Patents
Literature
50results about How to "Reduce attack surface" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
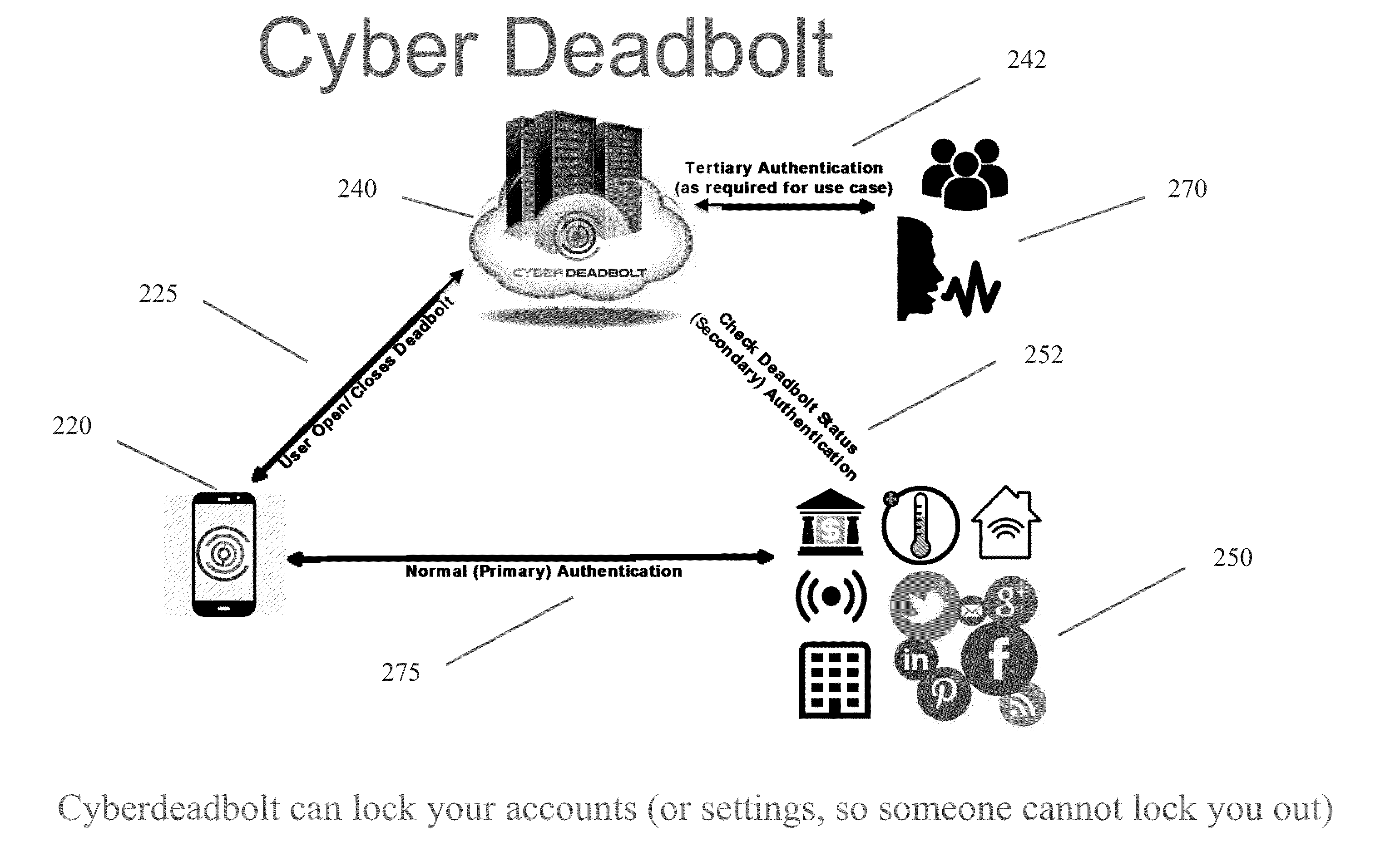
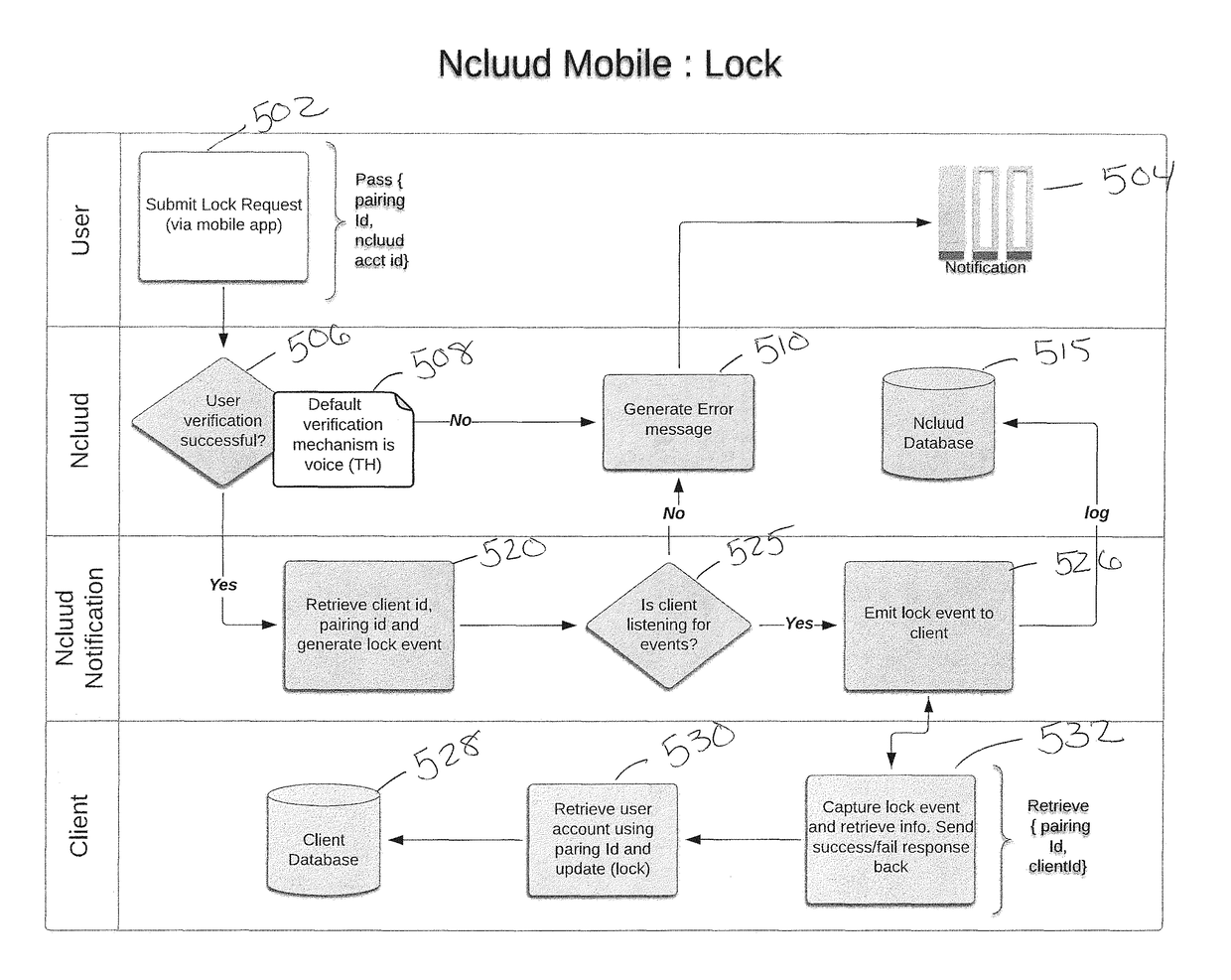
Locking Applications and Devices Using Secure Out-of-Band Channels
InactiveUS20160277439A1Reduce surfaceReduce attack surfaceTransmissionSecurity arrangementClient-sideUser authentication
Systems and methods are provided for locking / unlocking a user account for accessing a client application. The systems and methods pair a user account for accessing a client application to a separate user authentication account. The user authentication server managing the user authentication account provides heightened measures for authenticating the identity of the user, such as by voice samples and human authenticator. After the heightened authentication of the user, the user may lock or unlock paired accounts from the user authentication account, wherein preventing all attempts to access the client application using the paired account. The client application may also capture information regarding login attempts to the paired user account. The captured information may be sent to the authentication server for providing reports of login attempts and generating alerts to automatically lock the paired account in cases of suspicious behavior.
Owner:RIVETZ CORP
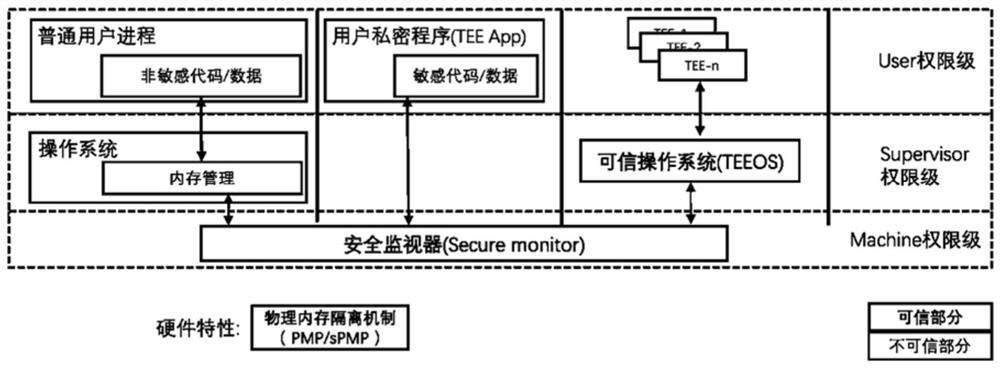
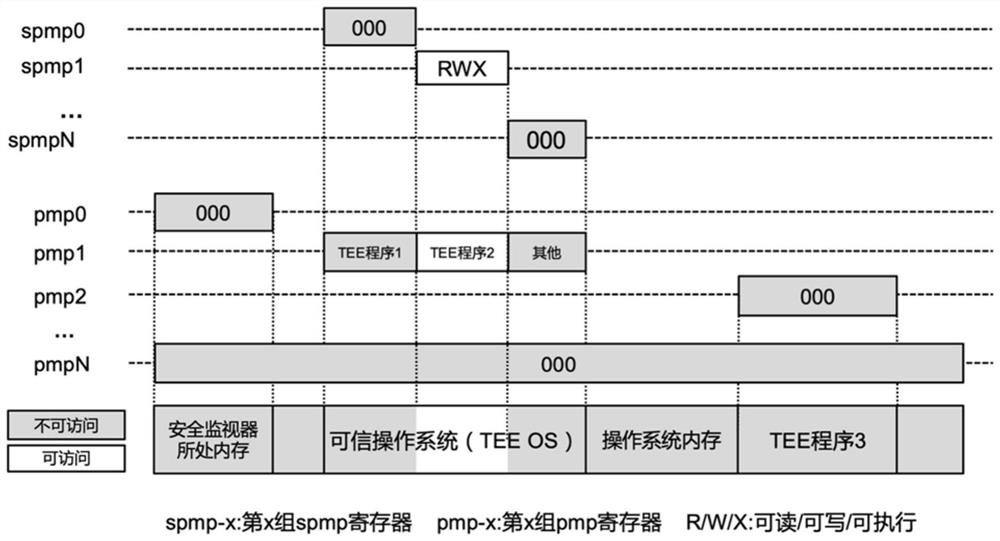
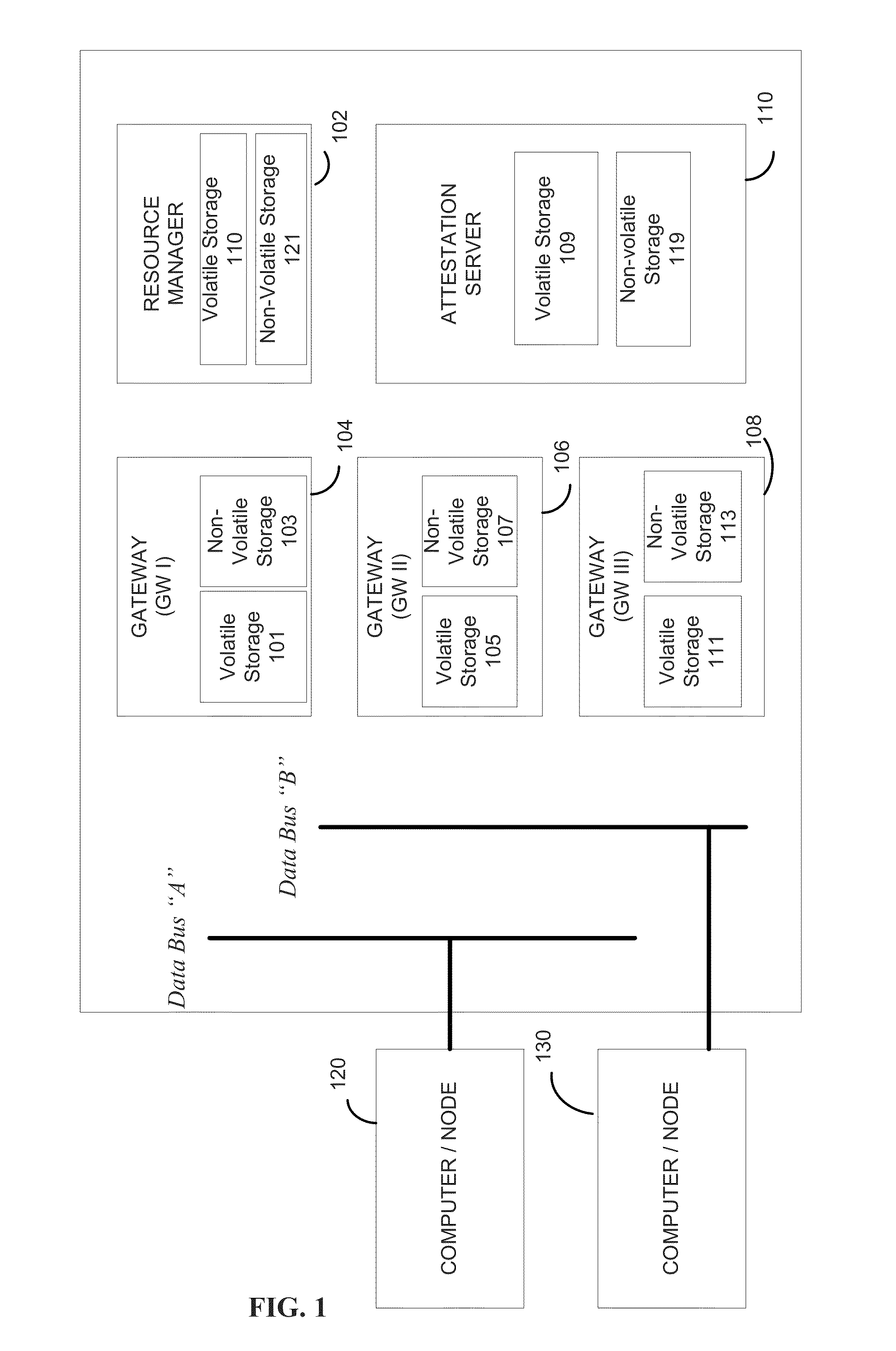
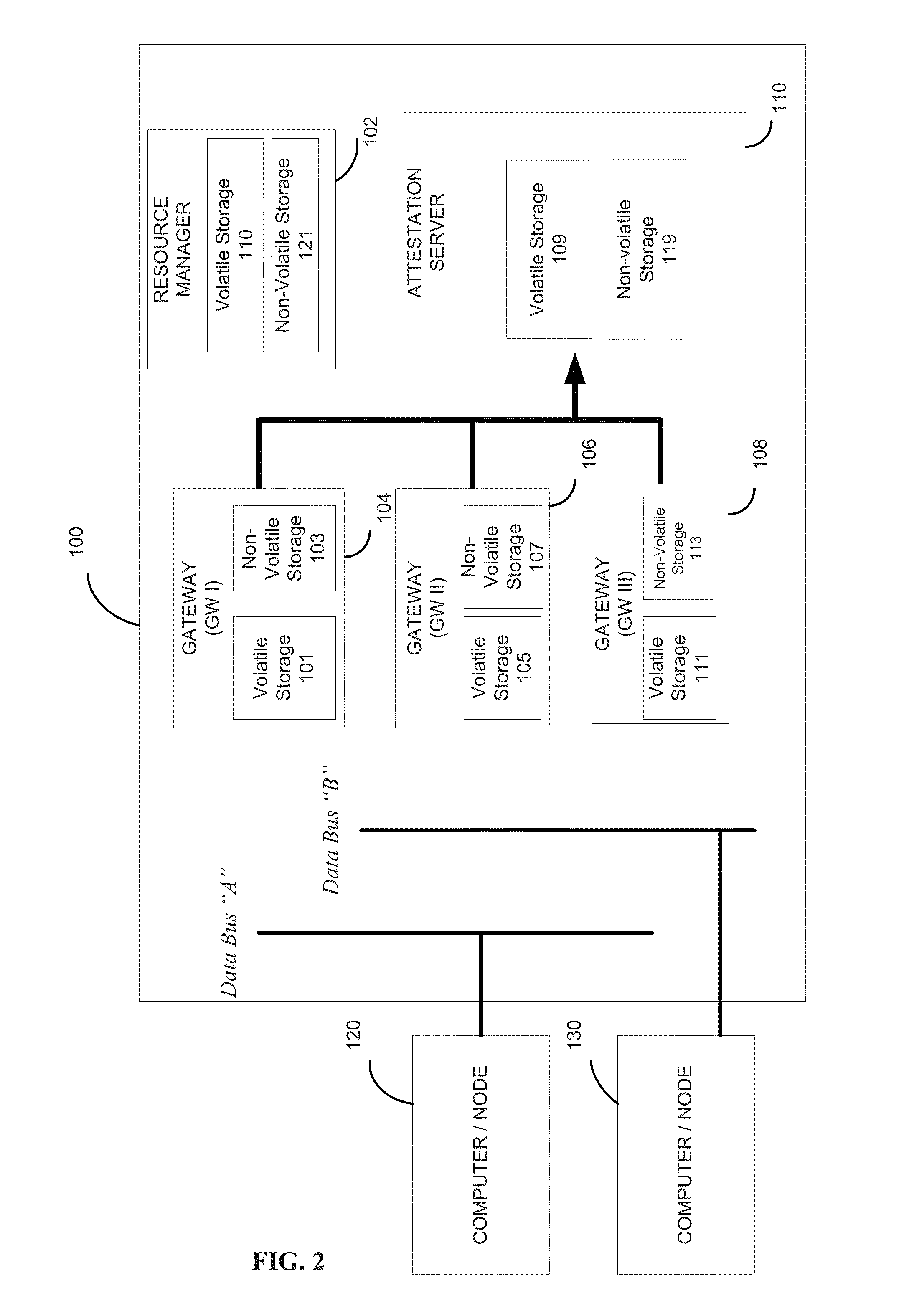
Physical memory isolation method based on RISC-V instruction architecture
ActiveCN111651778AImprove securityAchieving verifiabilityDigital data protectionInternal/peripheral component protectionComputer architectureEngineering
The invention provides a physical memory isolation method based on an RISC-V instruction architecture. According to the method, on the basis of an existing PMP (physical memory isolation) technology capable of being configured by a Machine mode of an RISC-V instruction architecture, an sPMP (physical memory isolation) technology capable of being configured by a Supervisor mode is added; the physical memory isolation technology sPMP depends on a plurality of groups of sPMP registers which can only be read and written by a Machine mode program and a Supervisor mode program. According to the invention, the limitation of the number of security applications of the existing TEE system based on the PMP register set is broken through, and the characteristics of efficient security application starting, efficient security application communication, fine-grained security application memory resource allocation and the like can be provided. Compared with the existing TEE design, the safety and theexpandability of the system are greatly improved.
Owner:SHANGHAI JIAO TONG UNIV
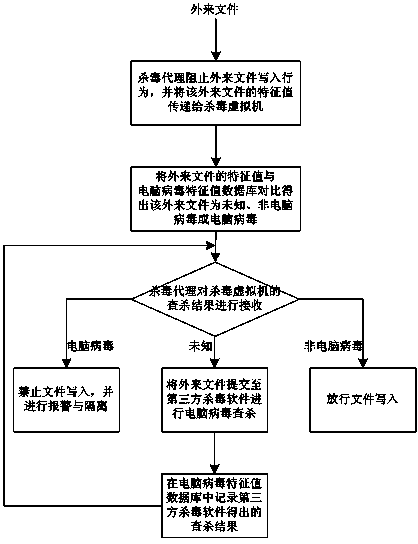
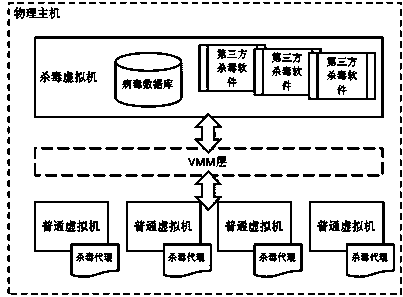
Computer virus searching and killing method based on desktop cloud virtualization technology
InactiveCN103810429AReduce consumptionReduce attack surfacePlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtualizationThird party
The invention discloses a computer virus searching and killing method based on the desktop cloud virtualization technology. The method mainly solves the problems that in the prior art, when virus killing is carried out on a virtualization platform, resources of a server are occupied, a virus storm and a virus killing storm are easily formed and management is inconvenient to achieve. When more than two independent virtual hosts are allocated for each physical host, one of the virtual hosts serves as an antivirus virtual machine, the rest of the virtual hosts serve as common virtual machines, a third-party antivirus software is integrated in the antivirus virtual machine so that the antivirus virtual machine can have capacity for searching and killing viruses and recording searching and killing results, antivirus agents are installed in the common virtual machines, and a computer virus characteristic value database is installed in the antivirus virtual machine. By the adoption of the scheme, the method is convenient to use and high in extendibility and has high practical value and promotional value.
Owner:CHENGDU CHANGTIAN INFORMATION TECH CO LTD
Secure Layered Iterative Gateway
ActiveUS20130298219A1Avoid attackPartly effectiveMultiple digital computer combinationsPlatform integrity maintainanceWeb resourceSoftware
In methods and a device for mitigating against cyber-attack on a network, a distributed intermediary device is placed into a network between computers or network nodes of the network to mitigate cyber-attacks between the computers or nodes of a network from remote systems. Threats are assessed by utilizing internal information assurance mechanisms of the device to detect such cyber-attacks without requiring external modification of the software and / or hardware of the computers or nodes of the network to be protected. The device prevents attacks at the platform level against the OS and network resources.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
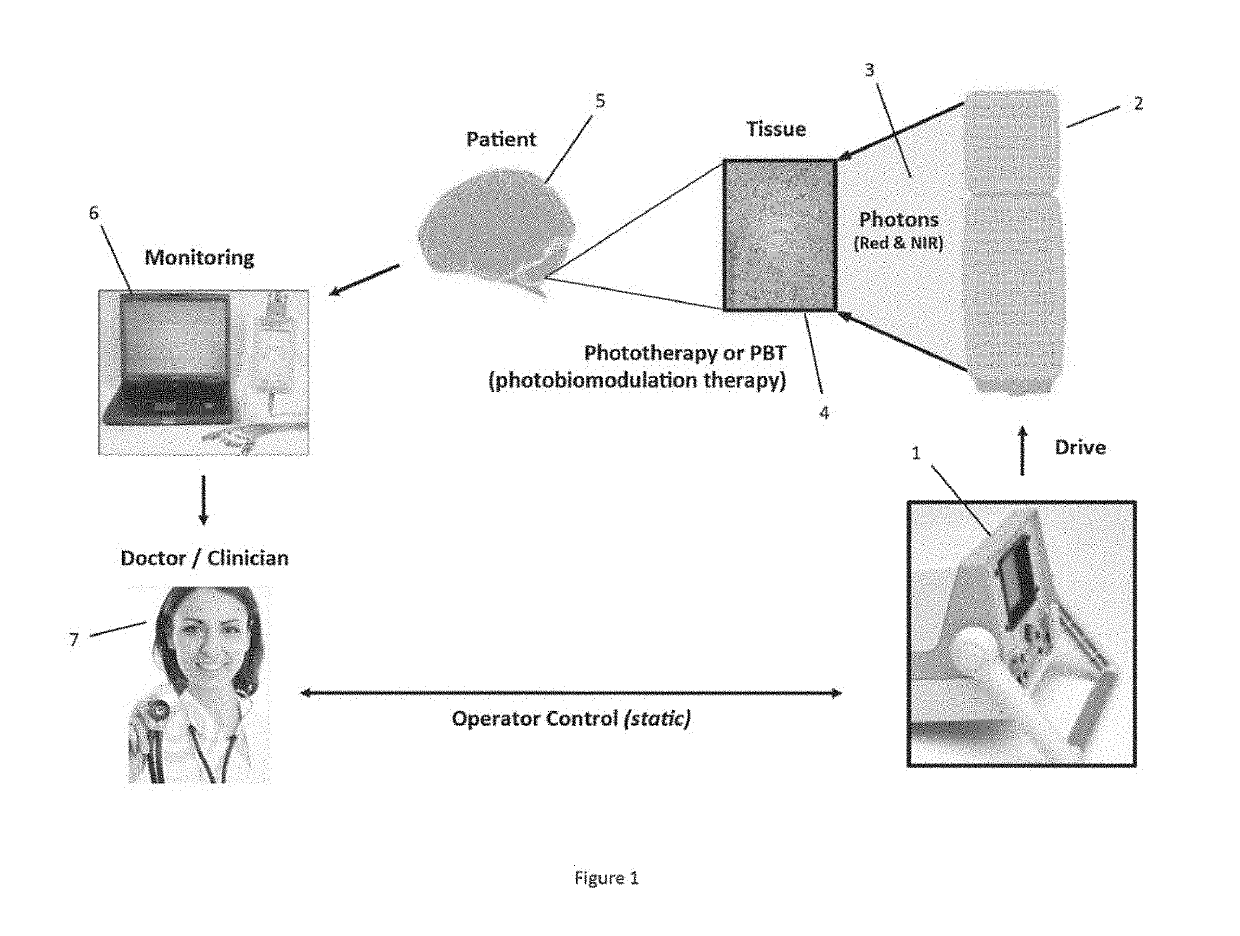
Distributed Photobiomodulation Therapy System And Method
ActiveUS20190246463A1Reduce inflammationReduce joint painElectrical apparatusElectroluminescent light sourcesMicrocontrollerLight treatment
A phototherapy system includes a channel driver, a first microcontroller and a pad comprising a string of light-emitting diodes (LEDs). The pad also comprises a second microcontroller that autonomously controls the string of LEDs such that the LEDs are controlled even if communication between the first microcontroller and the pad is interrupted.
