Segmentation method for trust domain of virtual machine monitor
A virtual machine monitor and trust domain technology, applied in the field of cloud computing security, can solve the problems of consuming system memory resources, unable to resist overflow attacks, easy to enter a busy state, etc., to reduce startup time, easy configuration and auditing, and simple sharing the effect of the strategy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
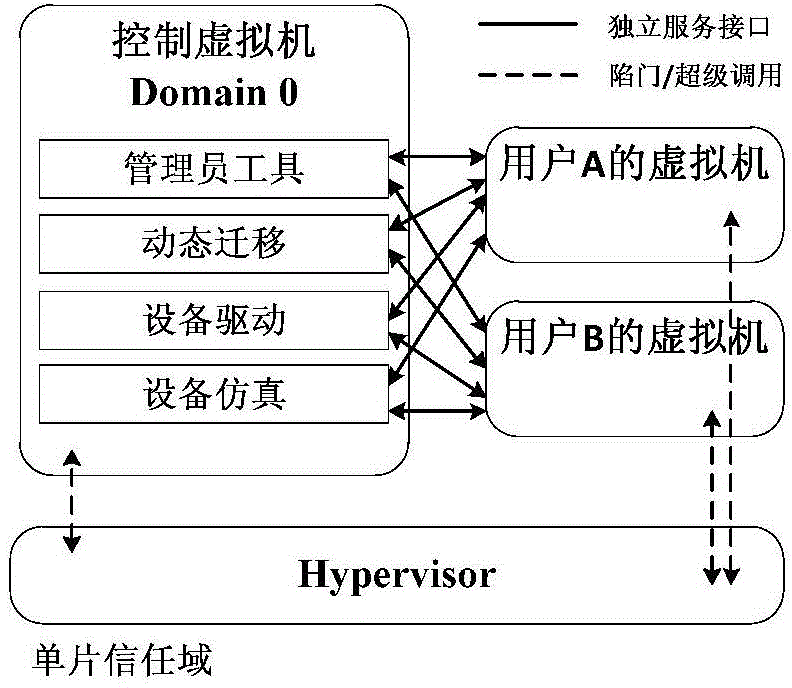
[0021] attached figure 1 It is a schematic diagram of a traditional single-chip trust domain. The control virtual machine shown in the figure has a complete operating system, has high-level system permissions similar to the Hypervisor, and is connected to the customer virtual machine through many interfaces to provide services for each customer virtual machine. In such a structure, the control virtual machine and the hypervisor form a single trust domain, which makes the control virtual machine vulnerable to hacker attacks, and once compromised, the entire system will suffer huge losses.
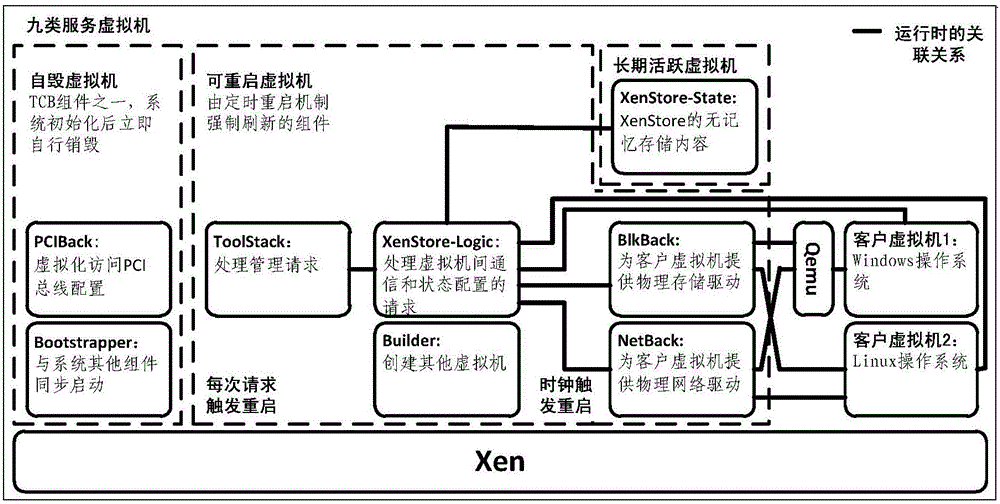
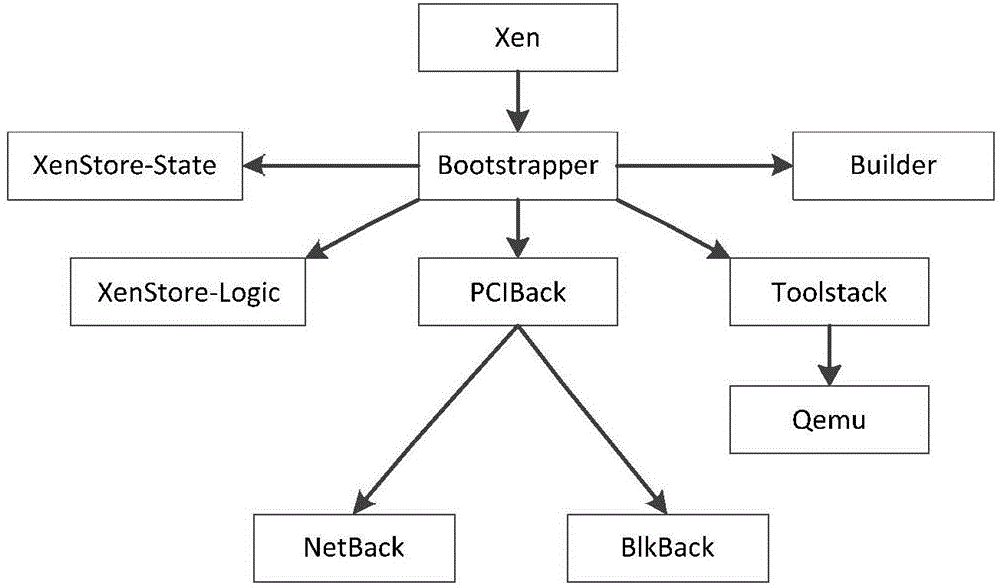
[0022] According to the function of the control virtual machine, the present invention decomposes it into nine types of service virtual machines. Each service virtual machine contains a single-purpose control logic and performs a single function. The essence of this is the trust domain of the virtual machine monitor. was split. These nine types of service virtual machines include: PCIBack (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com