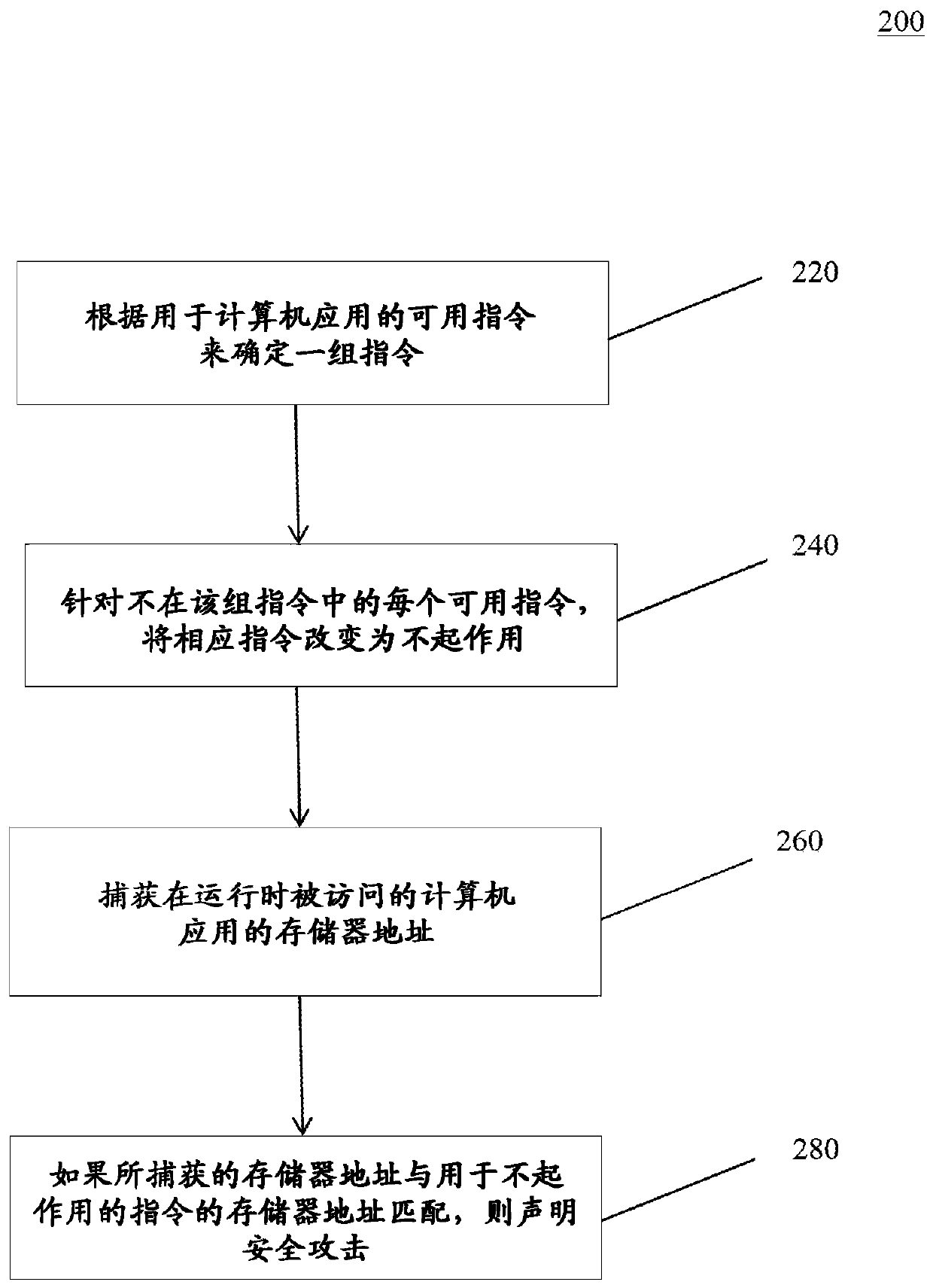
In an example embodiment, a system determines a set of instructions from the available instructions for a computer application. The determined set of instructions provides specific functionality of the computer application. The system may determine the set of instructions by performing functional testing and negative testing on the specific functionality. The system may reorganize and randomize the set of instructions in memory and write the reorganized set of instructions to a smaller memory space. For each available instruction not in the set of instructions, the system changes the respective instruction to inoperative to prevent execution of the respective instruction. The system may change the respective instruction to inoperative by overwriting the instruction with a NOP instruction. The system then captures a memory address of the computer application being accessed at runtime. The system may declare a security attack if the captured memory address matches a memory address for an inoperative instruction.
Owner:VIRSEC SYST
Data processing apparatus
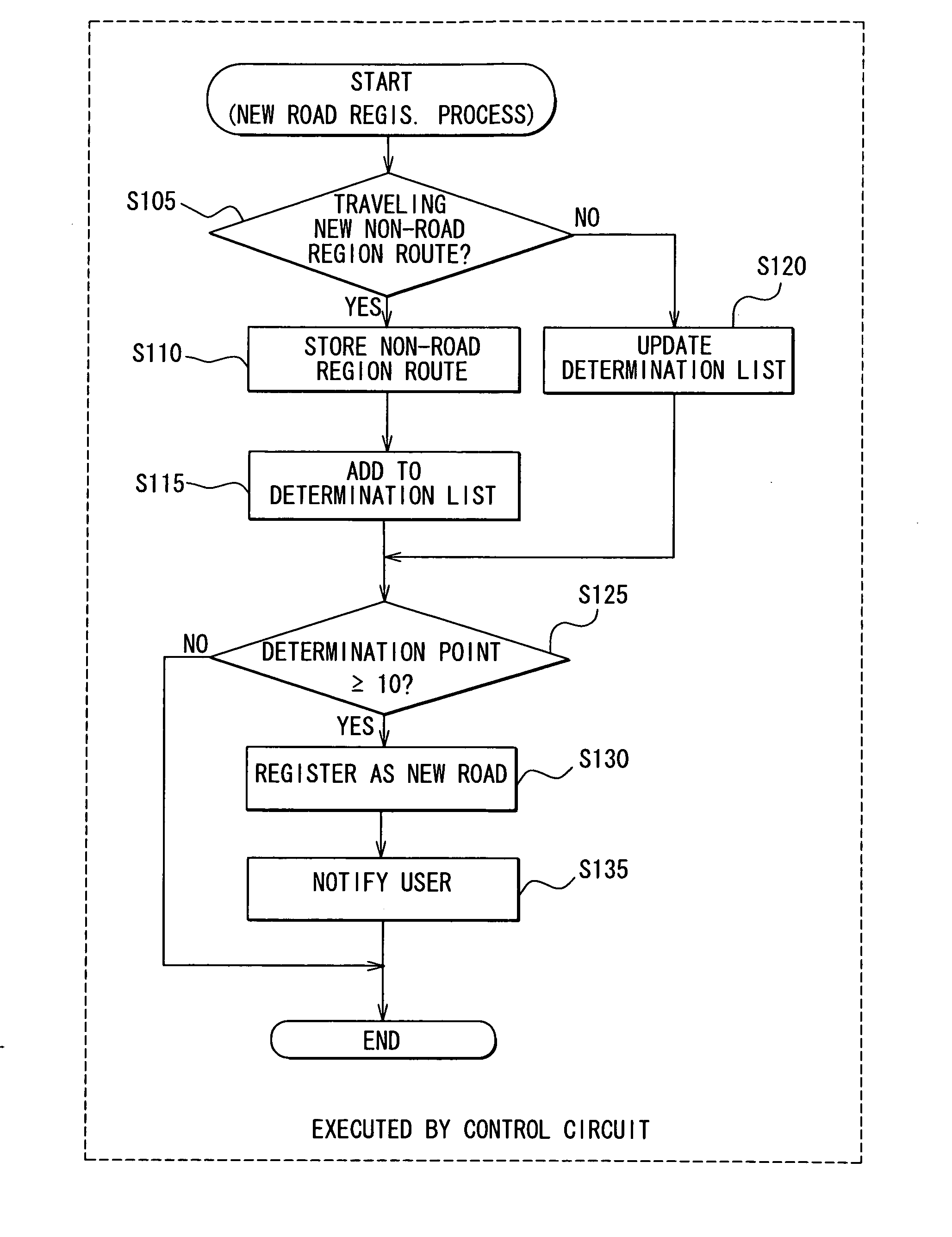
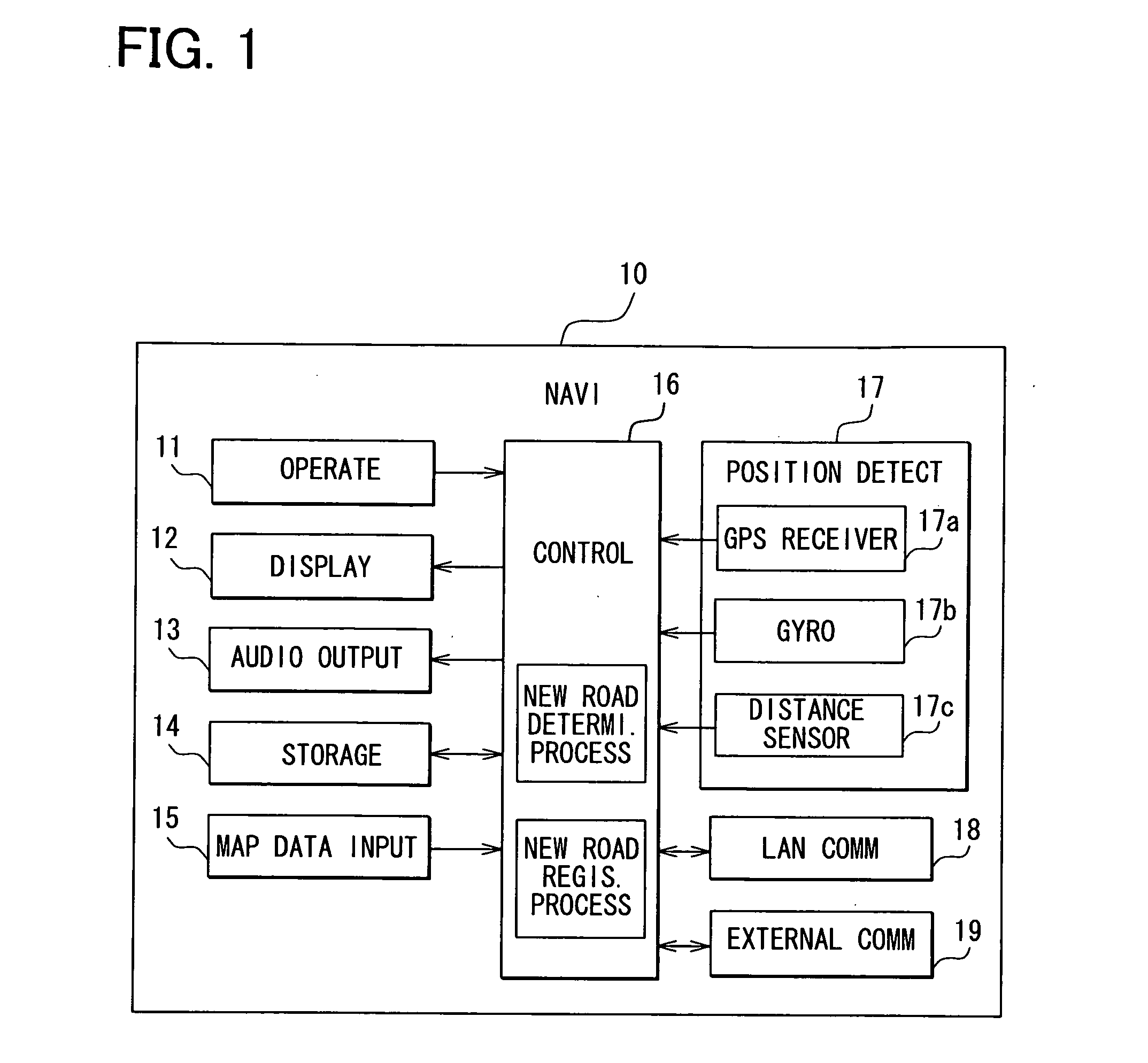
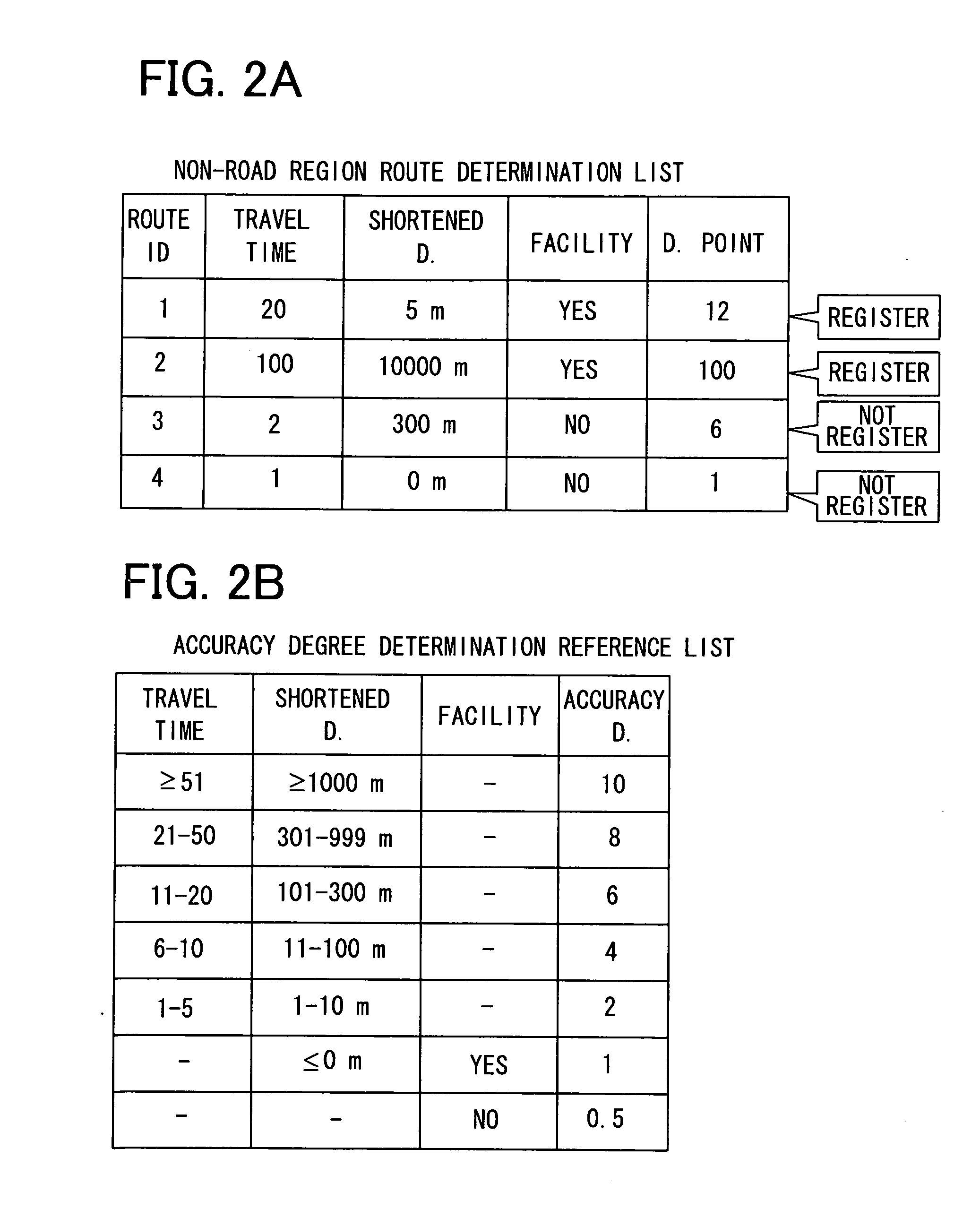
ActiveUS20100106412A1Prevent executionPreventing executionInstruments for road network navigationRoad vehicles traffic controlData processingMarine navigation
With respect to a non-road region route, which is in a region other than roads registered in map data, a navigation apparatus in a vehicle specifies three check items: travel times the vehicle traveled; a shortened distance reduced by traveling the non-road region route compared with a route registered in the map data; and presence or absence of a predetermined facility in the vicinity of the non-road region route. The navigation apparatus determines an accuracy degree as to whether the non-road region route is existent based on the specified check items, thereby determining whether the non-road region route is existent. A route guidance process is executed based on the non-road region route, which is determined to be existent.