Owner:APPLIED BIOPHOTONICS
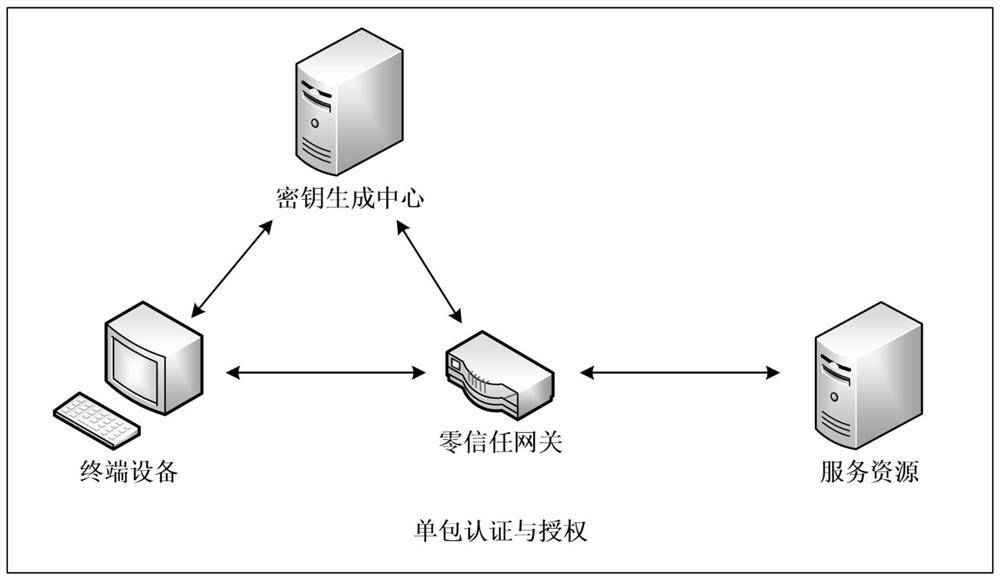
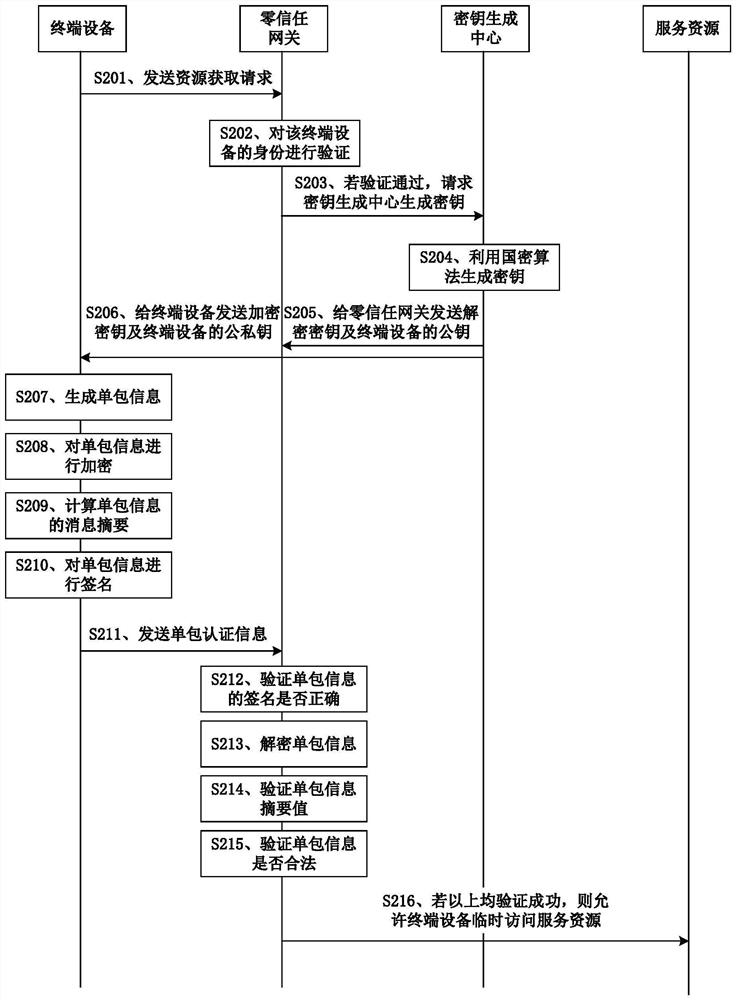
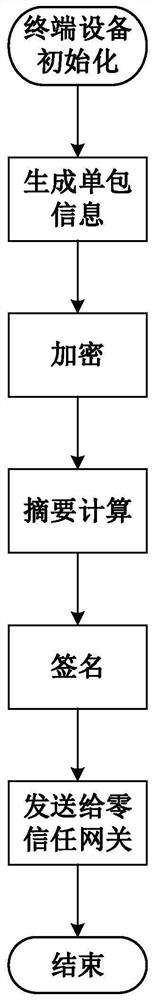
Resource access control method based on zero-trust single packet authentication and authorization
PendingCN114553568AImprove efficiencyImprove network securitySecuring communicationInternet privacyAuthorization
The invention belongs to the field of information security, and particularly relates to a zero-trust single packet authentication and authorization-based resource access control method, which comprises the following steps that: terminal equipment initiates an access request to a zero-trust gateway; the zero-trust gateway verifies the request information sent by the terminal equipment, and if the verification is passed, the key center generates a session key and a public key and a private key of the terminal equipment; the terminal equipment generates single packet information that a user accesses the zero-trust gateway, and encrypts the single packet information by using the session key; calculating a message digest of the single packet information, signing the encrypted single packet information and digest information by using a private key, and sending all information to a zero-trust gateway; the zero-trust gateway verifies the signature information, the encryption information and the summary information, if verification is passed, a consistent port is opened for the terminal equipment, and the terminal equipment is allowed to temporarily access the server; by adopting the method described by the invention, the hiding of the service port is realized, the network attack surface is reduced, and the network security is improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
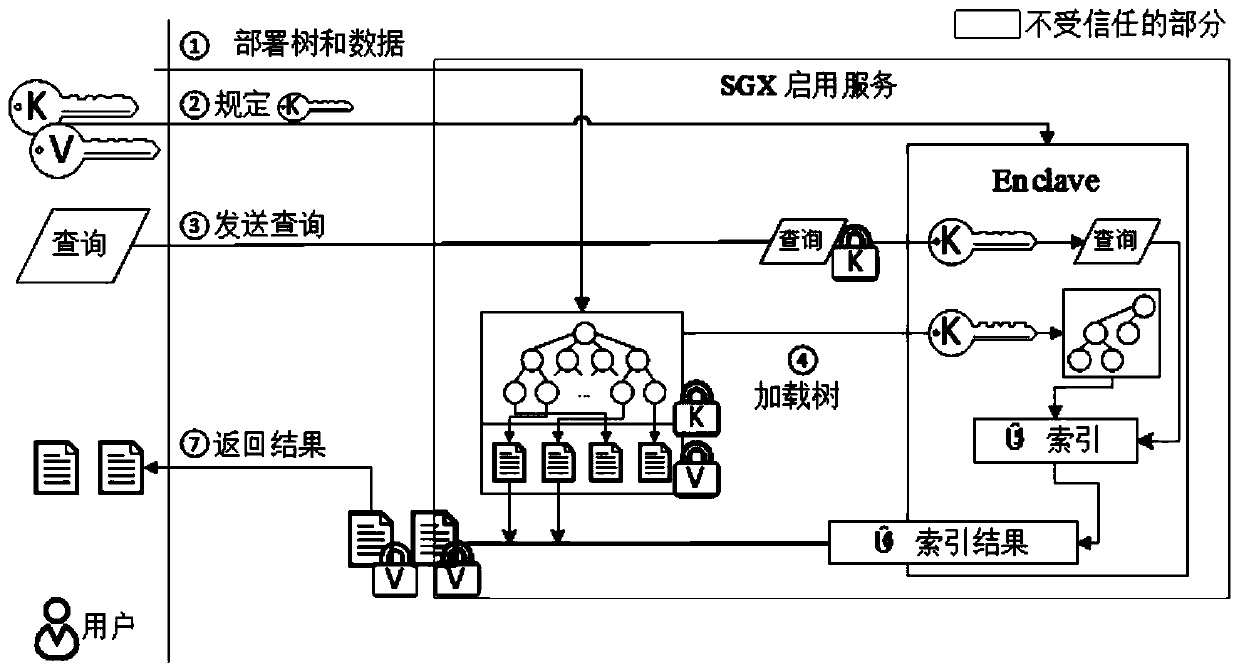
Security indexing system based on SGX
The invention discloses a security indexing system based on SGX. The security index system comprises the following steps: enabling a user to expand a data value by using an index keyword; inserting the key into a B + tree, and linking the B + tree with the expanded data value; providing the client to the enclave through secure connection at the client; enabling the client to send an indexing queryto the server; loading the B + tree structure from the untrusted storage into an enclave memory by the enclave, and decrypting the B + tree structure; enabling the tree to traverse from the root node, obtain a node indexing algorithm from the untrusted storage, and finally reache a group of leaf nodes to store a pointer; and obtaining the encrypted value from the untrusted storage by using the pointer, sending the encrypted value to the client, and decrypting the received file by using the client. According to the invention, the balance among the security, the performance and the function isrealized, the performance and the storage are greatly improved, and the index time also has great advantages even if complex indexing is carried out on big data.
Owner:NORTHEASTERN UNIV
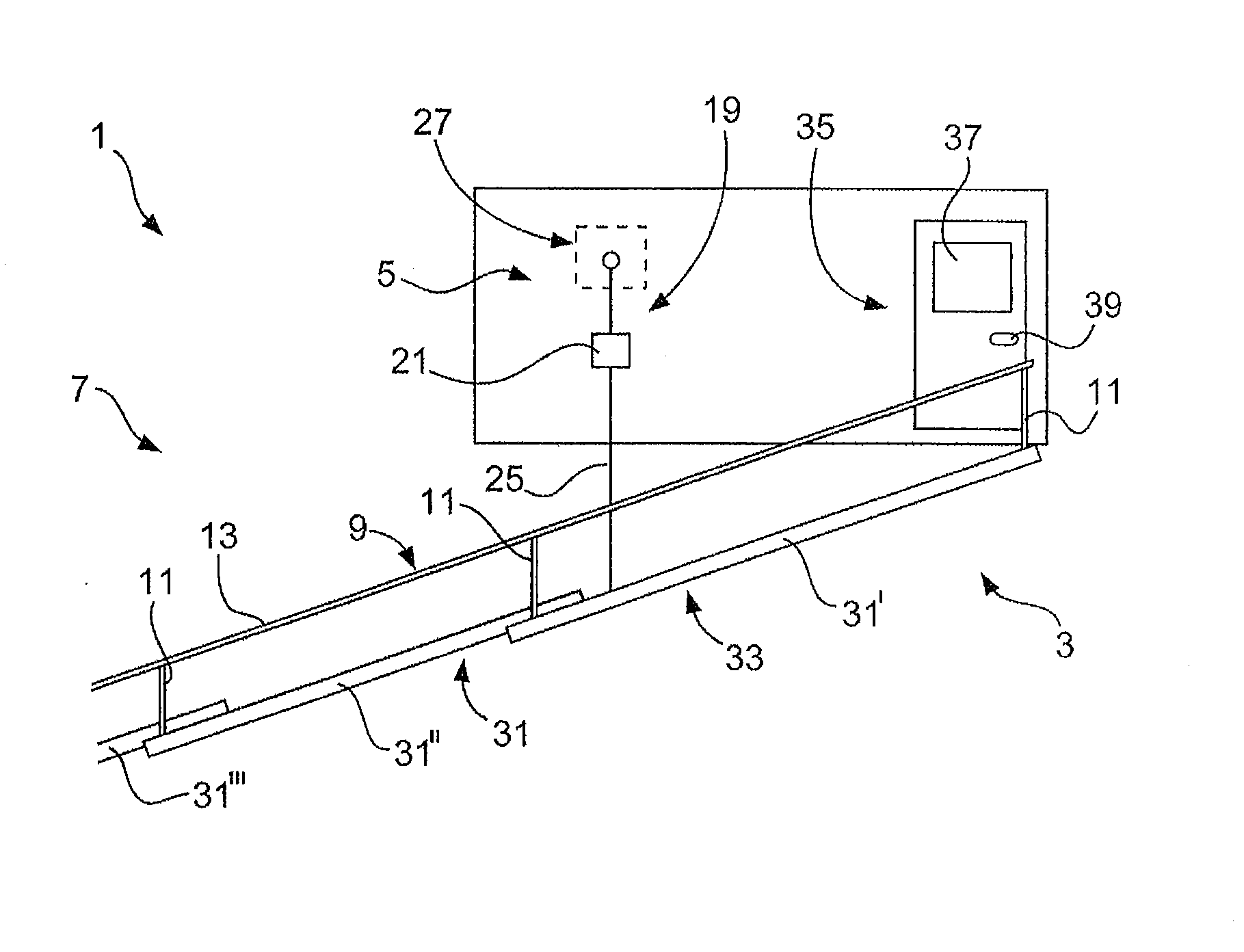
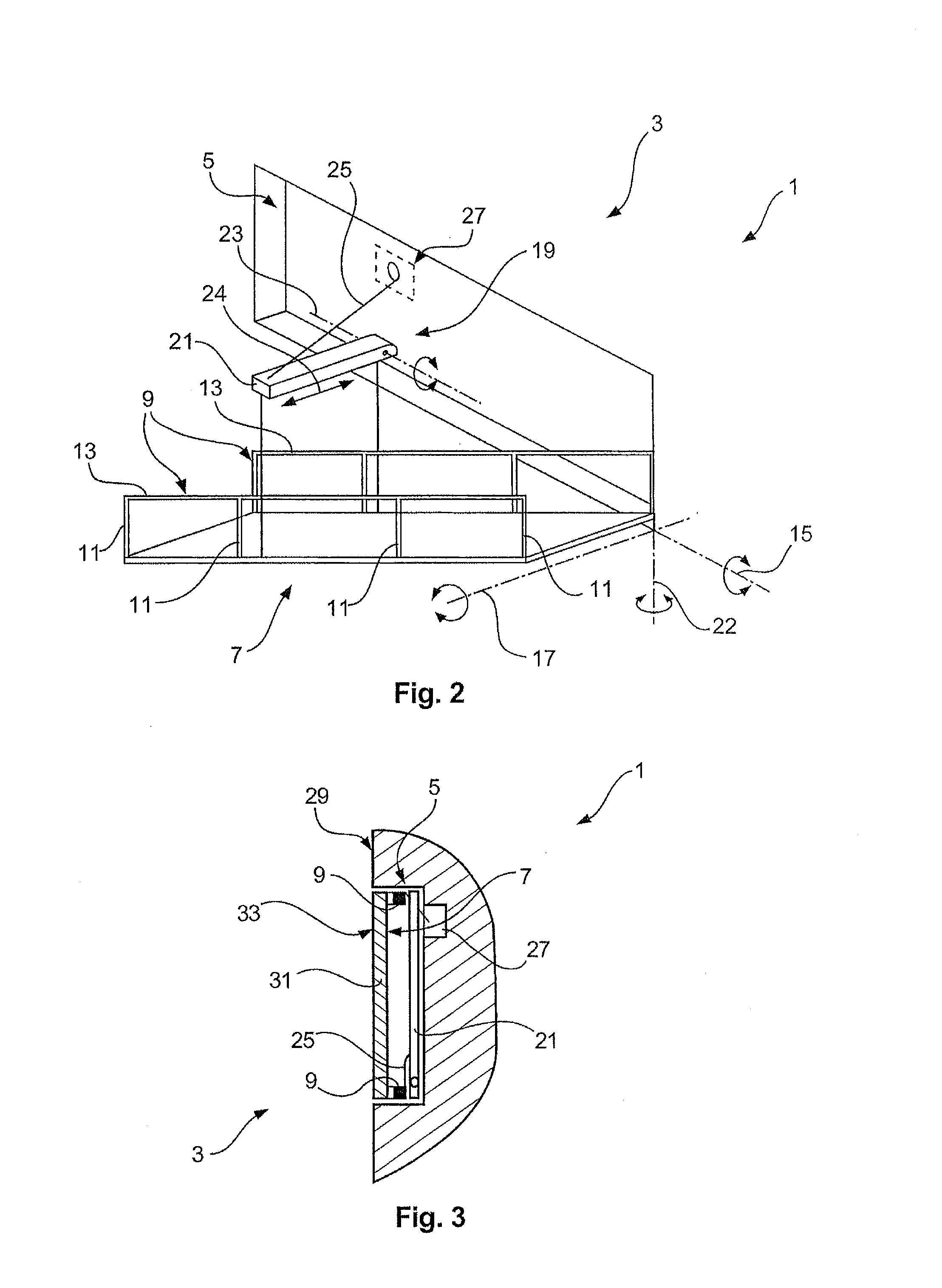
Ship and gangway for the same
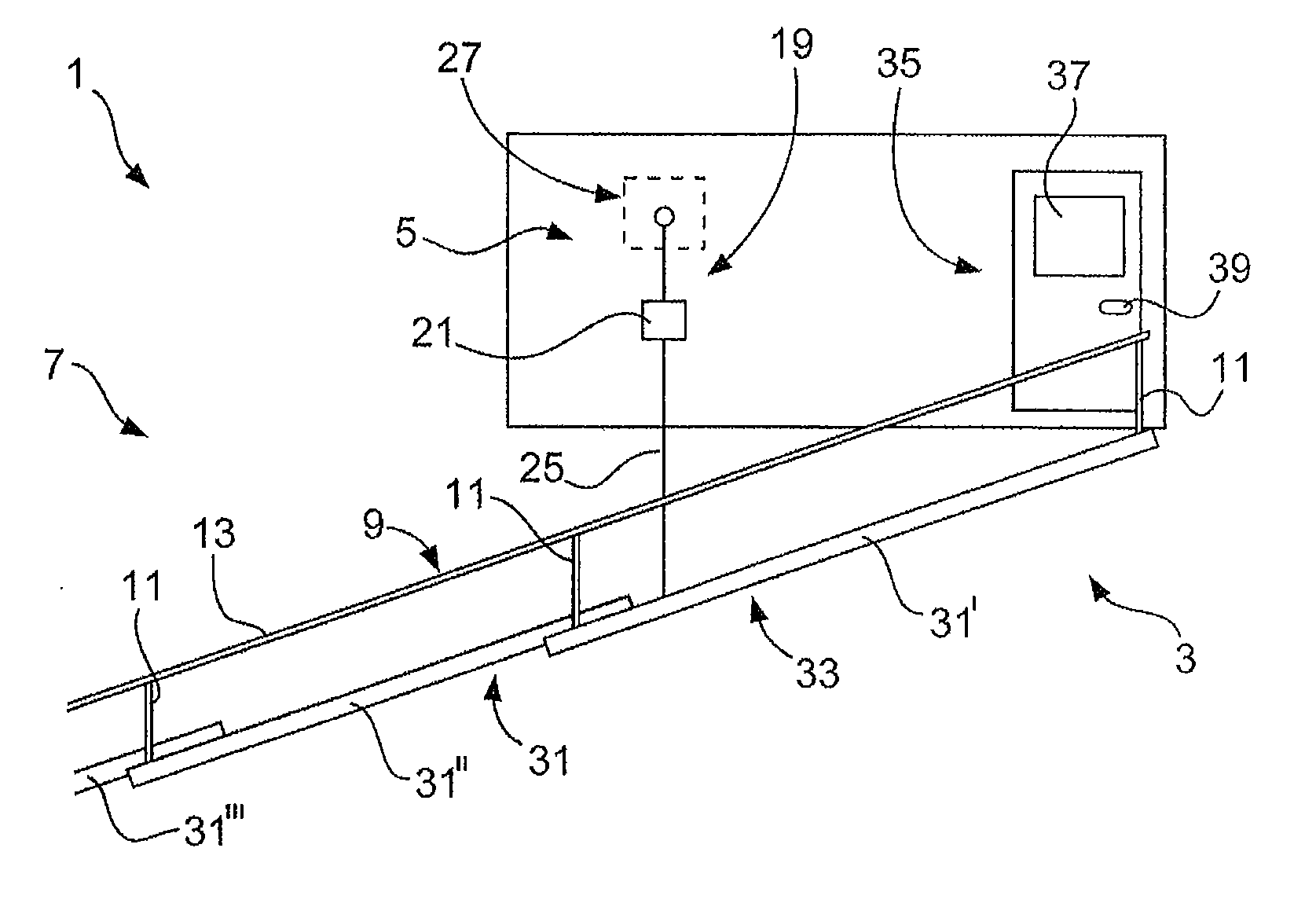
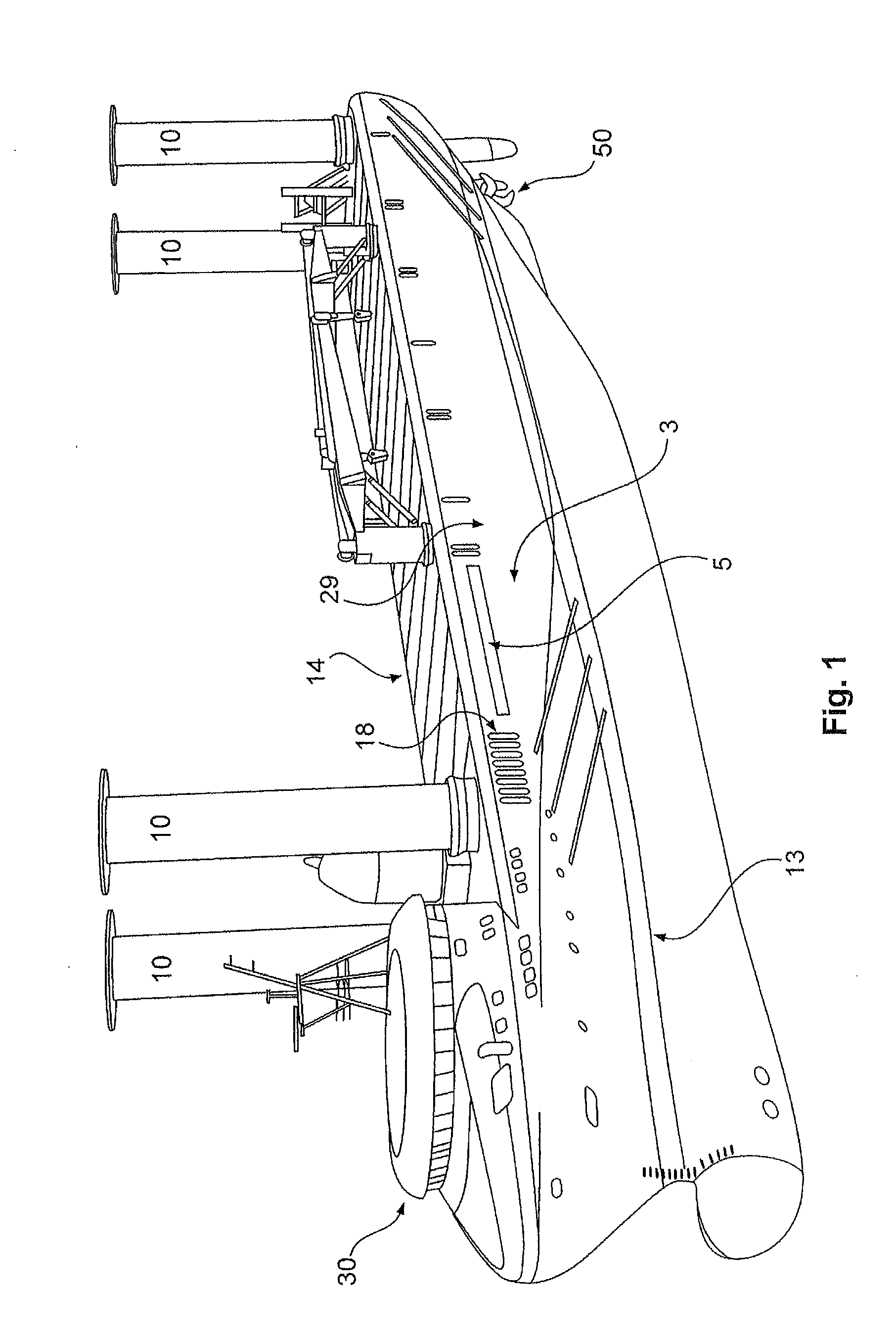
ActiveUS20130228110A1Space minimizationReduce air resistanceCargo handling apparatusPropulsion based emission reductionCargo vessel
The invention relates to a ship, in particular a freight ship, comprising an outer wall and a gangway for embarking and disembarking the ship, which can be moved backwards and forwards between an embarking / disembarking position and a stored position when the ship is being driven. The invention also relates to a ship in which the gangway comprises a base having a lower surface which, when said gangway is in the stored position, is flush with the surface of the outer wall. The invention also relates to a gangway for embarking and disembarking a ship, which is embodied according to the claimed invention for use on a ship.
