Systems and Methods for Improved Network Vulnerability Scanning and Reporting
a vulnerability and network technology, applied in the field of network and computer security, can solve the problems of not many resources available to assist organizations in complying with the bewildering array of standards, posing a significant financial and competitive risk, and not being able to perform rigorous and/or subjective assessments, so as to reduce the attack surface, reduce the number of connections, and improve the control of network access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016]The present subject matter relates to improved systems and methods for network vulnerability scanning, reporting, and compliance. As a preliminary matter, it will be understood that the following detailed description is merely exemplary in nature and is not intended to limit the inventions or the application and uses of the inventions described herein. Furthermore, there is no intention to be bound by any theory presented in the preceding background or the following detailed description. In the interest of brevity, conventional techniques and components related to network security and the operation of network components may not, and need not, be described in detail herein.
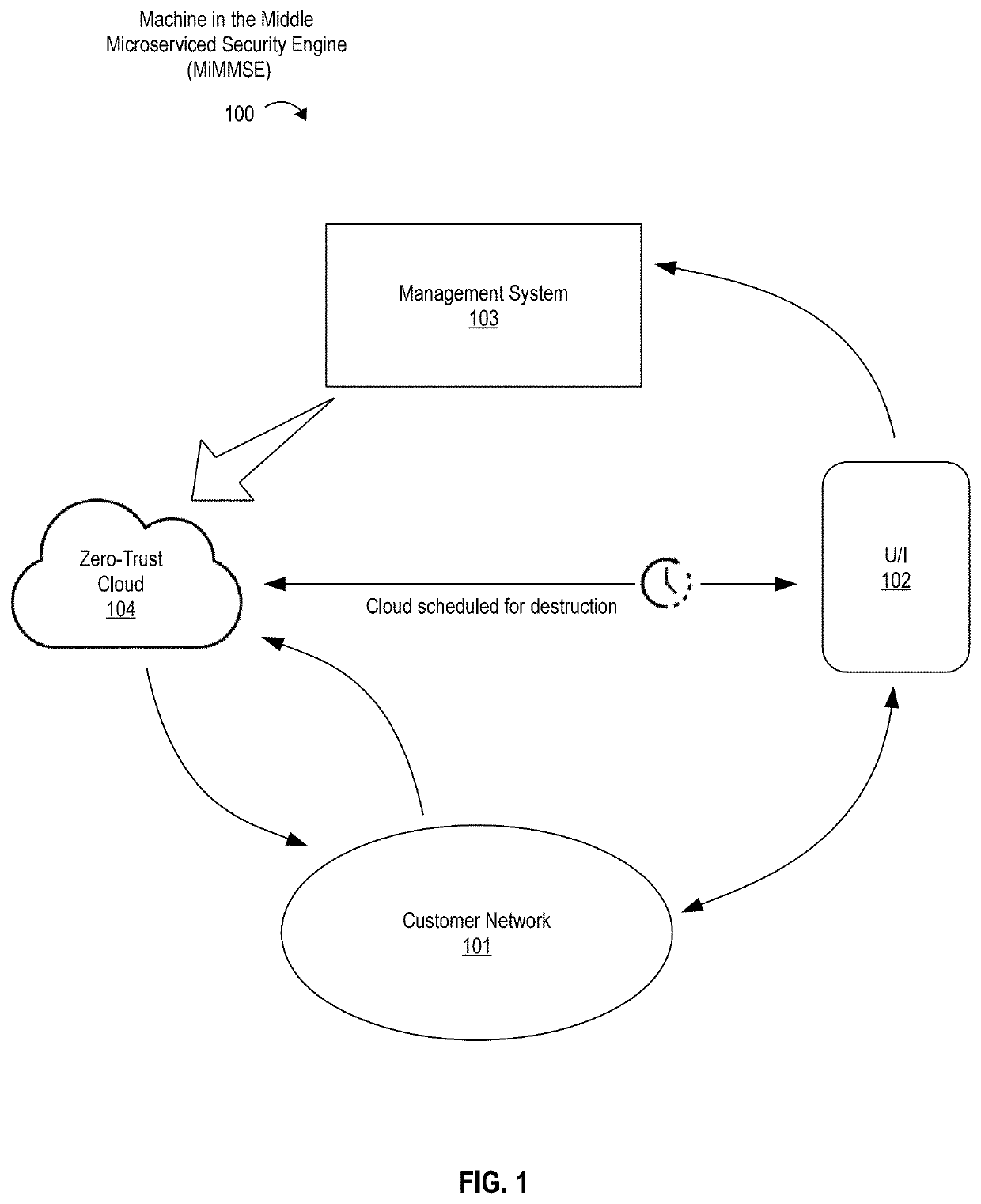
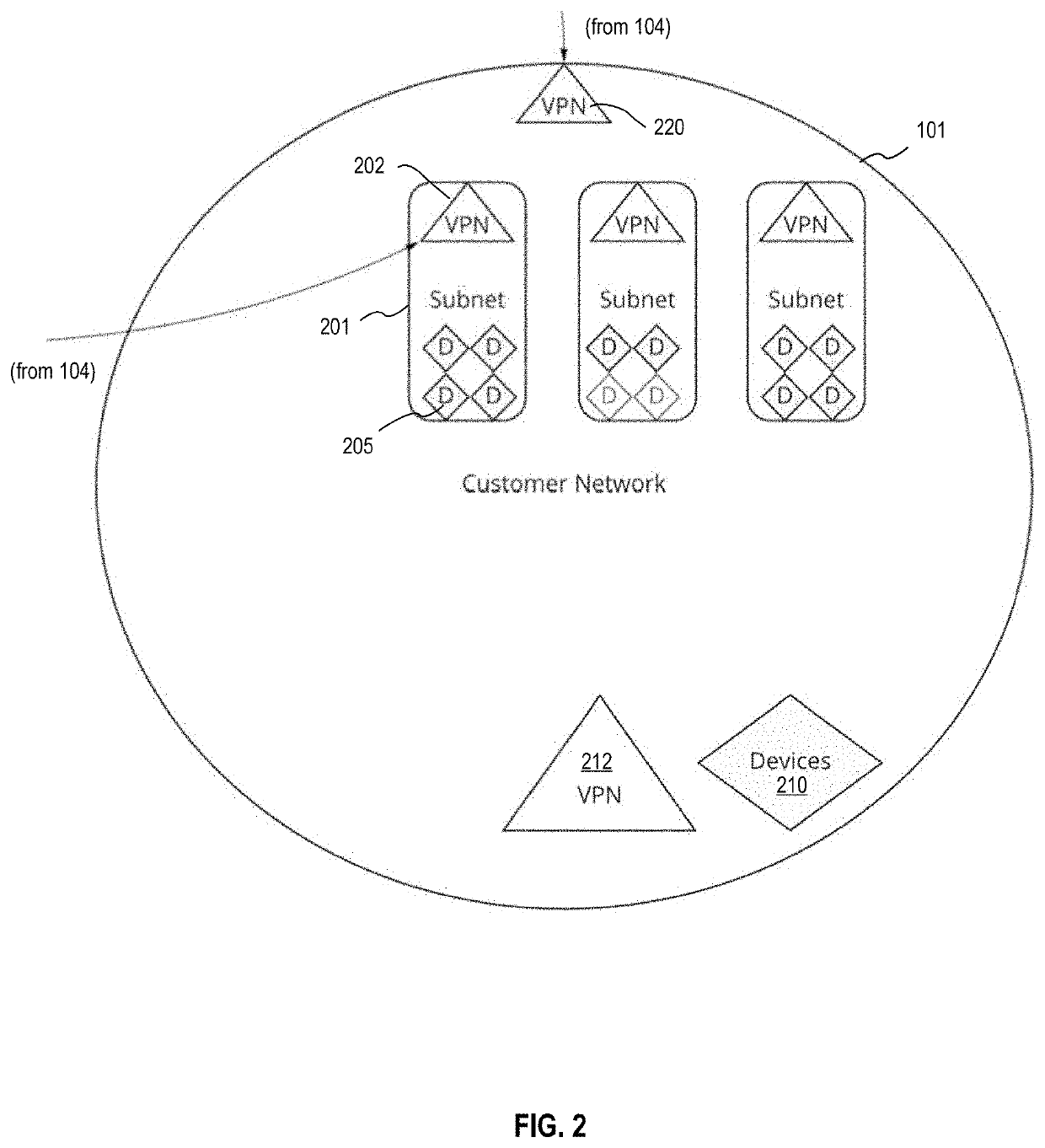
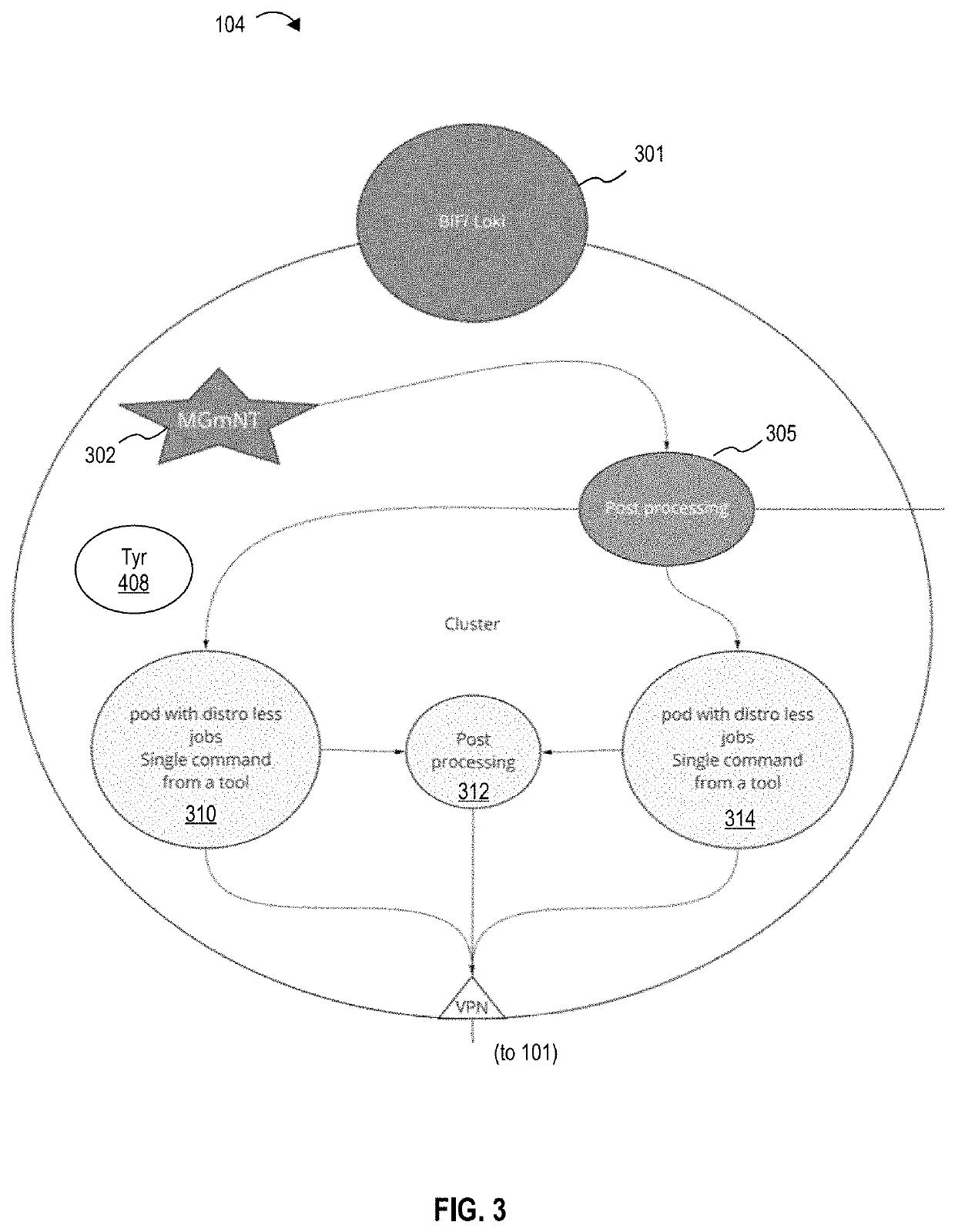
[0017]In general, a Machine-in-the-Middle Microserviced Security Engine (MiMMSE) system in accordance with various embodiments of the present includes a number of modules or subsystems that together form an improved, automated system for scanning and reporting vulnerabilities of a network and nodes present wi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com