Owner:DENSO CORP
Vehicle voice input control method for intelligent traveling
InactiveCN108099816AEnsure time-to-time accuracyAlert and prevent drivingSpeech recognitionElectric/fluid circuitIn vehicleControl system
The invention provides a vehicle voice input control system for intelligent traveling. The vehicle voice input control system comprises a main voice system and an auxiliary voice identification systemand is characterized in that the signal transmission of the auxiliary voice identification system and the signal transmission of the main voice system are synchronous, the auxiliary voice identification system and the main voice system are connected with a central control module, and the auxiliary voice identification system and the main voice system perform cross verification and identification;the auxiliary voice identification system comprises a fatigue driving identification control system built in the auxiliary voice identification system. The vehicle voice input control system has theadvantages that mutual verification and correction can be achieved by the cross verification and identification of the auxiliary voice identification system and the main voice system, false instruction implementation can be prevented effectively, fatigue driving can be prevented, the accuracy of intelligent voice input is increased greatly, and a foundation is laid for the accurate instruction receiving of the communication between other vehicular accessories in vehicles and the Internet of Vehicles, between the vehicles and homes, and the like.
Owner:WUHU WANJIANG INTPROP OPERATION CENT CO LTD
Method and system for preventing unauthorized computer processing
ActiveUS20180181731A1Prevent executionPublic key for secure communicationDigital data authenticationComputer hardwareComputer science
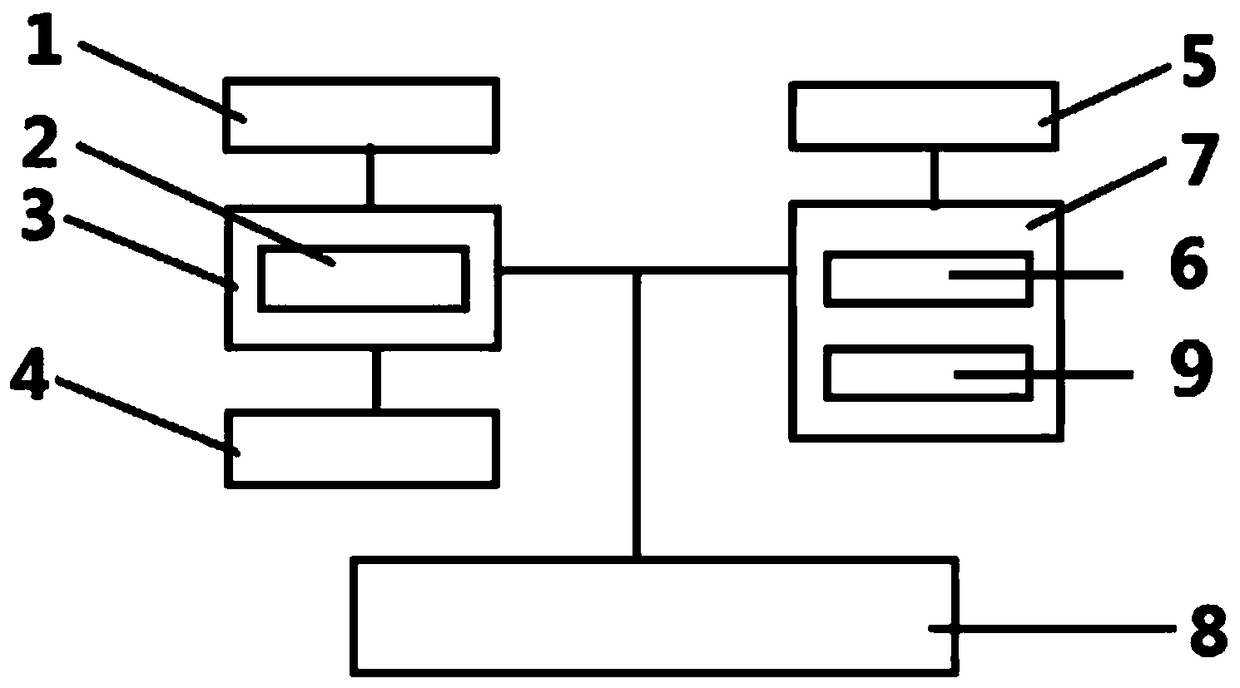
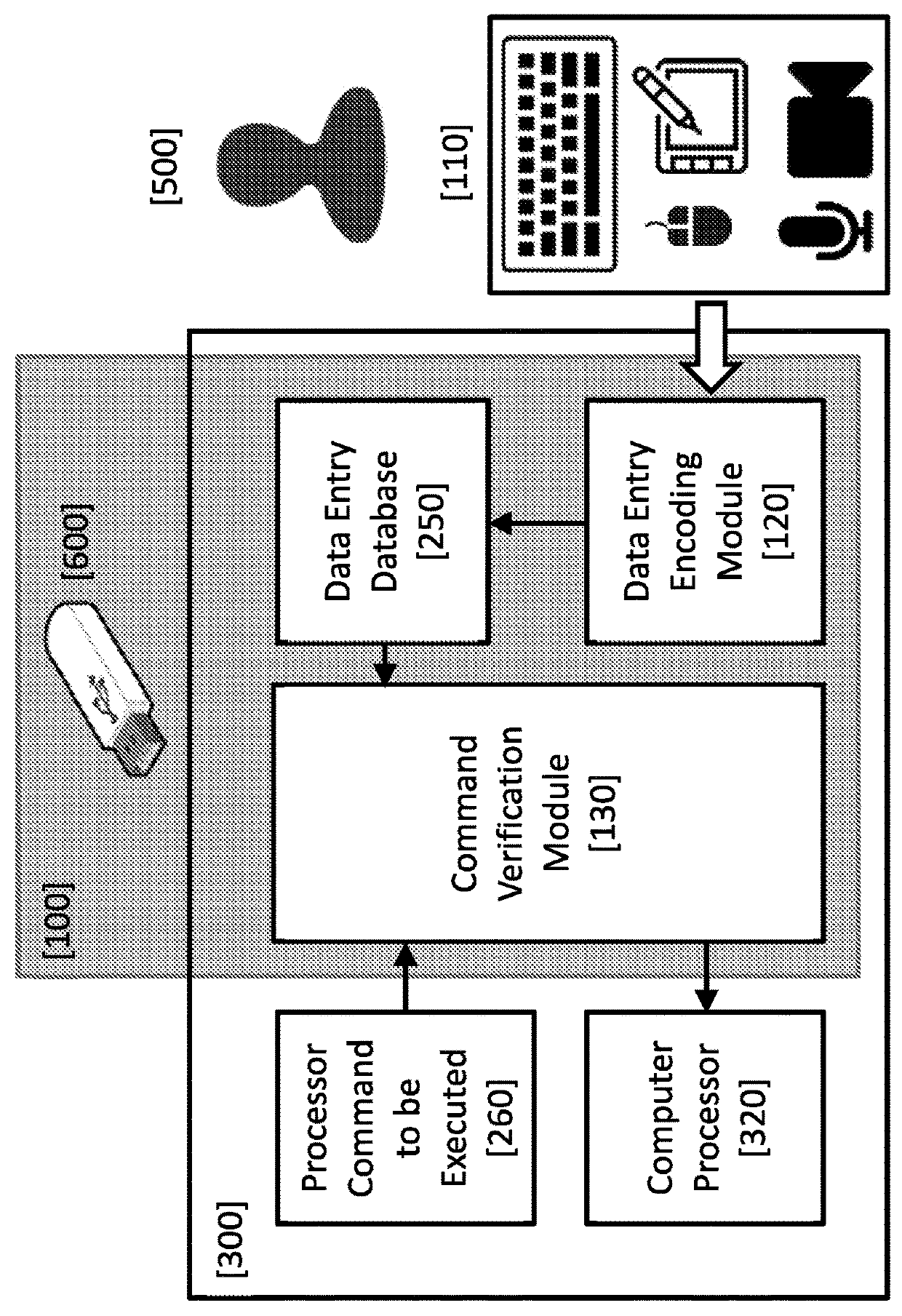
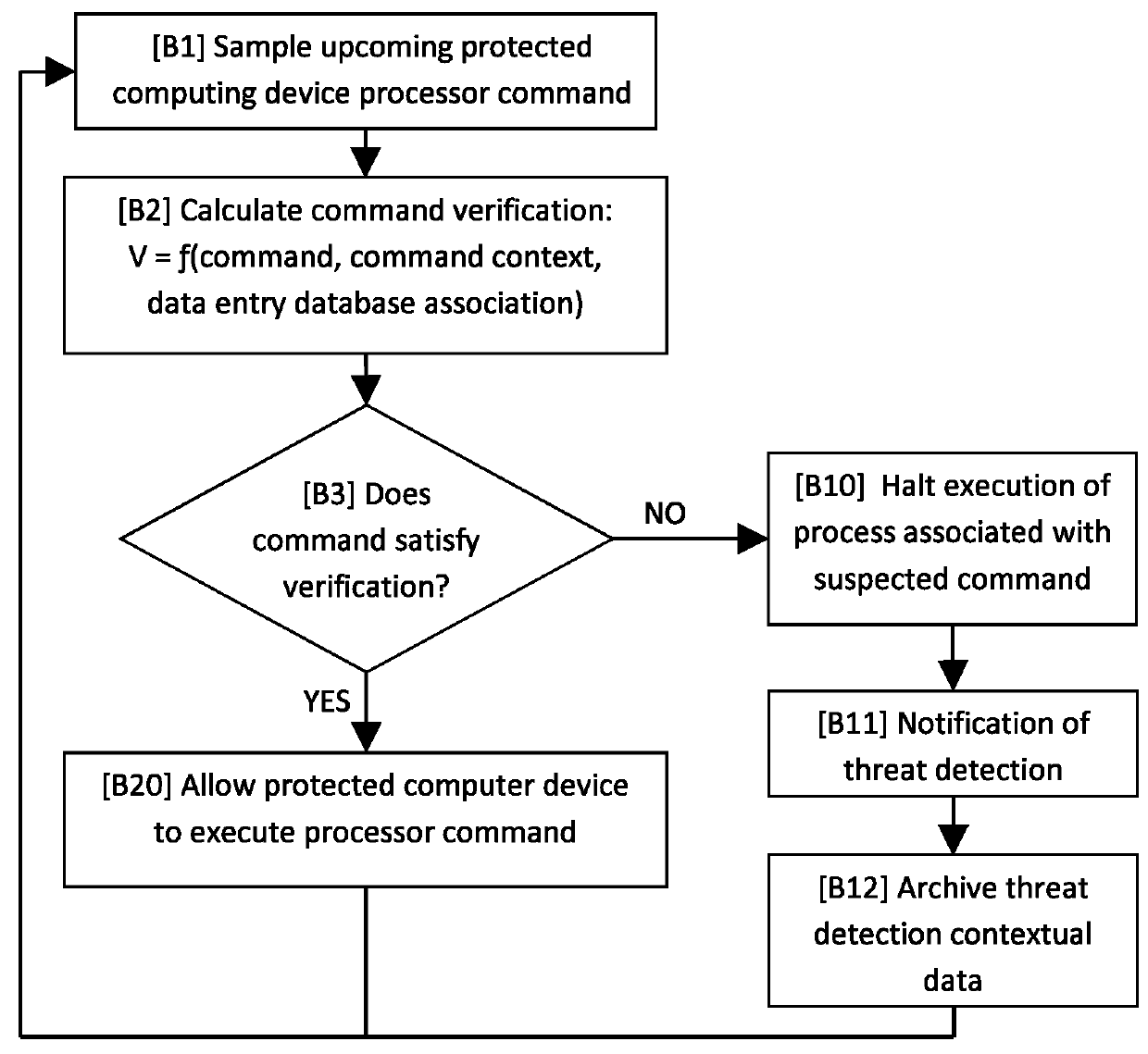
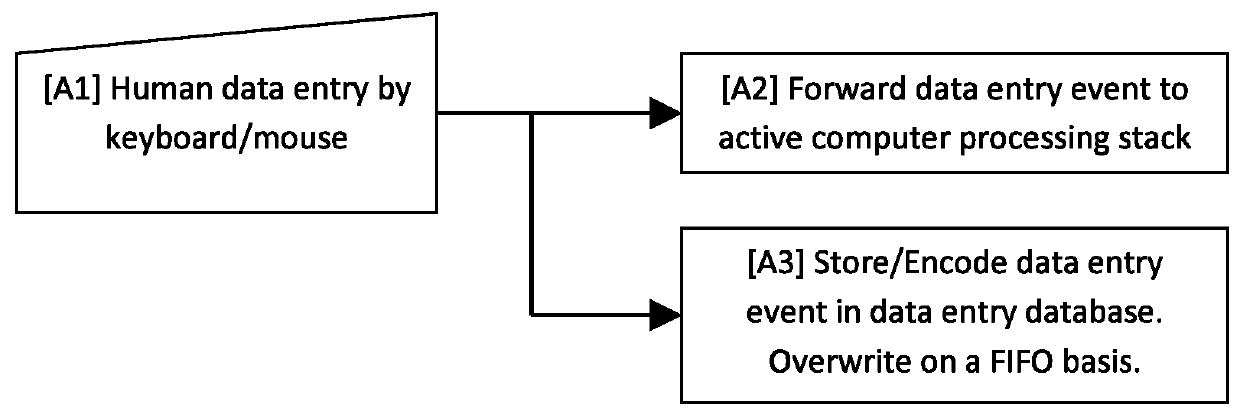
The invention relates to a system and method for preventing a protected computing device from executing unauthorized processor commands. A data entry database of the system stores encoded data entered by a human user as data entry events. A command verification module of the system implements an authentication algorithm for determining whether a processor command to be executed by the computing device originates from a trusted source. The command verification module determines the trustworthiness of a processor command as a function of parameters of the processor command, which include an association of the command with one or more of the data entry events. Determination can also be made based on other processor command parameters, such as the type of processor command and / or contextual parameters of the processor command. Upon making the determination, the command verification module allows authenticated processor commands to be executed and prevents non-authenticated processor commands from being executed by the computing device.