Owner:WOBBEN PROPERTIES GMBH
Secure access for B2B applications
PendingUS20210136041A1Reduce attack surfaceReduce operationKey distribution for secure communicationMultiple keys/algorithms usageComputer securityMultiple applications
Owner:ZSCALER INC
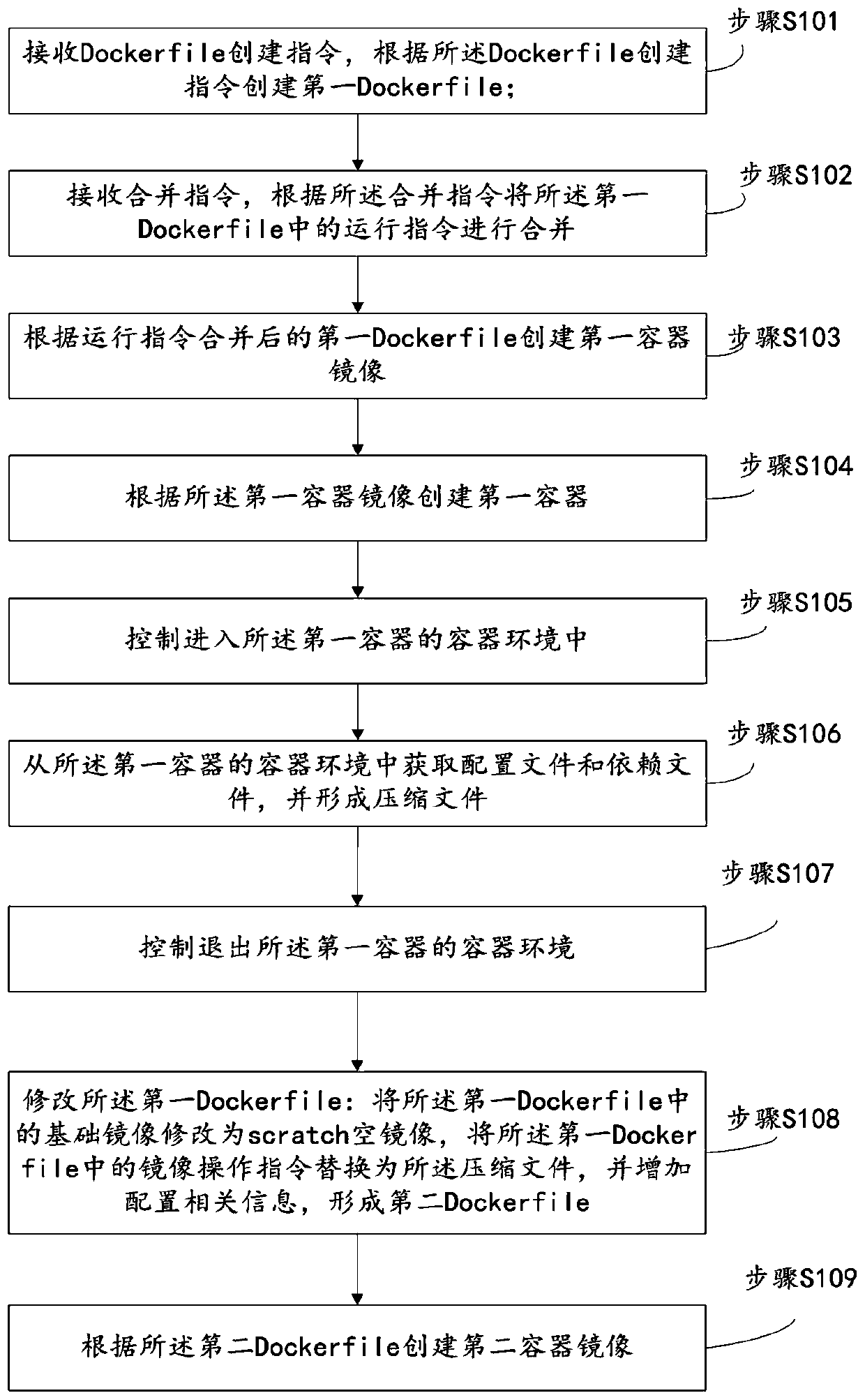
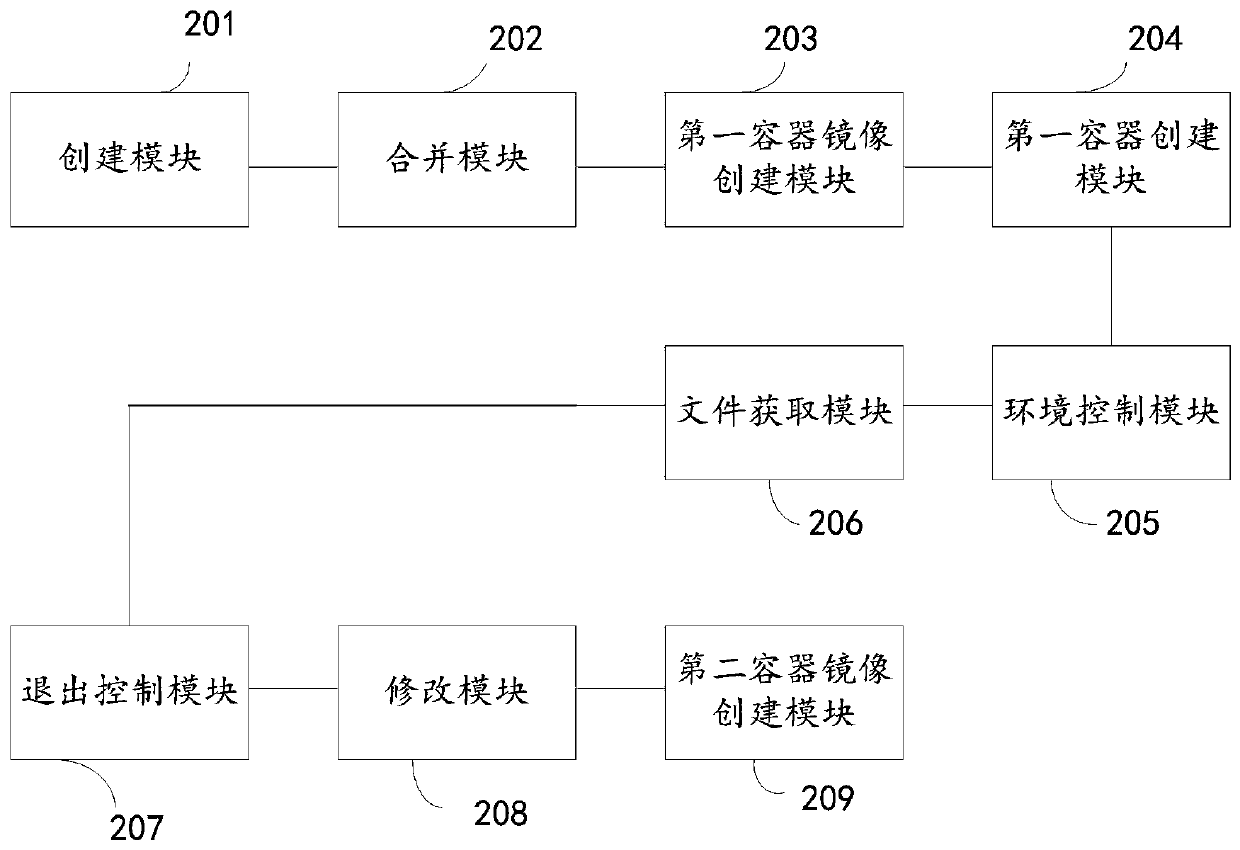
Method, device and equipment for container mirror image construction, and storage medium
ActiveCN111190687AReduce sizeReduce usageEnergy efficient computingSoftware simulation/interpretation/emulationComputer hardwareEngineering
The invention discloses a method, a device and equipment for container mirror image construction, and a storage medium. The method comprises the following steps: receiving a Docker file creation instruction, and creating a first Docker file according to the Docker file creation instruction; combining operation instructions in the first Docker file; creating a first container mirror image accordingto the first Docker file after the operation instruction combination; creating a first container according to the first container mirror image; controlling to enter a container environment of the first container; obtaining a configuration file and a dependent file from the container environment of the first container, and forming a compressed file; controlling to exit the container environment ofthe first container; modifying a basic mirror image in the first Docker file into a scatch empty mirror image, replacing a mirror image operation instruction in the first Docker file with the compressed file, and adding configuration related information to form a second Docker file; and creating a second container mirror image according to the second Docker file. The method can effectively reducethe size of the container mirror image.
Owner:安超云软件有限公司
Method and system for secure communications
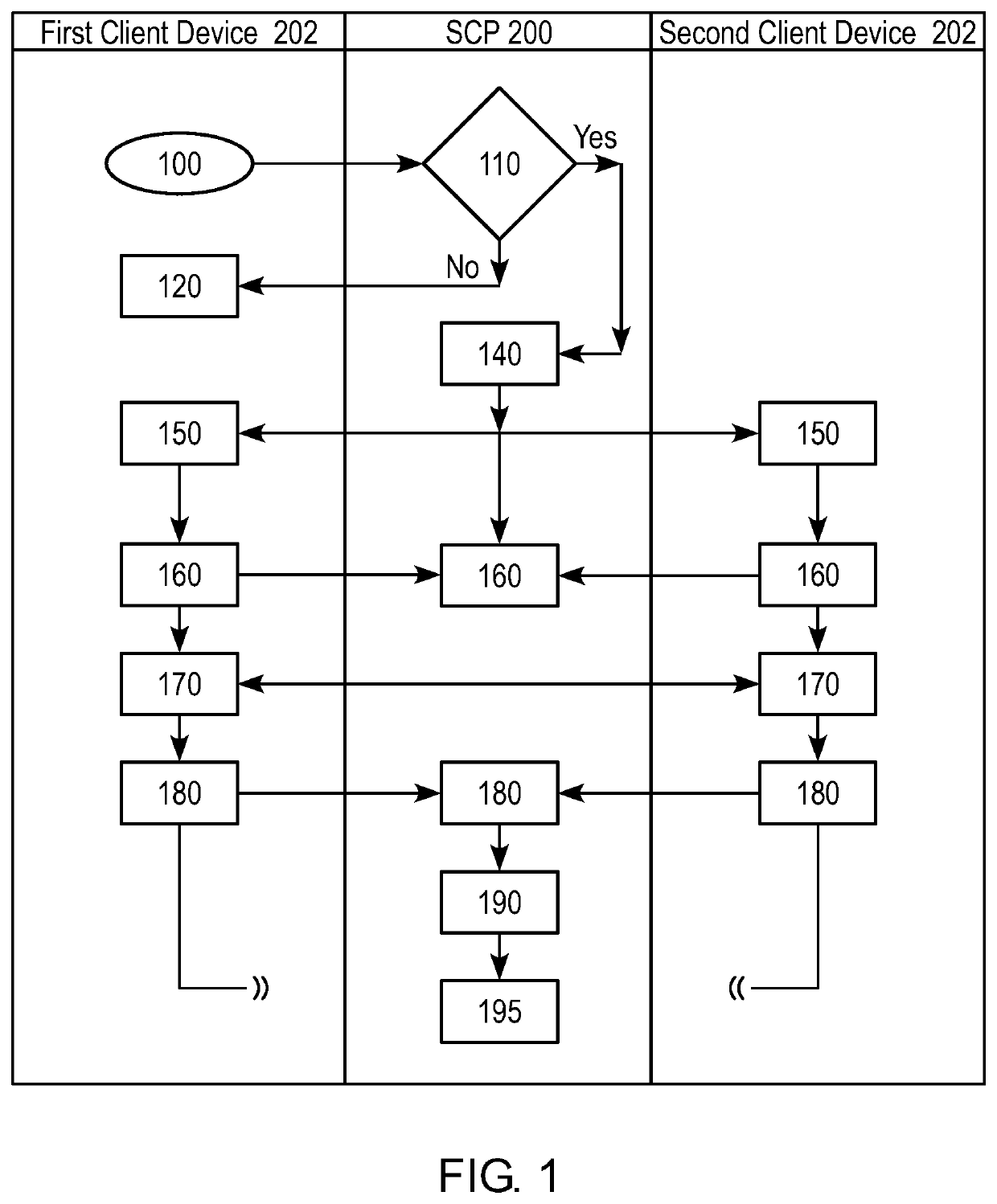
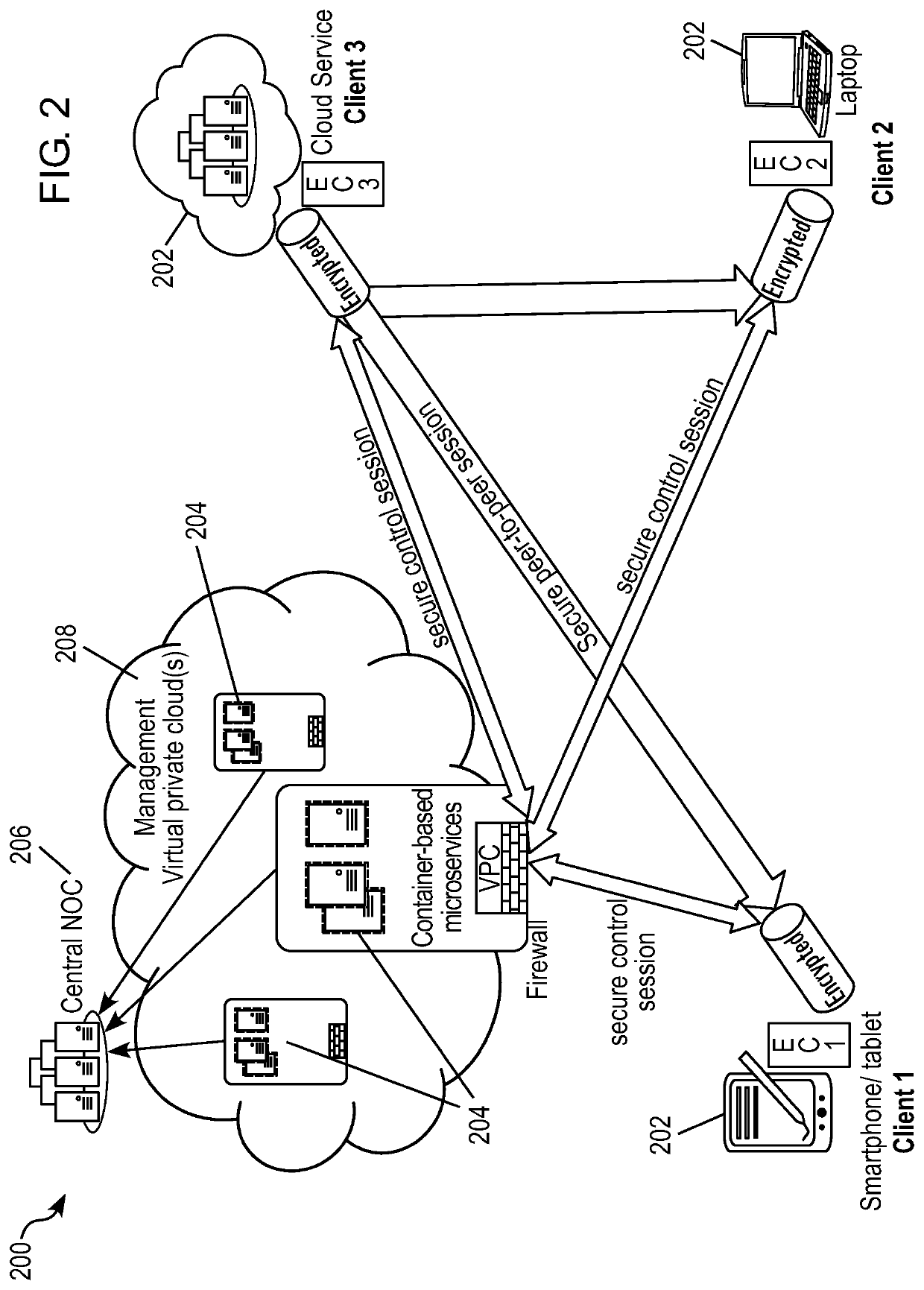
ActiveUS20210266303A1Reduce attack surfaceLess overheadSecuring communicationSecure communicationSingle use
A system / method for secure communication between client devices includes receiving a request, at a secure communication platform, from a from a first client device to communicate with a second client device; determining, by the secure communication platform, whether the first client device is permitted to communicate with the second client device; if communication is permitted: generating, by the secure communication platform, a one-time use ephemeral key; transmitting, by the secure communication platform, the generated one-time use ephemeral key to the first and second client devices; establishing, by the secure communication platform, a secure communication session directly between the first and second client devices, wherein communications between the first and second client devices are encrypted and decrypted using the one-time use ephemeral key; and destroying, by the secure communication platform, the one-time use ephemeral key upon termination of the secure communication session between the first and second client devices.
Owner:SDSE NETWORKS INC
Segmentation method for trust domain of virtual machine monitor
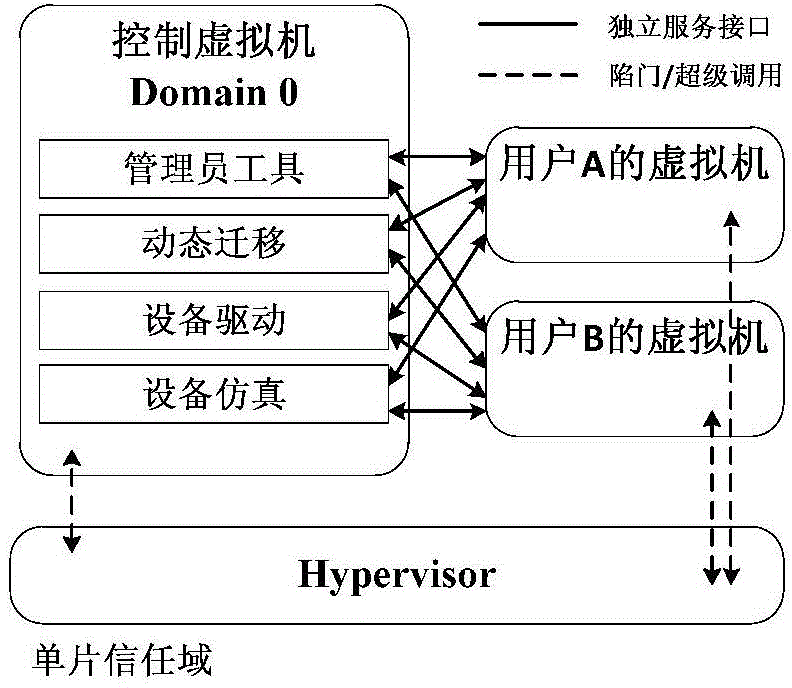
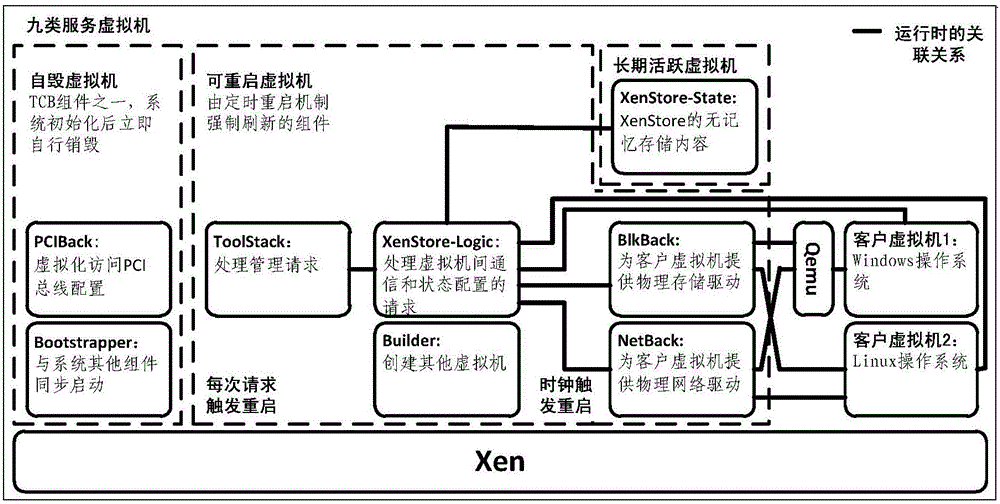
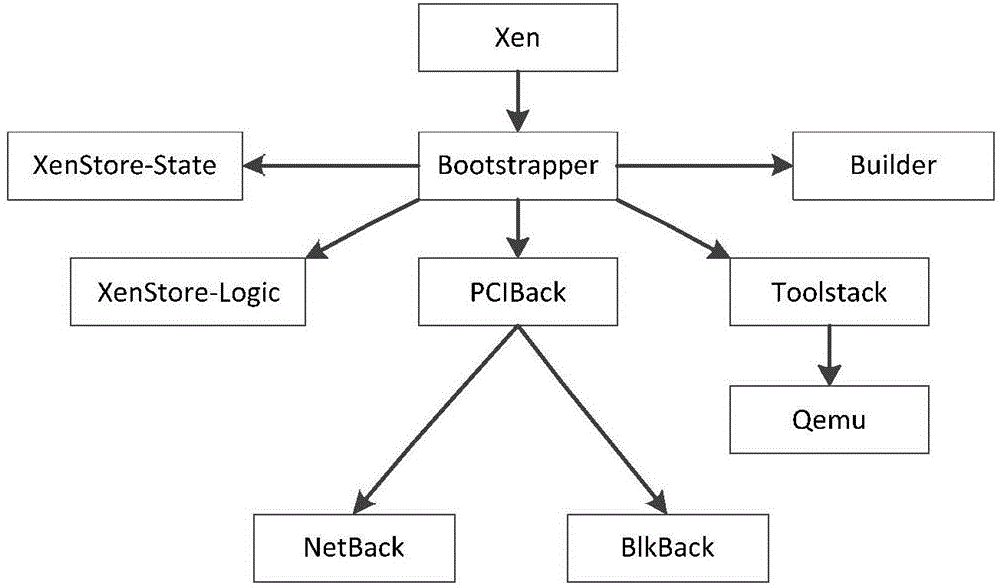
ActiveCN104598842AReduce the Trusted Computing BaseReduce attack surfaceInternal/peripheral component protectionPlatform integrity maintainanceSingle useVirtual machine
The invention discloses a segmentation method for a trust domain of a virtual machine monitor. The original control virtual machine is divided into nine service virtual machines according to different previous functions; each service virtual machine comprises a single-use control logic, and the control logic is deleted from the original control virtual machine. Each service virtual machine only has the authority of finishing the function per se, and each component is limited to access to Hypervisor with the required minimum authority, so the risk is clear. The method has the positive effects that vulnerability location can be effectively performed after attack accidents occur so as to perform remediation, the problem that the control power of the whole system can be obtained by breaking one component originally is solved, and the safety of the virtual machine is improved.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Method and system for realizing secure and high-performance inter-process communication
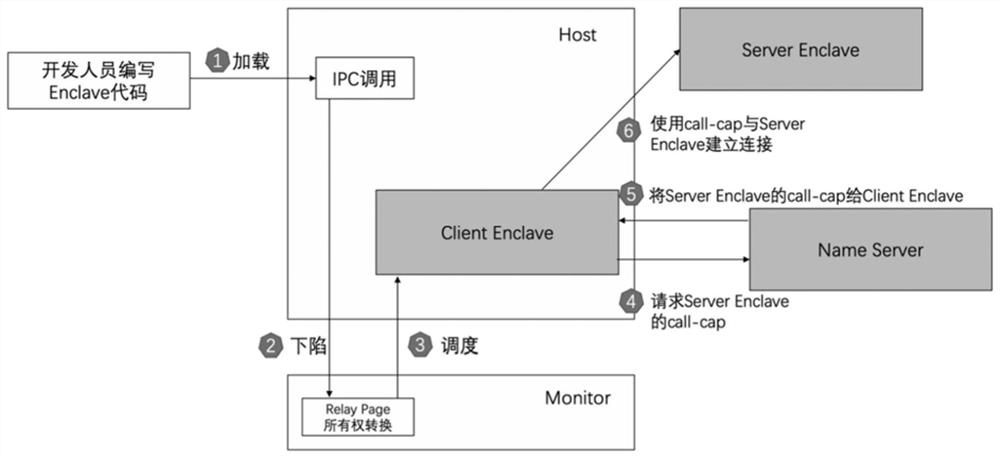
ActiveCN112817780AImprove performanceEnsure safetyProgram initiation/switchingResource allocationComputing systemsName server
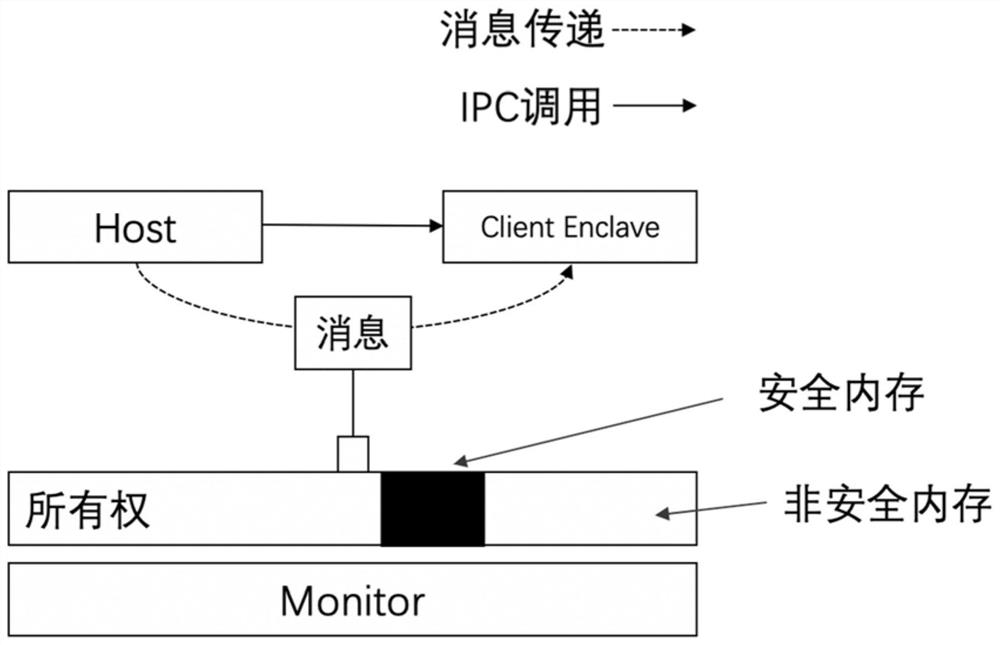
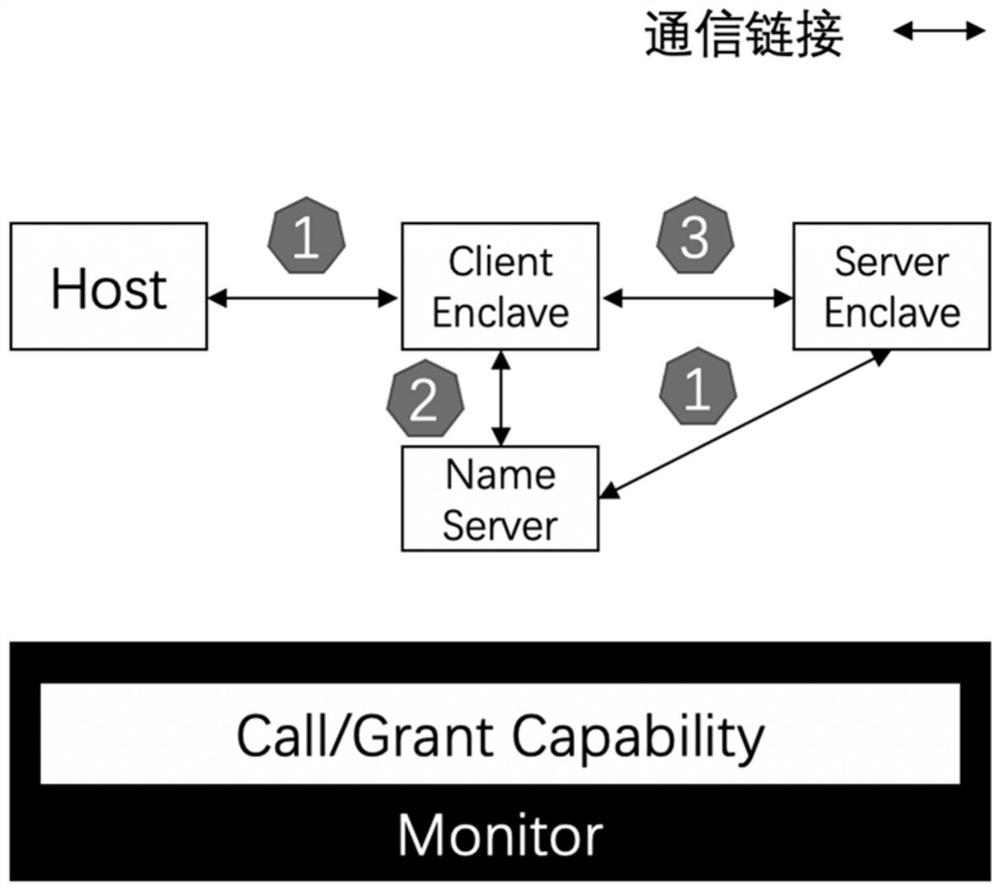
The invention provides a method and a system for realizing secure and high-performance inter-process communication, and the method comprises the following steps: a developer completes Enclave development and loads the Enclave development to a computing system; a host process Host program is loaded by a computing system, and thus starting an enclave process Enclave; a host process Host program starts communication with an enclave process Enclave, and a Monitor is called to request inter-process communication; the Monitor ensures that the relay page only has one memory mapping, and the ownership of the Monitor is transferred from the host process Host to the enclave process Enclave; inter-process communication between an enclave process Enclave program and another enclave process Enclave is started, and the monitor establishes connection between an enclave process Enclave 1 and a Name Server; the enclave process Enclave 1 requests the Capability of the enclave process Enclave 2 from the Name Server; and the Monitor remaps the relay page to realize the message transmission between the enclave process Enclave 1 and the enclave process Enclave 2. According to the invention, a relay page and software and hardware collaboratively provide integrity protection, so that an enclave process is subjected to high-performance inter-process communication (IPC) in a trusted computing scene.
