Online rapid identity verification method based on Hash chain
An authentication method and hash chain technology, applied in the field of online rapid authentication, can solve the problems of difficulty in maintaining a trusted list and a large number of UAF clients, so as to reduce the attack surface, ensure security, and improve the verification speed. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
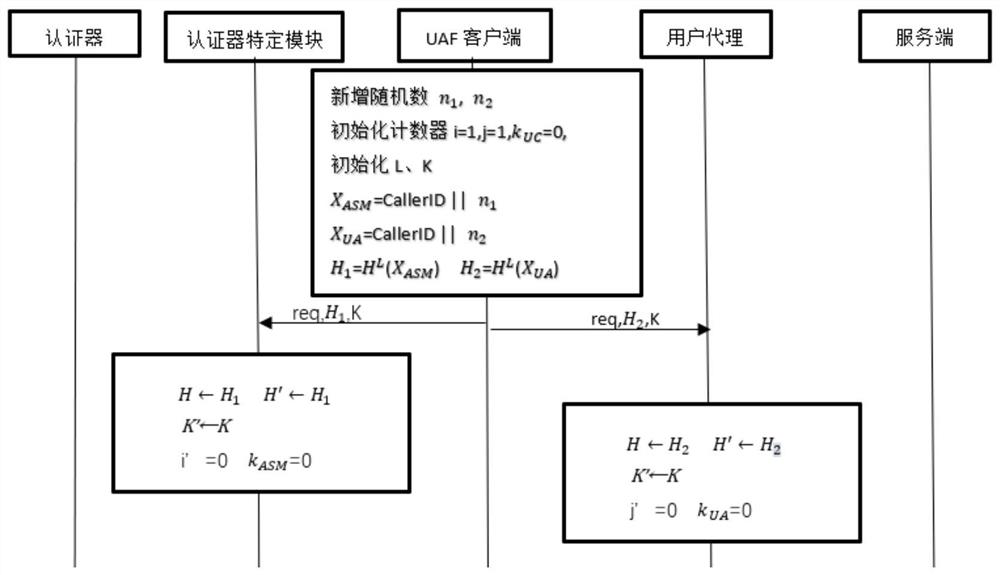
[0029] In order to further illustrate the technical means and effects adopted by the present invention to achieve the intended invention goal, the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0030] The present invention is an improvement to the existing online rapid identity authentication protocol FIDO, that is, by adding hash chain verification between the authenticator specific module, UAF client and user agent, the two processes of FIDO protocol registration and authentication are guaranteed to be normally executed Under the circumstances, it increases its security, reduces the attack surface of the protocol, and realizes fast online identity authentication using non-traditional text passwords.
[0031] refer to figure 1 , the implementation steps of this example are as follows:
[0032] Step 1, initialize each related entity of FIDO.
[0033] The existing online rapid identity authentica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com