Owner:RAM DAN
Method and apparatus for controlling a translation lookaside buffer
ActiveUS20120124325A1Prevent executionMemory adressing/allocation/relocationMultiprogramming arrangementsData bufferLoad instruction
A method and apparatus are provided for controlling a translation lookaside buffer in connection with the execution of an atomic instruction. The method comprises identifying load instructions within a plurality of instructions to be executed, and placing the identified load instructions in a queue prior to execution. An atomic instruction identified in the queue is prevented from executing until the atomic instruction is the oldest instruction in the queue. The apparatus comprises a queue and a translation lookaside buffer. The queue is adapted to: identify an atomic instruction within a plurality of instructions to be executed; prevent execution of the atomic instruction until it is the oldest instruction in the queue; and send a virtual address corresponding to the atomic instruction and an atomic load signal in response to determining that the atomic instruction is the oldest instruction in the queue. The translation lookaside buffer is adapted for maintaining at least one virtual to physical address translation, and is adapted to force a miss in the translation lookaside buffer in response to receiving the atomic load signal.
Owner:ADVANCED MICRO DEVICES INC
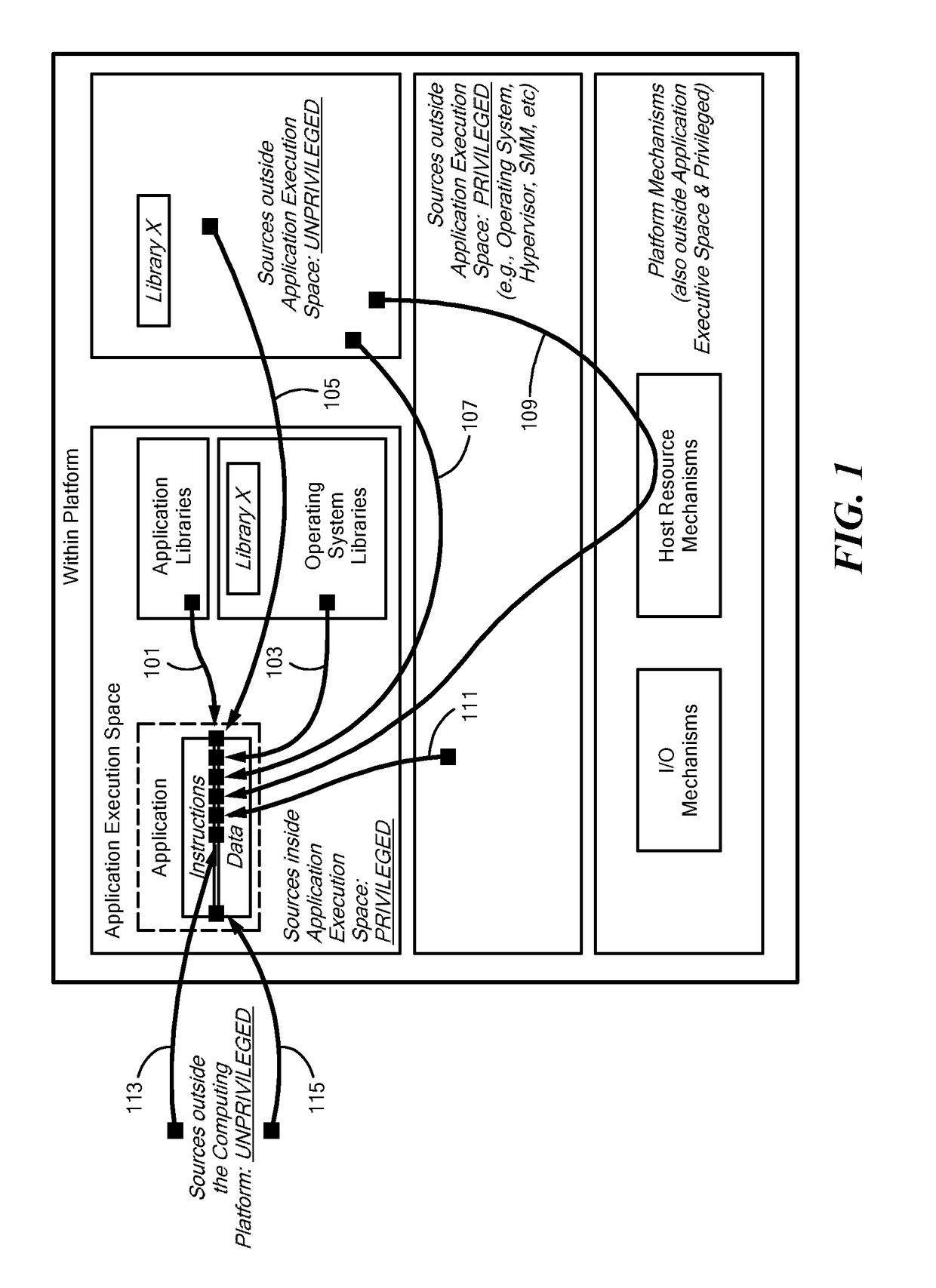
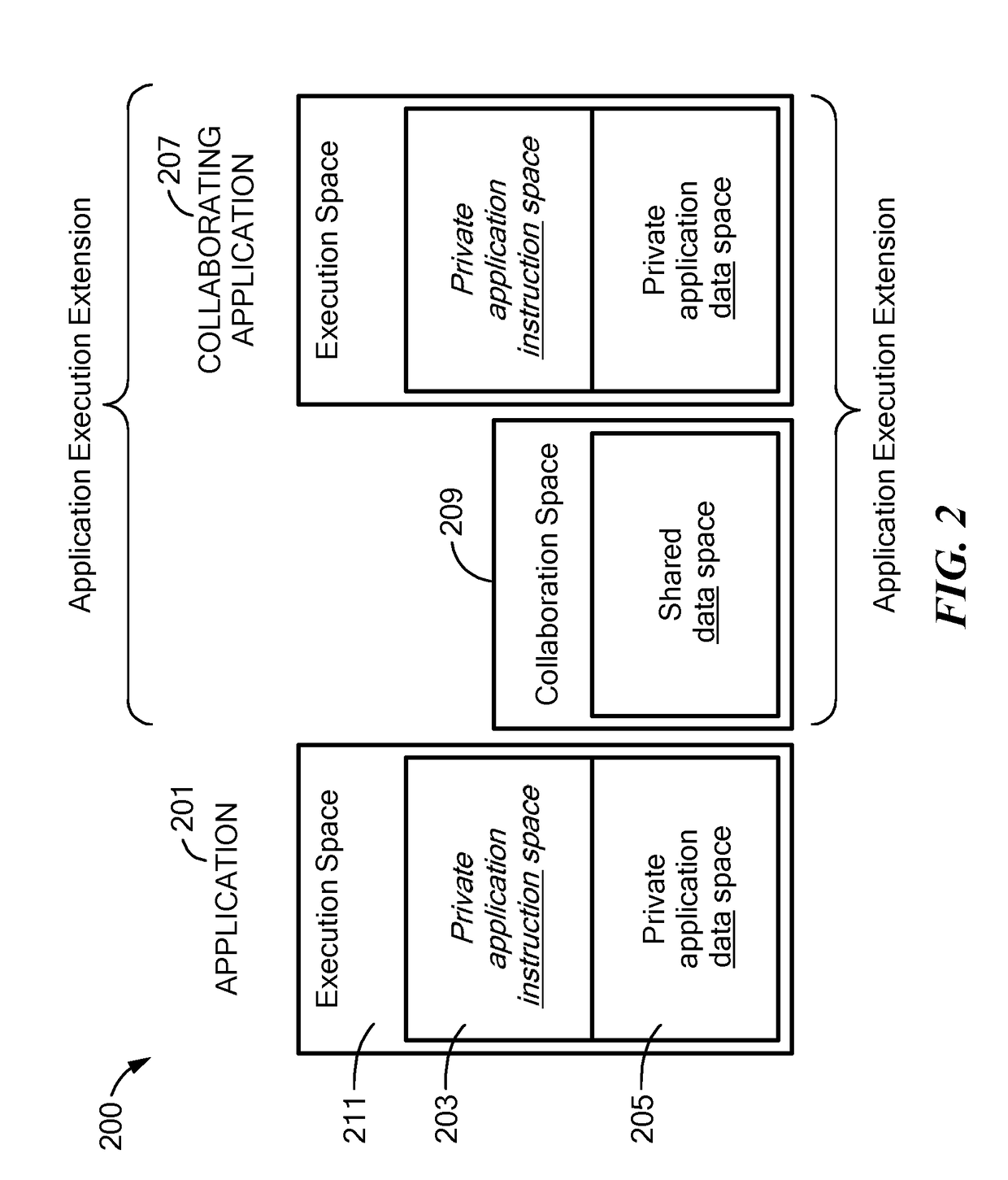
Method and Apparatus for Trusted Execution of Applications
ActiveUS20180330092A1Prevent executionDigital data protectionPlatform integrity maintainancePattern spaceTrusted application
A system and methodology for providing trusted execution of applications is provided. The computing system includes system hardware including memory. A Trusted Application Execution Provisioning (TAEP) operating on said computing system enforces a Trusted Application Pattern Space (TAPS) within the memory throughout the execution lifecycle of each application hosted on the computing system. The Trusted Application Execution Provisioning (TAEP) assigns each application a private application instruction space and a private application data in accordance with specifications governing the Trusted Application Pattern Space (TAPS), such that the Trusted Application Execution Provisioning (TAEP) prevents the private application instruction space of each application from being read, inferred, and / or modified by any application, and prevents the private application data space of each application from being read, inferred, and / or modified by other than its assigned application. Upon an extension request by a first application to extend with one or more collaborating applications, the Trusted Application Execution Provisioning (TAEP) assigns an application collaboration data space within the memory in accordance with the specifications governing the Trusted Application Pattern Space (TAPS), such that both the first application and the one or more collaborating applications have access to the application collaboration data space. The Trusted Application Execution Provisioning (TAEP) prevents the application collaboration space from being read, inferred, and / or modified by other than the first application and the one or more collaborating applications.