Owner:SHANGHAI JIAO TONG UNIV
Automated code lockdown to reduce attack surface for software
ActiveCN106687971ADoes not affect experienceReduce attack surfacePlatform integrity maintainanceMemory addressFunctional testing
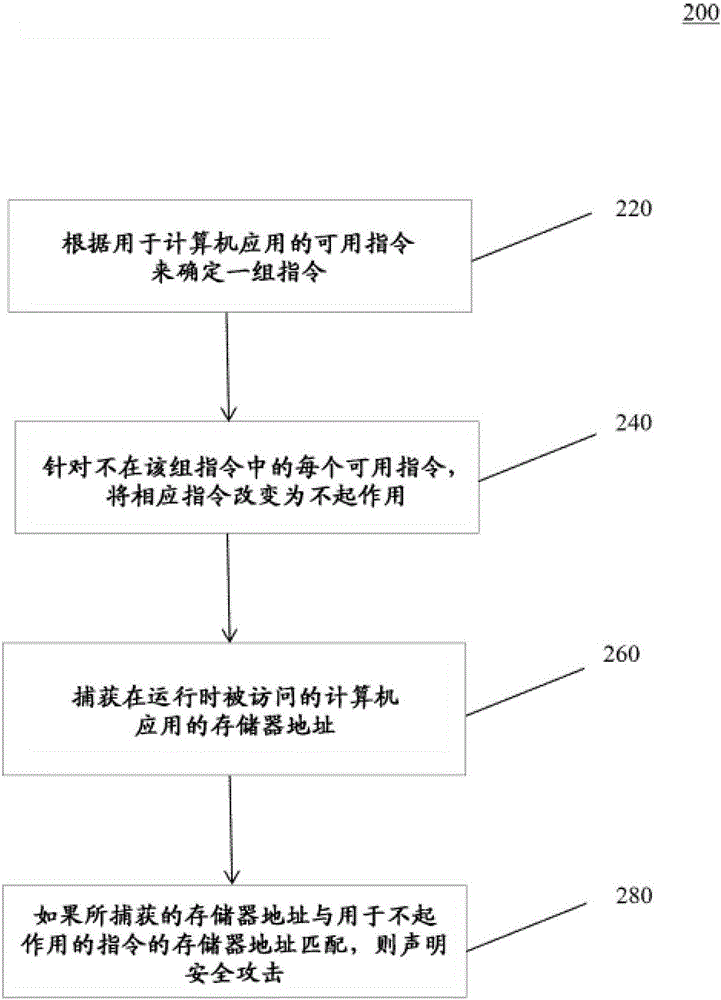
In an example embodiment, a system determines a set of instructions from the available instructions for a computer application. The determined set of instructions provides specific functionality of the computer application. The system may determine the set of instructions by performing functional testing and negative testing on the specific functionality. The system may reorganize and randomize the set of instructions in memory and write the reorganized set of instructions to a smaller memory space. For each available instruction not in the set of instructions, the system changes the respective instruction to inoperative to prevent execution of the respective instruction. The system may change the respective instruction to inoperative by overwriting the instruction with a NOP instruction. The system then captures a memory address of the computer application being accessed at runtime. The system may declare a security attack if the captured memory address matches a memory address for an inoperative instruction.
Owner:VIRSEC SYST
Mimicry bracket implementation device and method in distributed mode
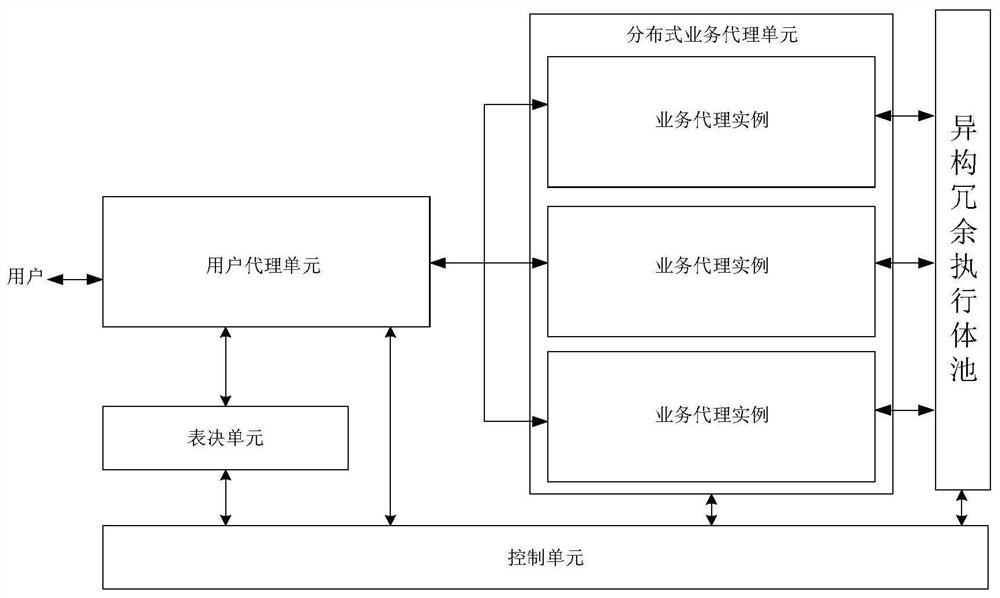
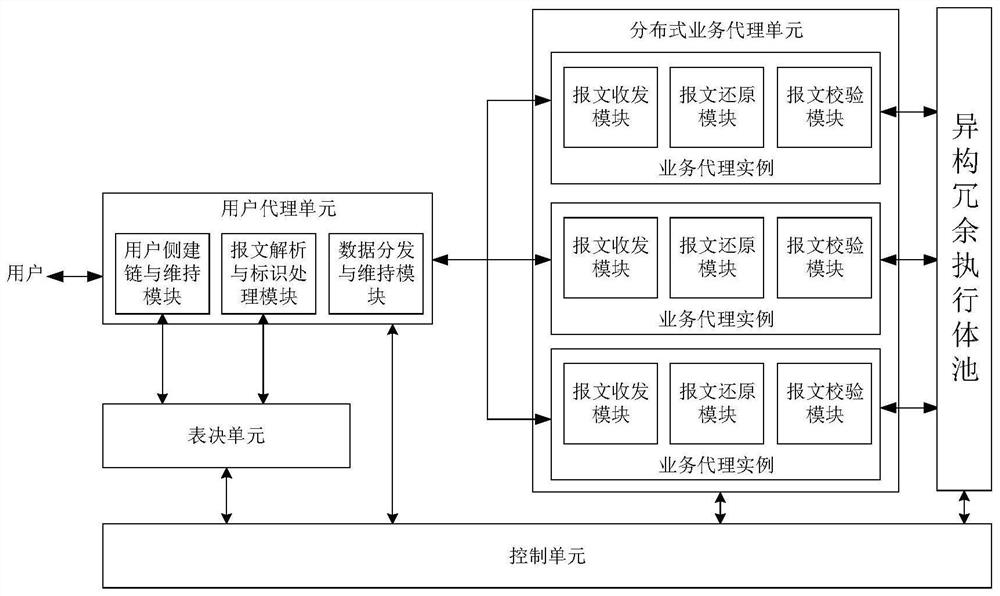
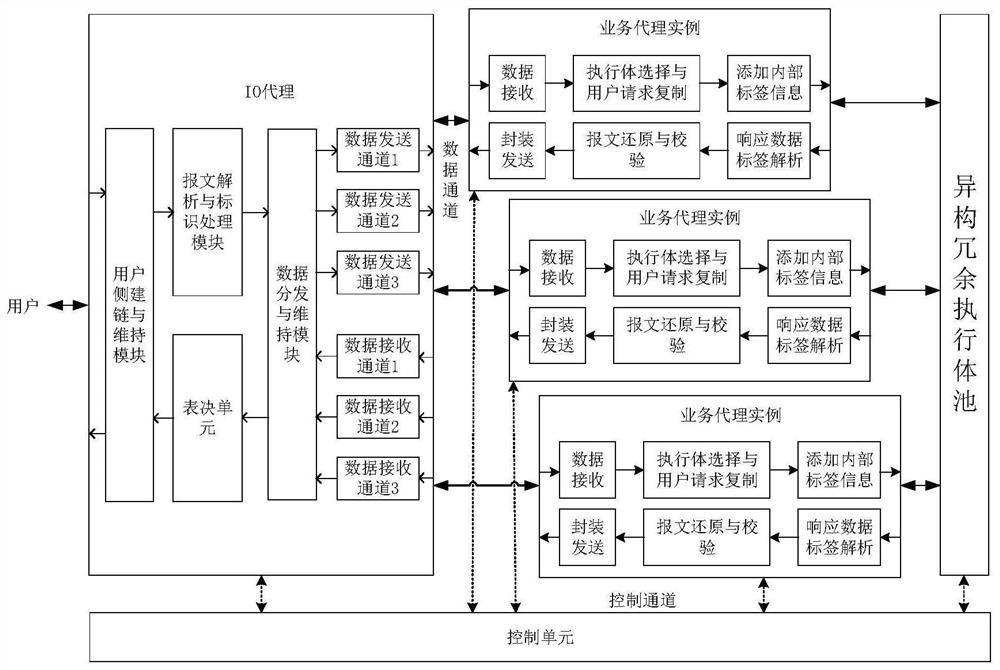
ActiveCN112235269AAvoid the impact of normal operationGuaranteed uptimeTransmissionControl cellEngineering
The invention belongs to the technical field of network security, and discloses a distributed mode mimicry bracket implementation device and method, and the device comprises a user agent unit, a distributed business agent unit, a voting unit, a heterogeneous redundant execution body pool, and a control unit. The user agent unit comprises a user side link establishment and maintenance module, a message analysis and identification processing module and a data distribution and maintenance module; the service agent example comprises a message transceiving module, a message restoring module and a message checking module; the user agent unit and the voting unit are both located on the IO agent; the IO agent further comprises a plurality of data sending channels and data receiving channels. According to the invention, an attacker can be prevented from maliciously attacking the mimicry system for the mimicry bracket, and reliable operation of the mimicry defense system is ensured.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
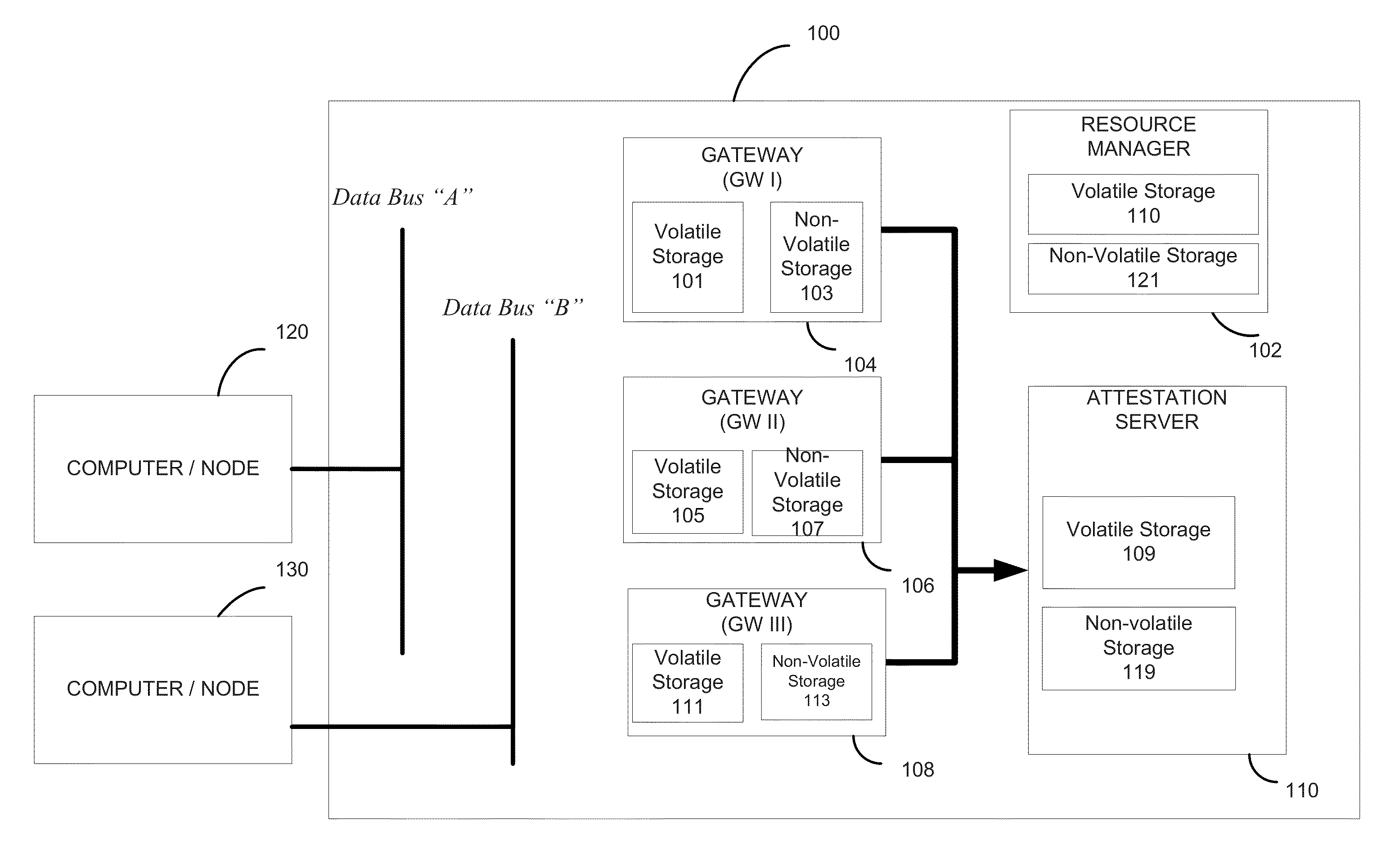
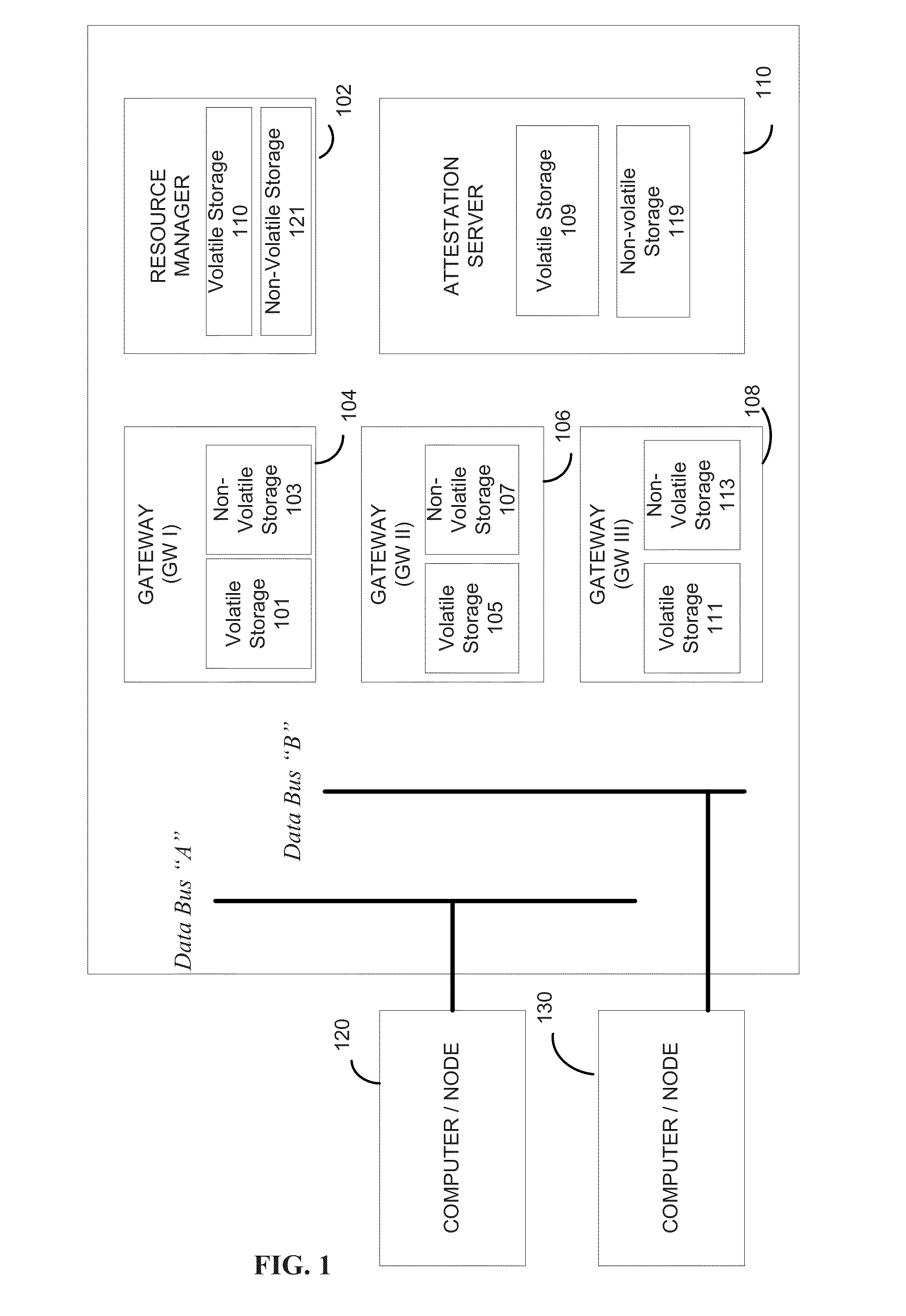
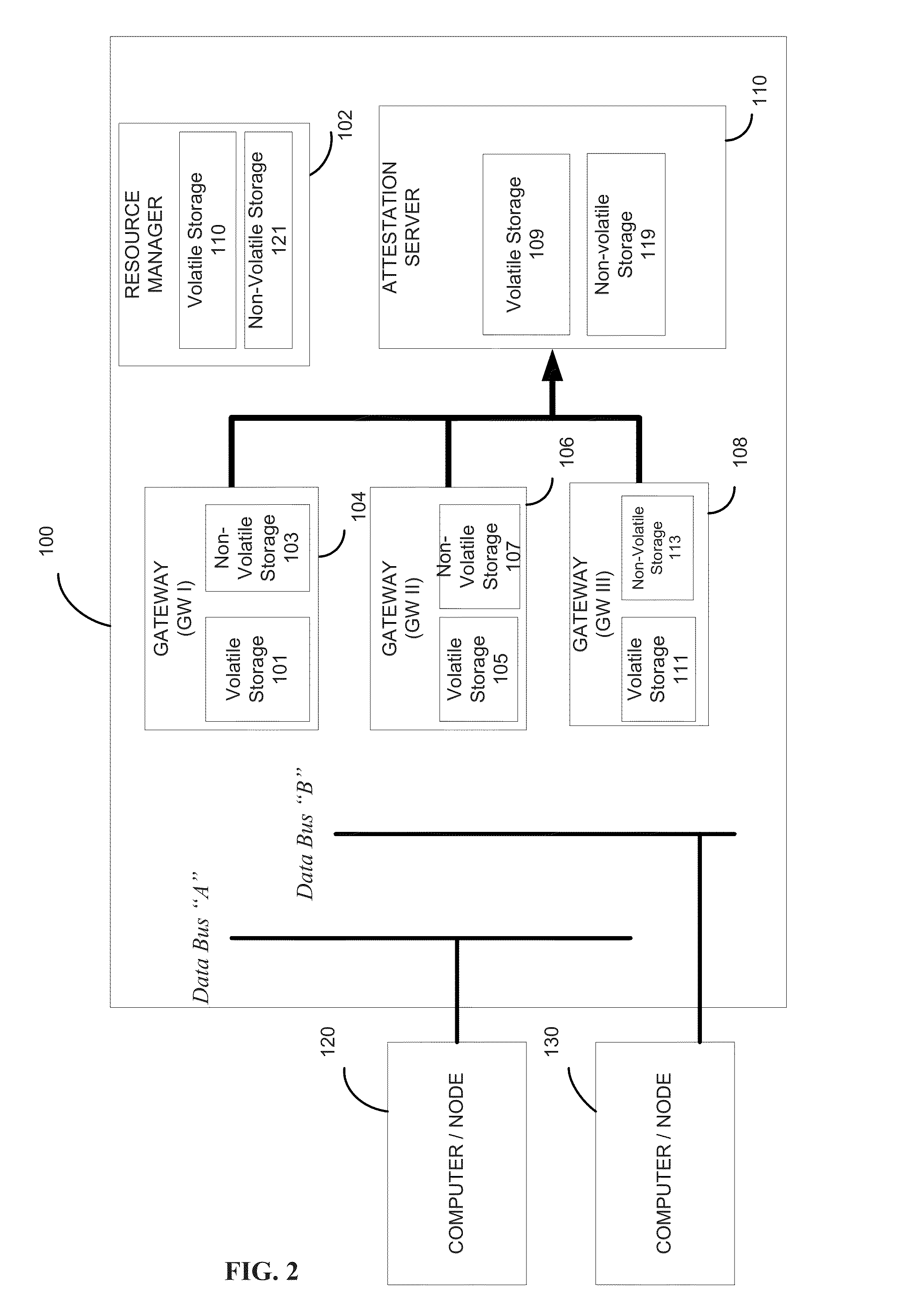
Secure layered iterative gateway
ActiveUS8973138B2Reduce attackReduce attack surfaceMemory loss protectionError detection/correctionOperational systemCyber-attack
In methods and a device for mitigating against cyber-attack on a network, a distributed intermediary device is placed into a network between computers or network nodes of the network to mitigate cyber-attacks between the computers or nodes of a network from remote systems. Threats are assessed by utilizing internal information assurance mechanisms of the device to detect such cyber-attacks without requiring external modification of the software and / or hardware of the computers or nodes of the network to be protected. The device prevents attacks at the platform level against the OS and network resources.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
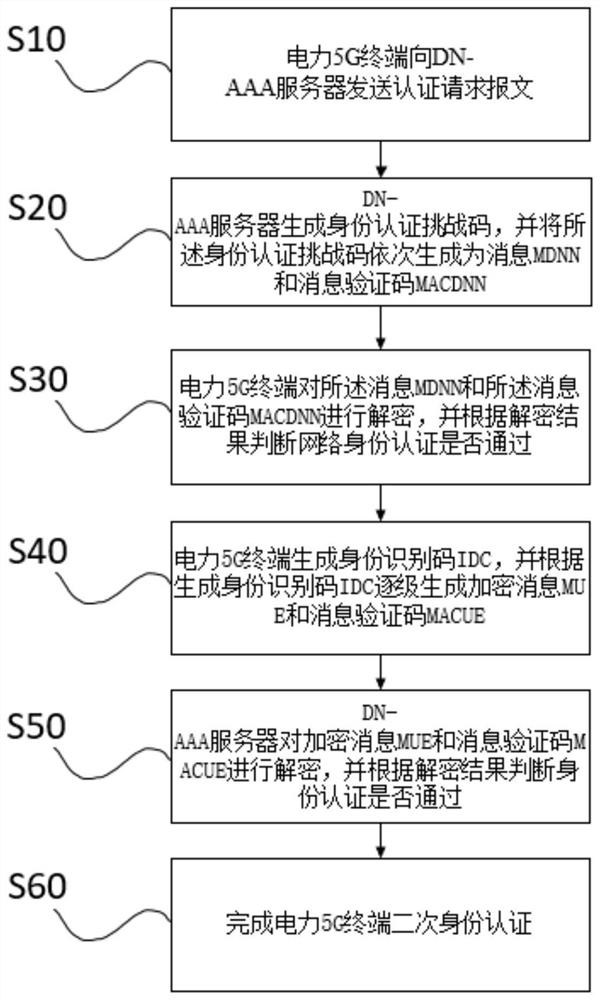
5G application access authentication method and 5G application access authentication network architecture
PendingCN112312393AReduce attack surfaceSolve problems with multiple security flawsUser identity/authority verificationSecurity arrangementCommunications securityElectric power system
The invention provides a 5G application access authentication method and a 5G application access authentication network architecture, and belongs to the field of communication security. The method comprises the steps that after a network access attachment request is completed, the electric power 5G system is accessed to an authentication network architecture through a 5G application for secondaryverification. The security authentication protocol interaction process among the electric power 5G terminal, the SMF / UPF and the DNAA server successively verifies network security and identity authentication of the electric power 5G terminal, realizes network and service dual authentication, can establish PDU (Protocol Data Unit) session connection only when 5G application access authentication islegal, otherwise, provides service for the PDU session connection through network rejection, and improves the security of the electric power 5G terminal. The attack surface of a power service domainis reduced, and the problem that a 5G terminal in a current power system has various security defects in 5G network access is solved.