Owner:CHARLES STARK DRAPER LABORATORY
Semiconductor designing apparatus
InactiveCN1828618APrevent executionCAD circuit designSpecial data processing applicationsComputer architectureRecords management
Owner:PANASONIC CORP
Method of controlling display device, and display device
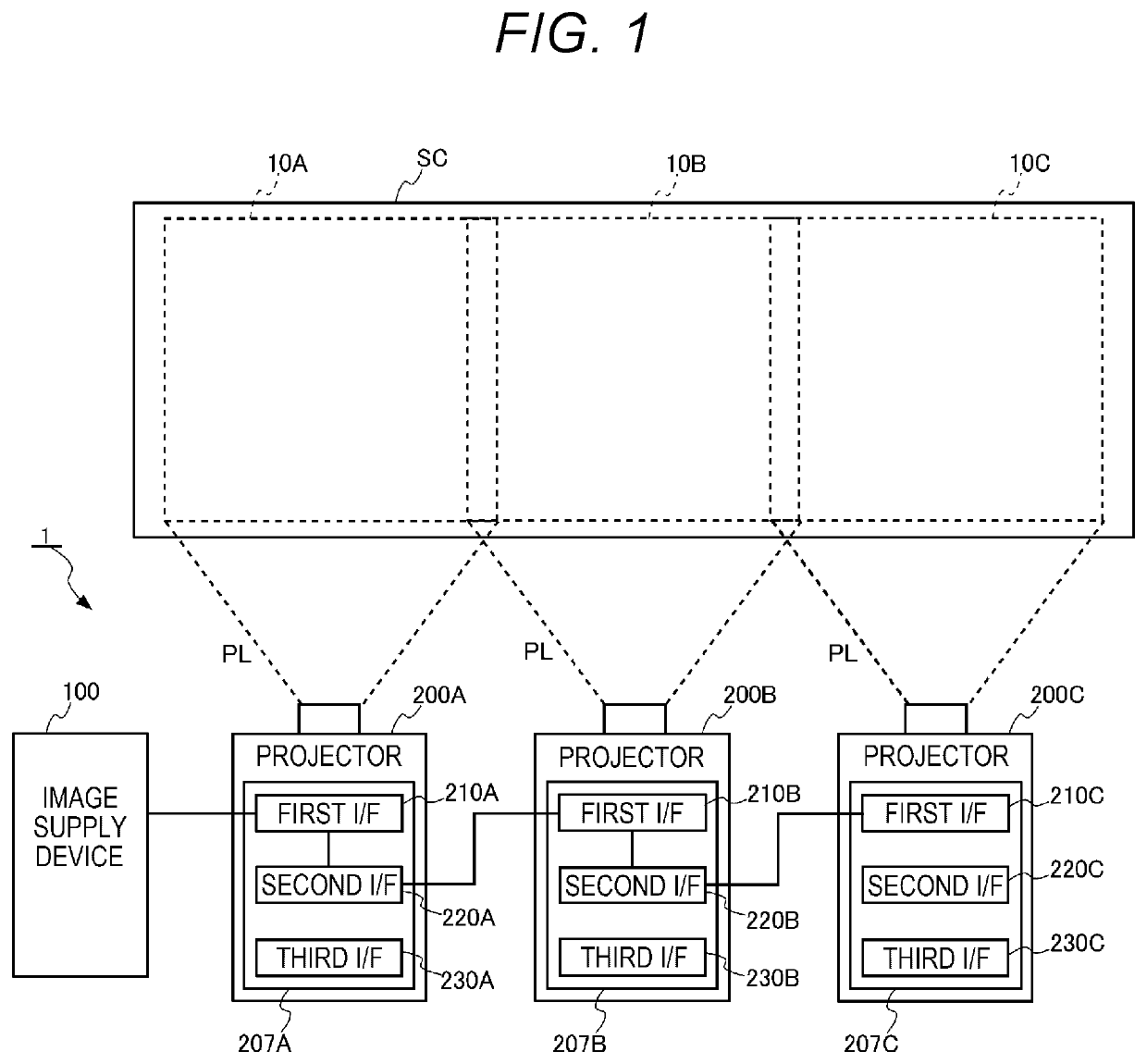
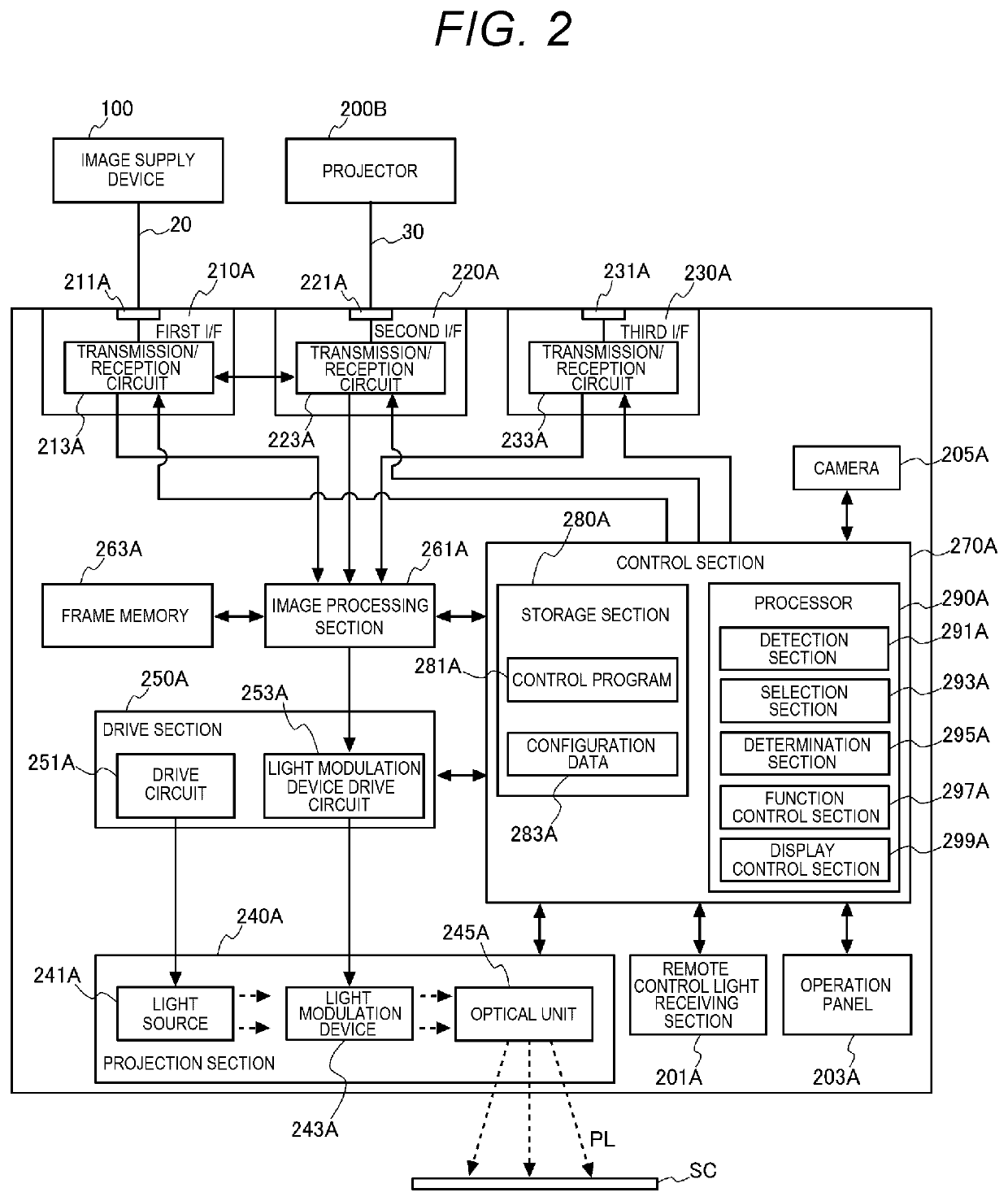
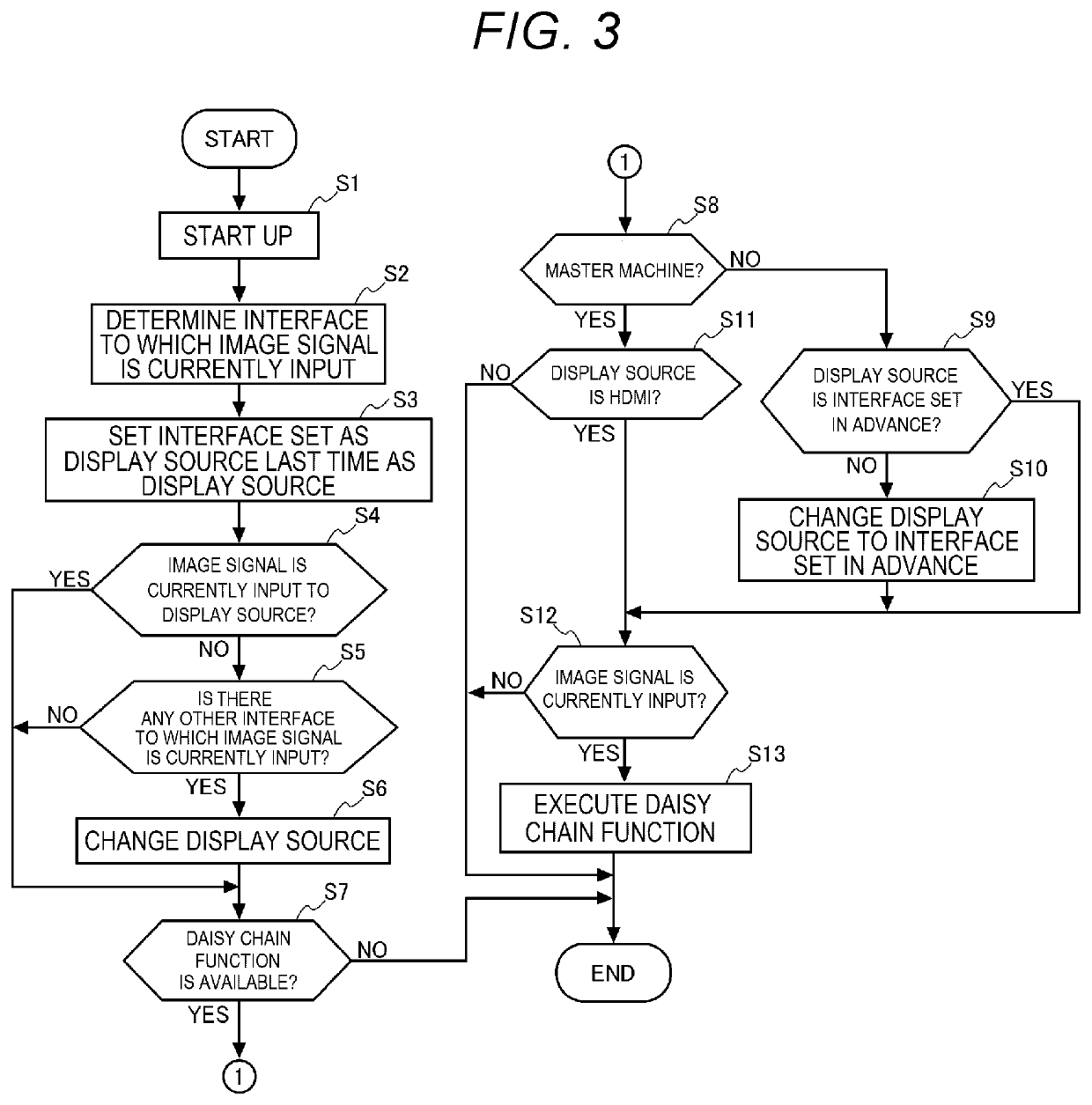
ActiveUS20200389630A1Prevent executionPicture reproducers using projection devicesCathode-ray tube indicatorsEmbedded systemDaisy chain
A projector includes a selection section configured to select an interface to which an image signal to be displayed by the projector out of the plurality of interfaces is input, a determination section configured to determine whether or not the interface selected is a compliant interface capable of establishing daisy chain connection, and a function control section configured to make the transition of the projector to a state of preventing a daisy chain function from being executed when the interface selected is not the compliant interface, and when the daisy chain function which can be executed in a state in which the projector is coupled to another projector with the daisy chain connection is set available.
Owner:SEIKO EPSON CORP
Method of interacting commands of transformer substation based on third-party verification
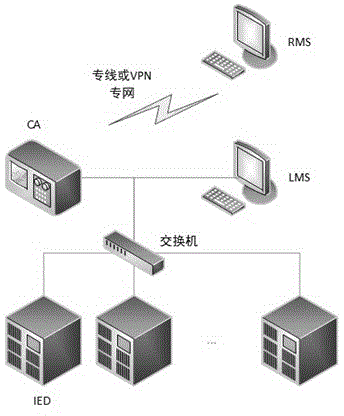
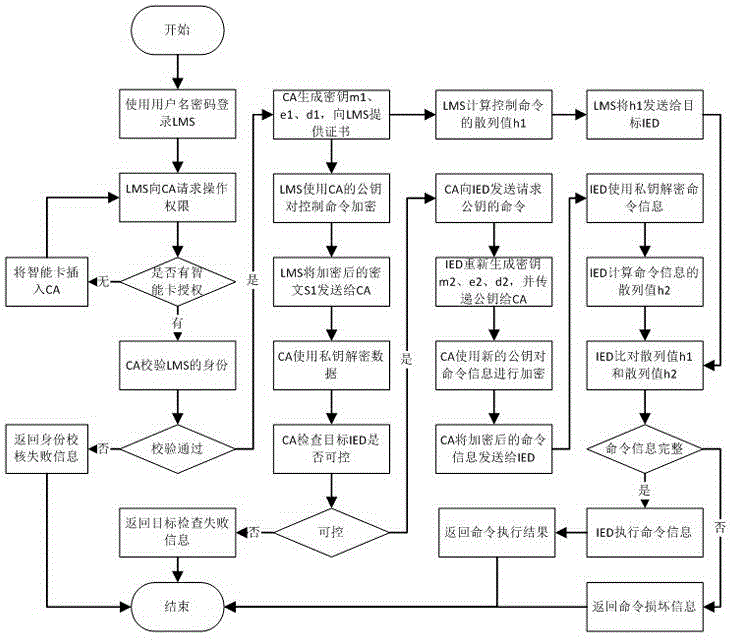
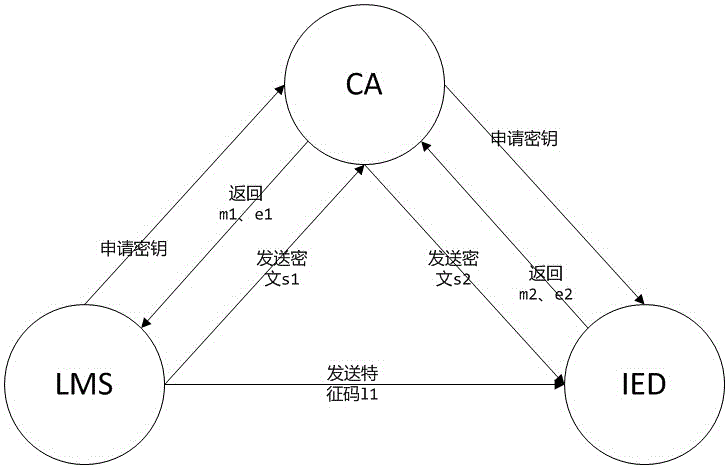
The invention discloses a method of interacting commands of a transformer substation based on third-party verification. A third-party certification device CA (Certificate Authority) is introduced to verify permission and identity of both parties of the commands, the CA is utilized as a trusted source, and credibility of the CA is guaranteed by adopting an intelligent card or a digital certificate technology, so that control permission and range of a target IED (Intelligent Electronic Device) can be effectively controlled to prevent command information from being intercepted and tampered; the third-party certification device CA is utilized to repackage the command information, so that security of transmission information is guaranteed; a hashed value is used for verifying integrity of mutual information, so that wrong data are effectively filtered, execution of the bad command is prevented, and information security of a control process of the transformer substation can be greatly improved. The method has the beneficial effects that: security of transmission of a control signal in the transformer substation is improved, so that the signal is prevented from being intercepted or tampered, security of data is guaranteed, operation crowd is limited, illegal users are isolated, information security is protected, the wrong data are effectively filtered, and execution of the bad command is prevented.
Owner:NARI TECH CO LTD
Method of distributing piracy protected computer software
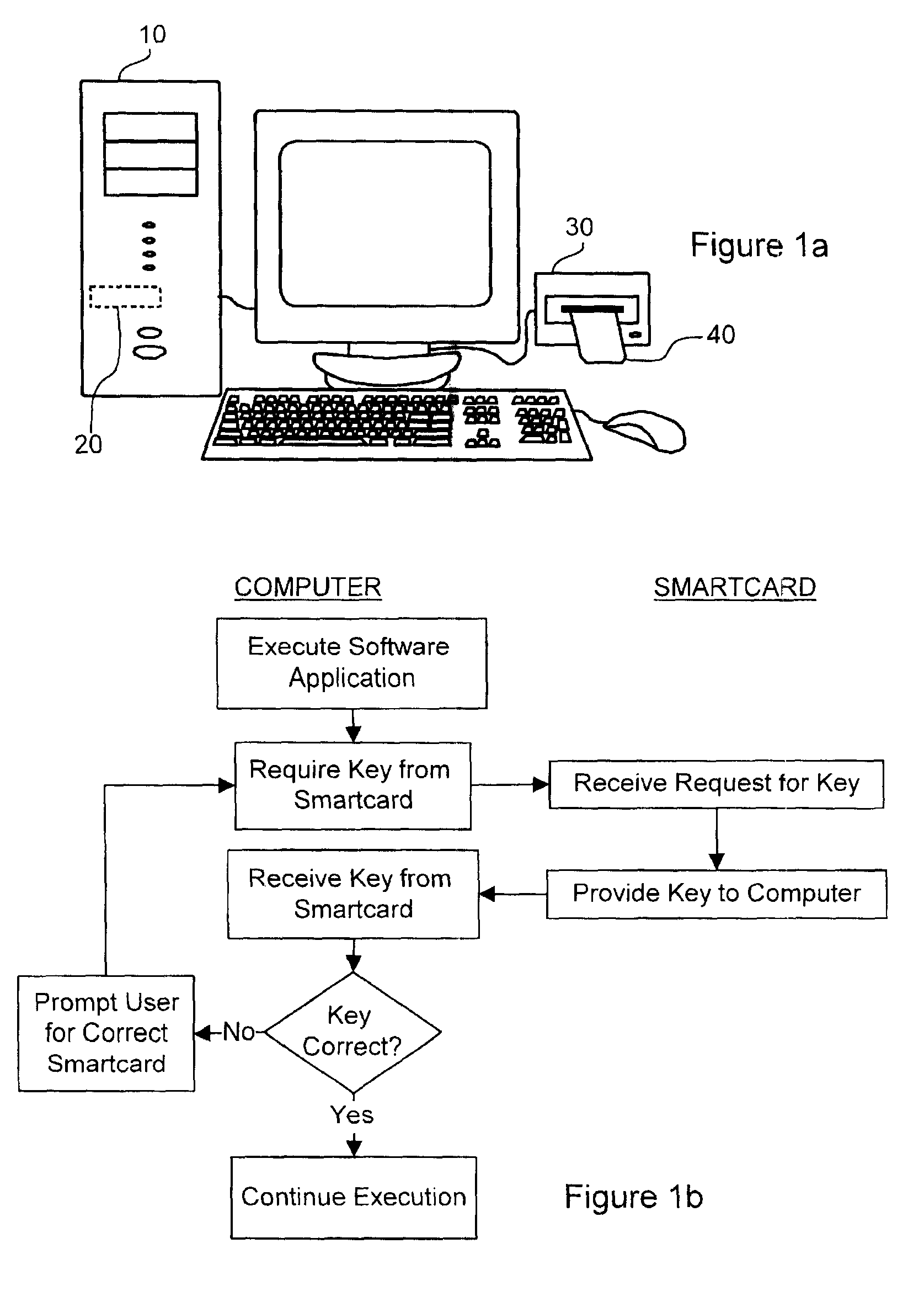
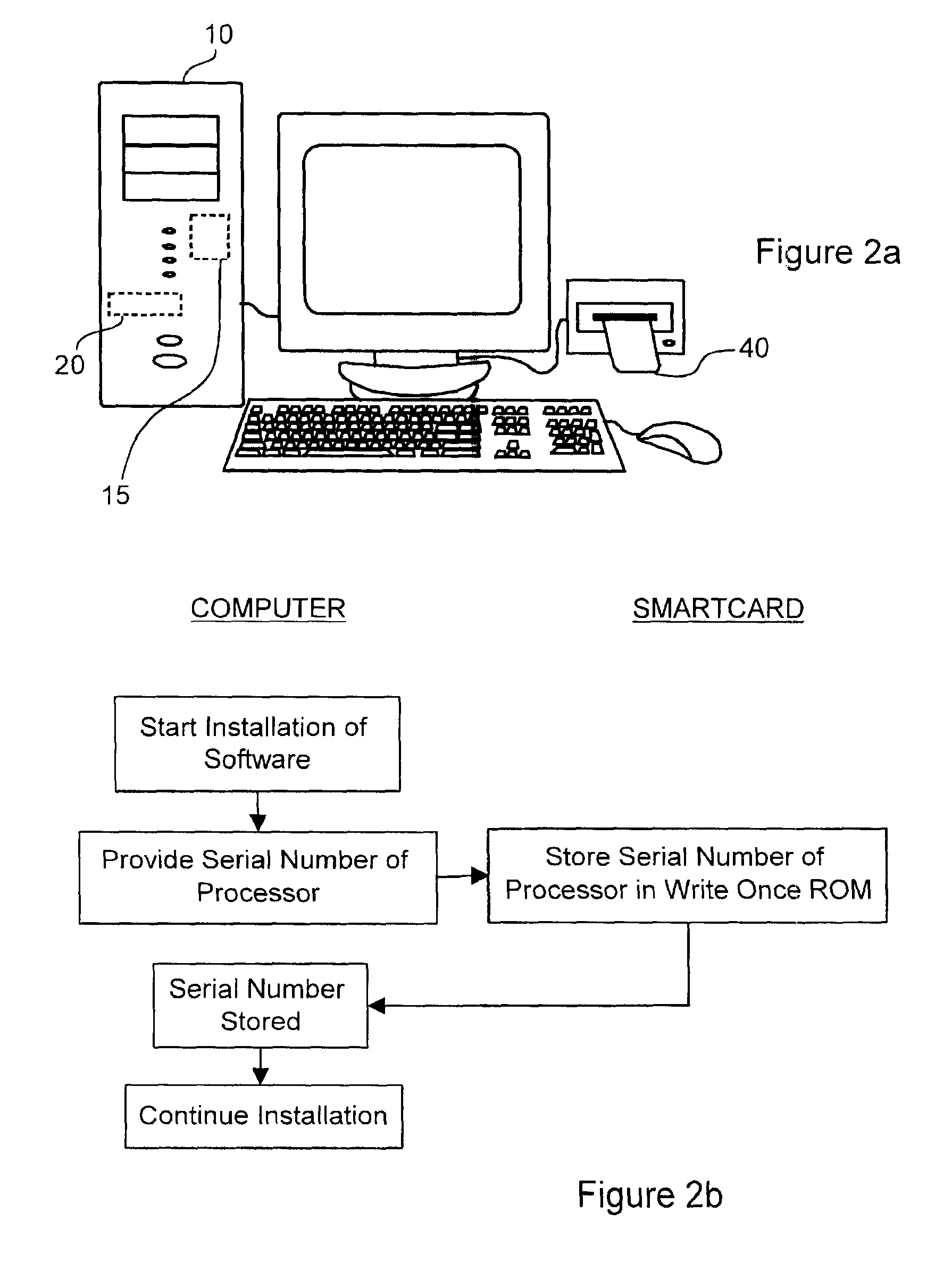
InactiveUSRE42861E1Prevent executionDigital data processing detailsUser identity/authority verificationUser inputSmart card
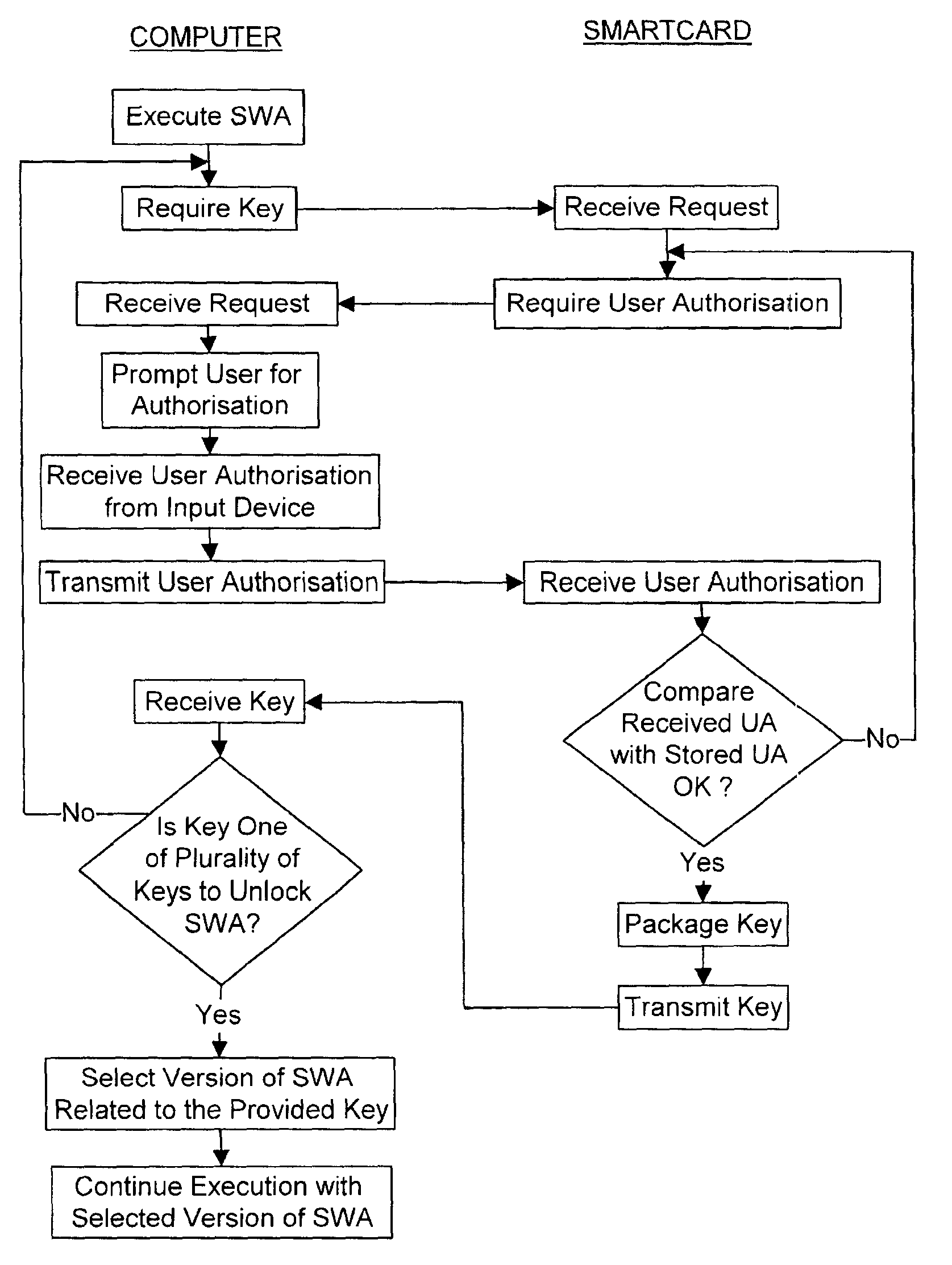
A method and a system for disabling execution of a software application stored within a computer absent data indicative of an authorized use of the software application are disclosed. At start up or during execution of a software application a user is prompted for user authorization information. Using a processor within a smart card the received user authorization information is compared with user authorization information stored in memory of the smart card to produce a comparison result. If the comparison result is indicative of an authorized user of the software application, then data indicative of the authorized use of the software application is provided from the smart card to the computer. Upon receipt of the data indicative of the authorized use of the software application execution of the software application is continued. When the data is not data indicative of the authorized use of the software application further execution of the software application is disabled. For example, biometric information in the form of a fingerprint may be used for user authorization.