Owner:STATE GRID ANHUI ELECTRIC POWER +3
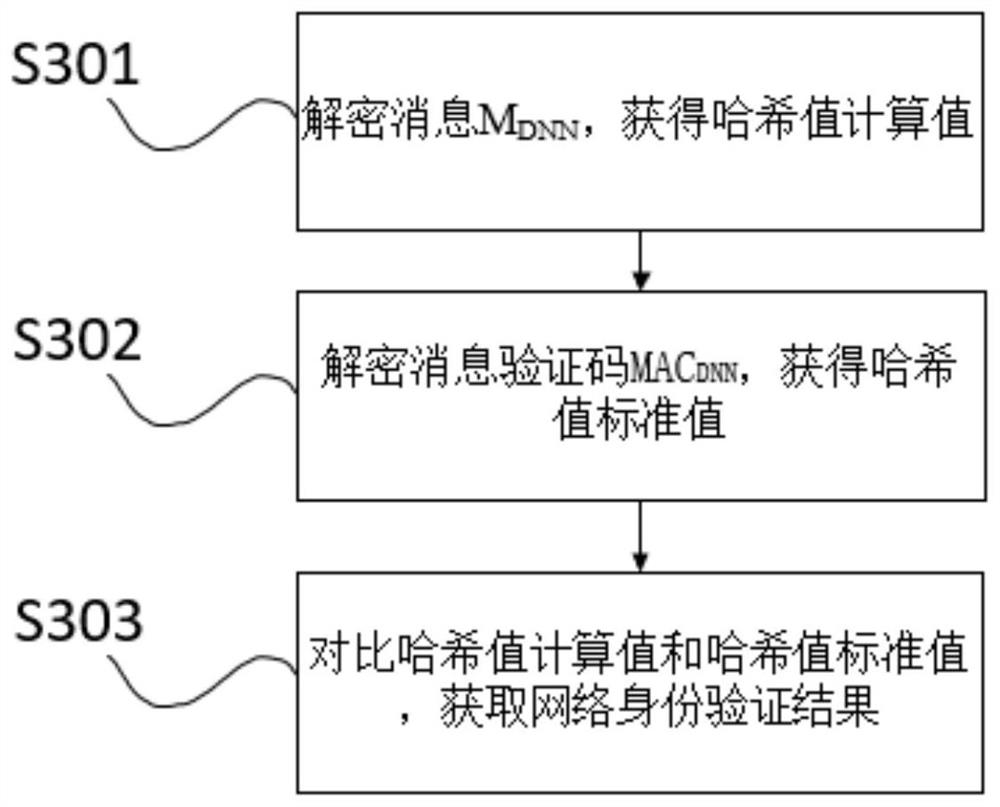
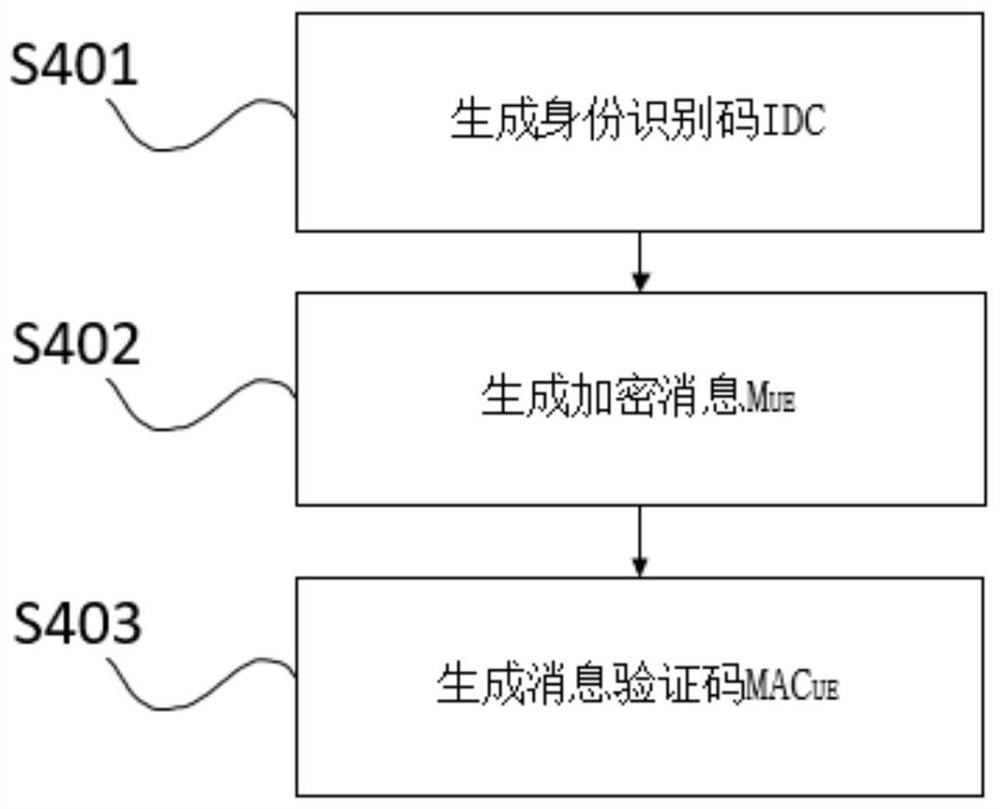
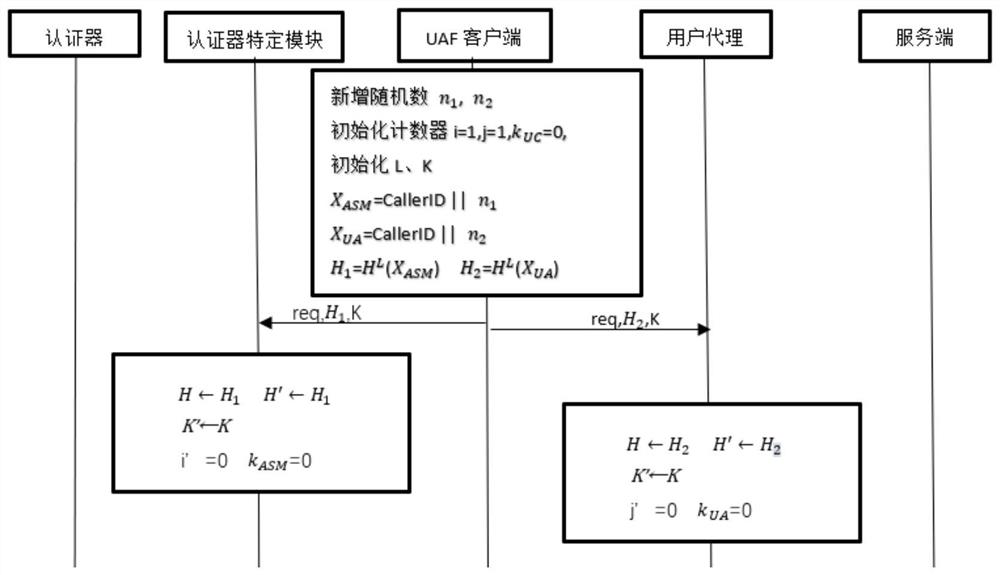
Online rapid identity verification method based on Hash chain
ActiveCN114430324AImprove securityReduce attack surfaceUser identity/authority verificationInformation technology support systemConfidentialityInternet privacy
The invention discloses an online rapid identity authentication method based on a hash chain, and mainly solves the problems that according to an existing online rapid identity authentication protocol FIDO, a malicious UAF client and a malicious authenticator specific module possibly appear in the normal registration or authentication process of a honest entity, so that messages are leaked, the protocol confidentiality is affected, and malicious login is caused. The implementation scheme is as follows: initializing each related entity of the FIDO protocol; calling a local security environment instruction to verify the integrity of the entity; performing hash chain registration; the FIDO protocol is operated, on the premise that normal operation of the protocol is guaranteed, verification of the authenticator specific module and the user agent to the UAF client side and verification of the UAF client side to the authenticator specific module are achieved based on the Hash chain, the security of the protocol is enhanced, and identity registration and authentication of the user in online service are achieved. The method is high in security, high in speed and low in overhead, and can be used for remote login, identity authentication and transaction authentication of online services.
Owner:XIDIAN UNIV
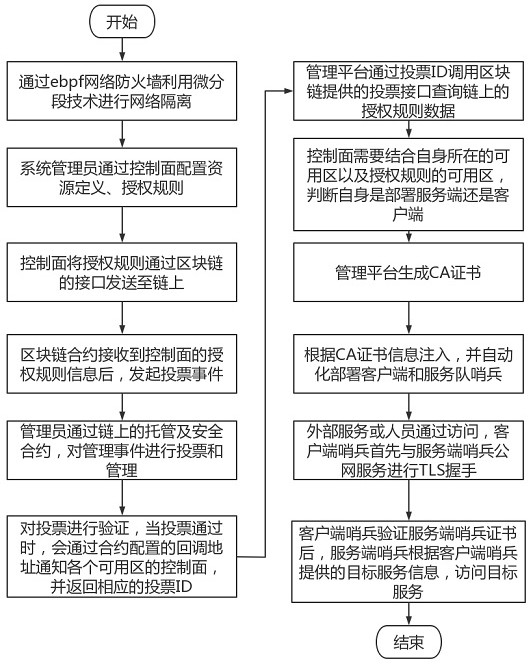
Network security communication system based on block chain smart contract
ActiveCN114430350AImprove securityGuaranteed traceabilityUser identity/authority verificationNeural architecturesSystem administratorAuthorization
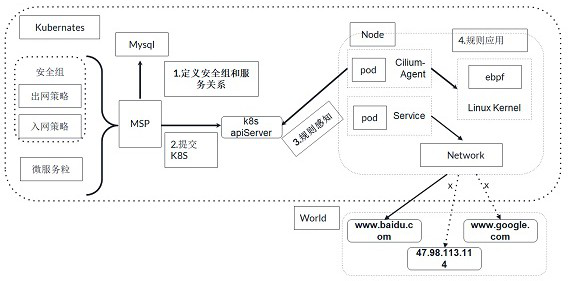
The invention discloses a network security communication system based on a block chain smart contract, and belongs to the technical field of digital information transmission. The system comprises a network isolation module, a user-defined configuration module, an authorized access module, an intelligent contract module, a certificate management module, an automatic deployment module and a sentry verification module. Network isolation is carried out through a network isolation module by adopting an ebpf network firewall and utilizing a micro-segmentation technology; through the custom configuration module, a system administrator configures custom resources and authorization rules on the platform and initiates voting; the administrator votes and manages the management event through the trusteeship and security contract on the block chain by using the authorization access module; querying a contract through an intelligent contract module to obtain a corresponding state change; generating a CA certificate by using a certificate management module; automatically deploying a client and a service team sentinel by using an automatic deployment module according to CA certificate information injection; and the guard verification module is used for accessing a specified interface.
Owner:南京智人云信息技术有限公司
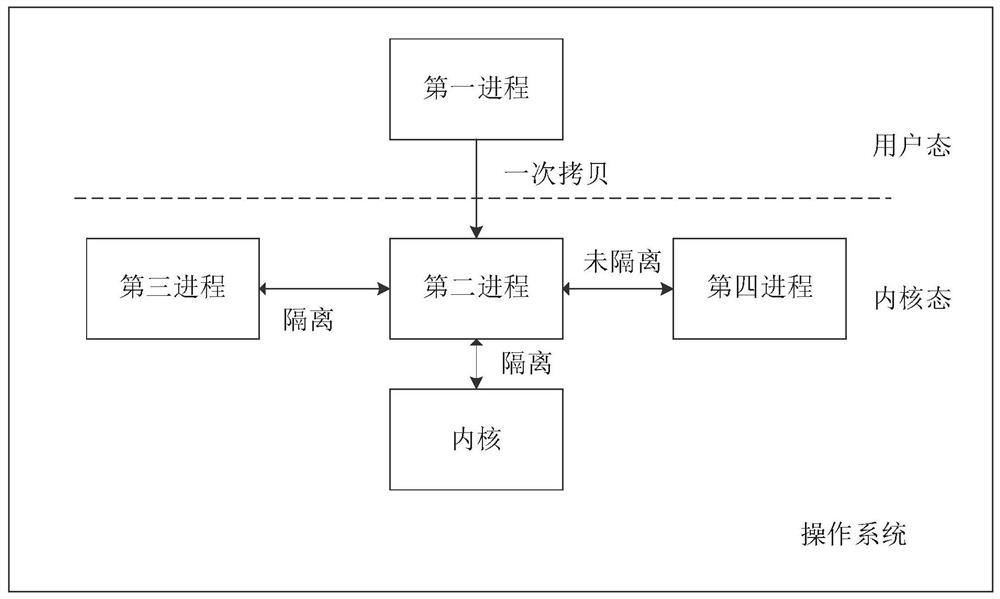
Inter-process communication method and device, and computer storage medium
PendingCN114090273AReduce sizeReduce attack surfaceInterprogram communicationMemory adressing/allocation/relocationOperational systemSoftware engineering
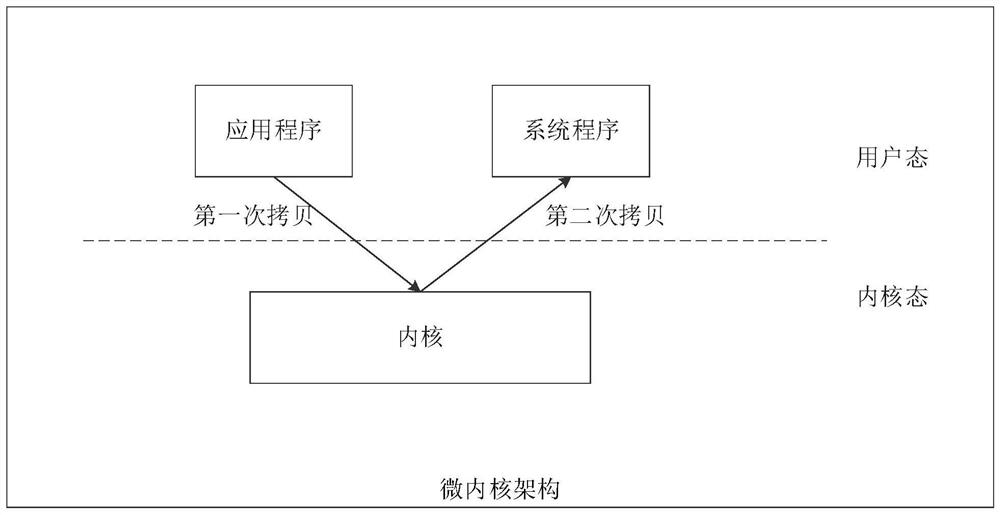
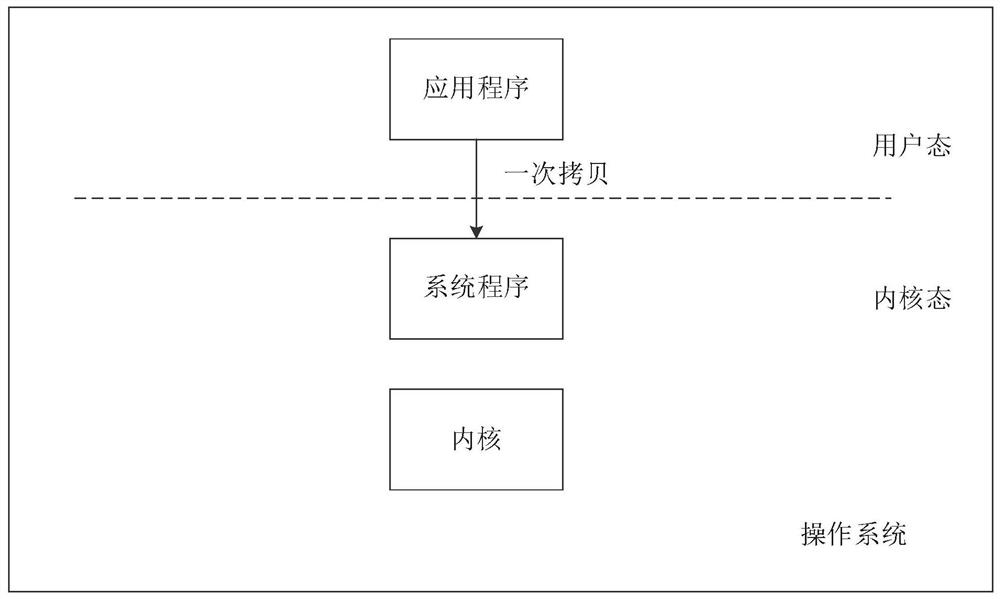
The embodiment of the invention discloses an inter-process communication method and device, and a computer storage medium. The method and the device are used for improving the performance of an operating system. The method comprises the steps that a first instruction is executed, wherein the first instruction is used for indicating a first process to call a second process; in response to the first instruction, the kernel switches the context of the first process to the context of the second process according to the first instruction; and a second process is executed. The first process can be an application program in a user mode and can also be a system program in the user mode, and the second process is a first system program in a kernel mode.