Owner:ACTIVCARD IRELAND
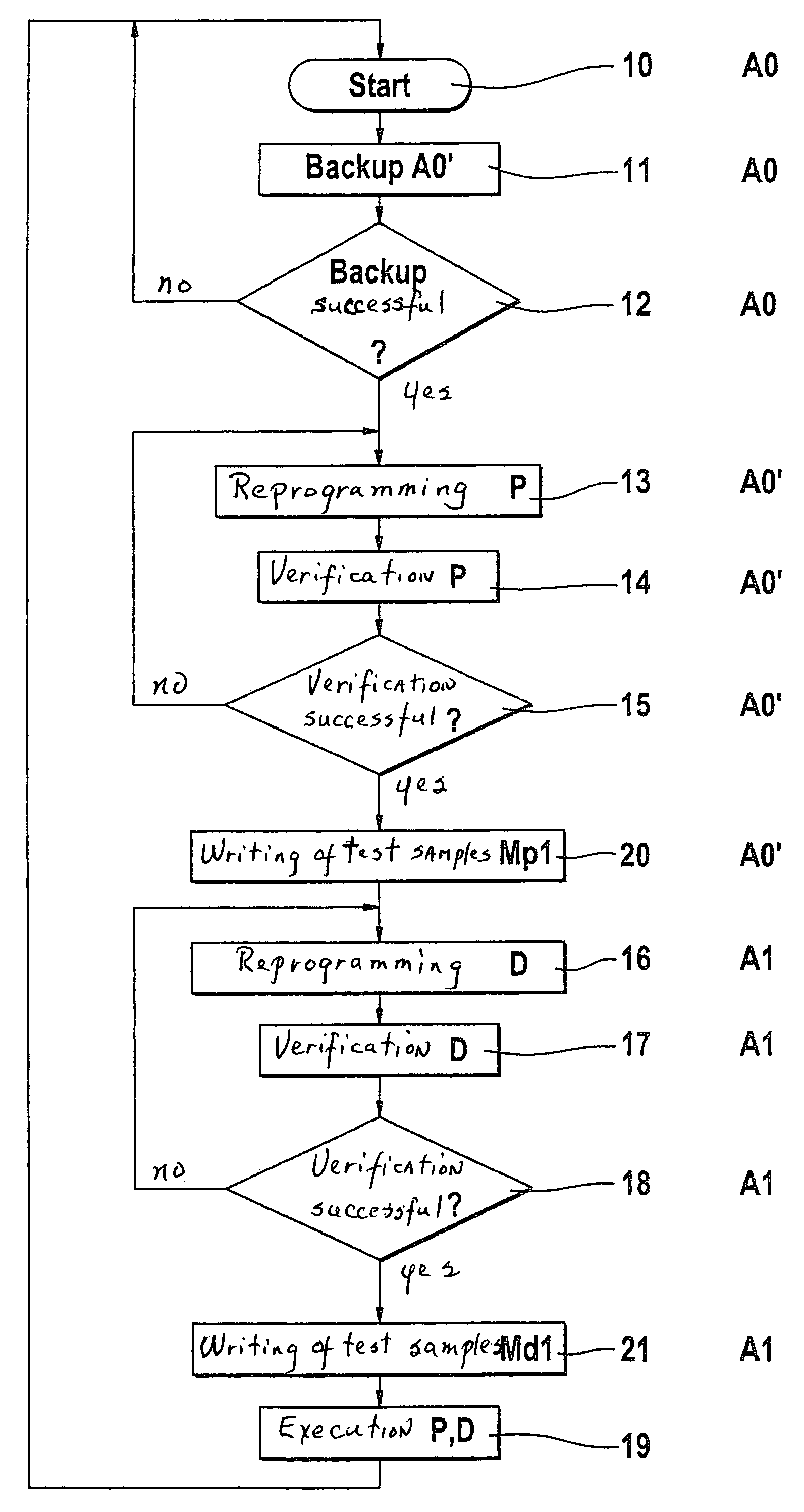
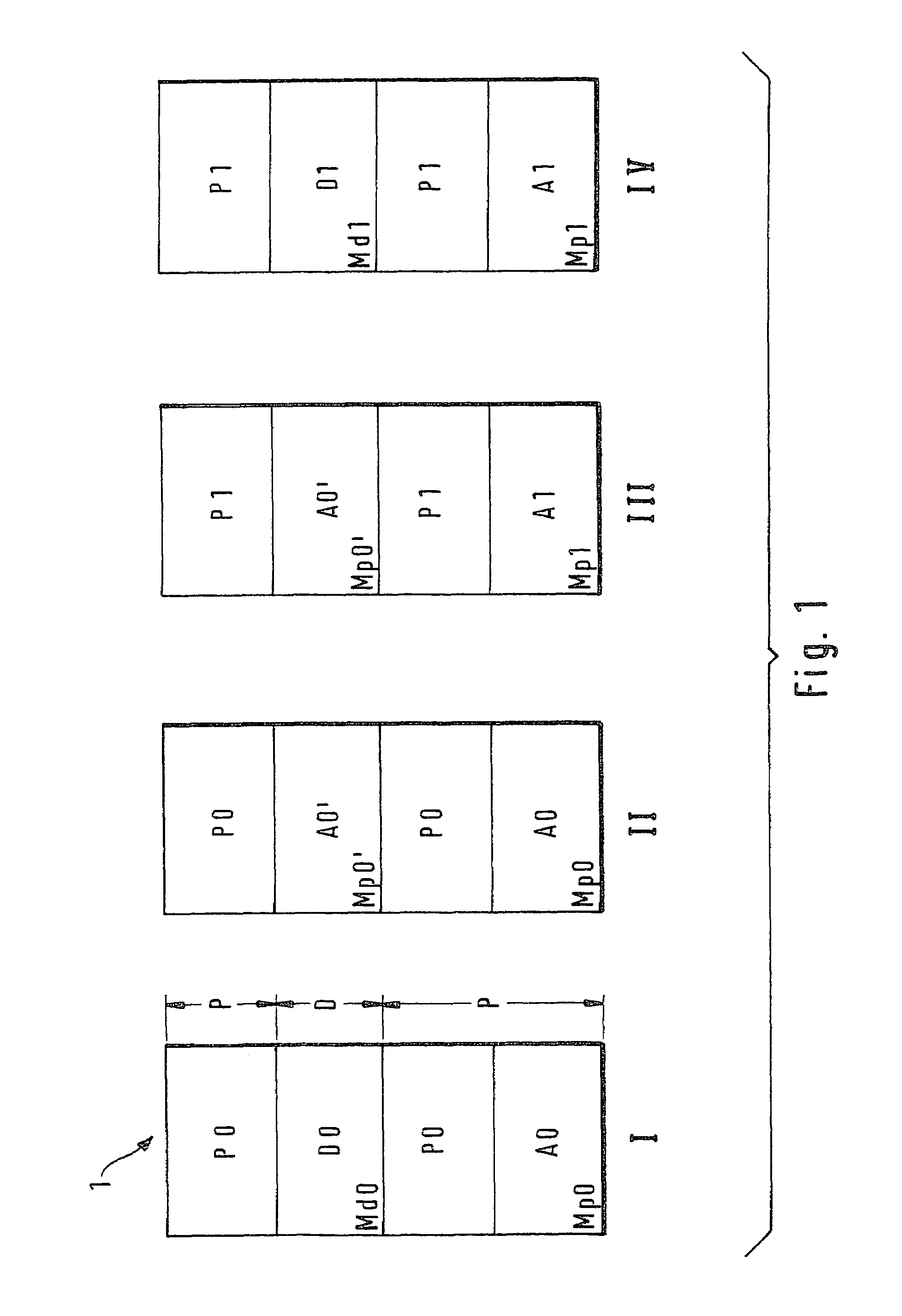
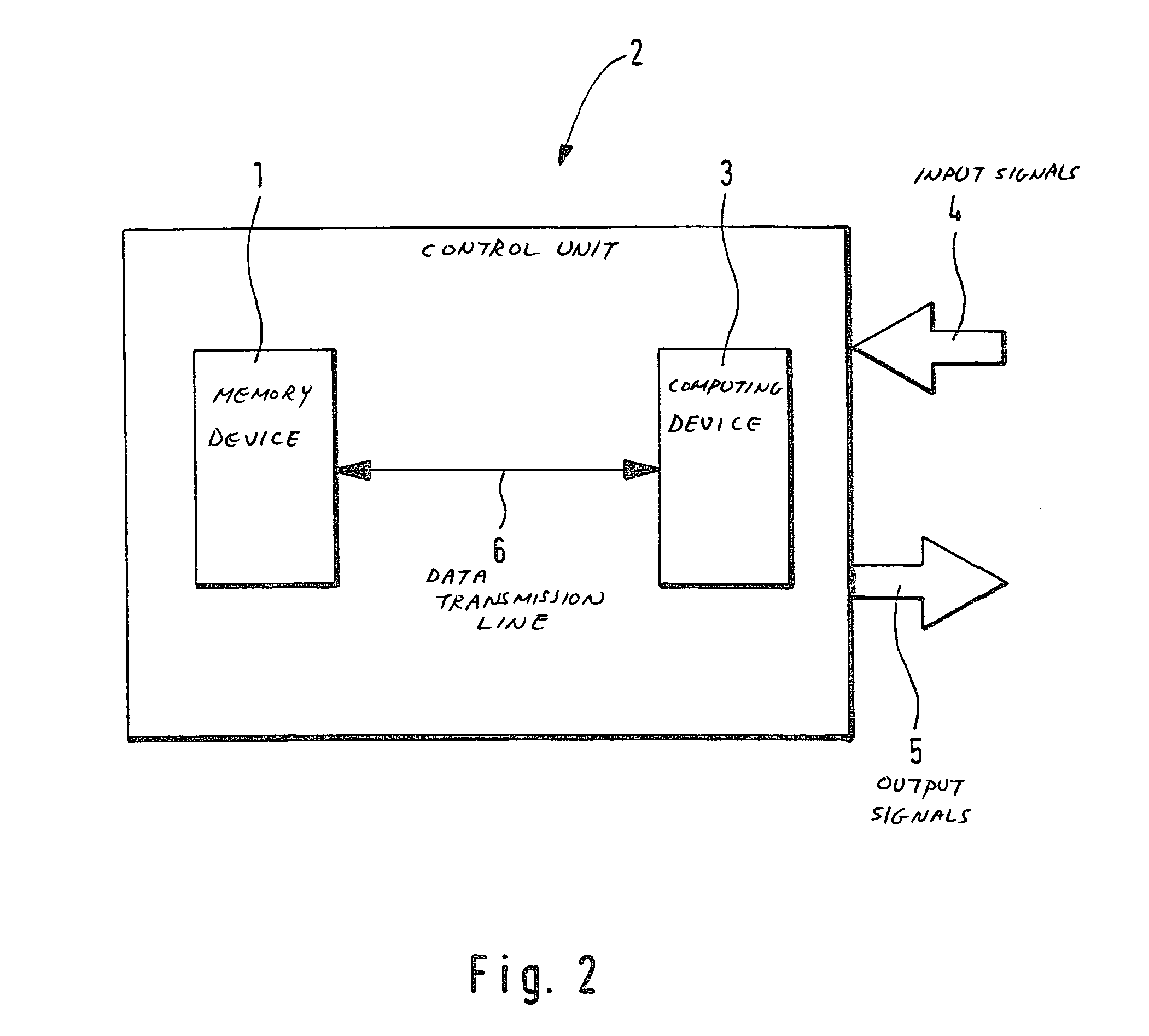
Method for operating a control device
InactiveUS7406717B2Prevent executionProgramme controlComputer controlMobile vehicleControl equipment
The present invention relates to a method for operating a control unit for controlling or regulating a function of a motor vehicle. The control unit includes a programmable memory device. The control or regulation is realized by executing a computer program (P0) at least partially stored in the memory device and by using data (D0) stored at least partially in the memory device. In order to offer the most efficient protection against manipulation of the contents of the memory device by an unauthorized person, it is provided that, at least following a modification of the computer program (P0) stored in the memory device or of the data (D0) stored in the memory device, the modified computer program (P1) is executed only and / or the modified data (D1) are used only if the modified computer program (P1) and / or the modified data (D1) has / have been successfully verified.
Owner:ROBERT BOSCH GMBH
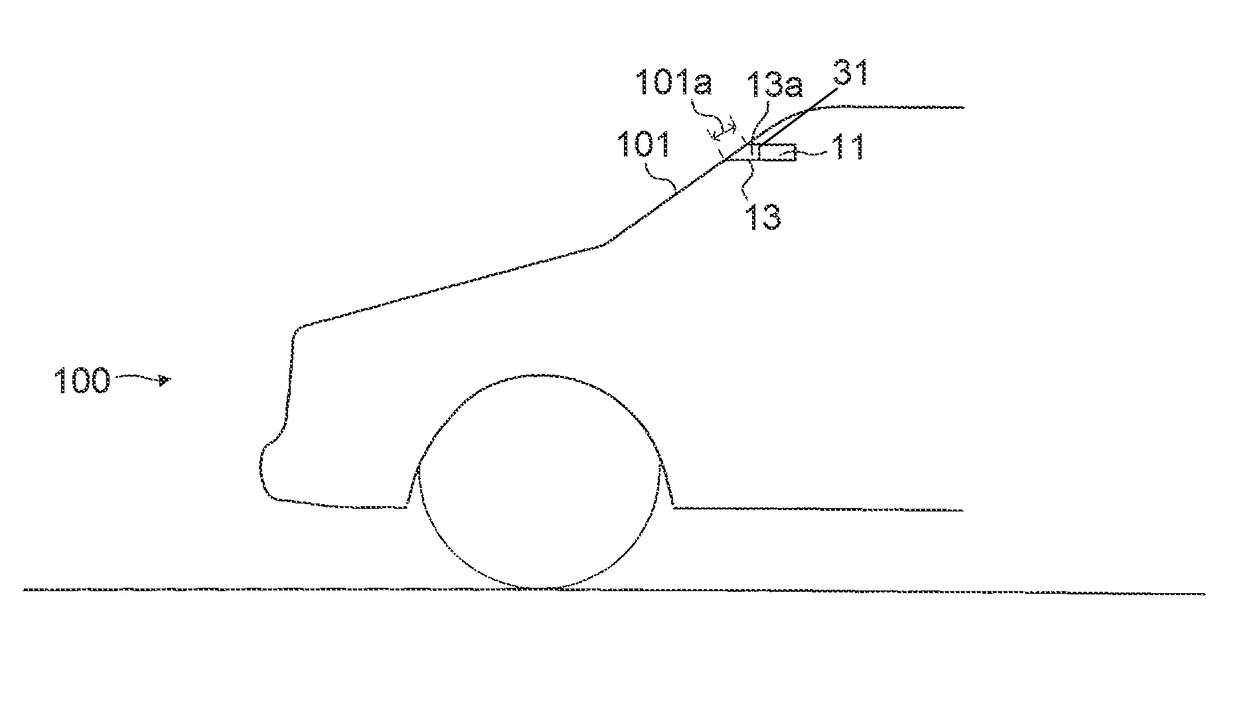
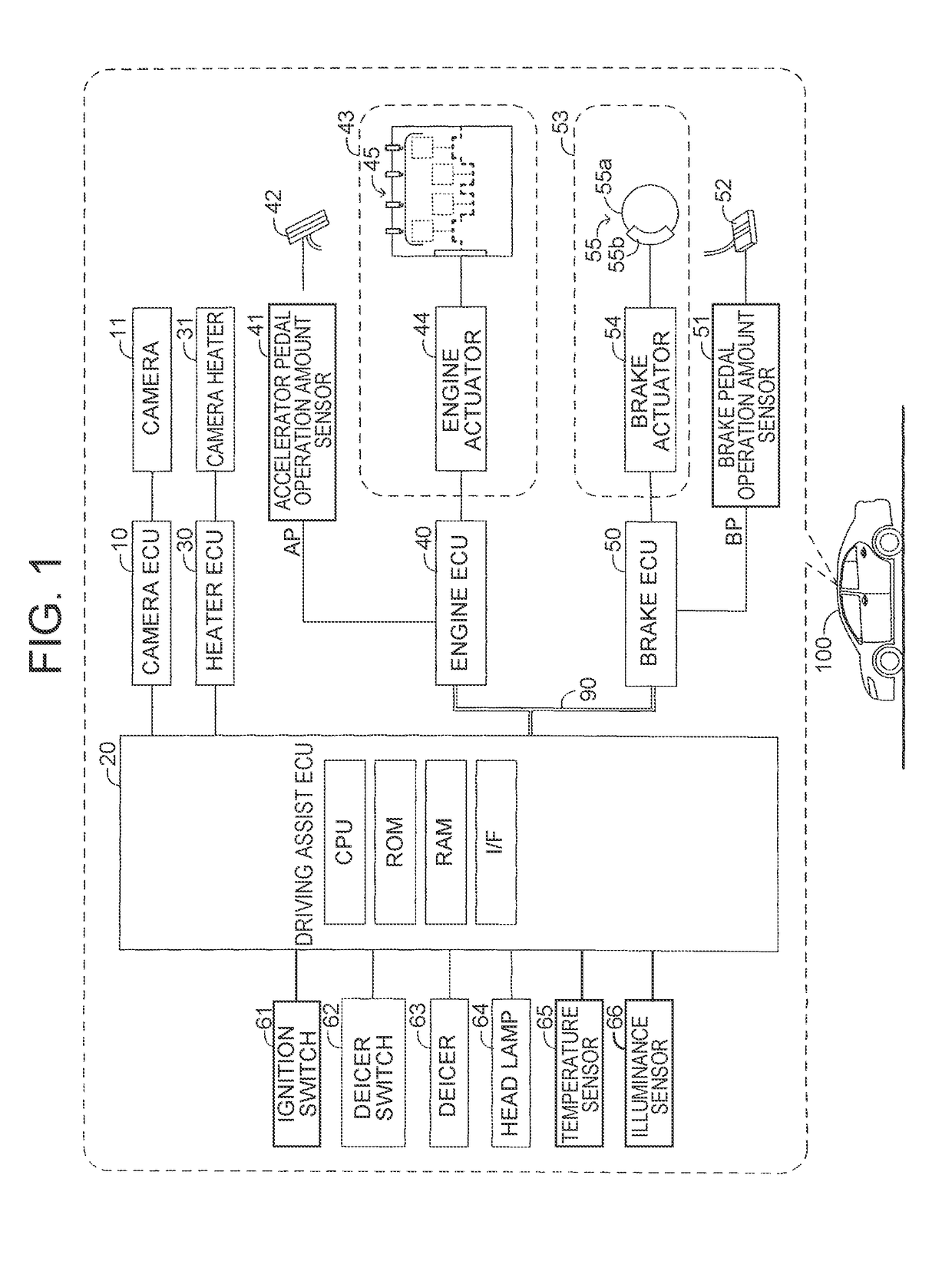
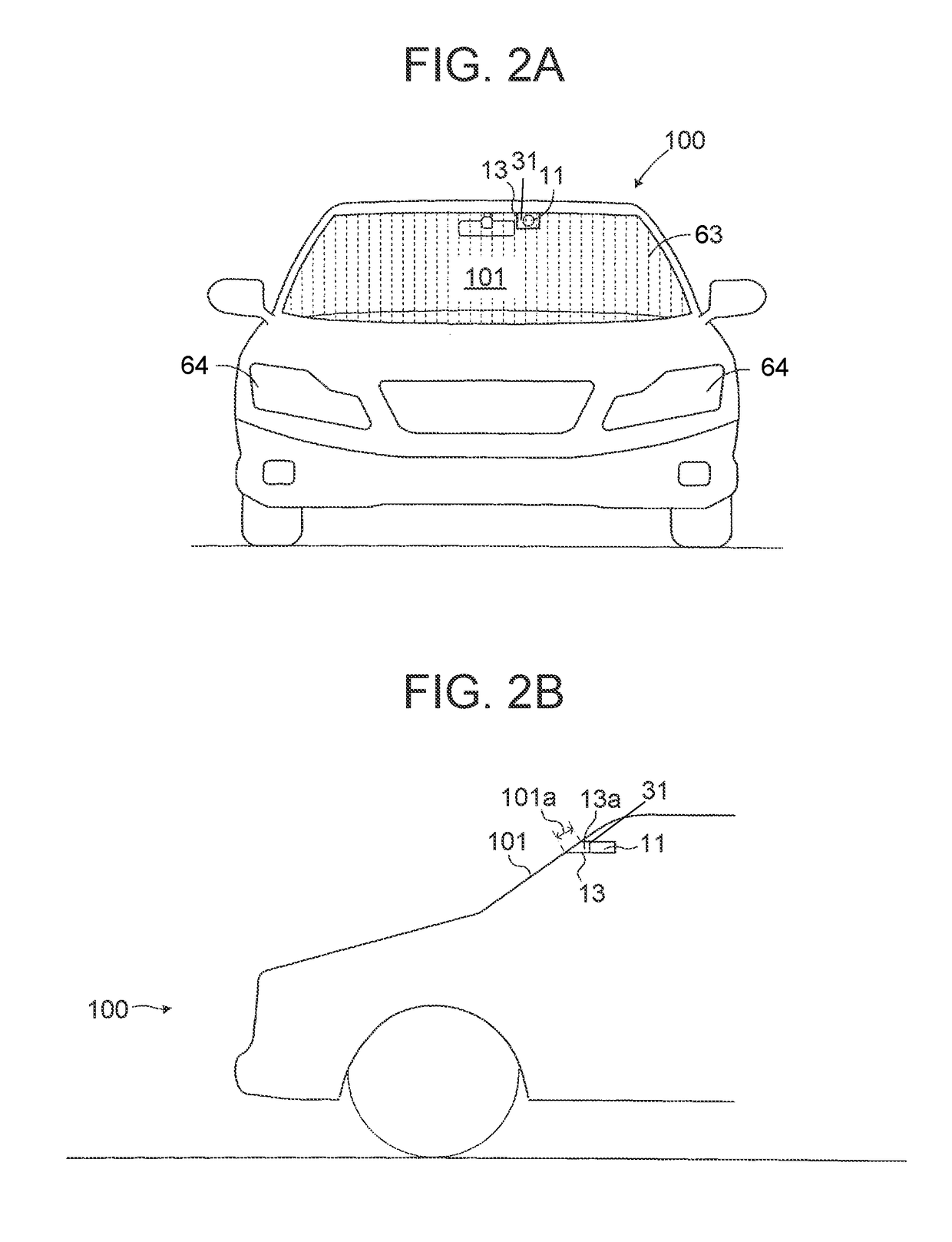
Control device for vehicle heater
A control device for a vehicle heater includes: a camera; a heater configured to heat a portion of the window glass located in front of the camera; a temperature sensor configured to acquire a camera temperature; an illuminance acquisition unit configured to acquire an illuminance outside the vehicle; and a control unit configured to determine that a control prohibition condition to prohibit execution of the heater energization control is satisfied when the camera temperature is equal to or larger than a prohibition threshold temperature, execute the heater energization control when execution of the heater energization control is requested, prevent execution of the heater energization control when the control prohibition condition is satisfied, and when the illuminance is lower than a threshold illuminance, set the prohibition threshold temperature to be lower than when the illuminance is equal to or larger than the threshold illuminance.
Owner:TOYOTA JIDOSHA KK
Electric document anti-disclosure system and its implementing method
InactiveCN100592313CPrevent executionUnlimited useDigital data protectionTransmissionElectronic documentComputer module
The invention discloses an electronic document divulgence prevention system and a realizing method. The system essentially comprises a server and a client. The server implements an information communication with the client through a computer network. A user interface module I in the server is respectively connected with an encryption division module I, a loading key generation module and a communication module I which is connected with an encryption