Owner:HUAWEI TECH CO LTD
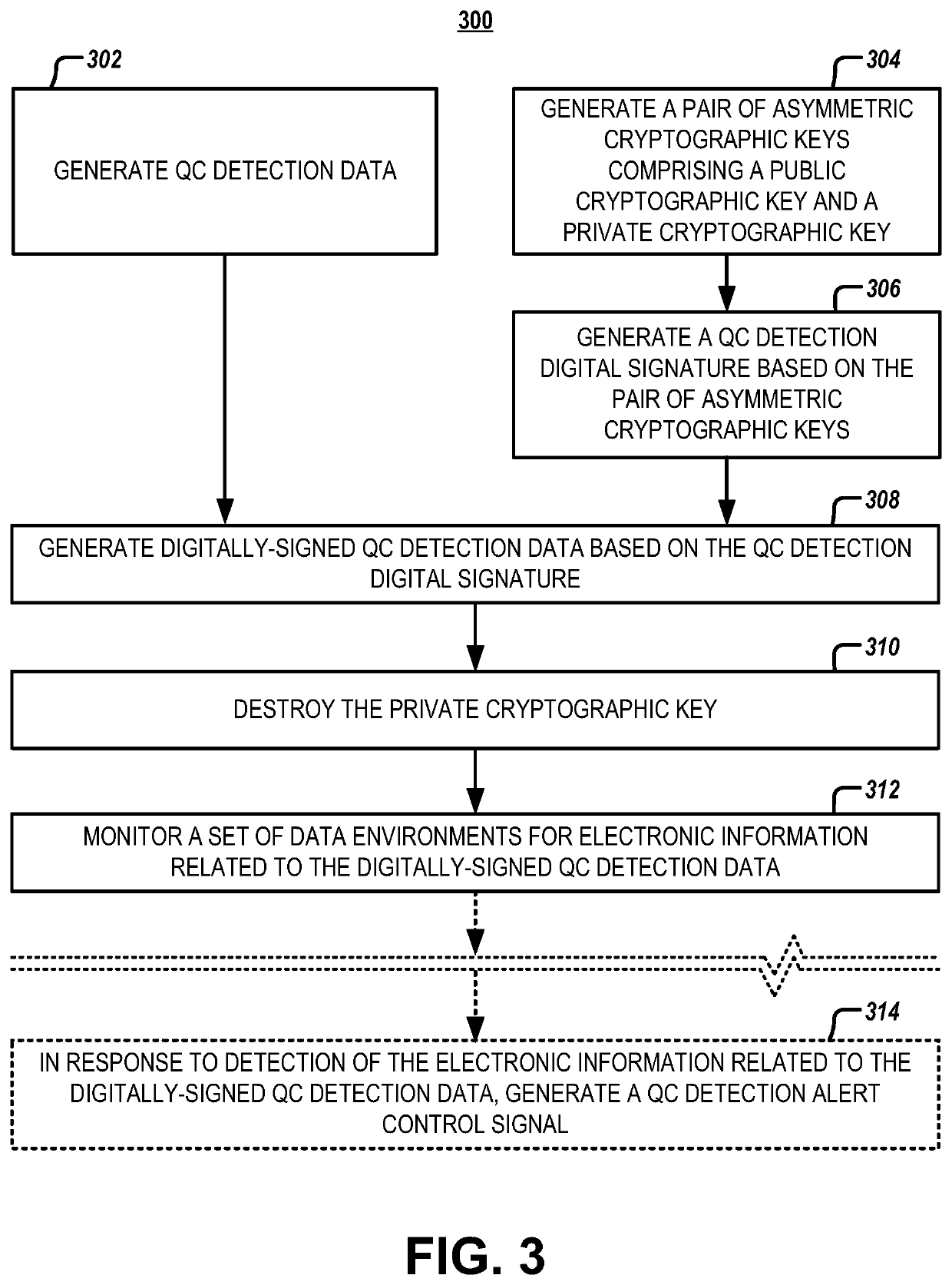
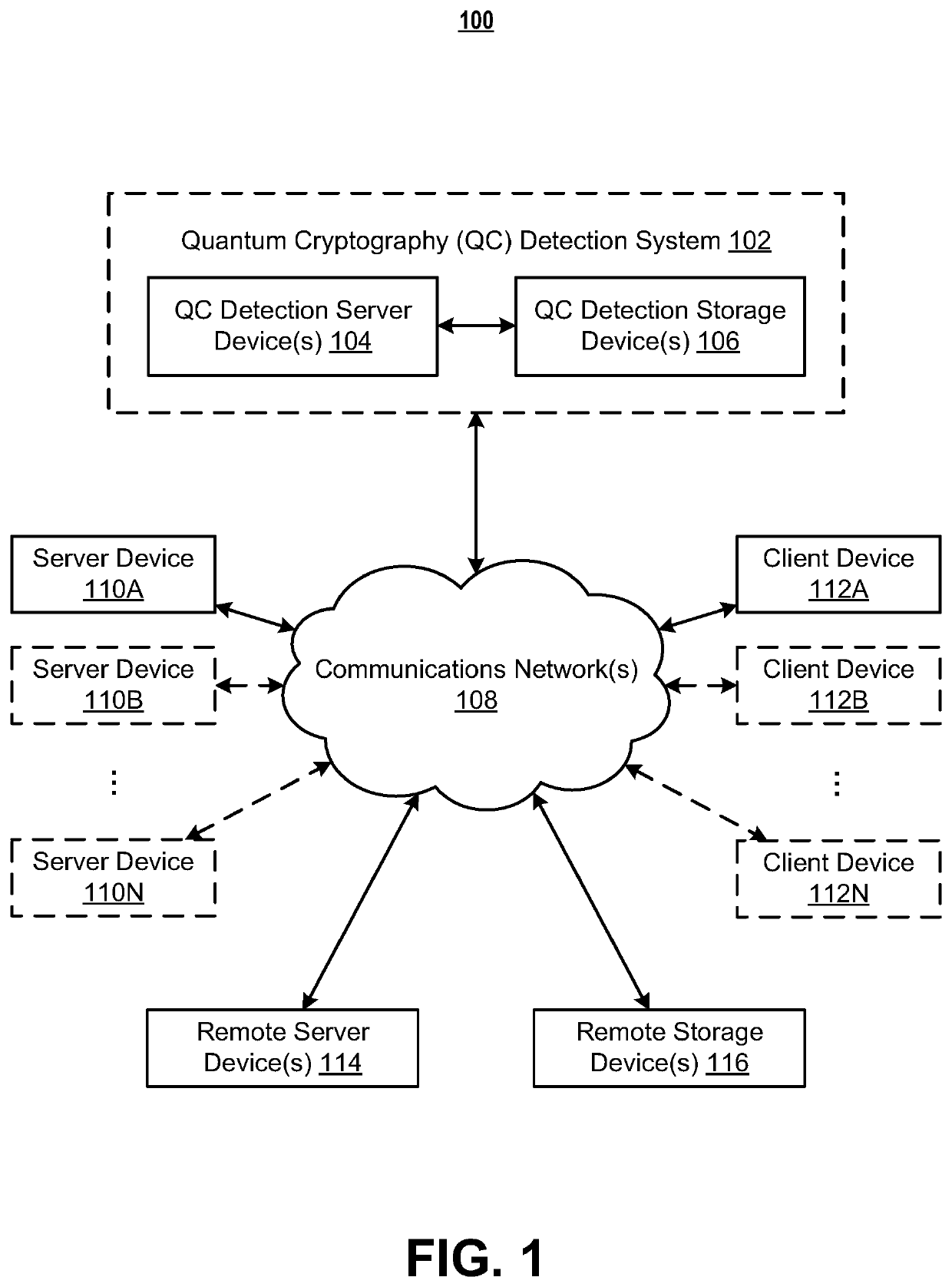
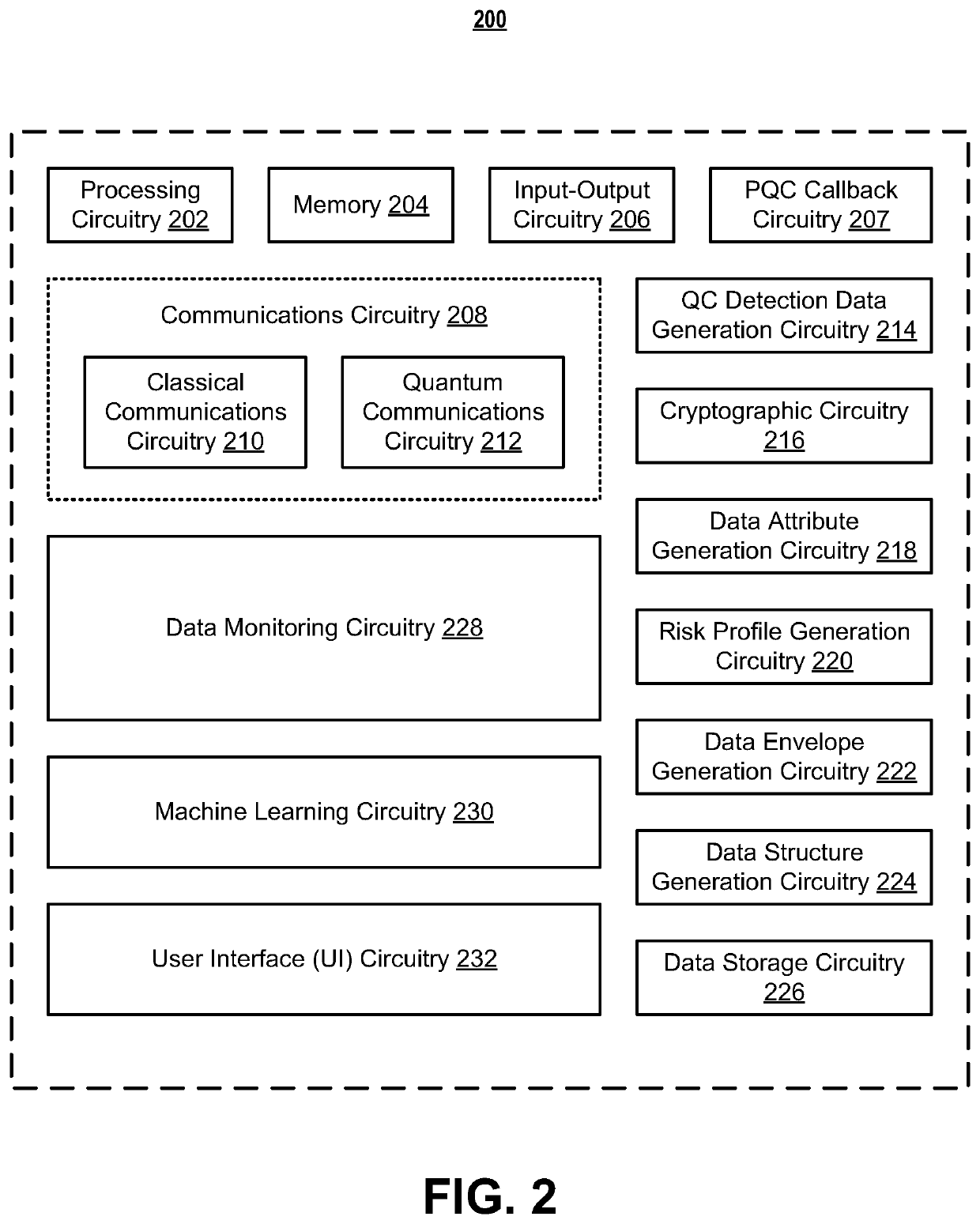
Systems and methods for post-quantum cryptography optimization
ActiveUS11336462B1Reduce attack surfaceAvoid problemsKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey (cryptography)Control signal
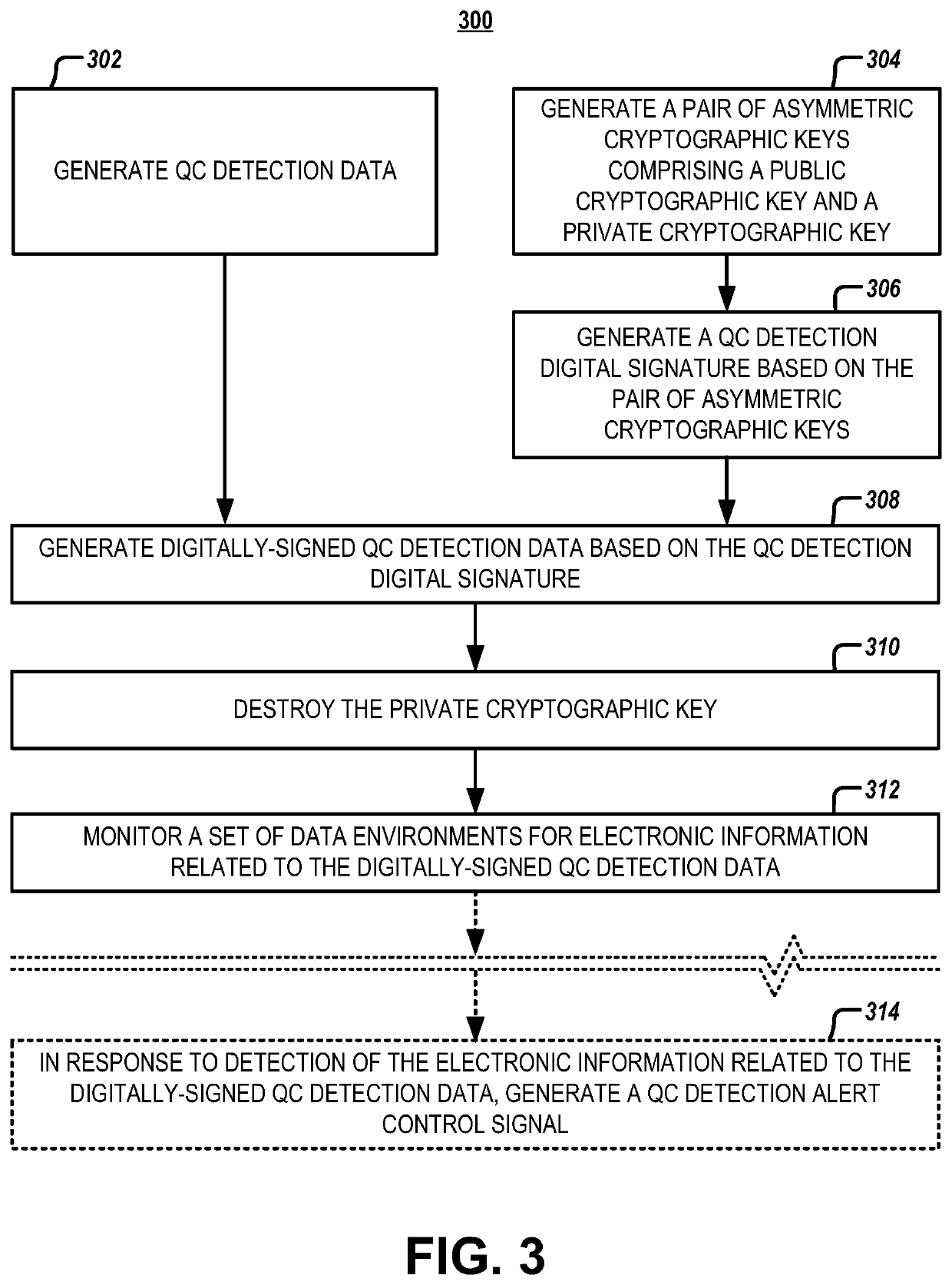
Systems, apparatuses, methods, and computer program products are disclosed for quantum computing (QC) detection. An example method includes generating QC detection data. The example method further includes generating a pair of asymmetric cryptographic keys comprising a public cryptographic key and a private cryptographic key, generating encrypted QC detection data based on the pair of asymmetric cryptographic keys, and destroying the private cryptographic key. The example method further includes monitoring a set of data environments for electronic information related to the encrypted QC detection data. Subsequently, the example method may include generating a QC detection alert control signal in response to detection of the electronic information related to the encrypted QC detection data.
Owner:WELLS FARGO BANK NA
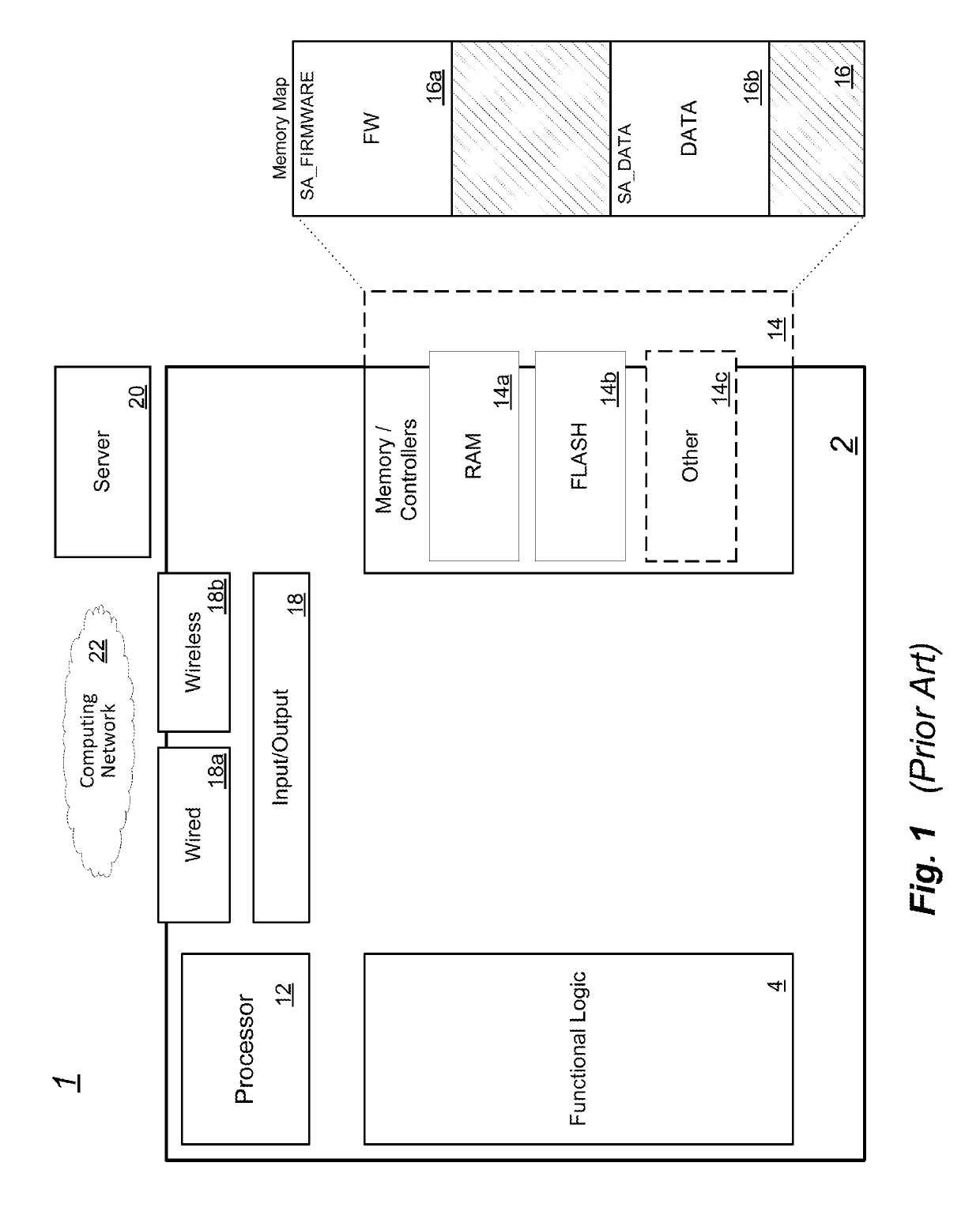
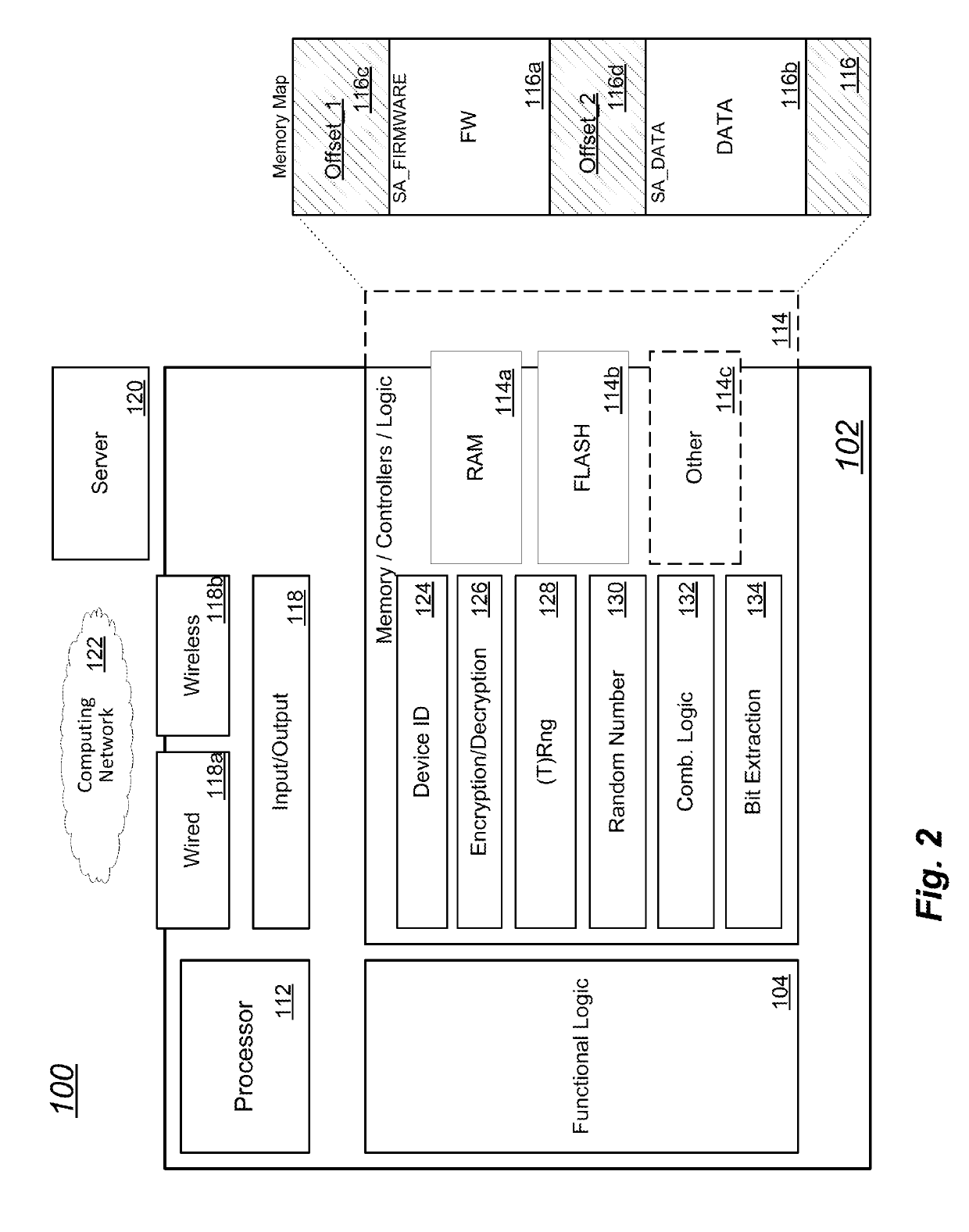
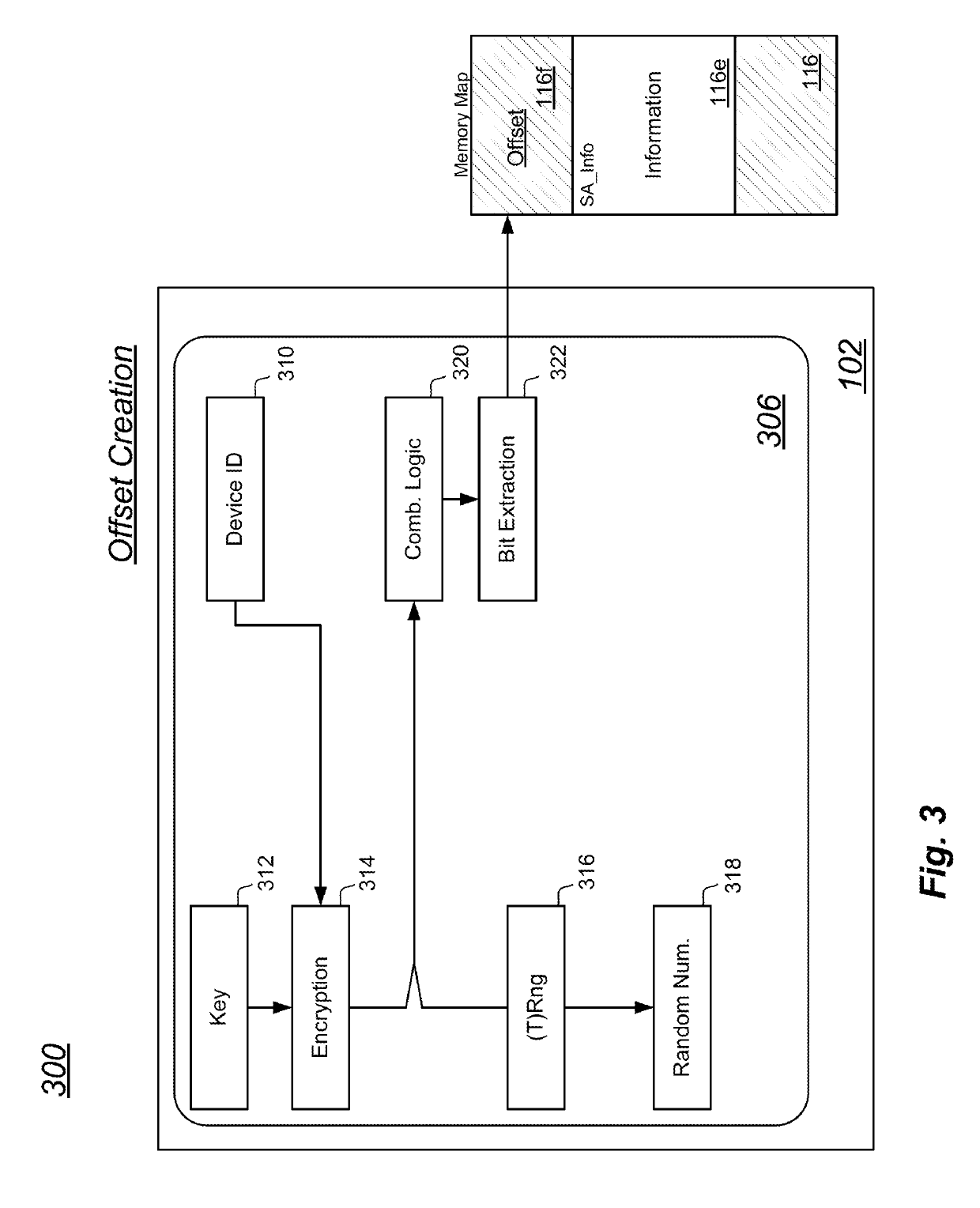
Secure firmware provisioning and device binding mechanism
ActiveUS20190171819A1Function increaseReduce attack surfaceUnauthorized memory use protectionPlatform integrity maintainanceUnique device identifierDevice Identifiers
Electronic computing devices provide a method to update firmware. The method includes receiving a firmware image at an electronic device, the electronic device having a processor and a memory arranged to store instructions executed by the processor. In the electronic device, a unique device identifier is retrieved and a random number is generated. The generated random number is securely stored. The random number and a representation of the unique device identifier are computationally combined to create a device-binding value, and an address-offset is generated from the device-binding value. The firmware image is stored in the memory at the address-offset.
Owner:STMICROELECTRONICS SRL
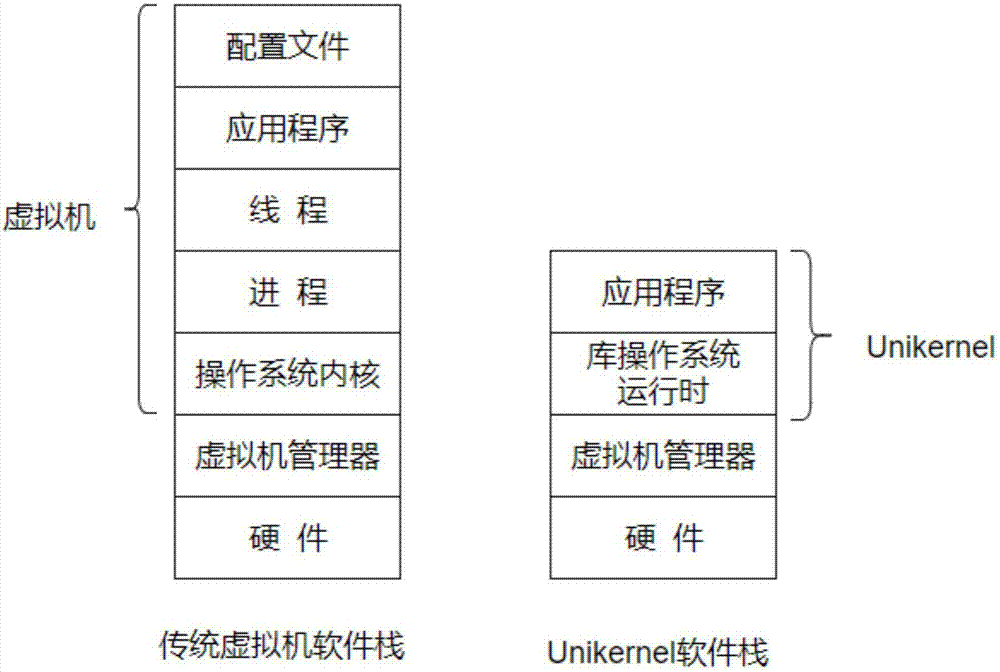
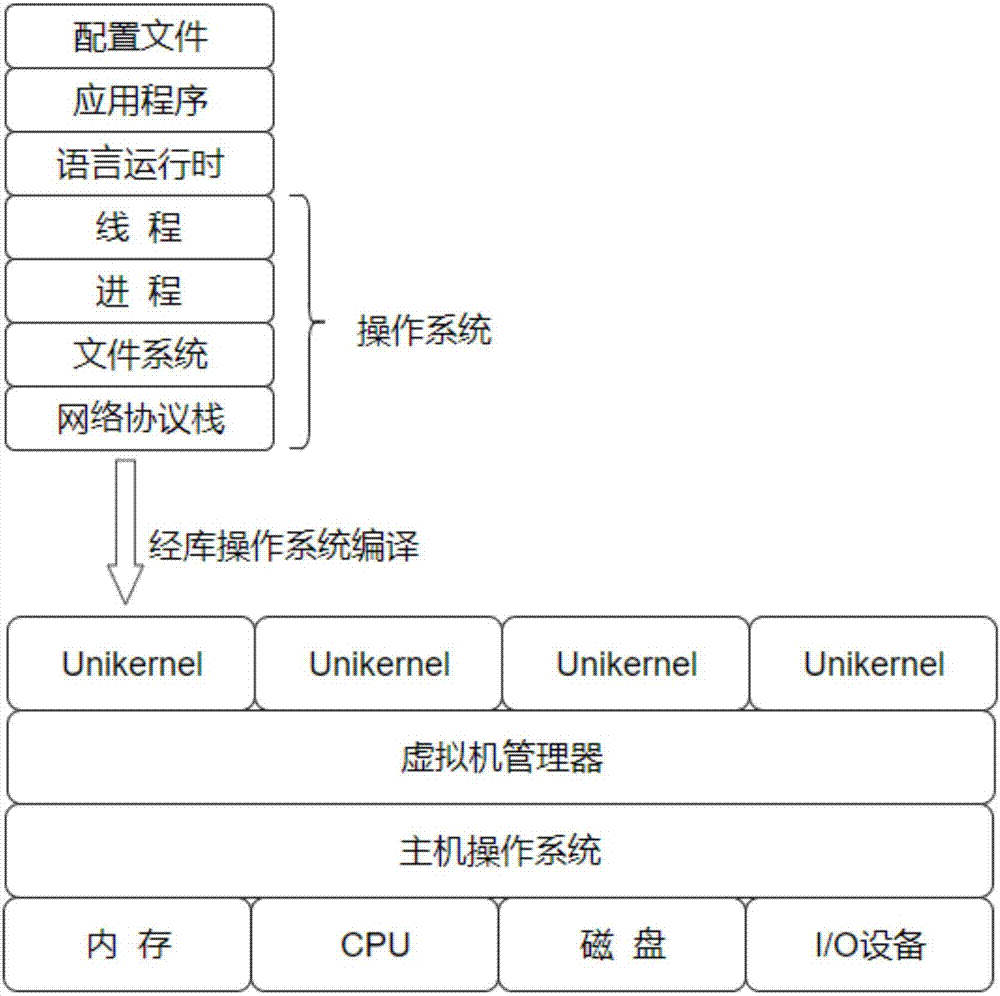
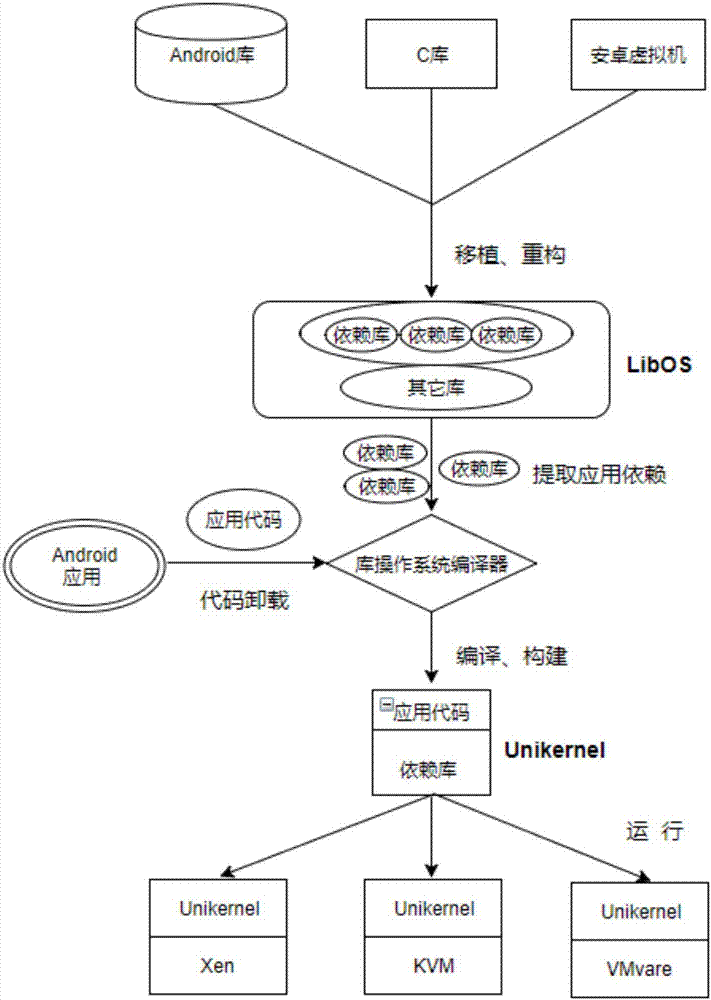
Unikernel-based cloud Android operating environment construction method
InactiveCN107957902AReduce attack surfaceImprove securitySoftware simulation/interpretation/emulationVirtual machineOperating environment
The invention discloses a Unikernel-based cloud Android operating environment construction method, and belongs to the technical field of cloud computing virtualization. The method comprises the stepsthat firstly, an Android subsystem assembly which must be supported for achieving the minimum Android operating environment cloud under the Android code unloading scene is analyzed and obtained at first; then, an Android essential subsystem and a Bionic and Dalvik virtual machine are transplanted into a library operating system; then, an Android application code is compiled, and a related dependence package is extracted from the library operating system for generating a Unikernel virtual machine mirror image; finally, the Unikerel is started on a KVM, an XEN and other Hypervisor, and the Android code is operated. The essential Android environment support is added to the library operating system, the Android application code is compiled to the Unikernel, the characteristics that the Unikernel mirror image is large in size, low in cost, rapid in starting, high in isolation performance and the like are utilized, the cloud resource cost can be effectively lowered, the number of virtual machine instances provided by the cloud is increased, meanwhile, the delay of cloud and terminal communication is greatly lowered, and the user experience of terminal applications is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
Systems and methods for disparate quantum computing threat detection
ActiveUS11334667B1Reduce attack surfaceAvoid problemsQuantum computersKey distribution for secure communicationQuantum computerComputer security
Systems, methods, and computer program products are provided for disparate quantum computing (QC) detection. An example system includes QC detection data generation circuitry that generates a first set of QC detection data and generates a second set of QC detection data. The system also includes cryptographic circuitry that generates a first public cryptographic key and a first private cryptographic key via a first post-quantum cryptographic (PQC) technique and generates a second public cryptographic key and a second private cryptographic key via a second PQC technique. The cryptographic circuitry further generates encrypted first QC detection, second QC detection data, and destroys the first private cryptographic key and the second private cryptographic key. The system further includes data monitoring circuitry that monitors for the first encrypted QC detection data and the second encrypted QC detection data.