module I. A user interface module II in the client is respectively connected with an encryption division module II, a process monitoring module, afile monitoring module and a communication module II which is connected with an encryption module II. The realizing method of the system includes the following steps: (1) the server is initialized; (2) the client is initialized; (3) an encryption division is used for the client. The electronic document divulgence prevention system and the realizing method of the invention not only facilitate freecommunication of electronic documents on the network, but also effectively avoid the divulgence of the electronic documents, thus having good application prospect.
Owner:李硕 +2
Automatic code locking to reduce the attack surface of software
ActiveCN106687971BDoes not affect experienceReduce attack surfacePlatform integrity maintainanceMemory addressFunctional testing
In an example embodiment, the system determines a set of instructions from available instructions for a computer application. The determined set of instructions provides specific functionality for the computer application. The system can determine the set of instructions by performing functional tests and negative tests on specific functions. The system can reorganize and randomize the set of instructions in memory, and write the reorganized set of instructions to a smaller memory space. For each available instruction that is not in the set of instructions, the system changes the corresponding instruction to be inactive to prevent execution of the corresponding instruction. The system can change the corresponding instruction to be non-functional by rewriting the instruction with the NOP instruction. The system then captures the memory address of the computer application being accessed at runtime. If the captured memory address matches the memory address used for the non-functional instruction, the system can declare a security attack.
Owner:VIRSEC SYST
Methods and apparatus for configuring plasma cluster tools
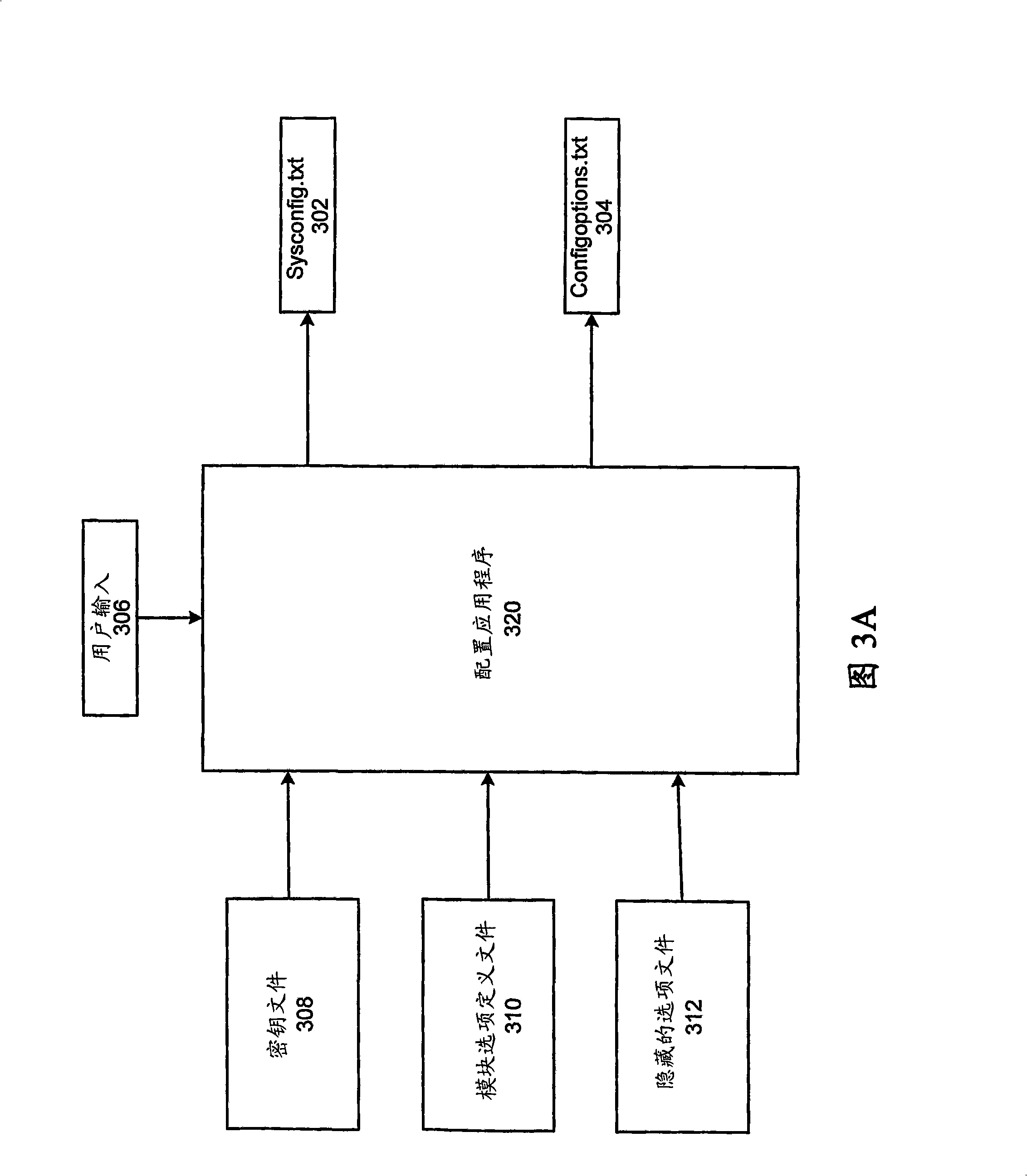
ActiveCN101283360APrevent executionPrevent permissionDigital computer detailsProgram loading/initiatingRunning timeDatabase
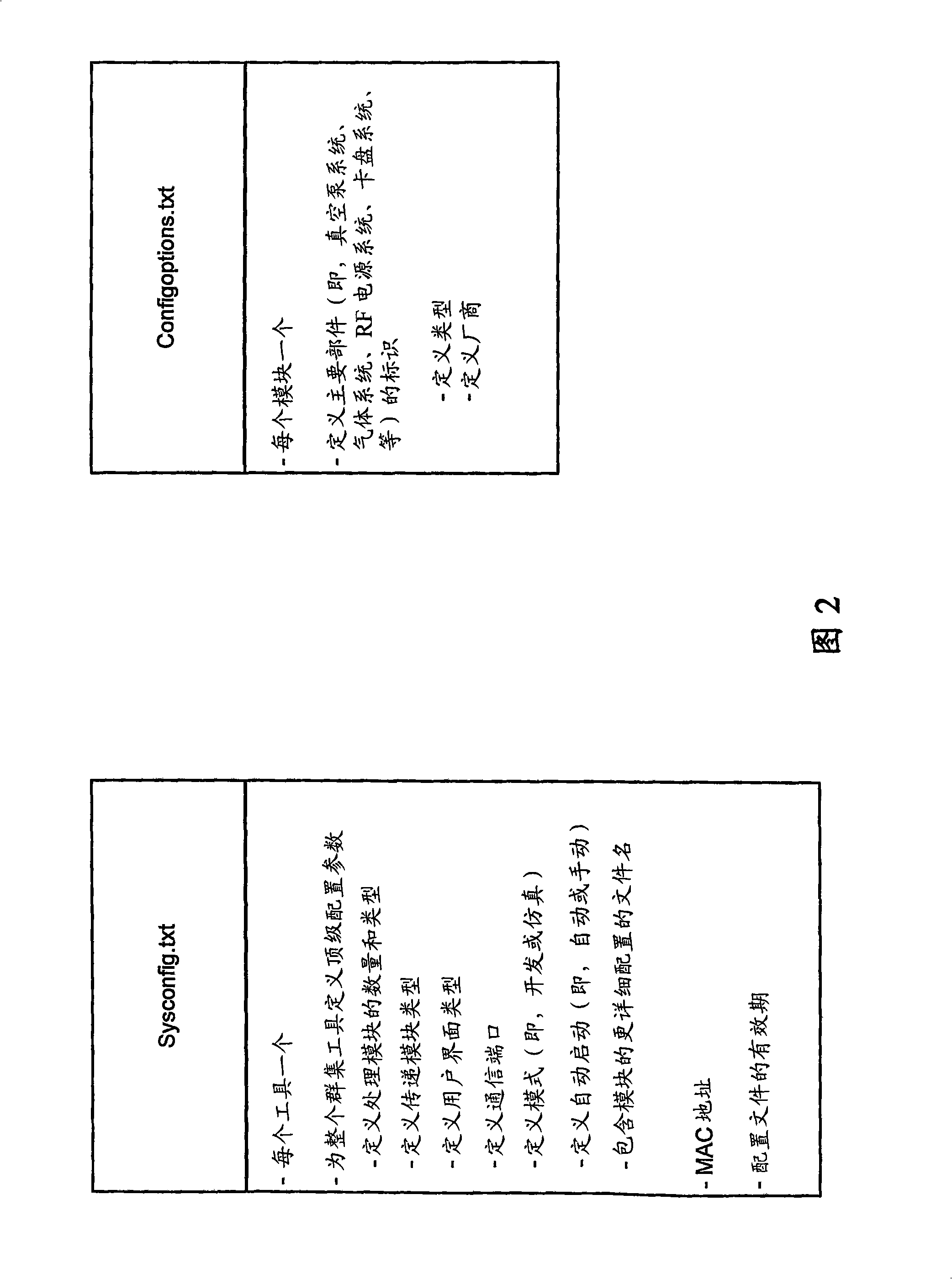
A method for configuring a plasma cluster tool is disclosed. The method includes generating a key file from option specifications, the key file encapsulating configuration restrictions specifically imposed on the plasma cluster tool. The method also includes generating at least one system-wide configuration file and at least one component-level configuration file using the key file. The method additionally includes generating run-time executable objects from a database of option definition files, the at least one system-wide configuration file and the at least one component-level configuration file. Furthermore, the method includes employing the run-time executable objects to configure the plasma cluster tool.
Owner:LAM RES CORP
Information processing apparatus and information processing method
InactiveCN106161837APrevent executionStatic indicating devicesTransmissionInformation processingComputer hardware
An information processing apparatus and method are provided; the information processing apparatus is connectable to a server via a network, and includes an acquisition unit, a first display control unit, a storage unit, and a permission control unit. The acquisition unit acquires a first screen including an execution procedure of a first command from the server. The first display control unit performs control to display the first screen acquired by the acquisition unit. The storage unit stores therein one or more pieces of command information indicating information on a command permitted to be executed. The permission control unit does not permit execution of the first command when the one or more pieces of command information stored in the storage unit include no command information corresponding to the execution procedure of the first command selected from the first screen.
Owner:RICOH KK
Washing machine control method
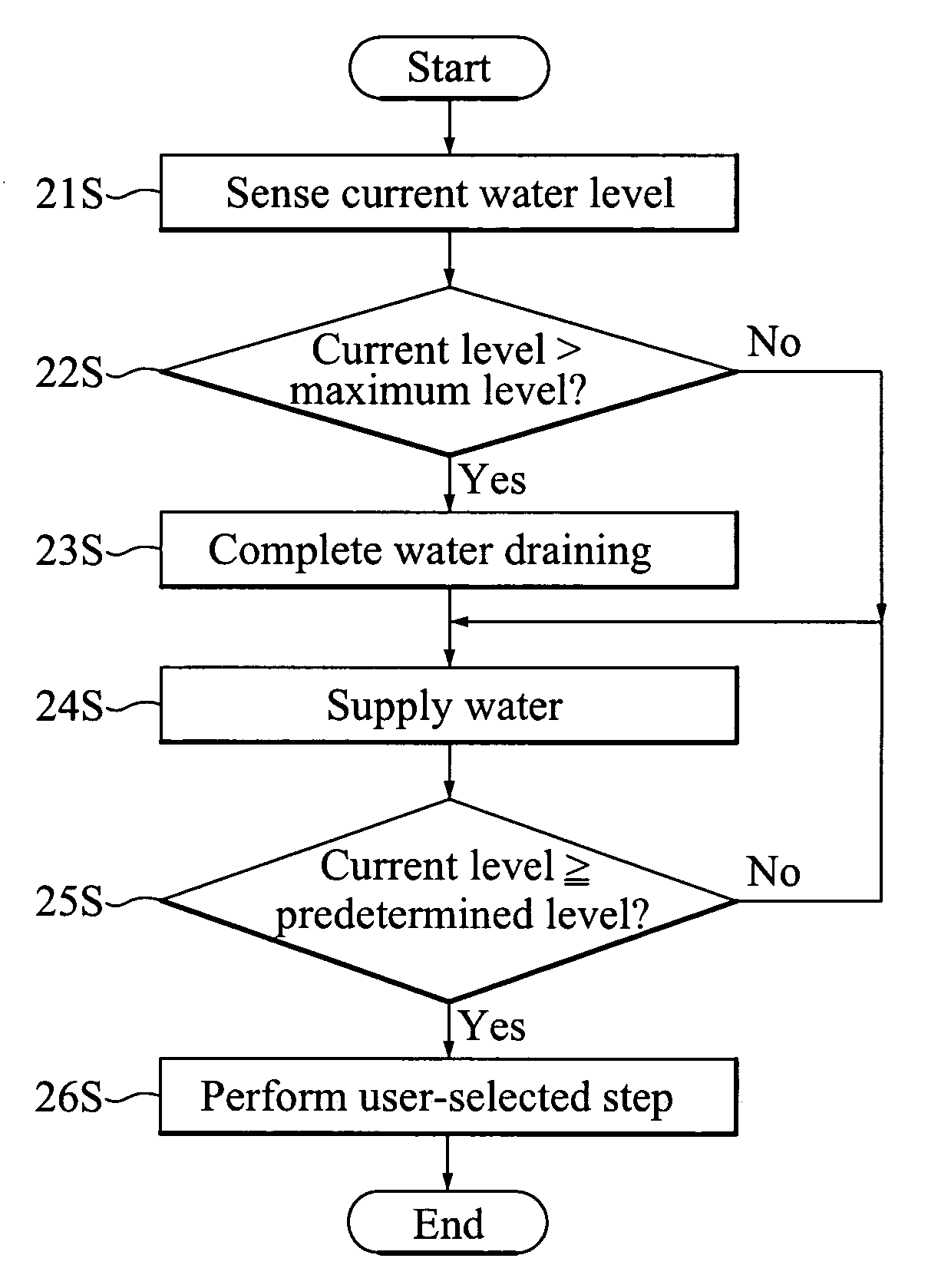
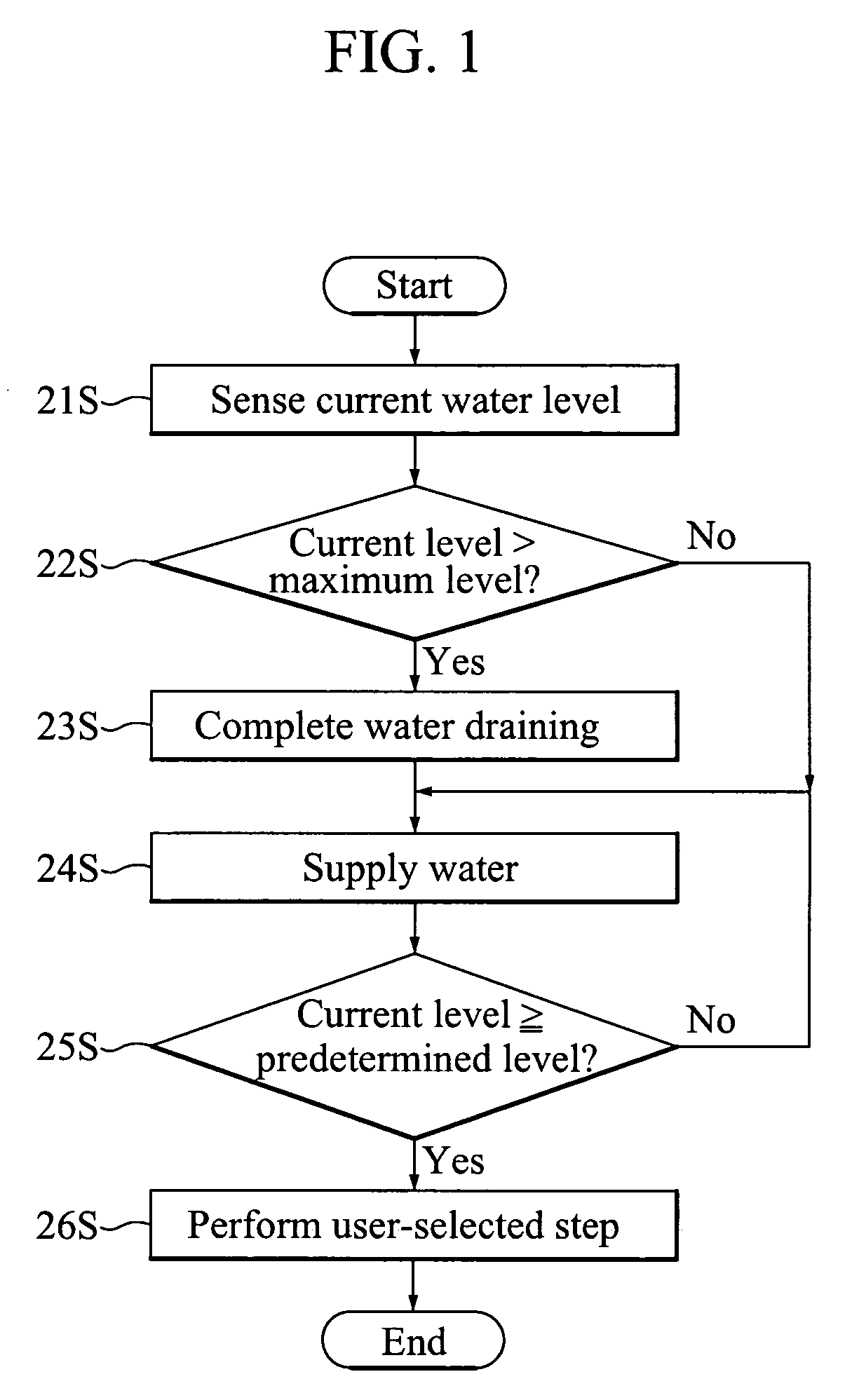
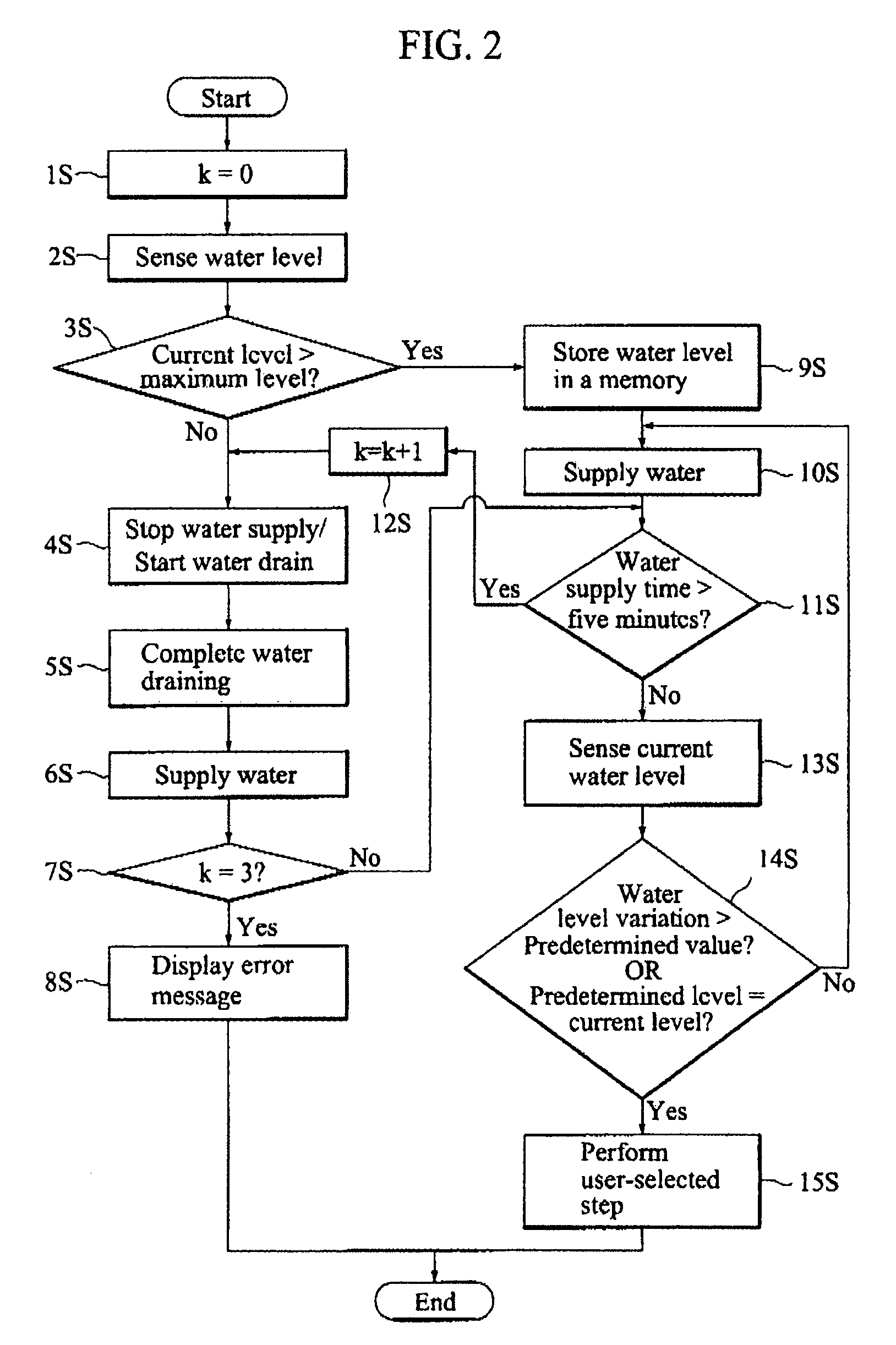
InactiveUS7340793B2Prevent executionPreventing executionData processing applicationsOther washing machinesAntisyphon deviceEngineering
In a method of controlling to a water supplying step and a water draining step in a washing machine having no anti-siphoning device, an error state is determined when water supplying and water draining are simultaneously performed. The error state is determined for cases where there is no change in water level after supplying water for a predetermined time. In such cases, water is then re-supplied after a complete draining. The method includes steps of (a) sensing an initial level of water remaining in the washing machine; (b) storing in a memory a value indicative of the sensed initial water level if the sensed initial water level exceeds a predetermined substantive amount and executing a first water supplying step; (c) discharging the remaining water from the washing machine, executing a second water supplying step, and sensing a current water level if the sensed initial water level is less than the predetermined substantive amount; (d) determining a water level variation based on the sensed current water level and the stored value; (e) repeating the step (c) if the determined water level variation continues to be less than a predetermined value for a first predetermined time period; (f) displaying an internal error if the determined water level variation continues to be less than the predetermined value after a predetermined number of repetitions of the step (e); and (g) executing a user-selected washing step if the determined water level variation exceeds the predetermined value.
Owner:LG ELECTRONICS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com