Owner:WELLS FARGO BANK NA
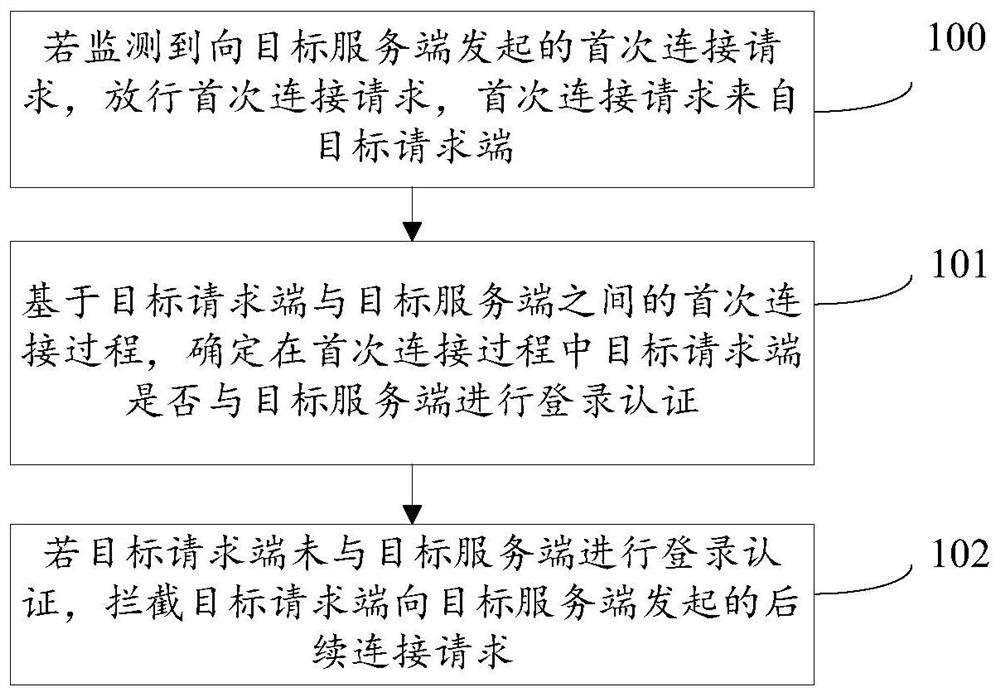
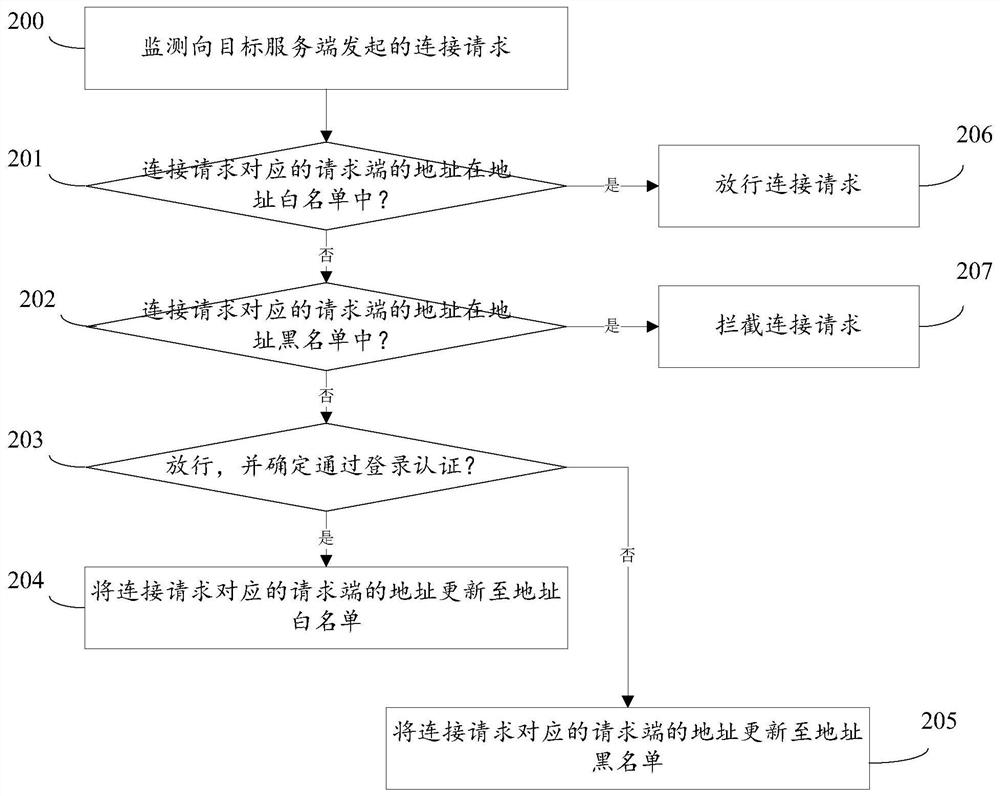
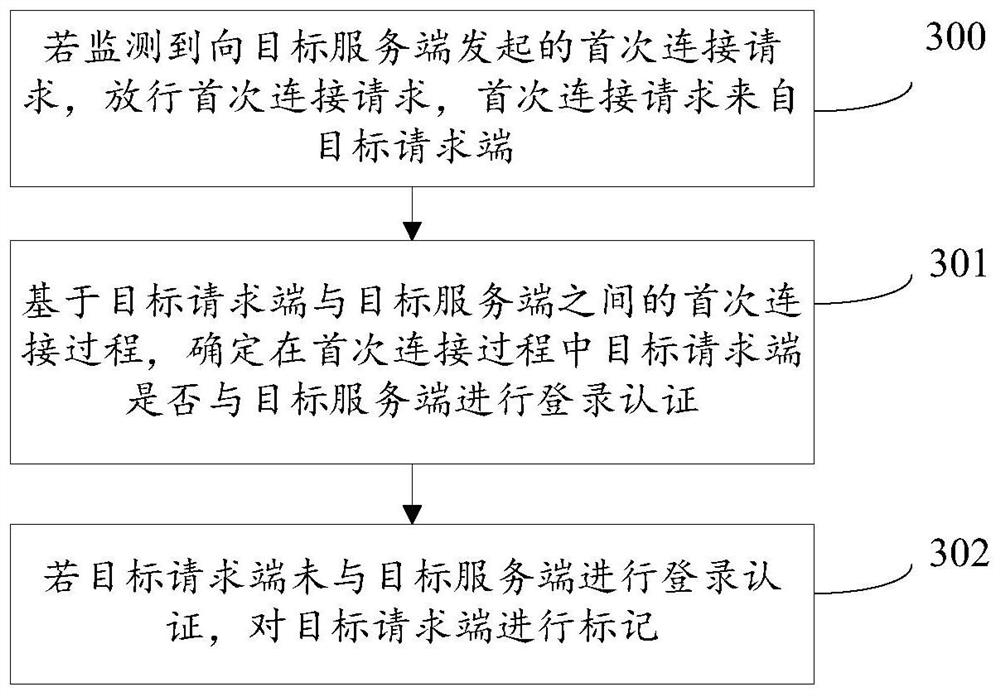
Safety protection method and device and storage medium
The embodiment of the invention provides a safety protection method and device and a storage medium. The method comprises the steps that if a first connection request initiated to a target server sideis monitored, the first connection request is released, and the first connection request is from a target request side; determining whether the target request end performs login authentication with the target server end or not in the first connection process; and if the target request end does not perform login authentication with the target server end, intercepting a subsequent connection request initiated by the target request end to the target server end. Therefore, the first connection request initiated to the target server is regarded as the suspicious traffic, the first release strategyis adopted for the suspicious traffic, and whether the suspicious traffic can be trusted is judged based on whether the suspicious traffic and the target server are subjected to login authenticationor not, so that subsequent access control can be performed on the suspicious traffic according to the judgment result; therefore, the missed blocking rate and the wrong blocking rate are reduced, theattack surface is reduced, and the security of the communication process is improved.
Owner:ALIBABA GRP HLDG LTD
Locking applications and devices using secure out-of-band channels
InactiveUS9887995B2Improve securityCut surfaceDigital data authenticationTransmissionUser authenticationAuthentication server
Systems and methods are provided for locking / unlocking a user account for accessing a client application. The systems and methods pair a user account for accessing a client application to a separate user authentication account. The user authentication server managing the user authentication account provides heightened measures for authenticating the identity of the user, such as by voice samples and human authenticator. After the heightened authentication of the user, the user may lock or unlock paired accounts from the user authentication account, wherein preventing all attempts to access the client application using the paired account. The client application may also capture information regarding login attempts to the paired user account. The captured information may be sent to the authentication server for providing reports of login attempts and generating alerts to automatically lock the paired account in cases of suspicious behavior.
Owner:RIVETZ CORP
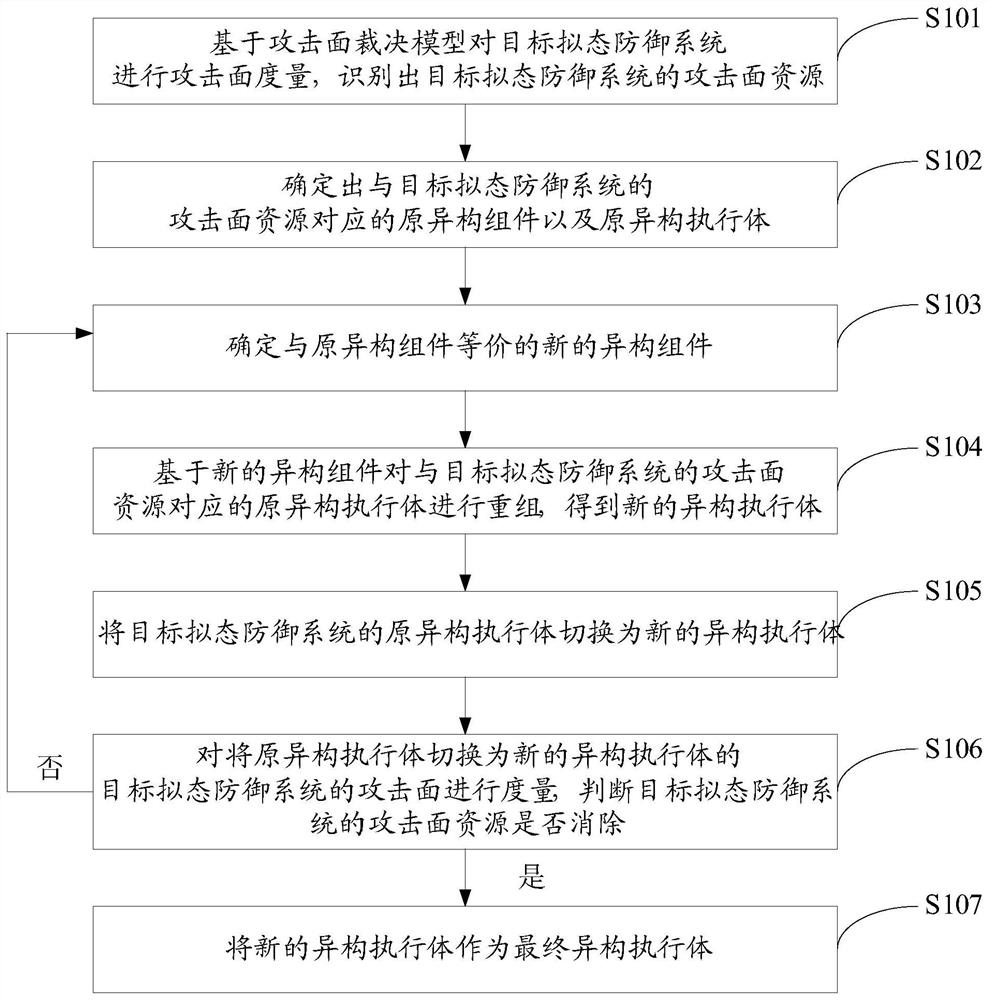
Method for constructing heterogeneous executive body and system thereof
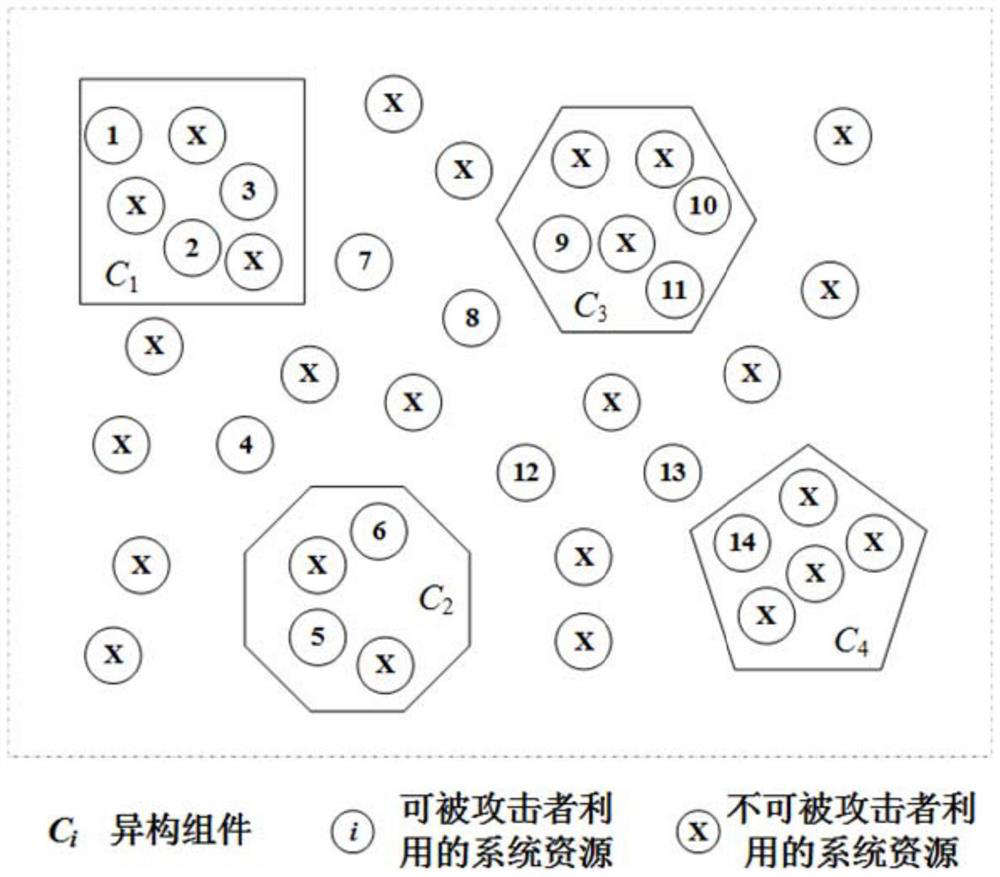
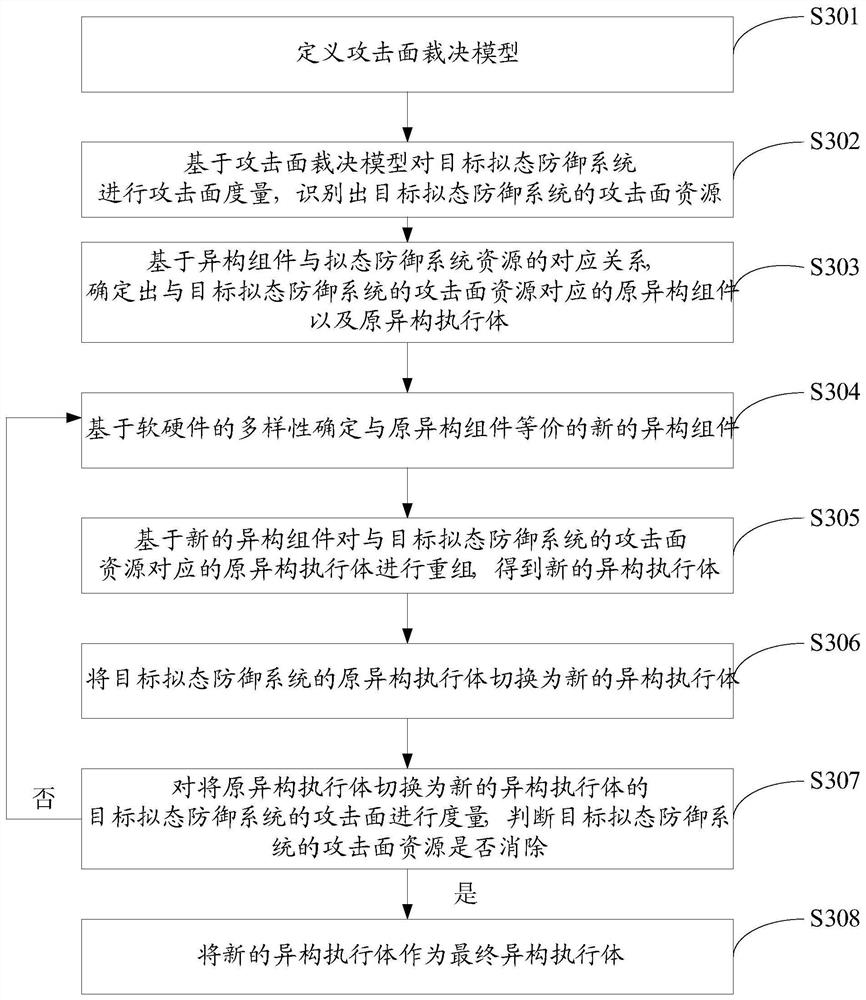
InactiveCN111641661AReduce attack surfaceImprove securityData switching networksReal-time computingDistributed computing
The invention discloses a heterogeneous executor construction method and a system, and the method comprises the steps: carrying out the attack surface measurement of a target mimicry defense system based on an attack surface judgment model, and recognizing an attack surface resource; determining an original heterogeneous component and an original heterogeneous execution body corresponding to the attack surface resource; determining a new heterogeneous component equivalent to the original heterogeneous component; recombining the original heterogeneous executive body based on the new heterogeneous component to obtain a new heterogeneous executive body; after the original heterogeneous execution body is switched into the new heterogeneous execution body, measuring the attack surface, judgingwhether attack surface resources are eliminated or not, if yes, serving the new heterogeneous execution body as a final heterogeneous execution body, and if not, returning to re-determine the new heterogeneous assembly until the determined new heterogeneous assembly can eliminate the attack surface resources. Based on the relationship between the heterogeneous component and the system resource, the attack surface model is used to guide the combination design of the heterogeneous executive body, and the attack surface of the mimicry defense system is effectively reduced.
Owner:SHENZHEN POWER SUPPLY BUREAU
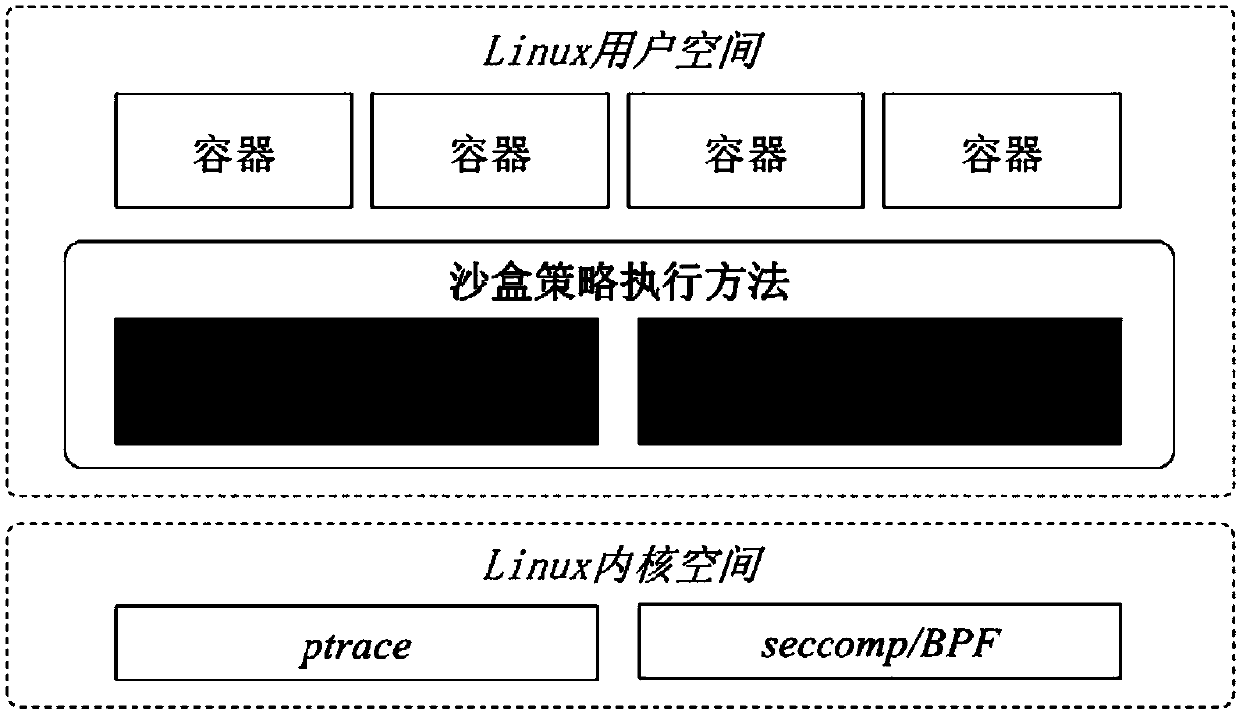
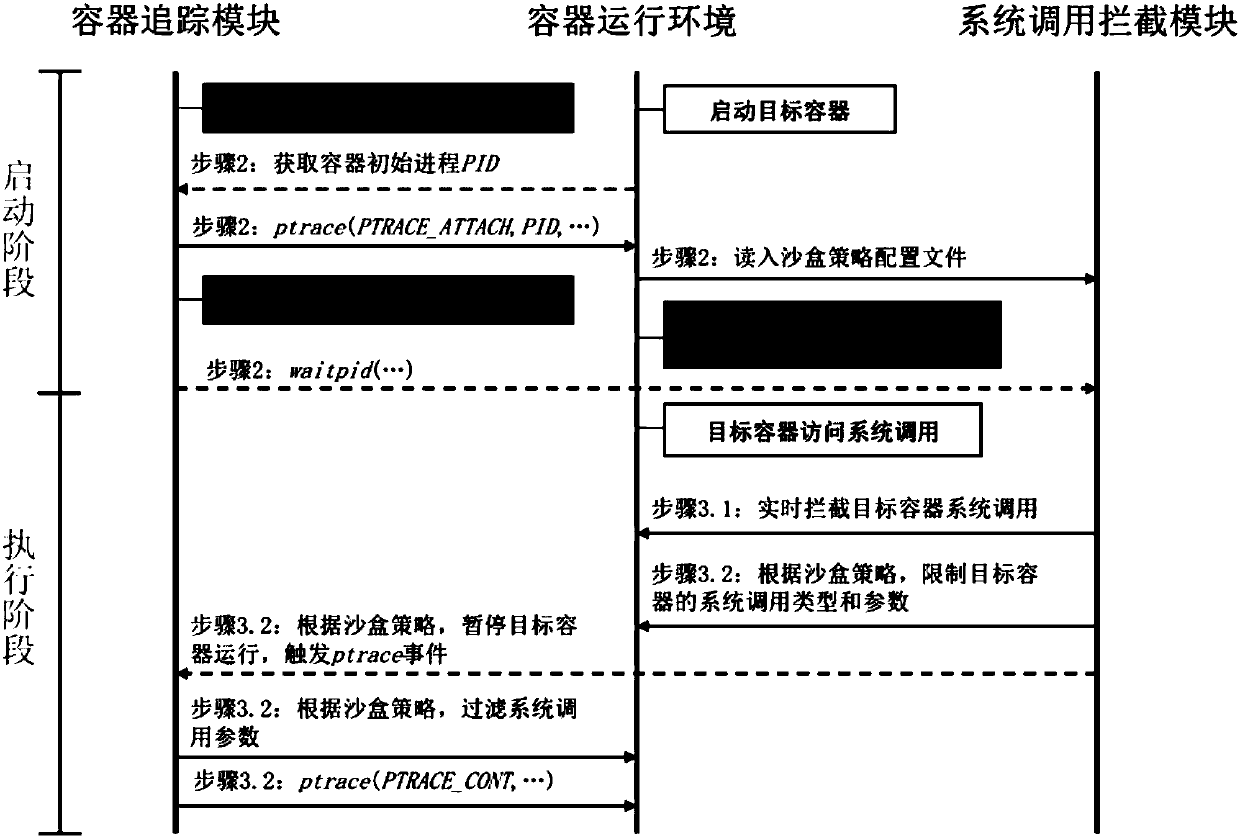
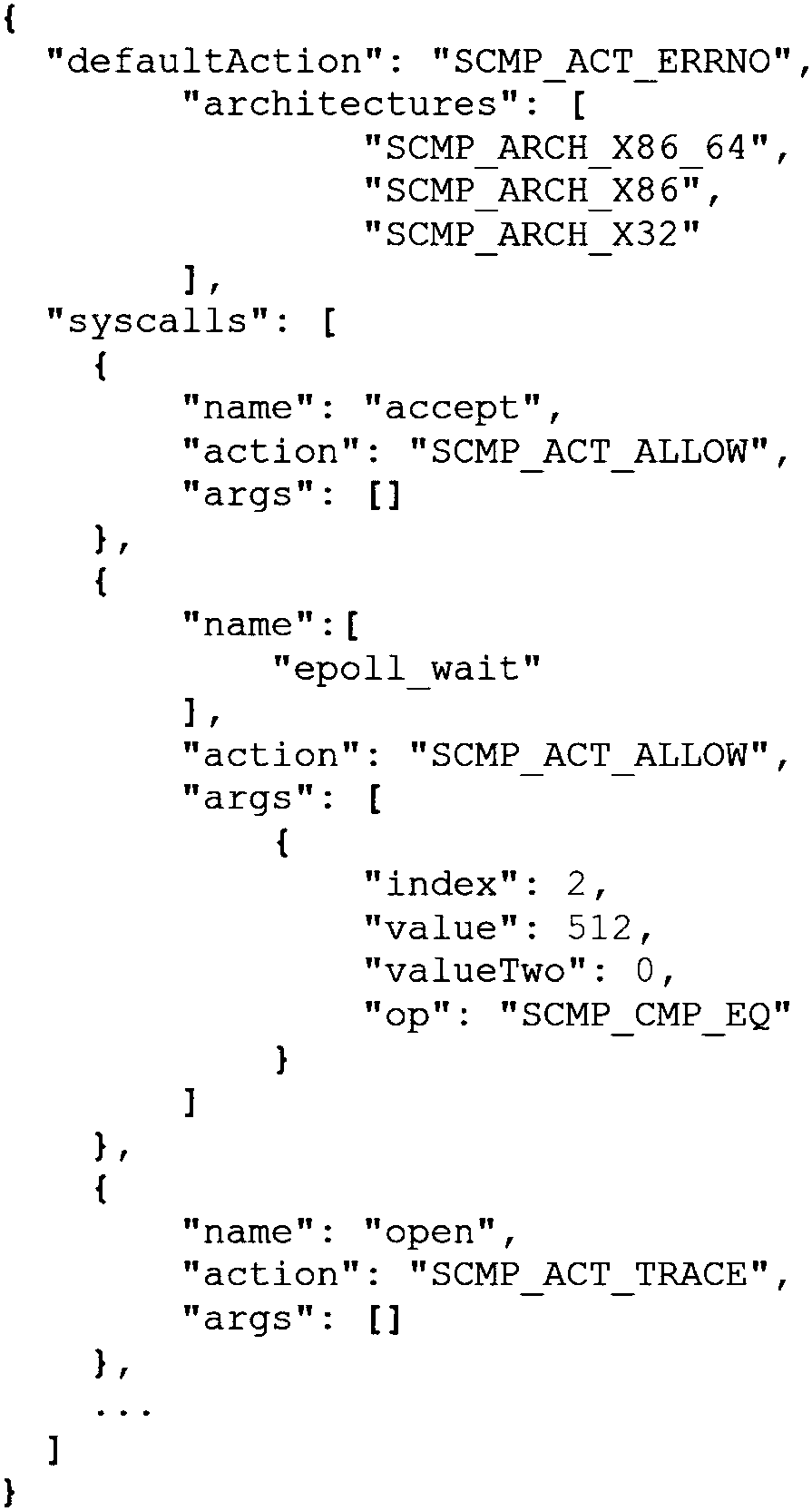
Execution method for fine-grained sandbox strategy of Linux containers
The invention provides an execution method for the fine-grained sandbox strategy of Linux containers. System calling behaviors of the Linux containers are limited, attack surfaces are reduced, and safe reinforcing of the Linux containers is achieved. The method includes the steps that a container tracking module calls an interface by calling a ptrace system, running of target containers is tracked, and according to the rule defined by the sandbox strategy, system calling access with character-string-type parameters is filtered. A system calling intercepting module intercepts the system callingaccess of the garget containers in real time by employing the seccomp / BPF technology, and according to the rule defined by the sandbox strategy, the system calling types and system calling access with non-character-string-type parameters are filtered.
Owner:ZHEJIANG UNIV
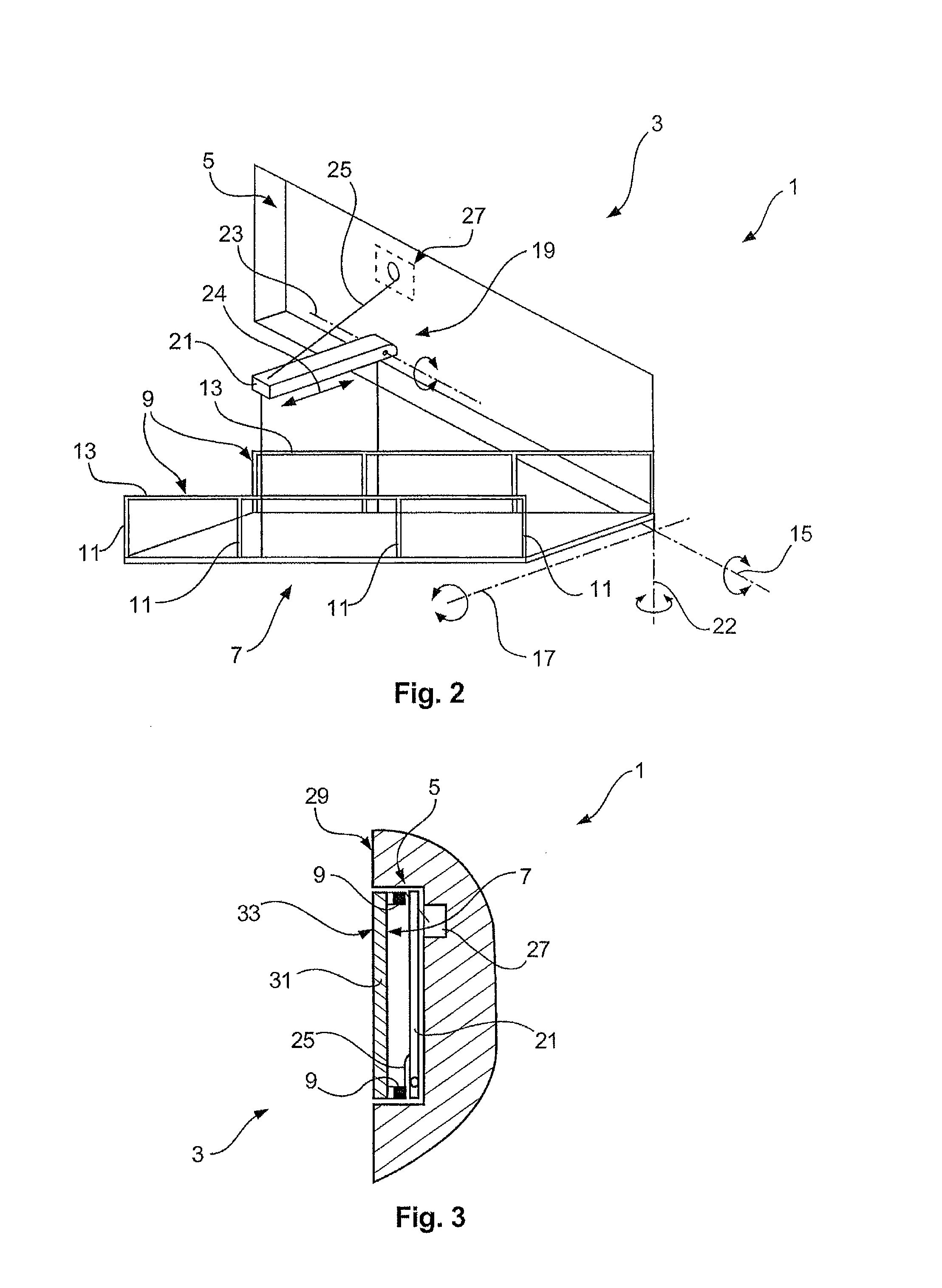
Ship and gangway for the same
ActiveUS8950353B2Reduce air resistanceReduce attack surfaceCargo handling apparatusPropulsion based emission reductionMarine engineering
The invention relates to a ship, in particular a freight ship, comprising an outer wall and a gangway for embarking and disembarking the ship, which can be moved backwards and forwards between an embarking / disembarking position and a stored position when the ship is being driven. The invention also relates to a ship in which the gangway comprises a base having a lower surface which, when said gangway is in the stored position, is flush with the surface of the outer wall. The invention also relates to a gangway for embarking and disembarking a ship, which is embodied according to the claimed invention for use on a ship.
Owner:WOBBEN PROPERTIES GMBH
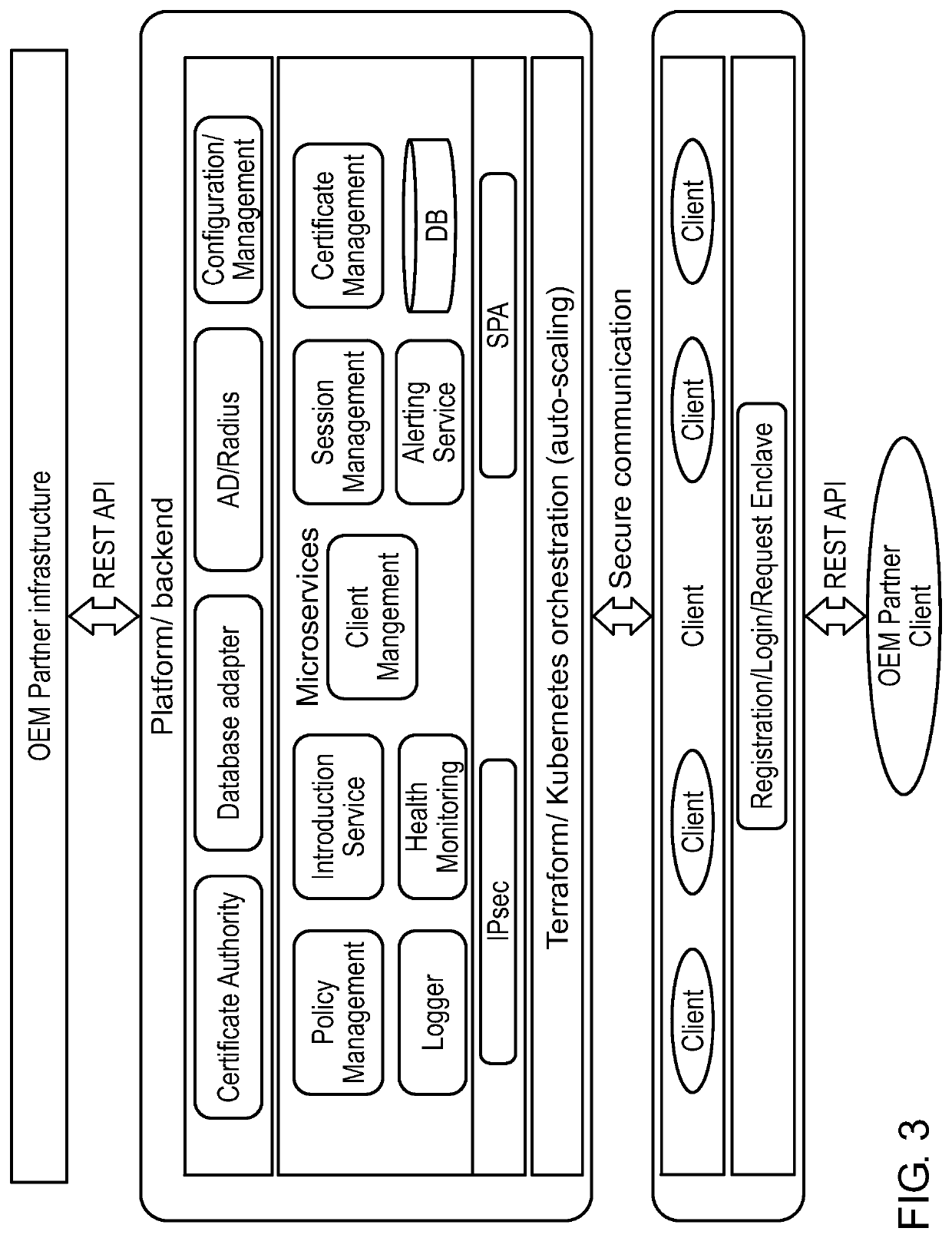
Systems and Methods for Improved Network Vulnerability Scanning and Reporting
ActiveUS20220247775A1Eliminate connectionMore control of network accessCharacter and pattern recognitionMachine learningOperational systemAttack
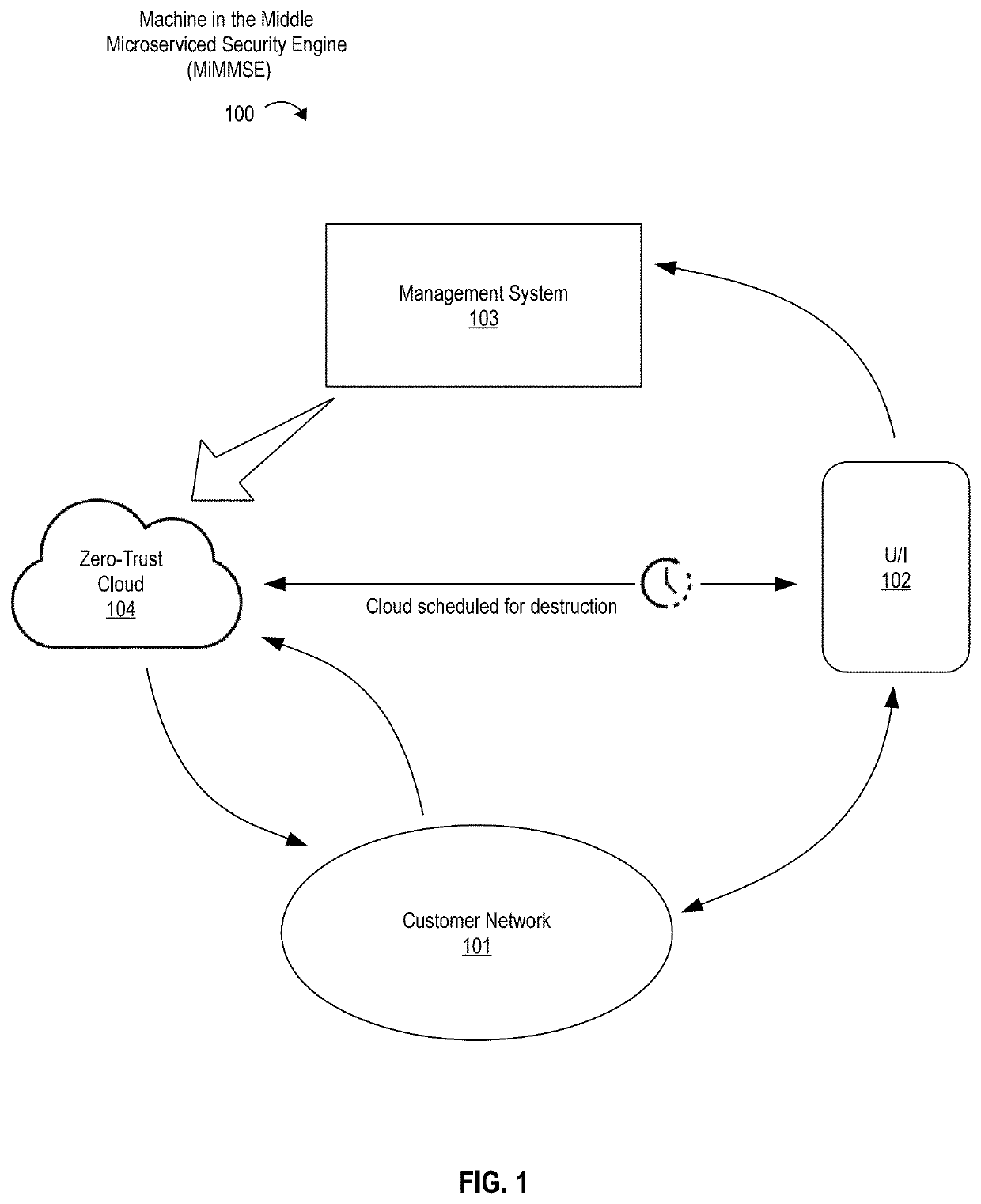
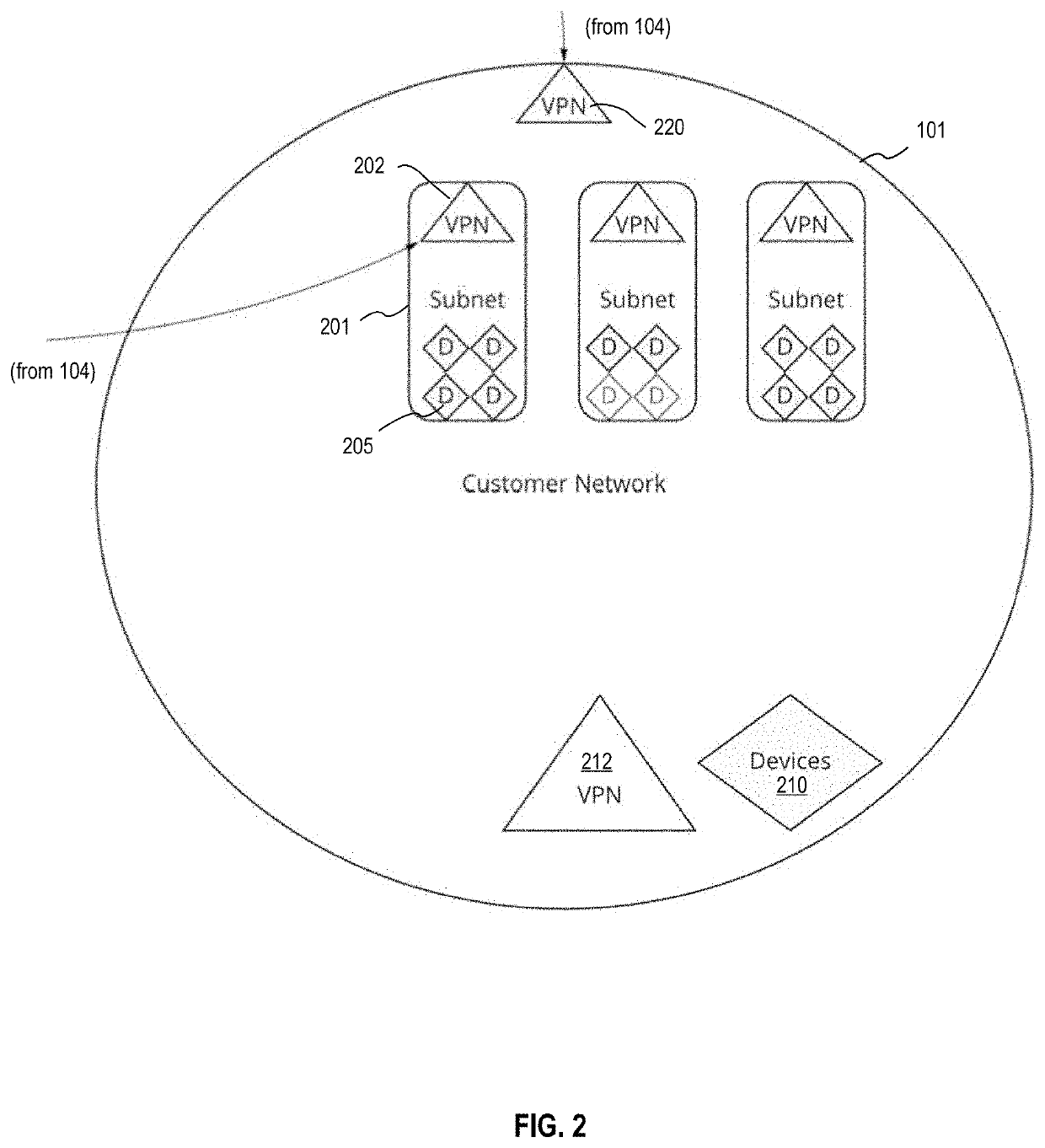
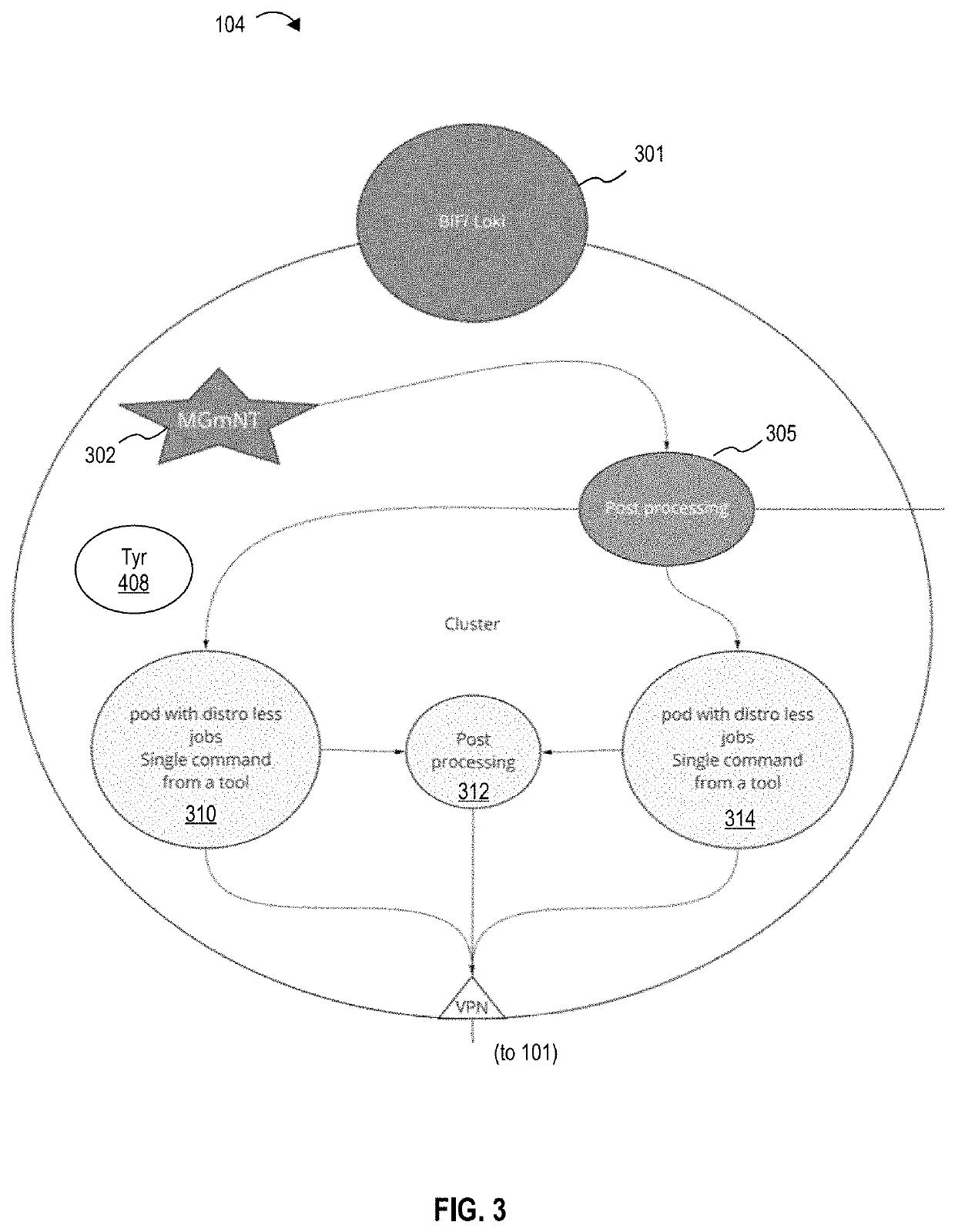
Vulnerability scanning systems and methods are provided for automatically performing the steps necessary for compliance testing and auditing of an organization's systems, and determining security posture in real time. A Machine-in-the-Middle Microserviced Security Engine (MiMMSE) is provided that provides one-way traffic for command execution and security improvement, management for automating services in OS containers, the elimination of multiple connections to services per client to give users more control of network access, total data destruction after each run to reduce attack surfaces, encryption over container services, reverse tunnel or VPN traffic between pods, clusters, and other separated networks, and machine learning (e.g., neural-network-based) maps for command execution order.
Owner:TECHSLAYERS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com